A method and system for re-encryption based on certificate proxy
A proxy re-encryption and certificate technology, which is applied to the public key of secure communication, user identity/authority verification, and key distribution, and can solve the problems of key escrow, complex certificate management, complex certificate management and key escrow.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
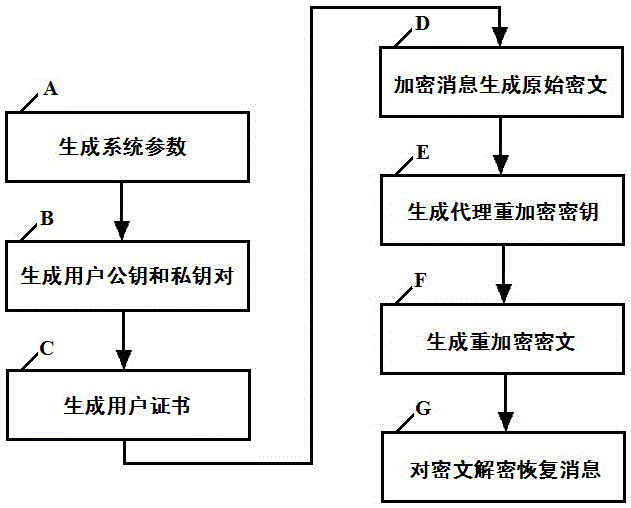
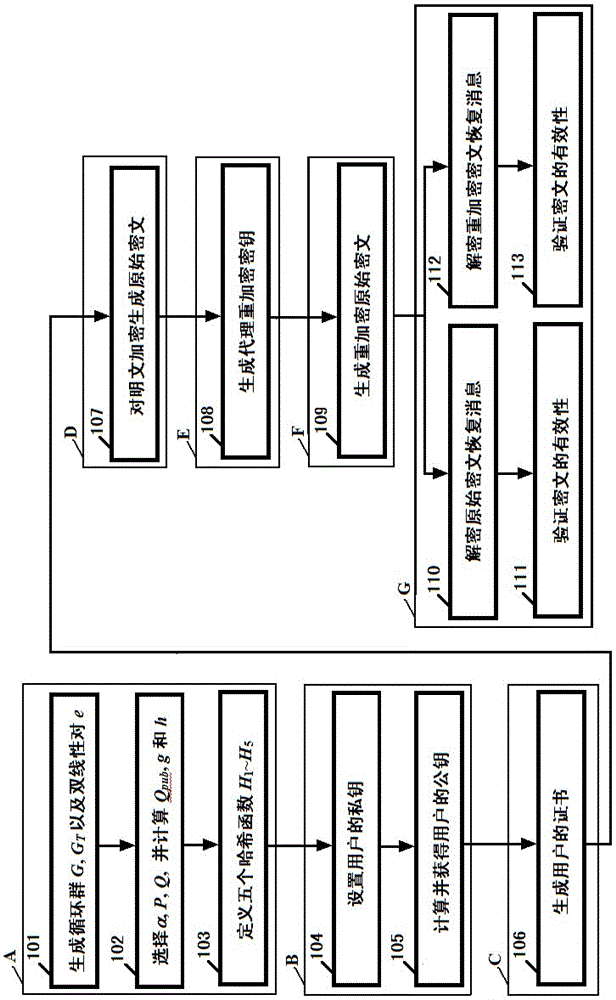
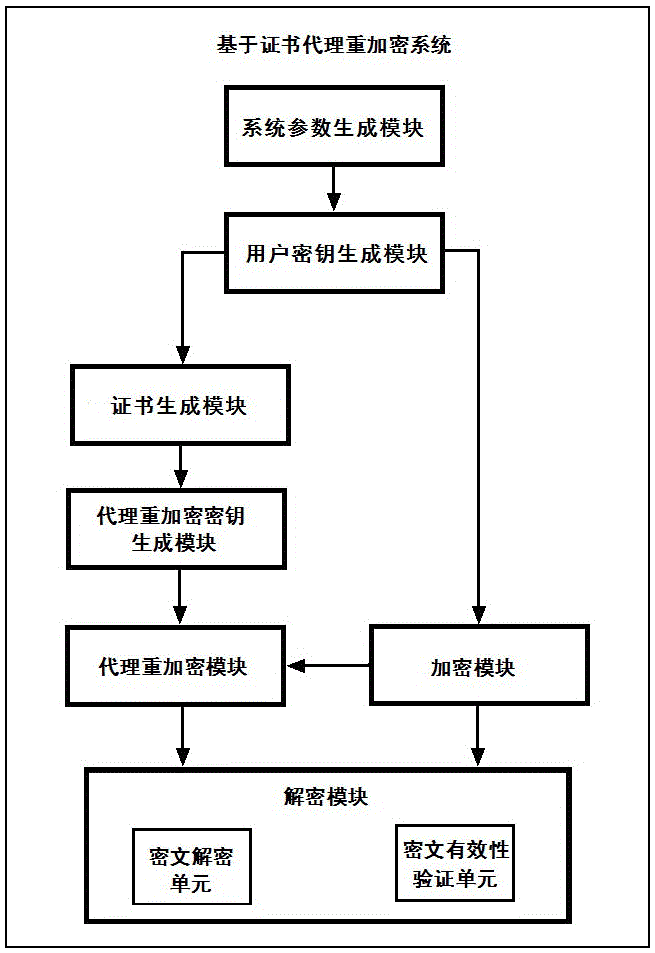
[0046] Below in conjunction with accompanying drawing, technical scheme of the present invention is described in further detail:
[0047] The certificate-based proxy re-encryption method of the present invention can be realized based on bilinear pairing. The basic definition of bilinear pairing and the properties it satisfies will be briefly introduced below.
[0048] Let G be an additive cyclic group of order p, G T is a multiplicative cyclic group of order p, and P is a generator of the group G, where p is a large prime number. Suppose G and G T The discrete logarithm problem on both groups is hard. If defined in group G and group G T Previous mapping e:G×G→G T Satisfy the following three properties, then the mapping is called a valid bilinear pairing. Bilinear pair e: G×G→G T is the Cartesian product G×G of the group G and itself to the group G T The mapping, that is, the bilinear pairing e:G×G→G T refers to the function z=e(P 1 ,P 2 ), where P 1 ,P 2 ∈G is an i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com