Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
69results about How to "Preclude obtaining" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
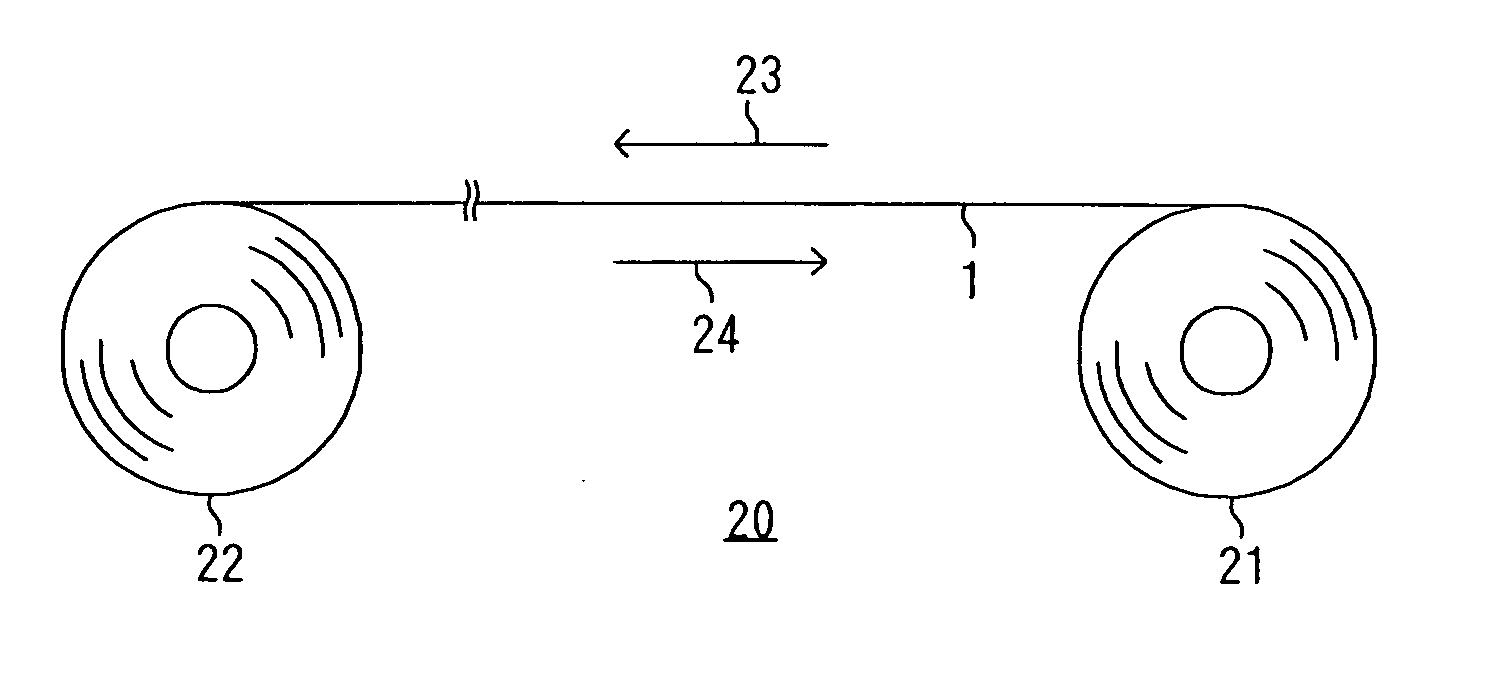
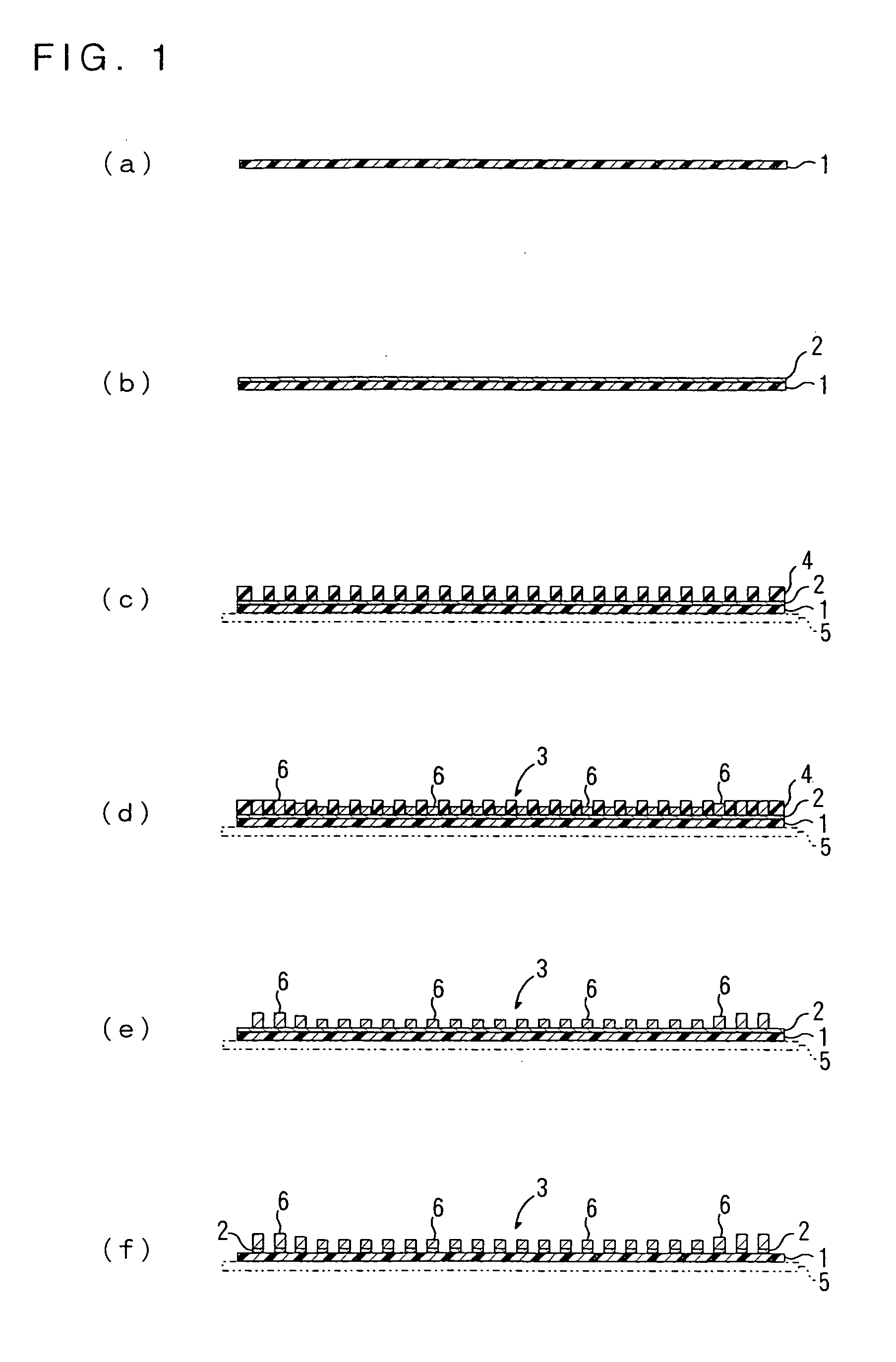
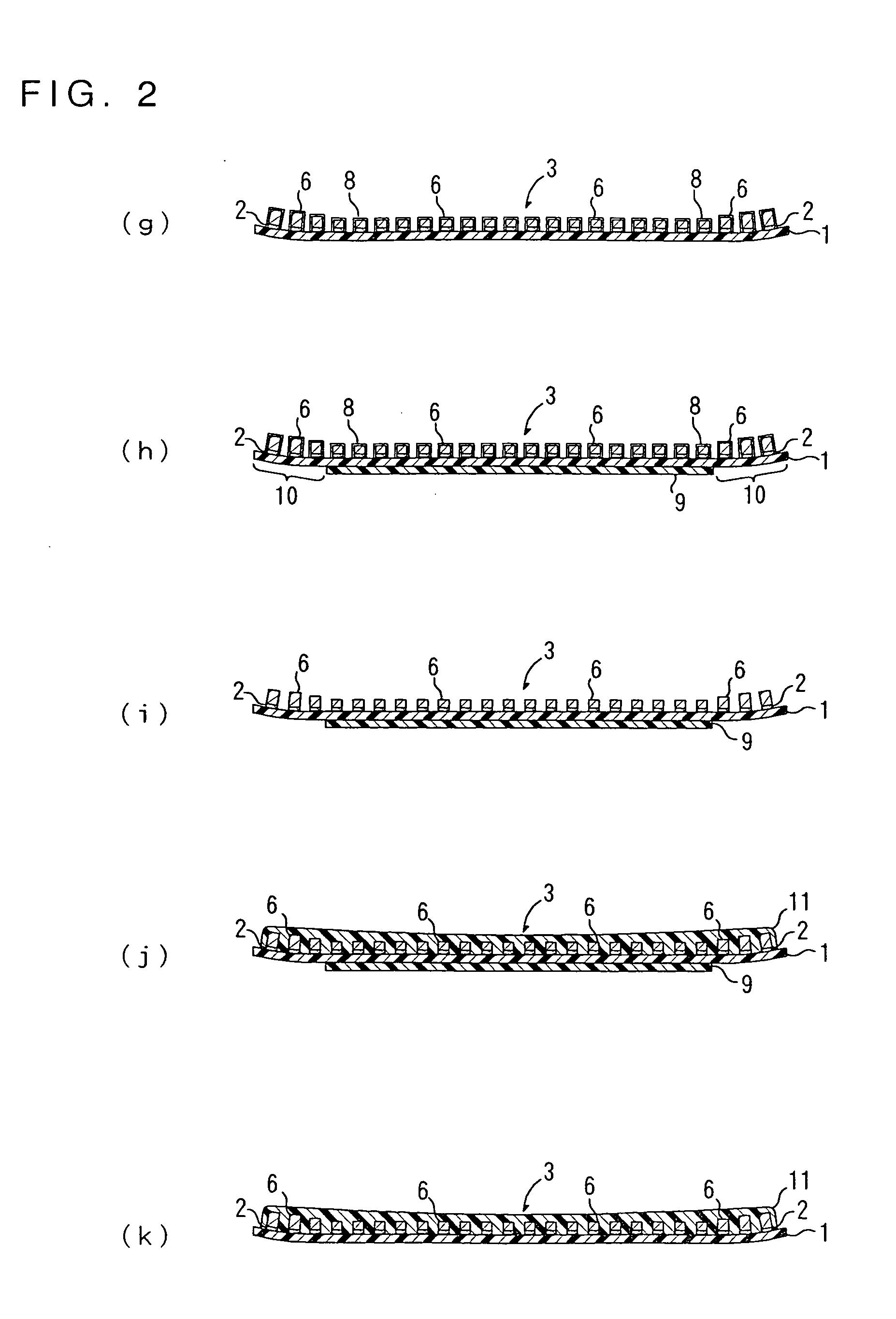
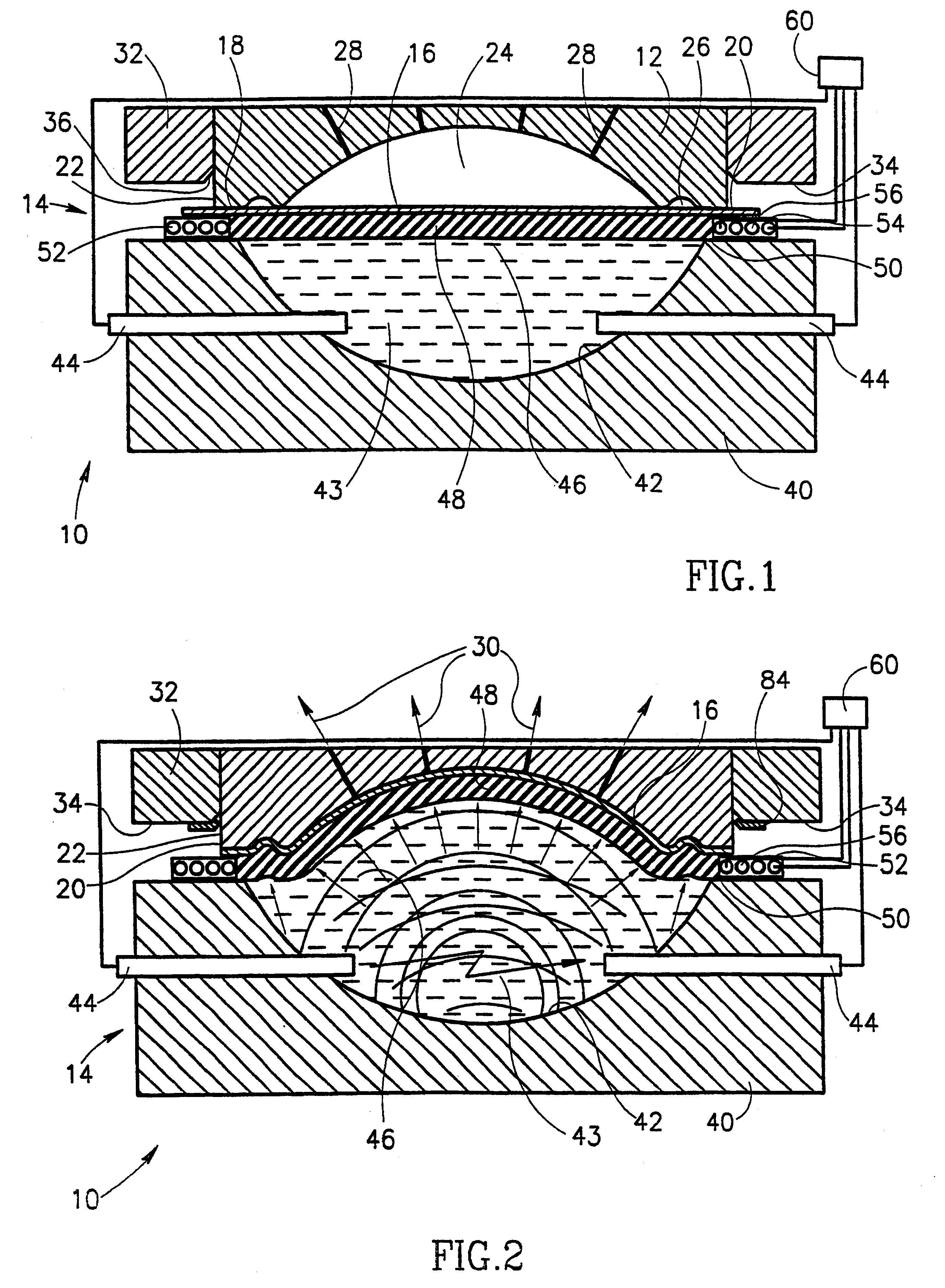
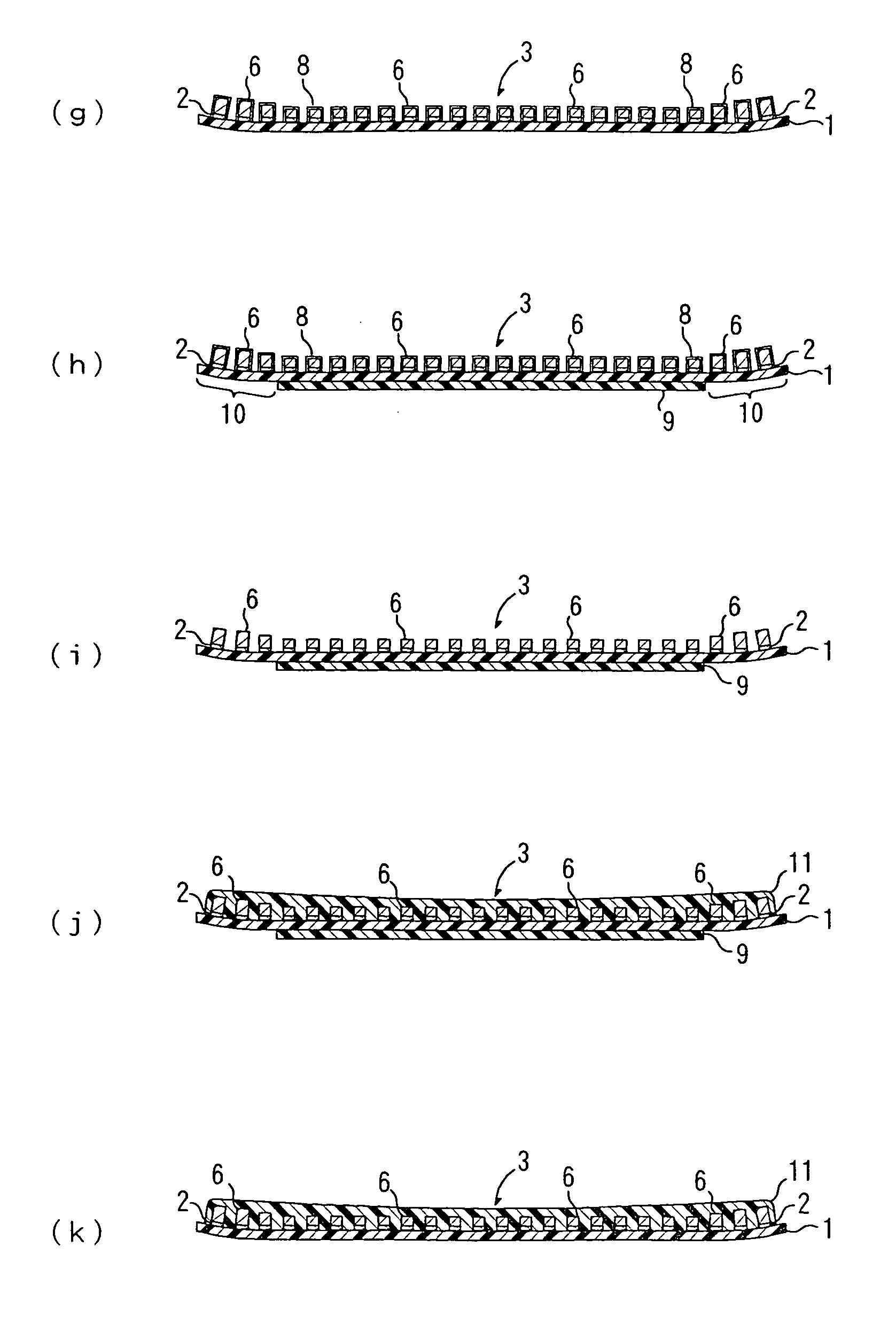
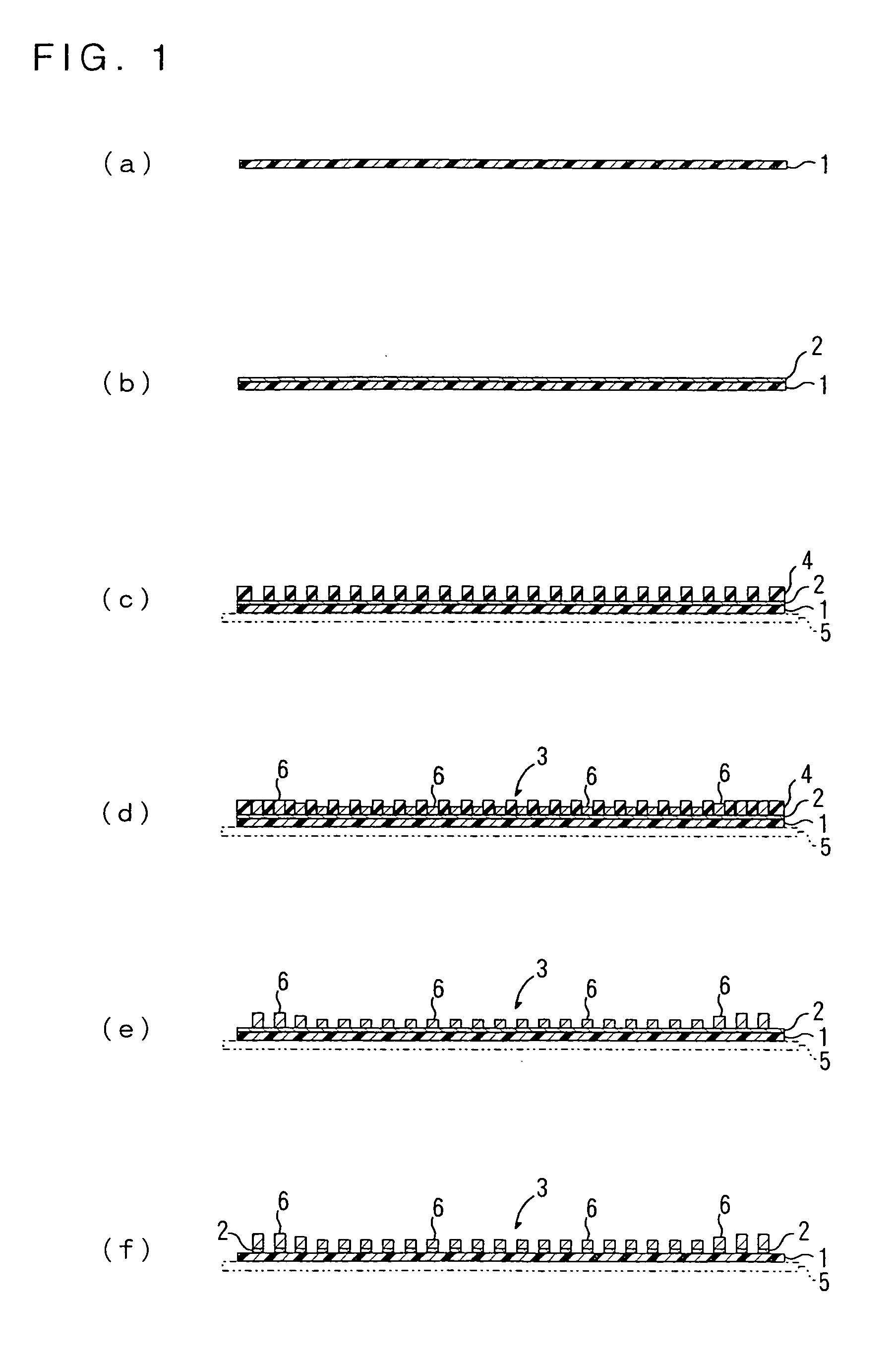
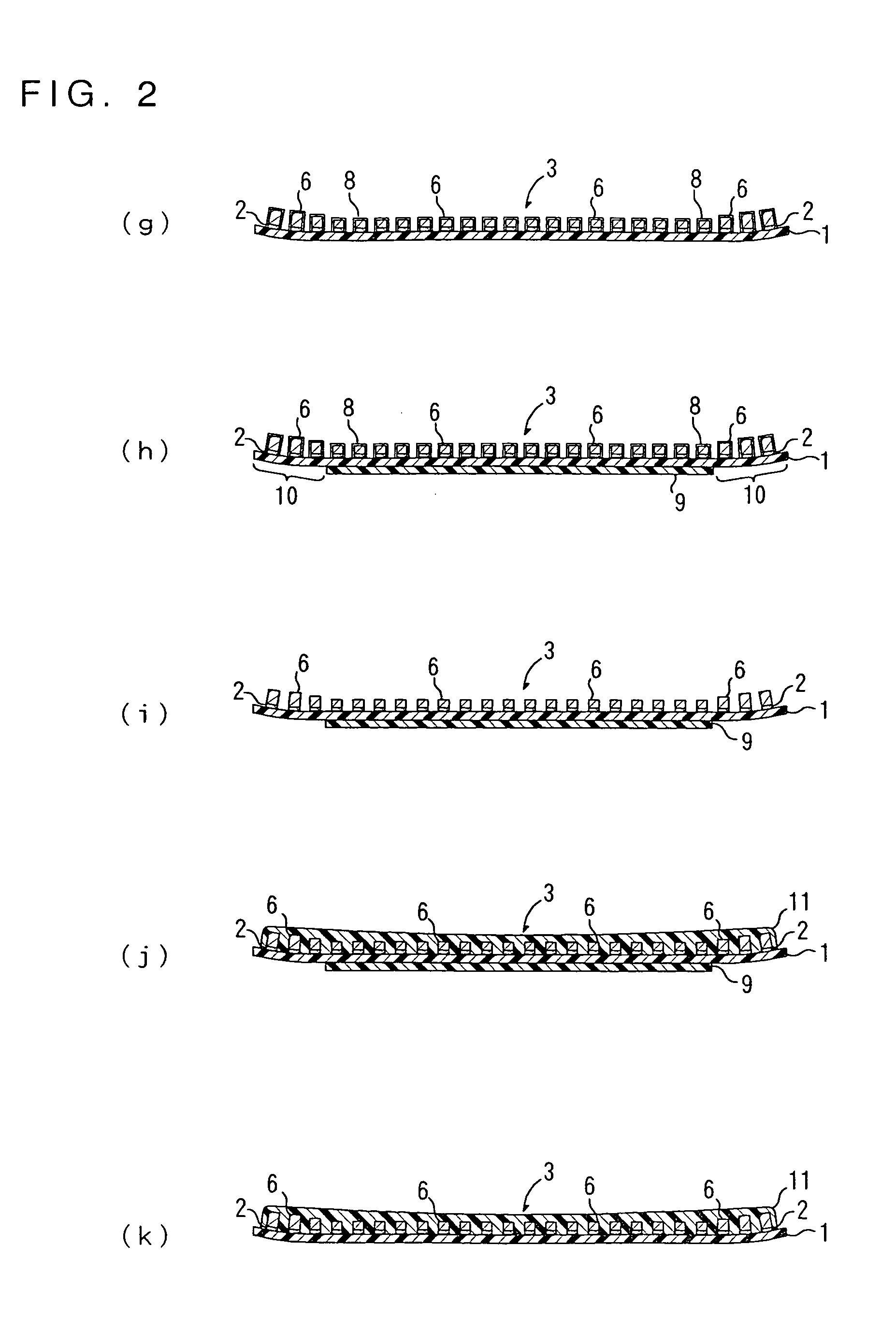
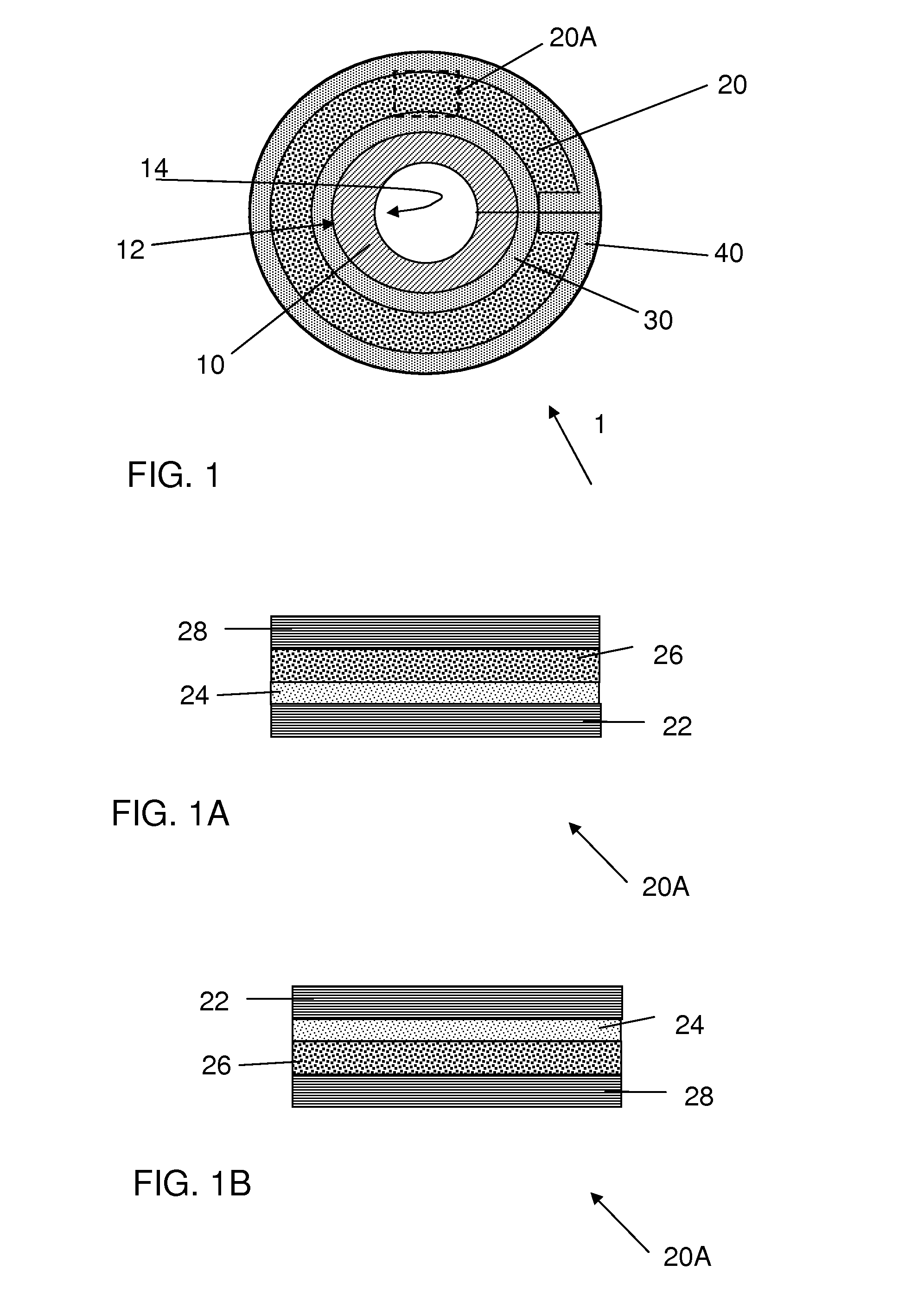
Producing method of flexible wired circuit board
InactiveUS20050067293A1Large thicknessAvoid it happening againPrinted circuit detailsDecorative surface effectsResistElectrolysis
A producing method of a flexible wired circuit board that can prevent the formation of a gap between an elongate substrate and a stiffener sheet bonded thereto to prevent contamination of the flexible wired circuit board obtained. In the process subsequent to the process of forming a conductive pattern 3 on a surface of the elongate substrate 1 by the semi-additive process using electrolysis plating and then annealing the elongate substrate 1 with the conductive pattern 3 in its wound up state, a stiffener sheet 9 having