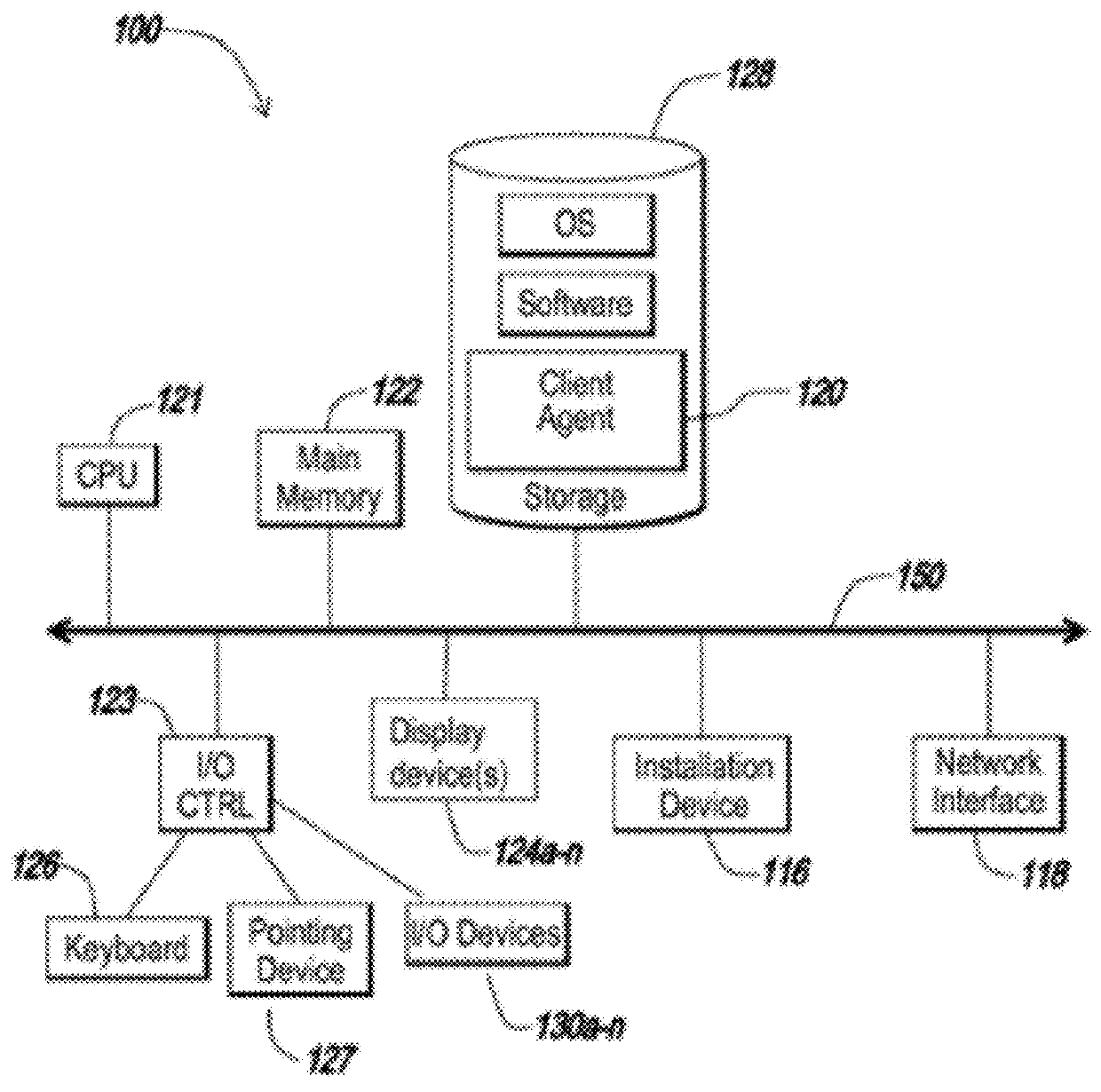
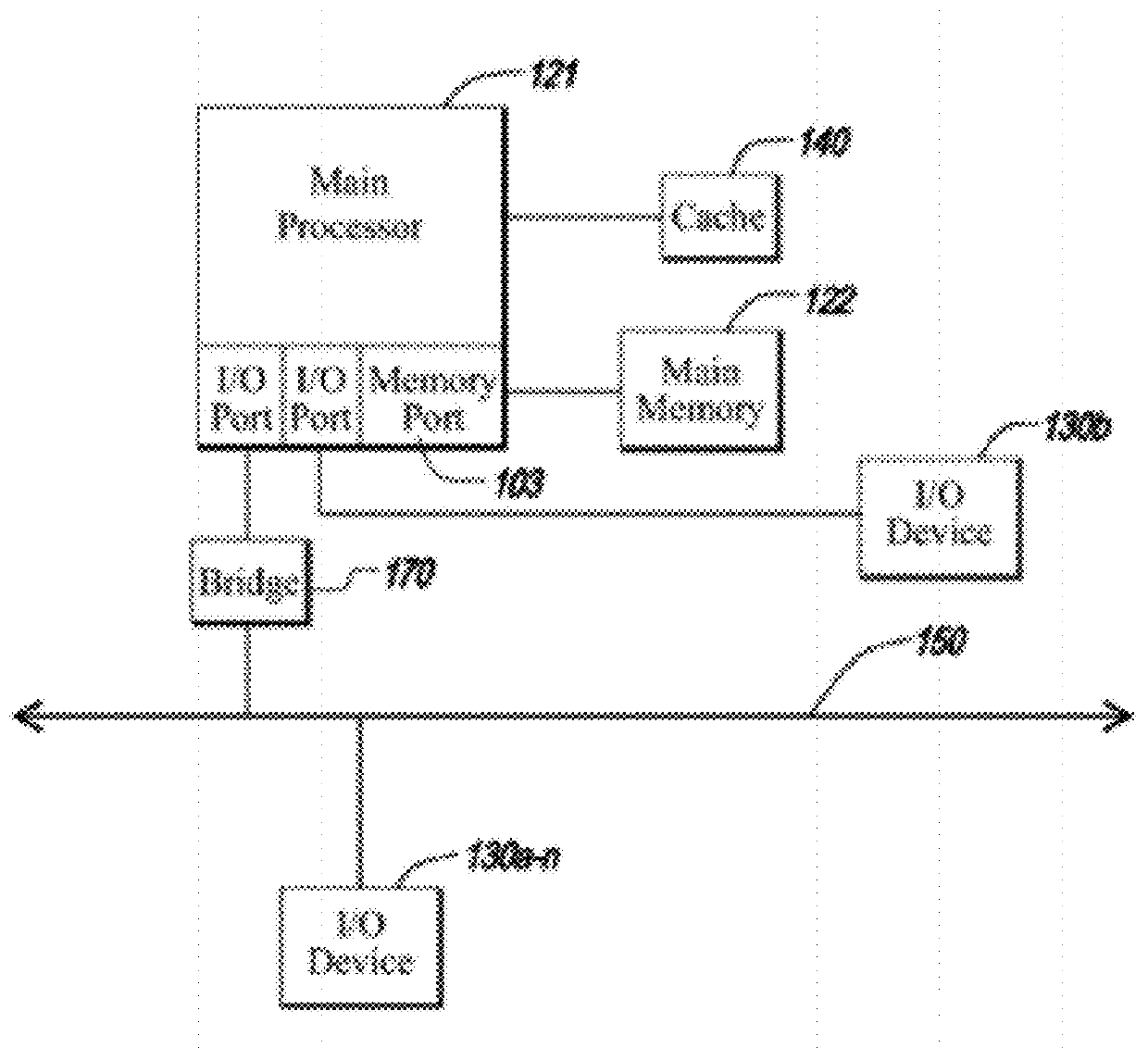
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
371 results about "Retargeting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In software engineering, retargeting is an attribute of software development tools that have been specifically designed to generate code for more than one computing platform.
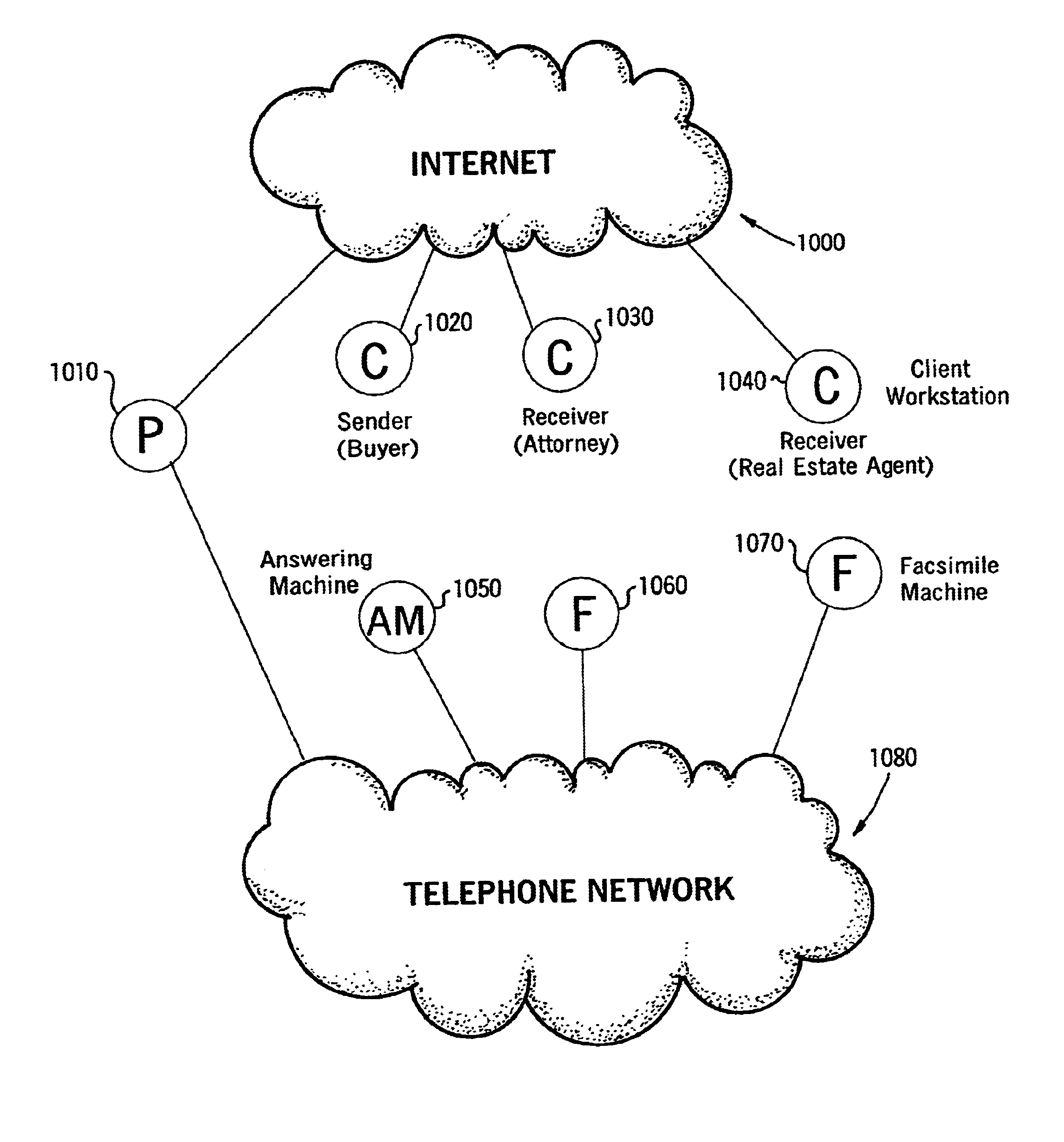
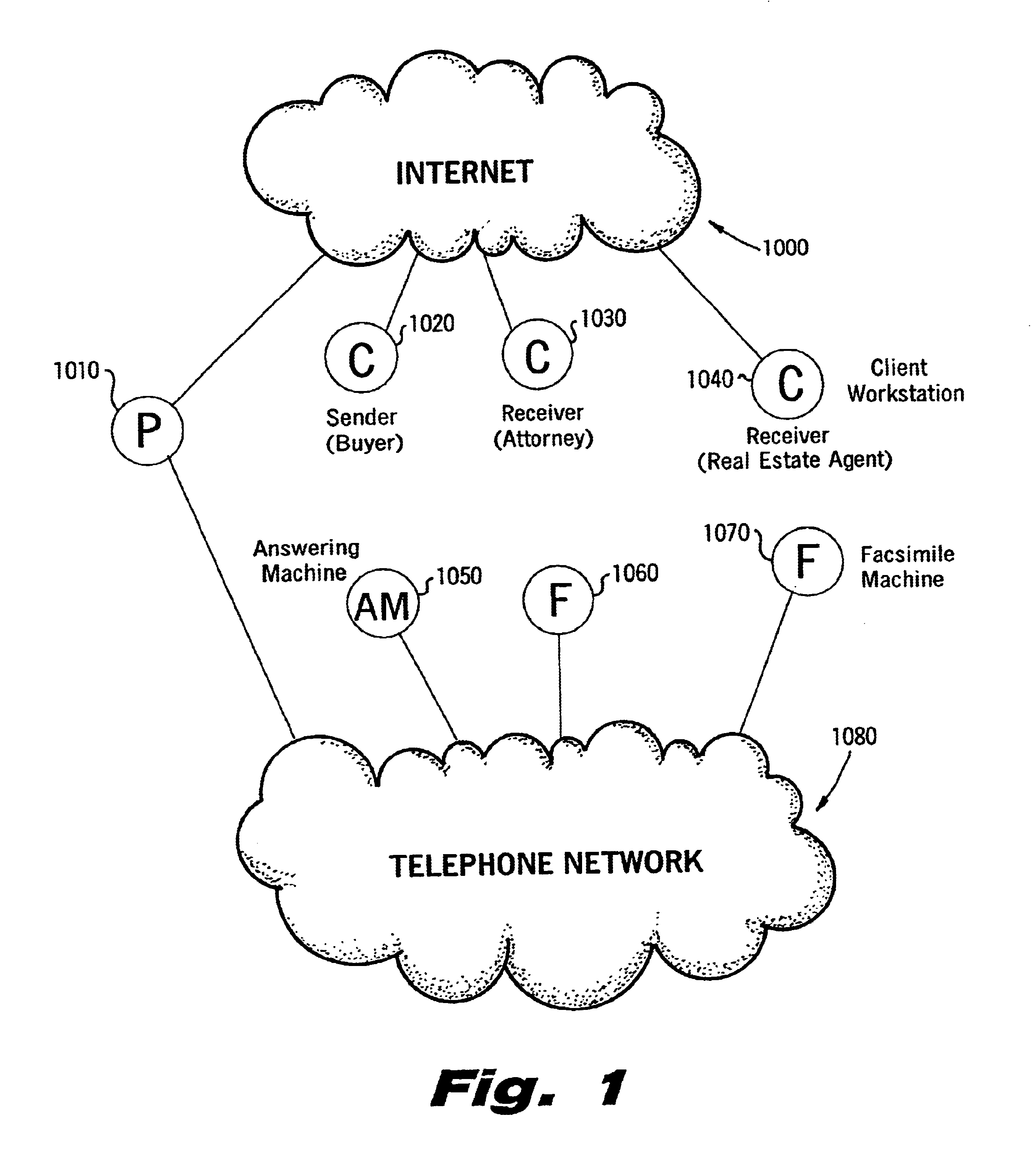
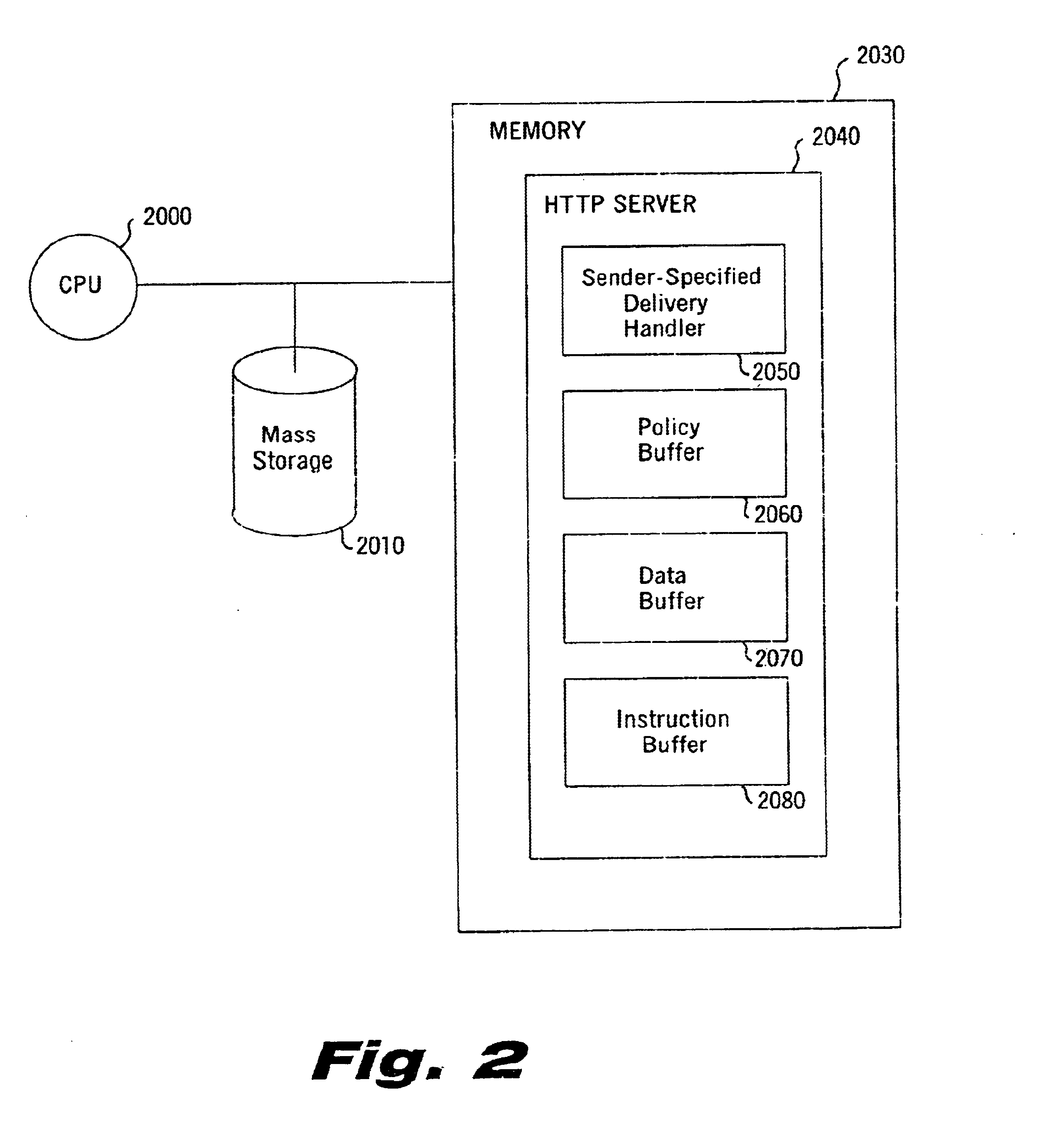
Sender- specified delivery customization
InactiveUS6643684B1Telephonic communicationMultiple digital computer combinationsSecure transmissionFacsimile
A system and method that enables a given sending user to specify a set of delivery policies and have them used for the electronic delivery of a given message, the message potentially having several heterogeneous parts (e.g., text and pictures) each of which is handled differently, and delivered to multiple heterogeneous devices (e.g., PCs, Smartphones, fax machines), and possibly to several distinct recipients. The factors with which a sender can qualify their delivery policies include: time / date, transmission cost; whether the transmission can be forwarded; receiving device capability; and network reliability, speed, and security transmission. Methods are also provided enabling a sender to specify that particular transmissions be redirected or copied, e.g., "send fax copy to my broker and my accountant." In one embodiment, the delivery policies may be specified using PICS.
