Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1046 results about "Resources of a Resource" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
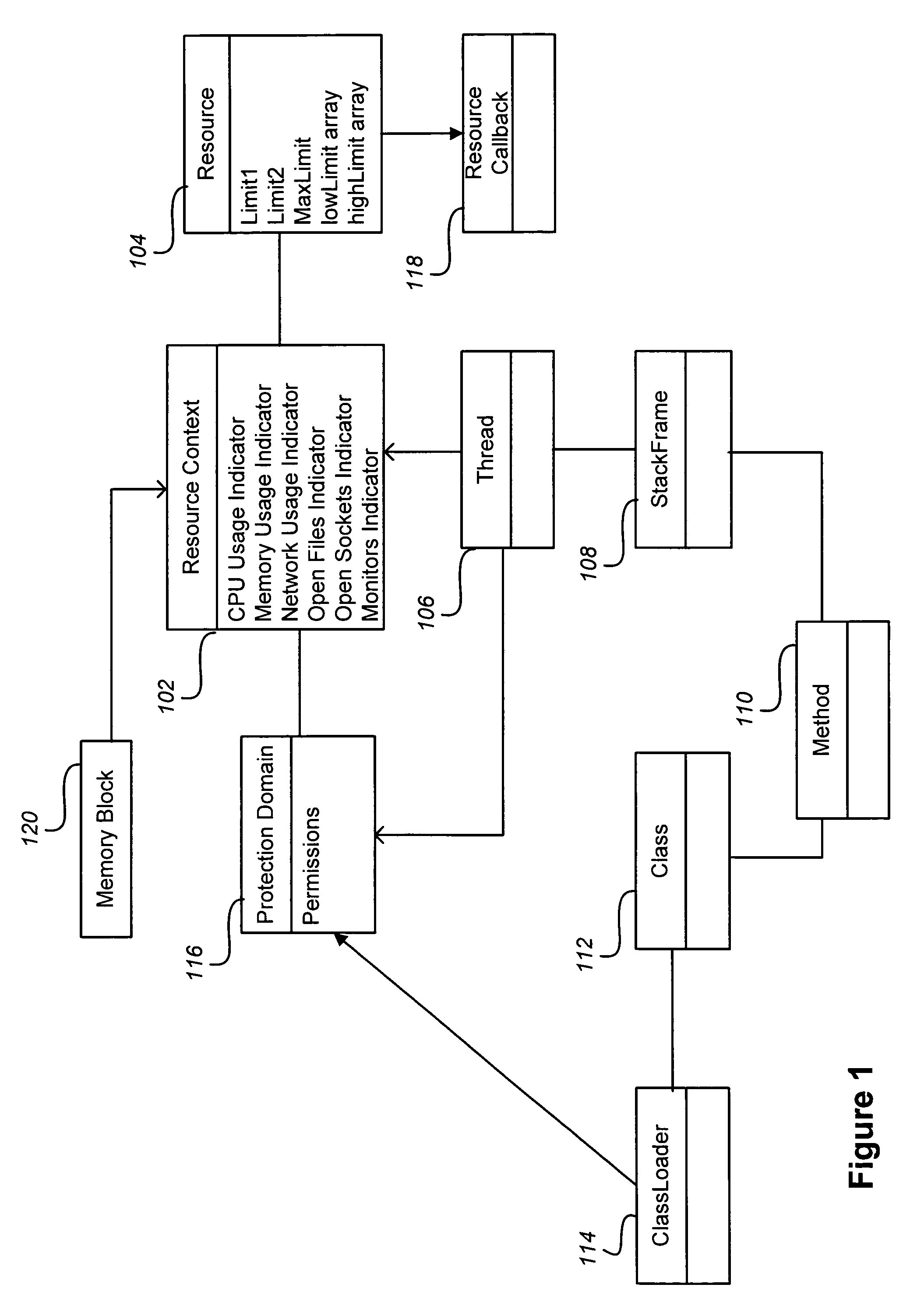
Resources of a Resource (ROR) is an XML format for describing the content of an internet resource or website in a generic fashion so this content can be better understood by search engines, spiders, web applications, etc. The ROR format provides several pre-defined terms for describing objects like sitemaps, products, events, reviews, jobs, classifieds, etc. The format can be extended with custom terms.
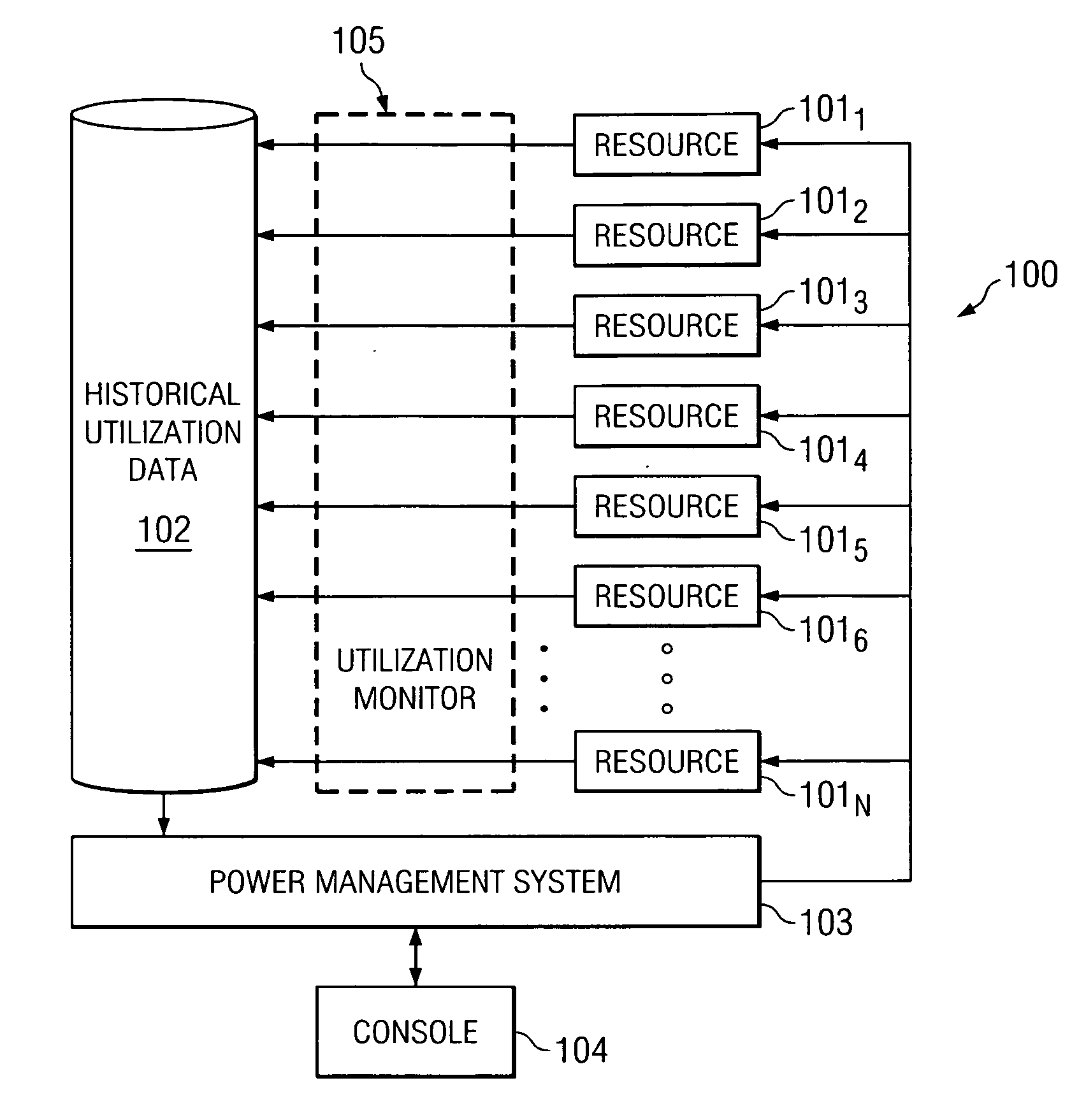
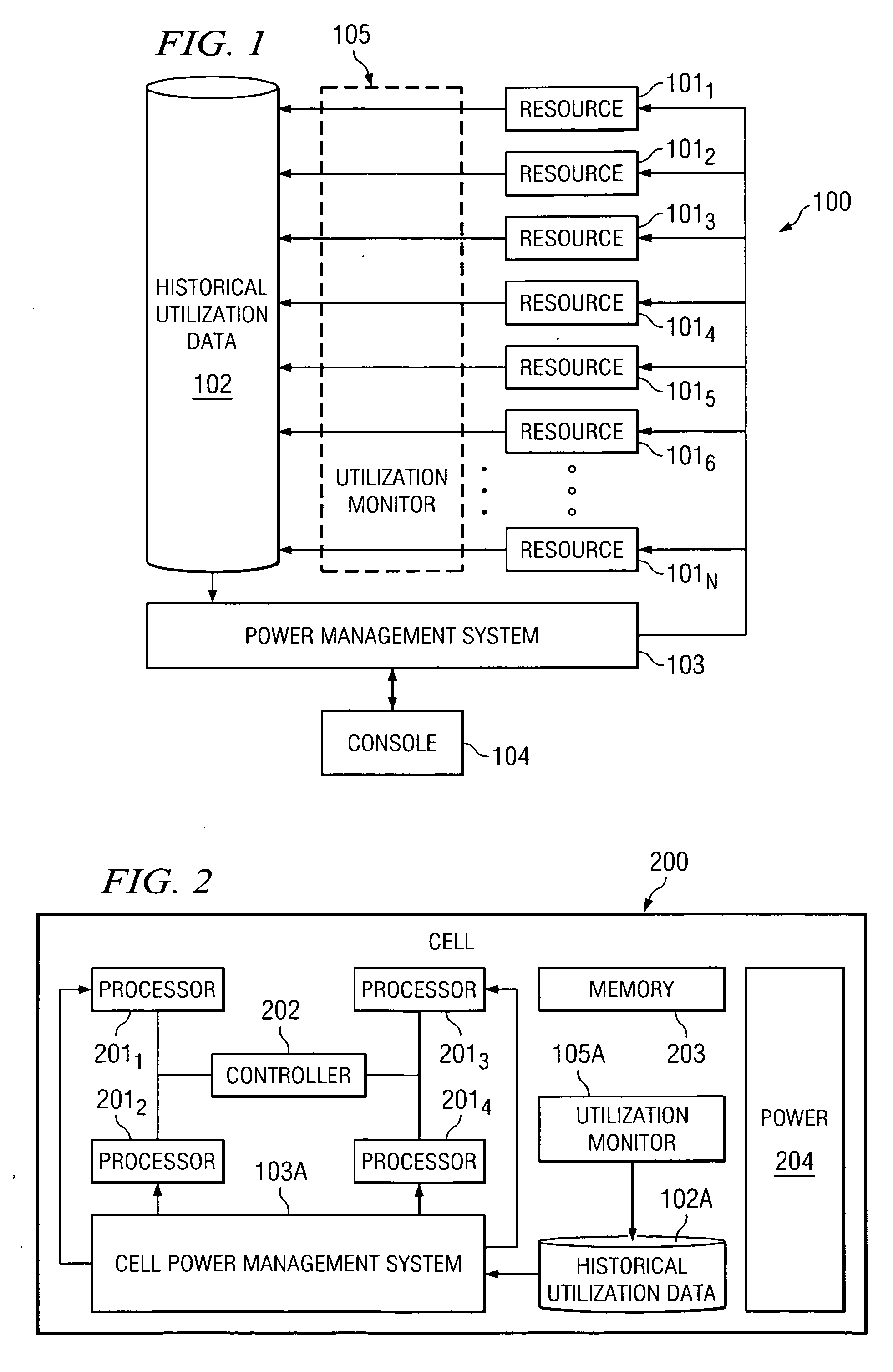
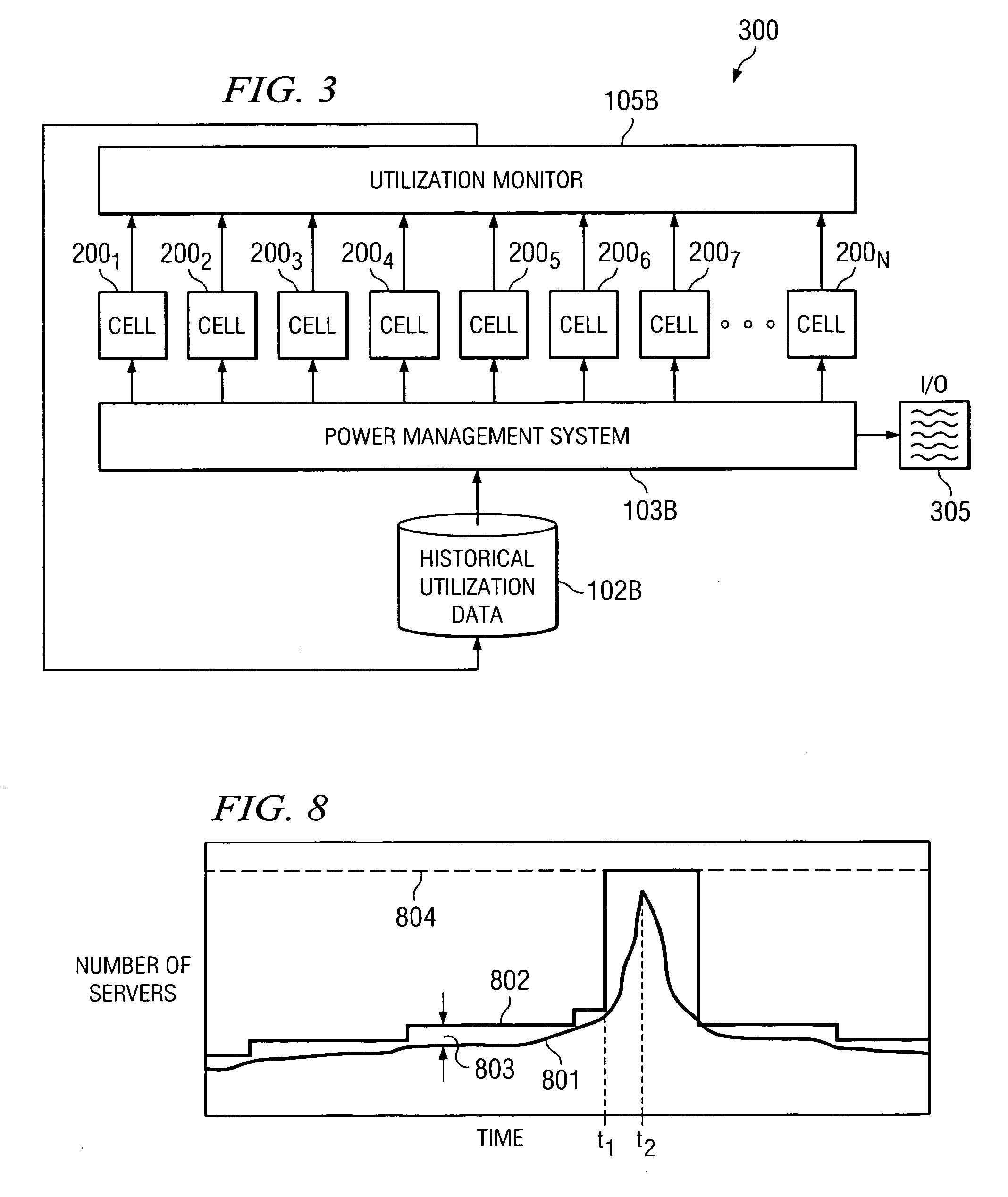
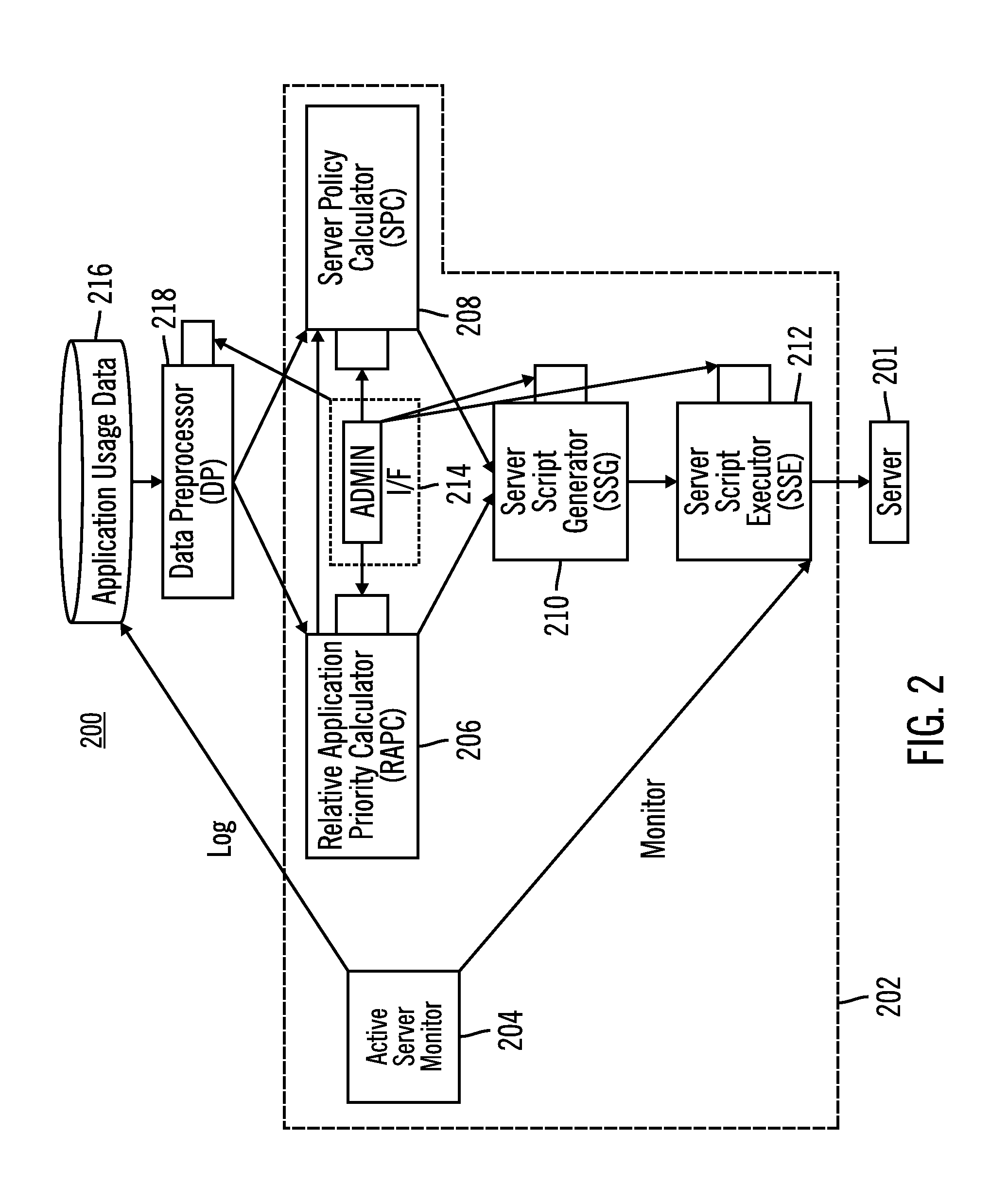
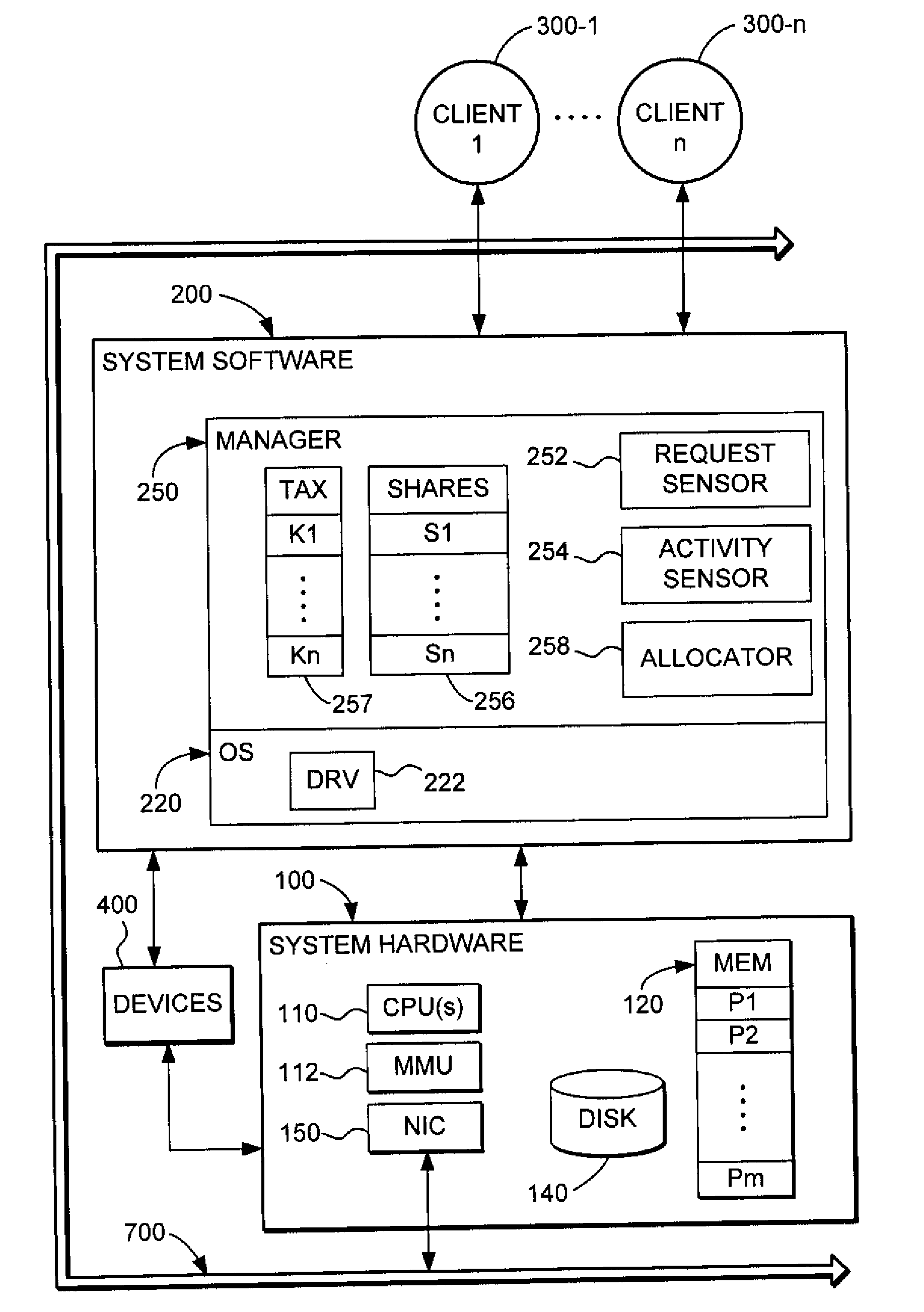
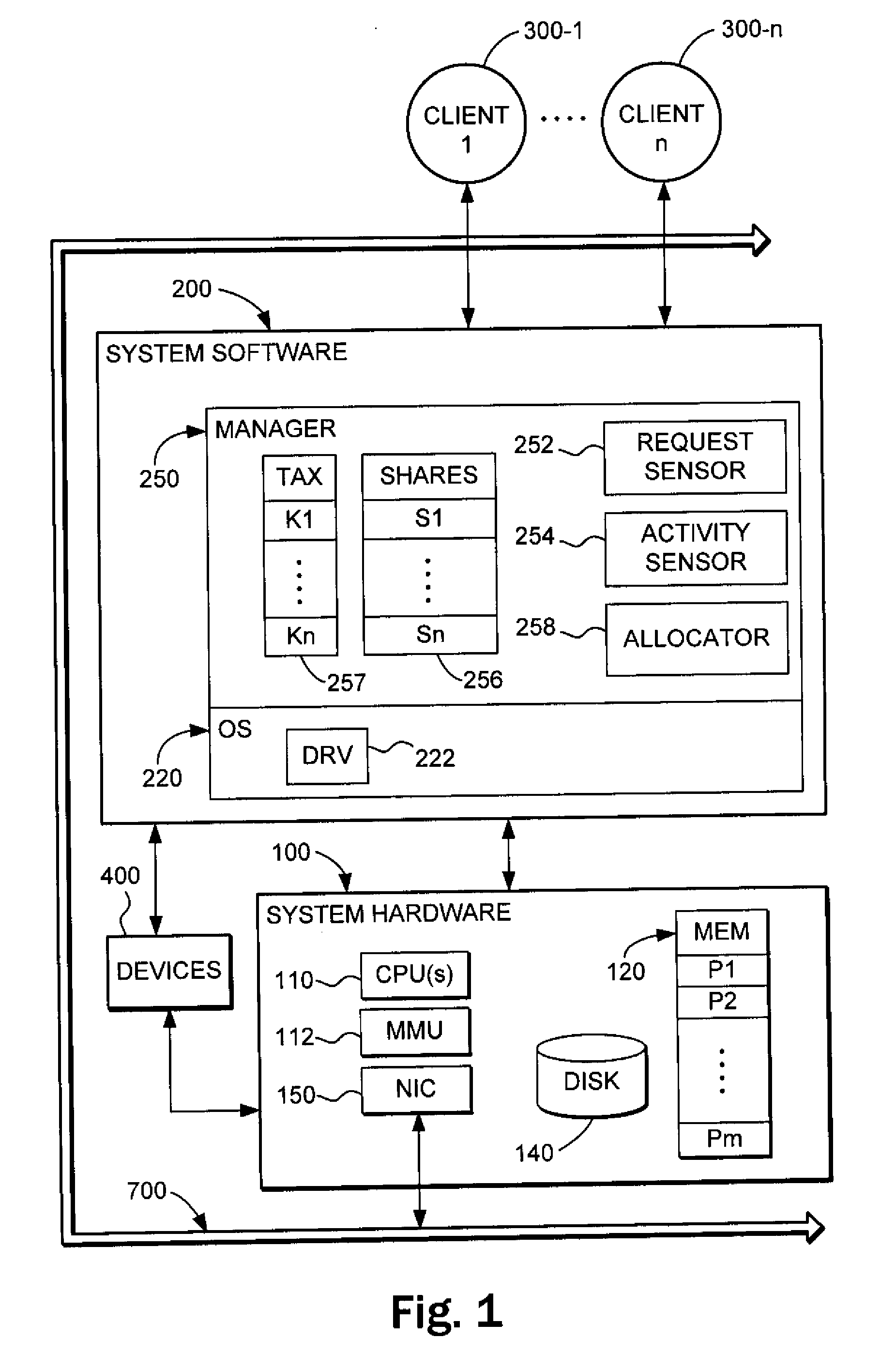
System and method for controlling power to resources based on historical utilization data
ActiveUS20060184287A1Energy efficient ICTMechanical power/torque controlResource basedSystem configuration
A method comprises collecting utilization data for a resource, and predicting by a power management system, based on the collected utilization data, future utilization of the resource. The method further comprises controlling, by the power management system, power to the resource, based at least in part on the predicted future utilization of the resource. In one embodiment, the utilization data is collected for a plurality of resources that are operable to perform tasks, and the method further comprises determining, by the power management system, how many of the resources are needed to provide a desired capacity for servicing the predicted future utilization of the resources for performing the tasks. The method further comprises configuring, by the power management system, ones of the resources exceeding the determined number of resources needed to provide the desired capacity in a reduced power-consumption mode.
