User portrait grouping and behavior analysis method and system based on log data of network security equipment
A network security and behavior analysis technology, applied in transmission systems, character and pattern recognition, instruments, etc., can solve problems such as user unauthorized access, economic loss of enterprises, abnormal access behavior cannot be well checked out, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
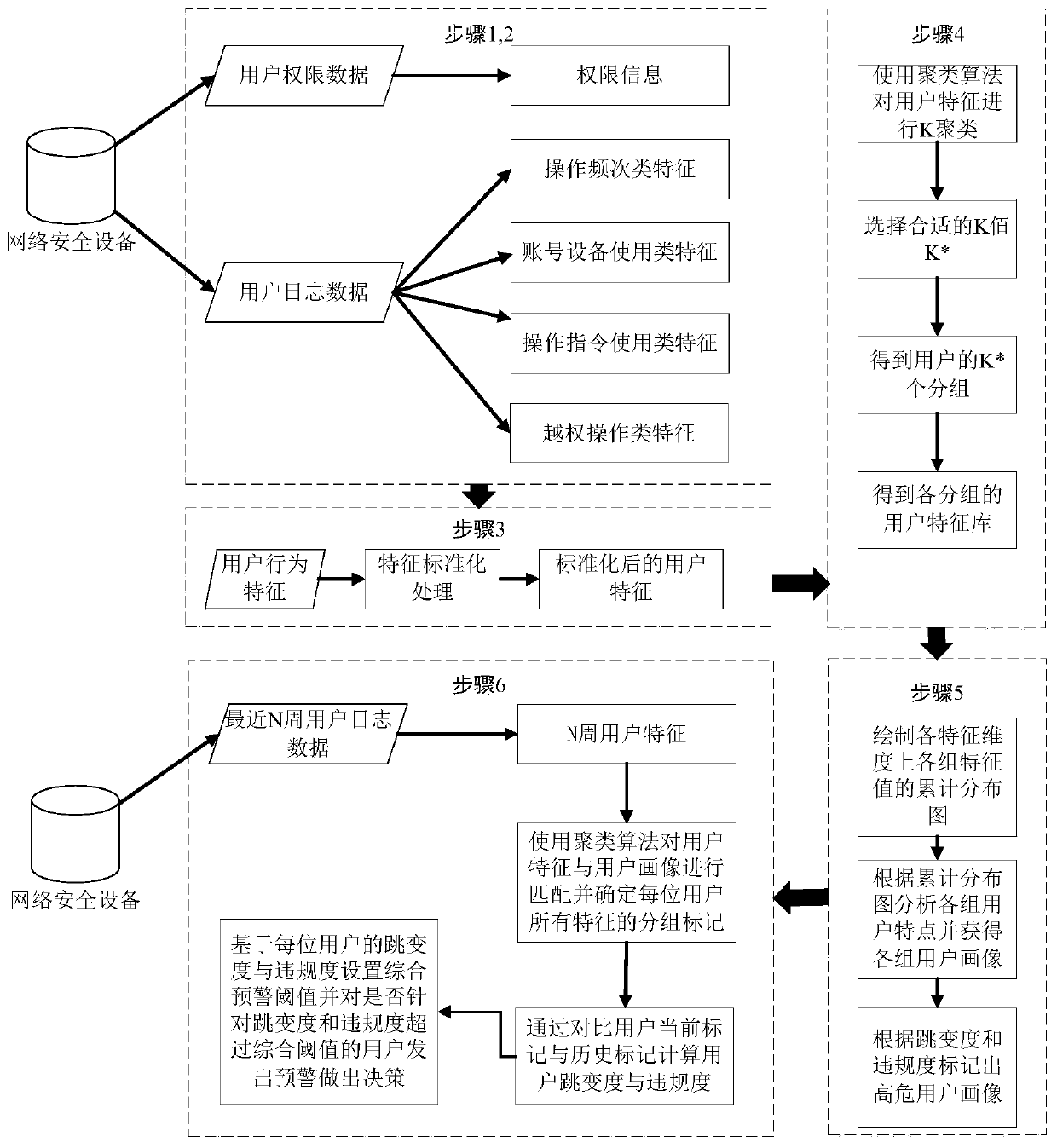
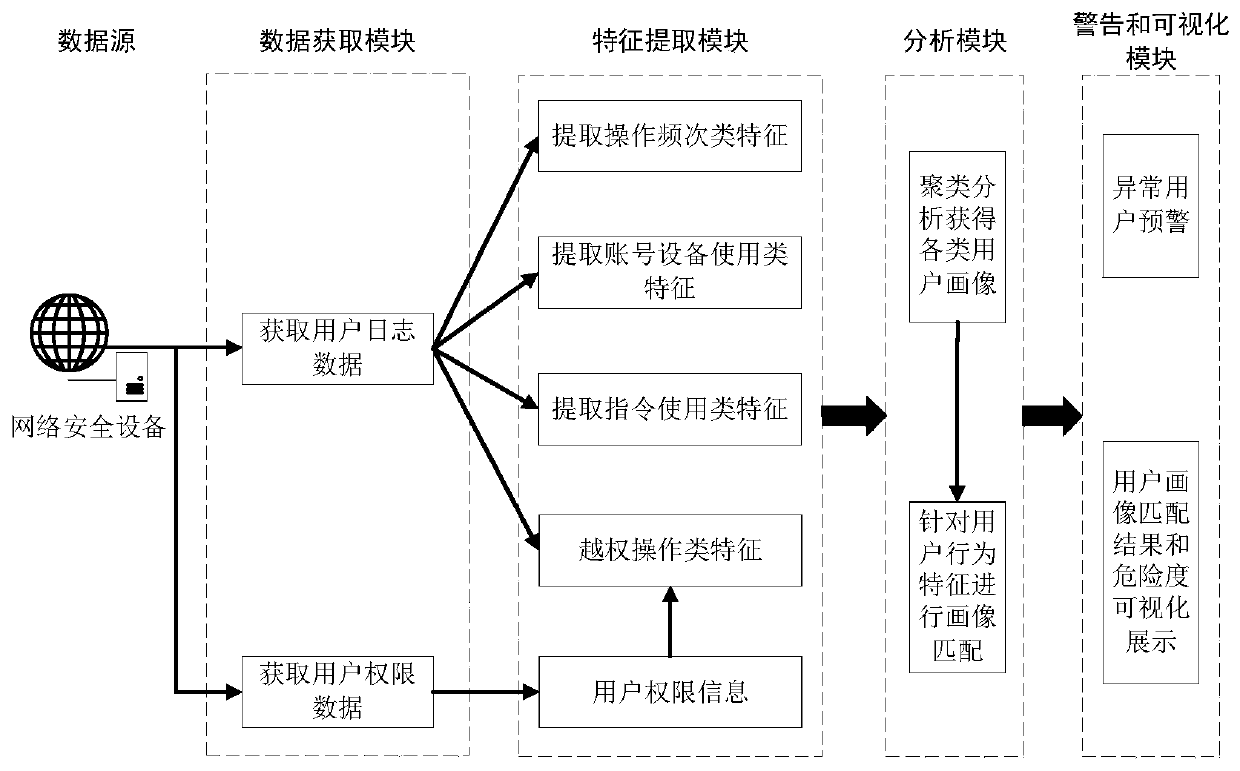
[0050] The method in the present invention will be divided into two parts: offline modeling and online analysis, specifically including data acquisition process, feature extraction process, clustering model building process, and online user behavior analysis process. figure 1 It is a block diagram of the user portrait grouping and behavior analysis method based on network security device log data of the present invention. The system of the present invention is illustrated in block diagram form. figure 2 It is a frame diagram of the user portrait grouping and behavior analysis system based on network security device log data of the present invention.
[0051] data acquisition process
[0052] image 3 It is an instance of the user authority data of the network security device. Figure 4 is an instance of network security device user log data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com