Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
304 results about "Exchange protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
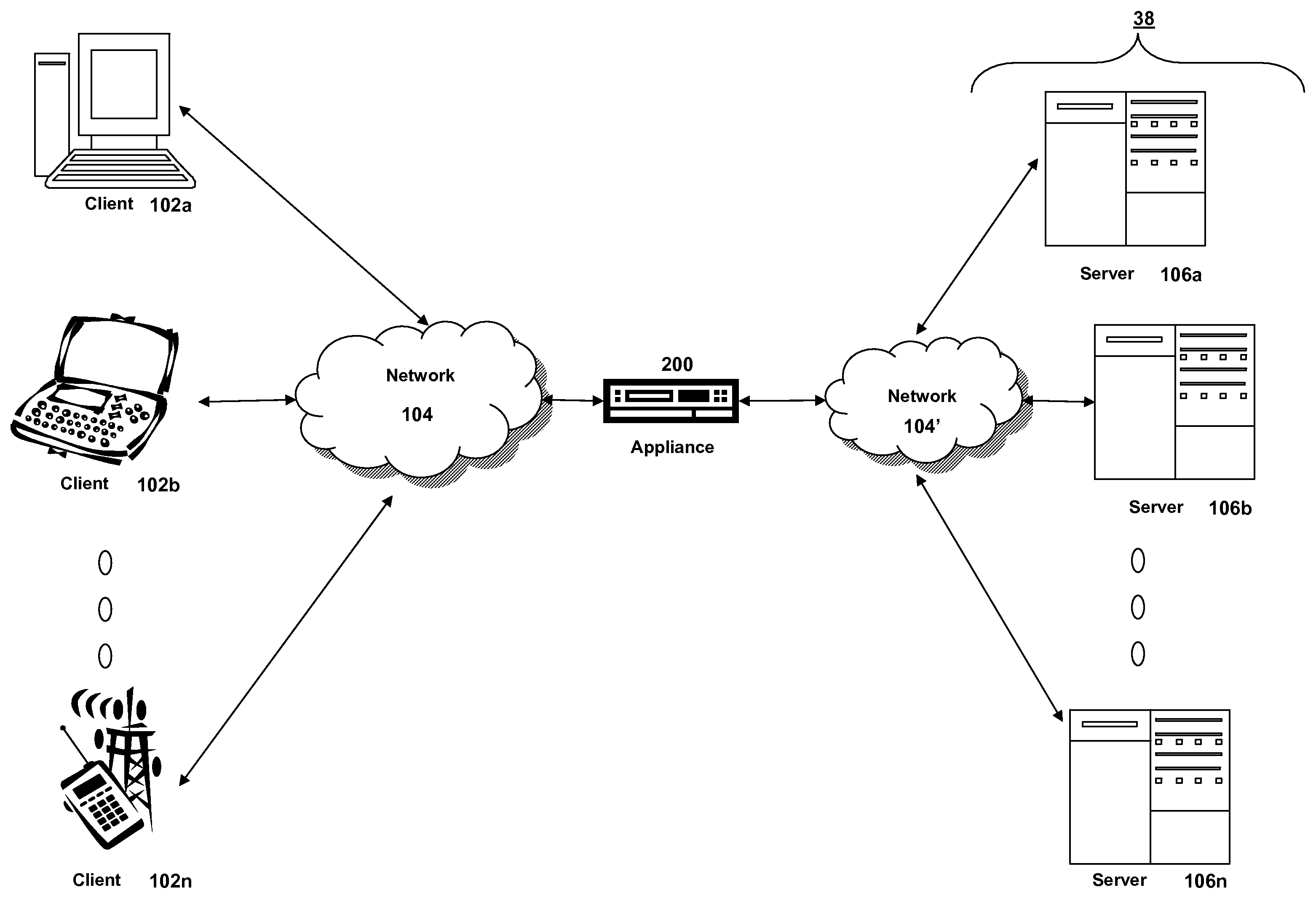
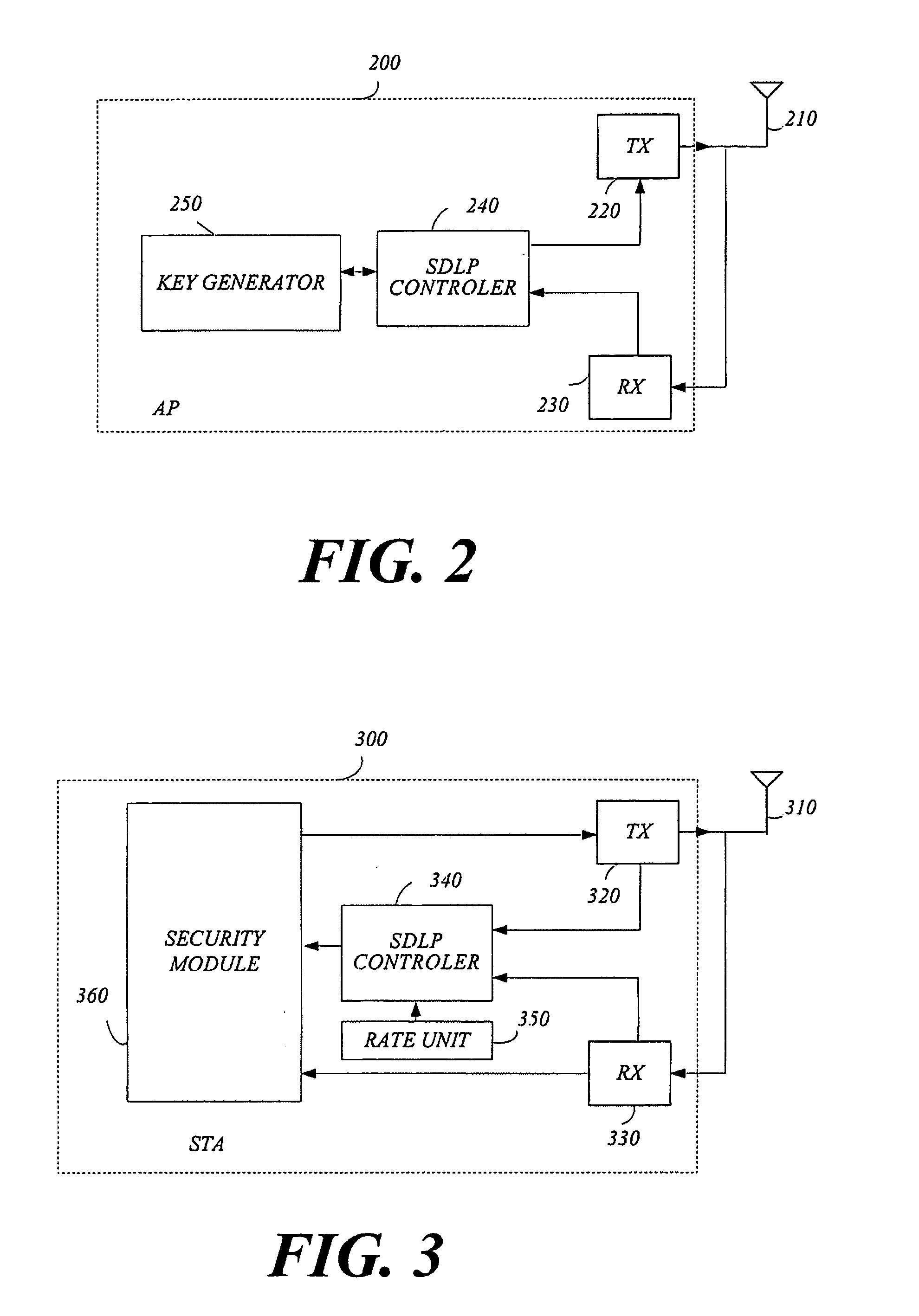
Systems and methods for authenticating communications in a network medium
InactiveUS20030149874A1Key distribution for secure communicationUser identity/authority verificationKey exchangeExchange protocol
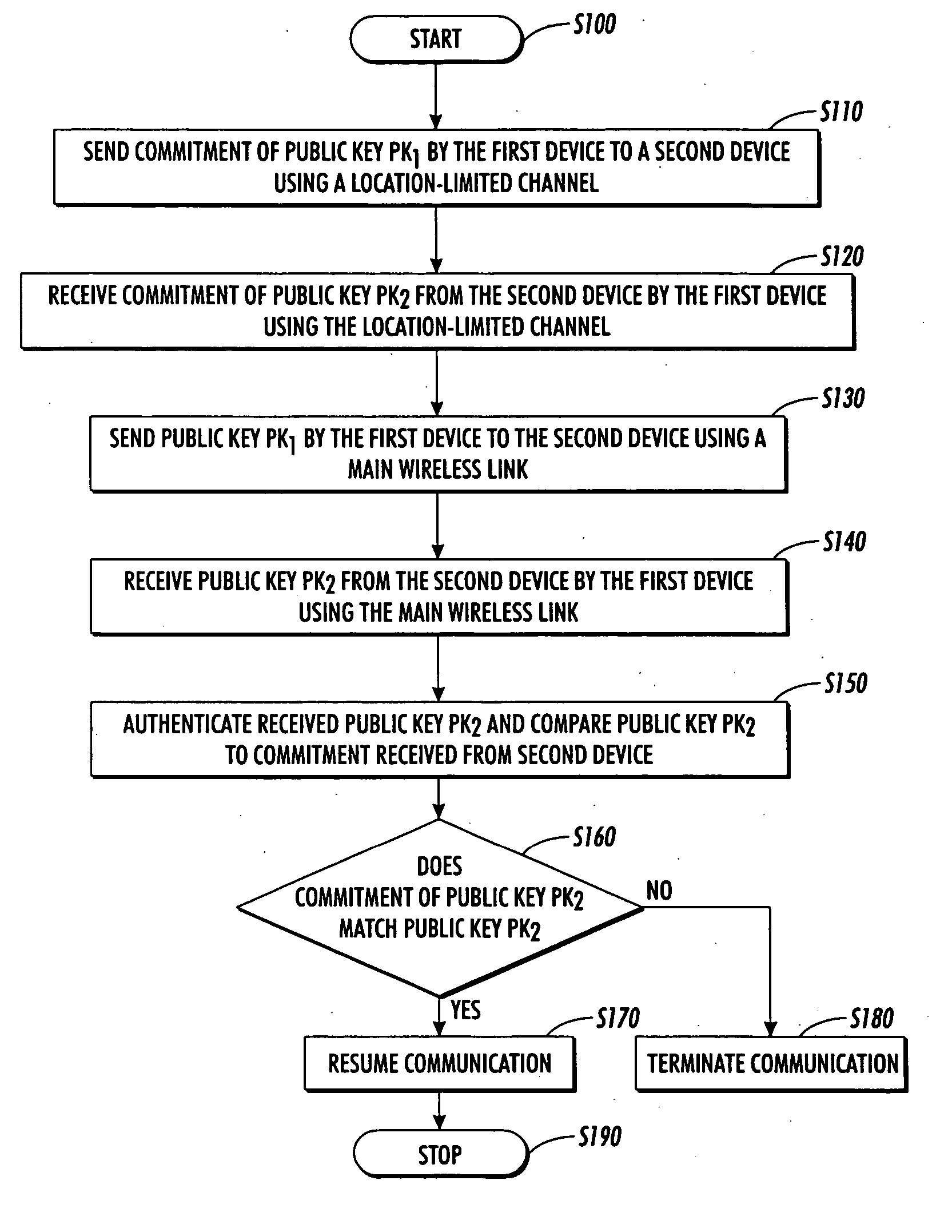
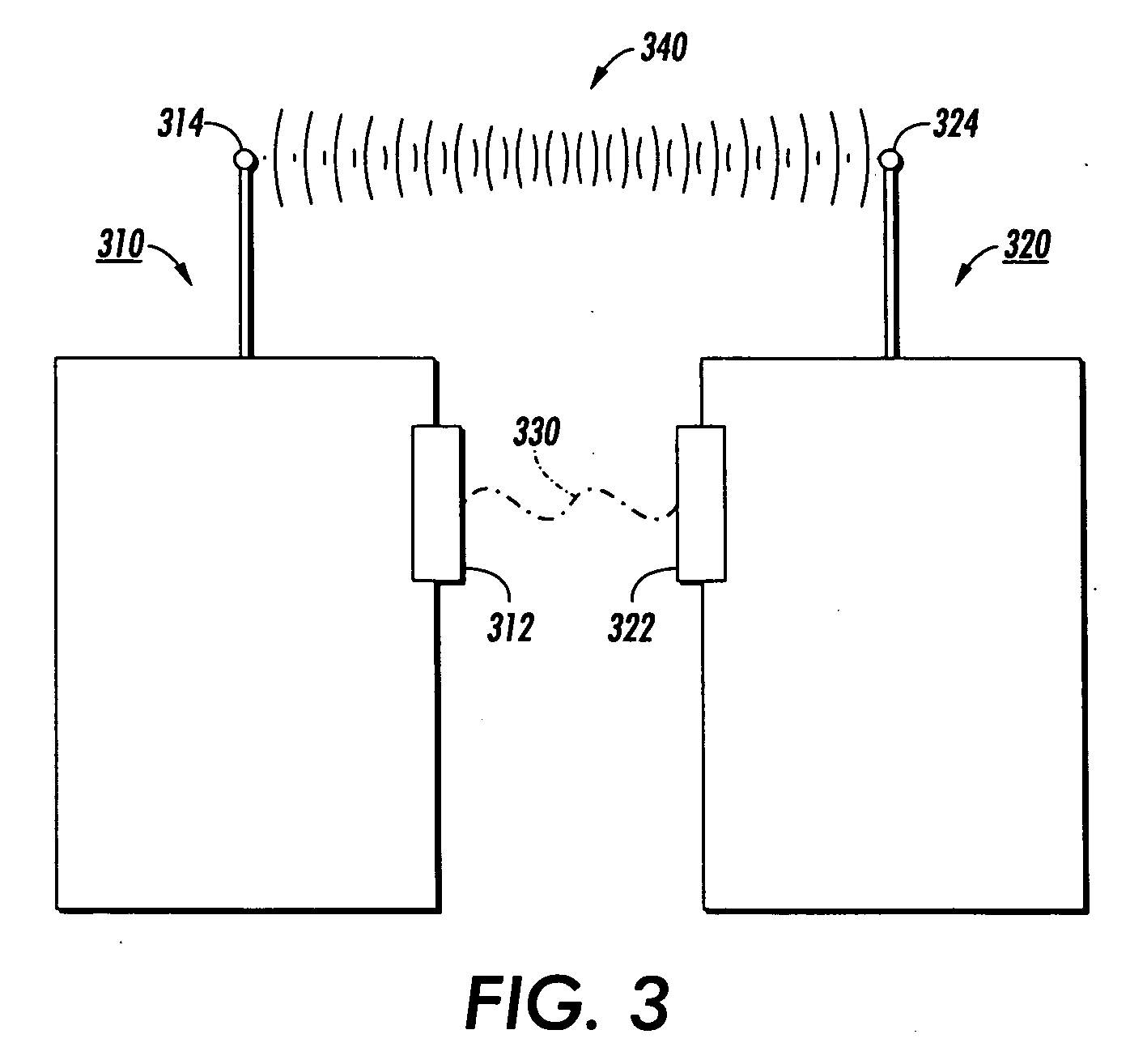
Pre-authentication information of devices is used to securely authenticate arbitrary peer-to-peer ad-hoc interactions. In one embodiment, public key cryptography is used in the main wireless link with location-limited channels being initially used to pre-authenticate devices. Use of public keys in the pre-authenticate data allows for the broadening of types of media suitable for use as location-limited channels to include, for example, audio and infrared. Also, it allows a range of key exchange protocols which can be authenticated in this manner to include most public-key-protocols. As a result, a large range of devices, protocols can be used in various applications. Further, an eavesdropper is forced to mount an active attack on the location-limited channel itself in order to access an ad-hoc exchange. However, this results in the discovery of the eavesdropper.
Owner:CISCO TECH INC
Identity negotiation switch protocols
A switch to switch protocol for network load balancing which negotiates among switches operable in accordance with the invention to assign a unique loop bit offset identifier value to each switch. Various other load balancing protocols associated with the switches then utilize the loop bit offset value as an identifier field when determining loops in the network of switches and costs associated with non-looped paths in the switches. A loop bit offset identifier requires less switch processing overhead than techniques which utilize an entire address value (i.e., MAC address value) for such protocols. Further, the loop bit offset identifier assigned by the present invention reduces the size of load balancing related packets. Specifically, cost computation related packets are reduced in size to the minimum 64 byte packet size through use of the loop bit offset identifier value of the present invention.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Systems and Methods for GSLB Remote Service Monitoring
ActiveUS20100131638A1Digital computer detailsMultiprogramming arrangementsExchange protocolOperating system
The present invention provides improvements to the integration between a metric exchange protocol and a monitoring mechanism supporting load balancing by a Global Server Load Balancing (GSLB) appliance in a GSLB hierarchy of appliances, using a method for triggering a monitor on a remote service. The method includes receiving, by a first appliance, metrics of a second appliance via a metric exchange connection between the first and second appliances. The first appliance includes a GSLB service and identifies a service provided via the second appliance as a remote service for GSLB. The first appliance may identify via the metrics that a state of the service is up, and determine that the metric exchange connection is down. Responsive to the determination, the first appliance may trigger a monitor to monitor the status of the service. Further, the first appliance may obtain via the monitor a second status of the service.
