Method and system for establishing communication key between nodes
A technology of communication key and establishment method, applied in the field of communication network application, can solve the problems of complex distribution and update process, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
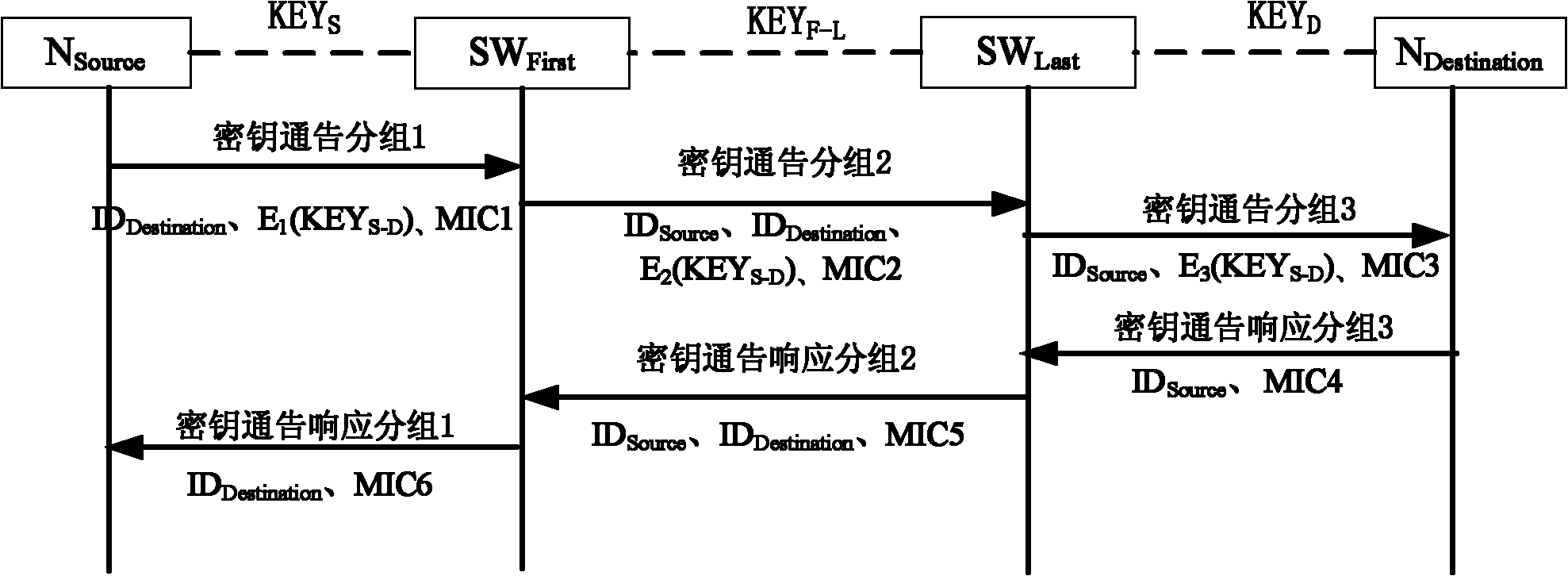
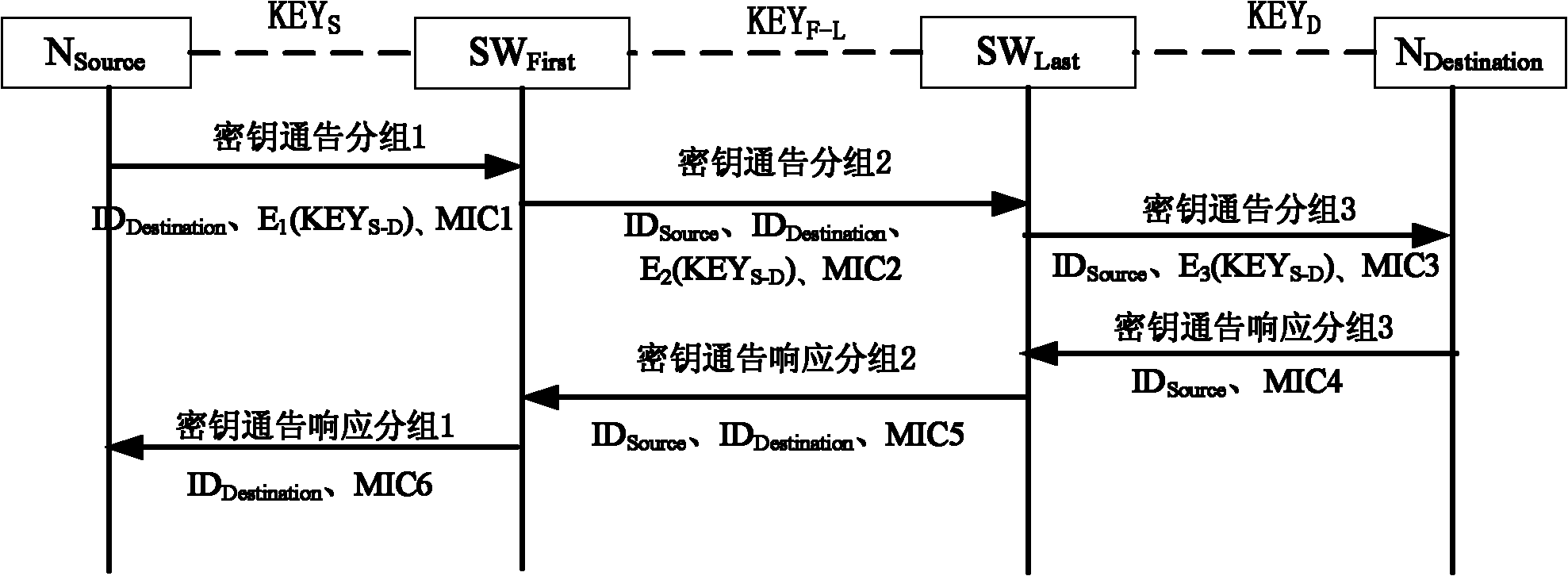
[0059] The node N (Node) defined in the present invention refers to a user terminal STA (STation) and a switching device SW (SWitch) in a local area network. Physical layer devices such as hubs in the LAN are not treated as nodes.
[0060] Assume that a secure connection has been established between adjacent switching devices and user terminals in the network through pre-distribution or other security mechanisms, that is, they already have a shared key; all switching devices communicate with each other through pre-distribution or other security mechanisms The mechanism has established a secure connection, ie already has a shared secret.
[0061] to send source node N Source with destination node N Destination The establishment of the communication key between First refers to the node from which the source node N Source to the destination node N Destination The first switching device that the data packet passes through, the switching device SW Last refers to the node from...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com