Owner:SNAP INC
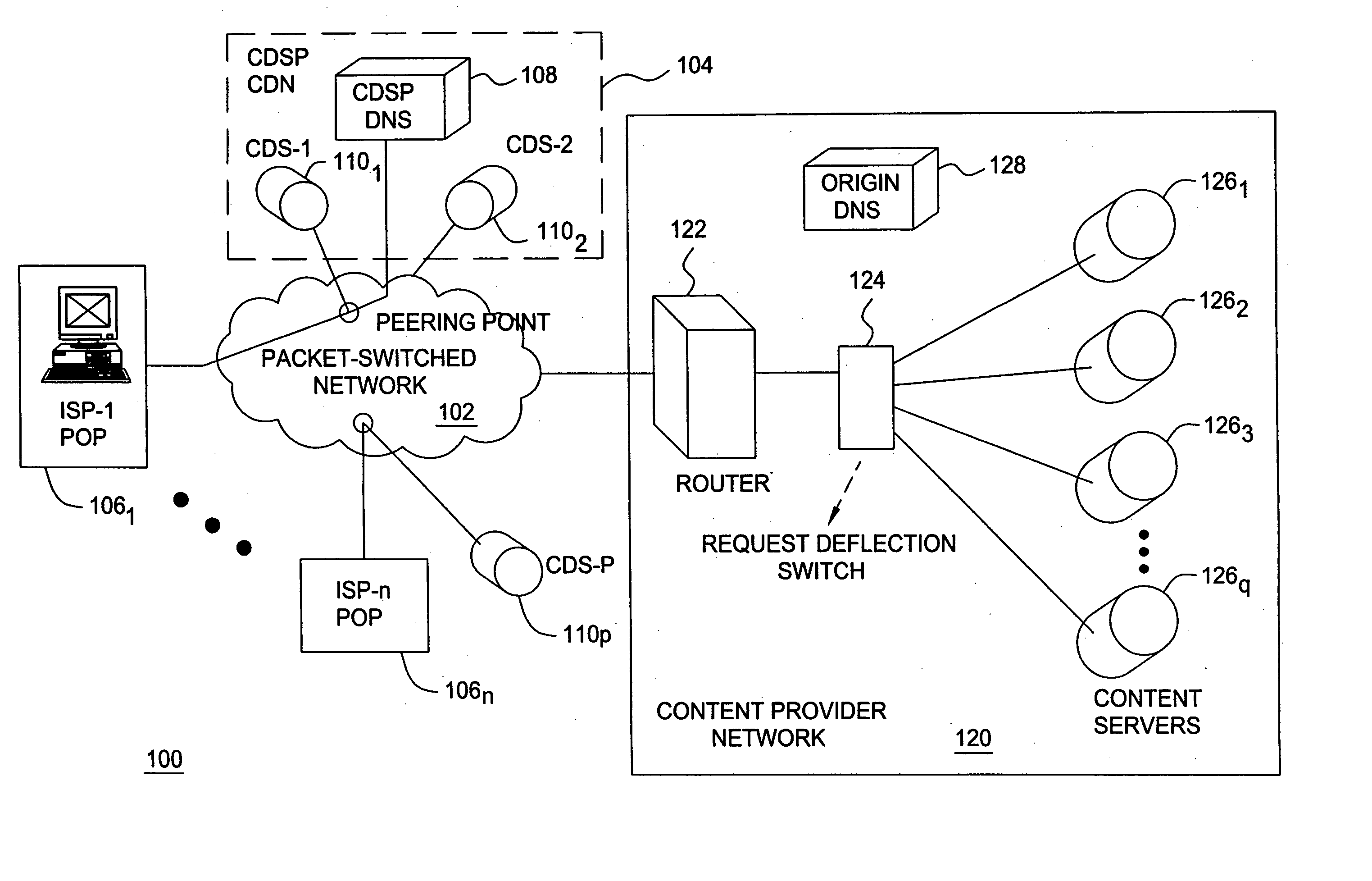
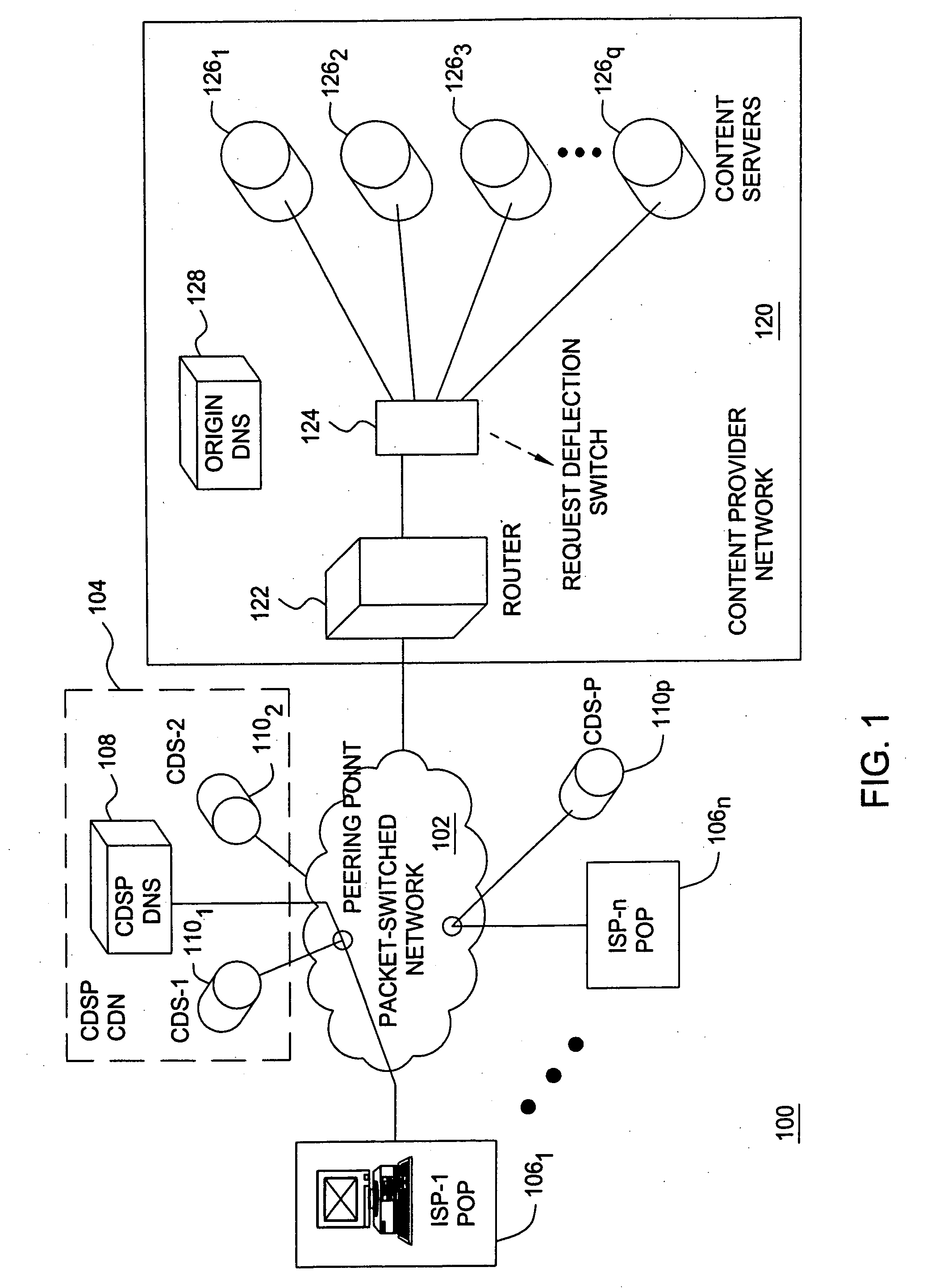
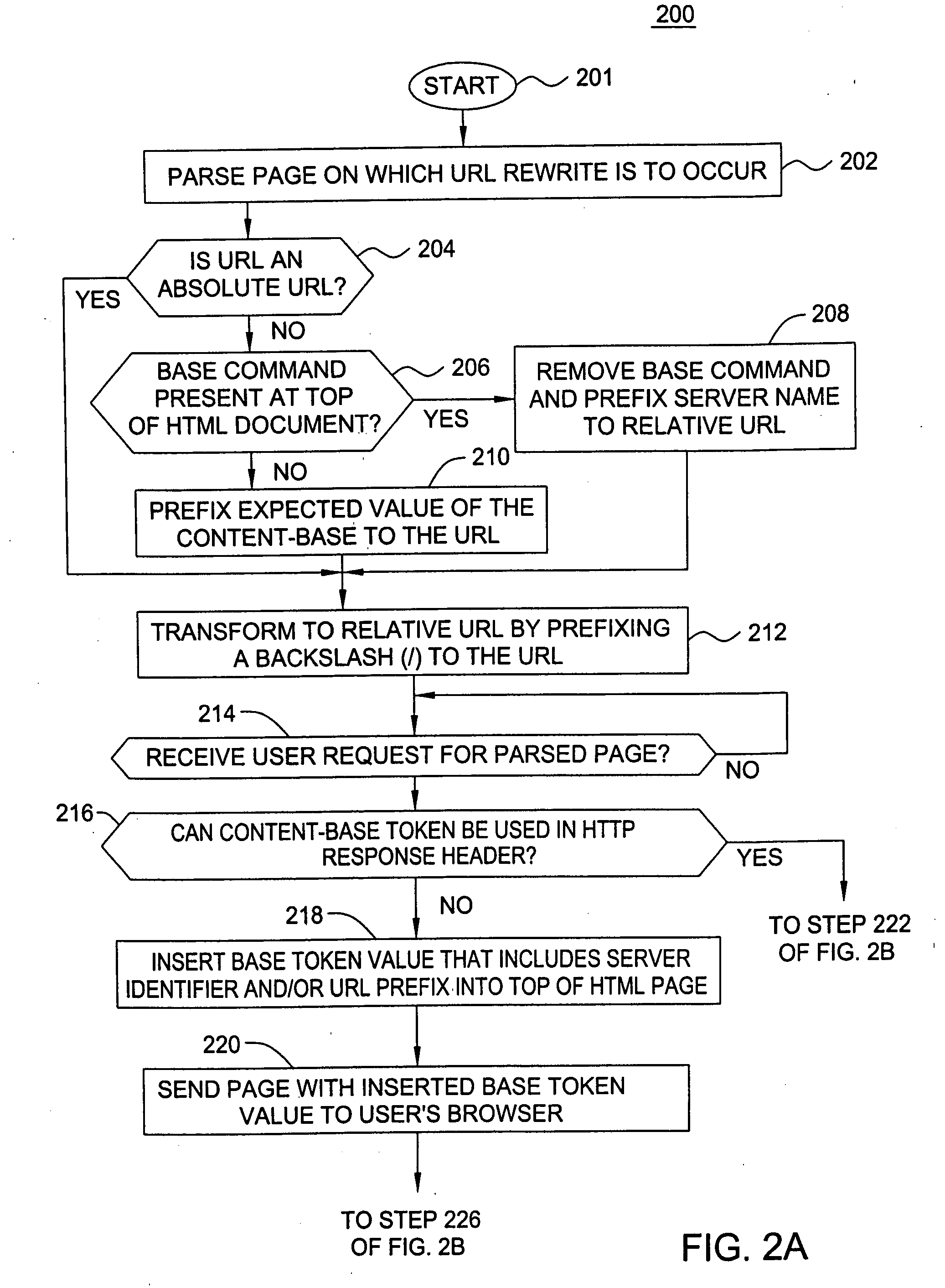
User specific request redirection in a content delivery network
A method and apparatus for providing user specific request redirection in a content delivery network includes parsing a page having embedded objects intended for redirection to at least one cache server, and transforming the embedded objects into relative uniform resource locators (URLs). A content-base token is inserted into an HTTP response header in response to a user request for the page. In an instance where the content-base token is not supported by the server and / or client devices, a base token is inserted into the page in response to a user request for the page. The content-base token and base token provide identification of a server or URL prefix where the embedded objects in the page are to be retrieved. The requested page is then sent to the user's browser. The browser constructs absolute URLs from the embedded URLs using either the received content-base token or base token, to retrieve embedded objects from the server.
Owner:SOUND VIEW INNOVATIONS
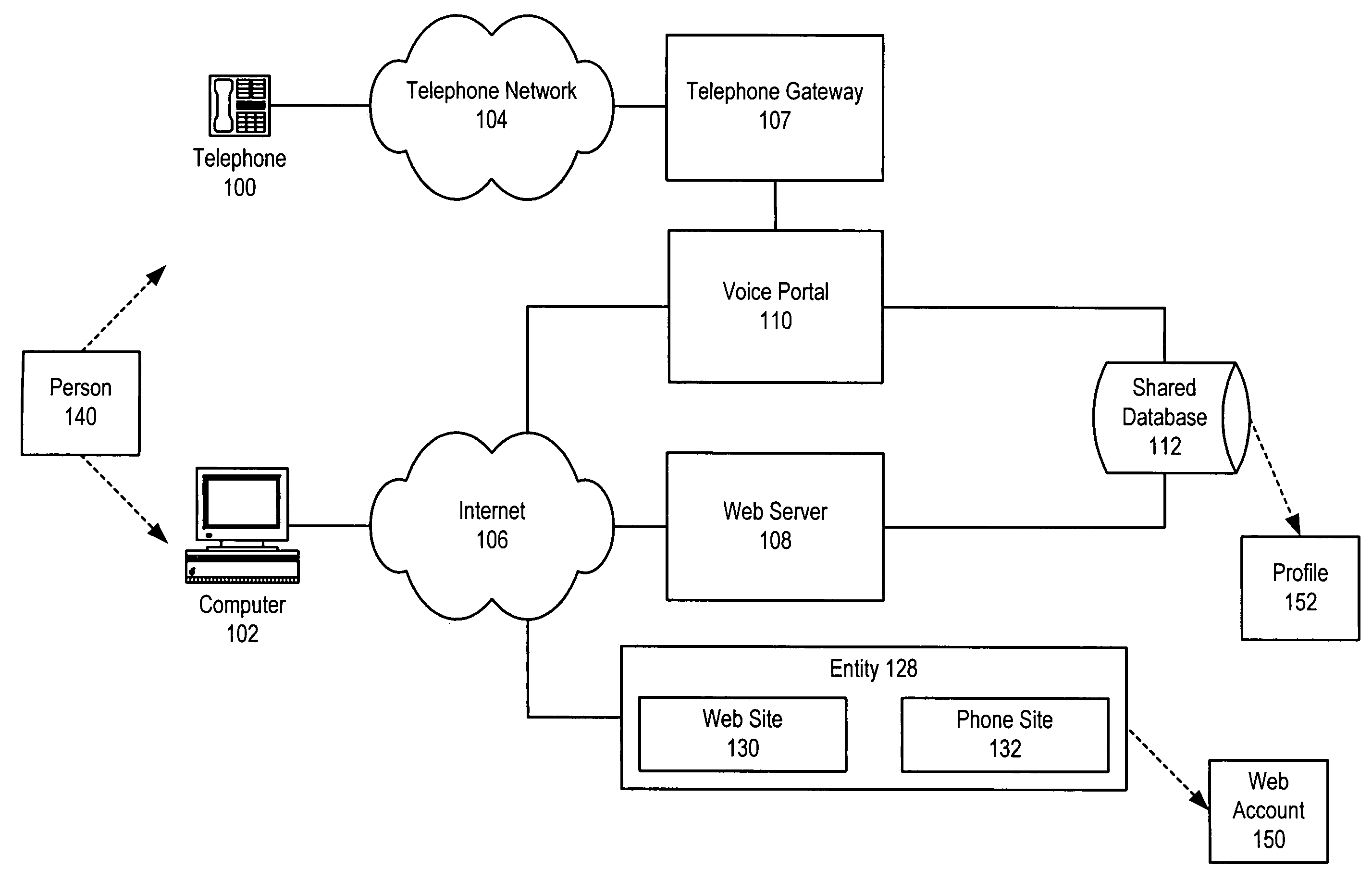
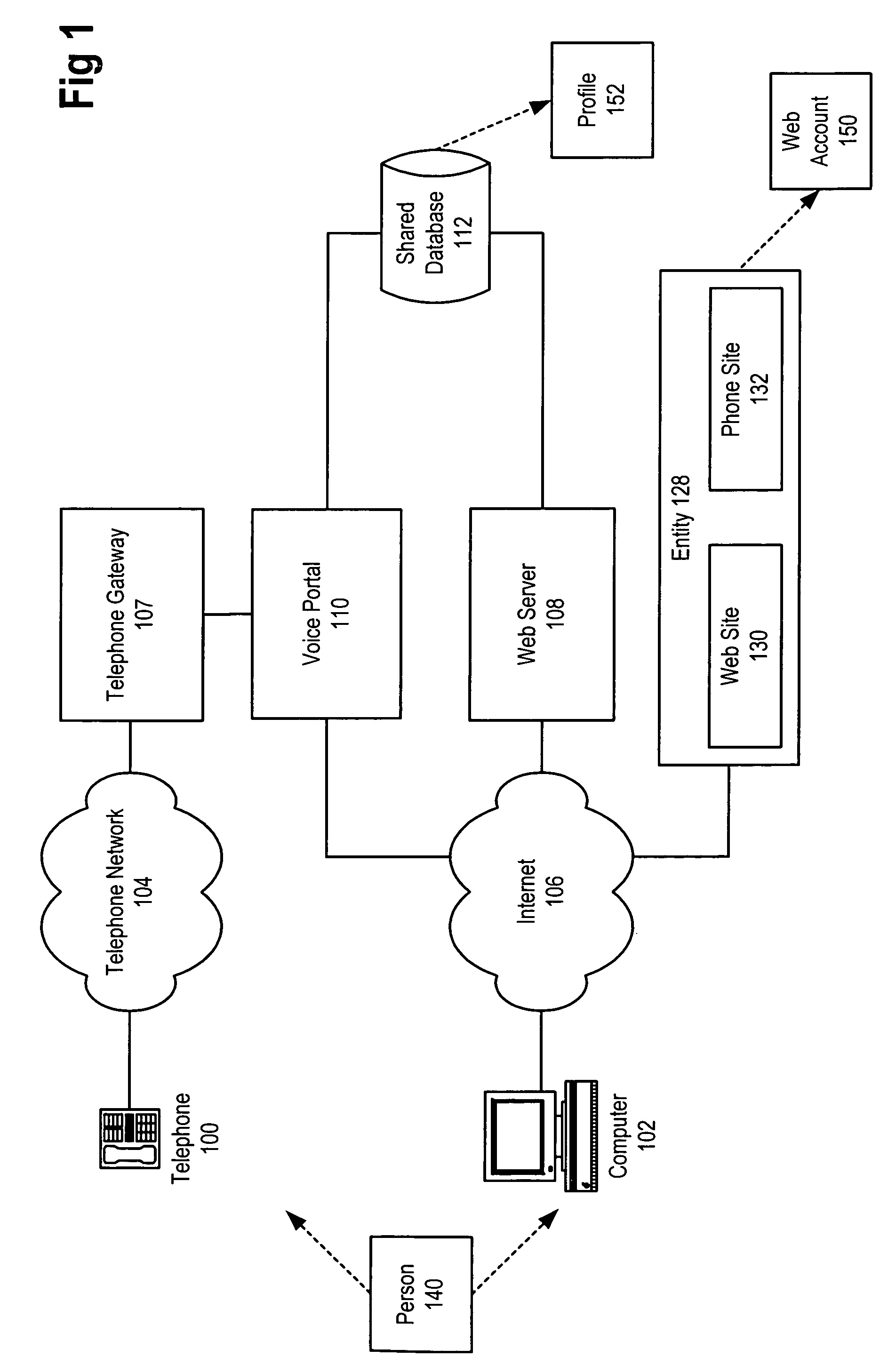
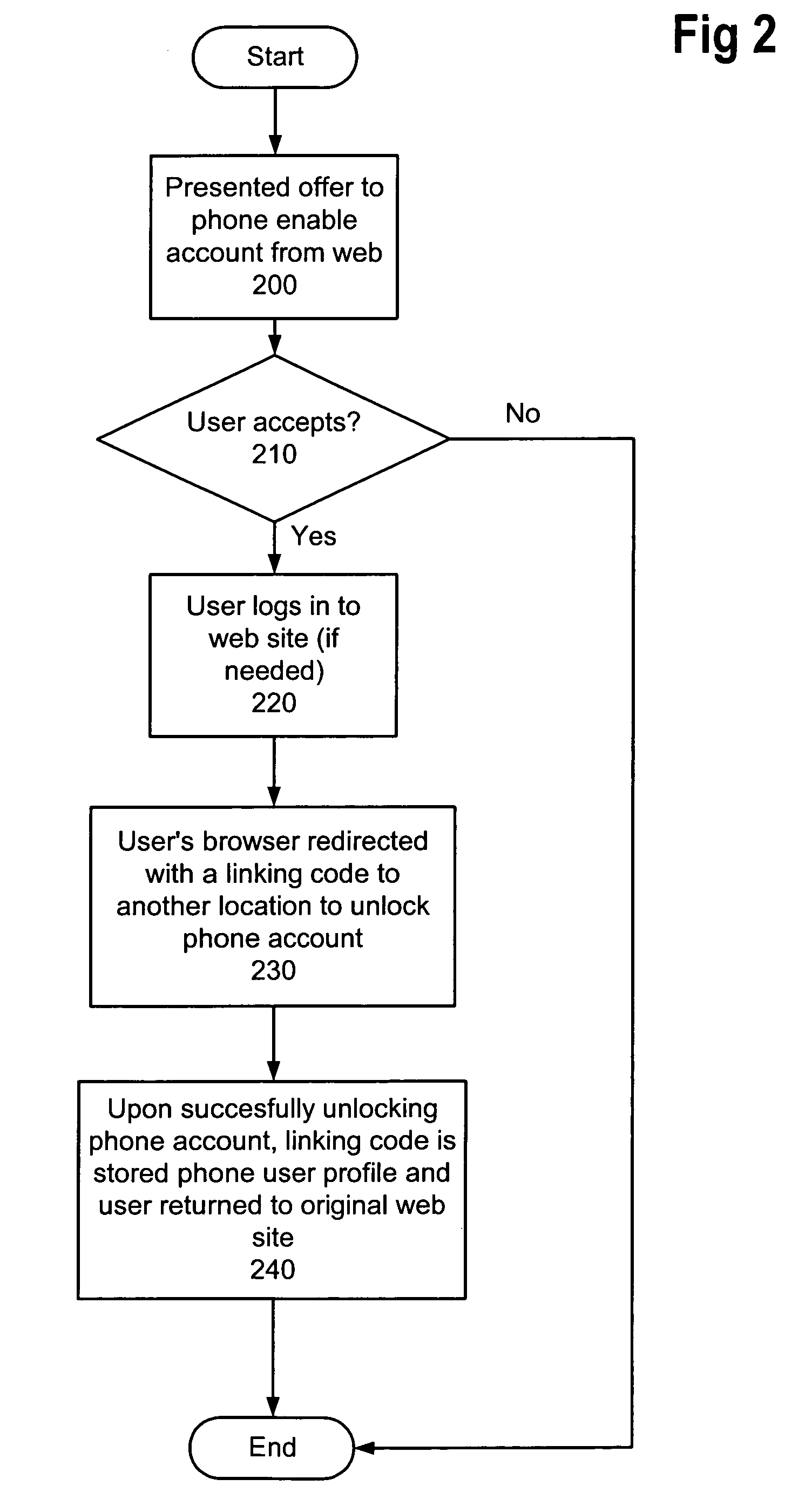
Web-to-phone account linking using a linking code for account identification
InactiveUS7089310B1Avoid the needMultiple digital computer combinationsAutomatic exchangesWeb sitePassword
A method and apparatus for linking a web based account to a phone based account is described. The method avoids the need to directly reveal account information, e.g. username / password, about one account to the provider of the other. The linking occurs on the web in one embodiment, with a user's browser being redirected from the web site to the web site of the provider of the voice service. The redirection URL will include account linking information. Once the user identifies herself to the web site of the provider of the voice service, the linking information can be stored in the user's phone account as a cookie. When the user access the voice service over the phone, her telephone identifying information can be used to identify her profile. When she visits the phone application corresponding to the web site, the cookie—now including linking information—can be passed to the application to identify the appropriate web account.
