Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
643 results about "Behavioral analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
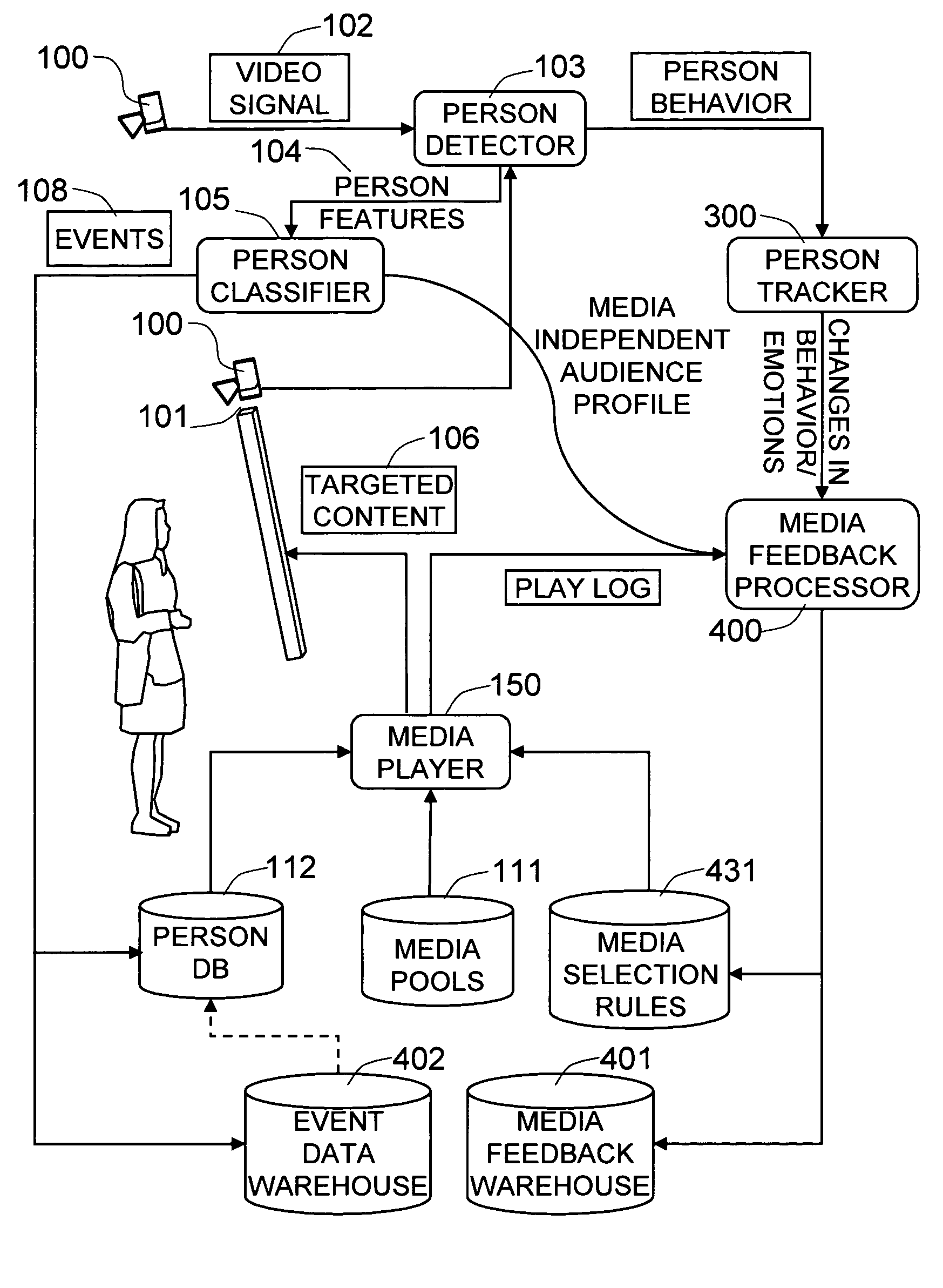
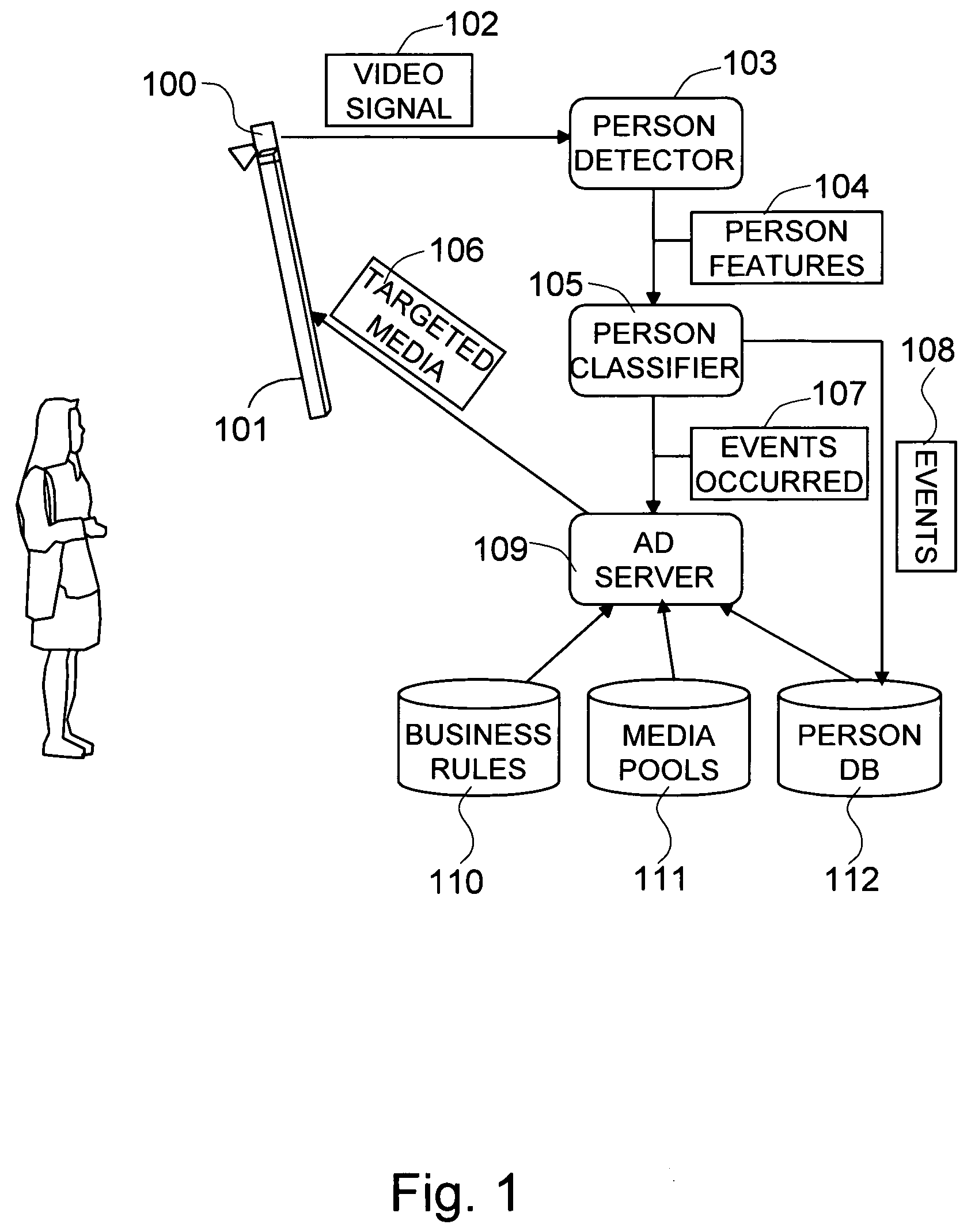
Method and system for dynamically targeting content based on automatic demographics and behavior analysis
InactiveUS7921036B1Computer security arrangementsPayment architectureBehavioral analyticsComputer graphics (images)
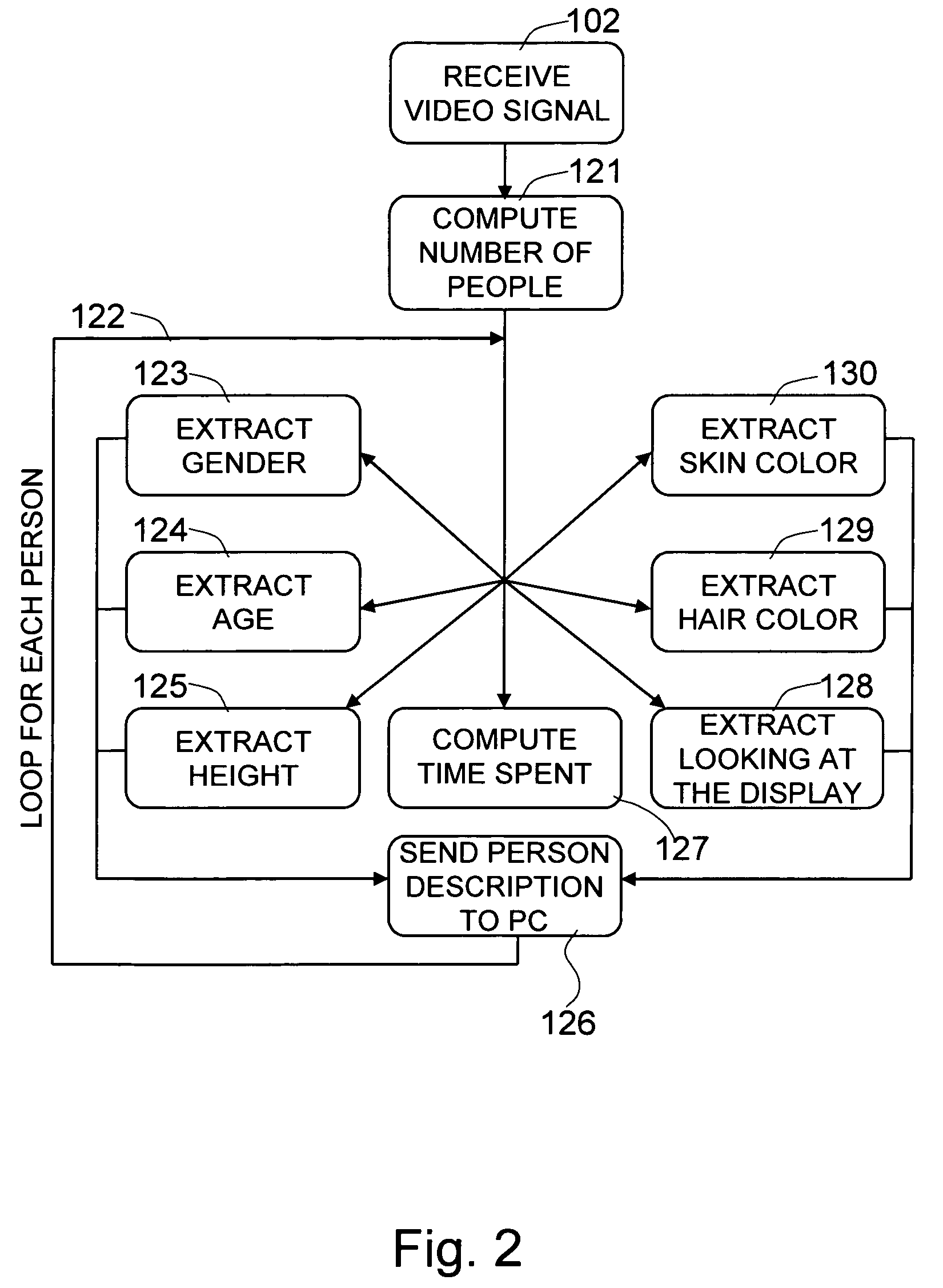
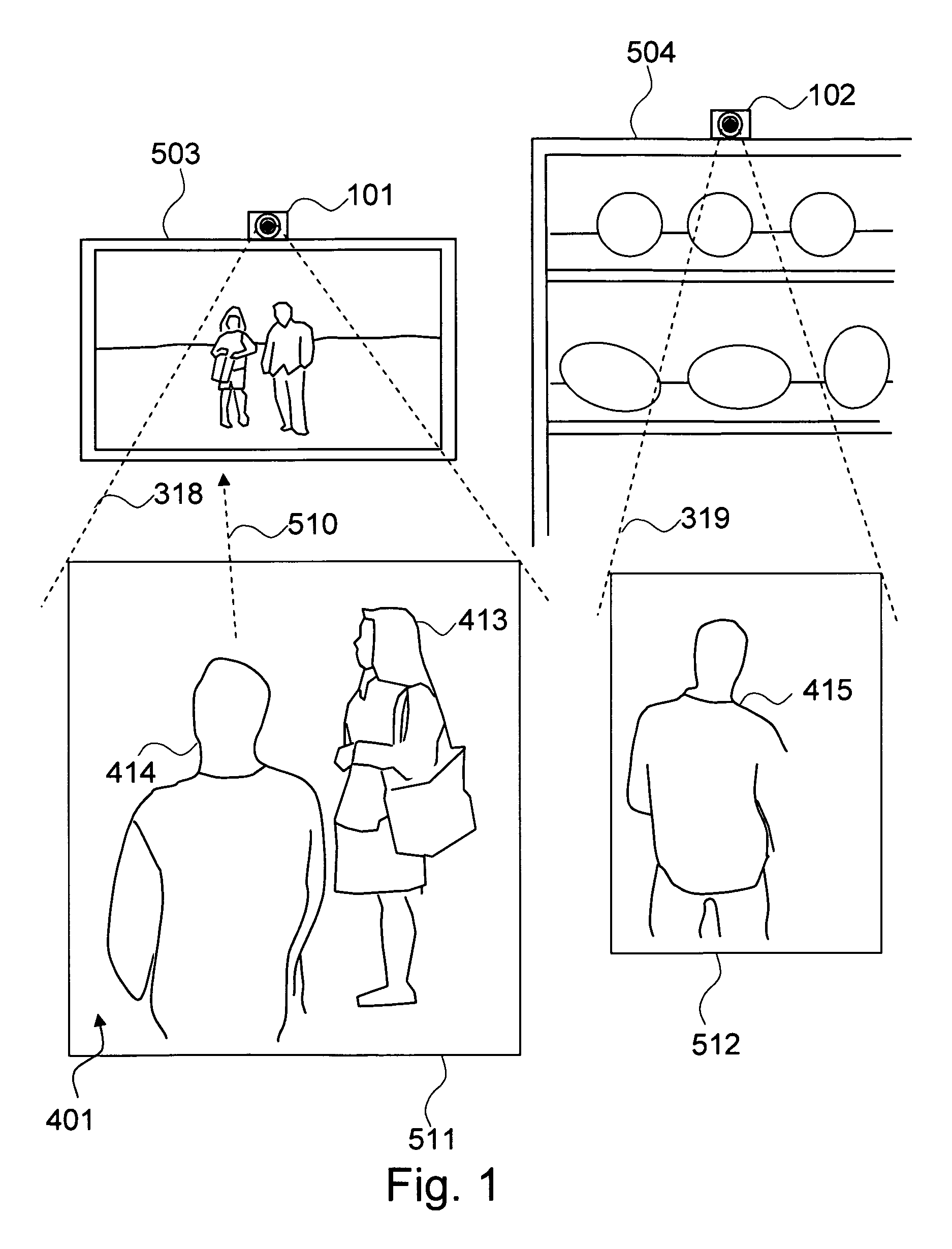
The present invention is a method and system for selectively executing content on a display based on the automatic recognition of predefined characteristics, including visually perceptible attributes, such as the demographic profile of people identified automatically using a sequence of image frames from a video stream. The present invention detects the images of the individual or the people from captured images. The present invention automatically extracts visually perceptible attributes, including demographic information, local behavior analysis, and emotional status, of the individual or the people from the images in real time. The visually perceptible attributes further comprise height, skin color, hair color, the number of people in the scene, time spent by the people, and whether a person looked at the display. A targeted media is selected from a set of media pools, according to the automatically-extracted, visually perceptible attributes and the feedback from the people.
