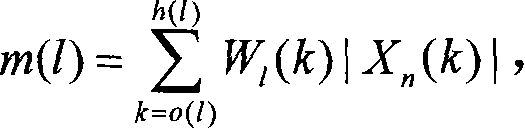Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
82 results about "Program fragment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
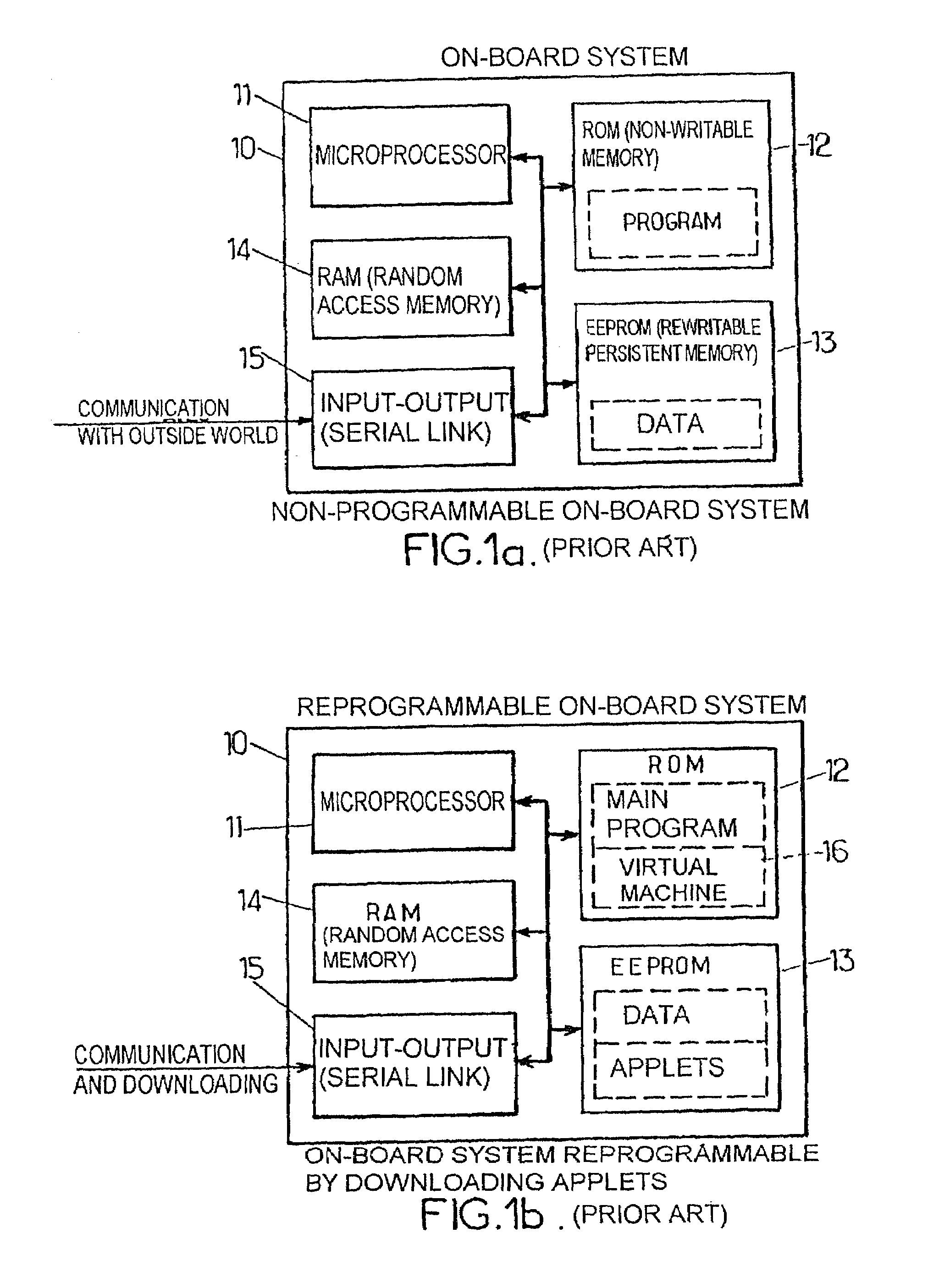
Systems And Methods For Software Analysis
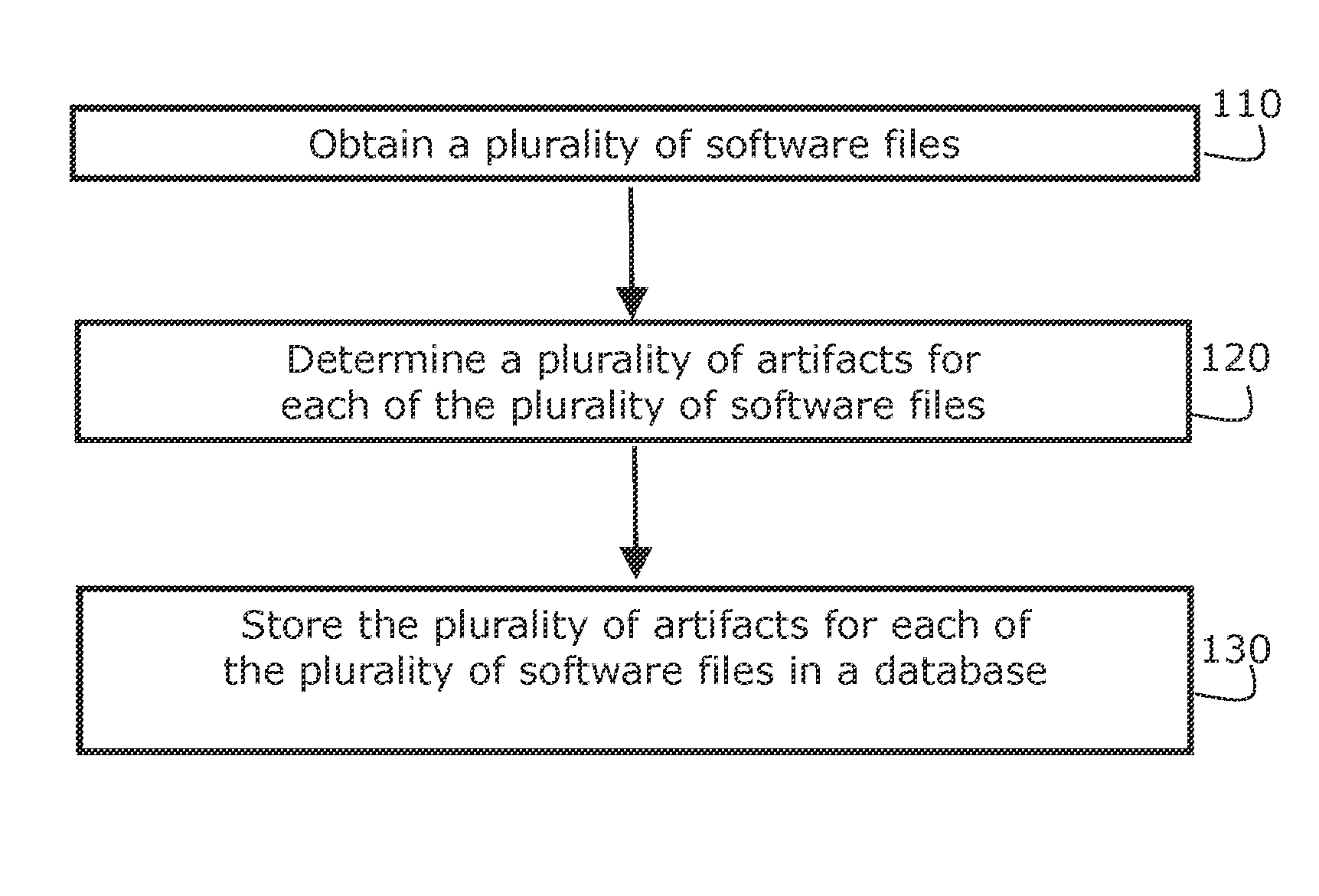
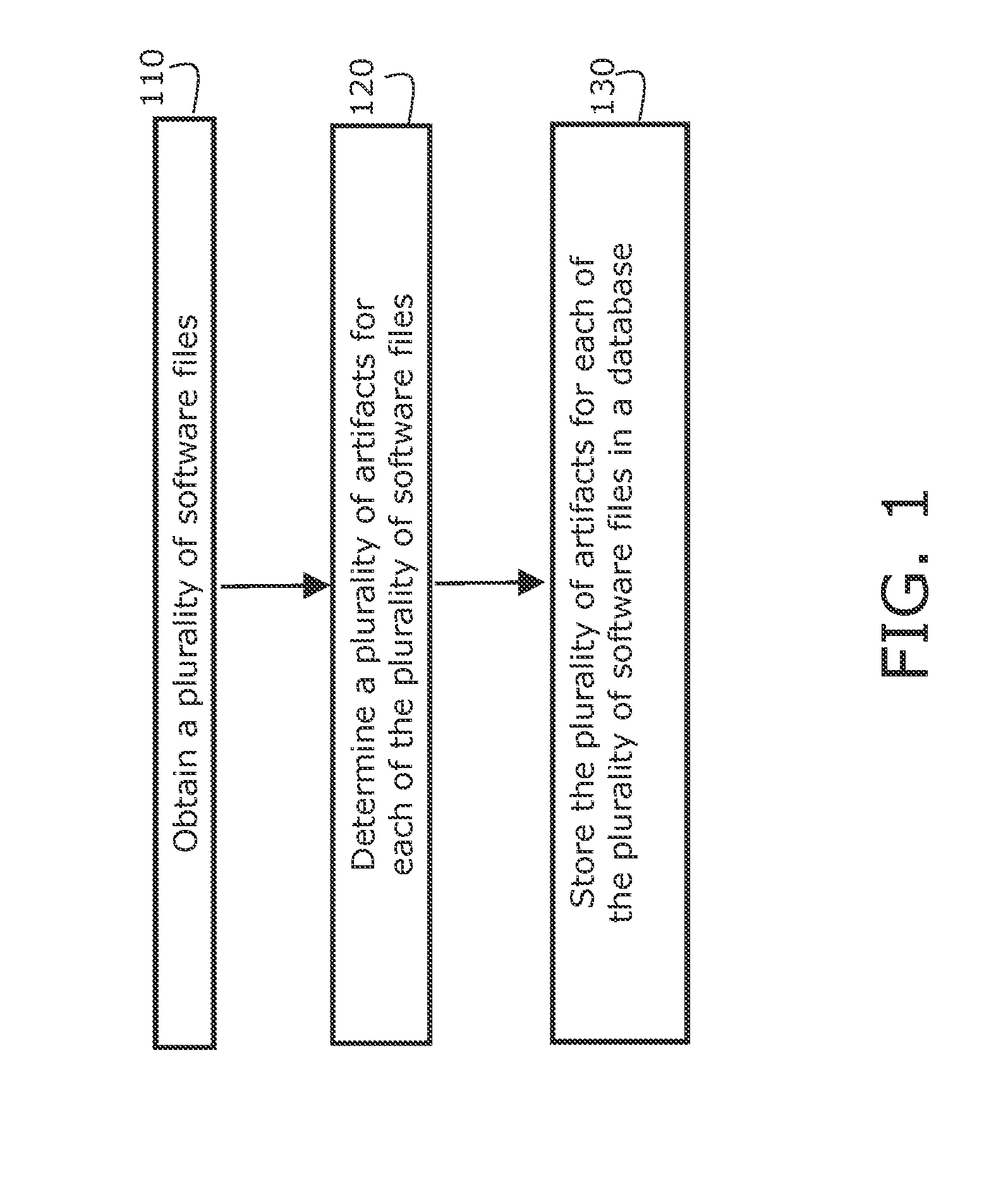
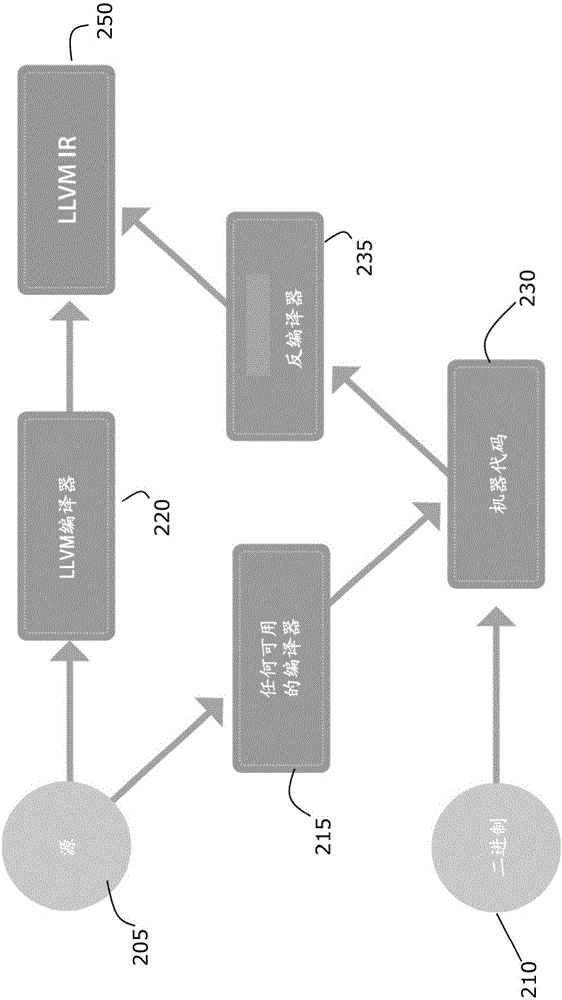
Systems, methods, and computer program products are provided for identifying software files, flaws in code, and program fragments by obtaining a software file, determining a plurality of artifacts, accessing a database which stores a plurality of reference artifacts for reference software files, comparing at least one of the artifacts to at least one of the reference artifacts stored in the database, and identifying the software file by identifying the reference software file having the reference artifacts that correspond to the plurality of artifacts. Certain embodiments can also automatically provide updated versions of files, patches to be applied, or repaired blocks of code to replace flawed blocks. Example embodiments can accept a wide variety of file types, including source code and binary files and can analyze source code or convert files to an intermediate representation (IR) and analyze the IR.
Owner:CHARLES STARK DRAPER LABORATORY
Process for rewriting executable content on a network server or desktop machine in order to enforce site specific properties
InactiveUS6865735B1Less processing overheadRun fastBinary to binaryMultiprogramming arrangementsProgram fragmentUnknown Source
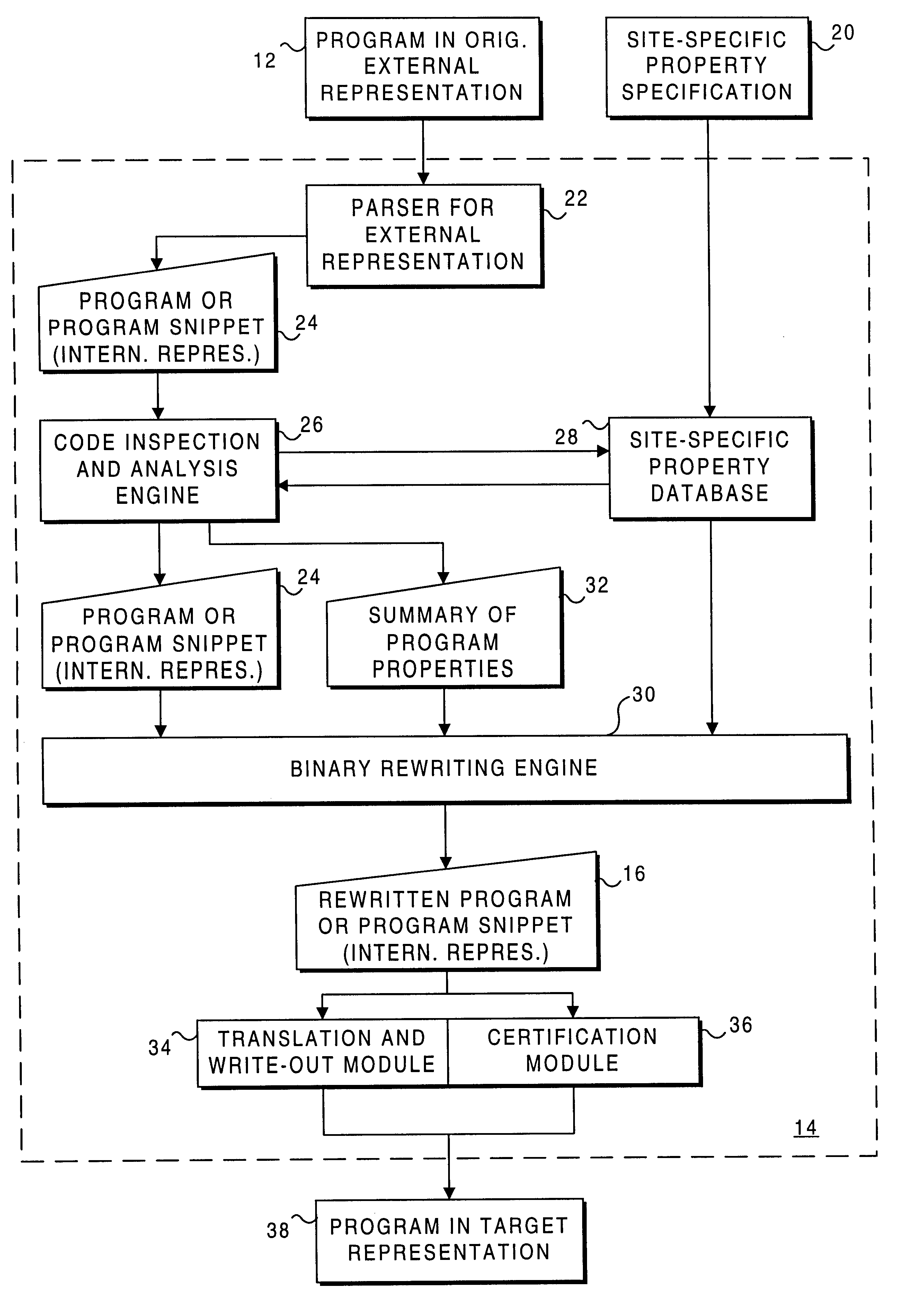
A program or program snippet is rewritten to conform to site-specific properties prior to being executed by a target host. The program or program snippet directed to a target host from a known or unknown source is either intercepted by a server before reaching the target host or can be redirected from the target host to the server to effect its rewriting. The program is parsed in its external representation, converting it to an internal representation that is inspected and analyzed with reference to a site-specific properties database. A summary of the program's properties is then compared to the site-specific properties database by a binary rewriting engine, which produces a rewritten program in an internal representation. If appropriate, the program or program snippet is rewritten to convert it to a format suitable for execution on the target host. Furthermore, certifications may be added to the rewritten program to mark that the rewritten program obeys site-specific constraints. The rewriting service thus produces a program in an appropriate target representation that conforms to site-specific properties. These properties may relate to security, auditing, optimization, monitoring, threading, and / or management of the rewritten program.
Owner:UNIV OF WASHINGTON
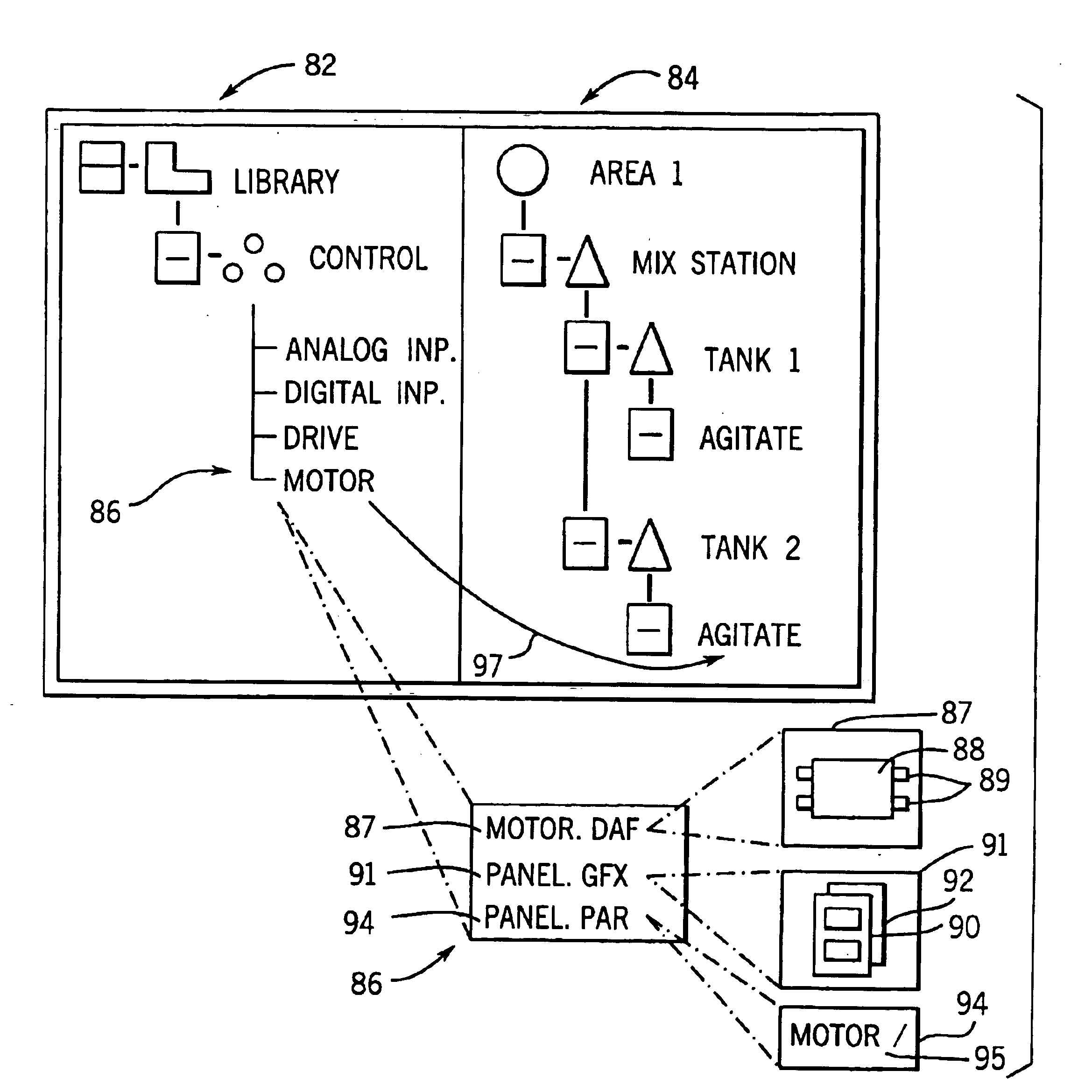
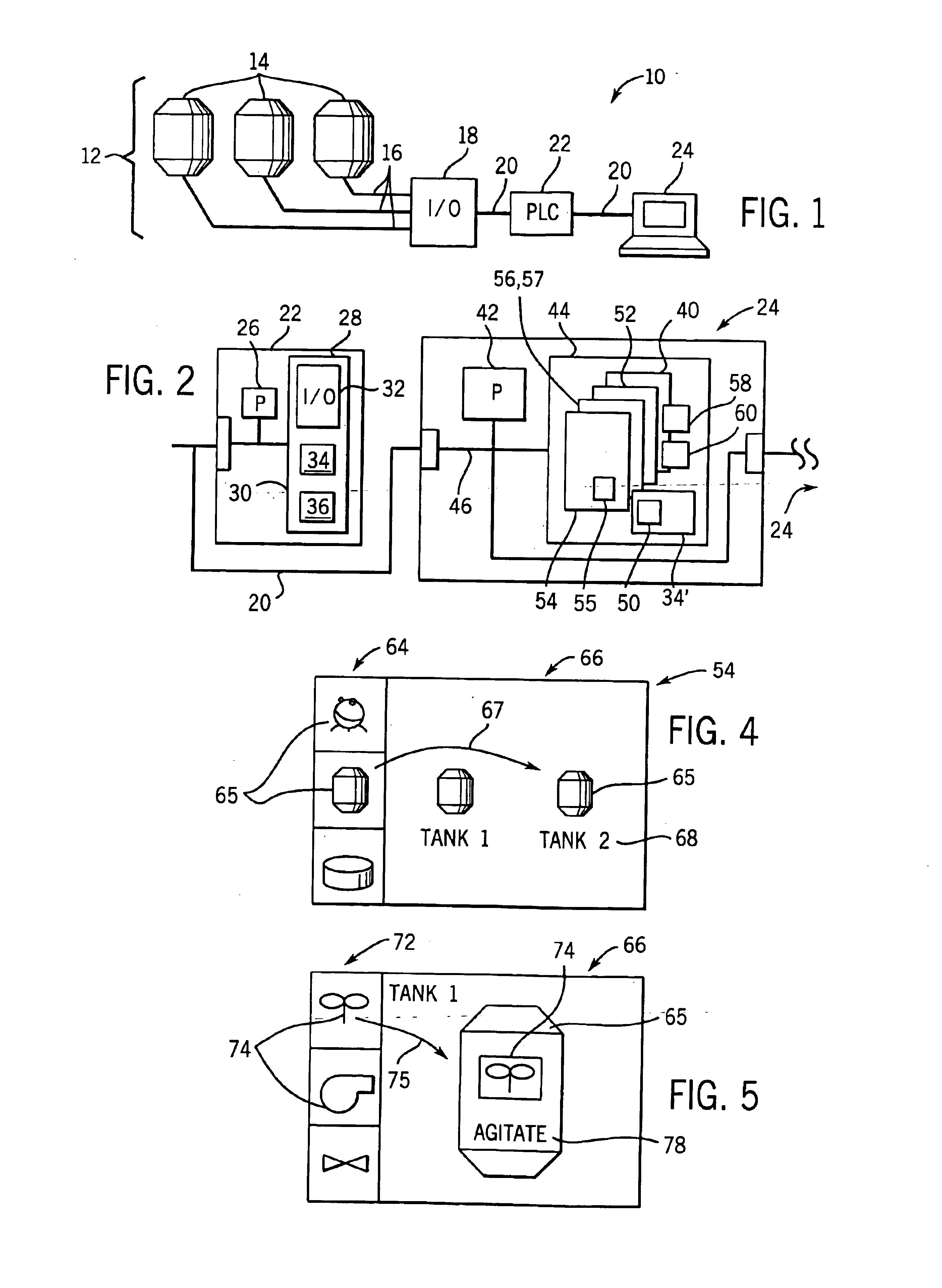
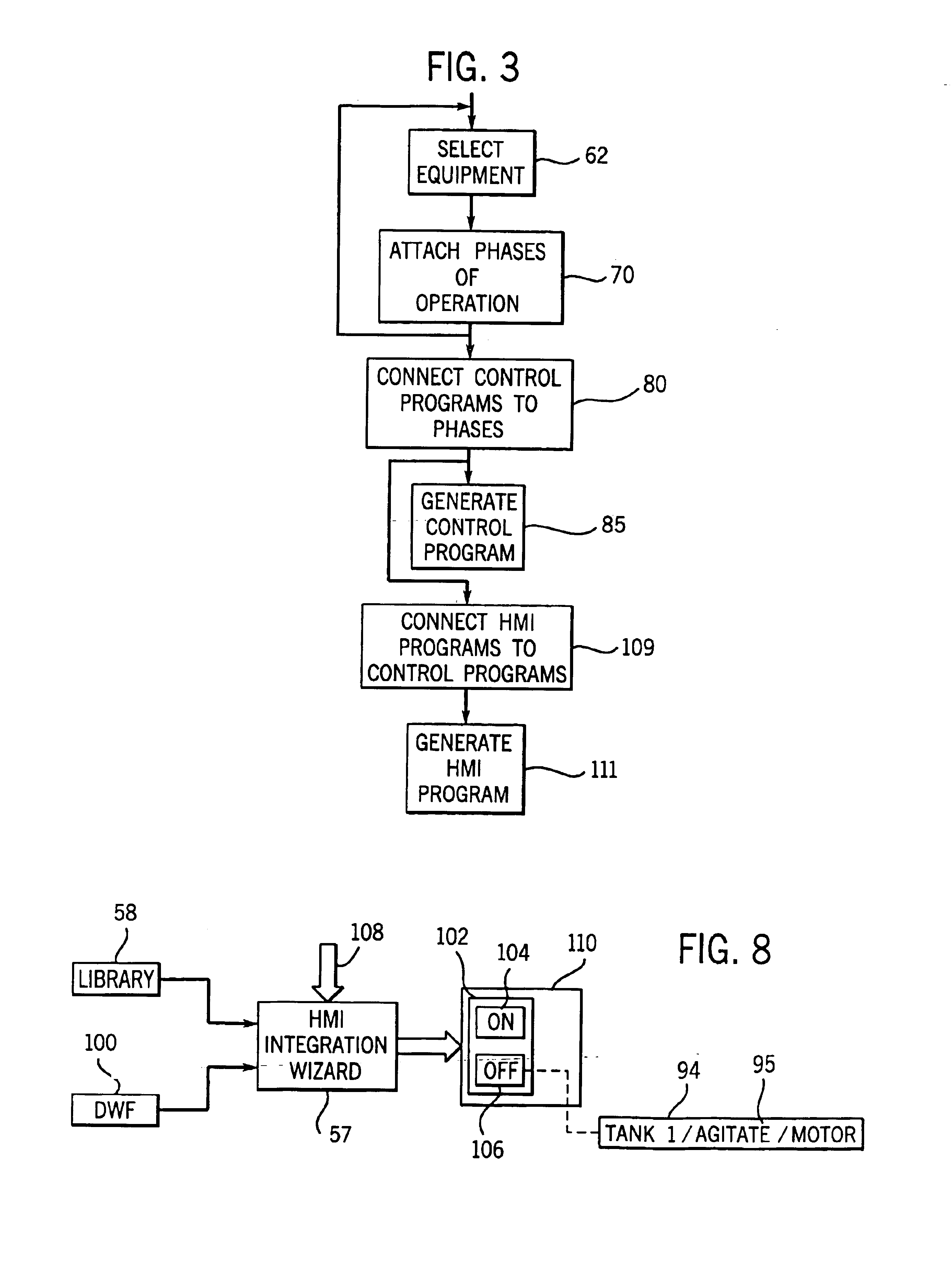
Library manager for automated programming of industrial controls
InactiveUS6854111B1Simplify the development processSimple meansComputer controlSimulator controlProgram fragmentAutomated programming
A library manager holds related program fragments, for example, control logic fragments and visualization program fragments sharing the same control variables, in library files. Multiple copies of control logic program fragments are instantiated to develop a control program and of the control variable tags for each copy of the control logic program fragments are renamed to prevent conflicts. At a later time, visualization program fragments related to the control logic program fragments are identified by their common origin in the library manger. The control variables of these visual program fragments may then be automatically renamed by using their library files as a guide. The library files may also hold related non-program information.