Owner:MICROSOFT TECH LICENSING LLC
Associating data with images in imaging systems
InactiveUS20060041591A1Readily apparentDigital data processing detailsMetadata multimedia retrievalDatabaseManagement system
A reference to auxiliary data is steganographically encoded within a media signal. The auxiliary data is stored in a metadata database that maps the reference encoded in the media signal to its corresponding metadata. Various application programs and devices can access the metadata by extracting the reference from the media signal, and querying the database for metadata corresponding to the reference. The metadata database may be implemented in a network server to make metadata readily available to devices and applications distributed throughout a network. This steganographic link to metadata may be used to retrieve metadata across media management systems. In one configuration, for example, media management systems have metadata servers that maintain metadata for a collection of media signals. The metadata server is responsible for responding to requests for metadata associated with media titles in its collection. In the event that a metadata server does not have metadata associated with a particular media title, it forwards the reference extracted from the media signal to a metadata router, which in turn, re-directs the request to the appropriate metadata server.
Owner:DIGIMARC CORP +1
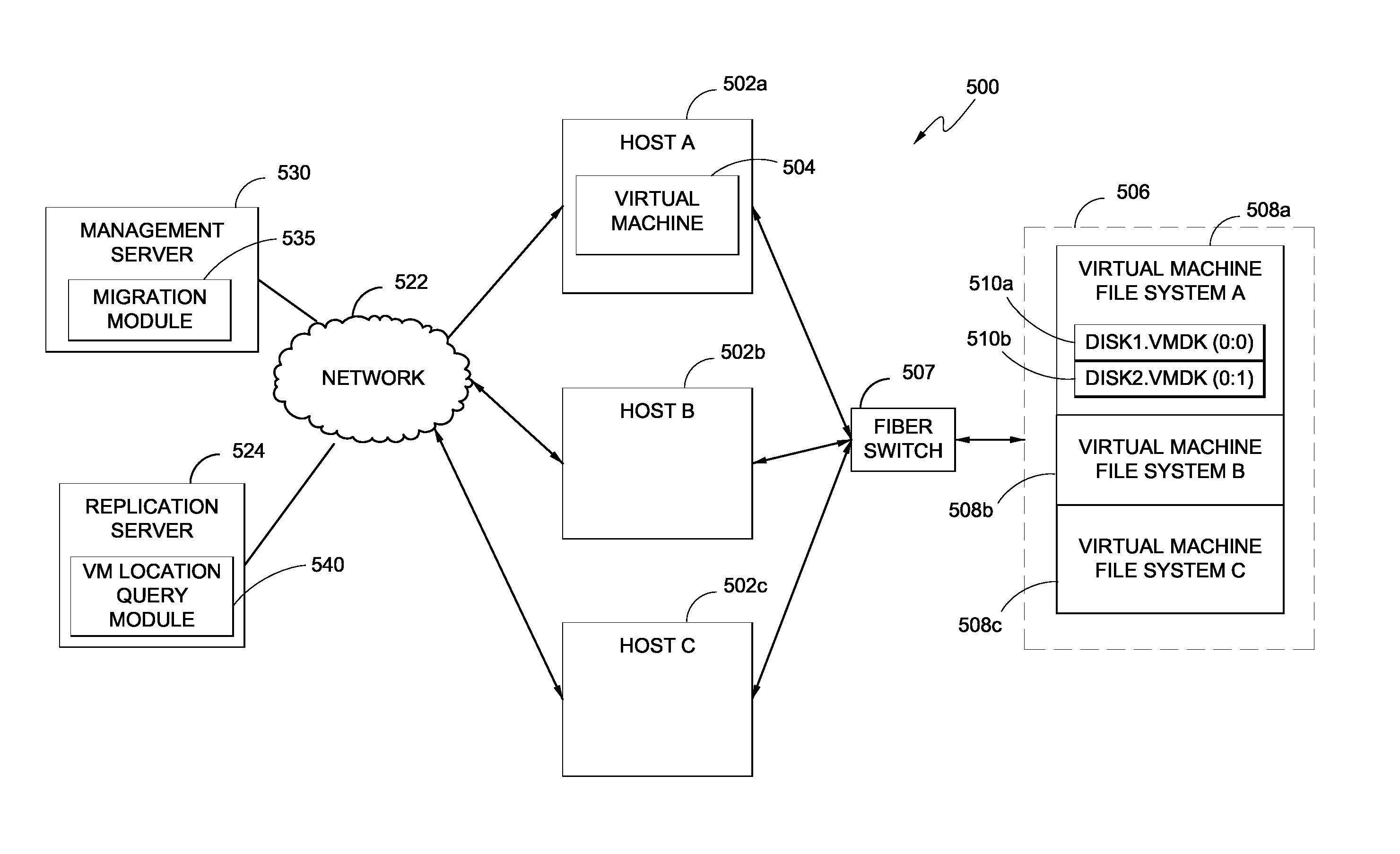
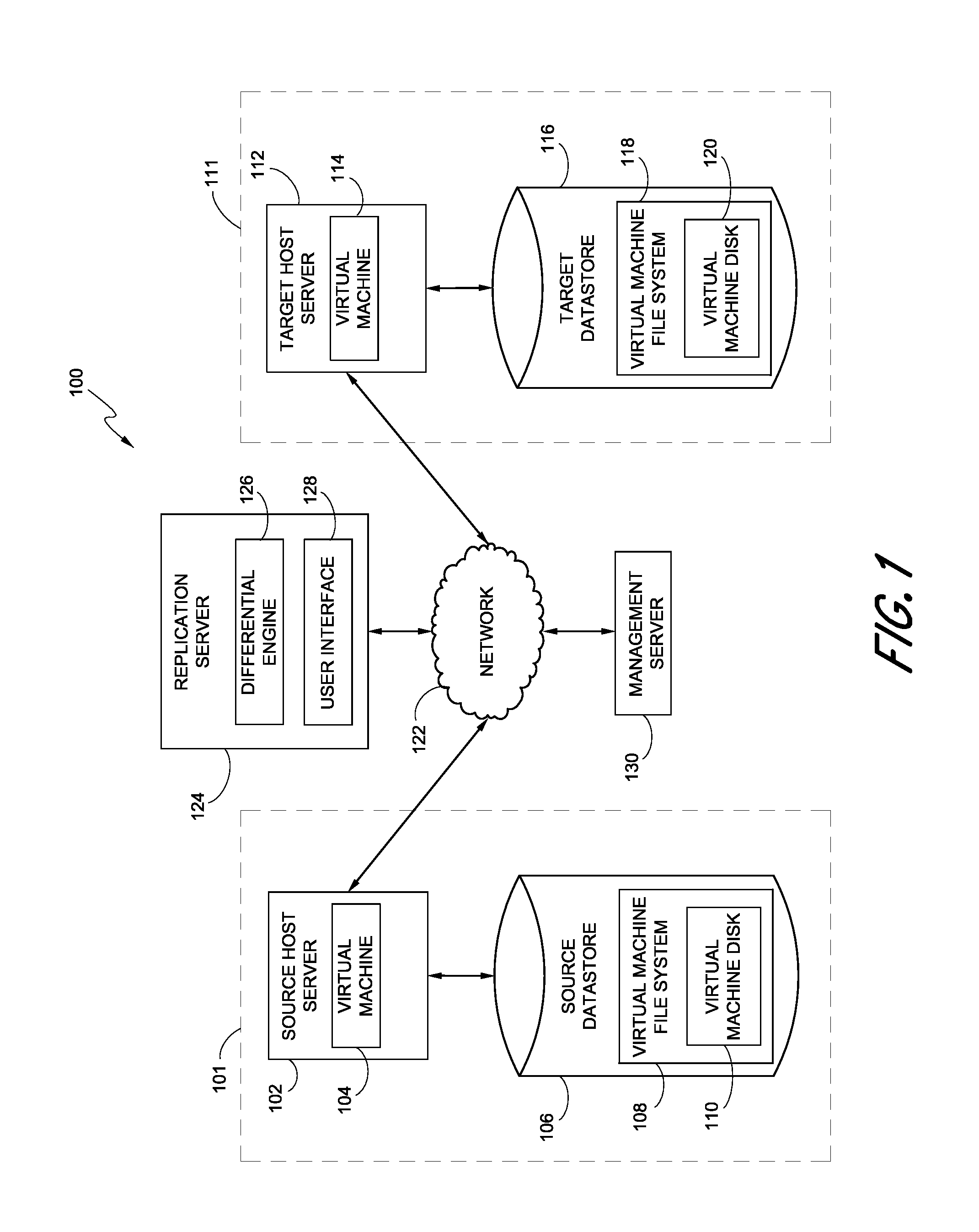
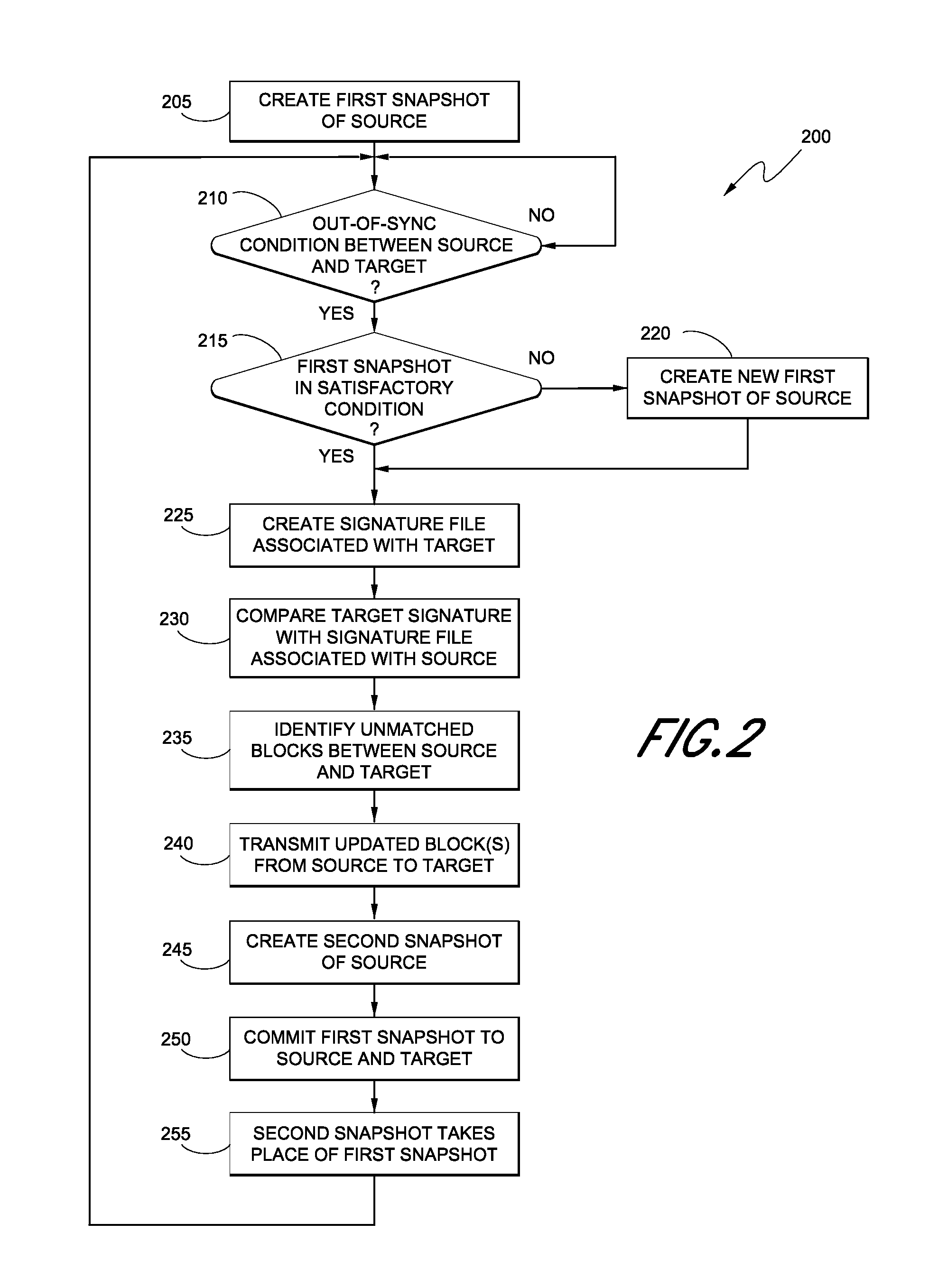
Replication systems and methods for a virtual computing environment
Hybrid replication systems and methods for a virtual computing environment utilize snapshot rotation and differential replication. During snapshot rotation, data modifications intended for a source virtual machine disk (VMDK) are captured by a primary snapshot. Once a particular criterion is satisfied, the data modifications are redirected to a secondary snapshot while the primary snapshot is committed to both source and target VMDKs. The secondary snapshot is then promoted to primary, and a new secondary snapshot is created with writes redirected thereto. If the VMDKs become out-of-sync, disclosed systems can automatically perform a differential scan of the source data and send only the required changes to the target server. Once the two data sets are synchronized, snapshot replication can begin at the previously configured intervals. Certain systems further provide for planned failover copy operations and / or account for migration of a virtual machine during the copying of multiple VMDKs.
Owner:QUEST SOFTWARE INC
Transparent User Interface Integration Between Local and Remote Computing Environments
ActiveUS20120226742A1Enhance theme-integrationUnified and transparentStatic indicating devicesMultiple digital computer combinationsOperational systemRadio button
Methods and systems for transparent user interface integration between remote (“published”) applications and their local counterparts are described, providing a seamless, unified user experience, and allowing integration of a start menu, dock, taskbar, desktop shortcuts, windows, window and application switching, system tray elements, client-to-host and host-to-client file type association, URL redirection, browser cookie redirection, token redirection, status message interception and redirection, and other elements. These methods and systems further enhance theme-integration between a client and remote desktop or virtual machine by remoting all UI elements to a recipient for generation, including text controls, buttons, progress bars, radio buttons, list boxes, or other elements; presenting them with the receiver's product and OS-specific UI; and returning status back to the sender. This may achieve a more unified and transparent UI integration. Furthermore, international text may be correctly received in cross-language environments, or translated into the language of the presenting environment.
Owner:CITRIX SYST INC
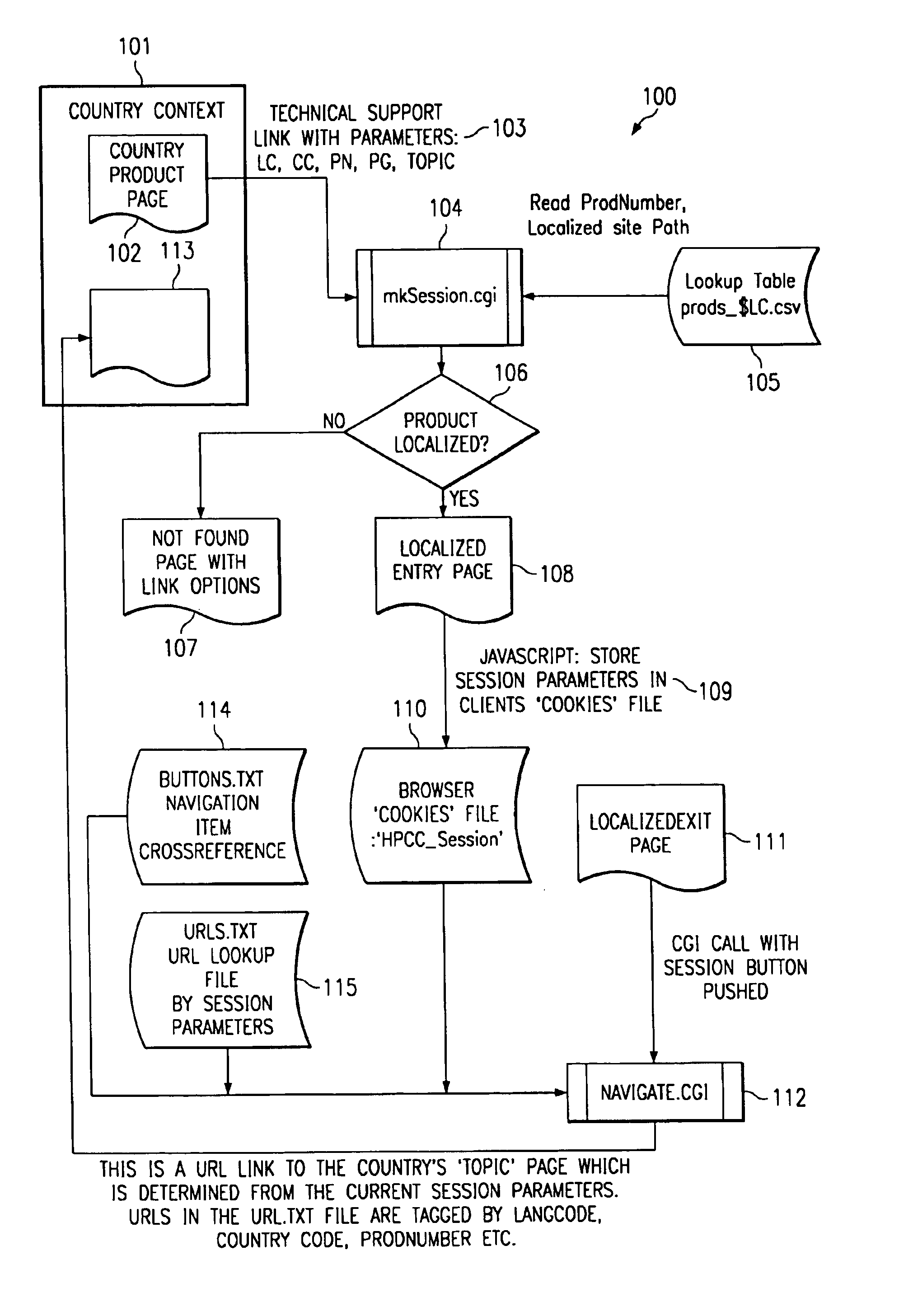
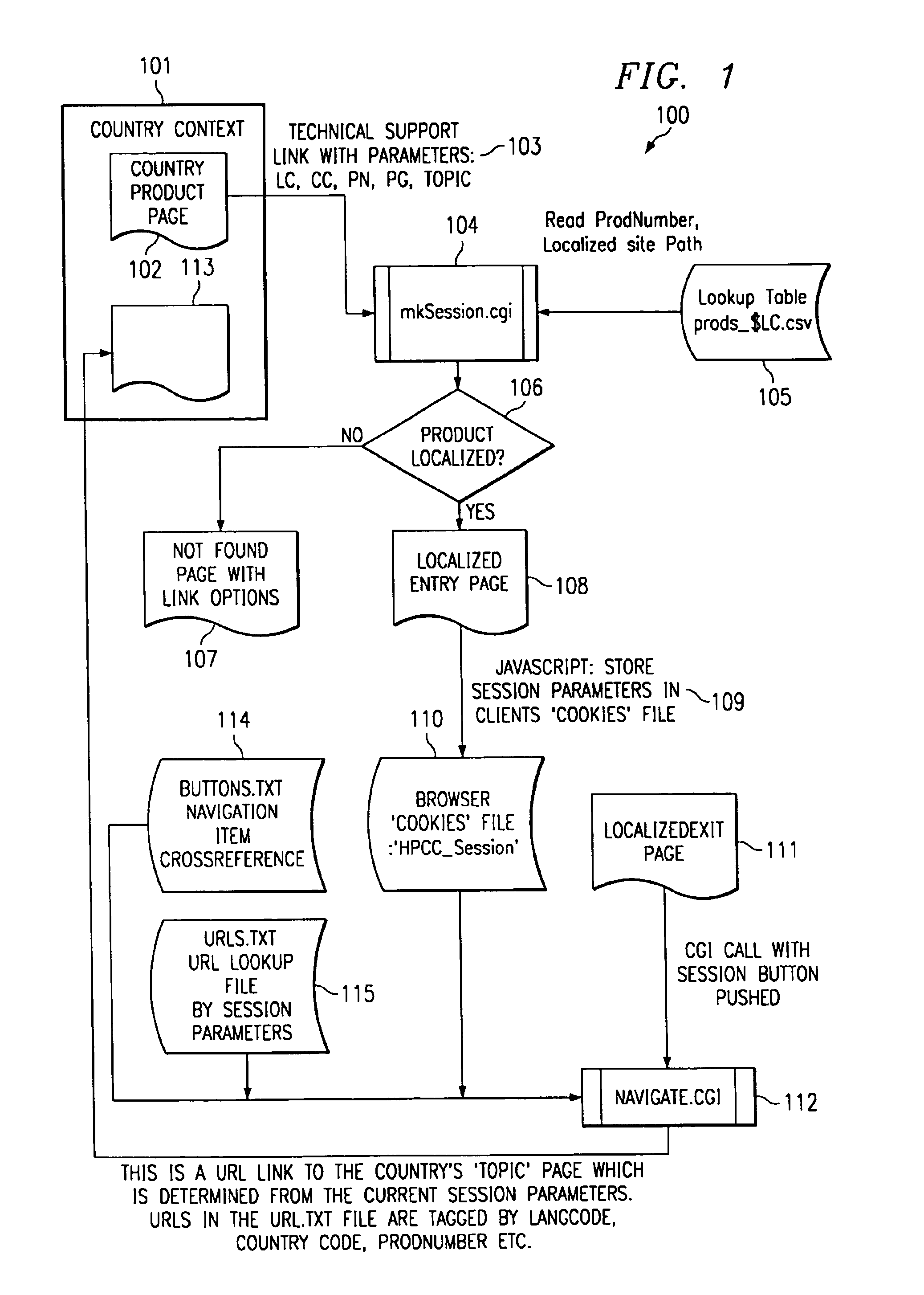
World wide contextual navigation
InactiveUS6839742B1Multiple digital computer combinationsSpecial data processing applicationsHome pageUniform resource locator
The invention maintains the context, e.g. the user's language and / or the user's country, while the user is navigating through different related sites or pages. The invention stores and maintains the information about the user's origin, language, country and product of interest during the navigation. This information is stored as arguments in the URL. A session application redirects the user into a particular page based on the arguments provided by the referring site or user's site. The application operates by matching the provided arguments against lookup tables that describe what is available on the main site. When a match occurs between the arguments in the URL and the lookup tables, the invention begins a session by storing information in the URL into a cookie that is stored on the user's computer. A navigation application will use the information stored in the cookie to return the user to their home page.
