Identity authentication method and device
An identity authentication device and identity authentication technology, applied in the field of identity authentication methods and devices in network function virtualization systems, can solve problems such as low efficiency and inability to adapt to VNF, and achieve high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
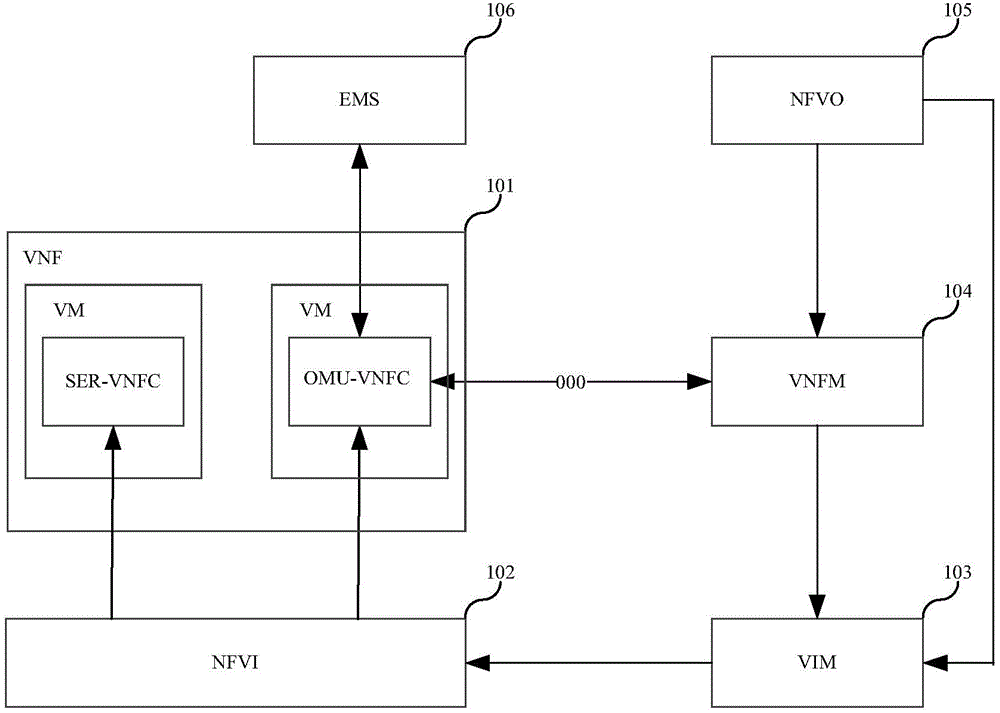
[0063] In Embodiment 1 of the present invention, the establishment of the VNF is initiated by the VNFM, such as figure 2 As shown, the VNFM generates all the configuration information required to establish the VNF, the configuration information includes the public key and private key of the OMU-VNFC, and the public key and private key of the SER-VNFC.
[0064] The public key and the private key are a key pair obtained by an algorithm. Among the two keys of the key pair, the non-secret key is called the public key, and the secret key is called the private key. When using this key pair, if the data is encrypted with the public key, it must be decrypted with the private key, and if the data is encrypted with the private key, it must be decrypted with the public key, otherwise the decryption will not succeed.
[0065] VNFM puts the identification information and private key of OMU-VNFC, the identification information and public key of SER-VNFC into OMU-VNFC, and puts the identifi...