Owner:CITRIX SYST INC
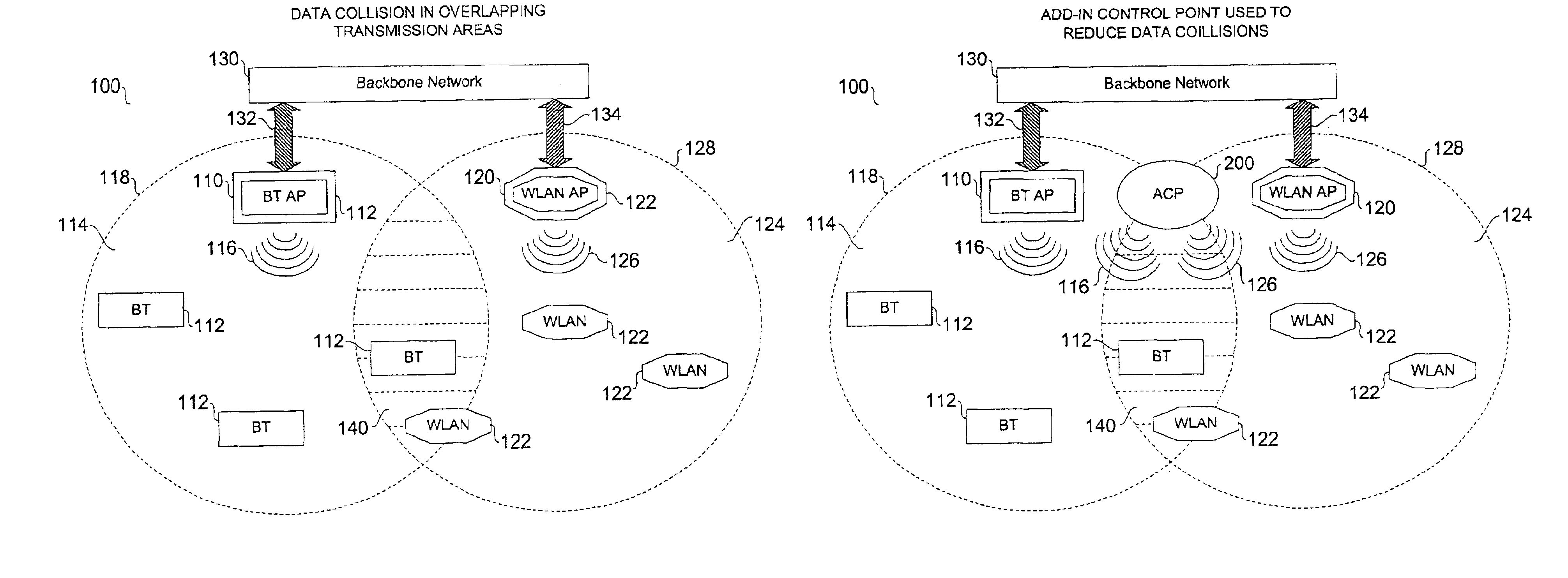
Top-level controller for wireless communication devices and protocols
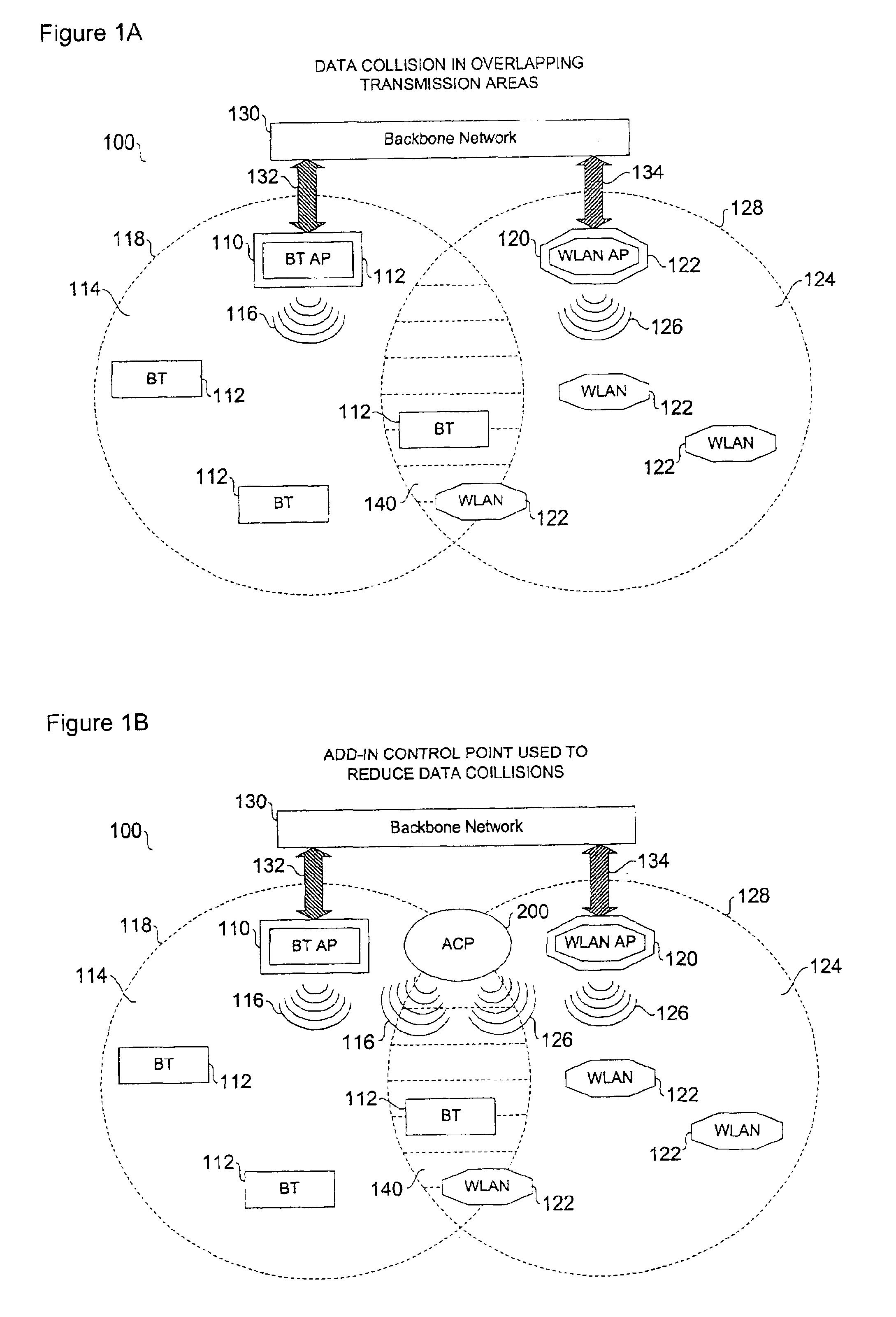
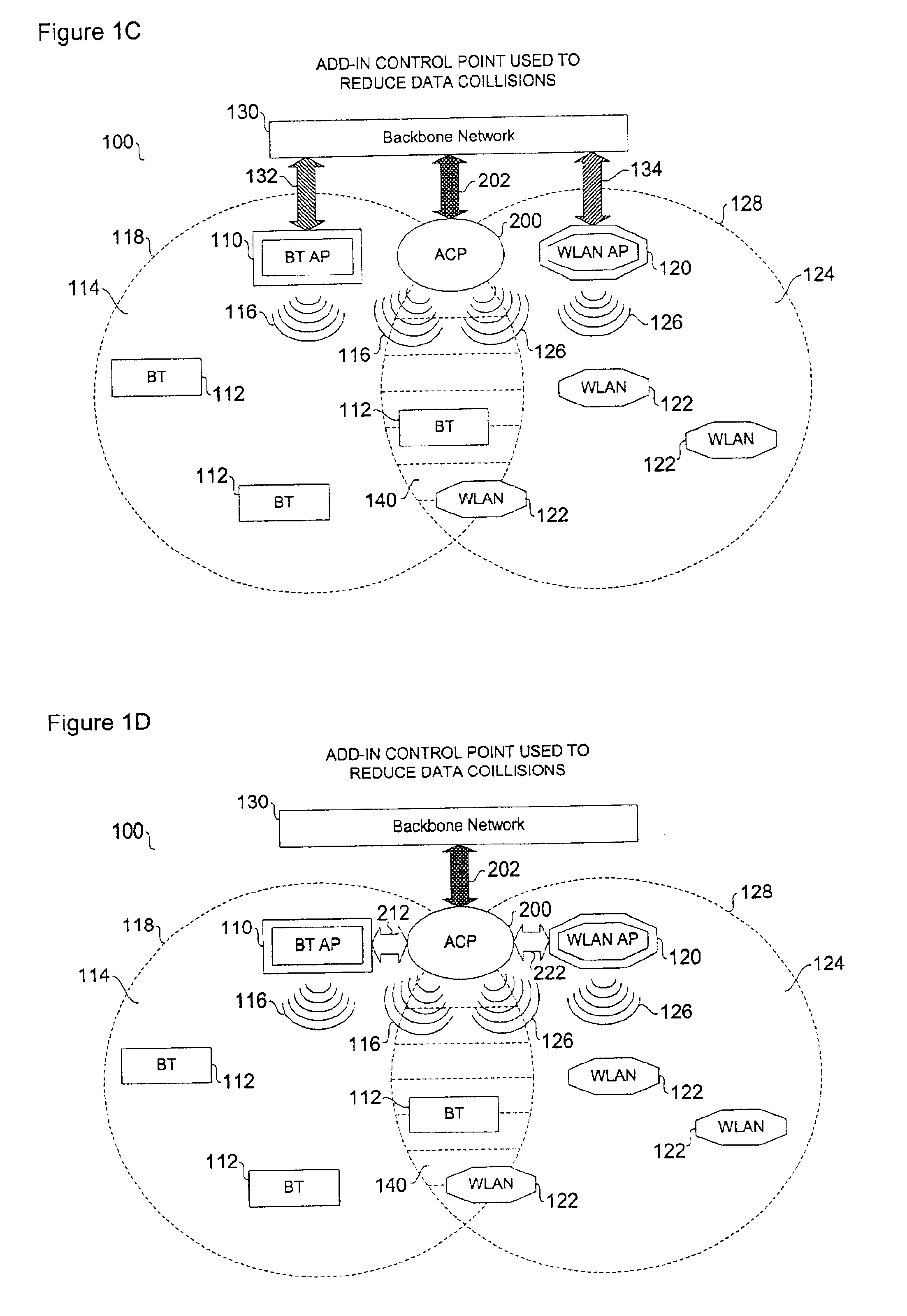
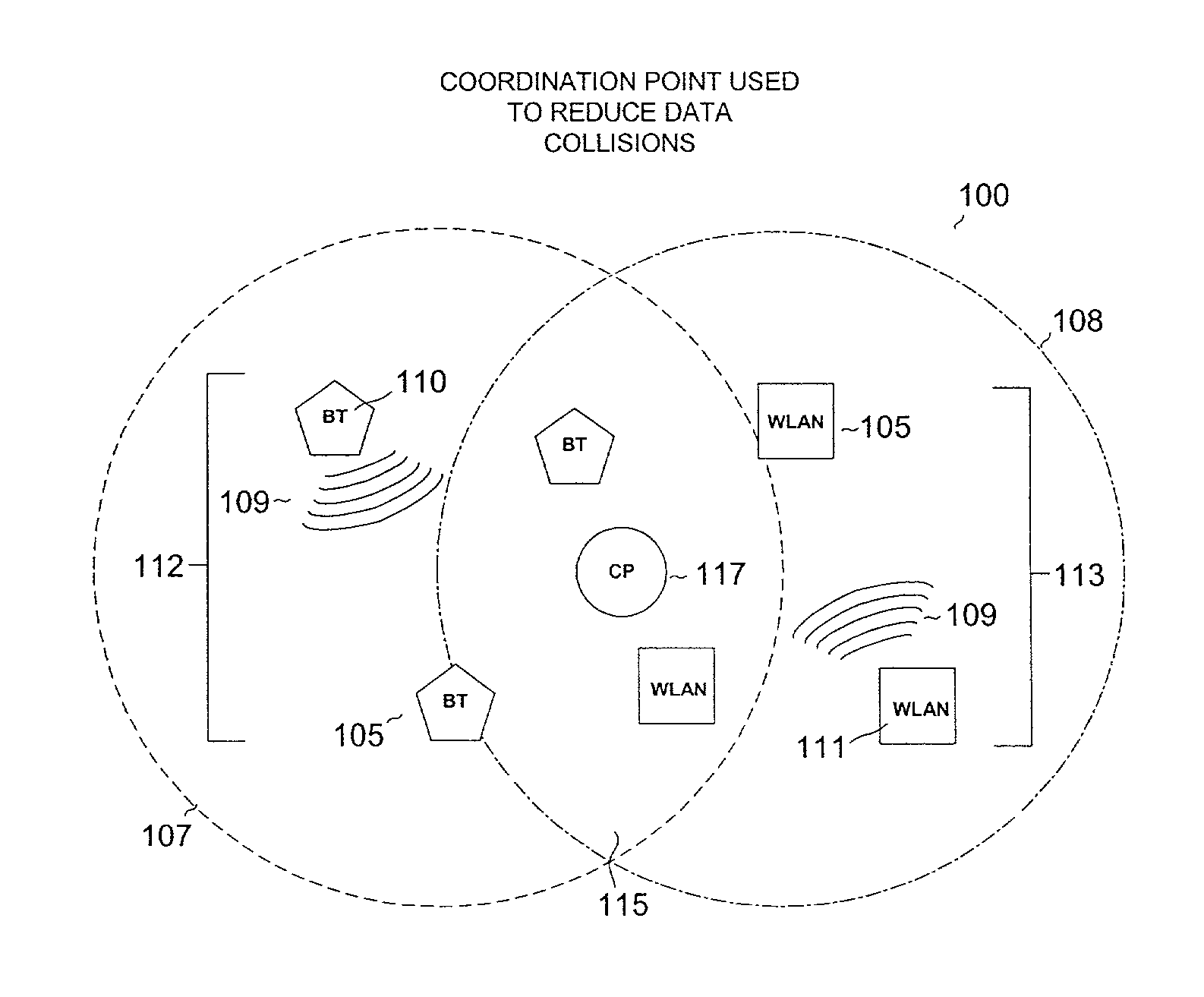
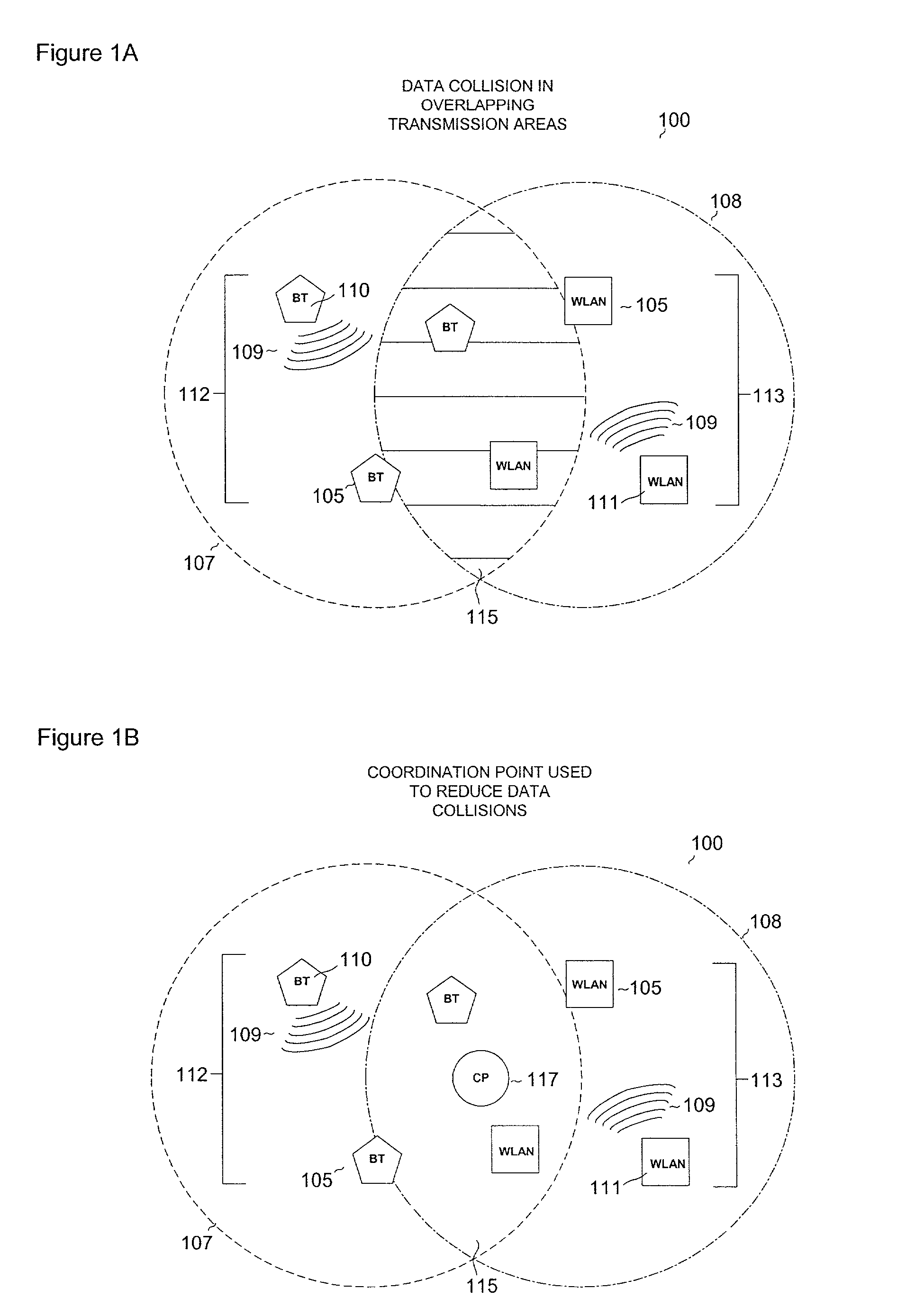
InactiveUS6954616B2Reduce collisionNetwork traffic/resource managementNetwork topologiesWireless transmissionInterference problem
Wireless communication networks utilize various communication protocols to exchange data between wireless network devices. Overlapping communication frequencies between data exchange protocols present a collision and interference problem when data transmissions are transmitted using similar timing and frequency characteristics during wireless transit. A device and various network configurations for monitoring, moderating, and / or coordinating wireless transmission traffic in a wireless communication network where overlapping communication frequencies coexist is described to significantly reduce or avoid interference caused by signal collisions.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Remotely-cooperative scheduling solution for moderating wireless protocols
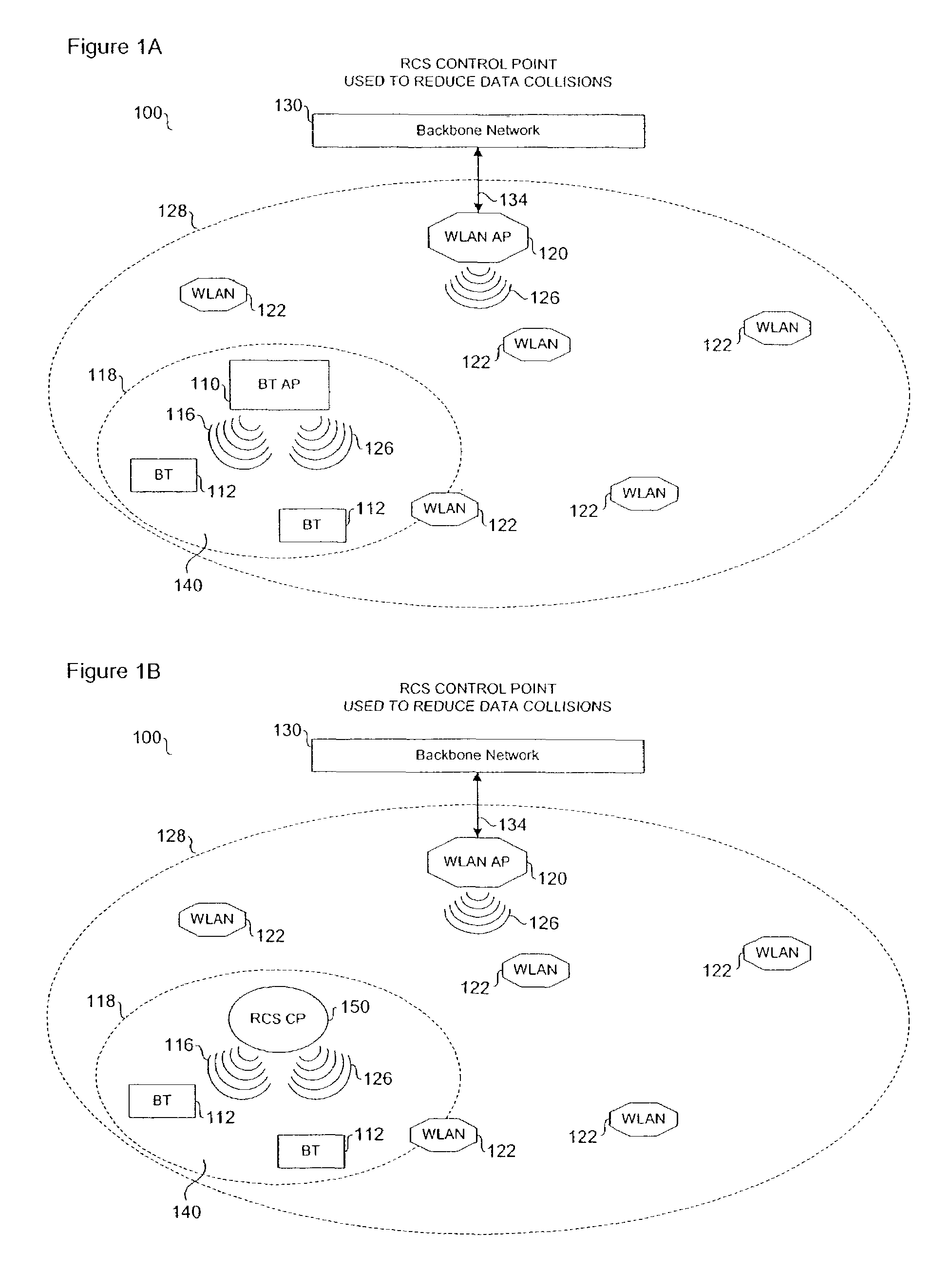
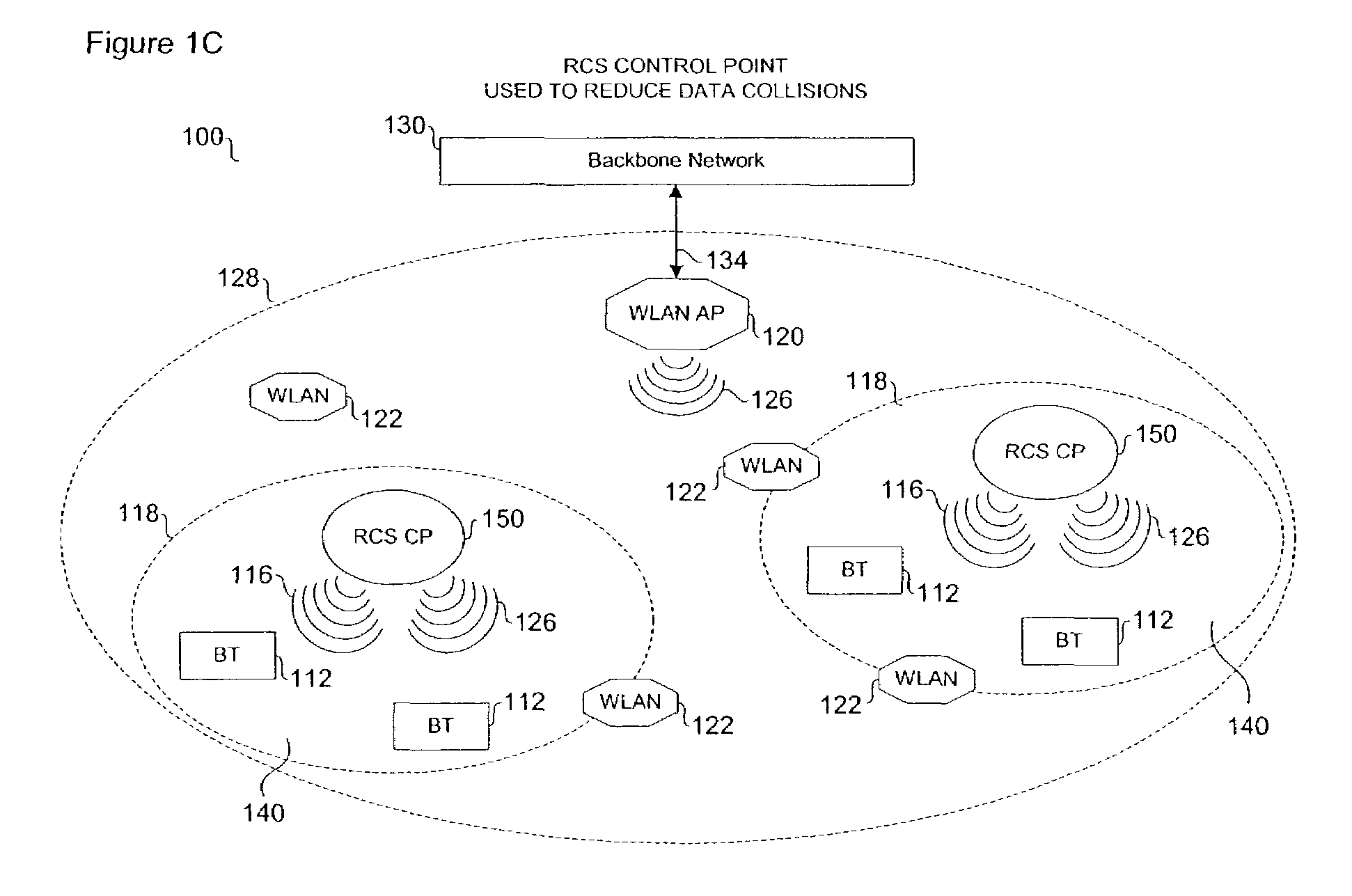
ActiveUS7215659B1Reduce frequency-overlapping collisionAvoid collisionTime-division multiplexRadio/inductive link selection arrangementsWireless transmissionWireless mesh network
Wireless communication networks utilize various communication protocols to exchange data between wireless network devices. Overlapping communication frequencies between data exchange protocols present a collision problem when data transmissions interfere with one another during wireless transit. A device for moderating transmission traffic in a wireless network where overlapping communication frequencies coexist is described to reduce or avoid interference caused by signal collisions.
Owner:AVAGO TECH INT SALES PTE LTD
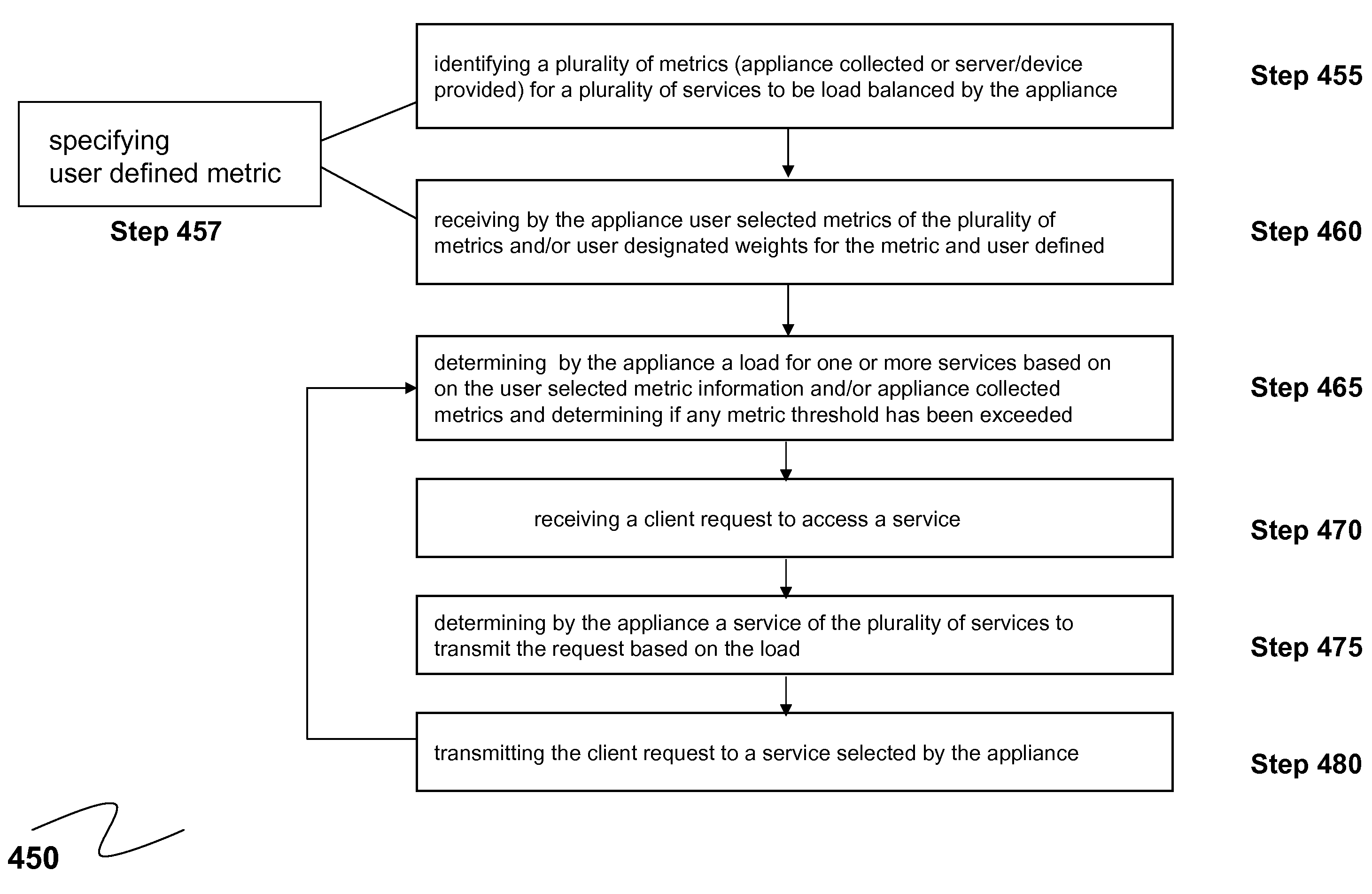
Systems and Methods for Providing Global Server Load Balancing of Heterogeneous Devices
ActiveUS20080225718A1Good for load balancingGood flexibilityError preventionTransmission systemsVia deviceExchange protocol
The present invention provides improvements to load balancing by providing a load balancing solution that distributes a load among a plurality of heterogenous devices, such as different types of local load balancers, using metrics collected from the different devices. The load balancing appliance collects metrics from heterogenous devices using a network management protocol and communication model, such as a Simple Network Management Protocol (SNMP). These heterogenous device metrics are available on the load balancing appliance with appliance determined metrics and metrics obtained by the appliance from homogenous devices using a metric exchange protocol. Via a configuration interface of the appliance, a user can select one or more of these different metrics for global load balancing. As such, the load balancing appliance described herein obtains a multitude of metrics from the different devices under management. Additionally, the load balancing appliance described herein provides great flexibility in allowing the user to configure the global load balancer based on the user's understanding of these multitudes of metrics and to take into account the different characteristics and behaviors of the heterogenous devices.
