Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47 results about "Static key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A cryptographic key is called static if it is intended for use for a relatively long period of time and is typically intended for use in many instances of a cryptographic key establishment scheme. Contrast with an ephemeral key.
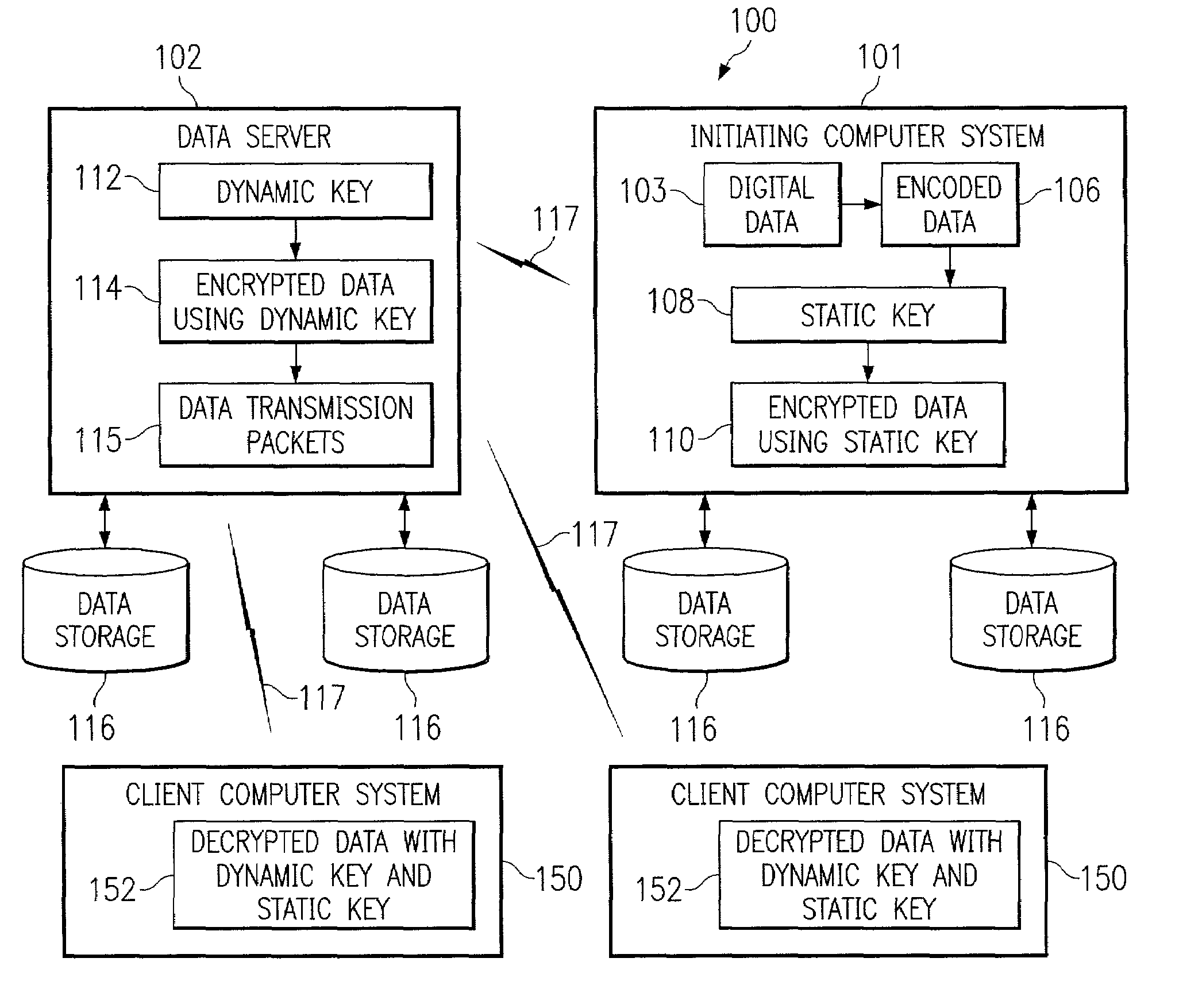
Systems, methods, and computer program products for accelerated dynamic protection of data
InactiveUS7280658B2Sufficient protectionKey distribution for secure communicationSecret communicationComputer resourcesEnd to end security
Owner:SNAP INC
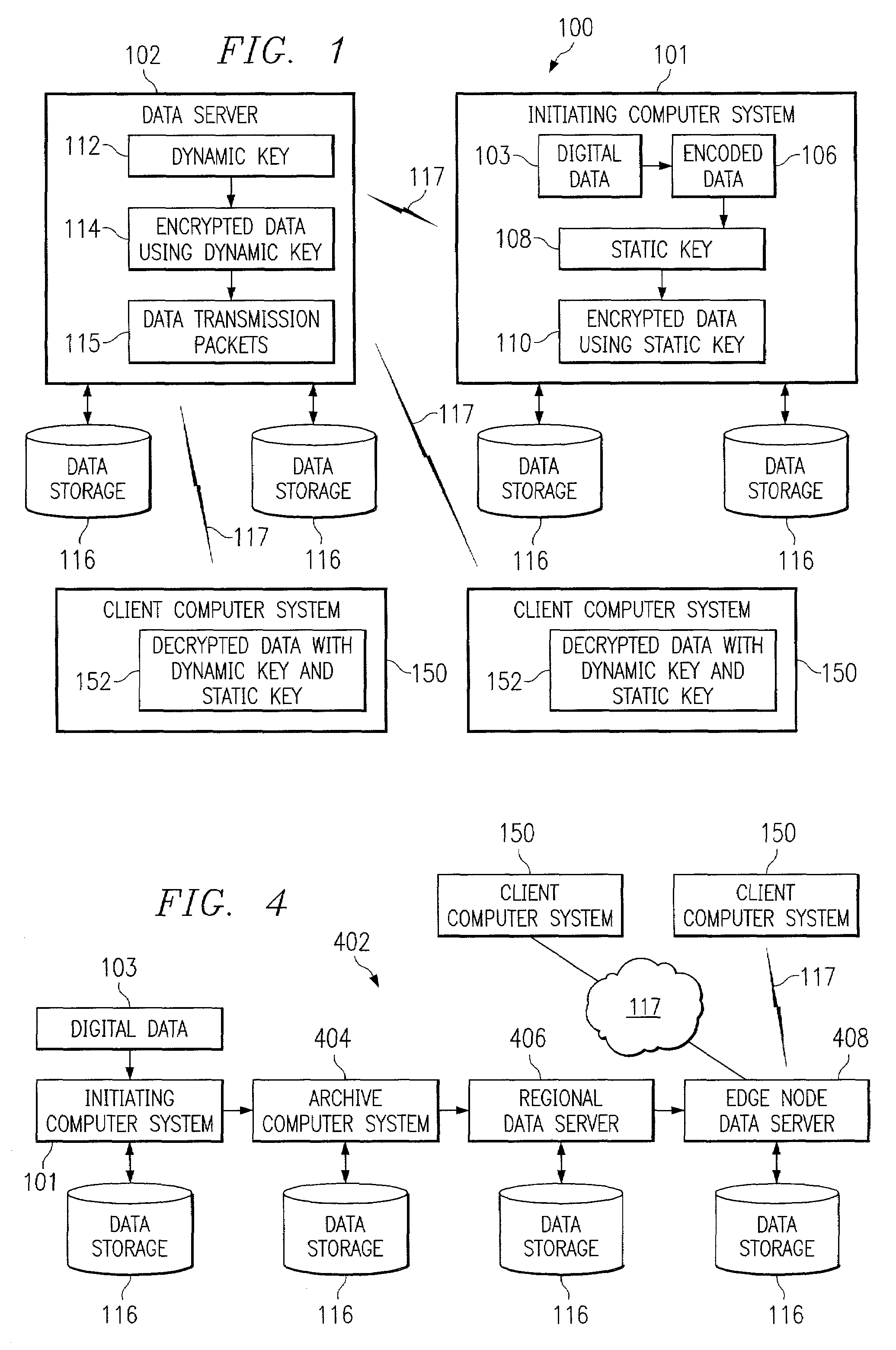
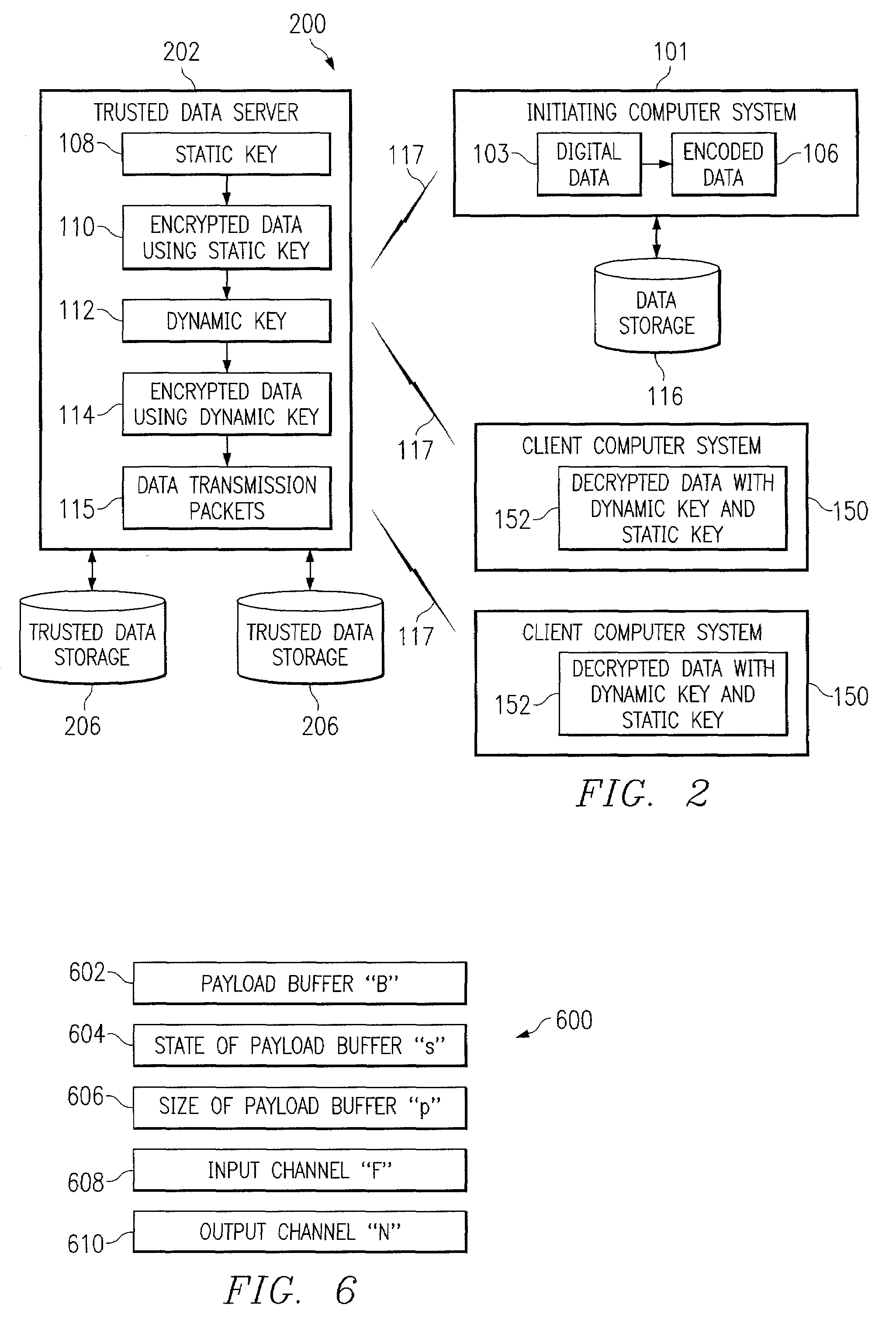
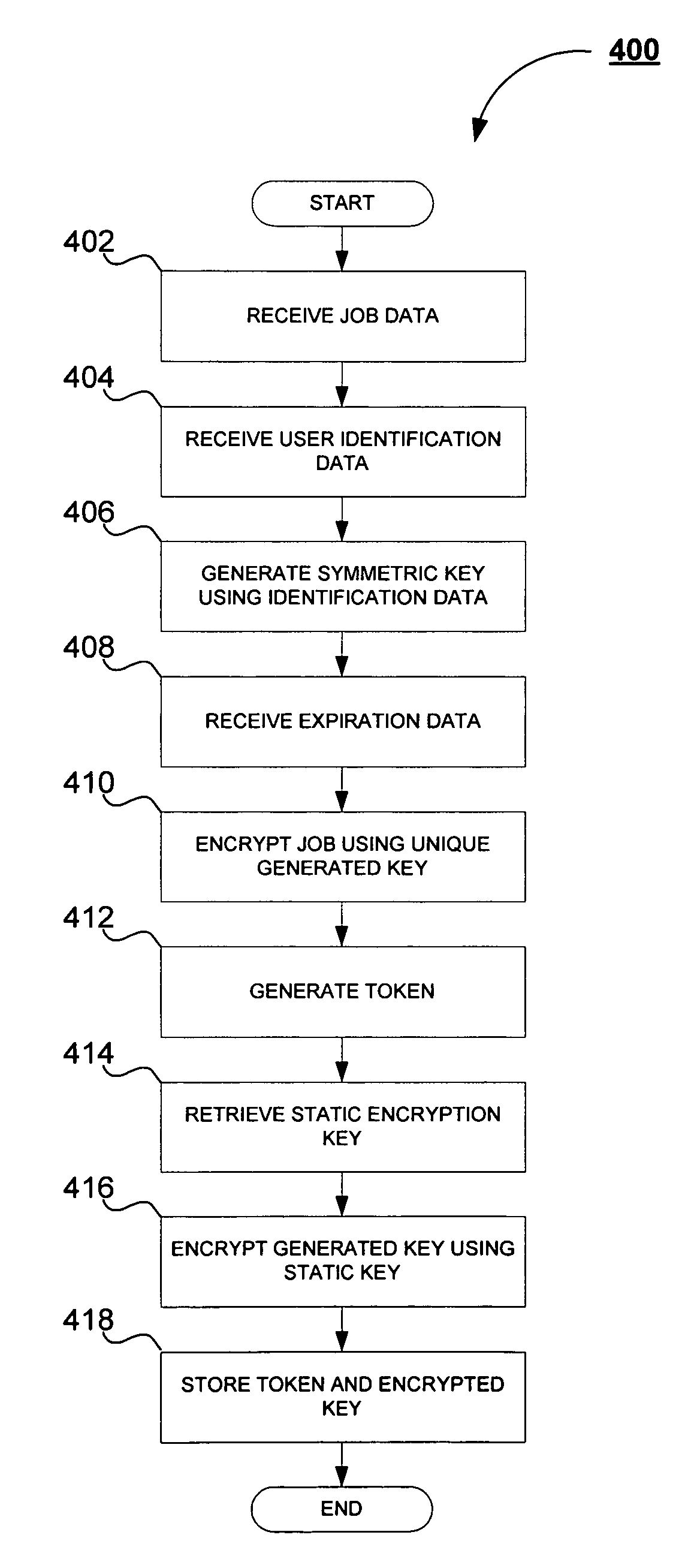
System and method for secure inter-process data communication
A system and method for secure inter-process data communication is provided. Identification data corresponding to a user is received and used to generate a symmetric encryption key. The symmetric encryption key is then used to encrypt job data. A token associated with the encrypted job data is then generated. Expiration data corresponding to the validity period of the token is then associated with the token, whereupon the token is stored. The generated symmetric key is then encrypted using a static symmetric encryption key, whereupon the encrypted symmetric key is also stored in association with the token. When a process receives the encrypted job data, the process retrieves the token and determines, based on the expiration data whether the token is still valid. When the token is valid, the static key is retrieved and used to decrypt the encrypted encryption key. The decrypted encryption key is then used to decrypt the job data, whereupon the process performs the function associated therewith upon the decrypted job data.