Owner:HEWLETT PACKARD DEV CO LP
System and method using interpretation filters for commercial data insertion into mobile computing devices
The present invention teaches a method to alter browser programming responses by the substitution of certain client-server communications commands allowing certain browser requests to be redirected to alternate servers for further interpretation and subsequent server responses. The purpose of this method is injection of custom content into browser-based device displays without disruption of the original page content. This method accomplishes the task without requiring additional plug-in applications, browser or client device code modifications. The invention teaches the use of a local proxy server or embedded device but also claims the use of remote network proxy servers to transparently alter the command request sequence of the client browser in order to request alternate information other than that normally requested by the browser for interpretation and display. The present invention also teaches how to identify web publishers or domain owners for registration notification and possible financial compensation.
Owner:DYE THOMAS A +1
Proxy based adaptive two factor authentication having automated enrollment
InactiveUS20050021975A1Transparent authenticationImprove simplicityDigital data authenticationSecret communicationClient-sideStrong authentication
A method of and system for adding strong authentication to an existing network based application. A proxy based monitoring process screens data sent to and from a client application and intercepts login requests. These intercepted requests are redirected to an authentication process which first checks to see if the user logging in has enrolled in strong authentication. If not enrolled, the user is allowed to continue with a normal login. If enrolled, the user is authenticated by requesting digital identification data, such as a digital certificate, from the user's computer. If authentication succeeds, the user is allowed to proceed on to the normal login process. If authentication fails, the login attempt is blocked. User enrollment is automated, requiring no user interaction beyond the initial request. Verification for purposes of issuing a digital certificate, or other identifying data, is by means of confirming that the user being enrolled is currently logged in to the client application.
Owner:LIU GOUPING
Method and apparatus to manage network client logon scripts using a graphical management and administration tool
A GUI (Graphical User Interface) Manager is used by a network administrator to fill-in predefined templates. The administrator does not need to compile, debug or write a single line of scripting code. The GUI manager has a “select the box” and “point and click” and “fill-in the blank” approach for selecting computer settings. The predefined configuration and / or template(s) are used by a logon script program on a client system to manage the configuration of resources on at least one client. There are three levels of resources that can be managed. The first type of resource is an operating system. The second type of resource is an application resource. And the third type of resource is to redirect a resource on the client to a resource on a network such as a drive letter mapping. Resources include configurations from the group of configuration settings consisting of drive mappings, shell folders, printer deployment, proxy server access, application paths, service packs, anti-virus updates, policies and automatic mail profile creation. In another embodiment, validation logic is used on the clients' system during the execution of an application program that takes the template and applies the defined configuration settings in the template to the clients' system so as to automatically configure at least one configuration setting for a user if the combination of one or more predefined conditions for a selected group, a selected operating system and a selected connection method are met. In still another embodiment, an interpretive engine is used on the client's system to permit the administration of client resources with a template while also allowing network administrators to build their own custom logon scripts.
Owner:QUEST SOFTWARE INC
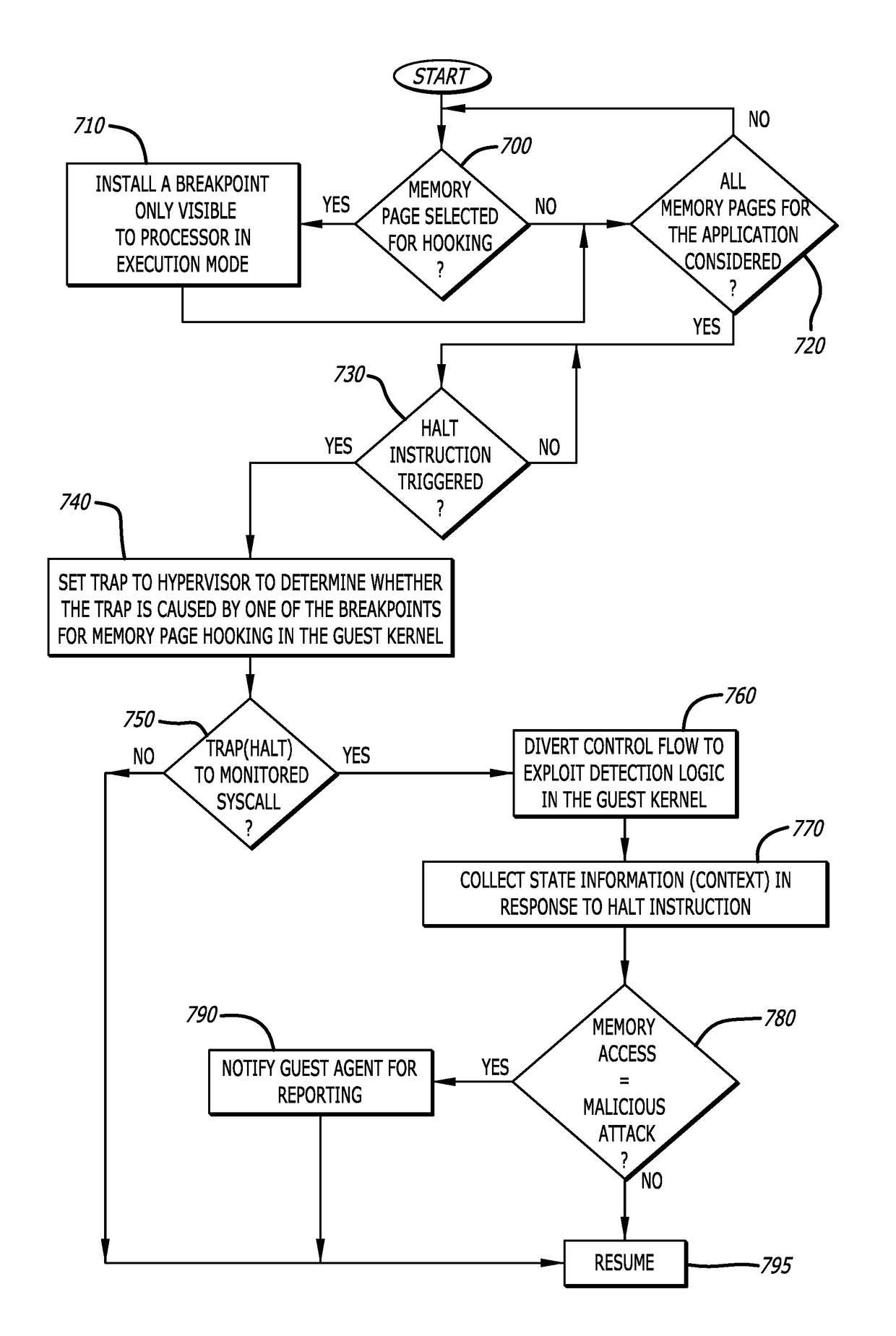
System and method of threat detection under hypervisor control
ActiveUS10033759B1Input/output to record carriersPlatform integrity maintainanceSystem callApplication software
A computing device is described that comprises one or more hardware processors and a memory communicatively coupled to the one or more hardware processors. The memory comprises software that, when executed by the processors, operates as (i) a virtual machine and (ii) a hypervisor. The virtual machine includes a guest kernel that facilitates communications between a guest application being processed within the virtual machine and one or more virtual resources. The hypervisor configures a portion of the guest kernel to intercept a system call from the guest application and redirect information associated with the system call to the hypervisor. The hypervisor enables logic within the guest kernel to analyze information associated with the system call to determine whether the system call is associated with a malicious attack in response to the system call being initiated during a memory page execution cycle. Alternatively, the hypervisor operates to obfuscate interception of the system call in response to the system call being initiated during memory page read cycle.
Owner:FIREEYE SECURITY HLDG US LLC
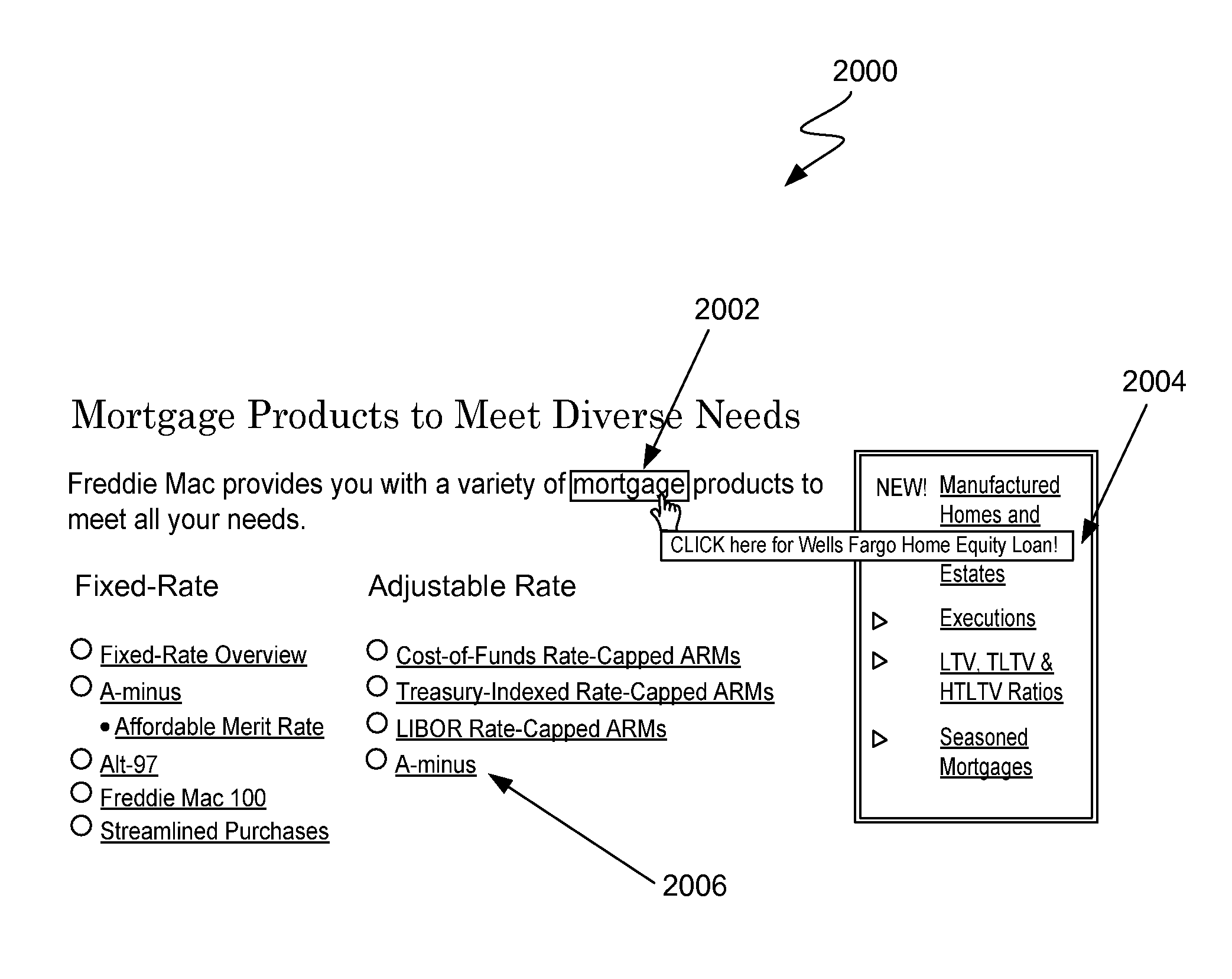
Dynamic document context mark-up technique implemented over a computer network
InactiveUS7284008B2CommerceSpecial data processing applicationsKeyword analysisUniform resource locator
A technique is disclosed for generating markup information to be displayed on a client computer system. The client system includes memory configured to store at least one update file which comprises keyword information relating to keywords suitable for markup. In one implementation, the update file is generated at a remote server system and downloaded to the client system. When a new document (e.g. a web page) is displayed on the client system to an end user, selected context associated from the document is analyzed for selected keywords. In a specific implementation, the selected keyword information is provided by an entity other than the end user. Using the selected keyword information, specific context in the document is selected to be marked up. According to a specific embodiment, the selection of the document context to be marked up may be performed at the client system. Markup operations are then implemented at the client system on at least a portion of the selected document context, thereby resulting in marked up document context which has a visual appearance that is different than the appearance of the initial parsed context. Additionally, a pop-up advertisement may be automatically displayed on the client system based upon the identified context in the document. When the user clicks on a portion of the marked up document context, the user may be redirected to a target URL which was not included as part of the initial parsed document context. Alternatively, a pop-up window or layer which includes a plurality of different links may be displayed to the user.
Owner:AMOBEE
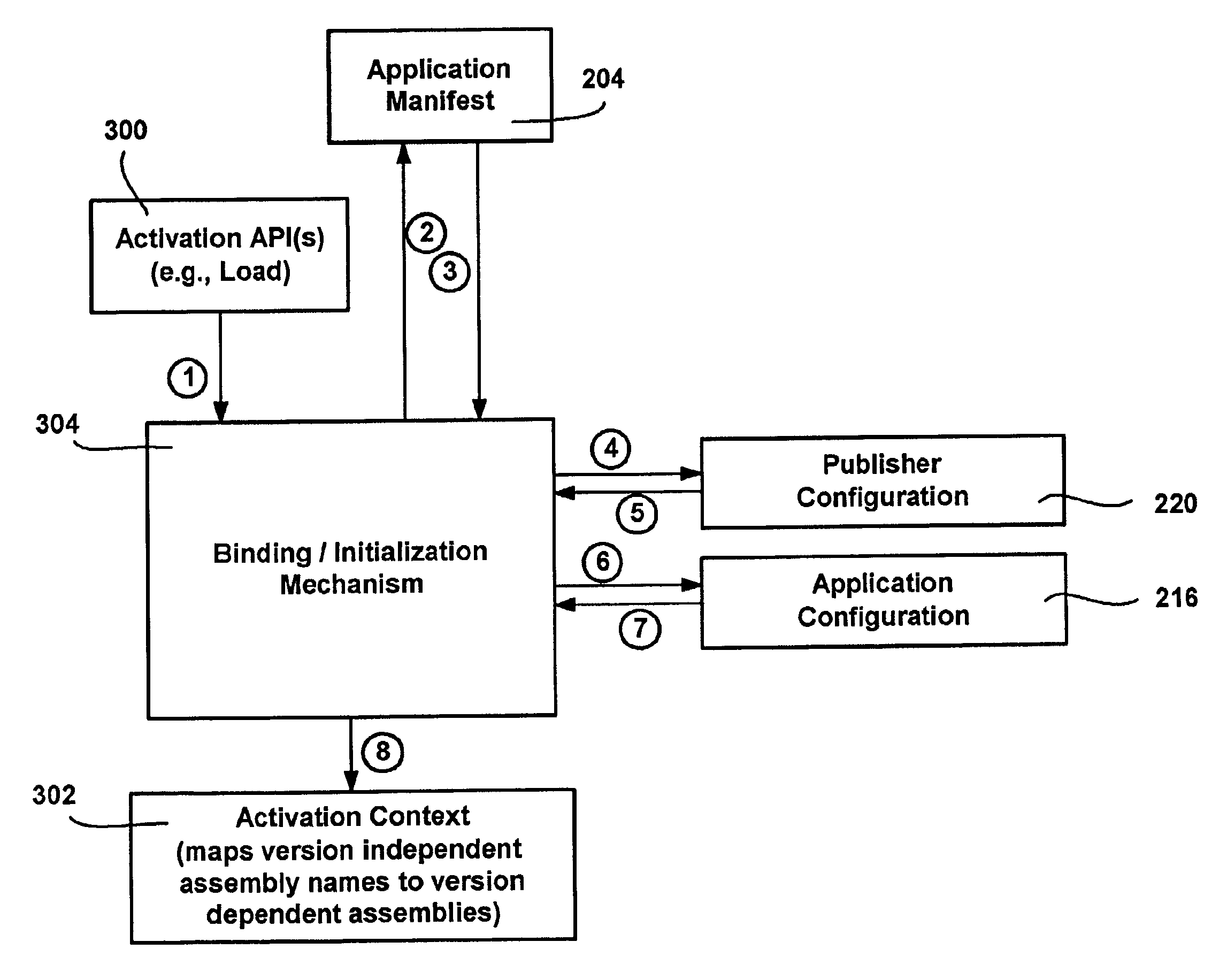
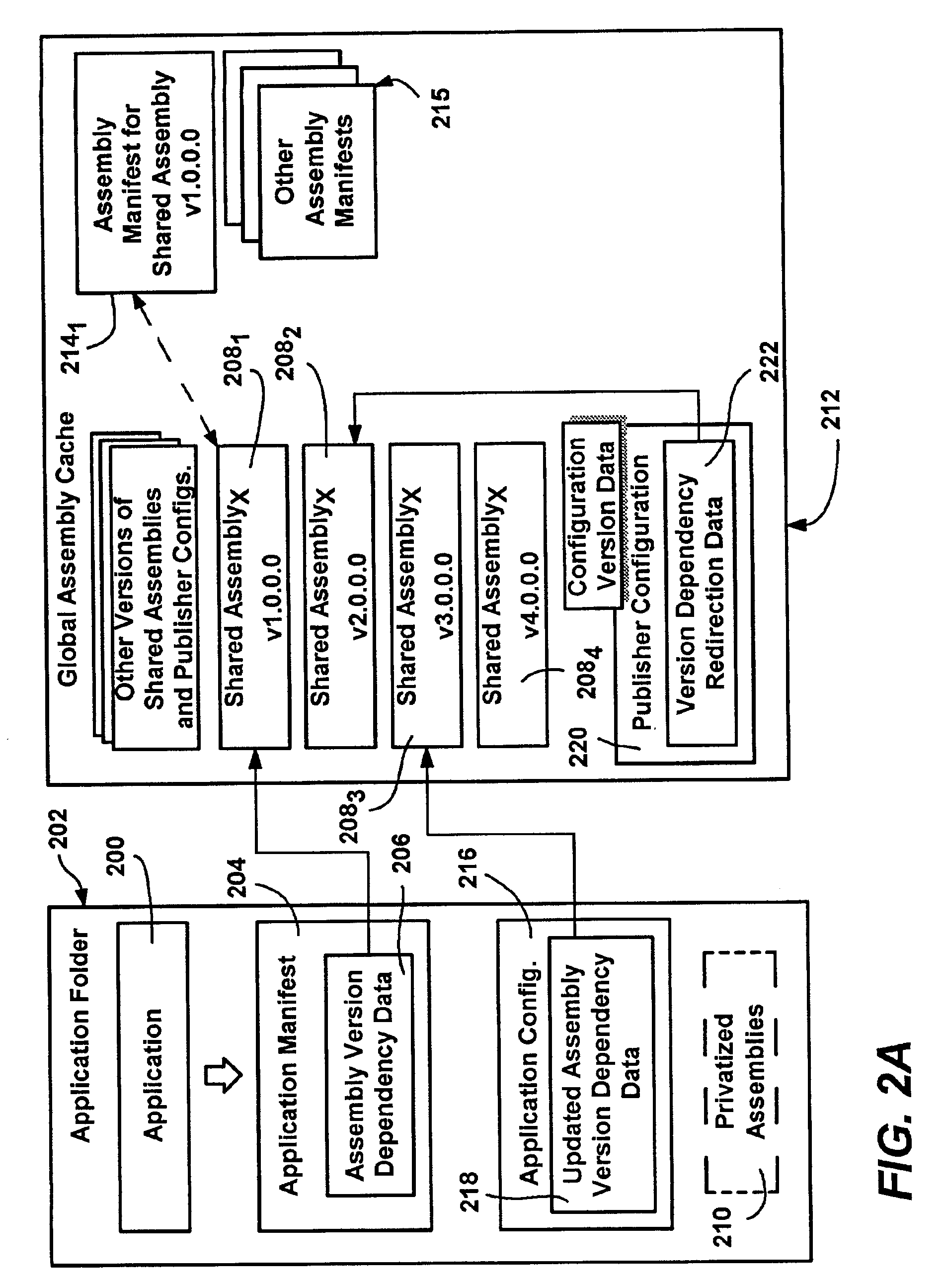
Configurations for binding software assemblies to application programs
A method, system and infrastructure that allow an application to run with specified versions of assemblies bound thereto, while allowing the application author, assembly publisher and / or an administrator to change the originally-specified version as desired. Each assembly may exist and run side-by-side on the system with other versions of the same assembly being used by other applications. An application manifest specifies any desired assembly versions, which may be redirected to another version (overridden) by an application configuration. A publisher configuration provided by an assembly publisher can similarly override the specified version. Lastly, an administrator configuration is capable of overriding other configuration versioning information. A table built from the manifest and any configuration redirection may be accessed during execution to quickly locate the appropriate version. The various configuration data structures themselves may be wrapped as assemblies, thereby enabling versioning of configurations.