a width narrower than the elongate substrate 1 is bonded to the back side of the elongate substrate 1. Thereafter, an oxidized film formed on a surface of the conductive pattern 3 is removed and then a solder resist 11 is formed thereon. This prevents the strip of the stiffener sheet 9 from the elongate substrate 1 and in turn prevents etching solution or developing solution from entraining in a gap therebetween.
Owner:NITTO DENKO CORP
Method and apparatus for pulsed discharge forming of a dish from a planar plate
InactiveUS6591649B1Move quicklyPreclude obtainingMetal-working apparatusElectric dischargeEngineering
An apparatus for forming a generally planar metal plate into a dish with a three-dimensional pattern is provided. The apparatus comprises a mold having a forming surface with a contour corresponding to said three-dimensional pattern, and having edges corresponding to boundaries of the dish, which edges are defined by side walls essentially perpendicular to the forming plane; a forming device comprising a fluid basin and pairs of electric discharge members within the fluid and having an opening facing the mold to allow transmission of a pressure wave from the fluid to the metal plate; and an electric discharge circuitry for discharging a short and intense electric current through the pairs of electric discharge members generating an electric spark or breakdown within the fluid to yield formation of plasma, vapor or both.
Owner:INFINITY IP COMMERCIALIZATION ISRAEL LTD
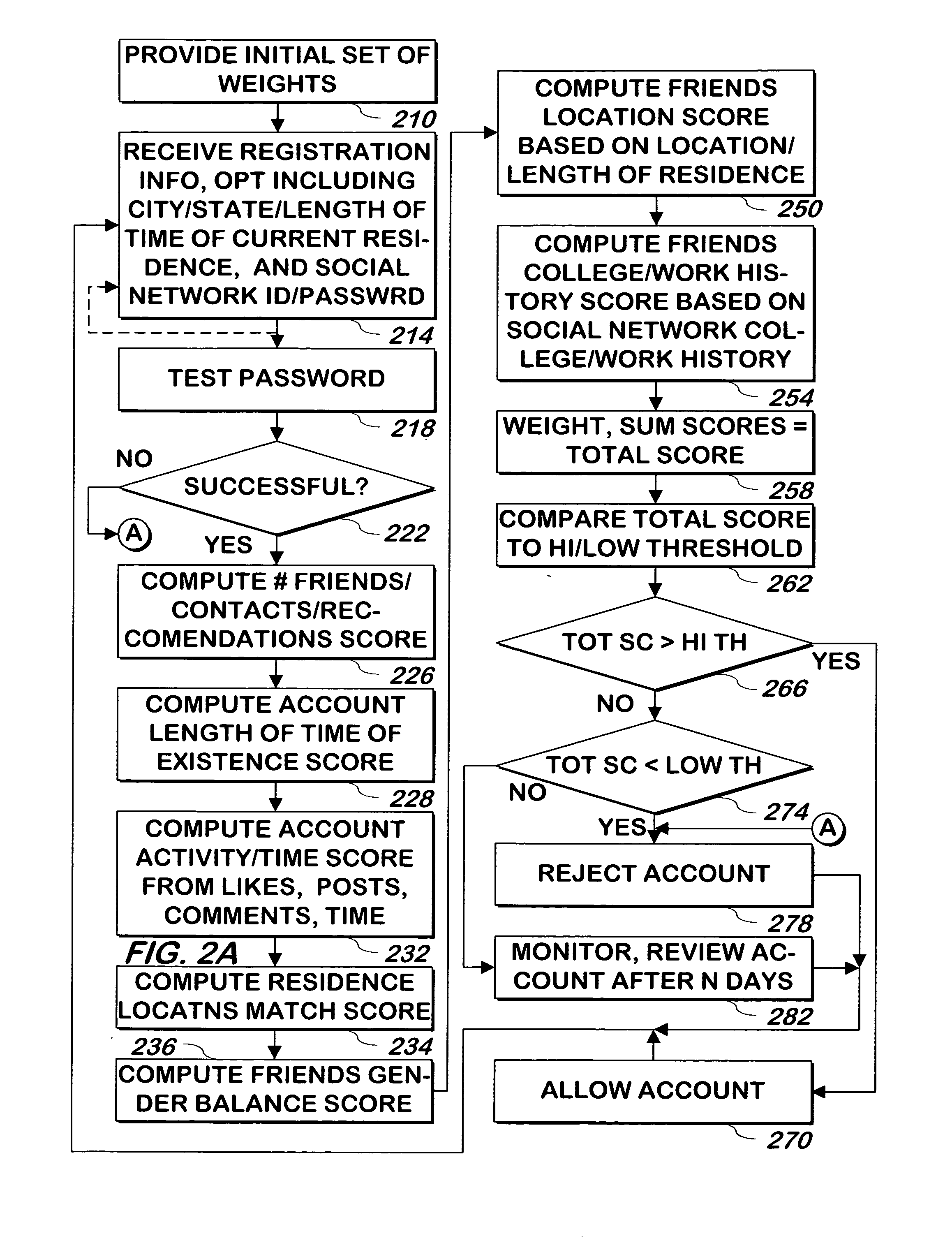
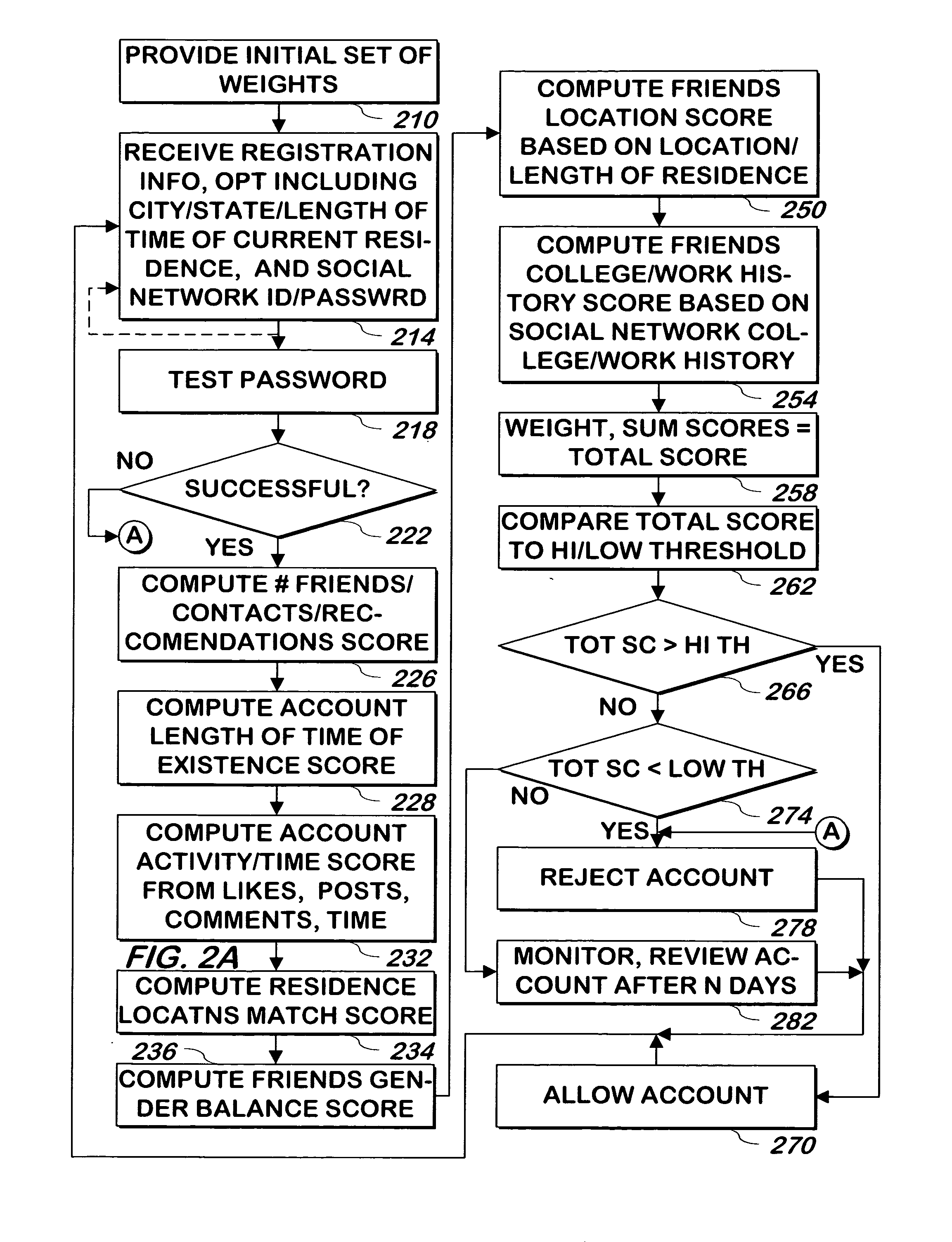
System and method for validating users using social network or other information from a wed site
ActiveUS20130086641A1Preclude obtainingData processing applicationsDigital data processing detailsSocial webMobile social network
A system and method uses any or all of information of a user and / or user's activity at a second web site, information of the user's friends or other connections at the second web site, or registration information of the user, to determine whether to allow the user to communicate with other users of a first web site, prevent the user from communicating with other users of the first web site, or monitor the user's communications and allow or prevent the user from further communication based on the monitored communications at the first web site.
