Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
307 results about "Online identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
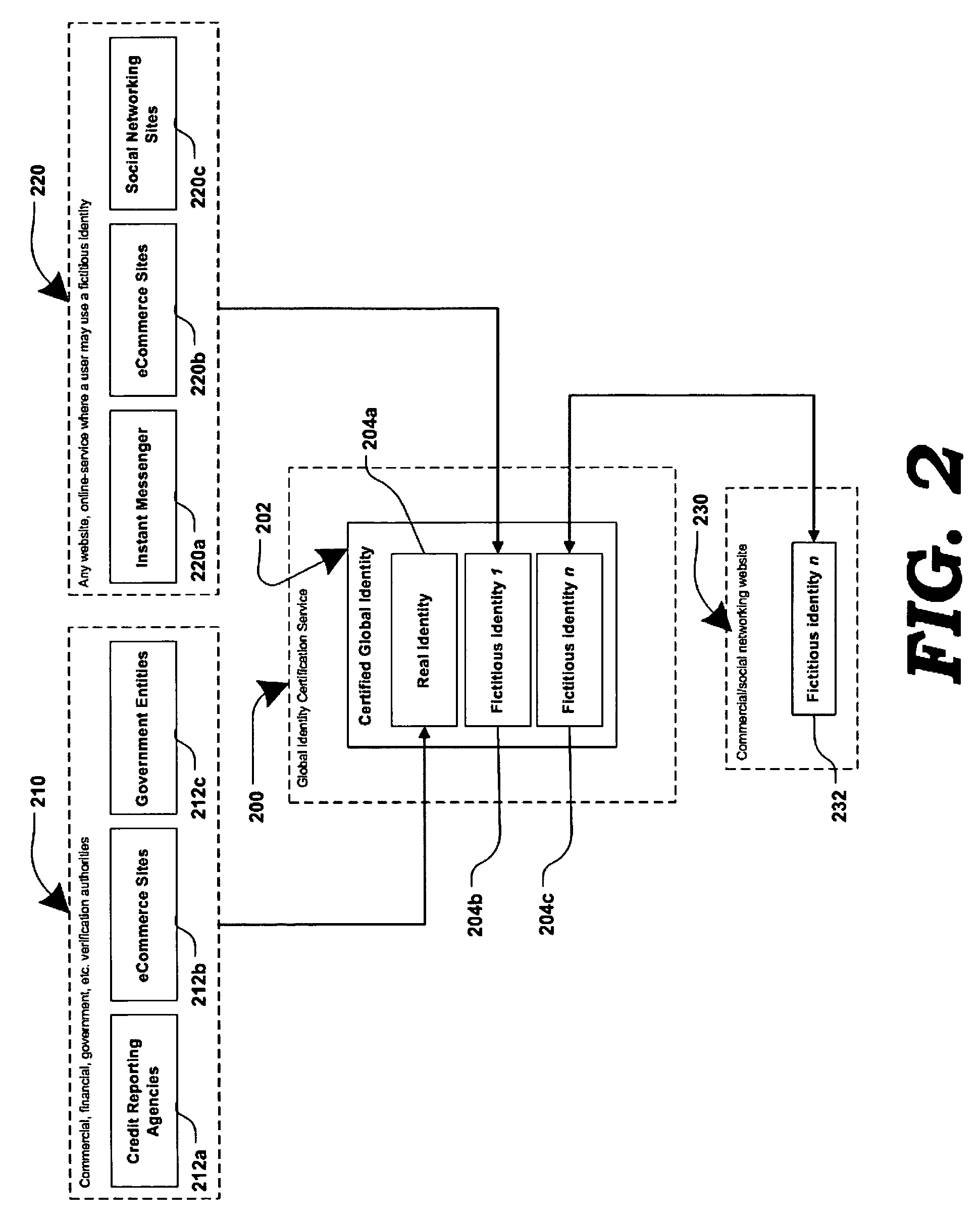
Internet identity (IID), also online identity or internet persona, is a social identity that an Internet user establishes in online communities and websites. It can also be considered as an actively constructed presentation of oneself. Although some people choose to use their real names online, some Internet users prefer to be anonymous, identifying themselves by means of pseudonyms, which reveal varying amounts of personally identifiable information. An online identity may even be determined by a user's relationship to a certain social group they are a part of online. Some can even be deceptive about their identity.
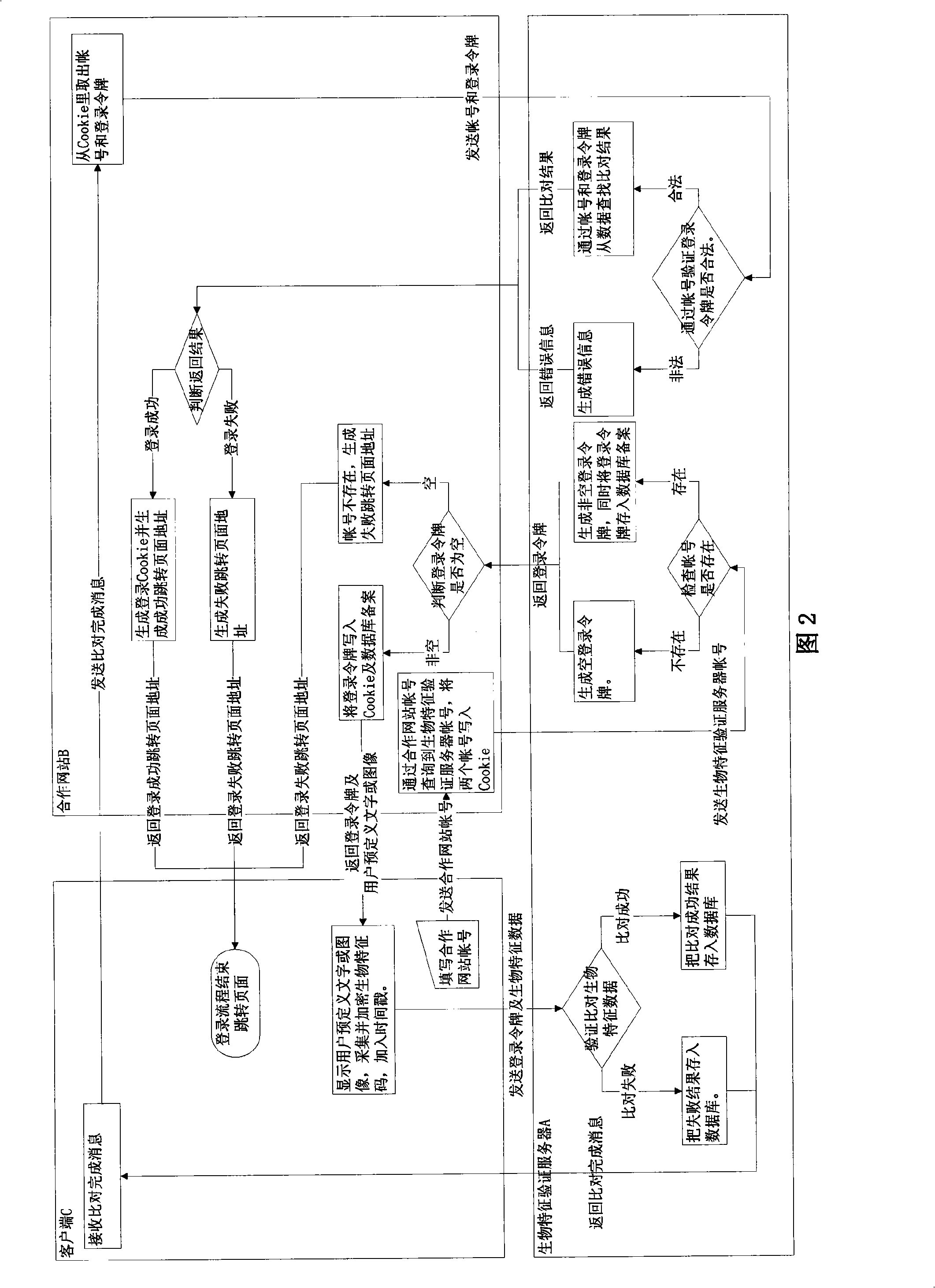
Method and system for securing online identities
InactiveUS8646103B2Targeted optimizationDigital data processing detailsUser identity/authority verificationUser verificationElectronic communication
Owner:JAKOBSON GABRIEL +1
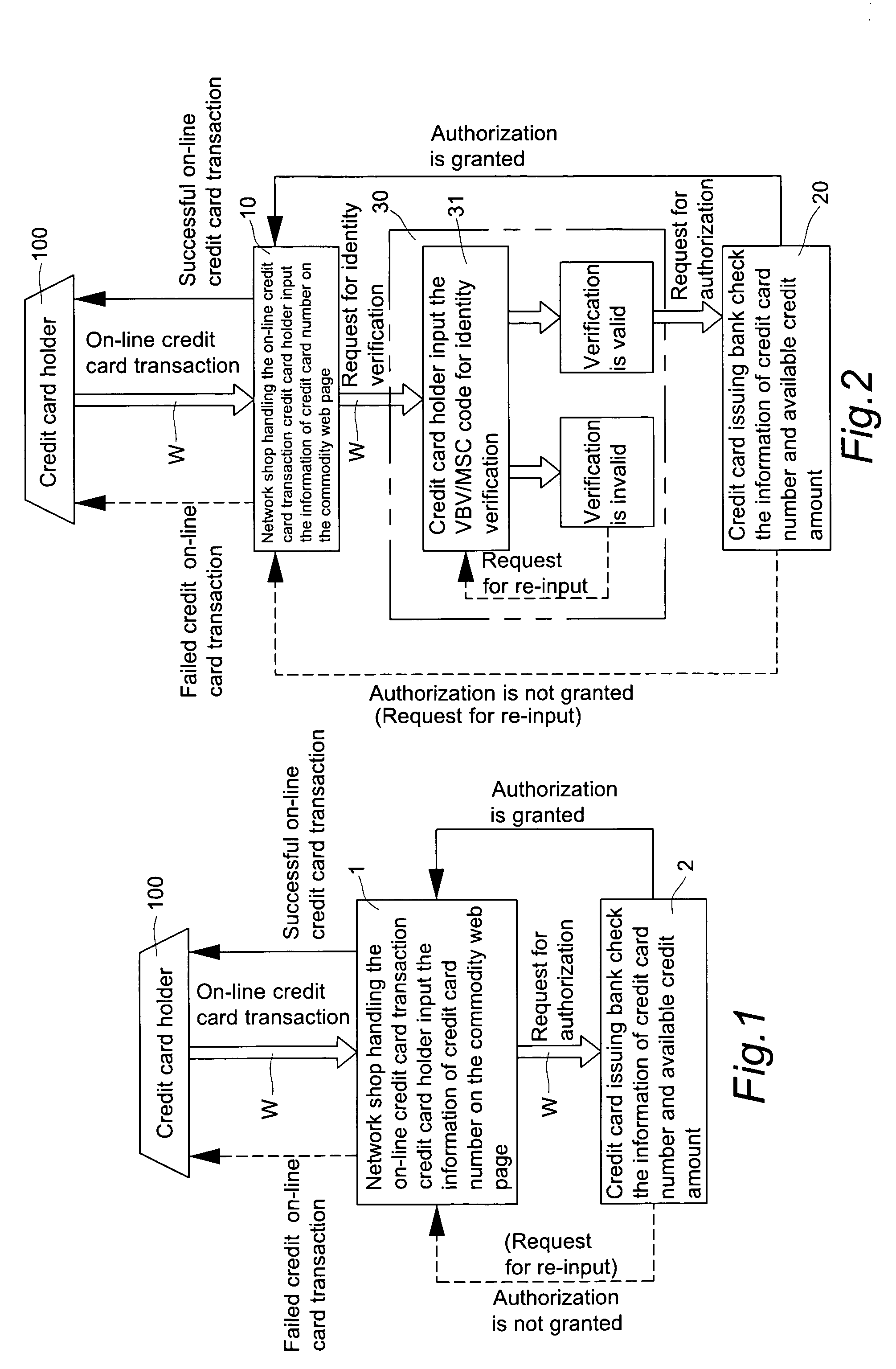
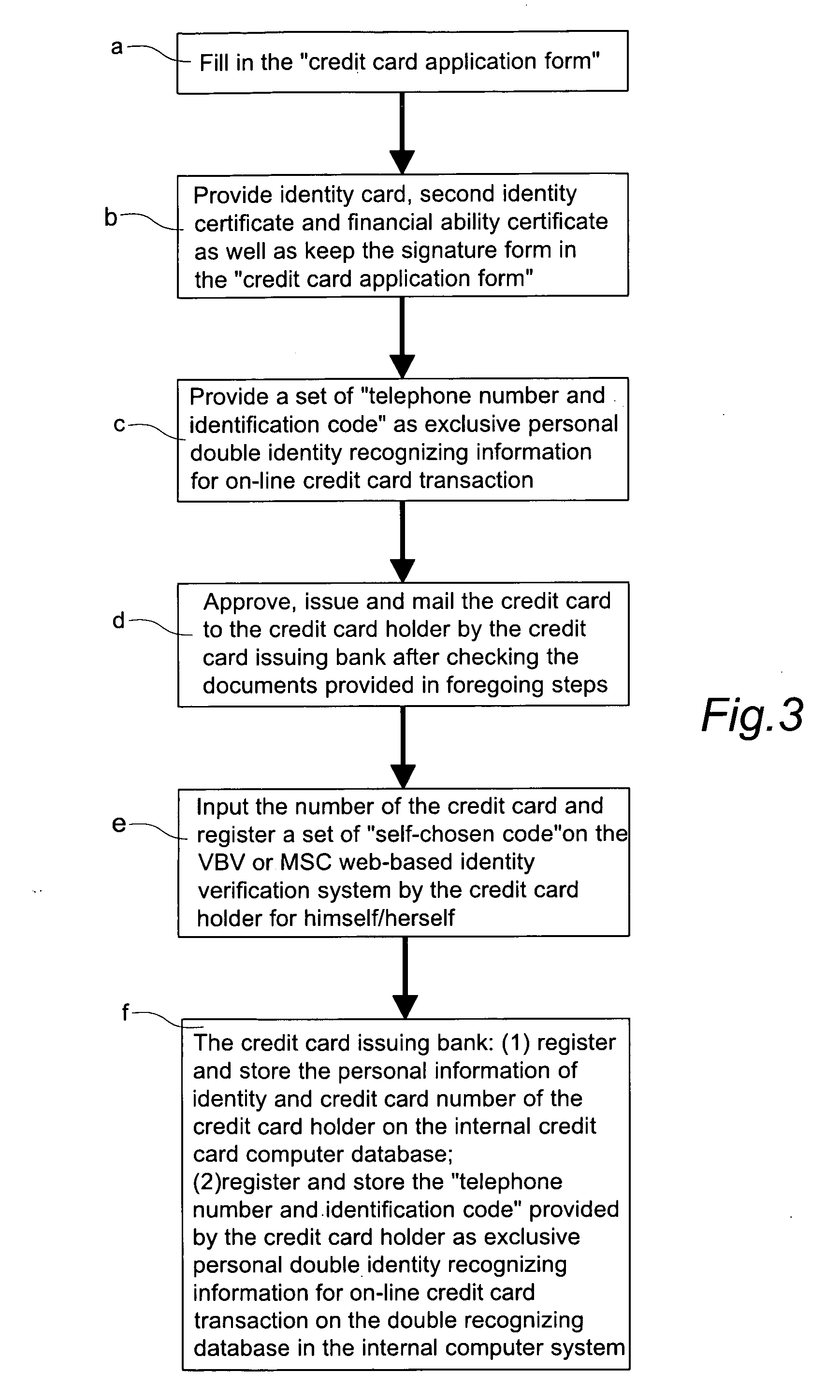
Double recognizing method by means of telephone number and identification code for online credit card transactions over the internet
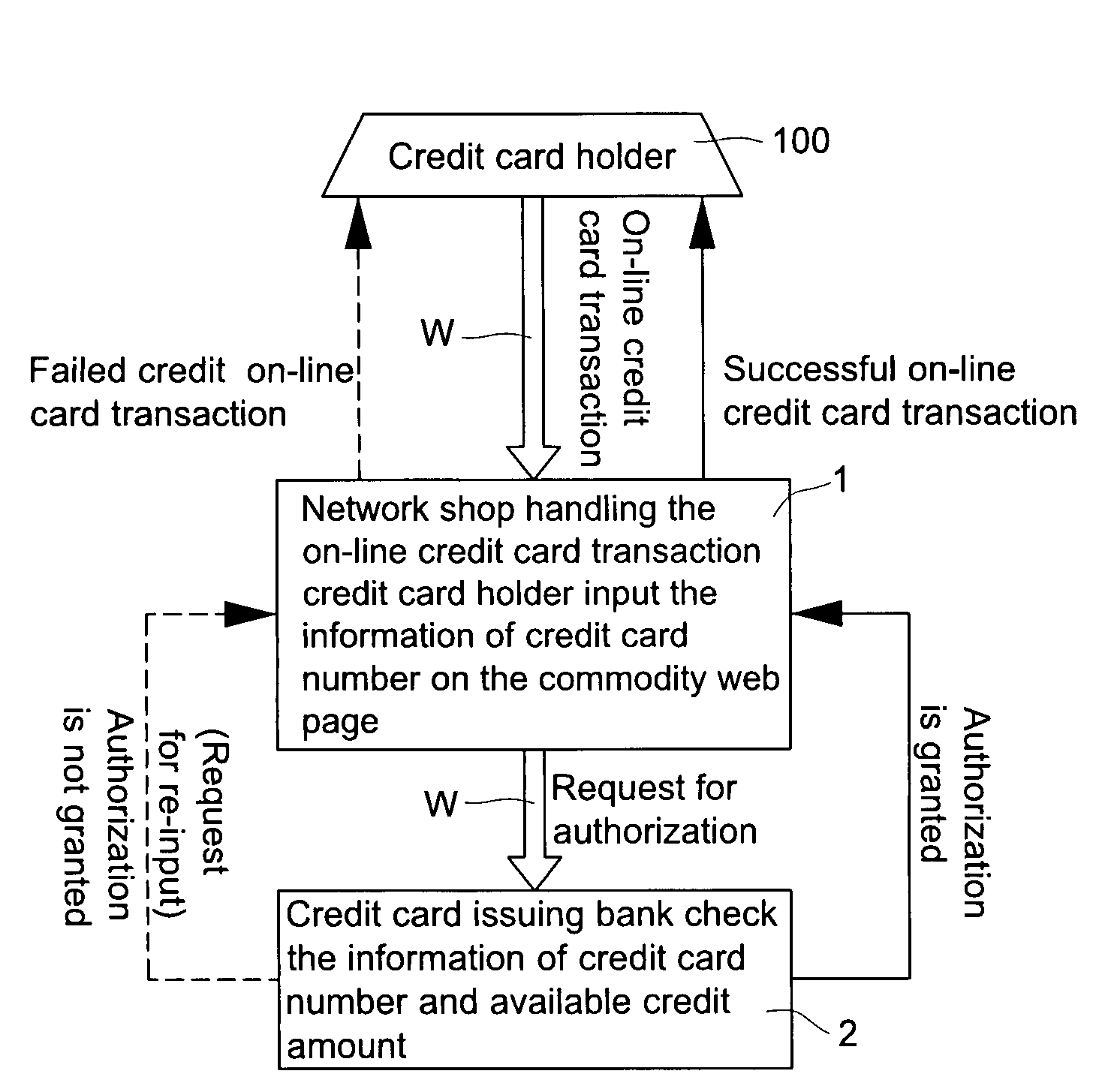
The present invention relates to a “double recognizing method by means of telephone number and identification code for online credit card transactions over the internet,” in which the credit card holder not only registers a “self-chosen code” by himself / herself for VBV (Verified By VISA) or MSC (MasterCard SecureCode) network identity verification but also registers another set of “telephone number and identification code” by himself / herself for serving as an exclusive personal double identity recognizing information for online credit card transactions. The credit card issuing bank registers and stores the set of “telephone number and identification code” on a double recognizing database after checking truth of the related identity certificate provided by the credit card holder. When the credit card issuing bank handles the online credit card transaction of the credit card holder over the network, the credit card issuing bank not only proceeds the check on the “self-chosen code” used in the original VBV or MSC verification system but also performs the double check on the “telephone number and identification code” used in the telecommunications transceiving processor platform of the internal credit card double recognizing computer system, for example by sending out a short message to the credit card holder for requesting him / her to immediately reply by another short message to his / her “telephone number and identification code.”
Owner:LIN CHUNG YU
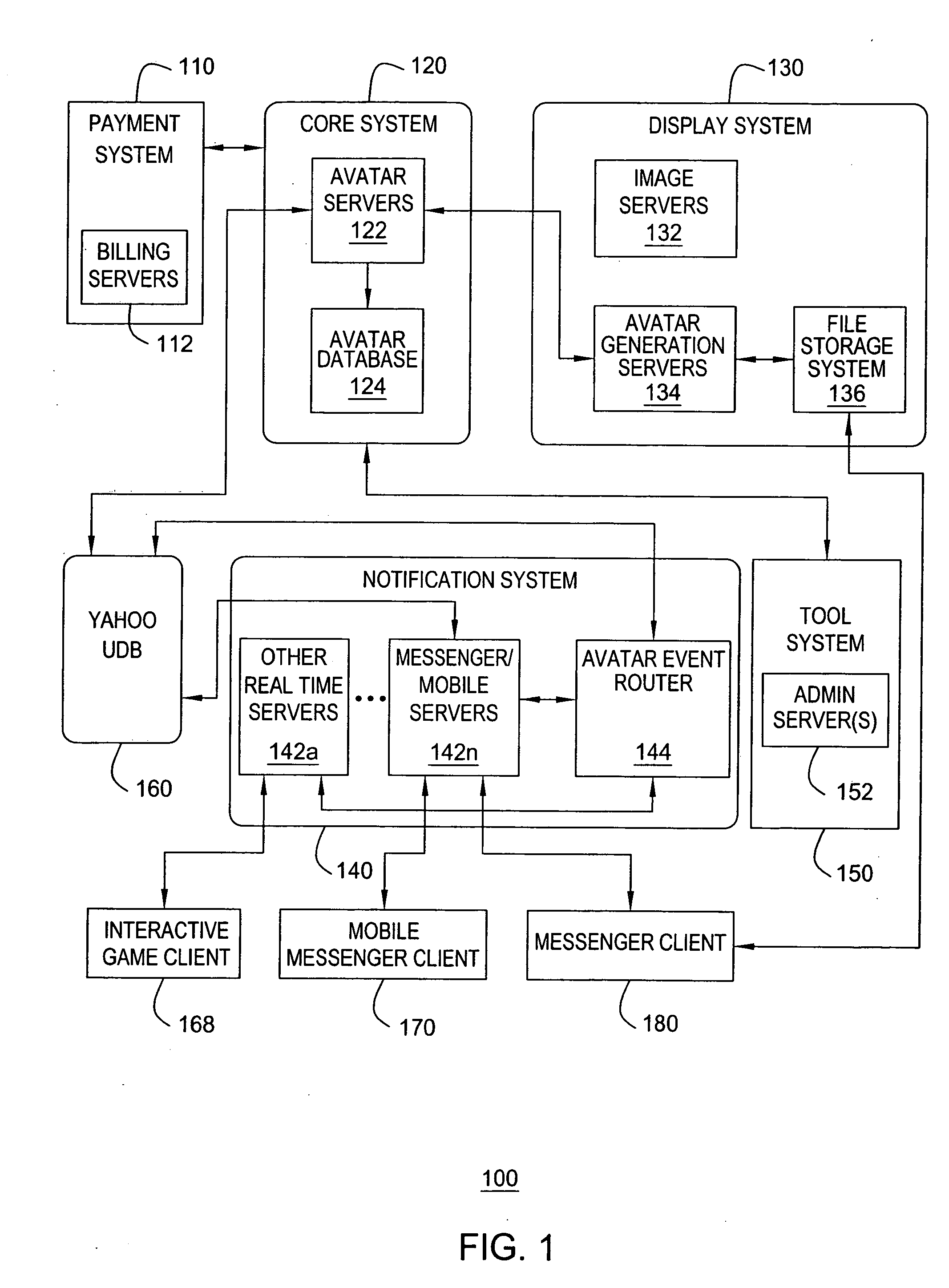
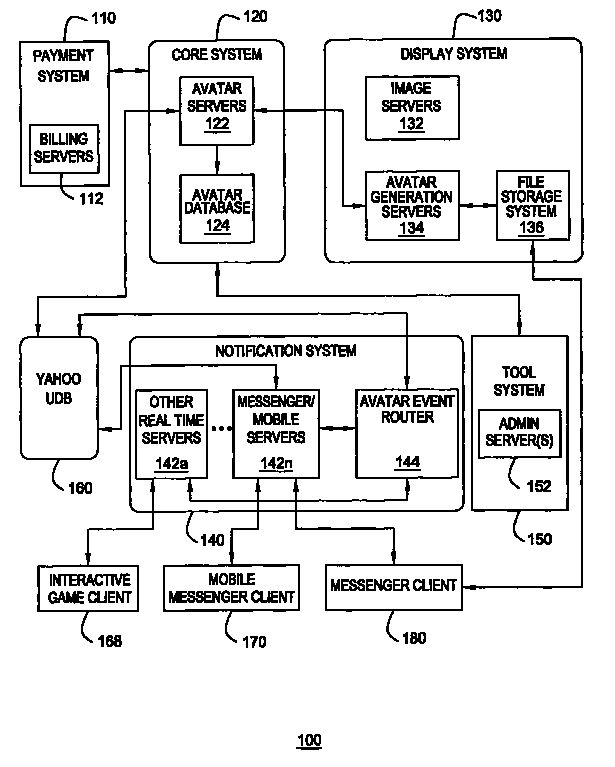
Method and apparatus for providing dynamic moods for avatars
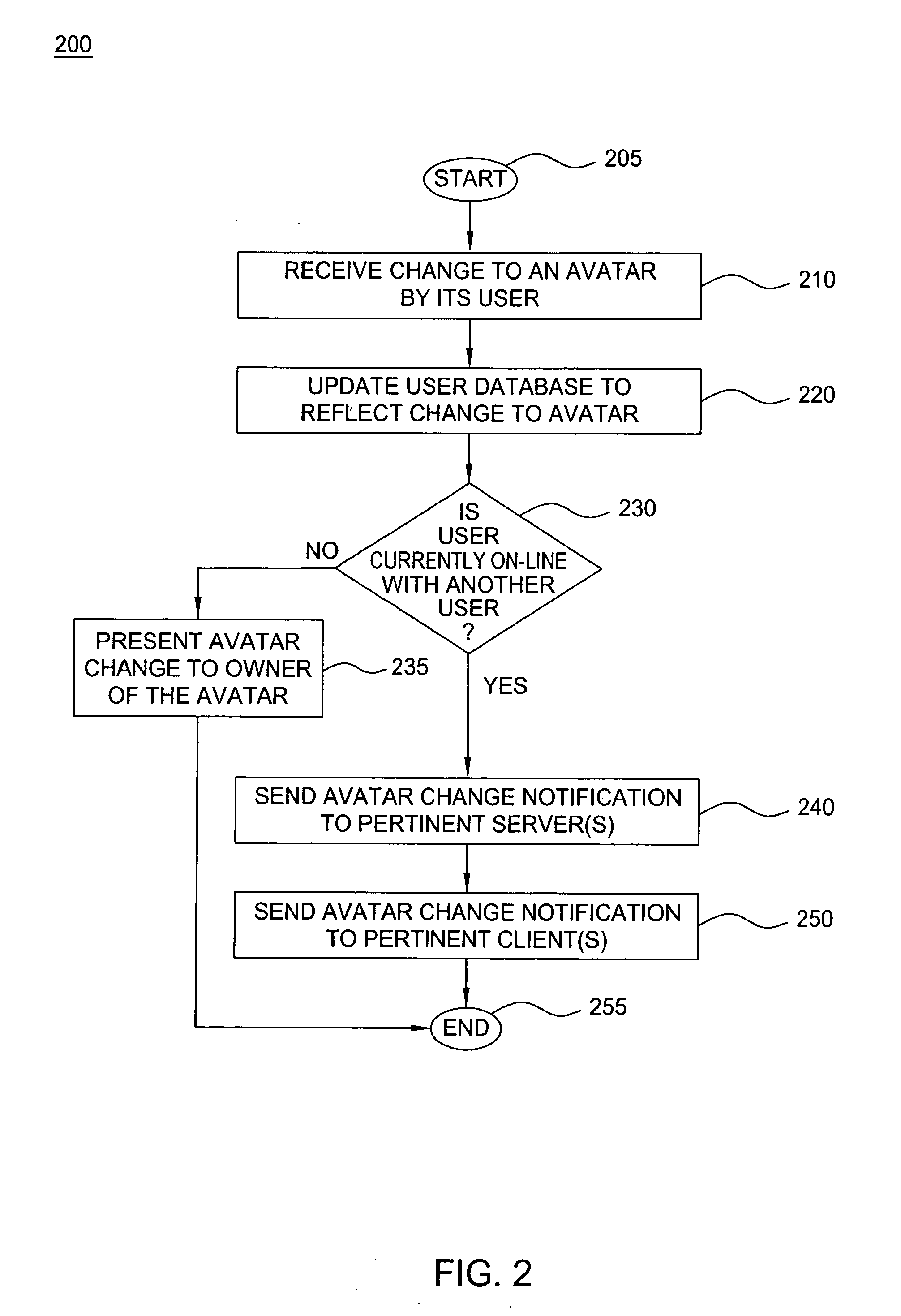
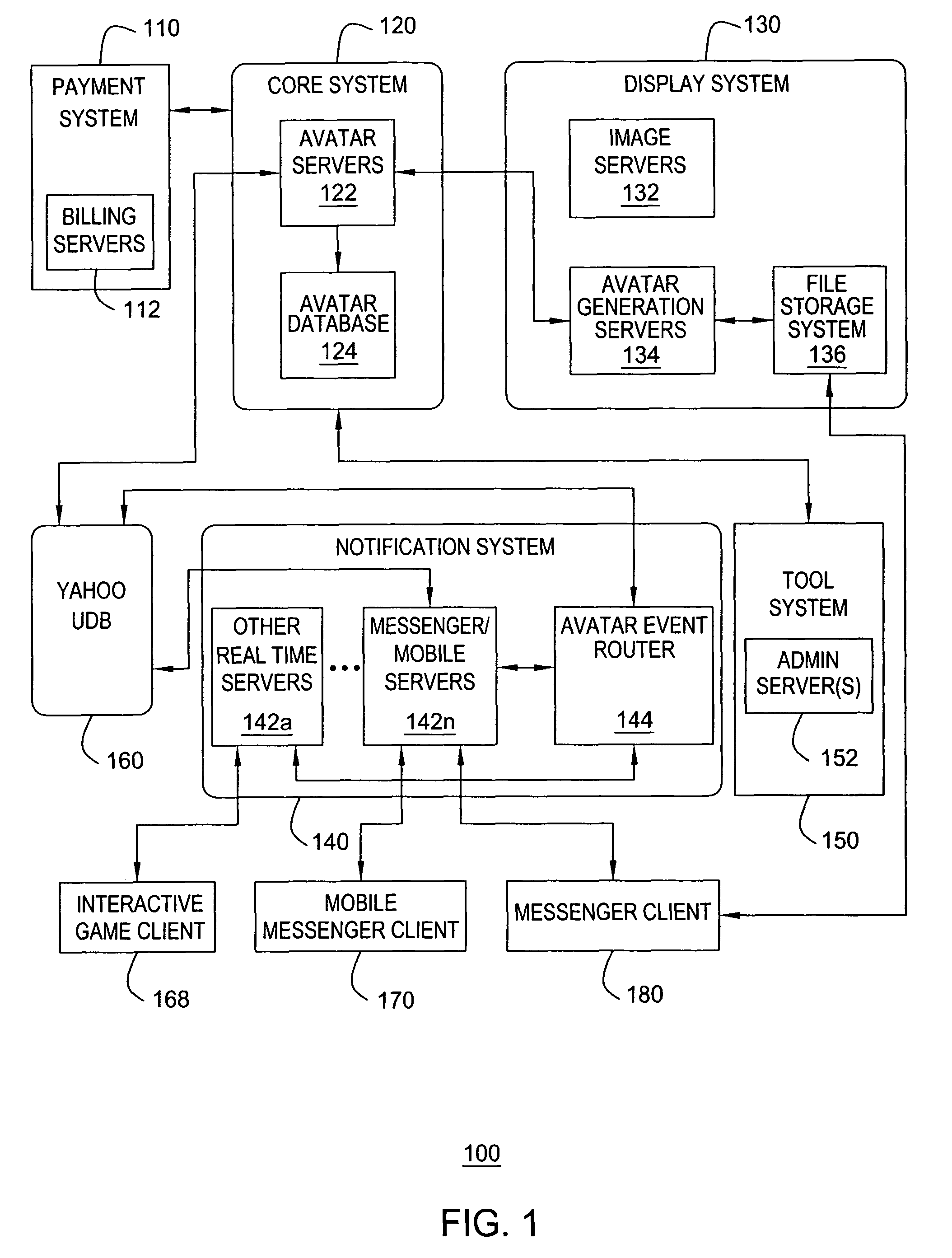
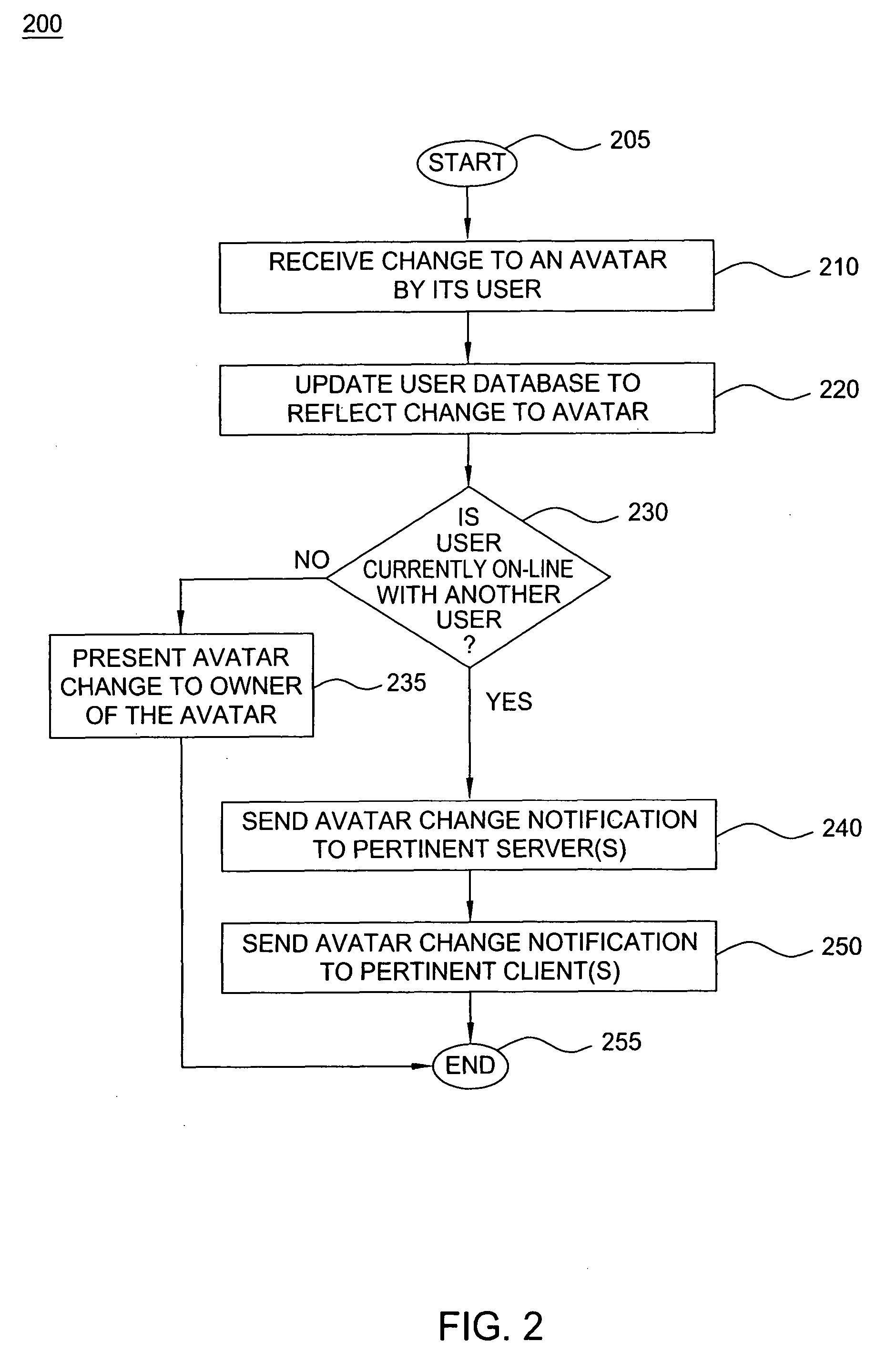
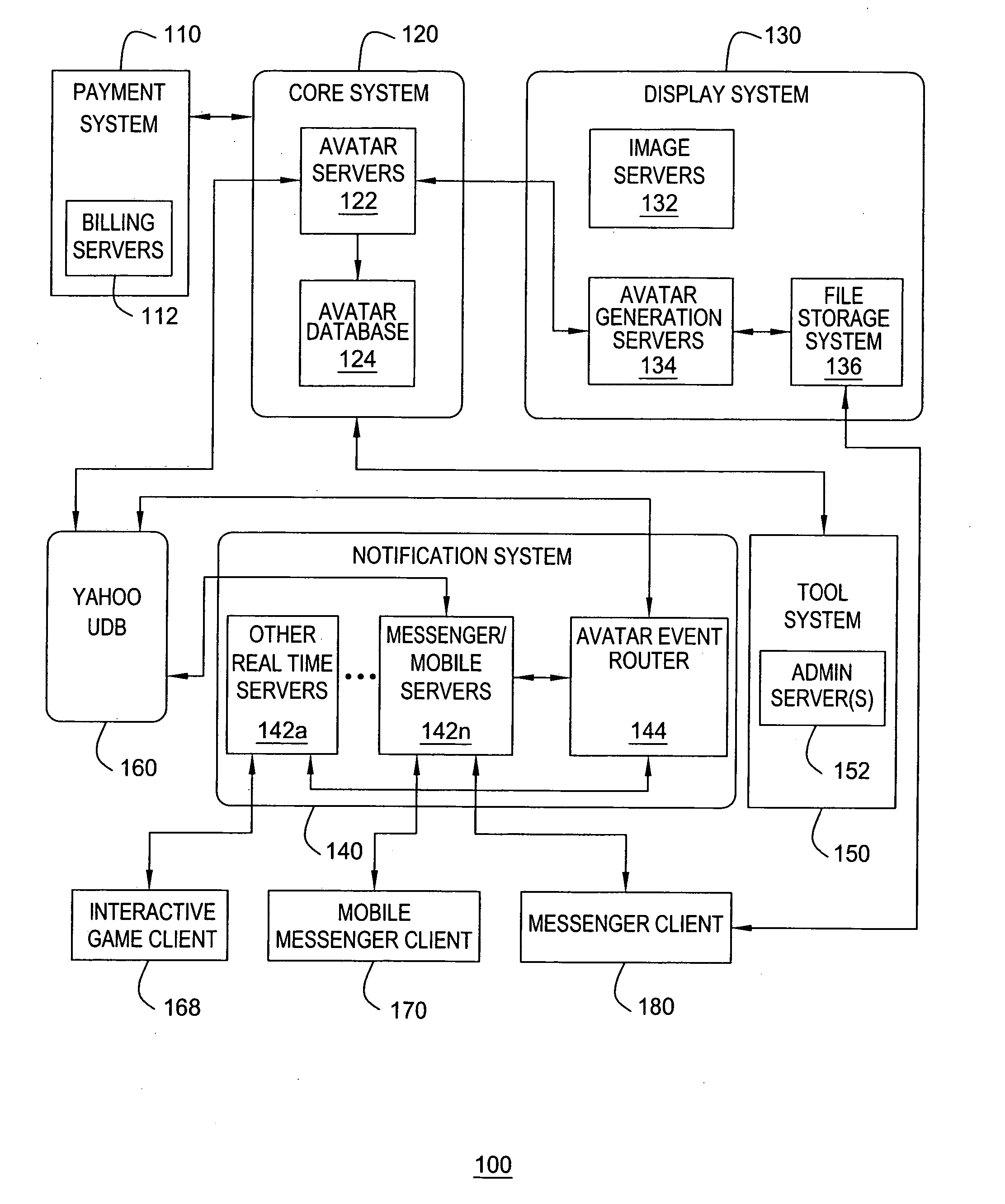
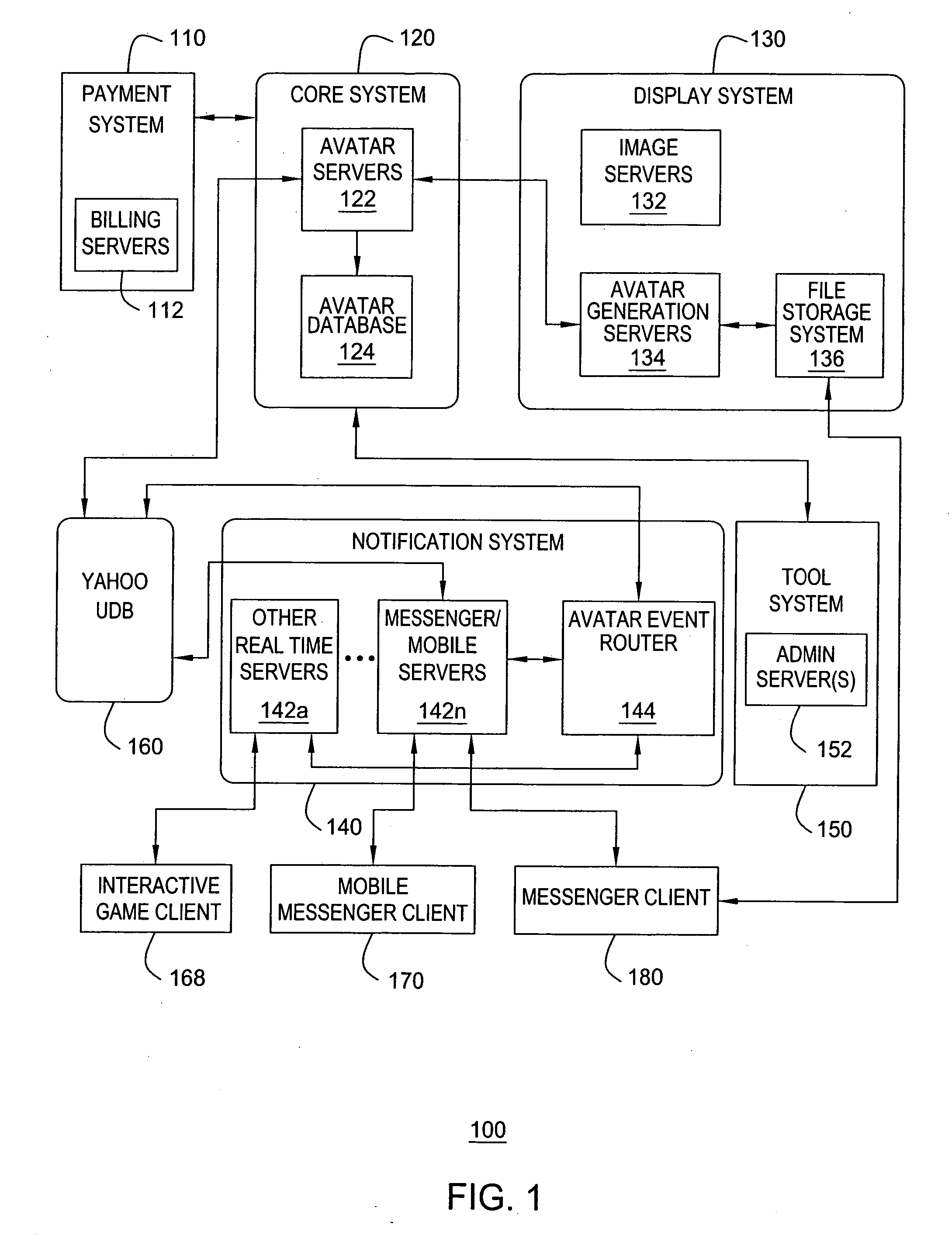
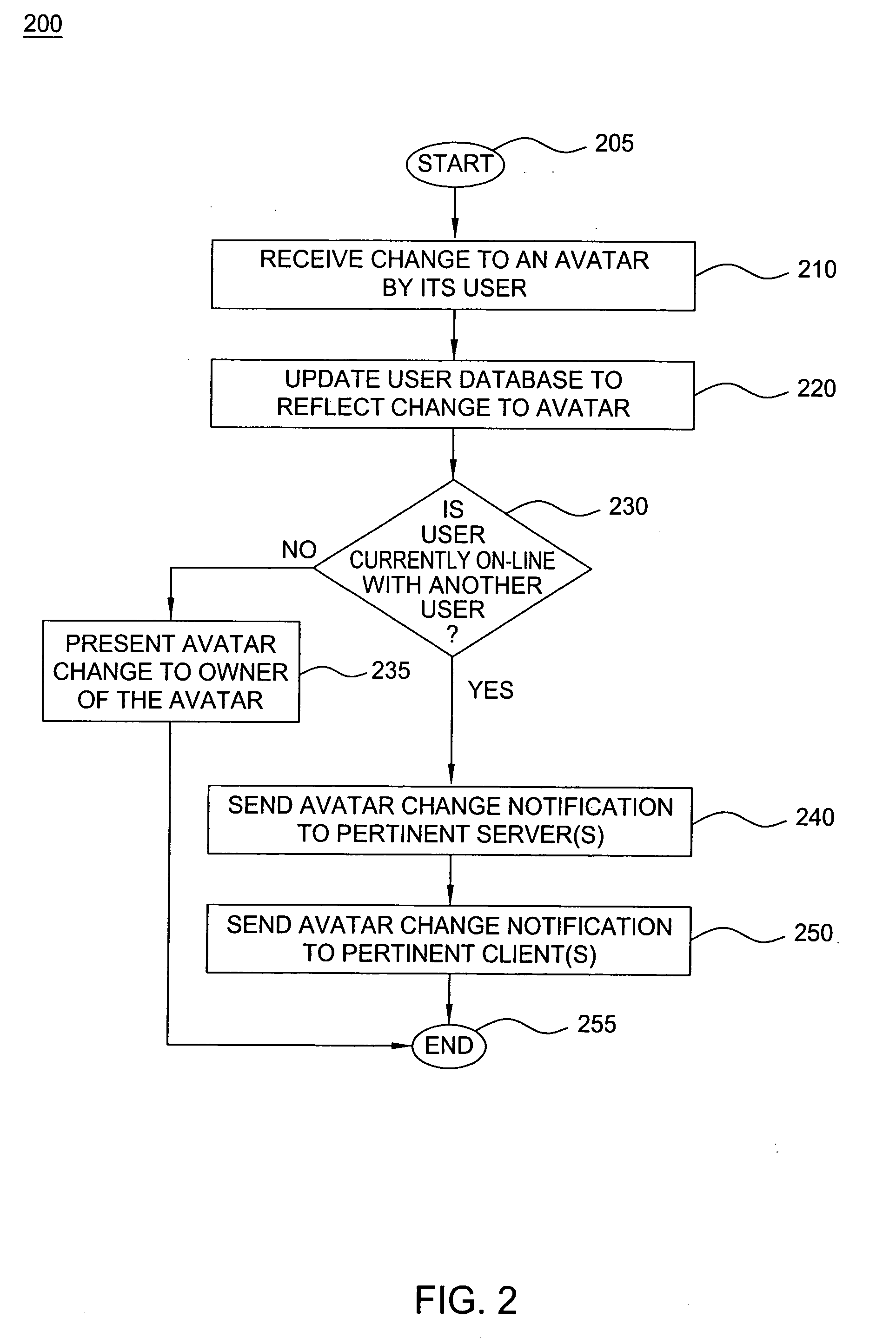