Embodiment 2
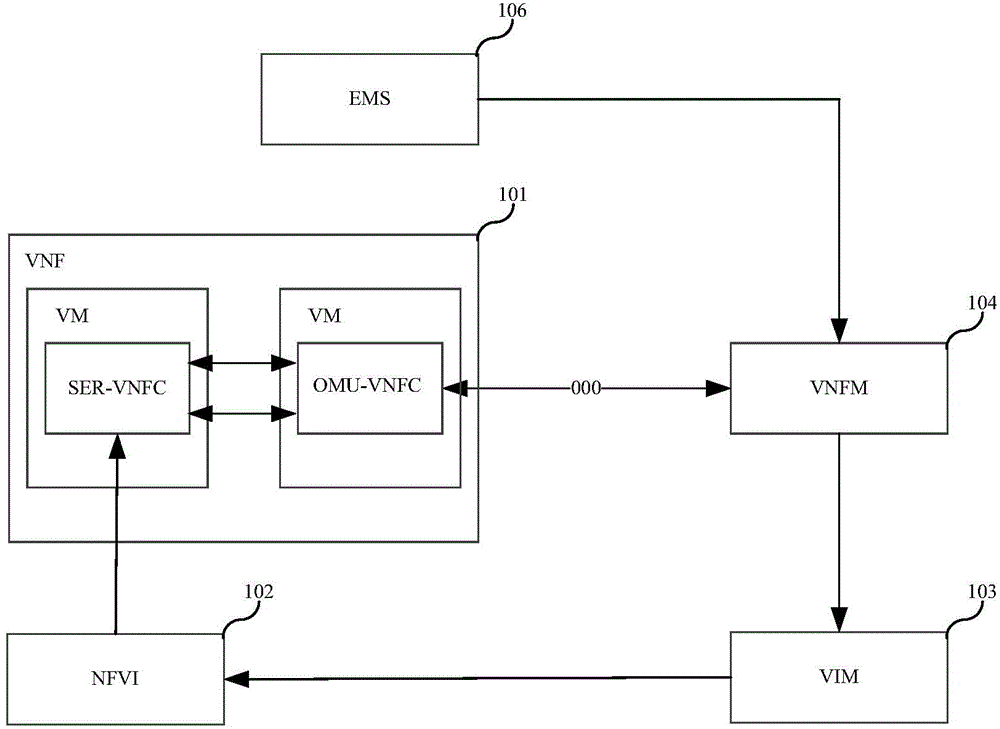
[0072] In Embodiment 2 of the present invention, the establishment of the VNF is initiated by the EMS, such as image 3 shown.
[0073] When EMS initiates the establishment of VNF, EMS does not need to participate in the generation of public key and private key, and VNFM still generates the public key and private key of OMU-VNFC, and the public key and private key of SER-VNFC. The subsequent insertion steps can be Refer to the above-mentioned embodiment 1; at this time, the execution body of the identity authentication method provided by the embodiment of the present invention is VNFM.
[0074] Or, EMS can also participate in the generation of public key and private key, that is, the public key and private key of OMU-VNFC and the public key and private key of SER-VNFC are generated by EMS, and the public key and private key of OMU-VNFC generated by EMS will be The private key, and the public key and private key of the SER-VNFC are sent to the VNFM, and the VNFM is instructed ...
Embodiment 3
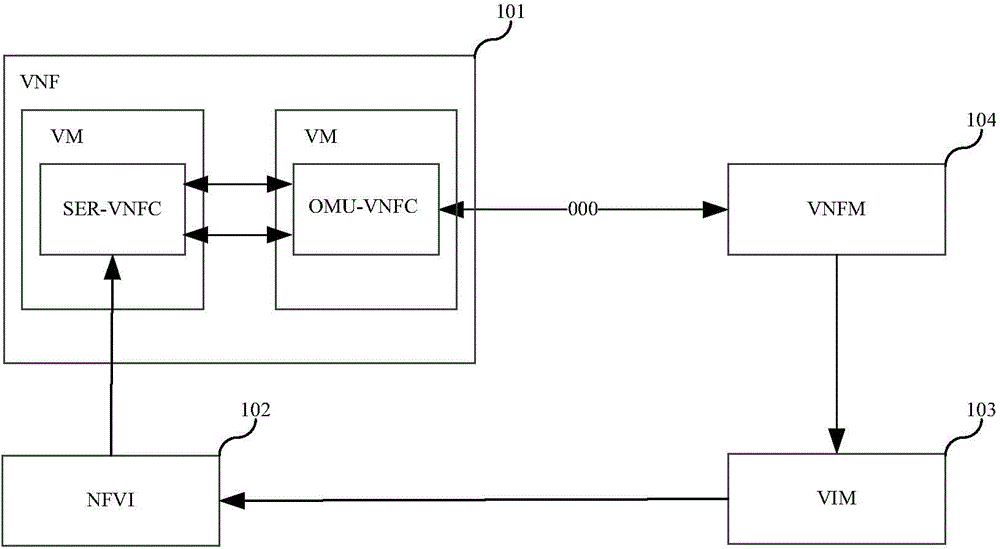
[0076] In Embodiment 3 of the present invention, the establishment of VNF is initiated by NFVO, such as Figure 4 As shown, NFVO may not participate in the generation of public key and private key, and VNFM still generates the public key and private key of OMU-VNFC, and the public key and private key of SER-VNFC. The subsequent insertion steps can refer to the above-mentioned embodiment 1 .
[0077] That is, in Embodiment 3, the execution body of the identity authentication method provided by the embodiment of the present invention is VNFM.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com