Owner:ALLEN-BRADLEY CO LLC
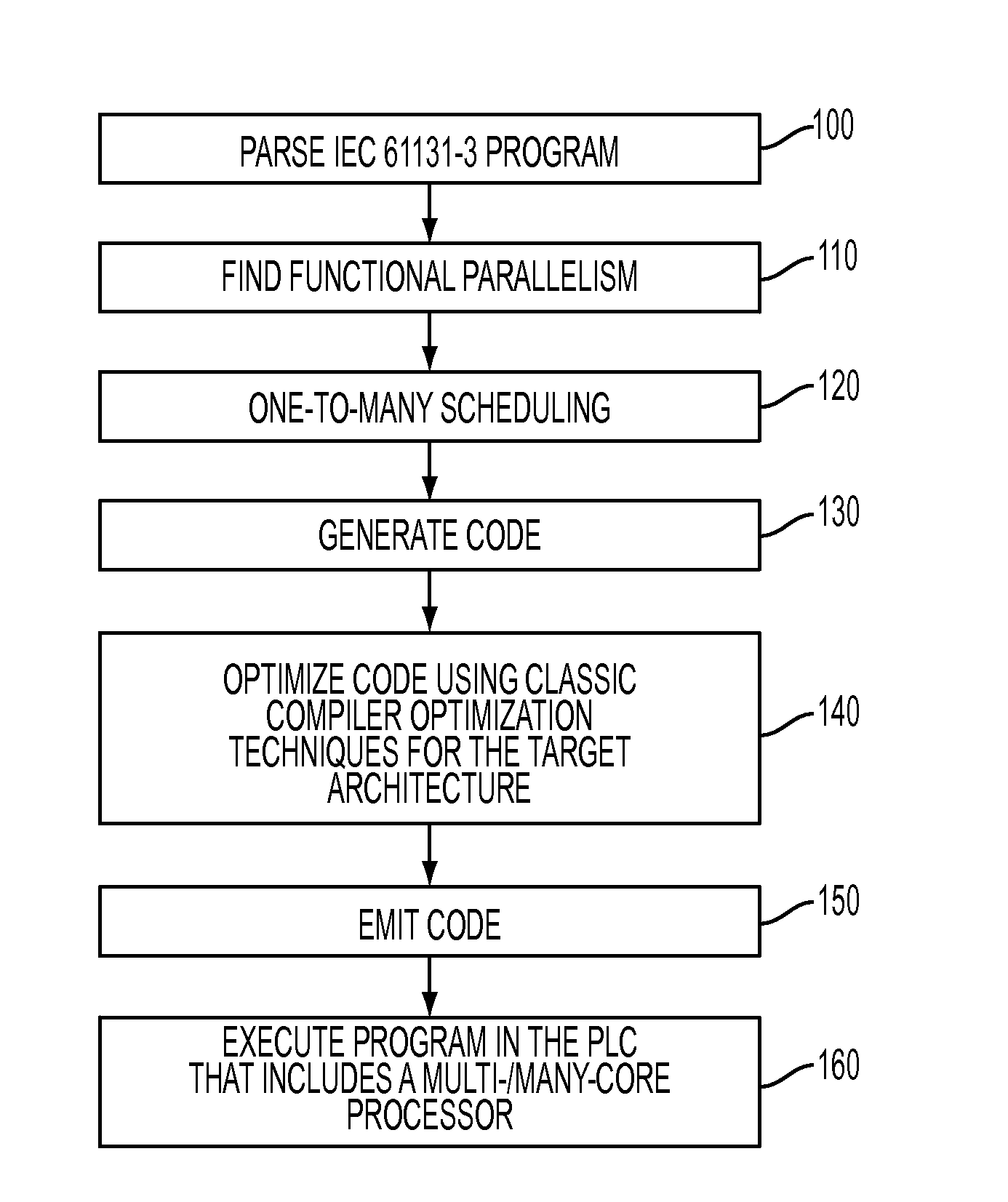
Parallelization of PLC programs for operation in multi-processor environments
ActiveUS20120260239A1Break dependenciesEfficient use ofSoftware engineeringProgram controlProgram fragmentMulti processor
A method of identifying and extracting functional parallelism from a PLC program has been developed that results in the ability of the extracted program fragments to be executed in parallel across a plurality of separate resources, and a compiler configured to perform the functional parallelism (i.e., identification and extraction processes) and perform the scheduling of the separate fragments within a given set of resources. The inventive functional parallelism creates a larger number of separable elements than was possible with prior dataflow analysis methodologies.
Owner:SIEMENS AG
Method For Creating A Telecommunications Application
InactiveUS20090132220A1Multiplex system selection arrangementsAnalogue computers for electric apparatusProgram fragmentTelecommunications link
Owner:IBM CORP
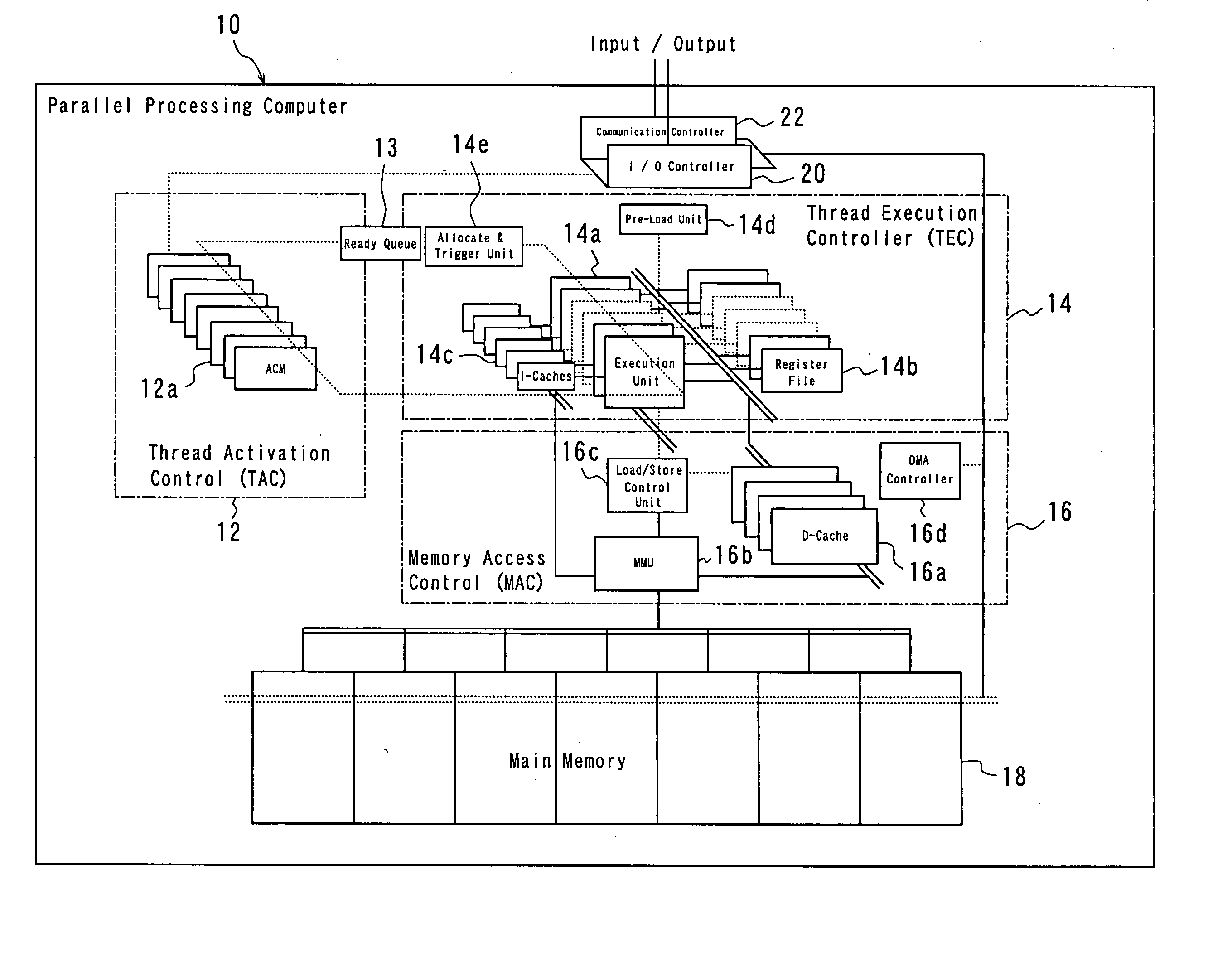
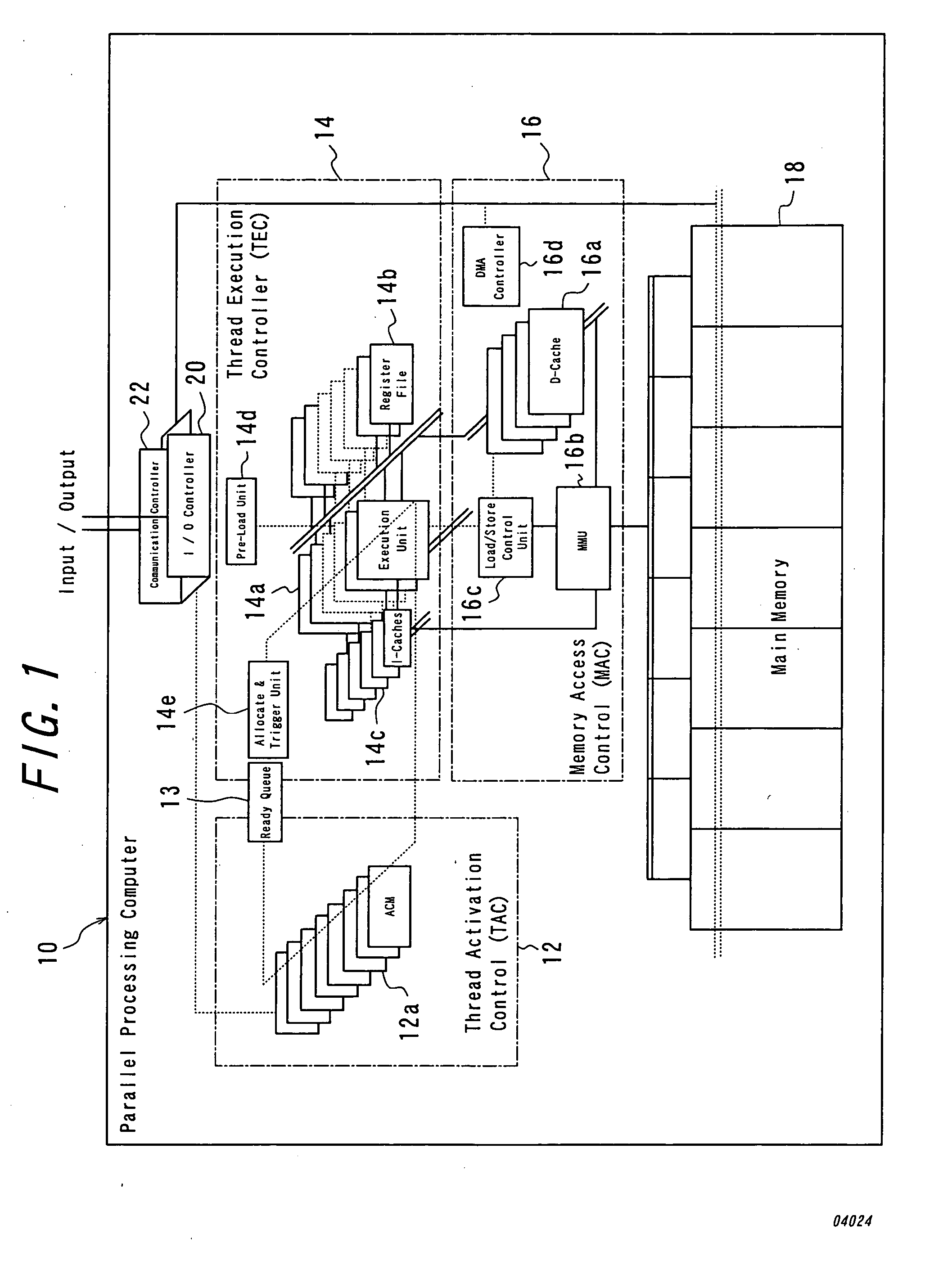
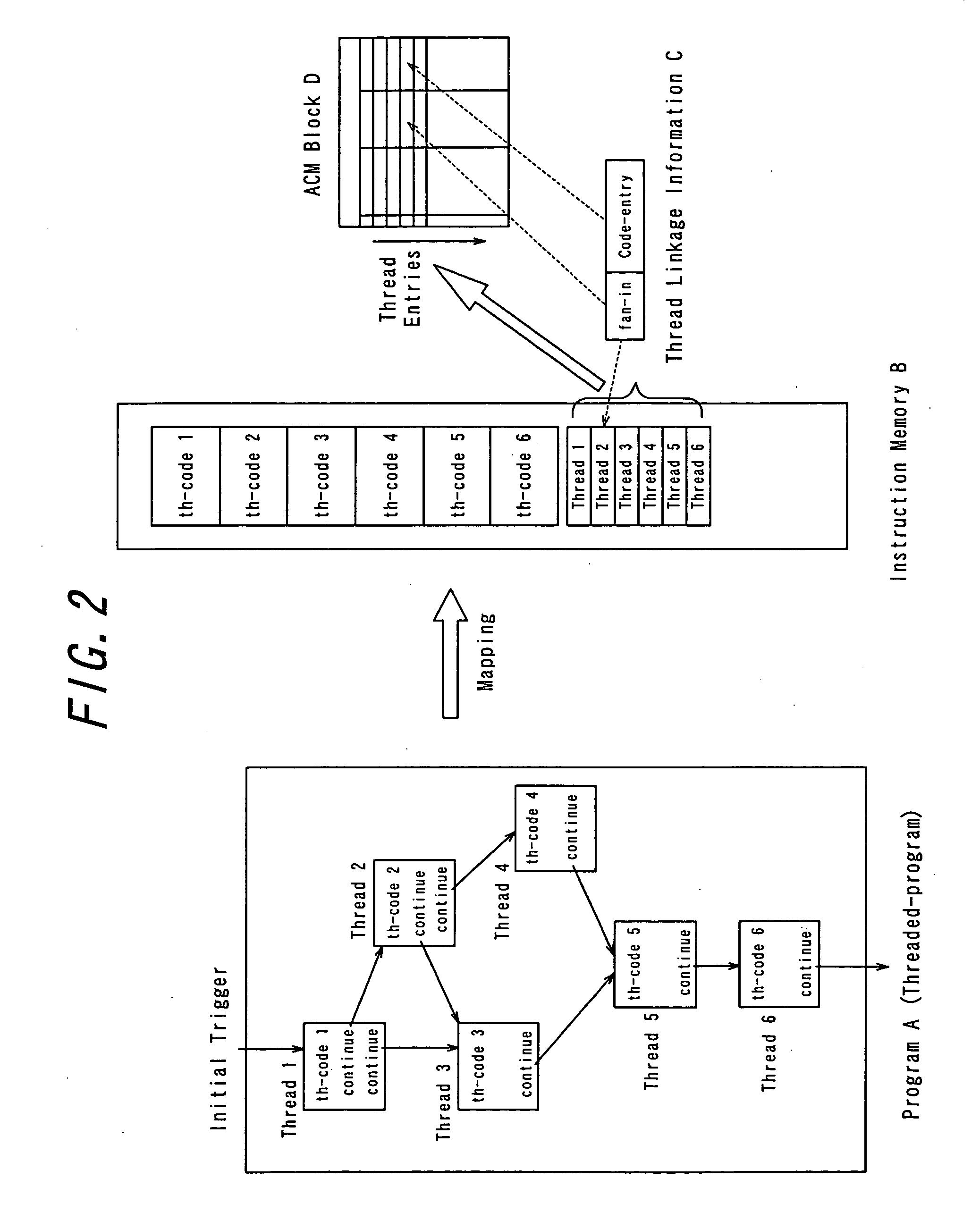
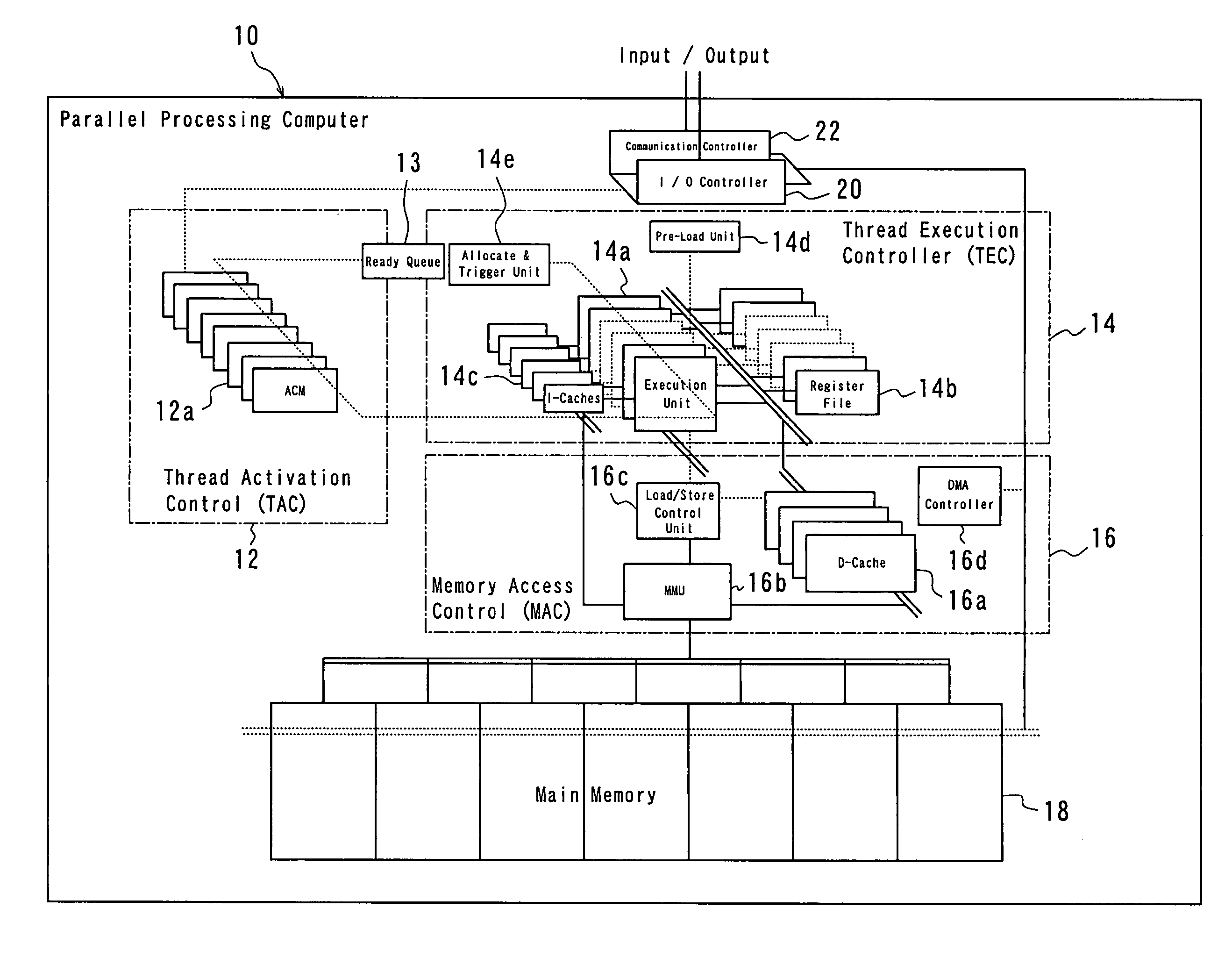
Parallel processing computer
InactiveUS20050240930A1Efficient executionImprove throughputProgram initiation/switchingRegister arrangementsProgram fragmentFile allocation
There is provided a parallel processing computer for executing a plurality of threads concurrently and in parallel. The computer includes: a thread activation controller for determining whether or not each of threads, which are exclusively executable program fragments, is ready-to-run, to put the thread determined ready-to-run into a ready thread queue as ready-to-run thread; and a thread execution controller having a pre-load unit, an EU allocation and trigger unit, a plurality of thread execution units and a plurality of register files including a plurality of registers, and the pre-load unit, prior to when each ready-to-run thread in the ready thread queue is executed, allocates a free register file of the plurality of register files to the each ready-to-run thread, to load initial data for the each ready-to-run thread into the allocated register file, and the EU allocation and trigger unit, when there is a thread execution unit in idle state of the plurality of thread execution unit, retrieves ready-to-run thread from the top of the ready thread queue, and to allocate the retrieved ready-to-run thread to the thread execution unit in idle state, and to couple the register file loaded the initial data for the ready-to-run thread with the allocated thread execution unit in idle state, and to trigger the ready-to-run thread. The plurality of thread execution units execute the triggered threads concurrently in parallel.