Method and apparatus for providing dynamic moods for updating online identities are disclosed. For example, when a user updates the moods and / or gestures of his or her avatar(s), the mood and / or gesture changes are stored in a user database. The changes are also detected by an event router that sends a mood change notification in real time to all pertinent servers that are currently supporting on-line applications for the user. The servers will send the mood change notification in real time to pertinent clients, e.g., an instant messenger client, a mobile instant messenger client, an interactive game client and the like. As a result, dynamic mood changes to a user's avatar can be shown in real time to other users interacting with the user.
Owner:OATH INC
Online identity tracking
InactiveUS20060230039A1Ease of evaluationFacilitate of entityTransmissionSpecial data processing applicationsDomain nameOnline identity
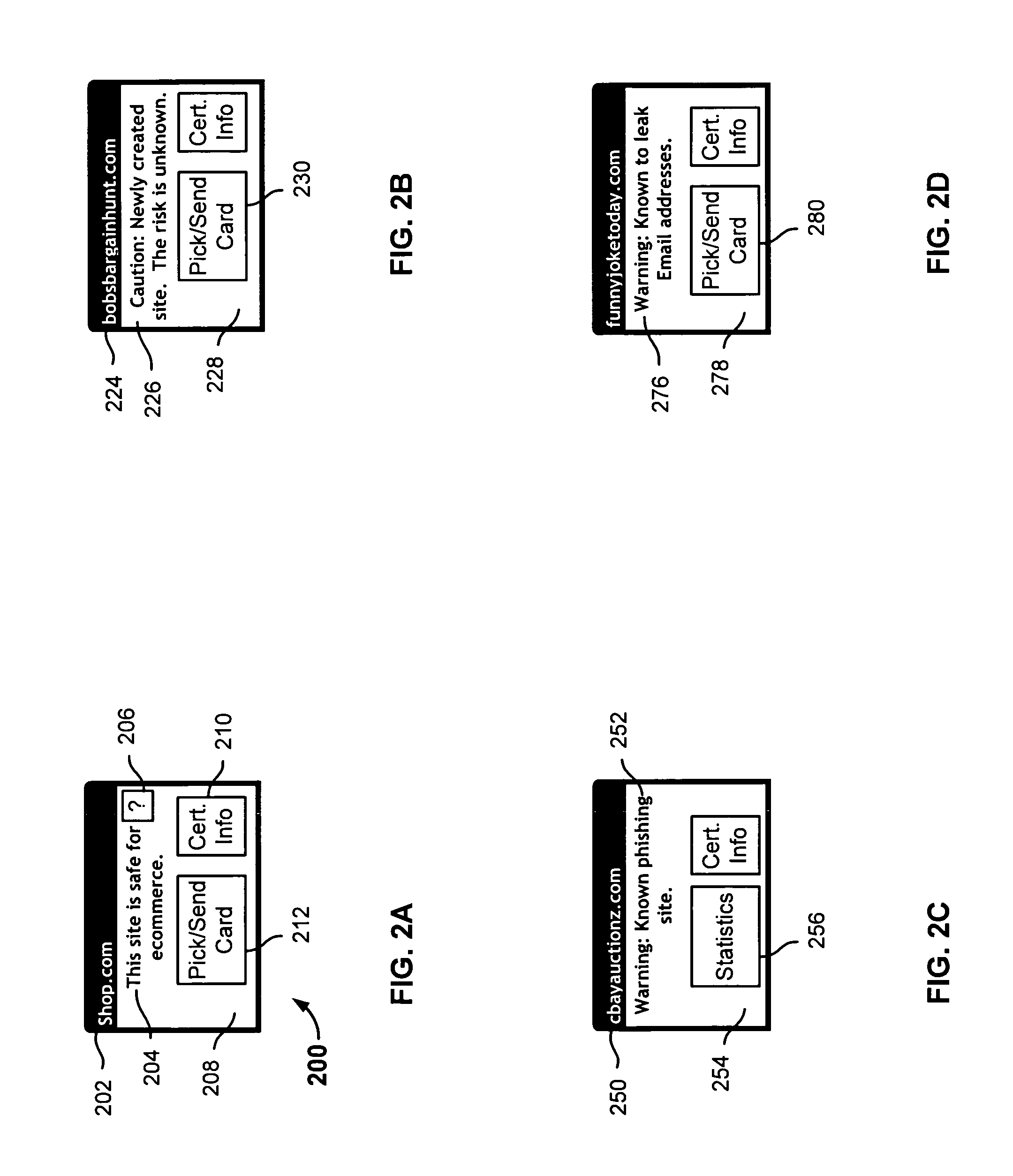
Embodiments of the invention provide novel systems, software and methods for gathering information about online entities and for identifying, evaluating and scoring such entities. Merely by way of example, the trustworthiness of an online entity, such as a domain, can be evaluated based information known about other online entities (e.g., the owner of the domain, other domains) associated with that domain. In an aspect of the invention, for example, publicly-available data (and, in some cases, other data) can be obtained and correlated to reveal previously-unknown associations between various online entities, despite, in some cases, the attempts of those entities to obscure such associations. This can facilitate the evaluation of such entities. For instance, if a new domain is registered, there generally is little basis on which to evaluate the trustworthiness of that domain (other than facially-apparent characteristics, such as the domain name itself), since it has not yet begun operating. By ascertaining the domain's association with other online entities, however, information known about the reputation and / or behavior of those entities can be used to inform an evaluation of the domain.
Owner:MARKMONITOR
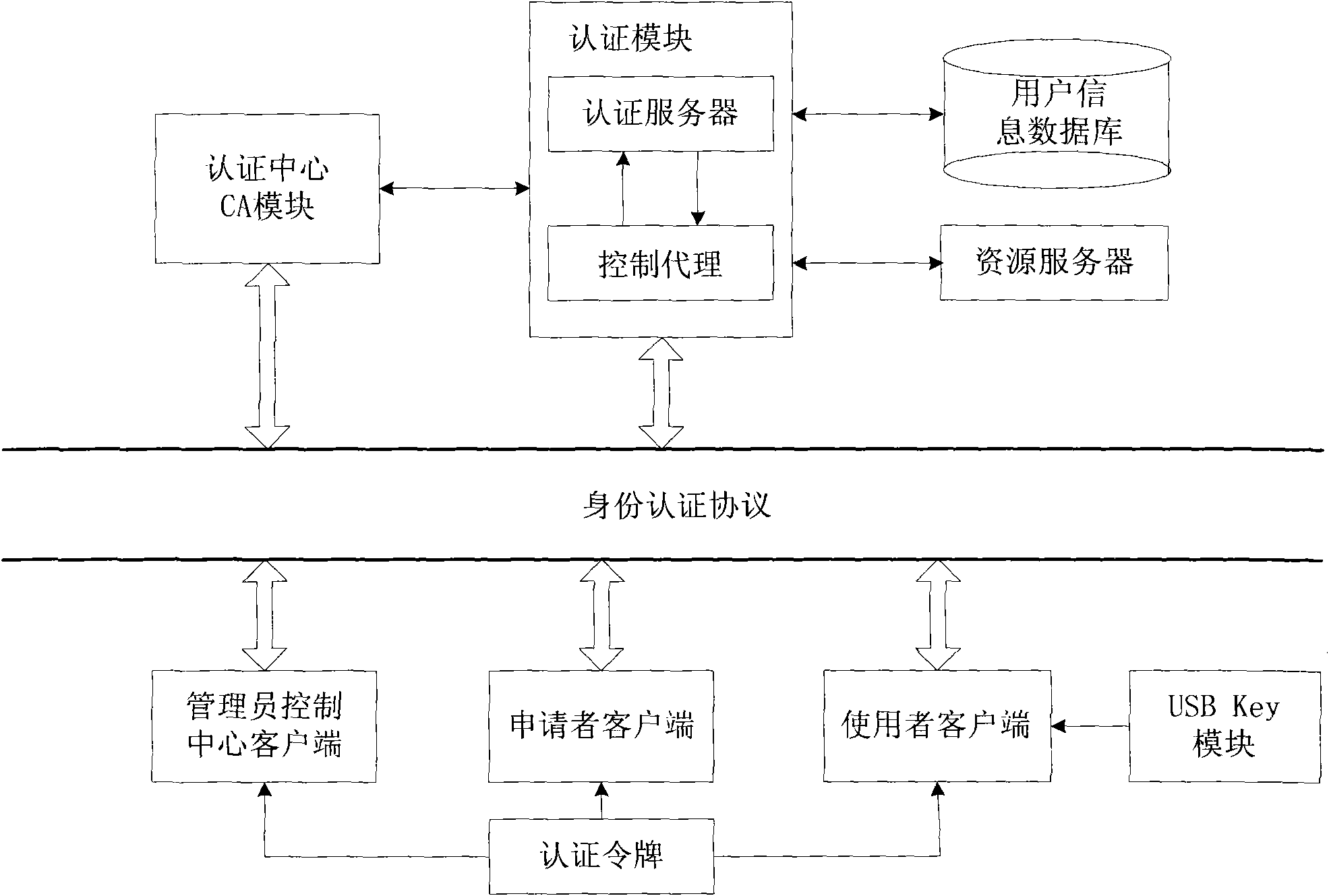
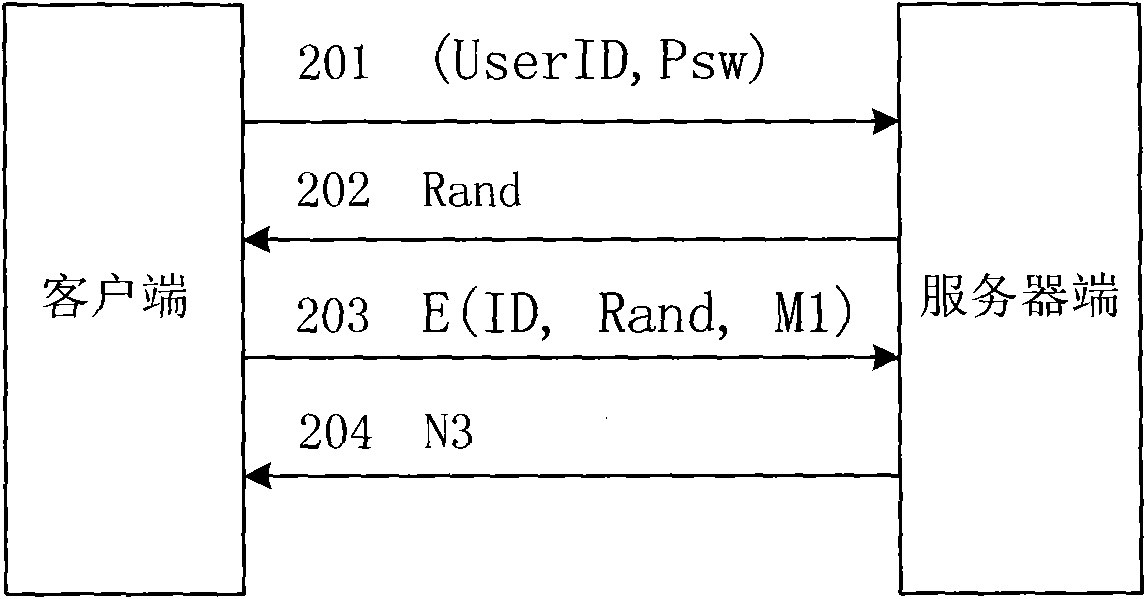
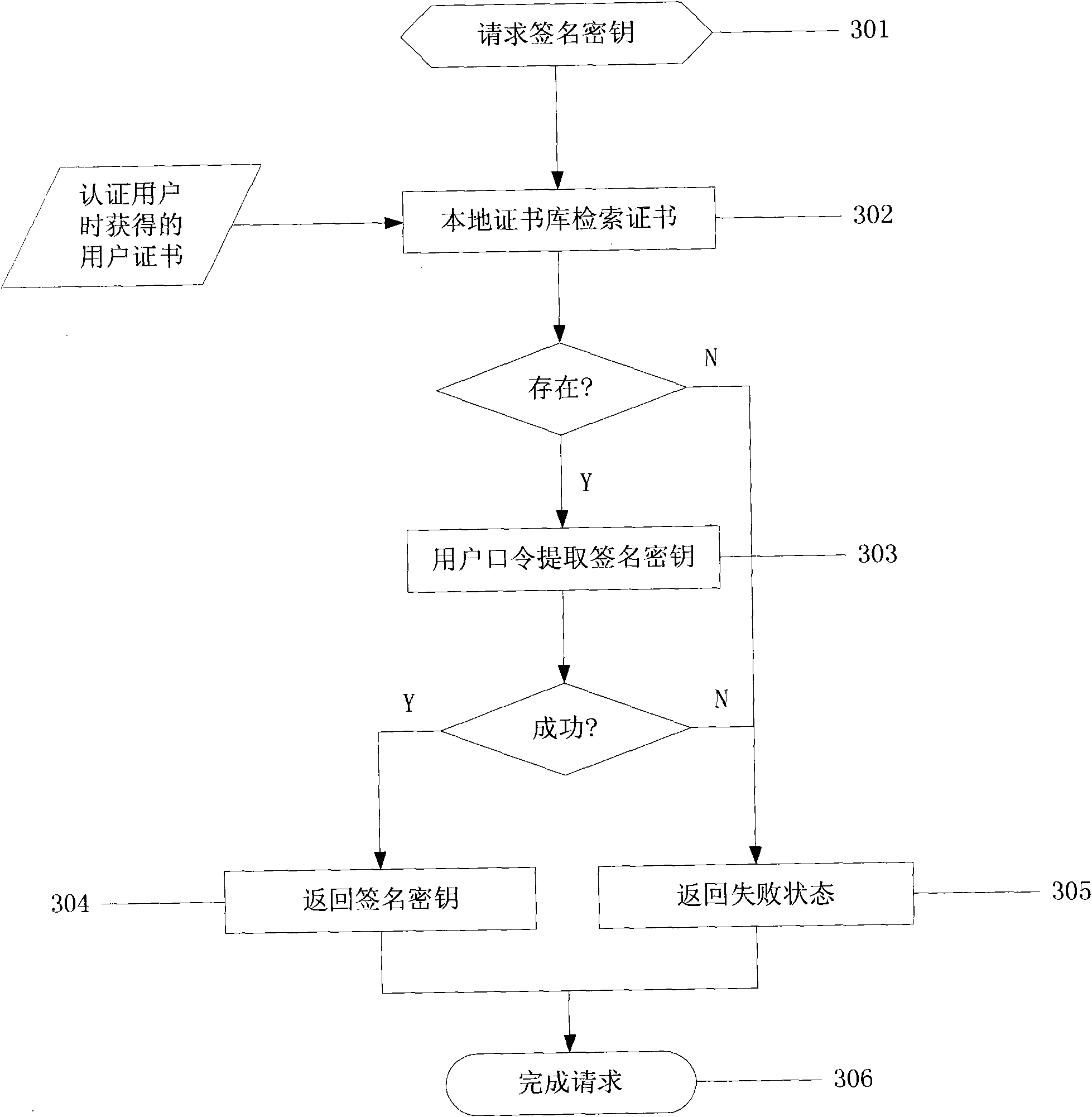
Network identity authentication system and method
InactiveCN101674304AEnsure safetyAchieve separationUser identity/authority verificationConfidentialityAuthentication server
The invention relates to an identity authentication system and an authentication method. The identity authentication system comprises an authentication center CA module, an authentication module, a client side and a USB Key module, wherein the authentication center CA module is responsible for the functions of application, examination and approval, issuing, updating and revocation of a certificate; the authentication module respectively carries out the generation of a digital envelope and the authentication of a digital certificate to the client side and a server side; the client side mainly realizes the management of the system and the clients; and the USB Key module mainly provides a medium for storing the digital certificate and a user private key to the user. The invention adopts a digital envelope technology, and can meet the high-confidentiality requirement of data transmission; an authentication token is used for sending a request to the authentication server by the client sidefor authentication and realizing the security of the authentication process; and the client side and the authentication server respectively carry out the generation of the digital envelope and the digital certificate, thus being capable of realizing the mutual authentication between the client side and the authentication server.