Owner:MICROSOFT TECH LICENSING LLC
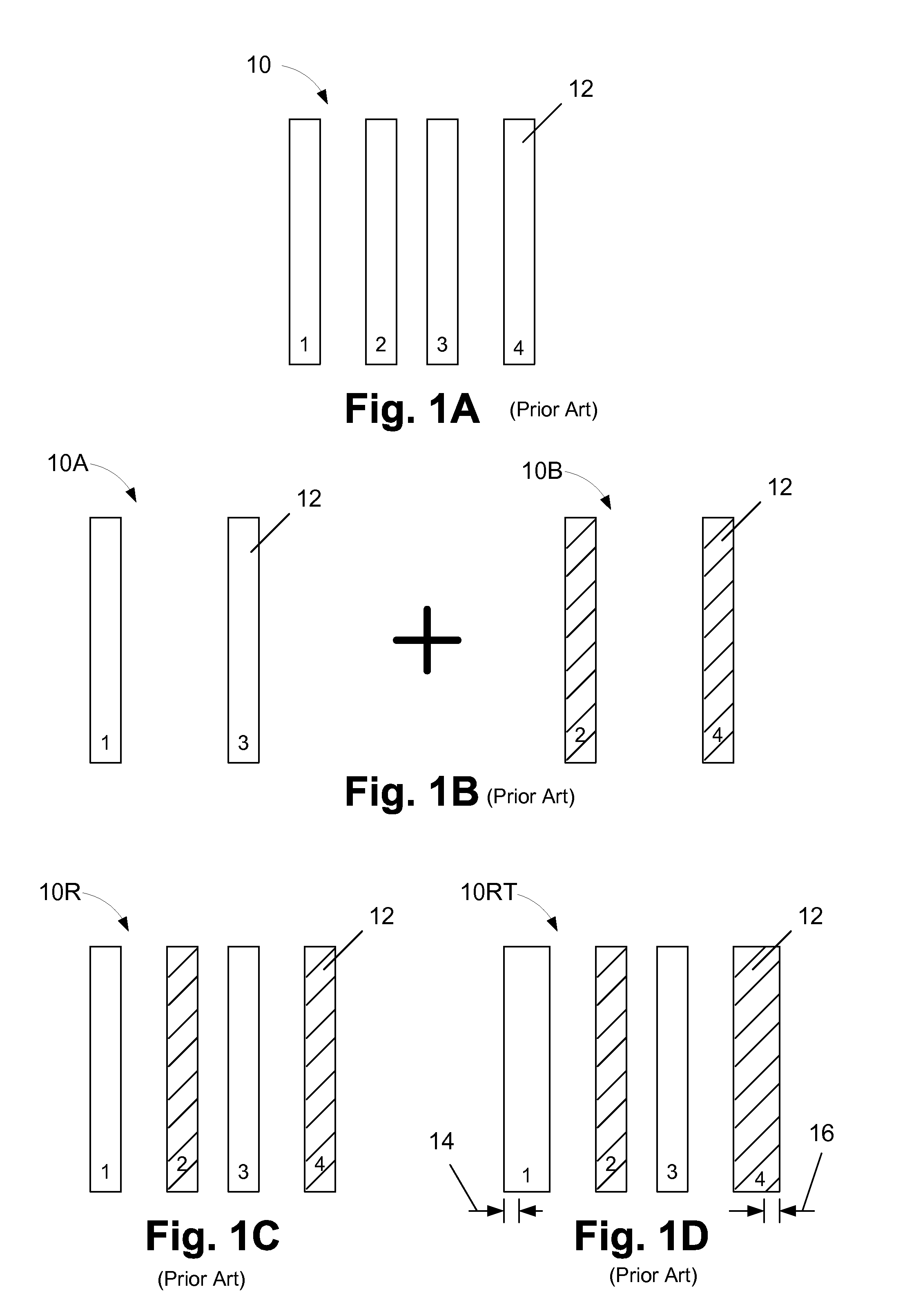
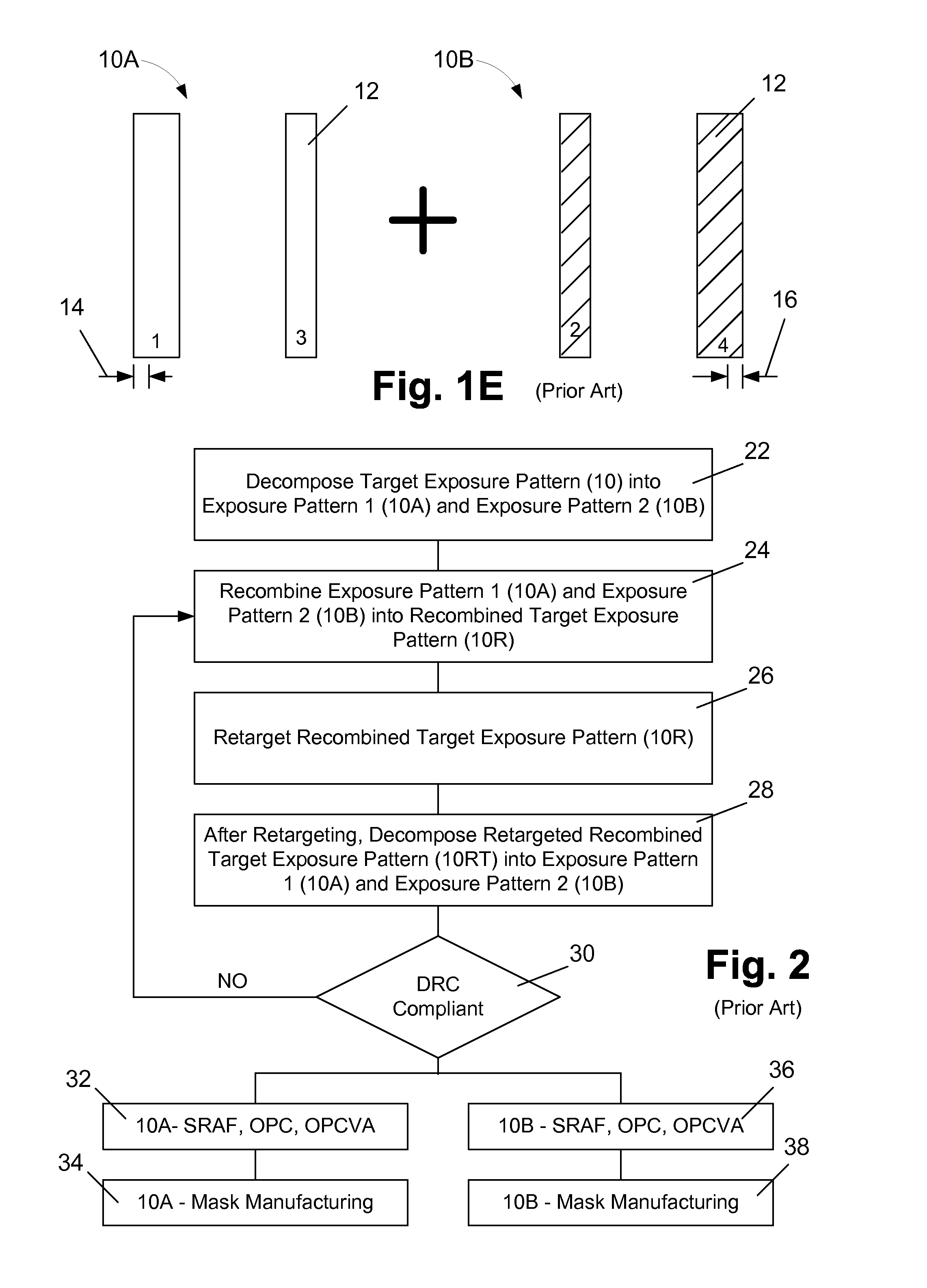
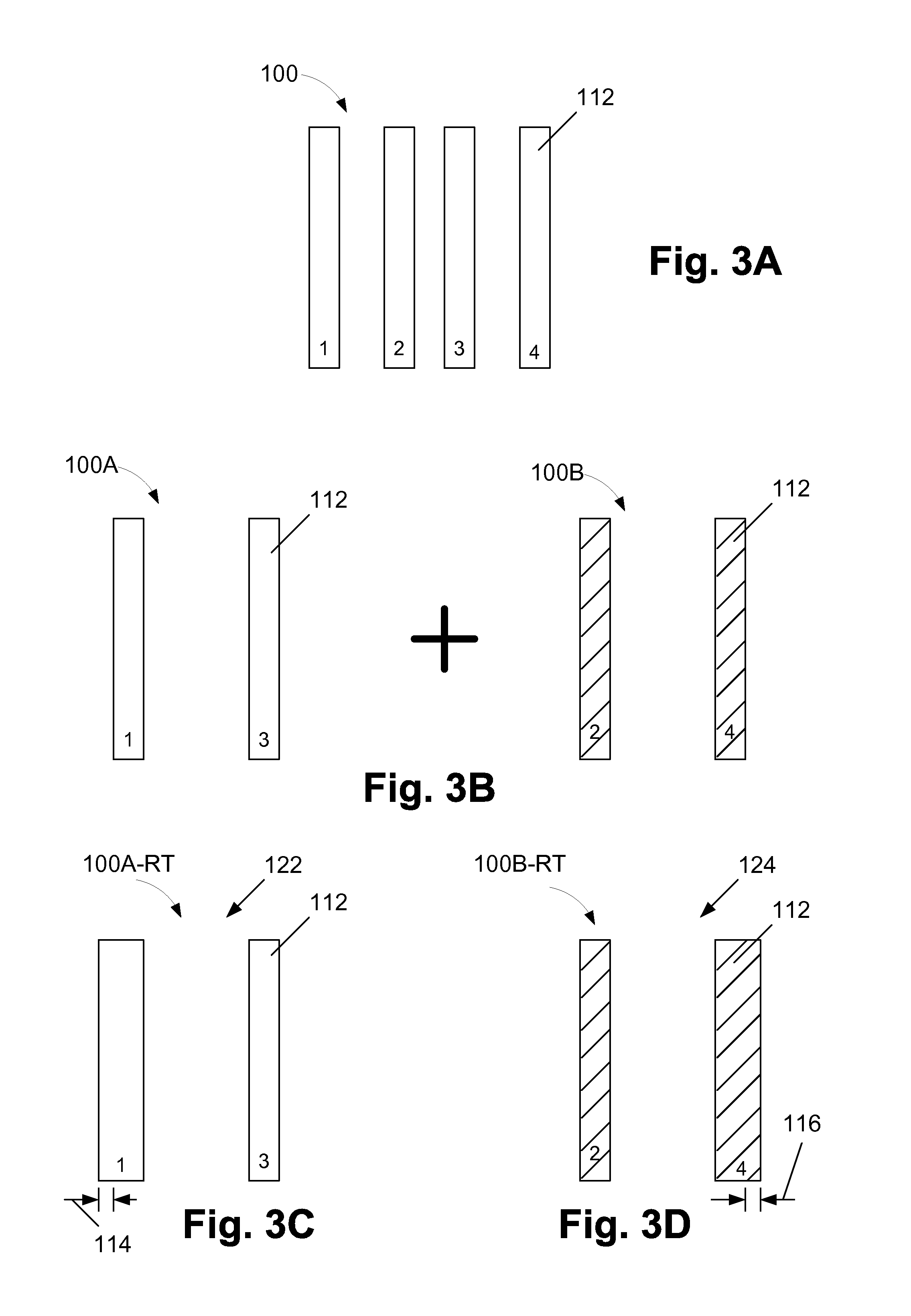
Methods involving color-aware retargeting of individual decomposed patterns when designing masks to be used in multiple patterning processes
InactiveUS8921016B1Originals for photomechanical treatmentSpecial data processing applicationsAlgorithmRetargeting
One illustrative method disclosed herein includes the steps of decomposing an initial overall target exposure pattern into at least a first decomposed sub-target pattern and a second decomposed sub-target pattern, performing first and second retargeting processes on the first and second decomposed sub-target patterns while using the other sub-target pattern as a reference layer, respectively, to thereby define retargeted first and second decomposed sub-target patterns, respectively, and, after performing the first and second retargeting processes, performing at least one process operation to determine if each of the retargeted first decomposed sub-target pattern and the retargeted second decomposed sub-target pattern is in compliance with at least one design rule.
Owner:GLOBALFOUNDRIES INC
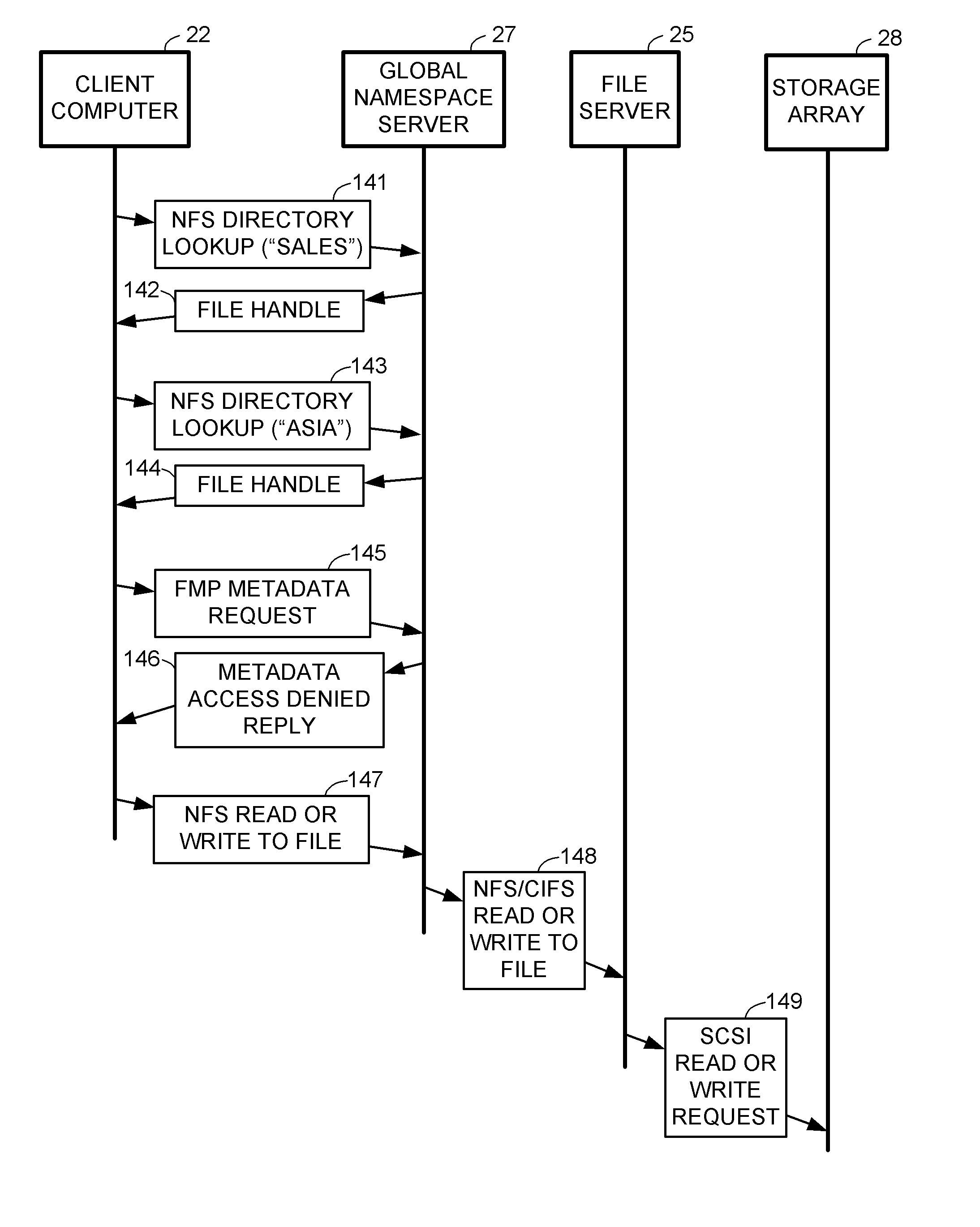
Scalable global namespace through referral redirection at the mapping layer
ActiveUS7937453B1Increase speedDigital data information retrievalDigital data processing detailsVirtual file systemStorage area network
Client computers, a namespace server, and file servers are linked in a data network so that the namespace server provides the clients with NFS or CIFS access to a virtual file system including files stored in the file servers, and also provides migration of files between the file servers in a fashion transparent to the client access using NFS or CIFS. The client computers and storage arrays storing the file data are also linked in a storage area network so that the clients have high speed block access to the file data using a file mapping protocol. The namespace server redirects a metadata access request in the file mapping protocol from a client to the appropriate file server when the file is not being migrated, and otherwise denies the metadata access request when the file is being migrated so that the client reverts to NFS or CIFS access.
