Behavior-based mobile terminal security protection system and method
A technology of behavior and terminal equipment, applied in the direction of transmission system, computer security device, platform integrity maintenance, etc., can solve the problems of large monitoring granularity, difficult to accurately distinguish, low efficiency and accuracy of killing, and achieve damage prevention and saving cost, efficiency and accuracy improvements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] 下面结合附图和具体实施例对本发明提供的一种基于程序行为的安全防护系统和方法进行详细描述。
[0014] 在以下的描述中,将描述本发明的多个不同的方面,然而,对于本领域内的普通技术人员而言,可以仅仅利用本发明的一些或者全部结构或者流程来实施本发明。为了解释的明确性而言,阐述了特定的数目、配置和顺序,但是很明显,在没有这些特定细节的情况下也可以实施本发明。在其他情况下,为了不混淆本发明,对于一些众所周知的特征将不再进行详细阐述。
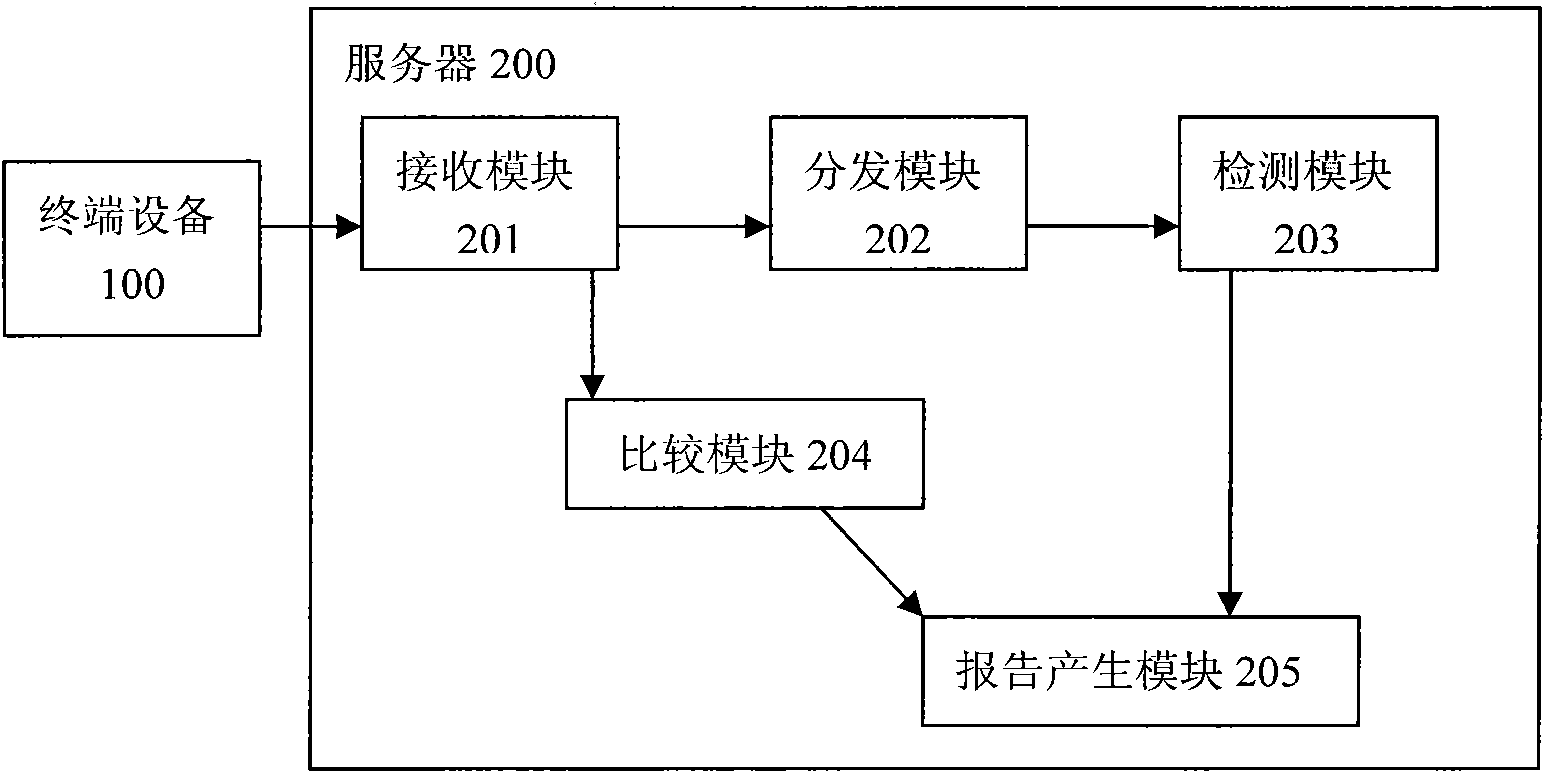
[0015] 总的来说,如 figure 1 所示,本发明提供的一种基于程序行为的移动设备的安全防护系统包括终端设备100和服务器200,服务器包括接收模块201,用来从终端设备100或者终端设备期望下载程序的源程序服务器端接收该程序。
[0016] 终端设备100是指经由通信设施和运营商设备或者应用服务器交互的设备,终端设备100通常设置在利用通信设施与服务器联接工作的方便场所,它主要由通信接口控制装置与专用或选定的输入输出装置组合而成,而移动终端设备却不受地域限制,更加灵活。本发明的终端设备包括但不限于移动通信设备(诸如手持电话、智能电话)、便携式娱乐设备(诸如苹果公司的IPAD、三星公司的GALAXY、索尼公司的PS系列)等等。
[0017] 本申请的终端设备100具有接收端口和发送端口,接收端口用于接收来自应用服务器的软件程序,发送端口用于将所接收的软件程序发送给服务器200。这里的应用服务器包括但不限于:提供软件下载的应用服务器、运营商服务器、与终端设备进行会话的会话服务器、对终端设备提供远程支持的应用服务器以及其他类型的静态和动态服务器。
[0018] 总的来说,如 figure 1 所示,本申请的服务器200包括接收模块201、分发模块202、检测模块203、比较模块204和报告产生模块205。其中,接收模块201用来接收来自终端设备100发送的软件程序或者其他文件;分发模块202用于将所接收的软件程序或者其他文件分发给由处理器组成的“云”中的其中一个的模拟器;检测模块203用于检测在服务器200的沙漏模型中运行的软件程序或者其他文件的行为;比较模块204用于将所检测到的该软件程序或者其他文件的执行过程中的行为和服务器200中的行为库进行比较,获知是否是已有行为,比较模块2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com