Owner:ZHEJIANG NORMAL UNIVERSITY
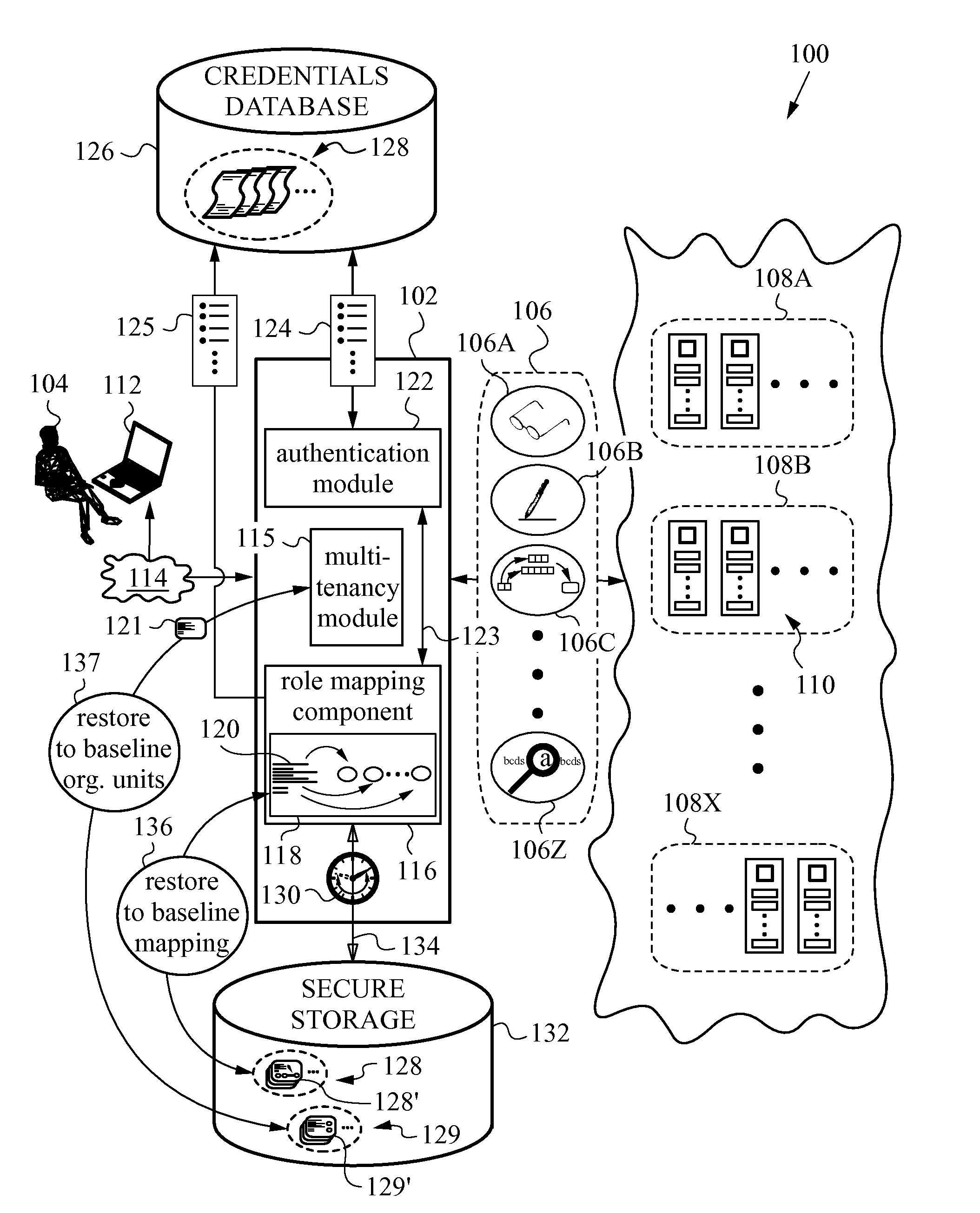
Monitoring of Authorization-Exceeding Activity in Distributed Networks
ActiveUS20140196115A1Minimal disruptionProvide supportDigital data processing detailsComputer security arrangementsUser authenticationOnline identity
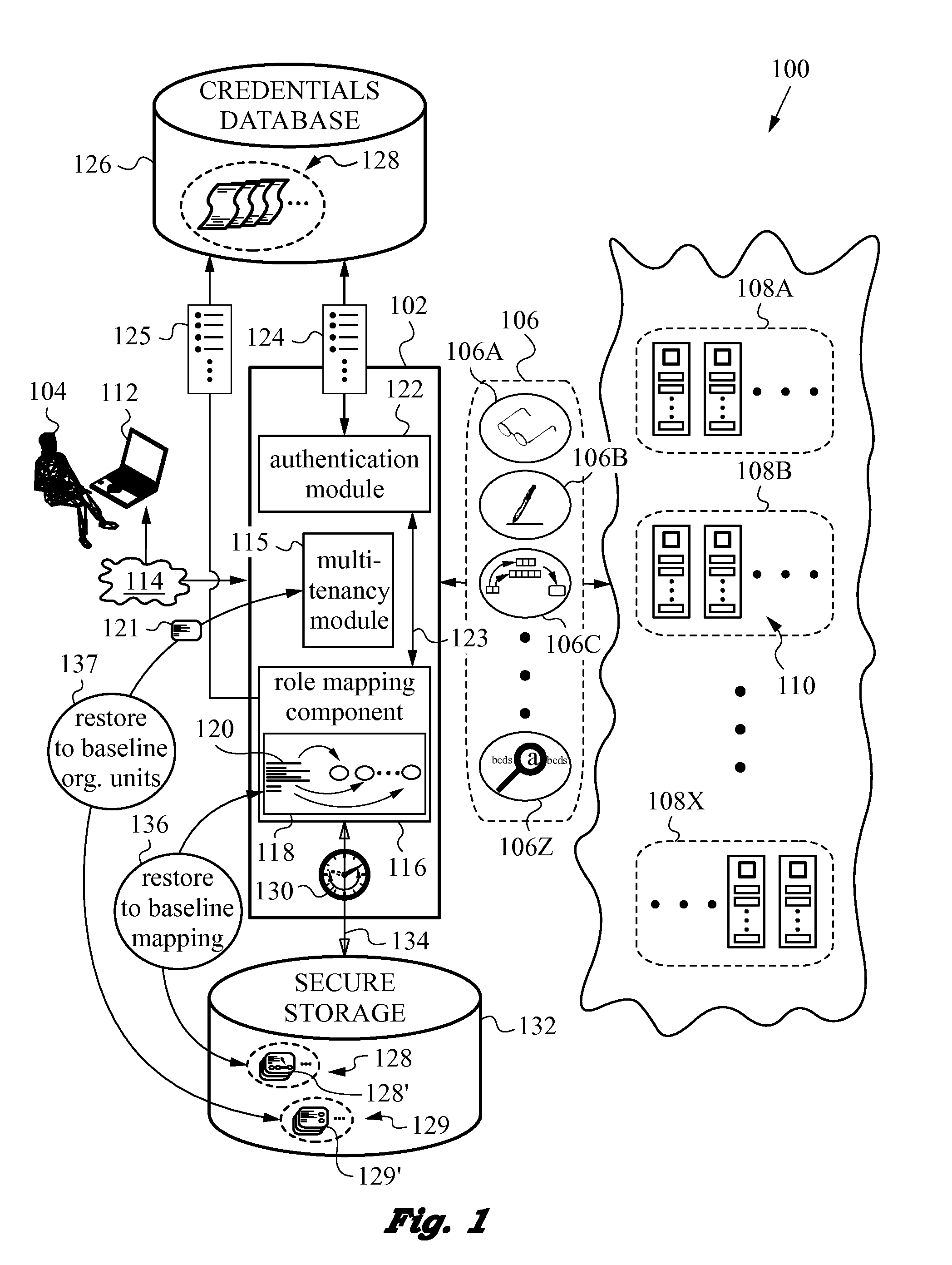
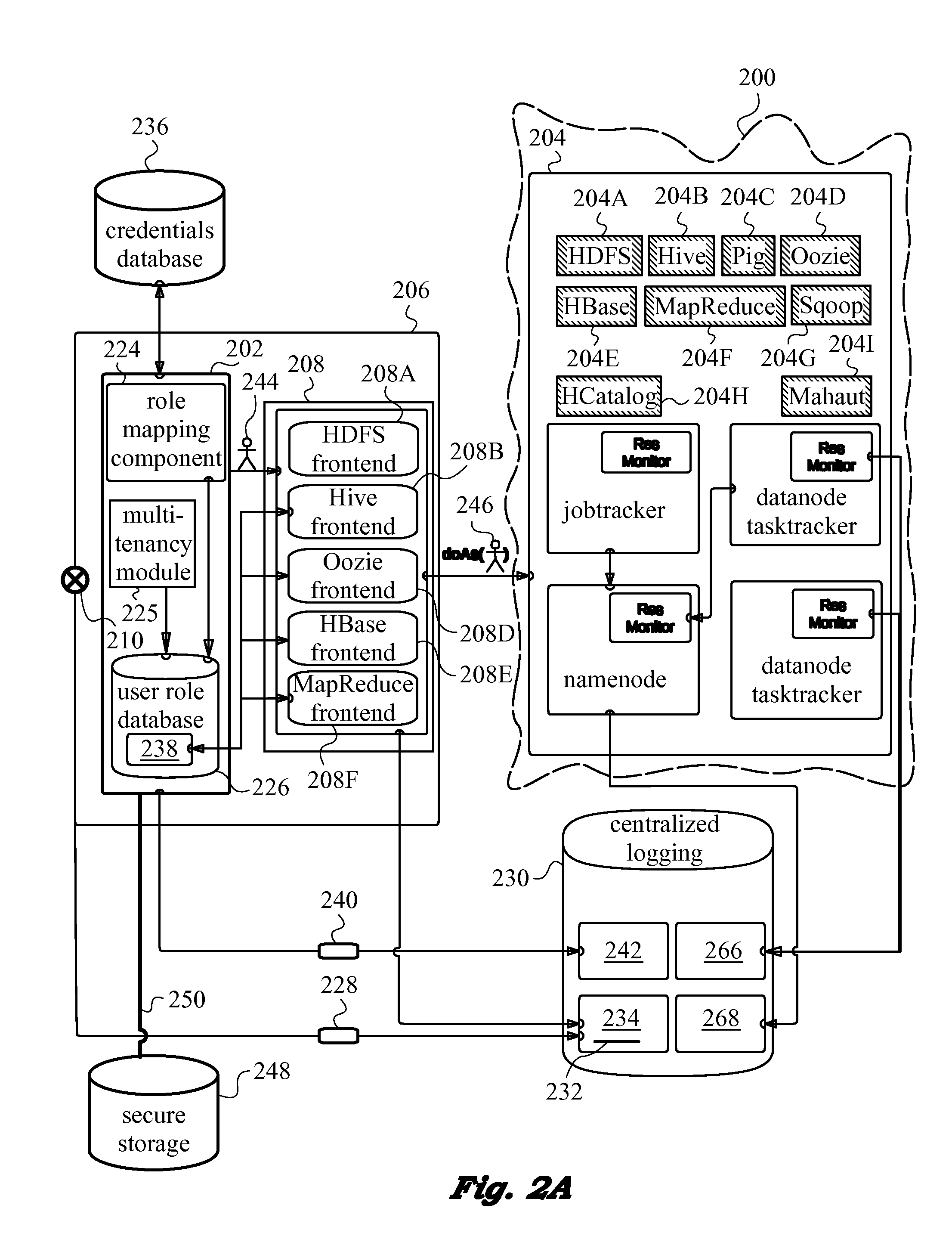
A network security layer with a role mapping component with a current role mapping between services and access permissions is provided between a user and the services. A multi-tenancy module with current membership mapping is also provided. The security layer has a network authentication protocol for user authentication at log-in. Snapshots of a baseline role mapping between services and permissions are taken at certain times. The role mapping component verifies snapshots at set intervals, and when the user performs certain actions, the current role mapping is compared with the baseline role mapping. Upon discrepancy, the role mapping component executes a set of rules, including forceful log-out to prevent system intrusion. Comparison of current membership mapping with a baseline membership mapping can also be applied. The security layer can thus monitor authorization-exceeding modifications to baseline policies attempted by logged-in and initially authorized users.
Owner:ZETTASET
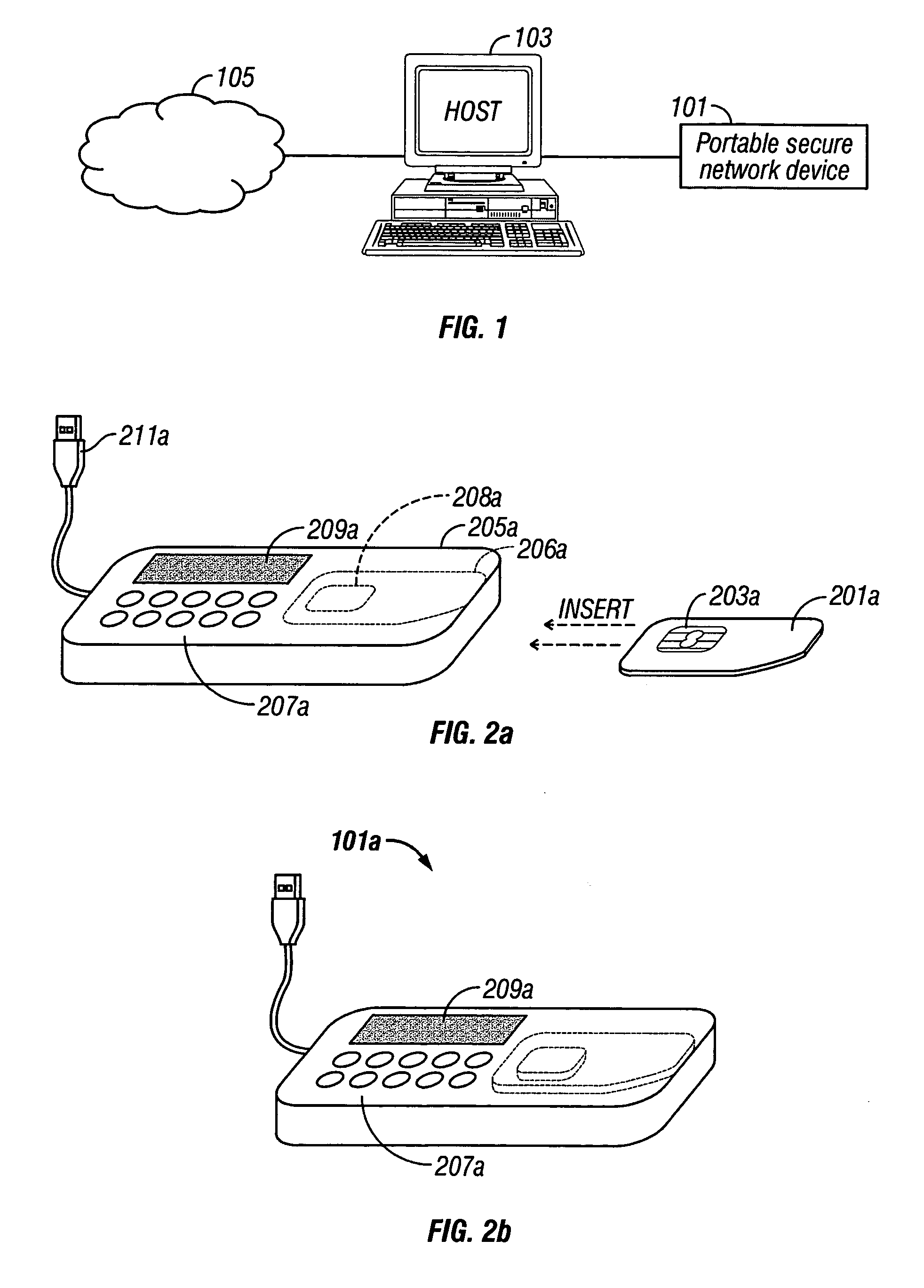
System and method for secure online transactions using portable secure network devices
InactiveUS20060294023A1Prevent online identity theftPrevent theftPayment architectureDigital data authenticationIdentity theftSmart card
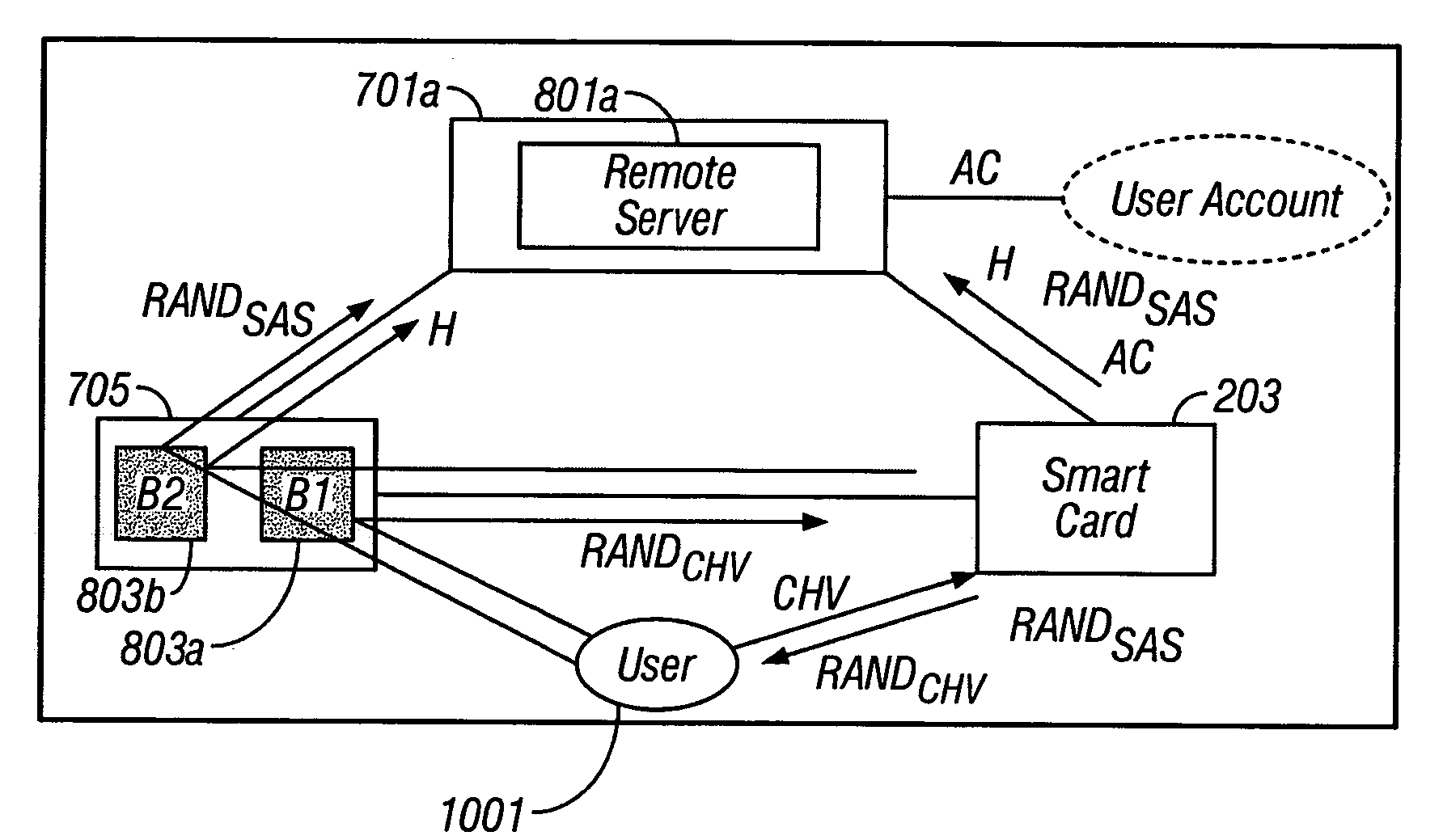
A portable secure network device and method to operate such a device to provide secure login, secure online transactions, and to prevent online identity theft. An embodiment of the invention may be constructed by inserting a network smart card into a card reader, wherein either the card reader or the card itself has an output device and input device wherein the processor is programmed to execute according to instructions to cause the microprocessor: to produce a shared association secret; to display the shared association secret on the output device; and to transmit the shared association secret to the remote server; thereby ensuring that a user observing the output device and the remote server computer both possess the shared association secret.