Owner:EMC IP HLDG CO LLC
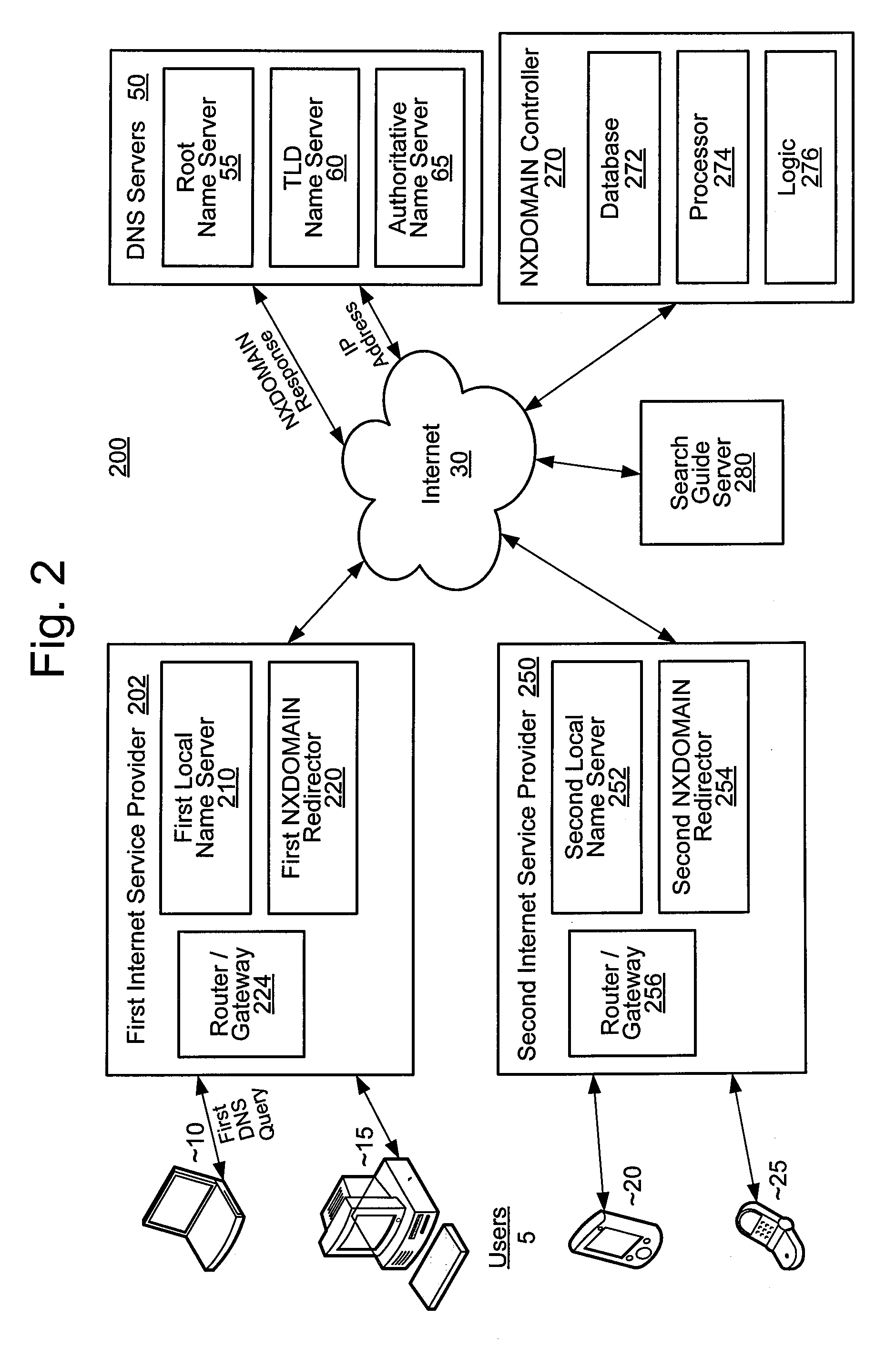
System and method for controlling non-existing domain traffic
A system and method for controlling internet traffic controls internet traffic directed to a non-existing domain in a centralized manner. Instead of a non-existing domain response, the user may receive alternative responses such as a landing page including useful information and resourceful suggestions under the control of a global controller. The centralized control over the user's request may be implemented by redirecting a DNS query to the global controller or an optimal search guide server at an individual internet service provider level. Redirection of the DNS query may involve a record modification of a domain name resolution response indicating the non-existing domain.
Owner:HOSTWAY CORP
Enhanced Features for Direction of Communication Traffic
InactiveUS20080201413A1Avoid problemsMultiple digital computer combinationsAutomatic exchangesTraffic capacityWeb browser
An internet traffic redirection architecture is disclosed that allows for directing of various traffic to specified sites. The system and method allow a controller, such as an ISP, to benefit from unresolved IP Address requests and keyword and hotword queries by capturing this traffic and directing it to participating partners who provide content relevant and / or geographically relevant results. The system and method can decrease lost traffic, irrelevant redirection by web browsers resident on user's personal computers. The technique further provides enhanced features at the ISP network level which are conventionally only available at the personal user level.
Owner:PAXFIRE
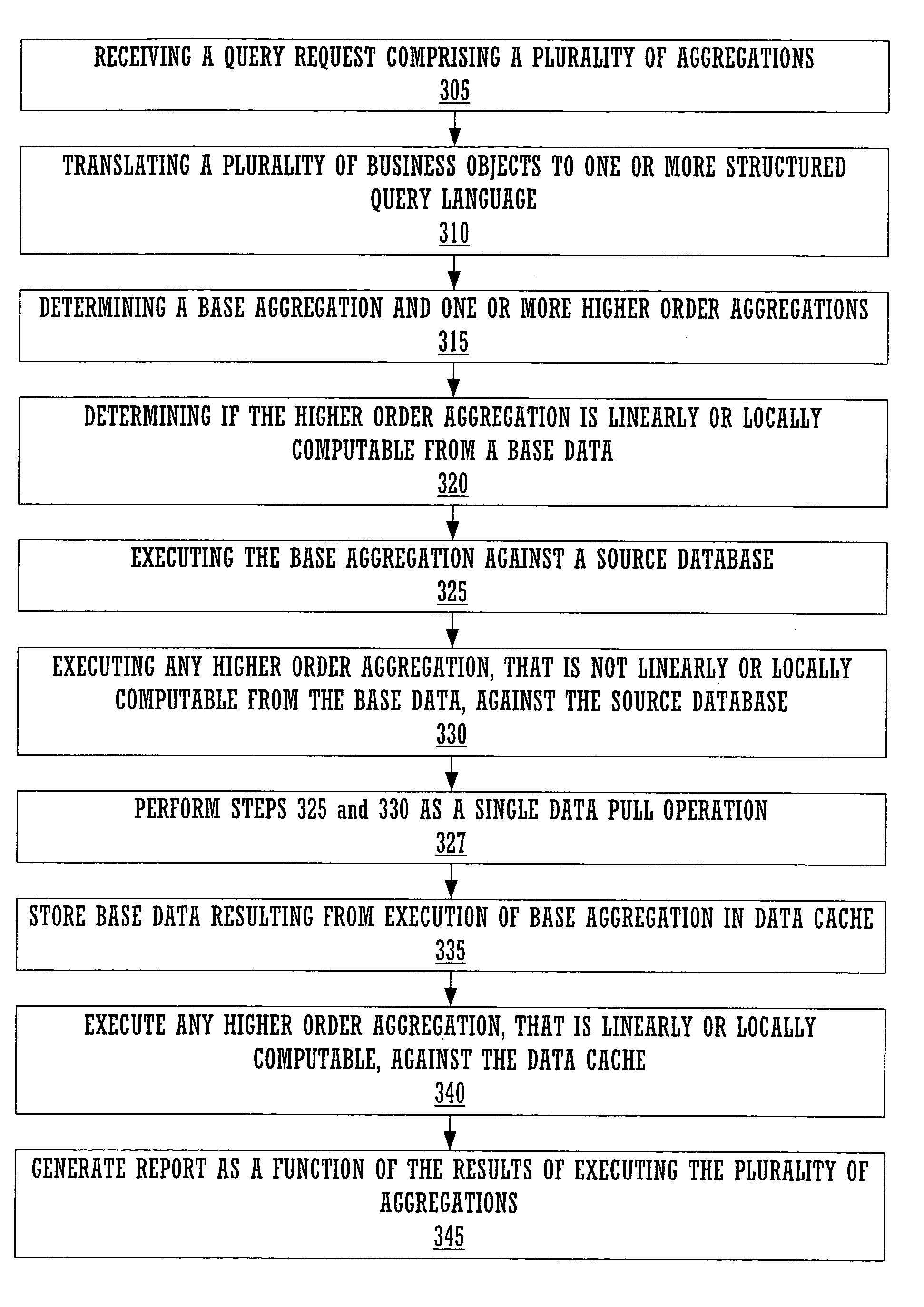
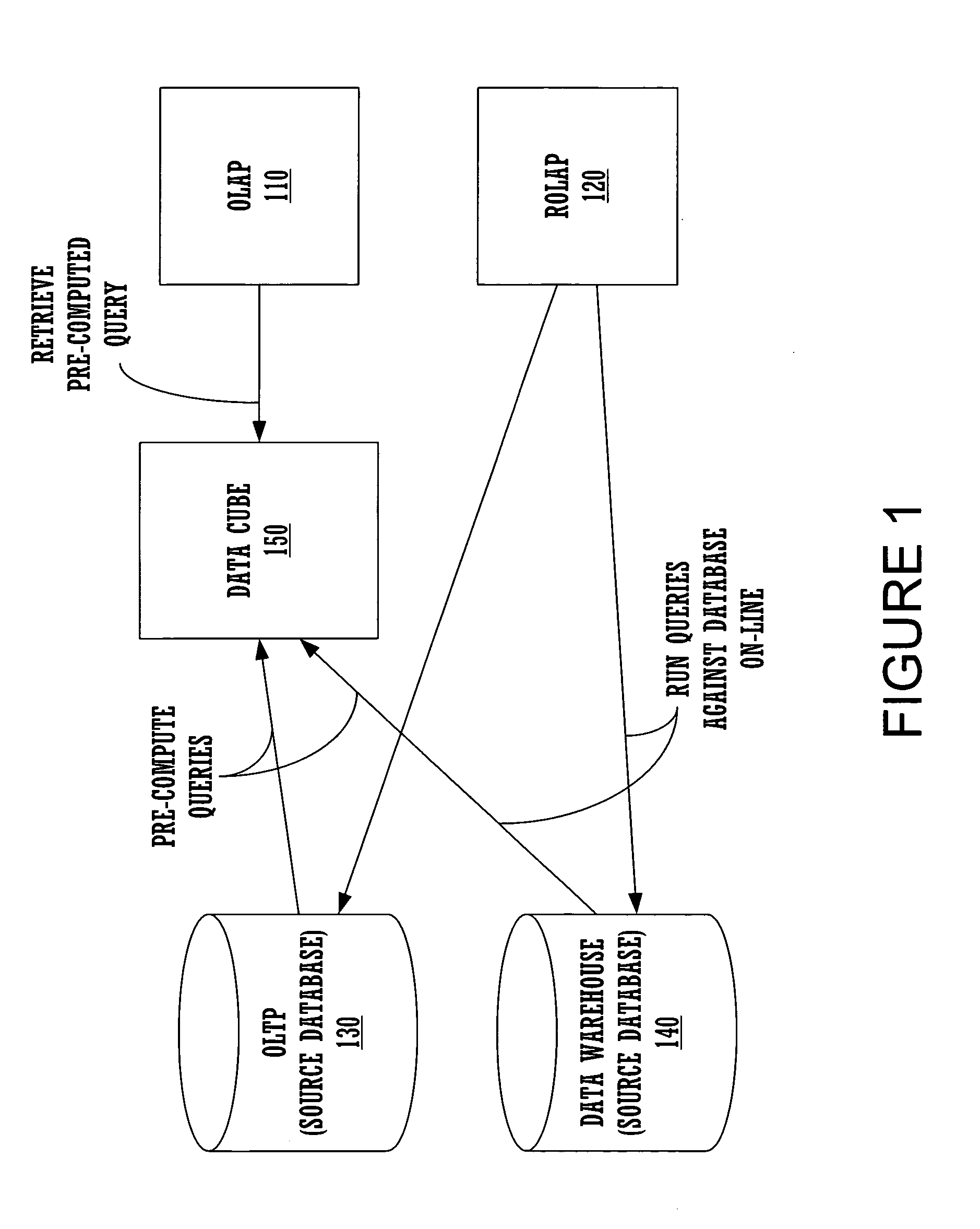
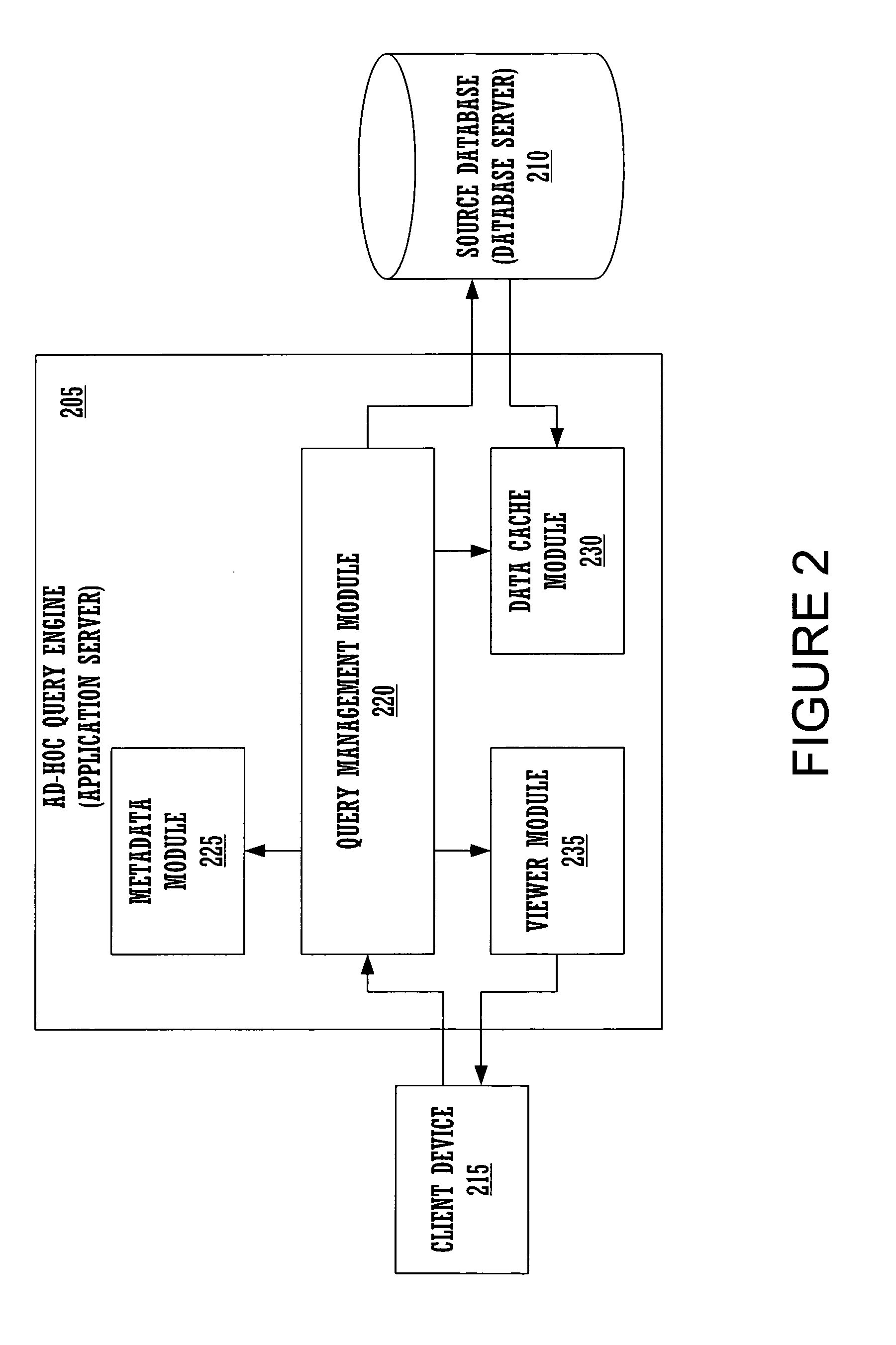
Enhanced ad-hoc query aggregation
ActiveUS7110997B1Reduce utilizationImprove performanceData processing applicationsDigital data information retrievalClient-sideQuery language
Embodiments of the present invention provide an ad-hoc query engine. The ad-hoc query engine comprises a query management module, a metadata module, a data cache module and a viewer module. The query management module receives a query request from a client device. The query request is specified in terms of a plurality of business objects. The query management module utilizes the metadata module to translate the business objects into a structured query language statement as a function of the content of the data cache module. The SQL statement comprises a plurality of aggregation. The query management module dynamically causes each aggregation to be re-directed to execute against the content of the data cache module, when the aggregation is locally or linearly computable from said content of said data cache module. The query management utilizes the viewer module to generate a report as a function of the results of the executed SQL statement.
Owner:ORACLE INT CORP
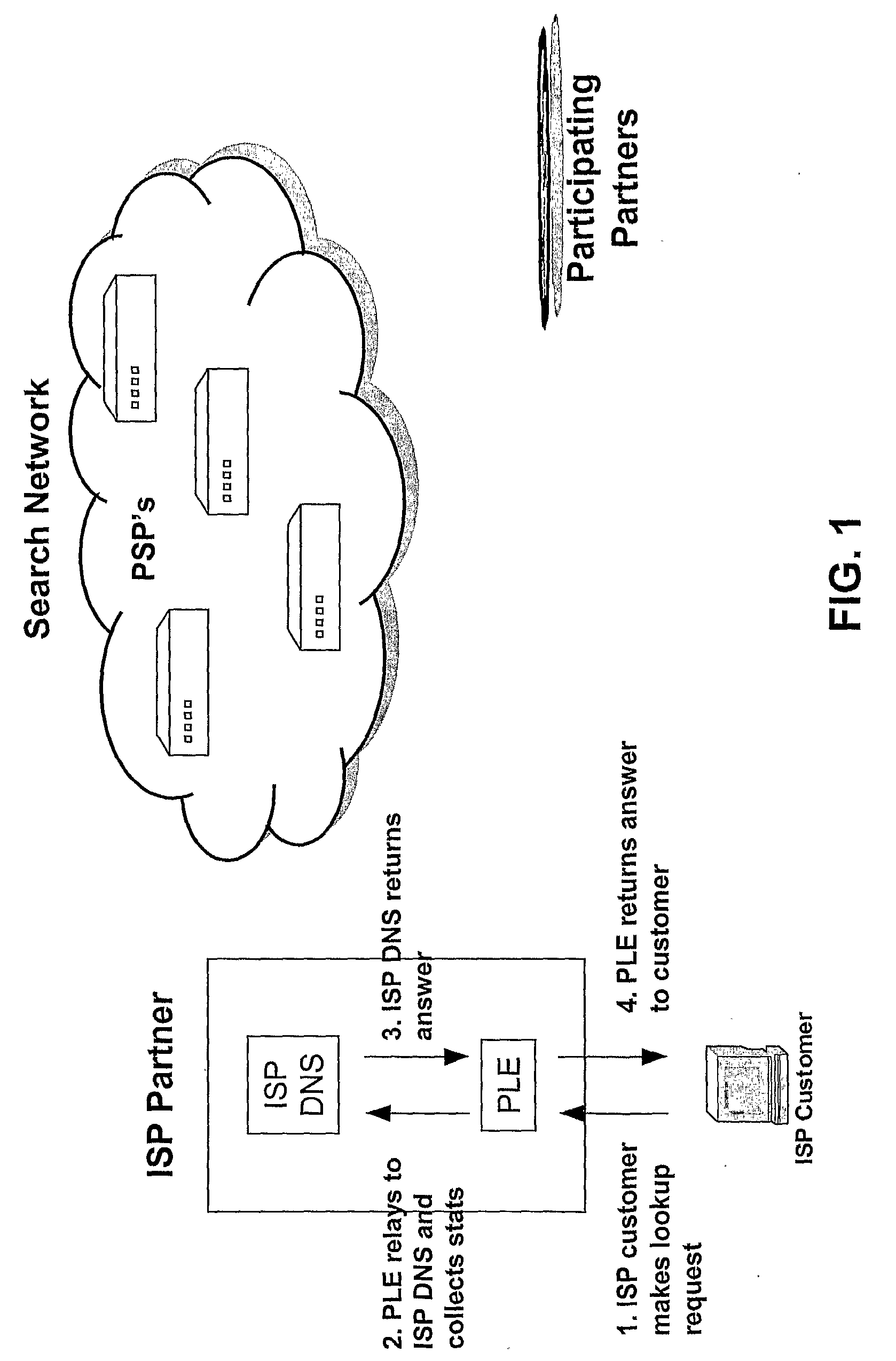
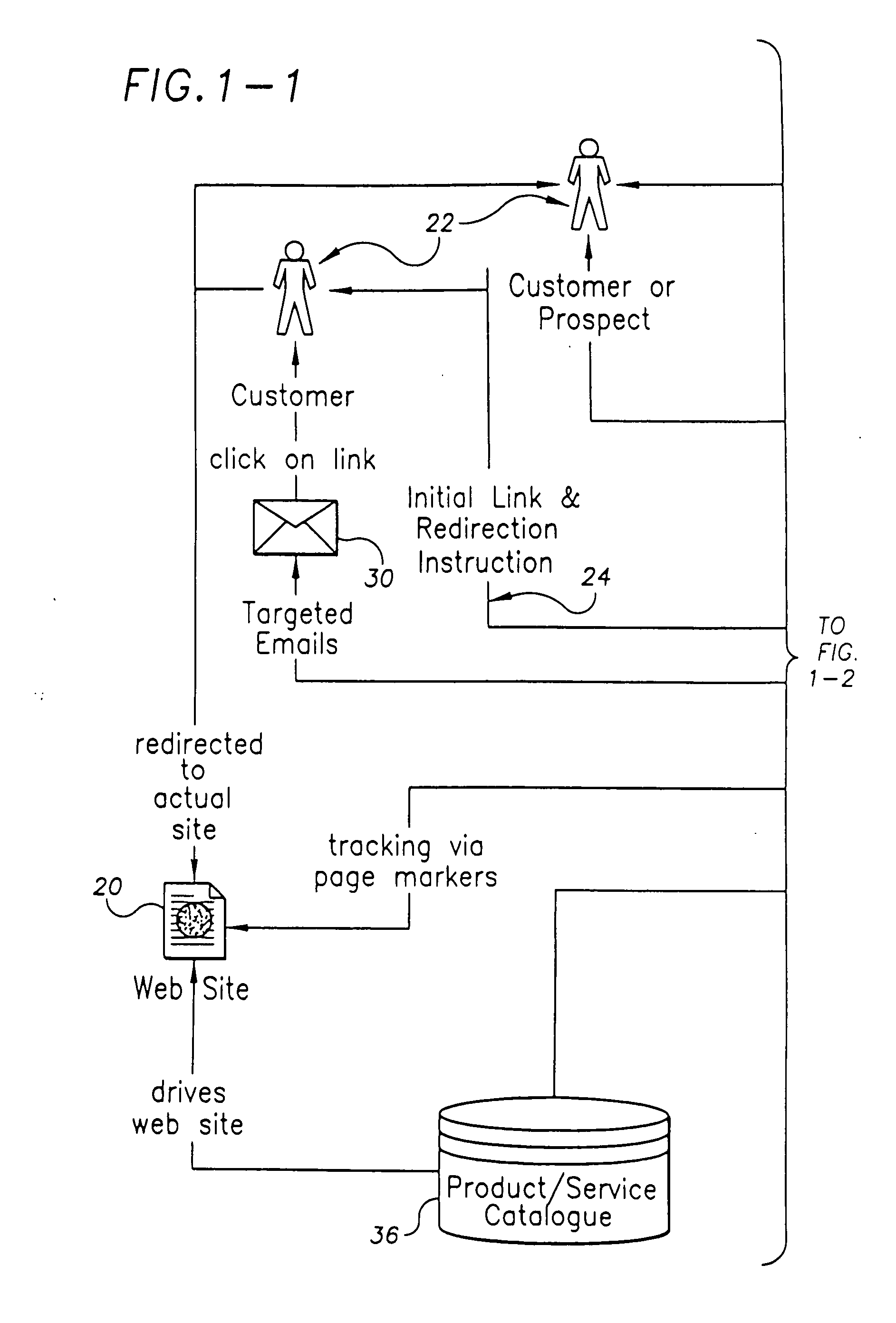
Method and system for enhanced Web page delivery and visitor tracking
InactiveUS20060248452A1Enhancing web page deliveryReduce deliveryWebsite content managementMarketingWeb siteWeb traffic
A system for and method of enhancing web page delivery and visitor tracking. The invention provides the ability to control redirection of Web traffic of humans. It can identify visitors to a Web page, track their movements, log critical information, and analyze the Web traffic in order to judge the success in driving quality traffic to some known goal on a Web site, such as a sale. The system tracks visitors via use of redirection with an image tag. The invention can also use unique image marker references to prevent browsers from accessing cached images.
