Secret key application method based on SM9 algorithm
A key and algorithm technology, applied in computing, computer security devices, instruments, etc., can solve the problems of SM9 algorithm key update, revocation difficulty, user ID cannot be changed, user is not the only owner of the private key, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
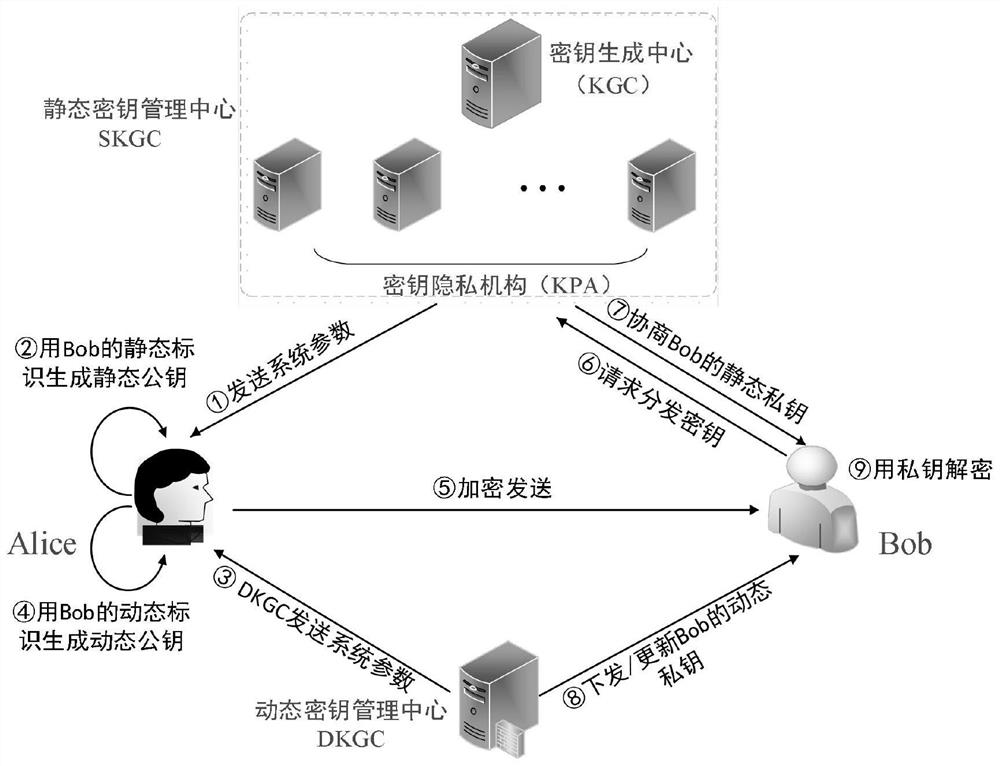
[0016] Such as figure 1 As shown, the present invention provides a kind of key application method based on SM9 algorithm, comprises the steps:
[0017] Step S01, according to the key generation rules of the SM9 algorithm, the static key generation center SKGC generates the user's static key based on the user ID, and the static key includes an encryption key pair and a signature key pair;