Owner:AXALTO INC
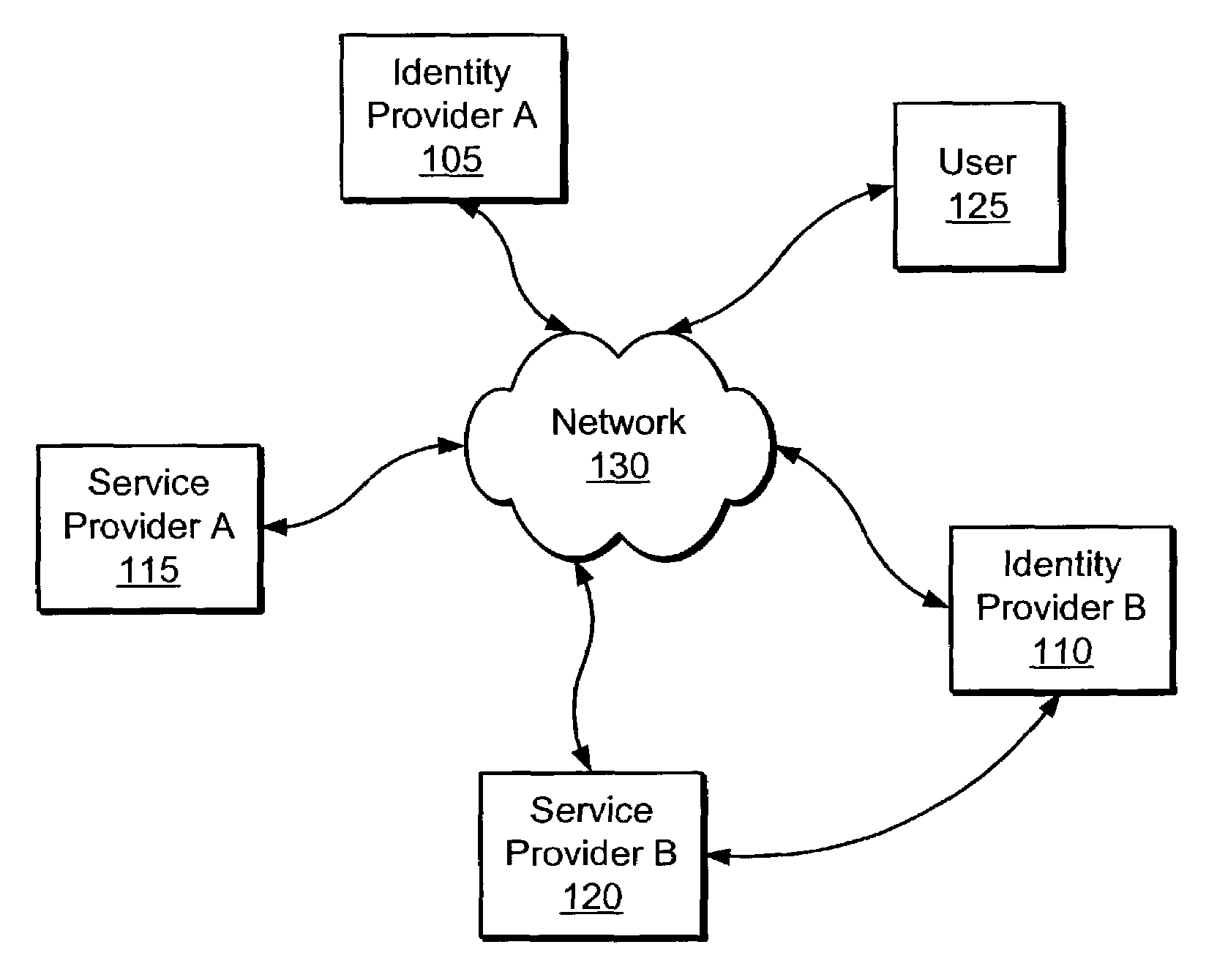
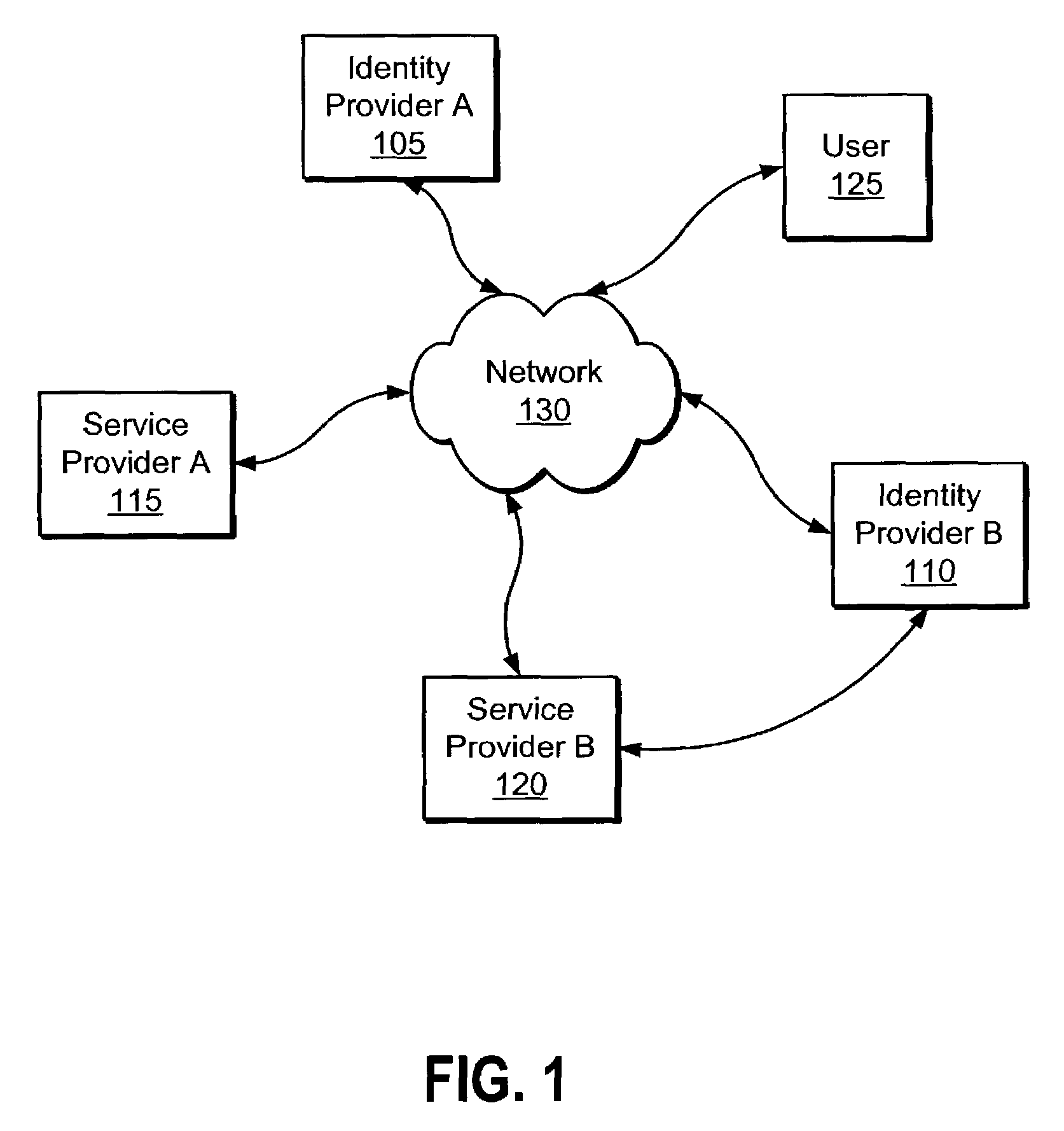
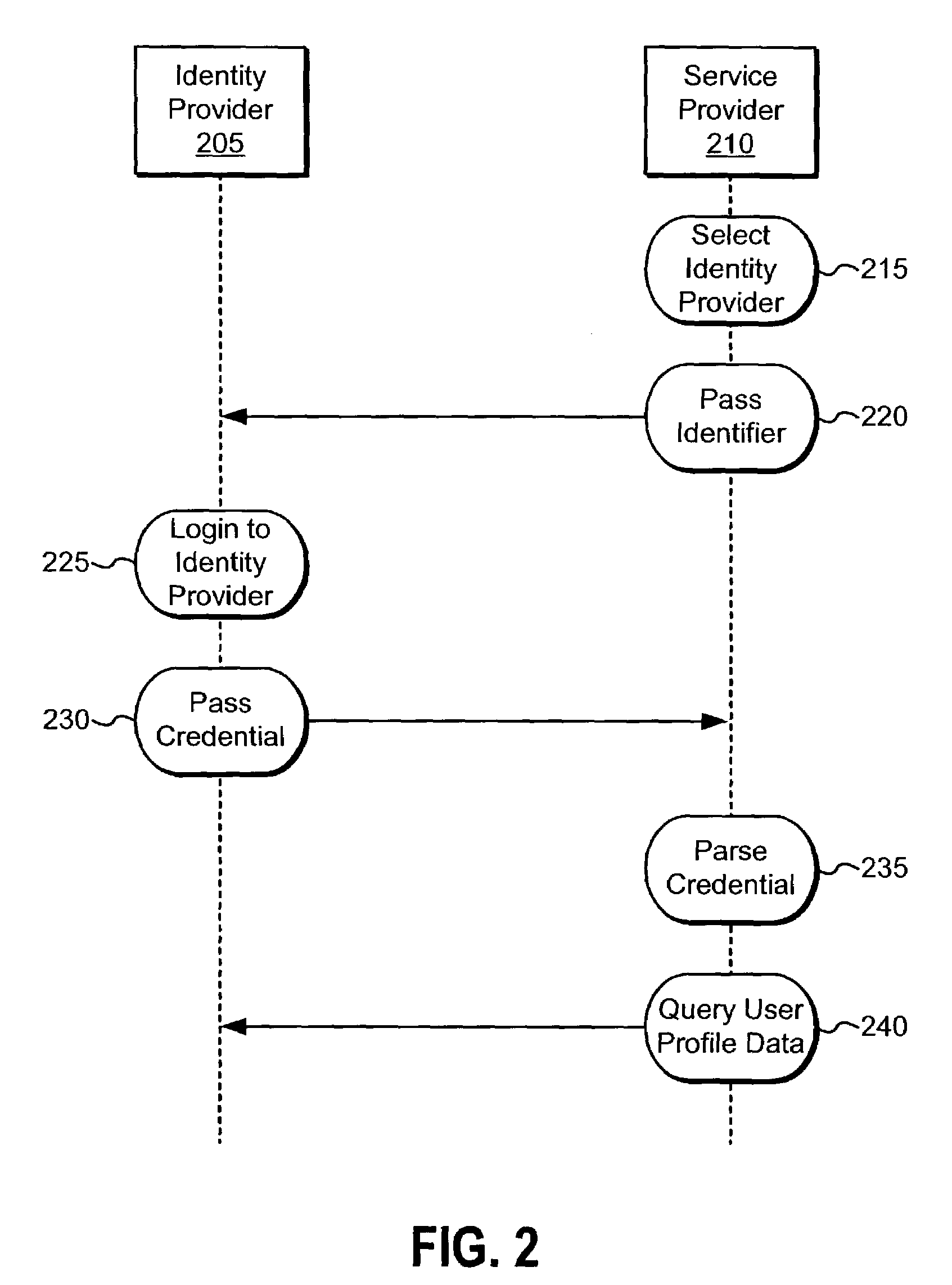
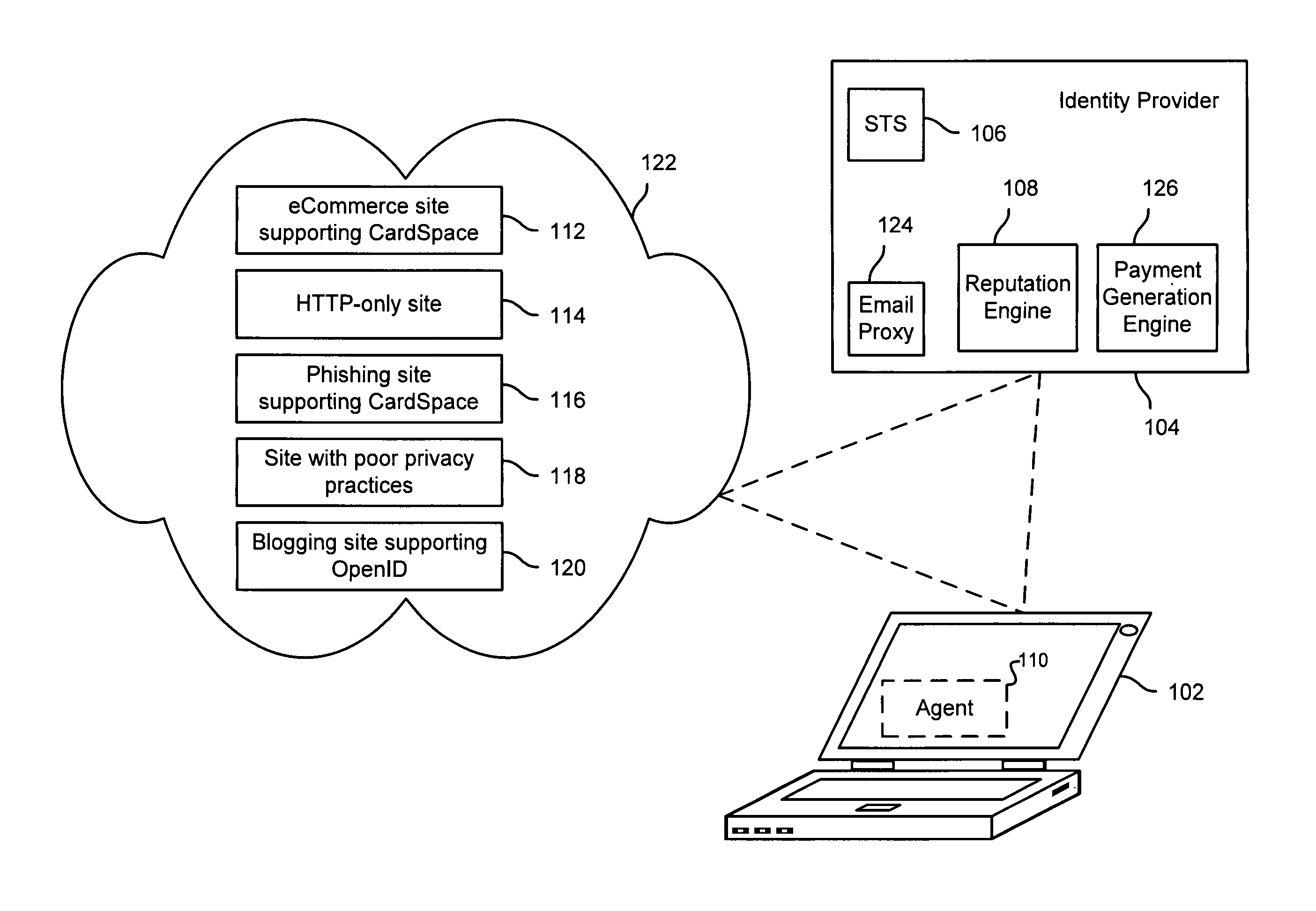
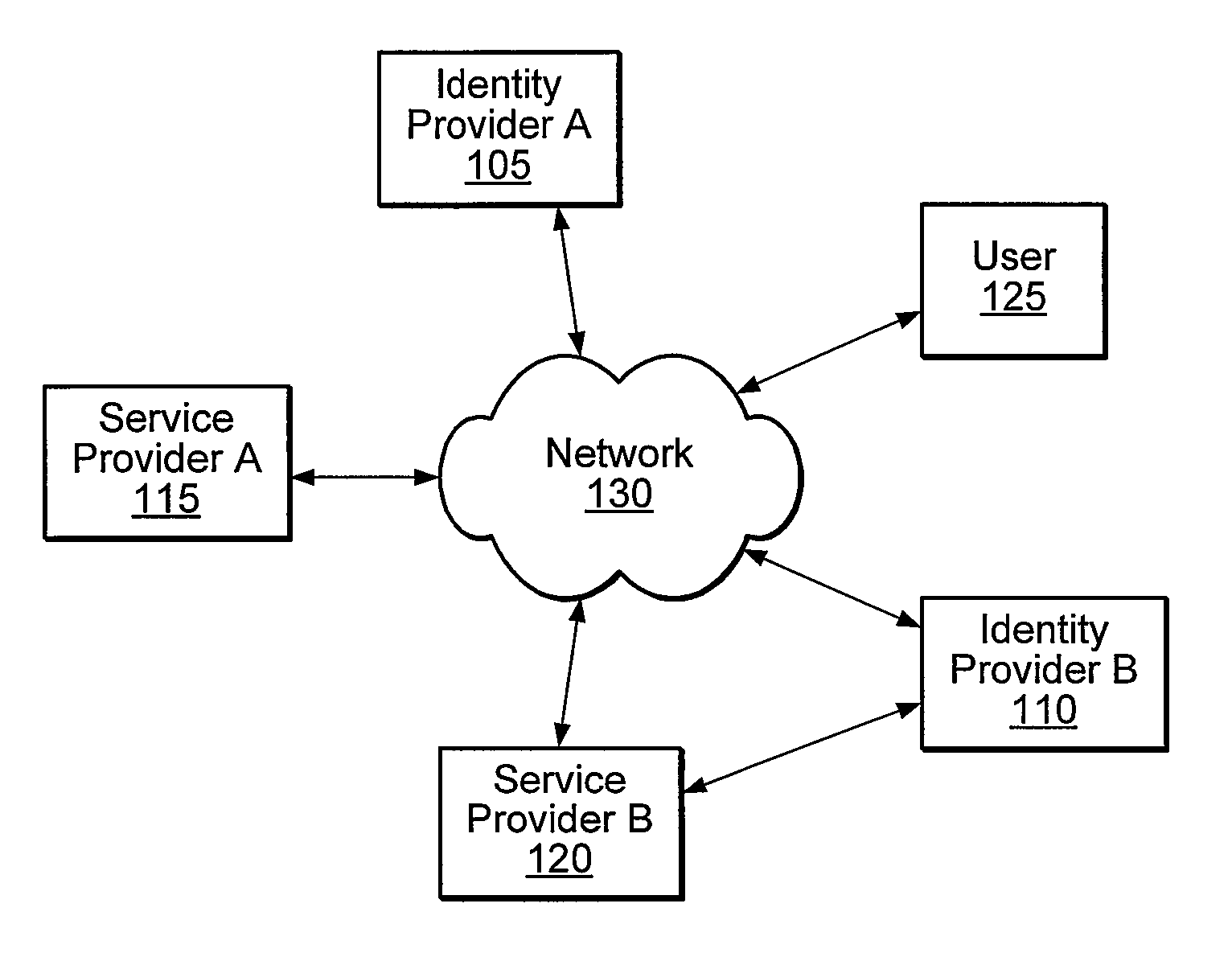
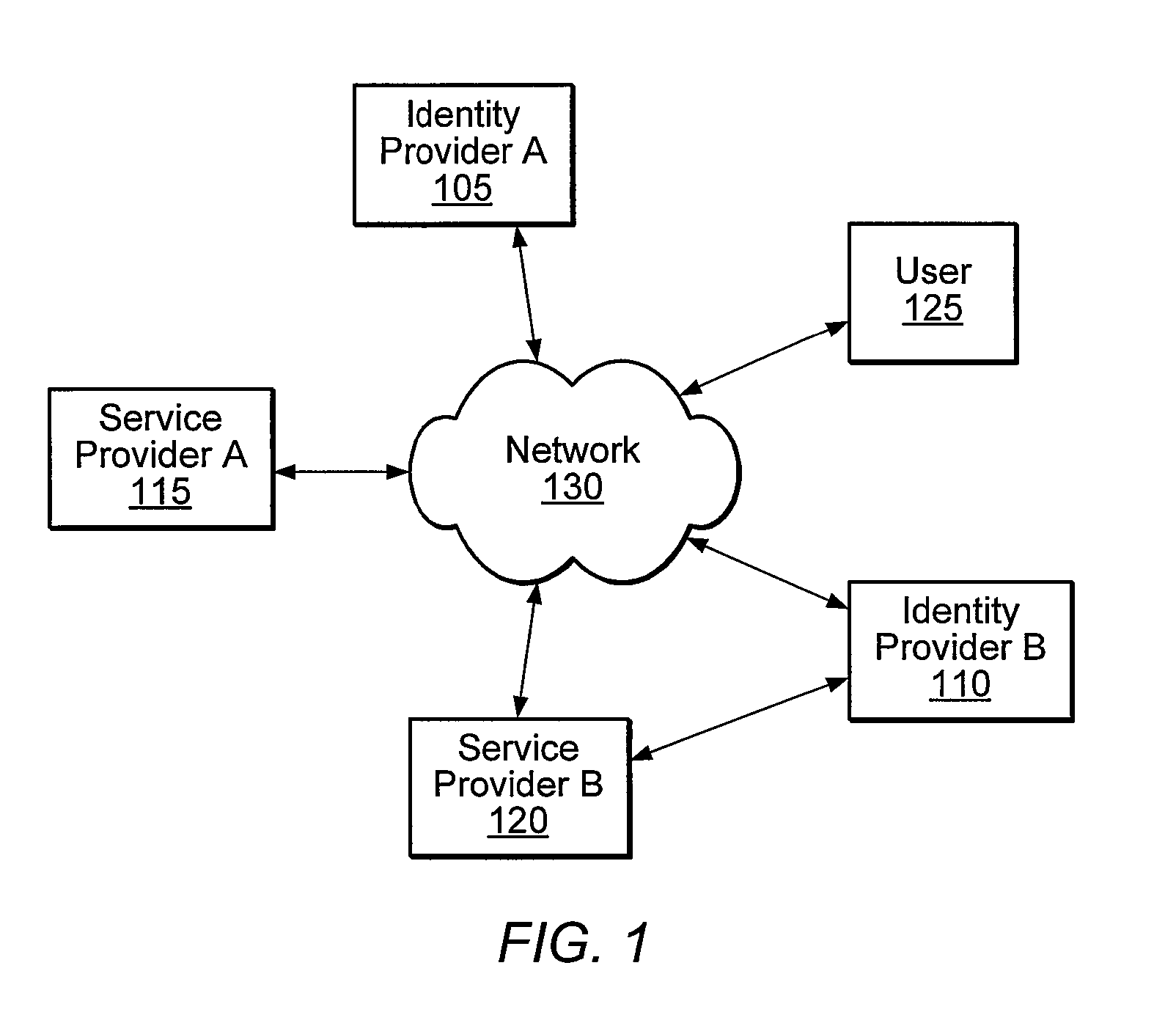
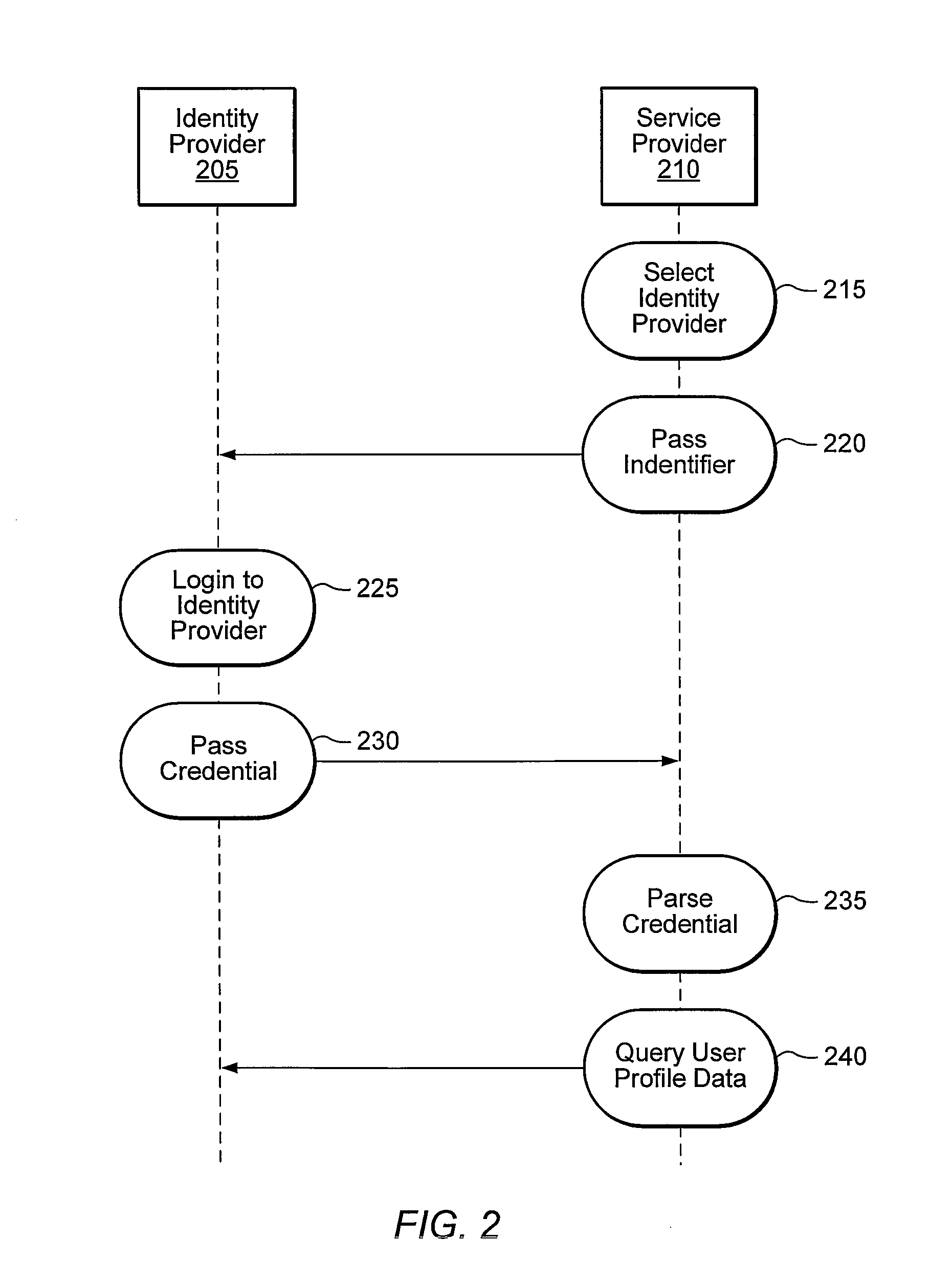
Distributed Network Identity
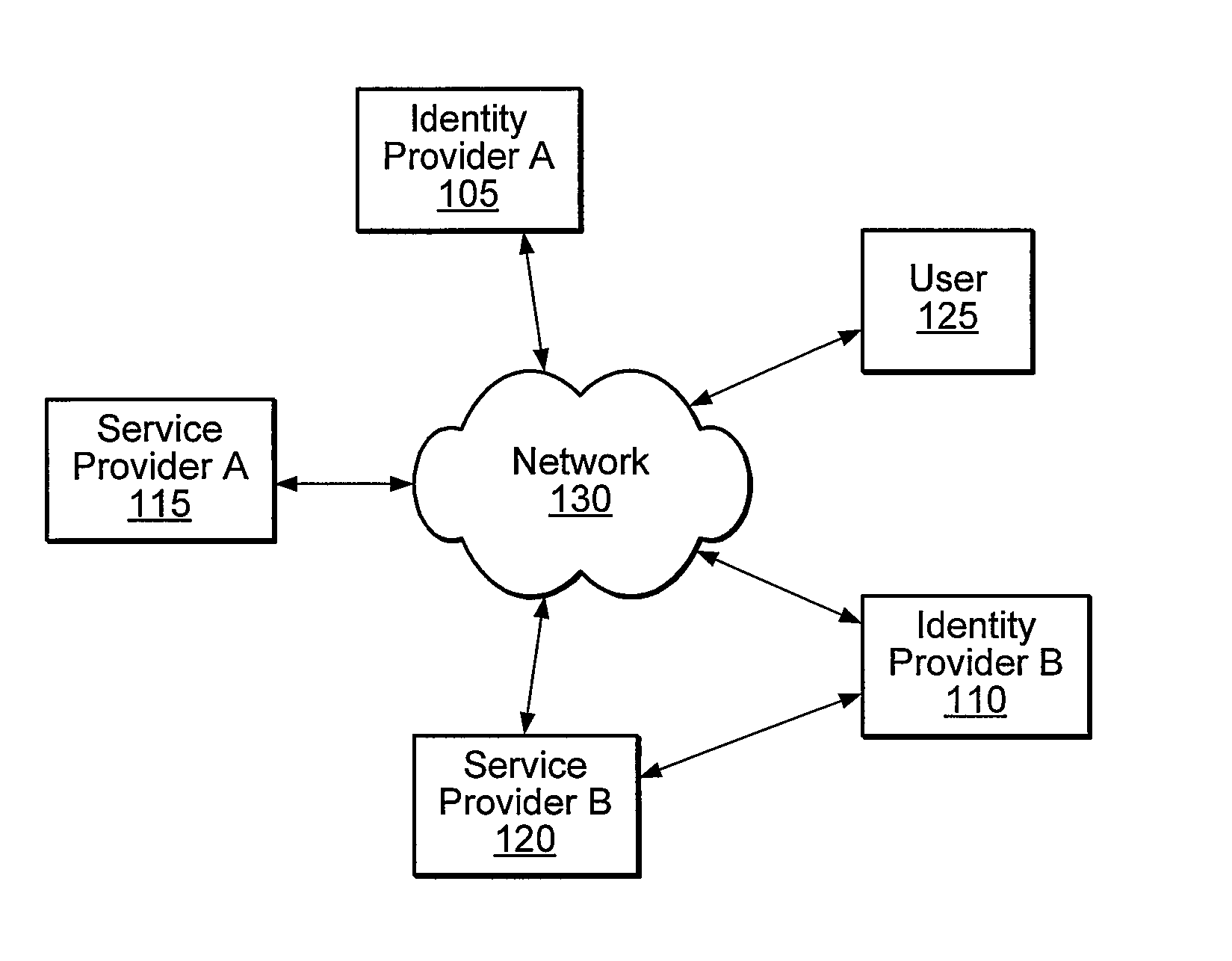
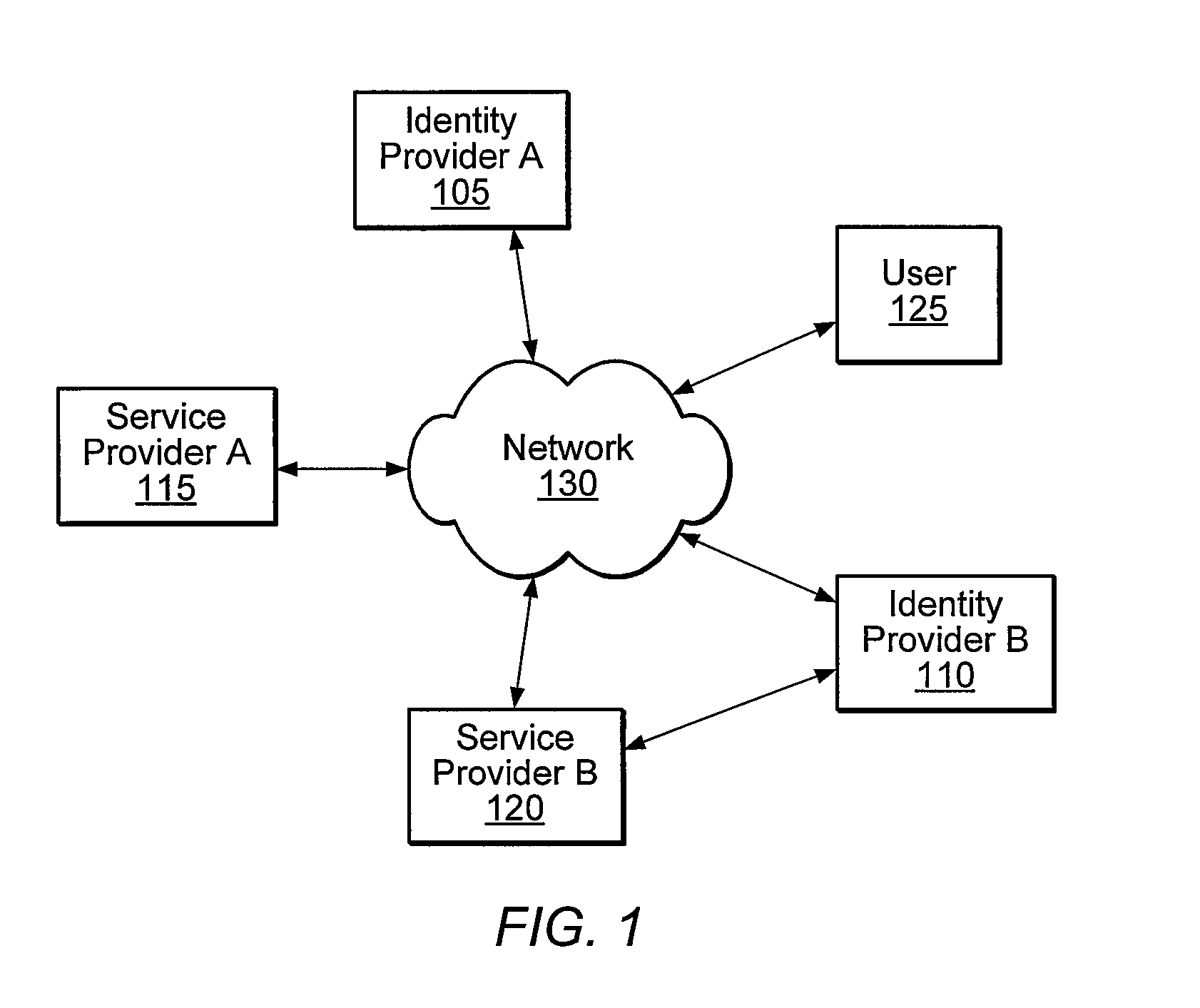
ActiveUS20080016232A1Improve user interactionAssure integrityMultiple digital computer combinationsDigital data authenticationInformation sharingInternet privacy
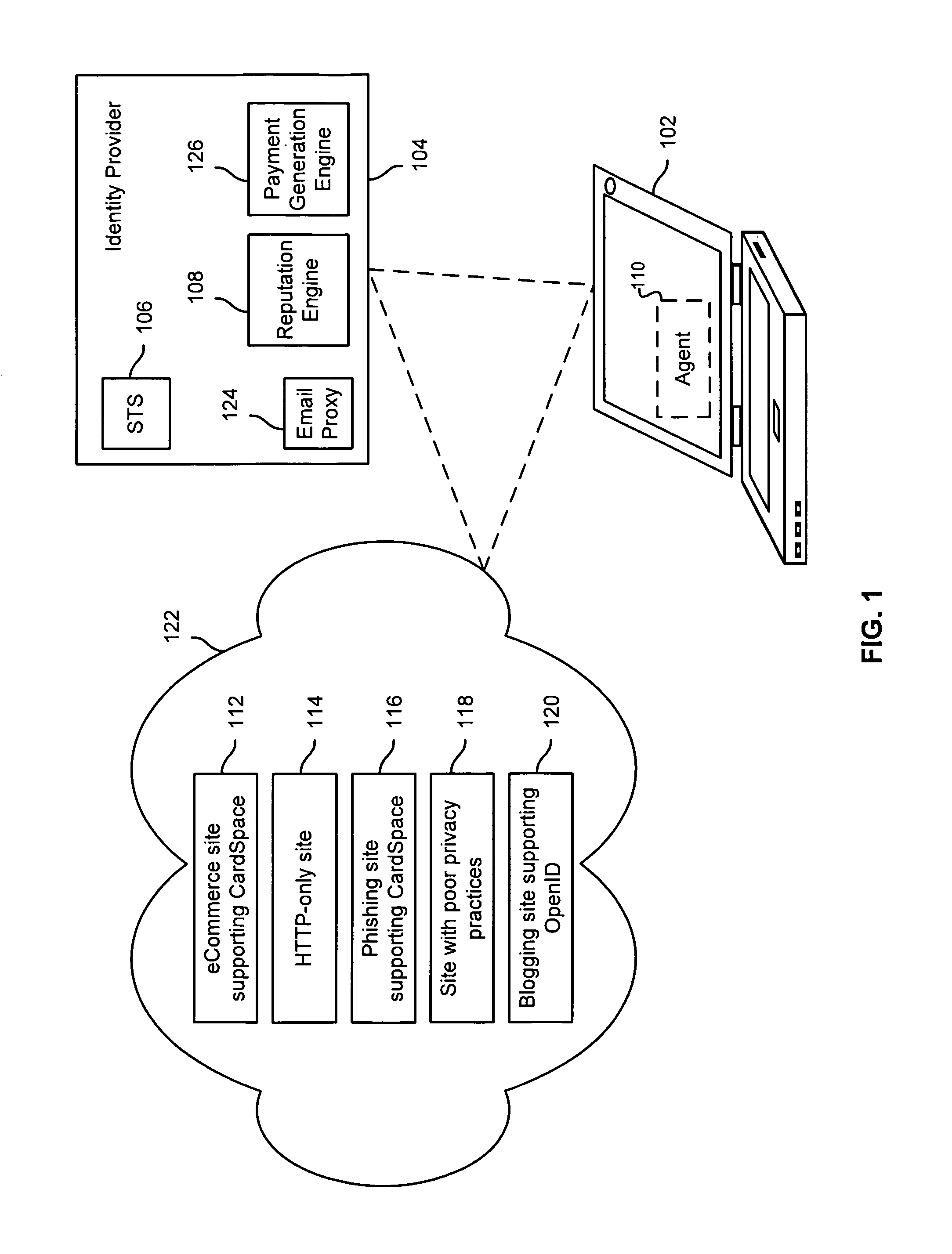
A distributed network identity is provided. An identity provider stores a portion of a user's personal information. A service provider accesses user information from one or more identity providers. System entities such as identity providers and service providers can be linked to enable information sharing and aggregation. User policies and privacy preferences are provided to control how information is shared. A single sign-on architecture is provided where an identity provider is used to facilitate cross-domain authentication and to enhance user convenience. Service delegation features are also provided.
