Method for processing hidden process based on hardware simulator
A technology of hiding processes and emulators, applied in the field of network security, can solve problems such as low accuracy, low degree of virtualization of analysis technology, and dependence on the integrity of operating system kernel data, etc., to achieve the effect of ensuring transparency and improving transparency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
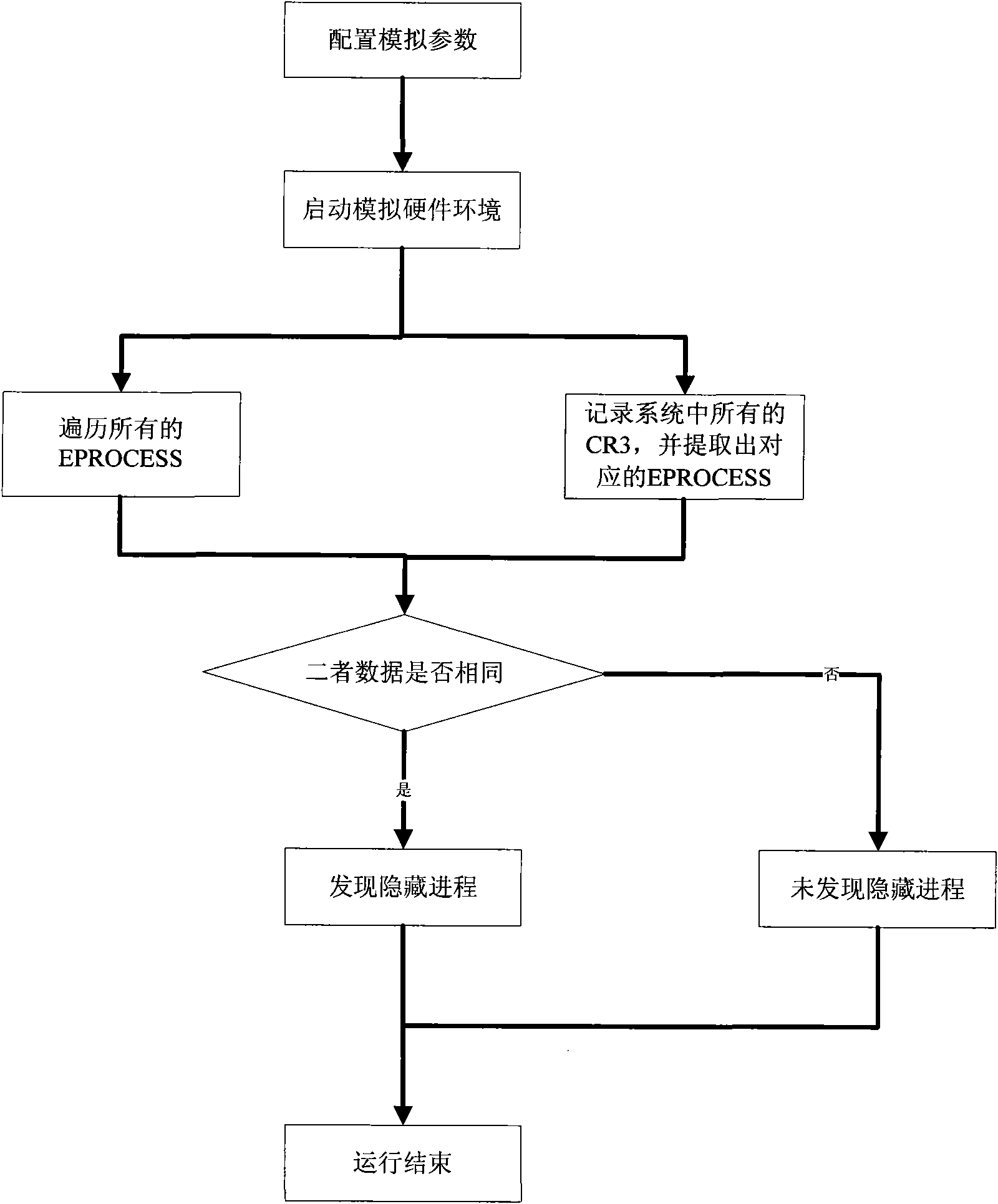
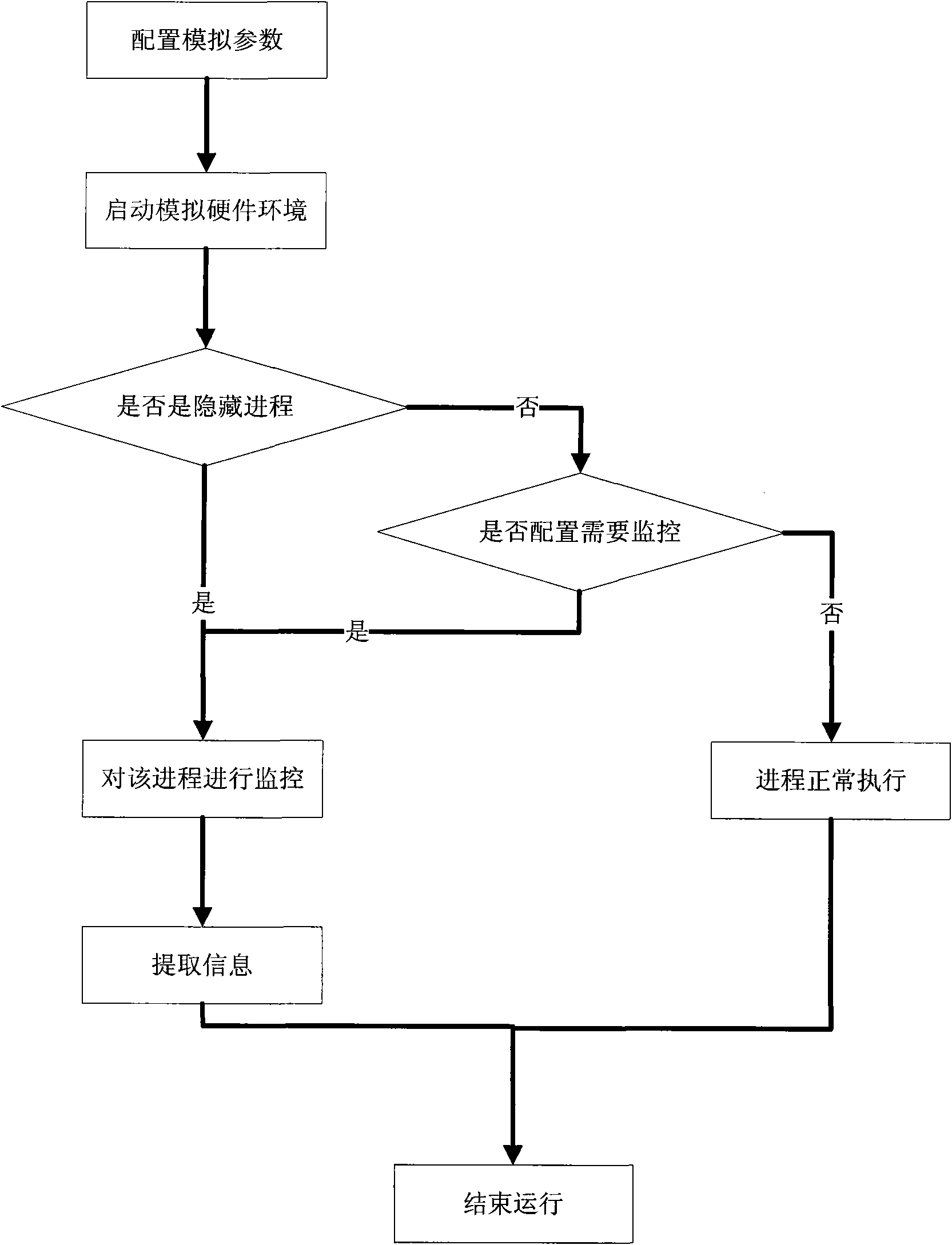
[0036] like figure 1 As shown, a method for processing a hidden process based on a hardware simulator includes steps:
[0037] 1. Create the operating system image required for the target file to run
[0038] The present invention adopts a linear addressing method to read all the contents of the disk where the target sample suspected of having malicious code is located. According to the sorting of all data blocks on the hard disk partition, the blocks are read from the hard disk, and then according to the order of their serial numbers, the read data is added to a file in sequence, and the file is used as a virtual hard disk to obtain hardware The data image file recognized by the simulator.
[0039] 2. Configure and start the hardware emulator
[0040] Configure the image path to obtain the location of the actual running operating system image; conf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com