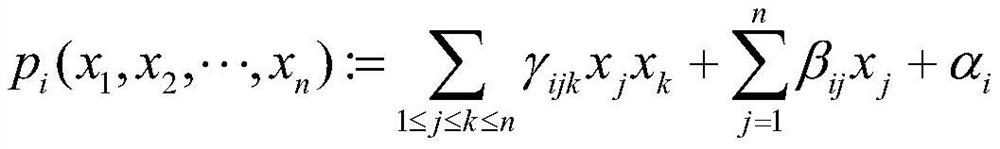Multi-variable broadcast multi-signature method based on certificateless
A multi-signature, multi-variable technology, applied in the field of network information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
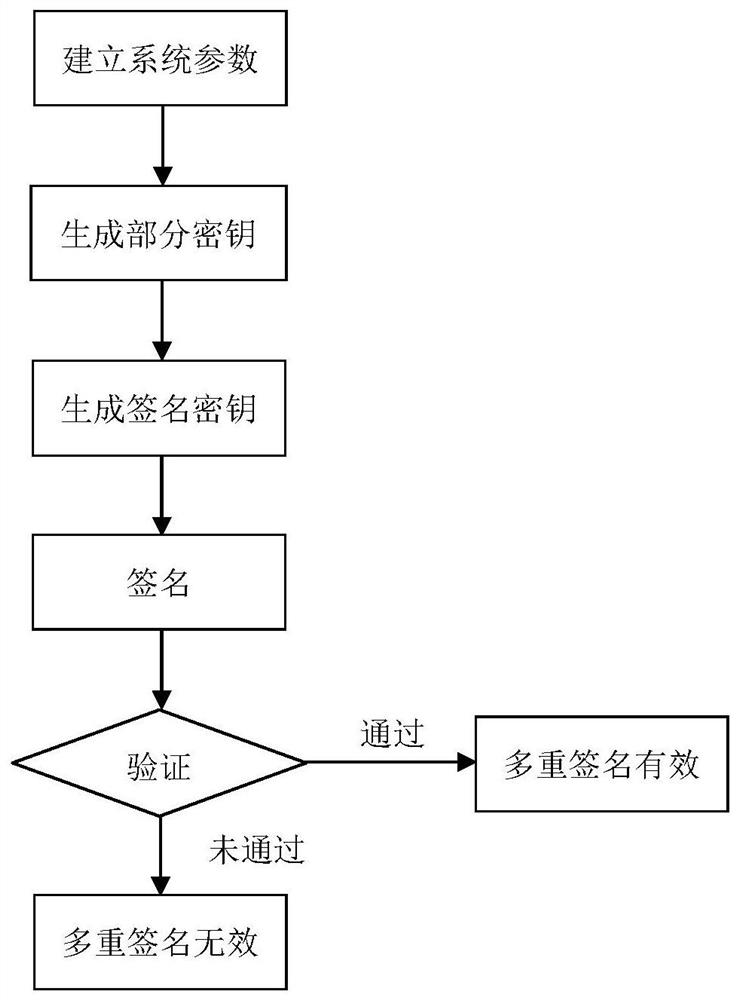
[0063] In this embodiment, the finite field K whose feature p is 2, order q is 256, n is 42, and r is 24 multivariate equations is taken as an example. The multivariate broadcast multi-signature method based on no certificate consists of the following steps (such as figure 1 shown):
[0064] A. Establish system parameters
[0065] (A1) The key generation center defines a finite field K with feature p and order q. In this embodiment, p is 2 and order q is 256.
[0066] (A2) The key generation center defines n-ary r multivariate equations on the finite field K. In this embodiment, n is 42 and r is 24.
[0067] P=(p 1 (x 1 ,x 2 ,···,x 42 ),···,p i (x 1 ,x 2 ,···,x 42 ),···,p 24 (x 1 ,x 2 ,···,x 42 ))
[0068] Each equation system p i is about the variable x being x 1 、x 2 ,...,x 42 The nonlinear quadratic equation for , where i is 1, 2, ..., 24:
[0069]
[0070] Among them, each coefficient α, β, γ and variable x are in the finite field K.
[0071] (A3) Th...
Embodiment 2
[0119] In this embodiment, the finite field K whose characteristic p is 2, order q is 256, n is 30, and r is 25 multivariate equations is taken as an example. The certificate-free multivariate broadcast multi-signature method consists of the following steps:
[0120] A. Establish system parameters
[0121] (A1) The key generation center defines a finite field K with characteristic p and order q. In this embodiment, p is 2 and order q is 256.
[0122] (A2) The key generation center defines n-ary r multivariate equations on the finite field K. In this embodiment, n is 30 and r is 25.
[0123] P=(p 1 (x 1 ,x 2 ,···,x 30 ),···,p i (x 1 ,x 2 ,···,x 30 ),···,p 25 (x 1 ,x 2 ,···,x 30 ))
[0124] Each equation system p i is about the variable x being x1 、x 2 ,...,x 30 The nonlinear quadratic equation for , where i is 1, 2, ..., 25:
[0125]
[0126] Among them, each coefficient α, β, γ and variable x are in the finite field K.
[0127] (A3) The key generation cent...
Embodiment 3
[0168] In this embodiment, the finite field K whose characteristic p is 2, order q is 512, n is 42, and r is 24 multivariate equations is taken as an example. The multivariate broadcast multi-signature method based on no certificate consists of the following steps:
[0169] A. Establish system parameters
[0170] (A1) The key generation center defines a finite field K with feature p and order q. In this embodiment, p is 2 and order q is 512.
[0171] (A2) The key generation center defines n-ary r multivariate equations on the finite field K. In this embodiment, n is 42 and r is 24.
[0172] P=(p 1 (x 1 ,x 2 ,···,x 42 ),···,p i (x 1 ,x 2 ,···,x 42 ),···,p 24 (x 1 ,x 2 ,···,x 42 ))
[0173] Each equation system p i is about the variable x being x 1 、x 2 ,...,x 42 The nonlinear quadratic equation for , where i is 1, 2, ..., 24:
[0174]
[0175] Among them, each coefficient α, β, γ and variable x are in the finite field K.
[0176] (A3) The key generation ce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com