Encryption method and device, equipment and storage medium
An encryption method and technology for encrypting data, applied in the field of communication security, can solve problems such as difficulty in supporting high-complexity encryption mechanisms and communication authentication, multi-system power consumption, computing resource consumption and bandwidth overhead, etc., to improve information security, avoid Eavesdropping and Attack Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
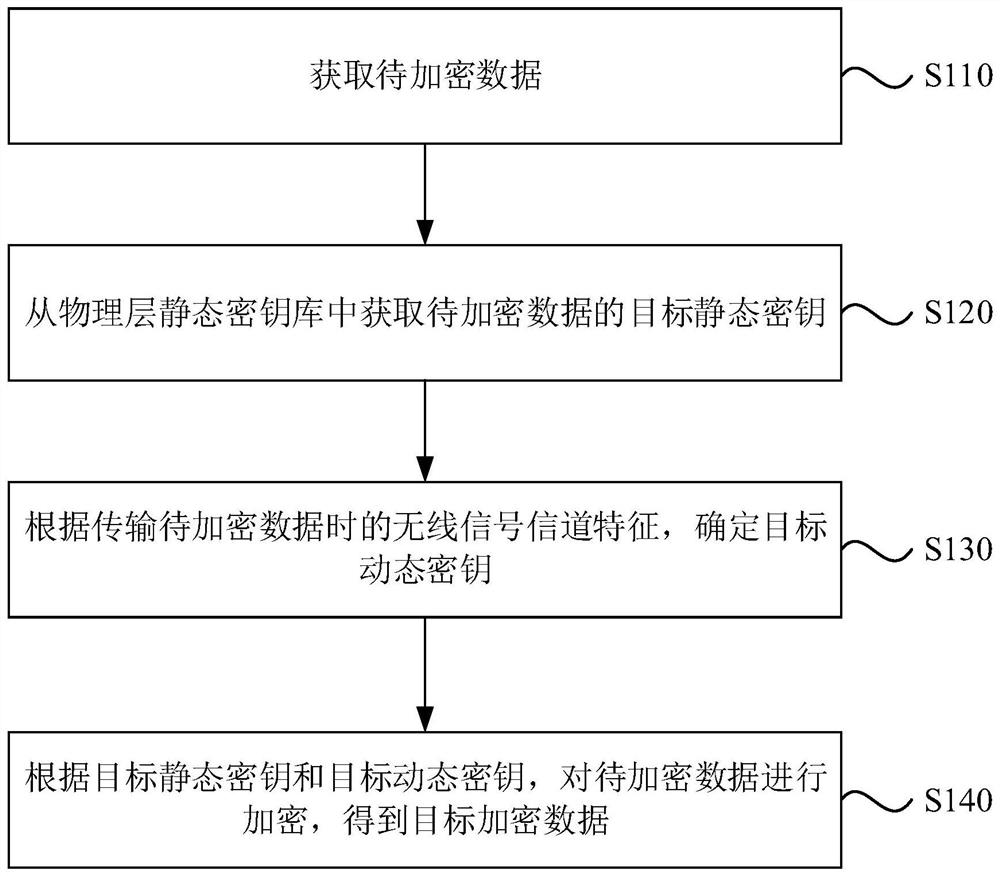
[0029] figure 1 It is a flow chart of an encryption method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of railway communication encryption, especially suitable for the situation of railway locomotive point-to-point communication encryption. This method can be executed by an encryption device. The device It can be realized by means of software and / or hardware, and can be integrated in electronic equipment carrying encryption functions, such as in a server, such as a railway locomotive vehicle networking system in a server. Optionally, the system includes on-board automatic protection (Automatic Train Protection, ATP) module, encryption management module, data processing module and data sending module.
[0030] Such as figure 1 As shown, the method may specifically include:
[0031] S110. Obtain data to be encrypted.
[0032] In this embodiment, the data to be encrypted refers to the data that needs to be encrypted, for ex...
Embodiment 2
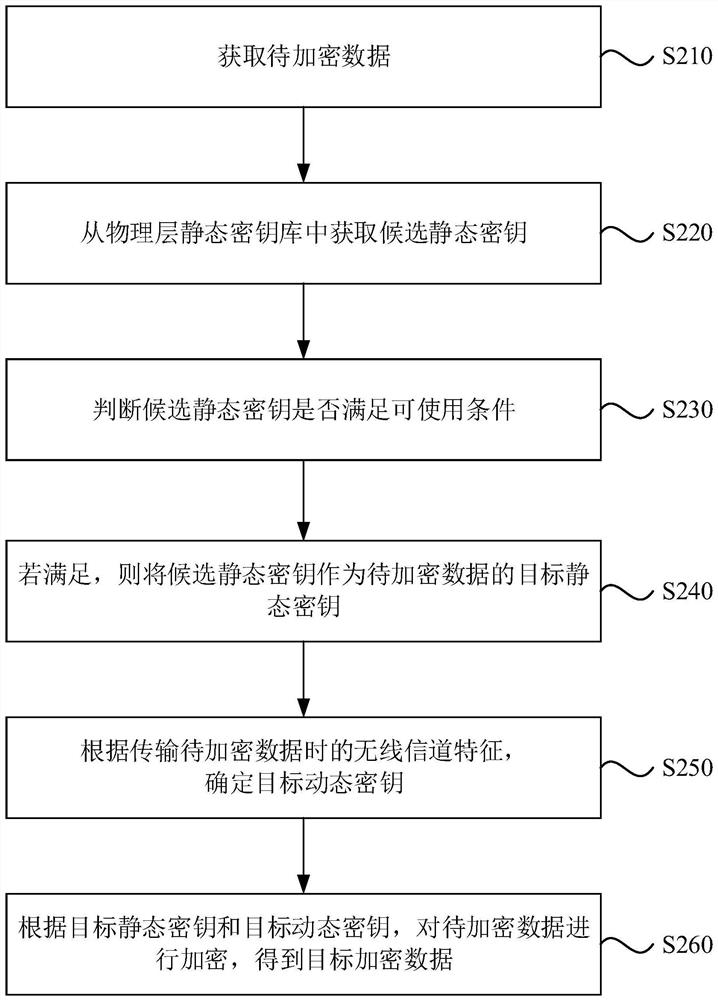
[0049] figure 2 It is a flow chart of an encryption method provided by Embodiment 2 of the present invention. On the basis of the above embodiments, the "obtaining the target static key of the data to be encrypted from the physical layer static key store" is further optimized to provide a Optional implementation.