[0018] Step S02, according to the key generation rules of the SM9 algorithm, the dynamic key management center DKGC constructs the user's dynamic identification through the user identification and the given dynamic variation, and generates the user's dynamic key based on the user's dynamic identification. The dynamic key Also contains encryption key pair and signing key pair;
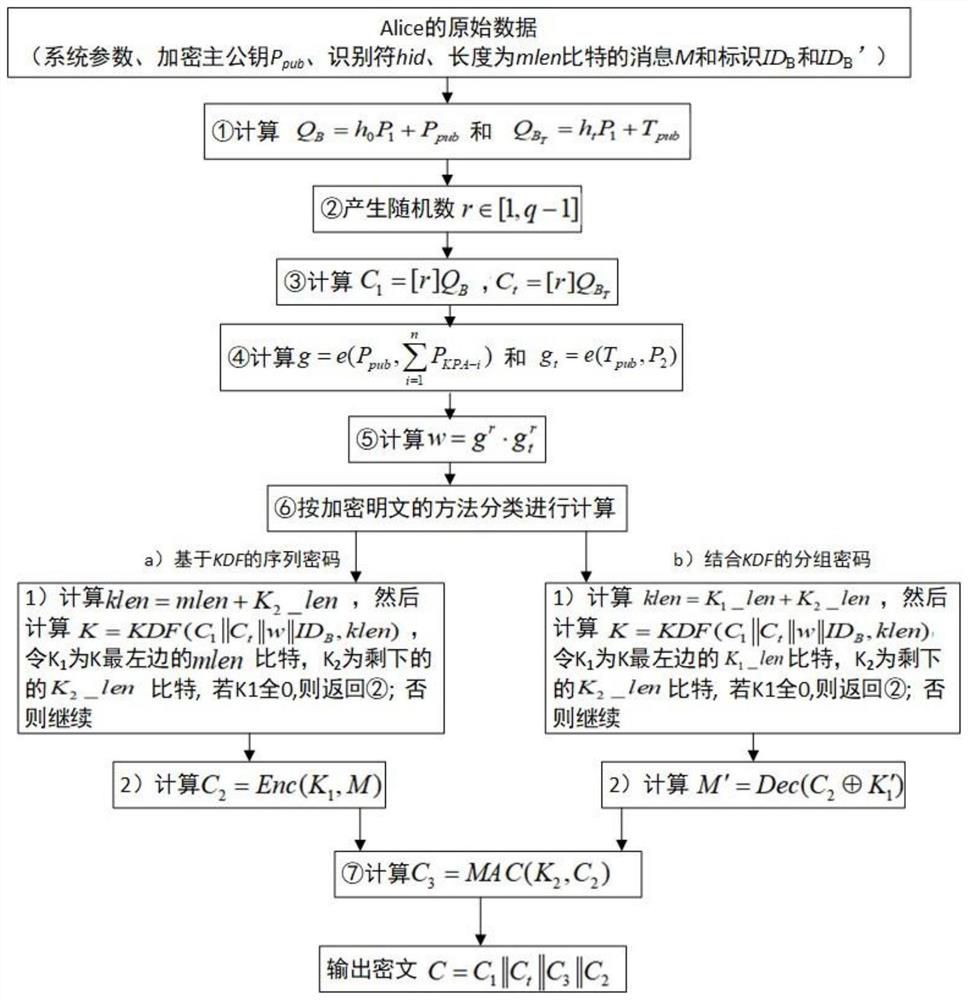
[0019] Step S03, under the joint action of the static key and the dynamic key, the functions of encryption, decryption, signature and signature verification of the SM9 algorithm are completed.
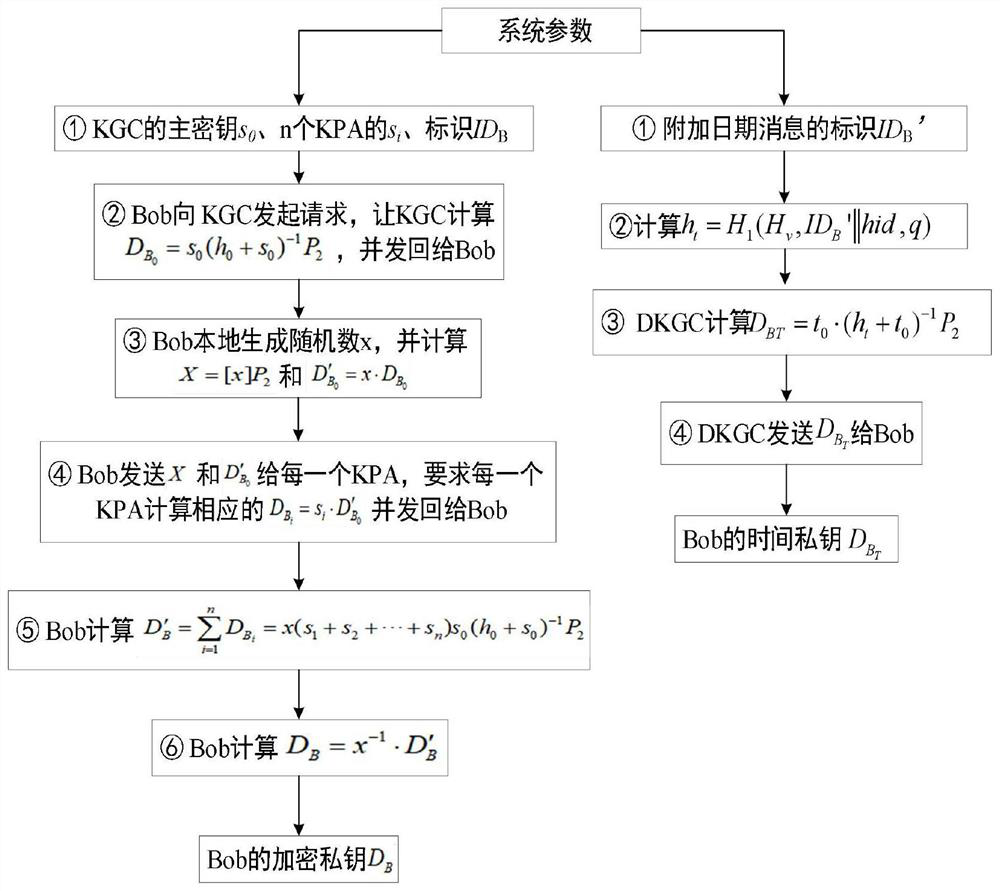
[0020] In the step S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com