Owner:THRYV INC
Method, computer program product, and system for non-blocking dynamic update of statically typed class-based object-oriented software
ActiveUS20110283256A1Efficient forwardingSoftware engineeringSpecific program execution arrangementsSoftware updateInit
Under the present invention, a method, computer program product, and system for non-blocking dynamic update of statically-typed class-based object-oriented software executing as byte-code on a virtual machine within an actively running computer system is provided. A set of objects instantiated from an existing module or multiple modules (identifiable collections of application resources and class definitions in the form of byte-code representations) is ready for execution on a virtual machine in an actively running computer system. New versions of one or more modules corresponding to those already loaded into the actively running virtual machine are dynamically loaded into the virtual machine for the purpose of updating the running software. The class definitions within the loaded modules are prepared for dynamic update by inserting byte-code that enables; transparent state transfer and shared object identity between objects of a former version and the new version of a class. On the event of a software update, the objects instantiated from a former version of an updated class become un-initialized surrogate objects with the potential to redirect to their future corresponding objects. Corresponding objects are created lazily on first access of the declaring class members. Besides lazy redirection of the behavior of objects and classes, non-blocking dynamic update is achieved by lazy migration of the state of former objects and classes while locking on a temporary field access lock. Thus, the algorithm for controlling field access and state migration is completely lock-free both before and after state migration; hence the performance degradation is minimal. Finally, any unreferenced objects are removed from memory.
Owner:ZEROTURNAROUND
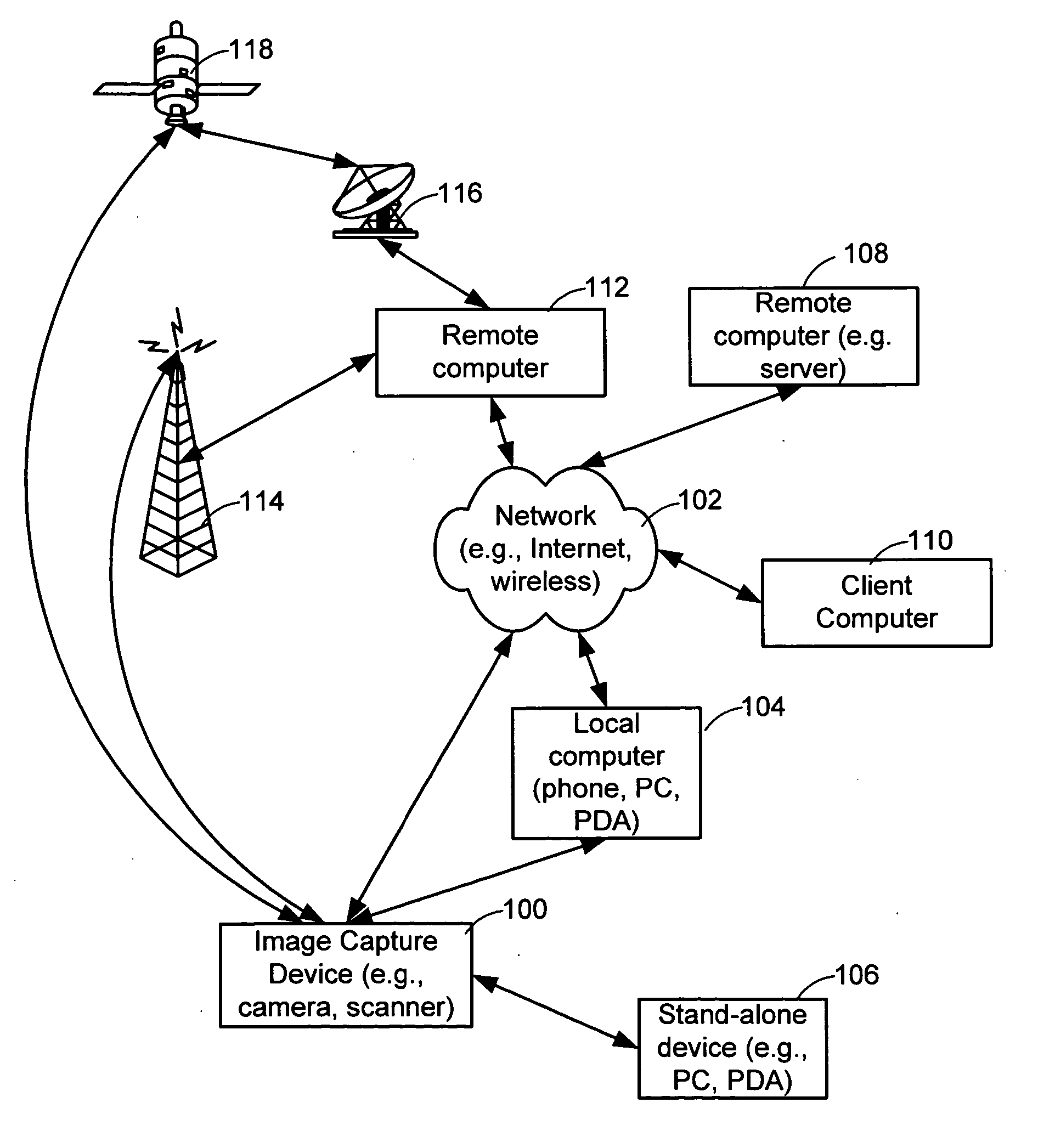
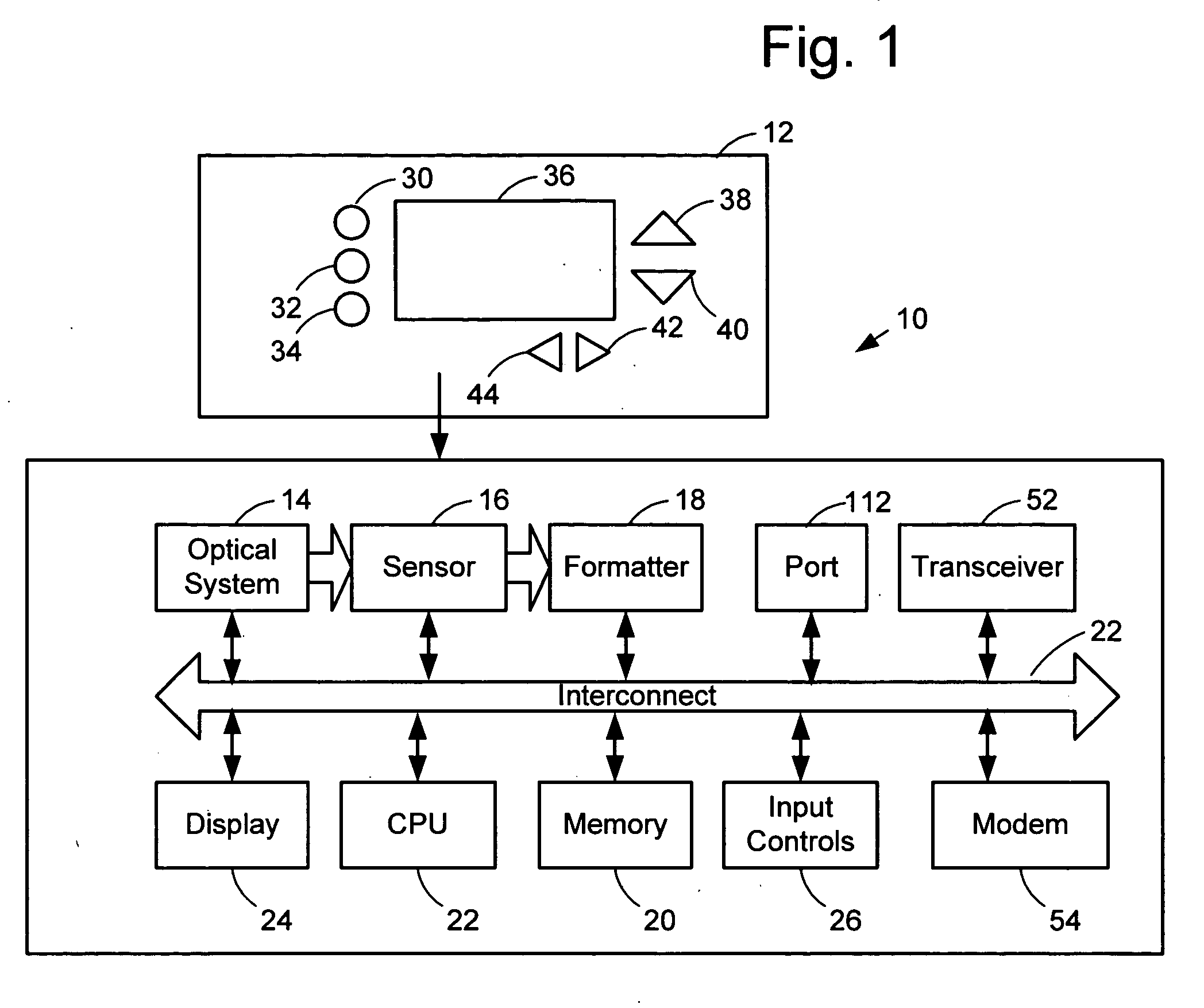
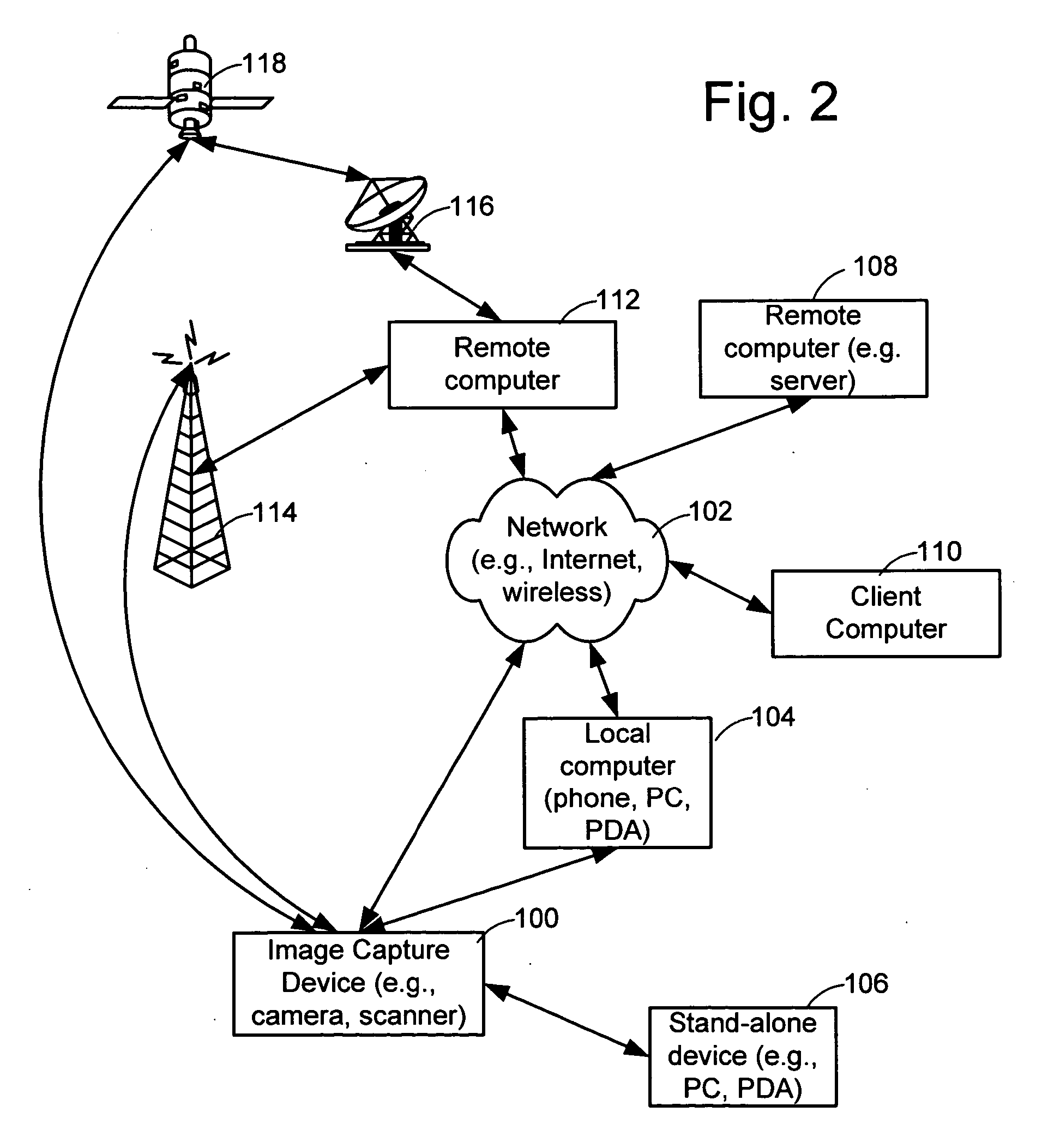
Retargeting a captured image to new hardware while in a pre-boot environment
ActiveUS7565517B1Facilitate computer executionError detection/correctionDigital computer detailsComputer hardwareComputer science
Methods are provided for retargeting captured images to new hardware. An image taken from a computer having hardware drivers and other system information in one hardware configuration can be modified to adapt it for use on a computer having different hardware requiring different drivers, even when the second hardware configuration was not known at the time of imaging. Systems and configured storage media for retargeting captured images to new hardware are also provided.
Owner:CA TECH INC
Apparatus, method and computer programming product for cable TV service portability
InactiveUS20040221305A1Television system detailsAnalogue secracy/subscription systemsConvertersComputer network
Owner:IBM CORP
User Location Dependent DNS Lookup
ActiveUS20100318631A1Save effortShorten the timeMultiple digital computer combinationsTransmissionWeb siteIp address
A system and method which may directly resolve a URL into the IP address of a web server running a regional website of a web service provider based on a user's geographic location. A user may type a URL of a website in his browser. A user location analyzer may decide the user's geographic location according to his IP address. With the user's geographic location, a DNS server may resolve the URL to a regional website of a web service provider which provides services specific to the user's geographic location. Consequently, the user may be presented a regional website of a web service provider without delays caused by re-directing, and save the user's time and effort to look for a regional website himself.