Owner:ORACLE INT CORP
Networked identity framework
ActiveUS20070143860A1Digital data processing detailsUser identity/authority verificationData setInternet privacy
A system and method provide a framework for networked identity management in a user-centric model by providing the ability for a user to delegate permissions to release identity information, by enabling a mechanism for releasing one of a requested plurality of data sets and by providing facilities for the retrieval of identity information from an external server. Anonymization of identity data is enabled through the use of an anonymizer system that can optionally be integrated with an identity store such as a homesite.
Owner:CALLAHAN CELLULAR L L C +1
Distributed network identity
ActiveUS7610390B2Improve user interactionAssure integrityMultiple digital computer combinationsDigital data authenticationInformation sharingInternet privacy
A distributed network identity is provided. An identity provider stores a portion of a user's personal information. A service provider accesses user information from one or more identity providers. System entities such as identity providers and service providers can be linked to enable information sharing and aggregation. User policies and privacy preferences are provided to control how information is shared. A single sign-on architecture is provided where an identity provider is used to facilitate cross-domain authentication and to enhance user convenience. Service delegation features are also provided.
Owner:ORACLE INT CORP
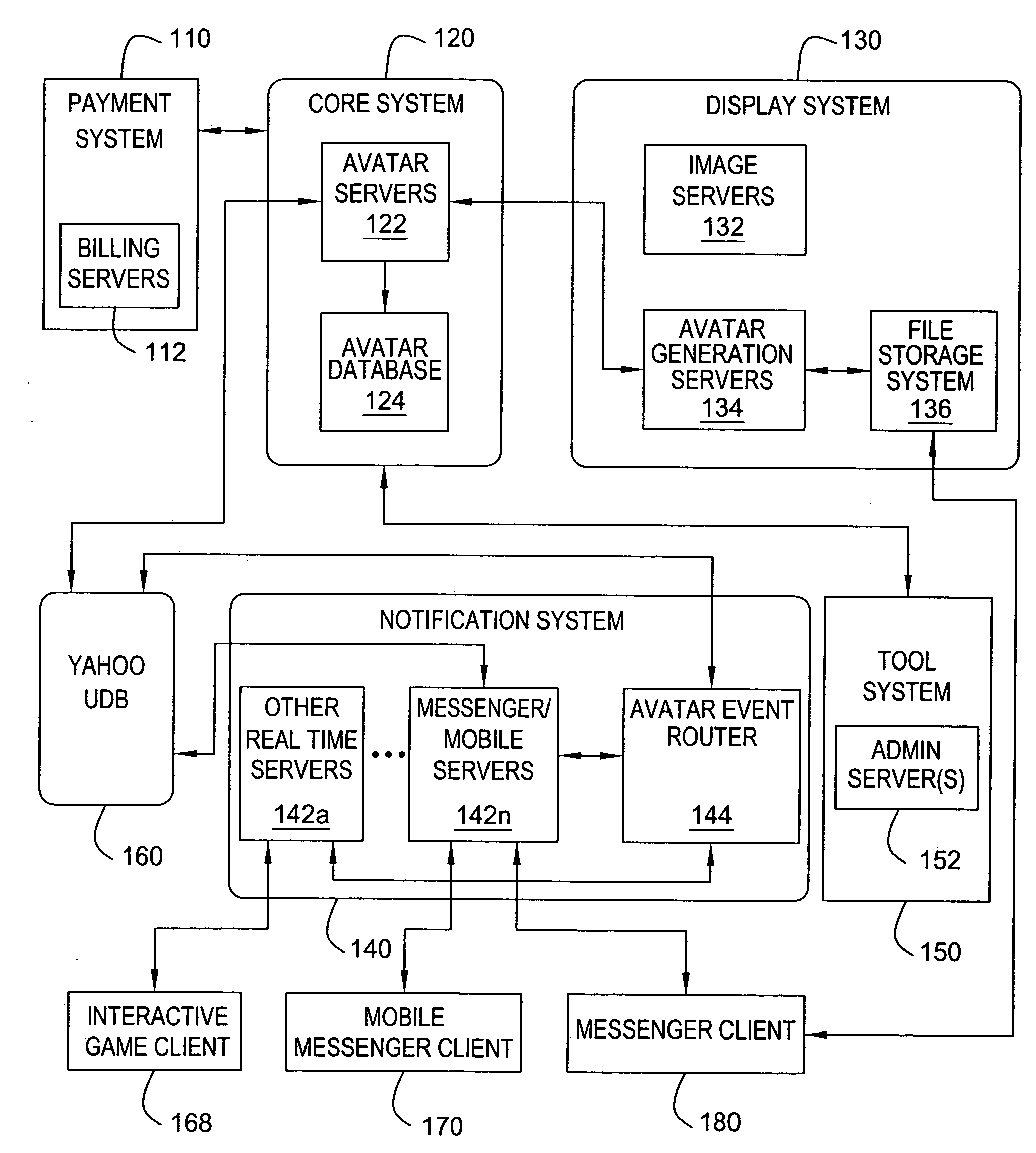
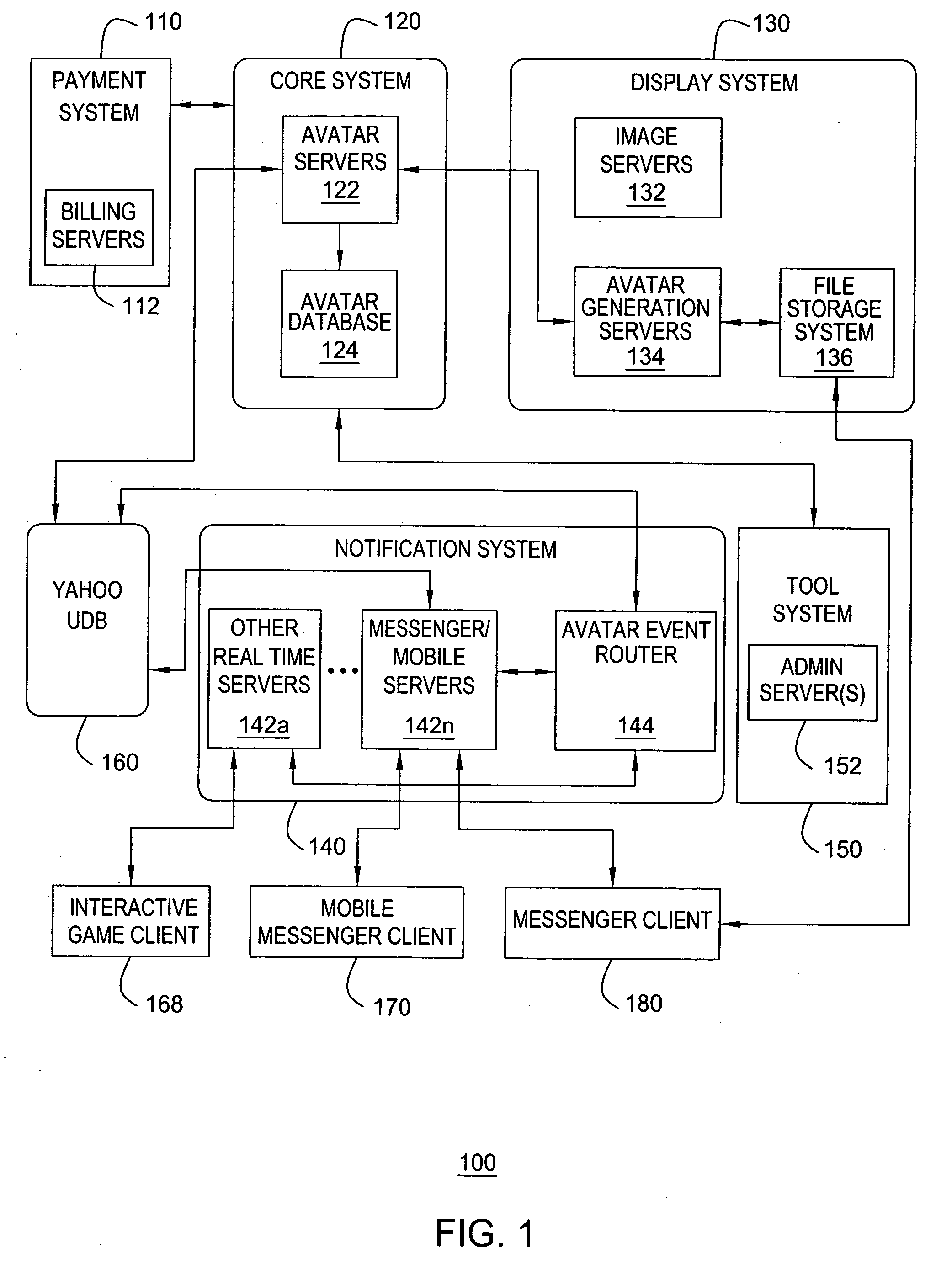
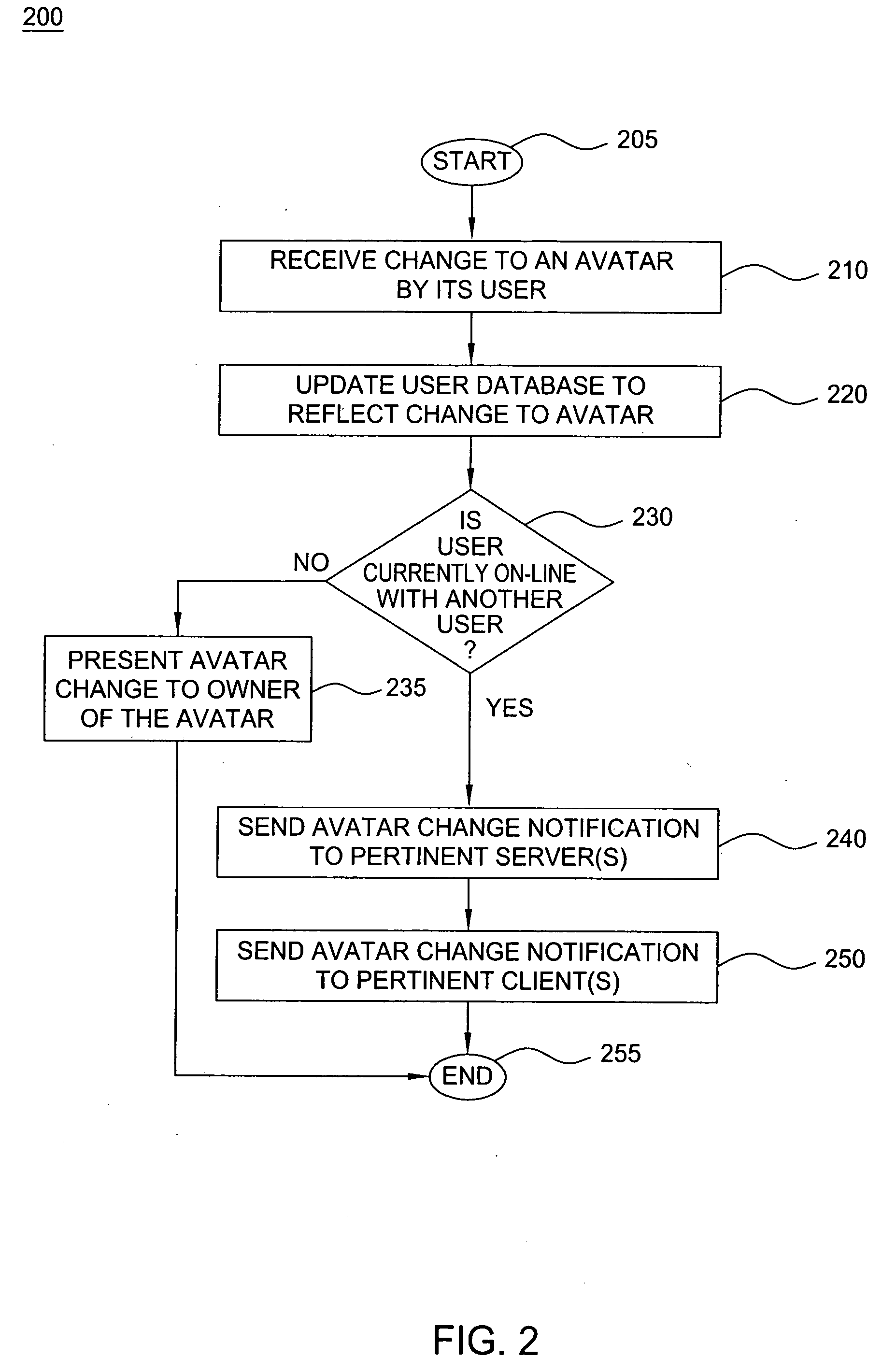
Method and apparatus for providing real-time notification for avatars
ActiveUS7865566B2Special service provision for substationMultiple digital computer combinationsApplication softwareOnline identity
A real time notification for updating online identities, known as avatars, is disclosed. For example, when a user updates his or her avatar(s), the changes are stored in a user database. The changes are also detected by an event router that sends a change notification in real time to all pertinent servers that are currently supporting on-line applications for the user. The servers will send the change notification in real time to pertinent clients, e.g., an instant messenger client, a mobile instant messenger client, an interactive game client and the like.
Owner:R2 SOLUTIONS
Trust inheritance in network authentication
InactiveUS20050198534A1Digital data processing detailsUser identity/authority verificationUnique identifierOne-time password
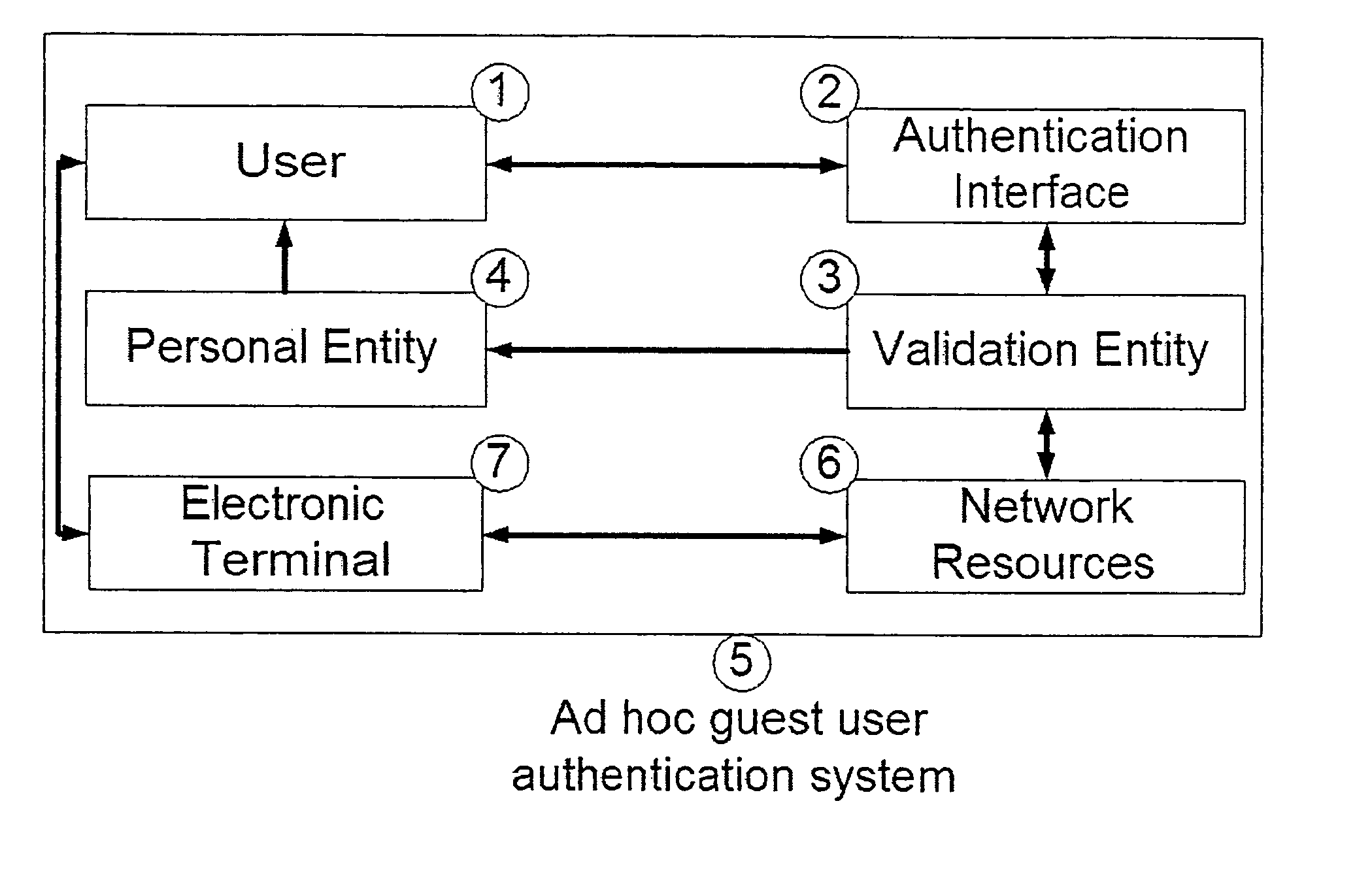
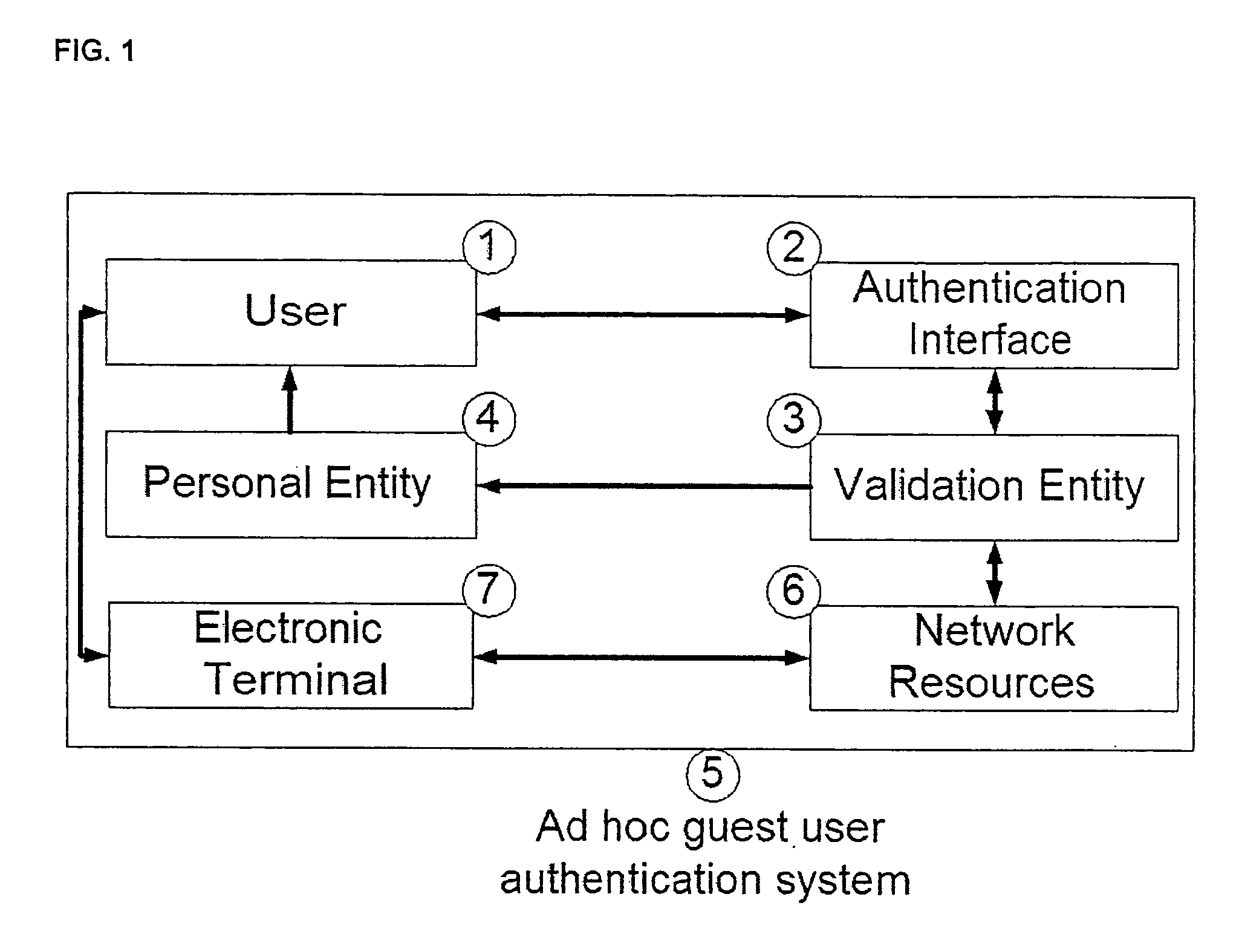
A system and method for providing ad hoc controlled user access to wireless and wireline IP communication networks while maintaining privacy for users and traceability for network providers. The method includes an authentication interface accepting user credentials, and a validation entity for credential verification and access authorization. The credentials include a unique identifier and a system generated password. The unique identifier is associated with a personal entity of the user such as a cellular telephone. The password is transmitted to the user through a SMS message to his cellular telephone. The user's Internet session is monitored by the system and all records are indexed by his cellular telephone number. The system and method therefore permit fast and traceable access for guest users at networks where they are were not previously known. Alternatively, users do not provide their unique identifiers such as cellular telephone numbers which are instead already stored in the system. A user provides a username and a one time password is generated by the system and sent to the user by SMS. This enables the system to validate the user's identity as well as the user to validate the Internet resources' identity.
Owner:SESAME NETWORKS +1
Method and apparatus for providing flash-based avatars
Method and apparatus for providing flash based online identities is disclosed. For example, the present invention applies a multimedia animation component such as a Flash component in the present avatars architecture. In one embodiment, each avatar is represented using a plurality of layers, where each layer employs at least two objects. Using two objects for each layer allows the present invention to minimize flicking when the avatar is animated.
Owner:R2 SOLUTIONS
Evaluating relying parties
InactiveUS7831522B1Electronic credentialsPayments involving neutral partyInternet privacyOnline identity
Determining reputation information is disclosed. A honey token is included in an online identity data. The honey token is to monitor for misuse of all or part of the online identity data. Optionally, information associated with at least one use of the honey token is aggregated with other reputation information.