Owner:CITRIX SYST INC
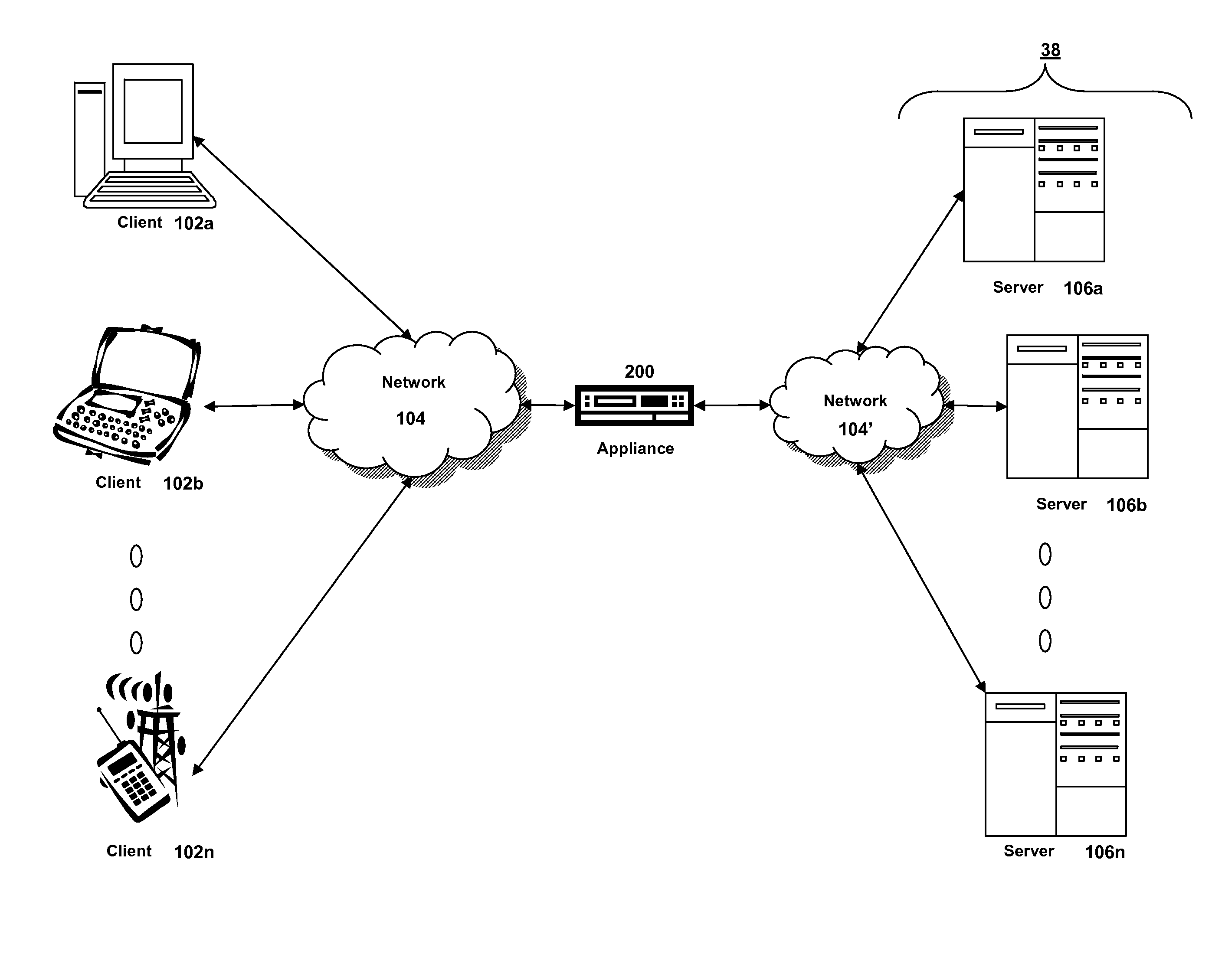
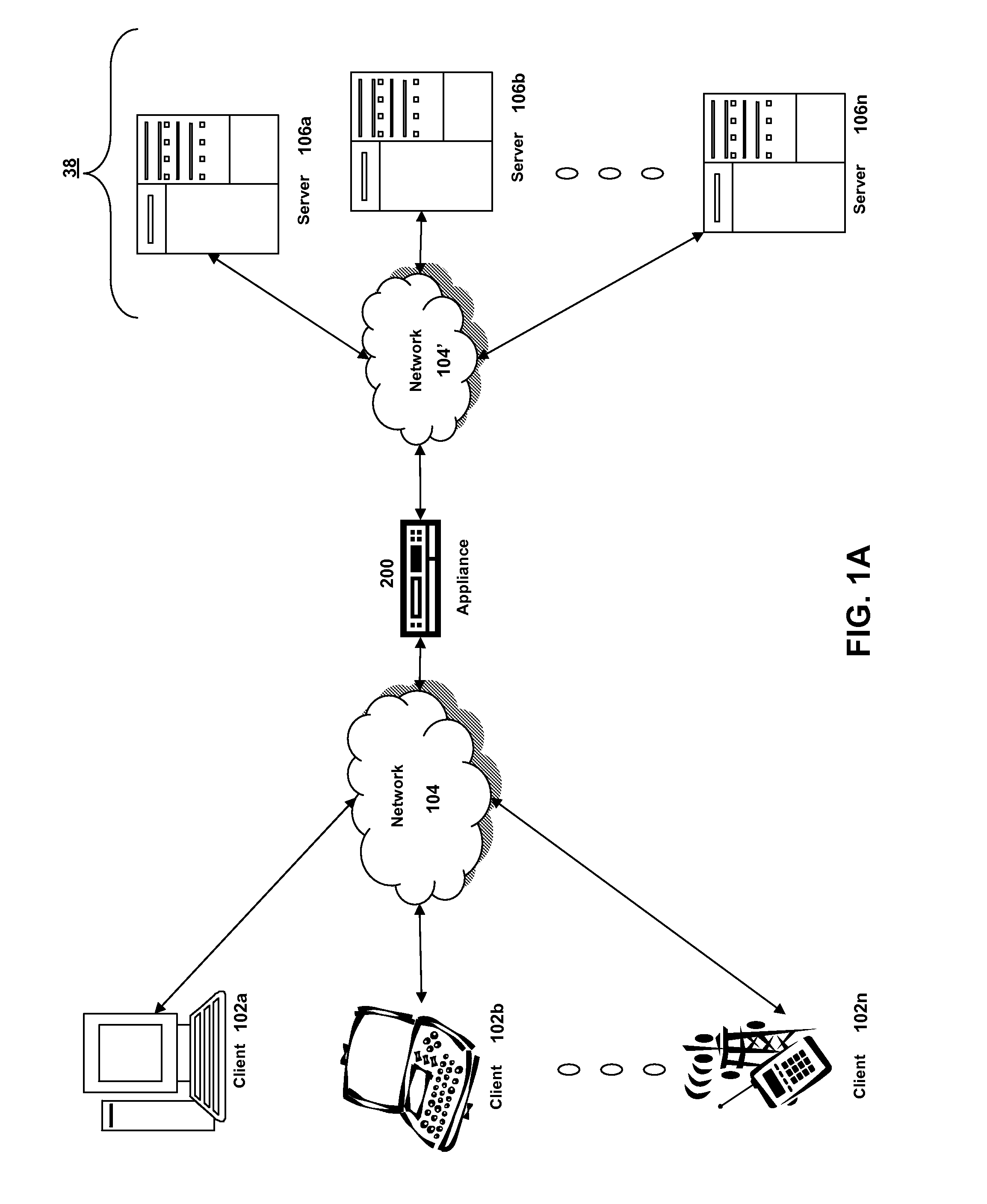
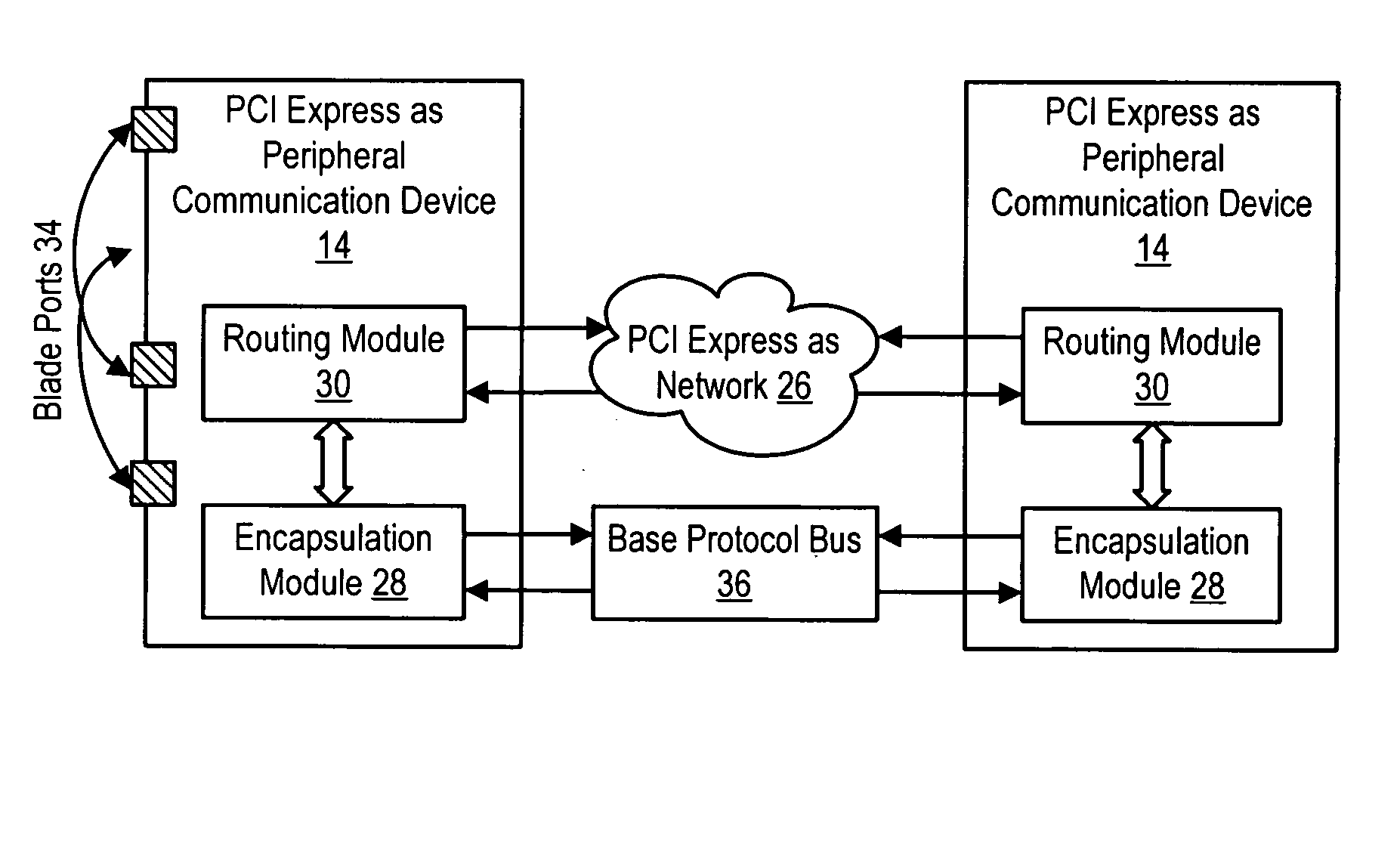
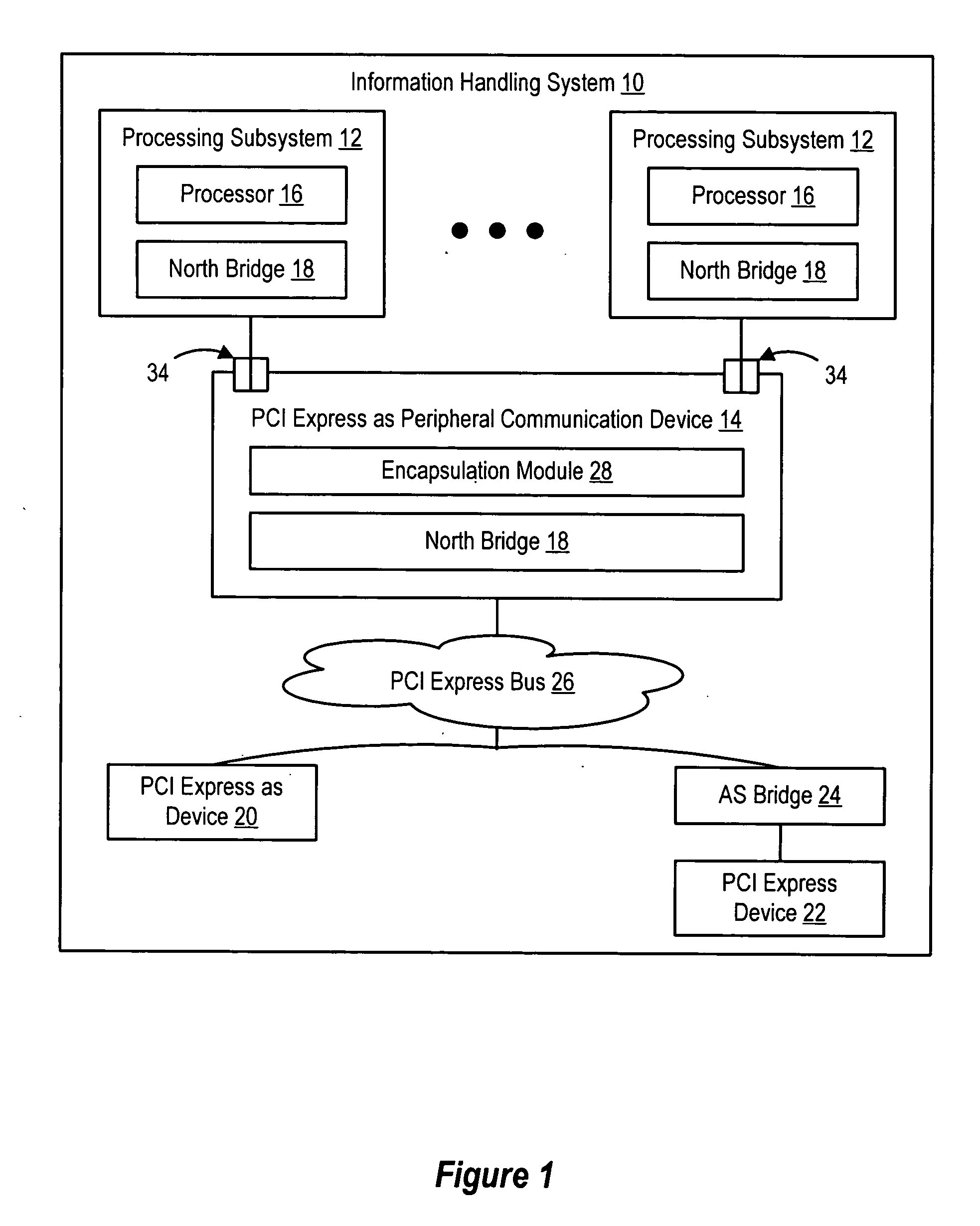
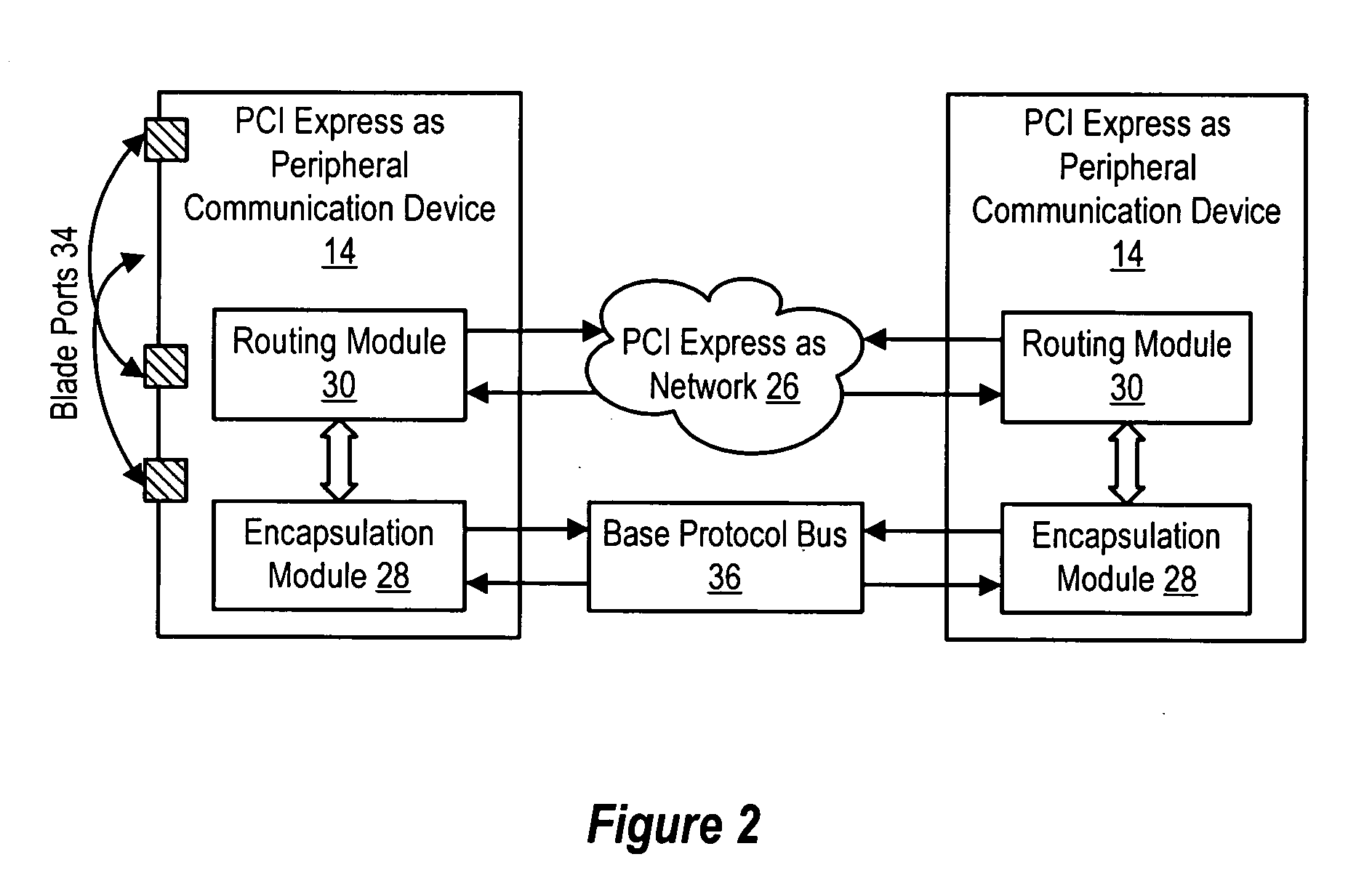
System and method for information handling system PCI express advanced switching
InactiveUS20050262269A1Simple processReduce disadvantagesConcurrent instruction executionMultiple digital computer combinationsInformation processingData pack
Plural processing subsystems of an information handling system, such as plural blades of a blade server, communicate through a base protocol, such as PCI Express, to a peripheral communication device with each processing subsystem interfaced through a port of the peripheral communication device. An encapsulation module of the peripheral communication device encapsulates the base protocol in an advanced switching packet, such as a packet formed with the PCI Express Advanced Switching protocol. A routing module of the peripheral communication device routes the packets through a bus, such as a blade server backplane bus, for use of the information by a selected peripheral. Peripherals communicate with selected processing subsystems by sending advanced switching packets to the routing module for the encapsulation module to extract the peripheral information from the packets and send the peripheral information to the port associated with the selected processing subsystem.
Owner:DELL PROD LP
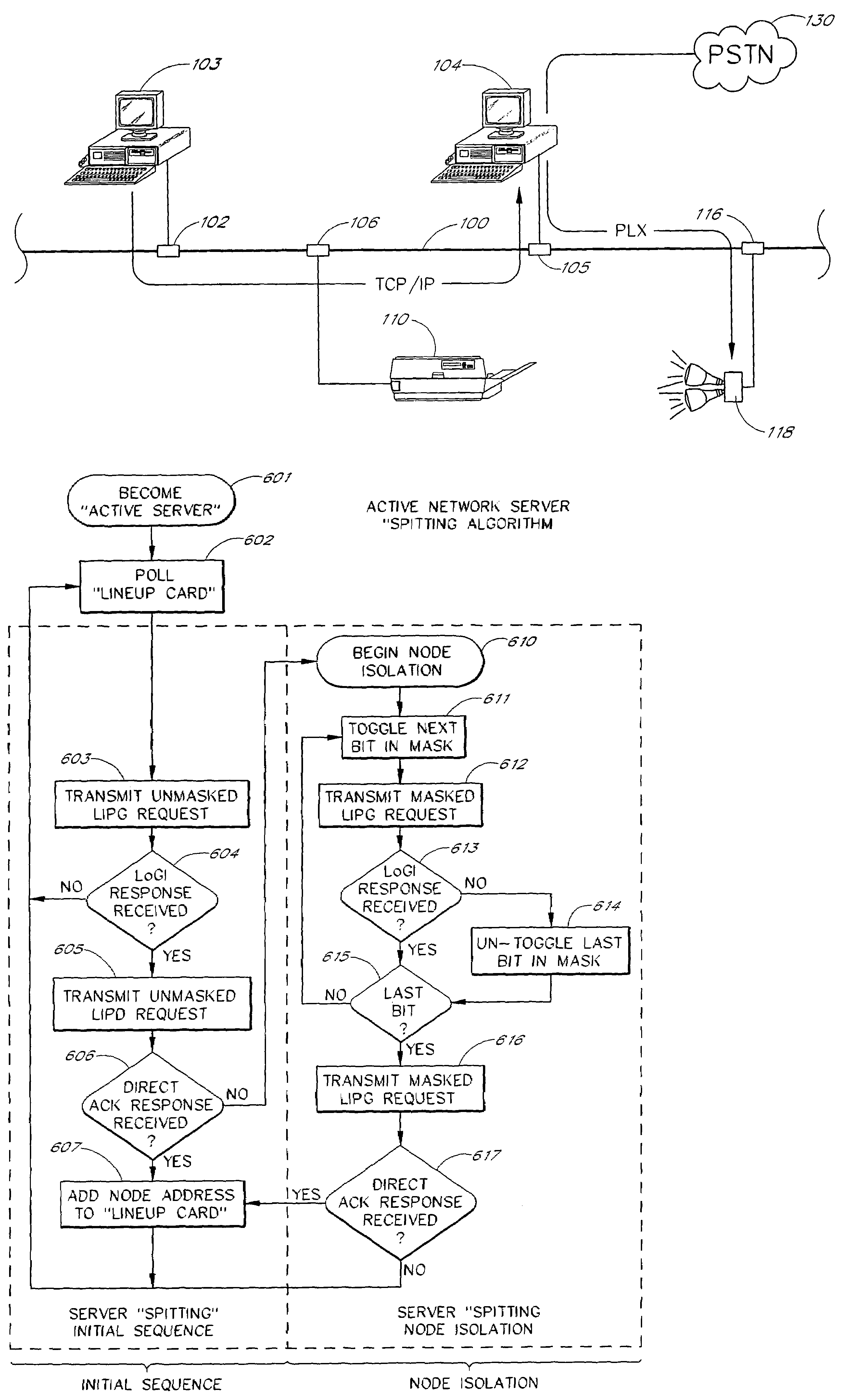
Multi-channel power line exchange protocol
InactiveUS7310670B1Easy to usePreserve bandwidthError prevention/detection by using return channelDigital data processing detailsStream dataExchange protocol
A scalable networking protocol that allows multiple nodes to communicate via a multi-channel network medium is described. The networking protocol allows any node on the network to assign itself as the active network server. The active network server polls client nodes based on a lineup card. The lineup card includes a high priority queue for low-latency devices, and a low priority queue for devices that can tolerate higher latencies. Network information is sent on the channels as fragments. The protocol provides bad-channel detection and retransmission of fragments in a fragment-by-fragment basis. Support for streaming data or asynchronous data is provided by allocating time slots on the network and allowing two intelligent nodes to talk directly to each other during count-limited token sessions, as arbitrated by the active network server. The network node serving as the active network server can be changed on a dynamic basis, and is typically determined by the first node initiating a transmit request on a sleeping network. Client nodes are addressed by dynamic-polling using an address isolation scheme.
Owner:INARI +2
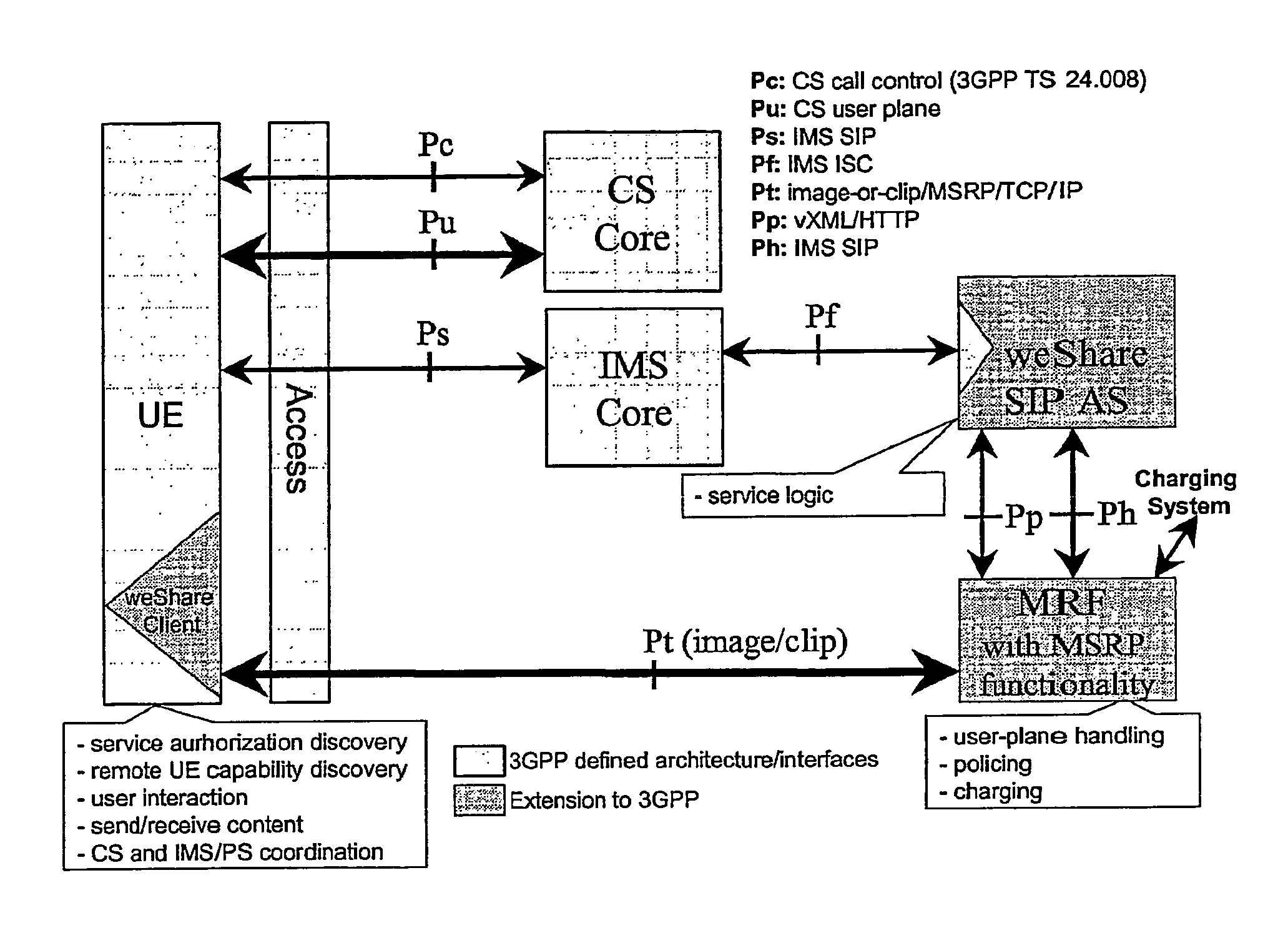
Exchange Protocol For Combinational Multimedia Services
A method of transporting information between end user terminals via a packet switched network whilst a circuit switched connection is established between the end users, the method comprising: using the Message Session Relay Protocol, MSRP, to encapsulate information transmitted between users.