Owner:ACCESSIFY LLC
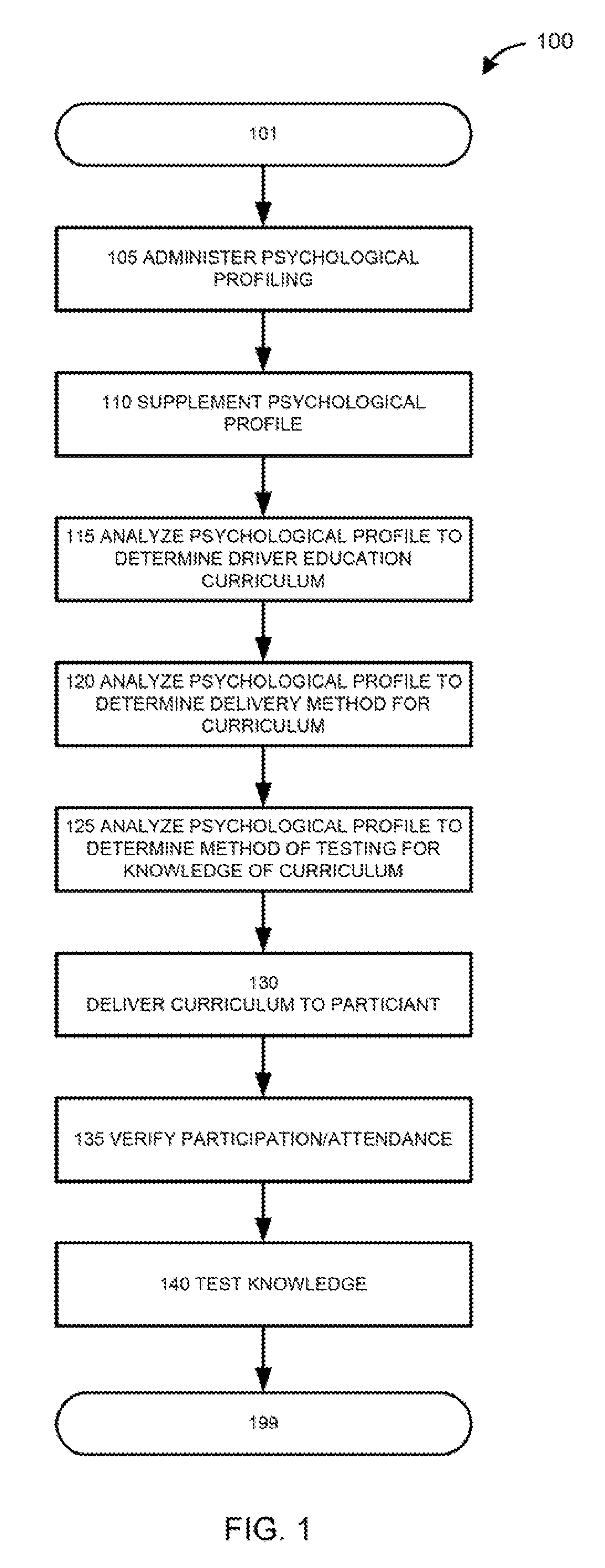
Driver safety program based on behavioral profiling
InactiveUS20100143872A1Cosmonautic condition simulationsSimulatorsBehavioral analyticsDriver/operator
A computer system is configured to administer a psychological profiling test to a participant in a driver education program, or receive such profile from another source; to determine the participant's psychological profile. The system then selects a driver education program for the participant based on the profile. The system also selects a method of delivering the curriculum to the participant based on the profile. The system further selects a method of testing the participant's comprehension and retention of the curriculum material, also based on the profile. The system delivers the selected curriculum to the participant using the selected delivery method, verifies attendance or participation, and tests the participant's comprehension and retention of the curriculum material using the selected testing method.
Owner:GOLD CROSS BENEFITS CORP
In-Car Driver Tracking Device
InactiveUS20130244210A1Accurate and reliable sensor inputAccurate and reliable inputCosmonautic condition simulationsRegistering/indicating working of vehiclesBehavioral analyticsData source
Disclosed are a device and method for providing driver tracking and behavior analysis, initiated without concurrent user input, by the presence detection of one or more drivers of the vehicle. Vehicle motion inferred from a location aware device sensor, as well as other driver smartphone sensors and application use are logged and analyzed to determine risk factors associated with identified drivers. Internet data sources are further utilized for associating road conditions and traffic regulations with the logged locations of the vehicle. Logged and analyzed data from the identified drivers is aggregated for reporting on vehicle risk.
Owner:KAARYA
Method and system for detecting application program behavior legality
InactiveCN101408917AReduce false alarm rateImprove recognition ratePlatform integrity maintainanceBehavioral analyticsMonitoring system
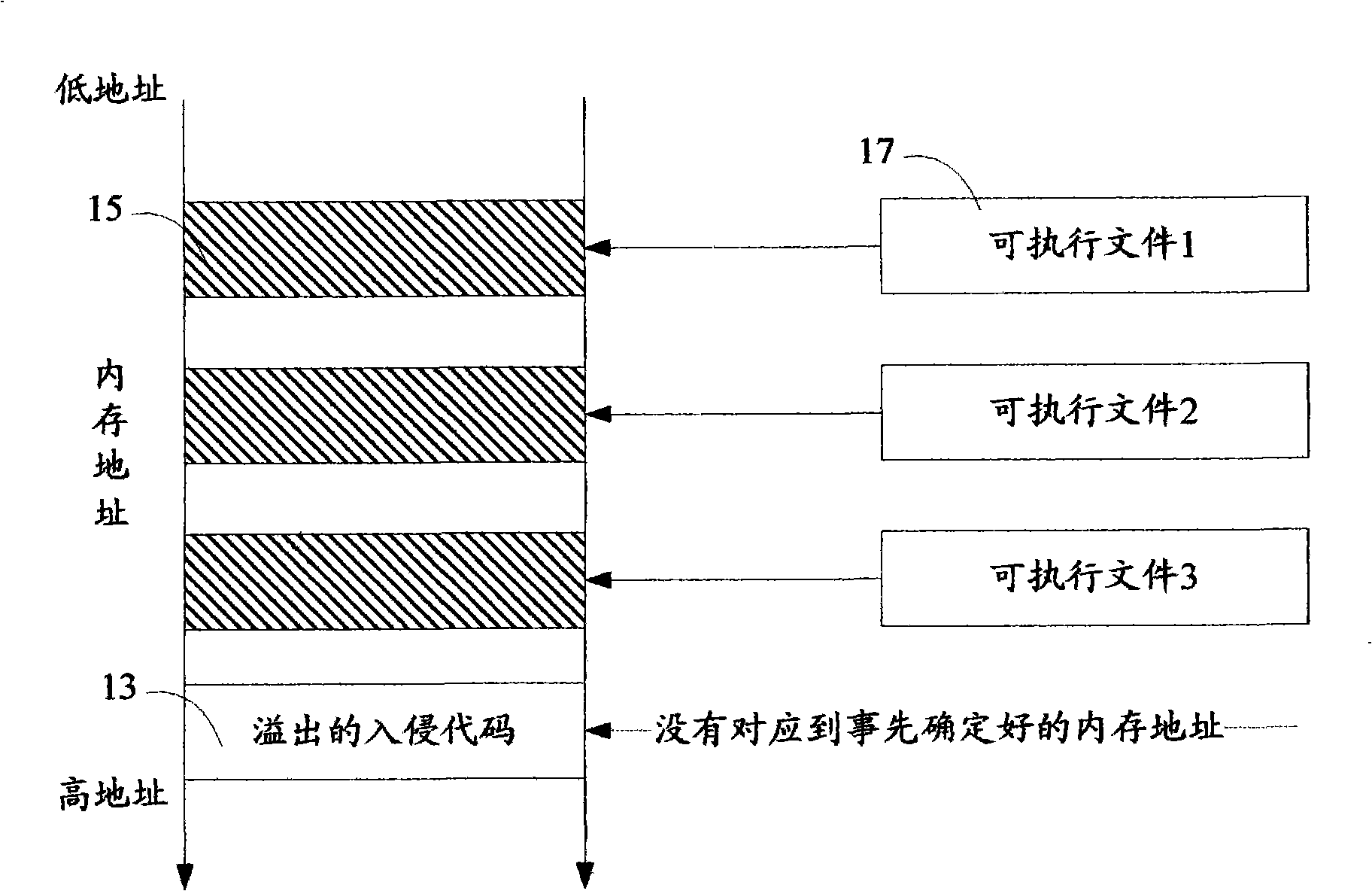
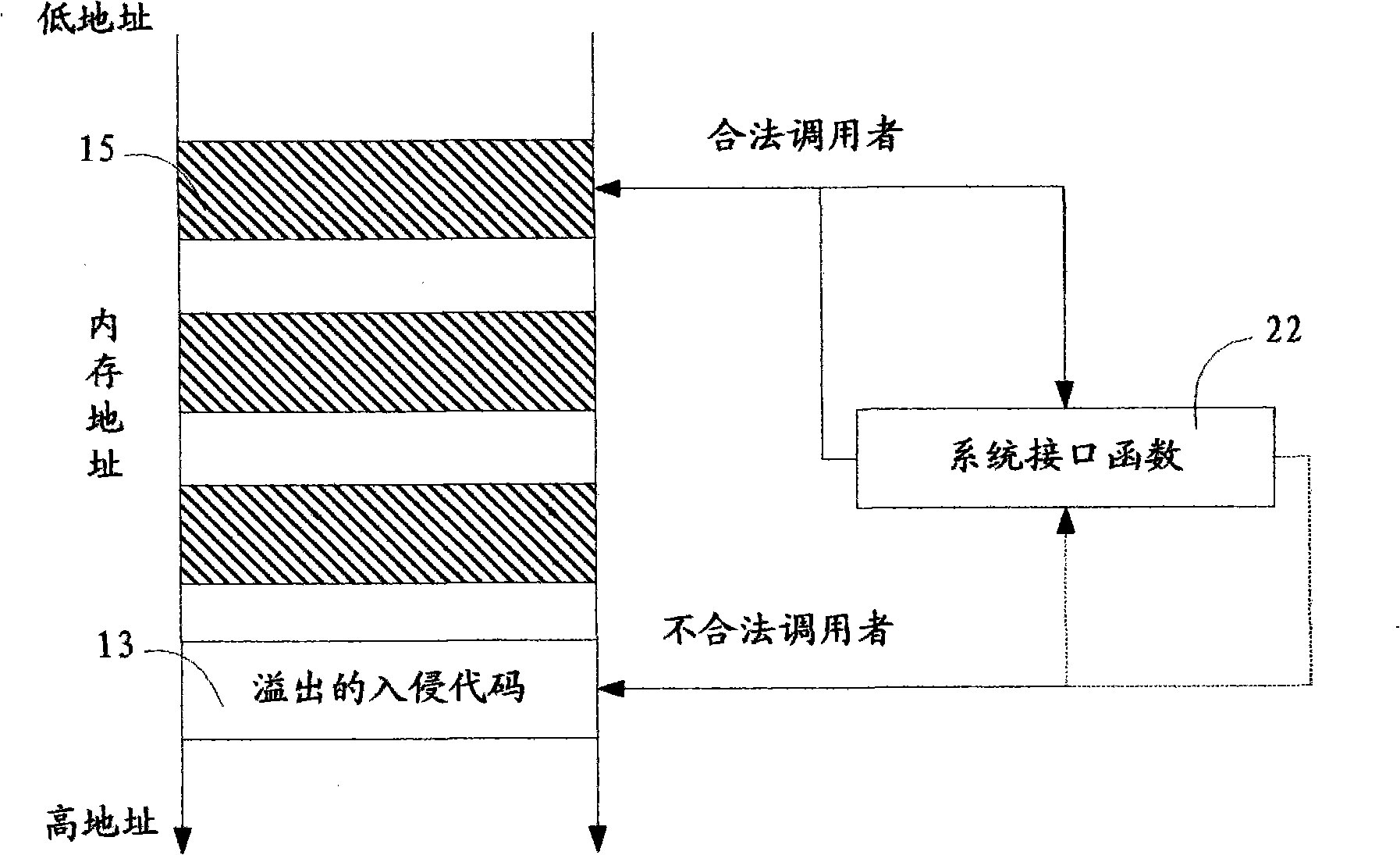
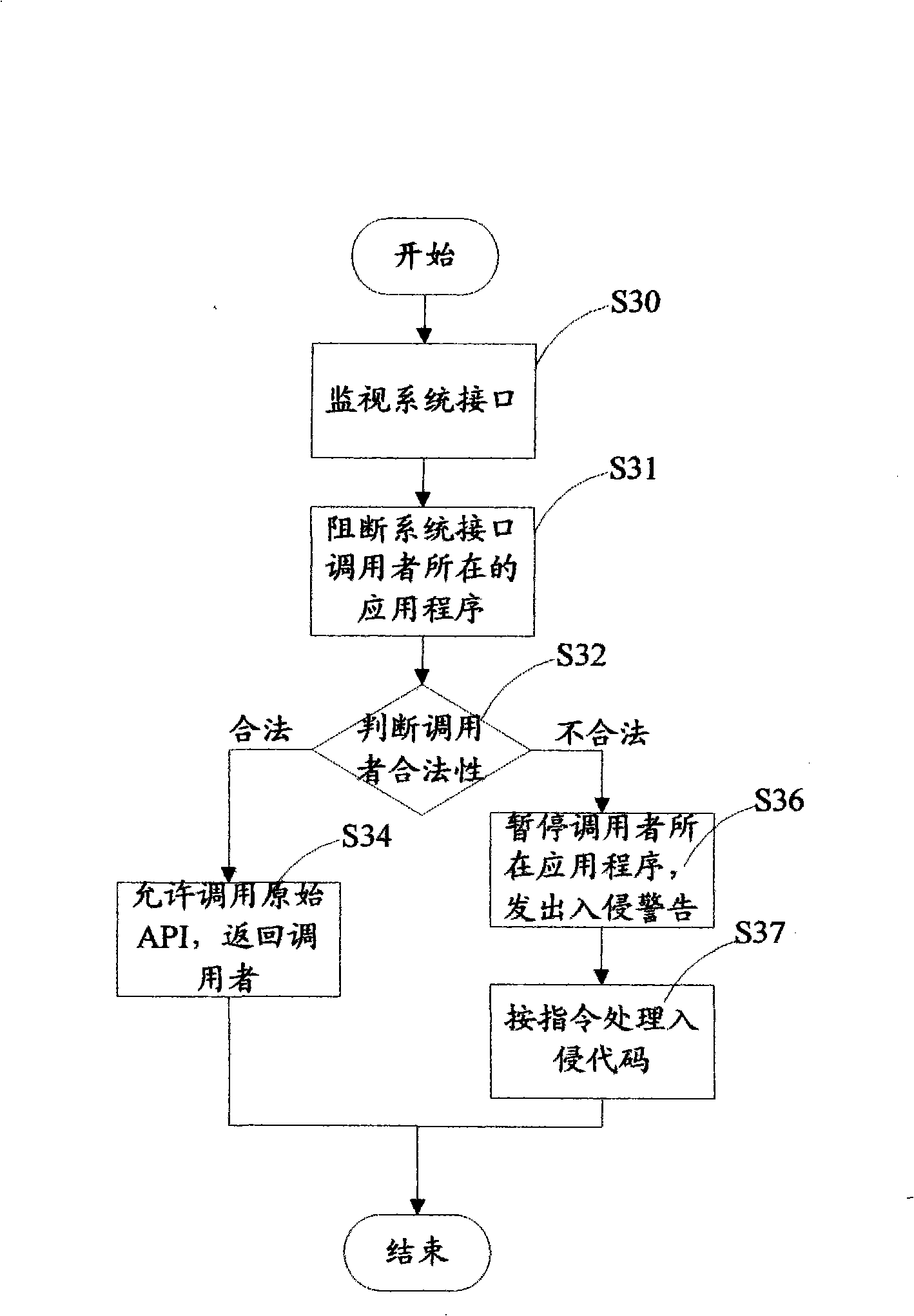
A method for detecting the legitimacy of an application program behavior comprises the following steps: monitoring one or more system interfaces of a computer to cause the monitored system interfaces to jump to a monitoring module for execution when the monitoring system interfaces receive a call; blocking the application program of a caller and judging the validity of the caller: permitting the caller to call an interface function and continuously perform the application program of the caller if the caller is legal; and, pausing the behavior of the application program of the caller and issuing an intrusion alarm if the caller is illegal. The detection method finds out whether an executor of the application program behavior is legal or not by monitoring the system interfaces of the computer so as to intercept the program behavior executed by illegal executors and give an alarm. Compared with the existing fuzzier behavioral analysis technology, the detection method has the advantages of low false alarm rate, high recognition rate and the like, especially has good defense effect against the intrusion behavior due to overflow vulnerability, so the detection method is an effective supplement to the existing behavior analysis defense technology.