Owner:MOSAID TECH
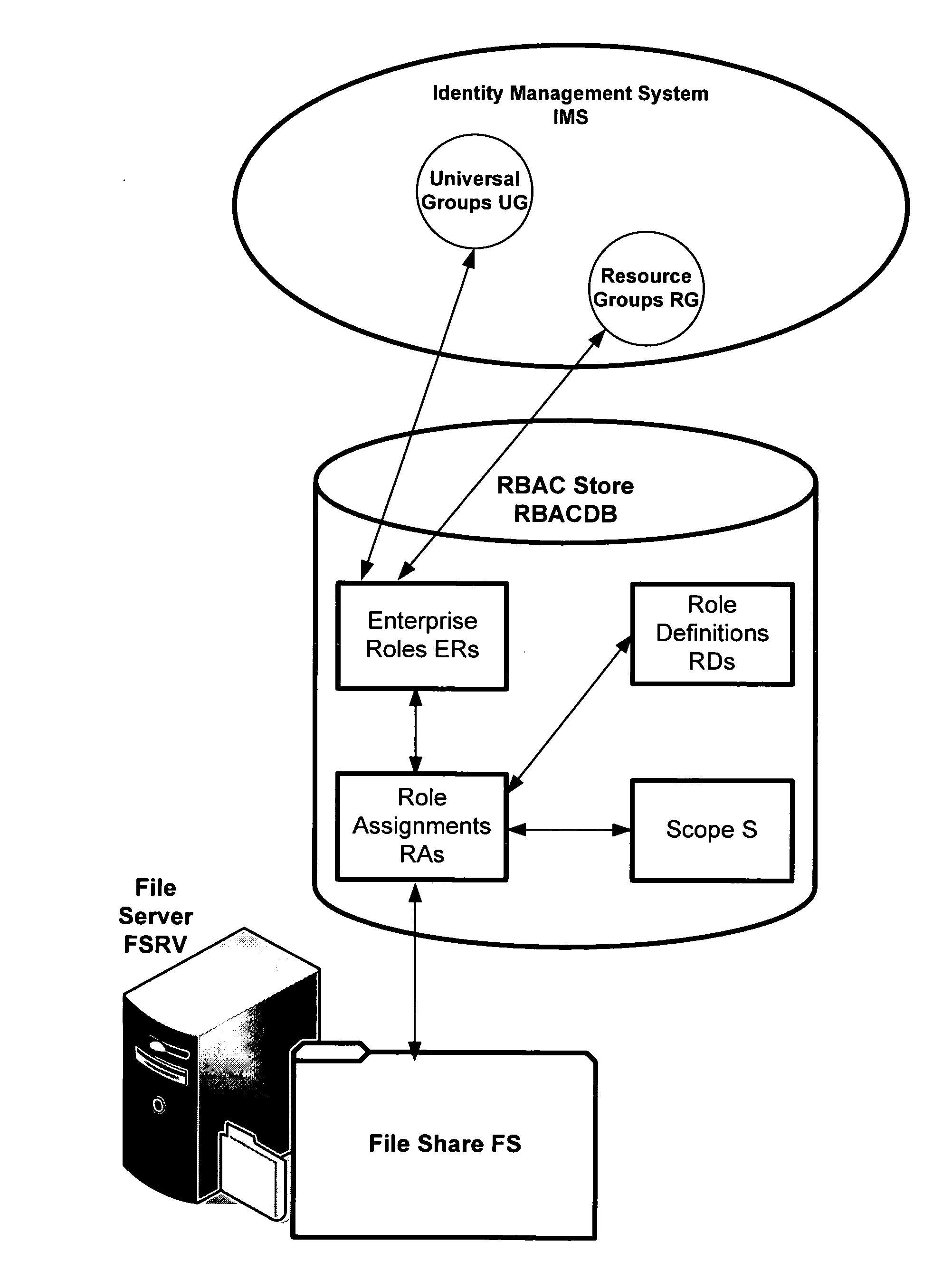
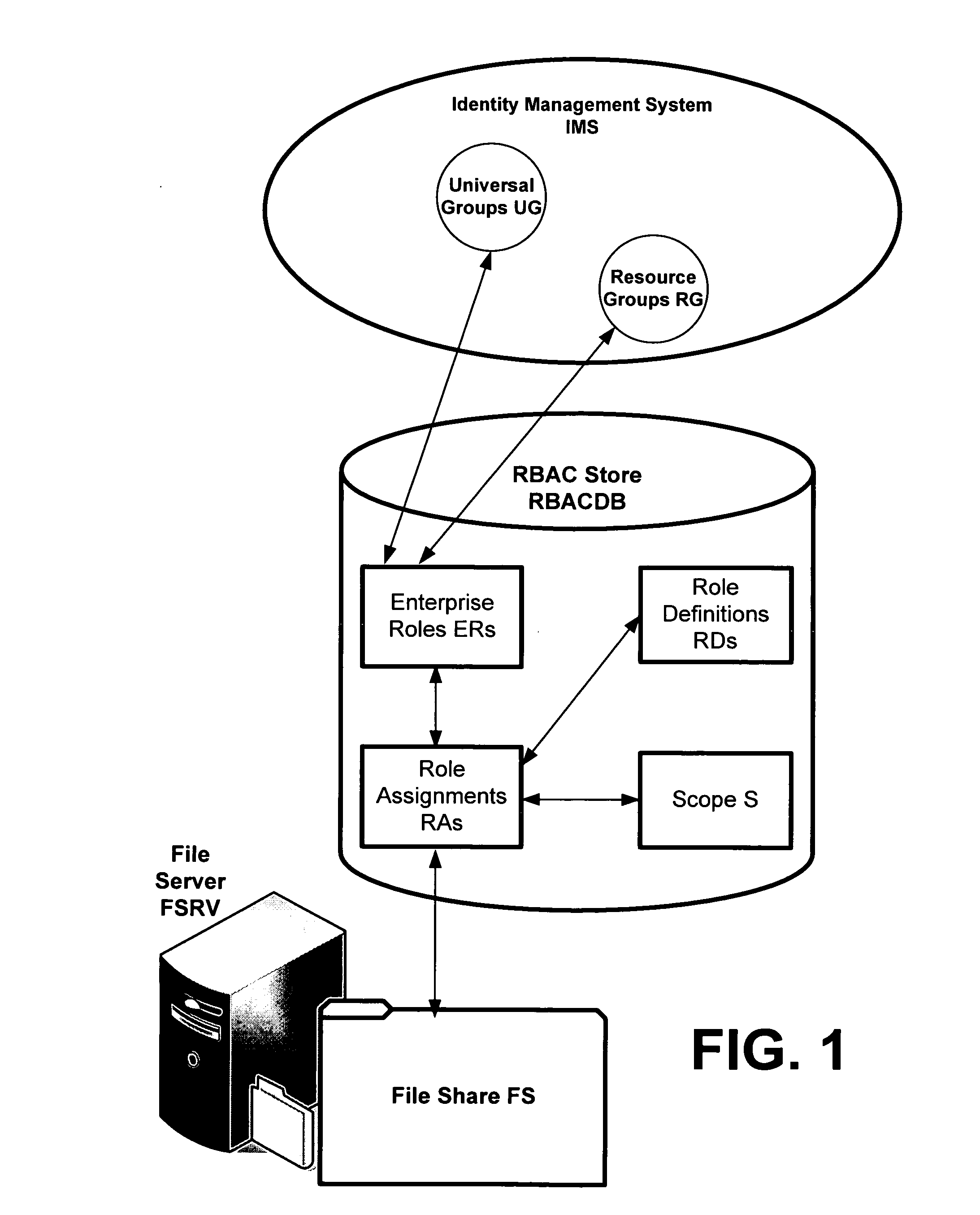
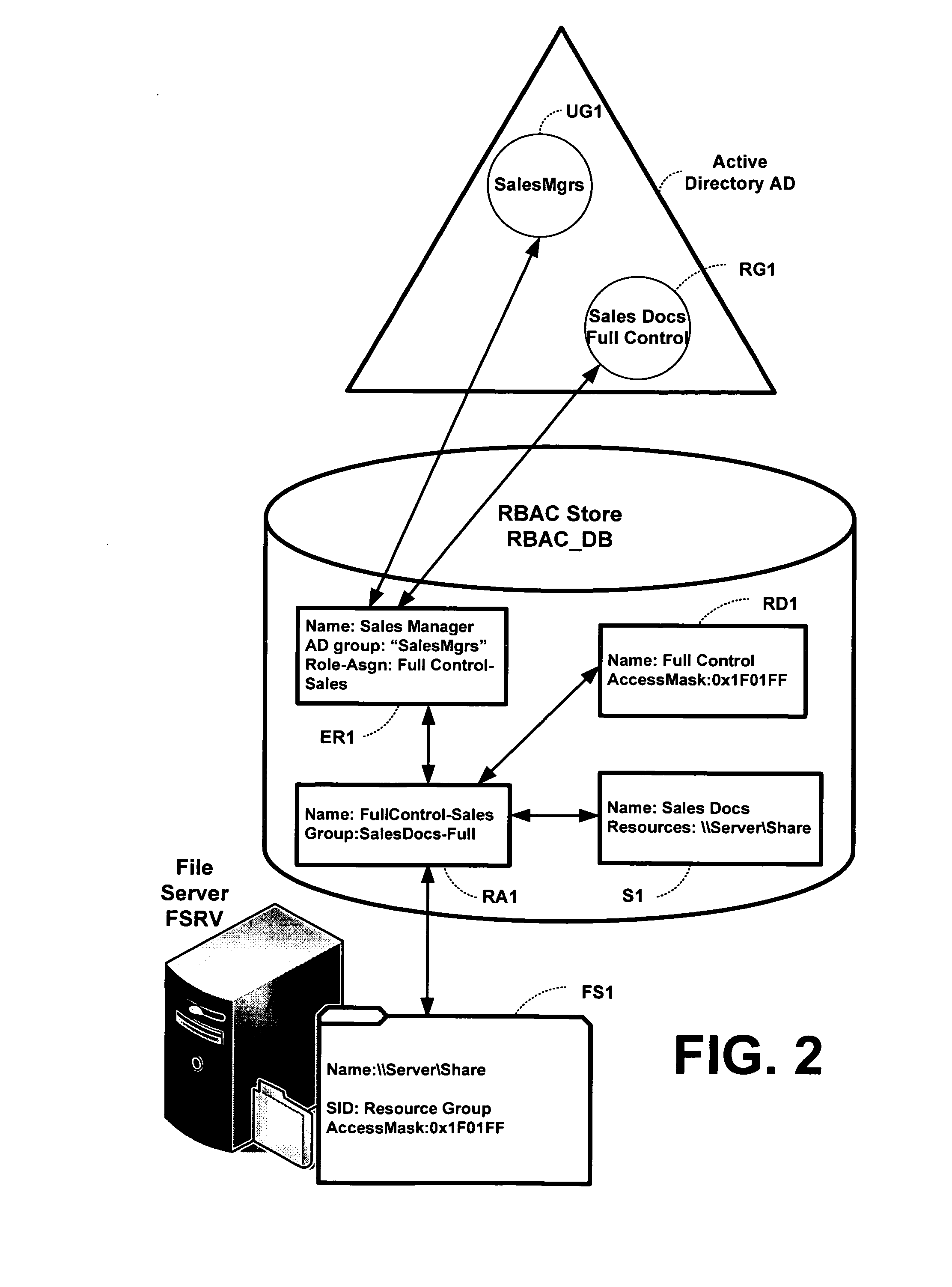
Translating role-based access control policy to resource authorization policy
ActiveUS20070283443A1Program control using stored programsDigital data processing detailsFile systemManaged object
Translation of role-based authoring models for managing RBAC “roles” to resource authorization policy (RAP), such as ACL-based applications, is provided. A generic RBAC system is defined from which mappings to other authorization enforcement mechanism make possible the translation of RBAC “roles” to resource authorization policies applied to resources managed by a resource manager, e.g., a file system resource manager. An implementation is described that uses Windows Authorization Manager as a storage mechanism and object model to manage object types and relationships translated from an RBAC system.
Owner:MICROSOFT TECH LICENSING LLC
Autonomic definition and management of distributed appication information
ActiveUS20090125619A1Facilitates adoptionDigital computer detailsMultiprogramming arrangementsInformation processingInformation handling system
A method, information processing system, and computer program storage product for associating jobs with resource subsets in a job scheduler. At least one job class that defines characteristics associated with a type of job is received. A list of resource identifiers for a set of resources associated with the job class is received. A set of resources available on at least one information processing system is received. The resource identifiers are compared with each resource in the set of resources available on the information processing system. A job associated with the job class with is scheduled with a set of resources determined to be usable by the job based on the comparing.
Owner:DAEDALUS BLUE LLC
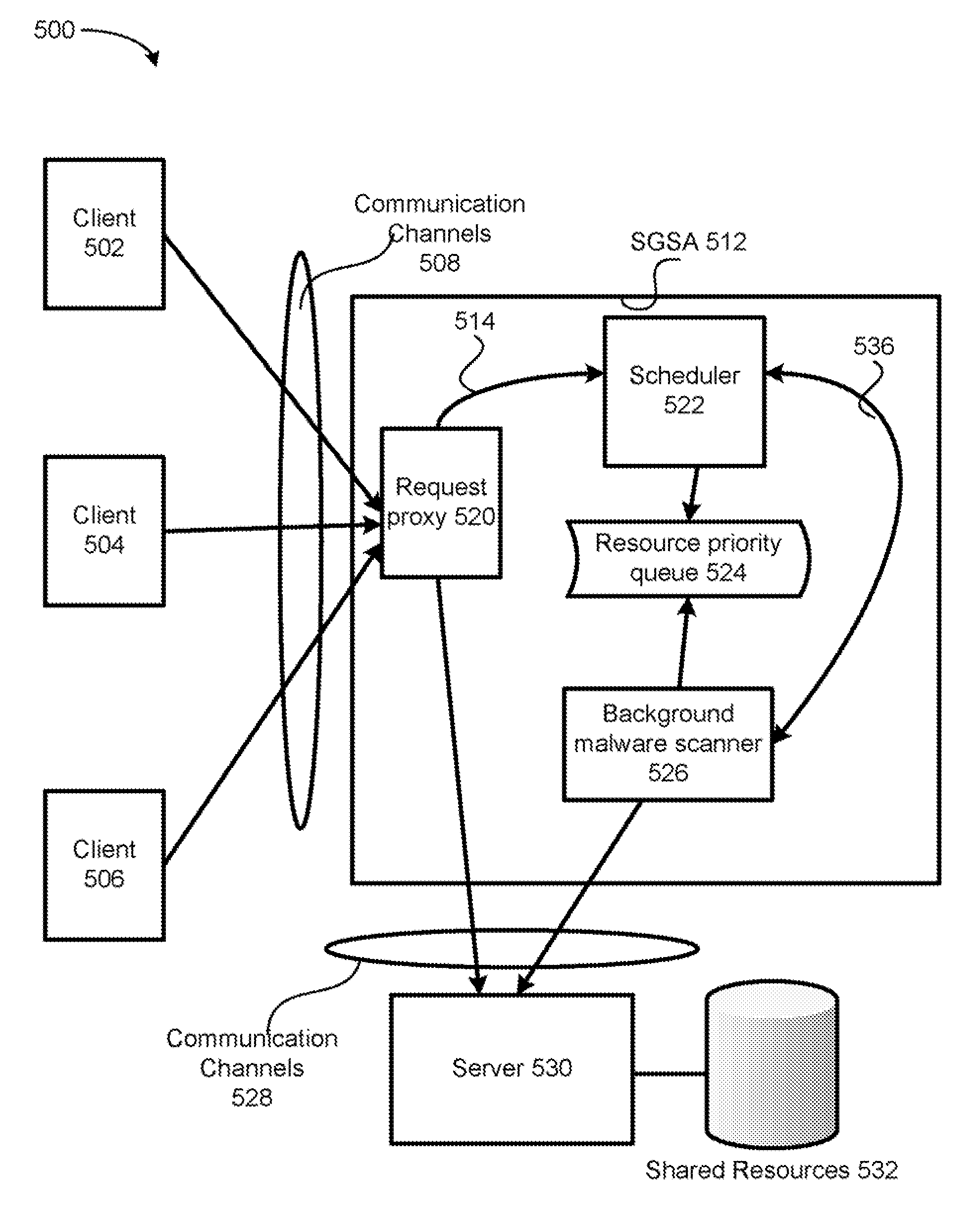
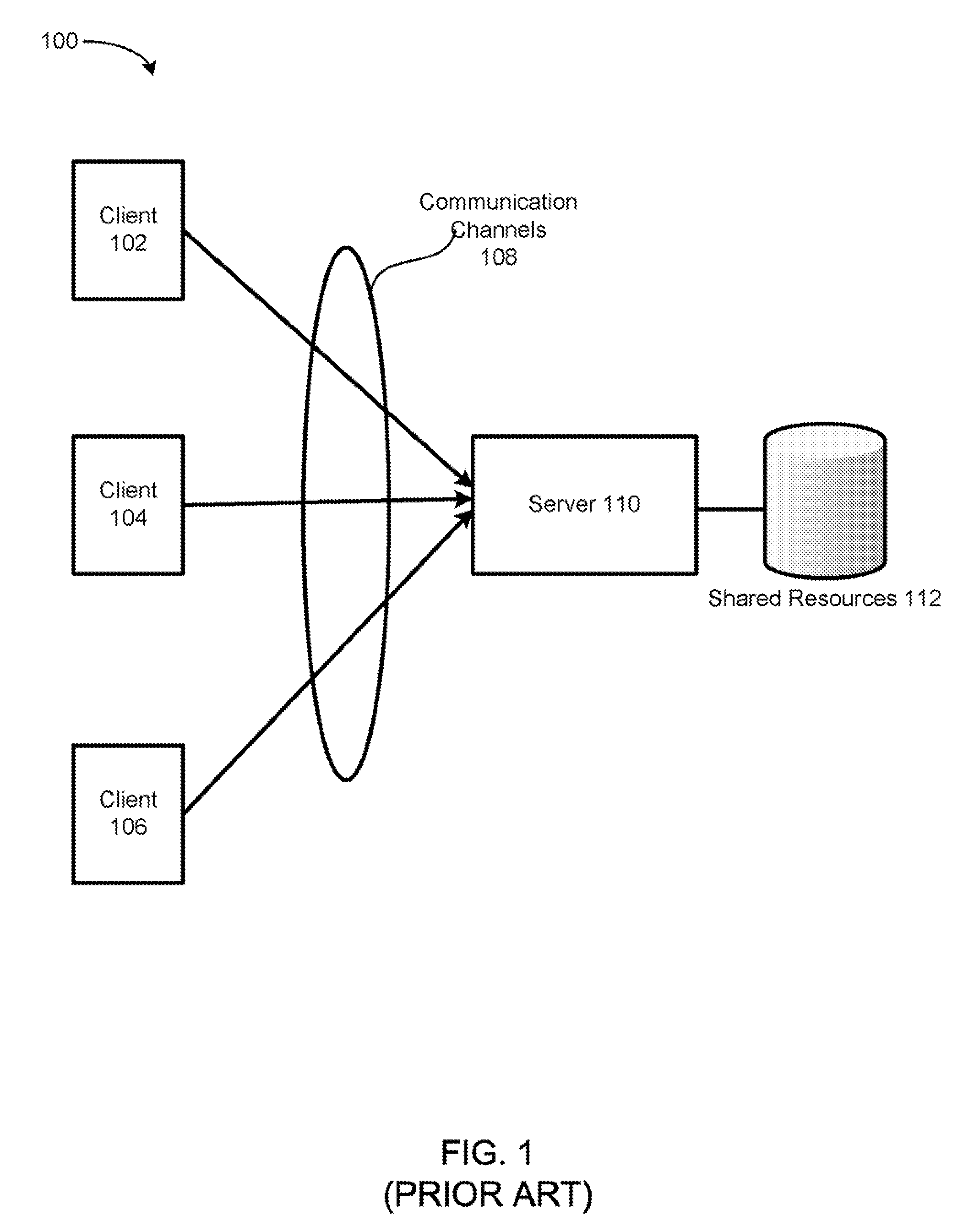
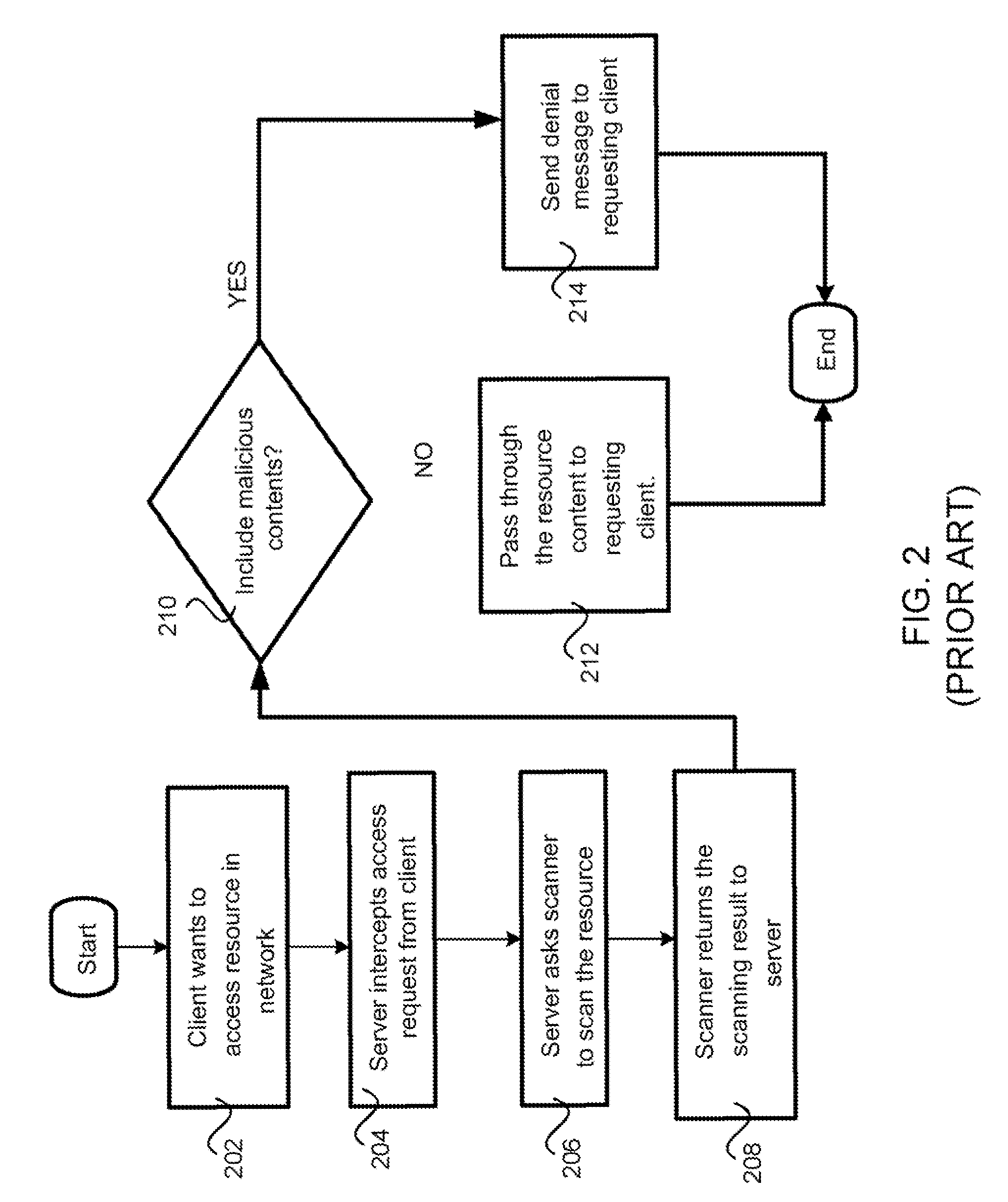
Scheduled gateway scanning arrangement and methods thereof
InactiveUS7836502B1Raise priorityMemory loss protectionError detection/correctionResource basedComputer science
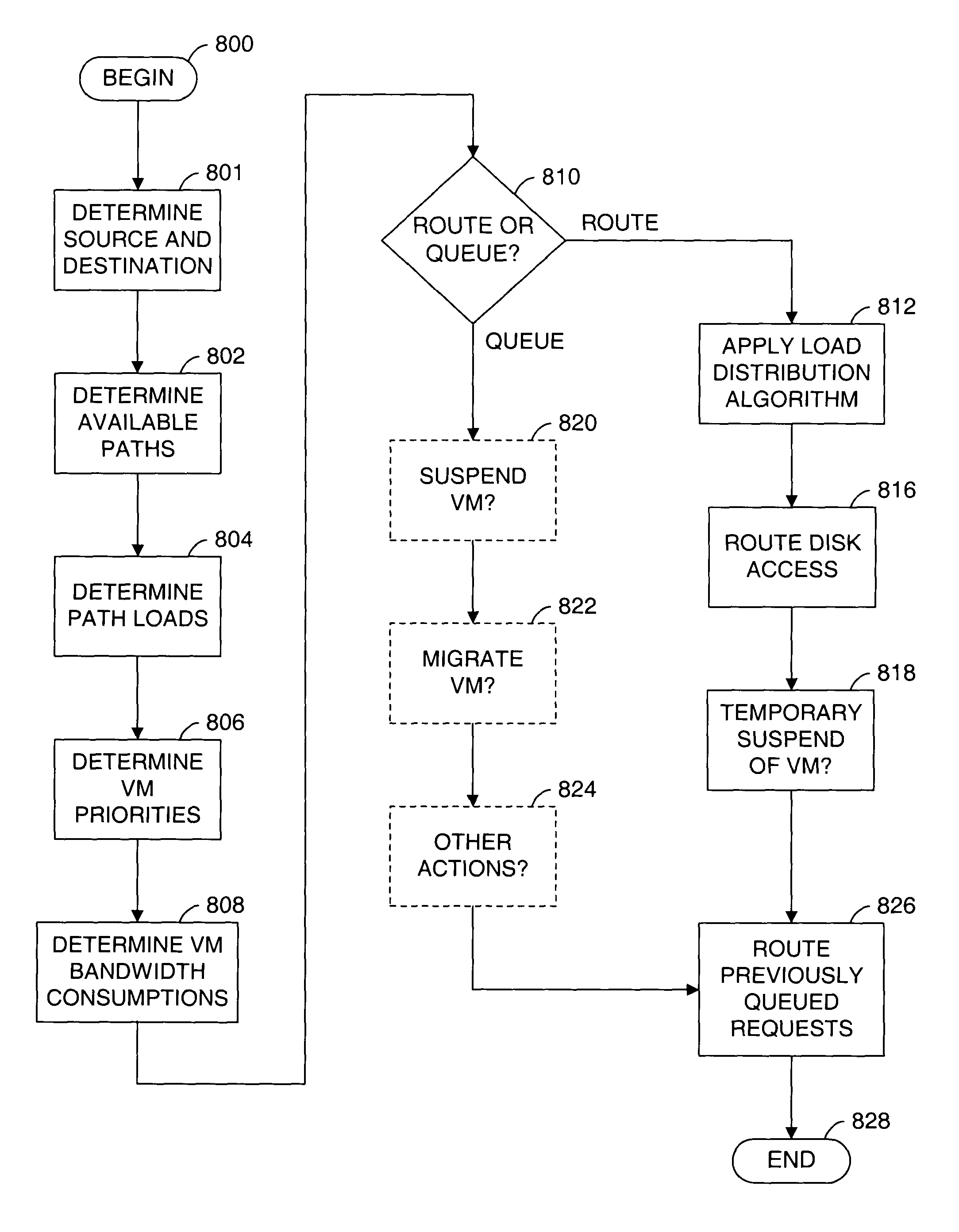
A method for performing content analysis of a plurality of resources is provided. The method includes performing background content scanning on the plurality of resources based on a resource priority queue. The method also includes storing already scanned resources of the plurality of resources in a scan result database. The method further includes receiving a first access request asynchronously with the scanning and the storing. The method yet also includes, if the first access request pertains to a given resource not contemporaneously designated as a satisfactory scan result according to the scan result database, granting the given resource a higher priority in the resource priority queue than resources remaining to be scanned in the plurality of resources, thereby enabling the given resource to be scanned ahead of the resources remaining to be scanned.
