Systems and methods for authenticating communications in a network medium
a network medium and communication authentication technology, applied in the field of systems and methods for authenticating communications in a network medium, can solve the problems of immense public key infrastructure, inability to provide information to others, and high cos
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
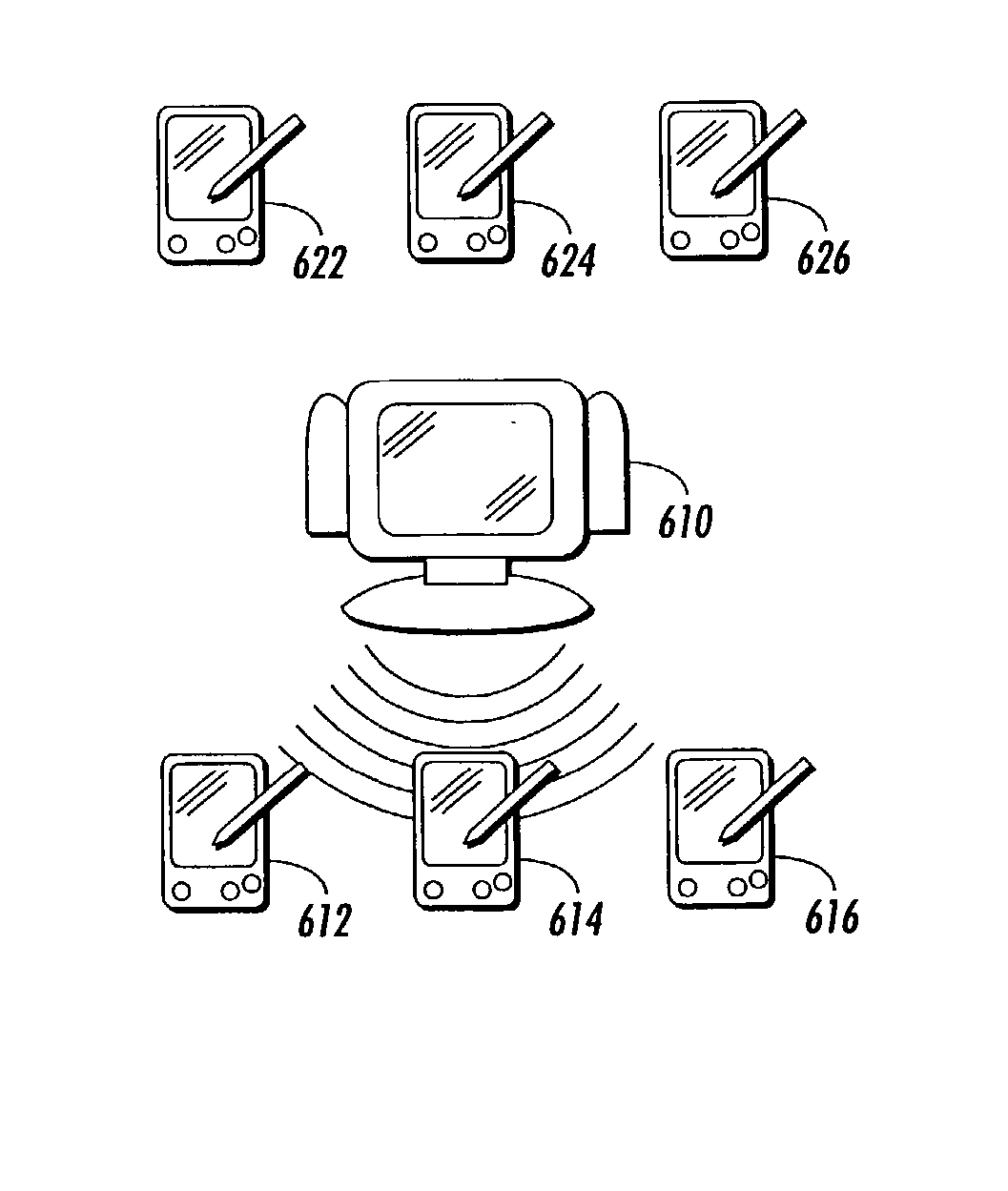
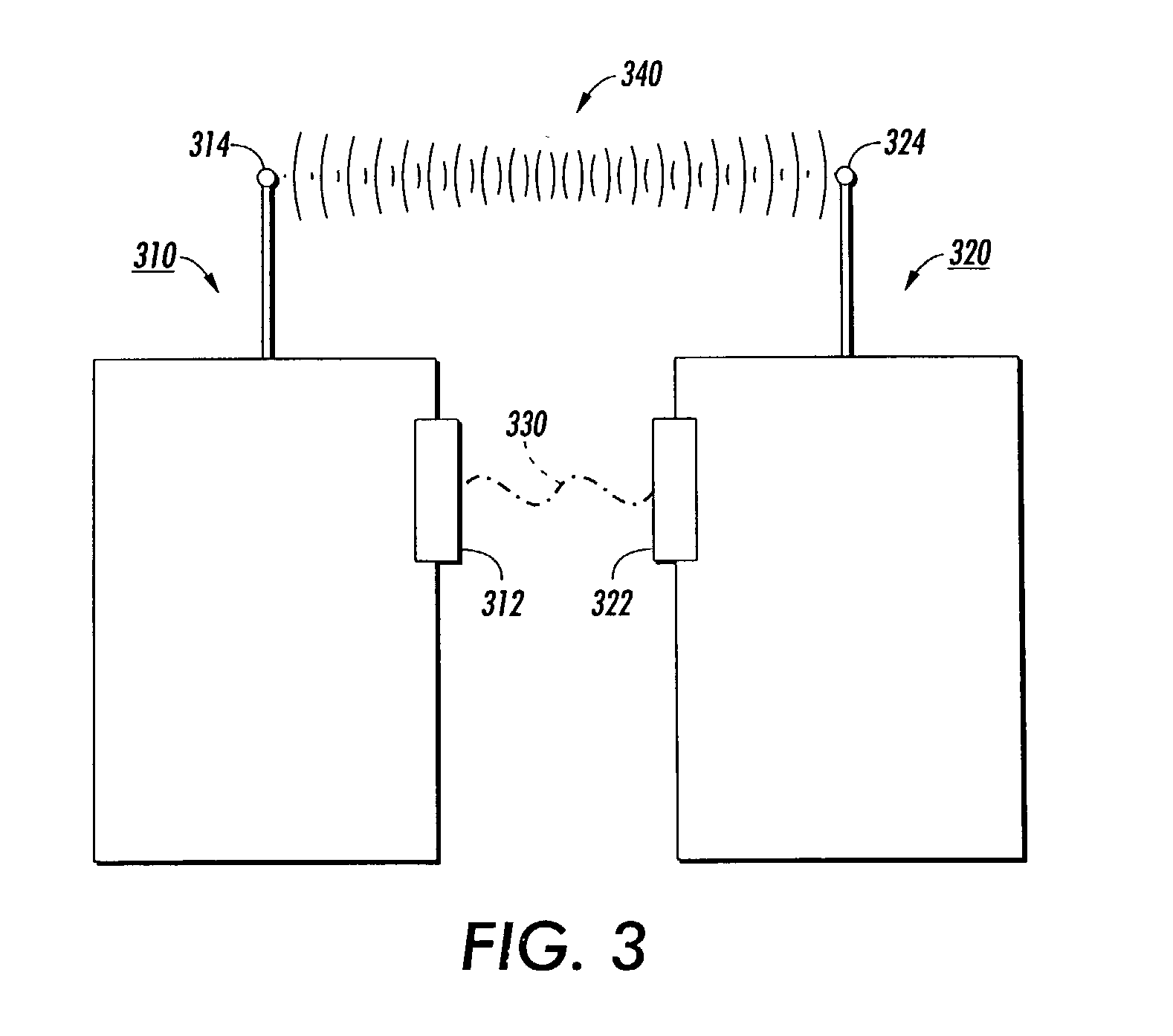
[0032] In various exemplary embodiments of systems and methods according to this invention, pre-authenticating a number of wireless devices is used to securely authenticate arbitrary peer-to-peer ad-hoc interactions. This may also include a bootstrap to a key exchange protocol that is used to set up an encrypted channel. In one exemplary embodiment, a public key is committed to on the pre-authentication channel. A key exchange protocol using public key cryptography is used in the main wireless link to establish secure communications. Due to pre-authenticating the wireless devices using public keys, the types of media usable as location-limited channels do not need to be immune to eavesdropping and can include, for example, audio and / or infra-red channels. In various embodiments, pre-authenticating the wireless devices using public keys allows a range of public-key-base key exchange protocols which can authenticate wireless devices to be used. As a result, a large range of location-l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com