Owner:厦门市美亚柏科资讯科技有限公司
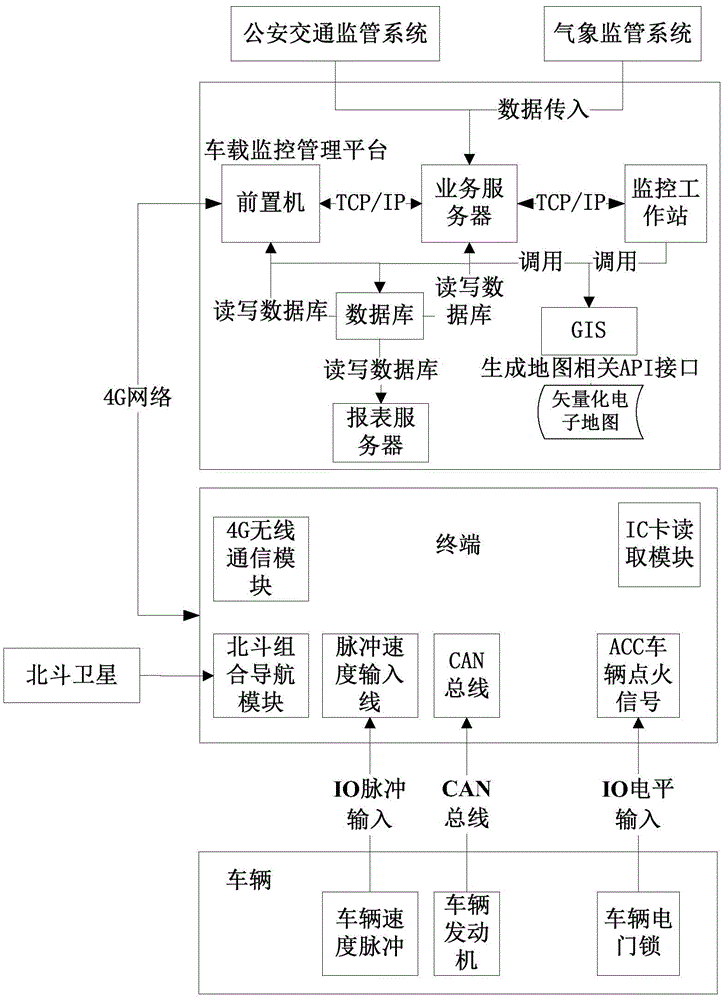
Driving behavior analysis method based on vehicle-mounted monitoring and management platform
InactiveCN105575115AEasy maintenanceImprove rationalityDetection of traffic movementGeneration processWorkstation
The invention provides a driving behavior analysis method based on a vehicle-mounted monitoring and management platform. The method comprises the steps that: a terminal collects vehicle state data; the terminal packages and uploads the vehicle state data; a front-end processor transmits data uploaded by the terminal to a service server; the service server stores the initial vehicle state data into a database; the service server calculates a driving behavior analysis result; after the driving behavior analysis result is obtained, a monitoring work station is informed of the driving behavior analysis result; after driving behavior analysis result is obtained, the terminal is informed of the driving behavior analysis result; and the driving behavior analysis result is stored in the database. According to the invention, in a driving behavior analysis model generation process, many factors such as different road conditions, weathers, different road segments and different drivers are considered, and the rationality of practical application of an original single driving behavior analysis model is improved.
Owner:FUJIAN XINGHAI COMM TECH
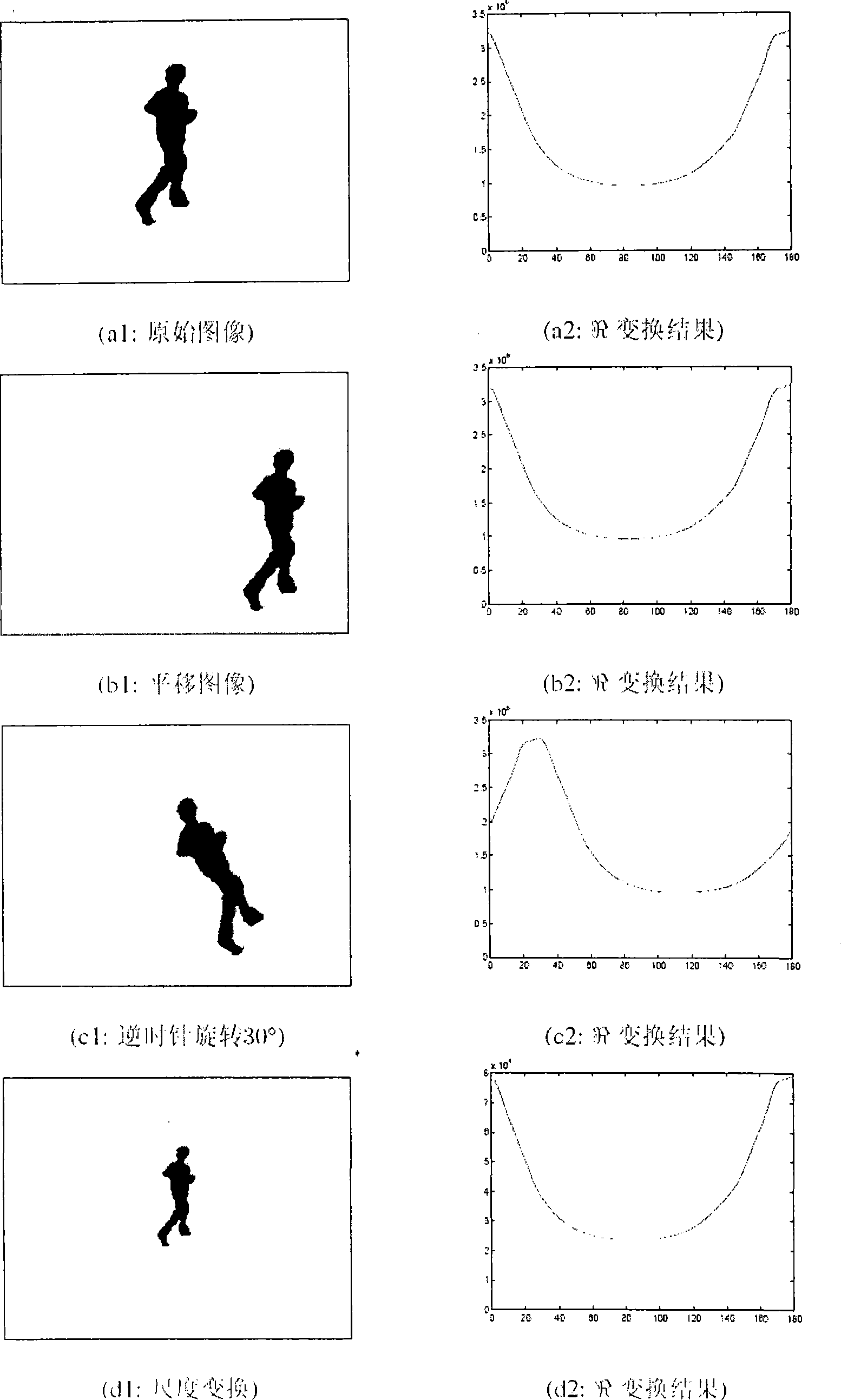
Abnormal behavior identification method based on contour
InactiveCN101464952AReduce intensityCharacter and pattern recognitionCharacteristic sequenceAnomalous behavior
The invention discloses a method for recognizing aberrant behaviors based on contours. The method is characterized in that the detection and the tracking of moving targets are primarily performed for the image sequences collected by a camera so as to extract target contours; then spatial information of the moving targets in each frame is indicated by utilizing R transformation; then the spatial information is rearranged and combined as characteristic vectors of behavior analysis and the characteristic dimension reduction is performed by adopting principal component analysis; finally the transformation relation of the contour sequences with spatial information in the time is indicated by utilizing a hidden Markov model, and all the behaviors can be indicated with respective parameters of the hidden Markov model. In the recognition process, the characteristic sequences of new behaviors are compared with the storage parameters, and the behaviors best matched are selected upon the maximum likelihood principle. Therefore, the method for recognizing aberrant behaviors has an important significance of automatic analysis for intelligent visual monitoring, so that time, places and characters of occurrence events in the scene can be known without assistance of the people; moreover, the method for recognizing aberrant behaviors also can be used for video retrieval so as to assist the people to seek for the interesting events in the video frequency.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
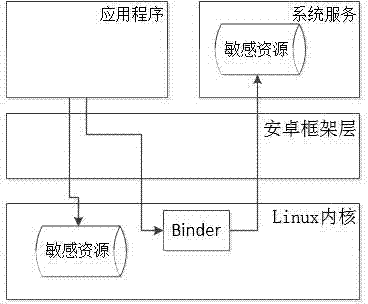
Android platform applications dynamic analysis system based on permission use behaviors
The invention belongs to the technical field of Android platform applications safety analysis and particularly relates to an android platform applications dynamic analysis system based on permission use behaviors. The system comprises a core display permission point-of-use recognizer, a hidden permission point-of-use tracker, an auxiliary application drive and a behavior analyzer. The display permission point-of-use recognizer and the hidden permission point-of-use tracker are based on an android permission implementation system. The display permission point-of-use recognizer completely records display permission points-of-use of an application running. The hidden permission point-of-use tracker tracks hidden permission points-of-use of the application running. The android platform applications dynamic analysis system based on permission use behaviors is capable of fully recognizing all permission points-of-use of one application running and related permission information, thus describing internal permission use behaviors for the application.
Owner:FUDAN UNIV
Automatic detection and aggregation of demographics and behavior of people
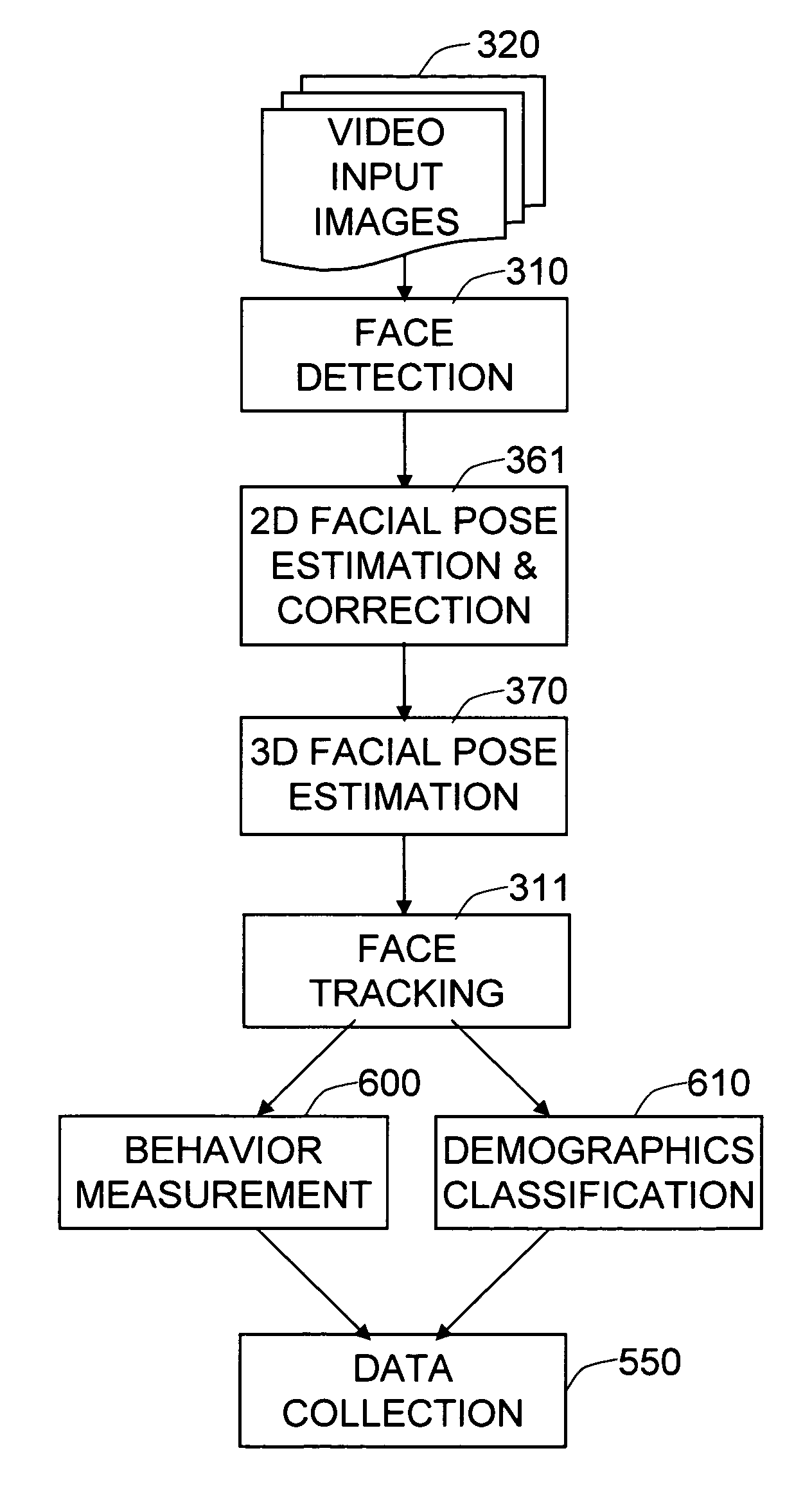
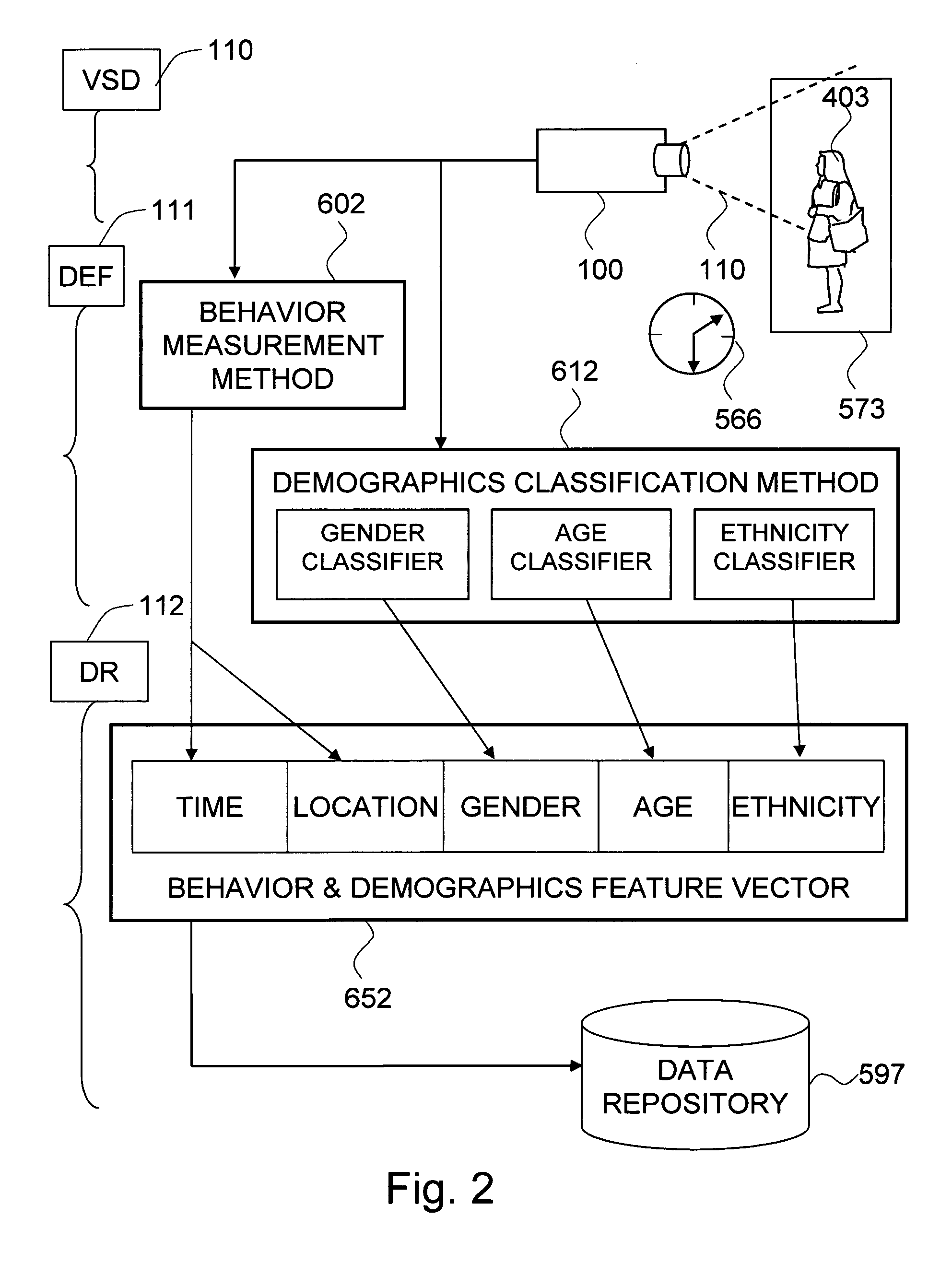
The present invention is a system and framework for automatically measuring and correlating visual characteristics of people and accumulating the data for the purpose of demographic and behavior analysis. The demographic and behavior characteristics of people are extracted from a sequence of images using techniques from computer vision. The demographic and behavior characteristics are combined with a timestamp and a location marker to provide a feature vector of a person at a particular time at a particular location. These feature vectors are then accumulated and aggregated automatically in order to generate a data set that can be statistically analyzed, data mined and / or queried.