Owner:KYUSHU UNIV
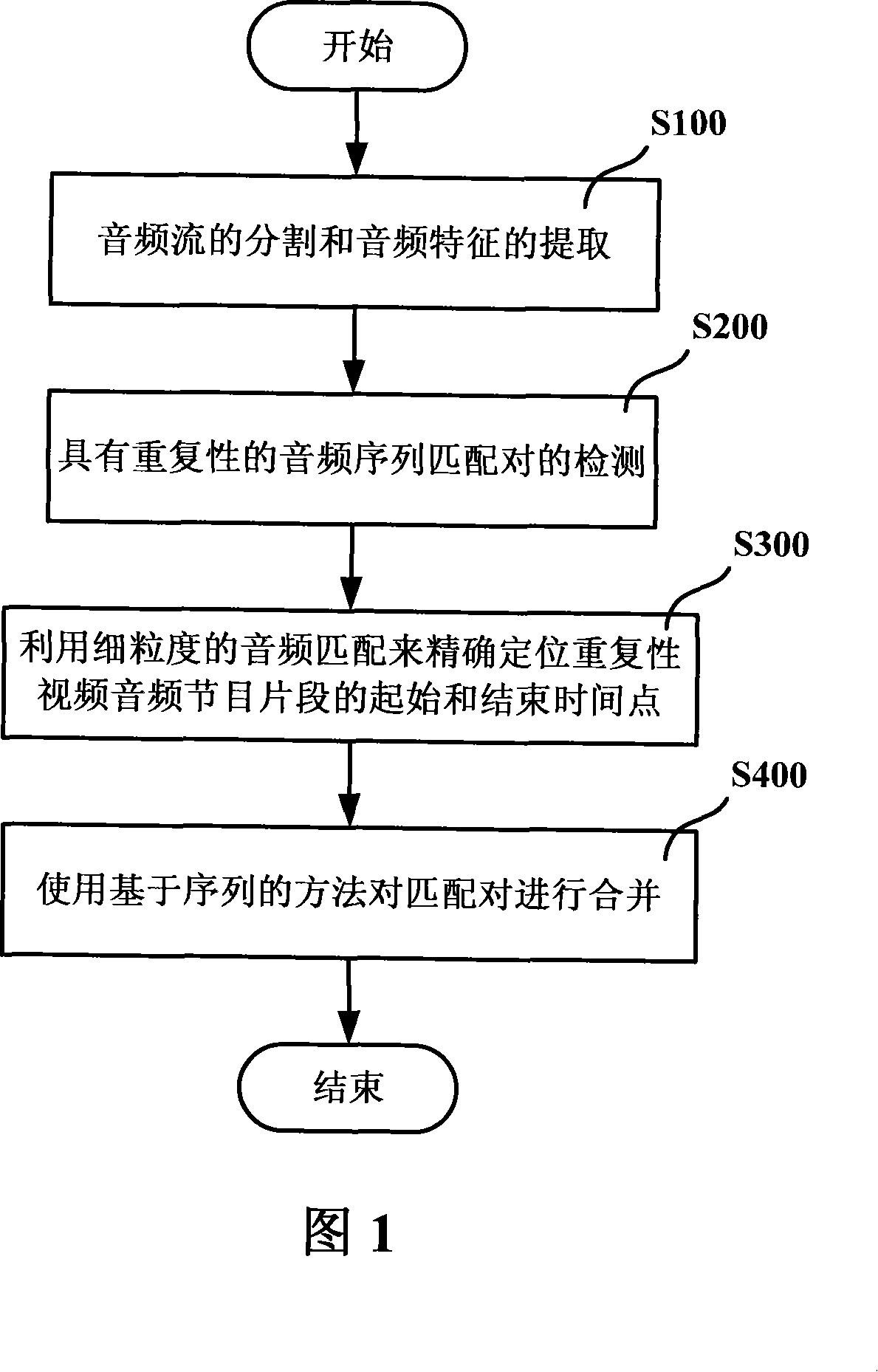
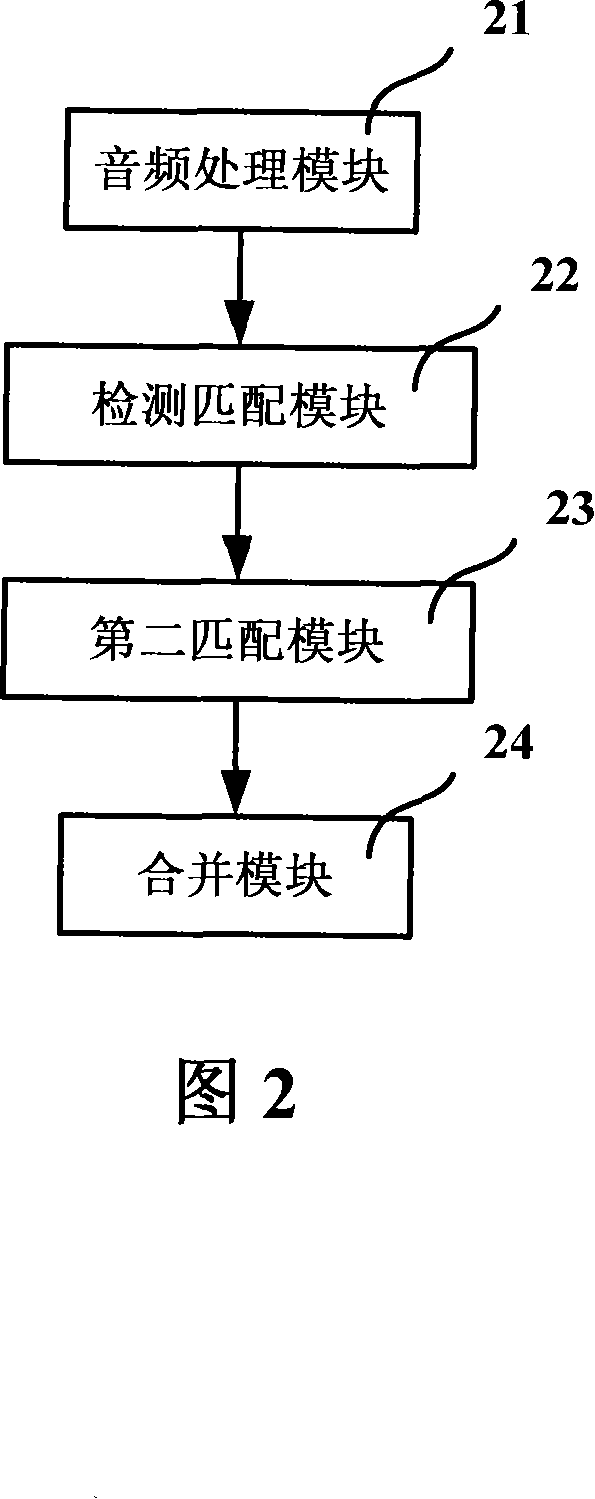
Method and system for detecting repeatable video and audio program fragment
ActiveCN101159834AImprove accuracyReduce data volumeTelevision system detailsCarrier indexing/addressing/timing/synchronisingProgram fragmentGranularity
The invention discloses a method and a system for detecting repeated video-audio program fragments. The method includes the following steps: dividing an audio stream in a to-be-detected video-audio program fragment to obtain audio stream fragments, and extracting audio features from each audio stream fragment; in the video-audio program stream, detecting an audio sequence of the repeated video-audio program fragment matching with the audio stream fragment to obtain the repeated video-audio program fragment; aimed at the primarily obtained repeated video-audio program fragment, precisely positioning starting and stopping time points of the repeated video-audio program fragment by matching audio of fine granularity; and combining matching pairs of the precisely positioned repeated video-audio program fragment with a method based on the sequence, thereby obtaining the whole repeated video-audio program fragment. The invention can detect certain video-audio program fragment in video-audio program with high precision and high efficiency.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Apparatus for visualizing program slices
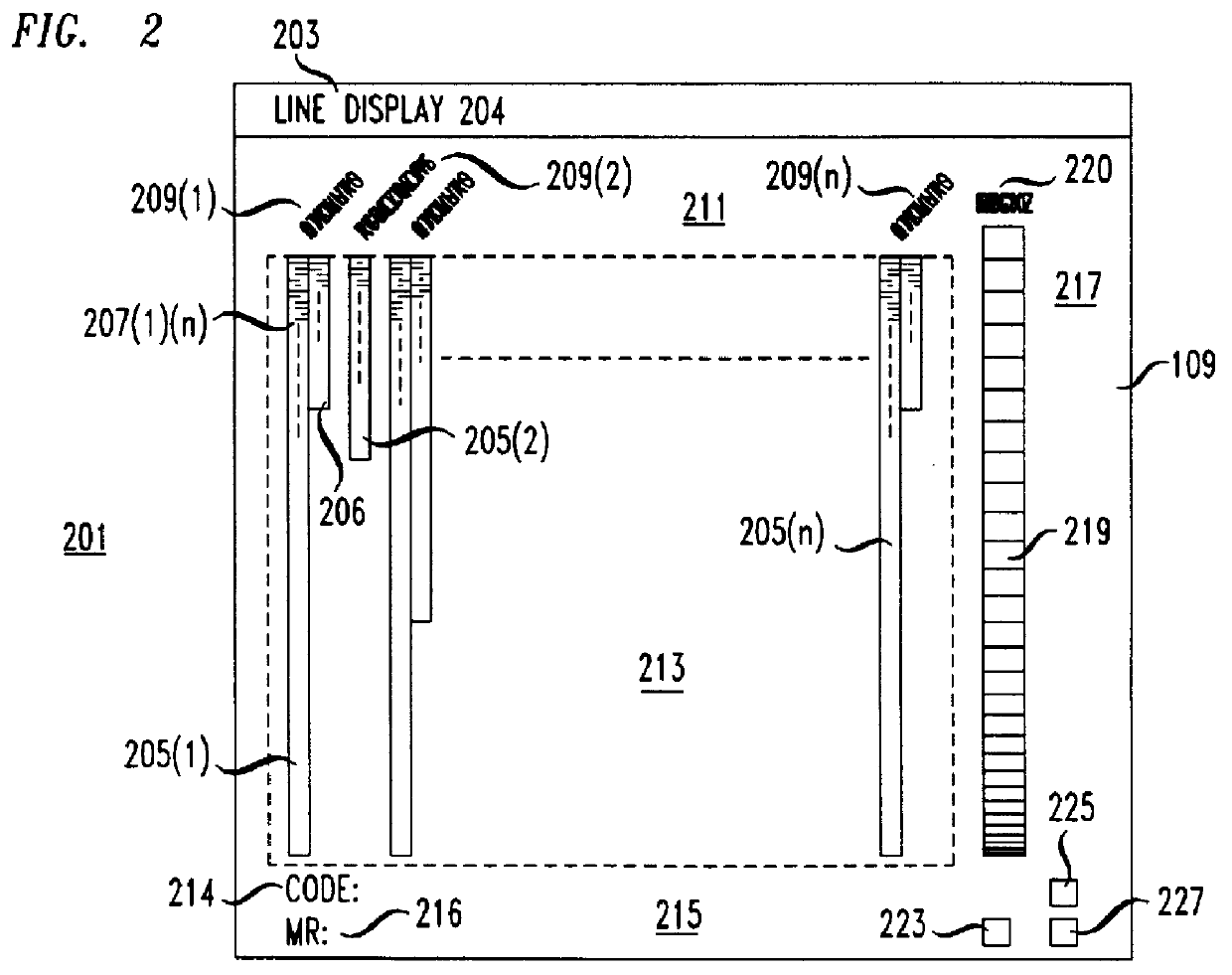
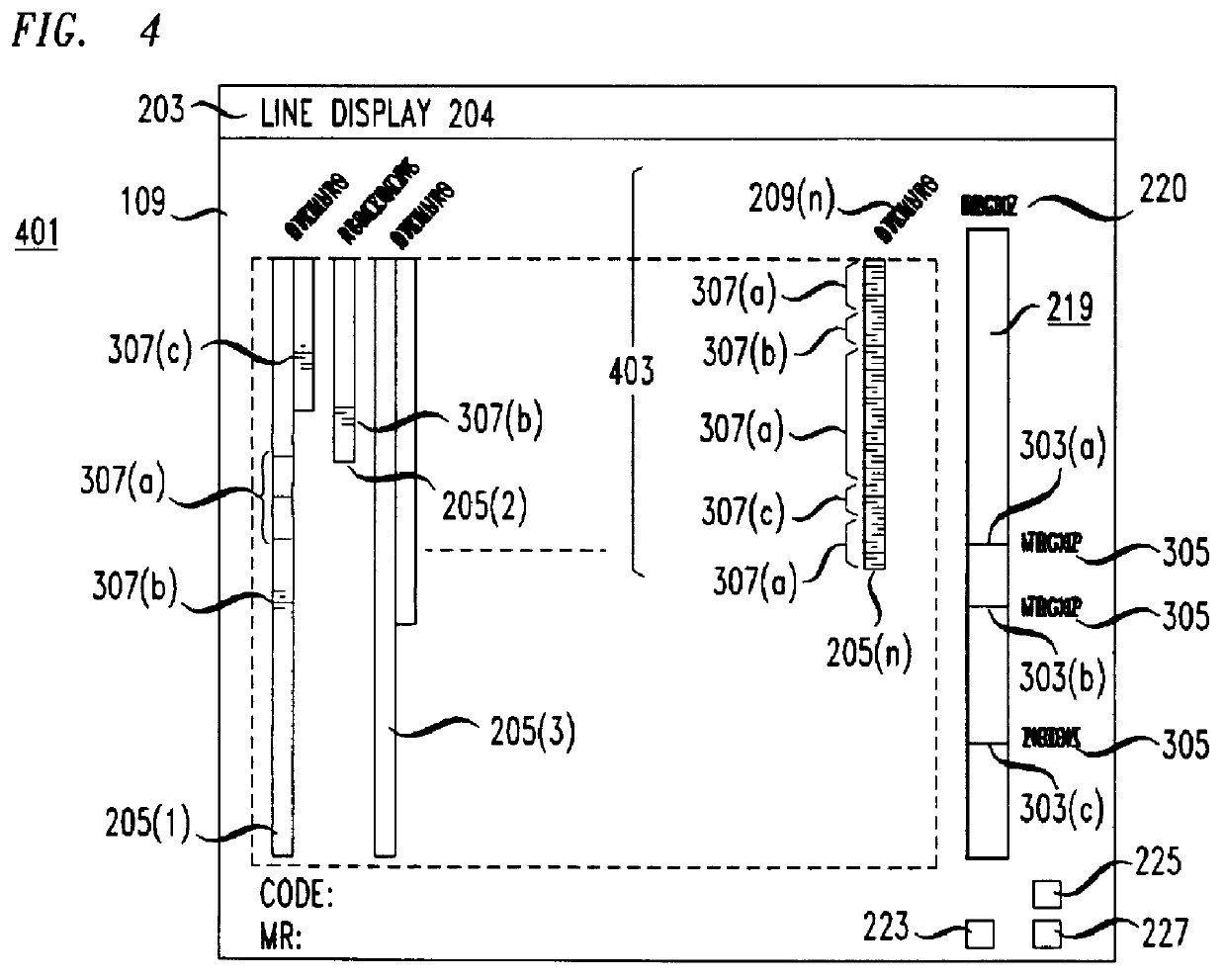
Apparatus for visualizing slices of transitive closures of entities having dependence relationships with one another. A preferred embodiment visualizes slices of programs. A display in a computer system includes reduced representations of the files, procedures, and lines making up a program. The user employs a pointing device to interactively select a reduced representation as the slice point and the apparatus computes the slice and changes the color of the reduced representations in the slice. The color of the reduced representation indicates the distance of the entity represented by the reduced representation from the slice point. The display may be rearranged so that files and procedures are ordered by distance from the slice point. Other aspects of the display include scaling the size of the reduced representation of a procedure to indicate the number of lines in the procedure and filling the reduced representation of the procedure according to the number of lines belonging to the slice which are contained in the procedure. A user may select open and closed representations of procedures. The open representation of a procedure contains reduced representations of the lines in the procedure. The apparatus also includes a viewer for viewing the text of lines in the program.
Owner:LUCENT TECH INC
Nondestructive self-publishing video editing system
InactiveUS20070250899A1Easy to findIntuitive experienceElectronic editing digitised analogue information signalsRecord information storageHigh bandwidthProgram fragment
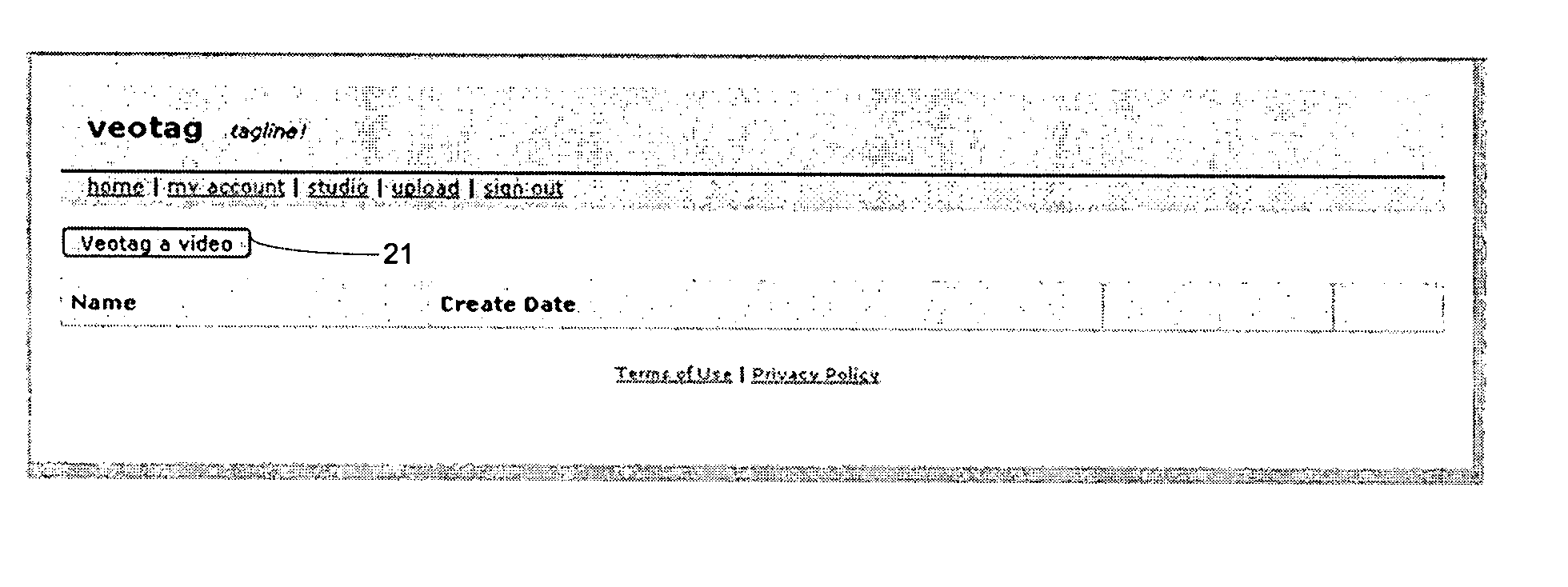
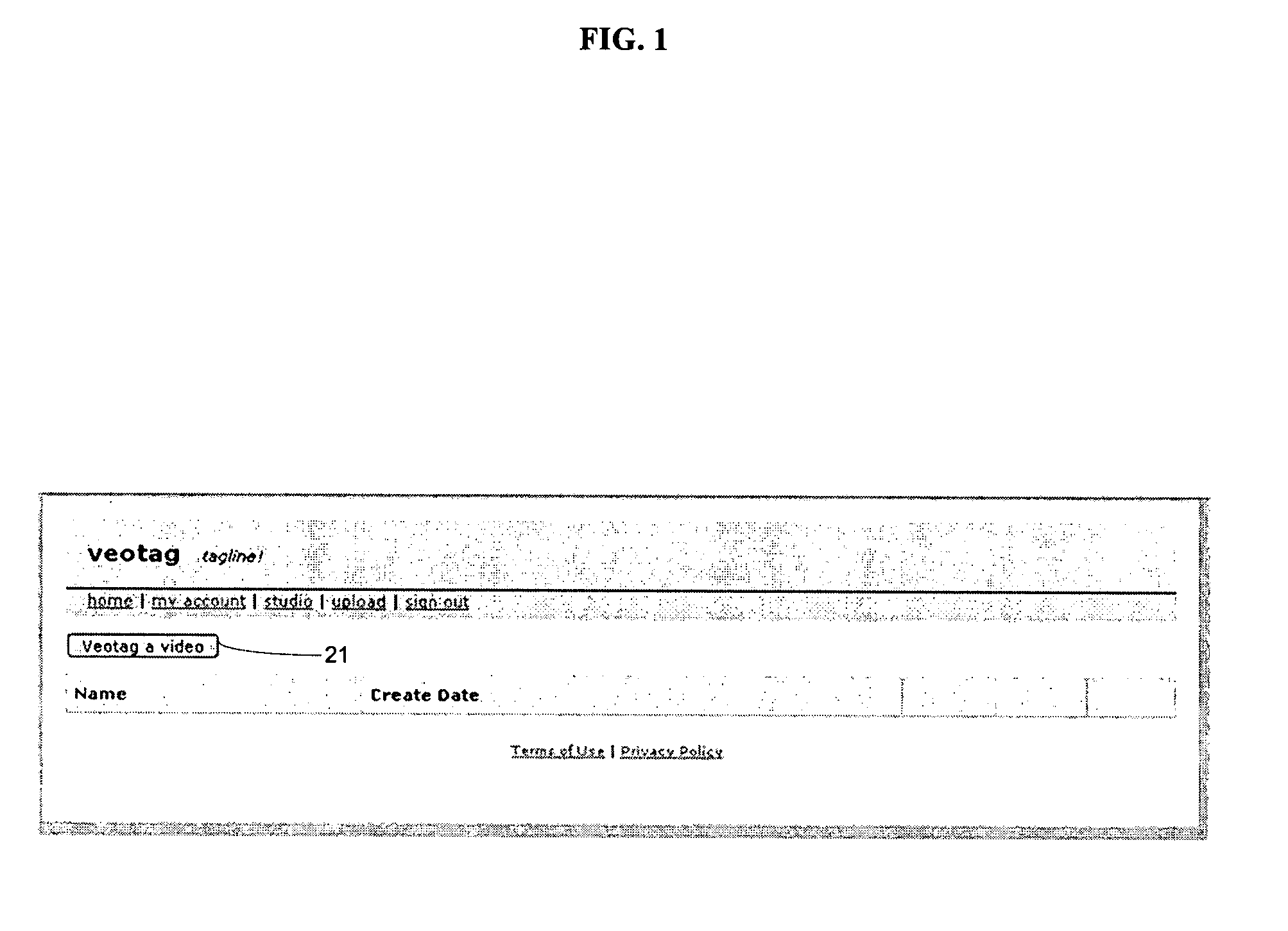
A video publishing and viewing system that allows the user to select a video on the user's network or on the Internet and produce a hierarchical menu describing the video content. The editing user can perform the entire process of selecting the video, creating the hierarchical menu along with descriptive text, and uploading the file from the same system, which is run entirely in a Web browser. The produced index is independent of the file formats as well as different play rates (low and high bandwidth). The same index appears for all viewings (or listenings) of the file. The system includes an auto-export feature that allows external search engines to look inside the video menu and make the video itself clickable and searchable as if it were a book (through the menu). The system also allows the user to build on already annotated videos by creating a new program from program fragments (hierarchical menu items) such that destructive video editing is not required.
Owner:VEOTAG
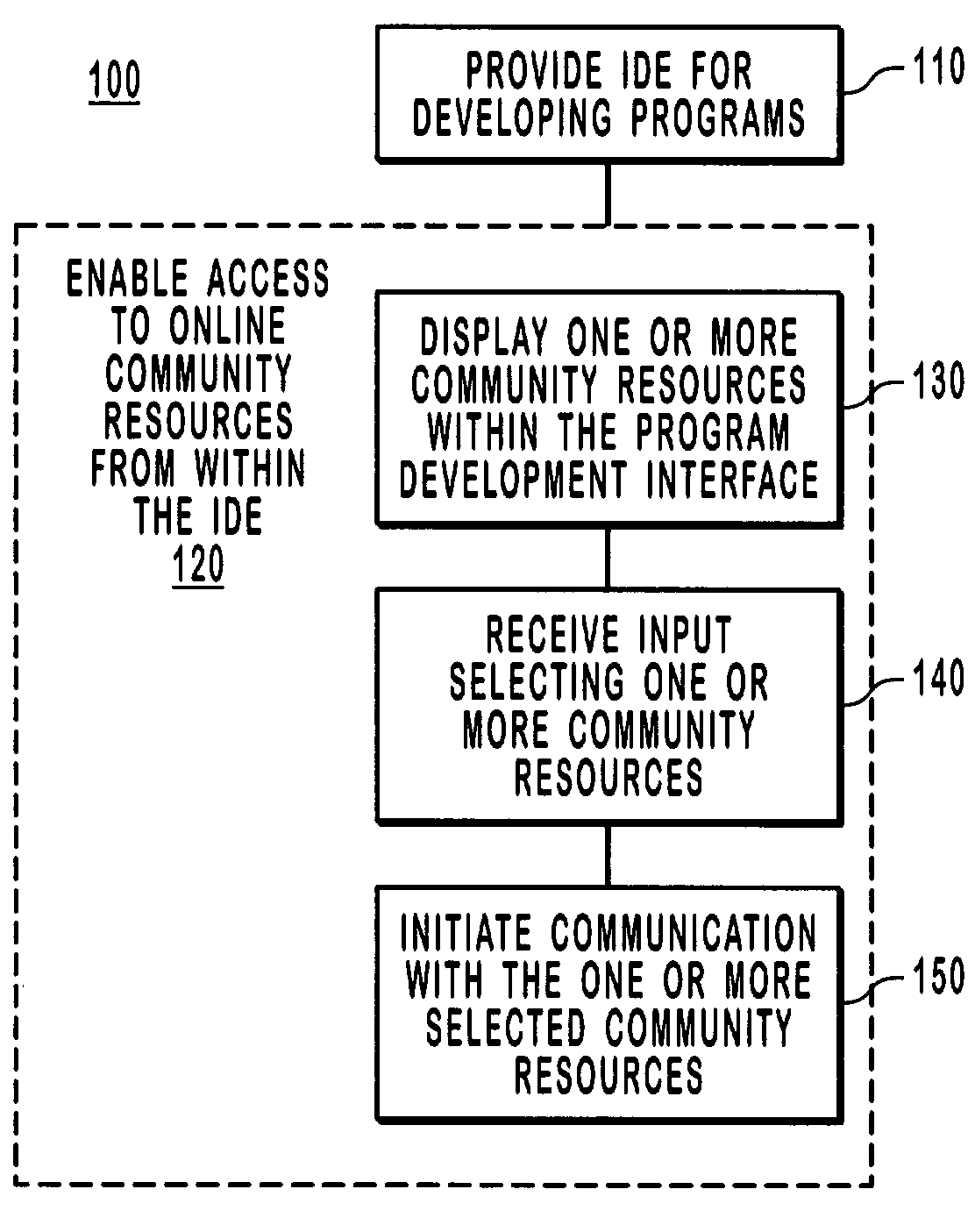
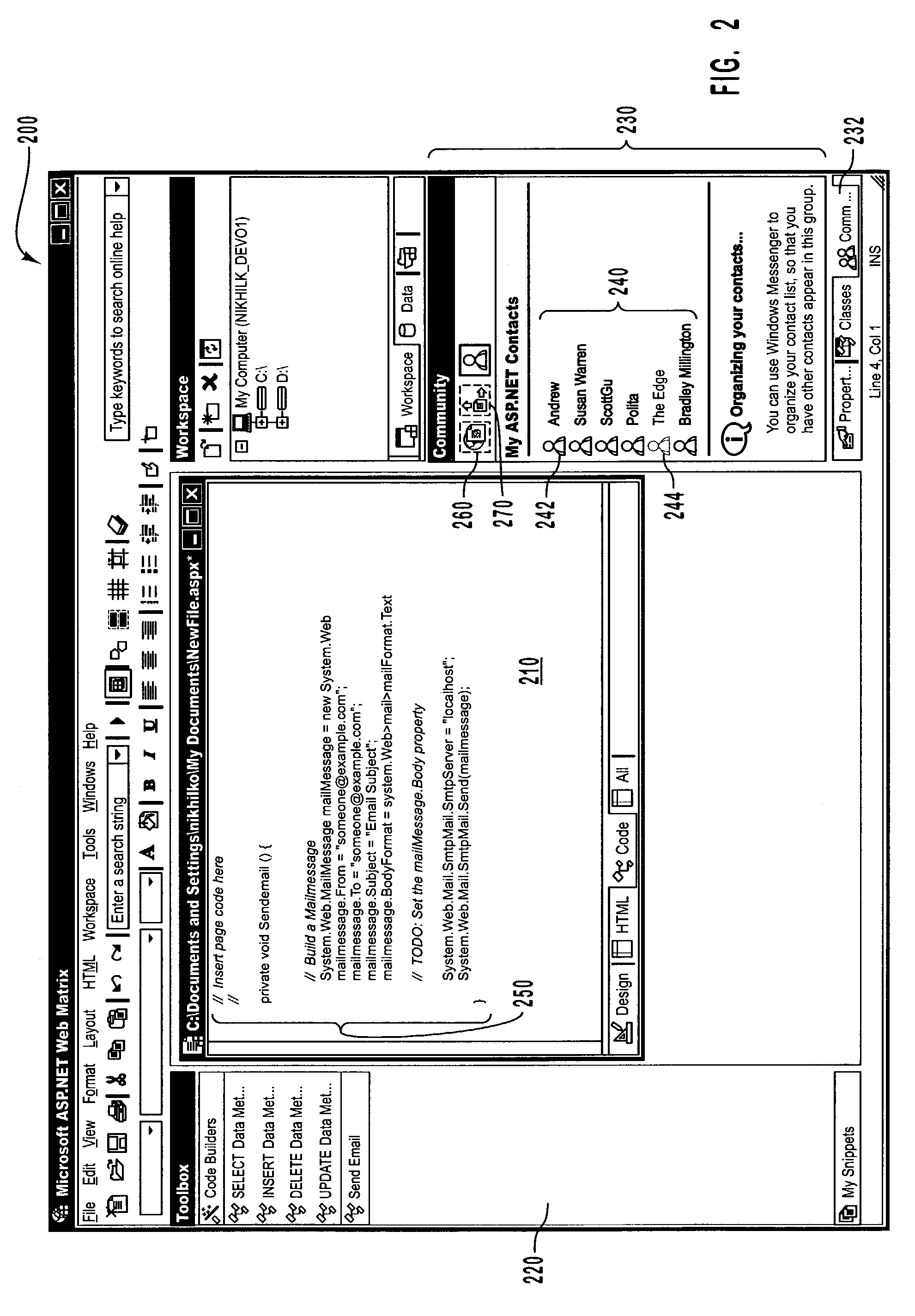
Integrating online community and program development environments
ActiveUS7395312B2Multiple digital computer combinationsSoftware designProgram fragmentMessage passing
An Integrated Development Environment (IDE) is configured with an online community interface for accessing online community resources, such as contacts and information, directly through the Internet or other networks. The online community interface displays icons and other selectable objects that are associated with contacts or webpages. Upon selecting an object associated with a contact, an email or instant messaging window is launched that enables communication with the one or more contacts. Upon selecting an object associated with a webpage, a browser is launched that accesses and displays the webpage. The online community interface also enables an IDE element, such as a development tool or program snippet to be copied from the IDE and sent to a desired contact through the IDE interface.