Owner:TREND MICRO INC
Resource allocation in computers
InactiveUS20080126547A1Digital computer detailsMultiprogramming arrangementsClient-sideResource allocation
A method and tangible medium embodying code for allocating resource units of an allocatable resource among a plurality of clients in a computer is described. In the method, resource units are initially distributed among the clients by assigning to each of the clients a nominal share of the allocatable resource. For each client, a current allocation of resource units is determined. A metric is evaluated for each client, the metric being a function both of the nominal share and a usage-based factor, the usage-based factor being a function of a measure of resource units that the client is actively using and a measure of resource units that the client is not actively using. A resource unit can be reclaimed from a client when the metric for that client meets a predetermined criterion.
Owner:VMWARE INC
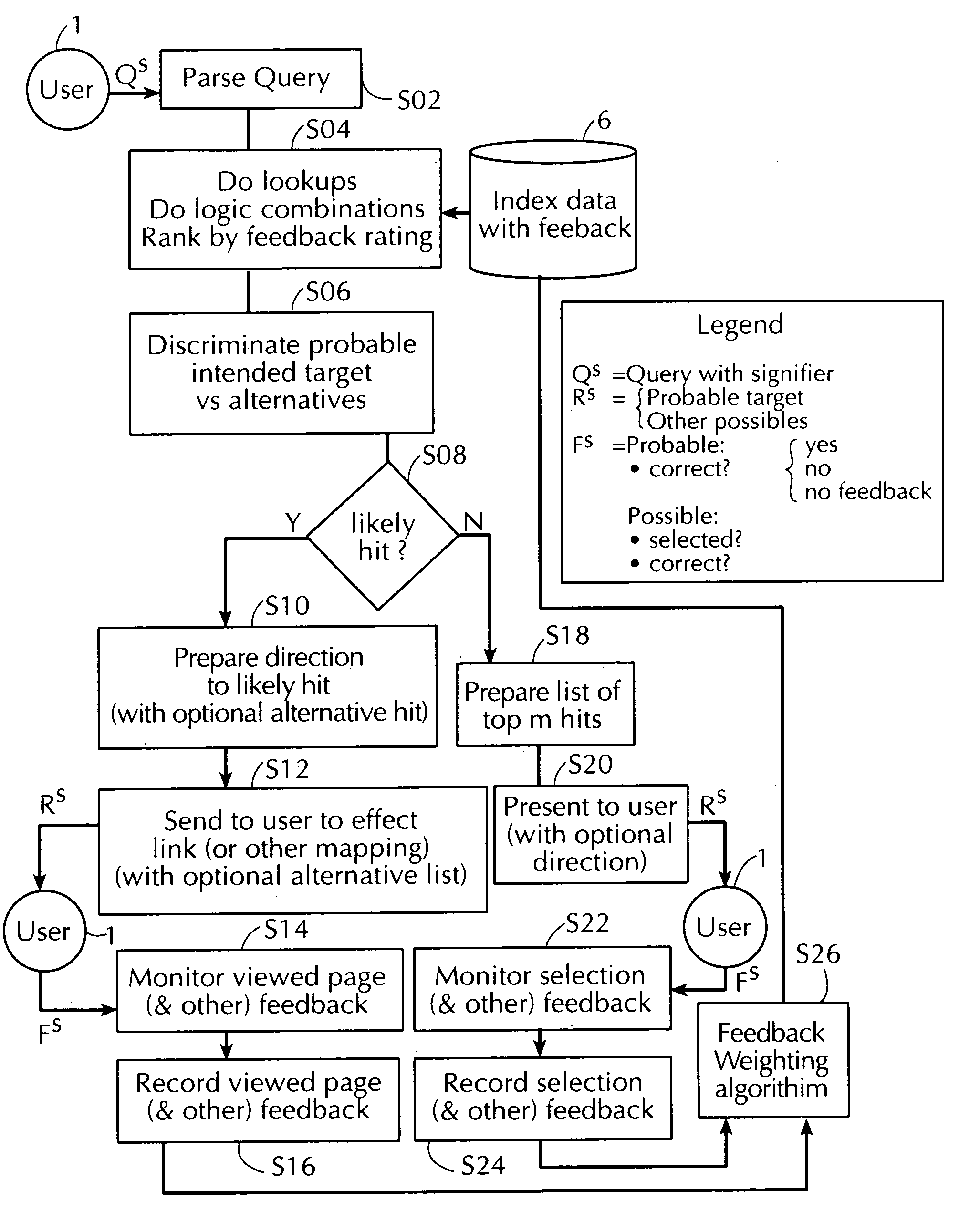
Method and apparatus for utilizing the social usage learned from multi-user feedback to improve resource identity signifier mapping
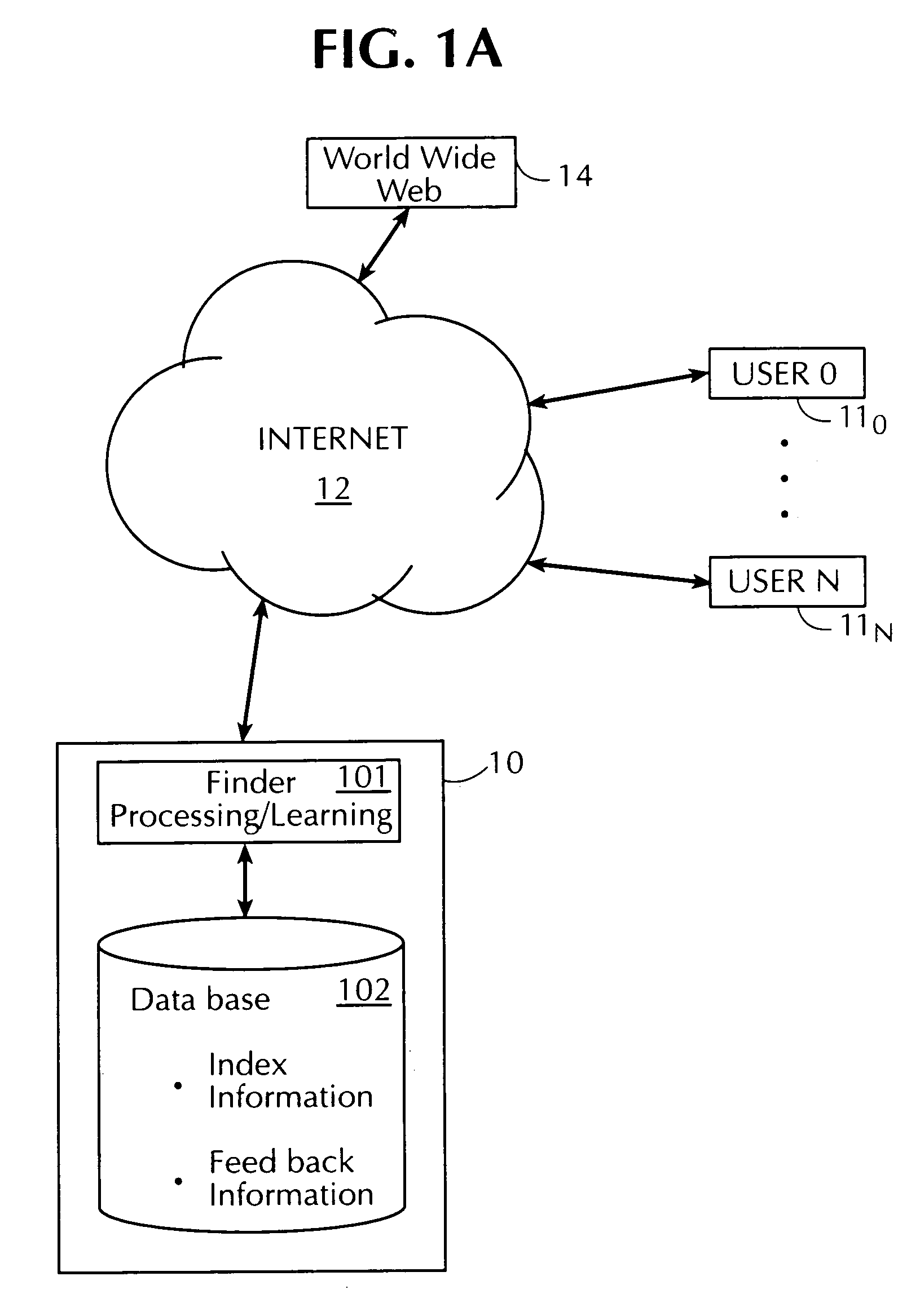
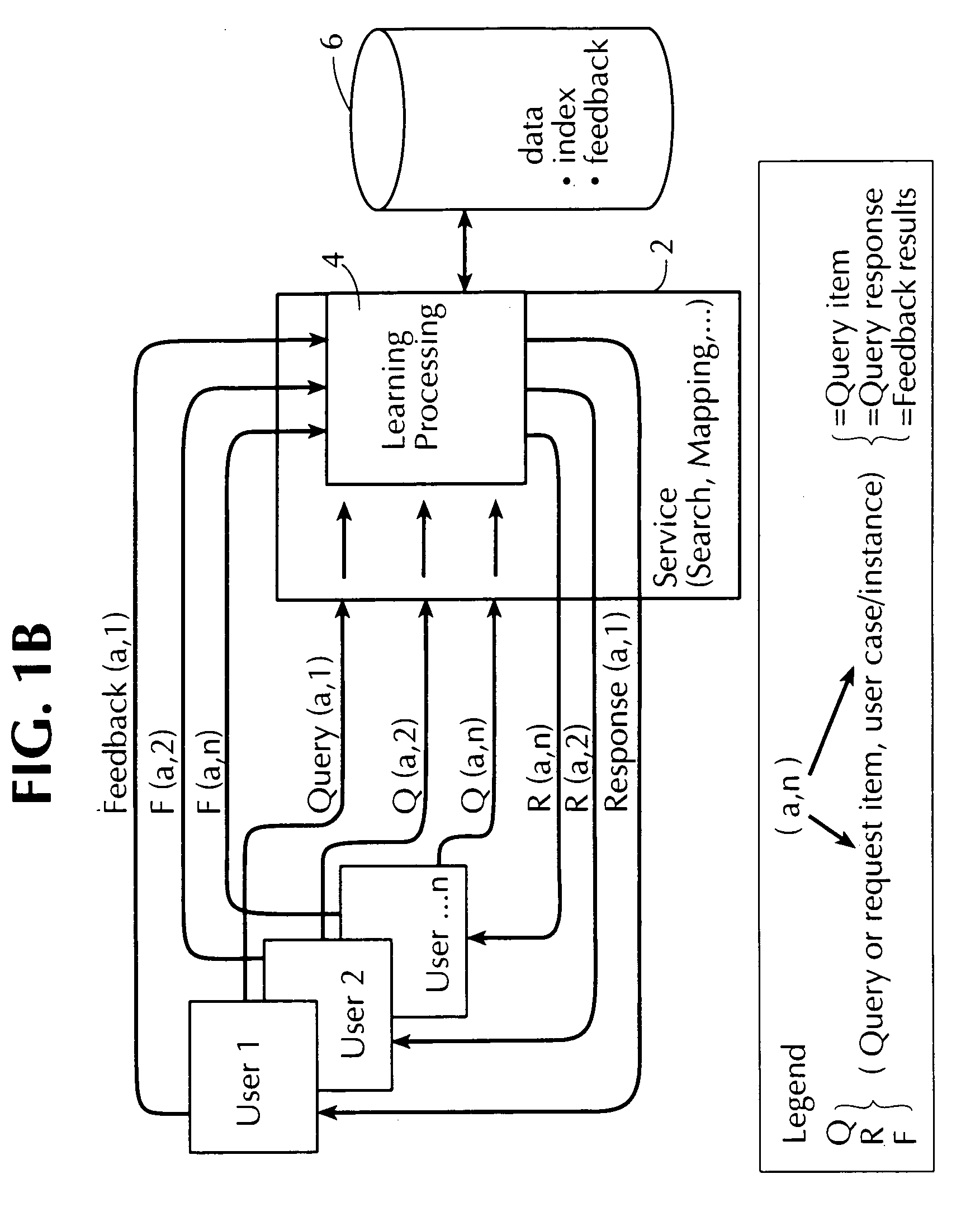
InactiveUS7062561B1Keep trackHandy search resultsWeb data indexingMultiple digital computer combinationsUser inputWorld Wide Web
An apparatus for finding resources on a network comprises a finder server having access to: (a) a database including: (i) an index of resources available on network of interconnected computers on which a plurality of resources reside; and (ii) information regarding user feedback gathered from previous operations of the apparatus by a user and plural previous users; and (b) a learning system operable to access and learn from information contained on the database. The finder server is operable to locate, in response to entry by the user of a resource identity signifier, a single intended target resource intended by the user to uniquely correspond to the resource identity signifier, from among a plurality of resources located on the network, by: receiving a resource identity signifier from the user; accessing the database to determine, based on the information in the database, which, if any, of the indexed resources is likely to be the intended target resource; and directing a computer of the user so as to cause that computer to connect the user to the address of the resource, if any, determined as likely to be the intended target resource.
Owner:OPEN TV INC +1
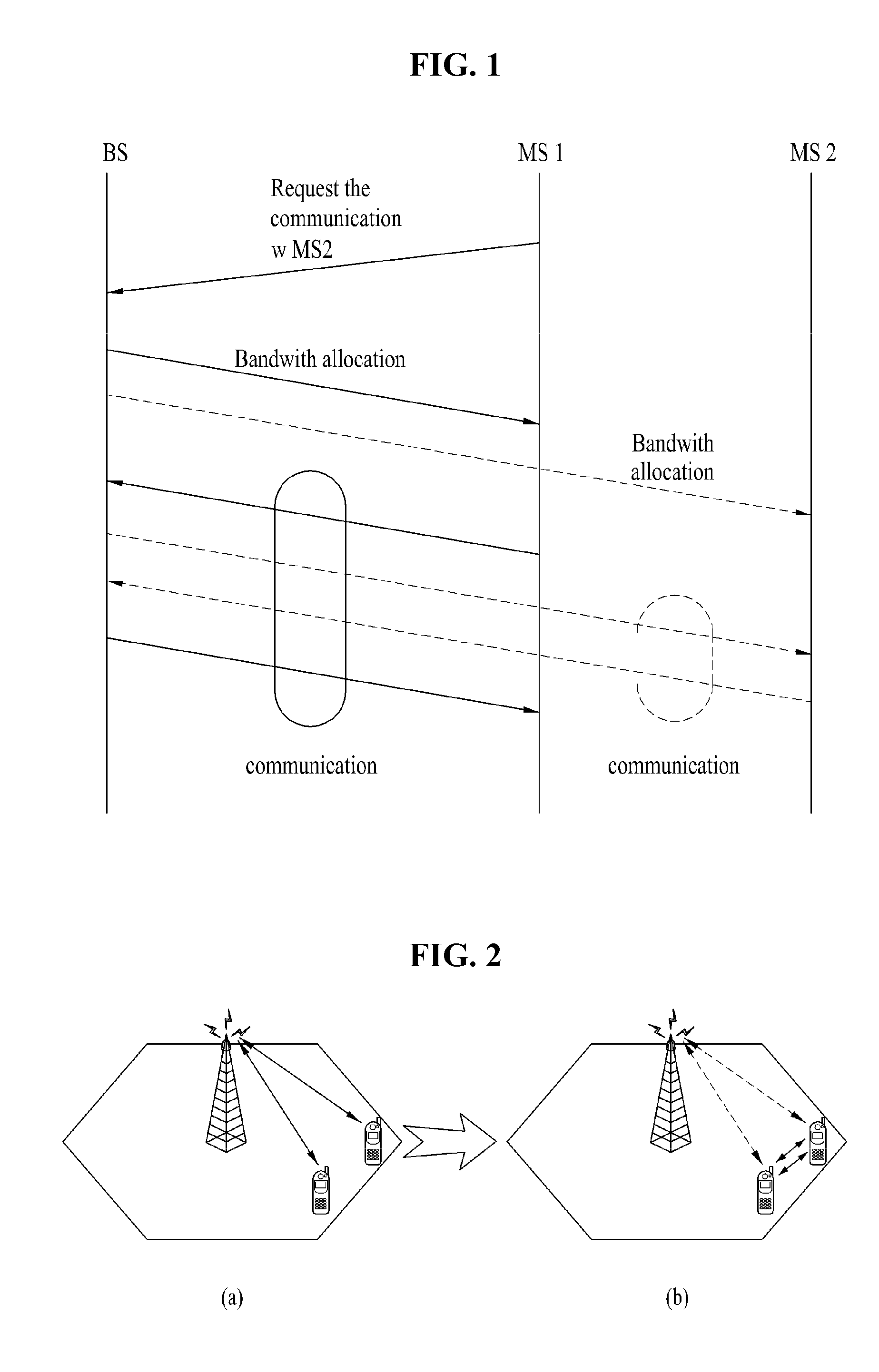
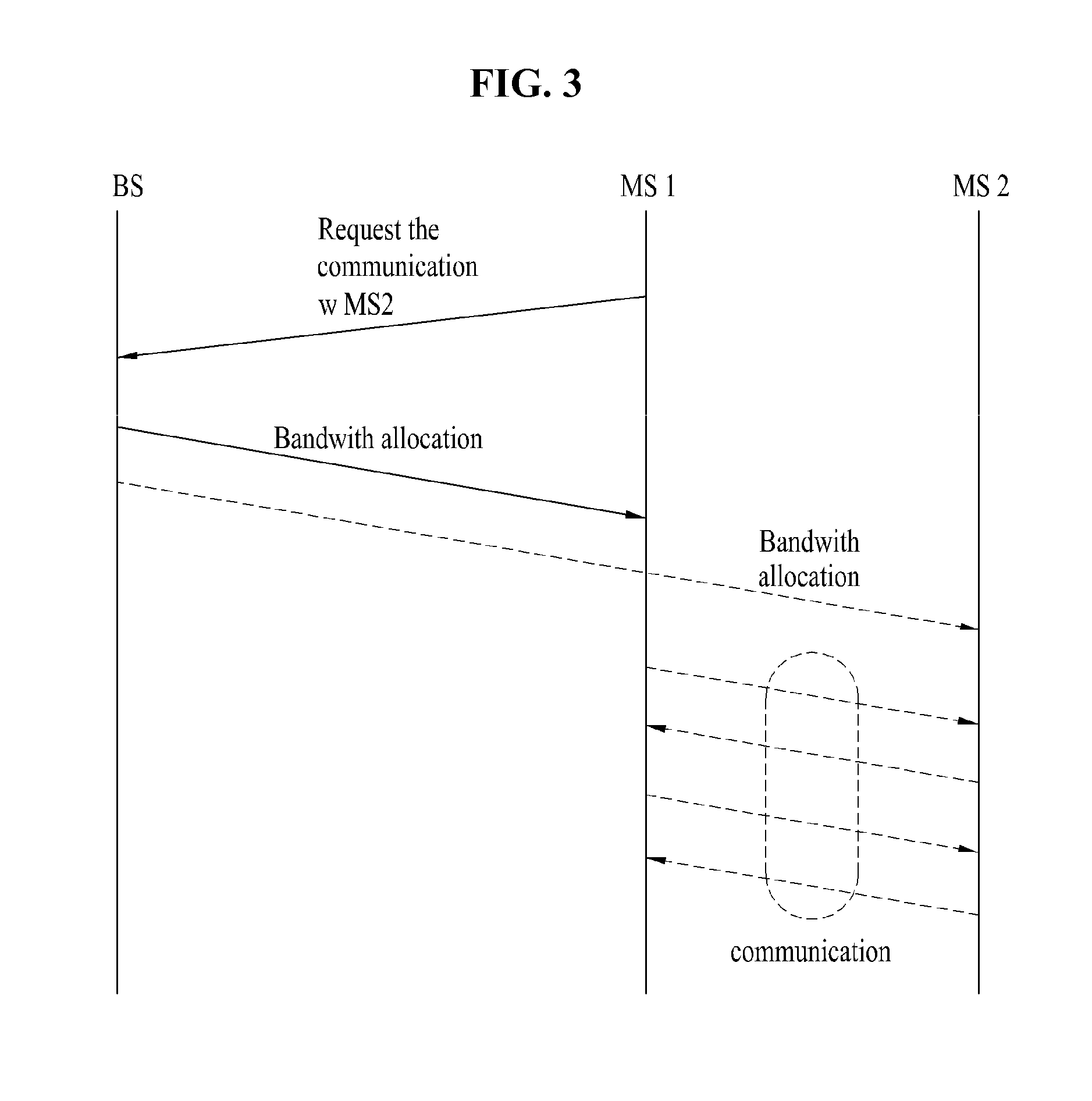
Happy Bit Setting In A mobile Communication System
ActiveUS20070297360A1Reduce the amount requiredPower managementCode division multiplexTelecommunicationsResource utilization
The invention relates to a mobile terminal communicating resource requests for dedicated uplink channel resources in a mobile communication system. Further, the invention also relates to a method for communicating resource requests for dedicated uplink channel resources in a mobile communication system. To allow the serving cell to detect “DOWN” commands from non-serving cells during soft handover the invention suggests a new definition of criteria for setting the “happy bit” in the control information associated to data transmitted on dedicated uplink channels. According to these criteria the mobile terminal may not indicate an unhappy condition while ramping up resource utilization. Only if resources equivalent to the maximum serving grant are utilized, the transmission buffer status requires to and the power status of the terminal allows for the happy bit is set to indicate a unhappy condition.
Owner:PANASONIC CORP
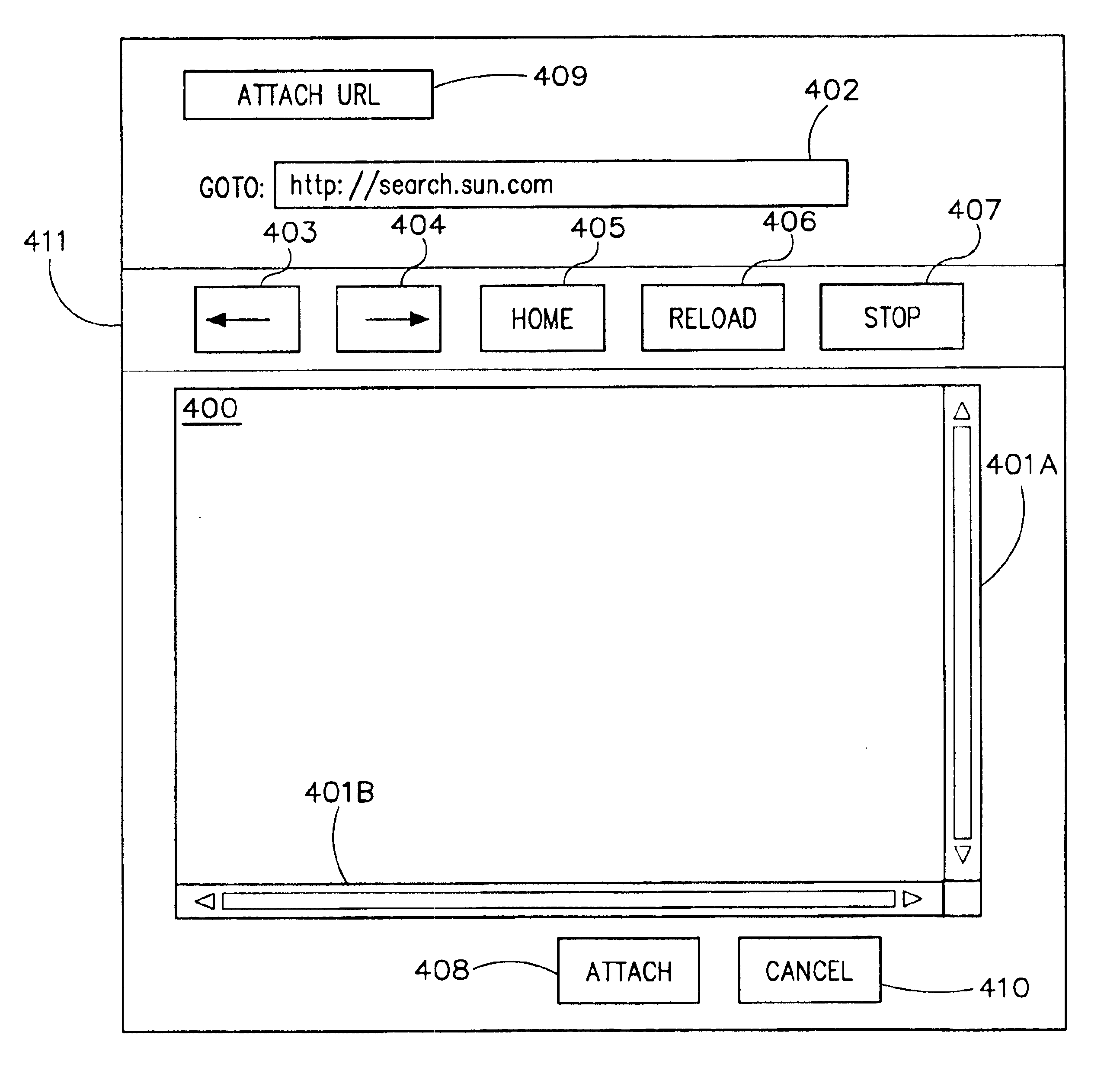
Method and apparatus for selecting attachments
InactiveUS6859213B1Cathode-ray tube indicatorsInput/output processes for data processingGraphicsDocumentation procedure
A method and apparatus for selecting attachments. When a sender indicates in an e-mail application or applet that an attachment is to be associated with an e-mail message, an attachment chooser window is presented. The attachment chooser window provides a browser-based graphical user interface (GUI) which allows a sender to browse data resources, such as HTML documents and associated links. An attachment mechanism is provided by which a sender can choose a currently displayed data resource for attachment in an e-mail message. In one embodiment, the attachment mechanism allows a user to select whether the attachment is retrieved and attached to an e-mail message as a resource locator (such as a URL) of the chosen data resource, or whether source data of the data resource is retrieved and attached to the e-mail message as one or more source files.