Owner:VIDEOMINING CORP
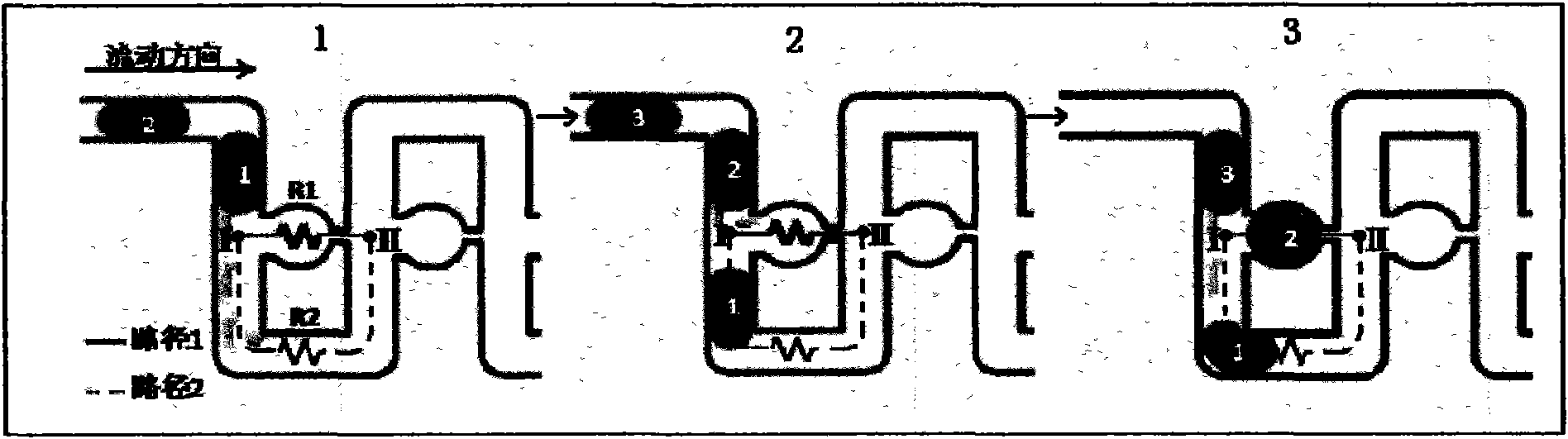
High-throughput nano-litre micro-droplet forming and fixing method based on microfluidic chip and special chip and application thereof
InactiveCN101570776AReduce consumptionEasy to operateBioreactor/fermenter combinationsBiological substance pretreatmentsNematodeEngineering
The invention relates to a high-throughput nano-litre micro-droplet forming and fixing method based on a microfluidic chip and a special chip and an application thereof. The method comprises the following steps: inlets of a continuous phase and a dispersed phase on the chip are respectively connected with two injection pumps through a teflon tube, the continuous phase and the dispersed phase are respectively infused into the chip under the driving action of the injection pumps, and continuous micro-droplets wrapped with single nematodes are formed in a T-shaped micro-droplet generation area; the generated micro-droplets enter in a droplet capture array and are captured in a circular droplet catcher in sequence; and after the micro-droplets are fully captured, the behaviors of the single nematodes in the droplet microenvironment are detected. The invention has the advantages that the microfluidic chip droplet technology is combined with the behavioral analysis to the single nematodes, a great amount of micro-droplets wrapped with the single nematodes are generated and fixed within the short time by using the characteristics of flexible combination and large-scale integration of various functional units on the chip, and the behavioral analysis to the high-throughput single nematodes on the microfluidic chip is realized for the first time.
Owner:DALIAN INST OF CHEM PHYSICS CHINESE ACAD OF SCI
Method for monitoring and eliminating generalized unknown virus
InactiveCN101226570AReduce false alarm rateKeep it broadPlatform integrity maintainanceComputer virusReporting rate
The invention relates to a method to monitor and eliminate general unknown viruses, which comprises: inducing virus basic behaviors composted of a plurality of behavior factors through analysis and research on large amount of computer virus, determining specificity of each behavior factor and each basic virus behavior and forming a specificity-adjusting virus behaviors database which is used to judge whether a program belongs to a virus; simultaneously forming an adjustable normal program false-virus behaviors database according to false-virus behaviors generated on normal programs, wherein the database is used to judge whether a program belongs to a normal program; sorting and processing the viruses which are detected by the above method. The invention can improve the specificity of unknown virus and reduce the error report rate of behavior analysis, ensures the adjusting properties of virus behaviors specificity, increases quantity and range of unknown viruses detecting, and has distinctive advantages compared with prior computer virus monitor technique.
Owner:江启煜
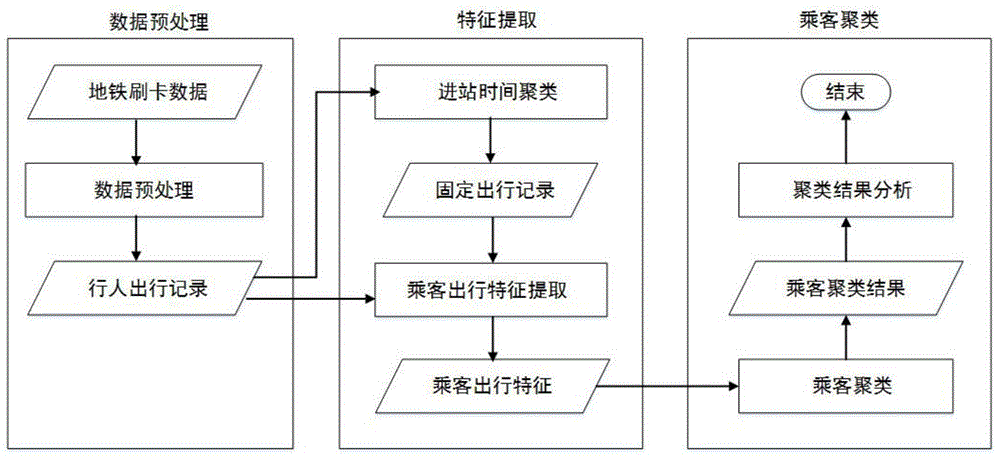
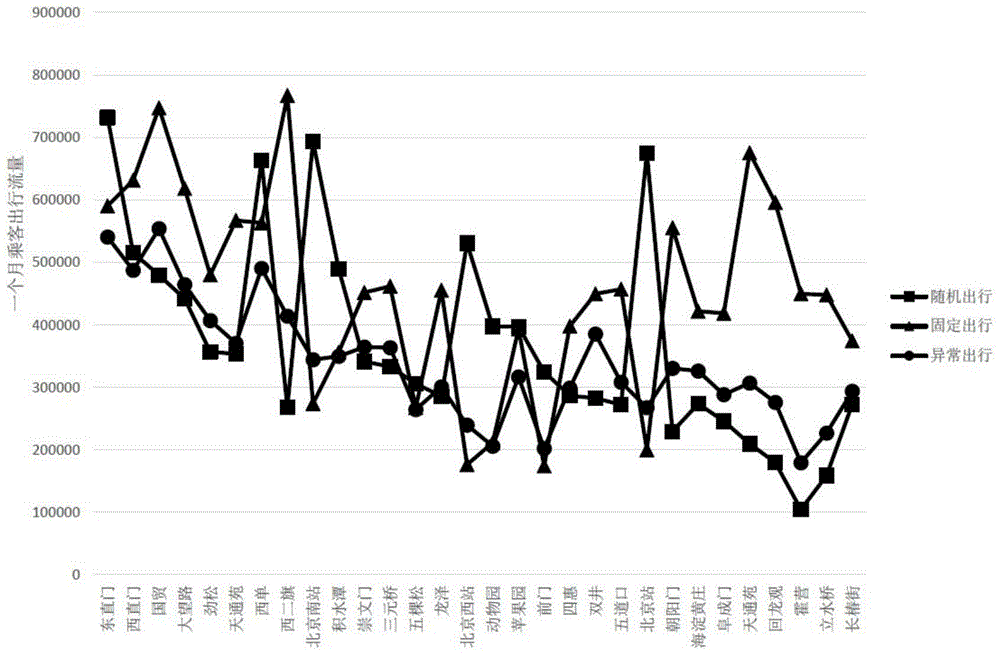
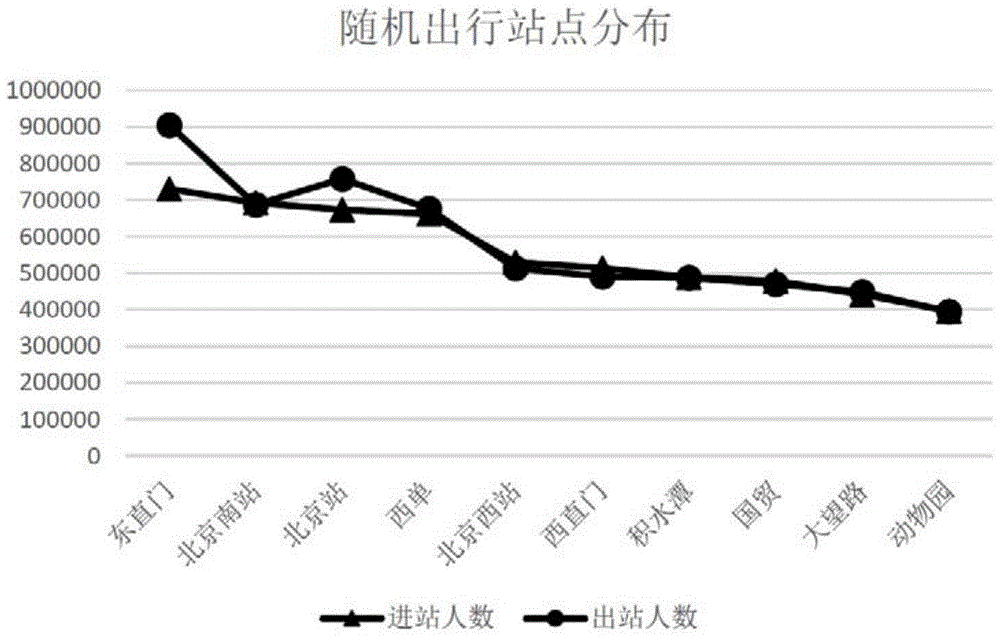
Passenger going-out behavior analysis method based on subway card-swiping data
InactiveCN105718946AEffective classificationImprove classification resultsData processing applicationsCharacter and pattern recognitionOriginal dataData pre-processing