Owner:ZOOSK
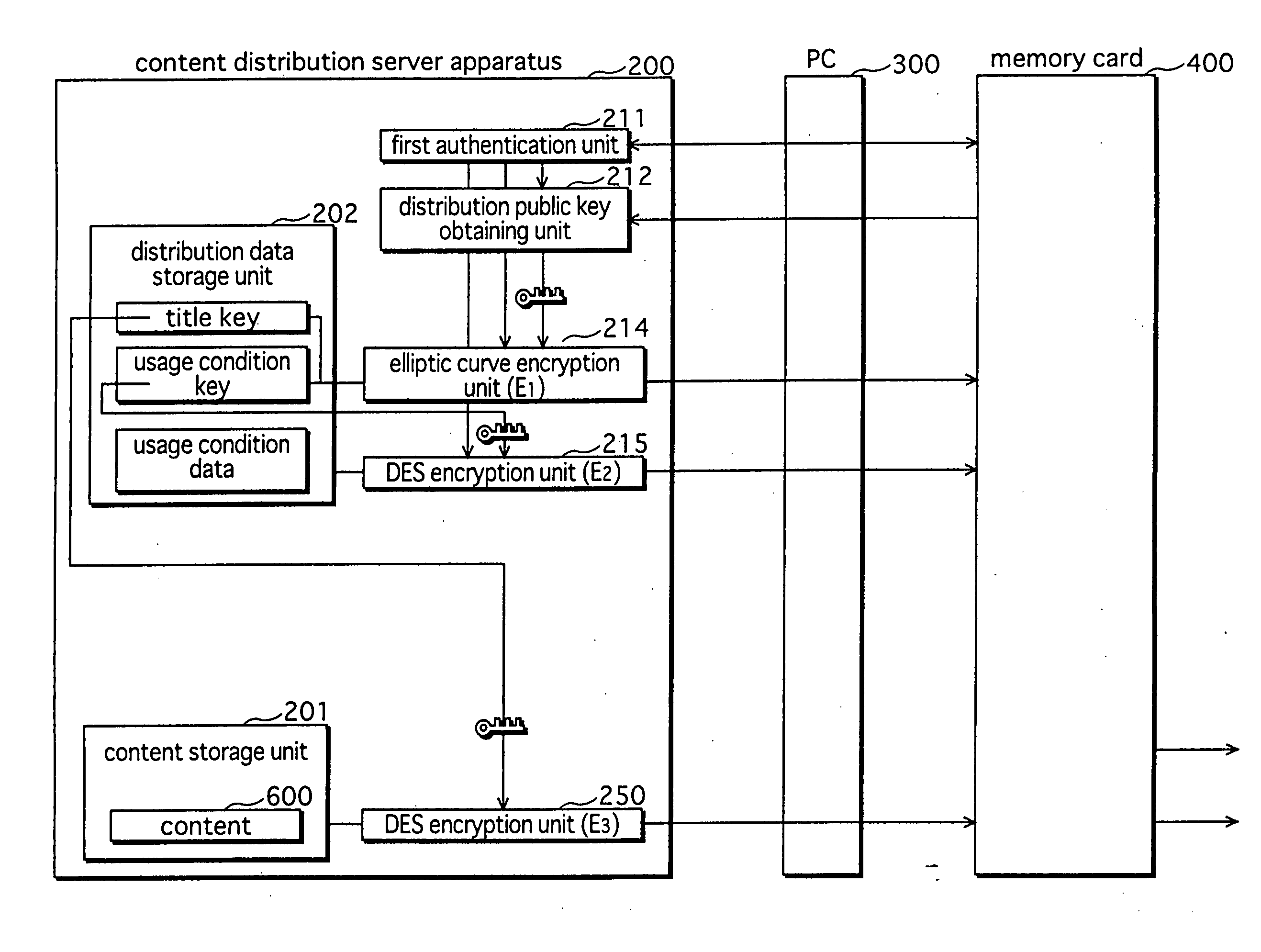
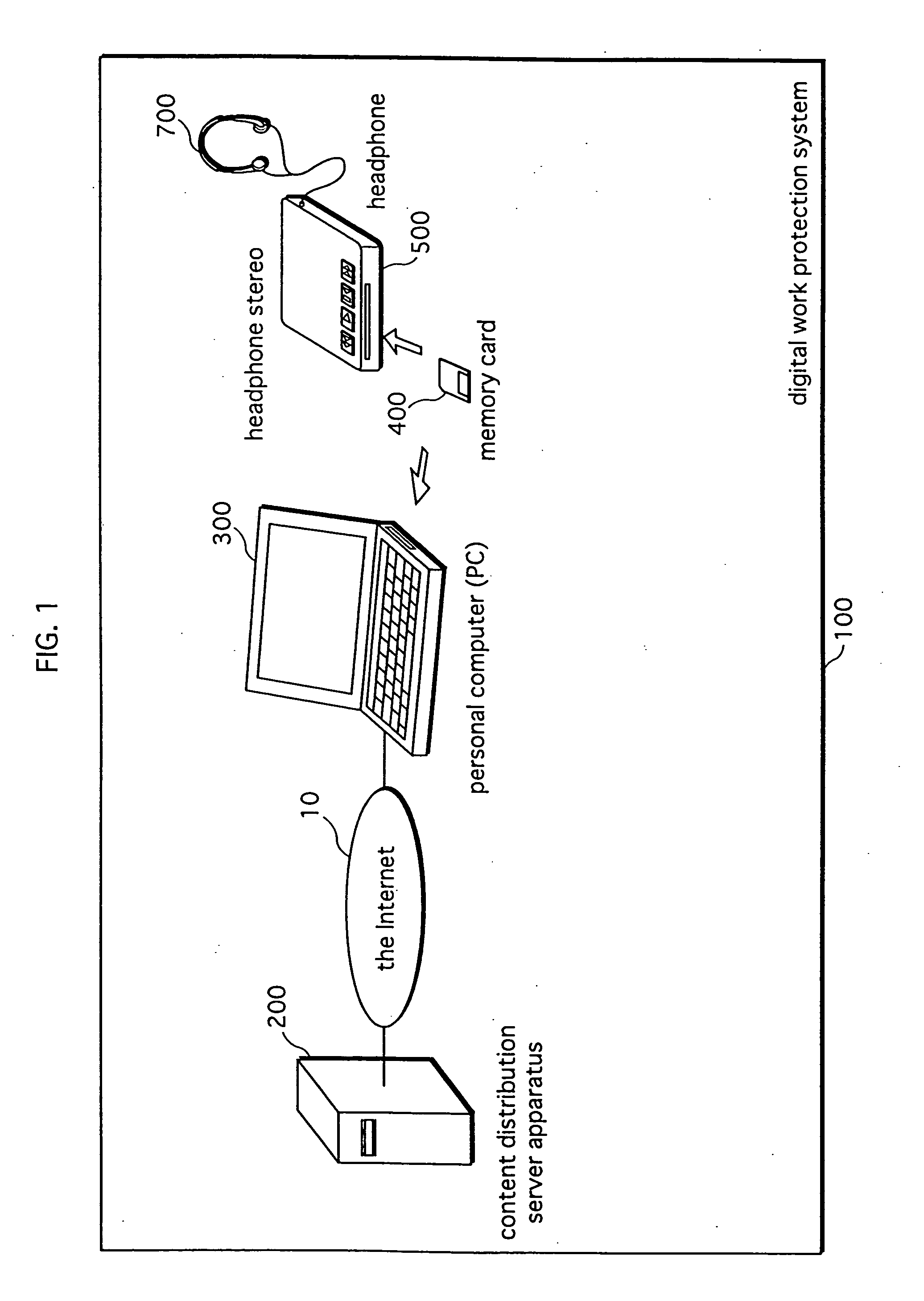
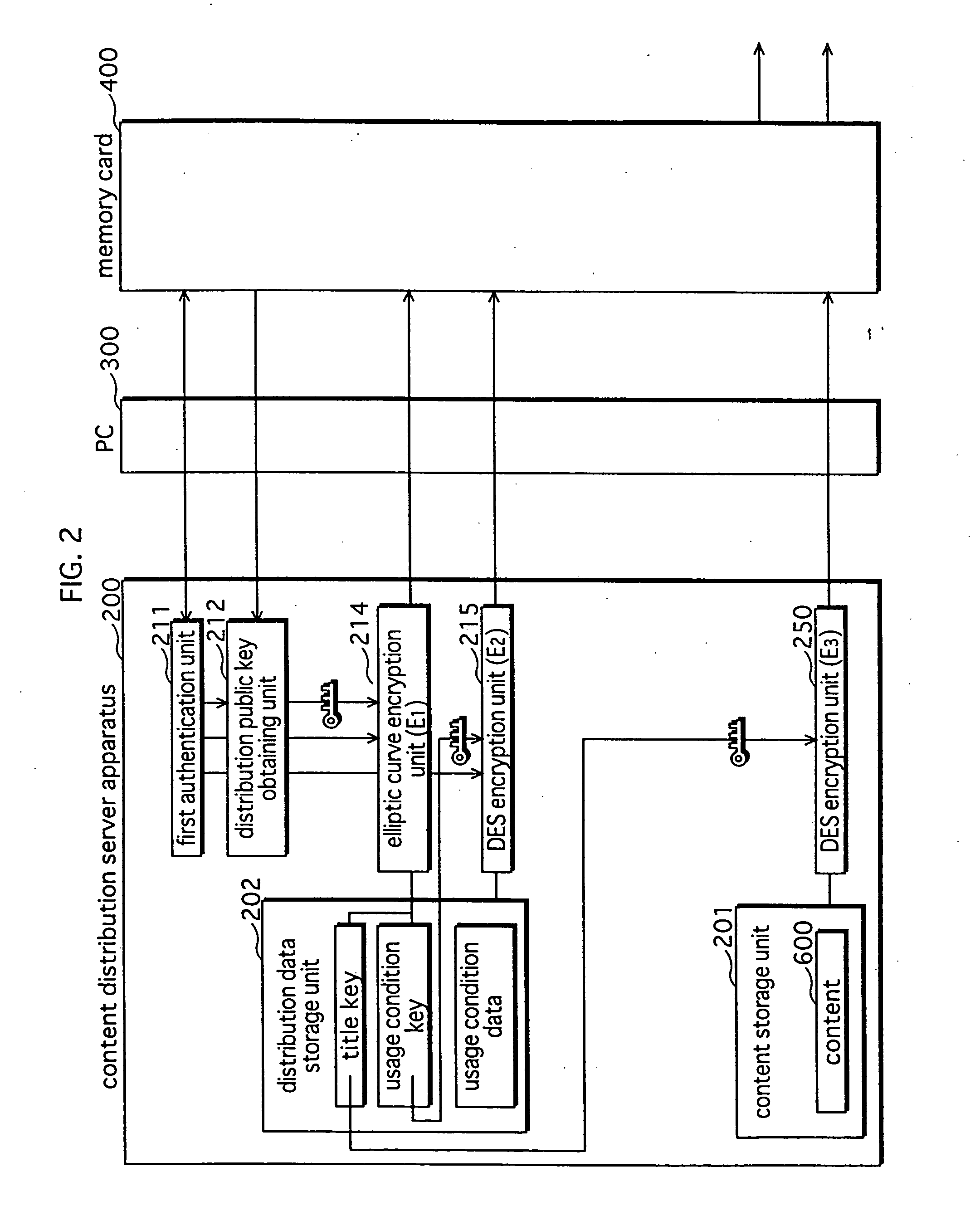
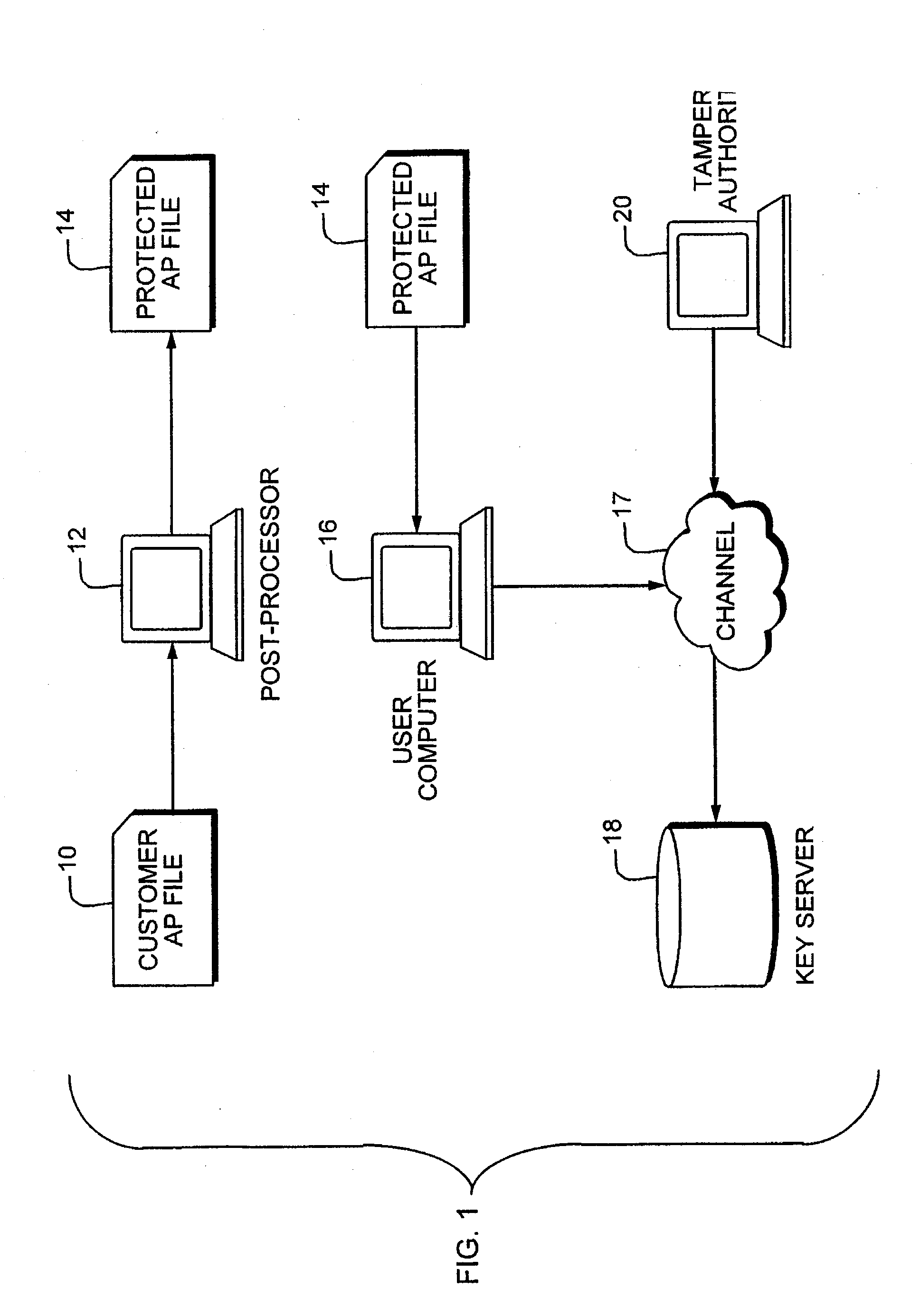
Digital information protection system, recording medium apparatus, transmission apparatus, and playback apparatus
InactiveUS20070198859A1Preclude obtainingIncrease in sizeDigital data processing detailsUser identity/authority verificationProtection systemData format
A server apparatus encrypts content, based on a distribution key, and transmits the encrypted content to a PC via a network. The PC, to which a memory card is connected, outputs the received encrypted content to the memory card. The memory card decrypts the encrypted content using the distribution key, converts the data format of the decrypted content, encrypts the content using a medium unique key that is unique to the memory card, and records the resulting re-encrypted content internally. A playback apparatus decrypts the re-encrypted content using the medium unique key, and plays back the decrypted content.