Owner:ORACLE INT CORP
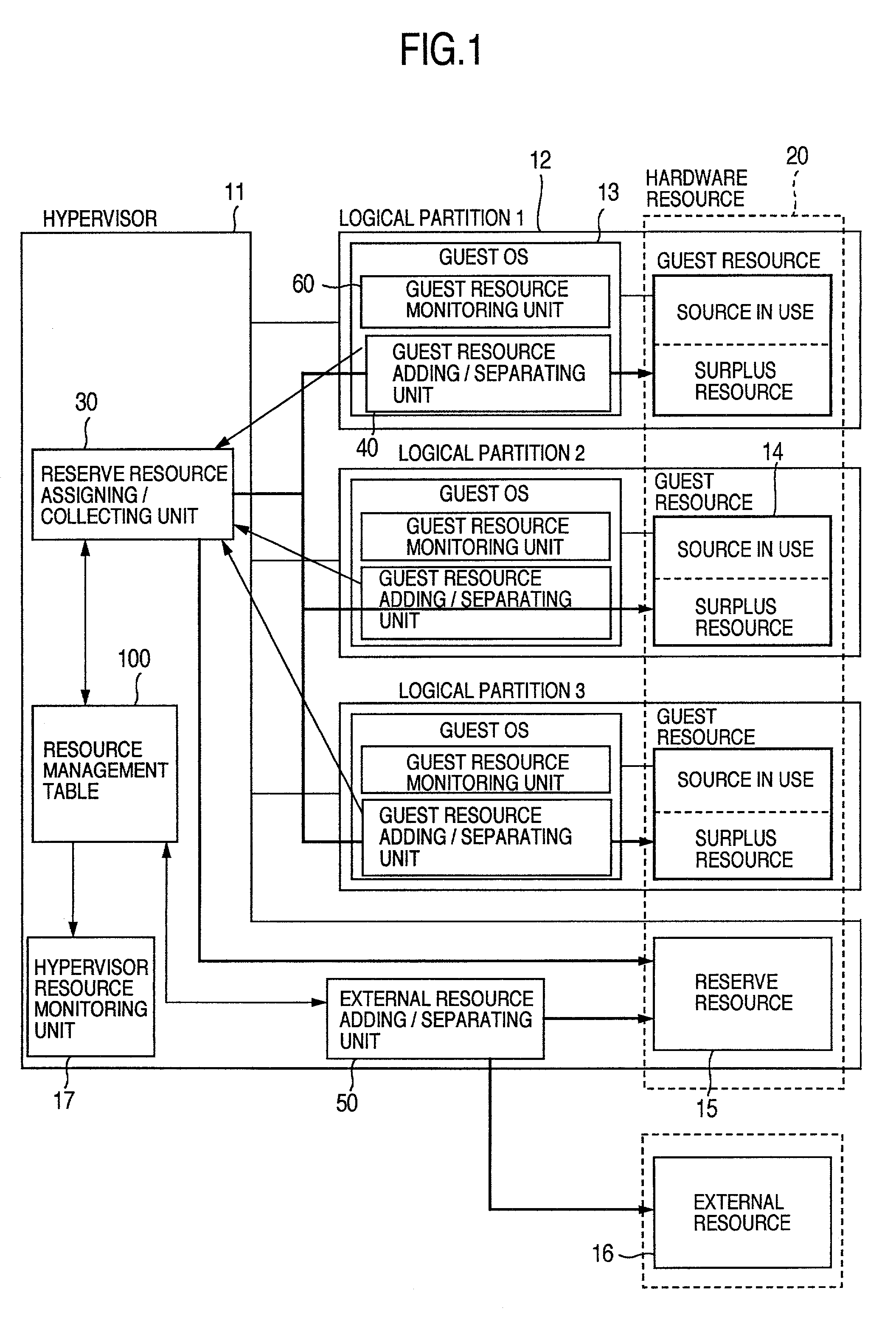
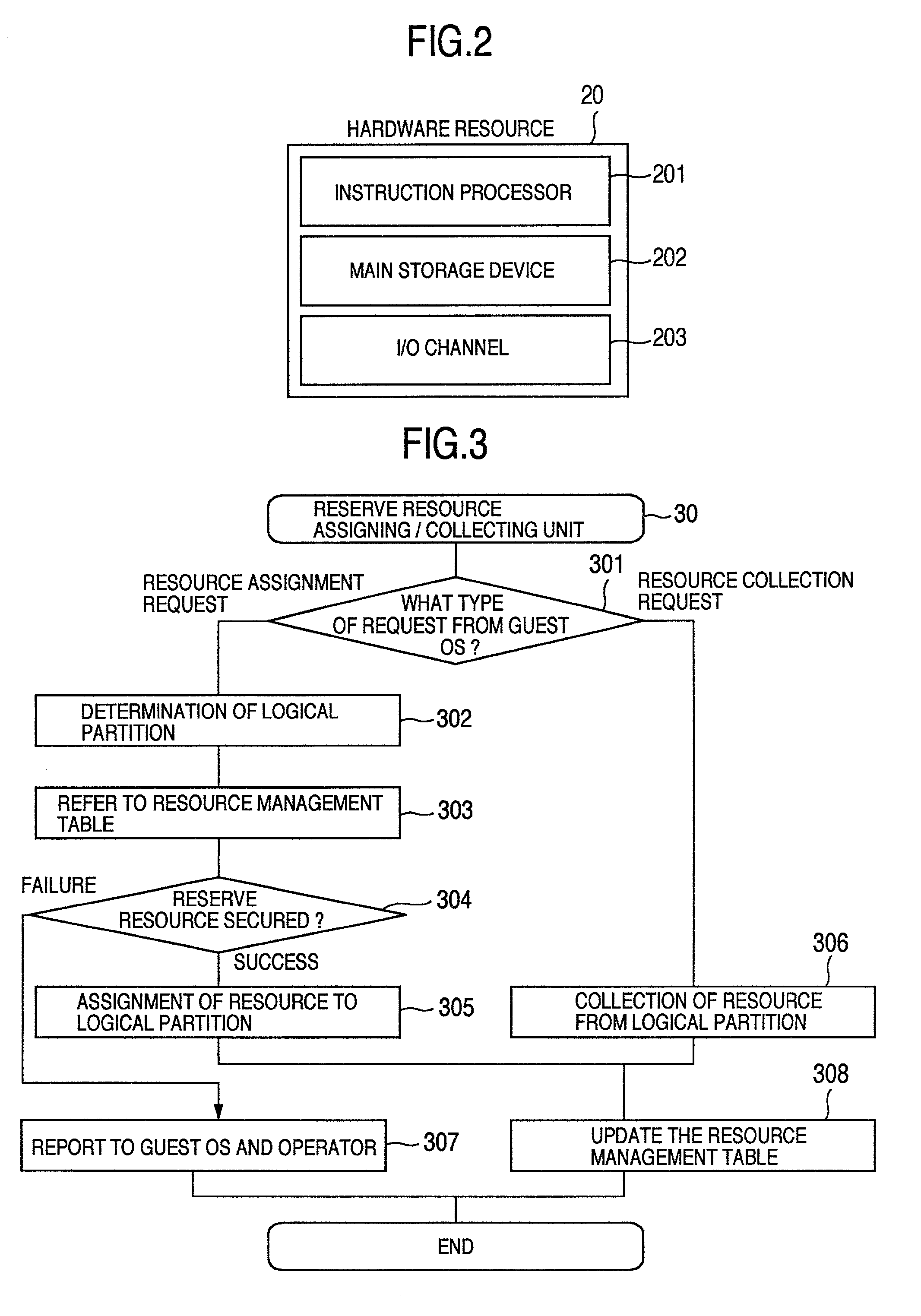
Method for automatically imparting reserve resource to logical partition and logical partitioned computer system
InactiveUS20020016812A1Resource allocationMemory adressing/allocation/relocationResource managementResource allocation
A logical partitioned computer system. A hypervisor includes a resource management table for managing resources assigned to the hypervisor and an assigning / collecting unit for assigning and collecting resources to logical partitions. Each logical partition has a guest resource monitoring unit for monitoring the amount of the resource being used out of the amount of the resource assigned to the logical partition and an adding / separating unit for requesting addition and separation of a resource to the assigning / collecting unit based on results of monitoring. In response to the request, assigning / collecting unit searches resource management table, assigns a resource to logical partition when a reserve resource exists in case of an assignment request, and collects a resource as a reserve resource in the resource management table in case of a collection request.
Owner:HITACHI LTD
DCI (Downlink Control Information) sending method, system and device as well as uplink transmission method, system and device
InactiveCN102083223AImprove uplink transmission efficiencyNetwork traffic/resource managementSignal allocationUplink transmissionModulation coding
The invention relates to a DCI (Downlink Control Information) sending method, system and device as well as an transmission uplink method, system and device, relating to the technical field of wireless communication and aiming at solving the problem that a network side is difficult to dispatch a user terminal to carry out uplink transmission because the traditional DCI does not support an LTE-A (Long Term Evolution-Advanced) system in the prior art. The DCI sending method disclosed by the embodiment of the invention comprises the following steps that: the network side generates the DCI used for dispatching the uplink transmission; the network side sends the generated DCI, wherein the DCI comprises the following information: resource indication information, modulation indication information, data indication information, mapping indication information and precoding indication information, wherein the resource indication information is used for indicating the positions of allocated resources; the modulation indication information is used for indicating a modulation coding order of a transmission block; the data indication information is used for indicating whether the transmission block transmits new data or not; the mapping indication information is used for indicating the corresponding relationship of the transmission block and a code word; and the precoding indication information is used for indicating the size of an uplink transmission order and an index of a used precoding code word. The DCI sending method can be used for enhancing the efficiency of the uplink transmission.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Apparatus for direct communication in a wireless system and method thereof
InactiveUS20110223953A1Efficiently enableLow powerConnection managementRadio transmissionCommunications systemDirect communication
An apparatus for direct communication in a wireless communication system and method thereof are disclosed, by which a communication is efficiently enabled with a low power. In performing a direct communication in a first terminal of a wireless communication system, the present invention includes receiving a resource allocation information on a resource allocated to the direct communication from a base station and performing the direct communication with a second terminal using the allocated resource. In this case, the allocated resource is defined in either an uplink resource region of the base station or a downlink resource region of the base station and the allocated resource is divided into a transmission region for the direct communication and a receipt region for the direct communication.
Owner:LG ELECTRONICS INC
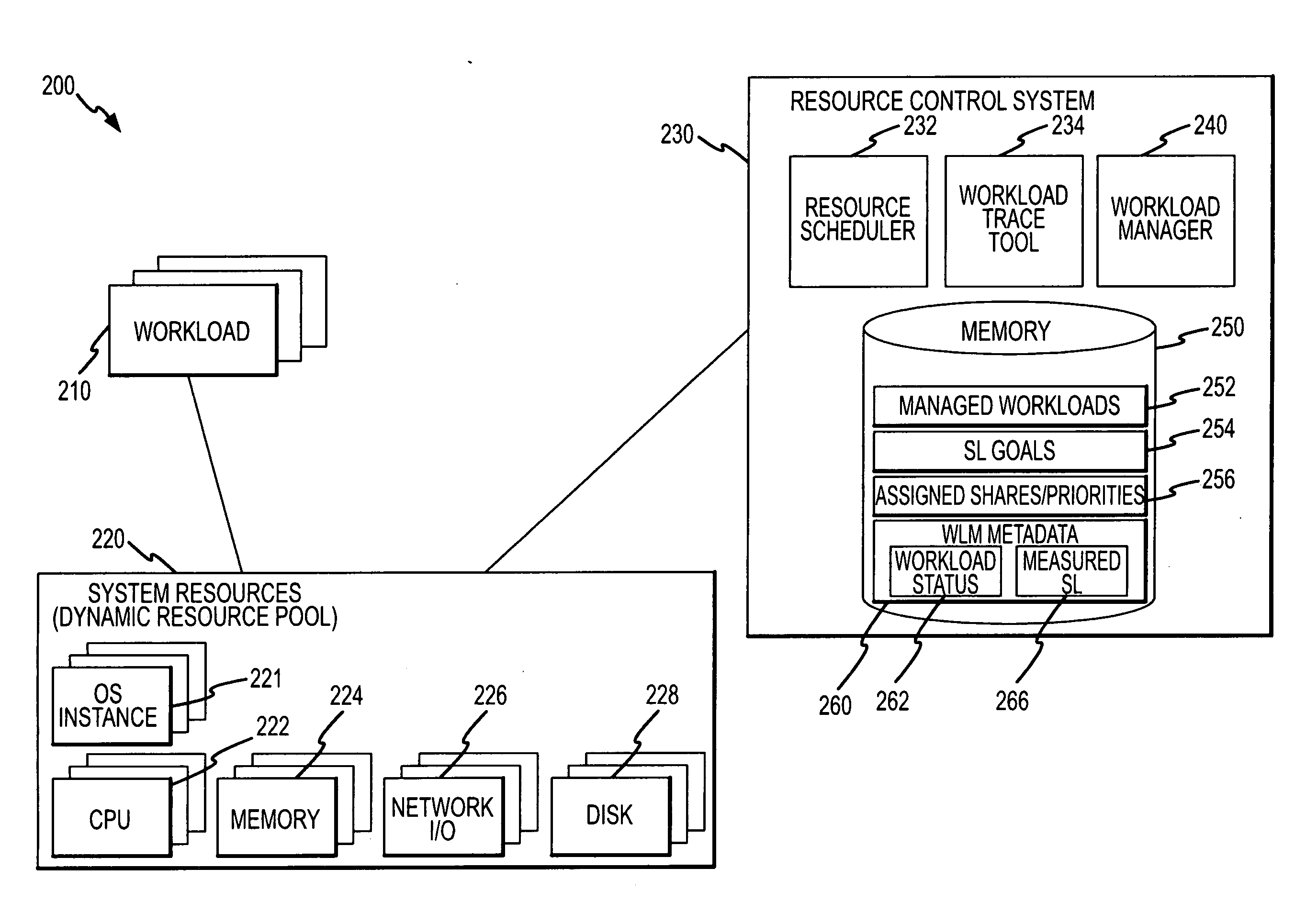
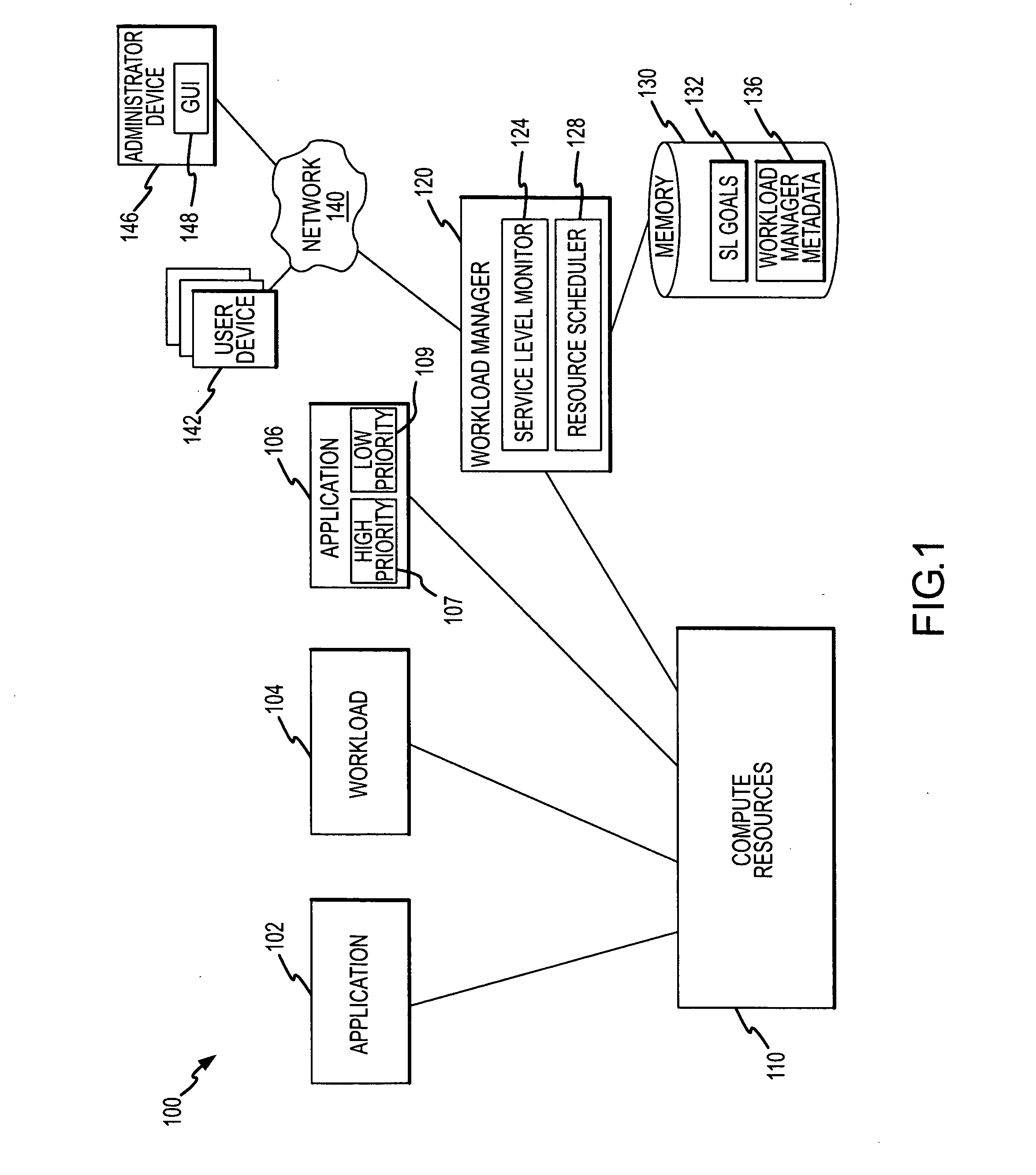
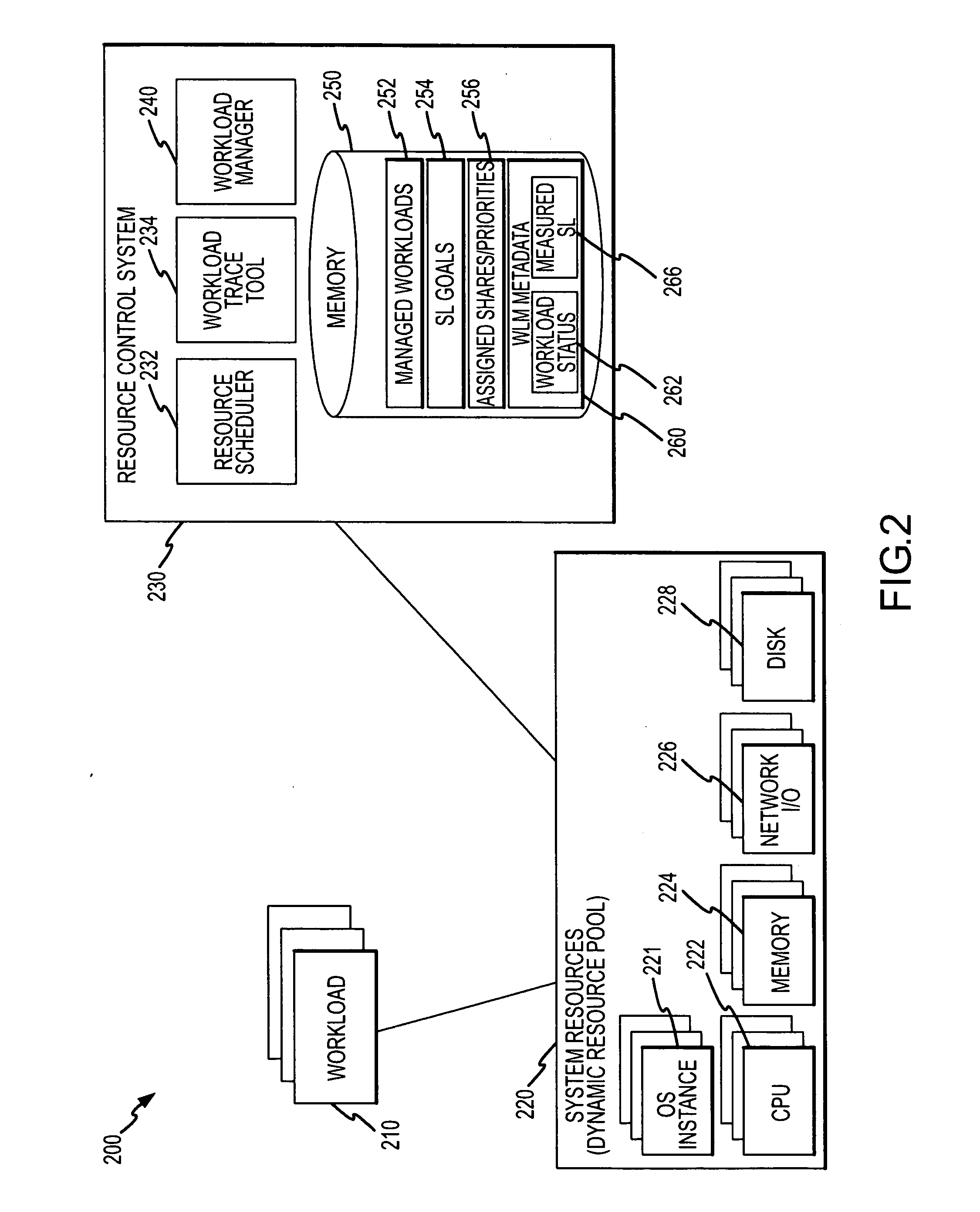
Computer resource management for workloads or applications based on service level objectives
ActiveUS20070234365A1Efficient managementEfficient allocationMultiprogramming arrangementsMemory systemsComputer resourcesOperational system
A resource allocation method and system for efficiently allocating compute resources. The method includes providing a workload manager and installing a workload in the computer system. During the installing, a service level goal for the workload is provided to the workload manager, and the workload manager assigns a first resource allocation for the compute resources to the workload. Then, a service level being achieved for the workload is determined in the compute resources. Based on results of the comparing, the workload manager reallocates the compute resource with the workload manager including assigning a second resource allocation for the compute resources to the workload. The workload may be made up of one or more applications running on the compute resources over multiple OS instances. The installing of the workload includes the application interfacing with the workload manager to provide the service level goal during installation.
Owner:ORACLE INT CORP
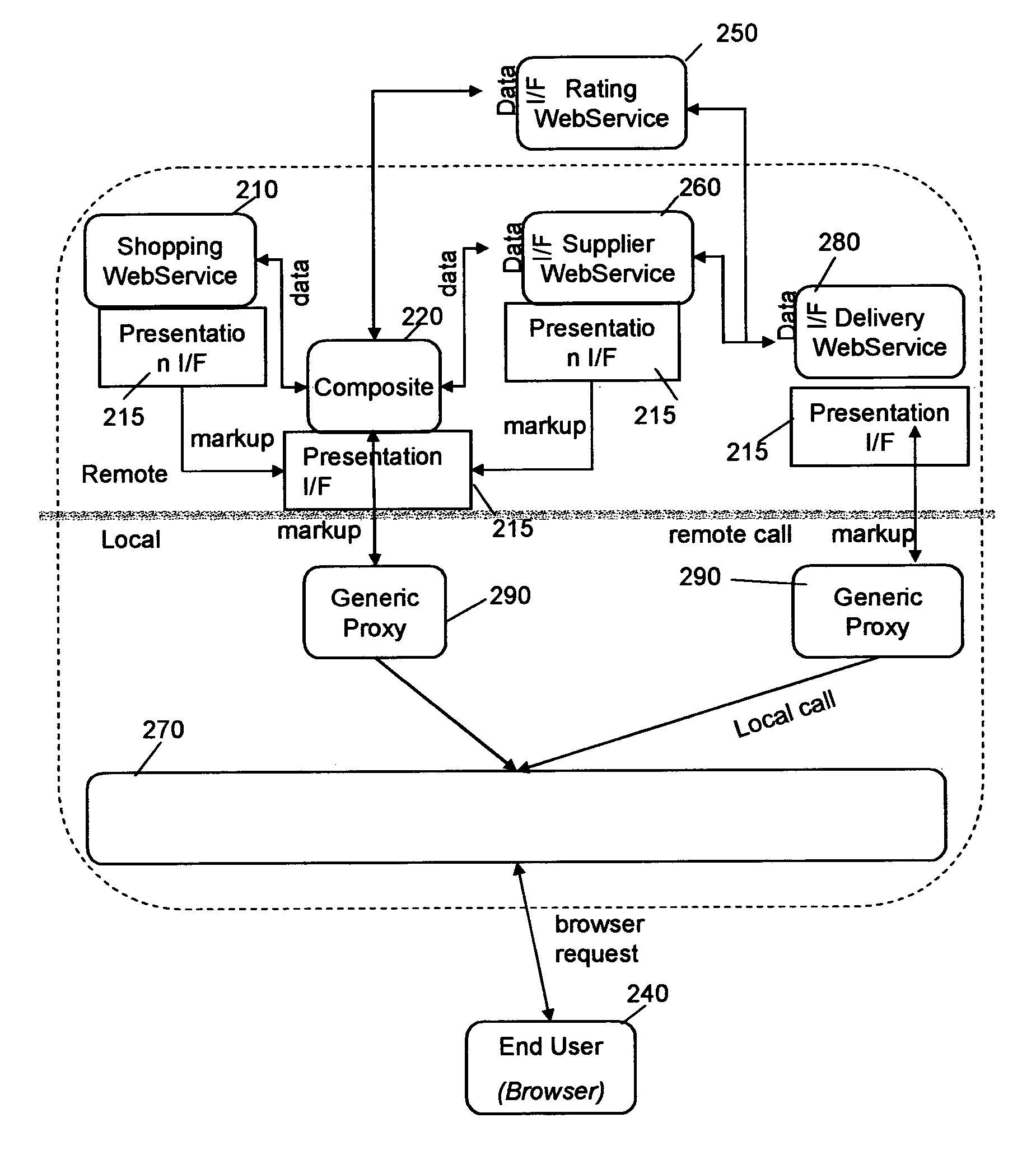
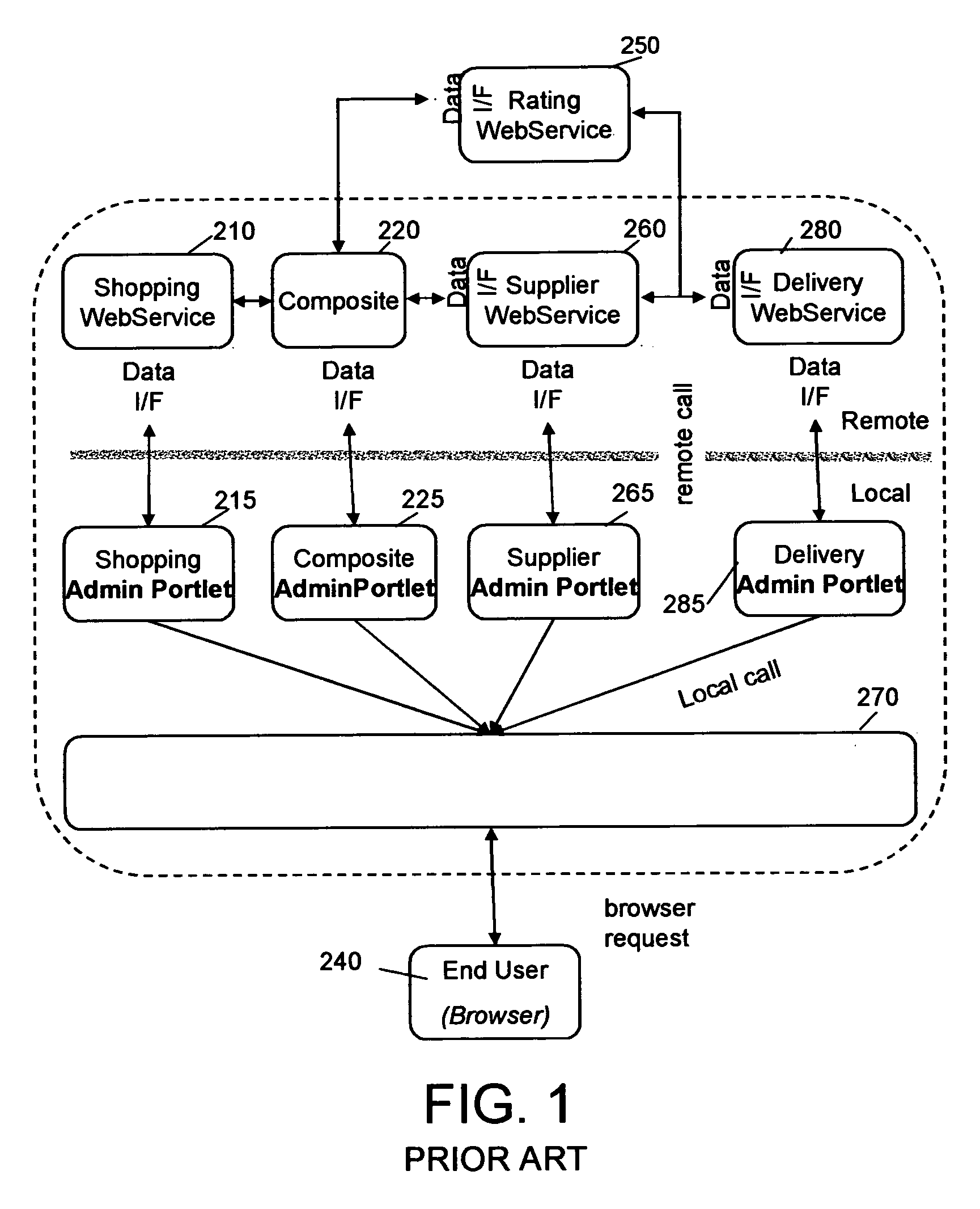
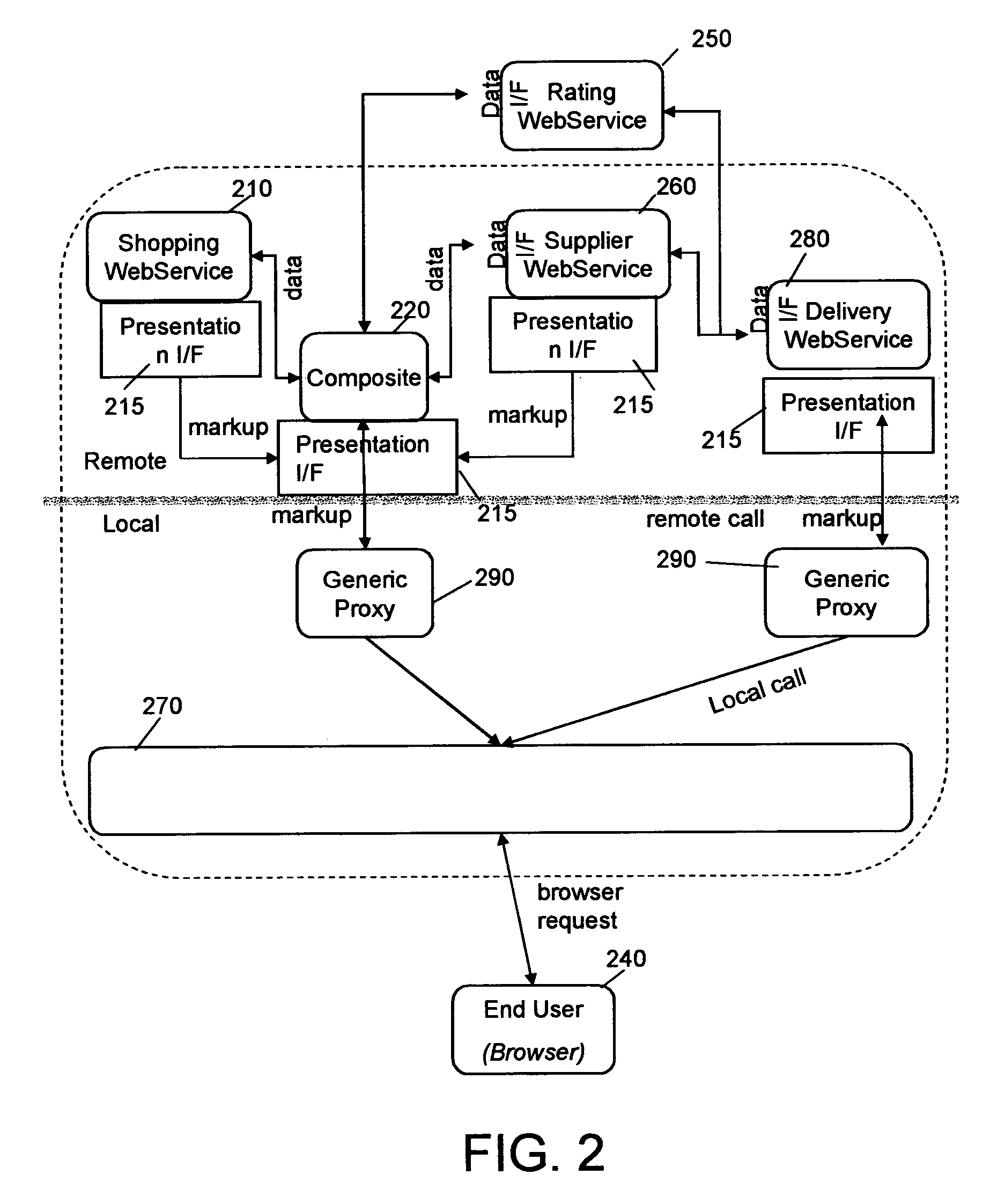
Managing resources through user-facing web services aggregated in portals
InactiveUS20060041641A1Multiple digital computer combinationsProgram controlGrid resourcesWeb service
The present invention relates to a method and respective system for managing the administration of electronic resources accessible in an electronic-network: A solution is offered, in which grid resources or services are enhanced with a presentation interface that provides an administration user-interface (UI) for configuring them, i.e., the administration UI of a distributed resource is provided by the server hosting the resource, or simply the resource itself. This includes also the resource-located logic required to configure the resource according to the user inputs and actions imparted on user controls, which are sent from a respective resource to a portal server. On this portal server, a simple, generic second user-interface software is implemented, which is able to aggregate the fragments or controls of different resources, to display such multiple controls to a human person, to process user inputs imparted on those controls, and to send user control data entered via the user-interface fragments to a resource configuration interface of a respective one of the resources in order to perform the configuration of a respective resource via the respective resource configuration-interface.