The invention discloses a passenger going-out behavior analysis method based on subway card-swiping data. The passenger going-out behavior analysis method is characterized in that the subway going-out behaviors can be classified, and the classification results have the obvious and easy-to-observe characteristics, and can be widely used for the intelligent traffic passenger going-out behavior analysis. The passenger going-out behavior analysis method is characterized in that S1, data pre-processing can be carried out; original data can be merged and organized, and passenger going-out records can be acquired; every passenger going-out record comprises a passenger going-out entrance station, an entrance card-swiping time, an exit station, and an exit card-swiping time; S2, characteristics can be extracted; according to the passenger going-out records, the passenger entrance temporal clustering can be carried out to acquire the fixed going-out days of every passenger, and then the passenger going-out characteristics can be acquired after the extraction of the passenger going-out characteristics; S3, passengers can be clustered; the passenger clustering can be carried out according to the passenger going-out characteristics, and the passenger clustering result can be acquired and analyzed.
Owner:BEIJING UNIV OF TECH
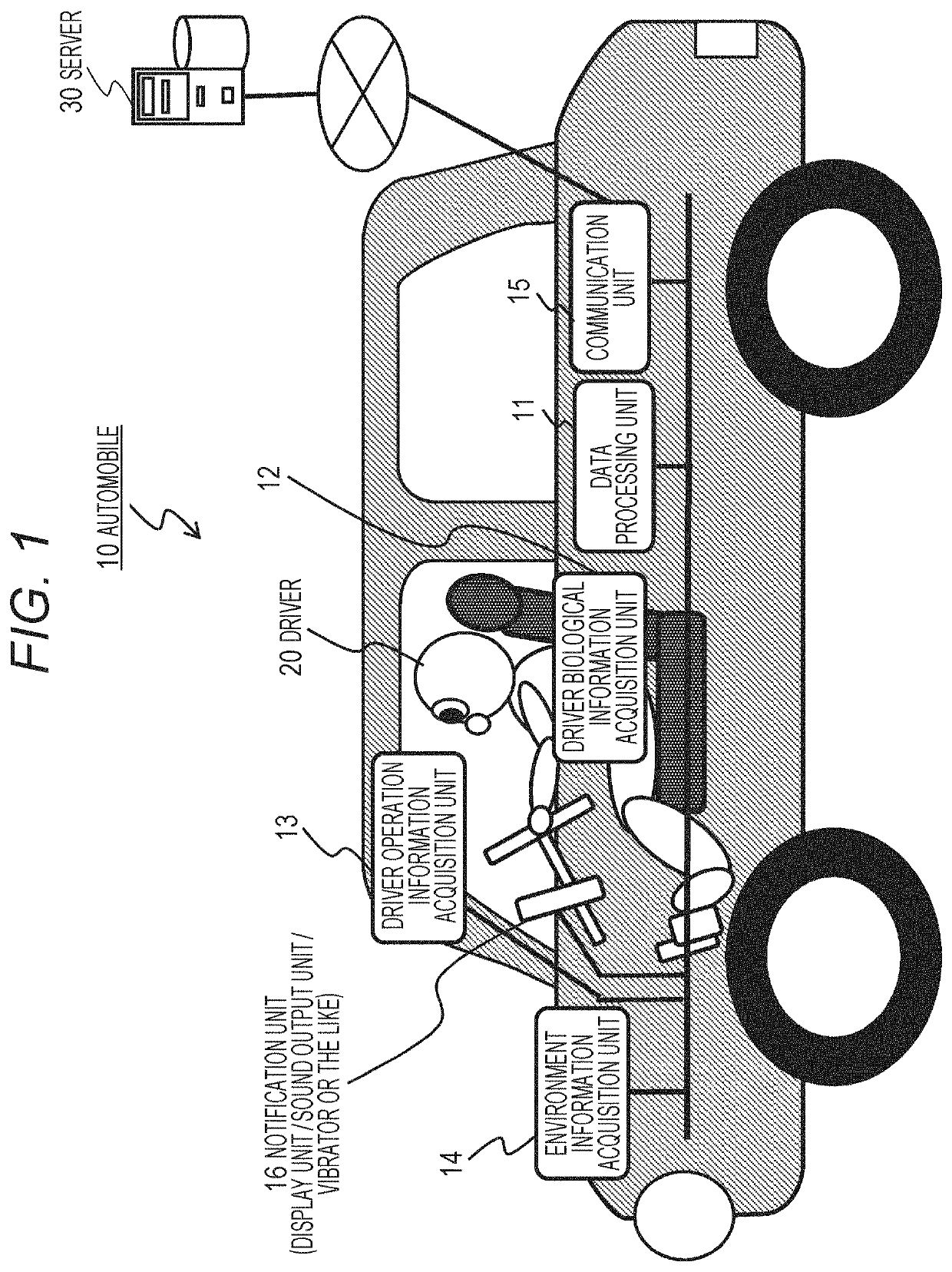
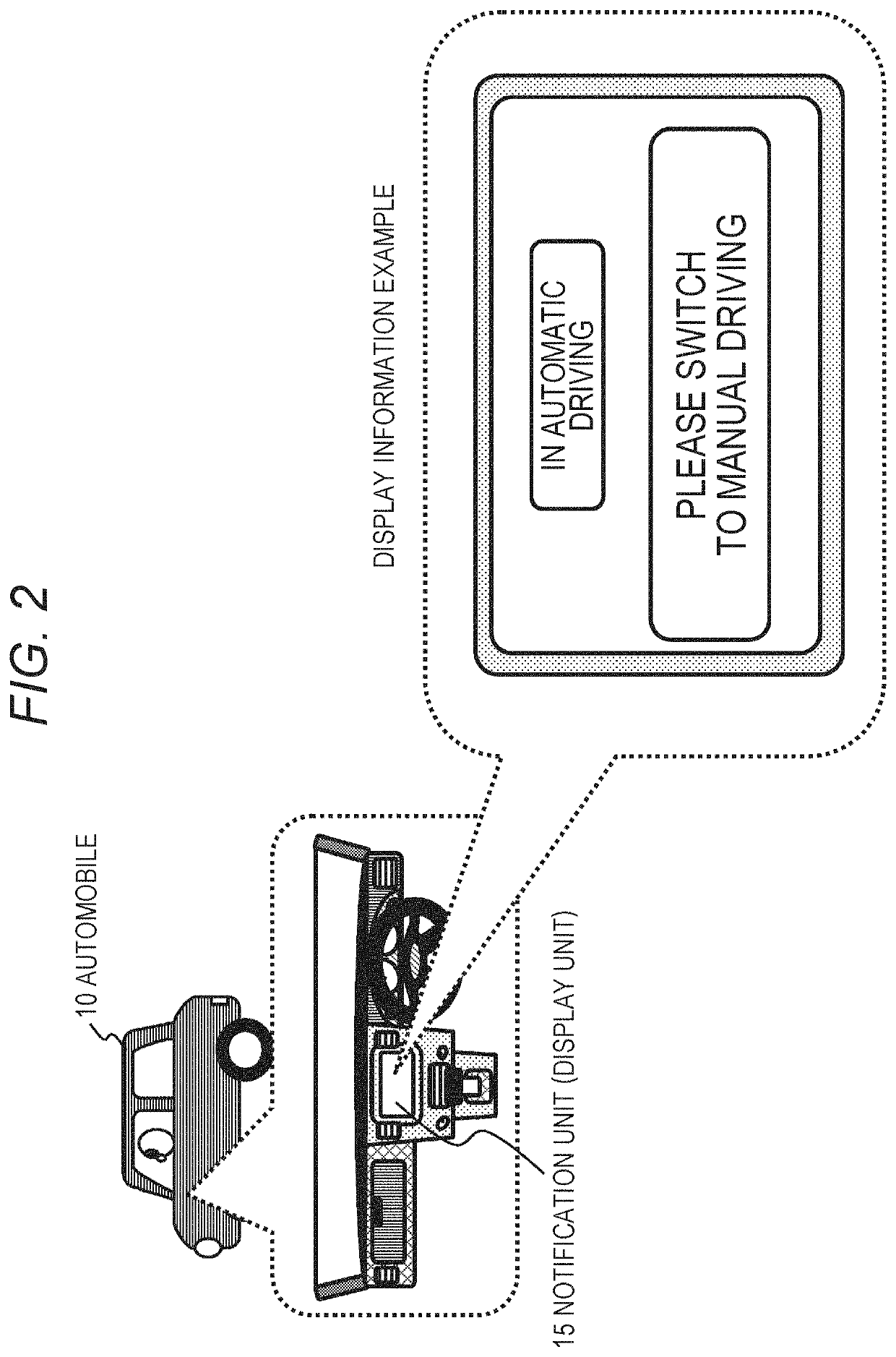
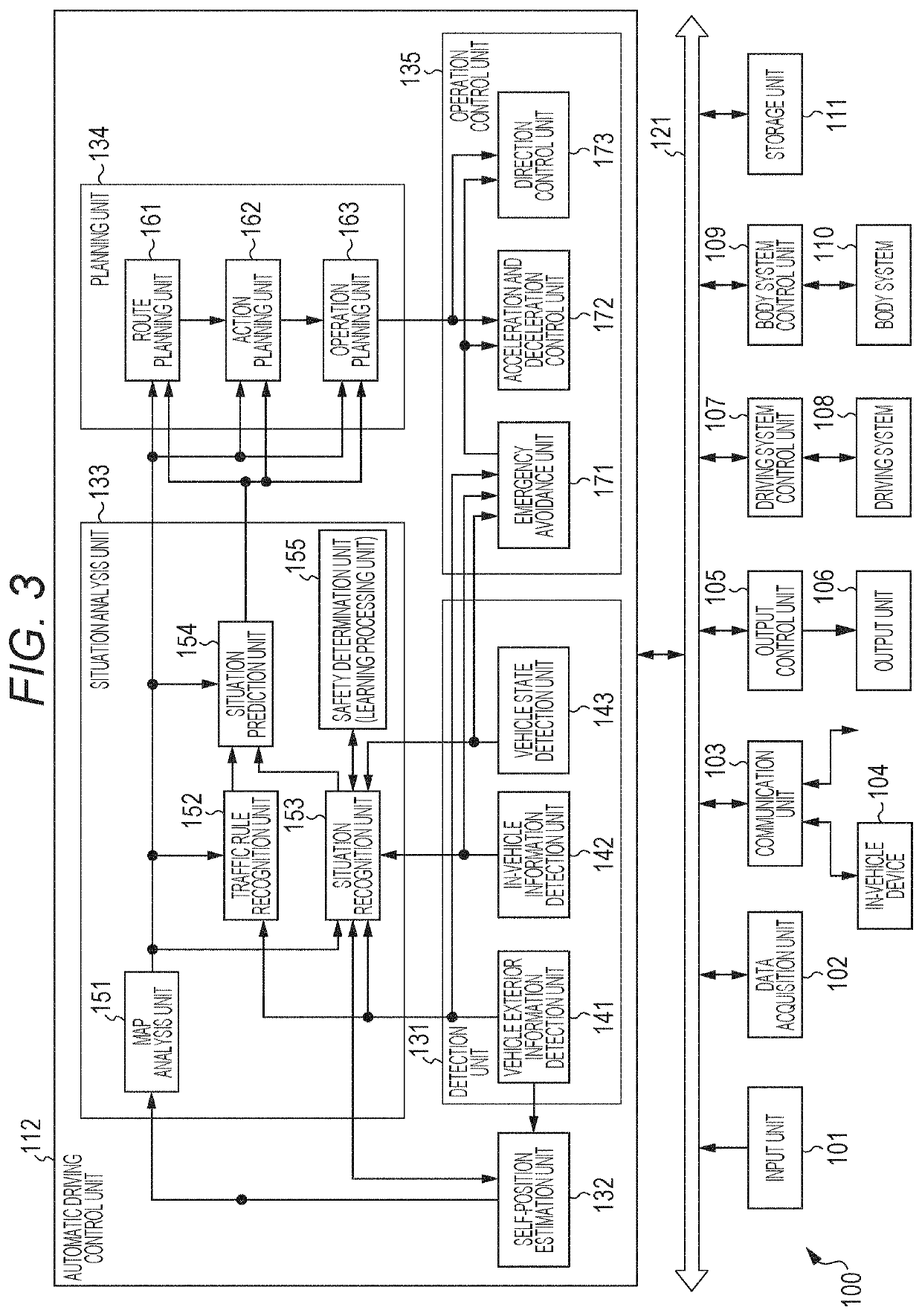
Information processing apparatus, moving device, method, and program
PendingUS20210016805A1Good effectImage analysisGeometric image transformationInformation processingDriver/operator
A configuration is realized in which driver's biological information is input and a driver's wakefulness degree is evaluated. The wakefulness degree of the driver is evaluated by applying a result of behavior analysis of at least one of an eyeball or a pupil of the driver and a wakefulness state evaluation dictionary specific for the driver. The data processing unit evaluates the wakefulness degree of the driver by using the wakefulness state evaluation dictionary specific for the driver generated as a result of learning processing based on log data of the driver's biological information. Moreover, a return time before the driver is able to start safety manual driving is estimated. A learning device used for estimation processing based on observable information is able to correlate an observable eyeball behavior of the driver and the wakefulness degree by a multidimensional factor by continuously using the learning device. By using secondary information, an index of an activity in a brain of the driver is able to be derived from a long-term fluctuation of the observable value.
Owner:SONY SEMICON SOLUTIONS CORP
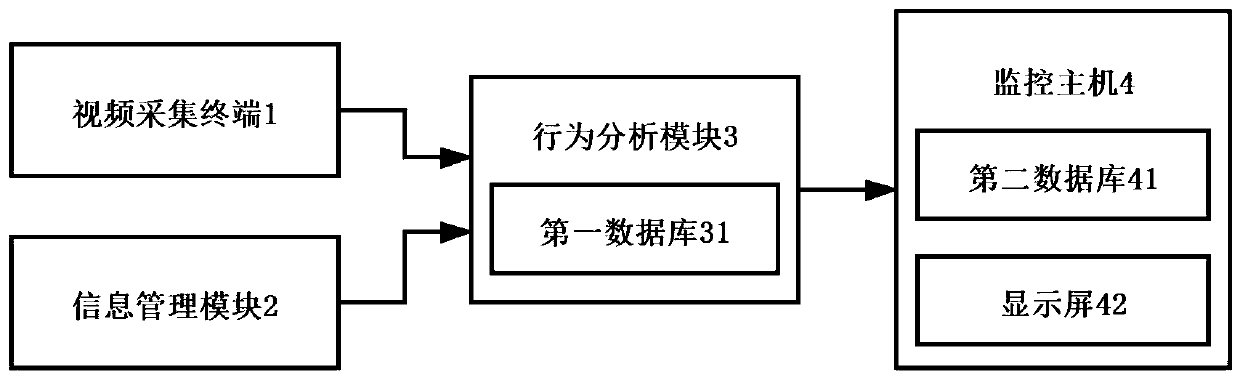
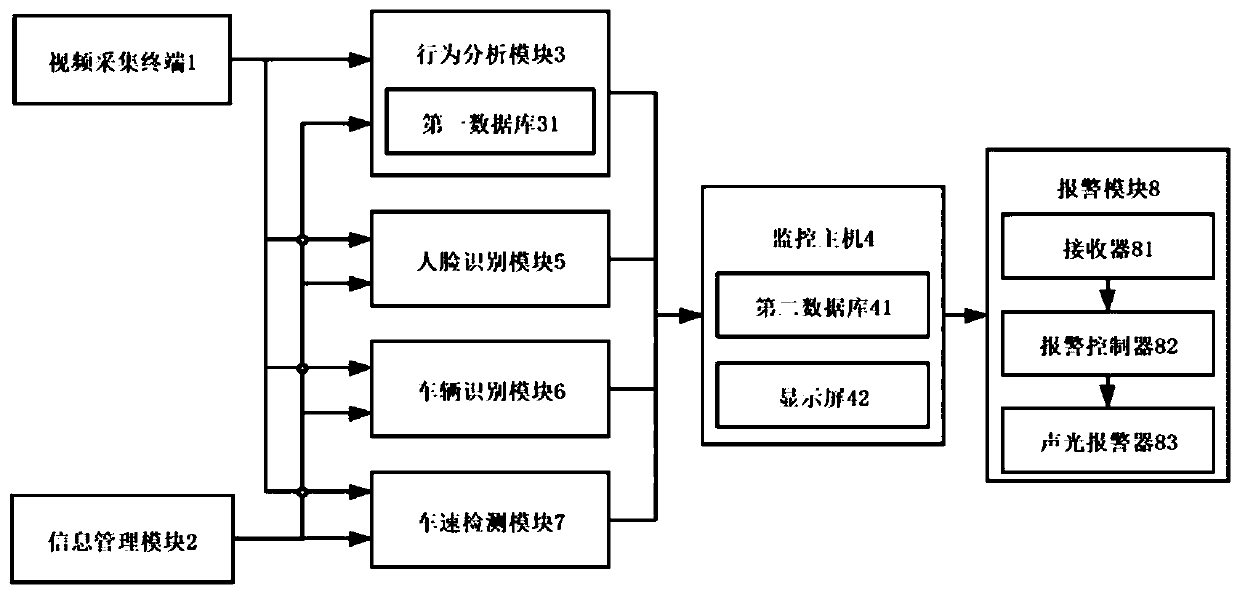
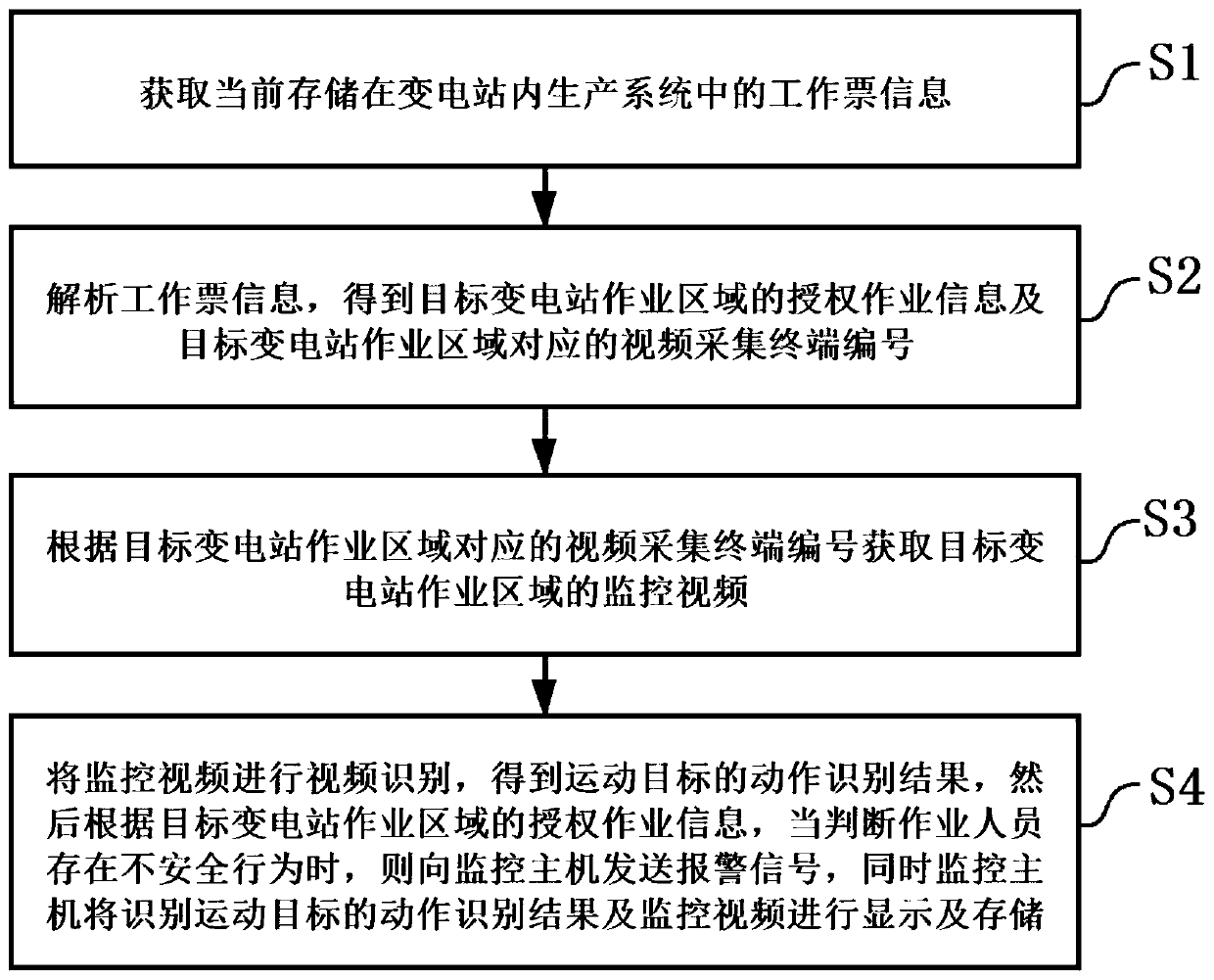
Transformer substation safety monitoring system and method based on video recognition technology
ActiveCN111507308AImprove work efficiencyRealize intelligent security monitoringRoad vehicles traffic controlClosed circuit television systemsTransformerSecurity monitoring
The invention provides a transformer substation safety monitoring system based on a video recognition technology. The transformer substation safety monitoring system comprises a video acquisition terminal, an information management module, a behavior analysis module and a monitoring host, wherein the information management module acquires and analyzes work ticket information in real time, and sends an analysis result to the behavior analysis module; the behavior analysis module acquires a monitoring video of a target substation operation region, intelligently identifies the monitoring video, judges whether an operator has an unsafe behavior or not, and sends the obtained monitoring video, the work ticket information analysis information and a moving target action identification result to the monitoring host to be displayed and stored, so that intelligent safety monitoring of the operator in the substation operation region is realized, and the substation on-site supervision working efficiency can be effectively improved. The invention further provides a transformer substation safety monitoring method based on the video recognition technology and applying the transformer substation safety monitoring system.