Owner:TELEFON AB LM ERICSSON (PUBL)
Methods and apparatus for data communication using a hybrid transport switching protocol
InactiveUS6631136B1Digital computer detailsData switching by path configurationStructure of Management InformationNetwork structure
A data communication method enables the transfer of data having different protocols without requiring increased bandwidth in the transmission line. The system efficiently re-routes data in the event of network alterations and determines a fast and efficient way to transport data based on the then-existing network structure using link-state and distance vector techniques.
Owner:HYPERCOM CORP
Collision rectification in wireless communication devices
InactiveUS7177294B2Reduce data conflictsReduced packetNetwork traffic/resource managementNetwork topologiesWireless transmissionWireless mesh network
Wireless communication networks utilize various communication protocols to exchange data between wireless network devices. Overlapping communication frequencies between data exchange protocols present a collision problem when data transmissions interfere with one another during wireless transit. A device for moderating transmission traffic in a wireless network where overlapping communication frequencies coexist is described to reduce or avoid interference caused by signal collisions.
Owner:AVAGO TECH INT SALES PTE LTD
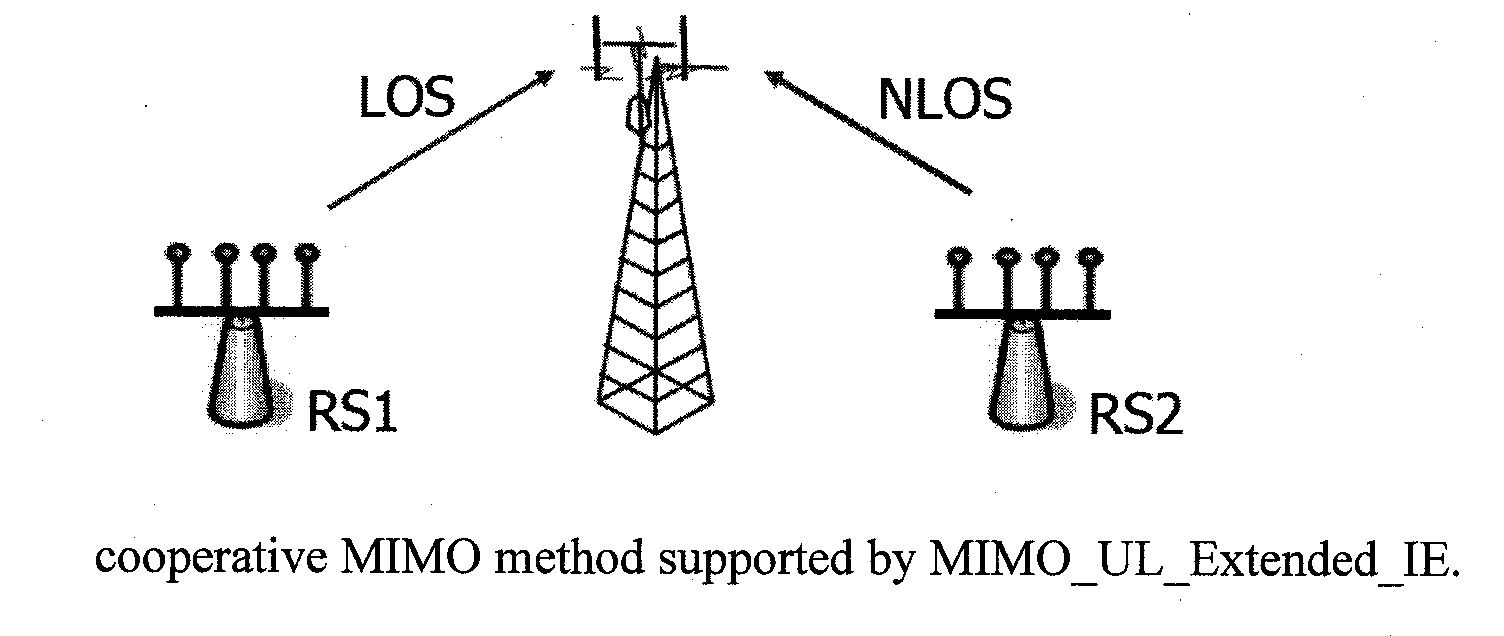
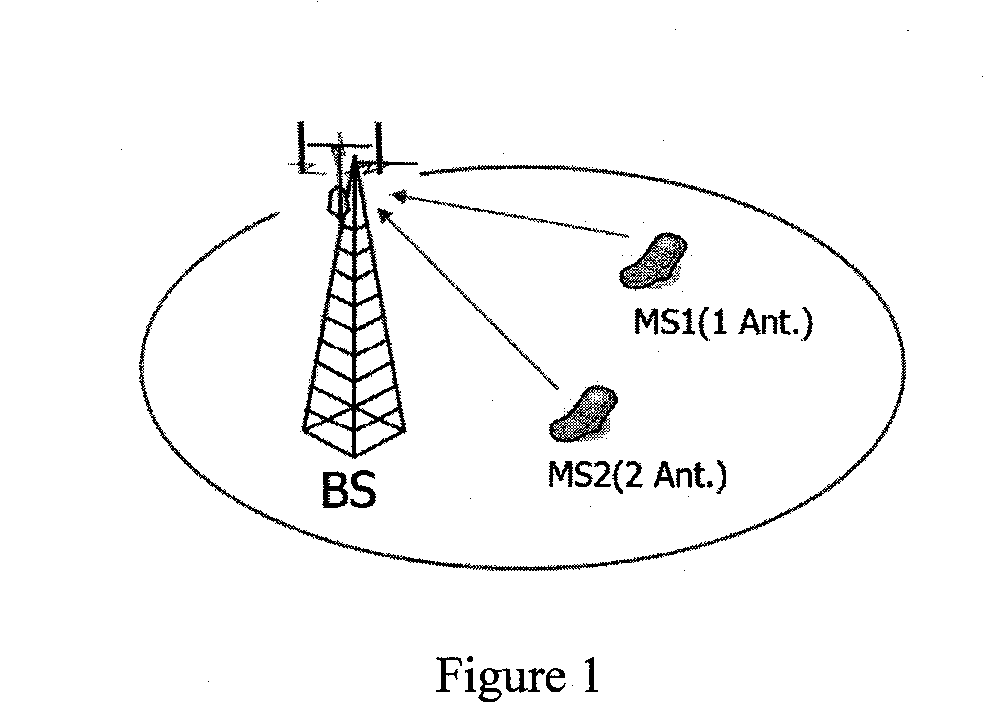
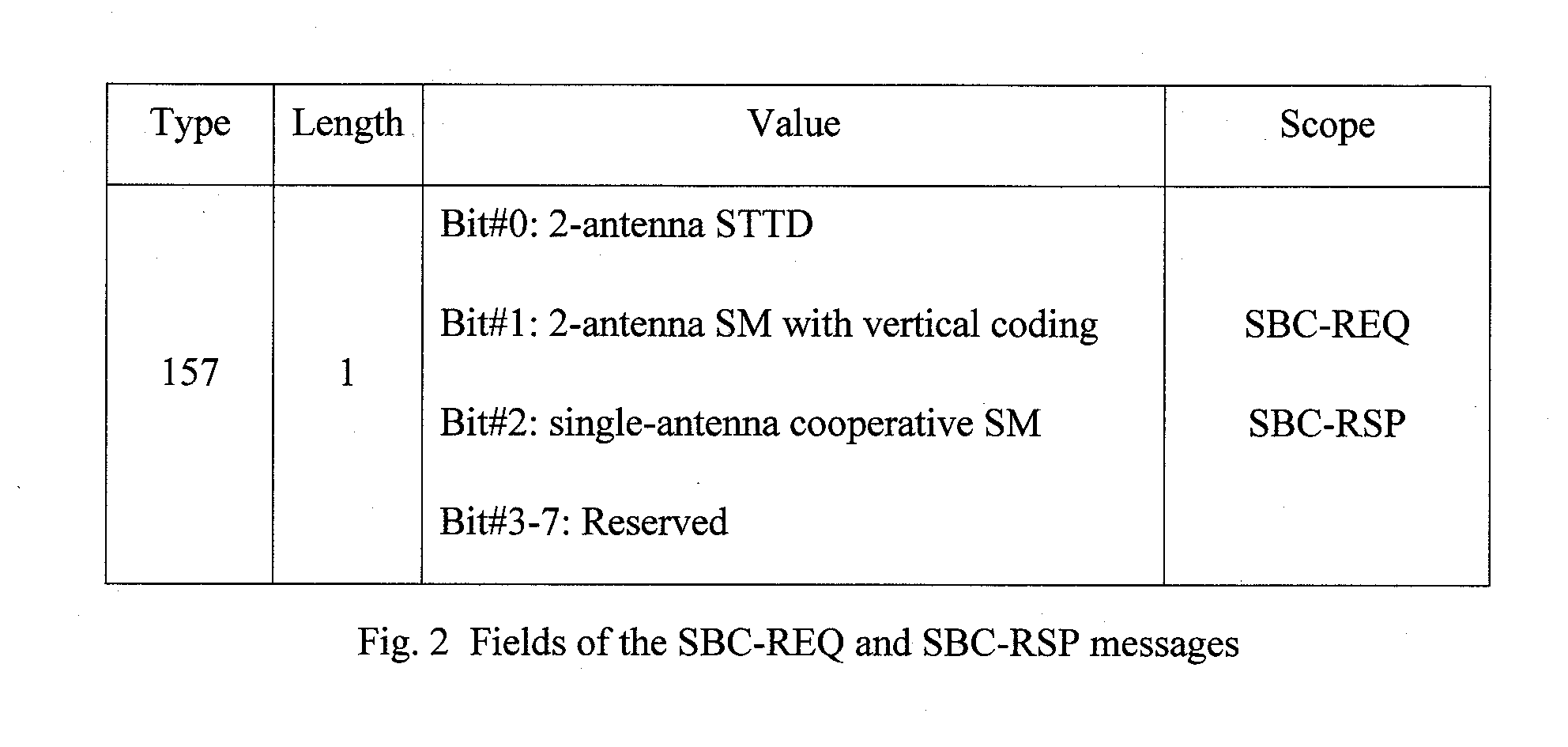
Uplink multiple-input-multiple-output (MIMO) and cooperative MIMO transmissions
A method is provided for MIMO uplink communications between a base station and a wireless station with more than two antennae. The method includes: (a) negotiating between the base station and the wireless station uplink MIMO / cooperative MIMO capabilities, using a message exchange protocol in which a message exchanged comprises a field for specifying uplink MIMO / cooperative MIMO capabilities; (b) the base station receiving a request from the wireless station for data transmission; (c) the base station sending the wireless station an allocated resource and an uplink MIMO / cooperative MIMO method for uplink transmission; (e) the wireless station mapping data symbols to the allocated resource with proper pilot pattern; and (f) the base station detecting the data symbols from the channel.
Owner:NTT DOCOMO INC
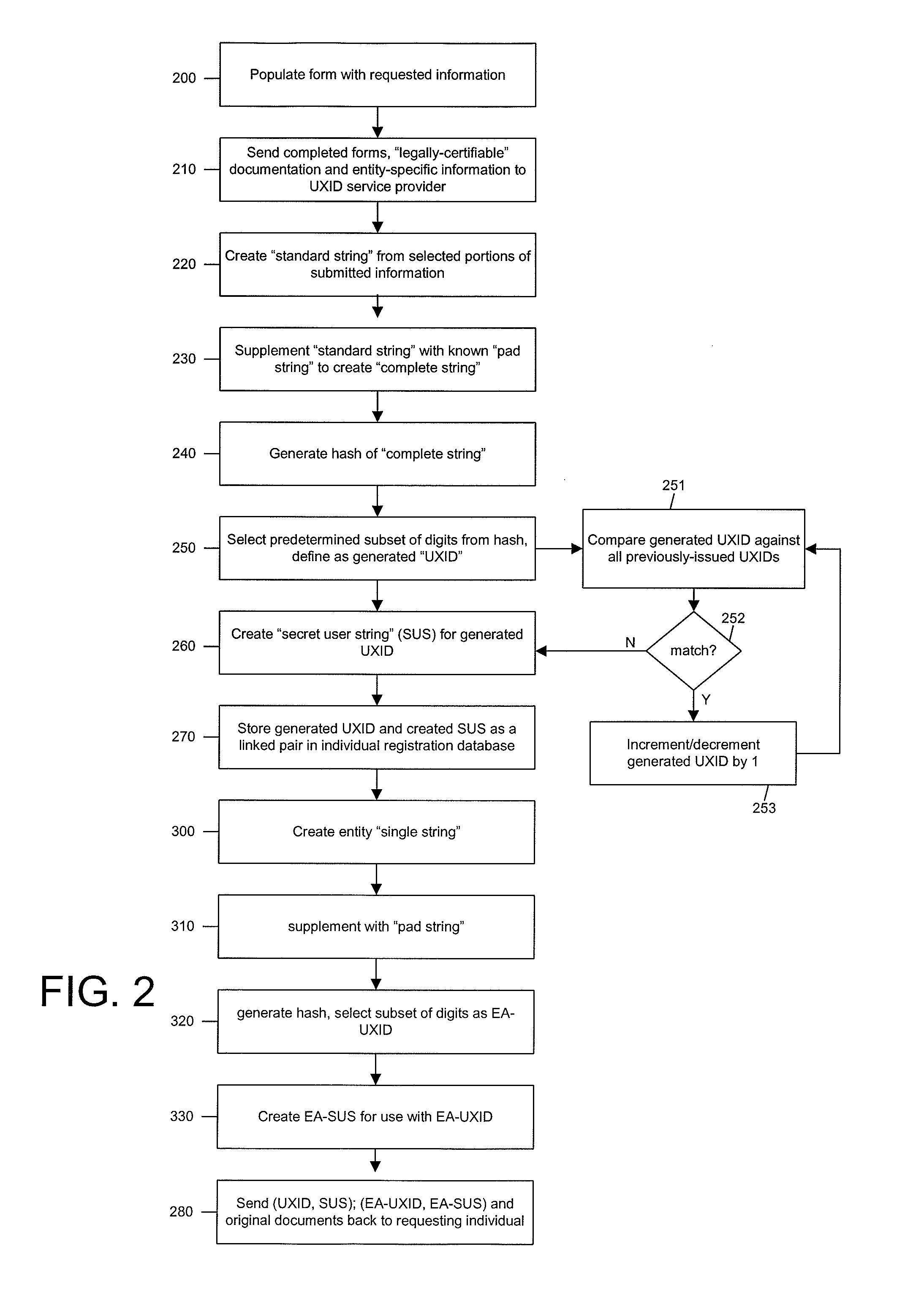
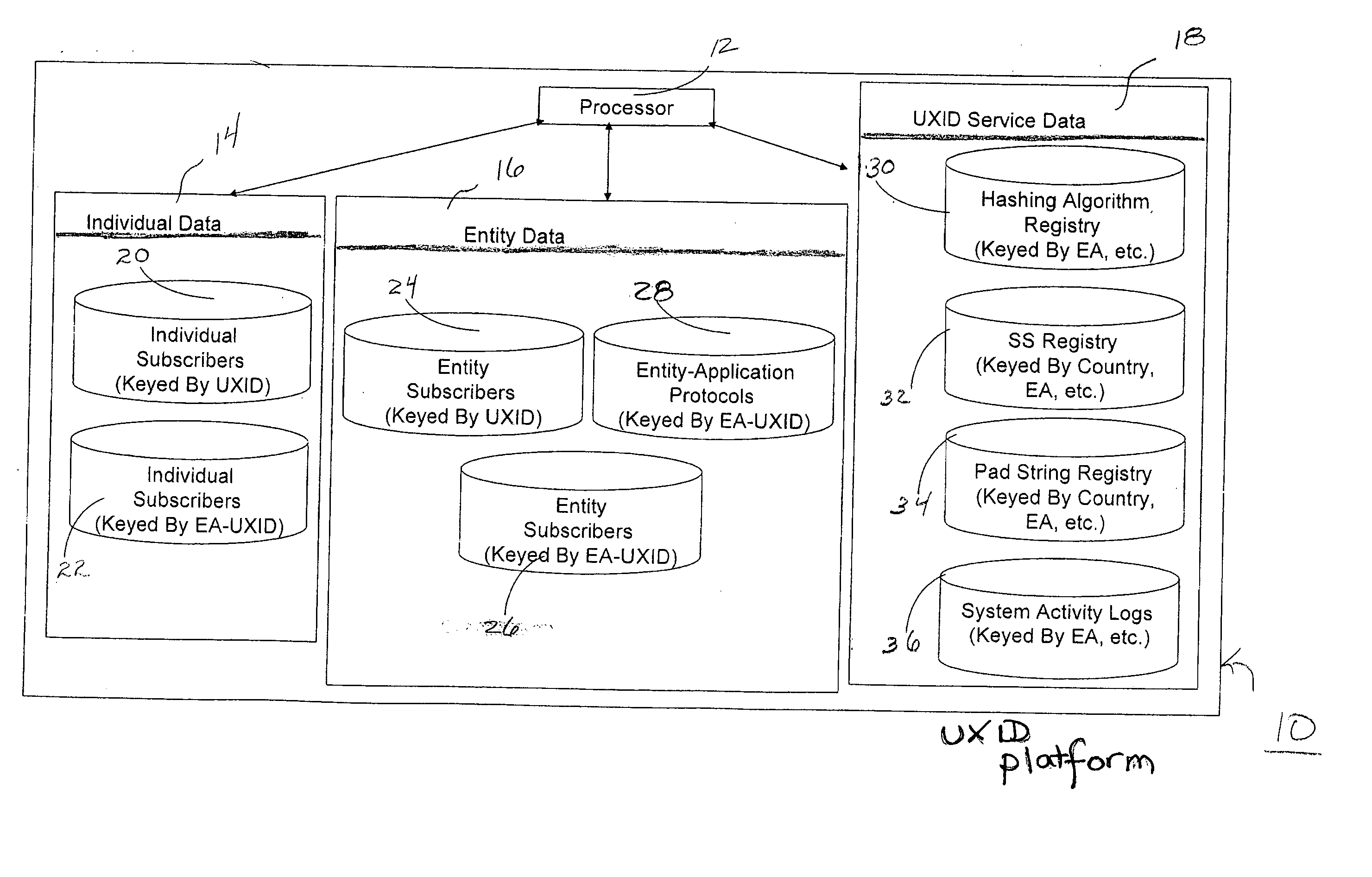
Systems and methods for controlling data access by use of a universal anonymous identifier
ActiveUS8042193B1Digital data processing detailsUser identity/authority verificationDocumentation procedureHash function
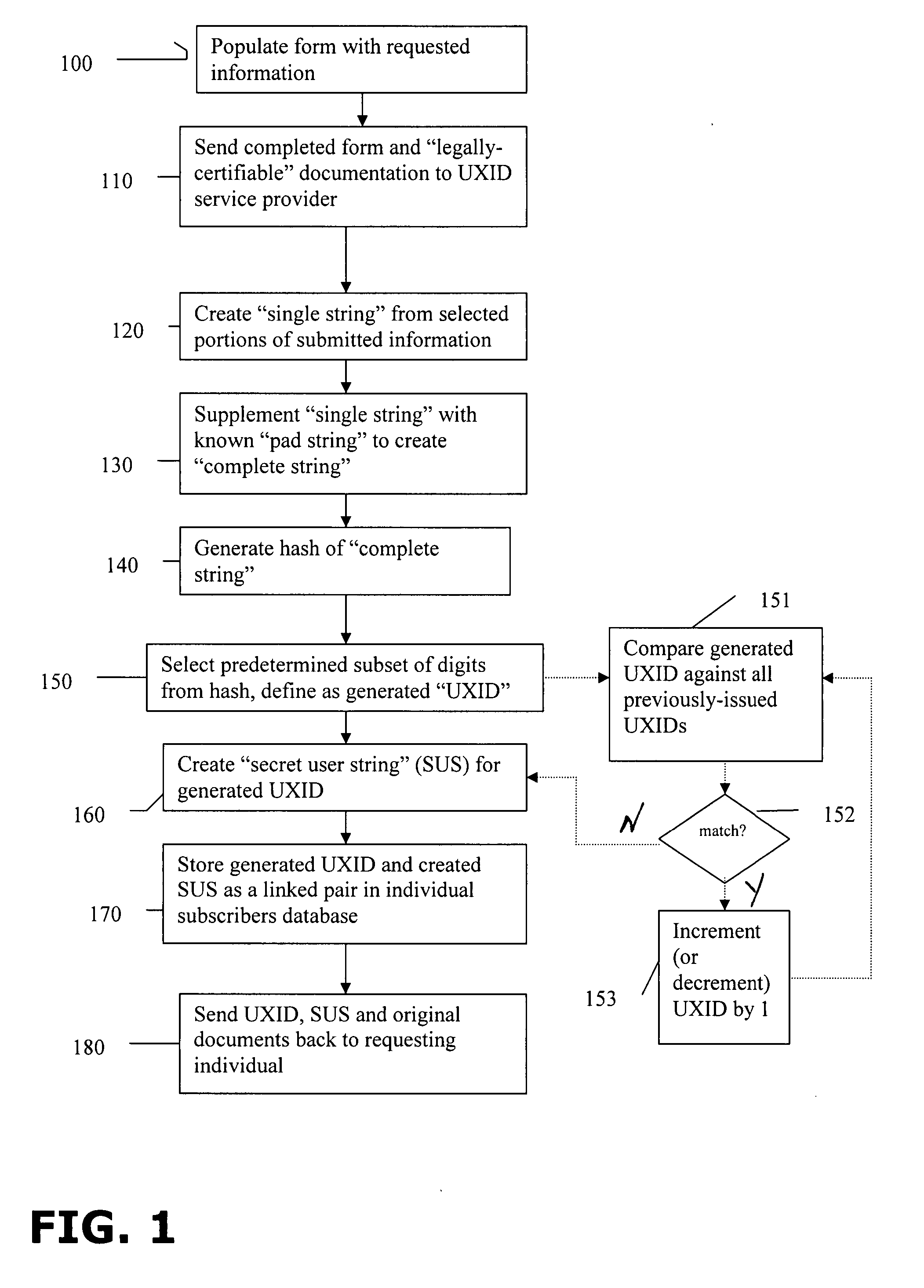
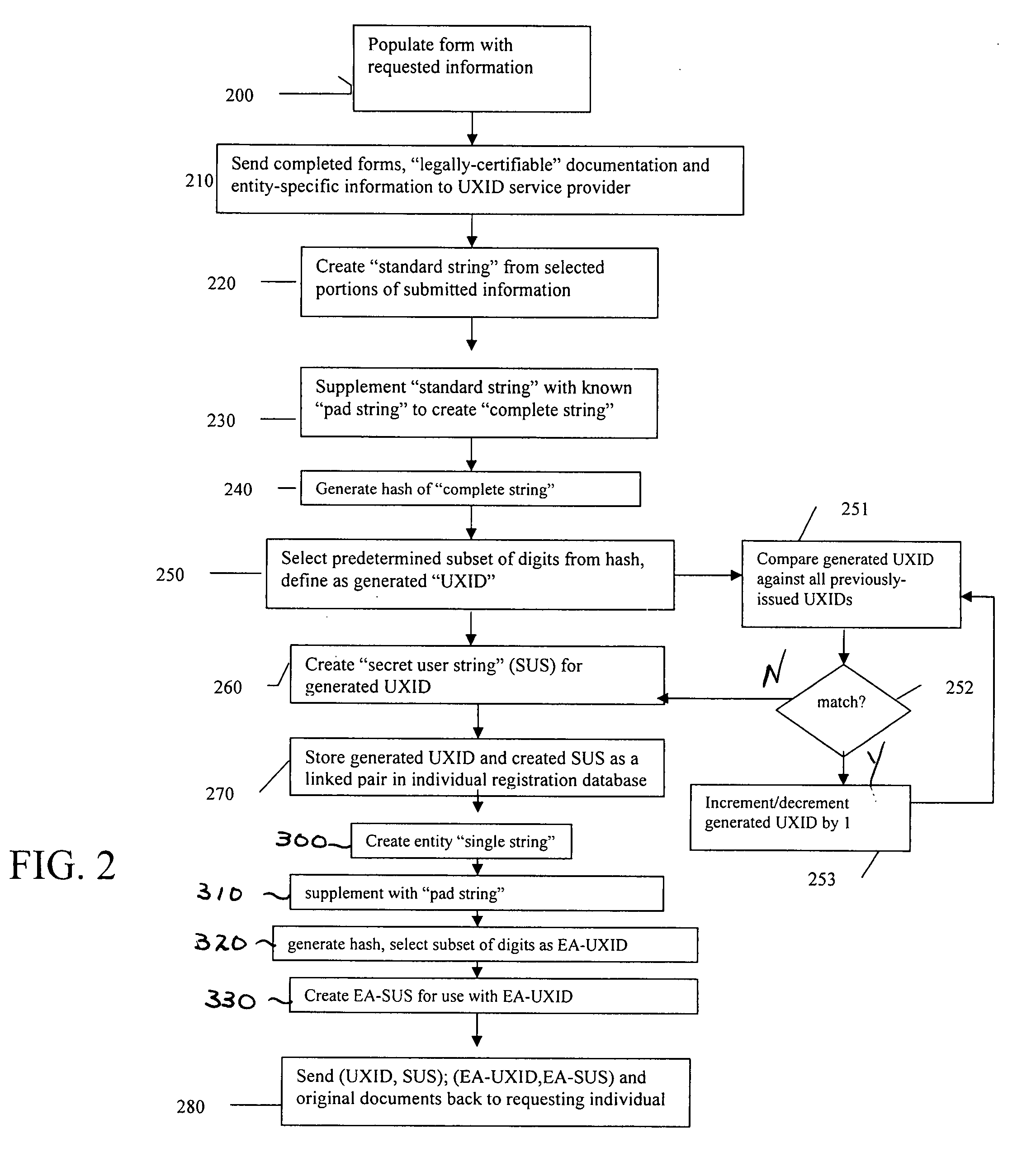
A universal anonymous data collection and exchange service is provided where individuals and entities initially register with the service utilizing “legally authentic” identity documentation to obtain a “universal ID” (UXID). The UXID consists of a sting of alphanumeric digits selected from a hash function that is performed on a string of personally identifying information. Once registered, the individual and entity UXIDs are used as a means by the service to engage in a pre-defined confidential data collection and exchange protocol between participating, registered UXID holders. The service is designed for use across many applications, individuals and entities, and may support one-time or recurring collection of data.