Owner:MICROSOFT TECH LICENSING LLC
Systems And Methods For Software Analytics
InactiveUS20150363197A1Error detection/correctionProgram documentationProgram fragmentSoftware analytics
Systems, methods, and computer program products are provided for locating design patterns in software. An example method includes accessing a database having multiple artifacts corresponding to multiple software, and identifying a design pattern for at least one of the software files by automatically analyzing at least one of the artifacts associated with the software. Additional embodiments also provide for storing an identifier for the design pattern for the software in the database. For certain example embodiments, the artifacts include developmental, which may be searched for a string that denotes a design pattern, such as flaw, feature, or repair. Additional example embodiments also include finding in the software file a program fragment that implements the design pattern.
Owner:CHARLES STARK DRAPER LABORATORY
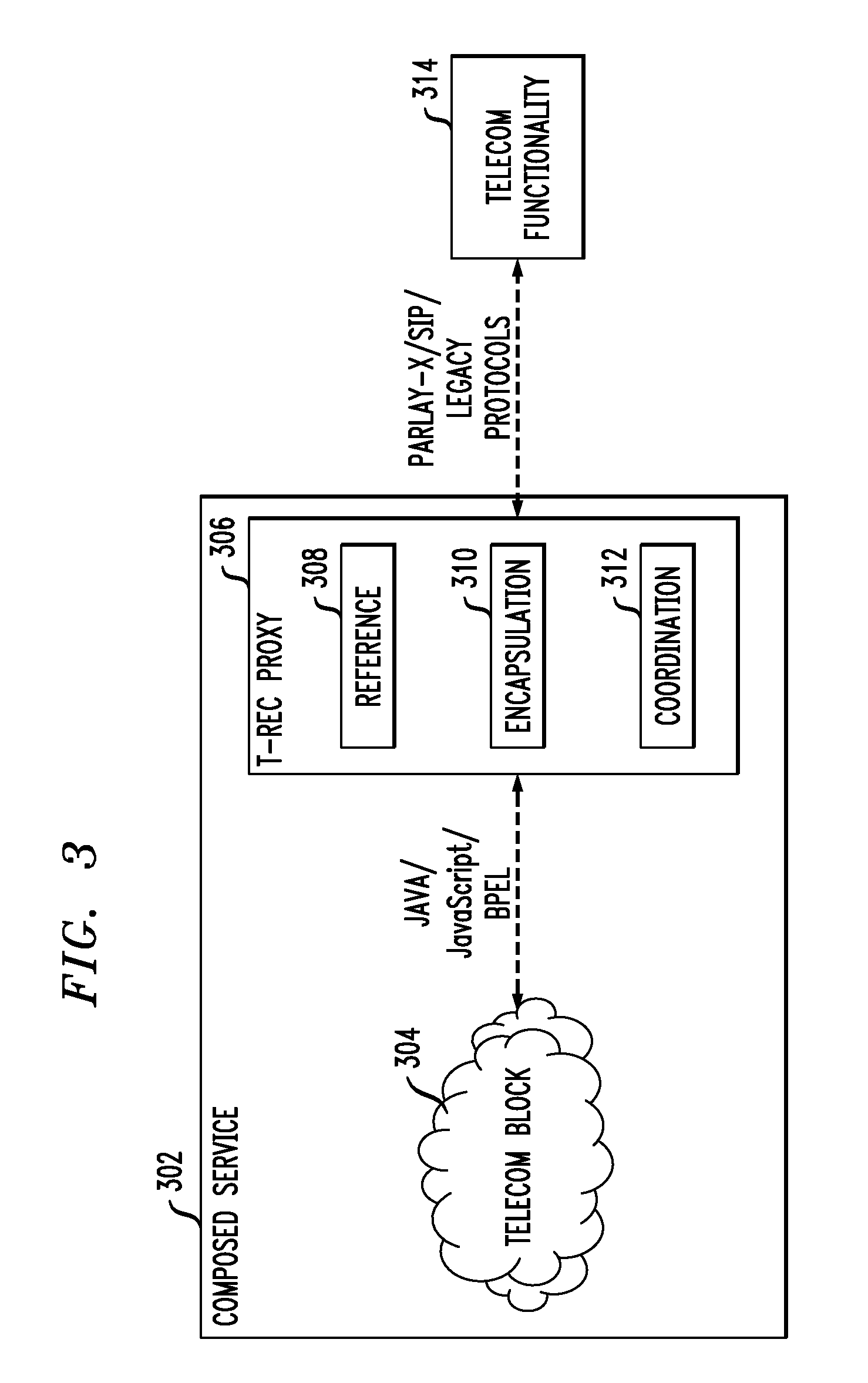
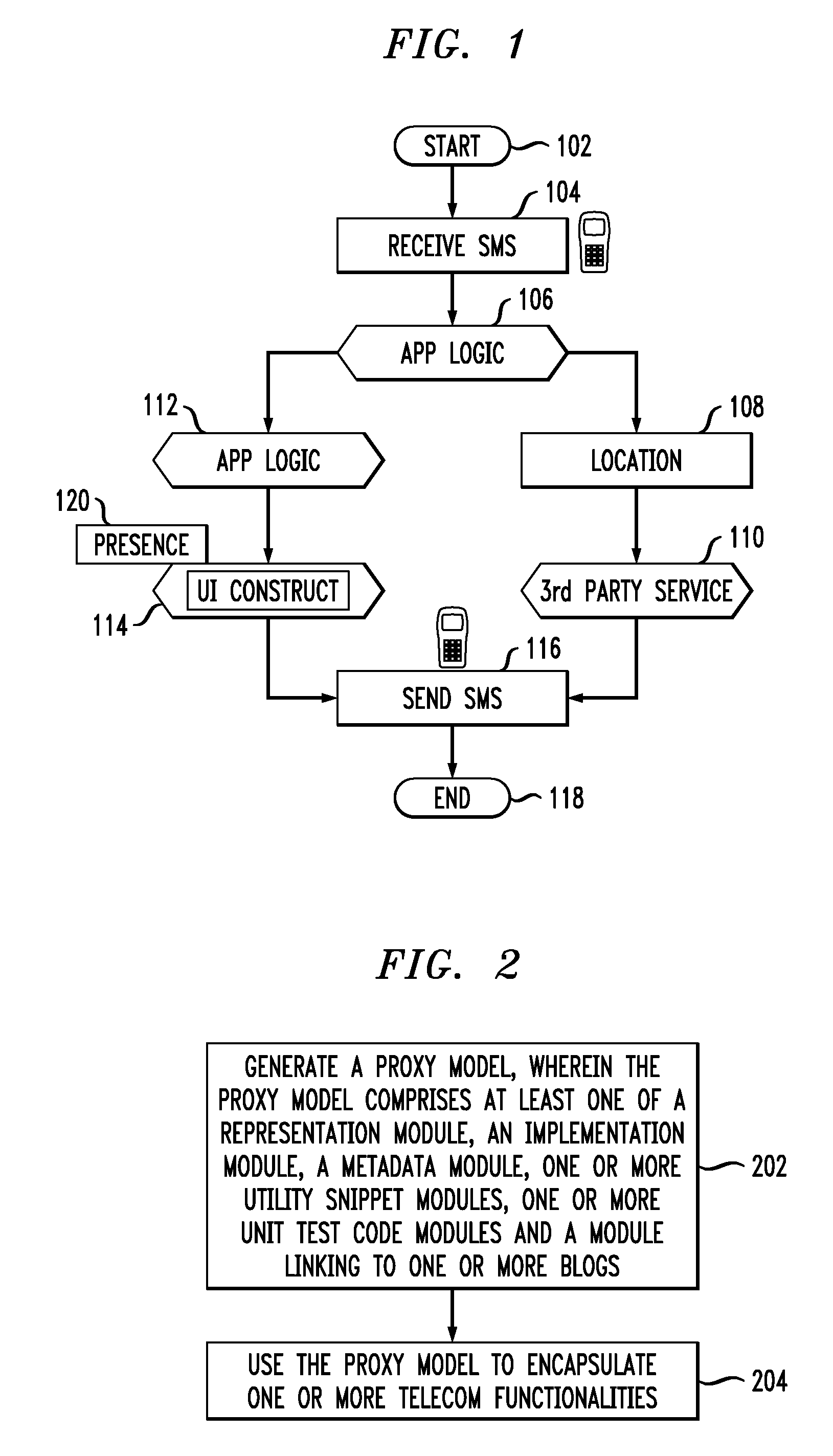
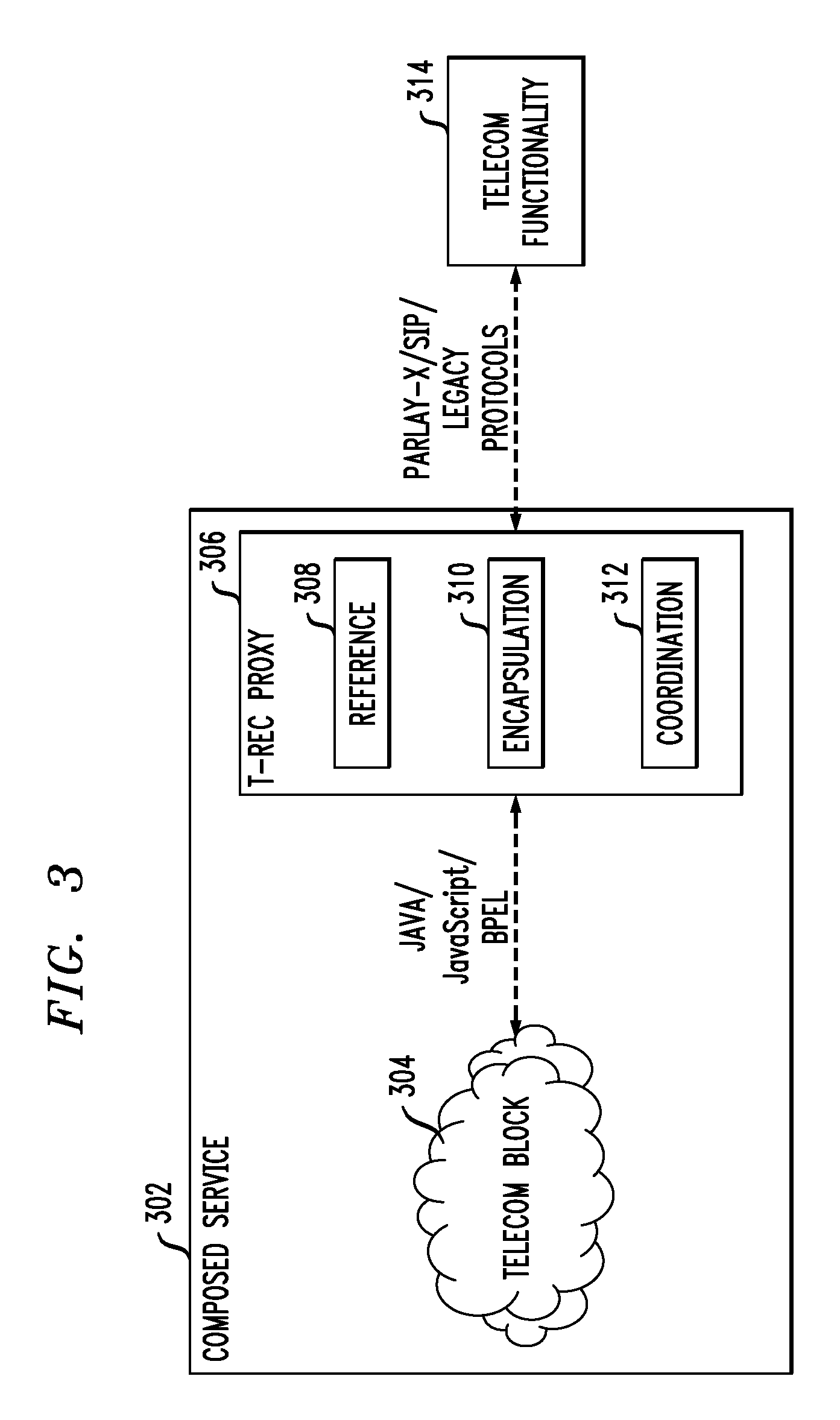
System And Computer Program Product For Creating A Telecommunications Application
InactiveUS20090129575A1Special service for subscribersWireless commuication servicesProgram fragmentTelecommunications link
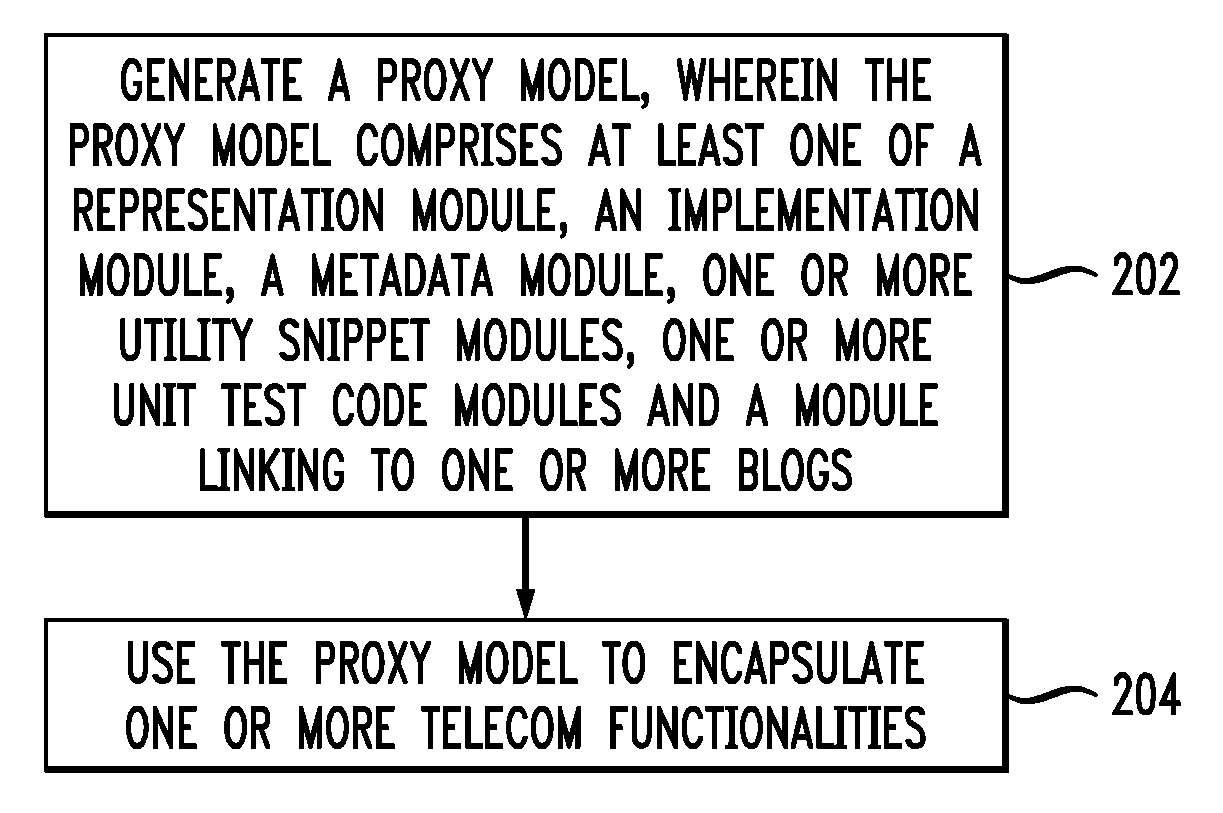
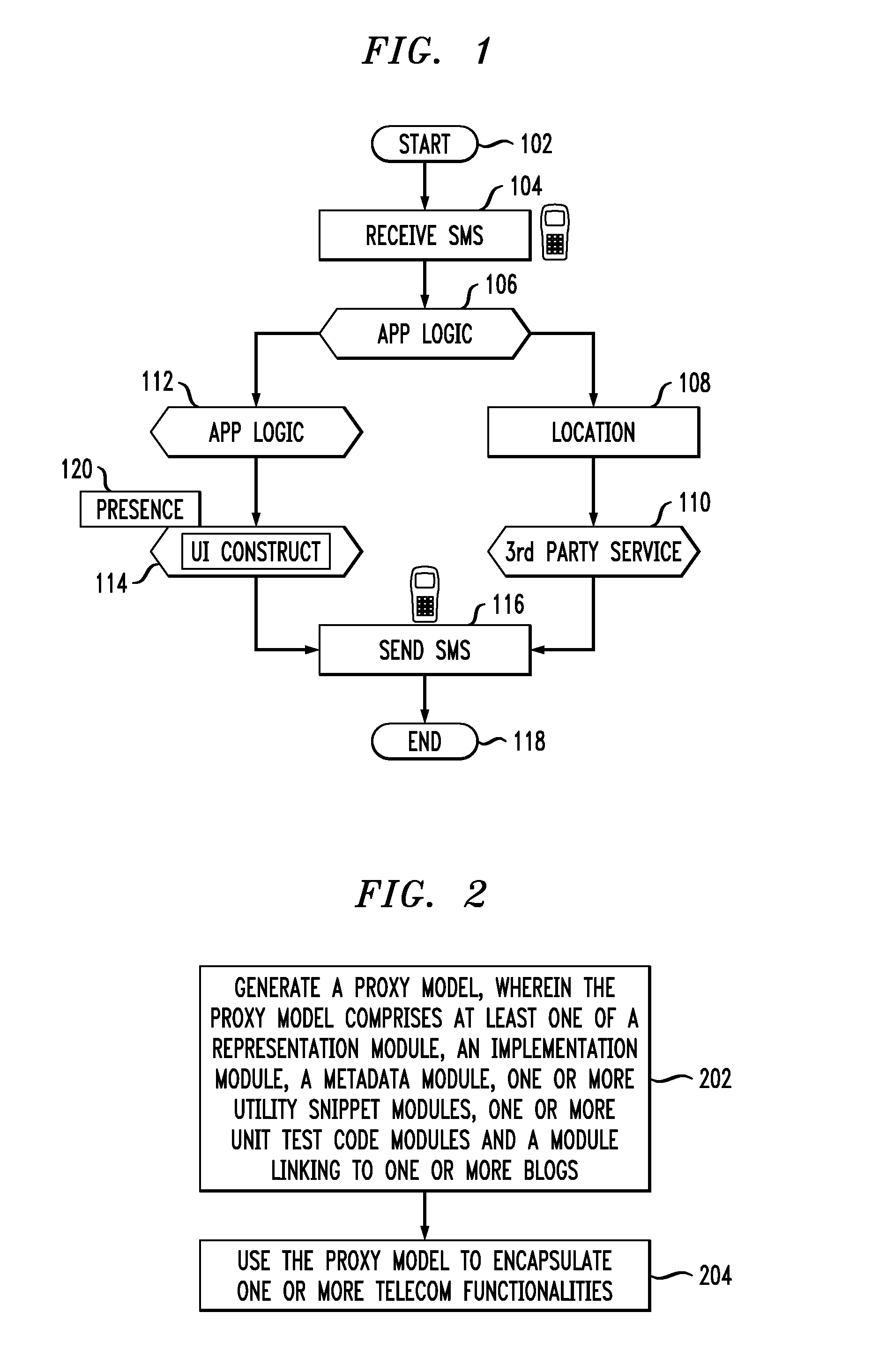
Techniques for using a proxy model to encapsulate one or more telecommunications (telecom) functionalities are provided. The techniques include generating a proxy model, wherein the proxy model comprises at least one of a representation module, an implementation module, a metadata module, one or more utility snippet modules, one or more unit test code modules and a module linking to one or more blogs, and using the proxy model to encapsulate one or more telecom functionalities. Techniques are also provided for creating a telecom service using the proxy model.