Owner:KK TOSHIBA +1
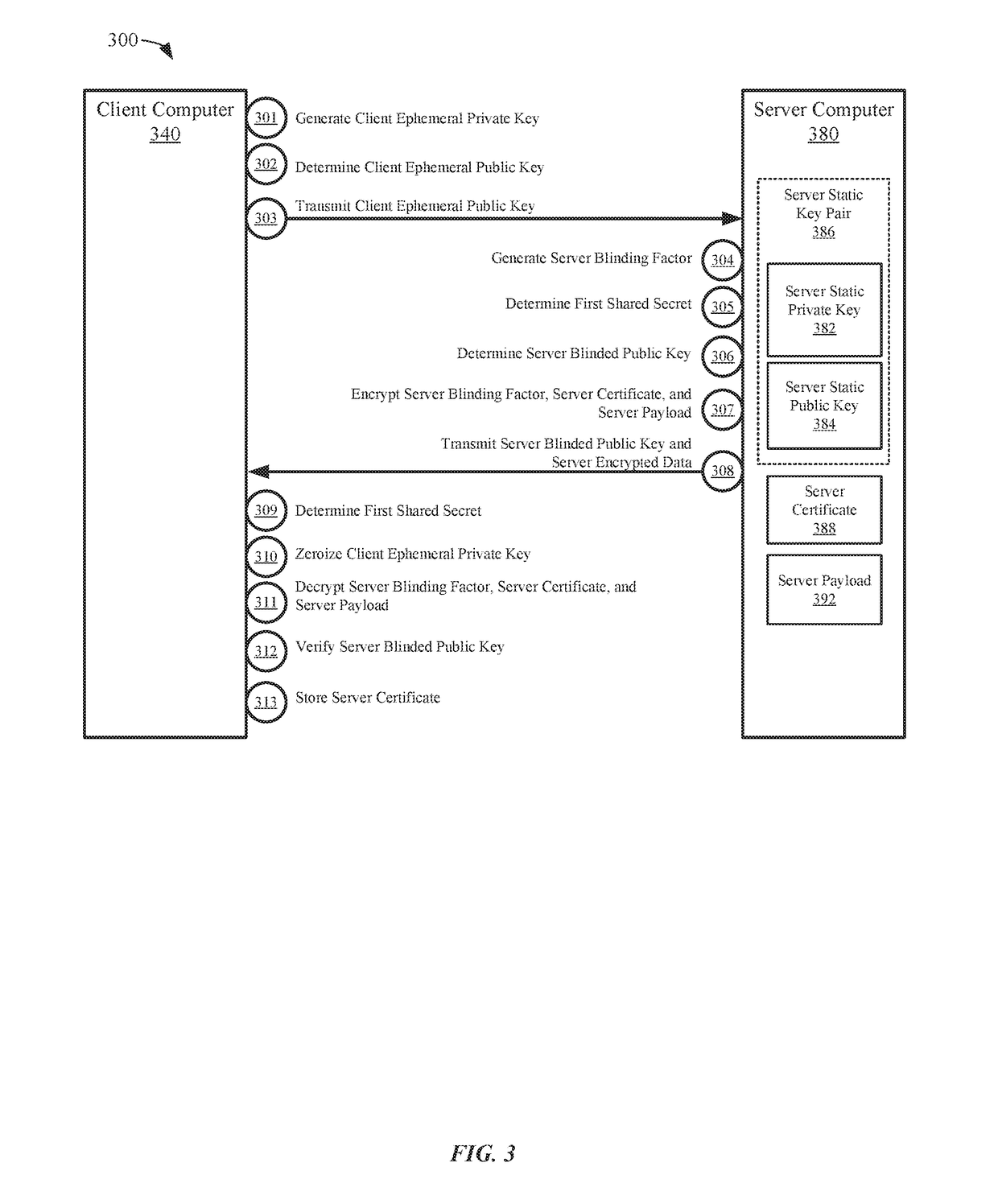
Secure communications providing forward secrecy
ActiveUS20180375663A1Public key for secure communicationUser identity/authority verificationComputer hardwareSecure communication
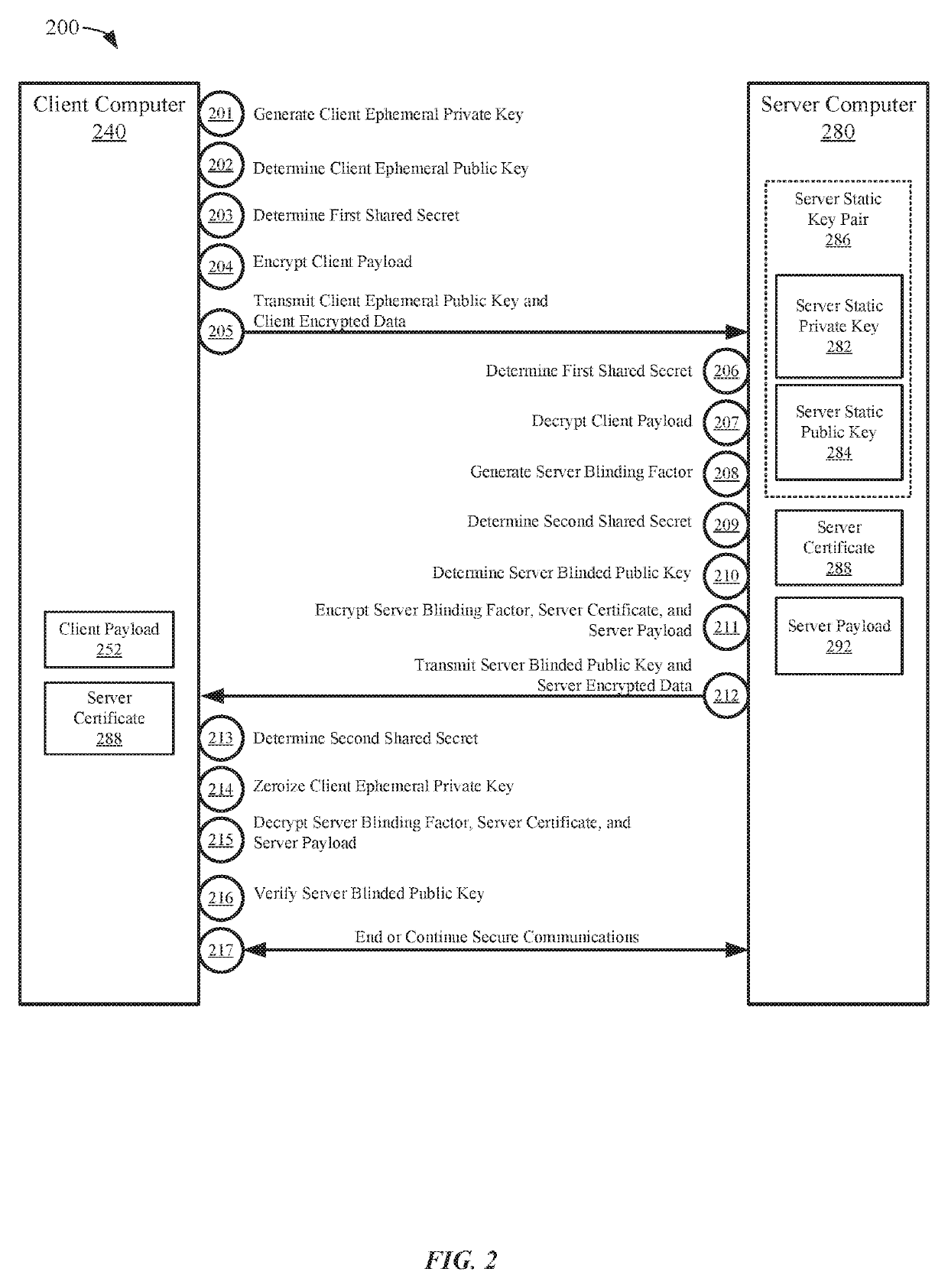
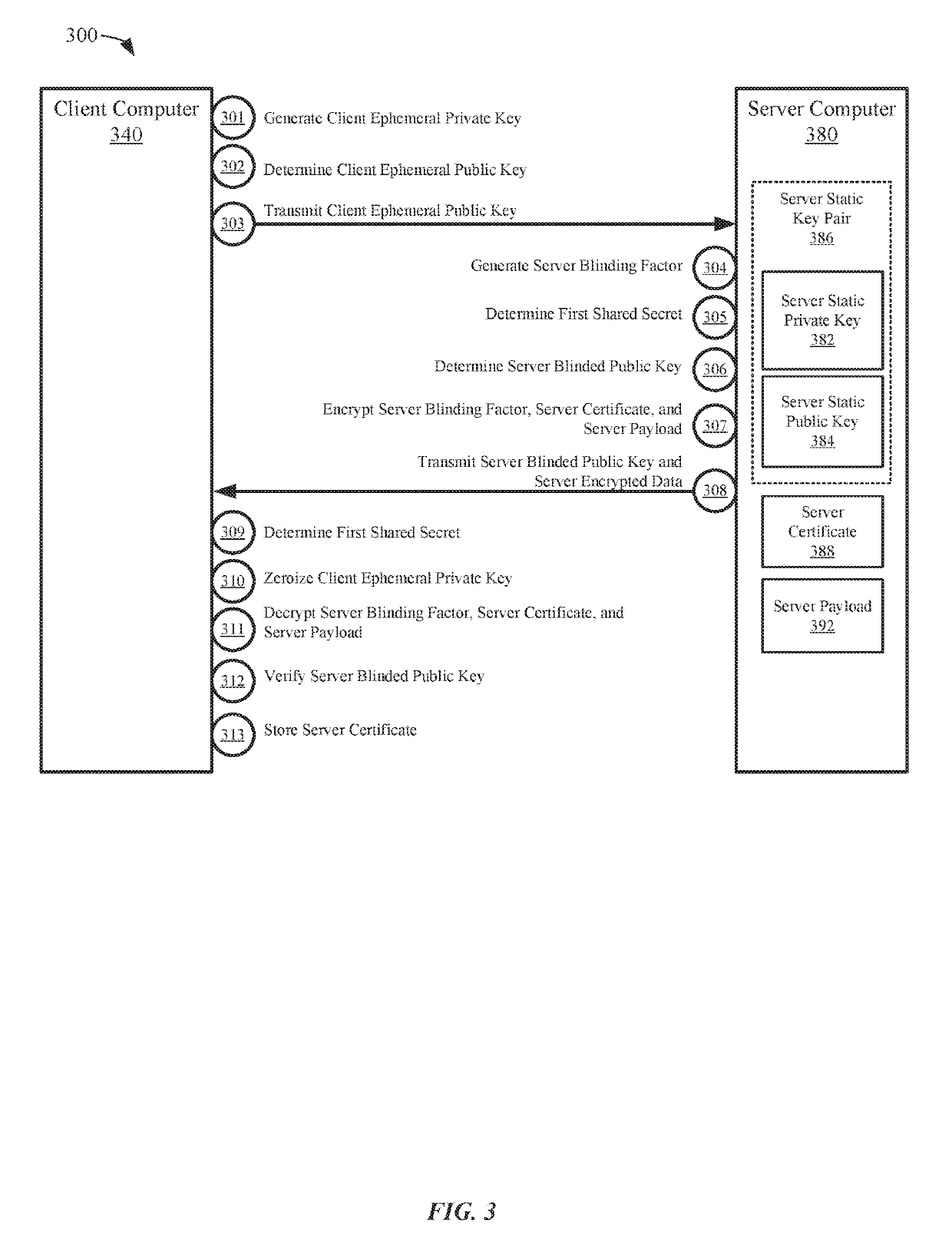
Embodiments of the invention can establish secure communications using a single non-traceable request message from a first computer and a single non-traceable response message from a second computer. Non-traceability may be provided through the use of blinding factors. The request and response messages can also include signatures that provide for non-repudiation. In addition, the encryption of the request and response message is not based on the static keys pairs, which are used for validation of the signatures. As such, perfect forward secrecy is maintained.
Owner:VISA INT SERVICE ASSOC
System, apparatus, and method for access control
InactiveUS20160210454A1Efficiently provideImprove user experienceDigital data processing detailsUnauthorized memory use protectionControl systemMedia access control
An aspect of the disclosure provides an access control system configured to verify a user device within a region, based on wireless communication and a confirmation code which may include one or more static key(s) and / or time-varying key(s), and to verify a user of the user device within the region, based on biometric recognition after the user device is verified. In this way, at least one resource is allowed to be accessed when at least the verification of the user is passed. Further, accessing a resource may be consuming, entering, or using the resource. A variety of practical applications may then be performed for the user, due to the allowance of accessing the resource.
Owner:CHOU PU YAO
Face expression detection method, apparatus, device, system and medium
InactiveCN109063679AImprove usabilityImprove user experienceAcquiring/recognising facial featuresPattern recognitionFace detection
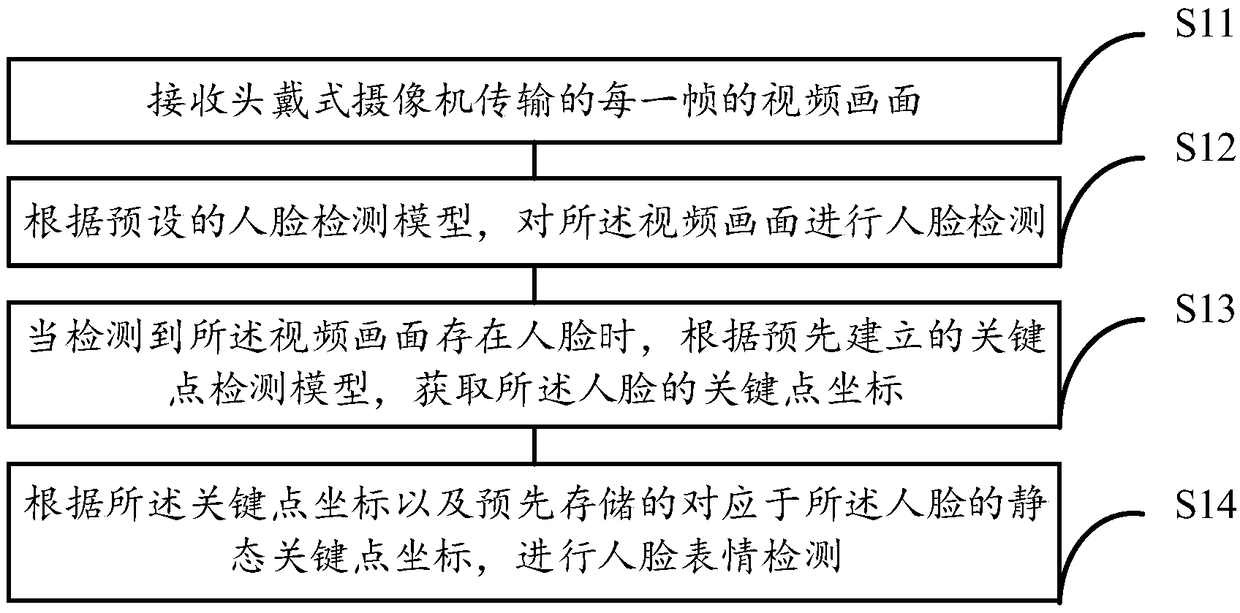
The invention discloses a facial expression detection method, an apparatus, a device, a system and a computer-readable storage medium. The method comprises the following steps: receiving a video picture of each frame transmitted by a head-mounted camera; performing face detection on the video picture according to a preset face detection model; When a human face is detected in the video picture, the coordinates of the key points of the human face are obtained according to a key point detection model established in advance; Detecting facial expression according to the key point coordinates and the static key point coordinates corresponding to the face stored in advance; The invention simply and efficiently realizes the facial expression detection process, improves the operation efficiency and realizes the comprehensive utilization of the operation resources.
Owner:GUANGZHOU DUOYI NETWORK TECH +2
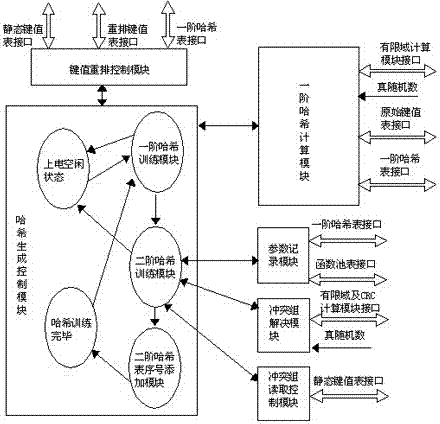
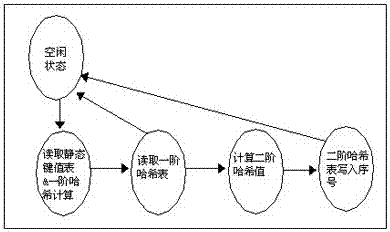
FPGA training and inquiry circuit achievement method based on perfect hash algorithm
ActiveCN107330047AReduce capacityMapping Space RelaxationSpecial data processing applicationsTheoretical computer scienceAssembly line
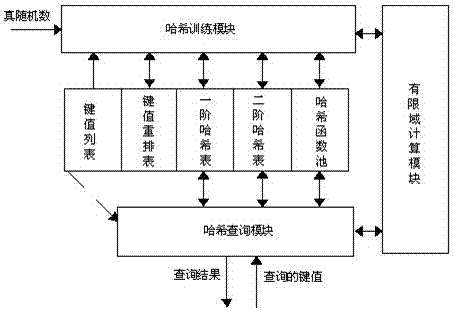
The invention discloses an FPGA training and inquiry circuit achievement method based on a perfect hash algorithm. The method comprises the following steps of creating a static key value table; conducting first-order hash calculation on static key values and a true random number, and mapping results to a first-order hash table; making the static key values which conflict with one another in the same slot position in the first-order hash table constitute a conflict group, and duplicating the conflict group into adjacent positions of a key value rearranging table; conducting second-order hash calculation on the conflict group to obtain a second-order hash table in which conflict group mapping address index values are mutually different, wherein when serial numbers of the static key values are inquired, the address index values of the static key values are searched in the first-order hash table and / or the second-order hash table, the serial numbers of the static key values are read, and the hash index numbers can be output through serial number query. By utilizing the strong assembly line calculation capability of an FPGA, the size of the mapping space of the conflict group in the second-order hash table is gradually widened through trials from being initially set larger than or equal to 2 of integer power of the least of the conflict number, which drastically saves the volume of the second-order hash table.
Owner:HUAXIN SAIMU CHENGDU TECH CO LTD
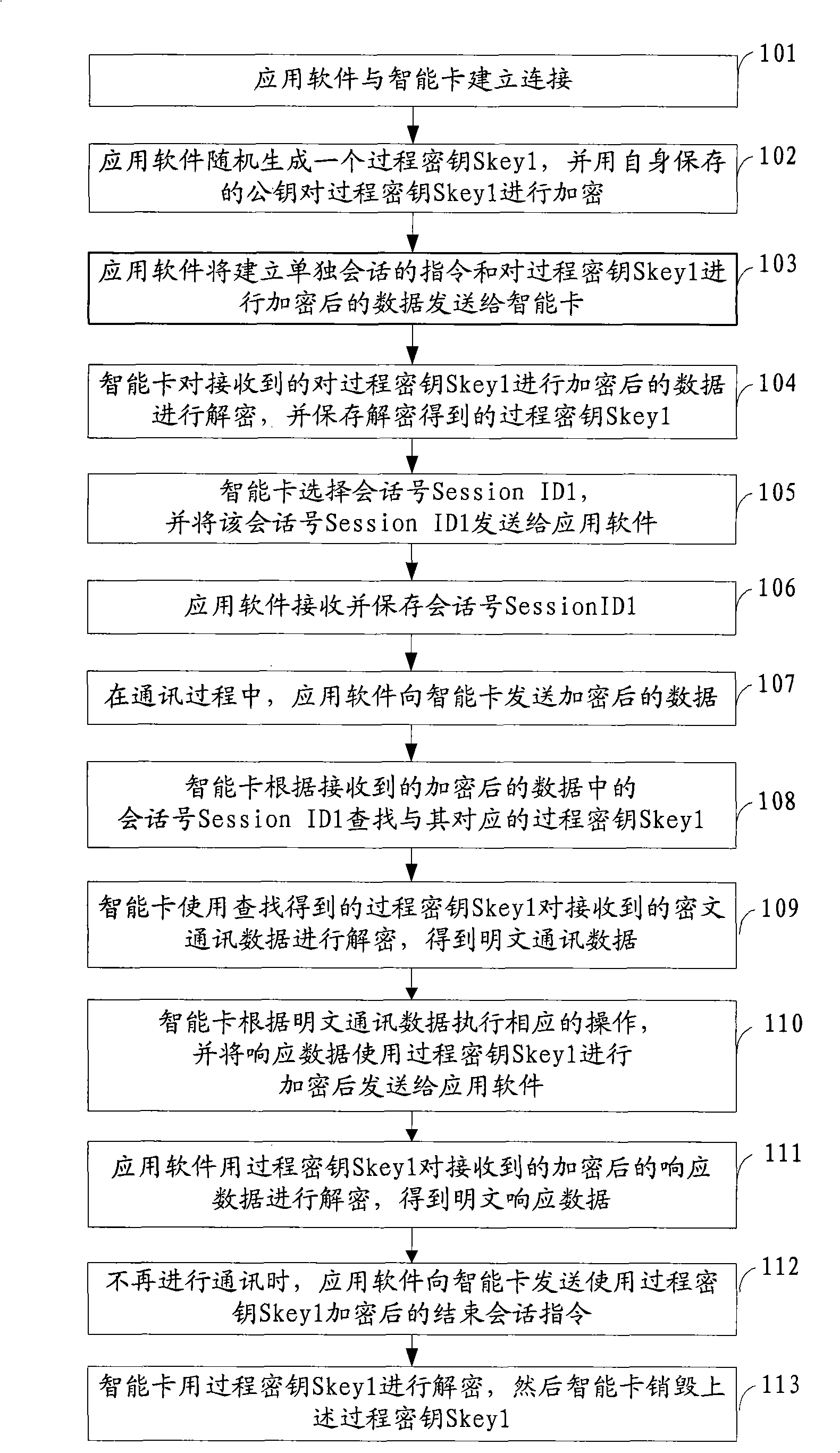
Smart key equipment and communication method and system of application software
The invention discloses smart key equipment and a communication method and a system of application software, belonging to the field of data communication. The method comprises the following steps: a connection is established between the smart key equipment and the application software; a single conversion is established between the smart key equipment and the application software and a process key is appointed by the smart key equipment and the application software; the application software uses the process key to encrypt the communication data and transmits the conversion number of the single conversion and the encrypted communication data to the smart key equipment; and the smart key equipment uses the process key corresponding to the conversion number to decrypt the encrypted communication data according to the conversion number of the single conversion so as to obtain plain text communication data. The system comprises a main machine and the smart key equipment. Through establishing the single conversion between the smart key equipment and the application software and using the conventional key to encrypt the communication data and then transmit the encrypted communication data, the problem of the plain text transmission or static key transmission between the current software and the smart key equipment can be solved.
Owner:FEITIAN TECHNOLOGIES
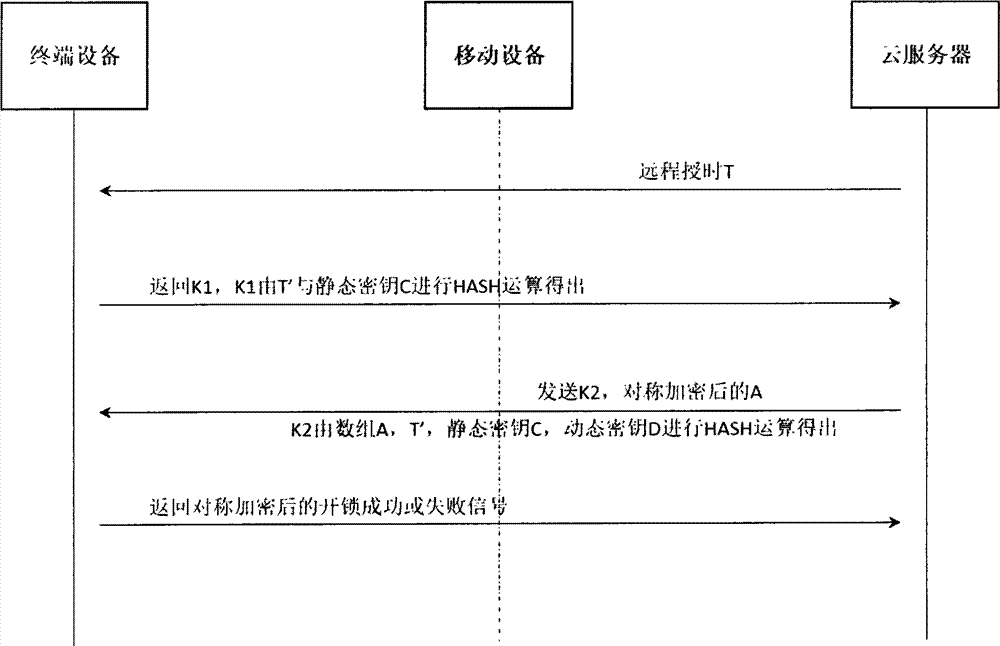
Composite dynamic password authentication method and authentication system applicable to plug-and-play terminal
InactiveCN104717230AIncrease uncertaintyGood exposure protectionUser identity/authority verificationArray data structurePassword
The invention discloses a composite dynamic password authentication method and an authentication system applicable to a plug-and-play terminal. The method and the system comprise the following steps: providing remote time service to an embedded terminal through a server, and calculating a first key K1 and feeding back the first key K1 to the server according to time factor change T' and a built-in static key C through the terminal; generating a random number group A according to the situation that terminal right is authenticated by using K1 through the server, and calculating second keys K2, wherein the random number group A comprises a change factor ai, and K2 are HASH values of A, T', C and a built-in dynamic key D; receiving K2 through the terminal, comparing K2 with K2' calculated by the terminal, if the result shows that K2 is accordant with K2', determining whether a password is jumped or not according to characteristic values calculated according to T', if the password is jumped, obtaining ai in the random number group A according to a sequence L and a pointer P, calculating a new key D' according to D so as to replace the key, and loading the new key D' into a non-volatile memory. Two time / event synchronous dynamic password modes are adopted simultaneously, the change characteristics of the password are increased, and the method and the system are particularly applicable to bidirectional authentication of plug-and-play terminals and servers.