Owner:GUANGDONG POWER GRID CO LTD +1
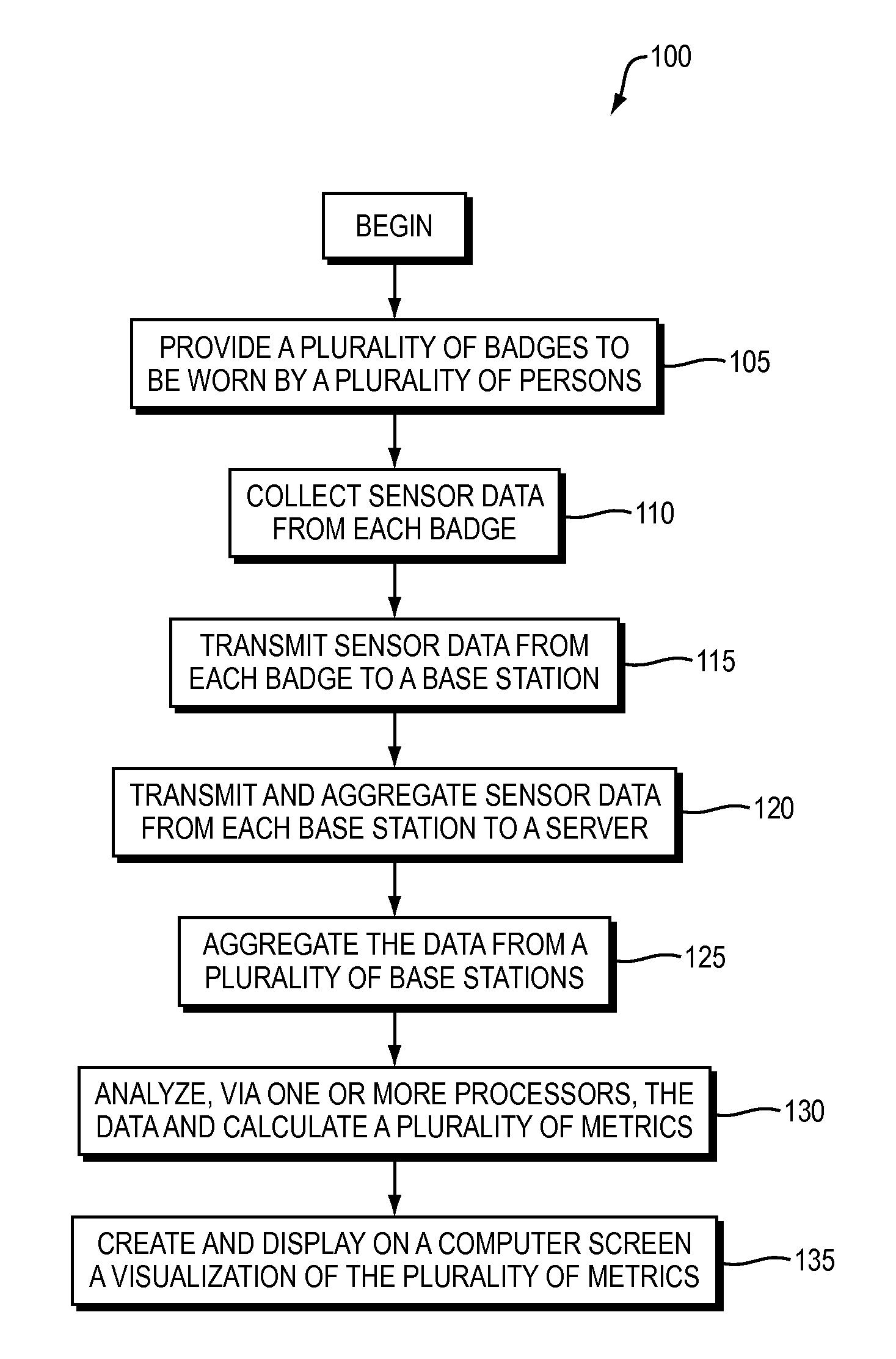
Social Sensing And Behavior Analysis System
ActiveUS20140249891A1Overcomes shortcomingEasy to analyzeResourcesHuman behaviorBehavioral analytics
A method and system for capturing and analyzing human behavior data is disclosed. The present disclosure describes a method and system for a plurality of people, wherein each person wears a badge. The badge transmits data collected from a plurality of sensors from the badge to a base station. The data is sent from the base station to a server, which aggregates the data from a plurality of base stations, and then analyzes and processes the data to create raw human behavior data. From the raw human behavior data and plurality of metrics is calculated, which can be displayed on a computer screen according to whichever metrics a user wishes to view.
Owner:SOCIOMETRIC SOLUTIONS
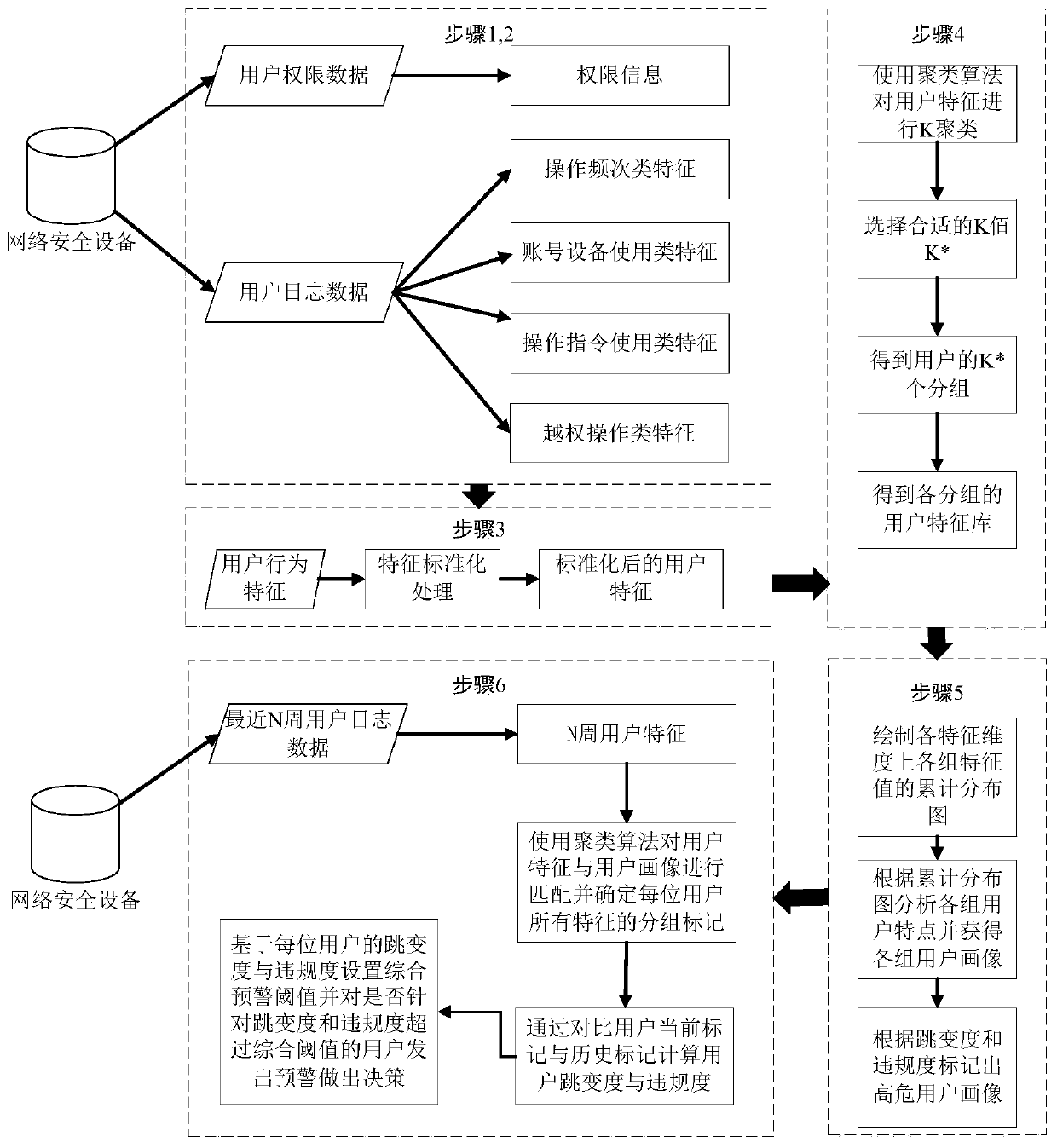
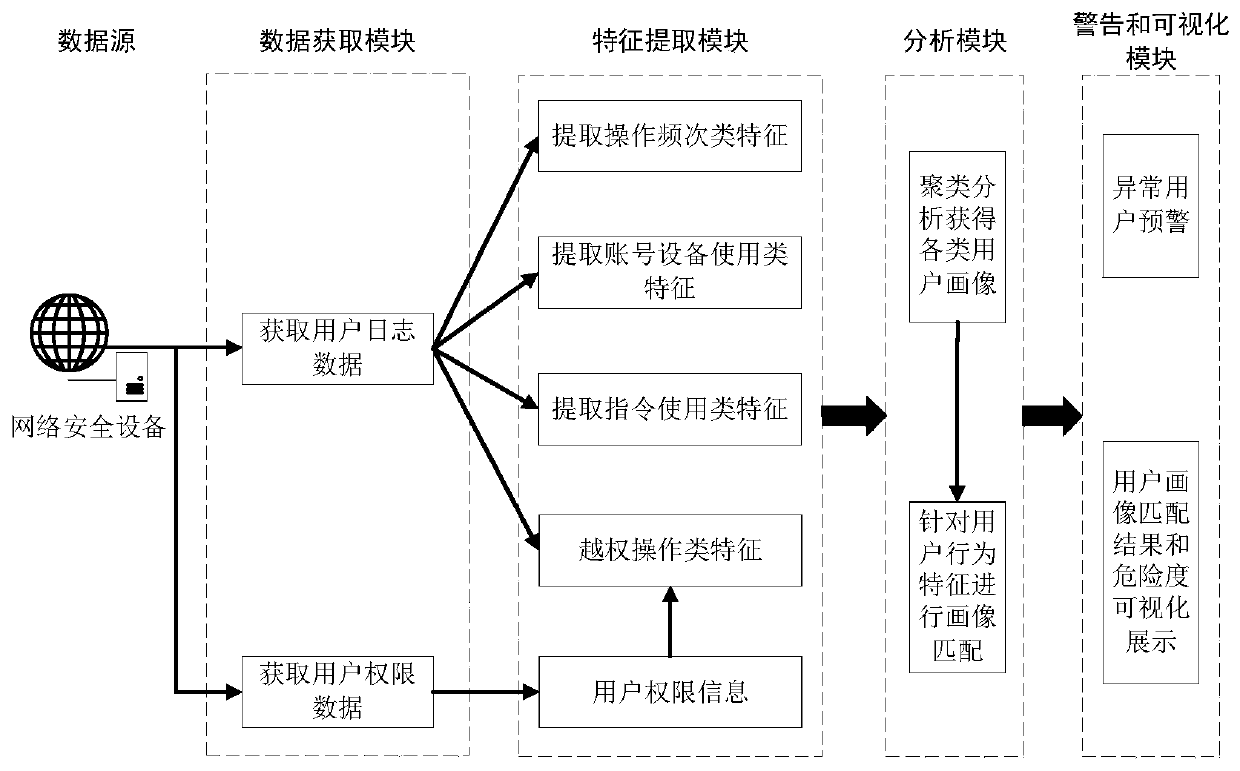
User portrait grouping and behavior analysis method and system based on log data of network security equipment
PendingCN110781930AReduce manpowerReduce time complexityCharacter and pattern recognitionTransmissionComputation complexityEngineering
The invention discloses a user portrait grouping and behavior analysis method and system based on log data of network security equipment. The method mainly comprises the following steps: 1) extractingfeatures from data such as user logs of the network security equipment; 2) carrying out preprocessing and data analysis on the features to obtain relationships between the features and relationshipsbetween the features and user behaviors; 3) constructing a clustering model of the user groups according to the user characteristics; 4) establishing a user portrait according to the clustering model,and determining whether the user has abnormal behaviors or not according to a matching result of the user characteristics and the user portrait; the method is simple to implement and low in calculation complexity; the computing resource overhead of behavior analysis in the user log can be effectively reduced. Compared with the prior art, the invention does not need any additional mark, only needsthe data automatically recorded by the network security equipment, has the advantages of practical application, provides a user grouping method and a portrait matching method with different behaviormodes, and carries out decision-making judgment on whether the user behavior is abnormal or not.
Owner:XI AN JIAOTONG UNIV
User identification system and method based on heterogeneous information network embedding algorithms
ActiveCN111163057AComprehensive Behavioral ModelingImprove recognition accuracyData switching networksNeural learning methodsAlgorithmInformation networks
The invention relates to a user identification system and method based on heterogeneous information network embedding algorithms. The user identification system comprises a data processing module, a joint embedding module and an evaluation analysis module. According to the invention, multi-source heterogeneous user behavior data is utilized for constructing a normal behavior model based on the thought of behavior analysis, and user identification is executed by comparing the similarity between a current behavior and the normal behavior model when behavior data of a new time period arrives. Forthe condition of identification errors, suspicious behavior sorting is given based on dot product similarity operation. The system and method can be applied to an enterprise intranet to detect potential internal threats, a more comprehensive and accurate behavior model can be obtained by combining two heterogeneous information network embedding algorithms, and the user identification accuracy isimproved by about 10%. In addition, event-level traceability clues can be provided for further analysis of the safety monitoring personnel.
Owner:INST OF INFORMATION ENG CAS
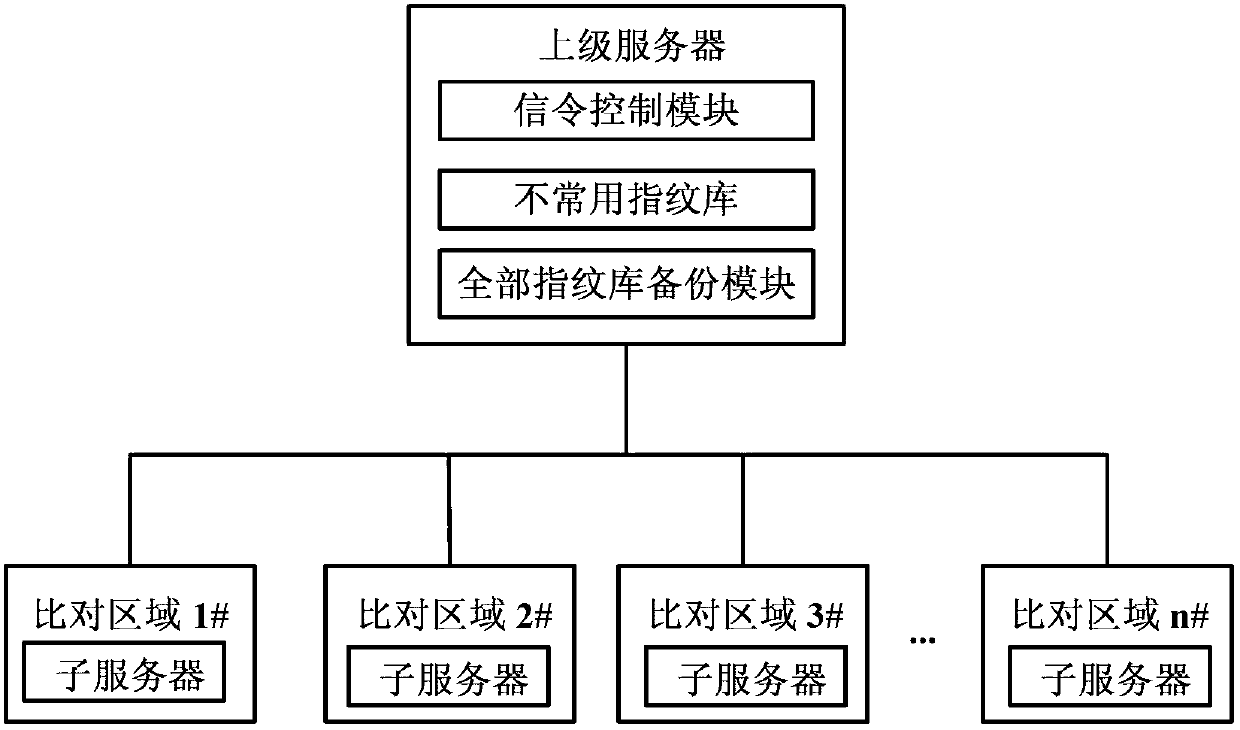
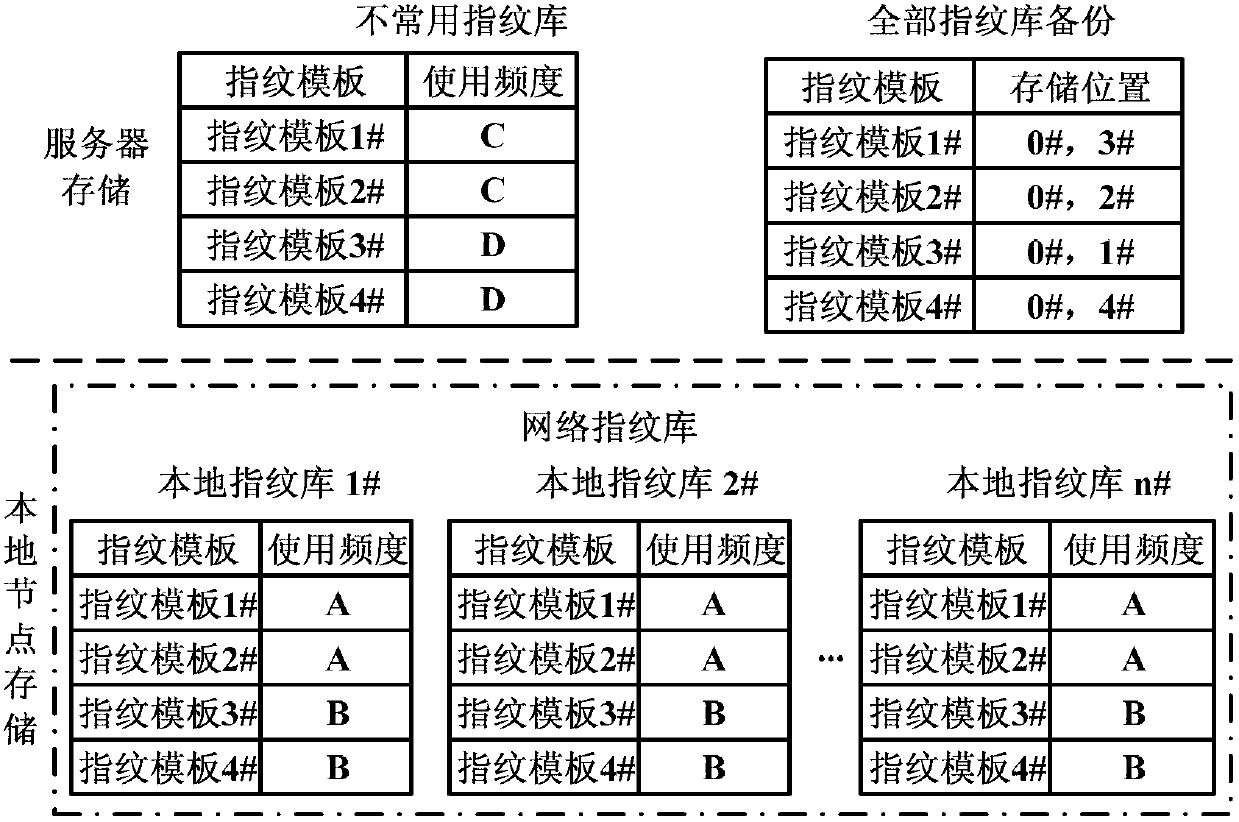
Fingerprint storage comparison system based on behavioral analysis
ActiveCN103345616AImprove hit rateImprove contrast efficiencyCharacter and pattern recognitionRedundant operation error correctionComputer moduleDistributed computing
The invention discloses a fingerprint storage comparison system based on behavioral analysis, and relates to the field of fingerprint comparison. The system comprises an upper level server and a plurality of sub servers in comparison regions. The upper level server comprises a signaling control module, a fingerprint database which is not commonly used and an all fingerprint database backup module. The signaling control module is used for forwarding and responding to all signaling and controlling transmission of instructions, the fingerprint database which is not commonly used is used for storing storage and comparison of fingerprint modules which are not commonly used in a management region, the all fingerprint database backup module is used for backing up all fingerprint modules in the region, each comparison region comprises a sub server and a plurality of local nodes, and each sub server also comprises a signaling control module, a fingerprint database which is not commonly used and an all fingerprint database backup module. The fingerprint storage comparison system can effectively reduce the comparison range, shortens comparison time and improves comparison efficiency.