Owner:R2 SOLUTIONS
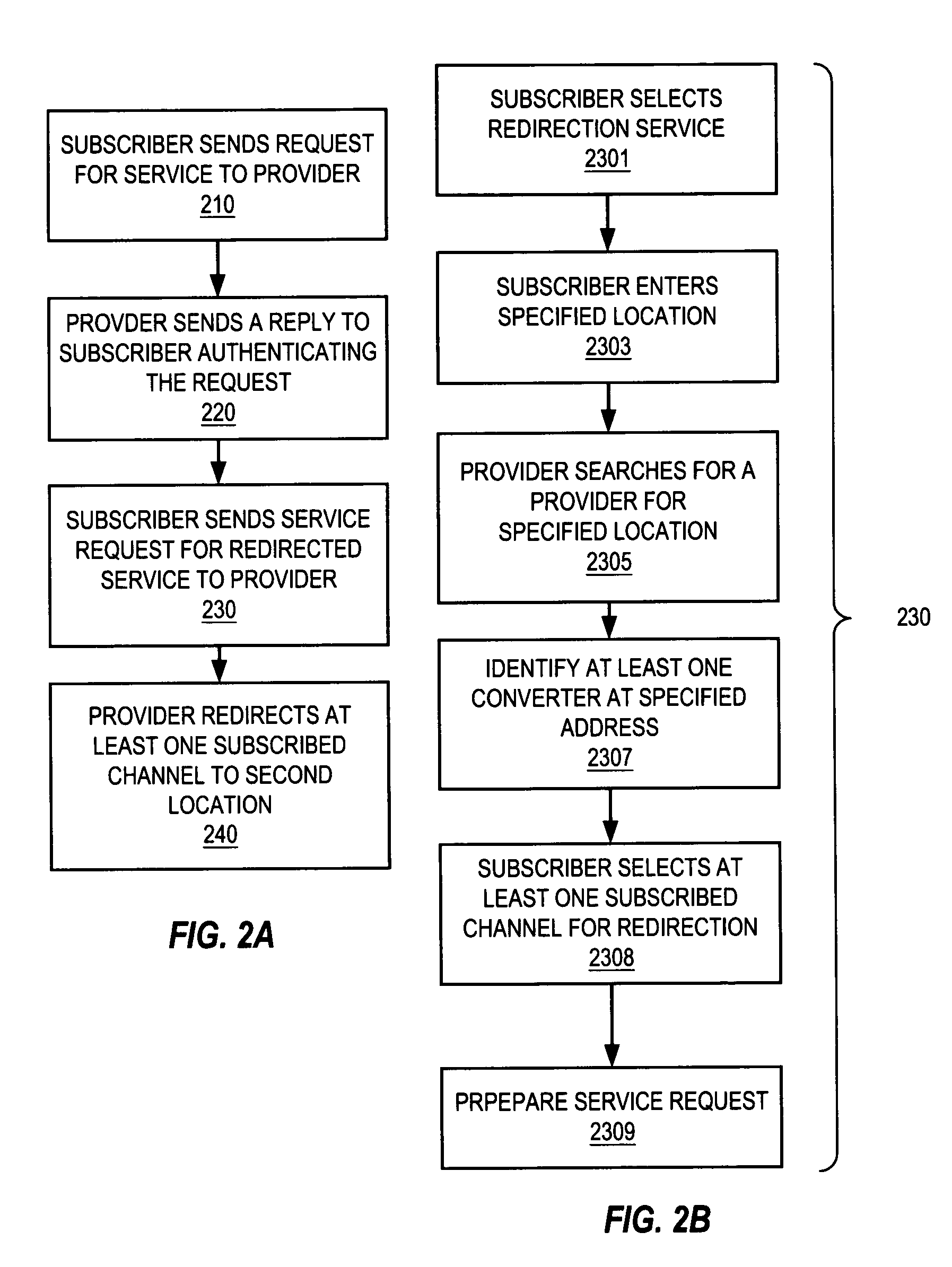
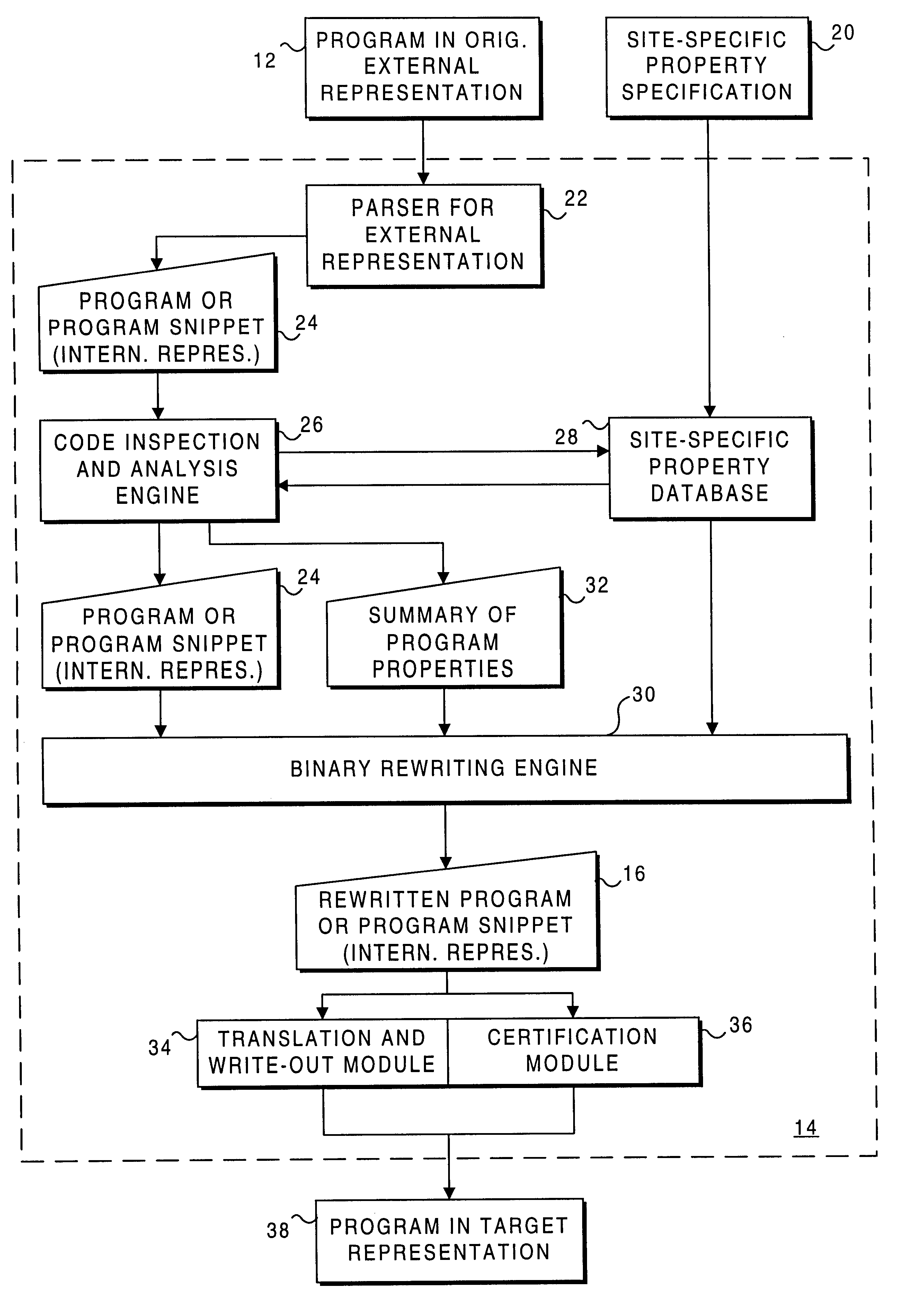
Process for rewriting executable content on a network server or desktop machine in order to enforce site specific properties
InactiveUS6865735B1Less processing overheadRun fastBinary to binaryMultiprogramming arrangementsProgram fragmentUnknown Source
A program or program snippet is rewritten to conform to site-specific properties prior to being executed by a target host. The program or program snippet directed to a target host from a known or unknown source is either intercepted by a server before reaching the target host or can be redirected from the target host to the server to effect its rewriting. The program is parsed in its external representation, converting it to an internal representation that is inspected and analyzed with reference to a site-specific properties database. A summary of the program's properties is then compared to the site-specific properties database by a binary rewriting engine, which produces a rewritten program in an internal representation. If appropriate, the program or program snippet is rewritten to convert it to a format suitable for execution on the target host. Furthermore, certifications may be added to the rewritten program to mark that the rewritten program obeys site-specific constraints. The rewriting service thus produces a program in an appropriate target representation that conforms to site-specific properties. These properties may relate to security, auditing, optimization, monitoring, threading, and / or management of the rewritten program.
Owner:UNIV OF WASHINGTON
Dynamic document context mark-up technique implemented over a computer network
InactiveUS7451099B2AdvertisementsAnalogue processes for specific applicationsUniform resource locatorClient machine
A technique is disclosed for generating markup information to be displayed on a client computer system. The client system includes memory configured to store at least one update file which comprises keyword information relating to keywords suitable for markup. In one implementation, the update file is generated at a remote server system and downloaded to the client system. When a new document (e.g. a web page) is displayed on the client system to an end user, selected context associated from the document is analyzed for selected keywords. In a specific implementation, the selected keyword information is provided by an entity other than the end user. Using the selected keyword information, specific context in the document is selected to be marked up. According to a specific embodiment, the selection of the document context to be marked up may be performed at the client system. Markup operations are then implemented at the client system on at least a portion of the selected document context, thereby resulting in marked up document context which has a visual appearance that is different than the appearance of the initial parsed context. Additionally, a pop-up advertisement may be automatically displayed on the client system based upon the identified context in the document. When the user clicks on a portion of the marked up document context, the user may be redirected to a target URL which was not included as part of the initial parsed document context. Alternatively, a pop-up window or layer which includes a plurality of different links may be displayed to the user.
Owner:AMOBEE
Data isolation system and method
InactiveUS7305577B2Memory loss protectionDigital data processing detailsSoftware engineeringData file
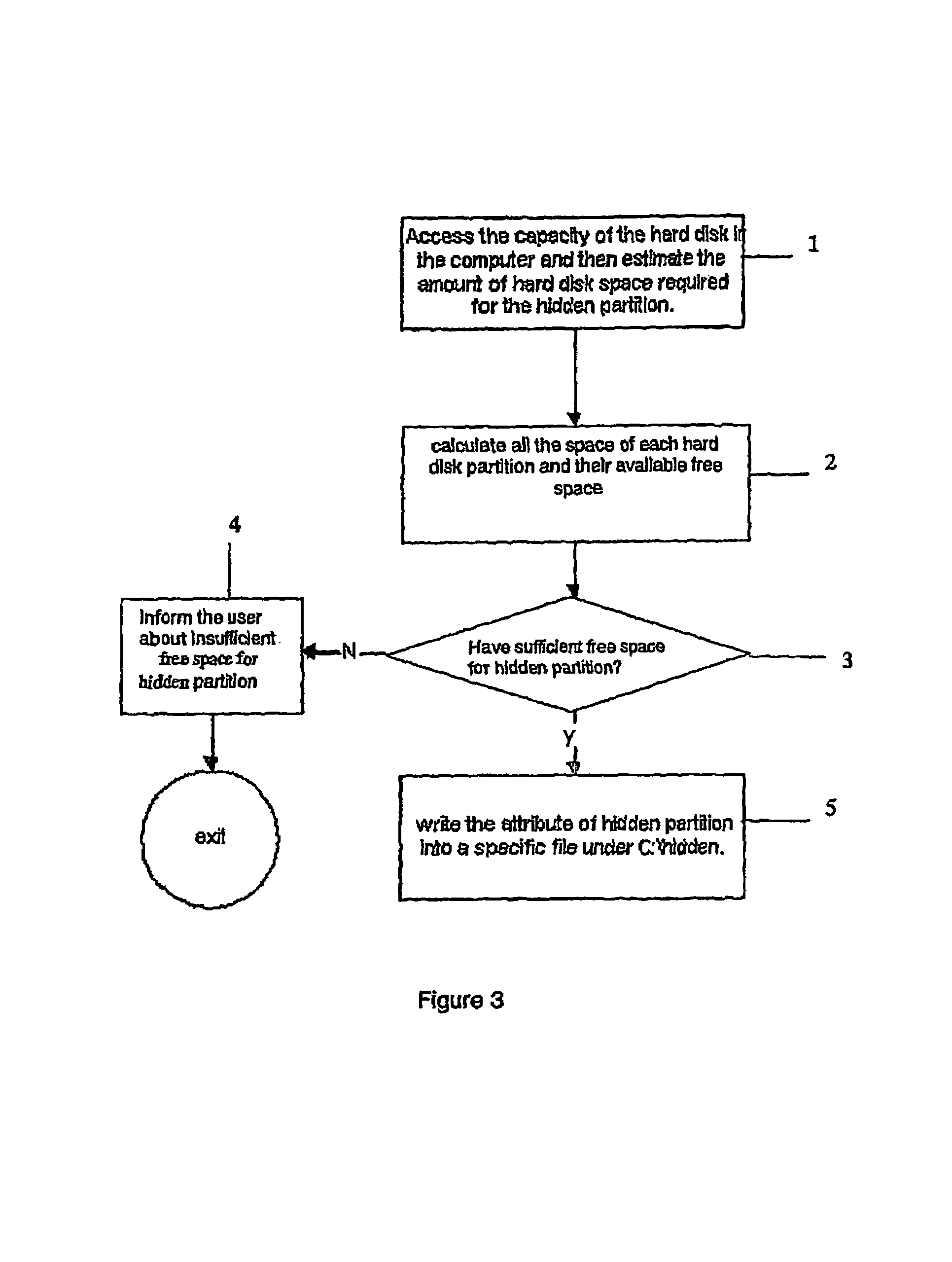
A data isolation system for software and data maintenance, back up and recovery for a computer wherein dynamic data files are identified and redirected or copied into a hidden partition (212) on a hard disk (210) of the computer. Automatic back ups are made to the dynamic data files in the hidden partition (212) whenever the dynamic data files are amended. The dynamic data files in the hidden partition (212) include the computer's operating environment so that the computer's operating environment can be restored from the dynamic data files in the hidden partition (212). The dynamic data files in the hidden partition (212) include data up to the time of a failure of the computer's system.
Owner:STAR SOFTCOMM PTE LTD
Database system with query interception and redirection
InactiveUS20110010379A1Lack capabilityDigital data processing detailsStructured data retrievalData storingData store
A database system includes: a first database having back-end functionality for data storage and database query execution, a database front-end and an interception unit. The database front-end is configured for processing user queries directed to a back-end of a second database, and lacks the capabilities for directly accessing the first database. The interception unit is networked with the first database over a data network, and is configured for monitoring user queries under processing by the front-end to identify queries pertaining to data stored in the first database, and redirecting the identified queries to the first database for execution. Thereby the functionality of the database front-end is provided for data stored in the first database.
Owner:XEROUND
Intercepting system API calls
InactiveUS6959441B2Minimizing performance impactMinimize impactMultiprogramming arrangementsSpecific program execution arrangementsVirtual memoryBiological activation
A system for intercepting API calls in a virtual memory system comprises an activation module comprising an executable program and an interception module comprising a dynamic link library (DLL). The activation module is first executed at system initialization time, its prime purposes being to: parse user configuration information supplied in a configuration file; act as a daemon to launch and thus retain the interception module in shared memory; and hook system APIs to redirect calls via the interception module.
Owner:IBM CORP
Remoting redirection layer for graphics device interface
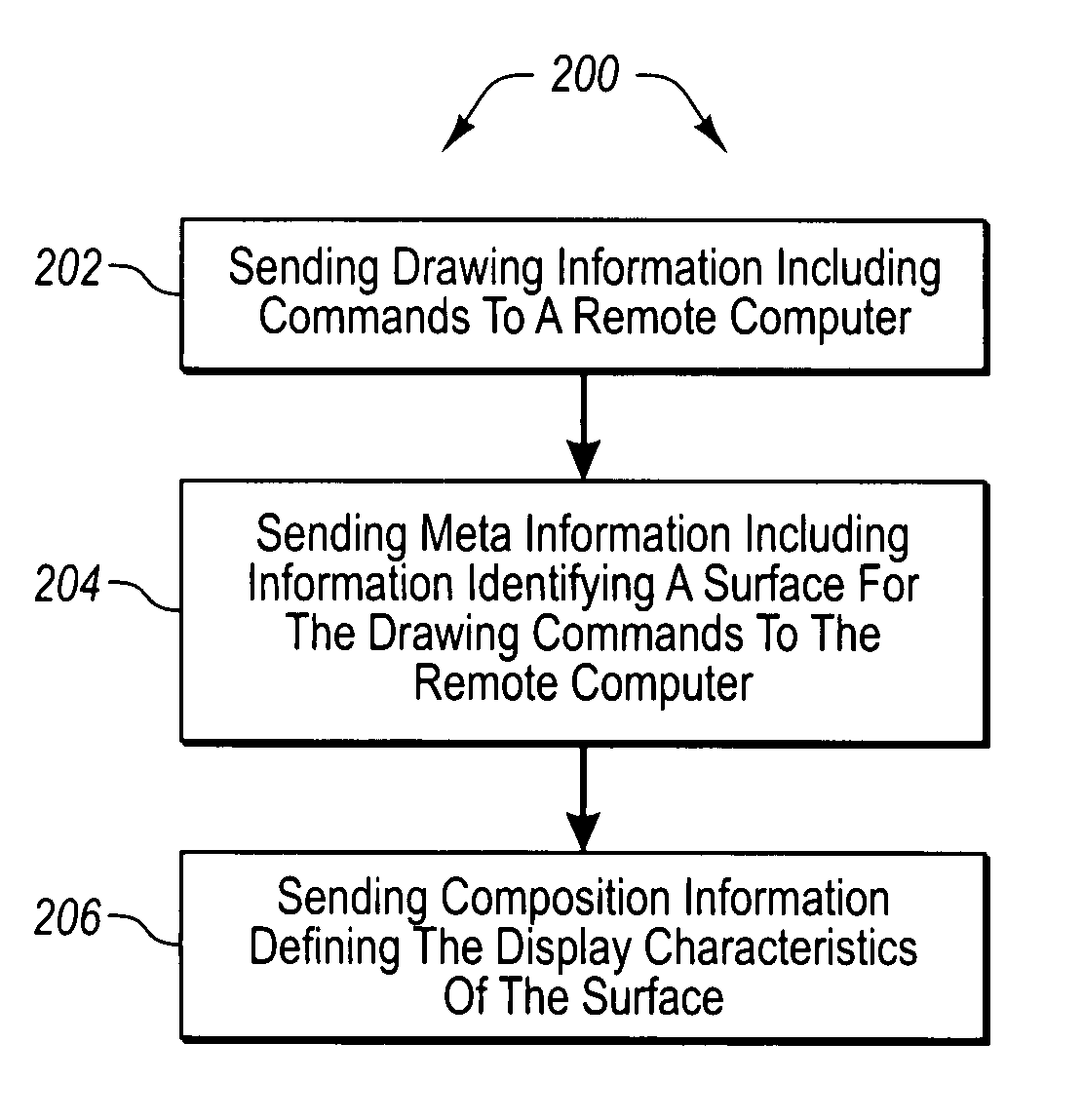
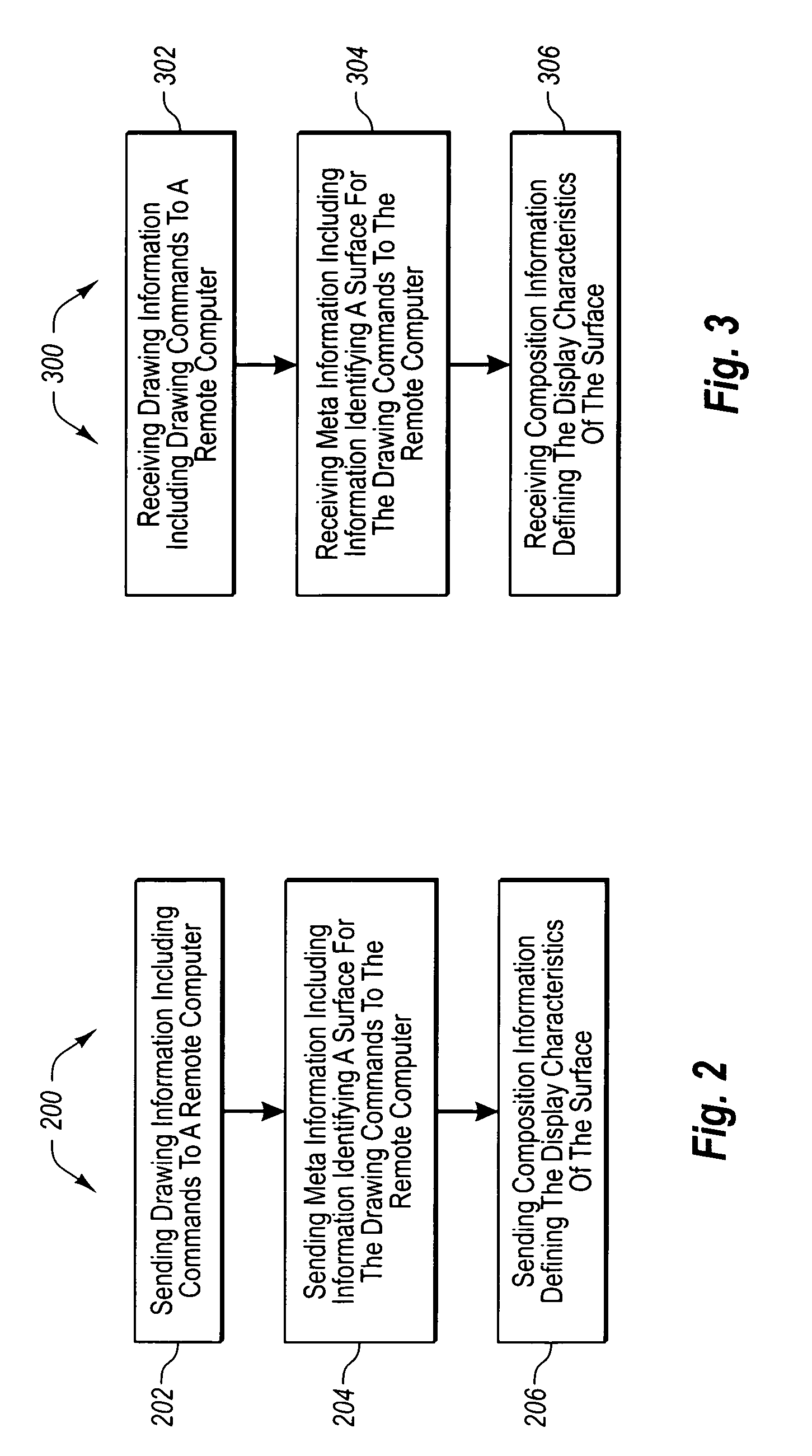
Remoting a display. A method that may be practiced, for example, in a networked computing environment including a local computer system running one or more applications and a remote computer that displays graphical information to a user for the one or more applications at the local computer system. The remote computer includes a number of surfaces. Drawing information including drawing commands is sent to the remote computer. Meta information is sent to the remote computer defining information about which surface from among the number of surfaces the drawing information applies. Composition information is sent to the remote computer defining the display characteristics of the surface.
Owner:MICROSOFT TECH LICENSING LLC
Attitude control system for small satellites
Various embodiments of the present invention include an attitude control system for use with small satellites. According to various embodiments, the system allows rapid retargeting (e.g., high slew rates) and full three-axis attitude control of small satellites using a compact actuation system. In certain embodiments, the compact actuation system includes a plurality of single-gimbaled control moment gyroscopes (SGCMG) arranged in a pyramidal configuration that are disposed within a small satellite.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com