Owner:赵姗姗
Custom static Diffie-Hellman groups
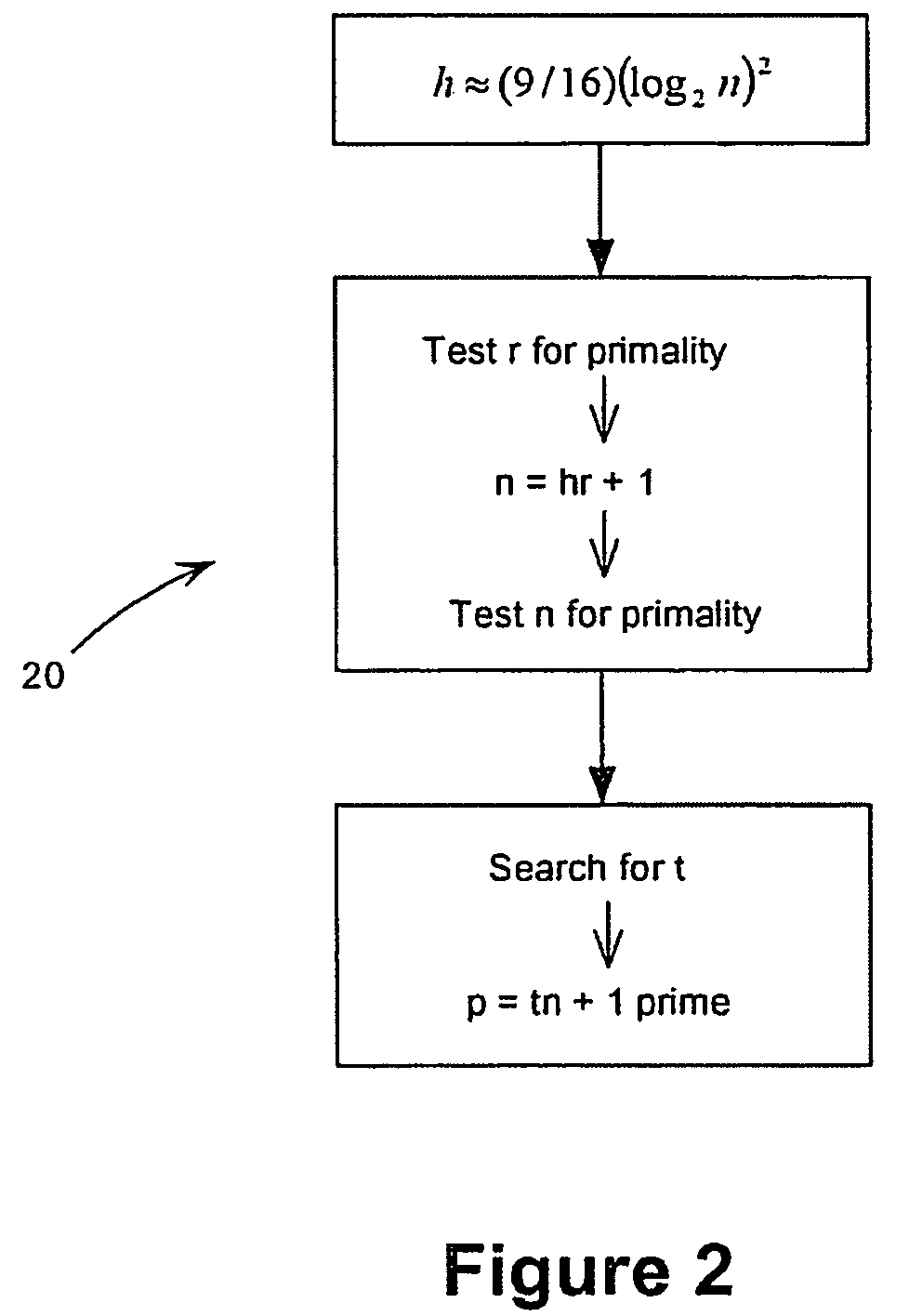
ActiveUS8588409B2Inhibit active attackPublic key for secure communicationComputer security arrangementsAdversaryAlgorithm
Methods for choosing groups for a static Diffie-Hellman key agreement protocol to inhibit active attacks by an adversary are provided. In mod p groups, an even h is chosen of value approximately ( 9 / 16)(log2n)2, values r and n are determined using sieving and primality testing on r and n, and a value t is found to compute p=tn+1 wherein p is prime. In elliptic curve groups defined over a binary filed, a random curve is chosen, the number of points on the curve is counted and this number is checked for value of 2n wherein n is prime and n−1 meets preferred criteria. In elliptic curve groups defined over a prime field of order q, a value n=hr+1 is computed, wherein n is prime and n−1 meets preferred criteria, and a complex multiplication method is applied on n to produce a value q and an elliptic curve E defined over q and having an order n.
Owner:MALIKIE INNOVATIONS LTD
Method and system for displaying results of a dynamic search
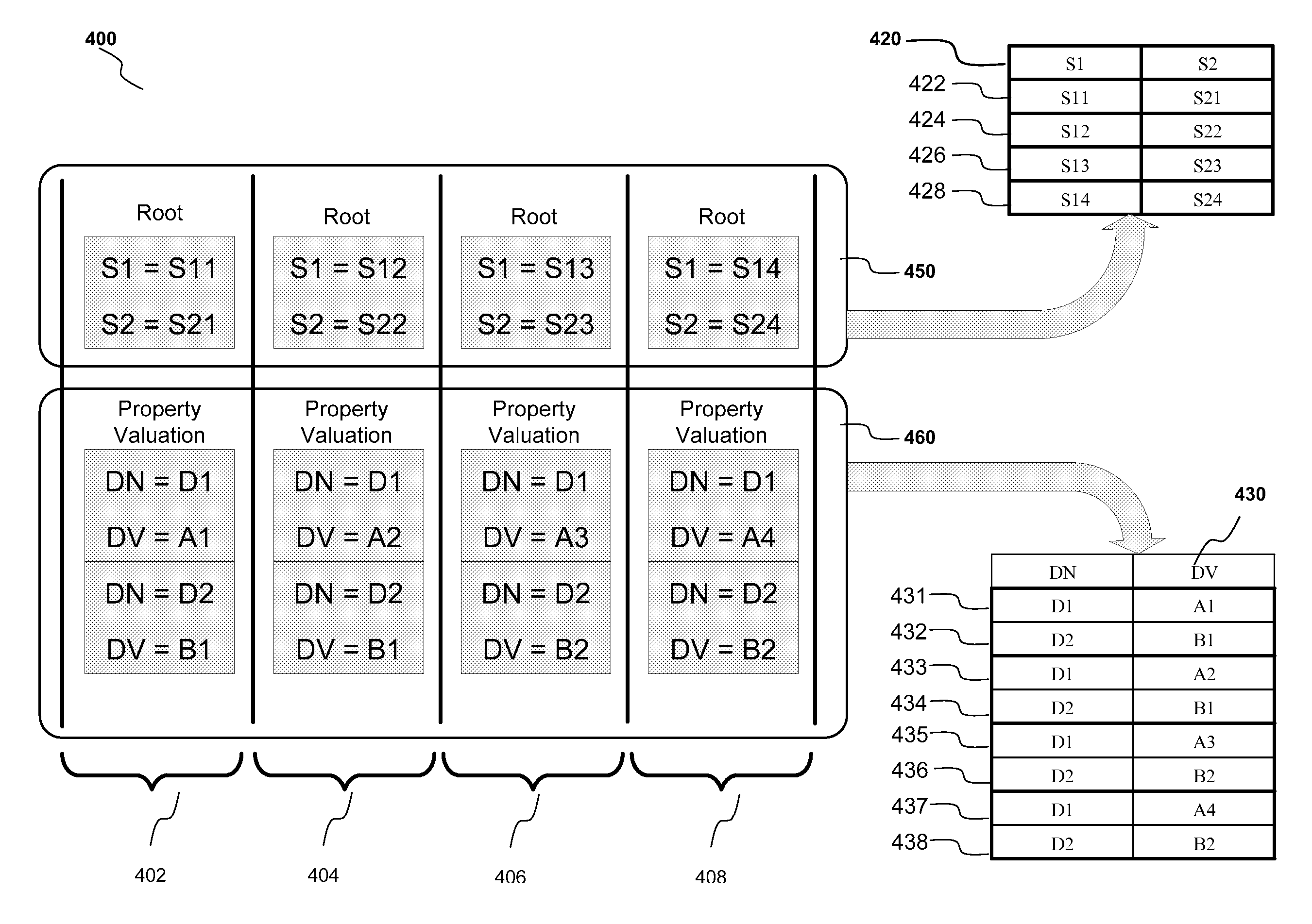
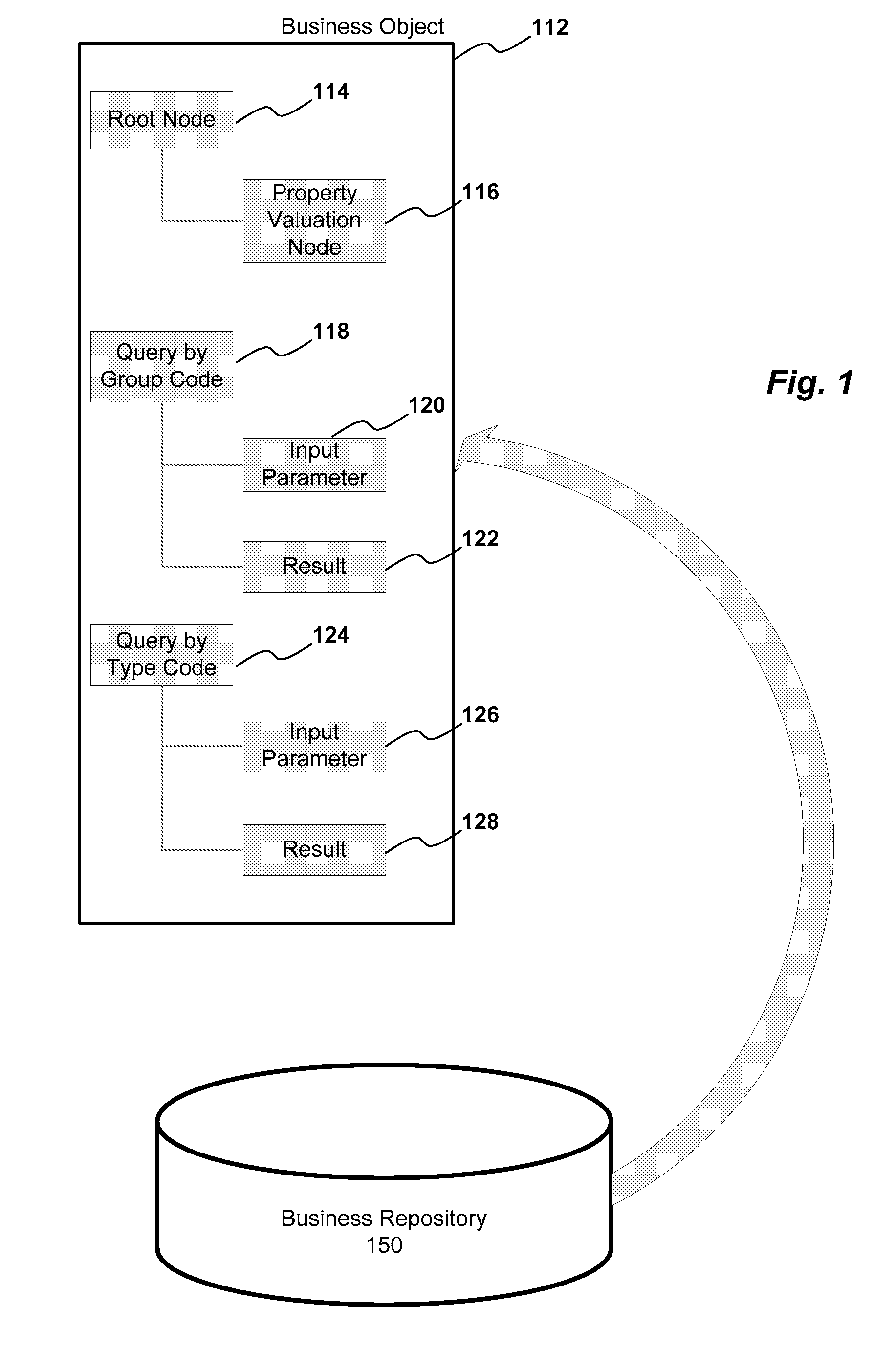
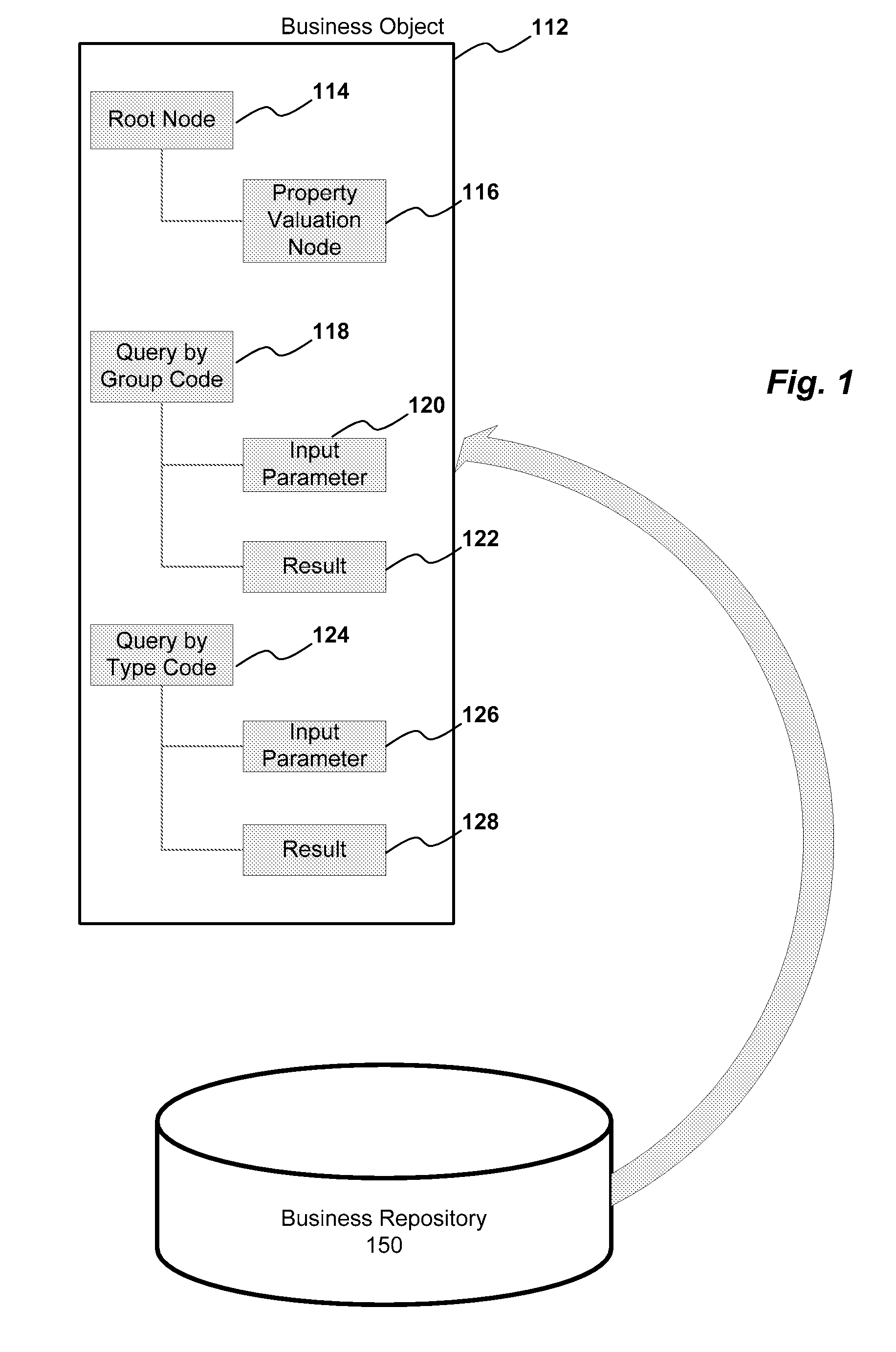
ActiveUS20080183669A1Digital data information retrievalData processing applicationsTheoretical computer scienceStatic key
A method and system for displaying results of a dynamic search are provided. Results of a search are received in a result node of a query wherein the result node comprises a first node and a second node. The first node has a static key data and the second node has a dynamic key data. The static key data and the dynamic key data are transferred to a dummy node. A table displaying the static key data and the dynamic key data is then generated based upon the dummy node.