Owner:SNAP INC
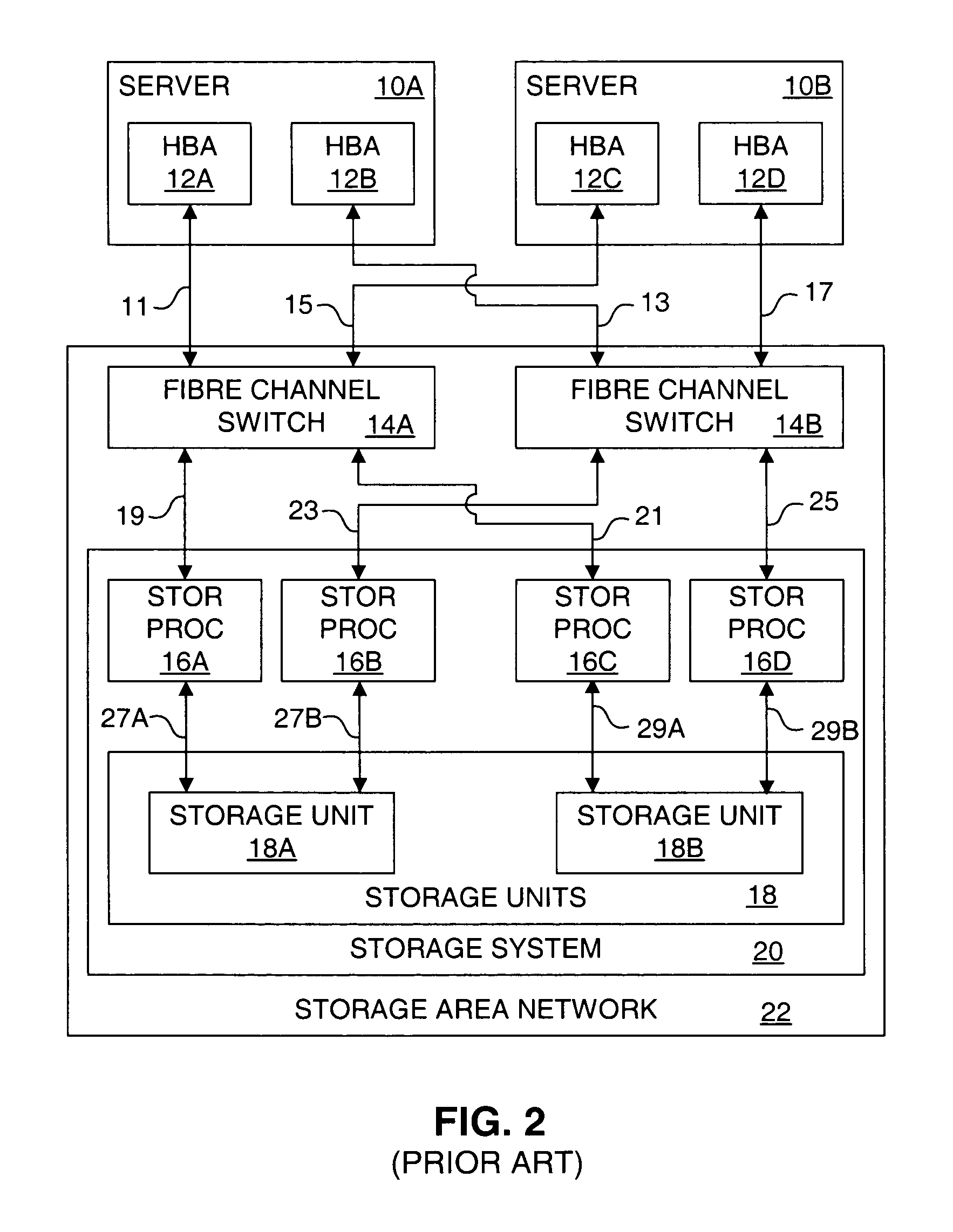
Storage multipath management in a virtual computer system
ActiveUS7783779B1Multiprogramming arrangementsMultiple digital computer combinationsFailoverComputerized system
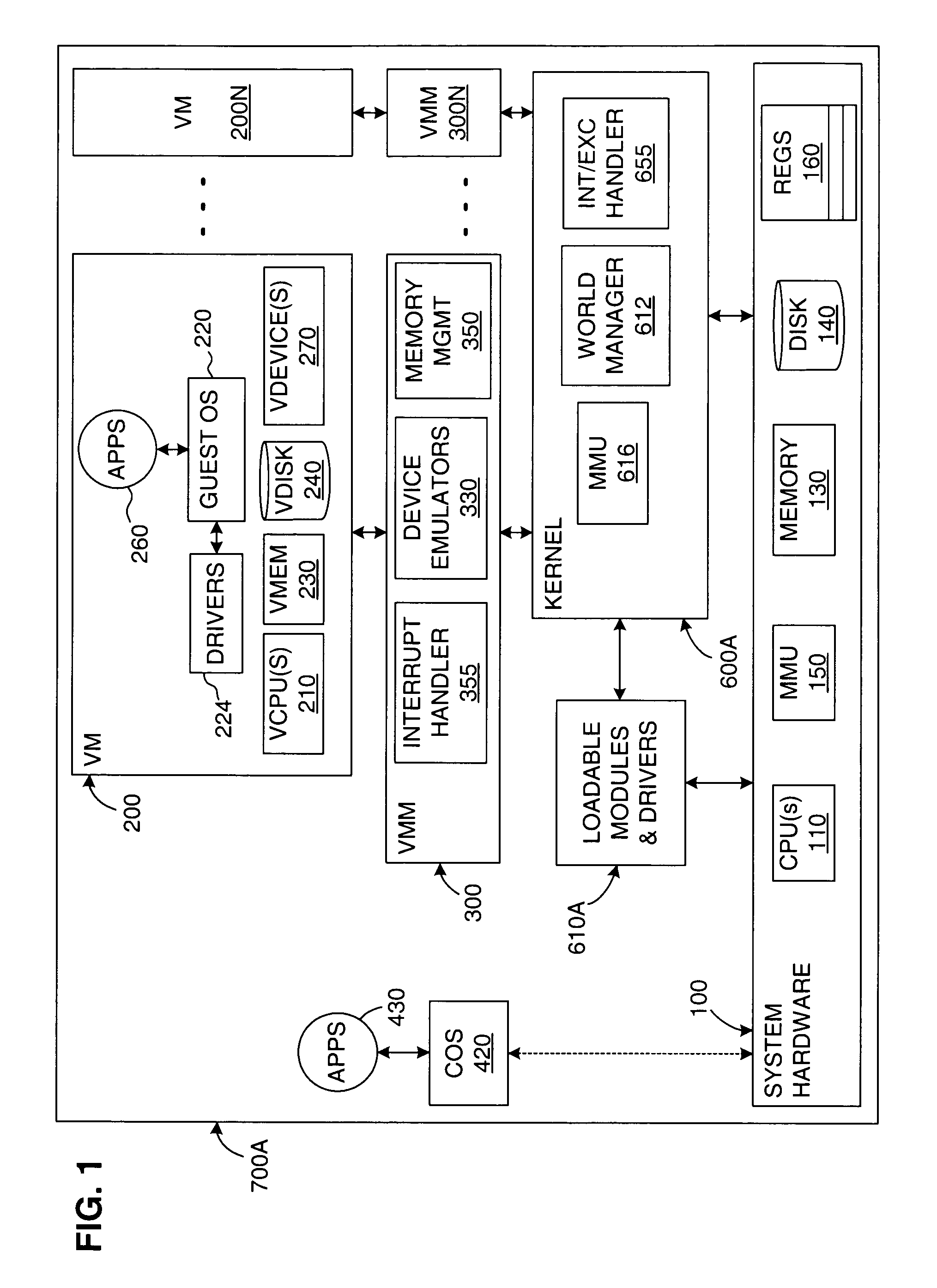
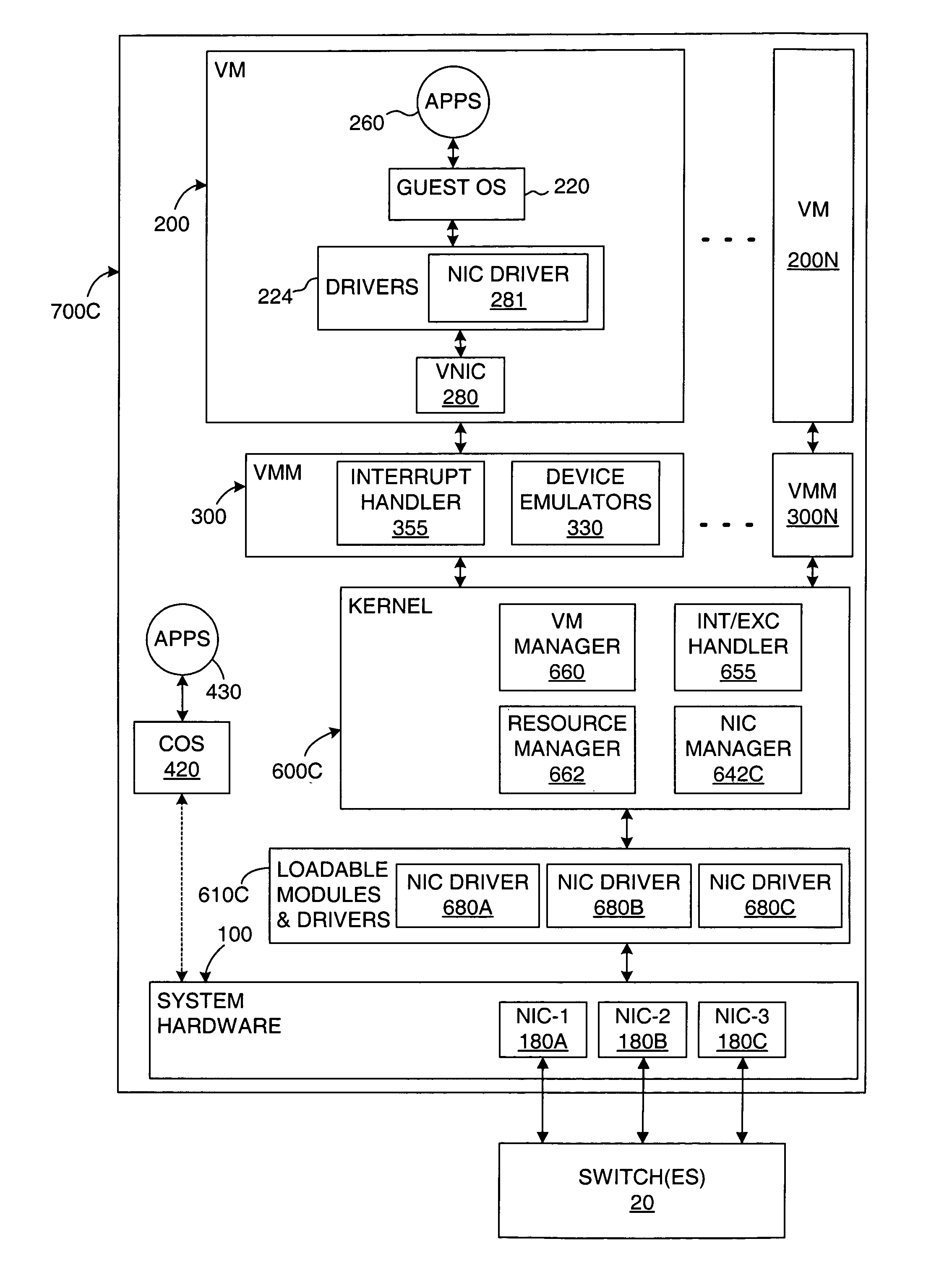
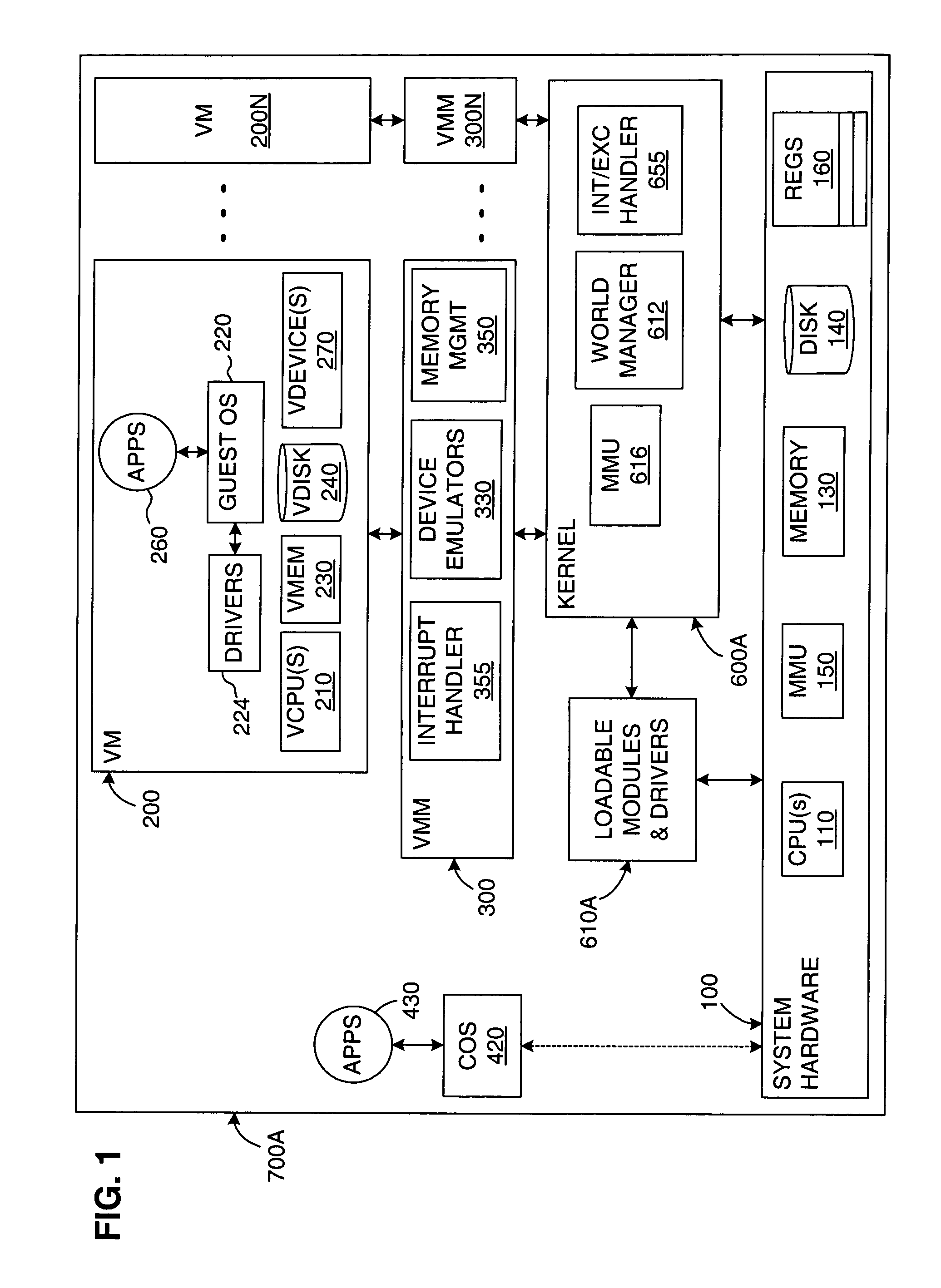
A virtual computer system, including one or more virtual machines (VMs), is connected to a redundant data storage system having multiple paths for routing data between the computer system and the data storage system. The VMs are supported by a kernel, which includes a resource manager for allocating system resources among the VMs, including data storage space and data storage bandwidth. A storage path manager (SPM) is integrated into the kernel for routing data between the computer system and the data storage system, including providing functions such as failovers and failbacks, as well as load distribution. Integrating the SPM into the kernel improves the kernel's ability to manage the VMs and to provide SAN resources to the VMs. For example, the SPM may enhance the isolation between multiple VMs by routing their respective data over different data paths. Also, the SPM may improve the allocation of system resources by coordinating with the resource manager.
Owner:VMWARE INC
System and method providing single application image
InactiveUS6868539B1Shorten the timeReduce complexitySoftware designProgram loading/initiatingGraphicsGraphical user interface
A system and method is provided that facilitates the administration of an application in accordance with the present invention. The system includes a resource identifier that identifies resources associated with the application and a manifest that logs the resources. An aggregator is provided that aggregates a subset of the resources into the manifest to facilitate administration of the application. The aggregator can be provided by a user interface and / or an automated builder. A graphical user interface is also provided to facilitate deployment, creation and enumeration of the application.
Owner:MICROSOFT TECH LICENSING LLC
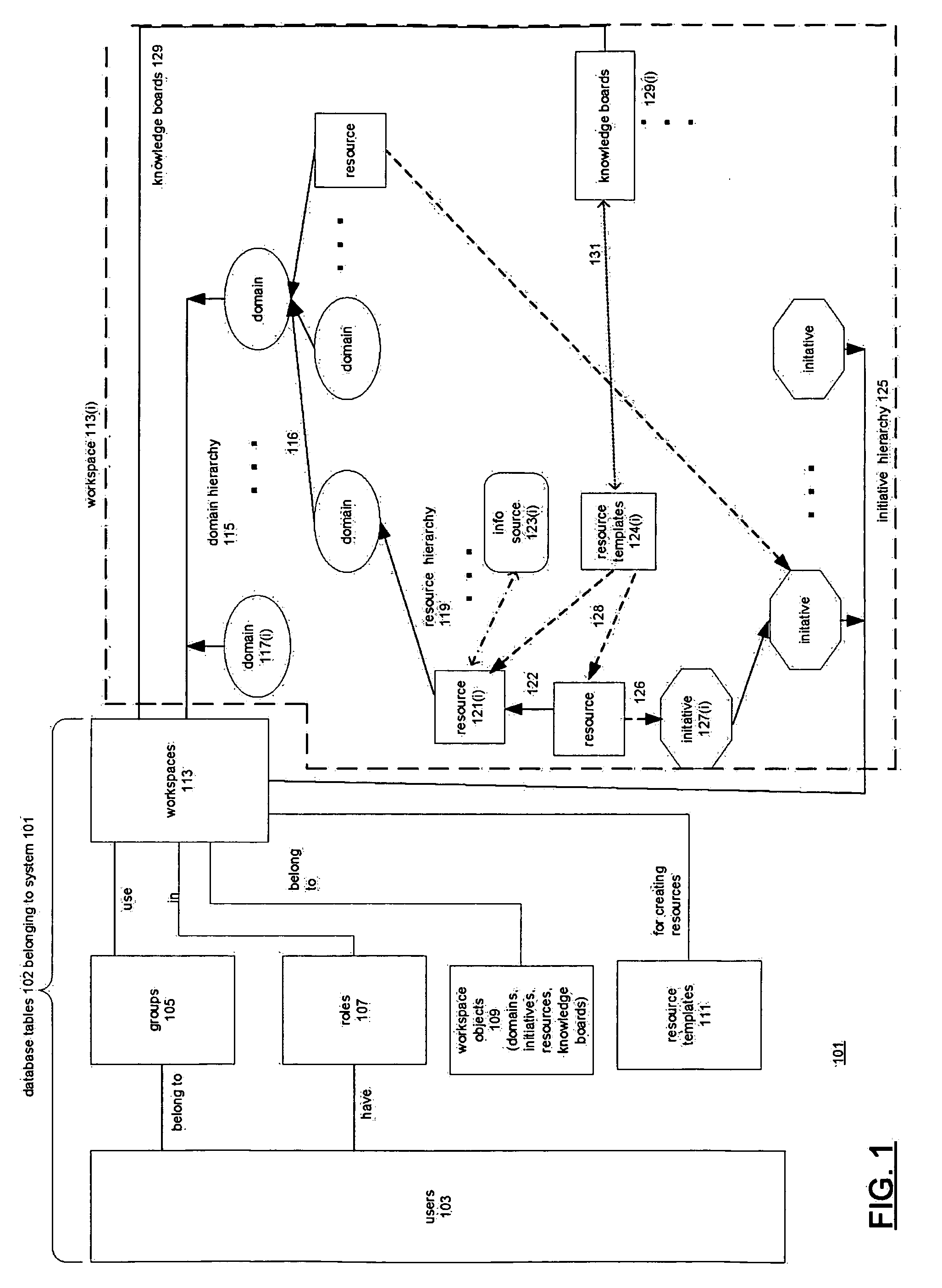
System for supporting collaborative activity
A system includes a processor which has access to a representation of model of activity, which includes workspaces. Each workspace includes domain hierarchies for representing an organizational structure of the collaborating users using the system, and initiatives hierarchies representing process structures for accomplishing goals. An interface permits users to view and modify the workspaces for which the user has access. Each user can have different access permissions in different workspaces. The domain and initiative hierarchies provide two views of the workspace objects without duplicating resources. A resource is a collection of shared elements defined by the users that give users associated with the workspace access to information sources. Users can define knowledge boards for creating reports based on information fields of the resources. The knowledge board is associated with a resource template from which the resource is created.