Owner:HARADA SHUNJI +5
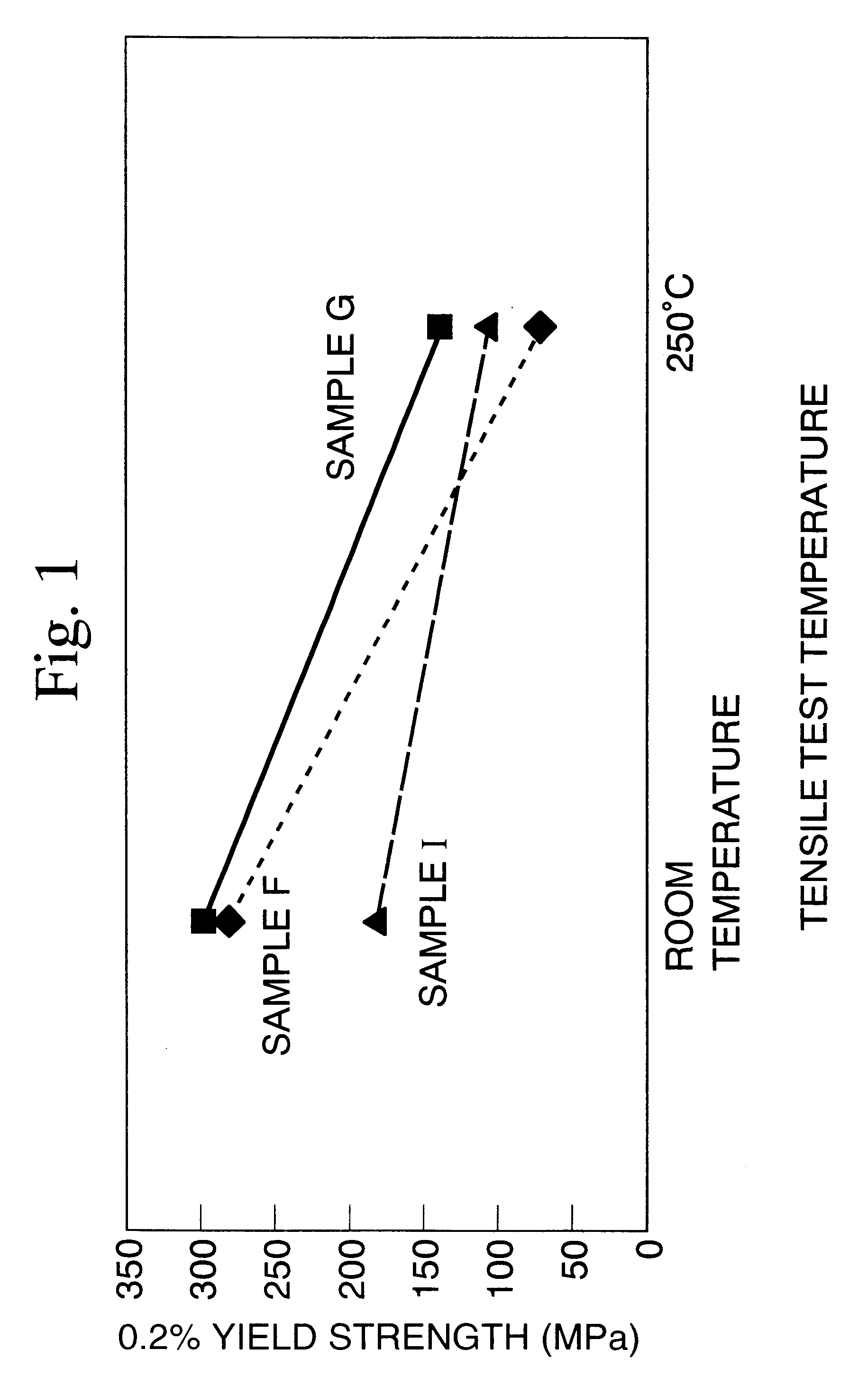
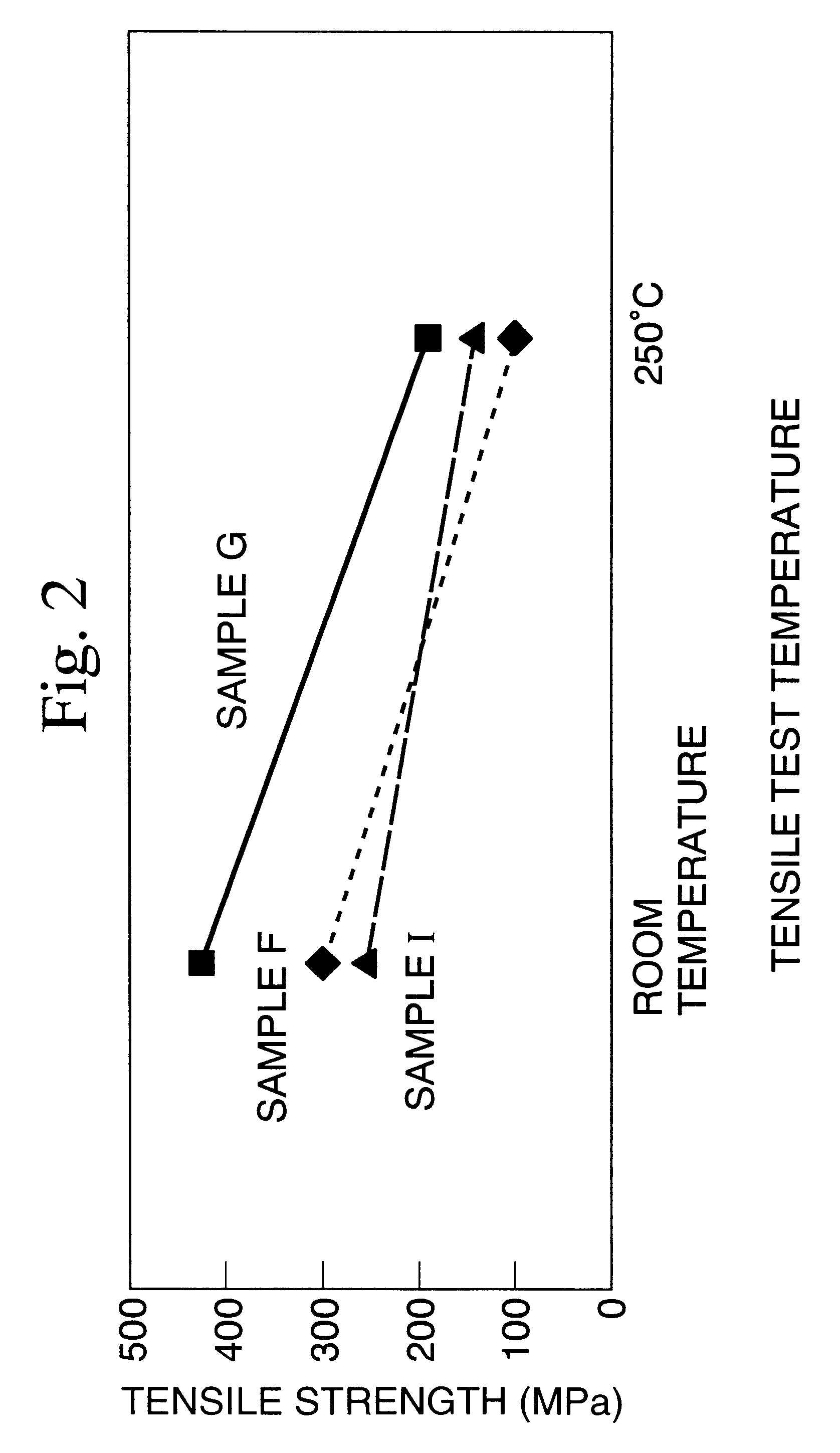
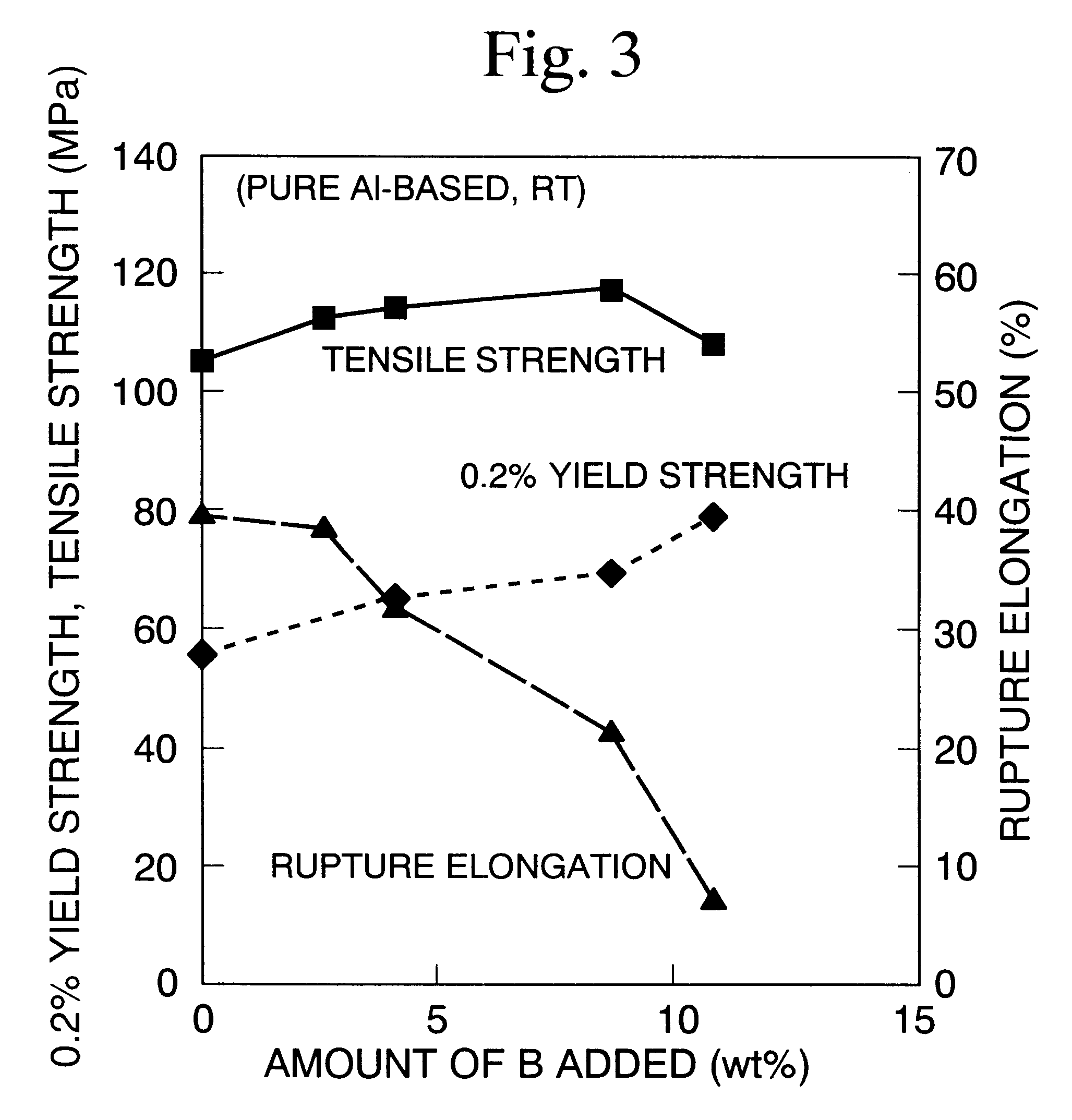
Aluminum composite material having neutron-absorbing ability
InactiveUS6602314B1Improve mechanical propertiesImprove workabilityNuclear engineering problemsNuclear engineering solutionsAlloyAbsorbed power
The present invention provides an aluminum composite material having neutron absorbing power that improves the ability to absorb neutrons by increasing the content of B, while also being superior to materials of the prior art in terms of mechanical properties and workability. The aluminum composite material having neutron absorbing power contains in Al or an Al alloy matrix phase B or a B compound having neutron absorbing power in an amount such that the proportion of B is 1.5% by weight or more to 9% by weight or less, and the aluminum composite material has been pressure sintered.
Owner:MITSUBISHI HEAVY IND LTD
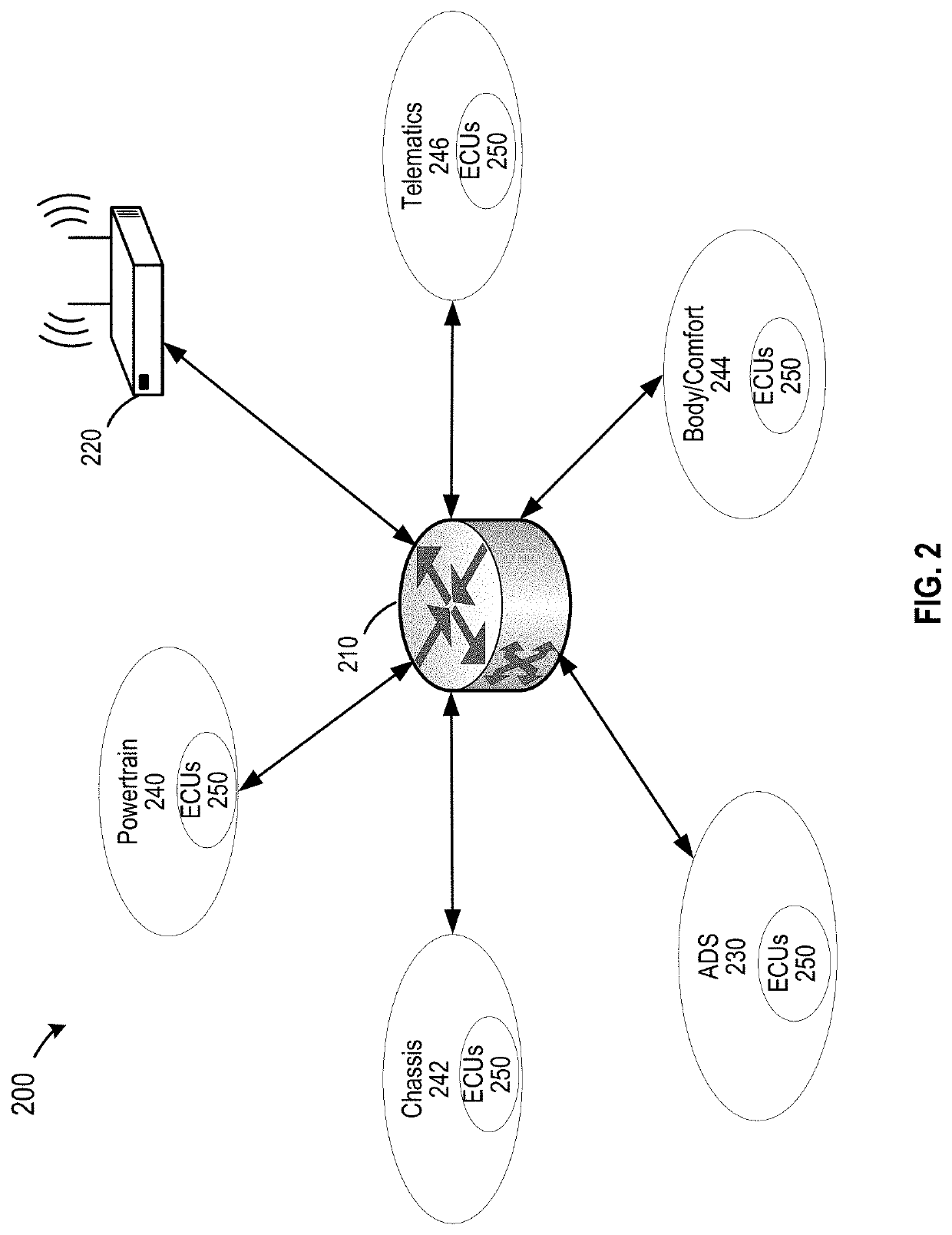
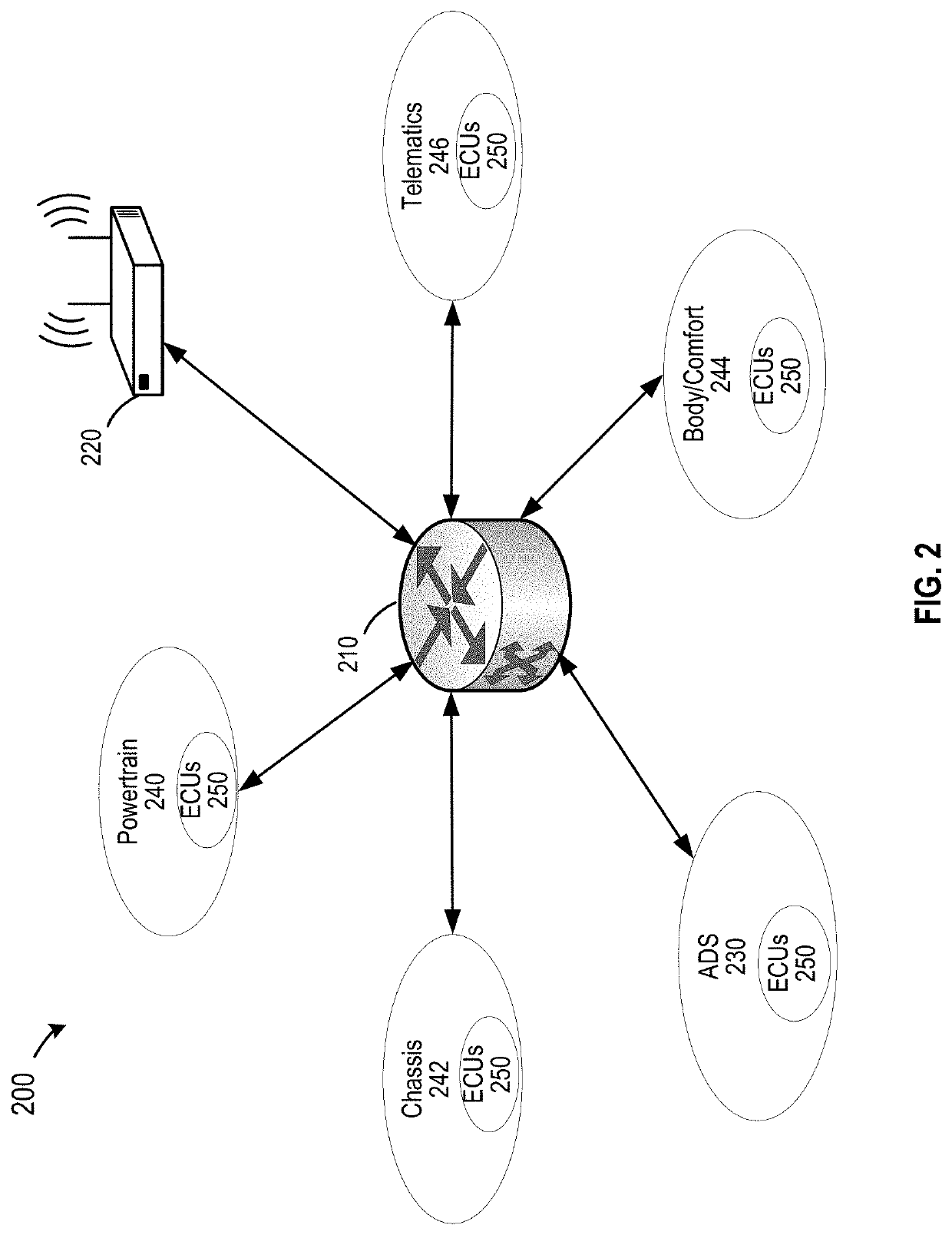
Repair management system for autonomous vehicle in a trusted platform
ActiveUS20200211301A1Detect changeReduce complexityRegistering/indicating working of vehiclesElectric/fluid circuitSecure communicationMaintenance management
Disclosed are techniques for securing electronic control units (ECUs) in a vehicle while allowing secure repairing of the ECUs. A method of repairing a vehicle includes disabling message authentication in secure communication between any two ECUs in a plurality of ECUs on the vehicle, detecting a first ECU that has been changed based on detecting an absence of a valid security key on the first ECU, verifying that a digital certificate associated with the first ECU is a valid certificate, generating one or more security keys for secure communication between the first ECU and a set of ECUs in the plurality of ECUs, provisioning the one or more security keys to the first ECU and the set of ECUs, and enabling the message authentication in secure communication between any two ECUs of the plurality of ECUs.