Owner:ALBRIGHT ASSOCS
Systems and methods for authenticating communications in a network medium
ActiveUS20060174116A1Communication securityKey distribution for secure communicationUser identity/authority verificationKey exchangeExchange protocol
Pre-authentication information of devices is used to securely authenticate arbitrary peer-to-peer ad-hoc interactions. In one embodiment, public key cryptography is used in the main wireless link with location-limited channels being initially used to pre-authenticate devices. Use of public keys in the pre-authentication data allows for the broadening of types of media suitable for use as location-limited channels to include, for example, audio and infrared. Also, it allows a range of key exchange protocols which can be authenticated in this manner to include most public-key-based protocols. As a result, a large range of devices, protocols can be used in various applications. Further, an eavesdropper is forced to mount an active attack on the location-limited channel itself in order to access an ad-hoc exchange. However, this results in the discovery of the eavesdropper.
Owner:CISCO TECH INC
Coordinating transactional web services
ActiveUS7047243B2Overcome disadvantagesData processing applicationsWebsite content managementWeb serviceExchange protocol
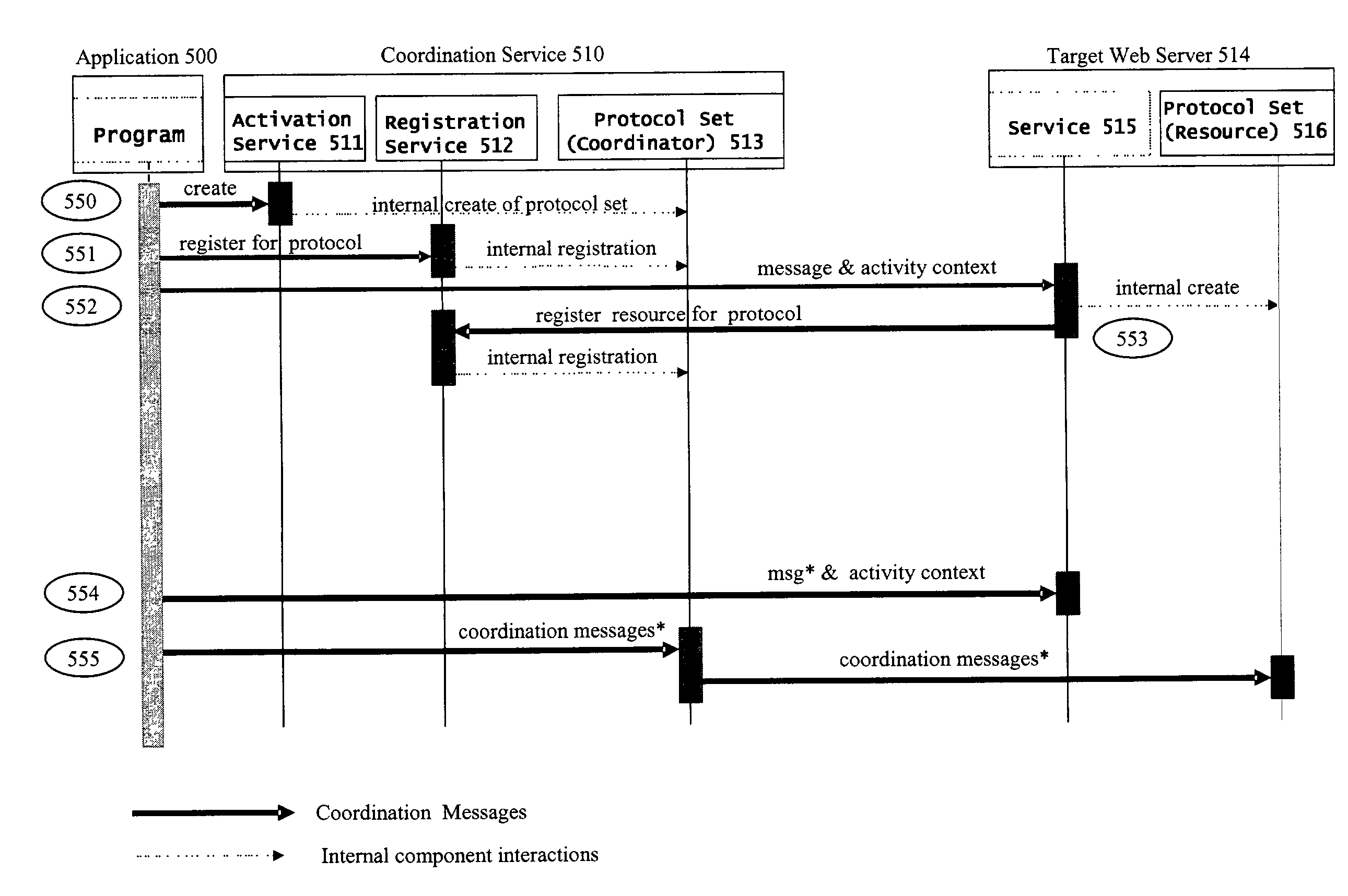
The present invention relates to coordinating web services wherein a coordination service acts as a rendezvous point through which participants such as web services may register to obtain protocol information to coordinate an outcome of an activity. The coordination of the activity may be accomplished through behaviors that may be expressed by message exchange protocols prescribed by the participants or web services themselves in an open-ended manner. A method and apparatus is also provided for coordinating web service activity with associated behaviors. Transactional coordination may be performed using the ACID model for activities requiring strict consistency or may be based on compensation actions for long running transactions, for example.
Owner:MICROSOFT TECH LICENSING LLC
Ultrasound information processing system and ultrasound information exchange protocol therefor
InactiveUS6839762B1Exact matchGuaranteed normal transmissionStethoscopeMultiple digital computer combinationsInformation processingEngineering
An ultrasound information processing system comprises a plurality of ultrasound devices coupled to a high-speed serial ultrasound information bus, wherein each ultrasound device comprises a program for communicating with other ultrasound devices according to an ultrasound information exchange protocol (UIEP). The UIEP is a lightweight, connection-oriented protocol adapted to efficiently transfer ultrasound information among different devices on the ultrasound information bus. Each ultrasound device comprises an application layer program for performing an ultrasound function, as well as a lower protocol layer program for receiving and sending data across the ultrasound information bus according to a high-speed serial bus standard that provides both isochronous and asynchronous data delivery. The ultrasound information exchange protocol (UIEP) program is adapted to receive a communication request from the application layer, open a connection-oriented communication session with the requested ultrasound device, and transfer ultrasound information through the lower protocol layer and across the ultrasound information bus to the requested device. Advantageously, any ultrasound device manufacturer provided with the UIEP program may readily generate application layer code capable of communicating with other manufacturers' ultrasound devices across the ultrasound information bus, without requiring specific knowledge of the internal structure of the other manufacturers' devices or of the specific frame / packet structure of the UIEP / lower layer protocols themselves.
Owner:U SYST
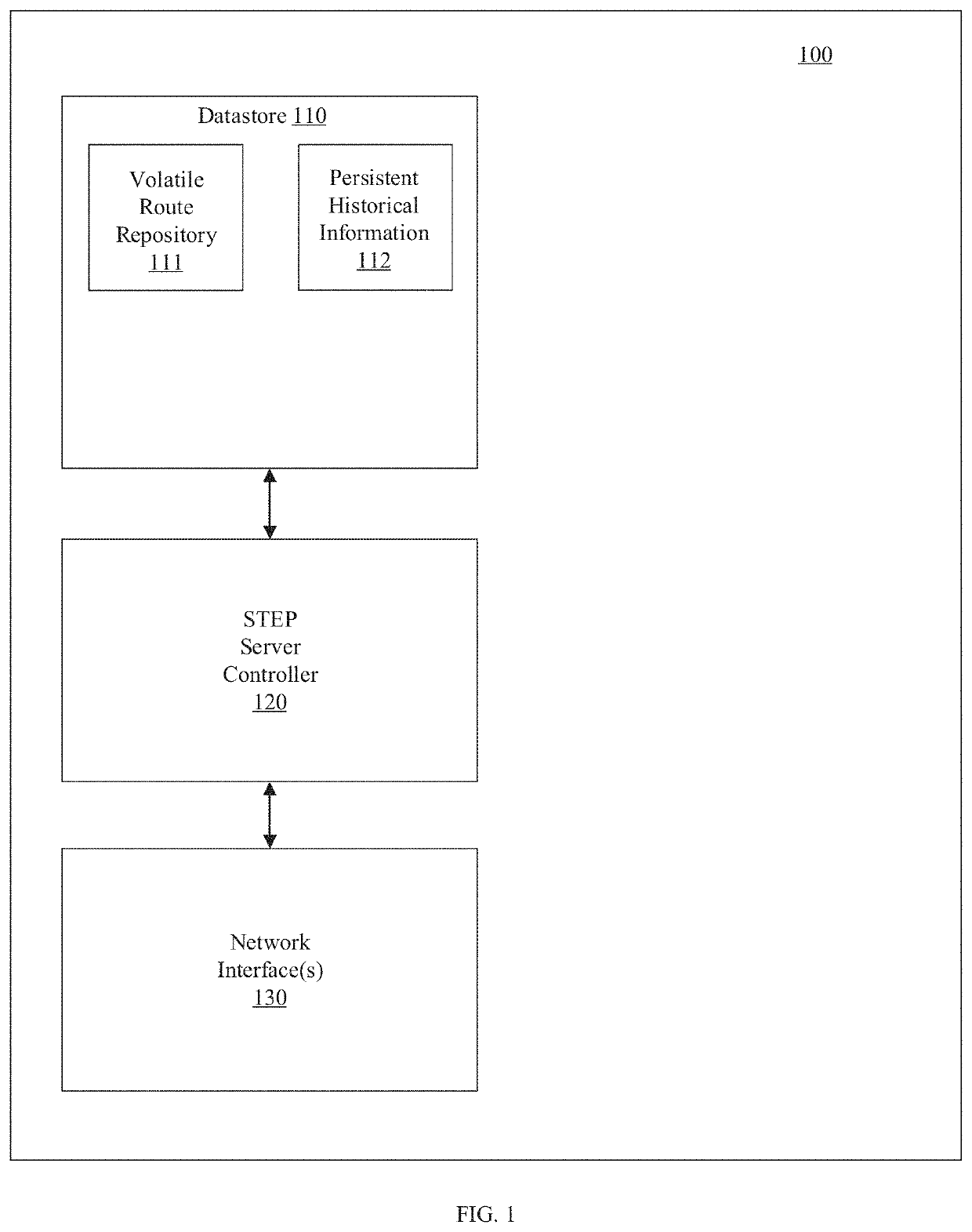
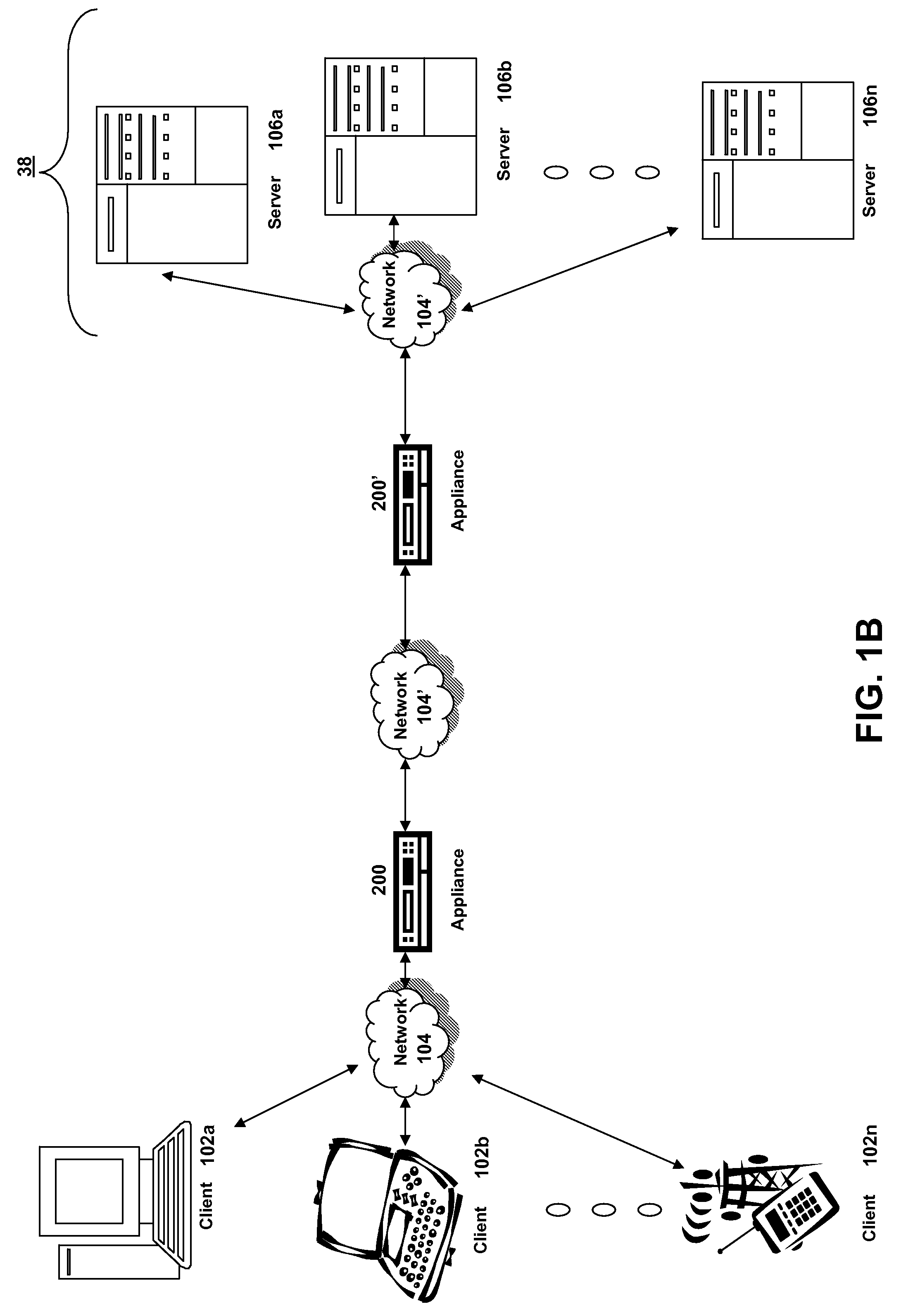
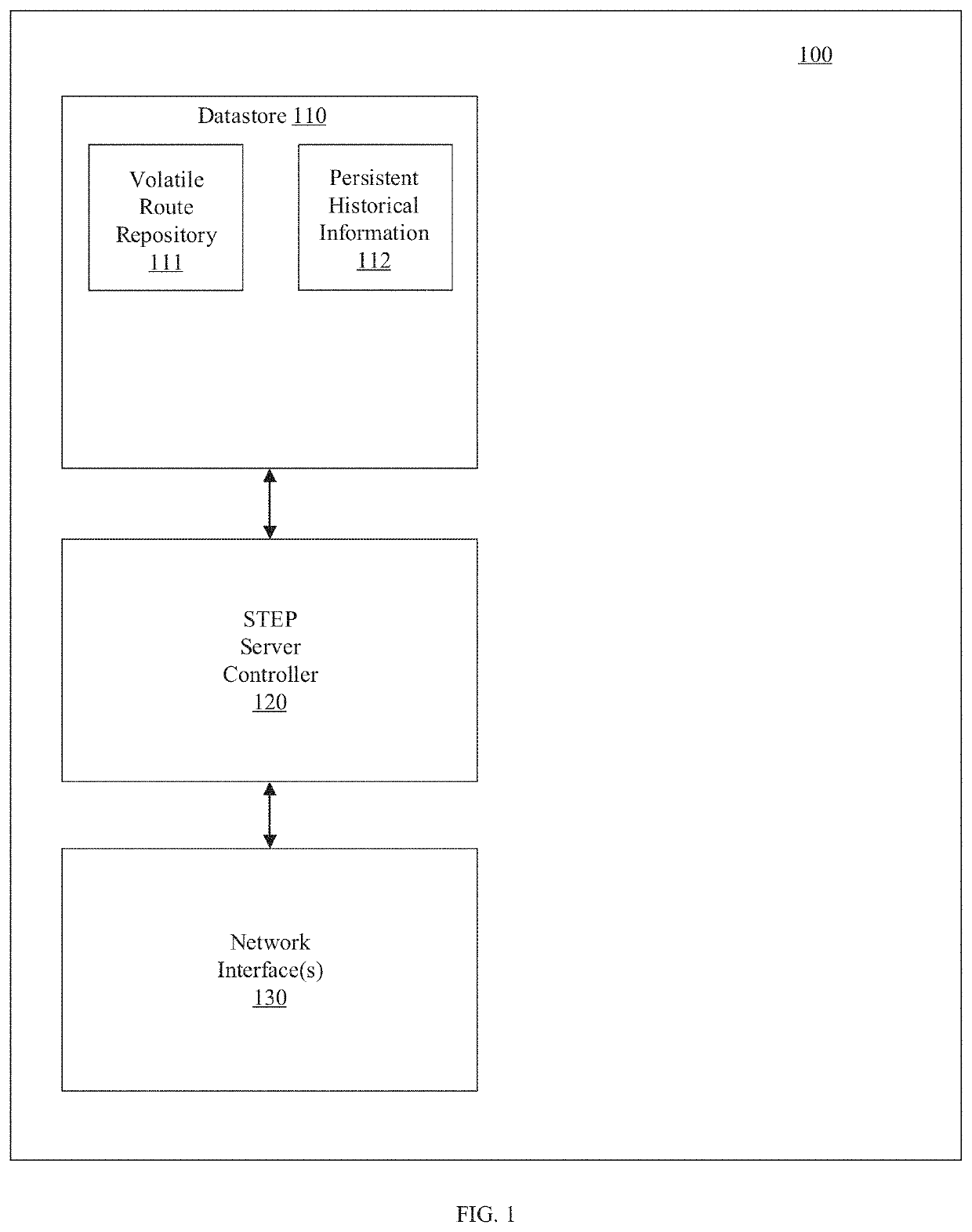
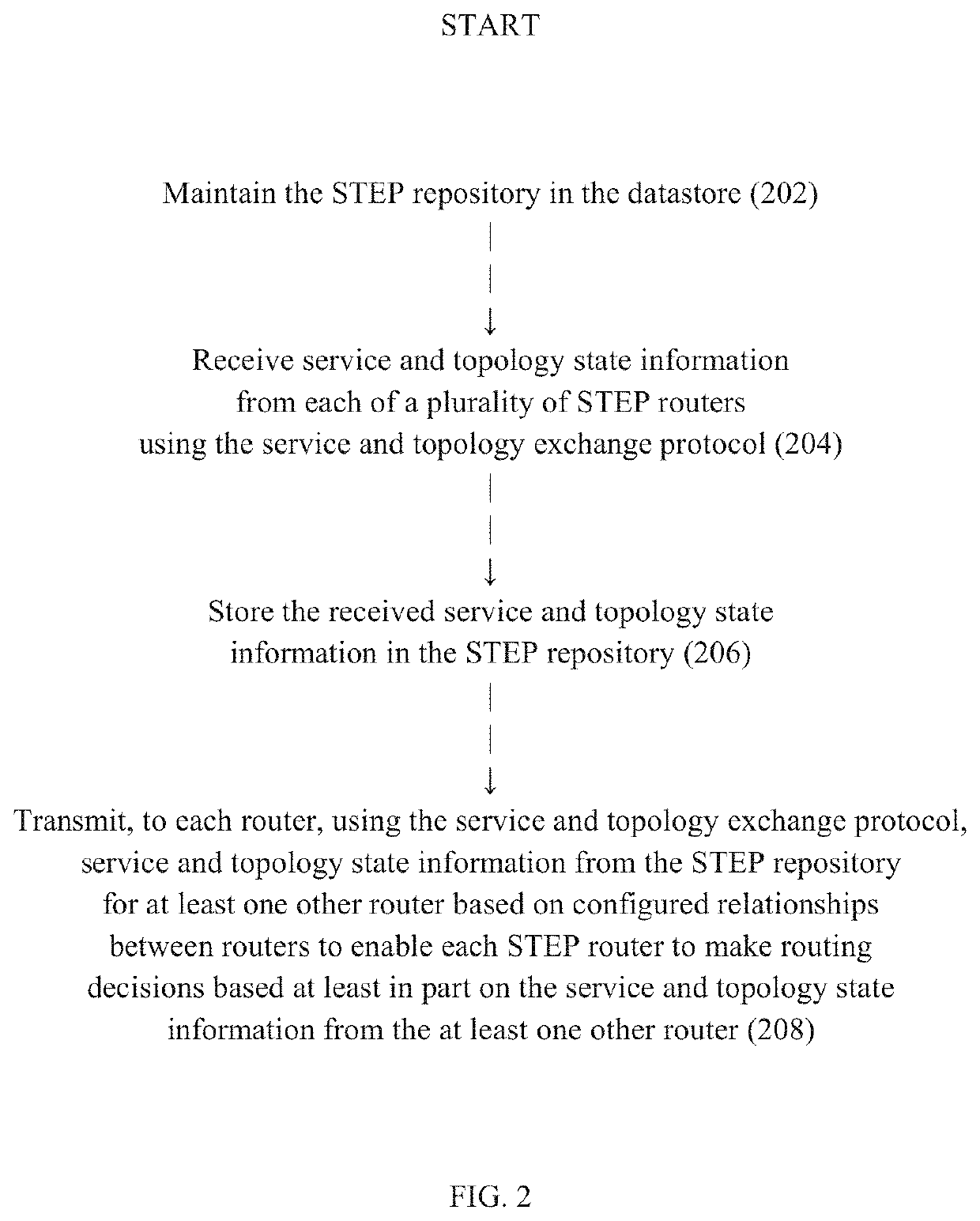
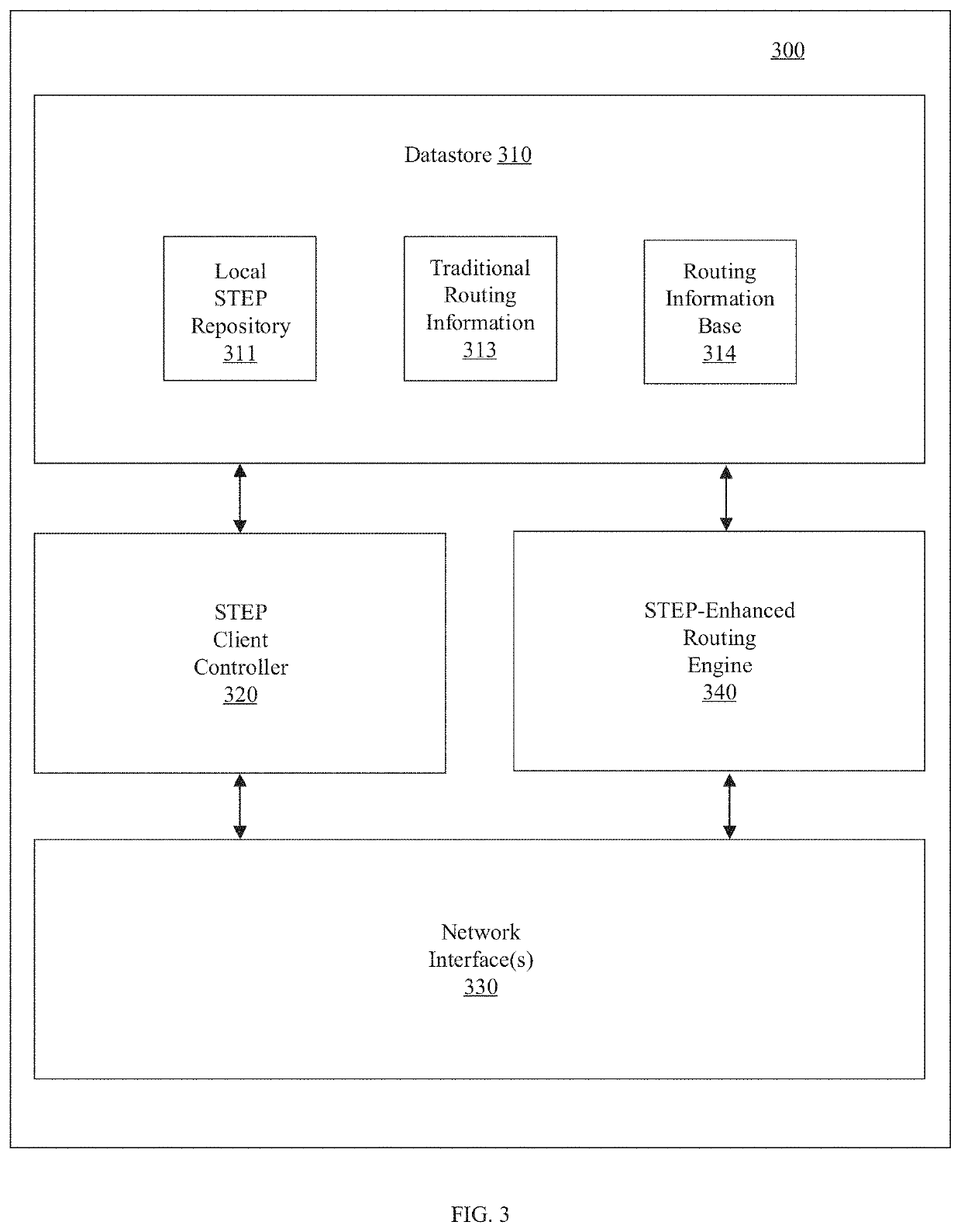
Central authority for service and topology exchange
A routing system for implementing a service and topology exchange protocol (STEP) comprises a primary STEP server configured to maintain a STEP repository and a plurality of routers, each router including a STEP client in communication with the primary STEP server. The STEP client of each router is configured to transmit, using the service and topology exchange protocol, service and topology state information for at least one route or service available through the router to the primary STEP server for storage in the STEP repository. The primary STEP server is configured to determine, for each router, whether the STEP repository includes any service and topology state information changes for the router based at least in part on the service and topology state information received from the routers and to transmit to the STEP client of each router for which there are service and topology state information changes, using the service and topology exchange protocol, only the service and topology state information changes.