Owner:SAP AG
Method and system for establishing safe connection between nodes
ActiveCN101834862ABuild flexibleUpdate flexibleData switching by path configurationComputer networkTelecommunications
Owner:CHINA IWNCOMM
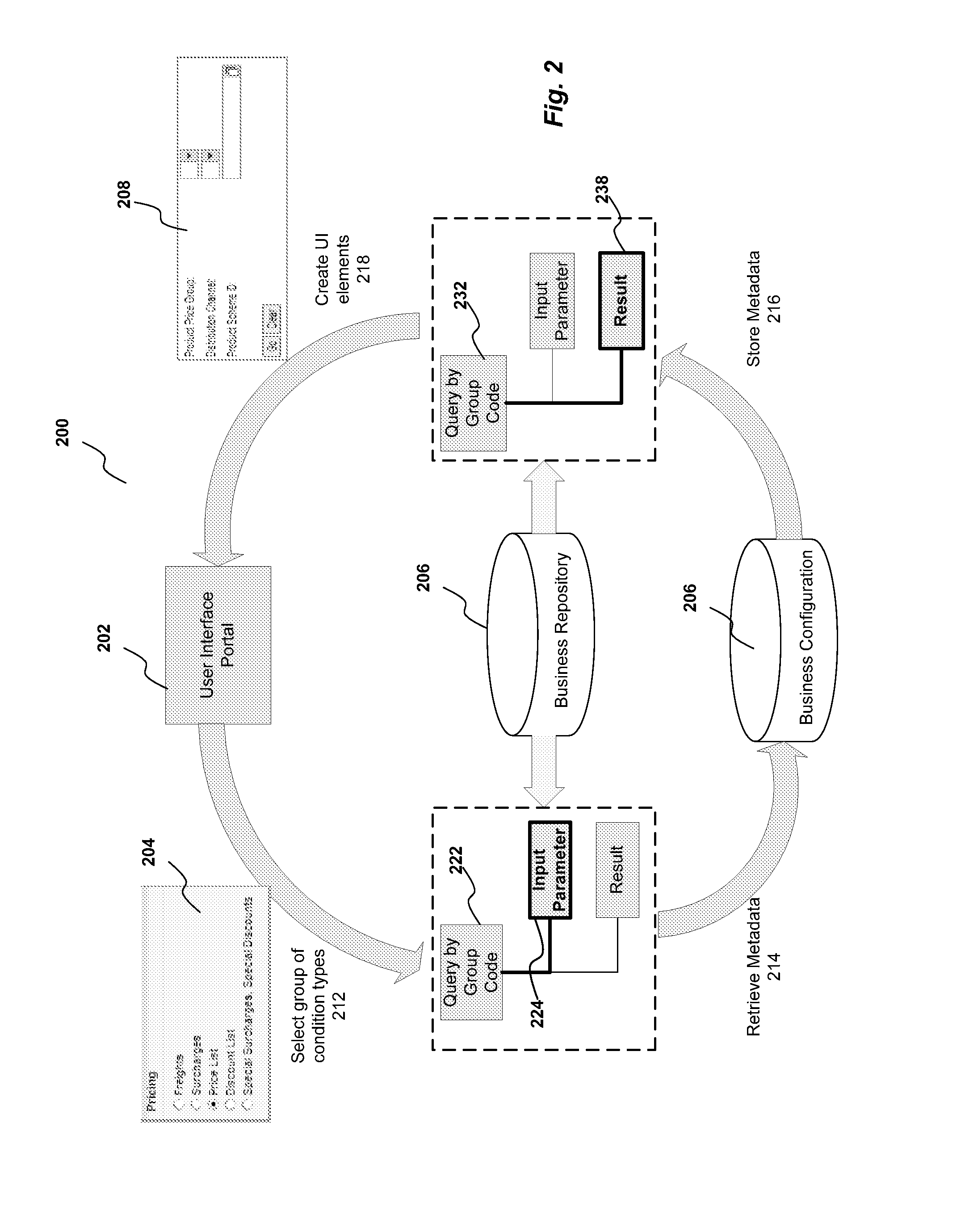
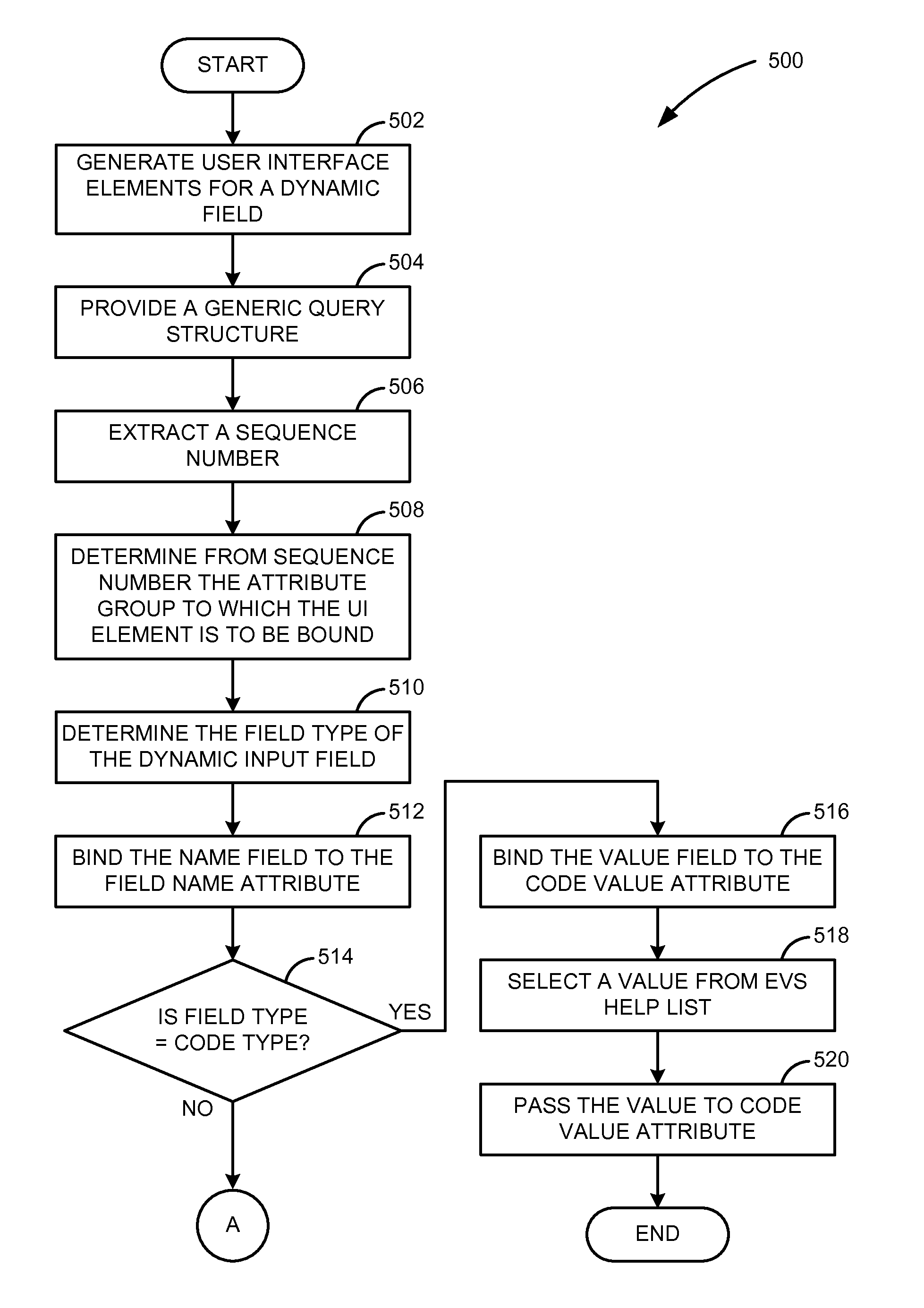
Method and system for providing value help features to input fields generated for dynamically selected columns
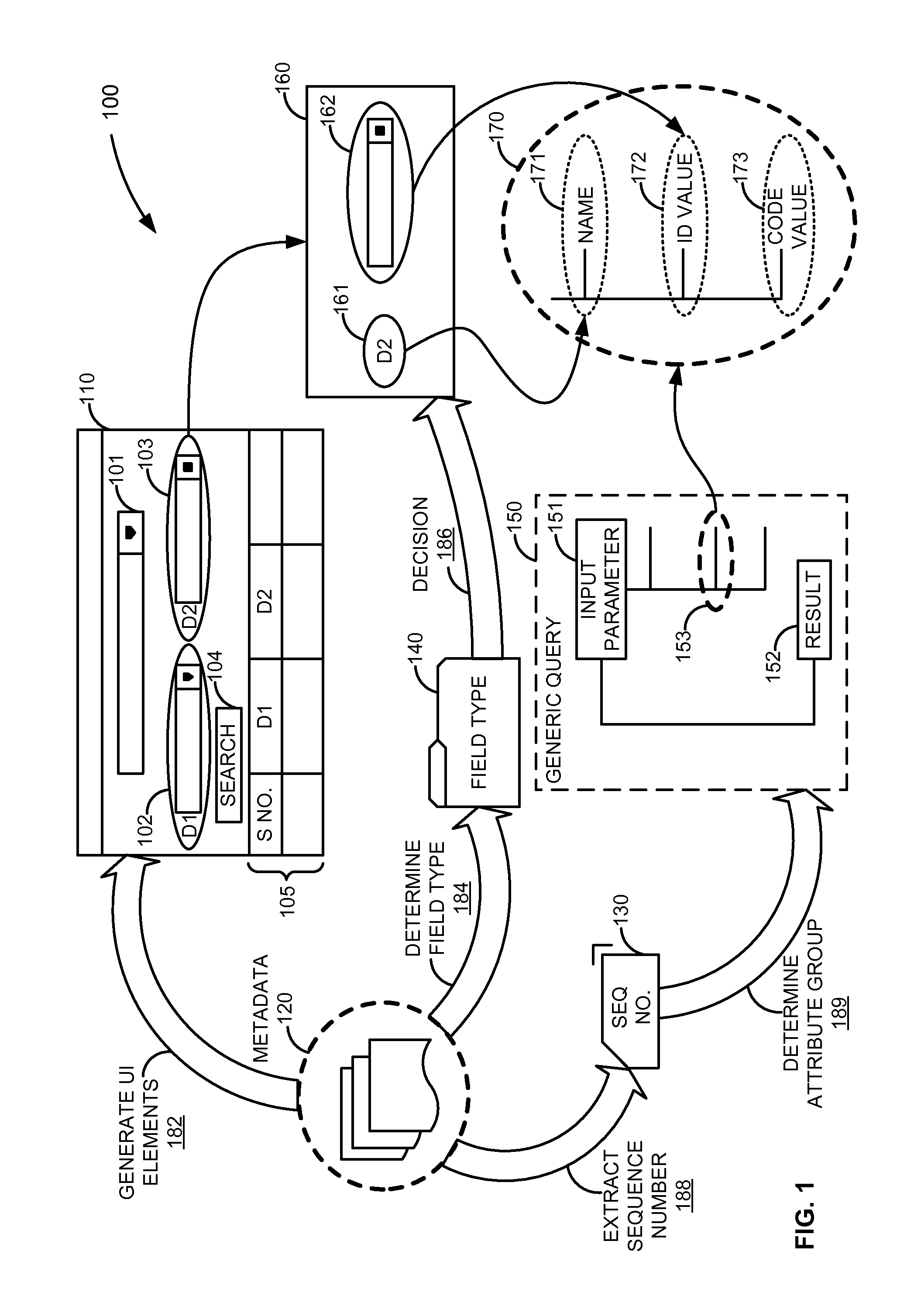
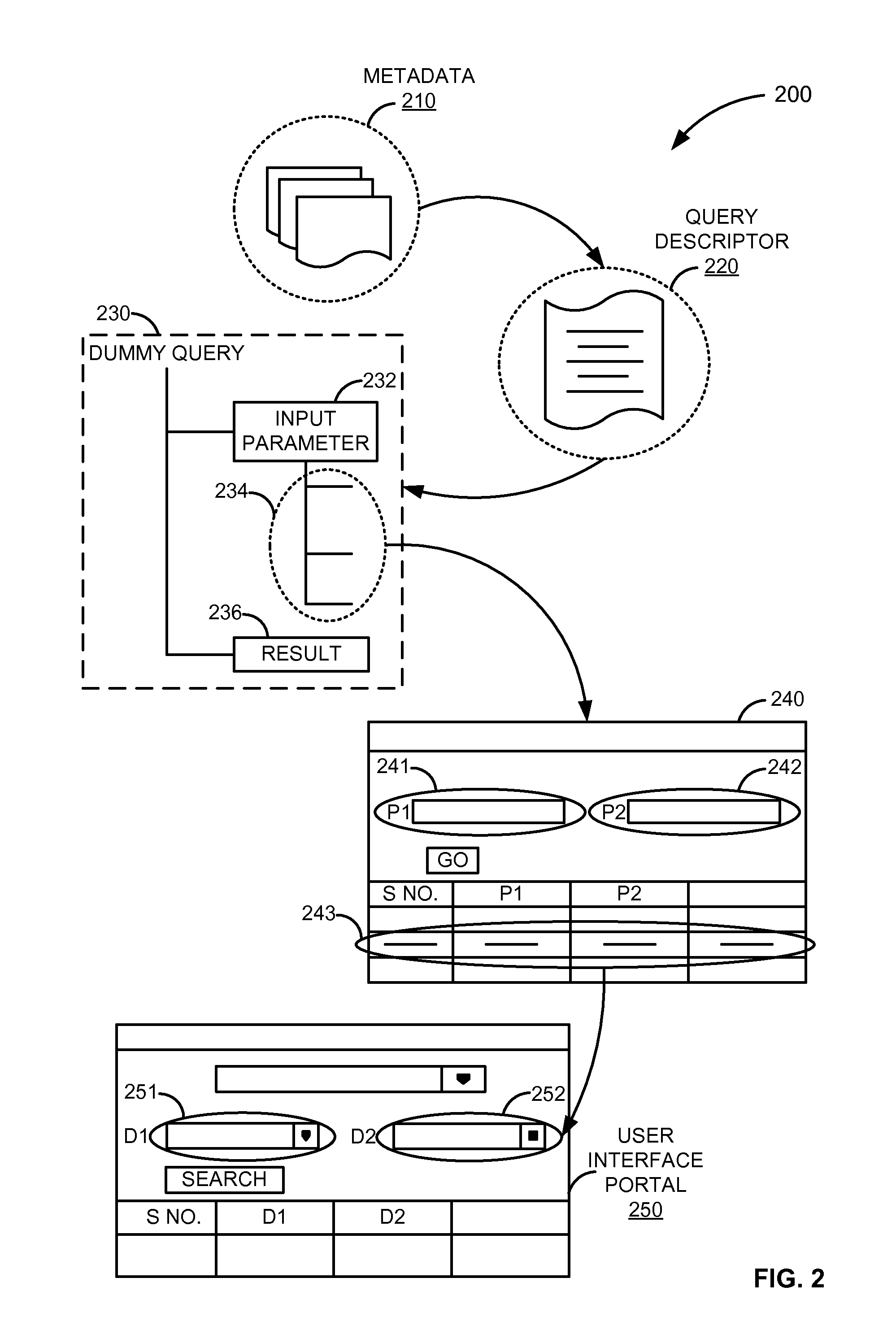
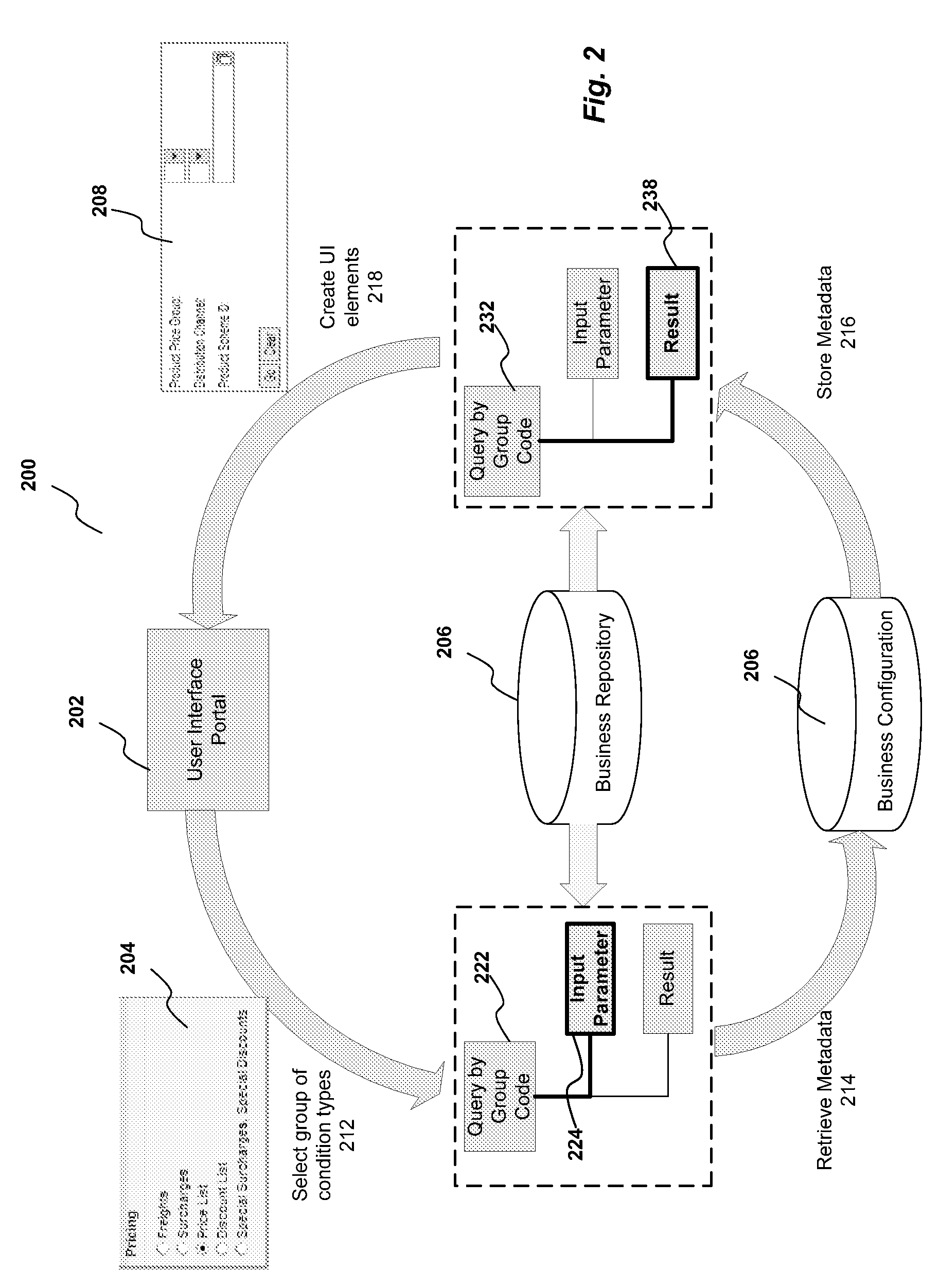
ActiveUS7865531B2Digital data information retrievalDigital data processing detailsData miningStatic key
Described are methods and systems for providing value help features to input fields. In response to a user selection of a condition type, an associated metadata is retrieved. Based upon the metadata, a user interface element comprising a static key and a dynamic key is generated. The dynamic key includes a name field and a value input field. Based upon the user interface element, a generic query including an input parameter node and a result node is generated. For the name field and the value input field of the dynamic key, a sequence number indicating an associated attribute group is extracted from the metadata. Based upon a field type of the value input field, the user interface element is bound to the associated attribute group indicated by the sequence number. Based upon the user entry received at the value input field, a corresponding value help feature is displayed.