Owner:IBM CORP
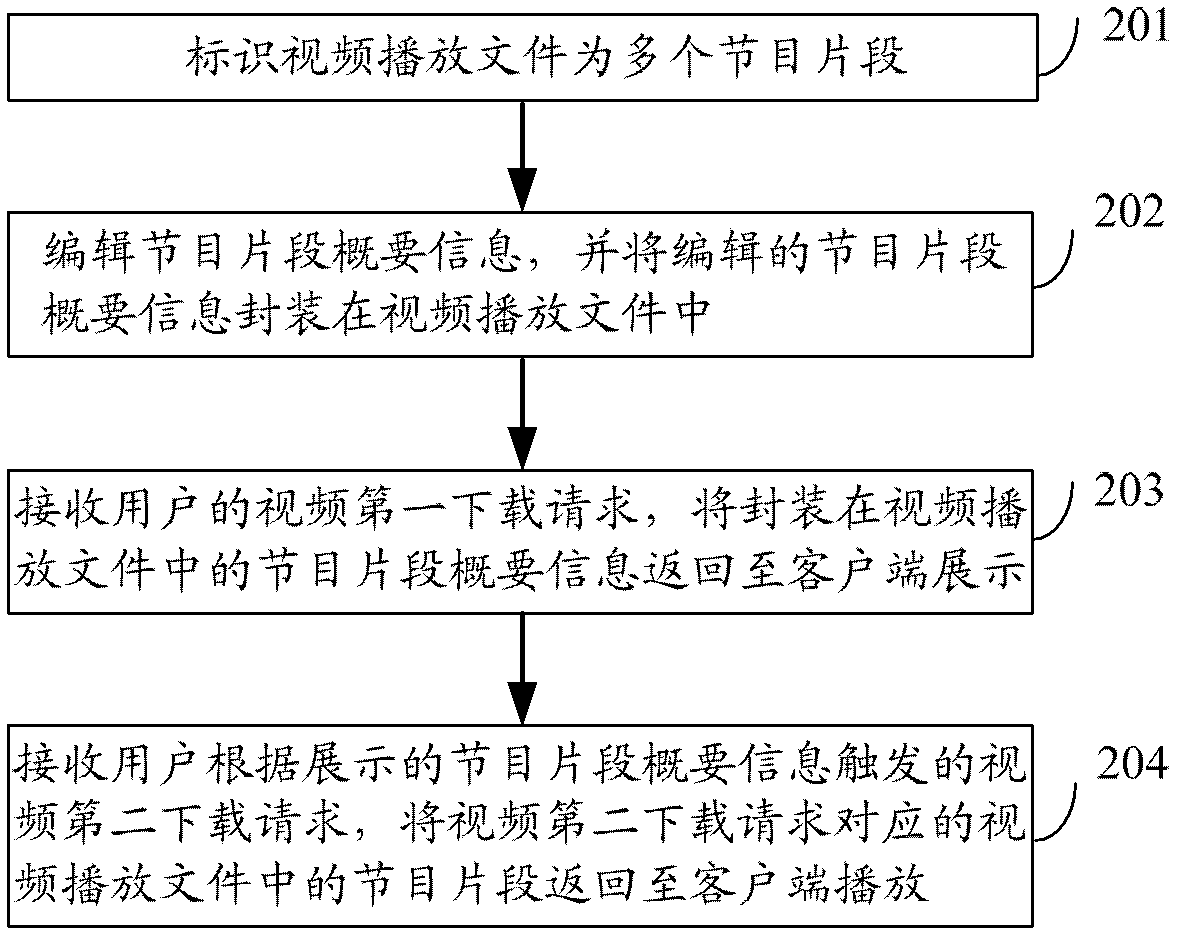
Online video playing method and video playing server
ActiveCN103024458AMeet individual needsEasy to shareSelective content distributionProgram fragmentService experience
The invention discloses an online video playing method and a video playing server. The method comprises the following steps: marking a video playing file into multiple program fragments; editing summary information of the program fragments and packaging the edited summary information of the program fragments in the video playing file; receiving a video first download request of a user, and returning the summary information of the program fragments, which is packaged in the video playing file to a client for display; and receiving a video second download request triggered by the user according to the displayed summary information of the program fragments, and returning the program fragments in the video playing file, which correspond to the video second download request, to the client for playing. By applying the method disclosed by the invention, the cost of the user can be reduced and the video service experience of the user can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
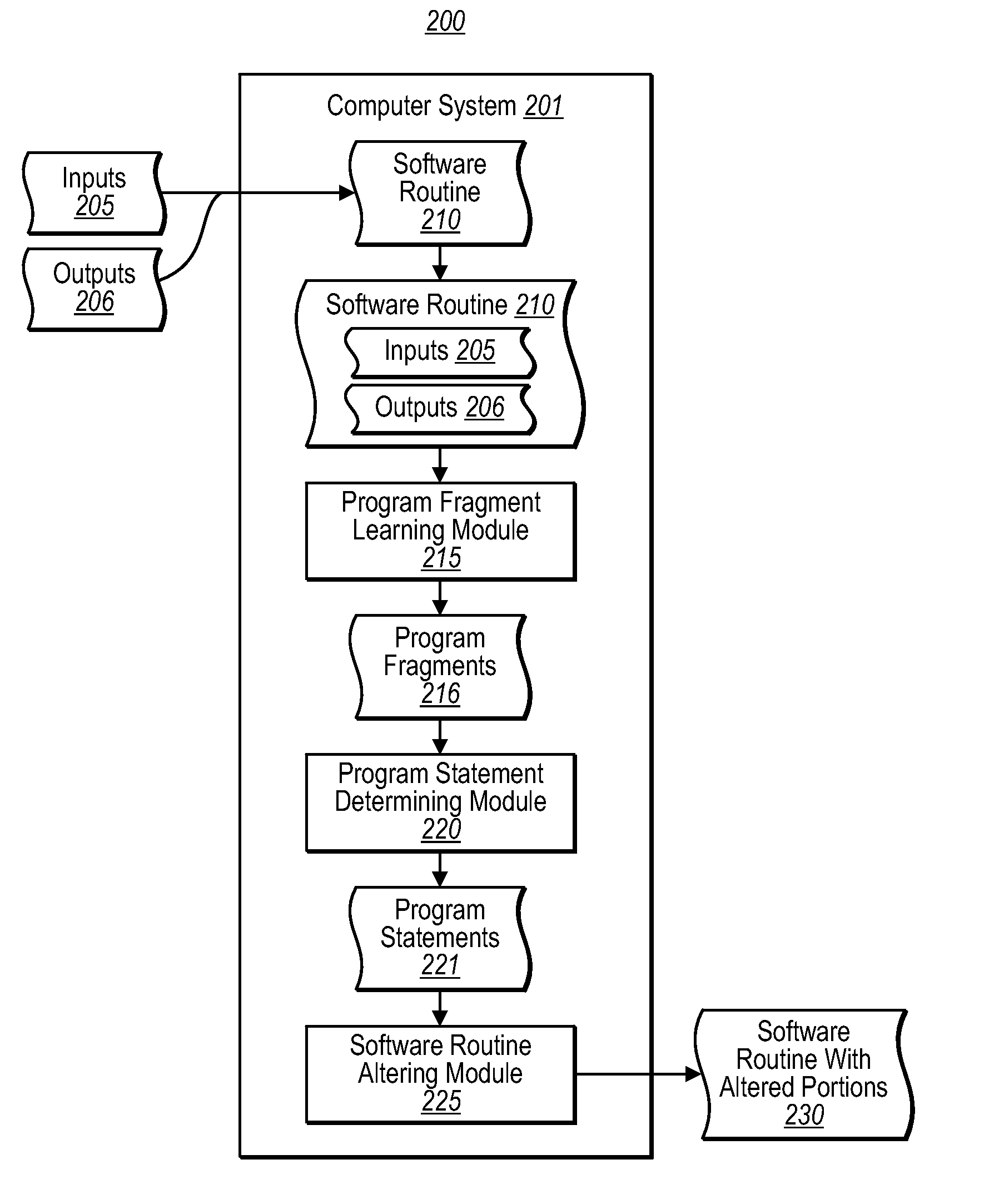
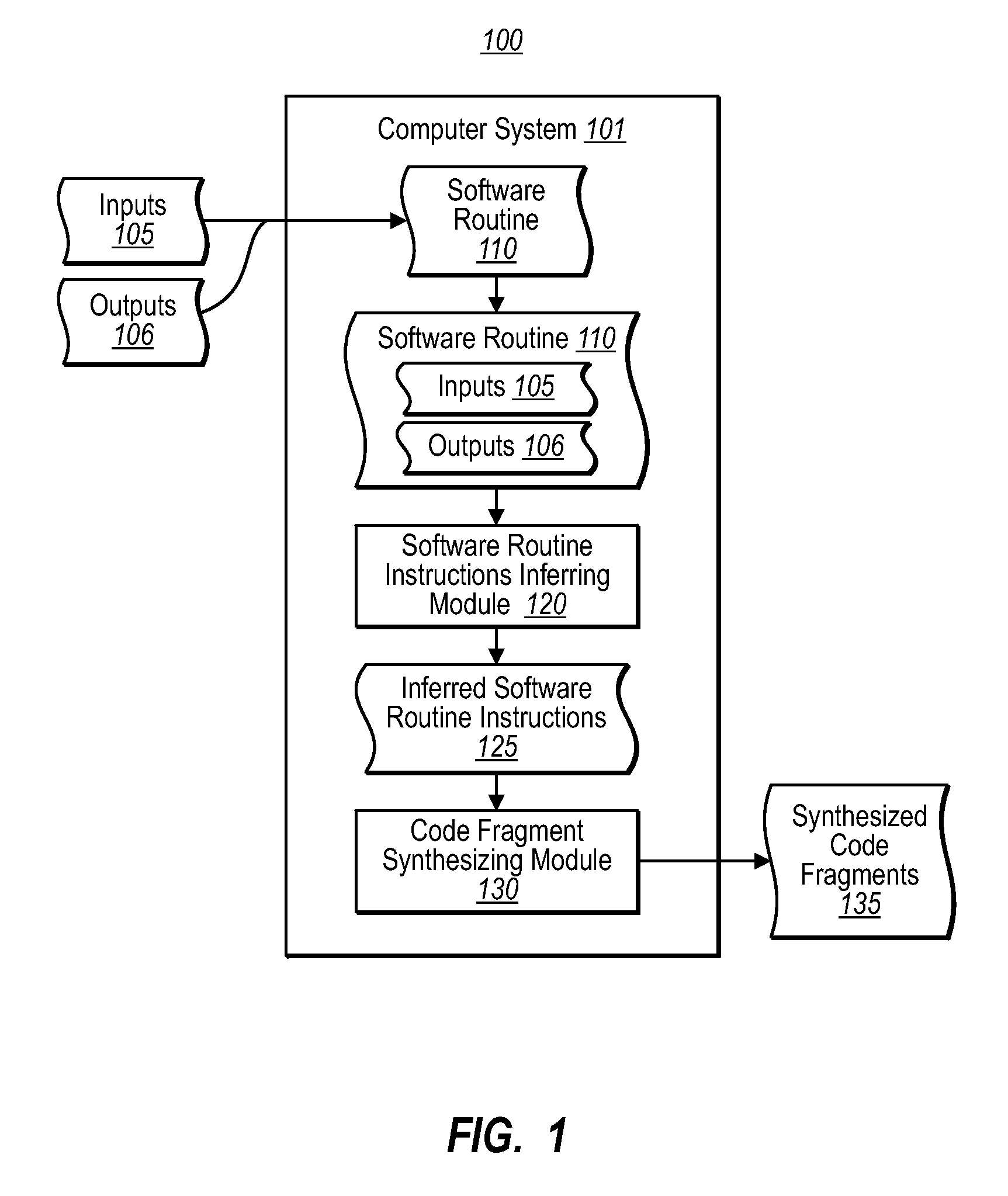
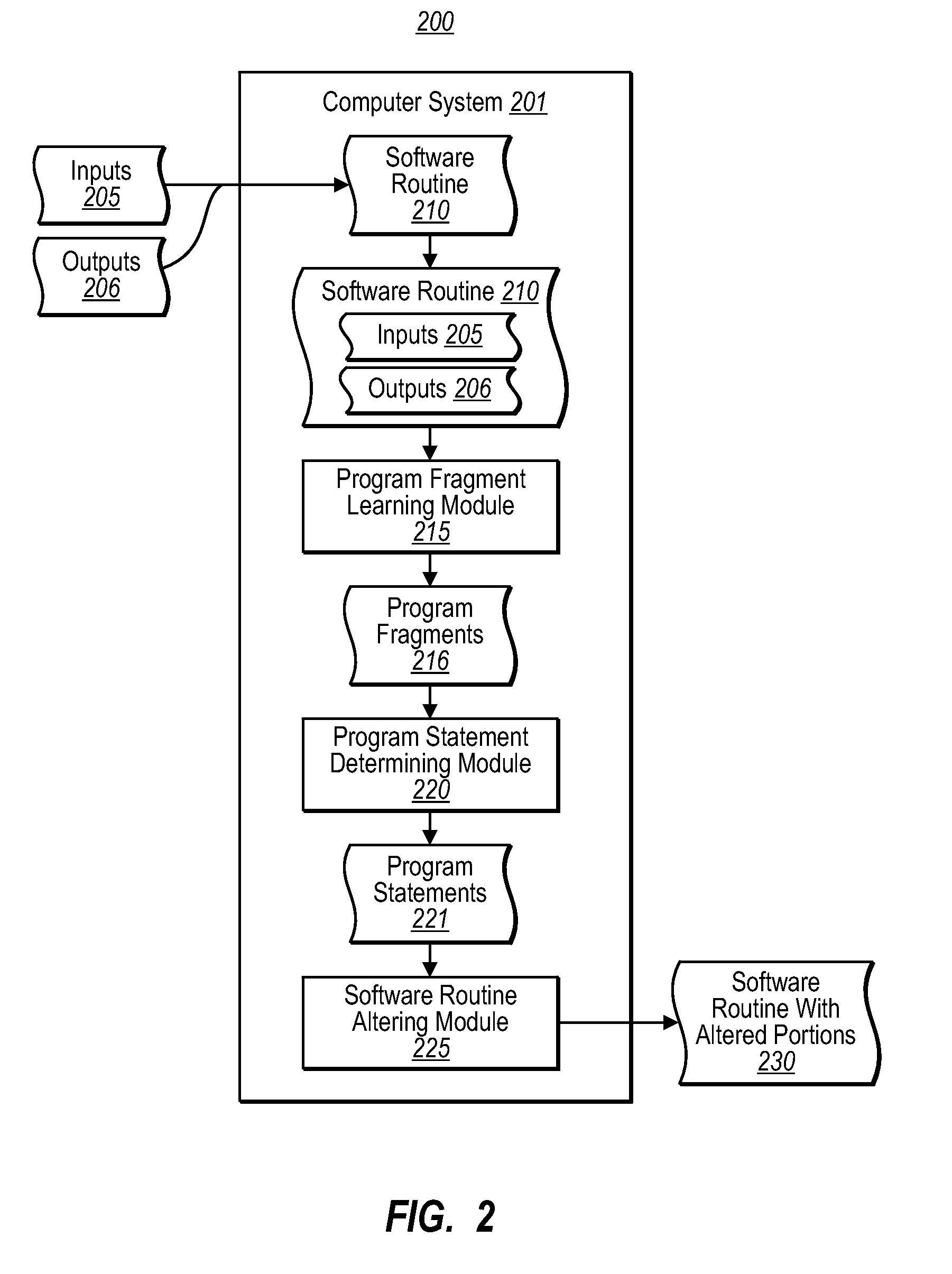
Program synthesis and debugging using machine learning techniques
ActiveUS20080282108A1Well formedSoftware engineeringError detection/correctionProgram fragmentState switching
One embodiment is directed to synthesizing code fragments in a software routine using known inputs and corresponding expected outputs. A computer system provides a software routine with known inputs and corresponding expected outputs, infers software routine instructions based on the known inputs and corresponding expected outputs, and synthesizes a correctly functioning code fragment based on the inferred instructions. Another embodiment is directed to automatically resolving semantic errors in a software routine. A computer system provides the software routine with known inputs and corresponding expected outputs for portions of a program fragment where an error has been localized. The computer system learns a correctly functioning program fragment from pairs of input-output descriptions of the program fragment, determines the program statements that can transform given input states into given output states after execution of those program statements, and alters portions of the software routine with the learned program fragments.
Owner:MICROSOFT TECH LICENSING LLC
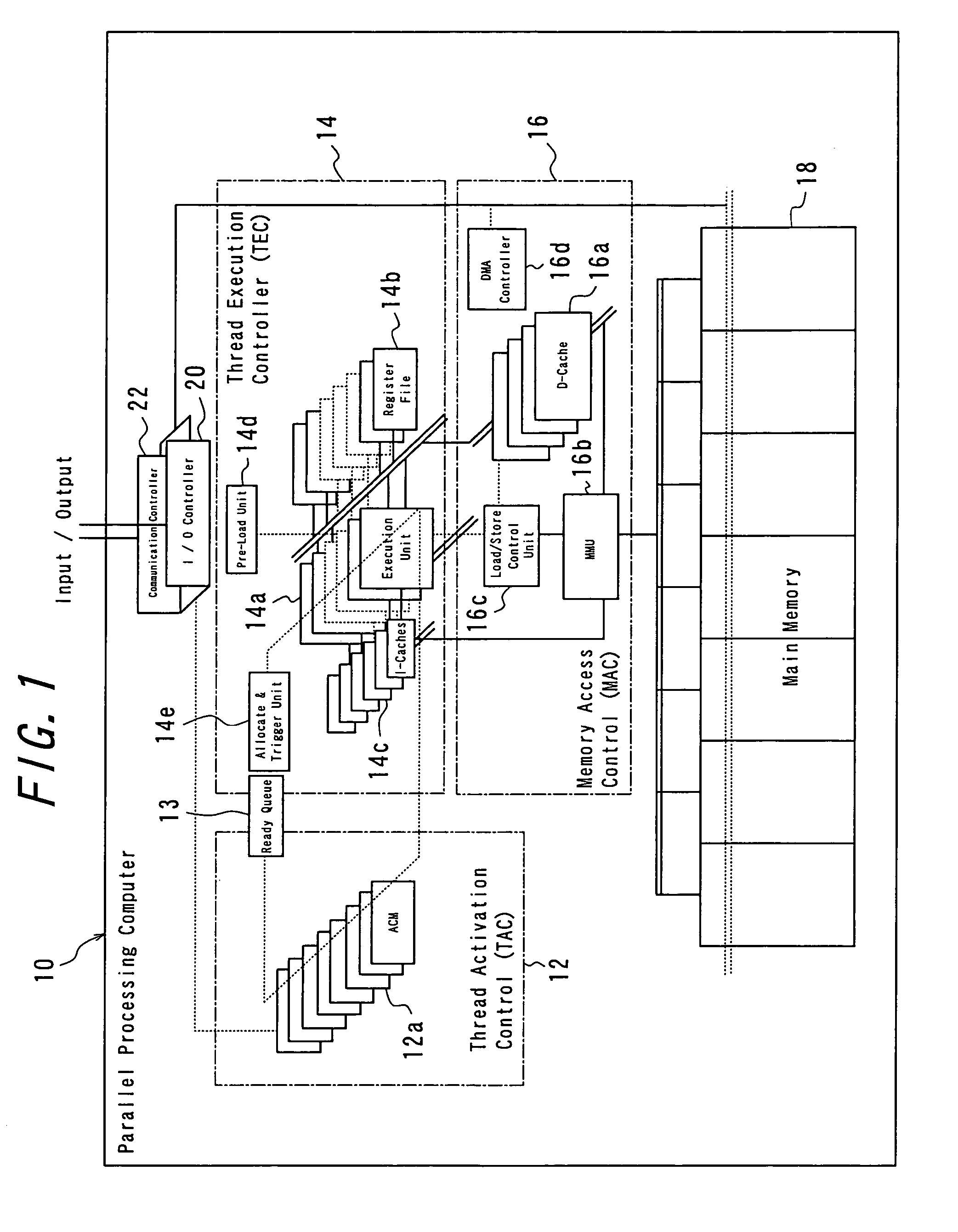
Parallel processing computer
InactiveUS7650602B2Large capacityIncrease speedProgram initiation/switchingRegister arrangementsProgram fragmentProcessor register
There is provided a parallel processing computer for executing a plurality of threads concurrently and in parallel. The computer includes: a thread activation controller for determining whether or not each of threads, which are exclusively executable program fragments, is ready-to-run, to put the thread determined ready-to-run into a ready thread queue as ready-to-run thread; and a thread execution controller having a pre-load unit, an EU allocation and trigger unit, a plurality of thread execution units and a plurality of register files including a plurality of registers, and the pre-load unit, prior to when each ready-to-run thread in the ready thread queue is executed, allocates a free register file of the plurality of register files to the each ready-to-run thread, to load initial data for the each ready-to-run thread into the allocated register file, and the EU allocation and trigger unit, when there is a thread execution unit in idle state of the plurality of thread execution unit, retrieves ready-to-run thread from the top of the ready thread queue, and to allocate the retrieved ready-to-run thread to the thread execution unit in idle state, and to couple the register file loaded the initial data for the ready-to-run thread with the allocated thread execution unit in idle state, and to trigger the ready-to-run thread. The plurality of thread execution units execute the triggered threads concurrently in parallel.
Owner:KYUSHU UNIV
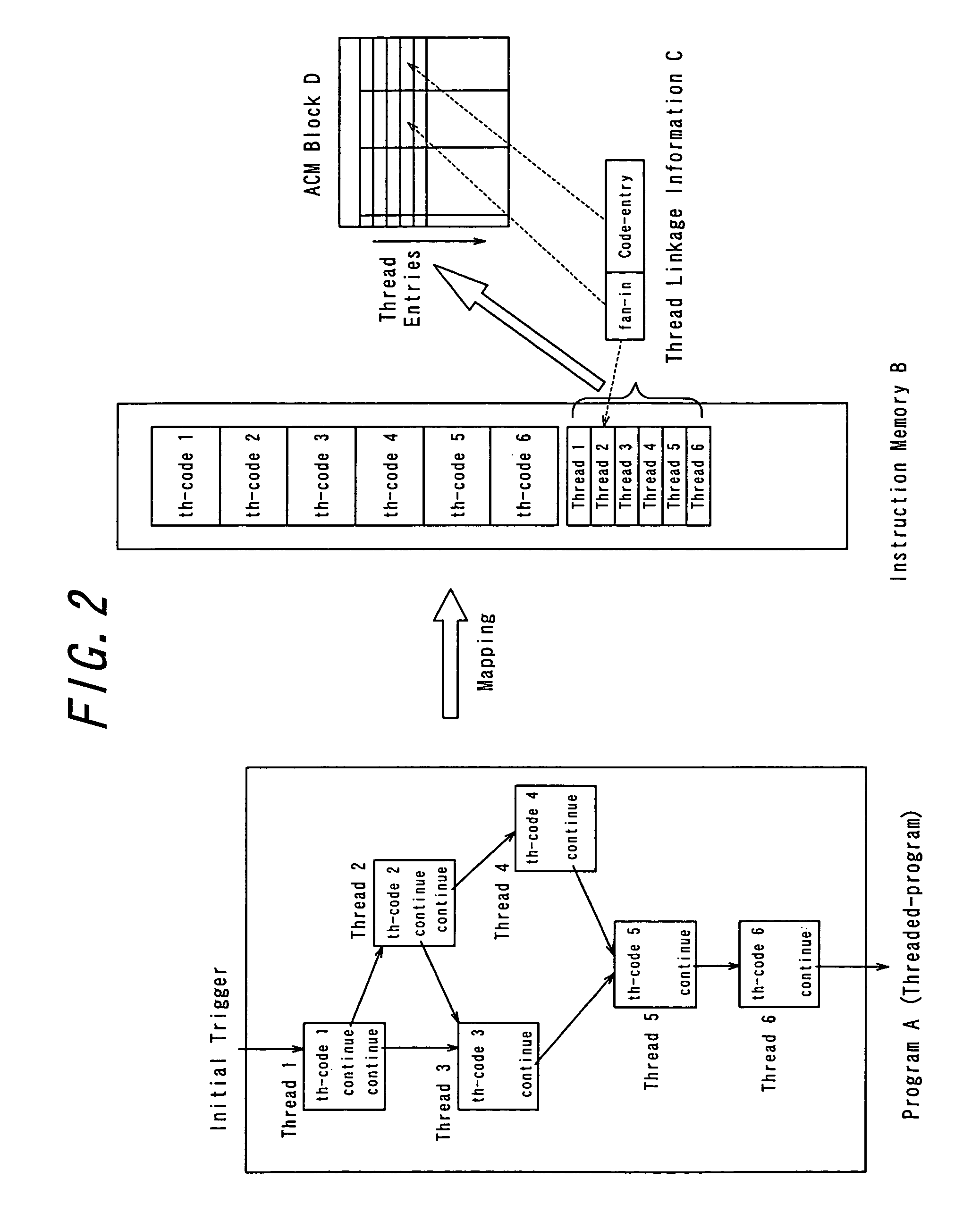
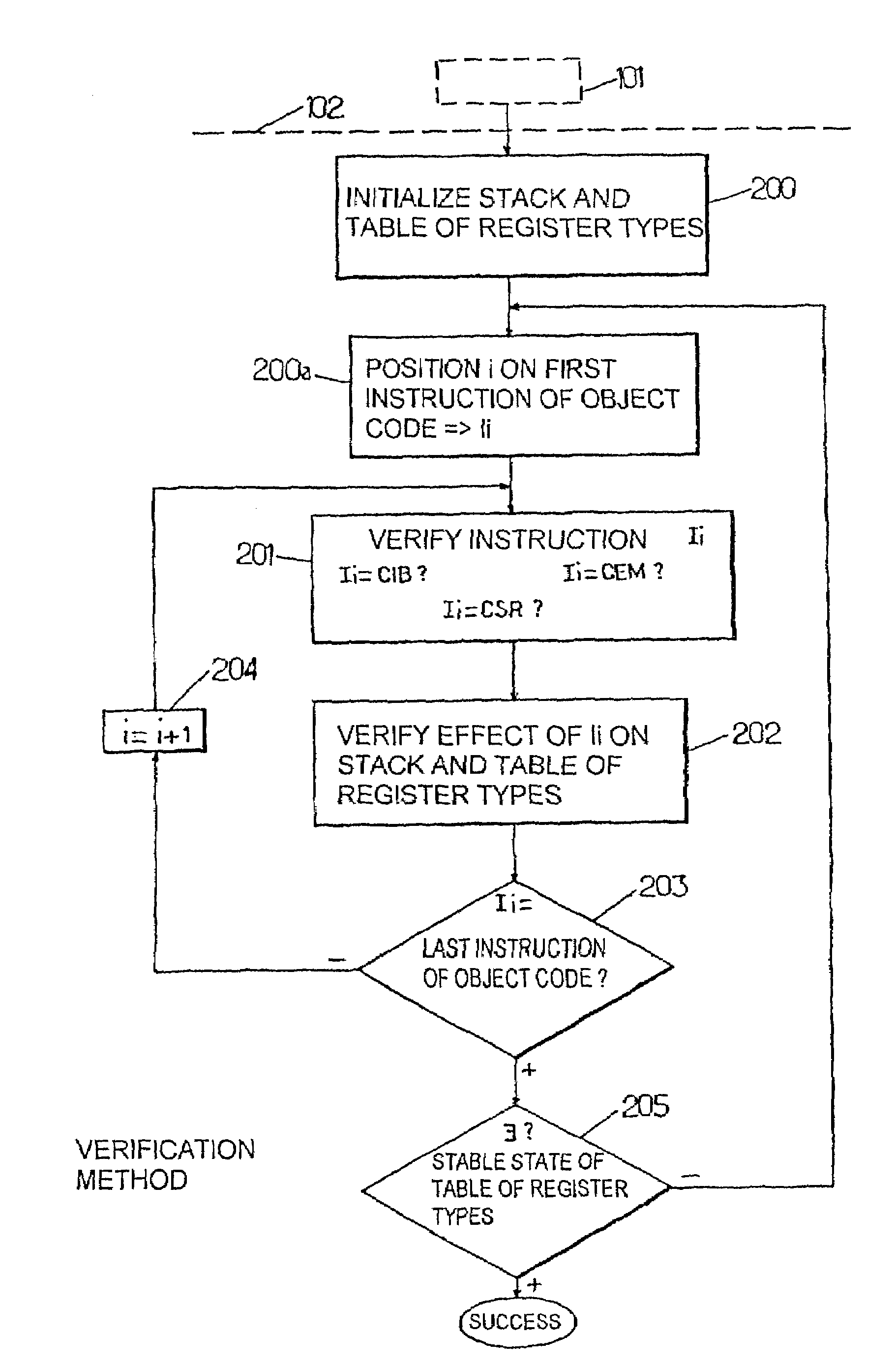
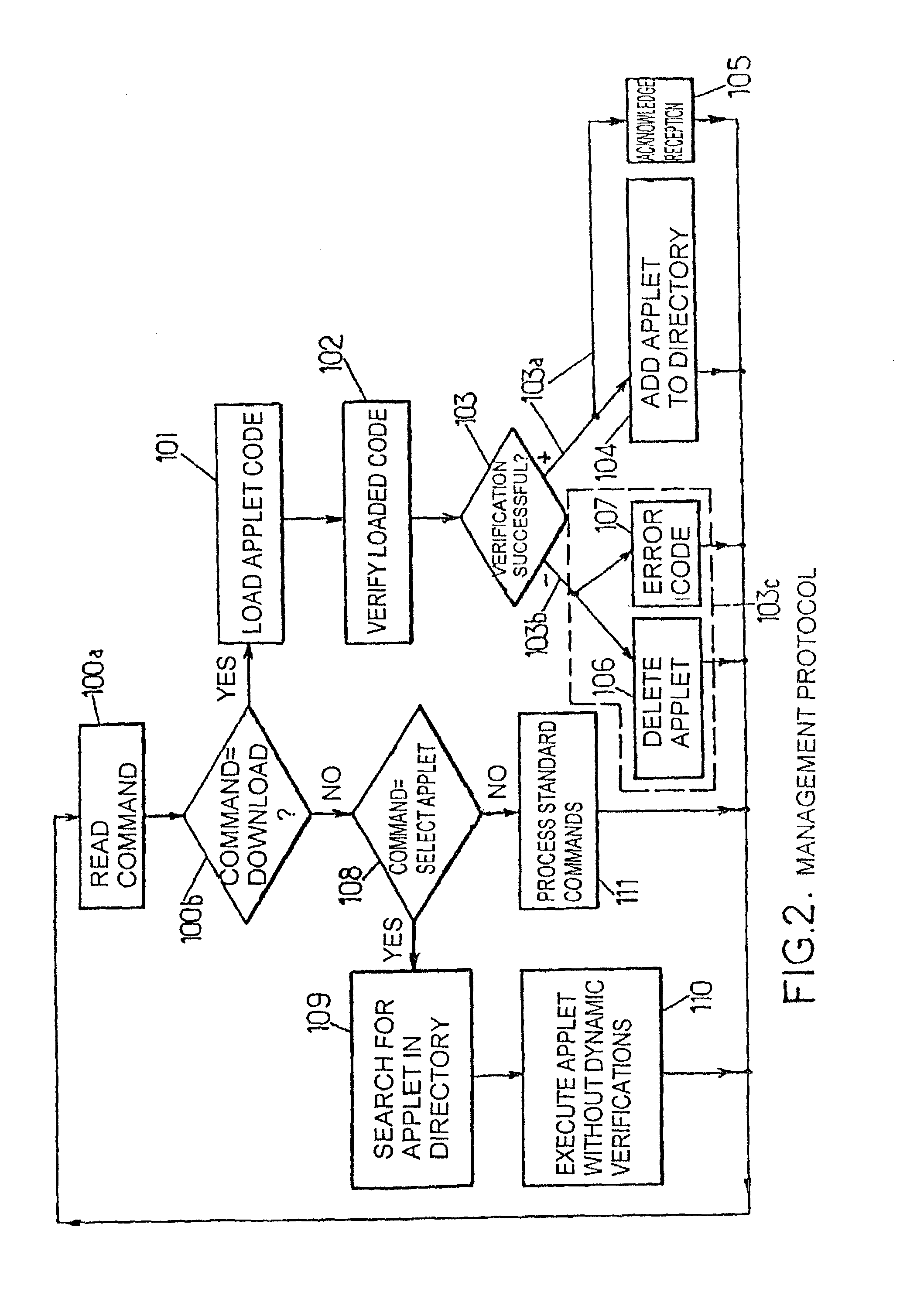
Method for transforming and verifying downloaded program fragments with data type restrictions and corresponding system
A method and system for transforming and verifying downloaded programs fragments with data type restriction in an embedded system in which a program fragment being temporarily stored a verification process of the stored program fragment object code is executed instruction by instruction so as to discriminate for each instruction the existence of a target, a branching instruction target, a target of an exception handler call or a target of a subroutine call. On the occurrence of a target of a branching instruction as the current instruction, the empty status of the stack is verified and the program fragment is rejected otherwise. A verification process and updating of the effect of the current instruction on the data types of the type stack and the table of register types is performed. The verification process is successfully executed instruction by instruction until the table of register types is stable, with no modification being present, and interrupted with the program fragment being rejected otherwise.