Owner:VIRTUALAGILITY
Multidimensional modeling of software offerings
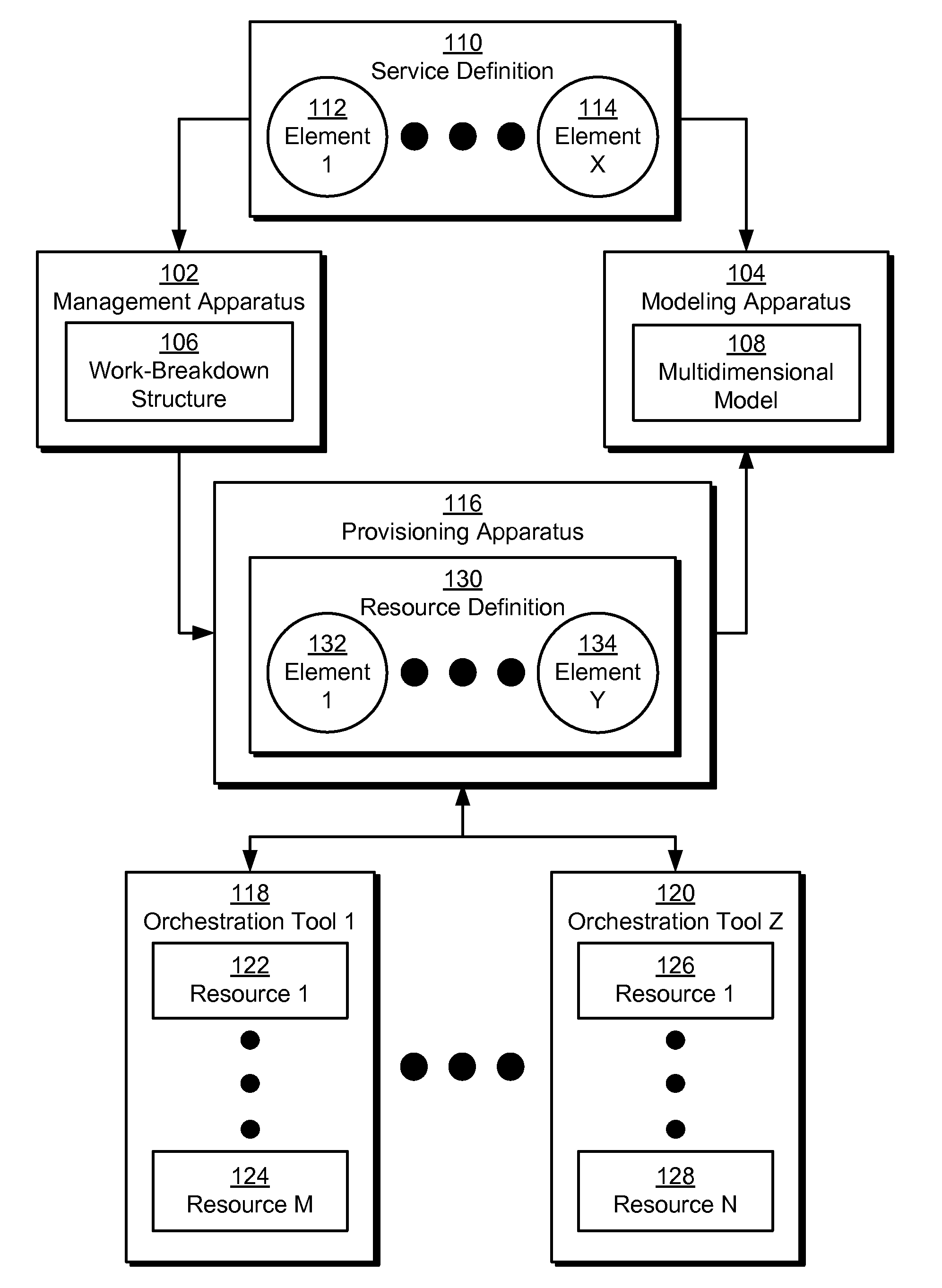
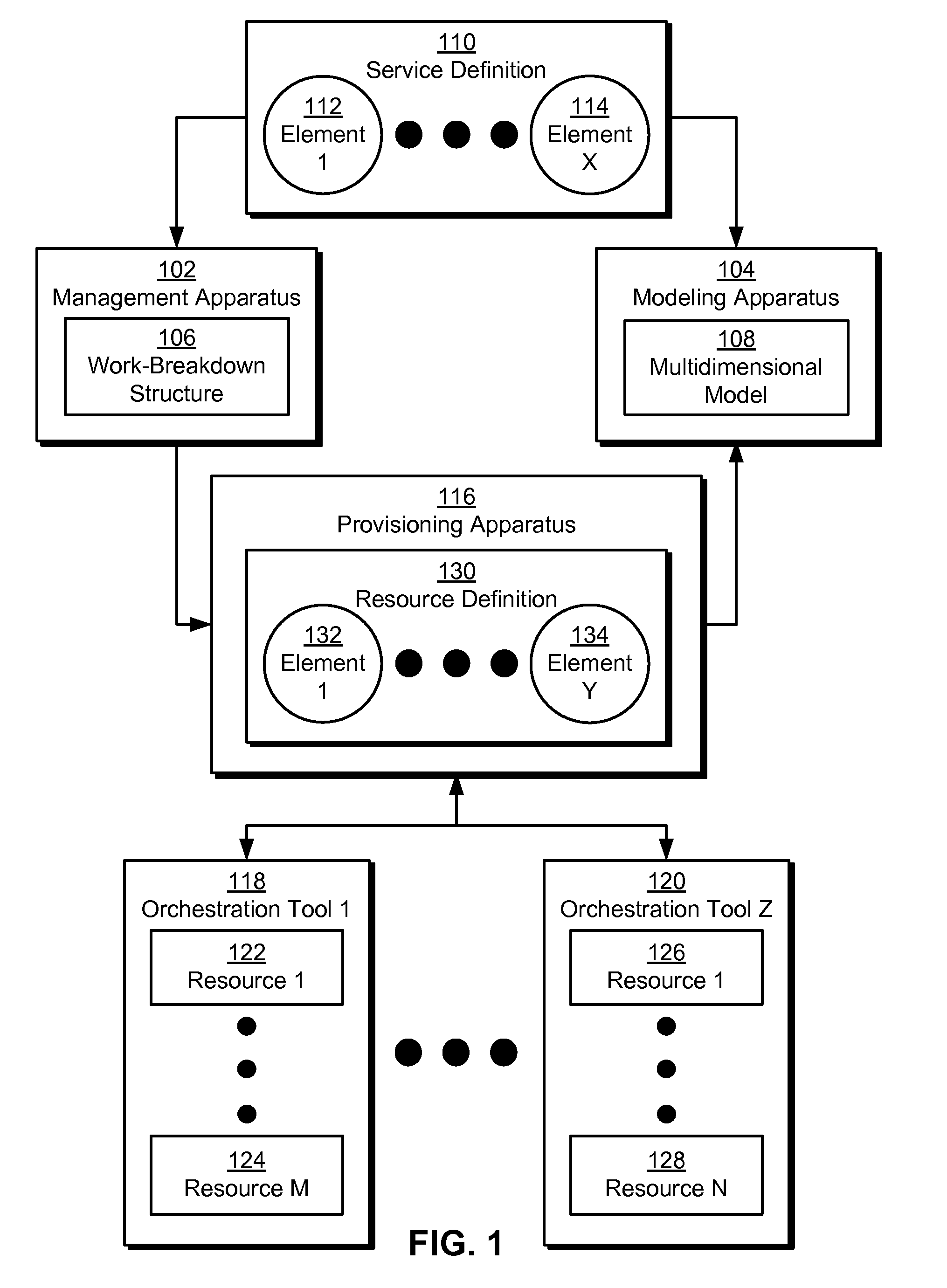
ActiveUS20120215919A1Easy to deploySimple to executeDigital computer detailsProgram controlMultidimensional scalingSoftware engineering
The disclosed embodiments provide a system that facilitates the deployment and execution of a software offering. During operation, the system obtains a service definition of the software offering and a resource definition of resources available for use by the software offering. Next, the system creates a multidimensional model of the software offering by mapping a first set of elements from the service definition to a second set of elements from the resource definition. Finally, the system uses the multidimensional model to manage the deployment and execution of the software offering without requiring manual configuration of the resources by a user.
Owner:INTUIT INC
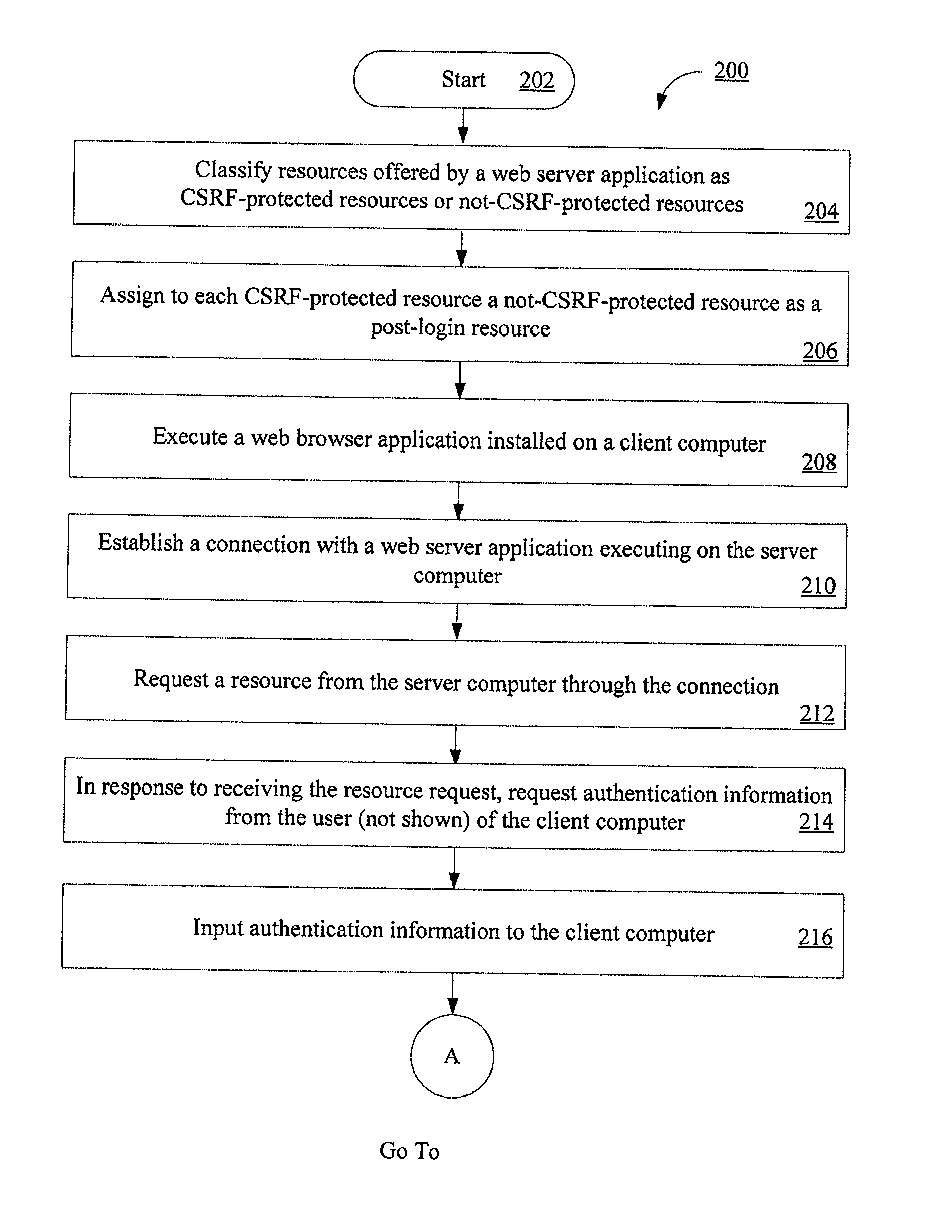
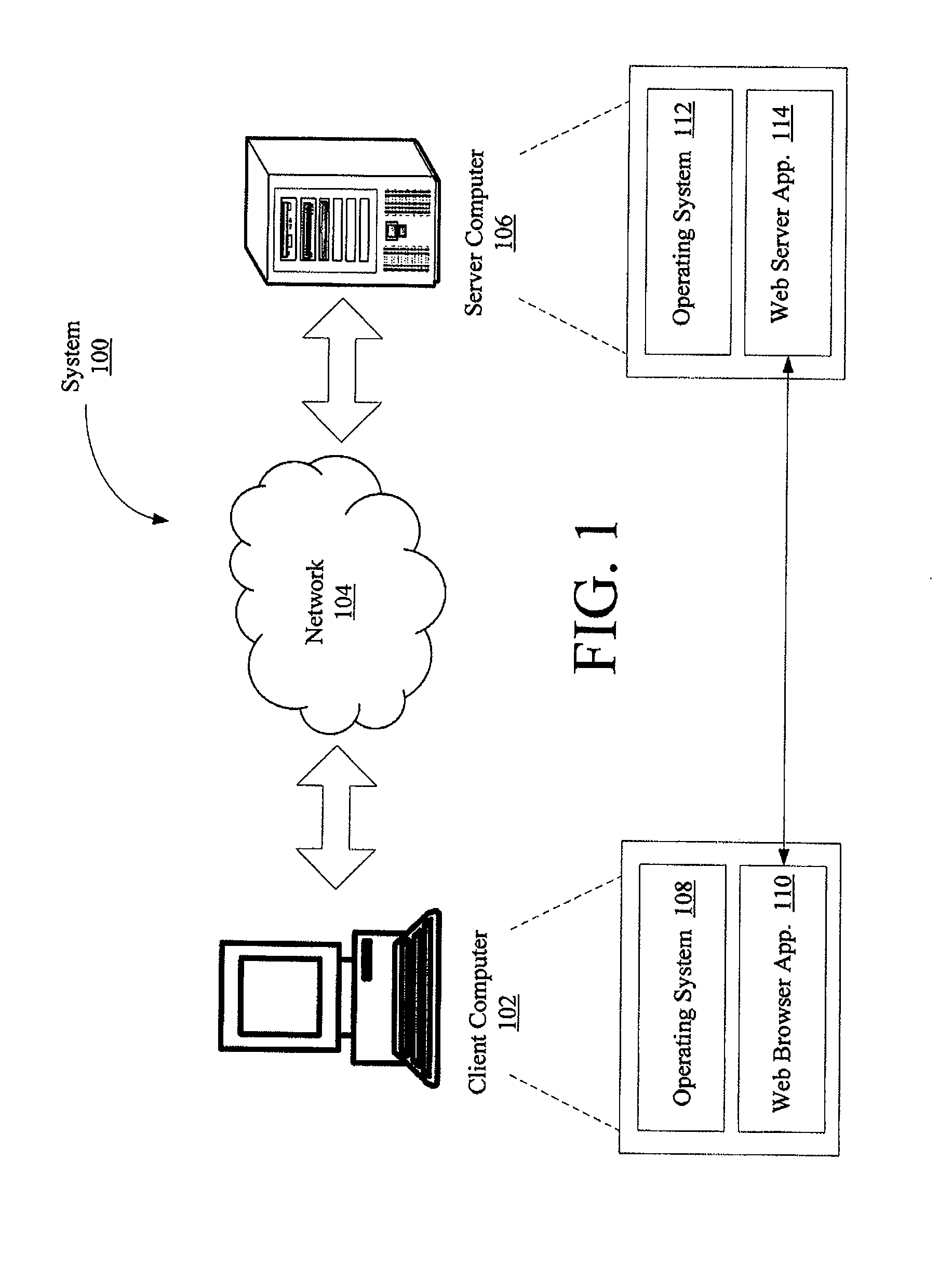
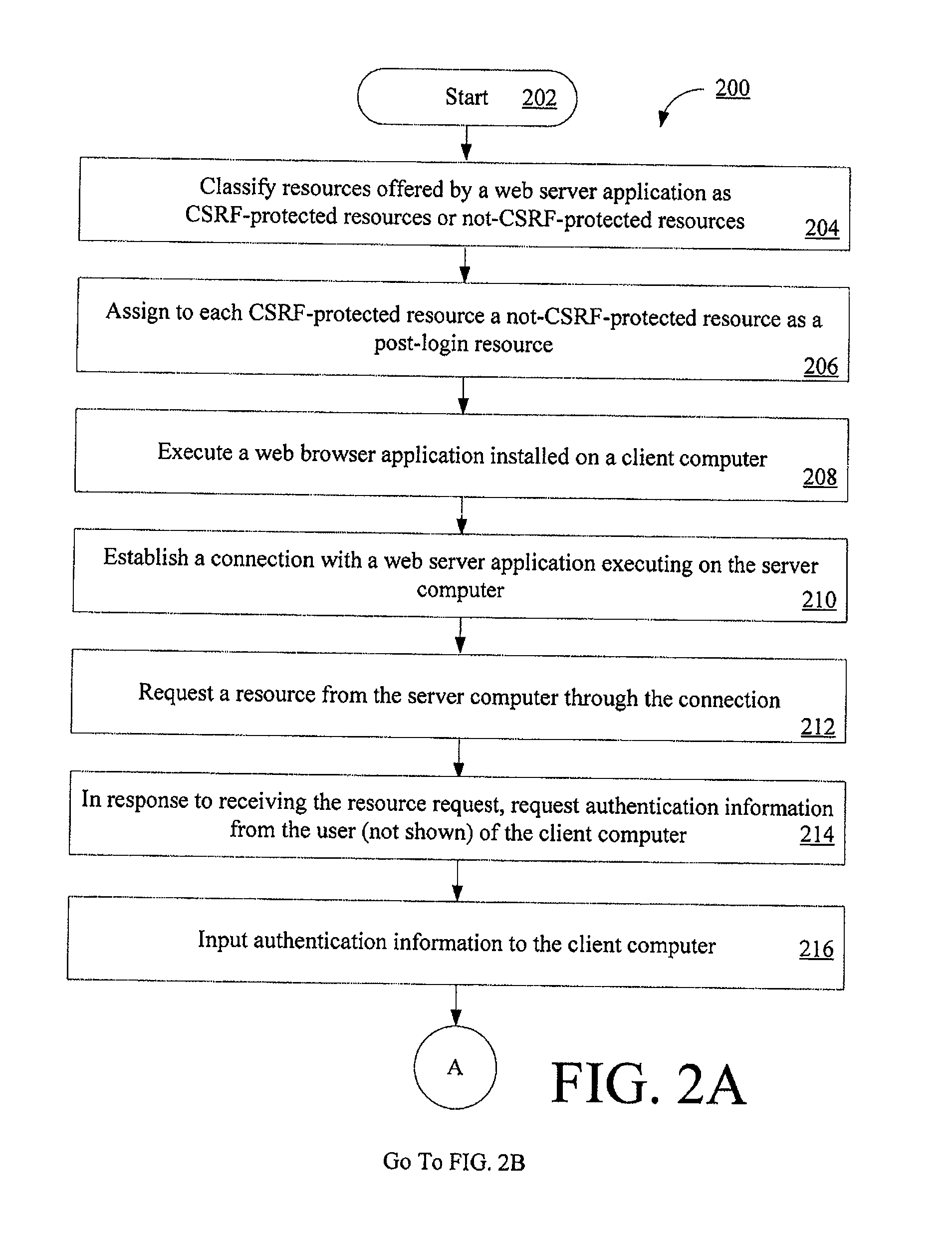
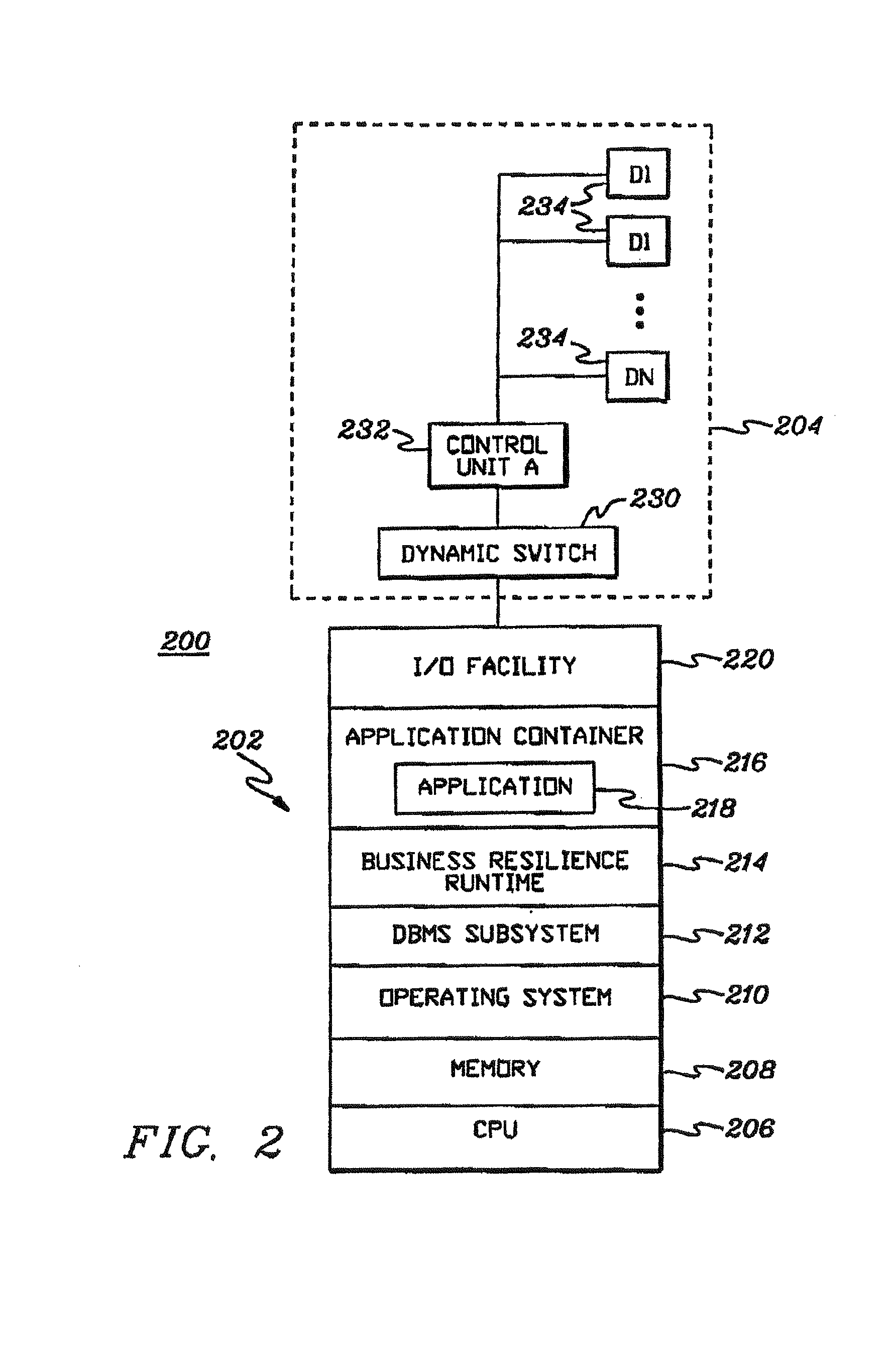
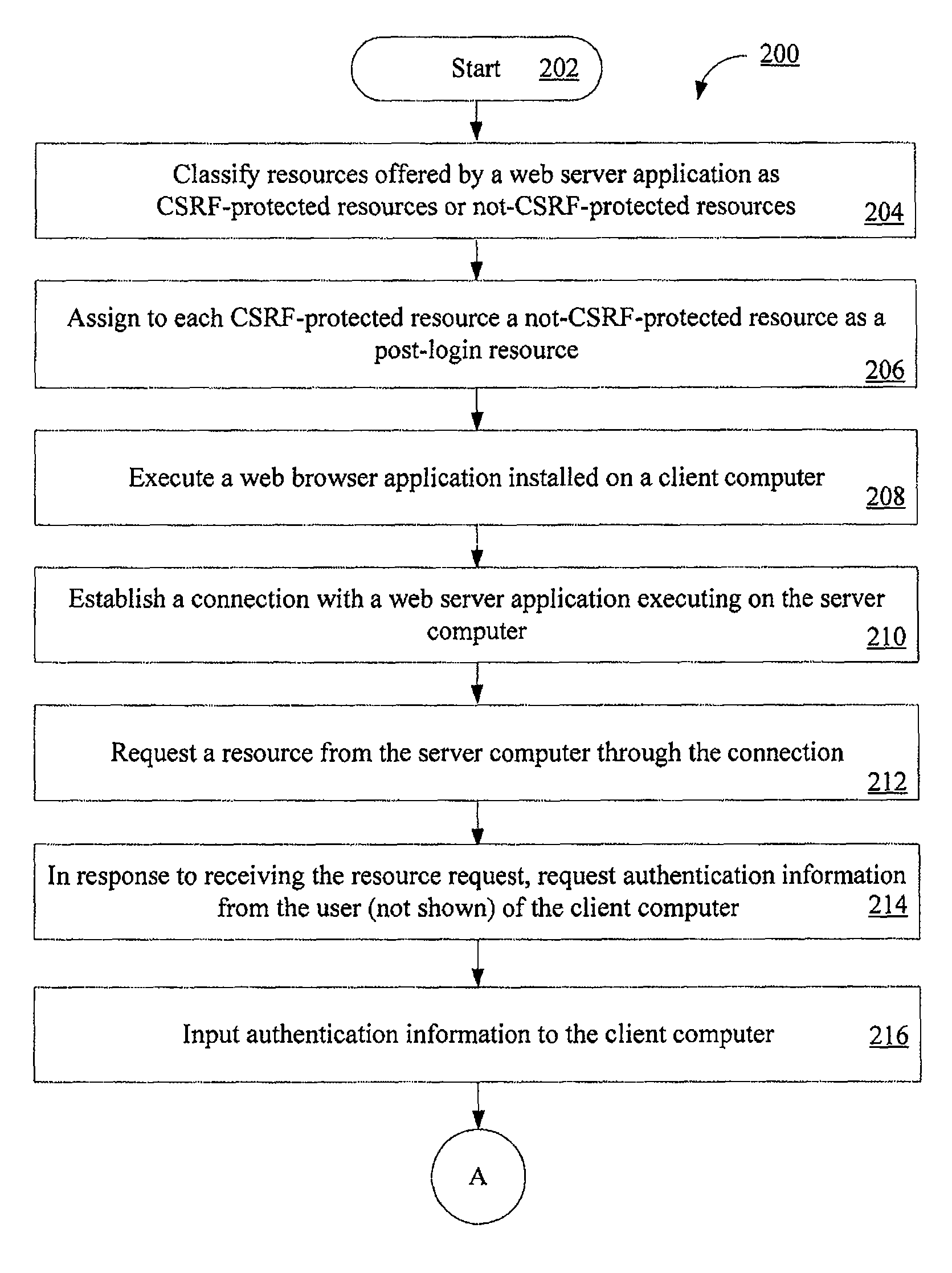
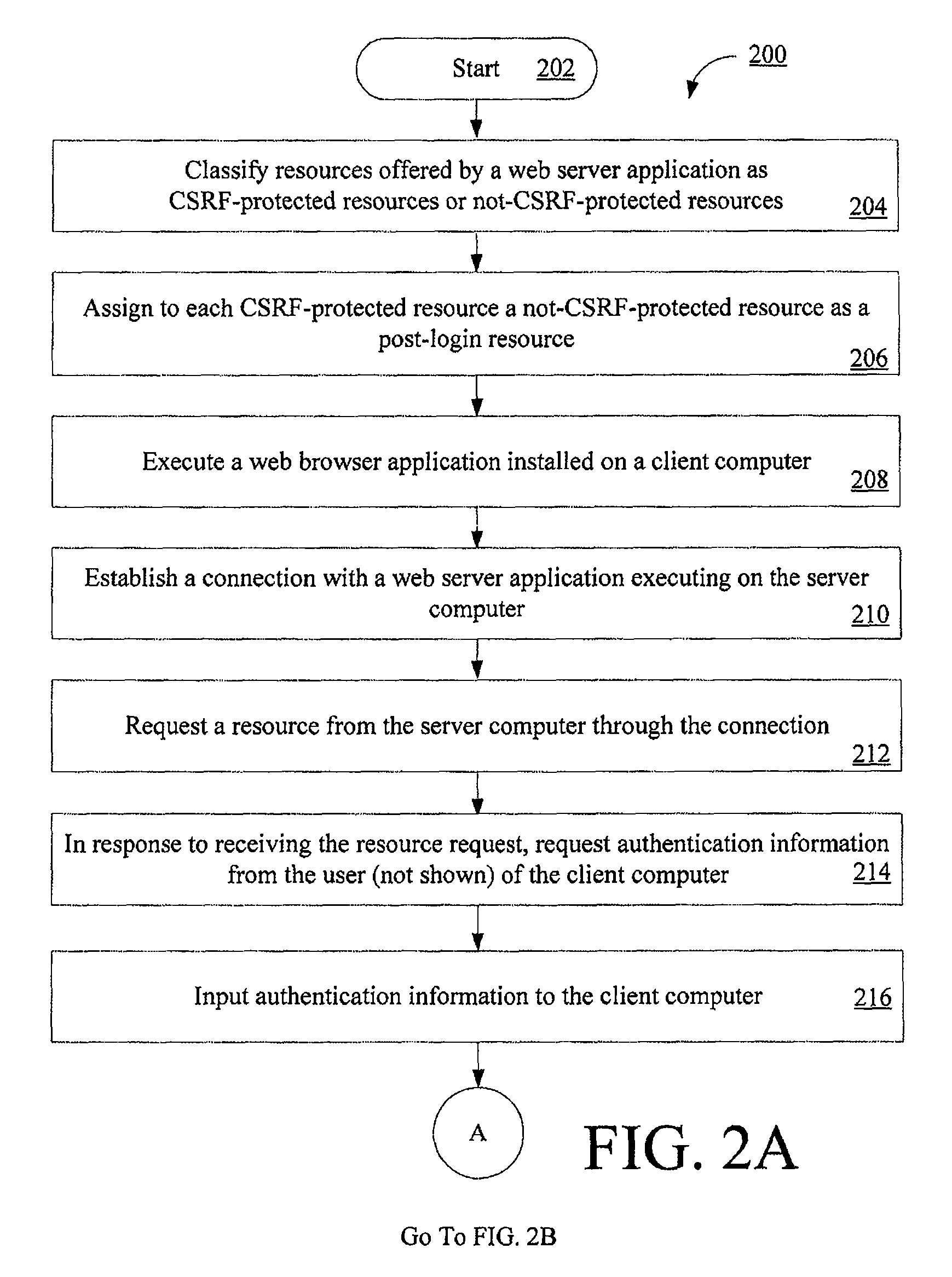
Systems and methods for protecting web based applications from cross site request forgery attacks
InactiveUS20100100927A1Digital data processing detailsUser identity/authority verificationCross-site request forgeryWeb service
Computer implemented methods (200) for protecting web based applications (110, 114) from Cross Site Request Forgery (CSRF) attacks. The methods involve (204) classifying each resource offered by a web server application as a CSRF-protected resource or a not-CSRF-protected resource. The methods also involve (214, . . . , 222) performing a user authentication, (224) initializing an authentication-token, and (226) initializing a CSRF protection secret that is used to validate CSRF protection parameters contained in resource identifiers for the resources. The methods further involve (228) performing a server-side rewriting process (300) to add the CSRF protection parameter to the resource identifiers for the resources and / or (230) performing a client-side rewriting process to add the CSRF protection parameter to a resource identifier for a second resource (e.g., a resource created at a client computer (102)).