Owner:SAP AG
Method for implementing efficient and safe transmission of data between cloud computing servers
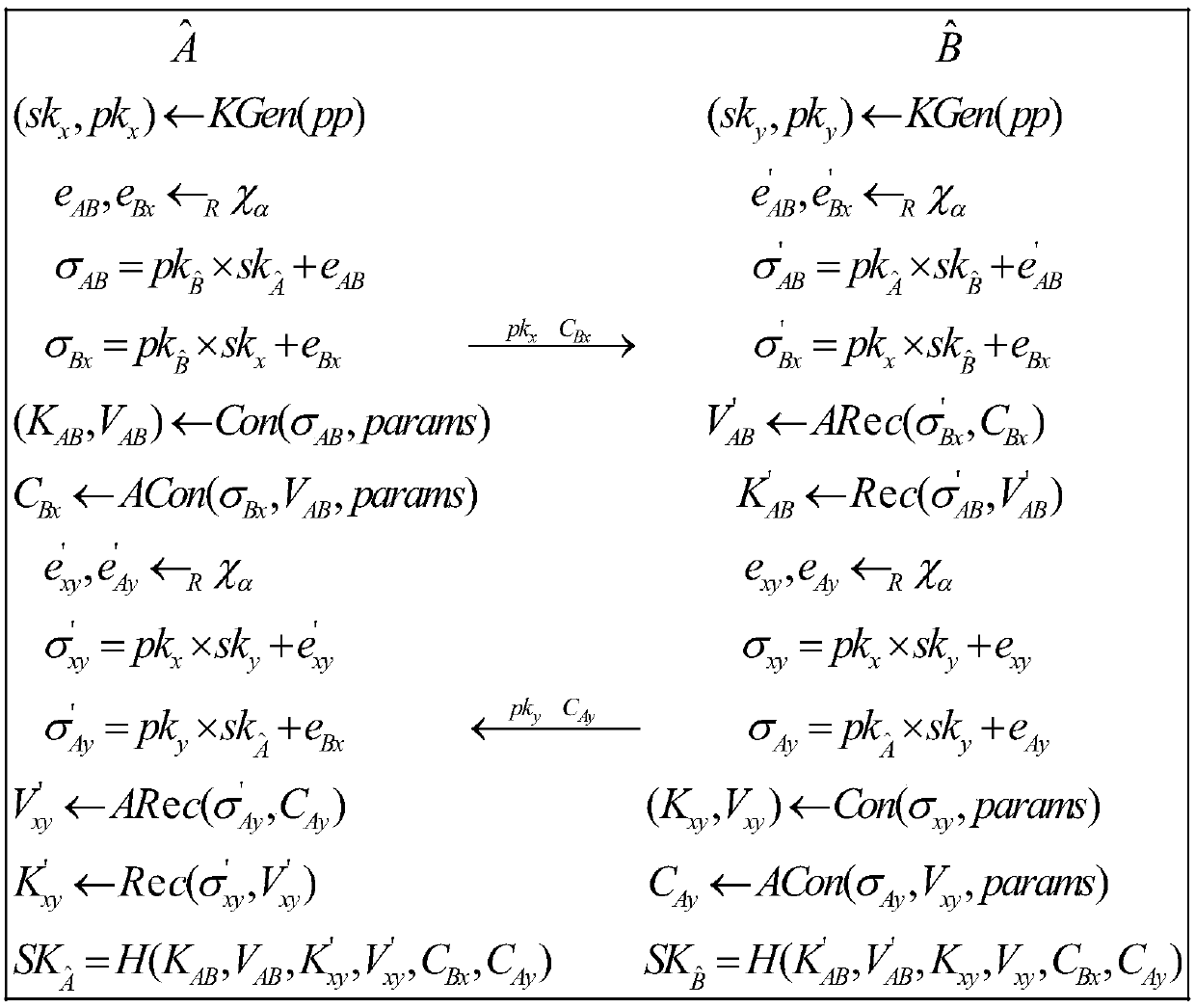
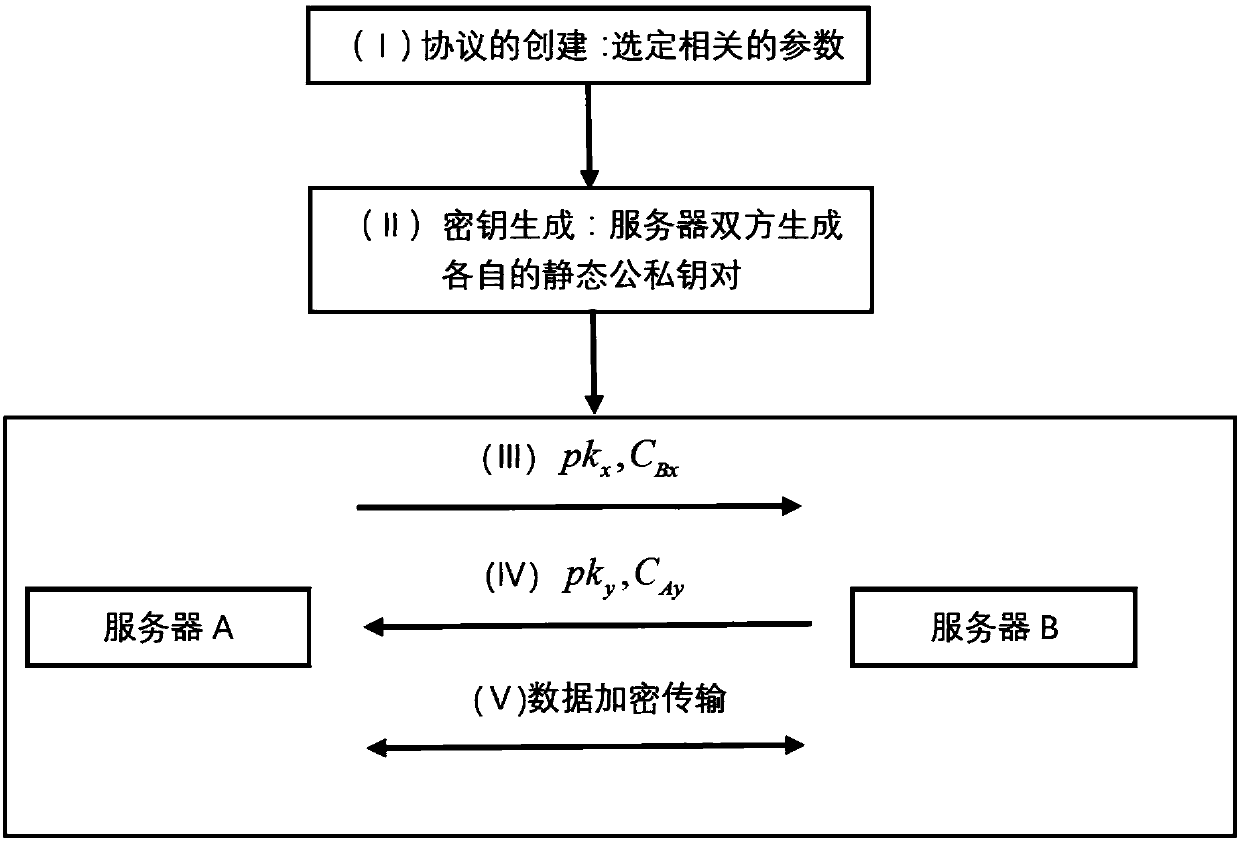
InactiveCN108599923AResistant to Quantum AttacksGood symmetryKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionSecure transmission
The invention discloses a method for implementing the efficient and safe transmission of data between cloud computing servers, and the method comprises the following steps: S1, protocol creating: enabling a system to select Rq=Zq[x] / (xn+1) as a quotient ring with the modulus being a positive integer, selecting a Gaussian distribution Chi*alpha with the standard deviation alpha on Zn and the mean value 0, selecting expressions (shown in the description) as an anti-collision hash function and defining a common parameter pp=(Rq, a, q, H, Chi*alpha), wherein n is a positive integer which is the positive integer power of 2; S2, static key pair generation: transmitting data between a server A<^> and a server B<^>, enabling the servers to generate respective static key pairs (shown in the description) through a secret key generation algorithm; S3, protocol execution: enabling a cloud computing server A<^> and the server B<^> to execute a protocol to finally obtain a shared session key (shownin the description) through negotiation; S4, data transmission: enabling the cloud computing server A<^> and the server B<^> to execute encrypted transmission of communication information through thegenerated session key (shown in the description) and a symmetric encryption algorithm. The method improves the safety through employing ACKN exchange and element encryption transmission while reducingbandwidth, and achieves the dual implicit authentication.
Owner:SOUTH CHINA NORMAL UNIVERSITY
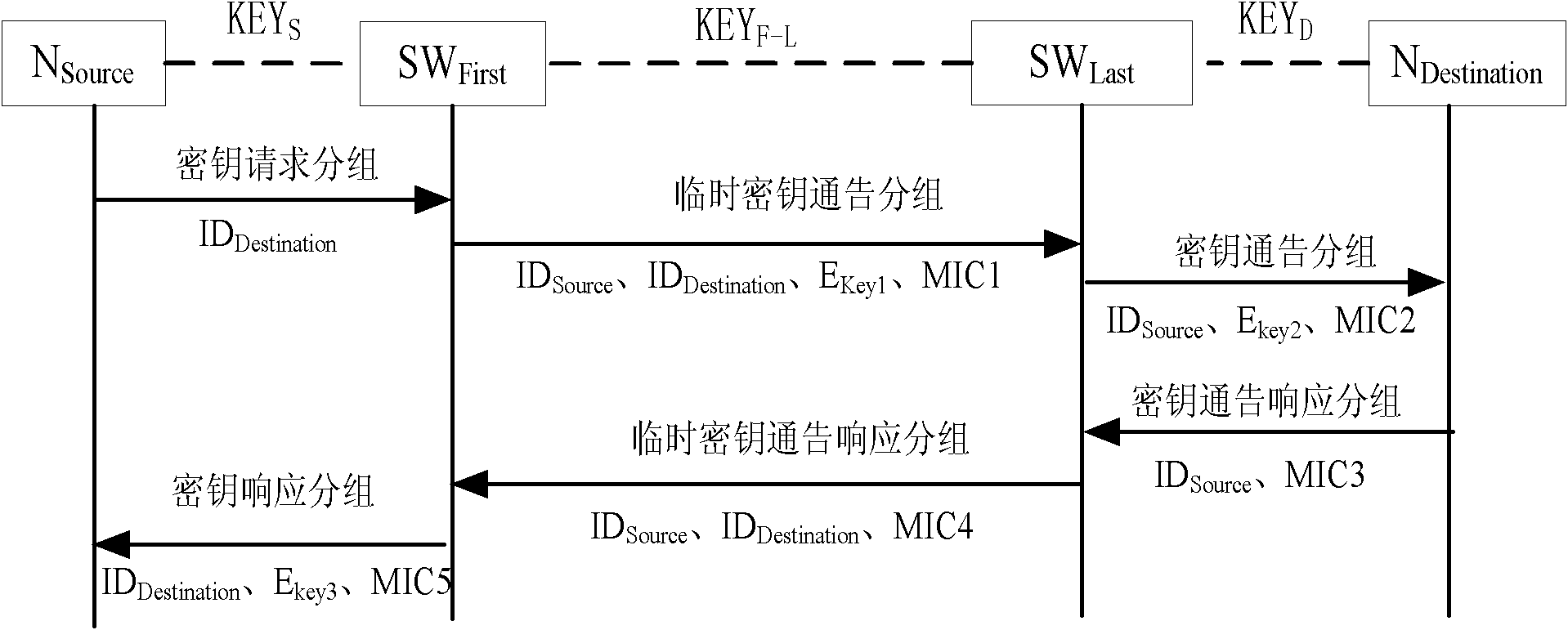
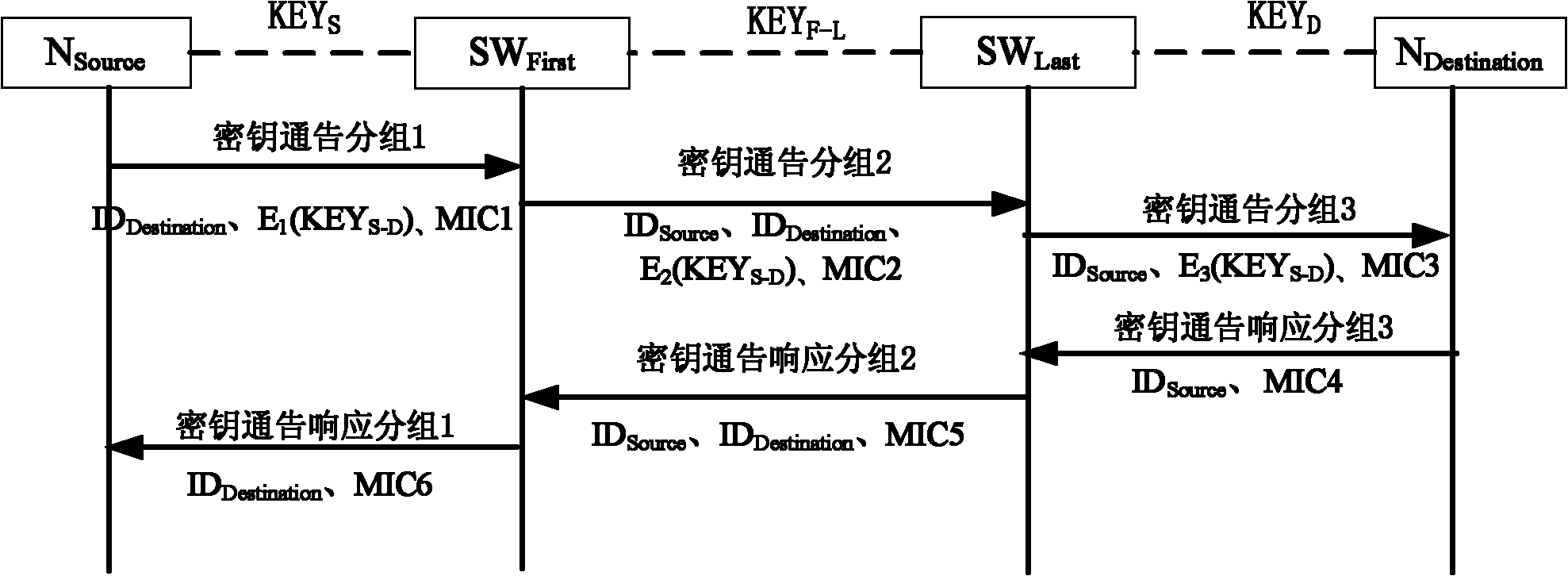
Method and system for establishing key between nodes
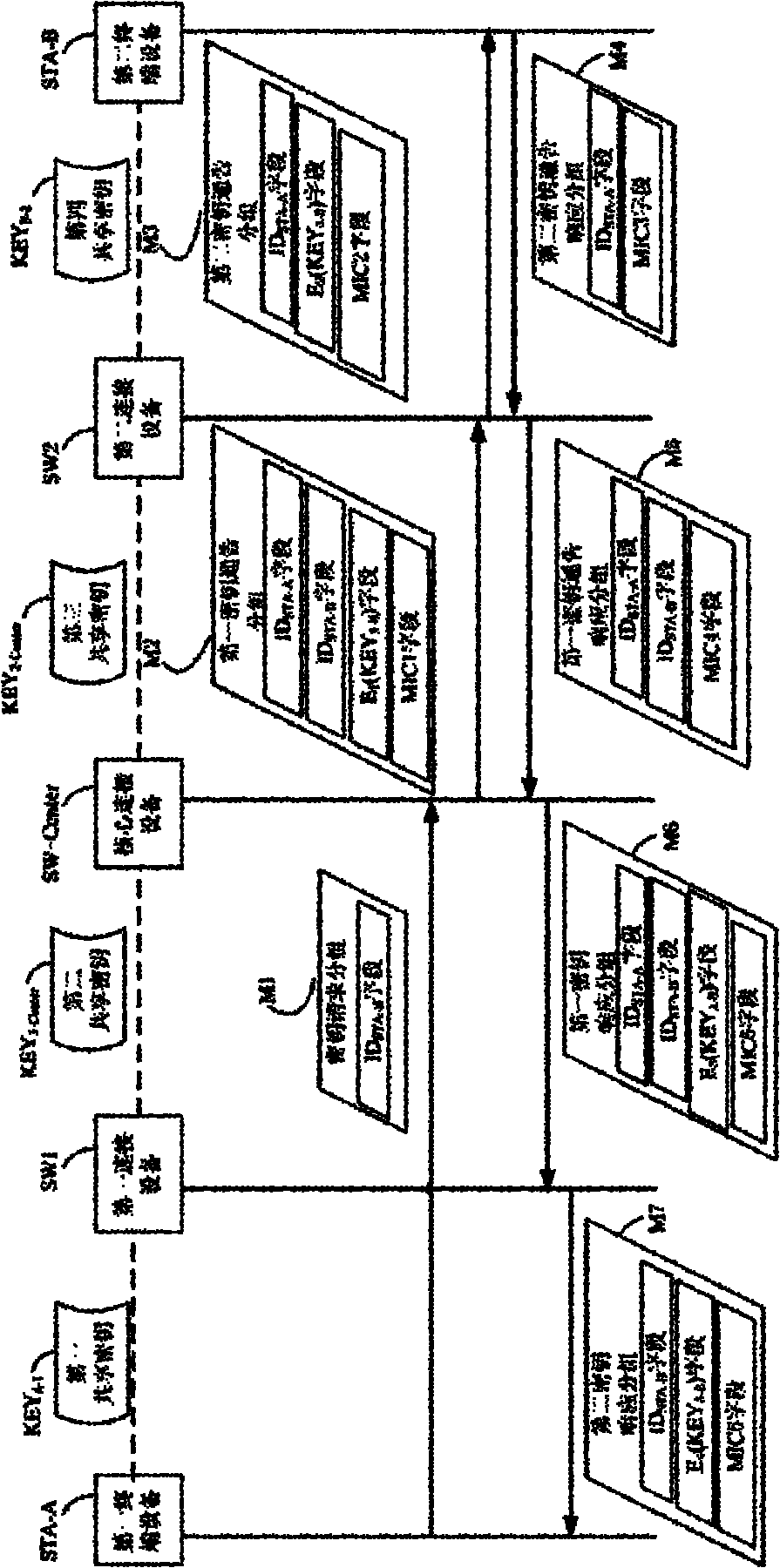
ActiveCN101814987ARekeyUpdate flexibleKey distribution for secure communicationData switching networksComputer scienceStatic key
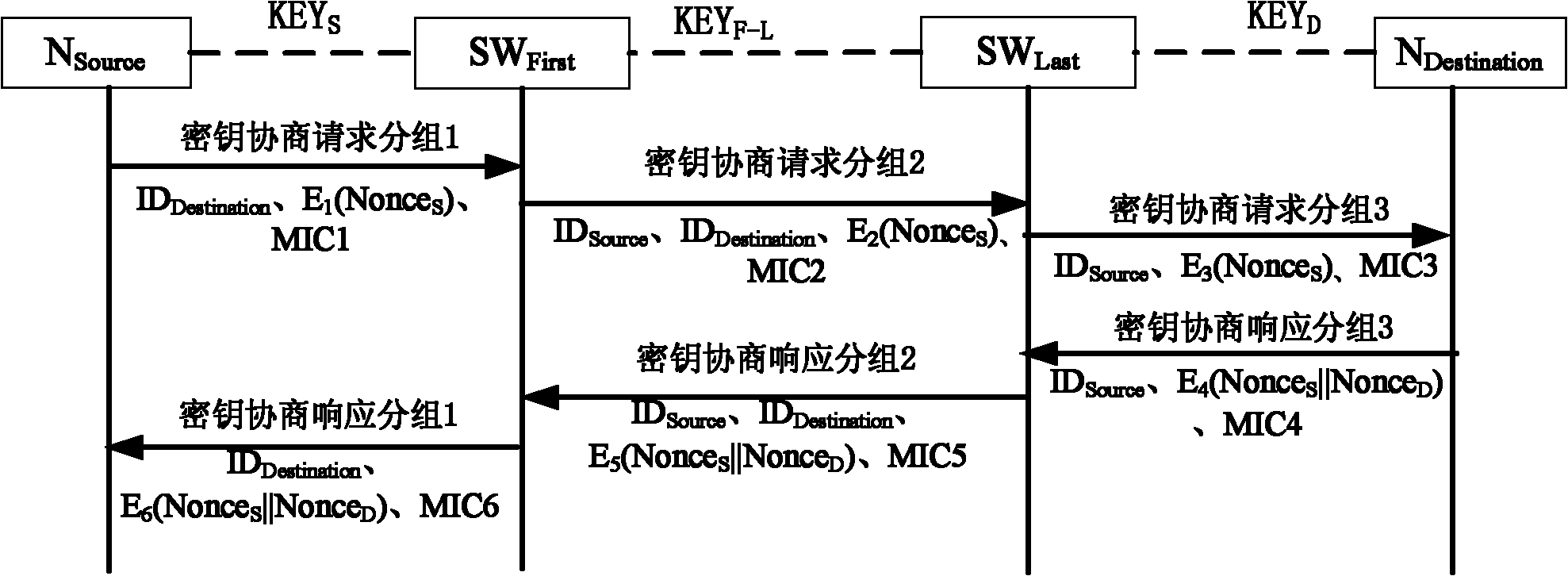
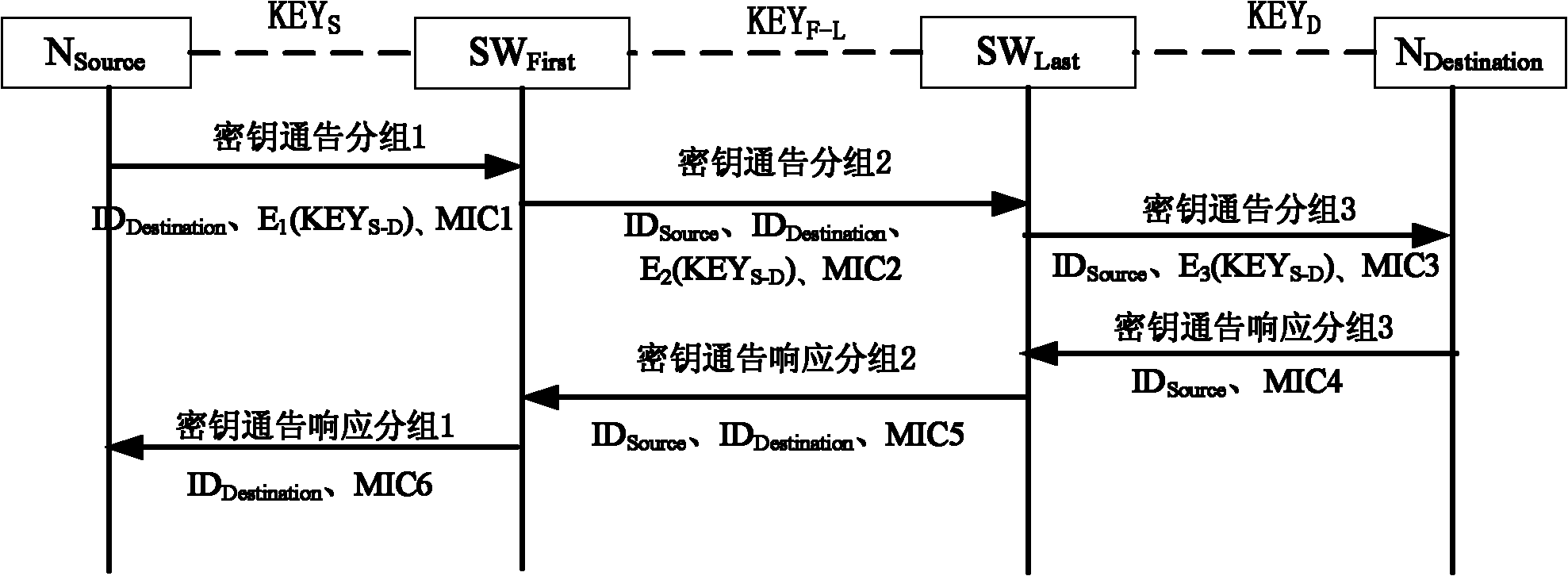
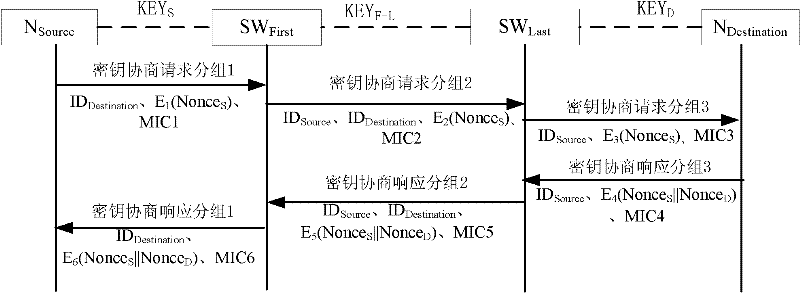
The invention discloses a method for establishing a key between nodes. The method comprises the following steps that: 1) a sending source node NSource sends a first key negotiation request packet to switching equipment SWFirst; 2) the switching equipment SWFirst sends a second key negotiation request packet to switching equipment SWLast; 3) the switching equipment SWLast sends a third key negotiation request packet to a destination node NDestination; 4) the destination node NDestination sends a third key negotiation response packet to the switching equipment SWLast; 5) the switching equipment SWLast sends a second key negotiation response packet to the switching equipment SWFirst; 6) the switching equipment SWFirst sends a first key negotiation response packet to the sending source node NSource; and 7) the sending source node NSource receives the first key negotiation response packet. The key between legal nodes of a local area network can be flexibly established and updated, and a manager does not need deploying a shared static key pair between every two nodes of the total network.