Owner:CA TECH INC
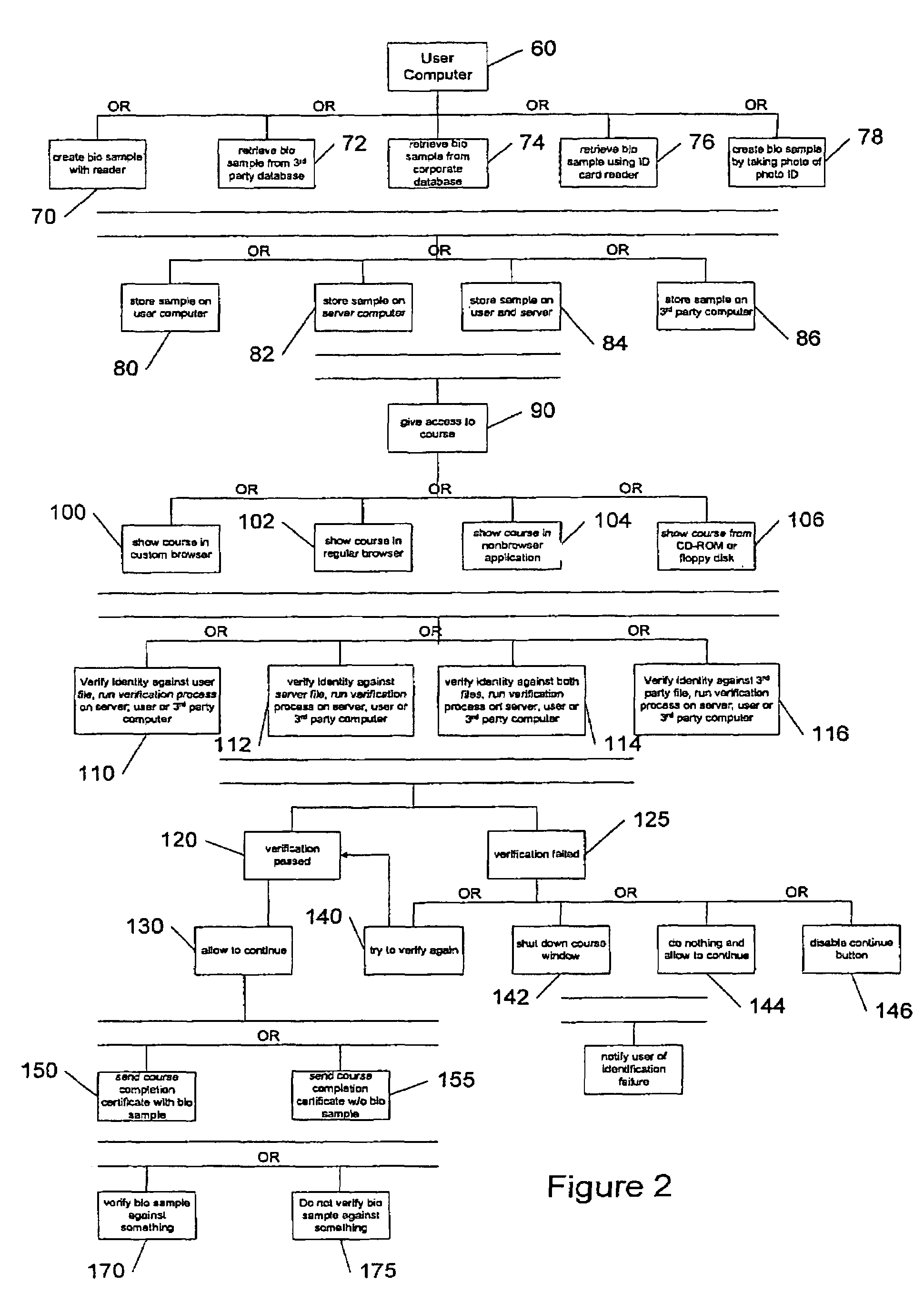
Systems and methods for online identity verification
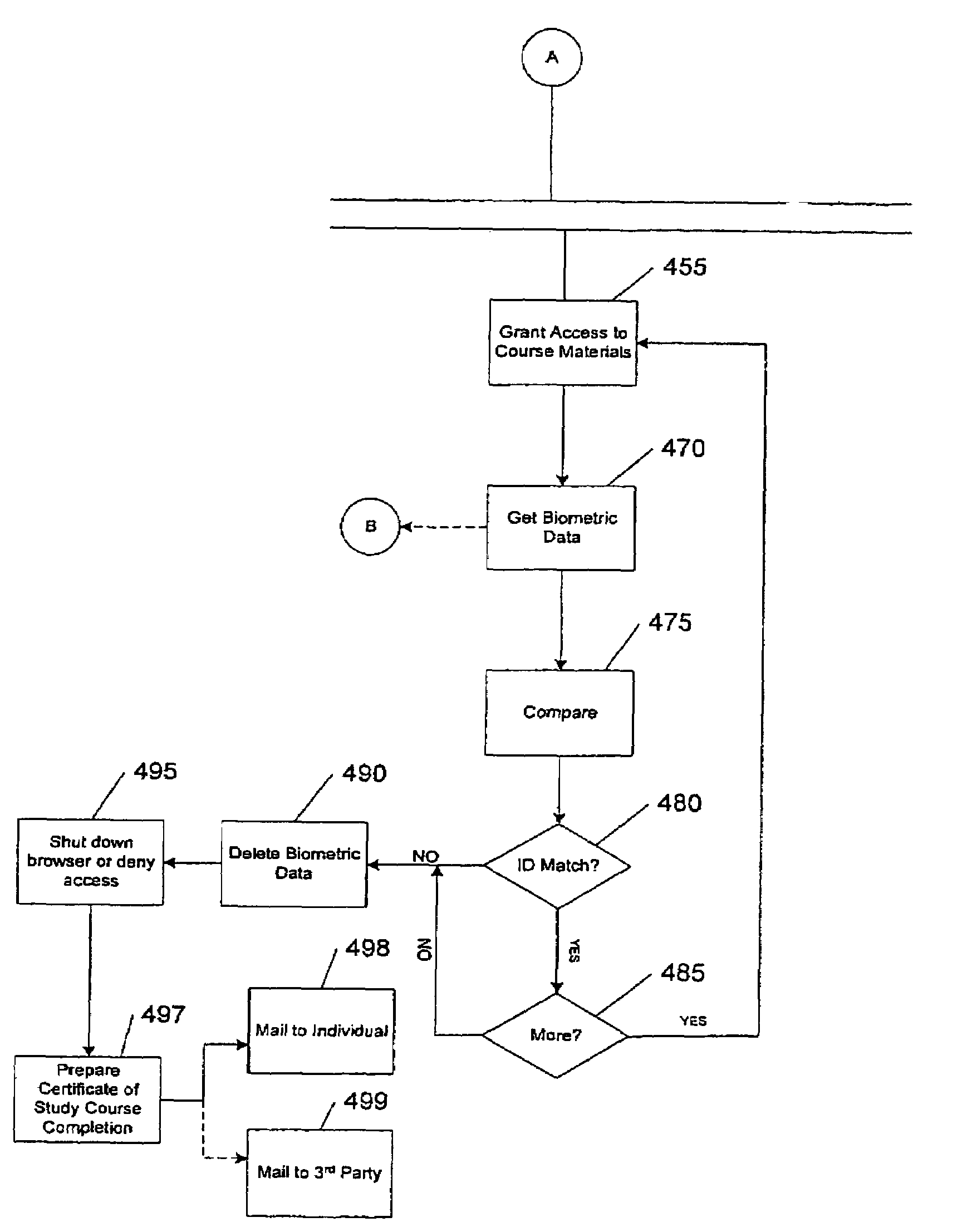
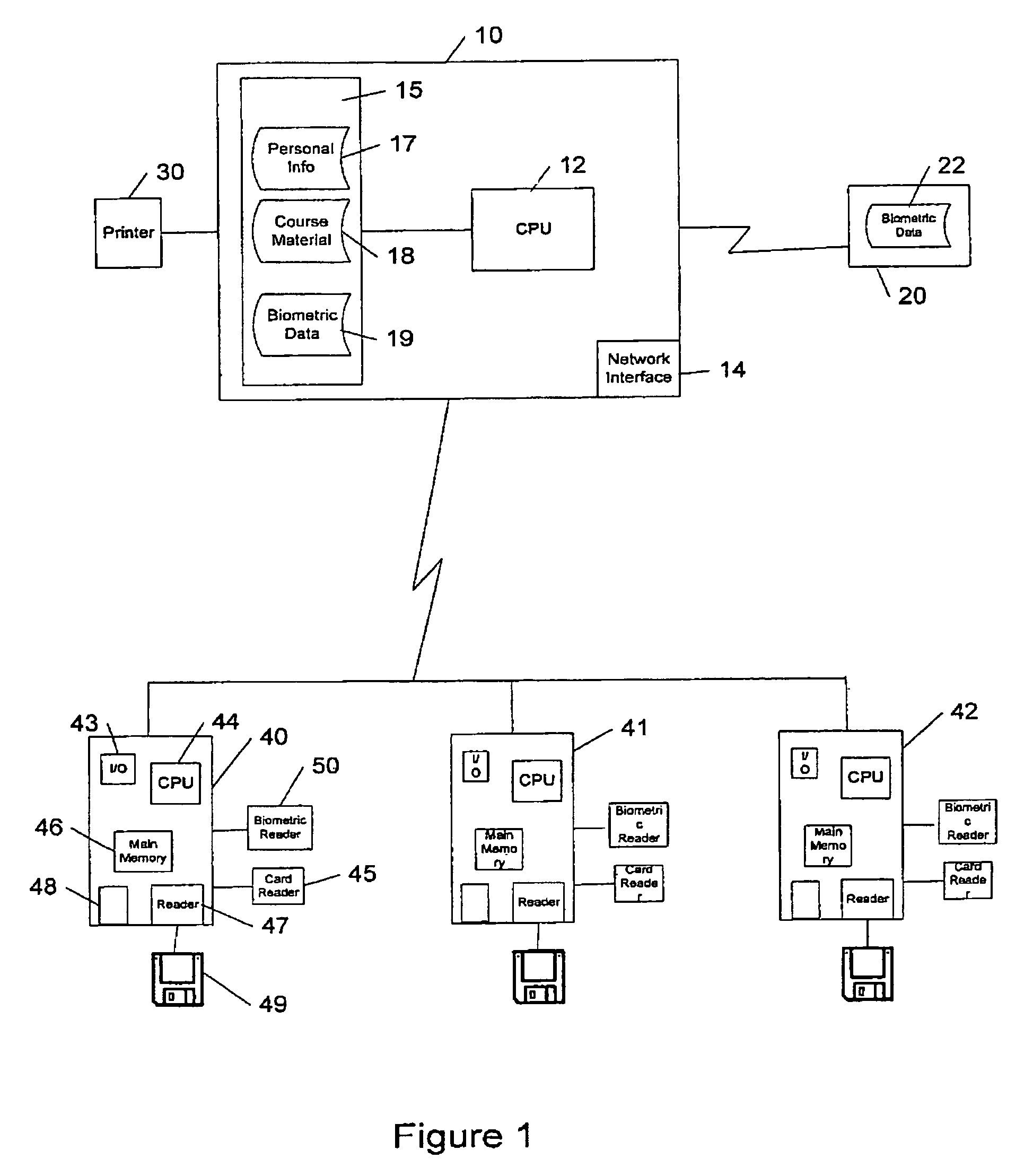
ActiveUS7308581B1Digital data processing detailsUser identity/authority verificationBiometric dataIncluded study
A system controlling online access to a study course verifies the identity of an individual taking a study course over a global computer network from a first computer at a node of the network. The first computer has a biometric identification program and communicates over the network with a second computer that is at a network node other than a node of the first computer. The second computer includes study course material. The first computer operates a biometric reader, which obtains a first set of biometric data from the individual and a second set of biometric data from the individual while access is granted to course material. The biometric identification program compares the first set of data with the second set of data to make a verification of the identity of the individual and communicates the verification to the second computer.
Owner:RAKUTEN GRP INC
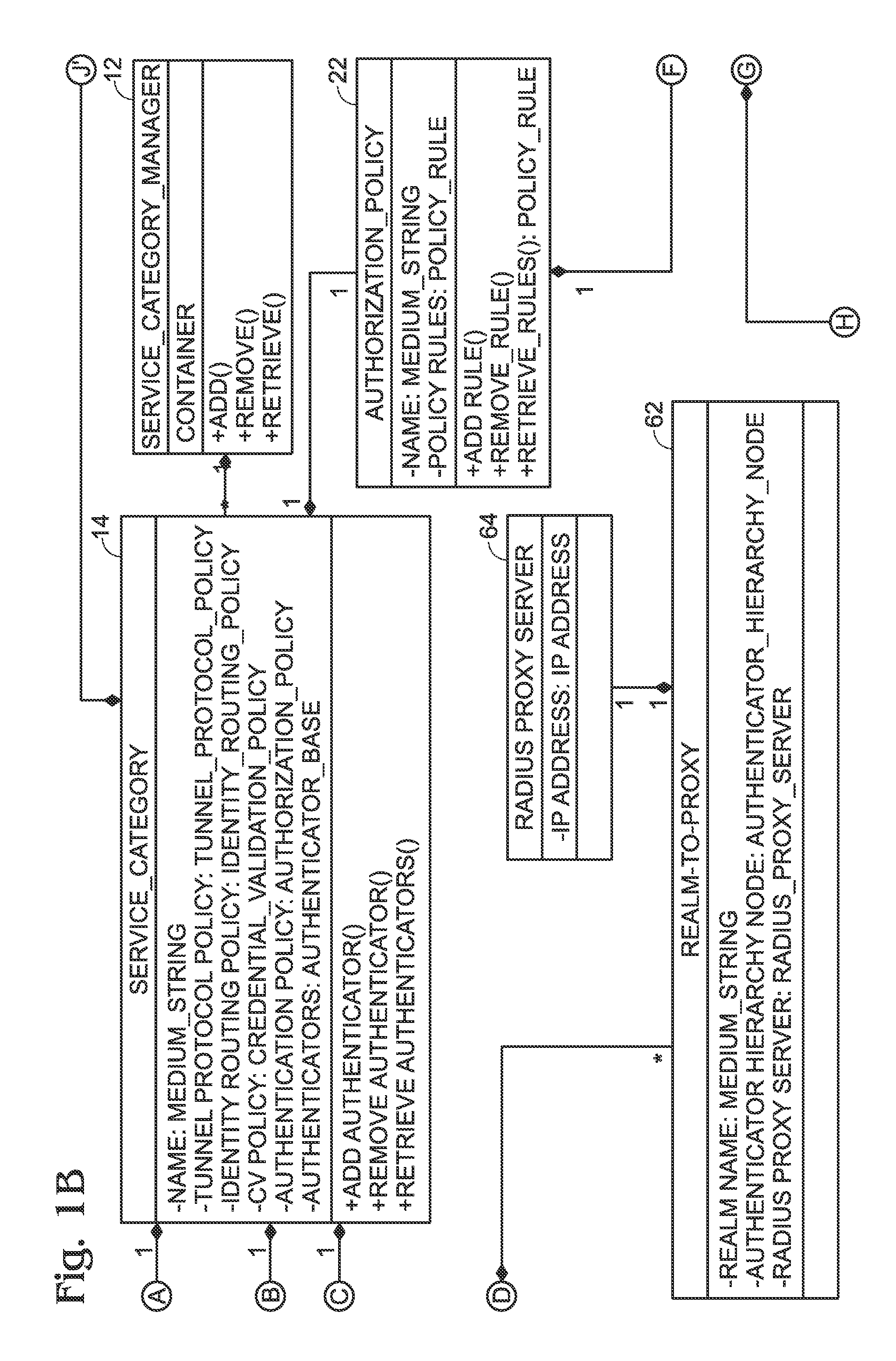
Segmented Network Identity Management
A service category associates a set of authenticators and a set of authentication and authorization policies. When an authenticator attempts to connect the network, the service category for such authenticator determined and the authentication and authorization policies applied. A feature of the present invention is that these policies are segmented into several sub-policies to support multiple services and apply different authentication and authorization policies for each type of service. These sub-policies are a tunnel policy, a credential validation policy, in inner tunnel policy and an authorization policy. Successful negotiation of each policy allows the authenticator to connect a network.
Owner:RPX CLEARINGHOUSE +2
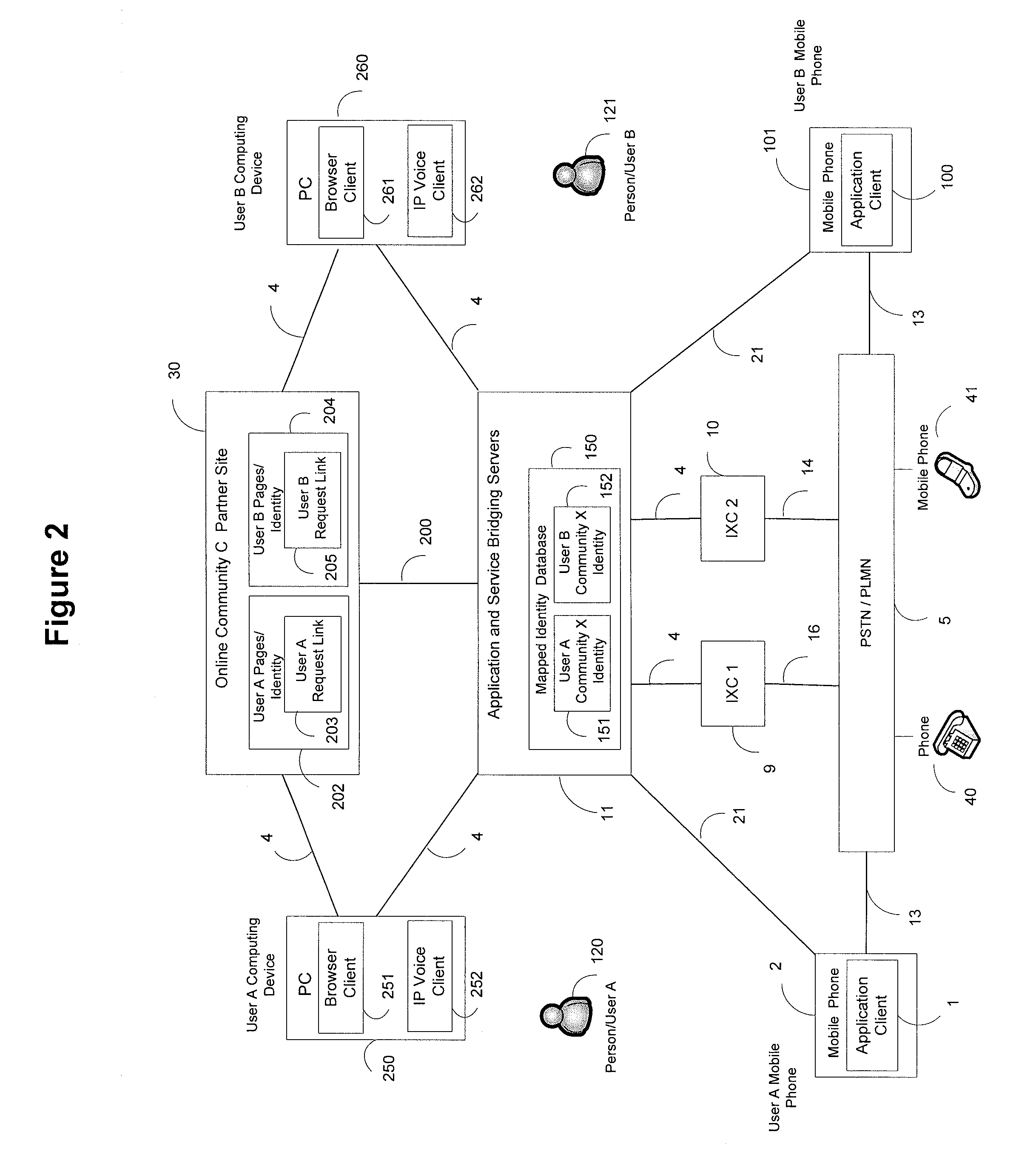
System and methods for using online community identities of users to establish mobile communication sessions
InactiveUS20070293212A1Privacy protectionEliminating exchangeAutomatic exchangesClient-sideMultiple modes
A system is disclosed that provides functionality for two users to establish multi-modal communication services including voice, messaging, and instance messaging on mobile devices using one or more online community identities. Based on the online identity and profile of a first user of on an online community, a second user may initiate a communications session request to the first user. A service bridging server may incorporate the profile and other information such as presence status of the second user into the session request message and then send the session request to the mobile client of the first user. The first user can act on the session request with a range of disposition options and multiple modes of communication types on the first user mobile device based on the online community identity of the first user and the second user.
Owner:NELTURA TECH
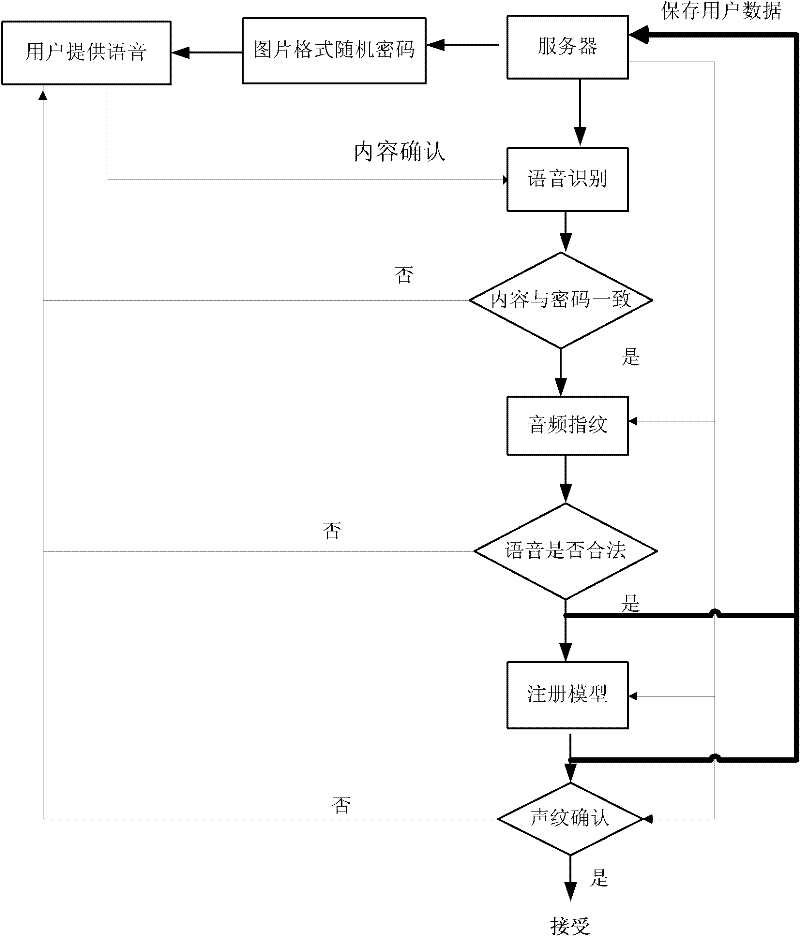
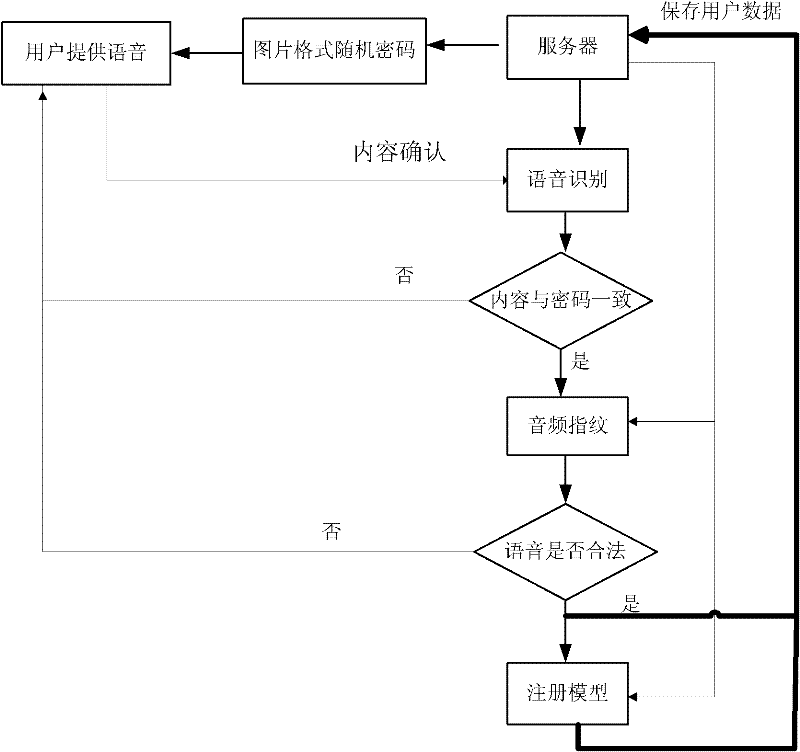
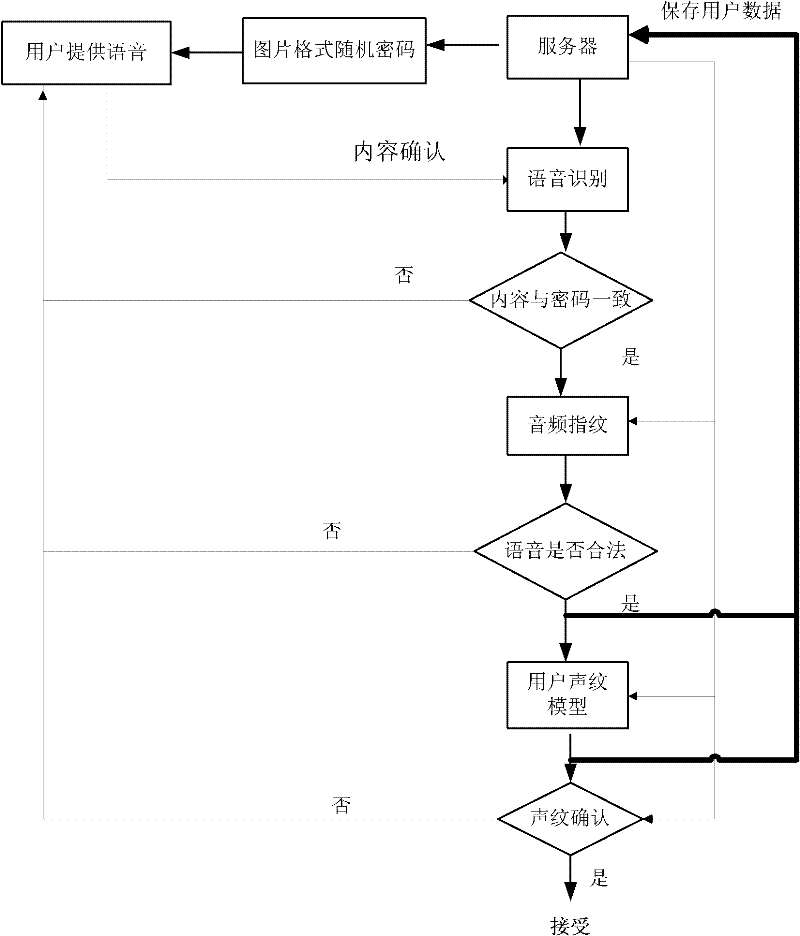
Online voiceprint recognition system and implementation method thereof
InactiveCN102543084APrevent recording attack problemImprove accuracySpeech analysisTransmissionPasswordAuthentication server
The invention discloses an online voiceprint recognition system and an implementation method thereof. The online voiceprint recognition system comprises a user recording module and an online voiceprint recognition server, and the implementation method comprises the following steps of: (1) providing generated password content for a user through the online voiceprint recognition server; (2) recording the voice of the user by utilizing the user recording module and providing the voice for a voice recognition module; (3) performing mode matching analysis on voice content provided by the user and the password content through the voice recognition module; (4) judging whether an audio fingerprint of the voice provided by the user is of the legal voice or not through an audio fingerprint recognition module; and (5) inspecting the matching degree between the voice provided by the user and a voiceprint module established by the registered user through a voiceprint recognition module, and regarding login is the real user login and receiving the login of the user if the degree achieves a set value. According to the online voiceprint recognition system and the implementation method thereof, disclosed by the invention, simple, easy-to-use and high-efficient online identity authentication can be realized.
Owner:SHENGLE INFORMATION TECH SHANGHAI
Network identity verification method based on internet third party biological characteristic validation
InactiveCN101316169AGuaranteed reliabilityEnsure safetyUser identity/authority verificationCharacter and pattern recognitionMultiple encryptionApplication software
The invention provides a network identity authentication method based on the biological characteristic authentication of a third party on the Internet. The biological characteristics (fingerprint, human face, iris, lip membrane and so on) are used as the identity identification of the user, the user can obtain an authentication request from the third party by submitting the biological characteristic codes through a client terminal widget provided by the third party, the identity authentication is carried out through the request password process and the matching algorithm, the Internet identity authentication can be carried out through a fully cooperative website or an application program provided by a cooperative network in a self-help mode, the third party provides request interfaces containing the registration, verification, reset of the biological characteristics, binding information,etc., the third party needs not to know the name of the user in the cooperative website or the application program provided by the cooperative network, thus avoiding to obtain the other information of the user in the cooperative website or the application program provided by the cooperative network, the reliability at the service terminal and the communication safety among the three parties can be guaranteed through the complete active service request of the cooperative website or the application program provided by the cooperative network, the Cookie, SSL, multi-encryption, digital signature of the widget, user-defined words or pictures,etc.
Owner:张曌 +2
Method and apparatus for providing real-time notification for avatars
A real time notification for updating online identities, known as avatars, is disclosed. For example, when a user updates his or her avatar(s), the changes are stored in a user database. The changes are also detected by an event router that sends a change notification in real time to all pertinent servers that are currently supporting on-line applications for the user. The servers will send the change notification in real time to pertinent clients, e.g., an instant messenger client, a mobile instant messenger client, an interactive game client and the like.