Owner:TRUSTED LOGIC
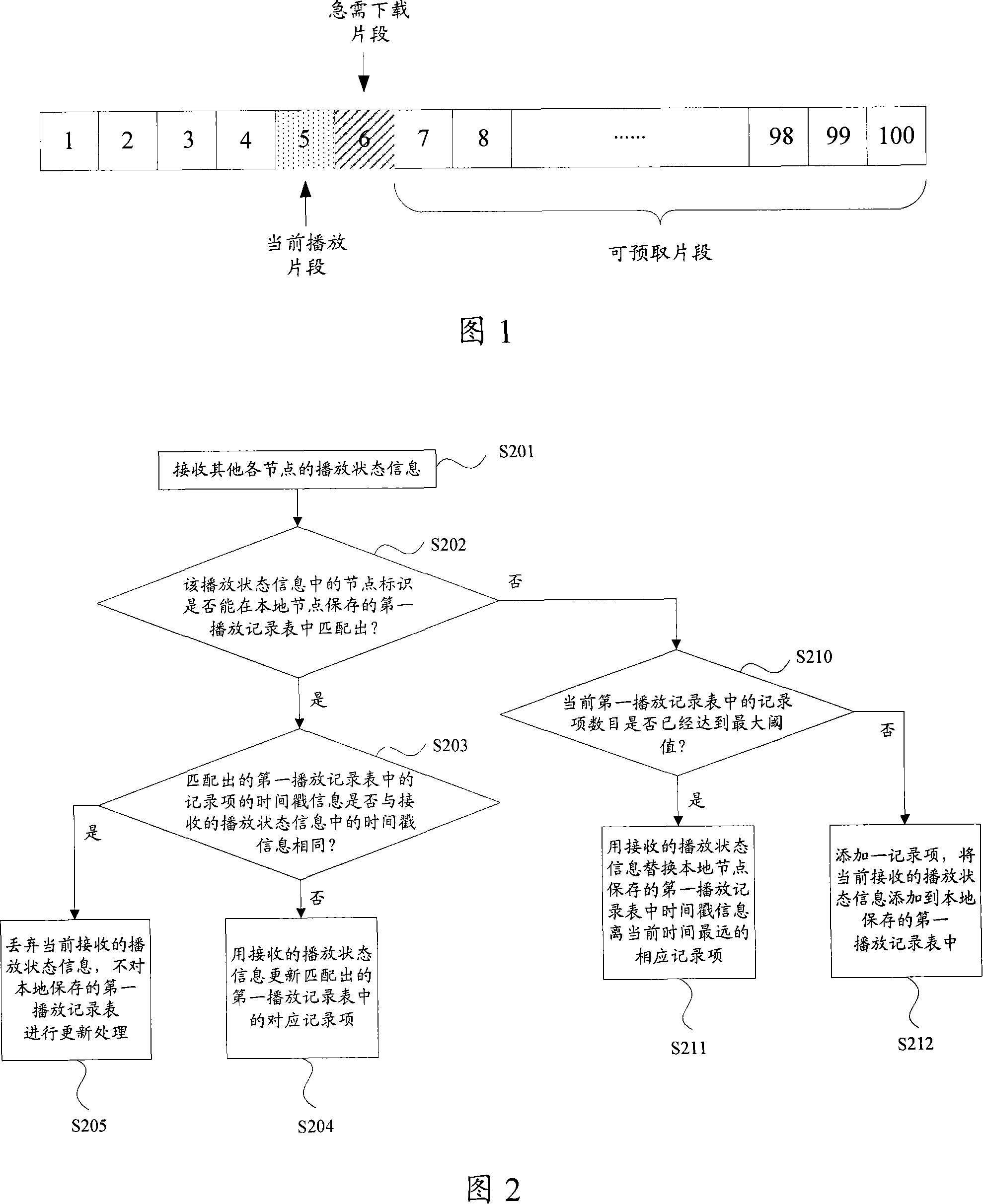
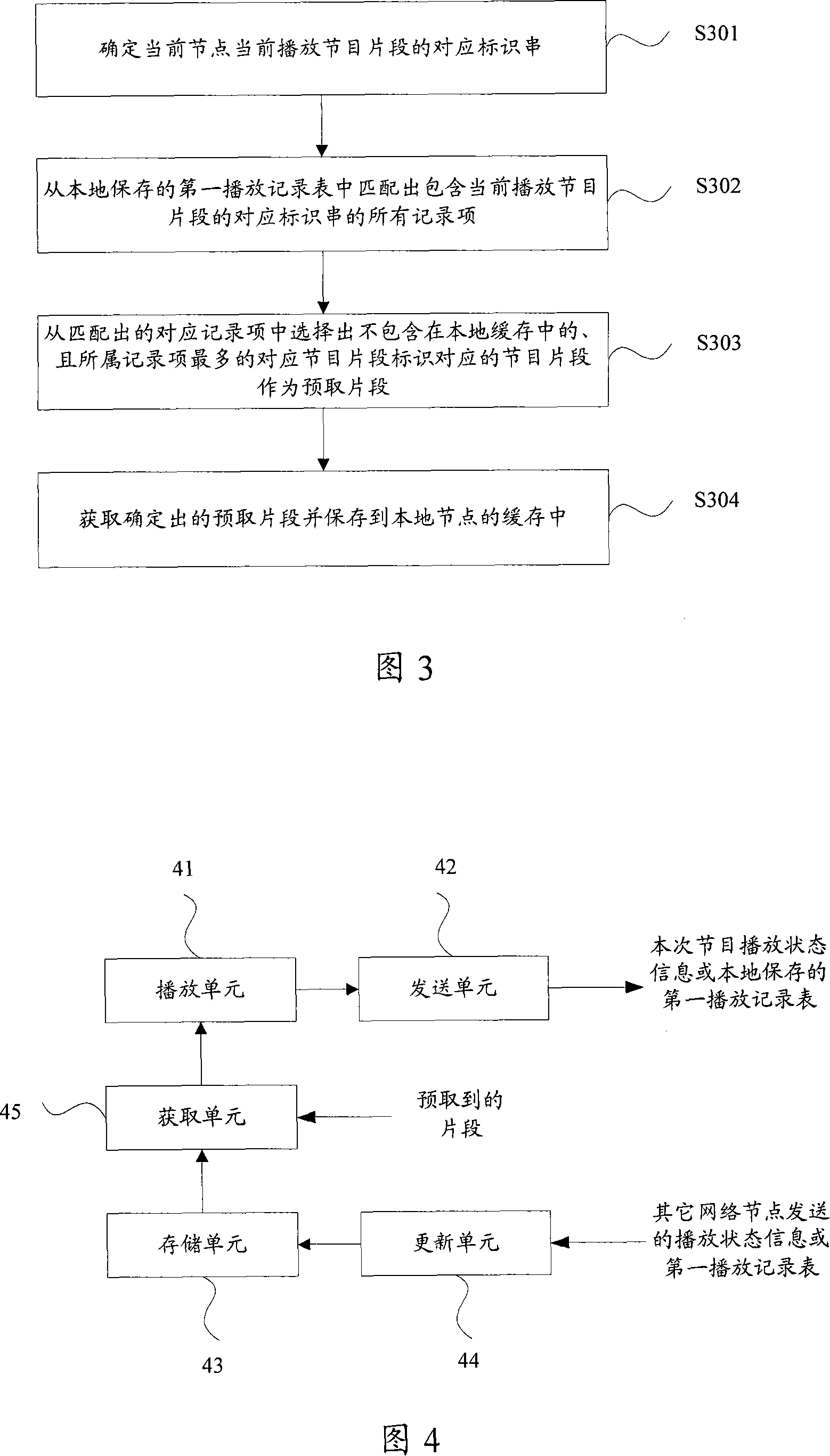
Program fragment prefetching method and peer-to-peer network node
ActiveCN101110844AImprove hit rateShorten the timeTwo-way working systemsTransmissionProgram fragmentDatabase
The present invention discloses a program fragment pre-fetching method, which is applied to the peer-to-peer network. The method comprises that a network node requesting programme searches a first playing record list and / or a second playing record list with the corresponding identification string of the programme fragment currently played by the node as an index, to at least one record item; the programme fragment identification with higher occurrence frequency in the record item and not contained in the local buffer memory of the node is obtained from the at least one record item, and the corresponding programme fragment of the programme fragment identification acts as a pre-fetching fragment and is pre-fetched. Through the proposal provided by the present invention, the hit rate of the pre-fetching fragment can be effectively improved, and therefore the download delay caused by the frequent VCR operations of each node user can be further effectively reduced.
Owner:HUAWEI TECH CO LTD
Systems and methods for software analytics
InactiveCN106537332AError detection/correctionProgram documentationProgram fragmentSoftware analytics
Owner:CHARLES STARK DRAPER LABORATORY
Search Utility Program for Software Developers
ActiveUS20130036129A1Improve programming efficiencySmall sizeDigital data processing detailsReverse engineeringGraphicsControl flow
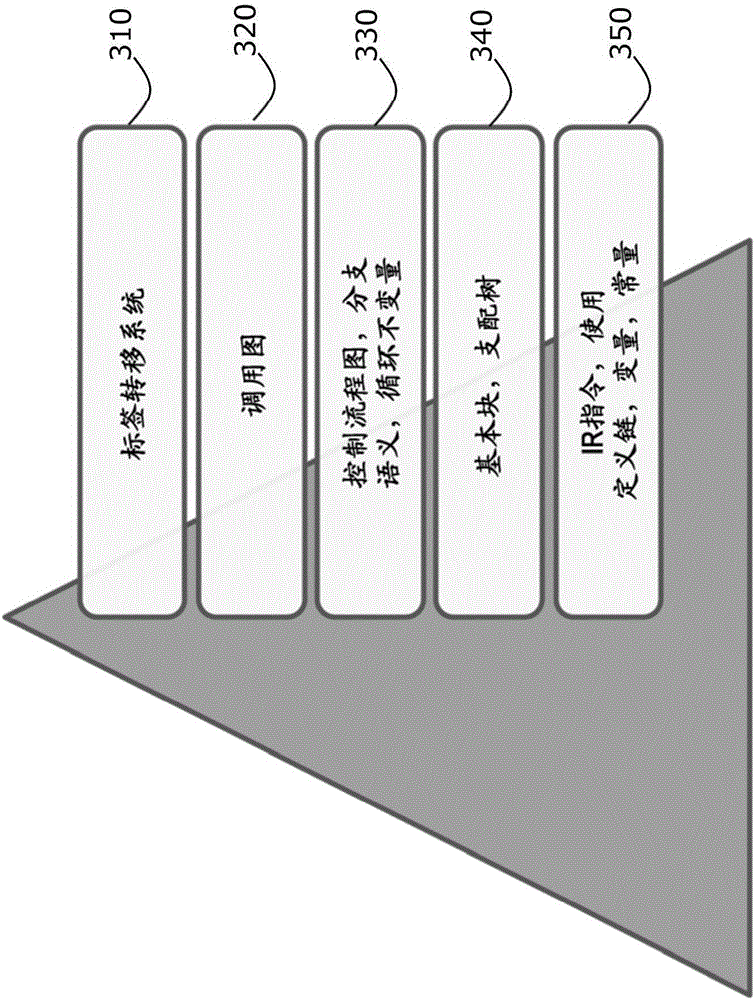
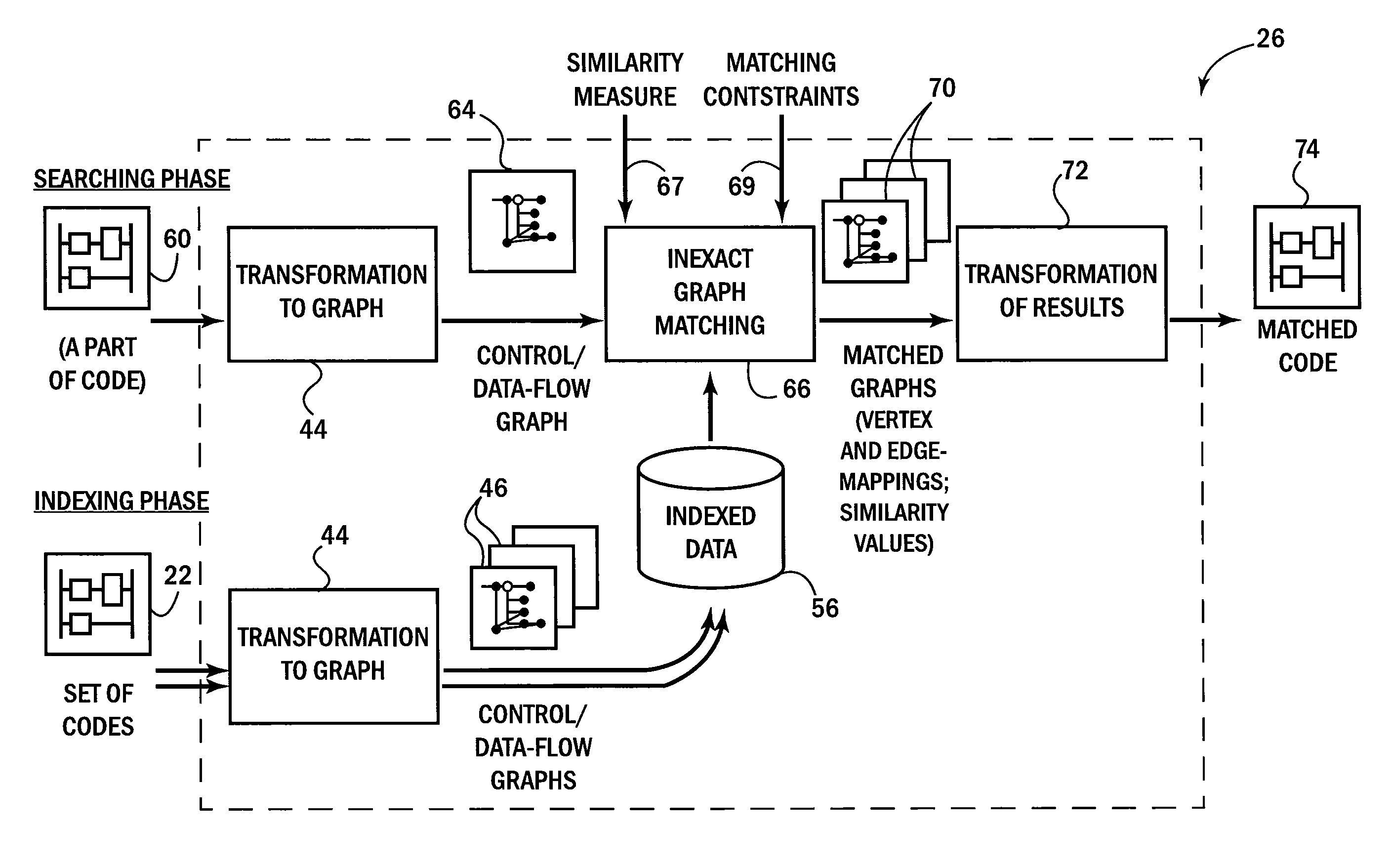
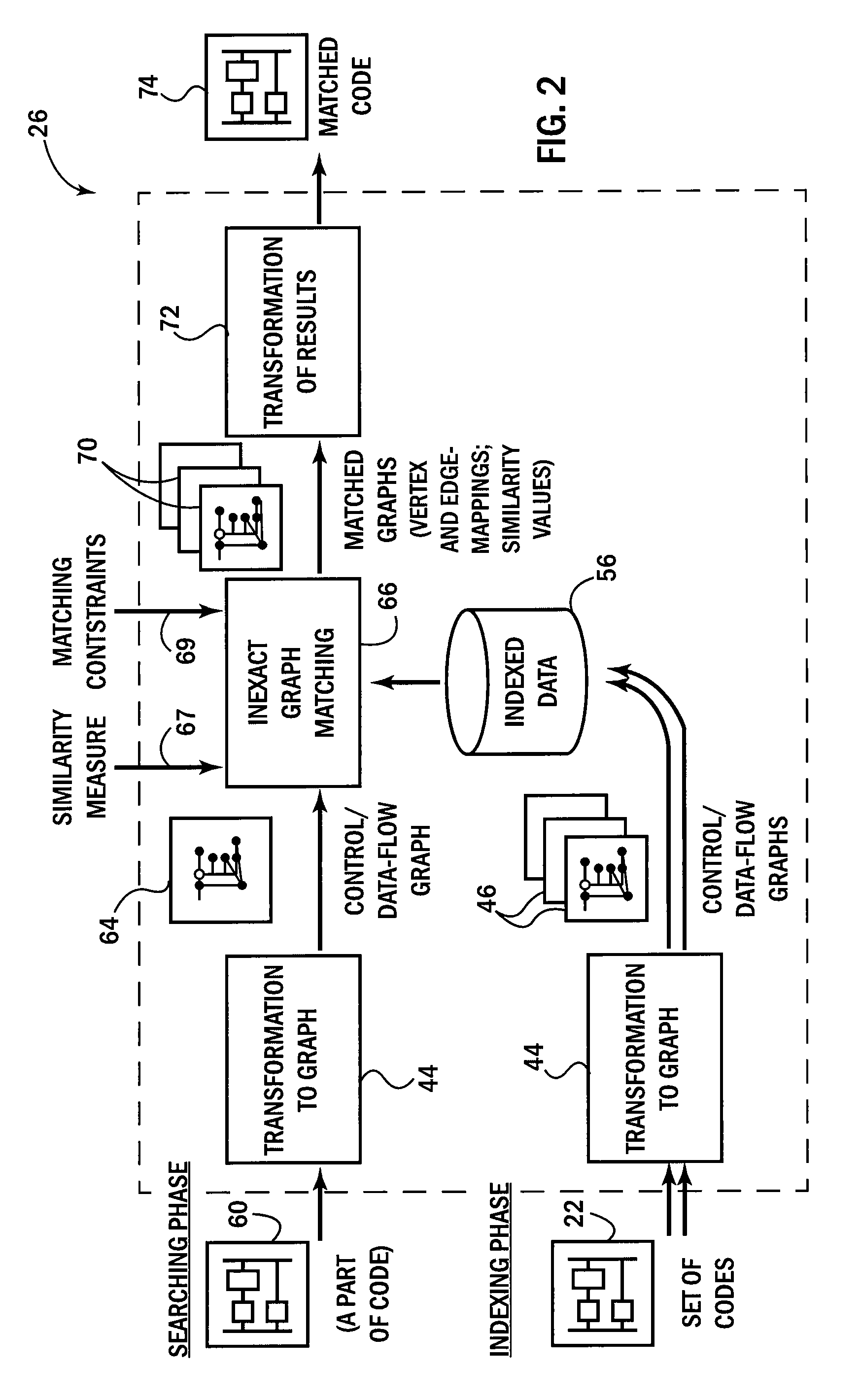
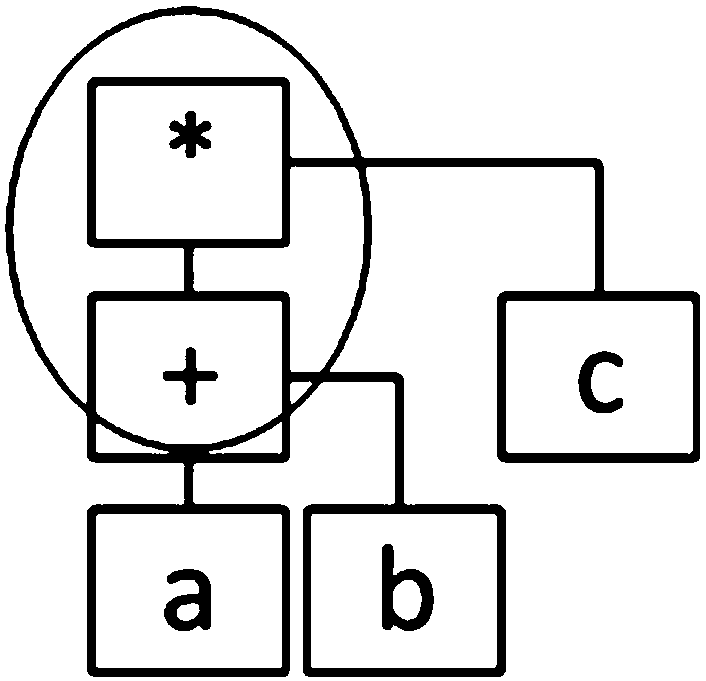
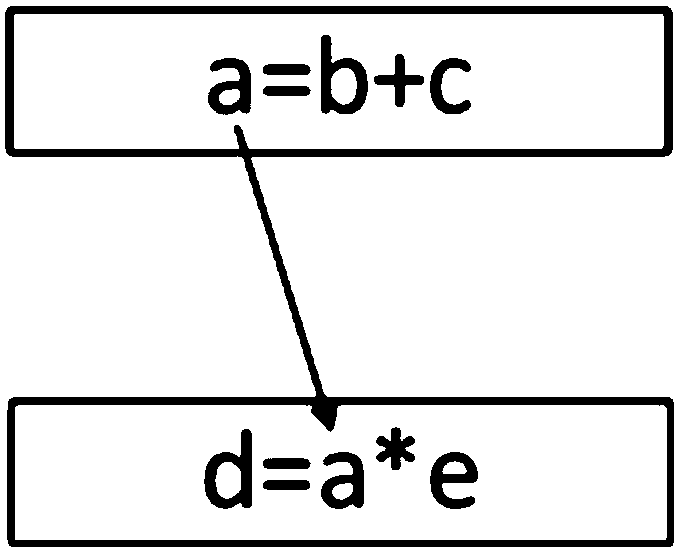
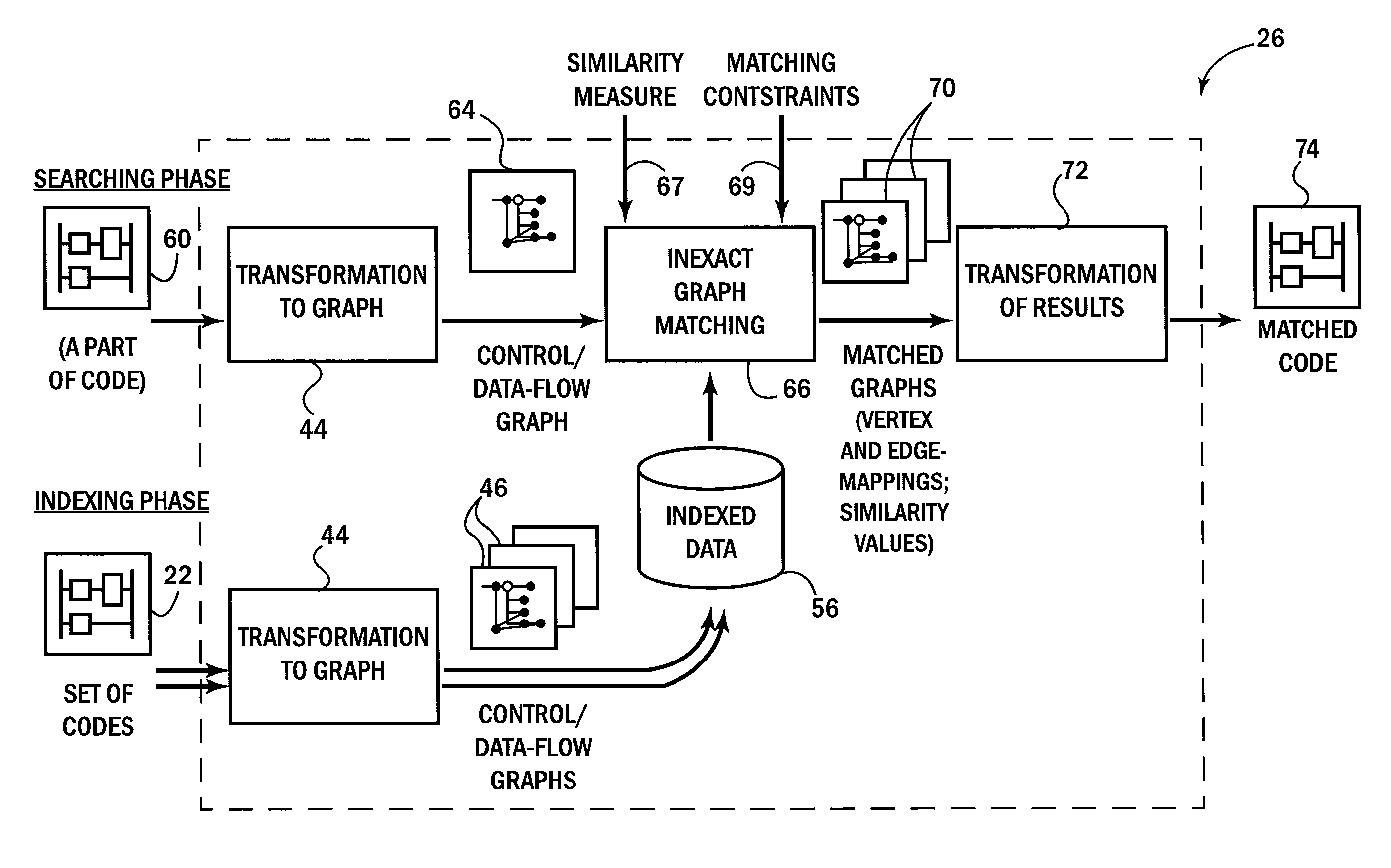
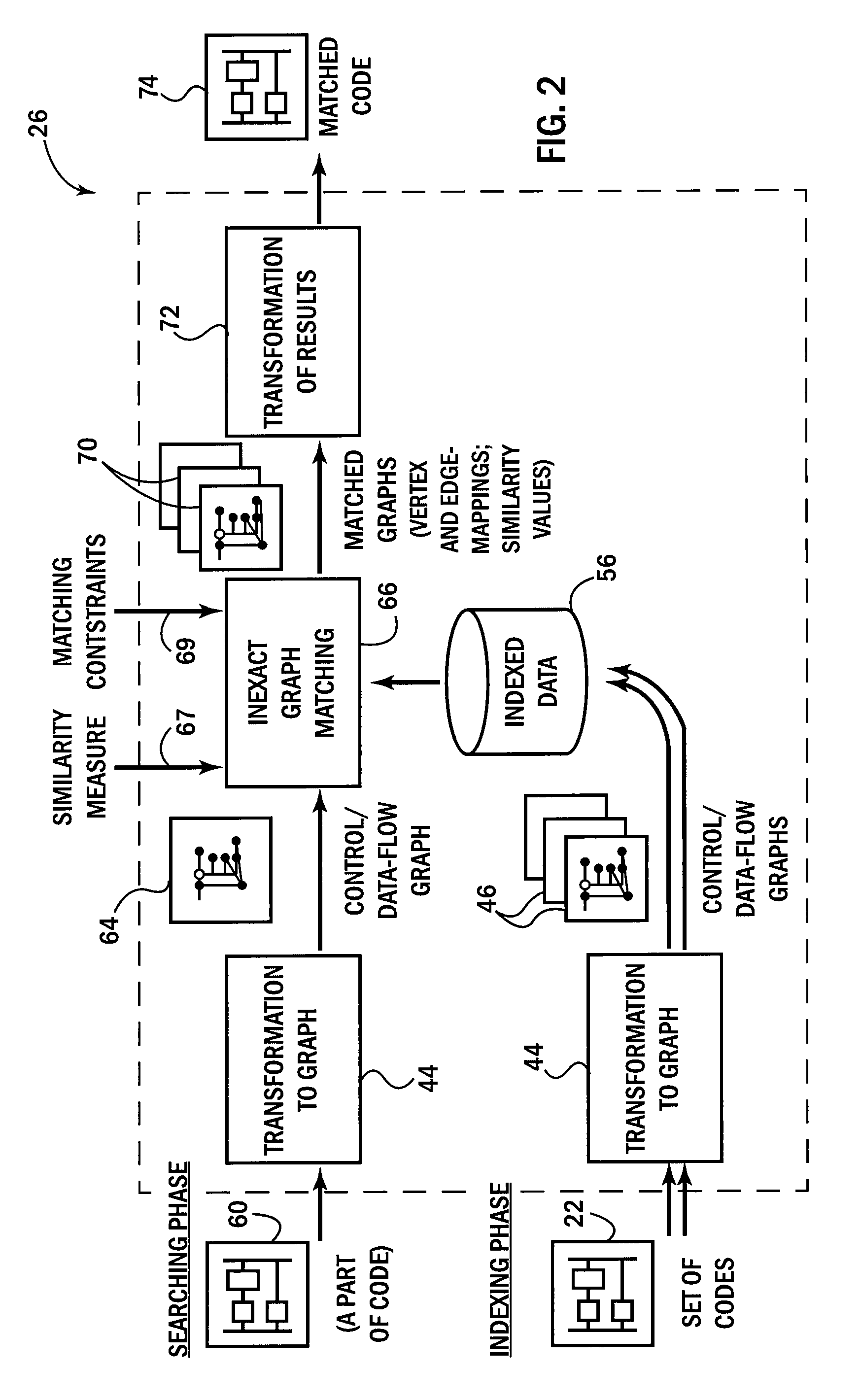
A search utility for industrial control programs accepts as a query an example program fragment which is abstracted into a graph-form capturing, for example, instruction control-flow and data-flow. This graph-form may be compared to a graph-form transformation of other portions of the program to provide a more sophisticated matching process that considers underlying logical hierarchy of the program elements rather than their superficial expression in the source code embodiment
Owner:ROCKWELL AUTOMATION TECH
Method for automatically classifying and grading program competition type source codes according to question answering method
ActiveCN107729925AImprove accuracyCharacter and pattern recognitionSoftware testing/debuggingFeature setProgram fragment
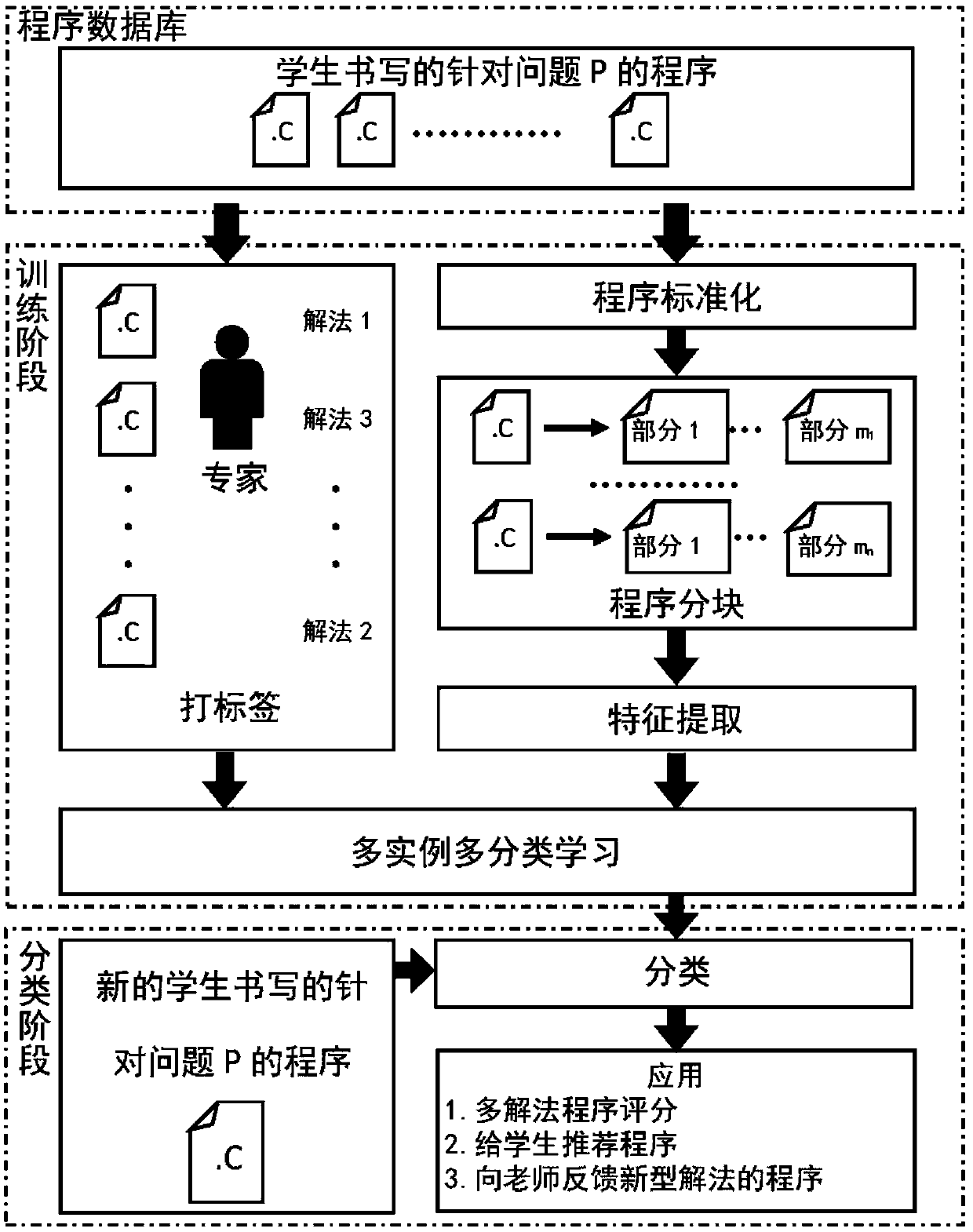
The invention discloses a method for automatically classifying and grading program competition type source codes according to a question answering method. The method comprises the steps of obtaining astandardized program by conducting program conversion on each program aiming at the problem P in the database on an abstract syntax tree, extracting features standardized programs or program fragments, obtaining all feature sets, carrying out multi-instance multi-classification learning on the basis of all the extracted feature sets, obtaining a classification model, and automatically classifyingand grading the newly input programs aiming at the problem P by using the classification model. According to the method, classification and grading can be accurately realized according to the programsource codes by a problem solving method.