Owner:128 TECH
Systems and methods for GSLB remote service monitoring
The present invention provides improvements to the integration between a metric exchange protocol and a monitoring mechanism supporting load balancing by a Global Server Load Balancing (GSLB) appliance in a GSLB hierarchy of appliances, using a method for triggering a monitor on a remote service. The method includes receiving, by a first appliance, metrics of a second appliance via a metric exchange connection between the first and second appliances. The first appliance includes a GSLB service and identifies a service provided via the second appliance as a remote service for GSLB. The first appliance may identify via the metrics that a state of the service is up, and determine that the metric exchange connection is down. Responsive to the determination, the first appliance may trigger a monitor to monitor the status of the service. Further, the first appliance may obtain via the monitor a second status of the service.
Owner:CITRIX SYST INC
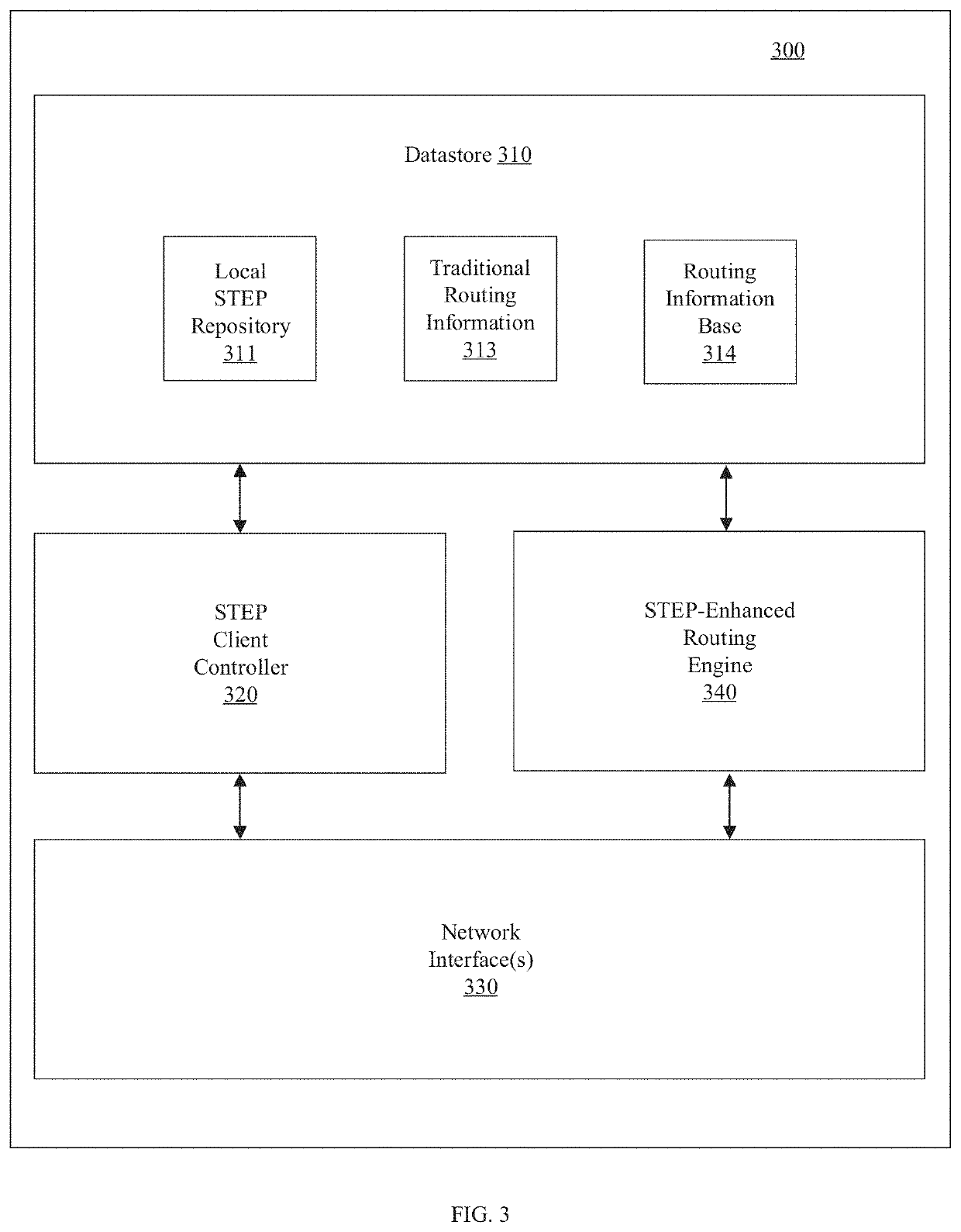
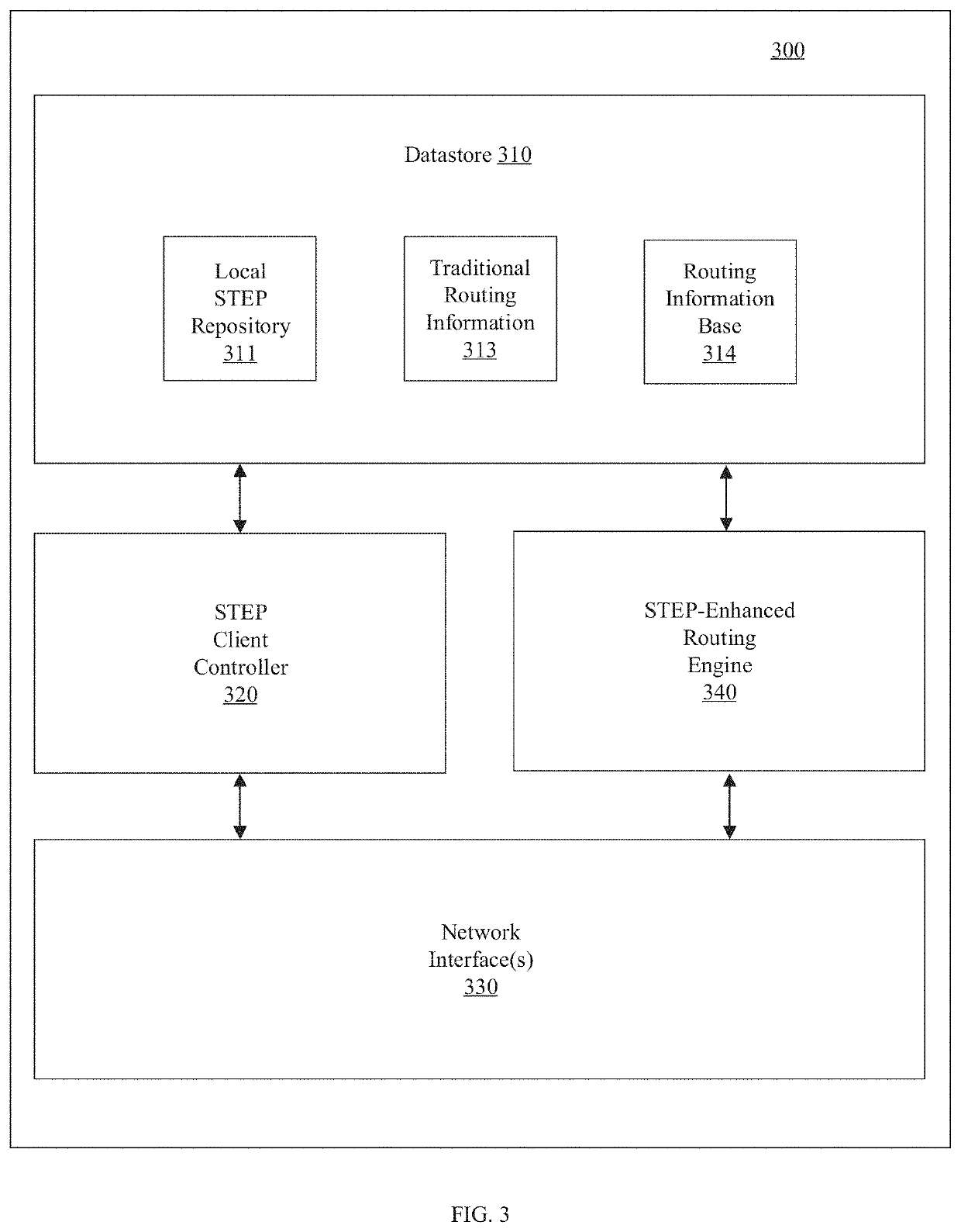
Service and topology exchange protocol
A routing system for implementing a service and topology exchange protocol (STEP) includes a primary STEP server configured to maintain a STEP repository and a plurality of routers, with each router including a STEP client in communication with the primary STEP server. The STEP client of each router is configured to transmit, using STEP, STEP documents containing service and topology state information for at least one route or service available through the router to the primary STEP server for storage in the STEP repository. The primary STEP server is configured to transmit to the STEP client of each router, using STEP, service and topology state information from the STEP repository for at least one other router based on configured relationships between routers. Each router is configured to make routing decisions based at least in part on the service and topology state information from the at least one other router.
Owner:128 TECH
Source-based routing
A routing system for routing packets for a route or service comprises a plurality of routers including a source router, wherein the source router is configured to receive, using a service and topology exchange protocol, service and topology state information from a STEP repository for at least one other router based on configured relationships between routers; determine a first path to a destination for a route or service based on the service and topology state information, the first path including an ordered list of successive routers to receive a packet associated with the route or service starting with a first successive router and ending with a destination router; and transmit a packet toward the first successive router with first metadata including a list of at least one remaining router of the ordered list of routers to receive the packet associated with the route or service. Each successive router, starting with the first successive router, is configured to receive a packet and determine if the router is the destination router based on metadata associated with the received packet, and when the router is not the destination router, forward the packet toward a next successive router in the ordered list of routers.
Owner:128 TECH
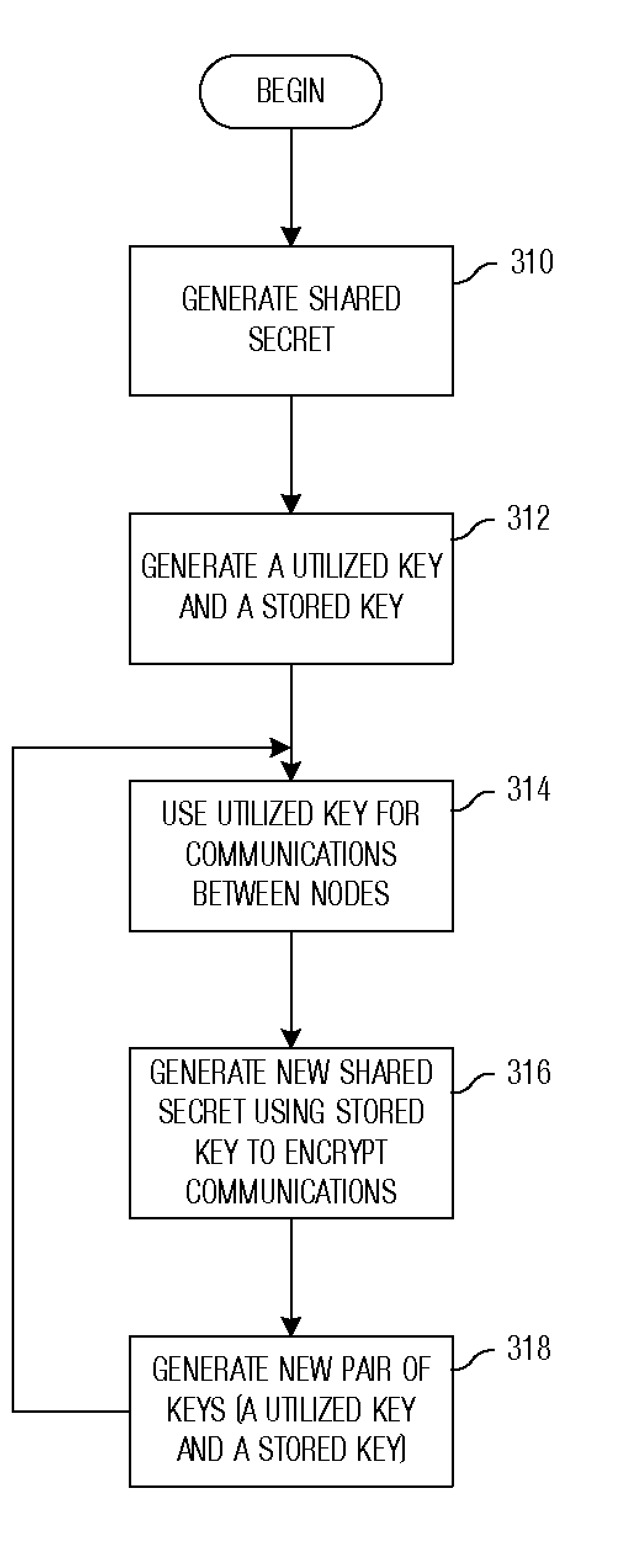
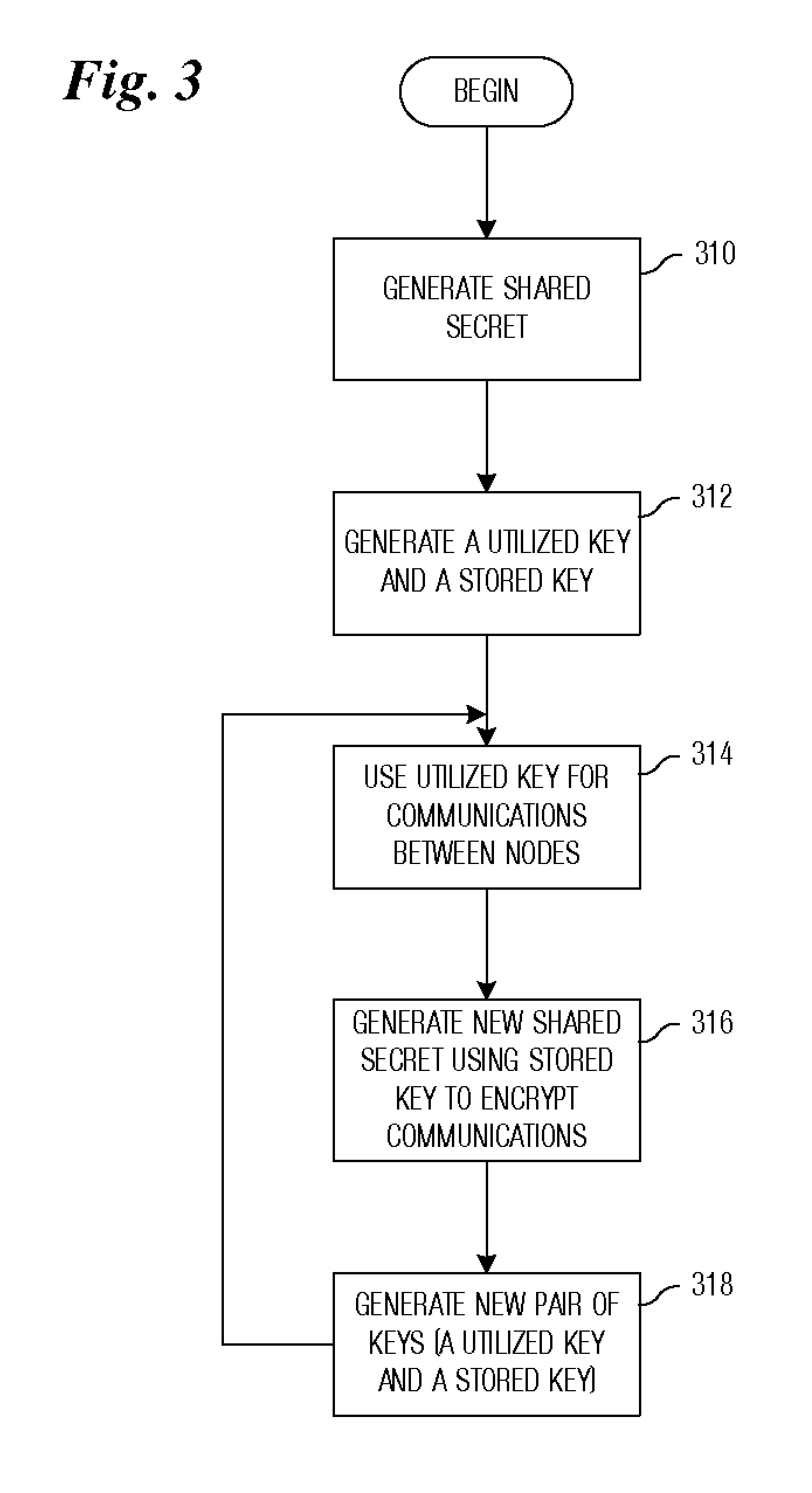
Updating and Distributing Encryption Keys
InactiveUS20100042841A1Key distribution for secure communicationPublic key for secure communicationSecure communicationPassword
System and method for providing secure communications is provided. Initially, an exchange protocol, such as a password-authenticated key exchange protocol, is used to create a shared secret. From the shared secret, two keys are created: a utilized key and a stored key. The utilized key is used to encrypt messages between nodes. When it is time to replace the utilized key to maintain security, the stored key is utilized to encrypt messages for generating / distributing a new shared secret. The new shared secret is then used to generate a new utilized key and a new stored key. This process may be repeated any number of times to maintain security.
Owner:LANTIQ BET GMBH & CO KG
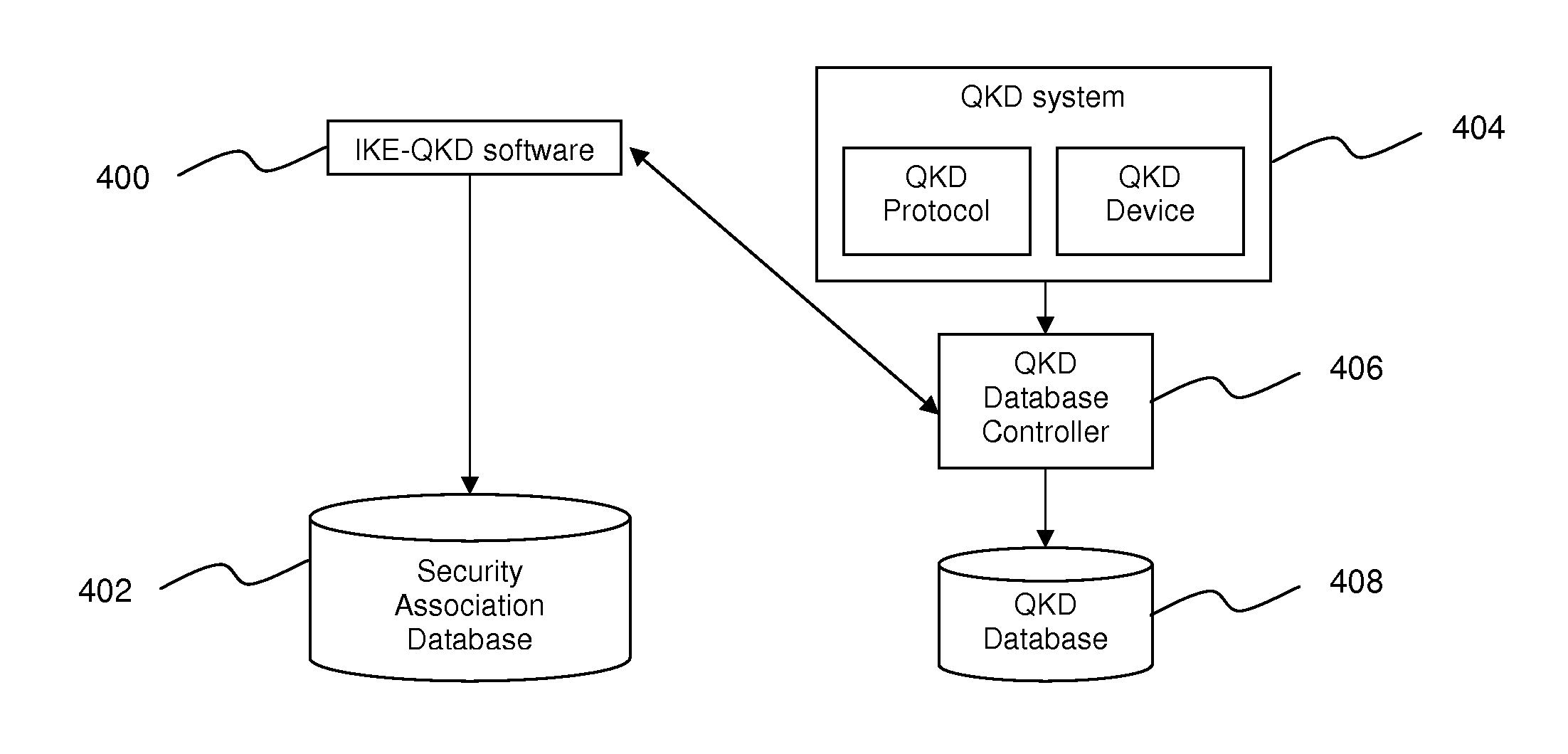
Method of integrating quantum key distribution with internet key exchange protocol
InactiveUS20110188659A1Key distribution for secure communicationUser identity/authority verificationKey exchangeInternet Key Exchange
A method of integrating quantum key distribution with Internet key exchange protocol, wherein the method comprises exchanging quantum-shared secret index from a cryptographic key database in Phase 1 of the Internet key exchange protocol between an initiator and a responder (100), integrating a number of quantum-shared secret from the cryptographic key database with classic shared secret using a predetermined operation mode in Phase 2 of the Internet key exchange protocol (200) to generate an array of security associations to be used by the initiator and the responder during a single Internet key exchange session, and managing inbound and outbound of the array of security associations in a security association database (402) using a database structure.
Owner:MIMOS BERHAD
System and method of providing unique personal identifiers for use in the anonymous and secure exchange of data
InactiveUS20080022414A1Digital data processing detailsUser identity/authority verificationHash functionDocumentation procedure
A universal anonymous data collection and exchange service is provided where individuals and entities initially register with the service utilizing “legally authentic” identity documentation to obtain a “universal ID” (UXID). The UXID consists of a sting of alphanumeric digits selected from a hash function that is performed on a string of personally identifying information. Once registered, the individual and entity UXIDs are used as a means by the service to engage in a pre-defined confidential data collection and exchange protocol between participating, registered UXID holders. The service is designed for use across many applications, individuals and entities, and may support one-time or recurring collection of data.