Owner:CHINA IWNCOMM
Apparatus and method for handling special windows in a display
InactiveUS20090037819A1Easy to detectEffective presentationCharacter and pattern recognitionCathode-ray tube indicatorsComputer hardwareWindow manager
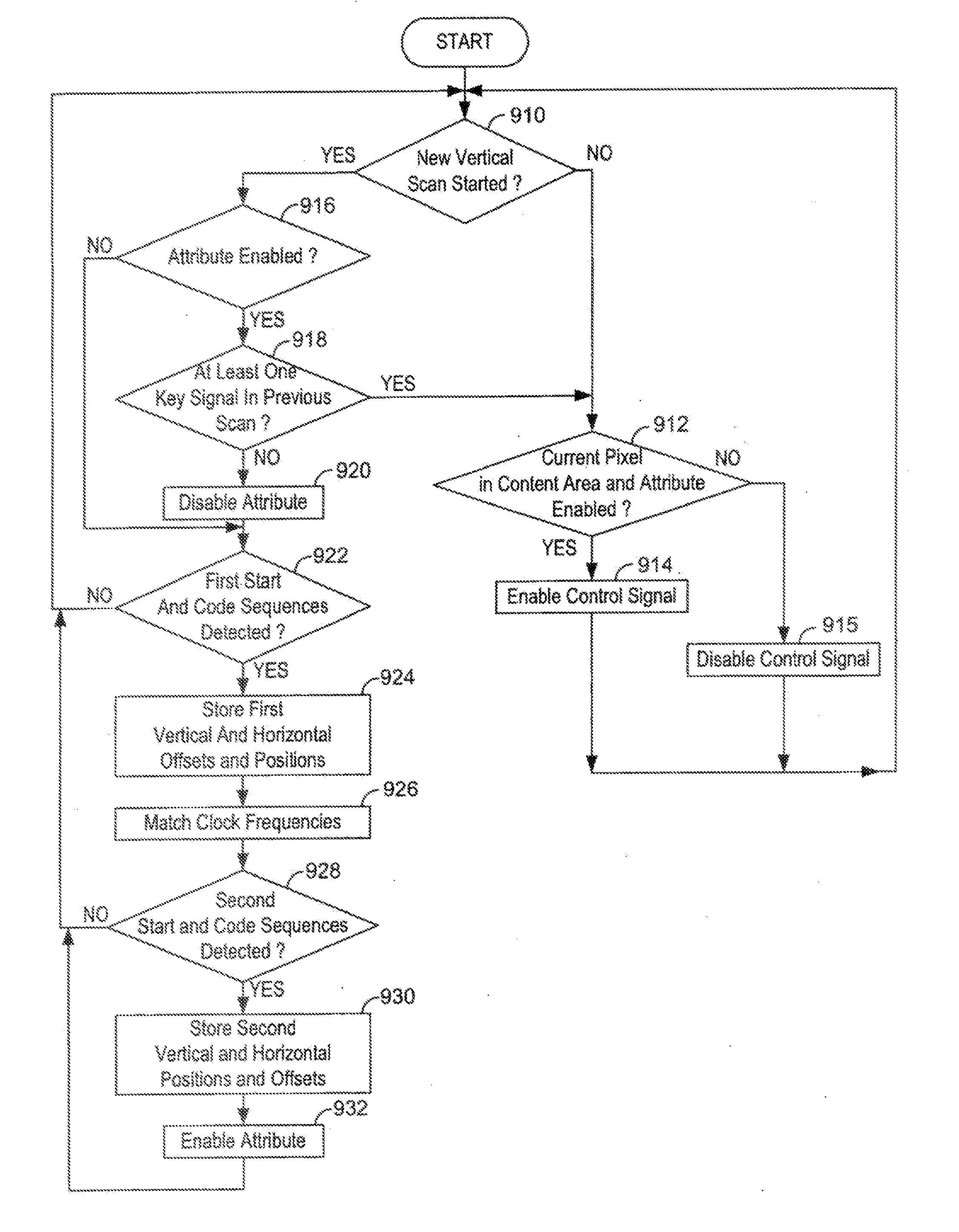
An apparatus and method for handling special windows in a display comprises a window manager in an operating system that is called by application programs to create special windows. The window manager embeds static key signals including encoded special window information, such as the coordinates of a window area to be specially processed, into a video RAM. An existing video interface scans the video RAM and transmits display information, including the key signals, to the display. The present invention further comprises a window decoder in the display, that detects the key signals, extracts the encoded special window information, and controls display circuitry performing the desired special processing. The key signal encoding scheme does not create visually discernible display aberrations that could distract the user or interfere with normal window management.
Owner:APPLE INC
Talking multi-surface keyboard
InactiveUS20150261312A1Input/output for user-computer interactionDigital data processing detailsTouchpadEngineering
An advanced portable keyboard comprising of a method of providing an interface for receiving contact information indicative of points of contact between parts of an operator's hand and one or a plurality of touch-sensitive pads built on the front surface, one or a plurality of back surfaces, and edges, interacting with one or a plurality of computers or computer-driven appliances.A mechanism mapping a plurality of interface elements onto touch-sensitive pads and static keys, each element corresponding to a key on a computer keyboard, each element being associated with one of the fingers of the operator, each element is mapped recurrently and dynamically, and activated by respective finger.A mechanism to read and / or pronounces letters, words, errors, actions, transcribe voice to text, and to switch touch pads into mouse pads at different operational modes, thus, providing faster speed, healthier posture, and greater efficiency.
Owner:GIRAGOSSIAN HOVSEP
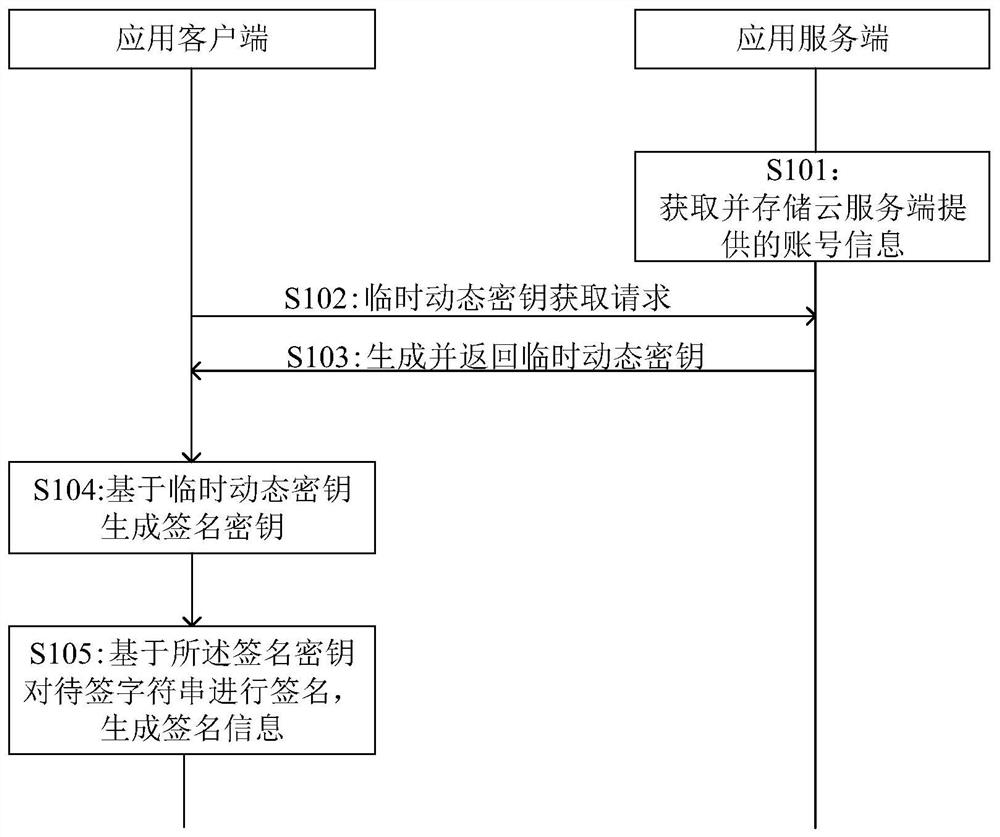
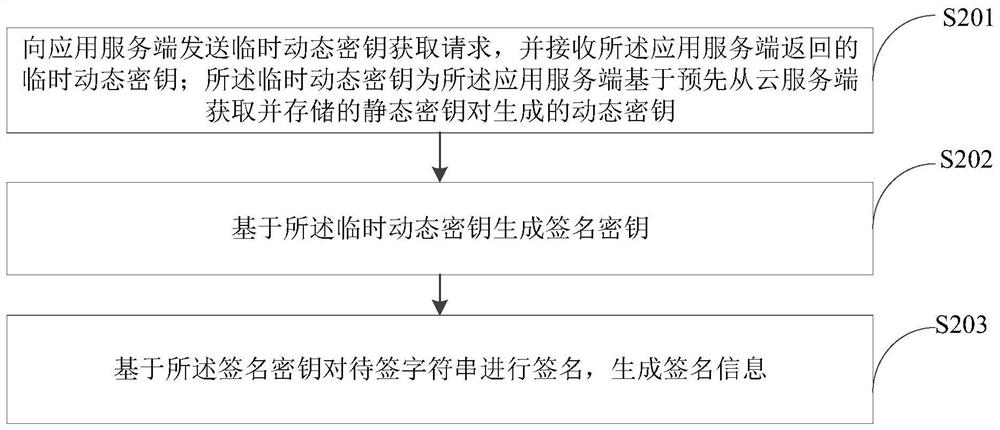
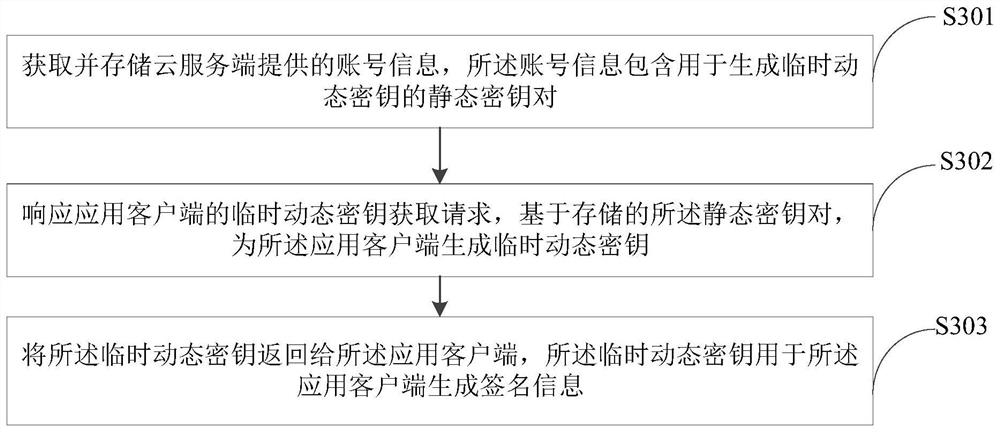
Signature method and device, computer equipment and storage medium
ActiveCN112003706AImprove securityShorten the signature pathKey distribution for secure communicationUser identity/authority verificationApplication serverDatabase
The invention provides a signature method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining and storing account information provided by a cloud server,and enabling the account information to comprise a static secret key pair for generating a temporary dynamic secret key; in response to a temporary dynamic key acquisition request of an application client, generating a temporary dynamic key for the application client based on the stored static key pair; and returning the temporary dynamic key to the application client, wherein the temporary dynamic key is used for the application client to generate signature information. According to the embodiment of the invention, the application client can obtain the temporary dynamic key through the corresponding application server for subsequent signature authentication, a remote request does not need to be initiated to the cloud server, the signature path is shortened, and the access efficiency is improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method and system for displaying results of a dynamic search
ActiveUS7617236B2Data processing applicationsDigital data information retrievalTheoretical computer scienceStatic key
A method and system for displaying results of a dynamic search are provided. Results of a search are received in a result node of a query wherein the result node comprises a first node and a second node. The first node has a static key data and the second node has a dynamic key data. The static key data and the dynamic key data are transferred to a dummy node. A table displaying the static key data and the dynamic key data is then generated based upon the dummy node.
Owner:SAP AG
Method for locking telecontroller
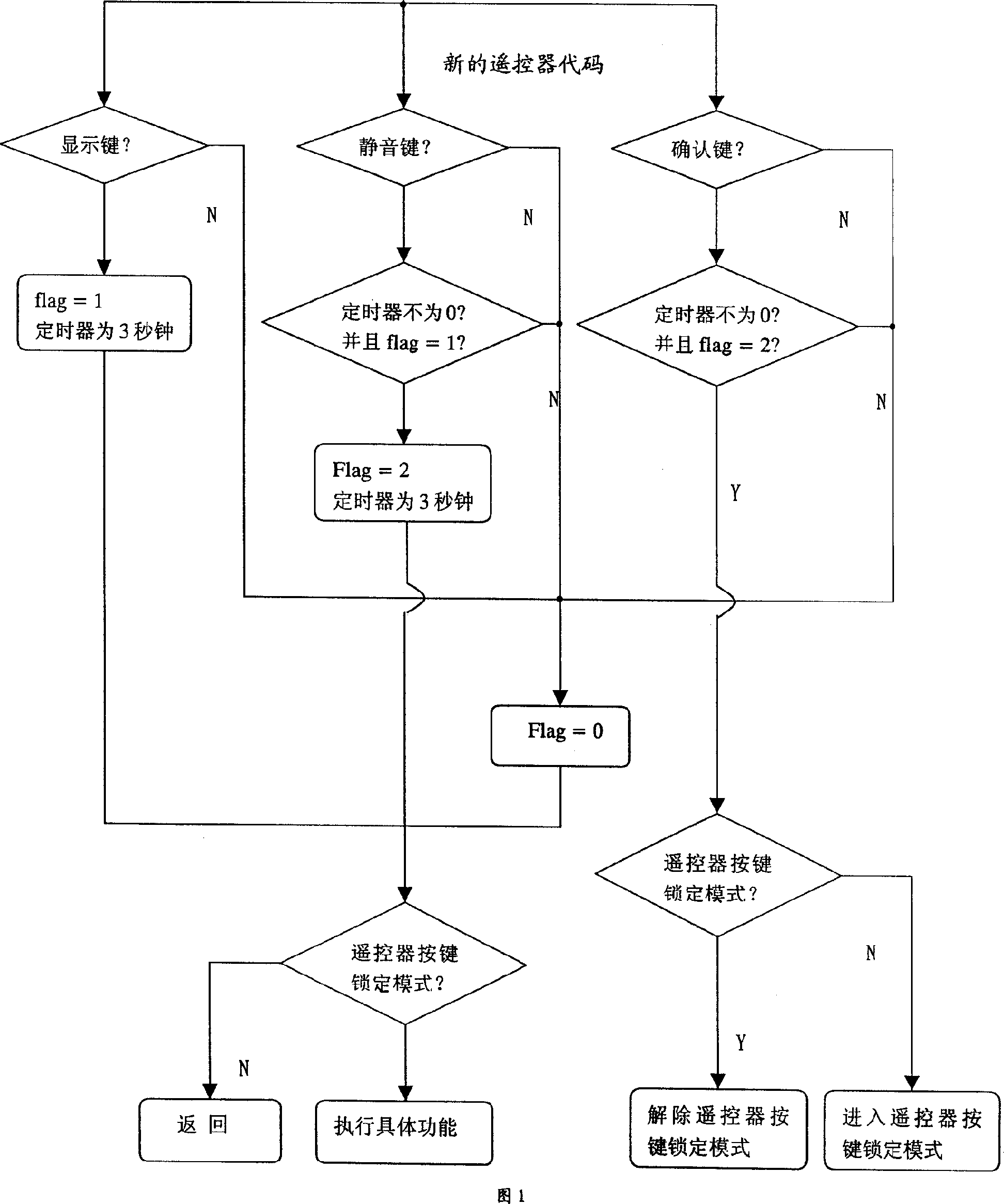
InactiveCN1979360AAvoid misuseReduce workloadTelevision system detailsColor television detailsKey pressingEngineering
The invention discloses a remote controller locking method, making a TV set remote controller have locking function. And the concrete method: in a normal power-on state, pressing display key and then pressing static key within three seconds, then pressing confirm key within three seconds, and thus completing the setting of key locking function of the remote controller. And releasing the key locking function also needs the same operating method. When inputting combined keys, if other keys but the combined keys are pressed or the key-pressing time interval exceeds three seconds, it will restore to the initial state and this operation is cancelled and the combined keys need to be inputted again. Thus, we can give the remote controller to children to play or thoroughly put an end to mis-operation.
