Identity verification method and device
An identity verification and identity document technology, applied in the Internet field, can solve the problem of high time cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] According to an embodiment of the present invention, an identity verification method is provided, the steps shown in the flowchart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although the logic shown in the flowchart order, but in some cases the steps shown or described may be performed in an order different from that presented here.
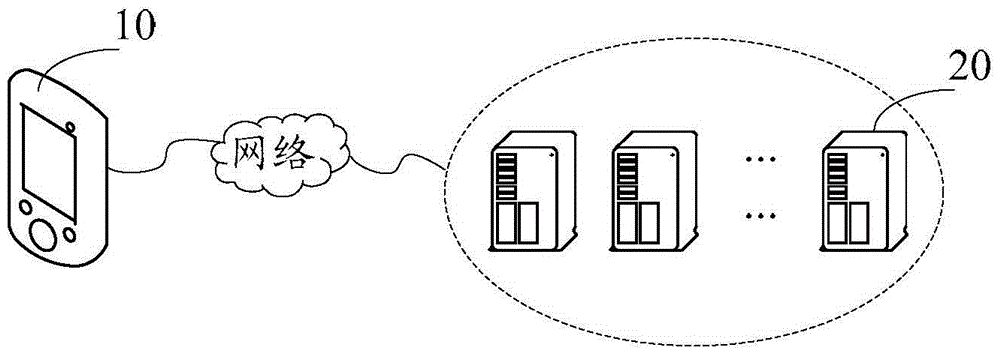
[0036] Optionally, in this embodiment, the above method can be applied to figure 1 In the hardware environment composed of the terminal 10 and the server 20 shown. Such as figure 1As shown, the terminal 20 is connected to the server 20 through the network. The above-mentioned terminals may be mobile terminals or fixed terminals, such as notebook computers, desktop computers, tablet computers, PDAs, and other handheld devices.
[0037] The above-mentioned network includes but not limited to: wide area network, metropolitan area network or local area network. ...
Embodiment 2
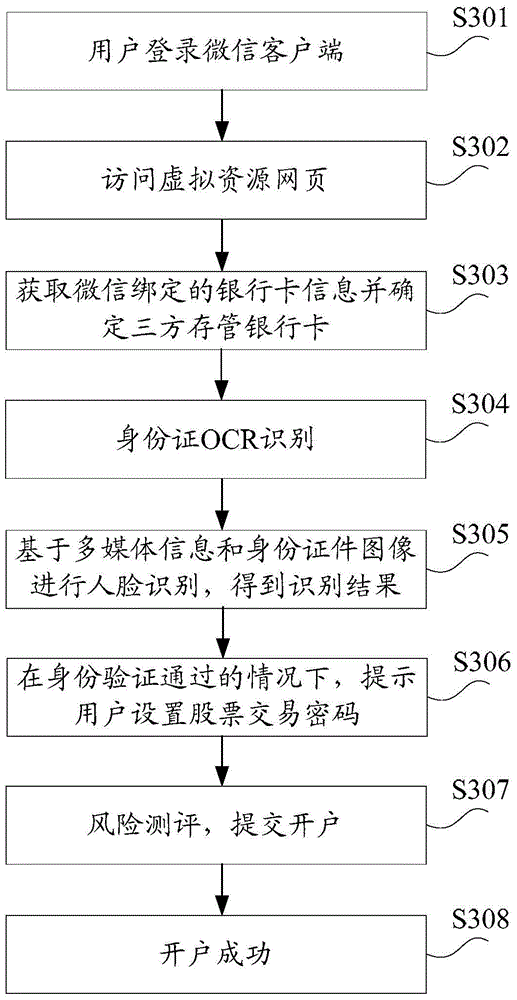
[0168] According to an embodiment of the present invention, an identity verification method is also provided, which can be applied to such as figure 1 In the hardware environment composed of the terminal 10 and the server 20 shown. Such as Image 6 As shown, the method includes:
[0169] Step S601, after receiving the collection instruction information sent by the server, collect the identity certificate image of the target identity certificate of the object to be verified, and send the identity certificate image to the server.
[0170] Step S602, receiving the information collection instruction sent by the server, wherein the information collection instruction is generated when the second identity information of the target ID card matches the first identity information of the resource account, the resource account has a corresponding relationship with the terminal, and the second The identity information is of the same type as the first identity information.
[0171] Step ...
Embodiment 3
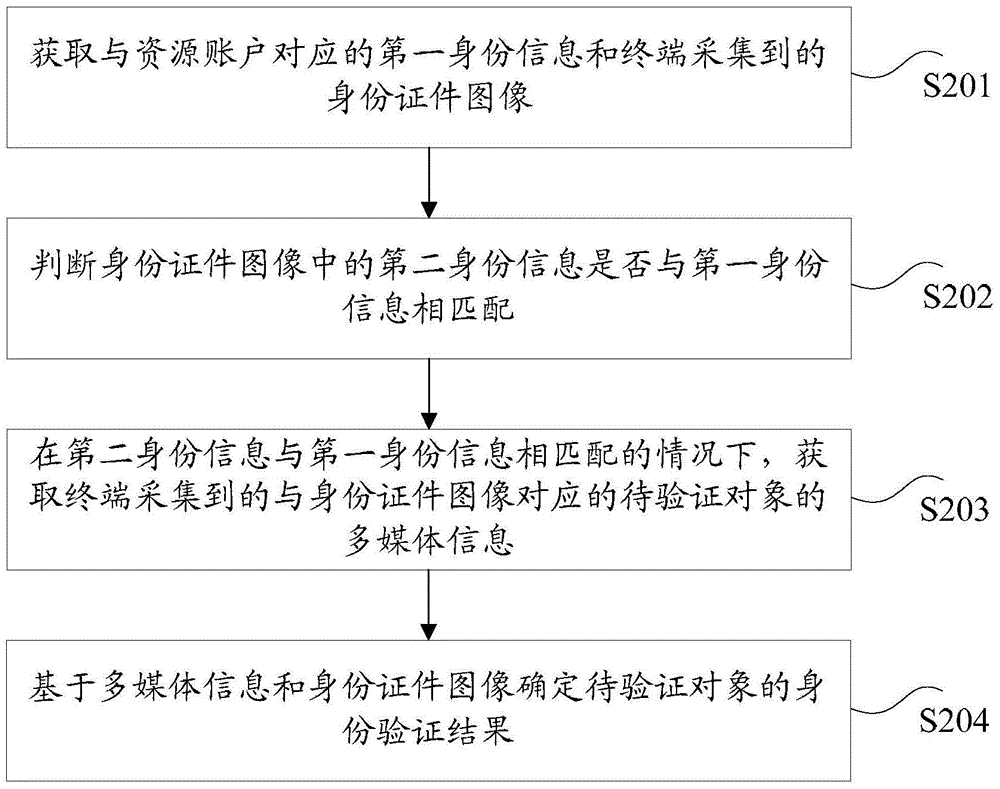
[0184] According to an embodiment of the present invention, an identity verification device for implementing the above identity verification method is also provided, such as Figure 7 As shown, the device includes: a first acquiring unit 30 , a judging unit 40 , a second acquiring unit 50 and a determining unit 60 .
[0185] The first obtaining unit 30 is configured to obtain the first identity information corresponding to the resource account and the image of the identity certificate collected by the terminal.
[0186] The judging unit 40 is used for judging whether the second identity information in the identity certificate image matches the first identity information.
[0187] The second acquiring unit 50 is configured to acquire the multimedia information of the object to be verified corresponding to the image of the ID card collected by the terminal when the second identity information matches the first identity information.
[0188] The determining unit 60 is configured...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com