Owner:ALBRIGHT ASSOCS
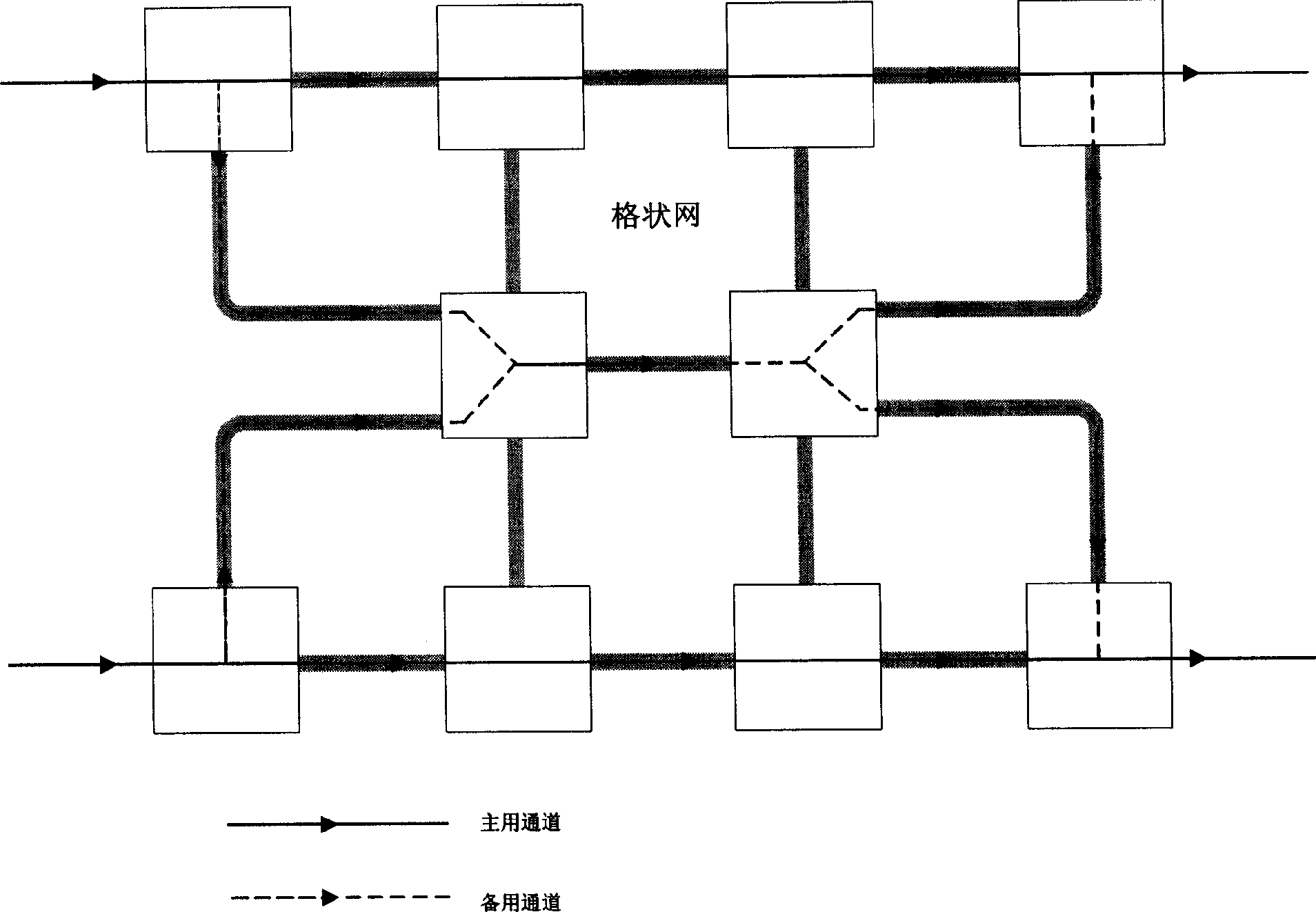
Method of proceeding failure recovery using shared spare passage in lattice shape network
InactiveCN1556637AShorten the timeSignaling process is simpleTransmissionExchange protocolPrimary channel
The invention relates to a method for carrying on failure restoration using shared backup channel in grating network, the method presets a backup channel when creating the primary channel, the backup channel presetting uses share mode, that is to say, the same resources can be used as the preset resources for several backup channels, when the primary channel is failed, it uses the label exchanging protocol to execute the signaling activating process of the backup channel, when one of the shared backup channel is activated, the other backup channels which carry on resources sharing to the activated channel are removed, then calculates these backup channels again. The invention uses sharing protection, upgrades the utilization rate of resources, because of the preset backup channel, the process activating the backup channel is simple and quick.
Owner:FENGHUO COMM SCI & TECH CO LTD
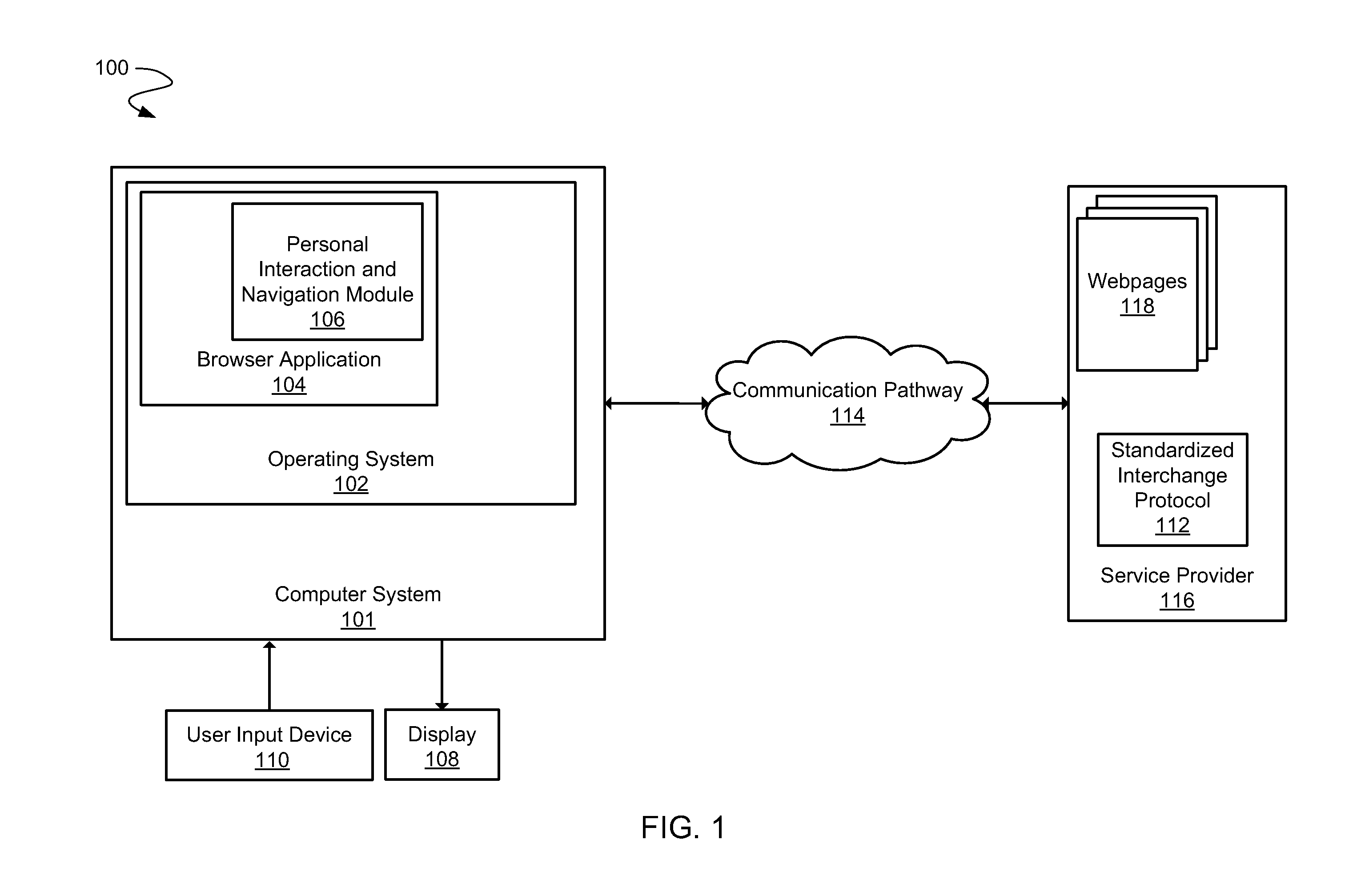
Personal web display and interaction experience system
ActiveUS20120198026A1Multiple digital computer combinationsWebsite content managementWeb siteGraphics
Embodiments of the present invention may be directed to an interactive system. The interactive system may include a browser application allowing a user to access a website using a communication pathway. The website provides website information in a standardized interchange protocol and also in webpages. The browser application is configured to allow user access to the webpages. The interactive system may also include a module of the browser application compatible with the standardized interchange protocol and configured to store and implement user personalized commands and to store recorded user history information. The module implements a graphical user interface with the website information that is personalized to the user. The graphical user interface includes a personalized display experience and a personalized interaction experience that are both custom designed for the user.
Owner:EGAIN COMM CORP
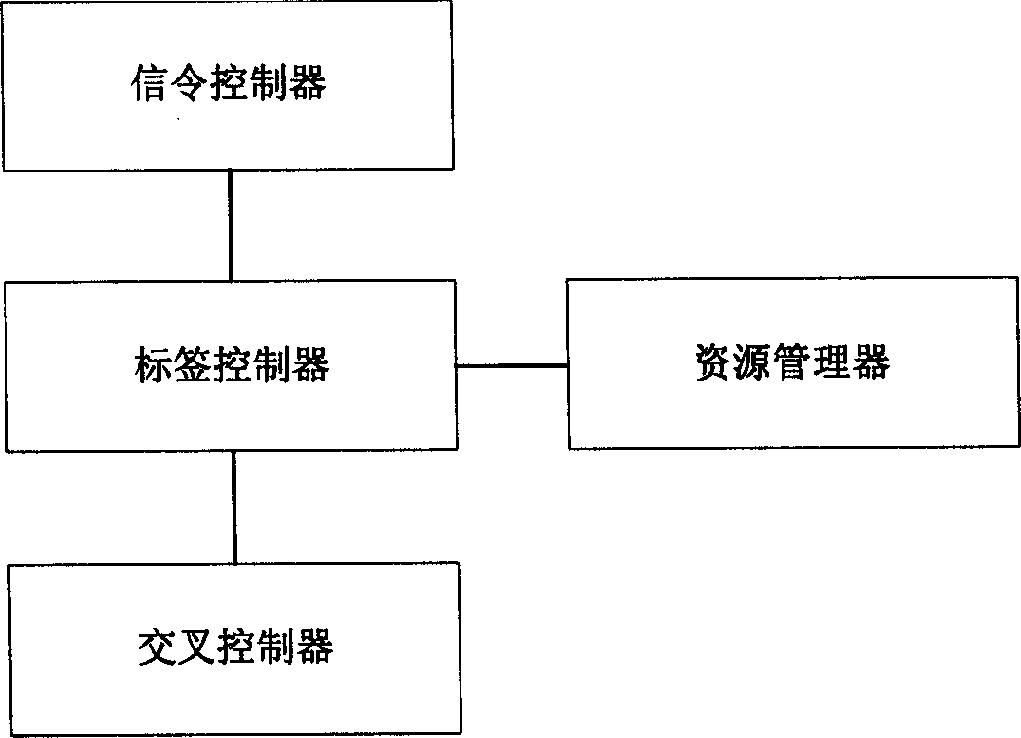
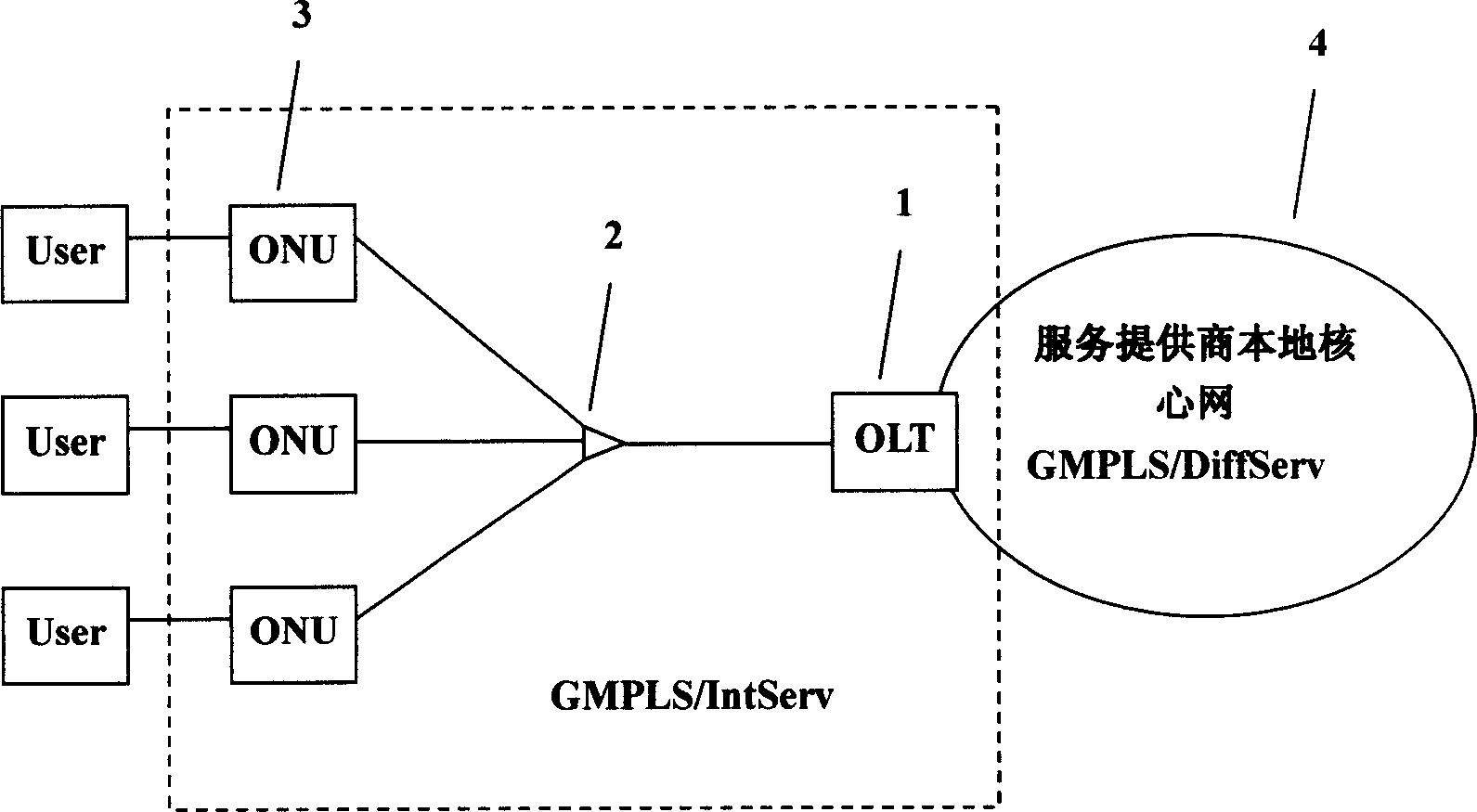
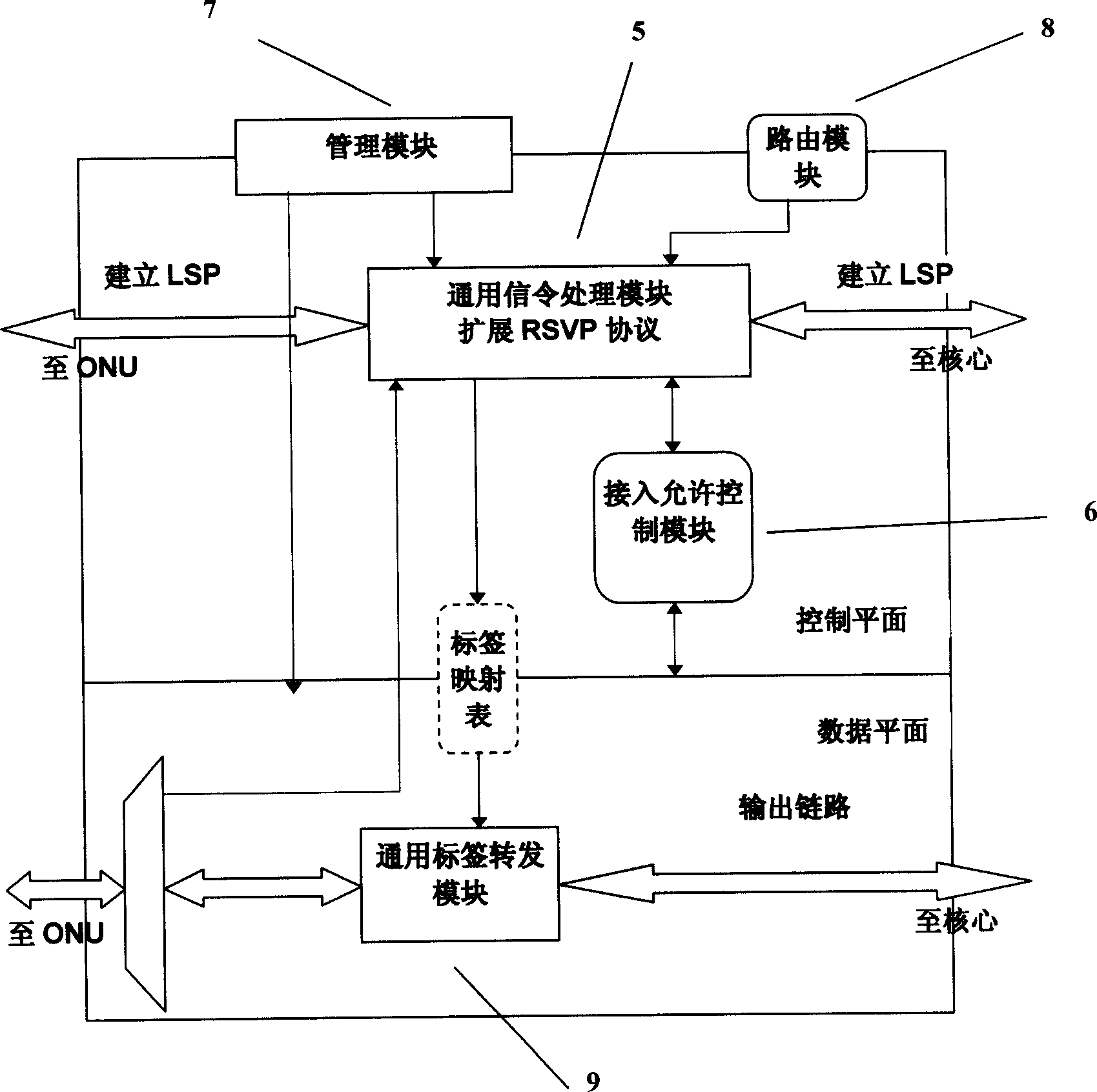
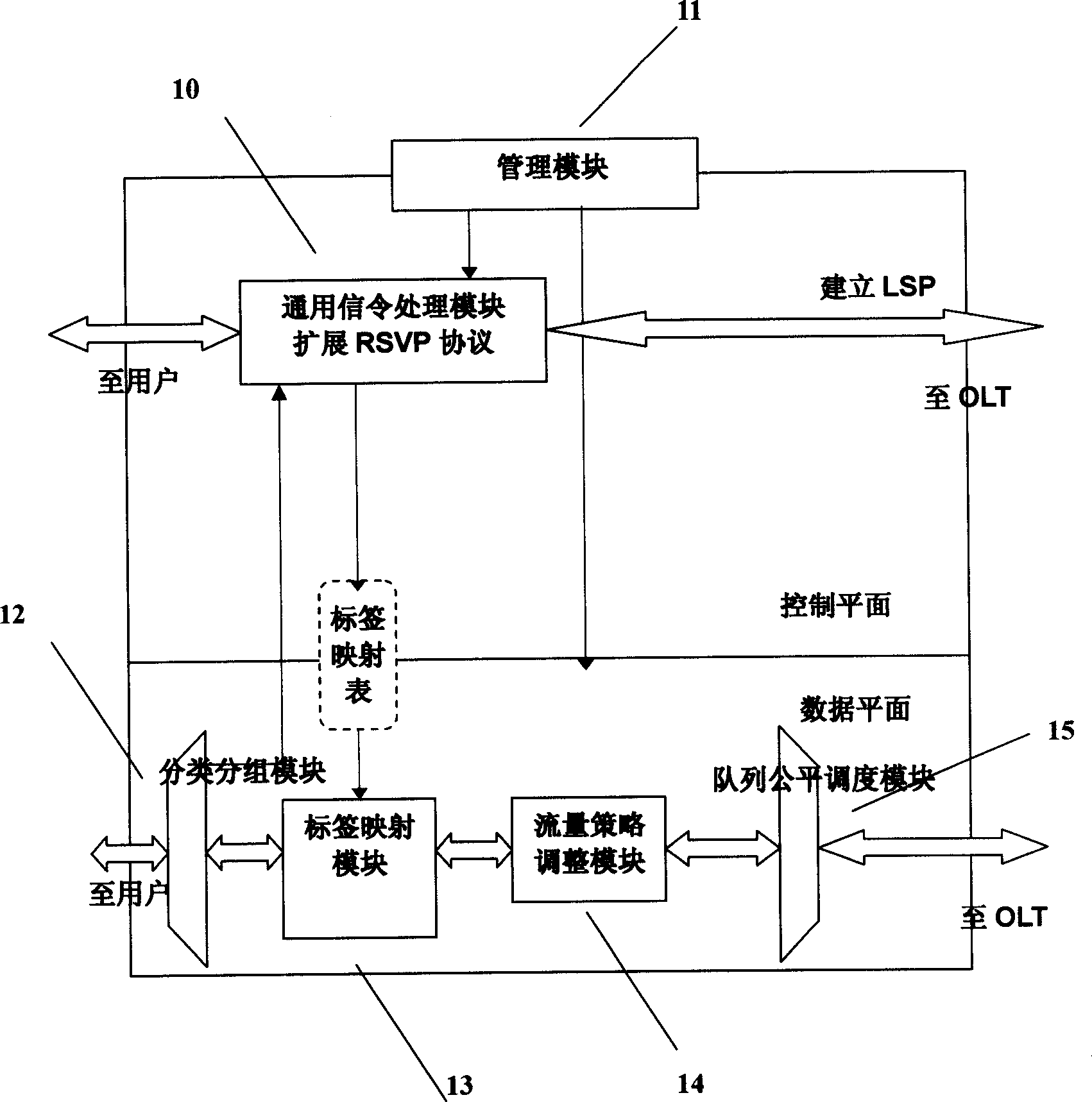
Passive optical network system based on generalized multiprotocol label switching (GMPLS) protocol
InactiveCN1725756ARealize intelligenceRealize intelligent controlTransmissionTelecommunications linkMultiprotocol Label Switching
A passive optical network system based on label exchanging protocol of universal multi-protocol is prepared as connecting optical line terminal OLT to multiple optical network unit ONU by wideband passive optical distribution network , using OLT and ONU as edge router and GMPLS domain of said exchanging protocol for being connected to the other GMPLS router in said multi-protocol by communication link , using OLT as intermediate router of integrated service in system individually for controlling all communication activities , using ONU as inlet router of integrated service in system for executing command of OLT .
Owner:SHANGHAI JIAO TONG UNIV
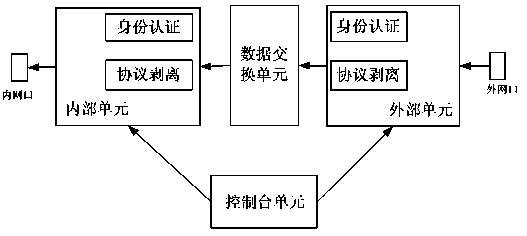
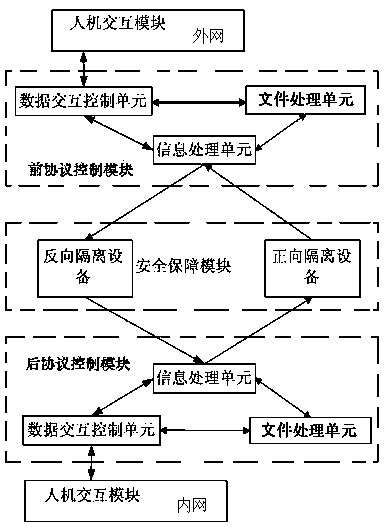
Security isolation file transmission control method
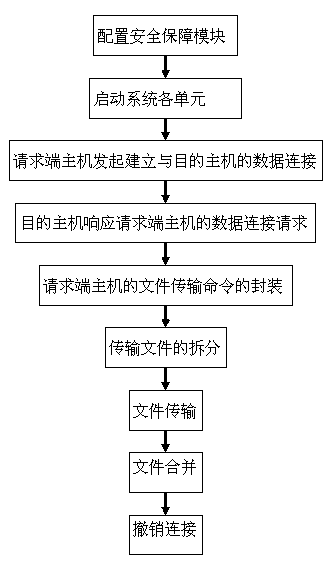
InactiveCN103997495AStrong process controllabilityImprove efficiencyTransmissionData connectionFile transmission
The invention discloses a security isolation file transmission control method. Security internal and external network file transmission is achieved through one-way transmission network architecture of a protocol control module and a security guarantee module. The method mainly comprises the steps that the security guarantee module is configured, all units of a system are started, a request end host initiates data connection with a target host, the target host responds to a data connection request of the request end host, a file transmission order of the request end host is packaged, a transmission file is detached, files are transmitted and merged, and connection is withdrawn. The request end host can send the files to the target host and can download the files from the target host, and concurrent file sending and file downloading of multiple tasks and multiple users can be achieved. According to the security isolation file transmission control method, internal and external data based on one-way network isolation equipment can be transparently transmitted, and the internal and external data transmission efficiency can be improved through a soft exchange protocol.
