Method, device and system for transaction by mobile phone
A transaction method and mobile phone technology, applied in security devices, payment system structures, instruments, etc., can solve problems such as insecurity and user bank information insecurity, and achieve the effect of ensuring legitimacy, easy maintenance, and simple transaction process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
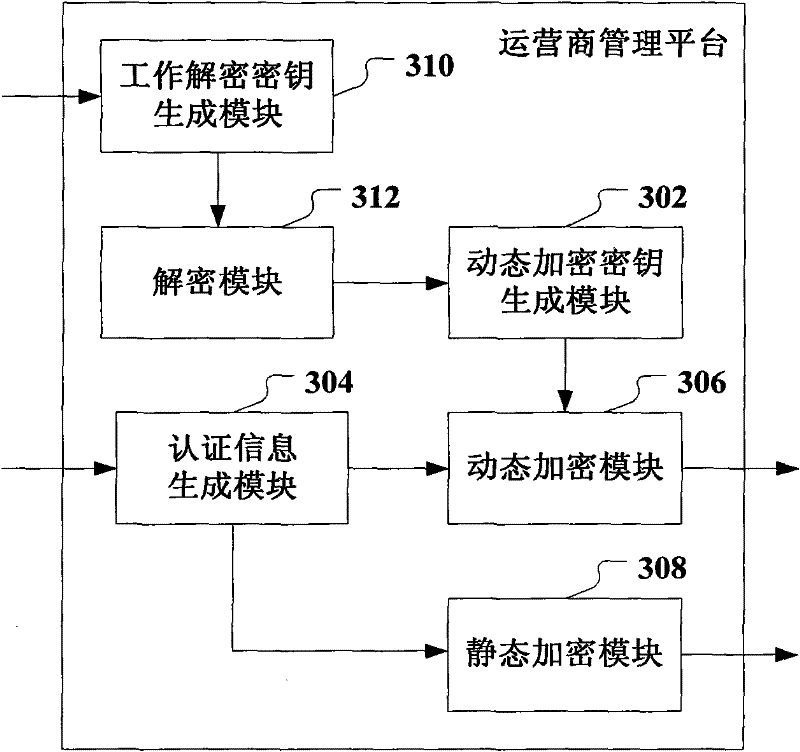
[0068] Such as image 3 As shown, the embodiment of the operator management platform of the present invention includes:
[0069] A dynamic encryption key generation module 302, configured to generate a dynamic encryption key corresponding to this transaction;
[0070] An authentication information generation module 304, configured to generate authentication information after bundling the terminal's IMSI and mobile phone number;
[0071] The dynamic encryption module 306 is configured to, after receiving the transaction message sent by the terminal, use the pre-generated dynamic encryption key to encrypt the transaction message and the authentication information and send it to the bank side.
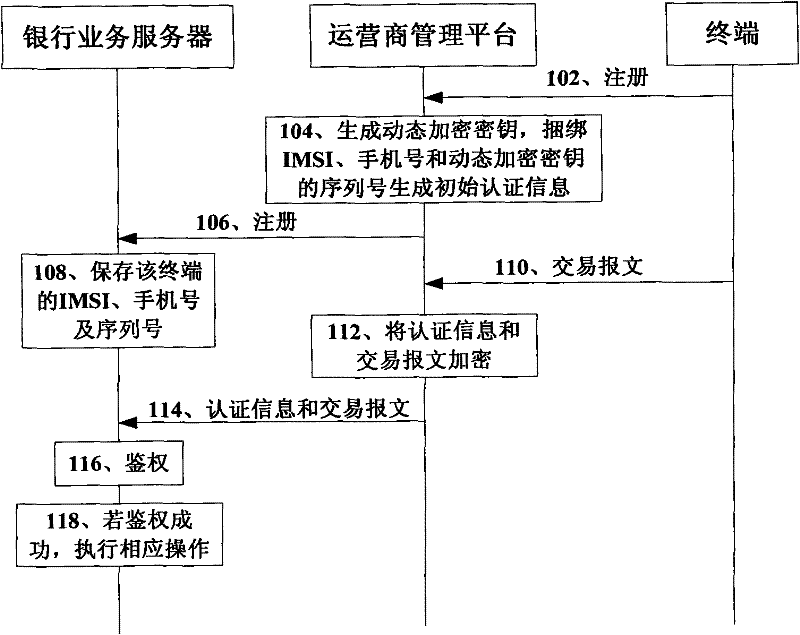
[0072] Preferably, this embodiment further includes: a static encryption module 308, wherein, when the terminal initiates a transaction, the authentication information generation module 304 receives the IMSI and mobile phone number registered by the terminal, and stores the terminal's IM...
Embodiment 2
[0076] Such as Figure 4 As shown, the banking service server embodiment of the present invention includes:
[0077] The dynamic decryption module 402 is used to decrypt the encrypted transaction message and authentication information sent by the operator side according to the dynamic decryption key, and obtain the authentication information and transaction message;
[0078] An authentication module 404, configured to perform authentication according to the authentication information;
[0079] The execution module 406 is configured to perform corresponding operations according to the transaction message after the authentication is successful.
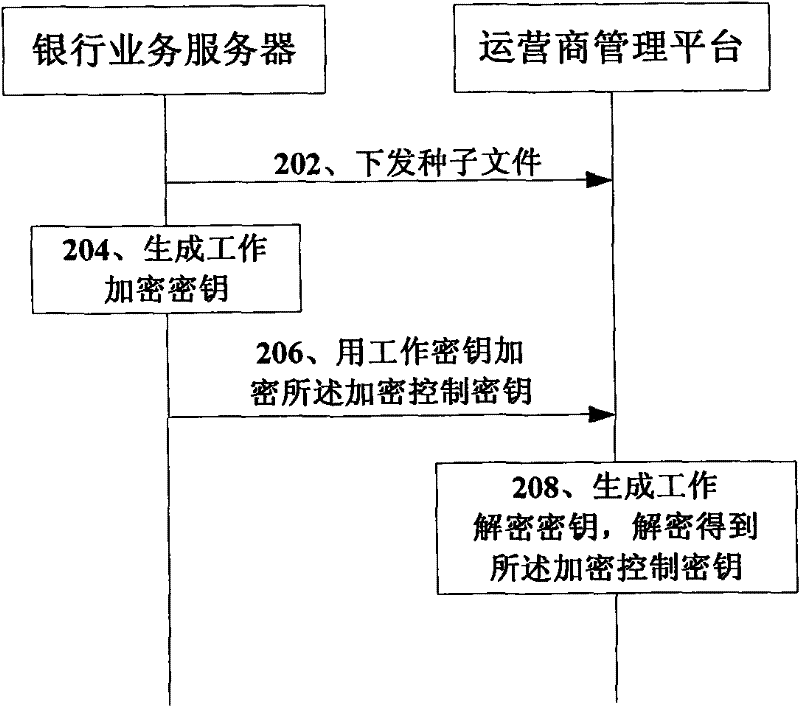
[0080] Preferably, this embodiment further includes: a static decryption module 408, configured to decrypt the encrypted initial authentication information sent by the operator according to a preset static key; a storage module 410, configured to store the terminal's The IMSI, the mobile phone number and the serial number correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com