Owner:TIANJIN SAMSUNG ELECTRONICS CO LTD
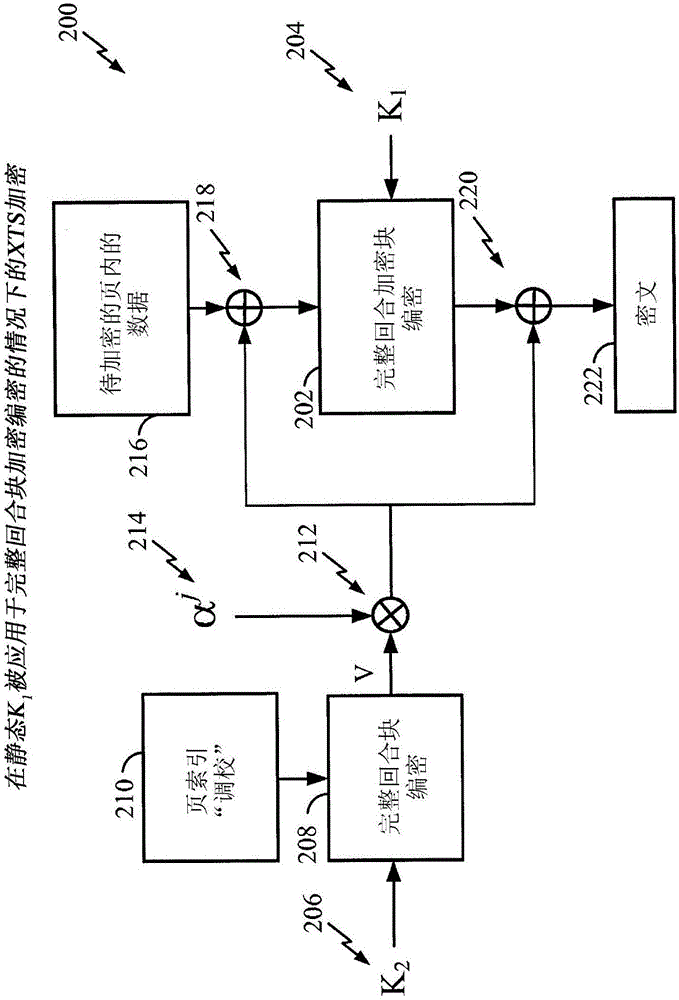
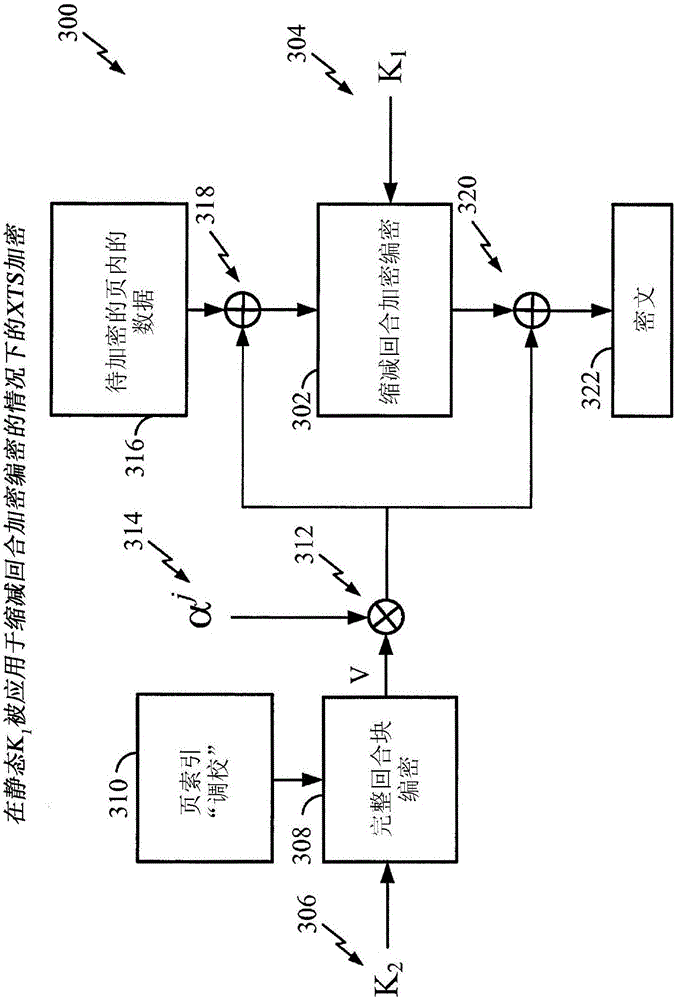
Dynamic encryption keys for use with XTS encryption systems employing reduced-round ciphers
InactiveCN106105089AKey distribution for secure communicationMultiple keys/algorithms usageConfidentialityStatic key
One feature pertains to encrypting data to improve data confidentiality. In one aspect, a modified form of XTS encryption is provided for use with reduced-round block ciphers. A data unit index of data to be applied to the reduced-round cipher is encrypted under a secret key to generate or otherwise obtain a modified secret key for applying to the reduced-round cipher. That is, data to be encrypted by the reduced-round cipher is not encrypted under a static key but is instead encrypted under a dynamic key that varies according to the index of the data. If an attacker were to derive the value of the key applied to the reduced-round cipher by analyzing data encrypted by the cipher, the attacker would only obtain the dynamic key corresponding to one particular data unit index, rather than a global static key applied to an entire address space. Decryption procedures are also described.
Owner:QUALCOMM INC
Symmetric key dynamic generation method based on Internet of Things
ActiveCN114024724AAvoid gettingEnsure safetyKey distribution for secure communicationHigh level techniquesCiphertextThe Internet
The invention discloses a symmetric key dynamic generation method based on the Internet of Things. According to the method, generated byte arrays are adopted as a part of symmetric encryption keys; the keys, terminal SNs and version numbers are correspondingly persistently stored in a cloud end; terminals prefabricate and store the part of symmetric encryption keys and the version numbers; the other part of keys are dynamically generated and transmitted to the cloud end or the terminals together with ciphertexts and the version numbers; and when the keys are used, the dynamic keys and the previous static keys are combined into complete keys for decryption. According to the method, key dynamic generation is combined with prefabricating a part of keys in advance, so that different keys of different terminals can be realized, the condition that other terminal ciphertexts can be obtained after one terminal key is cracked is prevented, and the safety of the ciphertexts is ensured.
Owner:四川启睿克科技有限公司
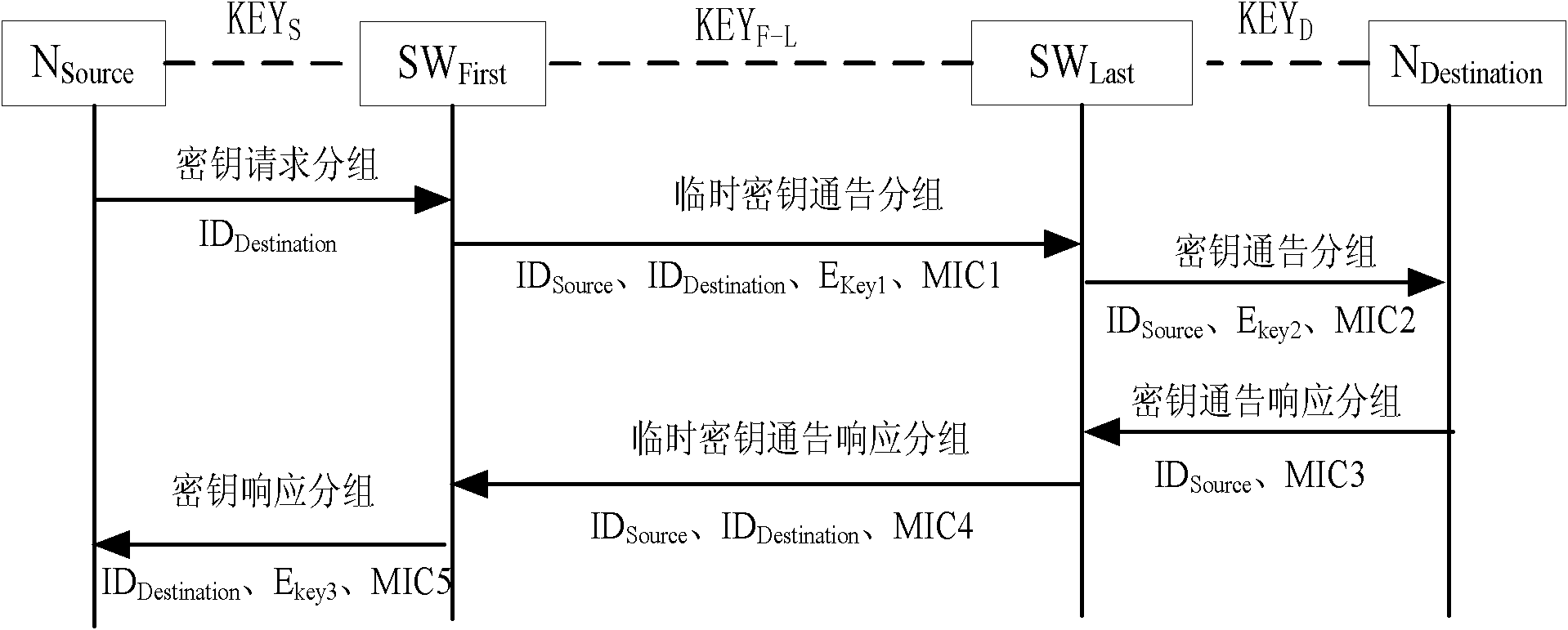
Method and system for establishing communication key between nodes
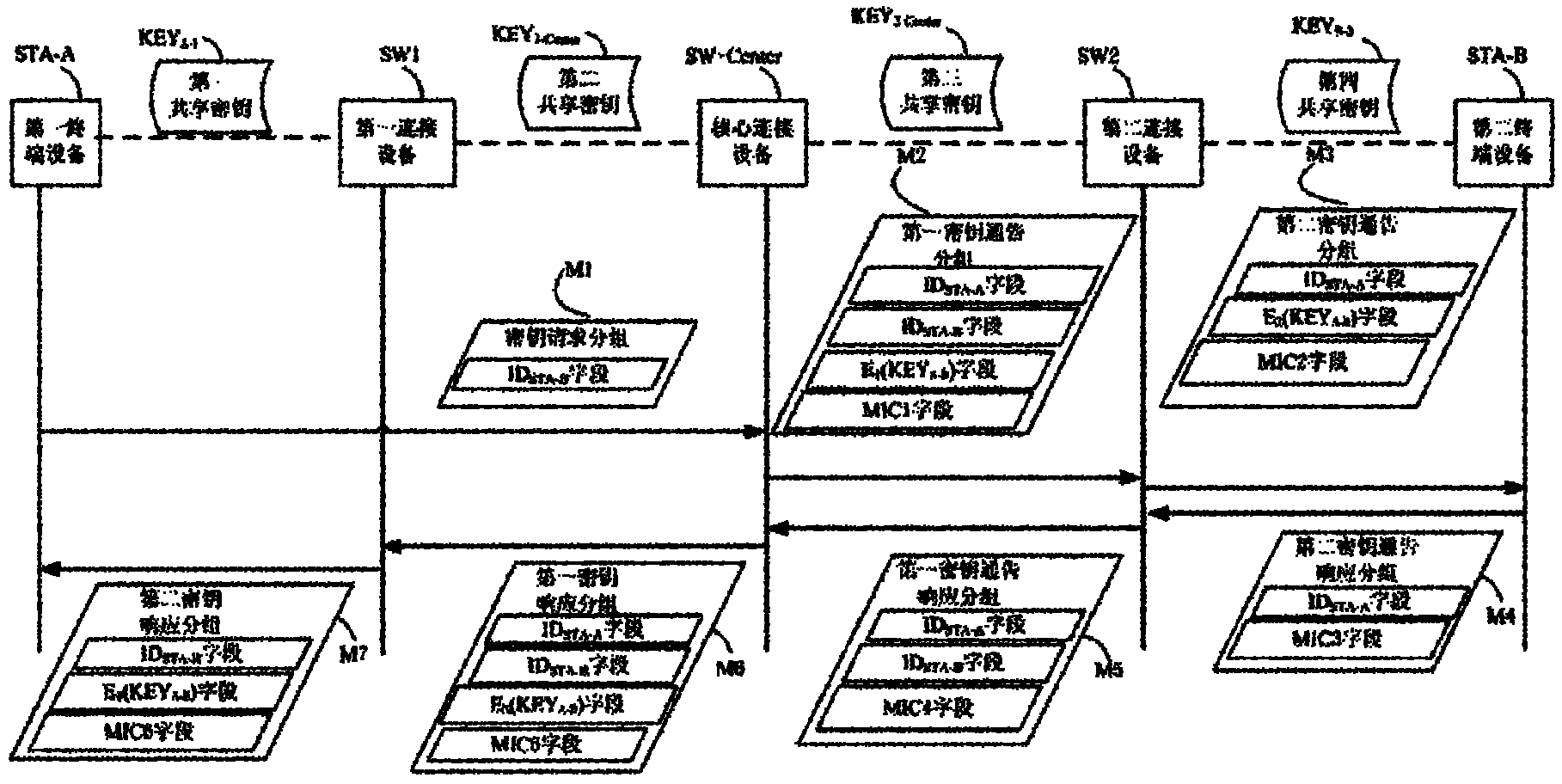
ActiveCN101902324AMultiple keys/algorithms usageData switching by path configurationTelecommunicationsStatic key
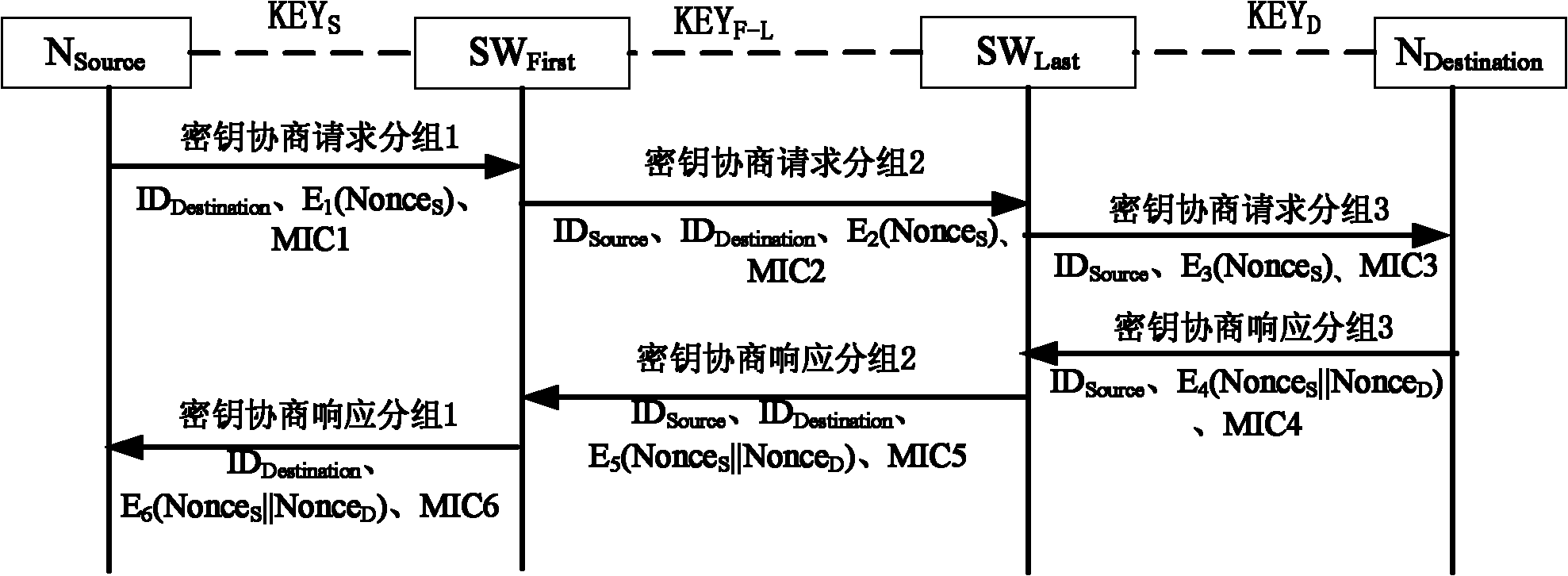
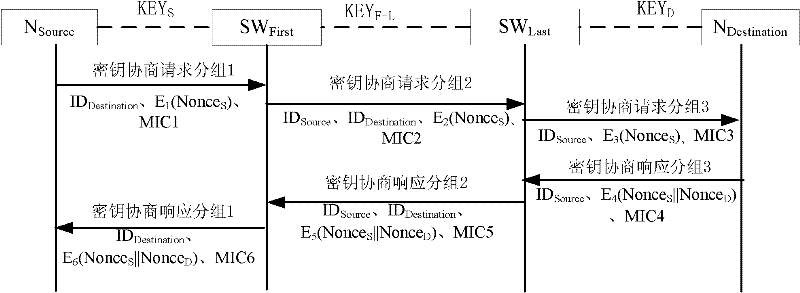
The invention relates to a method for establishing a communication key between nodes, comprising the following steps: 1) an N source sends a first key announce subgroup to an SW First; 2) the SW First sends a second key announce subgroup to an SW Last; 3) the SW Last sends a third key announce subgroup to an N Destination; 4) the N Destination sends a third key announce responding subgroup to the SW Last; 5) the SW Last sends a second key announce responding subgroup to the SW First; 6) the SW First sends a first second key announce responding subgroup to the N source; and 7) the N source receives the first second key announce responding subgroup. By utilizing the method of the invention, the key between legal nodes in a local area network can be flexibly established or updated and no administrator is needed for deploying a shared static node between every two nodes in an entire network.
Owner:RADIOSKY TESTING SERVICES BEIJINGLTD +1
Secret key application method based on SM9 algorithm
ActiveCN112699394ATroubleshoot key escrow issuesTroubleshoot key updatesDigital data protectionAlgorithmKey escrow
The invention discloses a secret key application method based on an SM9 algorithm, and the method comprises the steps that a static secret key management center generates a static secret key of a user based on a user identification according to a secret key generation rule of the SM9 algorithm, and a dynamic secret key management center constructs a dynamic identification of the user through the user identification and a given dynamic change amount, and a dynamic key of the user based on the user dynamic identifier is generated; the user generates a static public key based on the static identifier of the communication opposite side, generates a dynamic public key based on the dynamic identifier of the communication opposite side, and realizes encryption or signature verification operation based on the static public key and the dynamic public key; a user acquires the static private key from the static secret key management center, acquires the dynamic private key from the dynamic secret key management center, and realizes decryption or signature operation based on the static private key and the dynamic private key. According to the key application method, an SM9 key security management mechanism based on SKGC and DKGC is provided, and the problems of key escrow, update and revocation of an SM9 algorithm can be solved.