[0050] Such as figure 2 As shown, the method may specifically include:
[0051] S210. Obtain data to be encrypted.
[0052] S220. Acquire a candidate static key from a physical layer static key store.
[0053] In this embodiment, the candidate static key refers to a static key randomly selected from the physical layer static key store.
[0054] Specifically, a static key is randomly selected from the physical layer static key store as a candidate static key.
[0055] It should be noted that the static keys in the physical layer static key store will be updated periodically. Exemplarily, if the number of static keys in the static key storehouse of the physica...
Embodiment 3
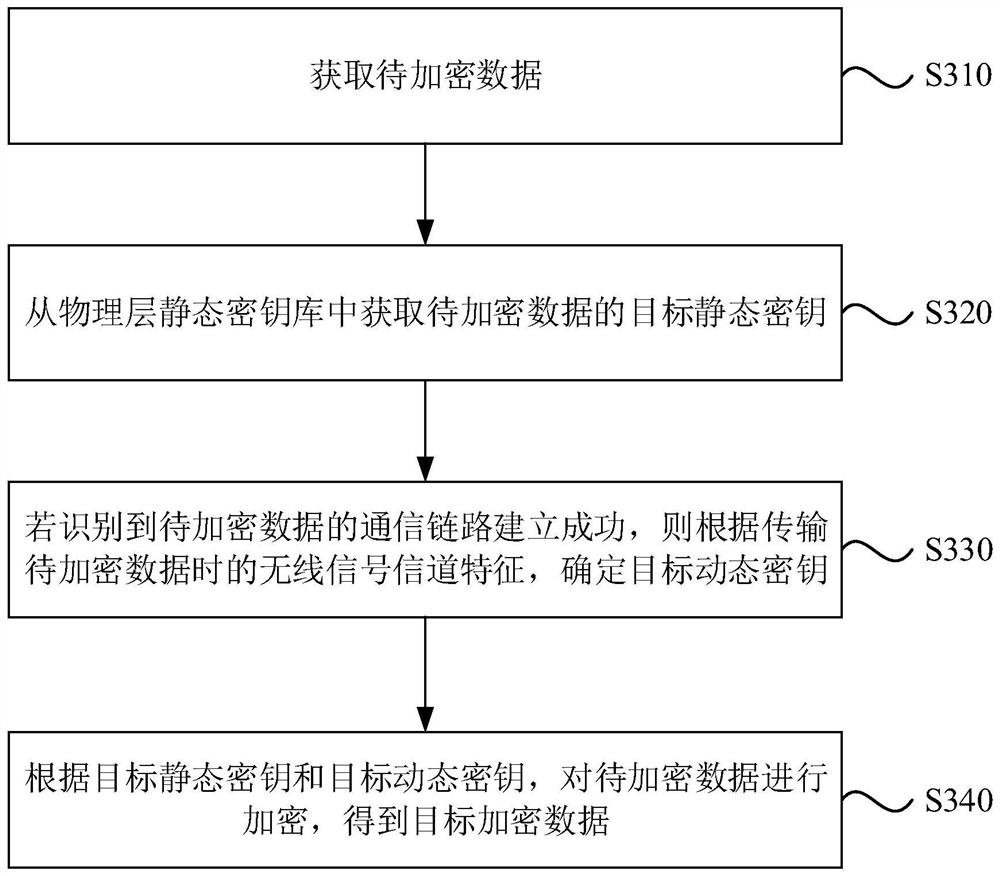
[0068] image 3 It is a flow chart of an encryption method provided by Embodiment 3 of the present invention. On the basis of the above embodiments, "determine the target dynamic key according to the characteristics of the wireless channel when transmitting the data to be encrypted" is further optimized to provide an encryption method that can Choose an implementation.
[0069] Such as image 3 As shown, the method may specifically include:
[0070] S310. Obtain data to be encrypted.
[0071] S320. Obtain the target static key of the data to be encrypted from the physical layer static key store.
[0072] S330. If it is identified that the communication link for the data to be encrypted is established successfully, determine the target dynamic key according to the characteristics of the wireless channel when the data to be encrypted is transmitted.
[0073] In this embodiment, if it is recognized that the communication link of the data to be encrypted is successfully establ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com