Owner:UNIV OF SCI & TECH OF CHINA
Method for removing fragment in record program
ActiveCN101207758AAvoid operabilityAvoid efficiencyTelevision system detailsElectronic editing digitised analogue information signalsUser needsProgram fragment
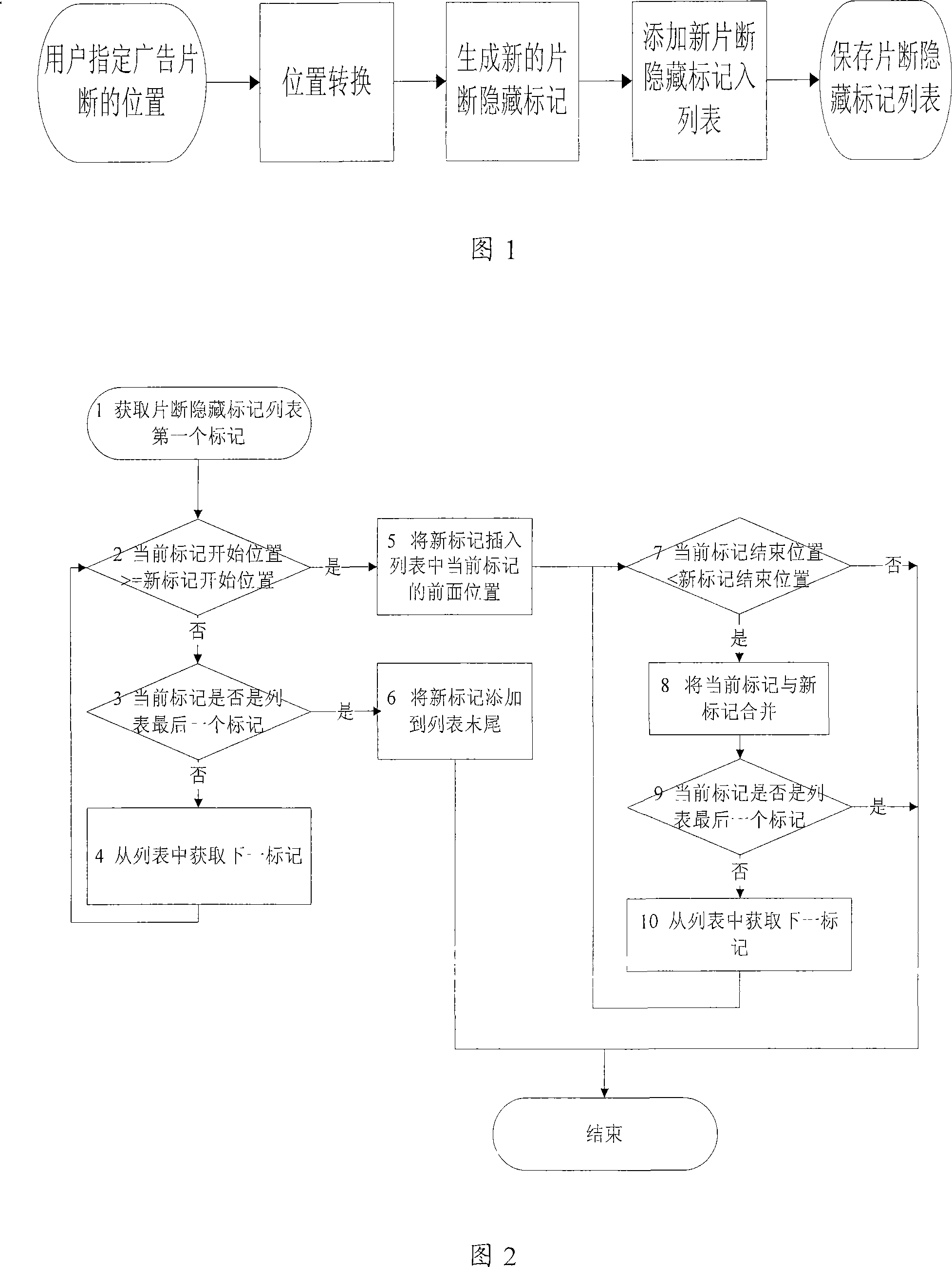
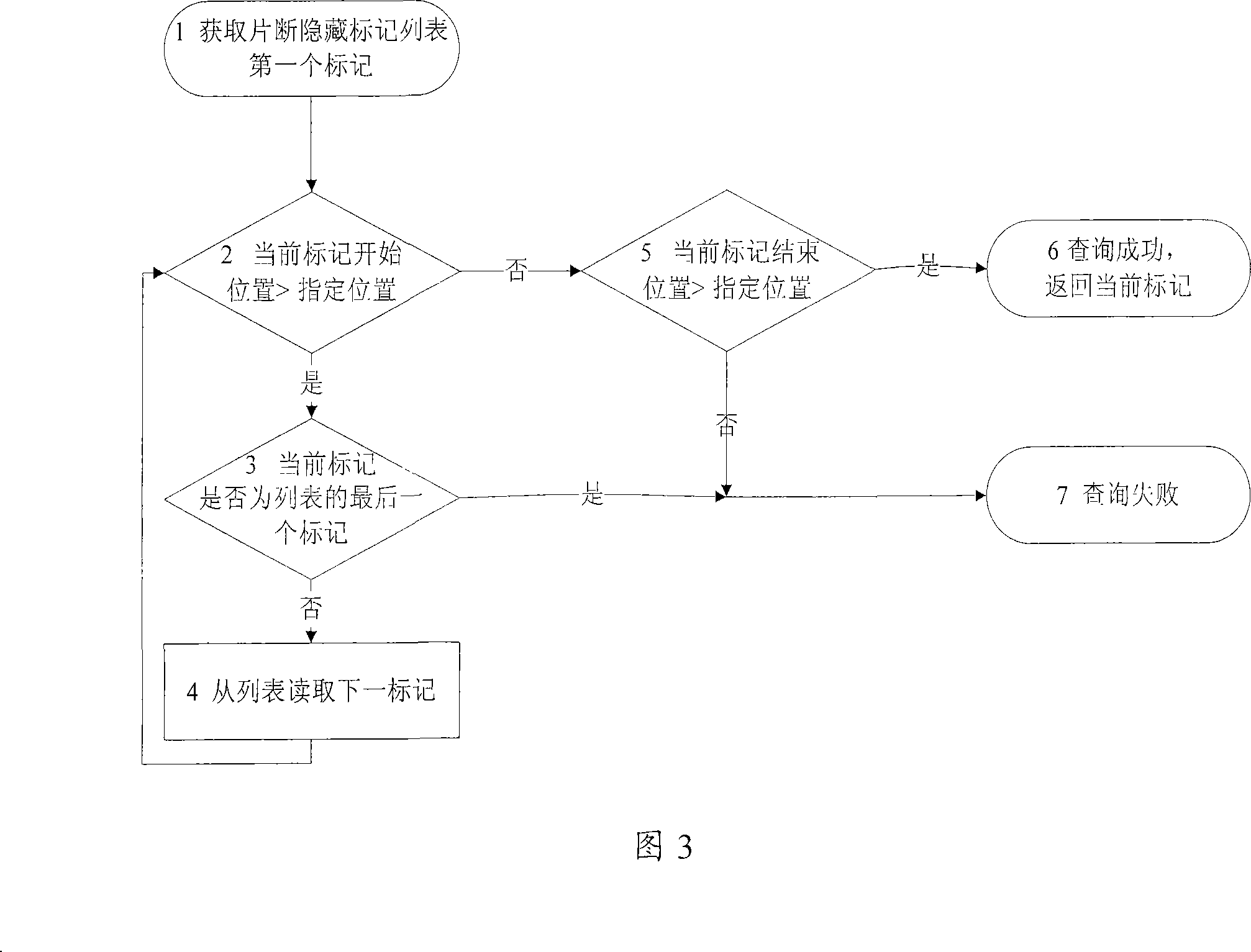
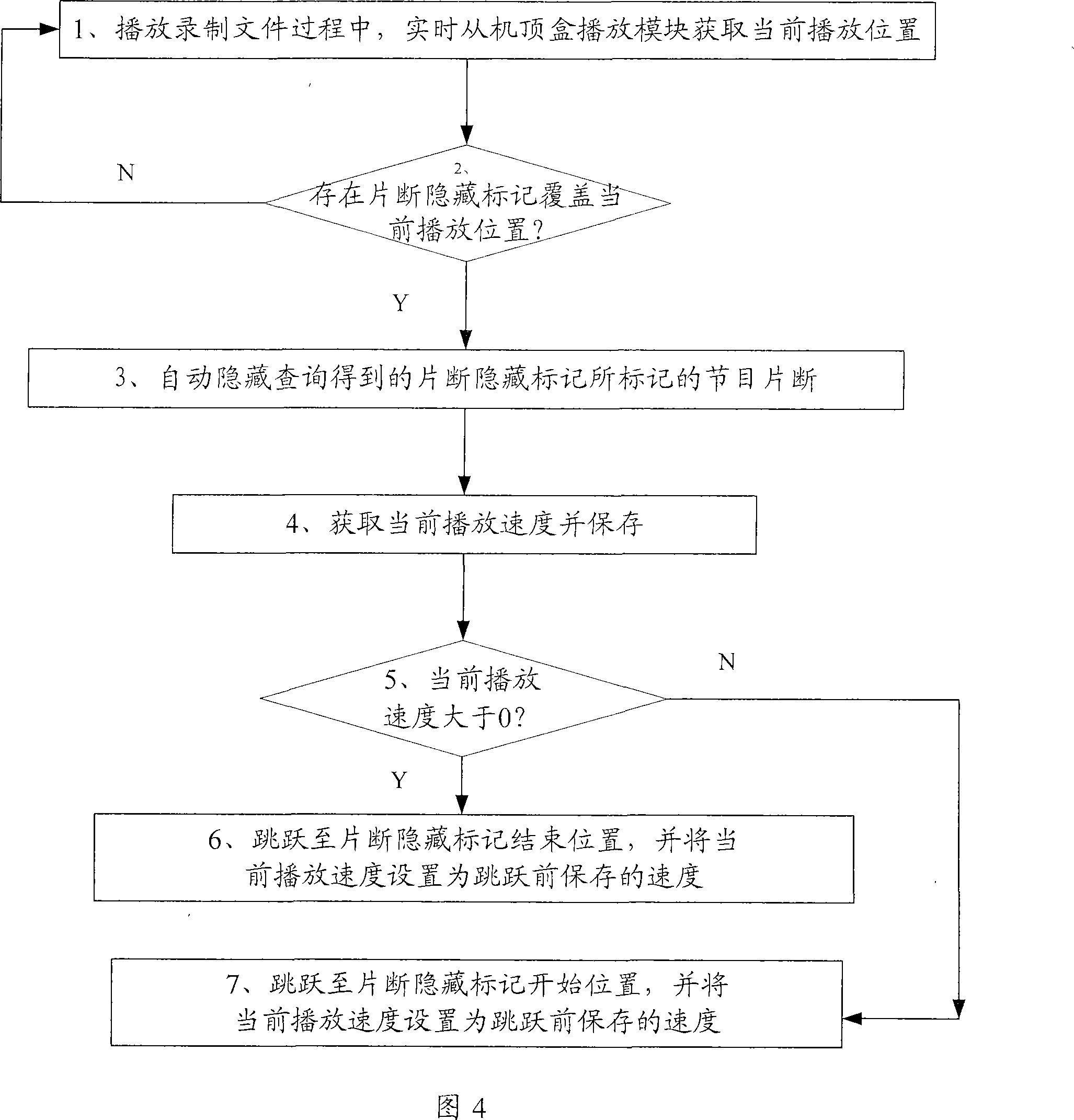
The invention provides a method used for cutting fragments in a recorded program, comprising the following steps: a. when in the process of recording program, at least one program fragment that needs to be cut is marked to be hidden, a program fragment hidden marker list is generated according to the program fragment hidden marker so that the plurality of program fragment hidden markers are not overlapped in the marking range; and b. when the recorded program is played, the program fragment that needs to be cut is skipped according to the program fragment hidden marker. The technical proposal provided by the invention can facilitate the user to quickly cut the needless fragments in the recorded program according to the need, thereby avoiding the problem of complex operation and over low efficiency when a document cutting method is adopted to delete and recombine the recorded program, and better satisfying the demand of the user.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
Method and terminal for repeatedly playing program
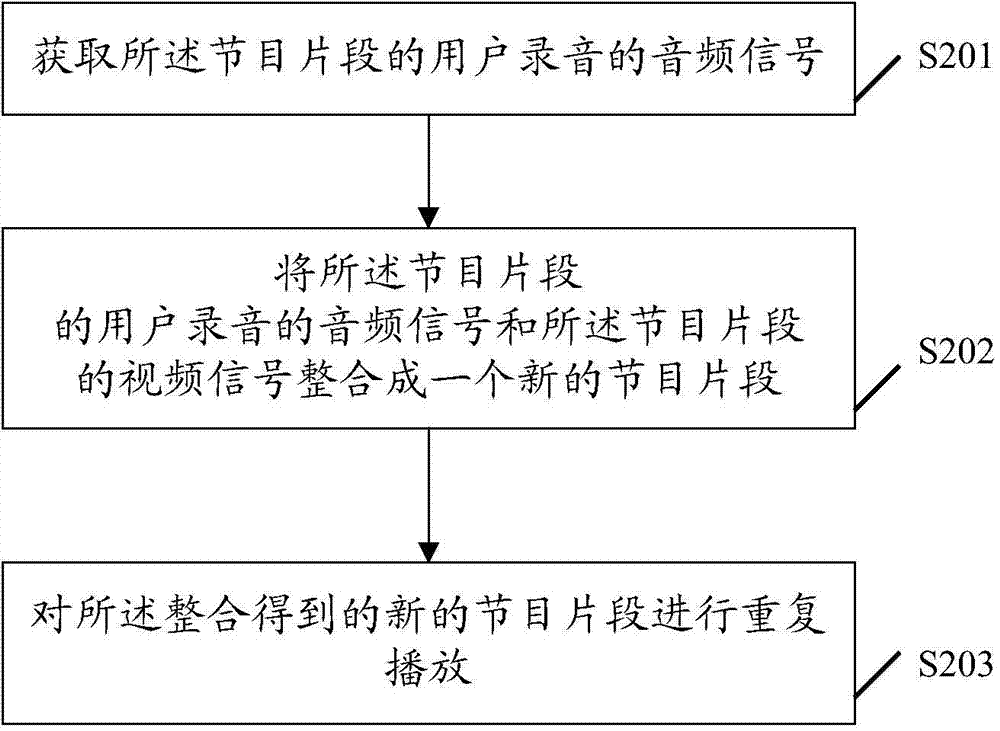
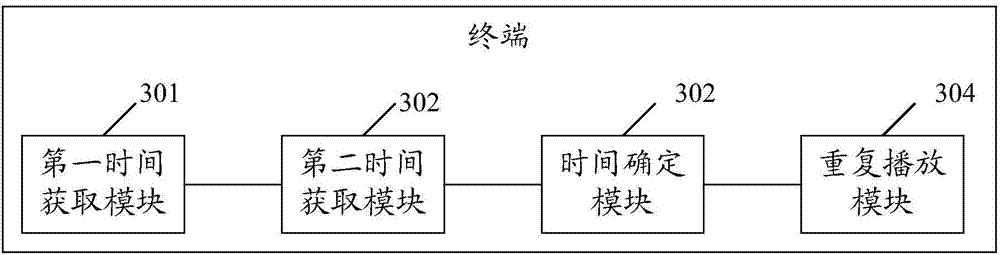
ActiveCN103905925APrecise positioningRapid positioningSelective content distributionStart timeProgram fragment
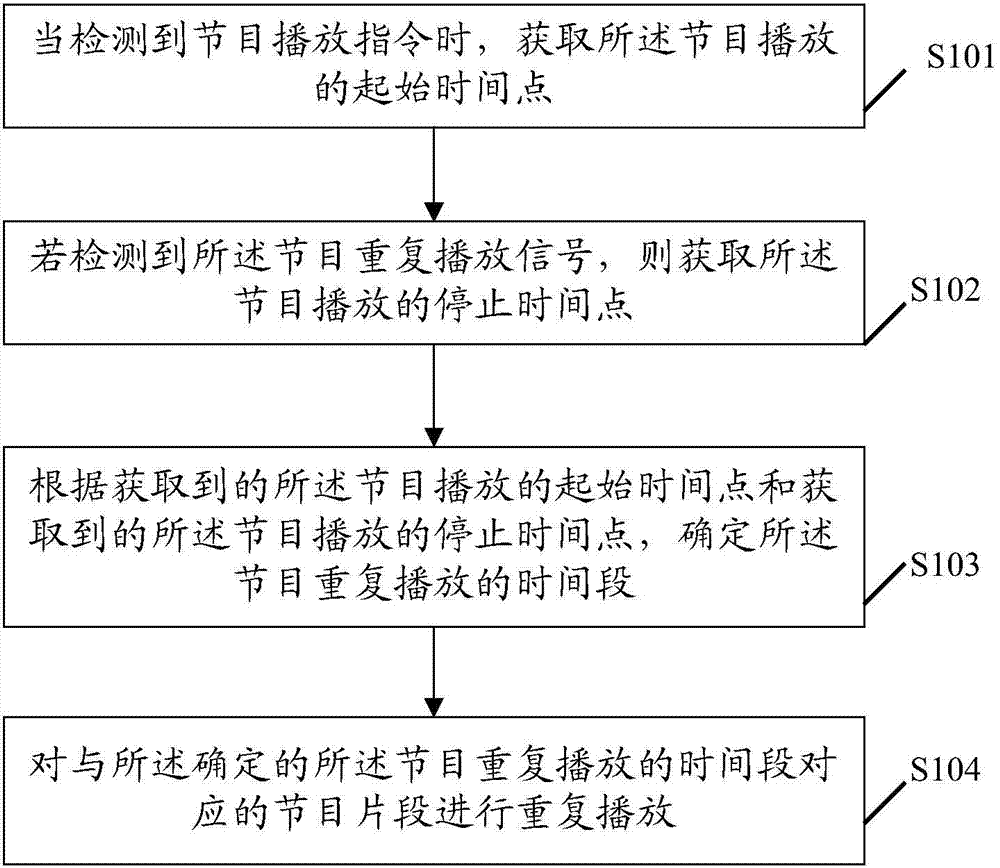
The embodiment of the invention discloses a method for repeatedly playing a program. The method comprises the steps that when a program playing instruction is detected, the program playing starting time point is acquired; if a program repeatedly-playing signal is detected, the program playing stopping time point is acquired; the time period when the program needs to be played repeatedly is determined according to the acquired program playing starting time point and the acquired program playing stopping time point; a program fragment corresponding to the time period when the program needs to be repeatedly played is played repeatedly. The embodiment of the invention further discloses a terminal for repeatedly playing the program. By means of the method and terminal, the program fragment needing to be repeatedly played can be positioned conveniently and quickly, and the using experience of a user is improved.