Owner:武汉世纪金桥安全技术有限公司
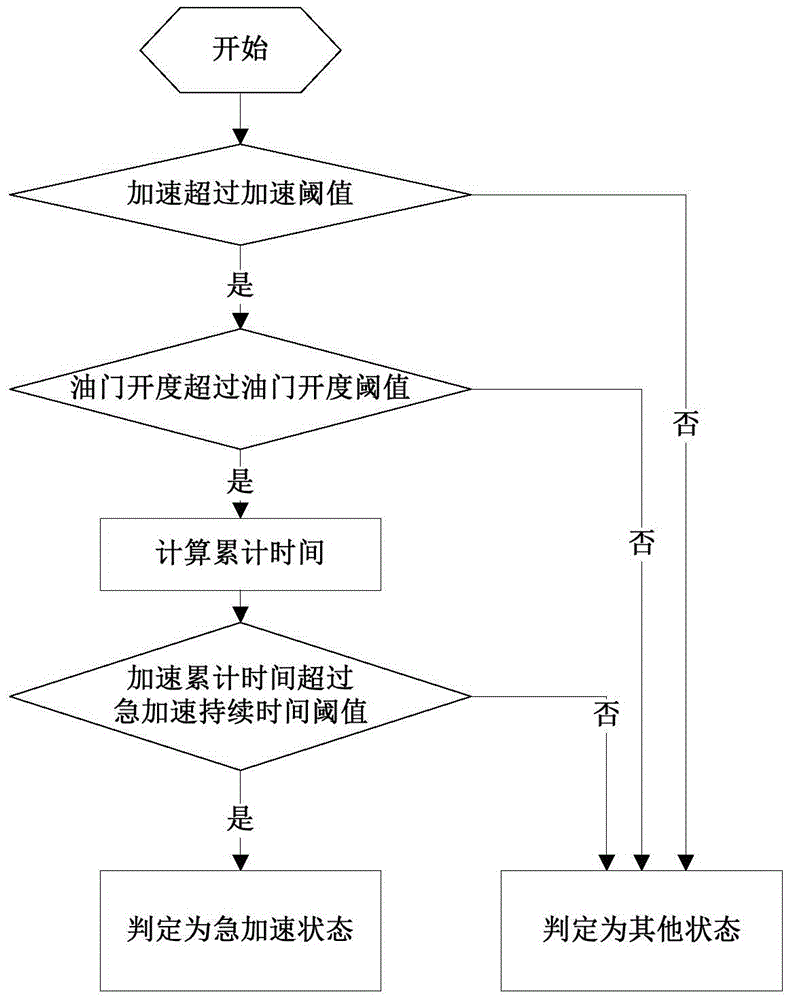
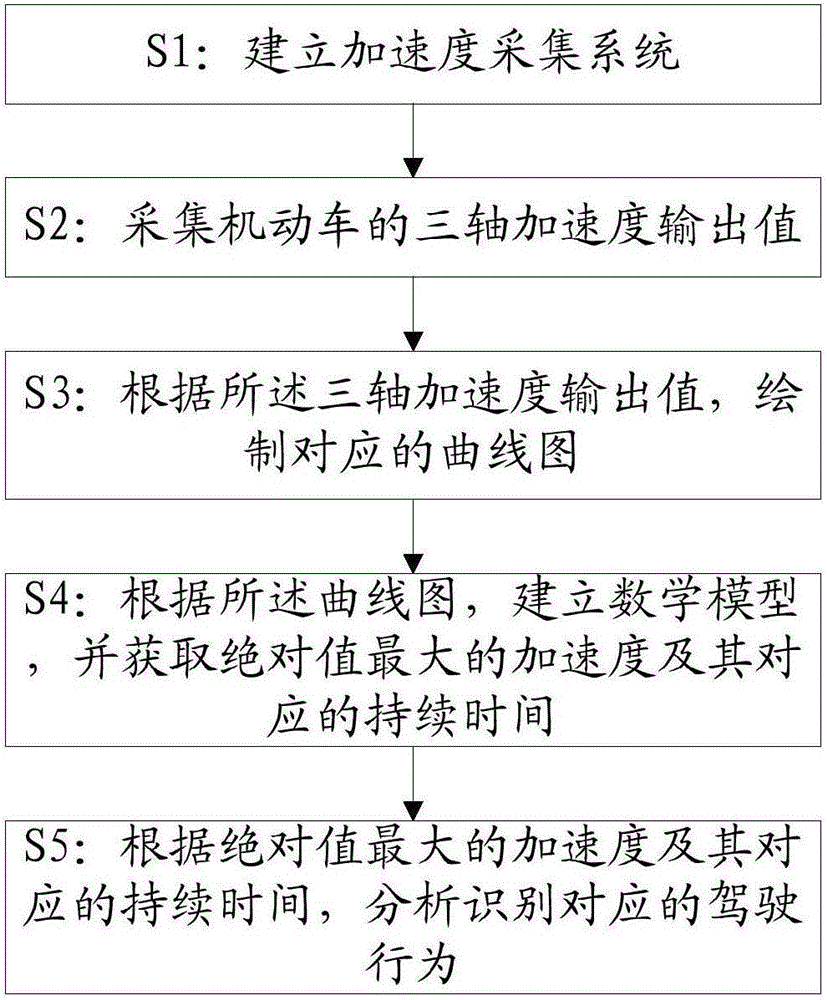
Driving behavior analysis and recognition method and system
InactiveCN105185112AImprove standard operationReliable data supportDetection of traffic movementDriver/operatorCollection system
The invention discloses a driving behavior analysis and recognition method and system, and the method comprises the steps: building an acceleration collection system; collecting a tri-axial acceleration output value of a motor vehicle; drawing a corresponding curve according to the tri-axial acceleration output value; building a mathematic model according to the curve, and obtaining an acceleration with the maximum absolute value, and the duration time corresponding to the acceleration; and analyzing and recognizing corresponding driving behaviors according to the acceleration with the maximum absolute value and the duration time corresponding to the acceleration. Through the above mode, the method can provide reliable data support for scientific analysis and research, so as to improve the operation of a driver and improve the economic benefit and social benefit of passenger transport enterprises.
Owner:深圳市北斗软核信息技术有限公司
System and method for performing agent behavioral analytics
A system and method for generating an agent behavioral analytics including transcribing an incoming call to produce a call transcription; and using a trained convolutional neural network (CNN) to produce behavioral labels for the agent in the incoming call for behavioral metrics, based on the call transcription. The CNN may include an embedding layer to convert words in the call transcription into vectors in a word embedding space; a convolution layer to perform a plurality of convolutions on the vectors and to generate vectors of features; a pooling layer to concatenate the vectors of features to a single vector by taking a maximum of each feature generated by the convolution layer; and a classification layer to produce grades of the agent in the incoming call for the set of attributes or behavioral metrics, based on the single vector generated by the pooling layer.
Owner:NICE LTD
Method and system, based on geographic model and moving track, for obtaining characteristic crowd in real time
ActiveCN103150156AClose to the needs of economic production activitiesTargetedSpecific program execution arrangementsSpecial data processing applicationsTraffic networkEconomic production
The invention discloses a method and a system, based on a geographic model and a moving track, for obtaining a characteristic crowd in real time. The method comprises the following steps: selecting a track analysis model, collecting positioning data of a mobile terminal from a base station of a region covered by the track analysis model, and performing matching filtering on the positioning data according to parameters of the track analysis model, so as to extract parameters coincident with the model. The method and the system propose an idea for setting a track analysis model according to geographical position information, such as hot spots, traffic networks and the like, and ensure that behavioral analysis based on mobile track is more close to the demands of economic production activities.
Owner:E-SURFING DIGITAL LIFE TECH CO LTD
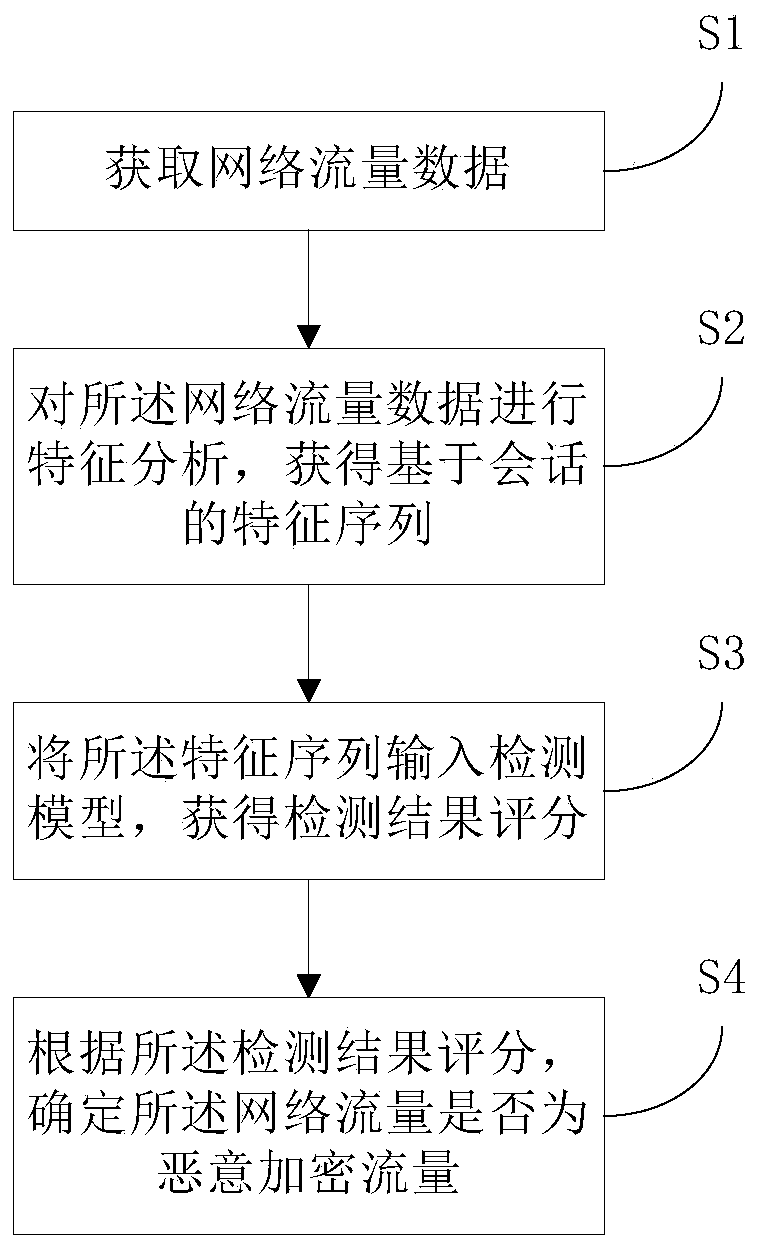
Malicious encrypted traffic detection method and system based on behavior analysis
InactiveCN111277587AEffective filteringReduce false alarm rateData switching networksPattern recognitionInternet traffic
The invention provides a malicious encrypted traffic detection method and system based on behavior analysis, and the method comprises the steps: carrying out the feature analysis of network traffic data after the network traffic data is obtained, and obtaining a feature sequence based on a session; and inputting the feature sequence into a detection model to obtain a detection result score, and determining whether the network traffic is malicious encrypted traffic or not according to the detection result score. According to the method, behavior characteristic analysis is carried out on the network traffic data, so that normal encrypted traffic in the network can be effectively filtered, malicious encrypted traffic is identified, and the false alarm rate is reduced. Meanwhile, through a detection model constructed in a machine learning mode, unknown data characteristics can be deduced according to known samples, and whether the network traffic data is malicious encrypted traffic or notis accurately judged.
Owner:武汉思普崚技术有限公司
Learning assistance method and system based on classroom emotion and behavior analysis
ActiveCN110992741ARealize Observational EvaluationAchieve recordElectrical appliancesData acquisitionContent analytics
The invention belongs to the technical field of computer teaching. The invention particularly relates to a learning assistance method and system based on classroom emotion and behavior analysis. The system comprises a data acquisition module, a student knowledge mastering detection module, a teacher teaching content analysis module and a learning pushing module, wherein the data acquisition modulecomprises a video acquisition module and an audio acquisition module; according to the method, the classroom learning mastery degree of students can be effectively analyzed, observation, evaluation and recording of the learning quality of the students are achieved, the mastery situation of the students for knowledge points is judged in combination with classroom audio information of teachers, andthe students are assisted in perfecting a knowledge system by conducting exercise pushing practice on the knowledge points which are not mastered.
Owner:深圳算子科技有限公司
Network equipment behavior analysis method and system
The invention provides a network equipment behavior analysis method and a network equipment behavior analysis method system. The network equipment behavior analysis method comprises the steps of establishing a behavior model for network equipment and applying the behavior model to monitor abnormal behaviors of the equipment. In the step of establishing the behavior model for the network equipment, data acquisition equipment is used for collecting and recording data packets received and / or sent by user equipment in normal state within one or more time periods; and a behavior analysis engine is used for converting information content of the data packets into a feature value containing one or more attributes, and the feature value is used for establishing a user equipment behavior model. In the step of applying the behavior model to monitor abnormal behaviors of the equipment, the data acquisition equipment collects data packets related to the equipment within one or more time periods; the data packets are quantified into a feature value containing one or more attributes through the behavior analysis engine, and the feature value of the equipment is compared with the behavior model to verify whether behaviors of the equipment are abnormal; and if the verification result is abnormal, an alarm is sent to the user.