Owner:IBM CORP
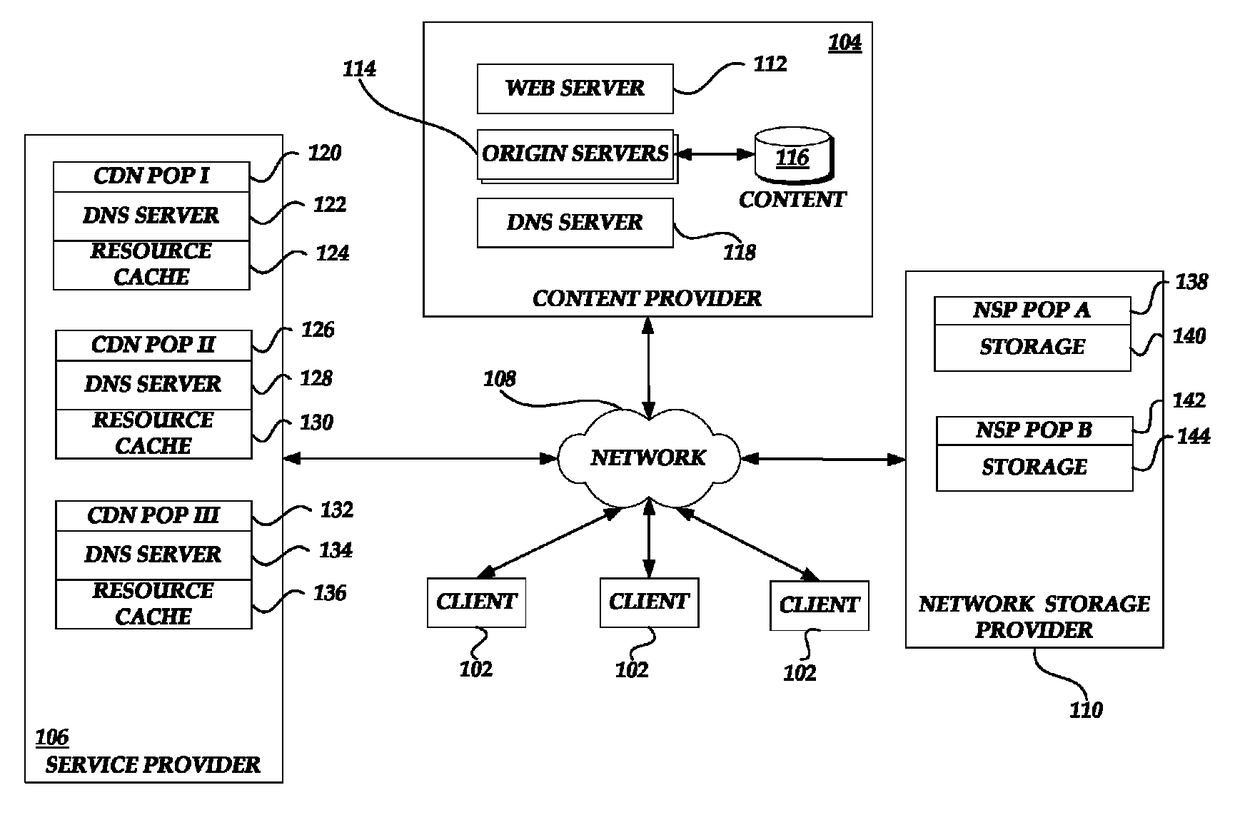
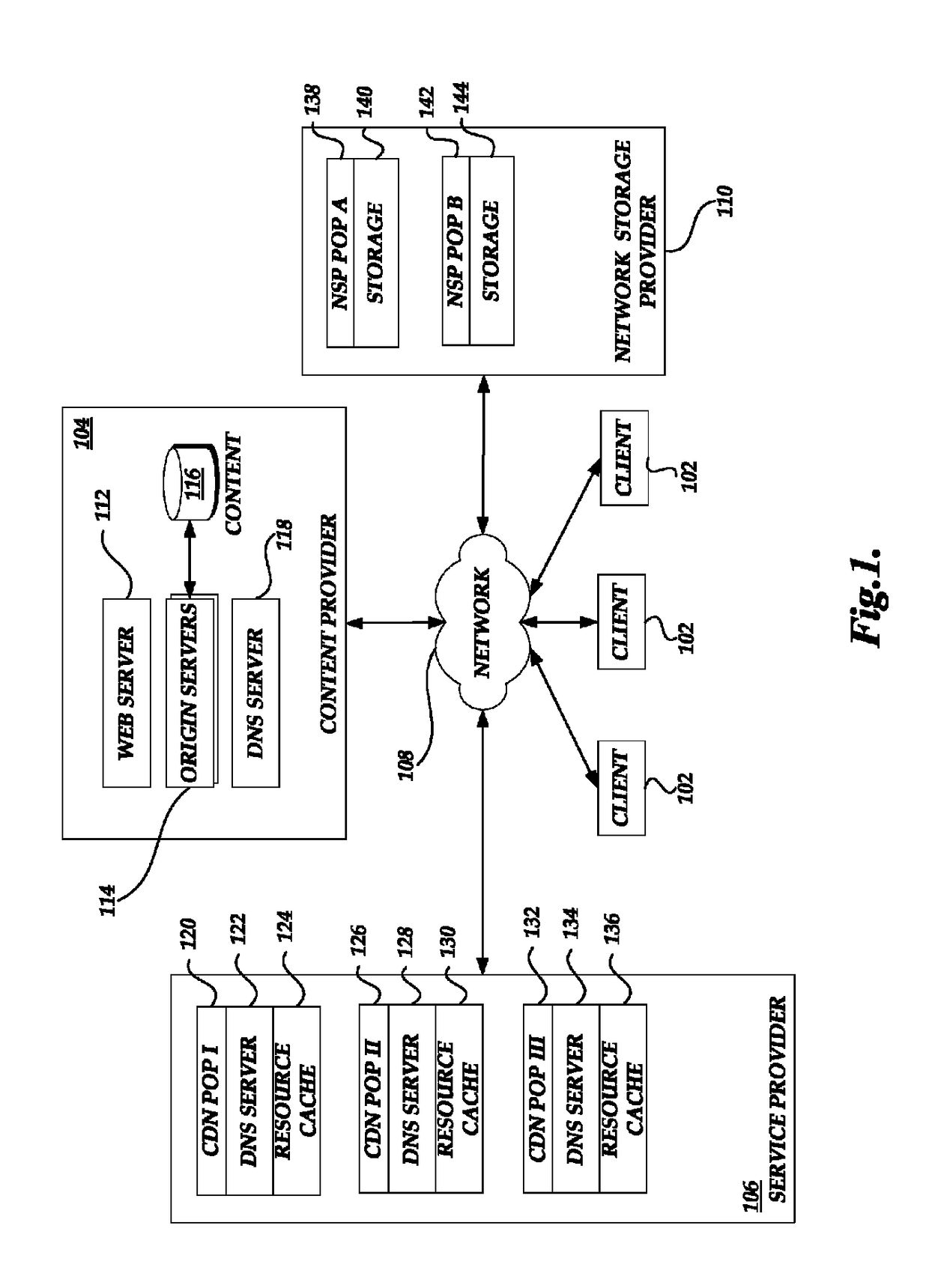
Request routing processing
Generally described, the present disclosure is directed to managing request routing functionality corresponding to resource requests for one or more resources associated with a content provider. The processing of the DNS requests by the service provider can include the selective filtering of DNS queries associated with a DNS query-based attack. A service provider can assign DNS servers corresponding to a distributed set of network addresses, or portions of network addresses, such that DNS queries exceeding a threshold, such as in DNS query-based attacks, can be filtered in a manner that can mitigate performance impact on for the content provider or service provider.
Owner:AMAZON TECH INC
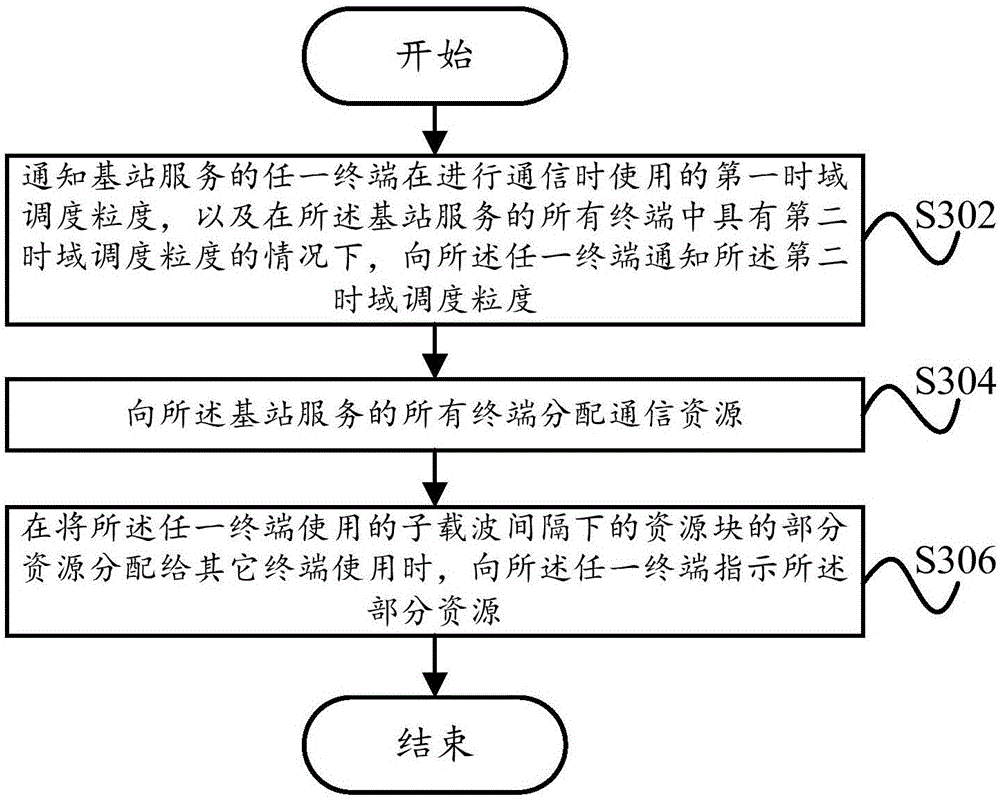
Resource allocation method and resource allocation device
ActiveCN106455103AGuaranteed maximum utilizationAccurately informedWireless communicationTime domainGranularity
The invention provides a resource allocation method and a resource allocation device. The resource allocation method comprises the steps of notifying any terminal served at a base station of a first time domain scheduling granularity used when communication is carried out, and under the condition of having a second time domain scheduling granularity in all terminals served at the base station, notifying the any terminal of the second time domain scheduling granularity; allocating communication resources to all terminals served at the base station; and when allocating partial resources of a resource block under a sub-carrier spacing used by the any terminal to other terminals to use, indicating the any terminal of the partial resources. According to the technical scheme provided by the invention, when the base station allocates the resources to multiple terminals which use different time domain scheduling granularities, the maximum utilization of the resources can be guaranteed, and the terminals can be indicated accurately to learn the allocated communication resources.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Apparatus and methods for managing resource usage
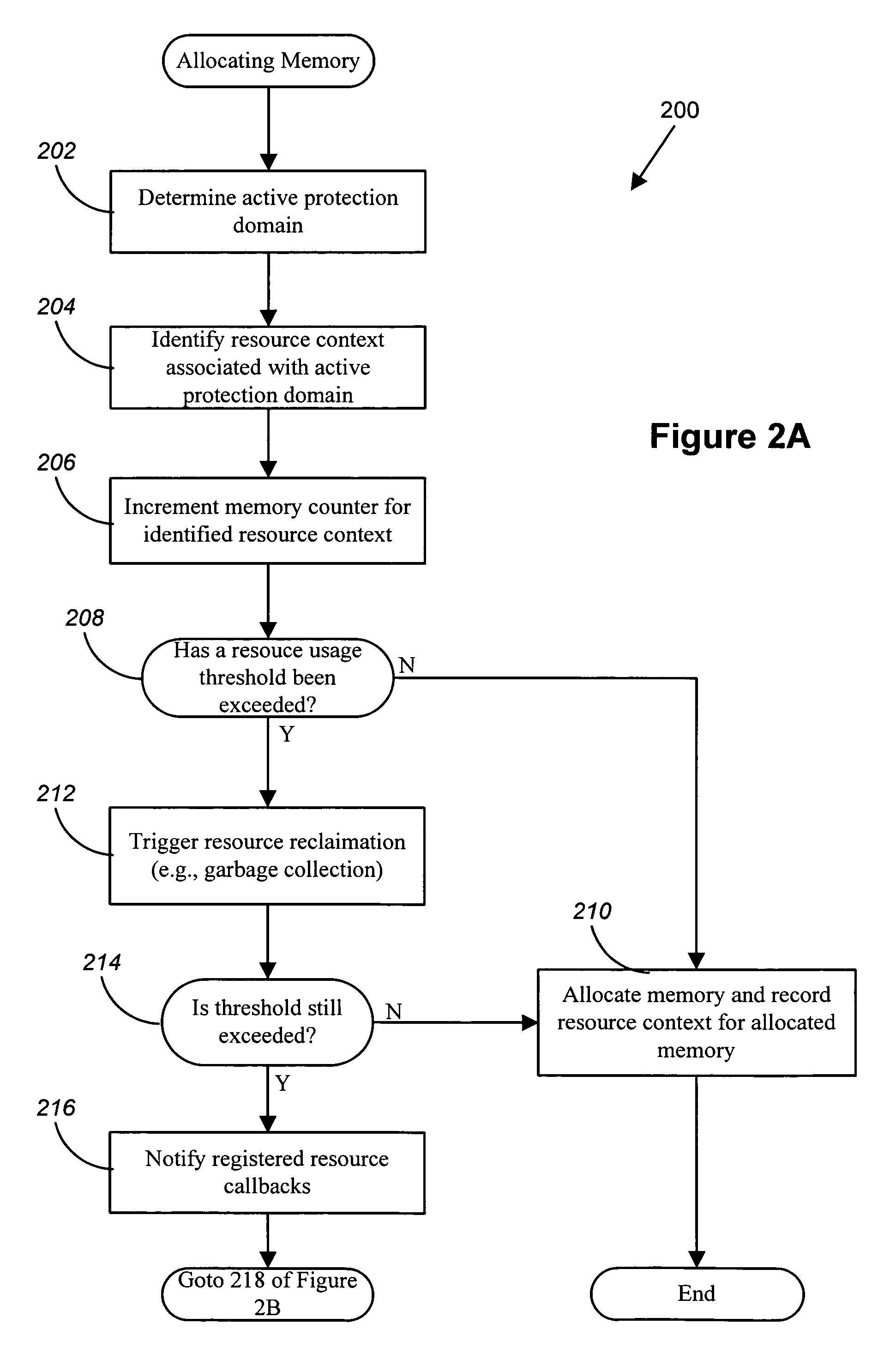
InactiveUS7028298B1Usage can be carefullyImprove resource utilizationEnergy efficient ICTResource allocationDistributed computingResources of a Resource
Owner:ORACLE INT CORP
Management of computer events in a computer environment
The scope and impact of an event, such as a failure, are identified. A Containment Region is used to identify the resources affected by the event. It is also used to aggregate resource state for those resources. This information is then used to manage one or more aspects of a customer's environment. This management may include recovery from a failure.
Owner:IBM CORP
Systems and methods for protecting web based applications from cross site request forgery attacks
InactiveUS8020193B2Digital data processing detailsAnalogue secracy/subscription systemsCross-site request forgeryWeb service
Computer implemented methods (200) for protecting web based applications (110, 114) from Cross Site Request Forgery (CSRF) attacks. The methods involve (204) classifying each resource offered by a web server application as a CSRF-protected resource or a not-CSRF-protected resource. The methods also involve (214, . . . , 222) performing a user authentication, (224) initializing an authentication-token, and (226) initializing a CSRF protection secret that is used to validate CSRF protection parameters contained in resource identifiers for the resources. The methods further involve (228) performing a server-side rewriting process (300) to add the CSRF protection parameter to the resource identifiers for the resources and / or (230) performing a client-side rewriting process to add the CSRF protection parameter to a resource identifier for a second resource (e.g., a resource created at a client computer (102)).
Owner:INT BUSINESS MASCH CORP
Extensible framework to support different deployment architectures
ActiveUS20110029673A1Metering/charging/biilling arrangementsError detection/correctionDistributed computingResources of a Resource
Owner:EBAY INC
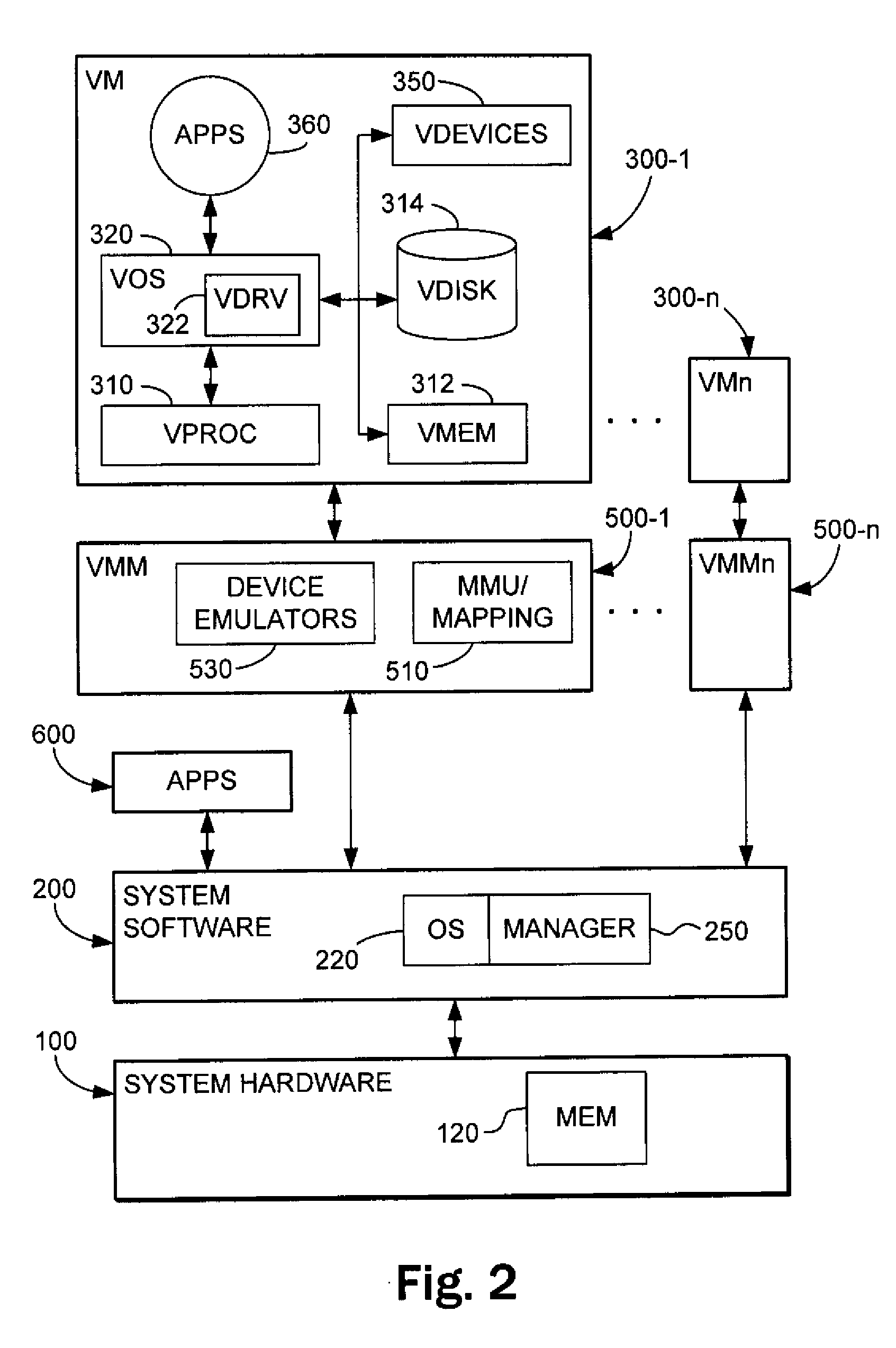
Negotiated assignment of resources to a virtual machine in a multi-virtual machine environment
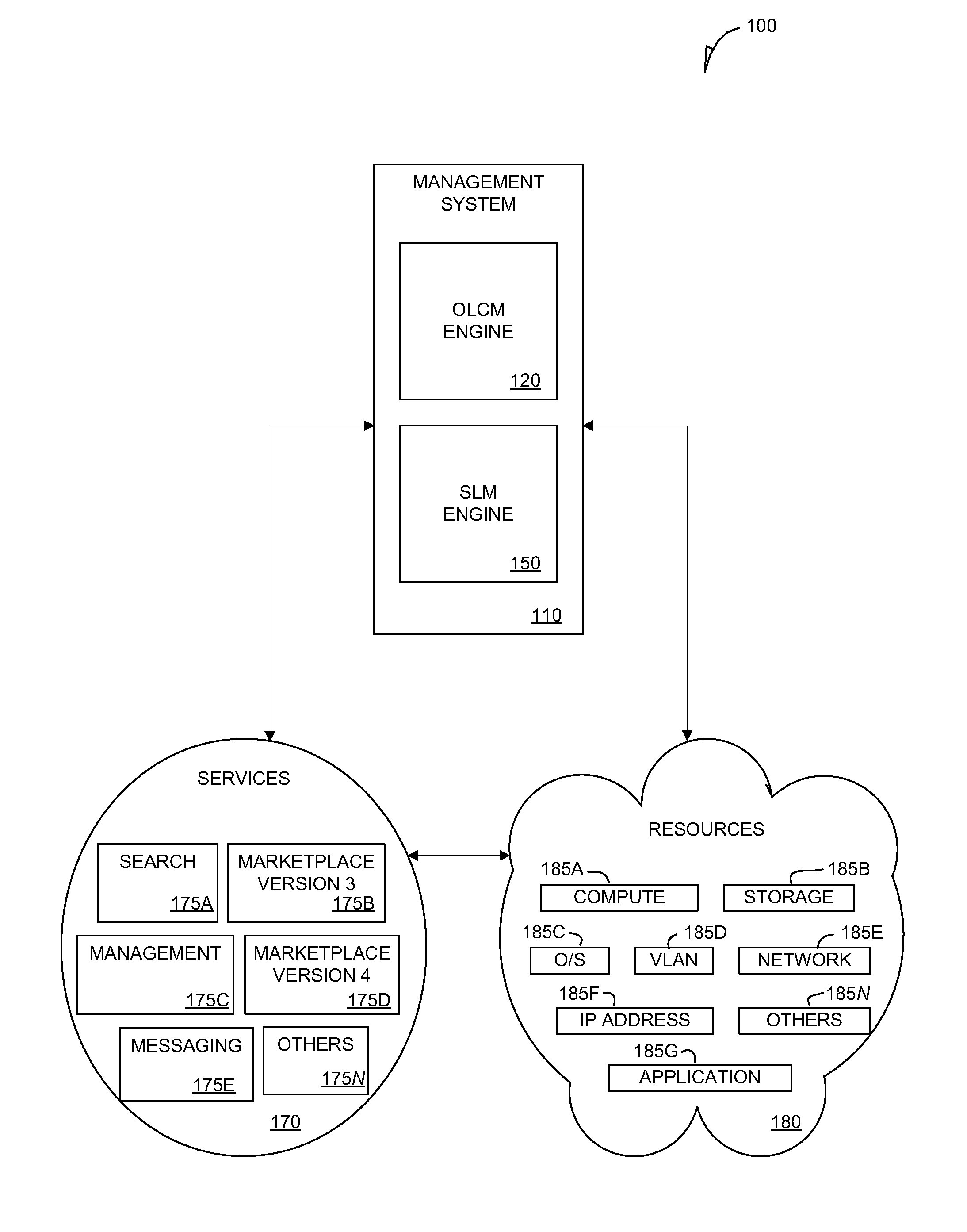
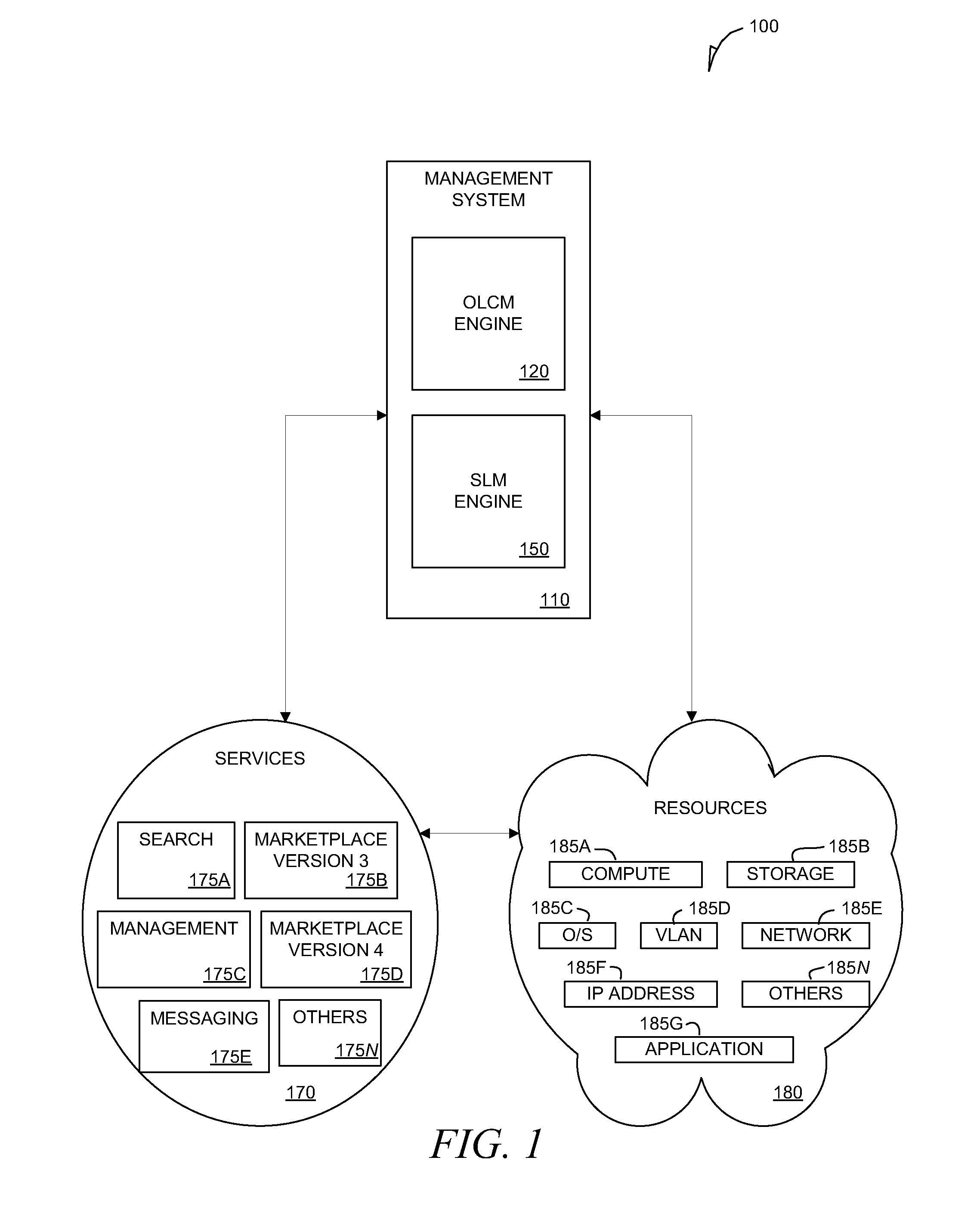
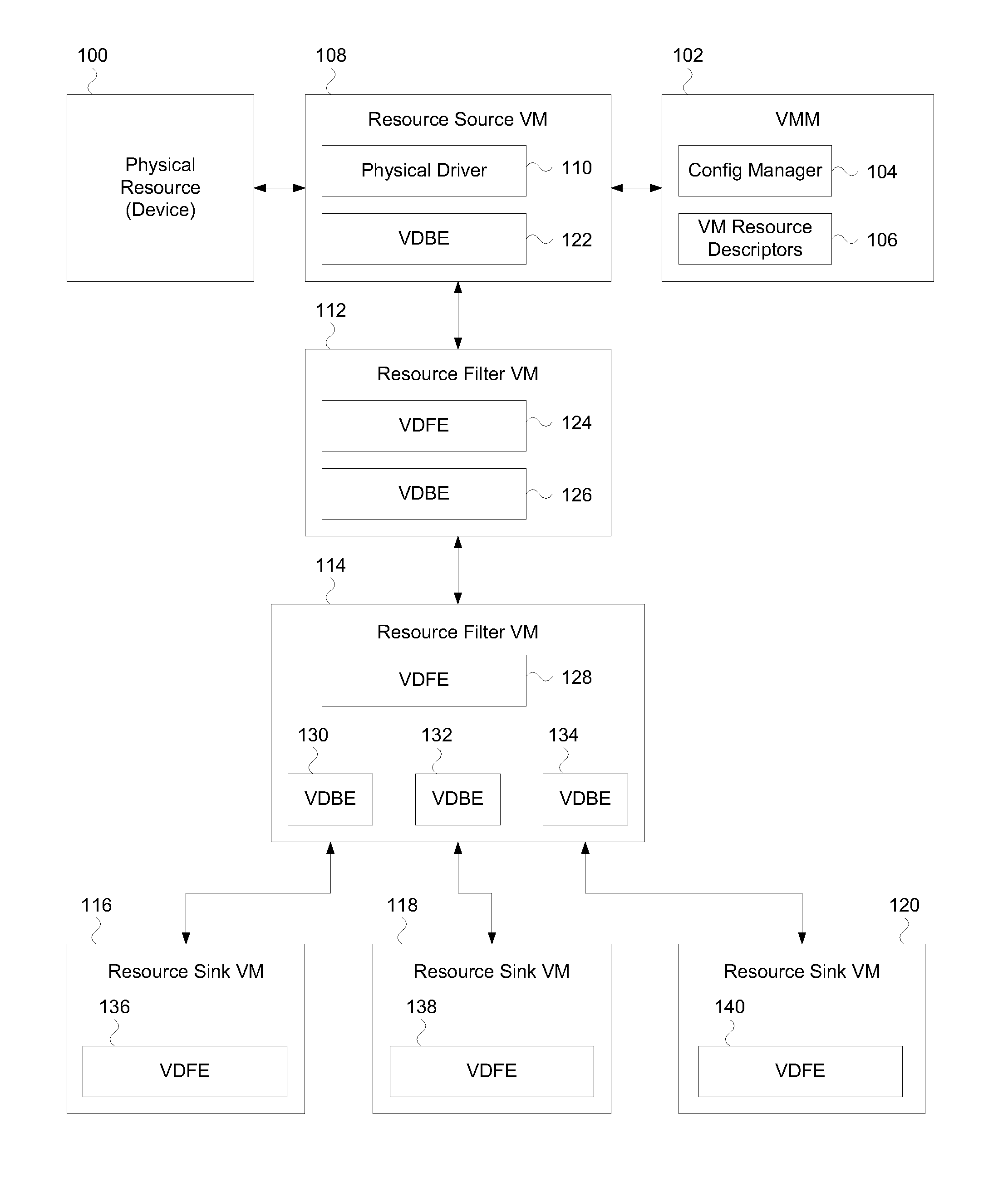
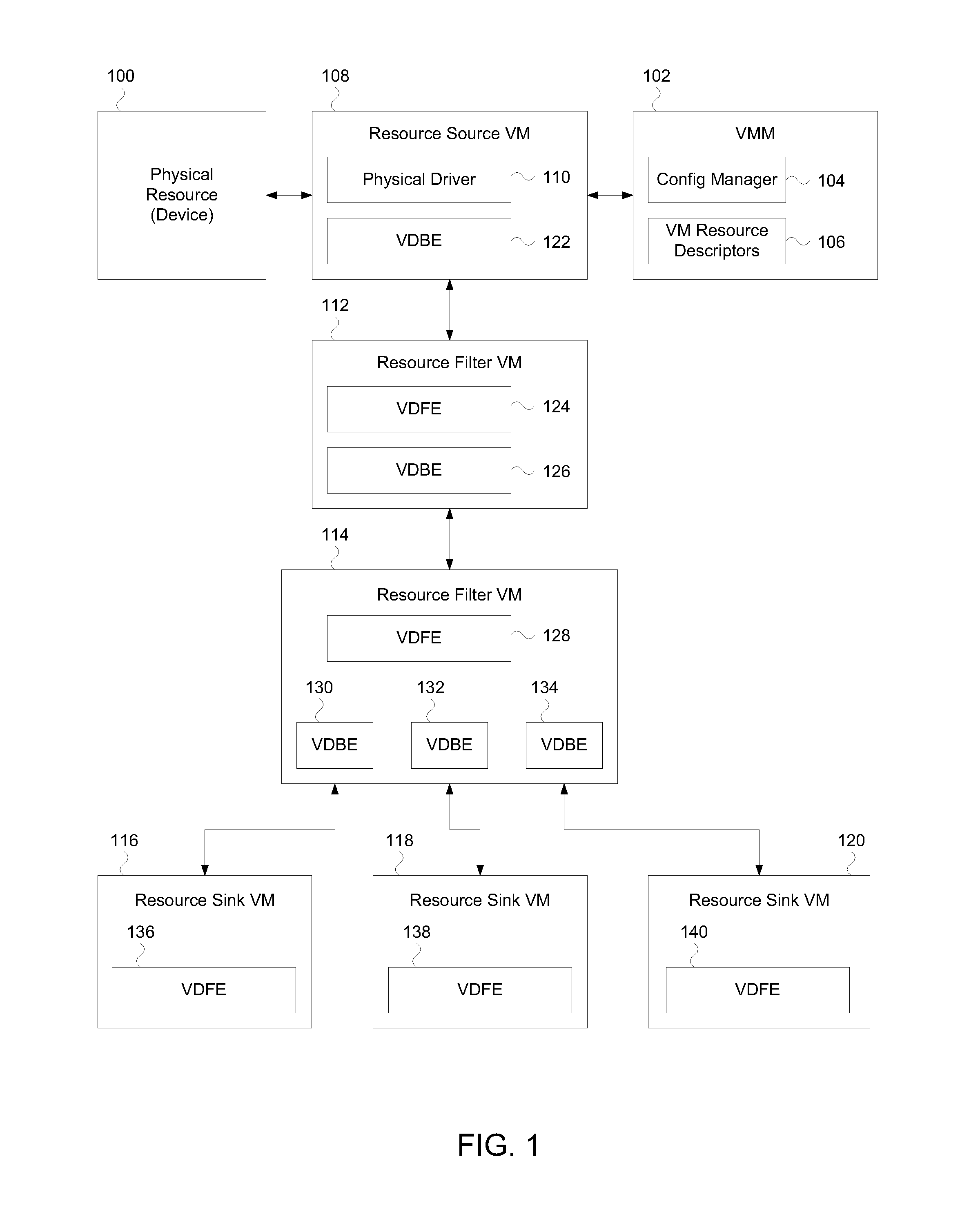
InactiveUS20090172660A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationResources of a ResourceVirtual machine
A system and method are disclosed. In one embodiment the system includes a physical resource that is capable of generating I / O data. The system also includes multiple virtual machines to utilize the physical resource. Among the virtual machines are a resource source virtual machine that is capable of owning the physical resource. The resource source virtual machine is also capable of sending a stream of one or more I / O packets generated from the I / O data that targets a resource sink virtual machine. The resource sink virtual machine is designated as a termination endpoint of the I / O data from the physical device. Also among the virtual machines are one or more resource filter virtual machines. Each of the resource filter virtual machines is capable of filtering I / O packets of a particular type from the stream prior to the stream reaching the resource sink virtual machine.