Owner:R2 SOLUTIONS
Identity verification method and device
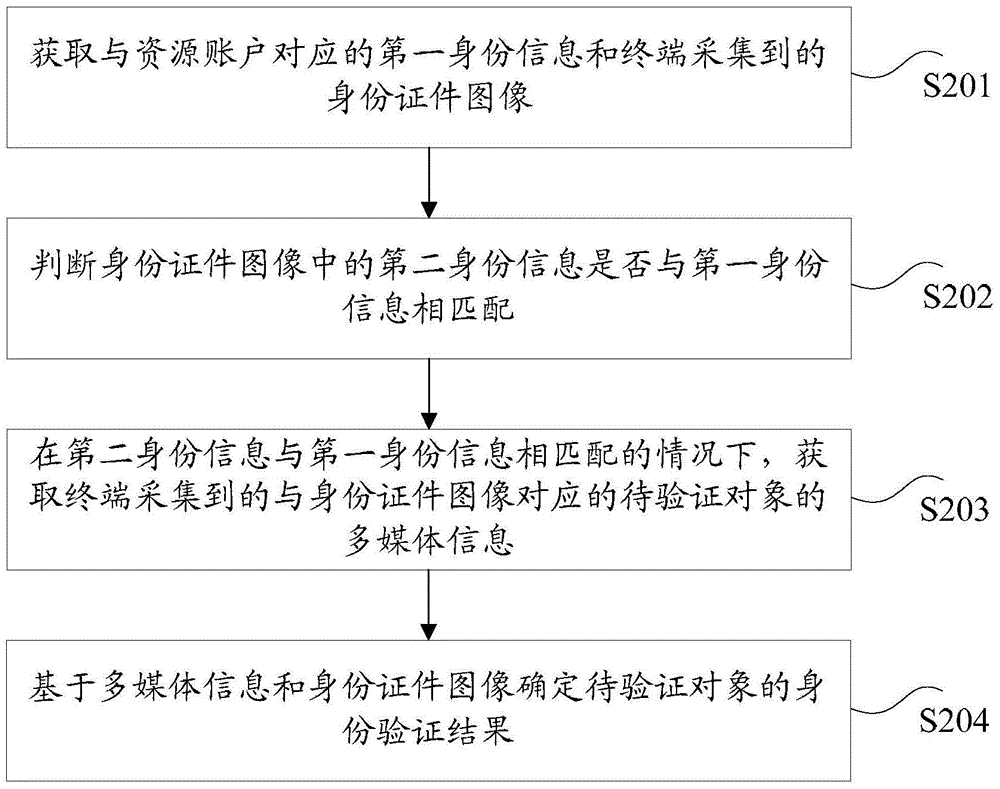
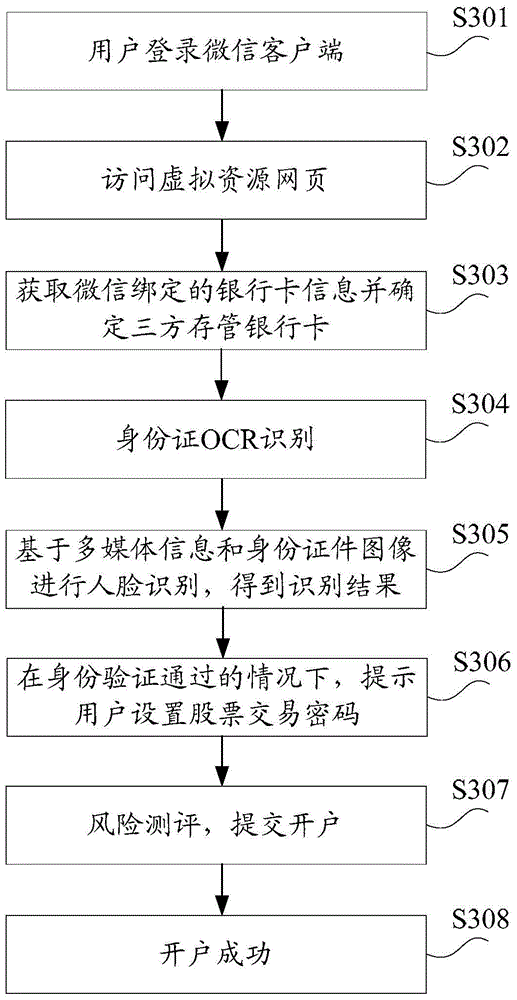
The invention discloses an identity verification method and an identity verification device. The method comprises the steps of acquiring first identity information corresponding to a resource account and an identity document image collected by a terminal; judging that whether the second identity information in the identity document image is matched with the first identity information; in the case that the second identity information is matched with the first identity information, acquiring the multimedia information of an object to be verified corresponding to the identity document image and collected by the terminal; and determining the identity verification result of the object to be verified based on the multimedia information and the identity document image. According to the method, the technical problem that in the related technologies, the time cost is high when the online identity verification is performed is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
InactiveUS20070186099A1Efficient and effectiveNetwork topologiesDigital data authenticationBrute forcePrivate network
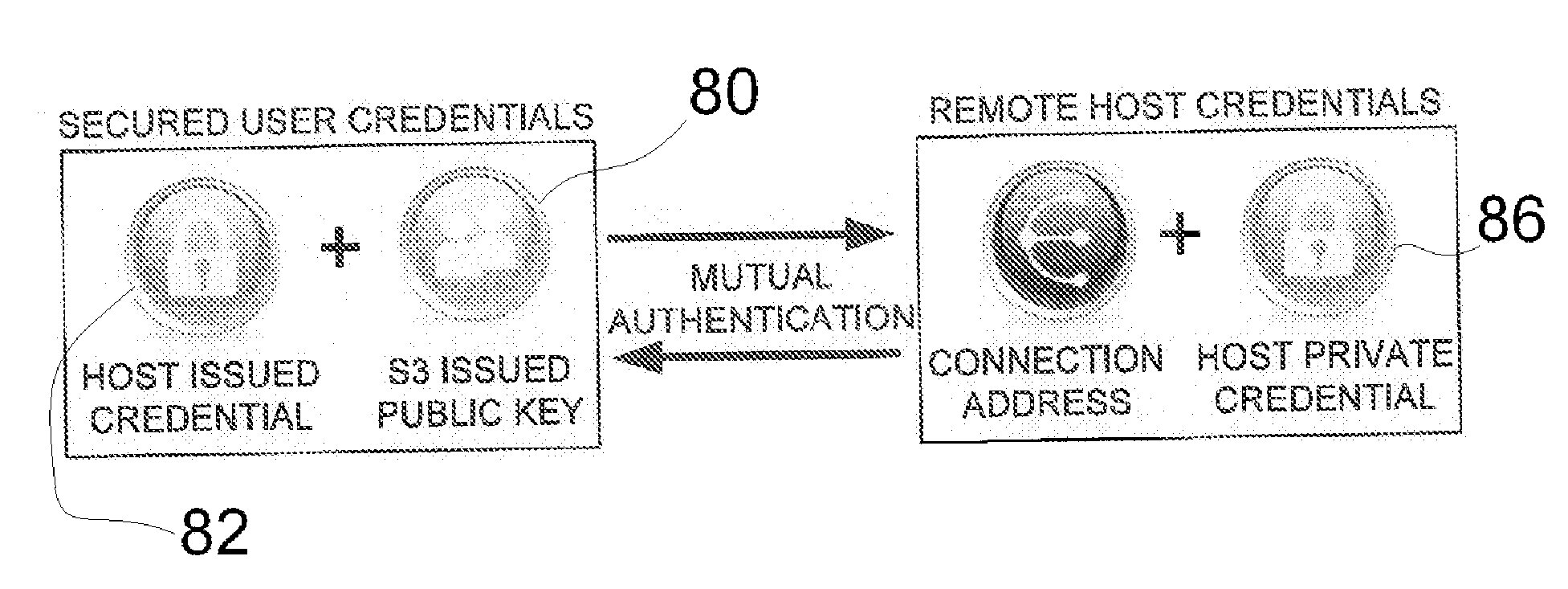
A two-factor network authentication system uses “something you know” in the form of a password / Pin and “something you have” in the form of a key token. The password is encrypted in a secure area of the USB device and is protected from brute force attacks. The key token includes authentication credentials. Users cannot authenticate without the key token. Four distinct authentication elements that the must be present. The first element is a global unique identifier that is unique to each key. The second is a private credential generated from the online service provider that is stored in a secure area of the USB device. The third element is a connection profile that is generated from the online service provider. The fourth element is a credential that is securely stored with the online service provider. The first two elements create a unique user identity. The second two elements create mutual authentication.
Owner:DIRECTPOINTE
Distributed Network Identity
InactiveUS20080014931A1Improve user interactionAssure integrityMultiple digital computer combinationsDigital data authenticationInformation sharingInternet privacy
A distributed network identity is provided. An identity provider stores a portion of a user's personal information. A service provider accesses user information from one or more identity providers. System entities such as identity providers and service providers can be linked to enable information sharing and aggregation. User policies and privacy preferences are provided to control how information is shared. A single sign-on architecture is provided where an identity provider is used to facilitate cross-domain authentication and to enhance user convenience. Service delegation features are also provided.
Owner:ORACLE INT CORP
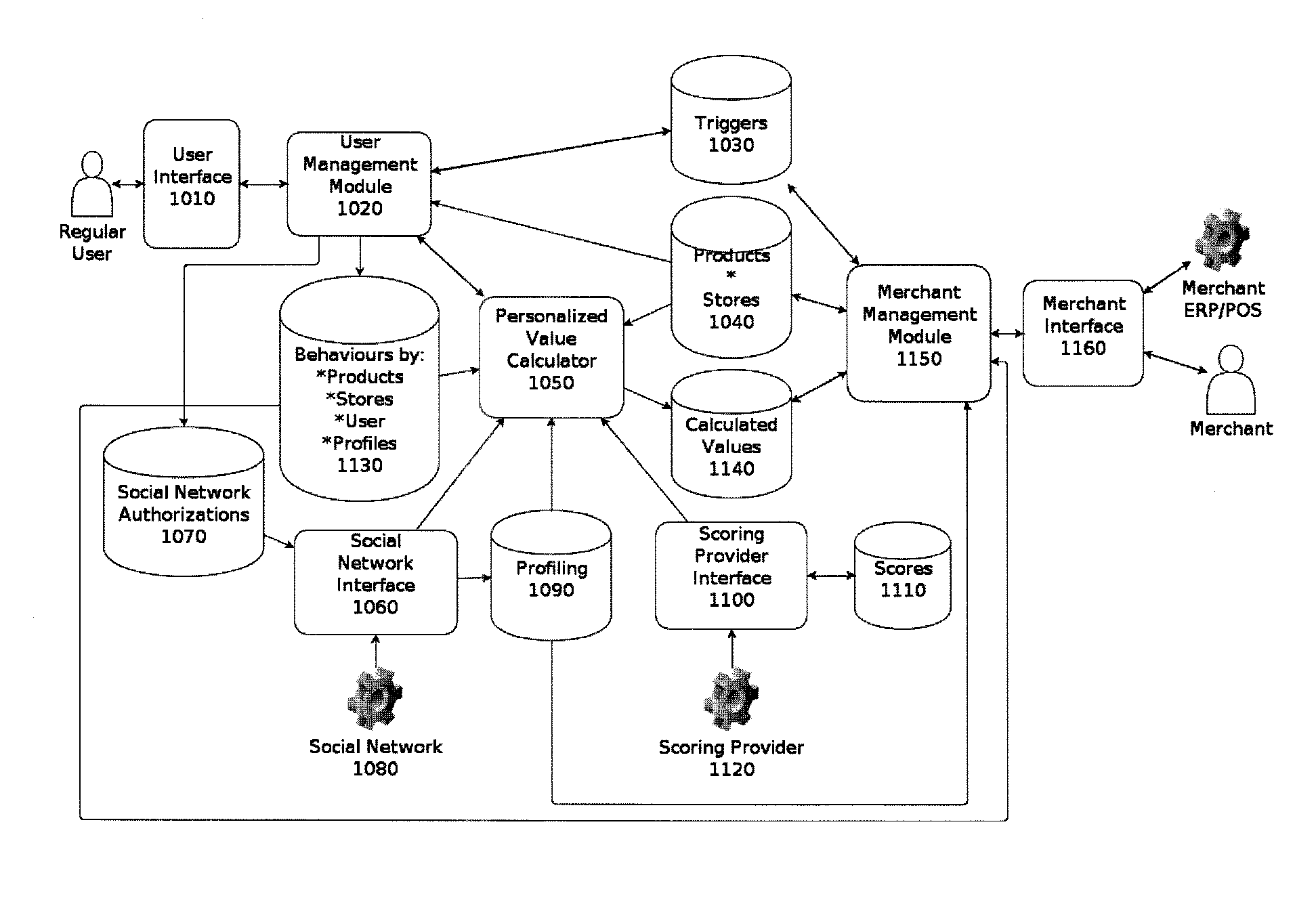
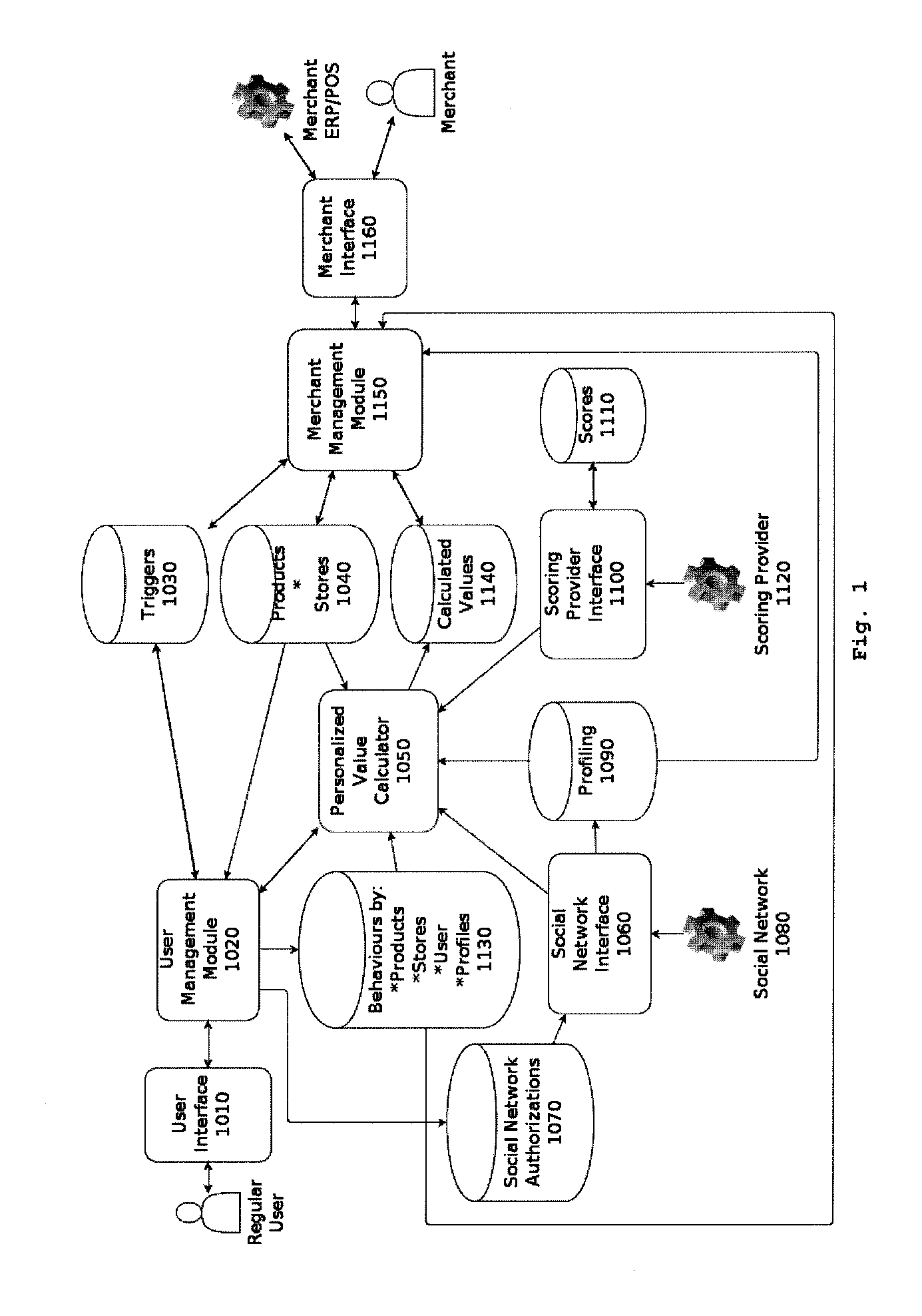
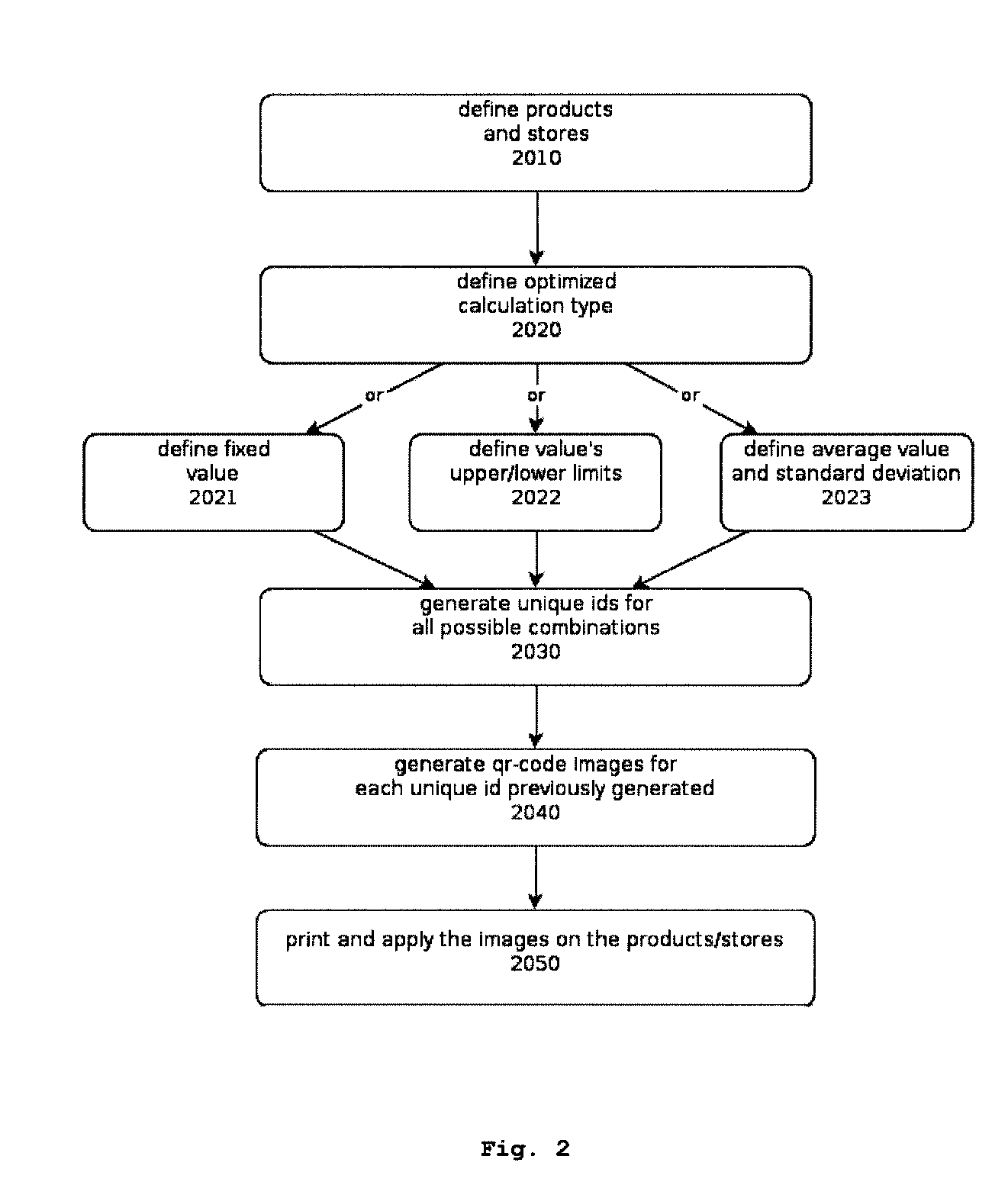
System and method for calculating dynamic prices
InactiveUS20150127439A1Convenient for advertisingStrengthen incentivesMarketingData connectionPersonalization
System to manage and provide dynamic personalized prices as a result of a promotion of the product by the customer on the internet, in particular through a mobile device.The present invention has application in the intersection between physical commerce and the online identity of its customers using their mobile phones and its data connections as a means for identification and communication.This invention consists in a computer system that allows customers of physical stores, using their mobile phones, to promote the store and its products and be rewarded with special deals with optimized value and customized for that particular customer, taking into account, among other things, the degree of his online social influence.Accordingly, the present invention is useful for allowing algorithmically optimization of the prices of their products, and for letting the store know automatically and in real time the identity of the customers present in their stores as well as the products they are interested.
Owner:UBIPRISM LDA
Log-in authentication system for service website and implementation method
InactiveCN101895513AEliminate worriesReduce the risk of stealing account informationUser identity/authority verificationSensing record carriersPasswordInternet users
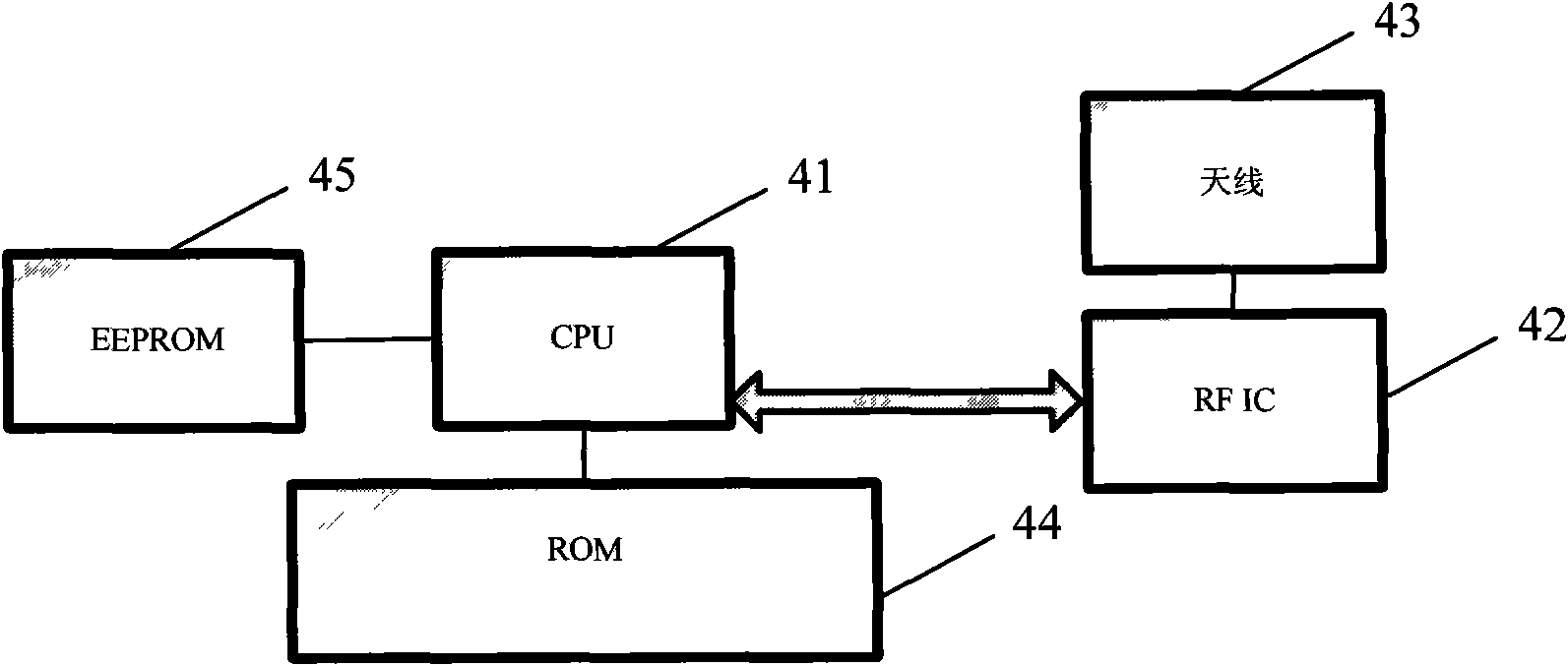
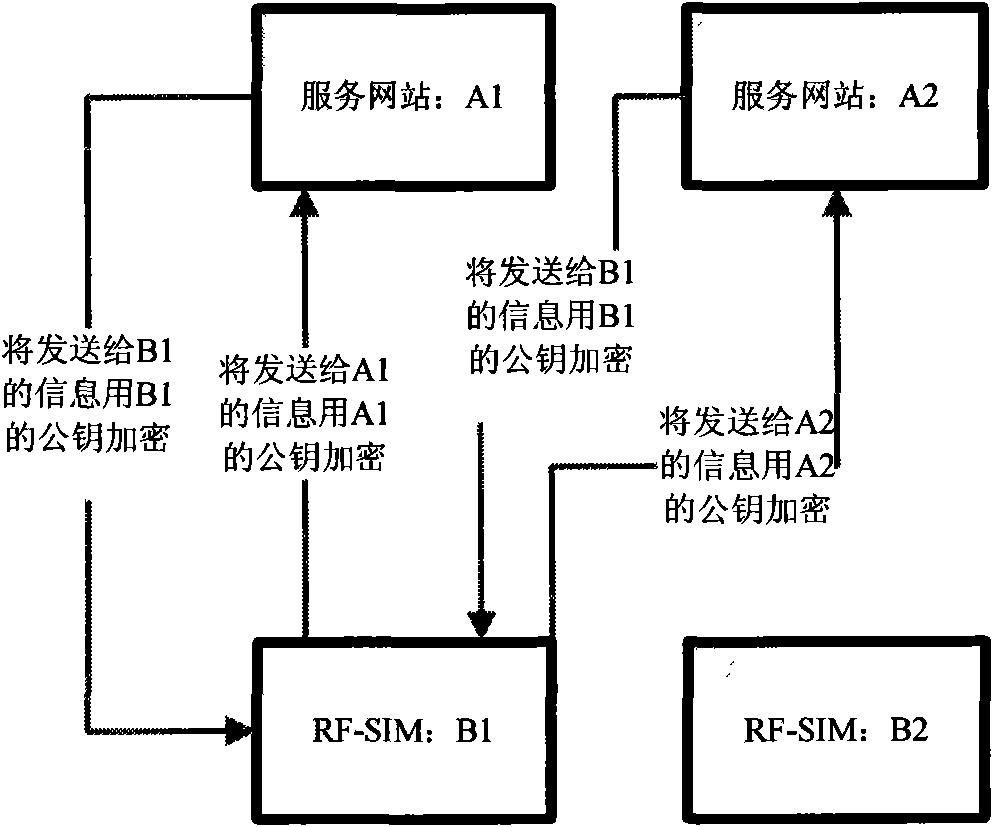
The invention provides a log-in authentication system for a service website and an implementation method. In the method, a radio frequency-subscriber identity module (RF-SIM) card is a storer of subscriber names and passwords of a subscriber, the subscriber can log in various websites by the RF-card, and a radio frequency-POS (RF-POS) which is connected with service website terminals is used for encrypted communication transmission of a log-in ID and a password, thereby avoiding the trouble that the subscriber has to remember information of the subscriber names and passwords of different websites and reducing risk that ID information is stolen by Trojans when the subscriber inputs information of the subscriber names and the passwords via a keyboard. In addition, the RF-SIM card can also be used a USB Key, which is easy and portable with multi-functions. By using the invention, the subscriber can easily manage frequently-used internet IDs and passwords, remember the IDs and the passwords even if internet services are increased day by day, and realize easy internet service log-in by safe and reliable internet ID authentication.