Owner:BEIJING KUANGEN NETWORK TECH
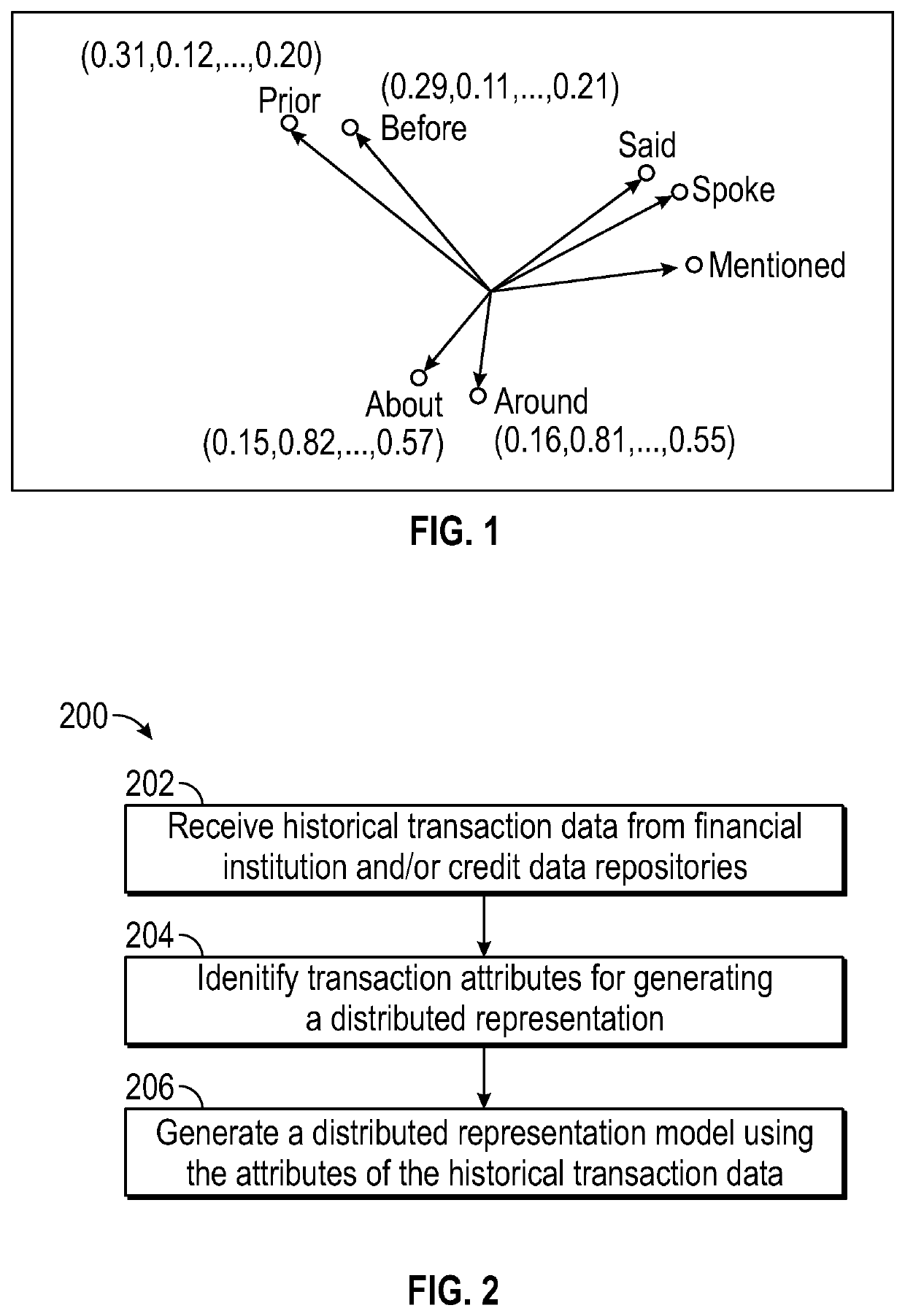
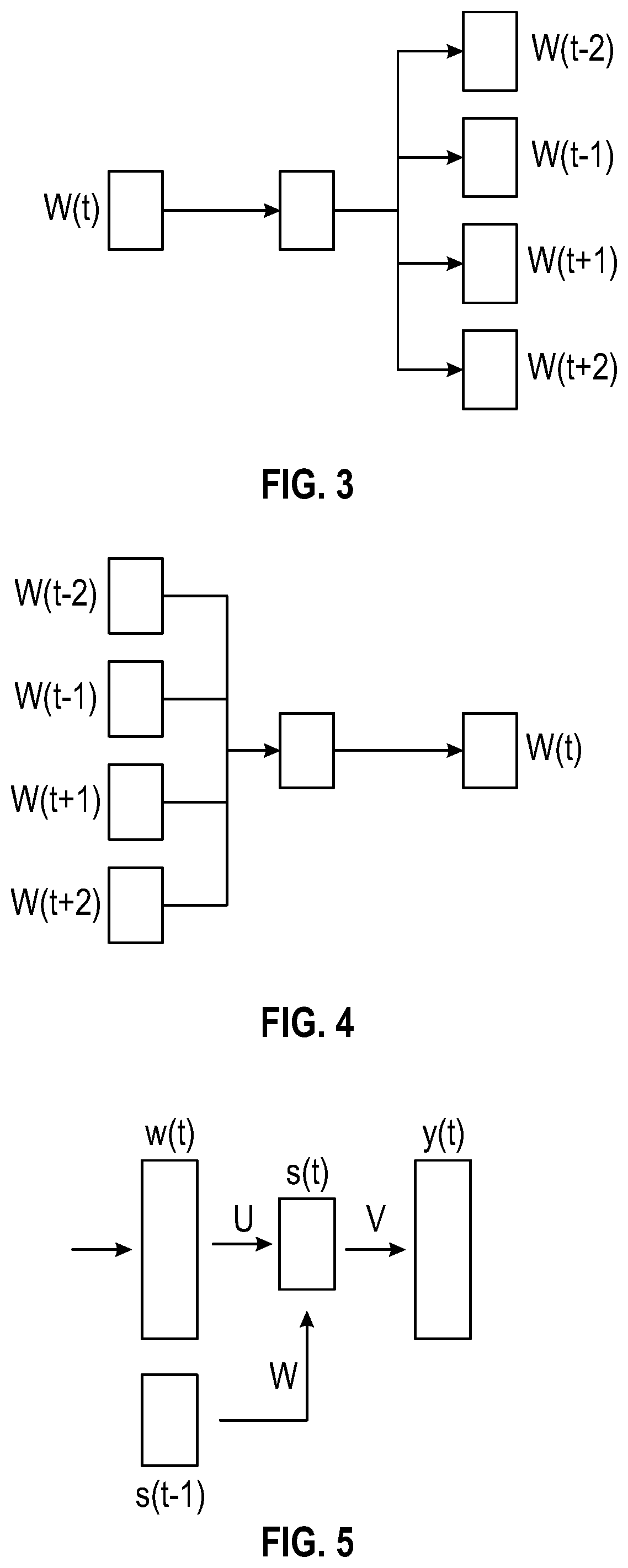
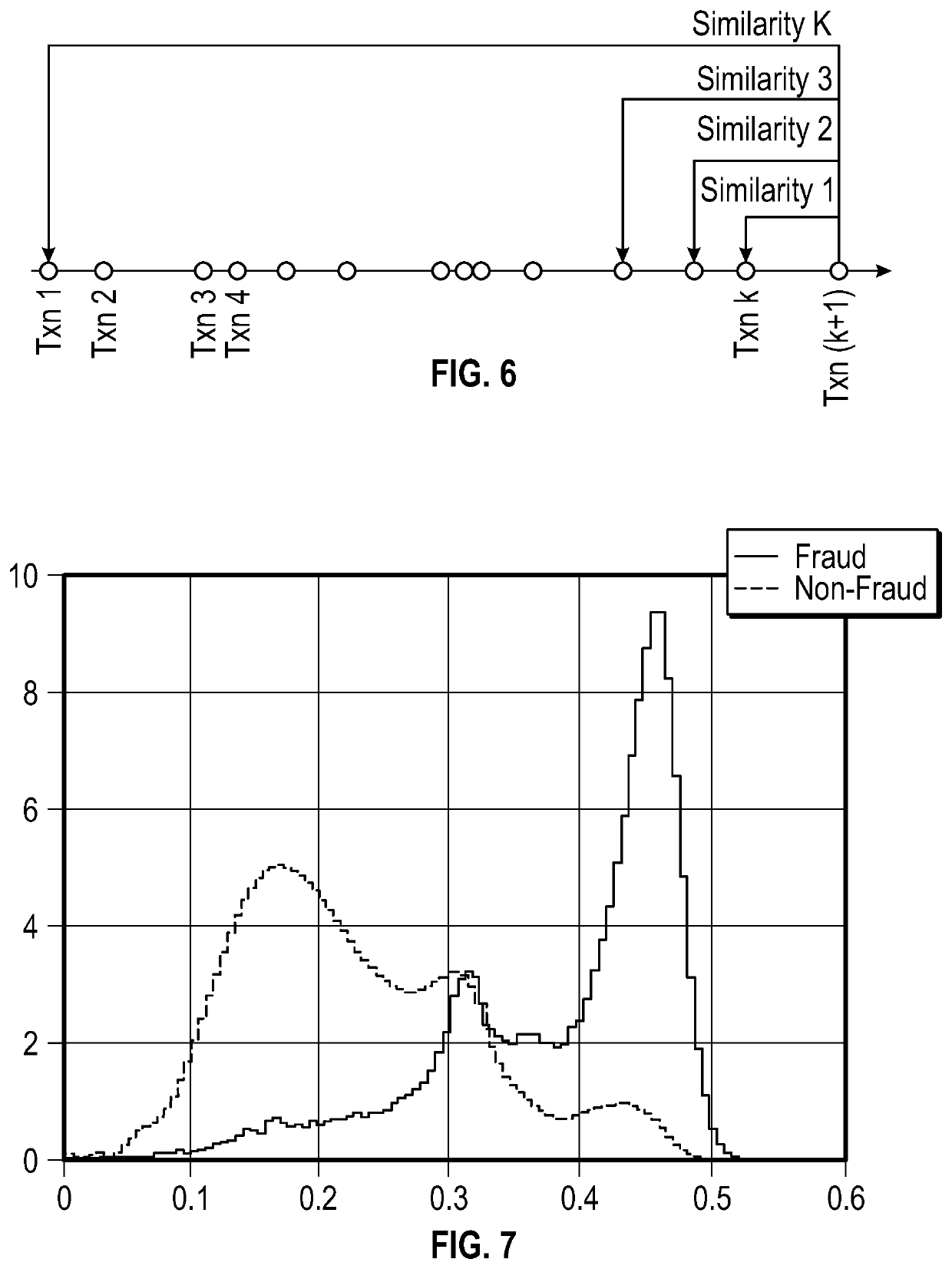
Behavior analysis using distributed representations of event data
ActiveUS11151468B1Reduce data volumeProbabilistic networksSpecial data processing applicationsLinguistic modelEvent data
The features relate to artificial intelligence directed detection of user behavior based on complex analysis of user event data including language modeling to generate distributed representations of user behavior. Further features are described for reducing the amount of data needed to represent relationships between events such as transaction events received from card readers or point of sale systems. Machine learning features for dynamically determining an optimal set of attributes to use as the language model as well as for comparing current event data to historical event data are also included.
Owner:EXPERIAN INFORMATION SOLUTIONS
Behavior analysis and alarm embedded equipment based on specific area
InactiveCN107948597AEasy to observeEffective preservationCharacter and pattern recognitionClosed circuit television systemsVideo transmissionAlarm device
The invention discloses behavior analysis and alarm embedded equipment based on a specific area and relates to the technical field of behavior analysis. The equipment comprises a camera, a video transmission module, an action capturing module, a face recognition module, an auxiliary processor, a database, a main processor, a main displayer, a second displayer and an alarm device, wherein the camera is dispersed in a to-be-monitored area and is used for monitoring the to-be-monitored area in real time and transmitting the video information to the action capturing module and the face recognitionmodule through the video transmission module. According to the behavior analysis and alarm embedded equipment based on the specific area in the invention, the camera, the face recognition module andthe action capturing module are used for carrying out video monitoring on a specific area needing to be monitored, automatically judging the person actions and the human face in the video, and judgingwhether the person has a danger coefficient or bad behaviors; and an alarm is given in time when the person is abnormal through the arrangement of the auxiliary processor; the information of a suspicious person can be displayed in time through the arrangement of the main displayer, thus bringing convenience for workers to observe.
Owner:HEFEI VRVIEW INFORMATION TECH
Abnormal behavior analysis method based on target trajectory
ActiveCN113011367AInsensitive to target shape changesEasy to trackCharacter and pattern recognitionMachine learningPattern recognitionVideo monitoring
The invention discloses an abnormal behavior analysis method based on a target trajectory. The method comprises the following steps: moving target tracking: inputting a video into a system, carrying out the target detection of the video through the system, carrying out the moving target tracking of a target in the video, obtaining the position of the moving target in each frame of image in a video sequence, and obtaining a target movement trajectory; path extraction: preprocessing the target movement track by adopting a polynomial fitting method, clustering by adopting a clustering algorithm, modeling data obtained after clustering, and extracting to obtain a scene path; behavior analysis: matching the input to-be-judged movement mode with the normal behavior model, and obtaining a behavior analysis result according to the matching condition; according to the method, the track of the moving object is obtained, and the behavior and activity of the moving object are further understood and predicted, so that the problem that judgment of the occurrence of a suspicious event mainly depends on manpower in a traditional video monitoring system is solved.
Owner:GUANGZHOU UNIVERSITY
Domestic multifunctional infant safety monitoring system
InactiveCN103536284AAbduction PreventionLess discomfortSensorsMeasuring/recording heart/pulse rateEngineeringMode selection
The invention provides an infant safety monitoring system which comprises a safety monitoring device and safety monitoring software. The safety monitoring device comprises a running mode selection unit used for selecting device running modes, a behavior monitoring unit used for monitoring body temperature, pulses and tumbling information of an infant, a time control unit used for setting time intervals according to a time control instruction, a behavior analysis unit used for analyzing monitored information and sending an analysis result to a result display unit and a Bluetooth communication unit according to the time control instruction, the Bluetooth communication unit used for sending the behavior analysis result to a smart phone, and the display unit used for displaying the display unit. The infant safety monitoring software conducts a safety assessment on received information and displays safety information or sends an early warning or alarm according to an assessment result. The infant safety monitoring system provides a powerful technical guarantee for safe growth of the infant, can help parents find that the infant has a fever, an injury due to tumbling and other situations in time, and also can effectively avoid the event that the infant is kidnapped.
Owner:王俊波
Product display rack system and purchasing behavior analysis program
InactiveUS7881988B2Co-operative working arrangementsCash registersComputer hardwareDirection detection
A system with an intelligent shelf (100) has product display shelves (110 to 130) displaying products having RFID tags R. The system includes antennas (112a to 112c) each having unique antenna numbers and detecting a tag serial number from an RFID tag on a product, human body sensors S disposed on each end of the product display shelf 120, a tag-product ID registration table storing the tag serial numbers of the RFID tags and the product IDs of the products and a control computer (200) detecting that a particular product is picked up from and / or returned to a particular product display shelf by combining the input tag serial number and the antenna number of the antenna detecting the tag serial number and analyzing which direction the detected human body has moved based on the difference of the detection times of the human body sensors.
Owner:TANAX INC +1
Cognitive modeling system including repeat processing elements and on-demand elements
The present design is directed to a system for performing cognitive modeling, including an event acquirer configured to acquire an event comprising an associated date and set of data fields, an analyzer element comprising a plurality of components repeated for each field in an event received from the event acquirer, wherein the analyzer element applies thresholds to each event, determines outliers, evaluates time-ordered behavior, and predicts threshold violations for the event, a periodic set of components configured to operate periodically on demand, the periodic set of components configured to perform peer to peer analysis, actor correlation analysis, actor behavior analysis, semantic rule analysis, and predict rates of change, and a plurality of signal managers interfacing with the analyzer element and the periodic set of components configured to exclude signals based on content properties of data transmitted.
Owner:SCIANTA ANALYTICS LLC
Driving behavior analysis method based on improved K-means
InactiveCN111461185AImprove accuracyImprove stabilityCharacter and pattern recognitionResourcesData setEngineering
The invention discloses a driving behavior analysis method based on improved K-means, and belongs to the technical field of driving behavior analysis. According to the method, the problem that the existing K-means method is poor in scientificity and accuracy of a driving behavior clustering result is solved. In order to select an optimal initial center, the invention provides a DC algorithm, the algorithm calculates the product of the density of samples in a data set, the reciprocal of the average difference degree among the samples in the class and the difference degree among the clusters asa center index, and the initial center is determined by the center index; then the initial center obtained through the DC algorithm is used as a default parameter to be input into the K-means algorithm, so that the accuracy and stability of the K-means algorithm on the clustering result of the driving behaviors are improved, and the clustering result of the improved K-means algorithm on the driving behaviors is more scientific. Experimental results show that on the research of driving behavior clustering analysis, the improved algorithm is higher in accuracy and stronger in anti-interference capability, and the accuracy reaches 90%. The method can be applied to driving behavior analysis.
Owner:HARBIN ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com