Owner:FUJIAN NORCA TECH
Method and device for encrypting and encapsulating two-dimensional code breast card with authority
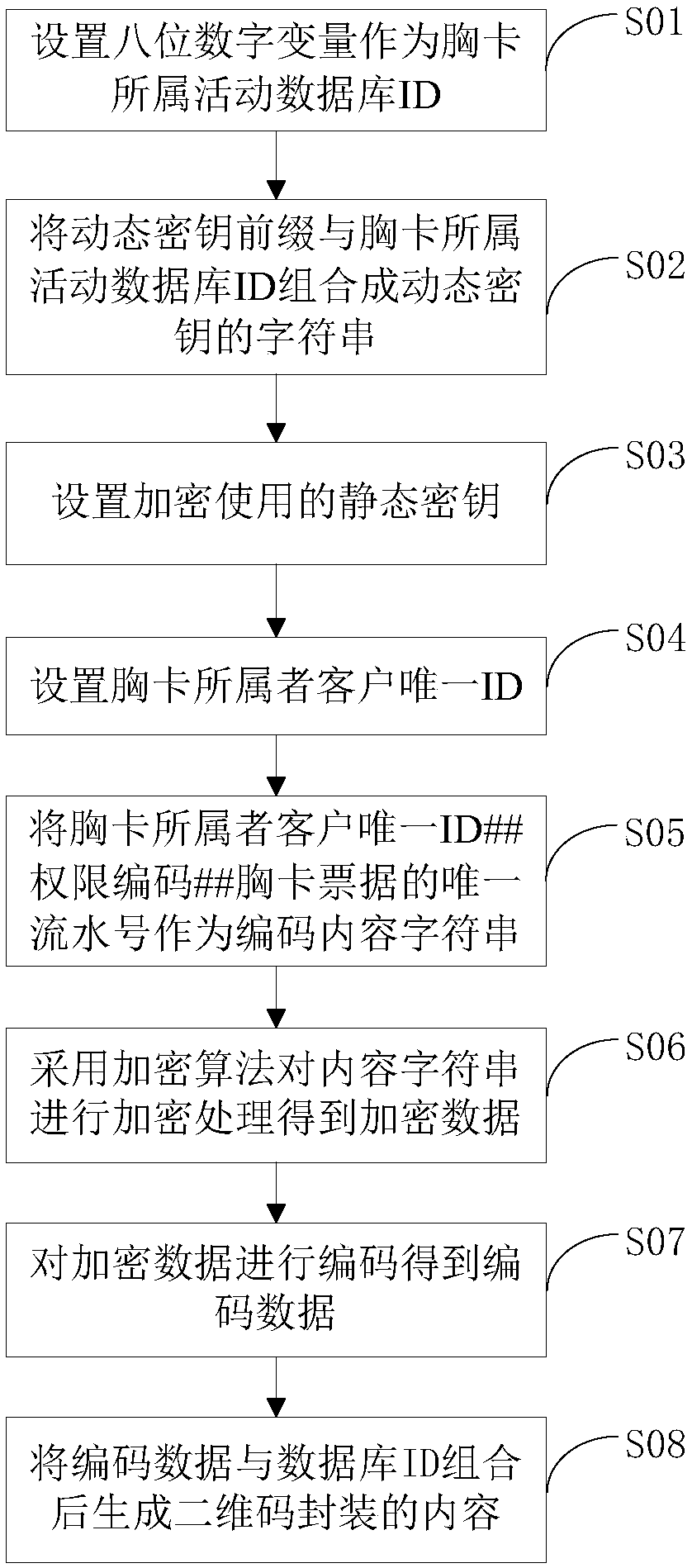
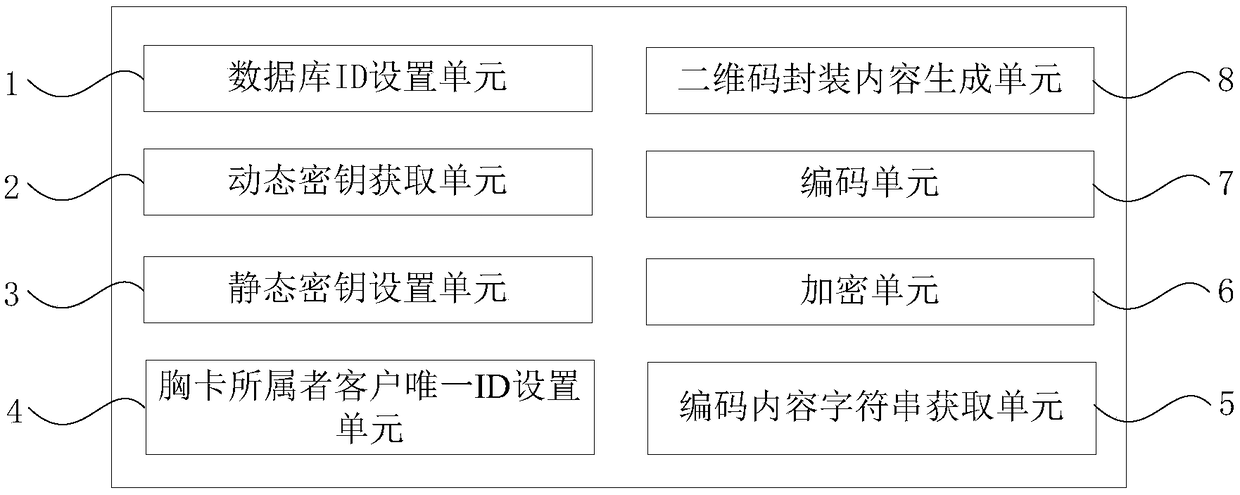
PendingCN109145635AAnti-counterfeitingReduce manufacturing costDigital data protectionRecord carriers used with machinesSerial codeStatic key
The invention discloses a method and a device for encrypting and encapsulating a two-dimensional code breast card with authority. The method comprises the following steps: setting eight-digit digitalvariables as an activity database ID belonging to the breast card; a dynamic key string being combined; setting the static key used for encryption; setting the unique ID of the customer to which the badge belongs; the unique ID # # permission code # # serial number of the badge ticket belonging to the badge customer being taken as the encoded content string; encrypting the content string to obtainencrypted data; encoding the encrypted data to obtain encoded data; combining the encoded data with the active database ID to which the badge belongs to generate two-dimensional code encapsulated content. The invention has the advantages of low production cost, anti-counterfeiting, high efficiency encapsulation of multiple conference authority, off-line authority correction, technical guarantee for on-site temporary blacklist and invalid badge, and the dynamic key composed of different SHOWIDs is suitable for large-scale standardized application, so as to distinguish different badge attributes of different activities and enhance anti-counterfeiting.
Owner:GUANGZHOU SHISHENG EXHIBITION
Secure communications providing forward secrecy
ActiveUS10313133B2Public key for secure communicationUser identity/authority verificationSecure communicationComputer hardware
Owner:VISA INT SERVICE ASSOC
Polarization code confidence propagation dynamic flipping decoding method based on key set
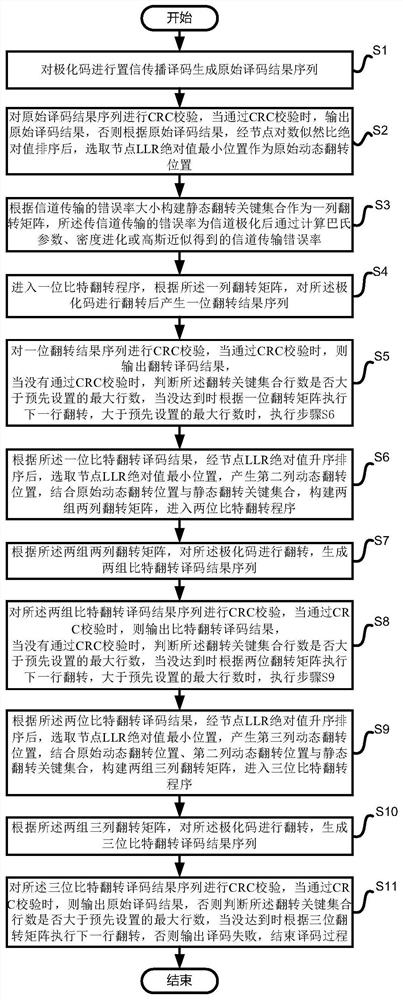
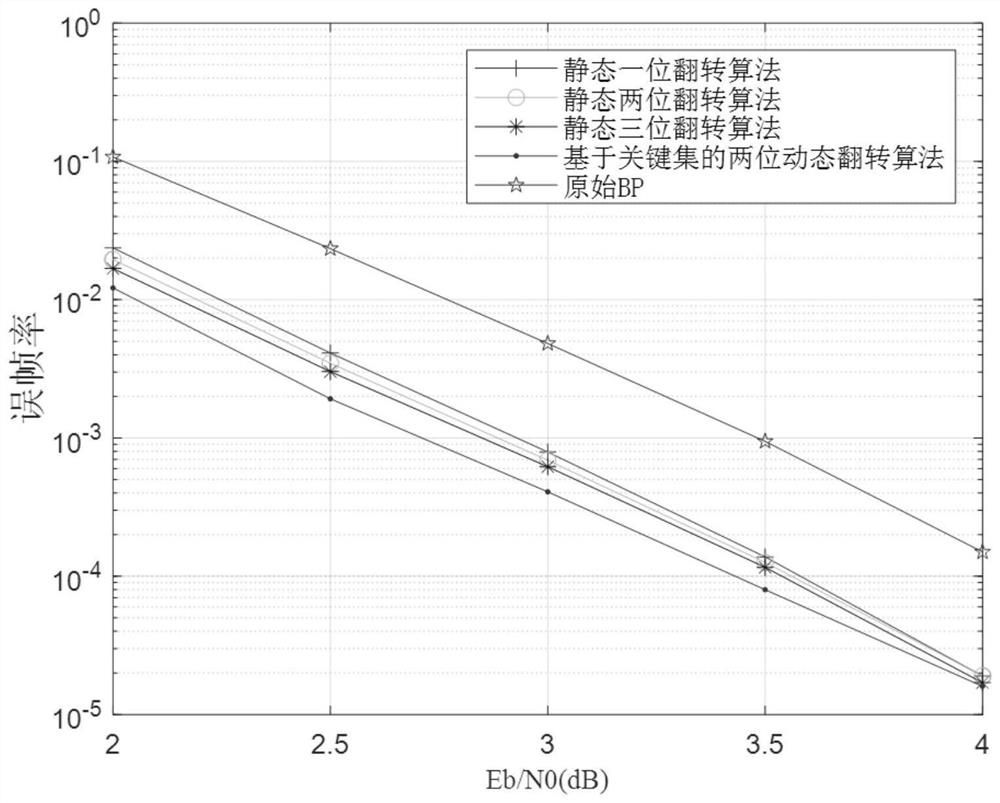
PendingCN112104379AImprove decoding performanceControlling and scaling down the number of multi-bit flip attemptsError correction/detection using linear codesTheoretical computer scienceEarly stopping
The invention provides a key set-based polarization code confidence propagation dynamic flipping decoding method, which comprises the following steps of: performing confidence propagation decoding ona polarization code, performing advanced cut-off judgment on a decoding result of each iteration in combination with a cyclic redundancy check auxiliary early stop standard to achieve a preset maximumiteration frequency and CRC (cyclic redundancy check) failure, and obtaining a decoding result of each iteration; and if not, generating a dynamic flipping position in combination with the absolute value of the log-likelihood ratio of the node, further constructing a flipping matrix in combination with the static key set, and improving the decoding performance through bit flipping. Simulation results show that under the condition that the frame error rate is 0.001 and the upset digit omega is 2, compared with a CS omega-based bit upset confidence propagation decoder, the key set-based polarization code confidence propagation dynamic upset decoding method improves the gain by about 0.17 dB, and compared with an original BP decoding algorithm, the key set-based polarization code confidencepropagation dynamic upset decoding method improves the gain by about 0.77 dB.
Owner:SHANDONG UNIV OF SCI & TECH
Centralized safety connection establishing system and method
ActiveCN101964802AGuaranteed confidential transmissionImprove transmission efficiencyKey distribution for secure communicationCiphertextTerminal equipment
The invention relates to centralized safety connection establishing system and method. The system comprises a terminal device and a connecting device, wherein the terminal device comprises an initiator terminal device and a receiver terminal device, the connecting device comprises a core connecting device, an initiator connecting device and a receiver connecting device, the initiator connecting device is arranged on a link between the initiator terminal device and the core connecting device, and the receiver connecting device is arranged on a link between the receiver terminal device and the core connecting device. The invention ensures that legal nodes of a local network can be flexibly established and keys among the legal nodes are updated for establishing safety connection among the legal nodes. The invention can be used for flexibly establishing the safety connection among the nodes without distributing static key pairs among the nodes of the local network, can ensure that the data among the nodes can be transmitted secretly through the safety connection among the nodes so that an attacker can not obtain real information even if information stolen by accessing into the networkis ciphertext information.
Owner:CHINA IWNCOMM
Graphic user interface apparatus of vehicle-mounted surround view system
InactiveCN105700777AImprove viewing angleThere will be no occlusionInput/output processes for data processingGraphicsContact position
The invention relates to a graphic user interface apparatus of a vehicle-mounted surround view system. The apparatus comprises a contact position acquisition module, a static key operation module, a menu operation module, a display module and a data storage module, wherein the contact position acquisition module detects a contact position of a user and notifies a corresponding module to make a response; the contact position comprises a static key region, a dynamic key region and a menu region; the static key operation module makes a response to a contact signal of the user in the static key region; the dynamic key operation module makes a response to a contact signal of the user in the dynamic key region; the menu operation module makes a response to a contact signal of the user in the static key region; the display module performs corresponding 3D graph display according to a response signal of the static key operation module, the dynamic key operation module or the menu operation module; and the data storage module stores data of the vehicle-mounted surround view system and an input number of the user. Compared with the prior art, the apparatus has the advantages of simplicity for operation, intuitiveness, wide view angle, capability of supporting custom operation and the like.
Owner:DELPHI ELECTRONICS SUZHOU
Encryption method and device, equipment and storage medium
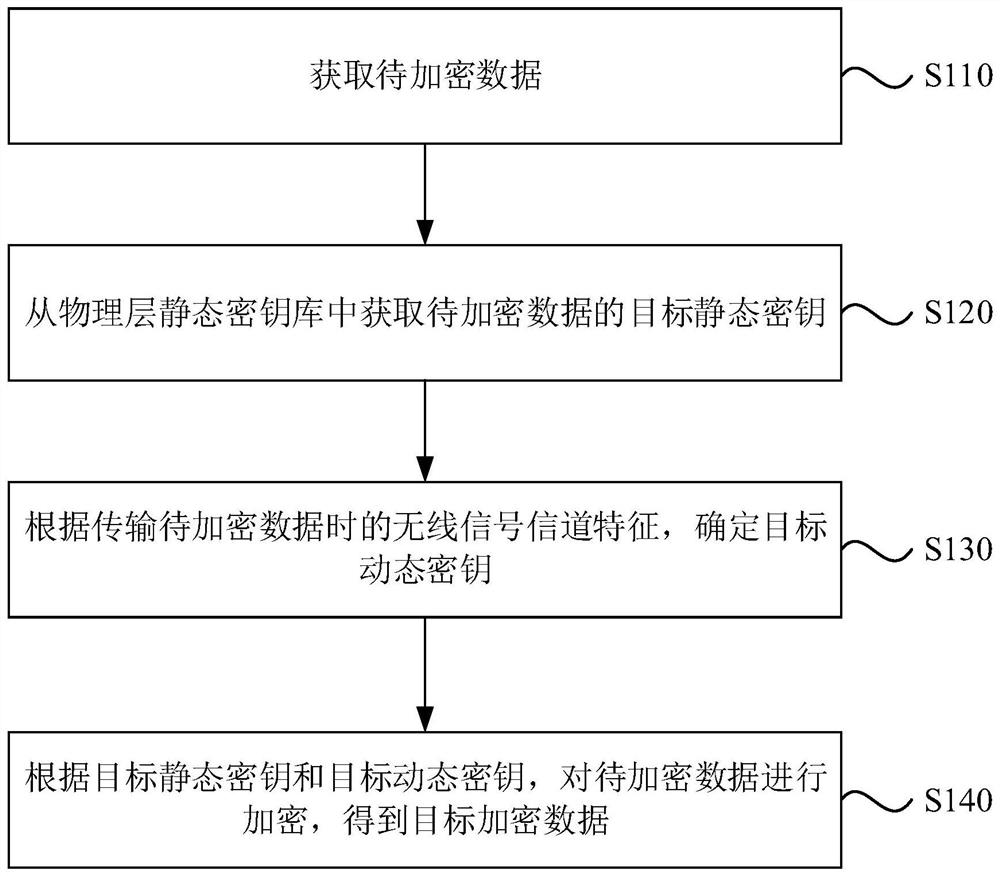
PendingCN114390518AImprove information securityPrevent eavesdroppingParticular environment based servicesFor mass transport vehiclesCommunications securityAttack
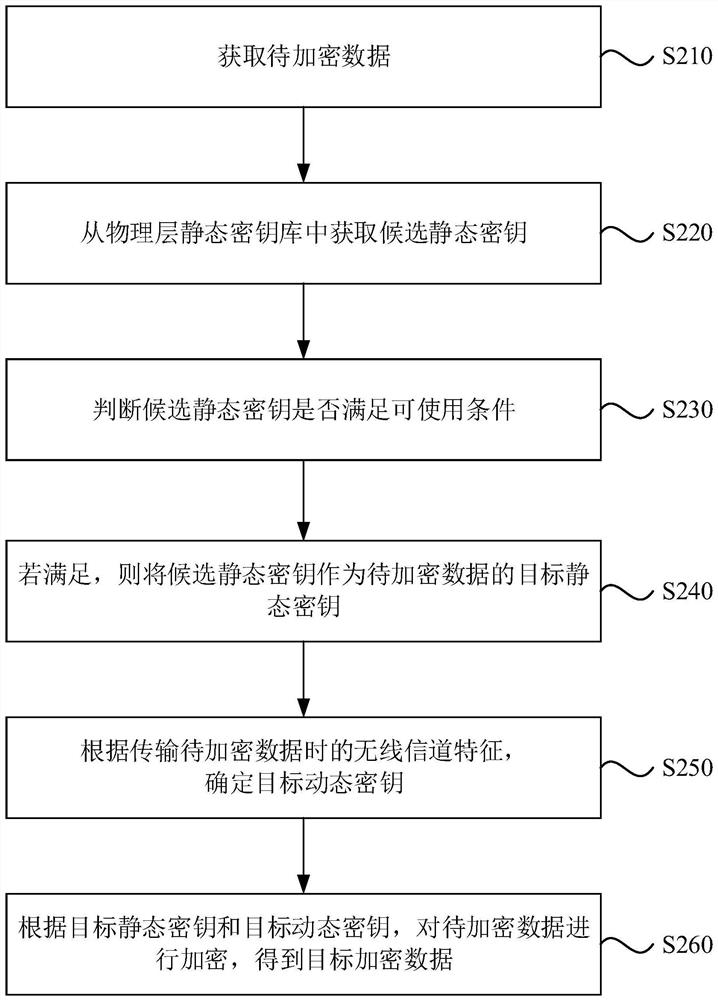
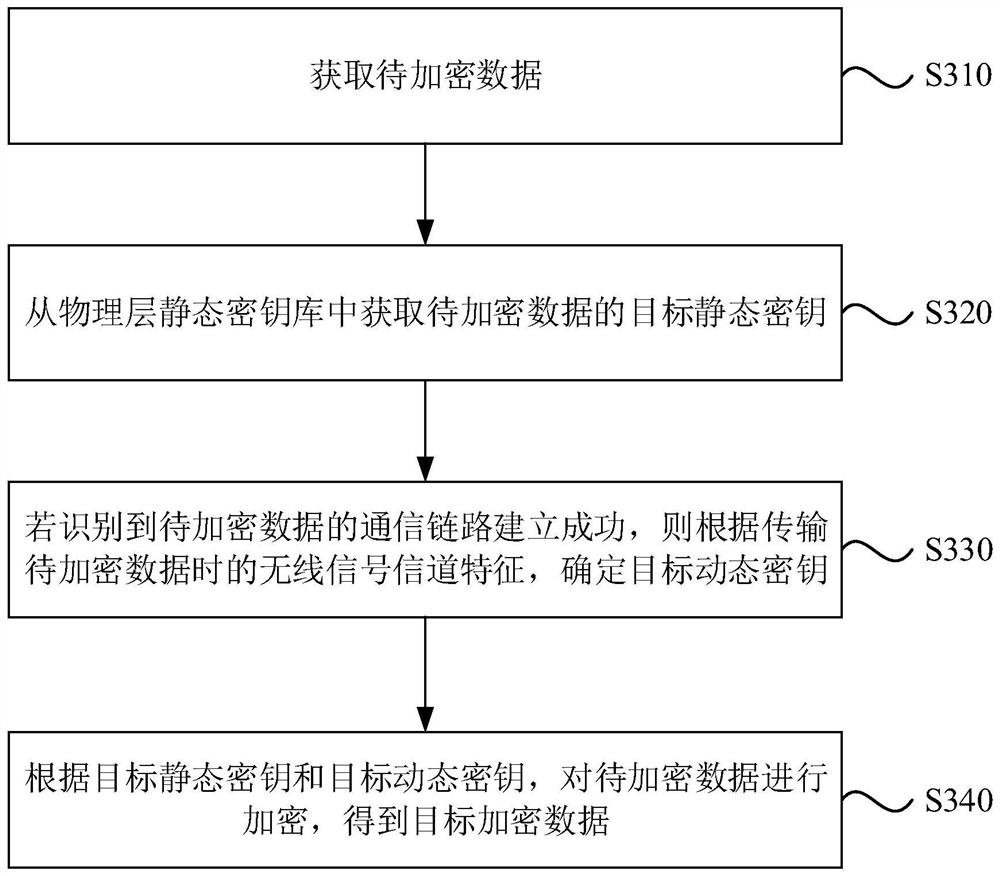
The invention discloses an encryption method, device and equipment and a storage medium, and belongs to the technical field of communication security. The method comprises the following steps: acquiring to-be-encrypted data; obtaining a target static key of the to-be-encrypted data from a physical layer static key library; determining a target dynamic key according to a wireless channel characteristic when the to-be-encrypted data is transmitted; and according to the target static key and the target dynamic key, encrypting the to-be-encrypted data to obtain target encrypted data. According to the technical scheme, the information safety of point-to-point wireless communication of the railway locomotive is improved, eavesdropping and attacks of illegal users are avoided, and a new thought is provided for railway communication safety.
Owner:CRSC RESEARCH & DESIGN INSTITUTE GROUP CO LTD
Method and system for establishing key between nodes
ActiveCN101814987BRekeyUpdate flexibleKey distribution for secure communicationData switching networksDistributed computingStatic key
Owner:CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com