Owner:CHINA ELITE INFORMATION TECH
Method and system for temporary network identity
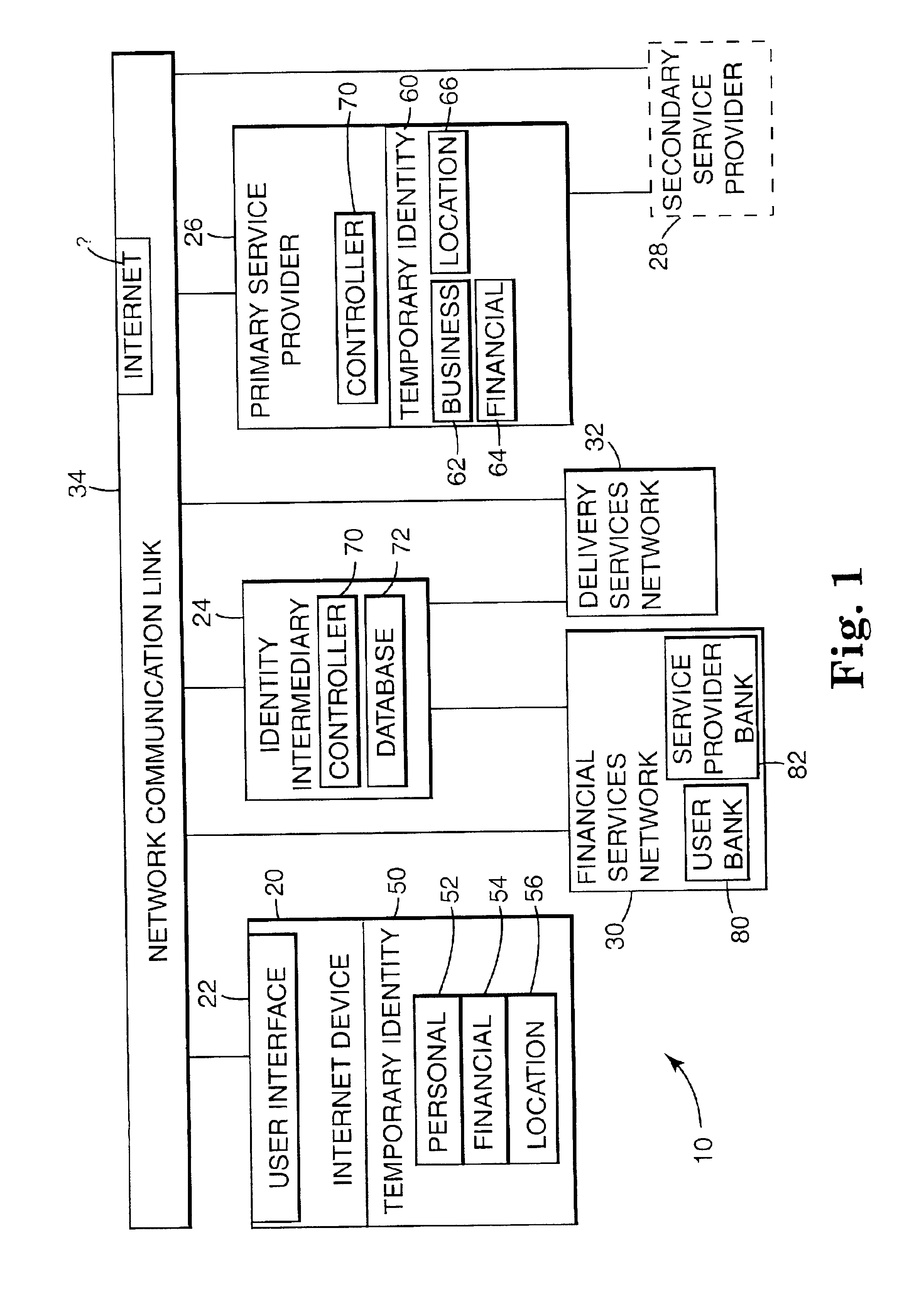
ActiveUS6937976B2Multiple digital computer combinationsBuying/selling/leasing transactionsFinancial transactionNetwork communication
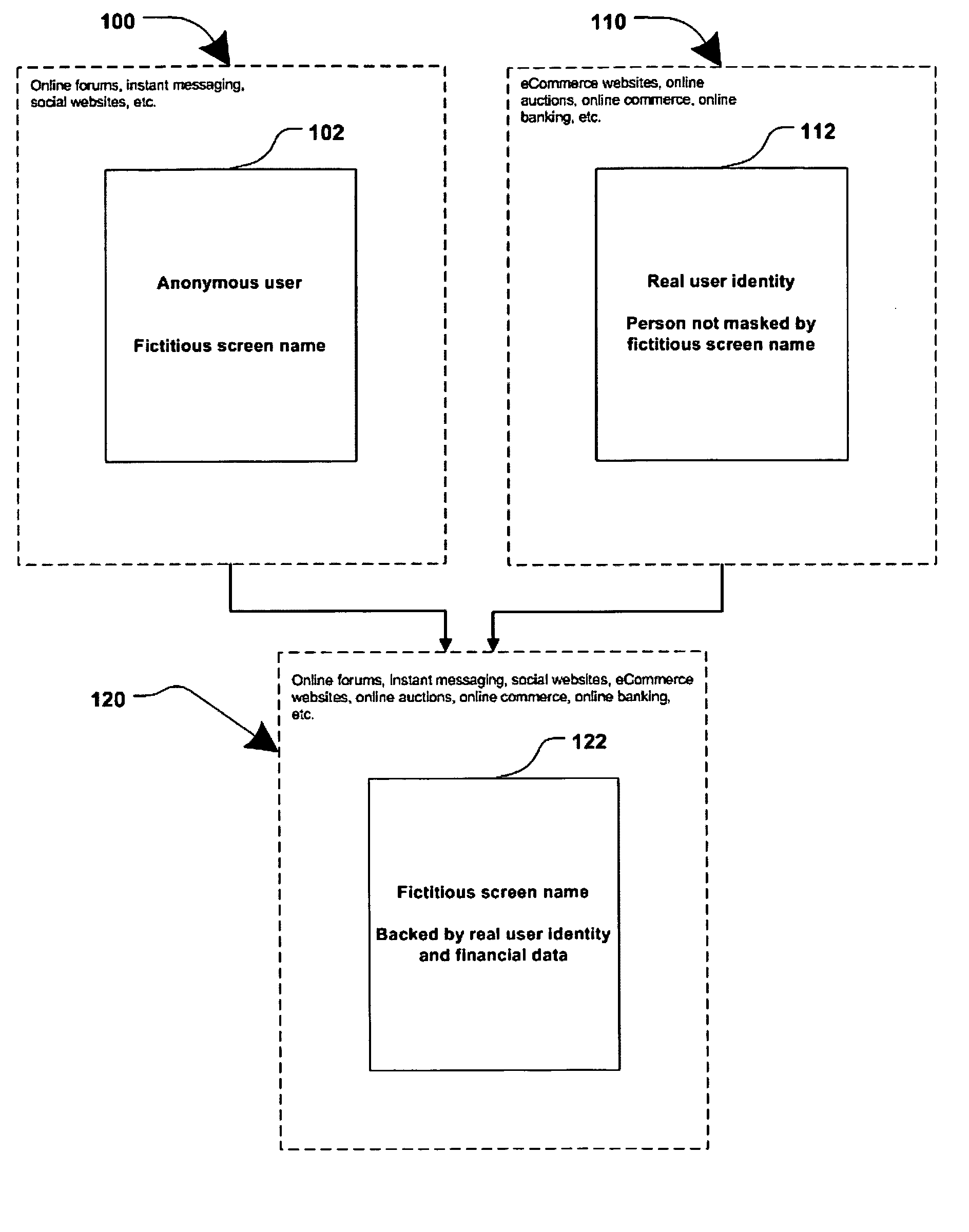
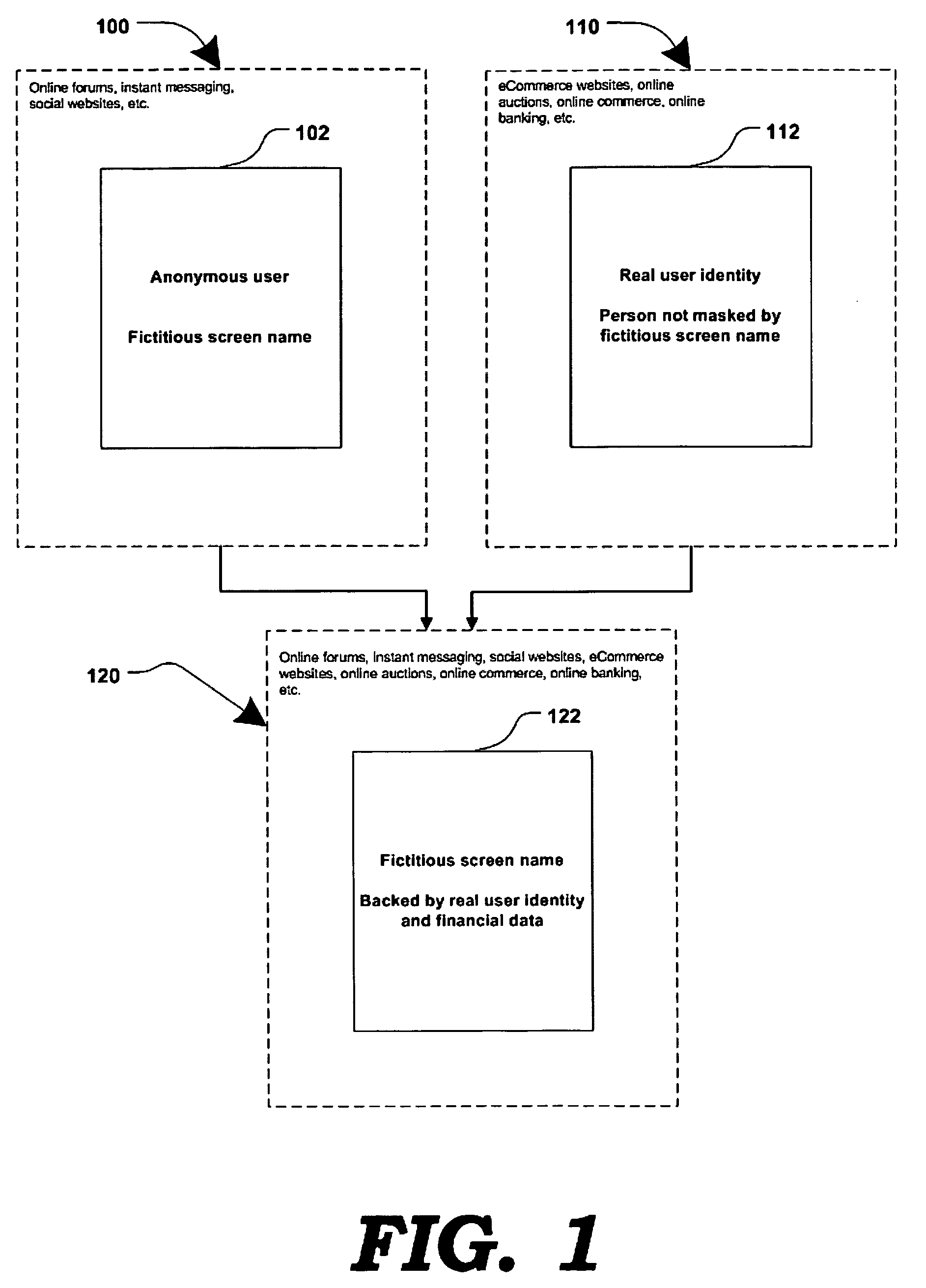
A method for network communications comprises assigning a temporary fictitious identity from a identity intermediary to at least one of a service provider and a user interface and performing a transaction between the user interface and the service provider using the temporary fictitious identity. A network identity intermediary system comprises a controller configured for assigning a temporary identity to at least one of a user interface and a service provider, and a database configured for maintaining private information of the at least one user interface and service provider in association with the temporary fictitious identity.
Owner:HEWLETT PACKARD DEV CO LP +1
System for non-repudiable registration of an online identity
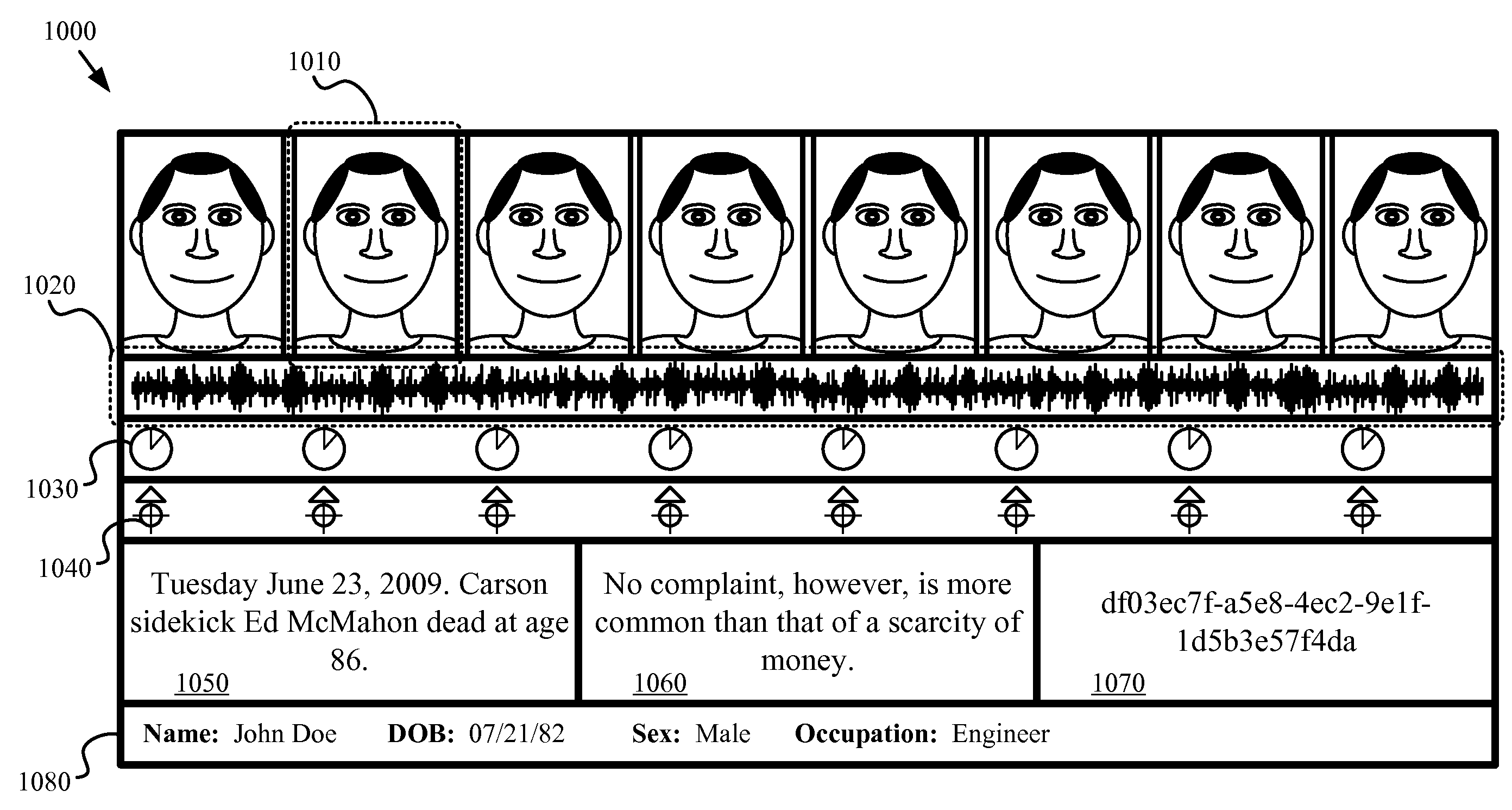
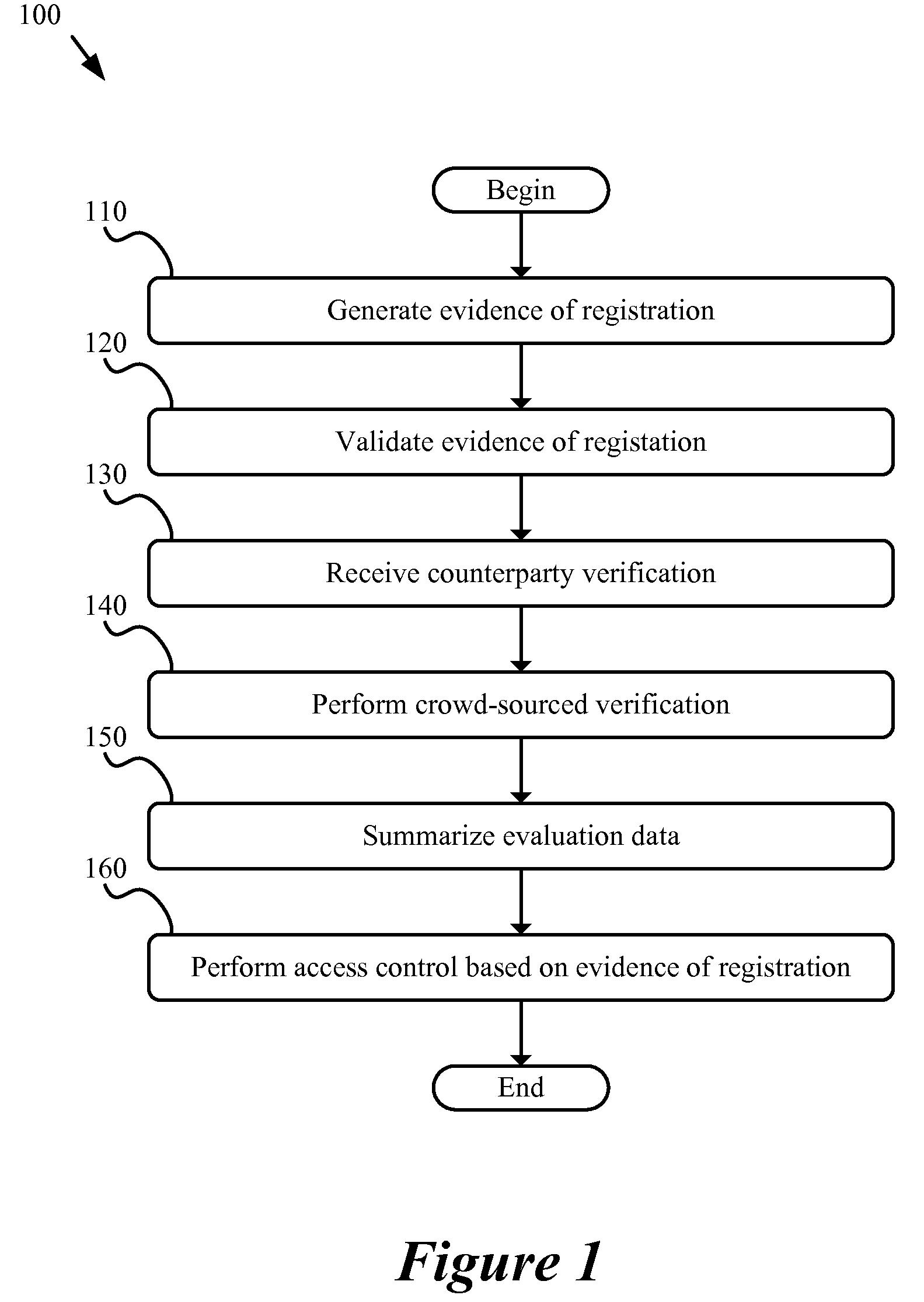
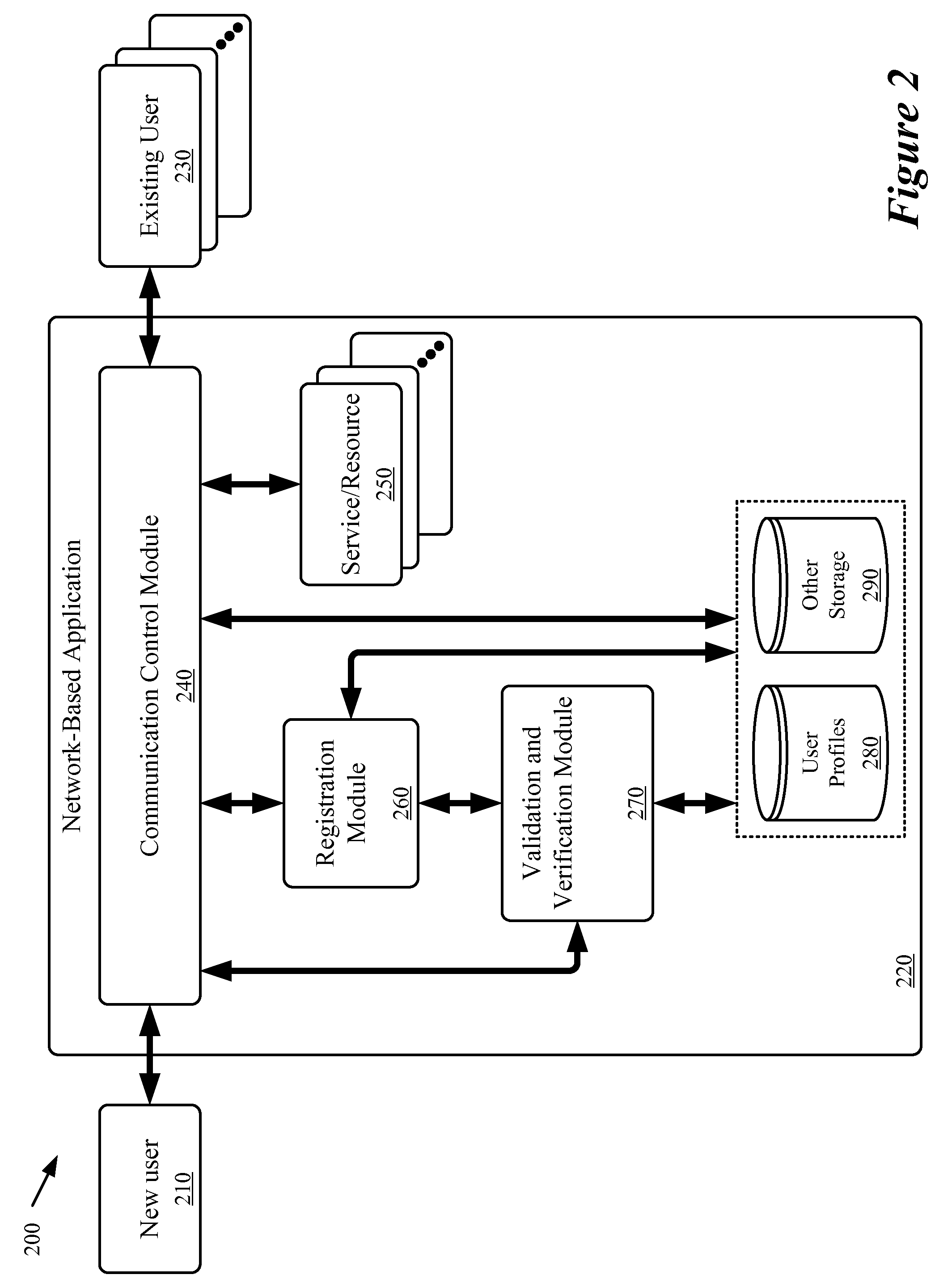
A method of generating irrefutable evidence of registration that cannot be repudiated by the registrant for a network-based application is described. The method initiates an image capture session to capture a plurality of images of an individual user. The method, during the image capture session, provides a sequence of tasks to be performed by the individual user in order to validate the image capture session in capturing an image of a person participating in a real-time event.
Owner:FREEDMAN STEVEN JAY
Identity authentication system and method based on electronic identification card
ActiveCN104994114AProtect identity privacyImprove reliabilityUser identity/authority verificationElectronic identificationOnline identity
The invention provides an identity authentication system and method based on an electronic identification card. The identity authentication system comprises an intelligent terminal, an operator server, a network identity authentication center and an application platform. The intelligent terminal is used for storing a first temporary secret key only associated with the electronic identification card of a user, and generating to-be-authenticated encryption information and first encryption information. The operator server is used for acquiring the first encryption information, authenticating the first encryption information preliminarily, and then generating second encryption information. The network identity authentication center is used for acquiring the second encryption information, generating a second temporary secret key and authenticated encryption information, and comparing the to-be-authenticated encryption information with the authenticated encryption information so as to realize authentication of the user identity. The application platform is connected with a secret key server. The application platform sends an authentication request and is used for acquiring a result of user identity authentication from the operator server. The first temporary secret key is stored in a safe area of the intelligent terminal, so that the user does not need to carry a hardware carrier and are not worry about risks, such as information leakage and so on when in online payment or online identity authentication.
Owner:尤磊
Global identity protector E-commerce payment code certified processing system
InactiveUS20120331557A1Digital data processing detailsAnalogue secracy/subscription systemsMedical recordCredit card
An identity theft protection system and method which employs several security features to prevent identity theft on all levels. The protection system database employs a member's address and telephone number as a numeric identity protector, security code and lock for Social Security numbers. Preventing the issuing of identity theft credit cards, and e-commerce address billing payment code numbers, and e-commerce telephone number billing payment code numbers. The locking address also prevents account hijacking, preventing checks from being mailed to identity thieves. The system employs a computer generated photo copy of the member's ID or drivers license, to prevent fraud on all big ticket items, and preventing identity theft bank fraud on checking accounts and medical records providing photo match and verify, identity theft prevention verification. The system protects its members against stolen and counterfeit checks. The G.I.P. computer database will ID the owner of the checking account at the cash register. The ID can also prevent cyber identity theft, also known as account hijacking.
Owner:WASHINGTON KEITH ANTHONY
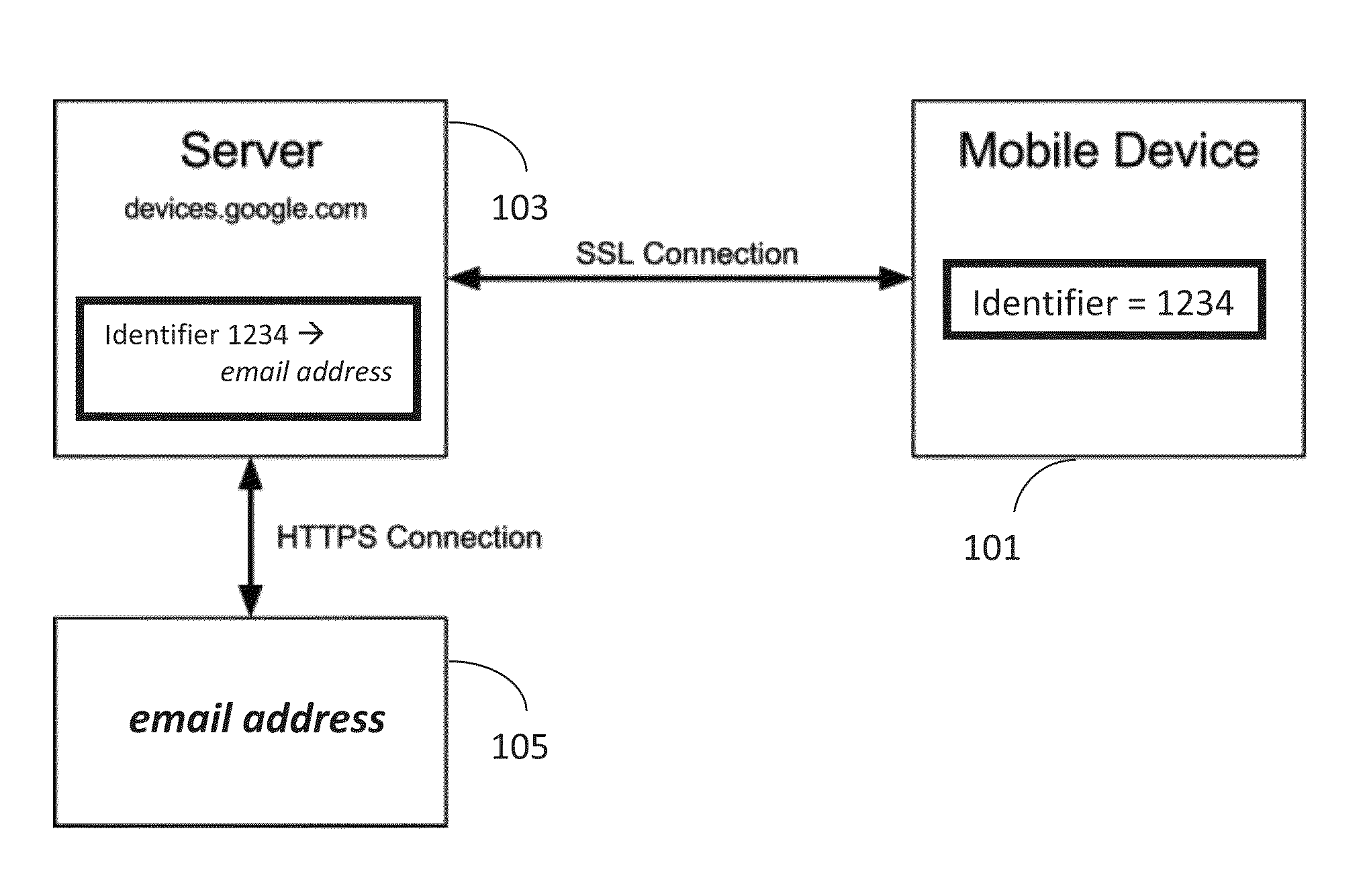
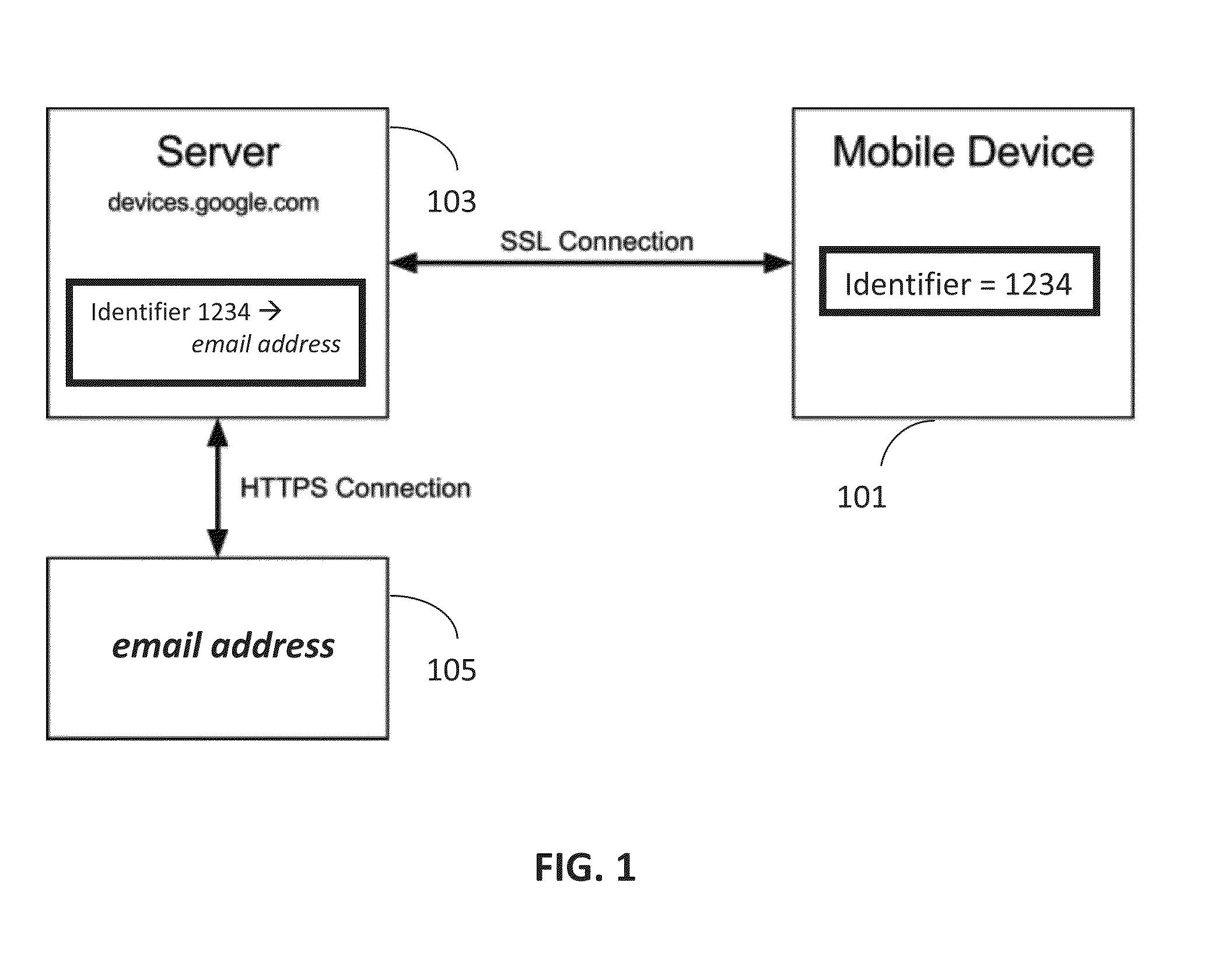
Mobility Device Security
ActiveUS20140038556A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsOperational systemUnique identifier
The present disclosure provides a system to establish a stable ownership relationship between an online identity and a mobile device. This relationship is persistent across device wipes and operating system reinstalls. Remote commands enable a user to: locate the mobile device; wipe user data off the mobile device; disable the mobile device; display a permanent message on the mobile device; and return a disabled mobile device to normal. Ownership is established when the mobile device is purchased. Thereafter, the ownership is maintained in a host sever through an association between a unique identifier of the mobile device and the owner's online identity. The owner of the mobile device may remotely send an encrypted command to the mobile device, for example, if the mobile device is lost or stolen. The encrypted command is decrypted by the mobile device and the result of the command may be returned remotely to the owner.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com