Owner:SHENZHEN SKYWORTH DIGITAL TECH CO LTD +1
Manufacture method of video karaoke and VOD system thereof
InactiveCN101521742ATelevision system detailsElectrophonic musical instrumentsProgram fragmentComputer science
The invention provides a manufacture method of video karaoke (PTV in short) and a VOD system thereof, belonging to the technical field of video and audio. The method can utilize the prior technologies and equipment to manufacture PTV video sources and the relative VOD system to form a PTV database, can manufacture various film fragments, cartoon fragments, artistic program fragments, classical commercial films, network short plays and song PTV and enables performers to dub and play in the background of music with original sound effect so as to truly simulate the environment of a film. PTV is a new rising show business, enables performers to imitate and play rolls in film and TV works, is similar to KTV and has higher unique values in entertainment, interaction and commerciality than the traditional KTV.
Owner:史强
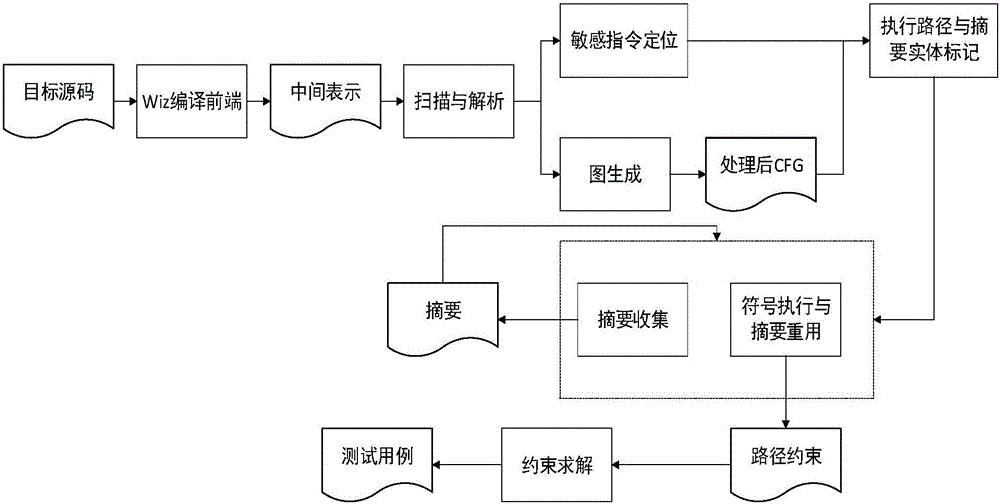
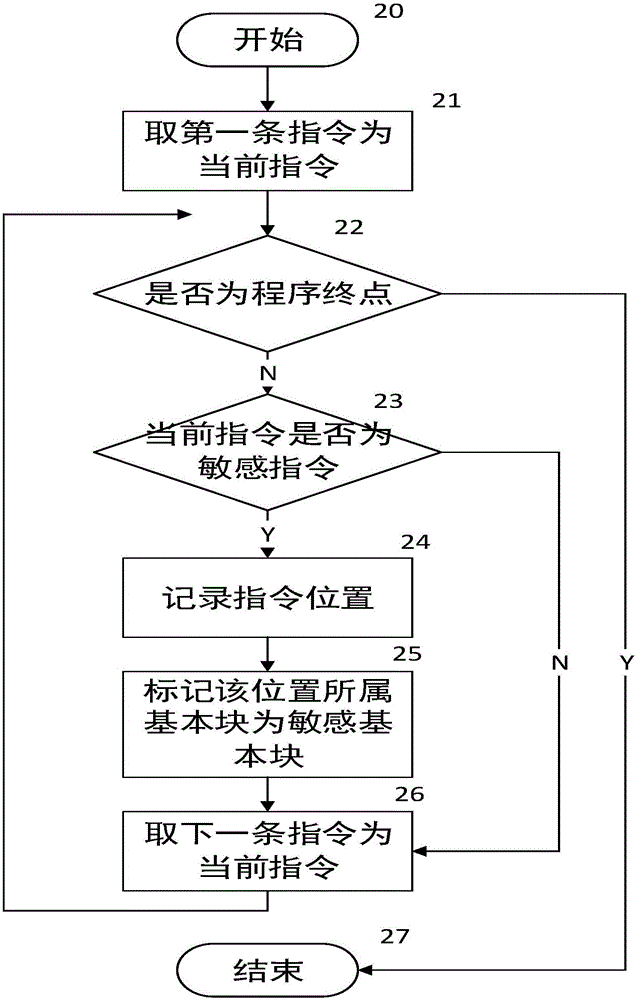
Bootable symbolic execution vulnerability detection method based on path combination
ActiveCN106599695AReduce the number of explorationsImprove execution efficiencySoftware testing/debuggingPlatform integrity maintainanceProgram segmentAbstract program
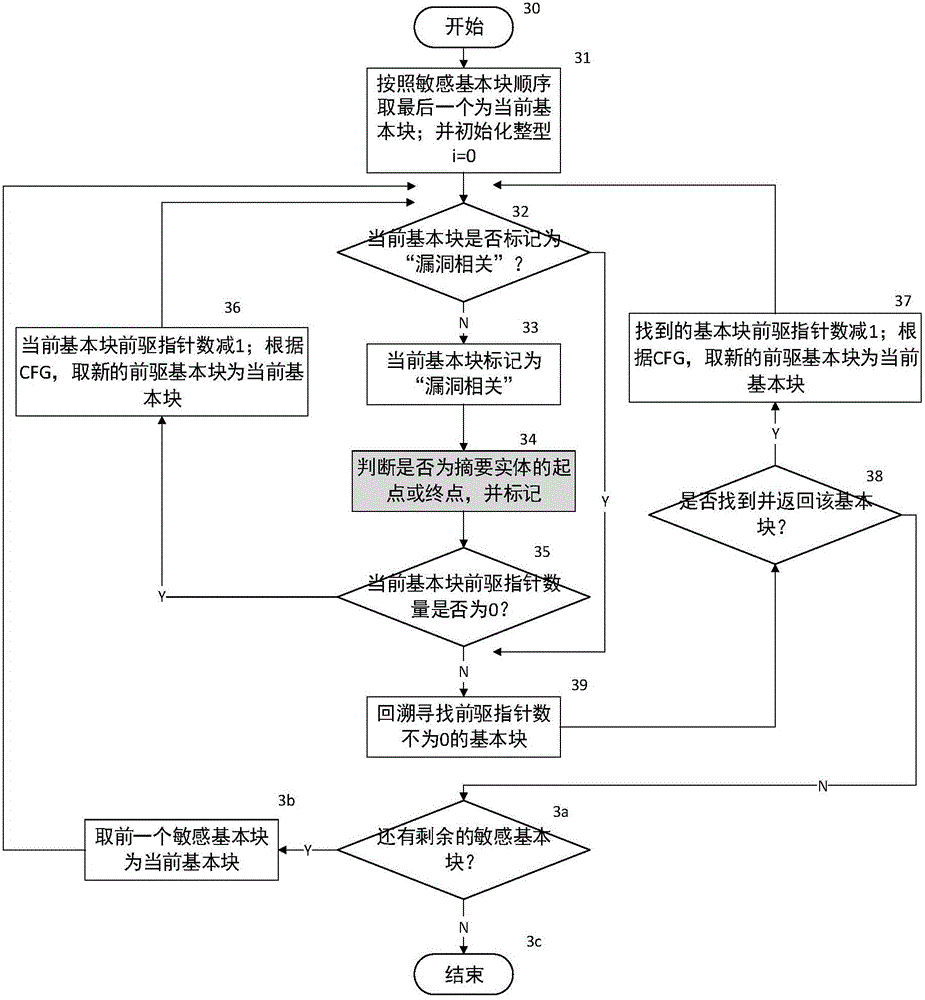
The invention provides a bootable symbolic execution vulnerability detection method based on path combination. The bootable symbolic execution vulnerability detection method based on path combination comprises the following steps: a, scanning and analyzing a target program to acquire a program control stream related to vulnerability, and marking a path combination range; b, in a symbolic execution process, carrying out abstract collection on the marked range according to information of the acquired program control stream; and c, in the symbolic execution process, directly reusing an abstract when meeting an abstracted program segment to eliminate redundancy exploration, and cutting off program paths unrelated to the vulnerability. The bootable symbolic execution vulnerability detection method has the beneficial effects that the bootable symbolic execution vulnerability detection method based on path combination can eliminate exploration of redundant paths, so that the symbolic execution efficiency and the vulnerability detection precision are improved, and more precise and efficient vulnerability detection is realized.
Owner:NANJING UNIV
Circuits and methods for mobility of effectful program fragments
InactiveUS20090265688A1Efficient collaborationProgram loading/initiatingExecution paradigmsProgram fragmentTheoretical computer science
Methods for mobility of effectful program fragments including a method for serializing and deserializing effectful program fragments, and a method for utilizing a program fragment in a type-directed way.
Owner:GOVEREAU PAUL +2
Method and device for transferring media files
ActiveCN102904907AReduce interruptionsImprove quality of experienceTransmissionProgram fragmentMedia server
An embodiment of the invention discloses a method and a device for transferring media files. The method includes acquiring a code rate upper limit of a next program period according to transmission history of a media data network, a current program period, a starting moment of the next program period and a finishing moment of the next program period when loading of media data of the current program period is completed; selecting a program fragment of the next program period from a media server according to the code rate upper limit of the next program period; and receiving the selected program fragment of the next program period.
Owner:重庆明航文化传媒有限公司
Two-step cluster software load feature extraction method based on SOM and K-means
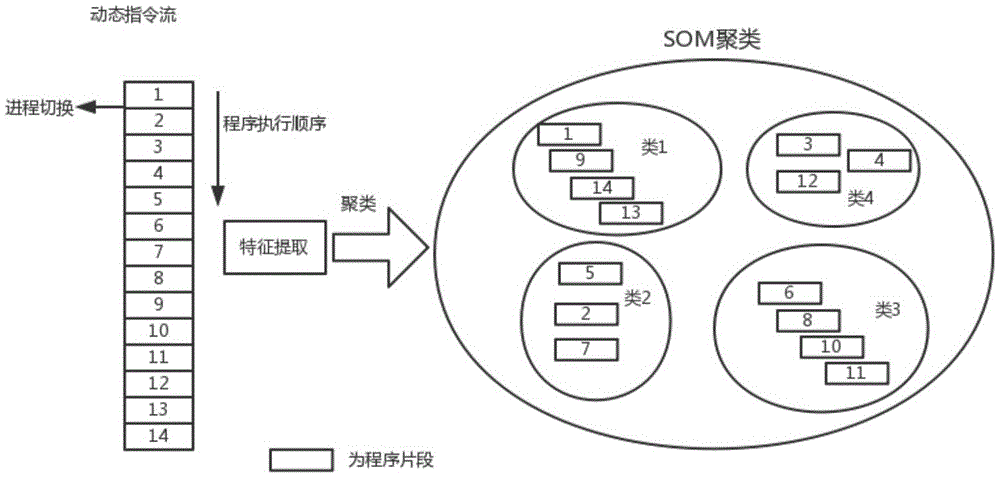
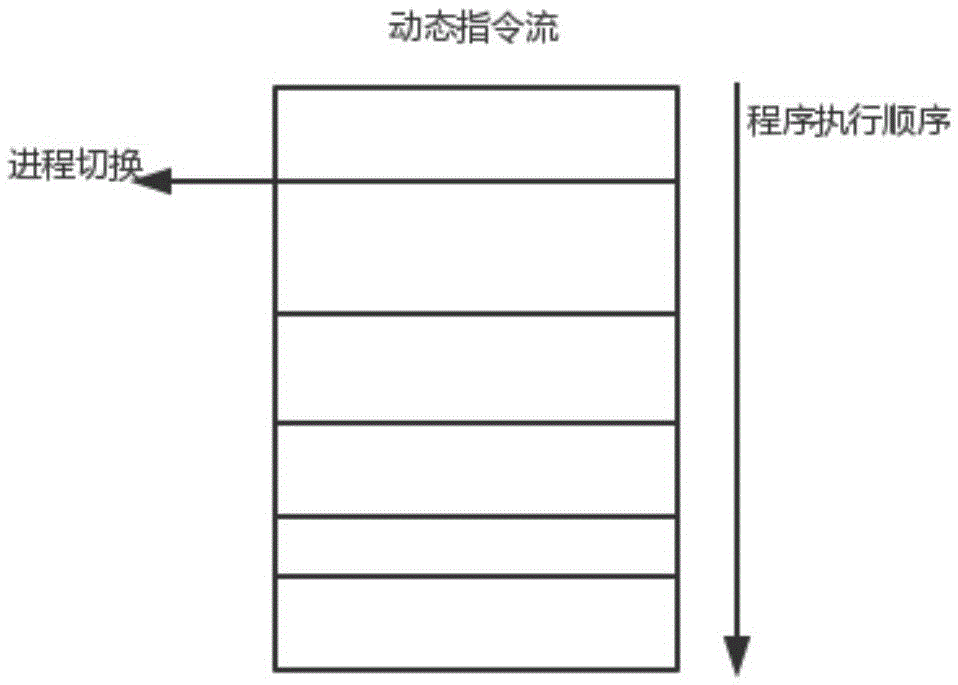
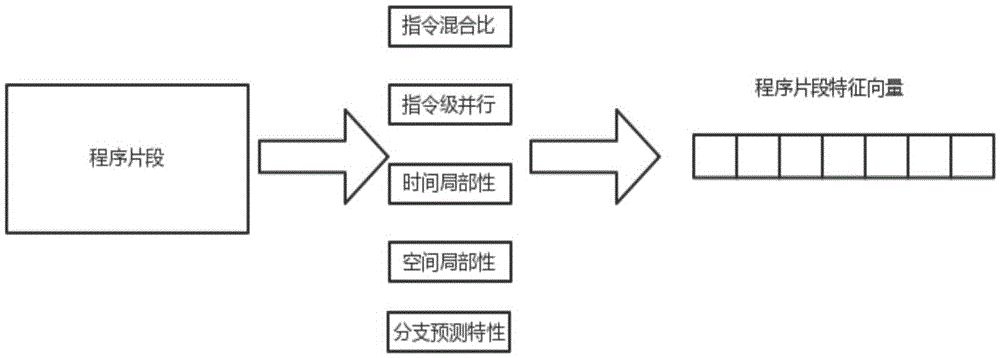
ActiveCN105654120AEffectively describe essential differencesMake up for being too sensitive to the initial pointHardware monitoringCharacter and pattern recognitionLocal optimumCluster algorithm
The invention discloses a two-step cluster software load feature extraction method based on SOM and K-means. The method comprises the following steps that (1) load features are extracted from a dynamic instruction stream in the software performing process: firstly the software performing process is divided into multiple fragments, then statistics of the feature parameters of each program fragment is performed, and each software outputs multiple sets of feature parameters so as to form a matrix formed by the multi-dimensional feature parameters; (2) typical program fragments are extracted from the feature parameter matrix: feature fragment clusters with different software load features are found from multiple program fragments by utilizing an SOM clustering algorithm, and then the fragment capable of most representing the features of the cluster is found from the feature fragment clusters of the same type by utilizing a K-means clustering algorithm. According to the method, the defects that SOM convergence time is excessively long and the K-means algorithm is excessively sensitive to an initial point and liable to fall into the locally optimal solution can be compensated simultaneously.
Owner:RES INST OF SOUTHEAST UNIV IN SUZHOU
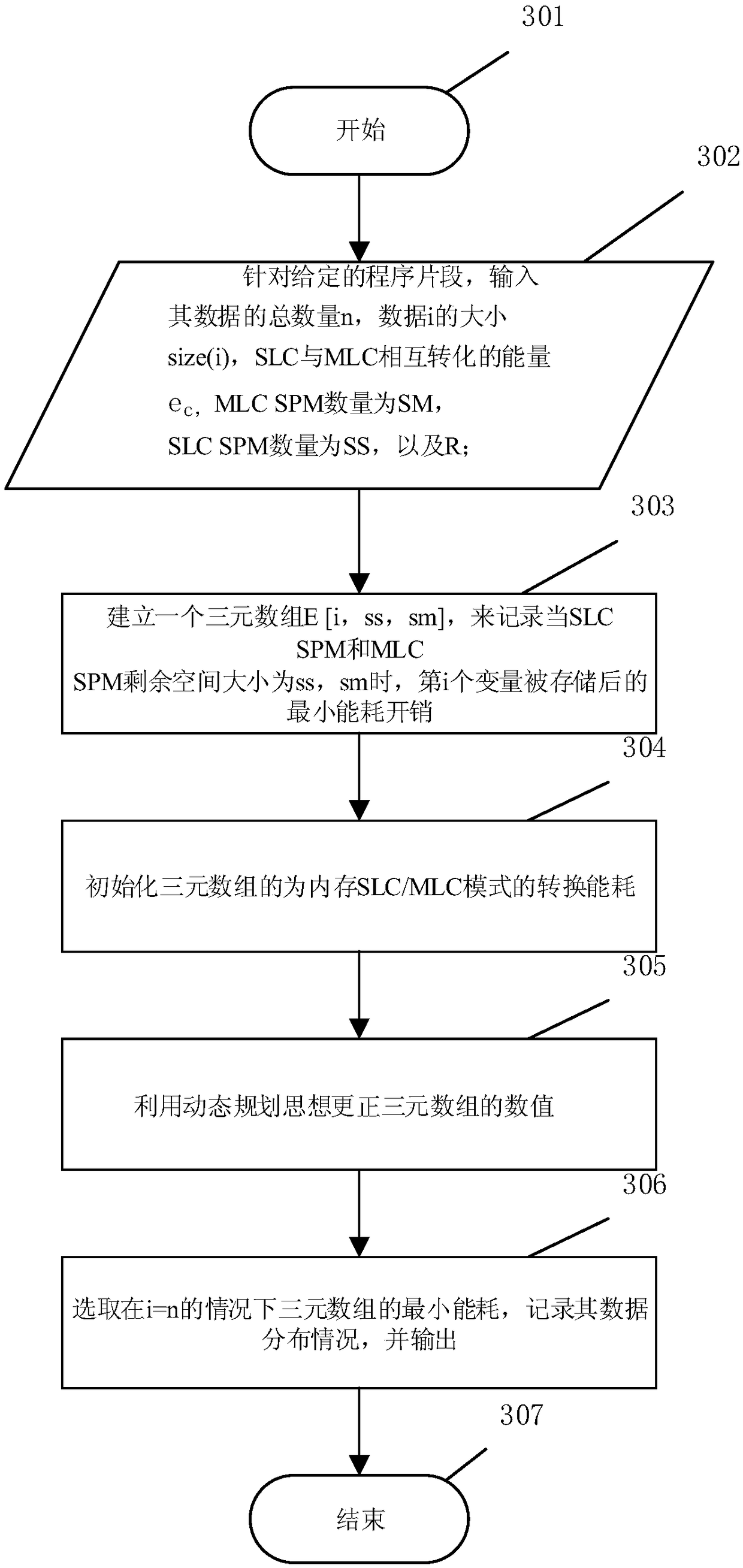
A data distribution optimization method based on a variable note memory
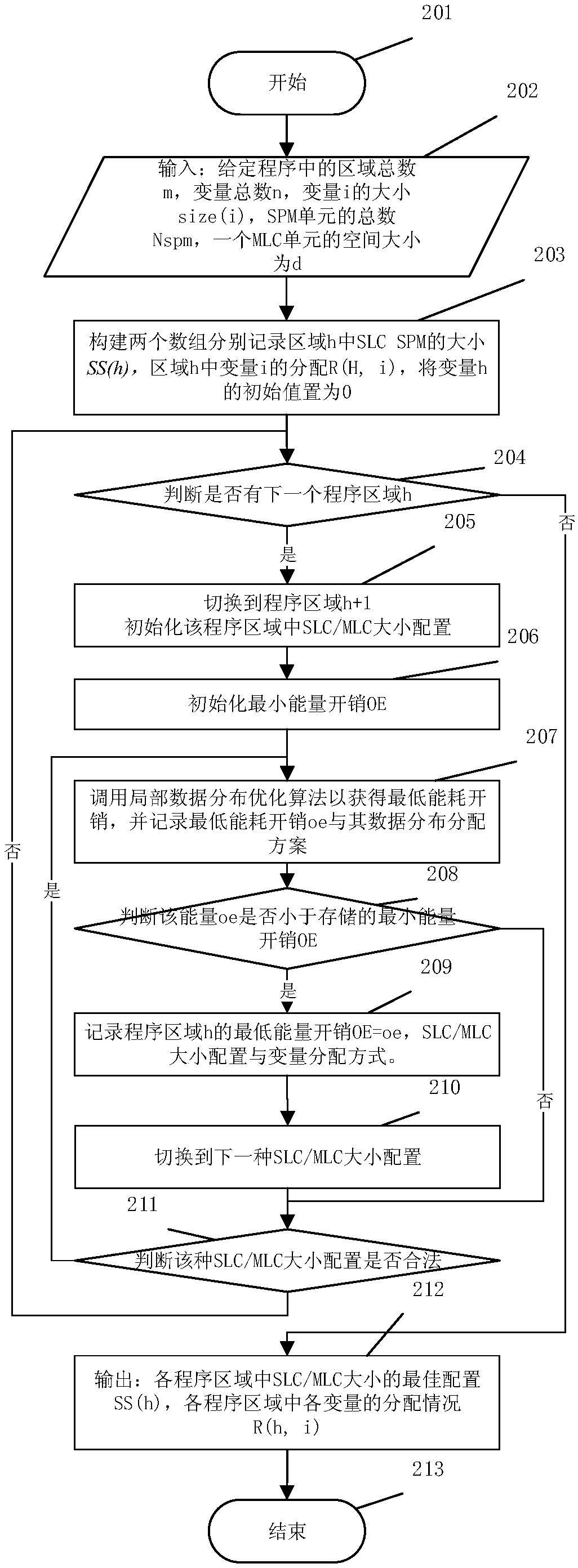
ActiveCN109002257AMake full use of access performanceMake the most of storage densityInput/output to record carriersProgram segmentProgram fragment
The invention relates to a data distribution optimization method based on a variable note memory, belonging to the technical field of computer storage. The method comprises the following steps: S1, according to the access characteristics of the application program, dividing the program into a plurality of program segments, and counting the variable access information of each program segment by using the profiling technology; S2, according to variable access information of program fragment, dynamically adjusting the number of units of single-layer storage mode and multi-layer storage mode in variable note memory, and searching for the optimal configuration of SLC / MLC size in variable note memory; S3, based on the given SLC / MLC size configuration, using the data distribution optimization algorithm to allocate the best storage address for each variable in the program segment; S4: adding the corresponding data distribution optimization program before each program segment, and running the program in the system. The invention realizes the variable memorizer of the note, and reduces the memory access energy consumption of the embedded system.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System and method for certifying cell phone number on basis of CN39 code
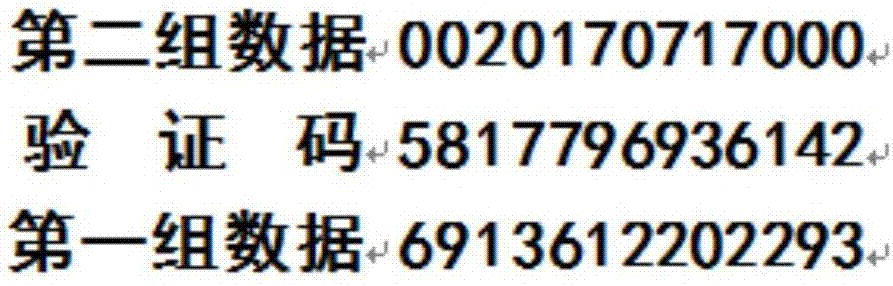
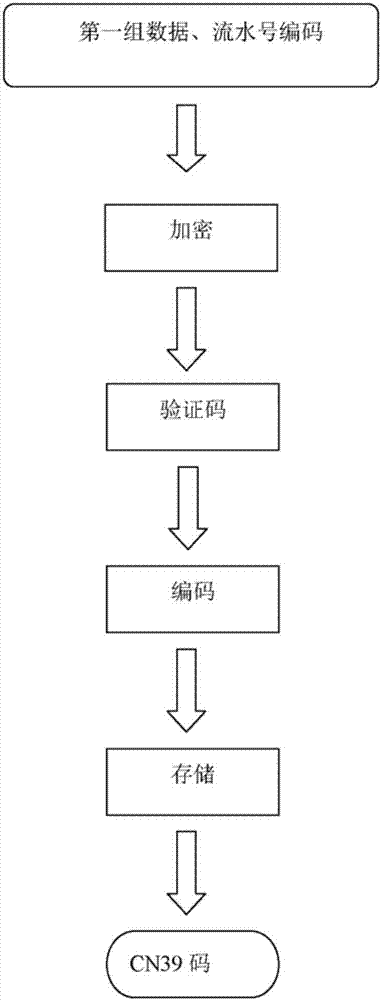
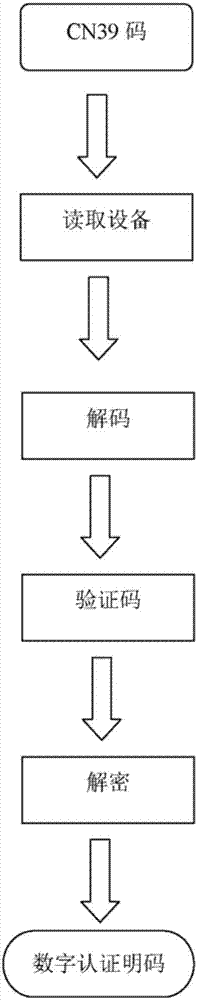
InactiveCN107333262AEasy to identifyShield passKey distribution for secure communicationUser identity/authority verificationReturn-to-zeroTelecommunications
The invention provides a system and method for certifying a cell phone number on the basis of a CN39 code. The system comprises a cell phone control unit, a communication base station control unit, a communication base station program fragment processing unit, a communication base station certification unit, a communication base station data processing unit and a visited person cell phone control unit. The method comprises the steps that a visitor cell phone emits a visiting signal to generate a first group of data; the cell phone control unit generates a second group of data; the cell phone control unit generates a third group of data; the cell phone control unit transmits the CN39 code and a visited person cell phone number to a communication base station; the program fragment processing unit of the communication base station processes the signal, and the certification unit of the communication base station decrypts the three groups of data and transmits the decrypted data to the data processing unit if the decrypted data passes verification; and the data processing unit of the communication base station converts the CN39 code into an original visitor cell phone number, generates a transmission permission signal and outputs a visiting signal to the visited person cell phone number; and the visited person cell phone control unit conducts decryption computation and gives a prompt if a decryption result returns to zero.
Owner:于志
Search utility program for software developers
ActiveUS8666999B2Improve programming efficiencySmall sizeDigital data processing detailsReverse engineeringGraphicsControl flow
A search utility for industrial control programs accepts as a query an example program fragment which is abstracted into a graph-form capturing, for example, instruction control-flow and data-flow. This graph-form may be compared to a graph-form transformation of other portions of the program to provide a more sophisticated matching process that considers underlying logical hierarchy of the program elements rather than their superficial expression in the source code embodiment.
Owner:ROCKWELL AUTOMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com