Owner:INTEL CORP
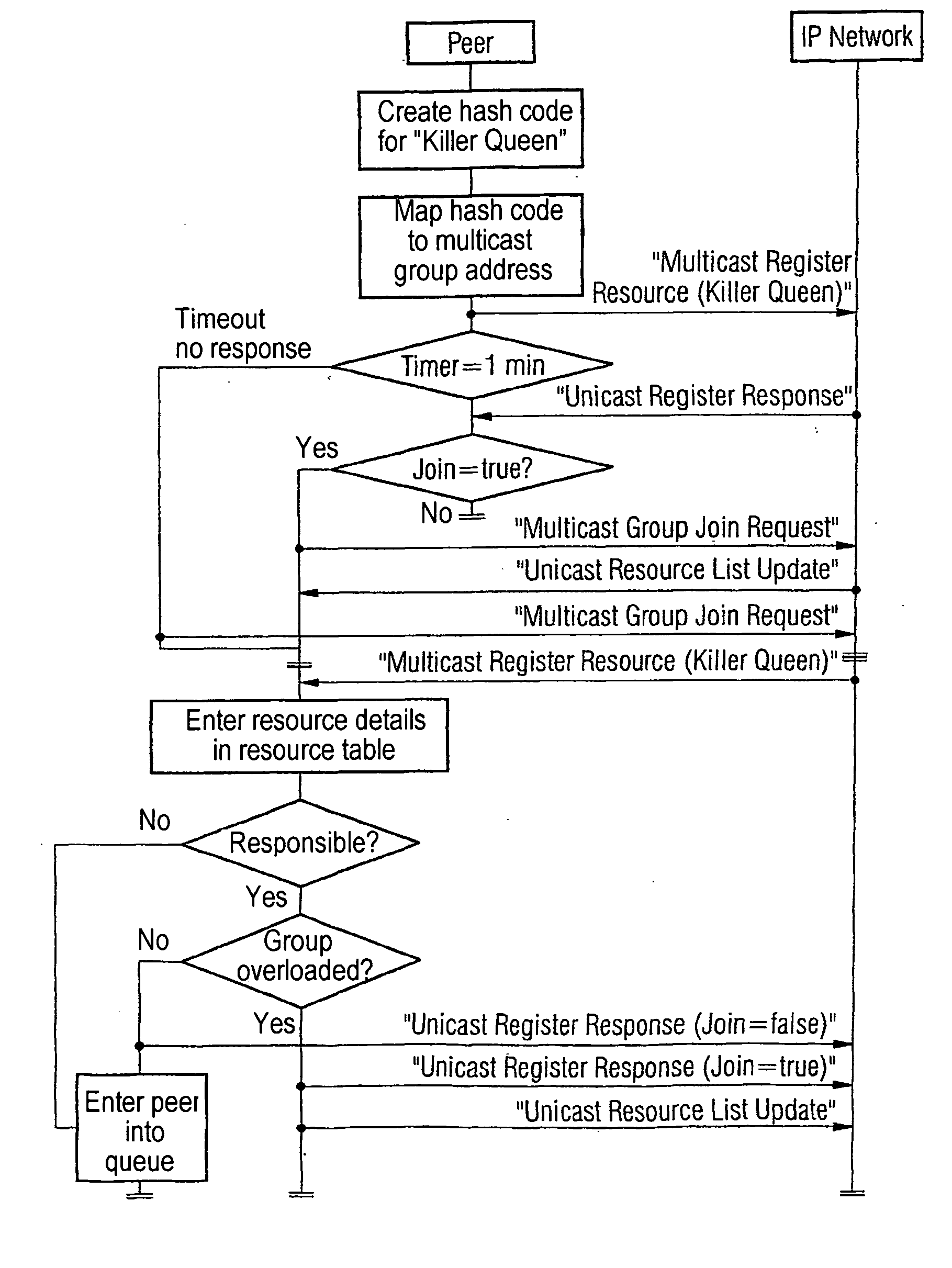
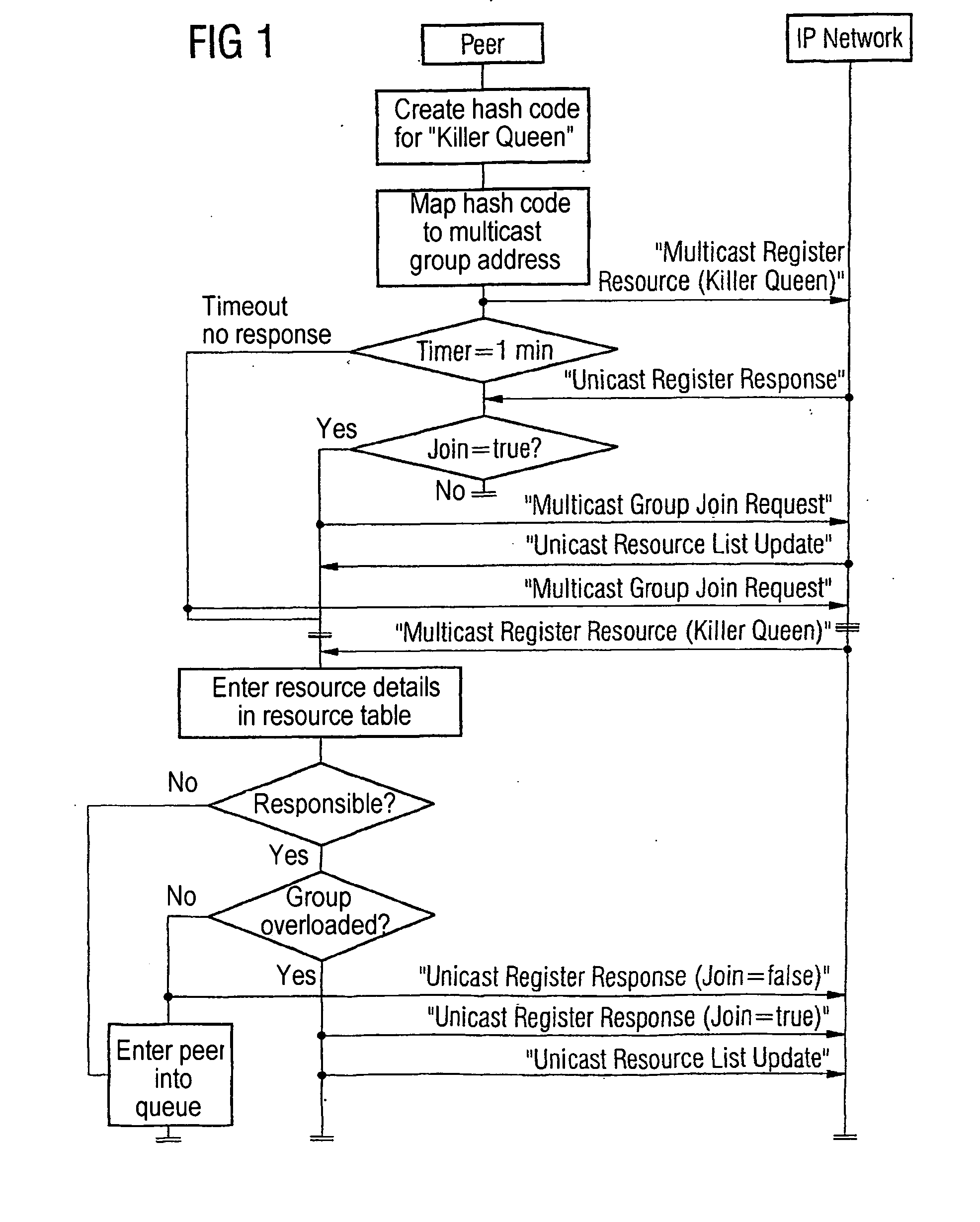
Scalable peer-to-peer network with a directory service
ActiveUS20050021617A1Quick searchImprove availabilitySpecial service provision for substationMultiple digital computer combinationsResource allocationDistributed computing
A method for creates a directory service in a scalable peer-to-peer-network, which is distributed to groups having at least one peer. In order to release a resource and to start a search enquiry for a resource, allocation values are formed using an allocation instruction according to the resource allocation values from a predefined address area. Only one group is responsible for each allocation value and the release of a resource or search enquiry for a resource is transmitted to the responsible group only.
Owner:SIEMENS AG
Multithreading framework supporting dynamic load balancing and multithread processing method using the same
InactiveUS20090150898A1Improve performanceMultiprogramming arrangementsMemory systemsDynamic load balancingApplication software
A multithreading framework supporting dynamic load balancing, the multithreading framework being used to perform multi-thread programming, the multithreading framework includes a job scheduler for performing parallel processing by redefining a processing order of one or more unit jobs, transmitted from a predetermined application, based on unit job information included in the respective unit jobs, and transmitting the unit jobs to a thread pool based on the redefined processing order, a device enumerator for detecting a device in which the predetermined application is executed and defining resources used inside the application, a resource manager for managing the resources related to the predetermined application executed using the job scheduler or the device enumerator, and a plug-in manager for managing a plurality of modules which performs various types of functions related to the predetermined application in a plug-in manner, and providing such plug-in modules to the job scheduler.
Owner:ELECTRONICS & TELECOMM RES INST
Managing network data transfers in a virtual computer system
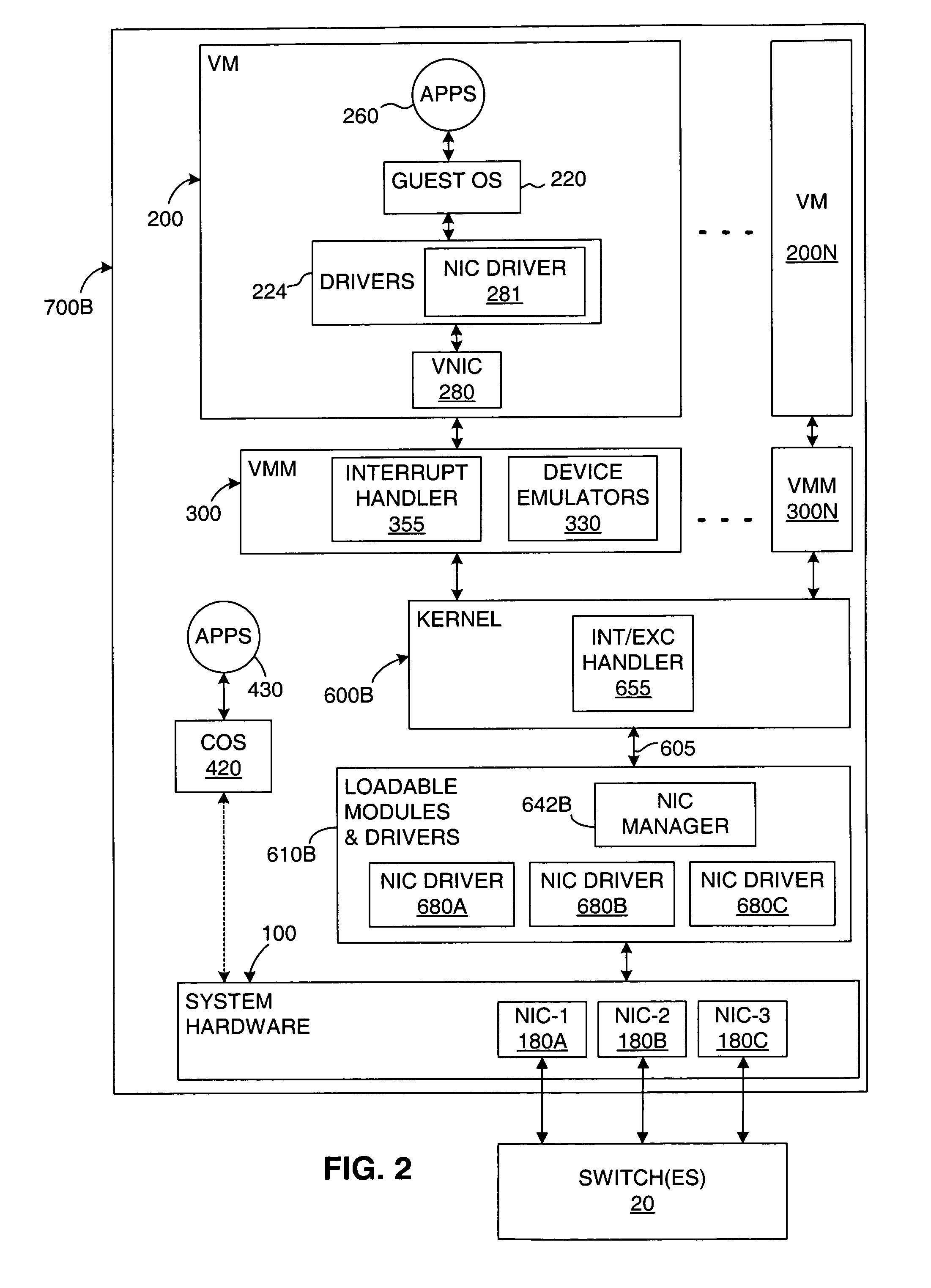
ActiveUS7934020B1Reduce riskComputer security arrangementsMultiple digital computer combinationsFailoverComputerized system
A virtual computer system, including one or more virtual machines (VMs), is connected to a computer network by multiple network interface cards (NICs). The VMs are supported by a kernel, which includes a resource manager for allocating system resources among the VMs, including network data bandwidth. A NIC manager is loaded into the kernel as a driver or is integrated into the kernel, for selecting NICs over which outgoing network data is transferred, including providing functions such as failovers and failbacks, as well as load distribution. Implementing the NIC manager in the kernel provides NIC teaming functions to each of the VMs without having to implement a NIC teaming solution in each of the VMs, adding to the simplicity, flexibility and portability of the VMs. In addition, integrating the NIC manager into the kernel improves the kernel's ability to manage the VMs and to implement network resource allocations for the VMs.
Owner:VMWARE INC
Uplink power control
Apparatuses, methods, and systems are disclosed for uplink power control. One method includes: receiving a message that configures a set of resources that each includes a downlink resource or an uplink sounding resource and is associated with an uplink transmission beam pattern; receiving scheduling information for an uplink transmission that is associated with a resource of the set of resources; determining an uplink transmission beam pattern associated with the resource; determining a configured maximum output power for the uplink transmission beam pattern that is based on an antenna array property associated with the uplink transmission beam pattern; determining a transmit power for the uplink transmission based on the configured maximum output power; and performing the uplink transmission using the uplink transmission beam pattern based on the transmit power.
Owner:LENOVO (SINGAPORE) PTE LTD
Systems and methods for flexible, extensible authentication subsystem that enabled enhance security for applications
ActiveUS20160381080A1Reduce inventory costsLow costDigital data processing detailsMultiple digital computer combinationsApplication softwareClient-side
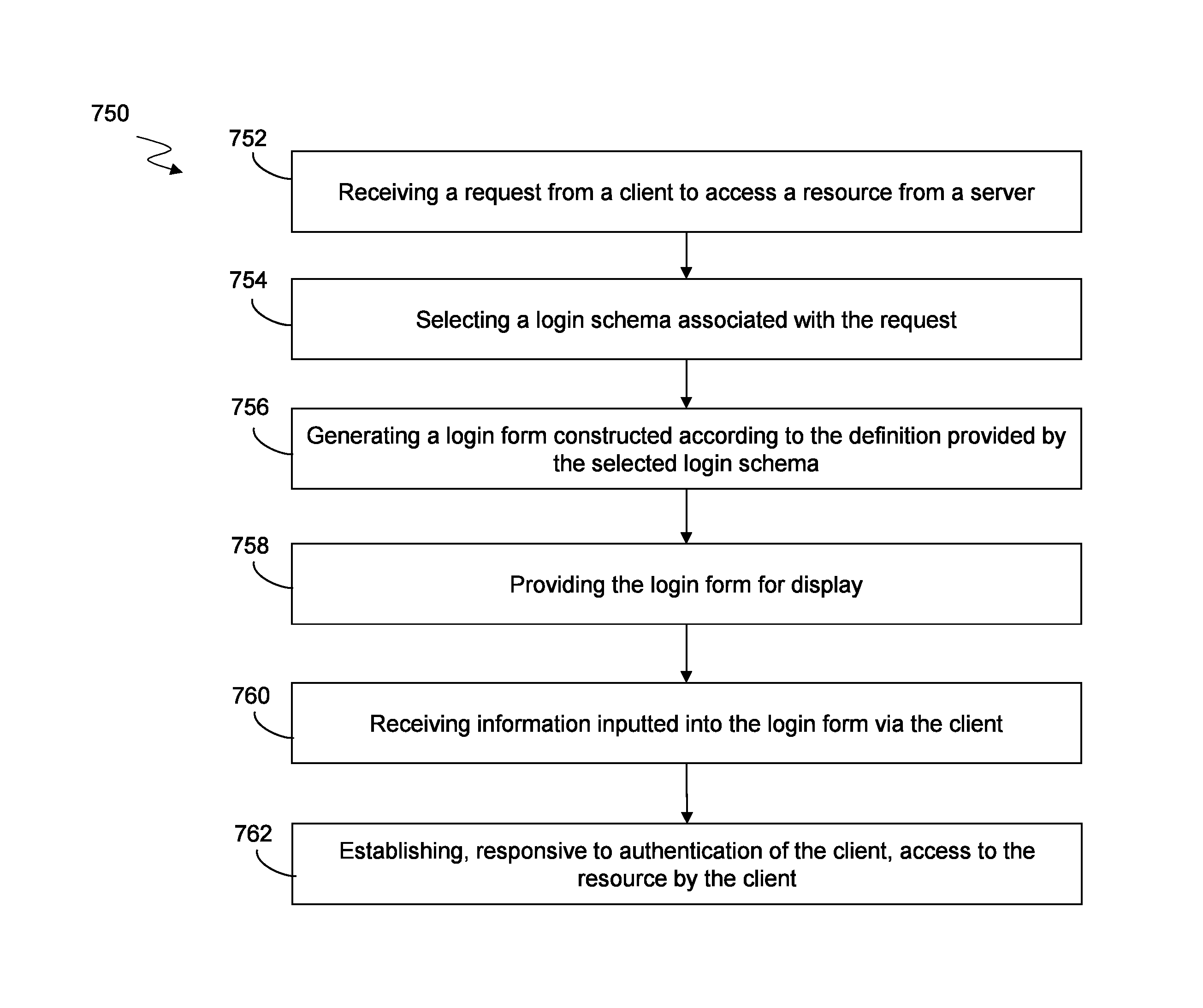
The present disclosure is directed towards systems and methods of authenticating a client. A device intermediary to clients servers that provide one or more resources can receive a request from a client to access a resource of the one or more resources. The device can select a login schema associated with the request that includes a definition of a login form. The login schema may correspond to an authentication protocol. The device can generate the login form responsive to the request. The login form can be constructed according to the definition provided by the selected login schema. The device can provide the login form for display via the client. The device can receive information inputted into the login form via the client. The device can establish access to the resource responsive to authentication of the client based on the information and the authentication protocol.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com