Owner:PLA UNIV OF SCI & TECH
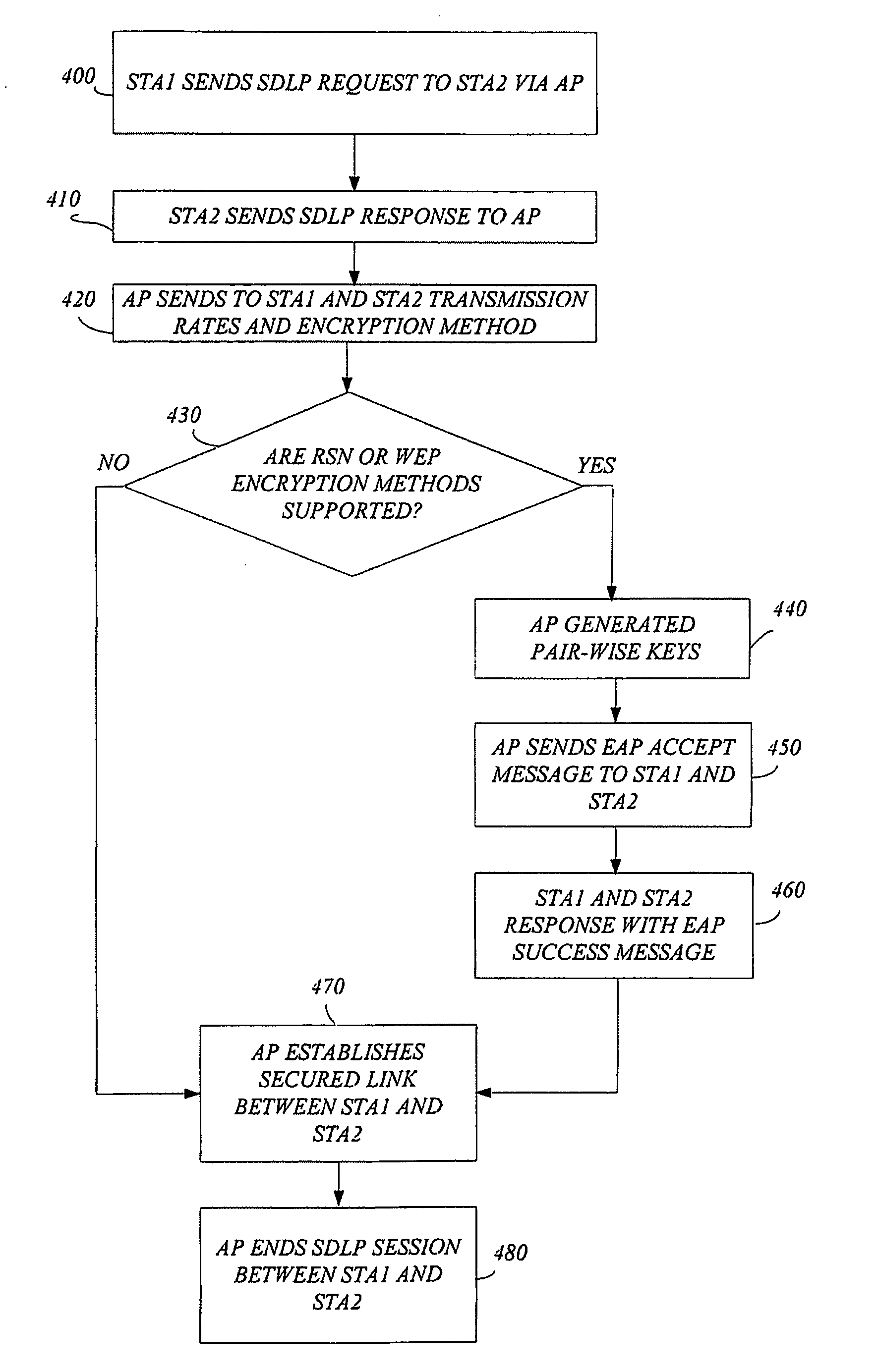
Method and apparatus to provide secured link
InactiveUS20050108527A1User identity/authority verificationNetwork topologiesExchange protocolWireless lan
Briefly, a method and apparatus that may establish a secured direct link between a first station and a second station of wireless local area network. The establishment of this secured direct link may be done by an access point that may exchange protocol messages between the first station the second station and the access point.
Owner:INTEL CORP
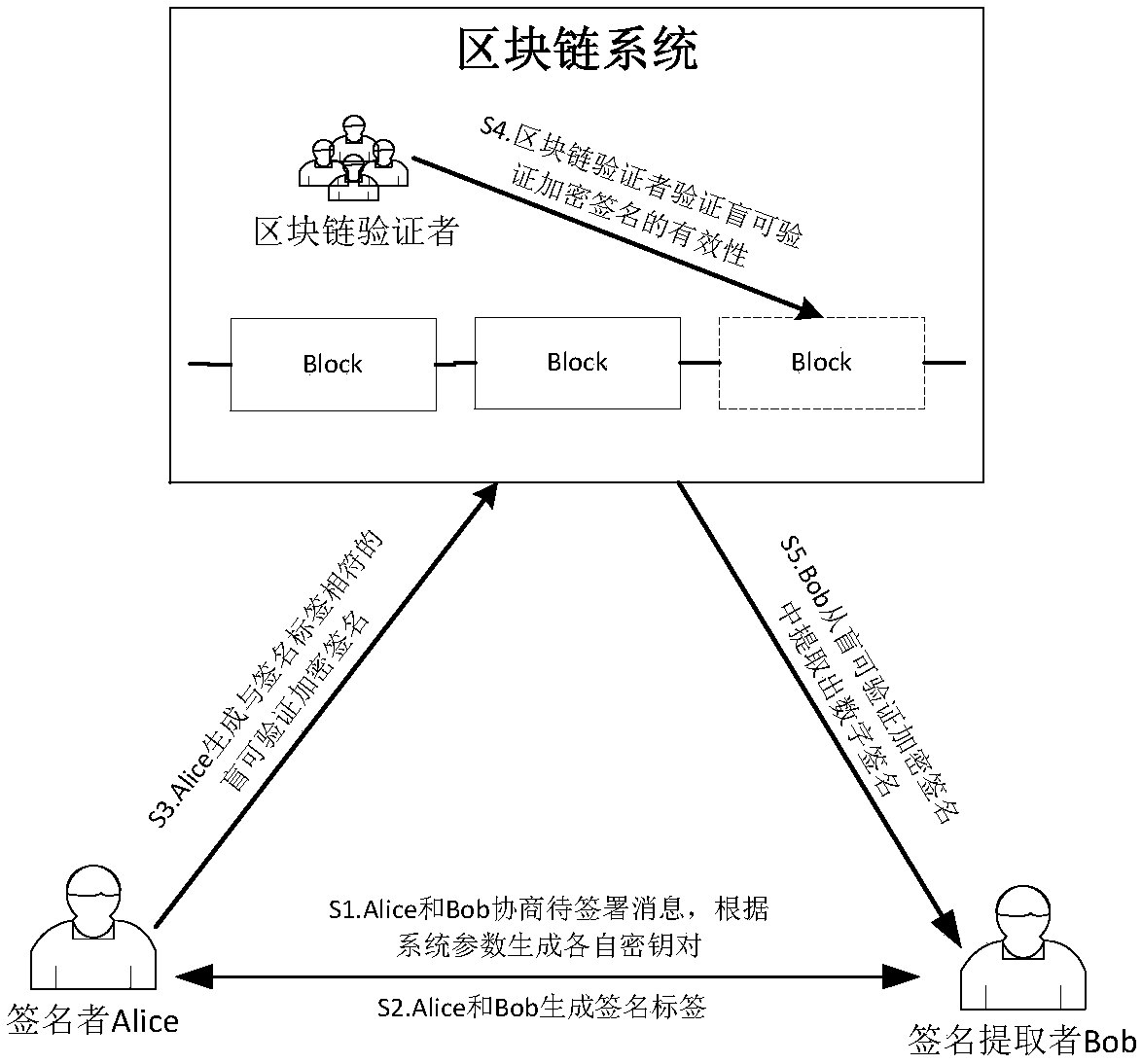
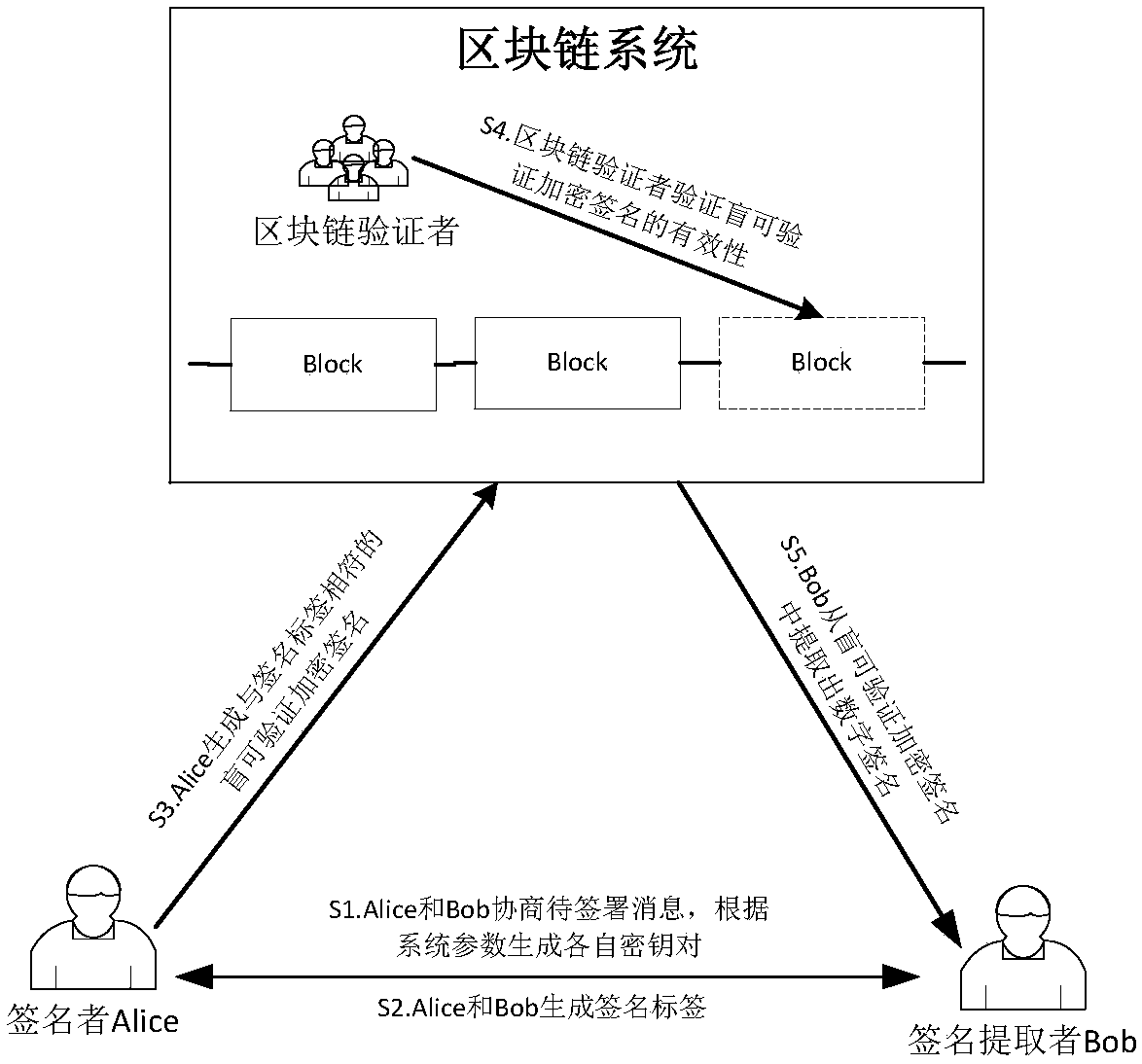
Blind verifiable cryptographic signature method based on block chain
InactiveCN107040383APrivacy protectionPublic key for secure communicationUser identity/authority verificationAlice and BobDigital signature
The invention relates to a blind verifiable cryptographic signature method based on a block chain. The method includes three parties: a signer Alice, a signature extractor Bob, and a block chain verifier. The method is implemented in the following steps: Alice and Bob negotiate a message to be signed and generate their own key pairs respectively according to system parameters; Alice and Bob generate signature tags; Alice generates a blind verifiable cryptographic signature that matches the signature tag; the block chain verifier verifies the validity of the cryptographic verifiable cryptographic signature; and Bob extracts a digital signature from the blind verifiable cryptographic signature. The method can be used to construct a fair digital signature exchange protocol that protects privacy in a public block chain environment. The method blindens the public key information of the signer so that a node on a block chain cannot obtain the real digital signature and the public key of the signer aside from verifying the validity of the signature, and the privacy protection for the signer is achieved.
Owner:深圳市数峰科技有限公司
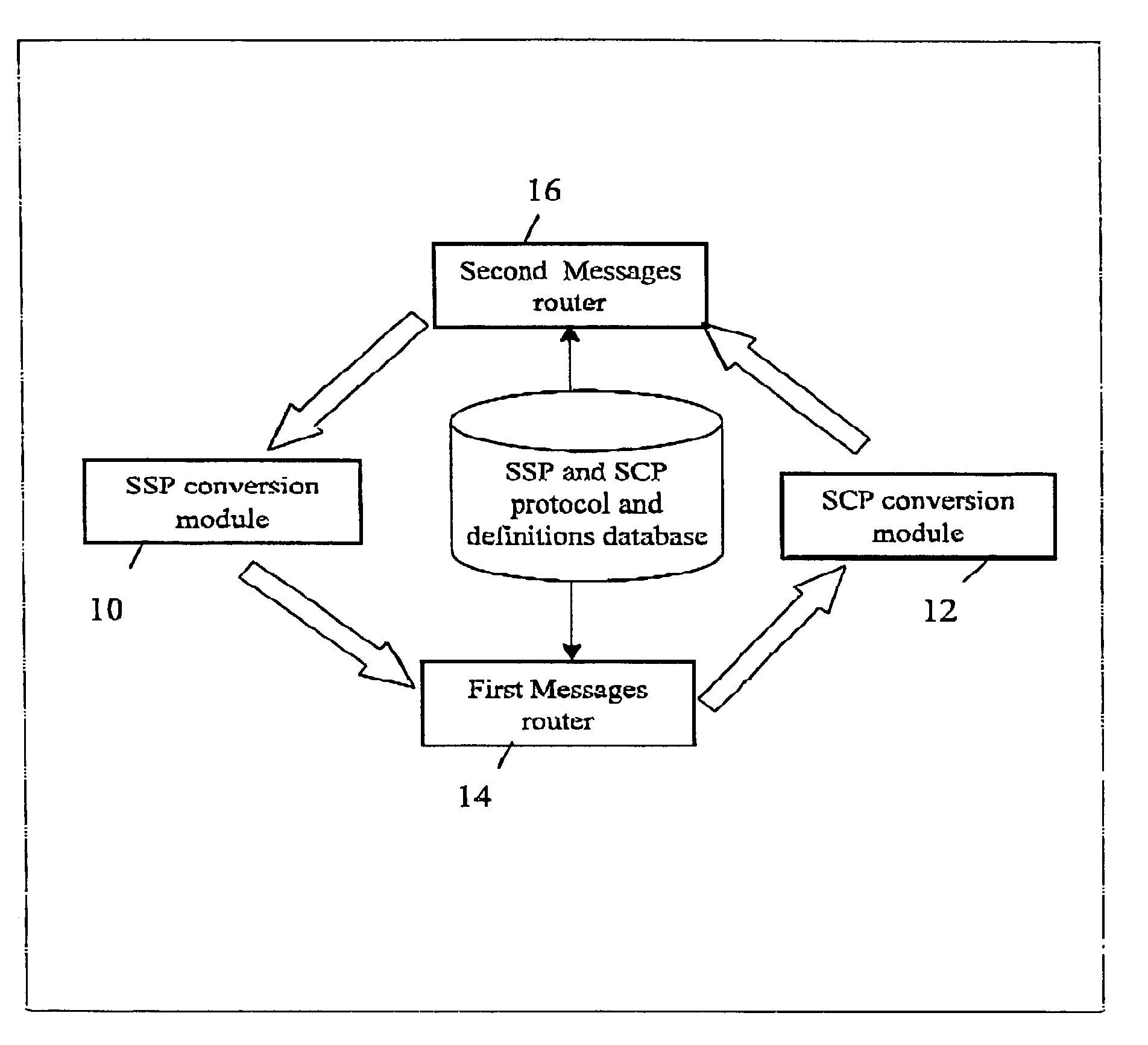
Method and system for integrating multi services for intelligent networks
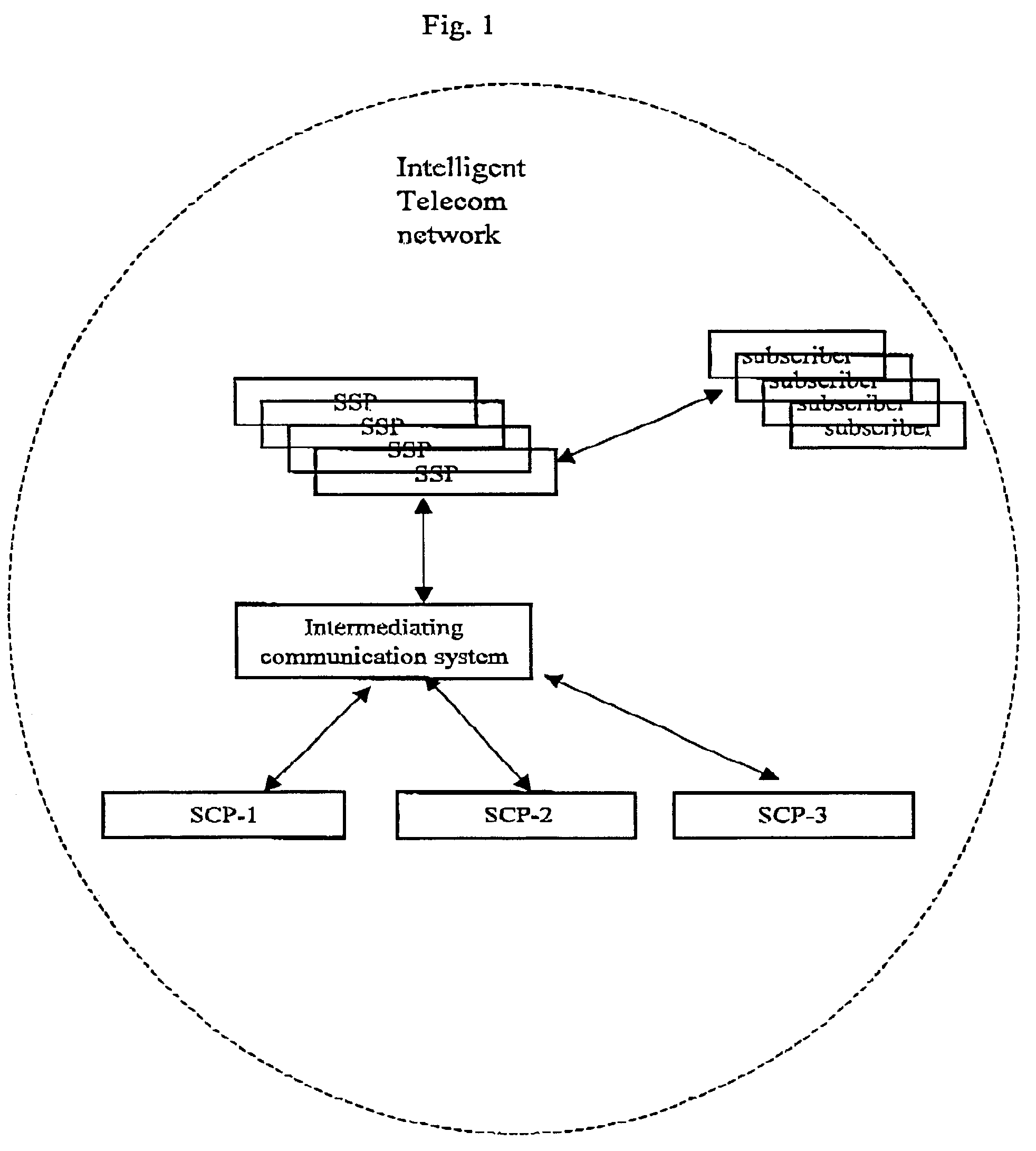
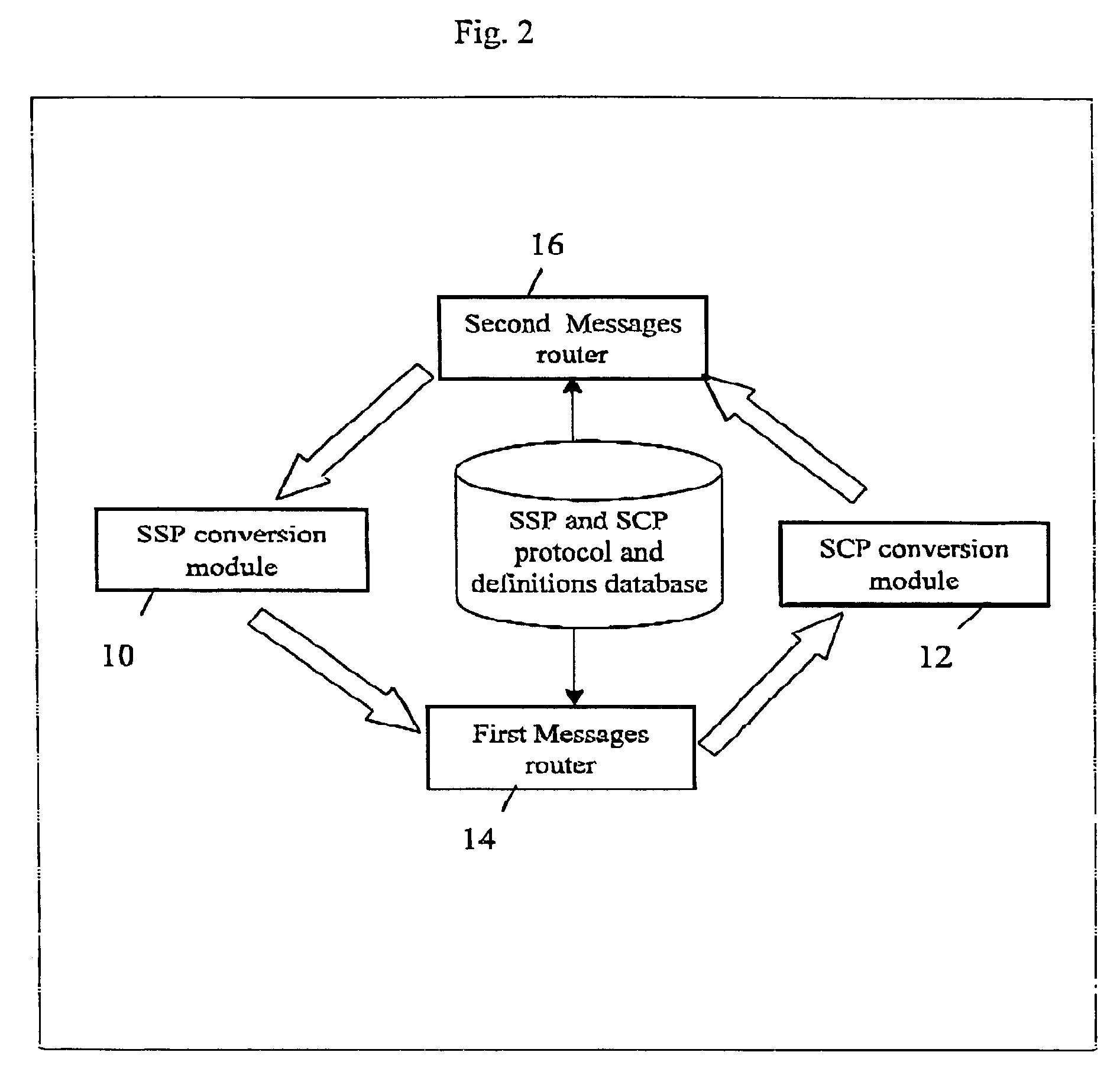
InactiveUS7139387B2Enable communicationInterconnection arrangementsSpecial service for subscribersIntelligent NetworkMessage switching
The invention includes a router and adapter enabling to receive any type of vendor Intelligent Network protocol message, then to direct the message (according to predefined rules) and ultimately, to translate one type of message into a unified format in order to meet with the destination protocol requirements and the mediating method according to the present invention enable communication between different (SSP) telephone message switching protocols and different control point system (SCP) message protocols; the method is based on conversion processes that enable identification of message definitions and information and the creation of unified message records.
Owner:OUTSTART INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com