Owner:BEIJING VOYAGER TECH CO LTD
Data processing apparatus and method for analysing transient faults occurring within storage elements of the data processing apparatus
ActiveUS20130103972A1Improve performancePreclude obtainingNon-redundant fault processingCountermeasureComputer science
A data processing apparatus has a plurality of storage elements residing at different physical locations within the apparatus, and fault history circuitry for detecting local transient faults occurring in each storage element, and for maintaining global transient fault history data based on the detected local transient faults. Analysis circuitry monitors the global transient fault history data to determine, based on predetermined criteria, whether the global transient fault history data is indicative of random transient faults occurring within the data processing apparatus, or is indicative of a coordinated transient fault attack. The analysis circuitry is then configured to initiate a countermeasure action on determination of a coordinated transient fault attack. This provides a simple and effective mechanism for distinguishing between random transient faults that may naturally occur, and a coordinated transient fault attack that may be initiated in an attempt to circumvent the security of the data processing apparatus.
Owner:ARM LTD
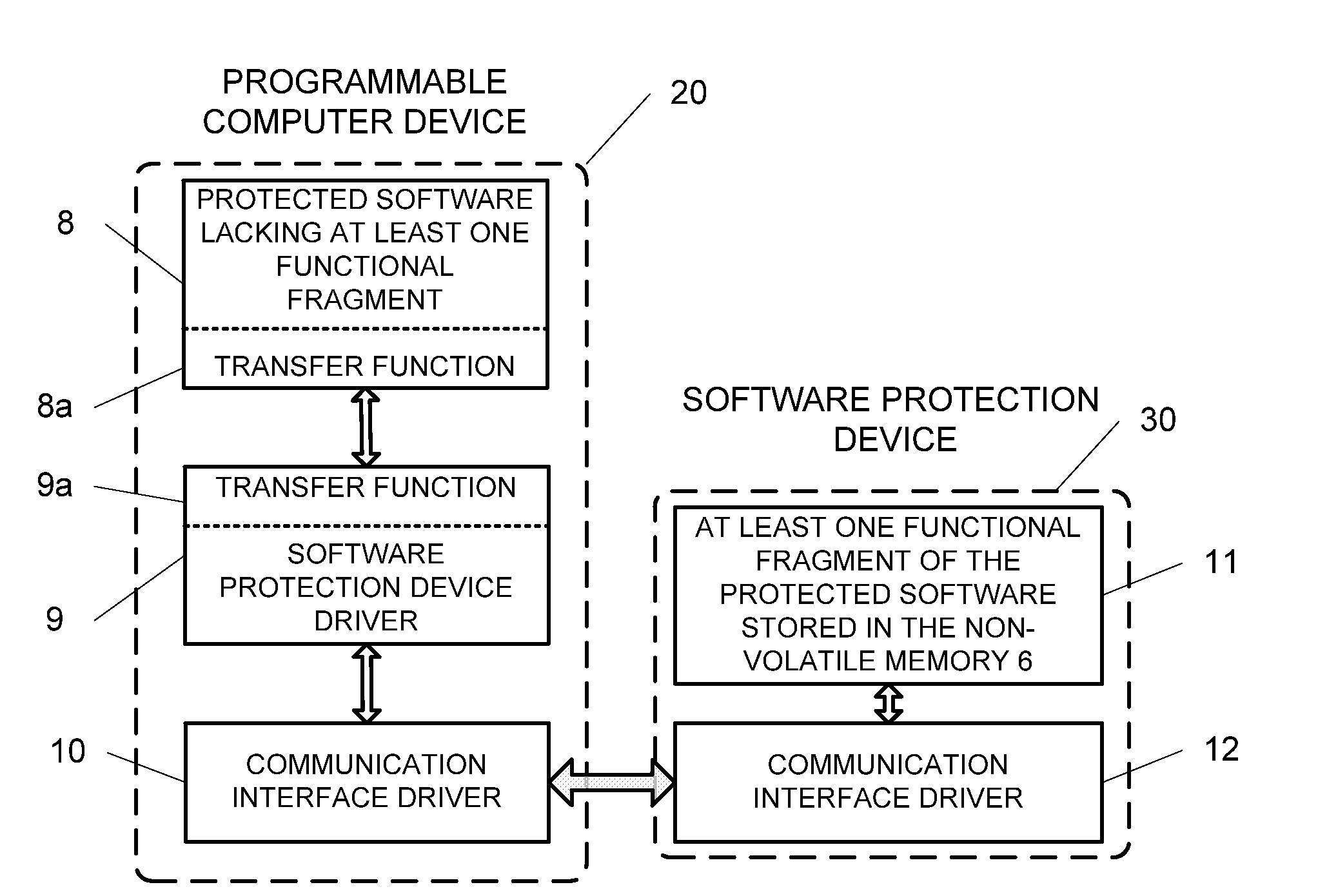
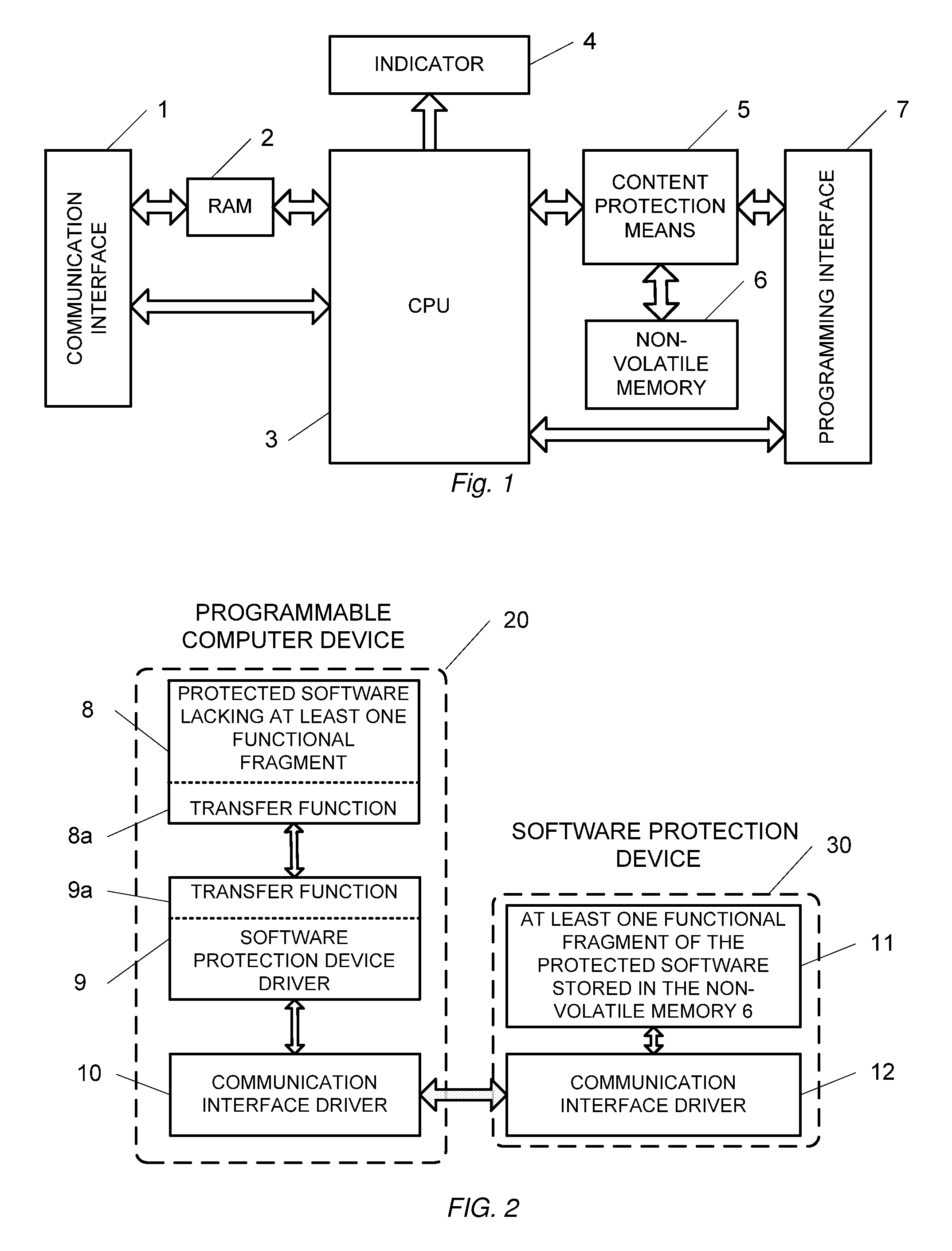
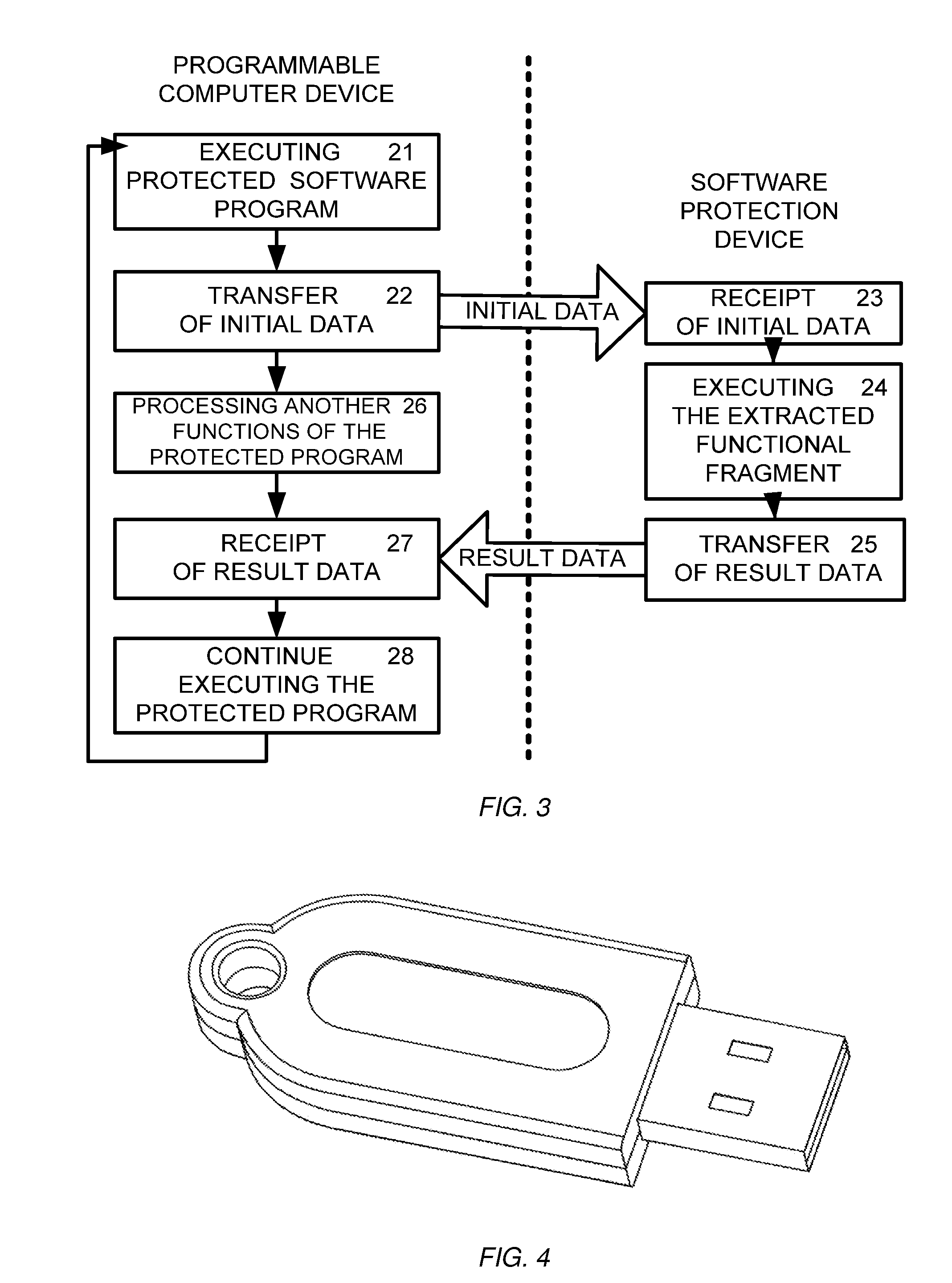
Method and device for protecting software from unauthorized use
InactiveUS20090094601A1Improve protectionPreclude obtainingMemory adressing/allocation/relocationProgram loading/initiatingCommunication interfaceComputer module
The present invention relation to a method and device for protecting a software program from unauthorized use, comprising a processor, a non-volatile memory, a content protection means, and a communication interface, wherein the non-volatile memory records and stores at least one functional fragment extracted from the said software program, wherein at least one transfer function is embedded into the remaining part of the software program for sending to the software protection device initial data and / or commands initiating execution of the extracted fragment to produce result data, and sending the result data to the programmable computer device, thus preventing hacking of the said software program. The software protection device can be implemented as an external or internal computer module.
Owner:VSTOVSKIY VLADIMIR NIKITICH +2
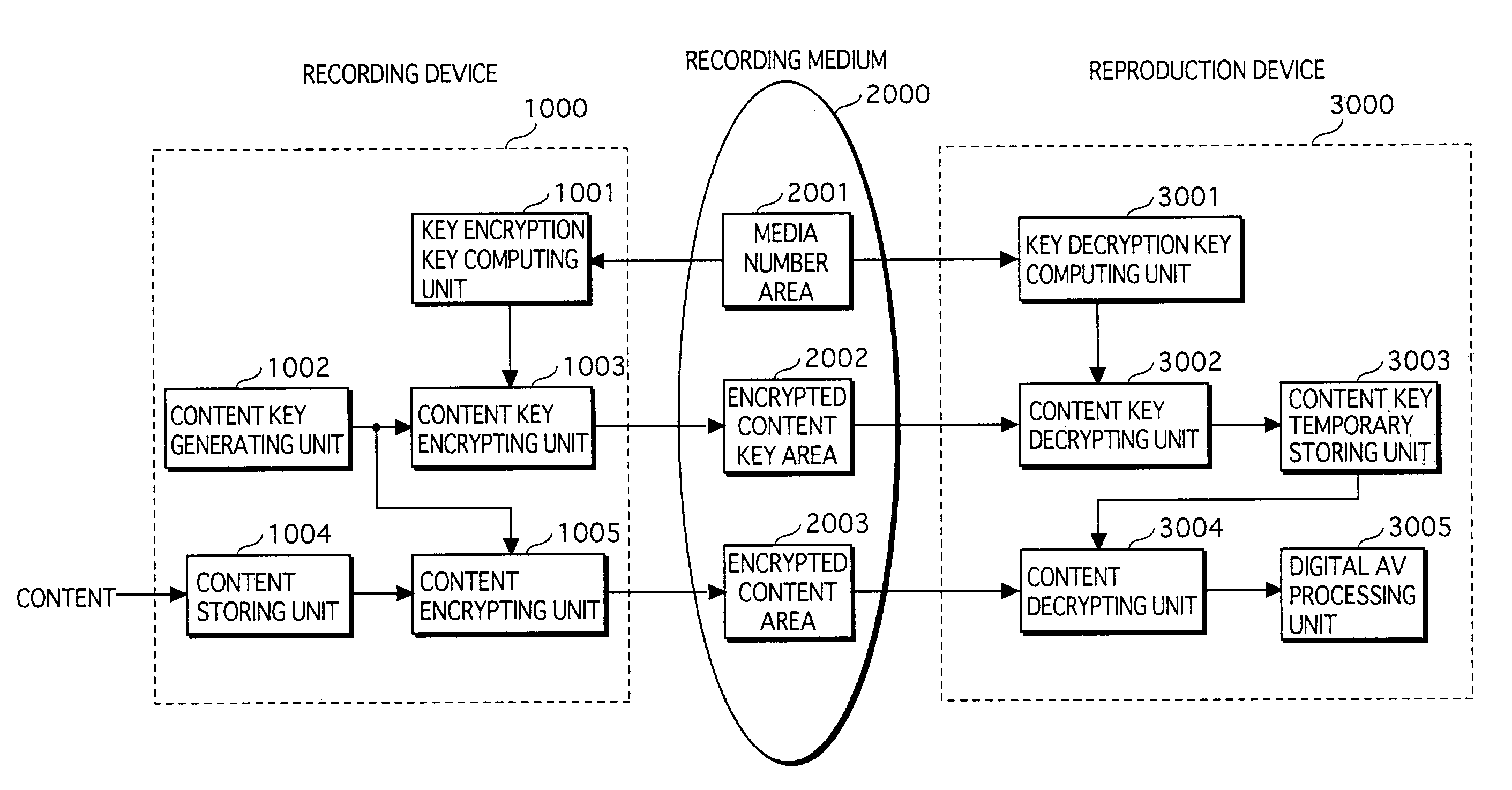
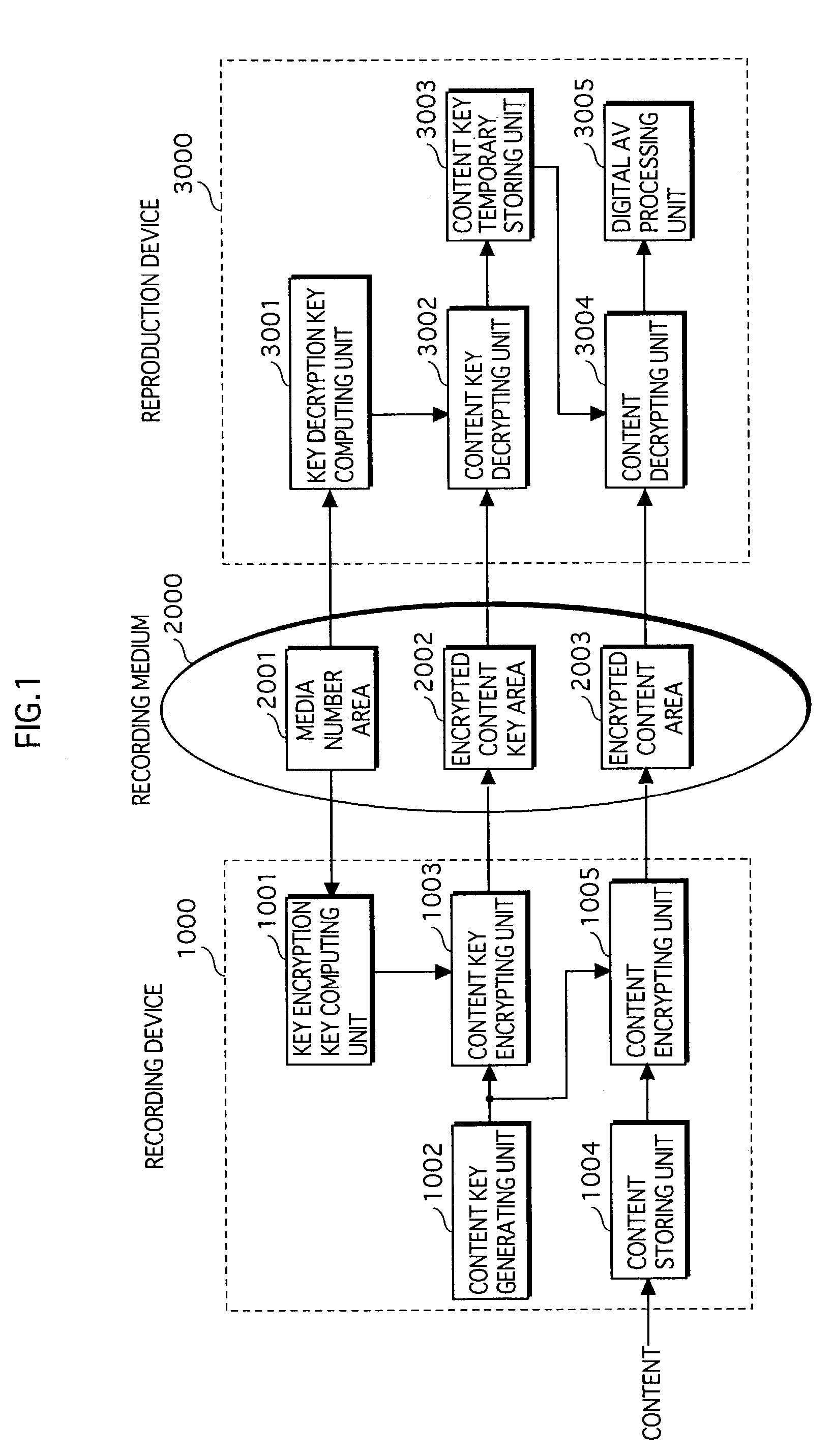
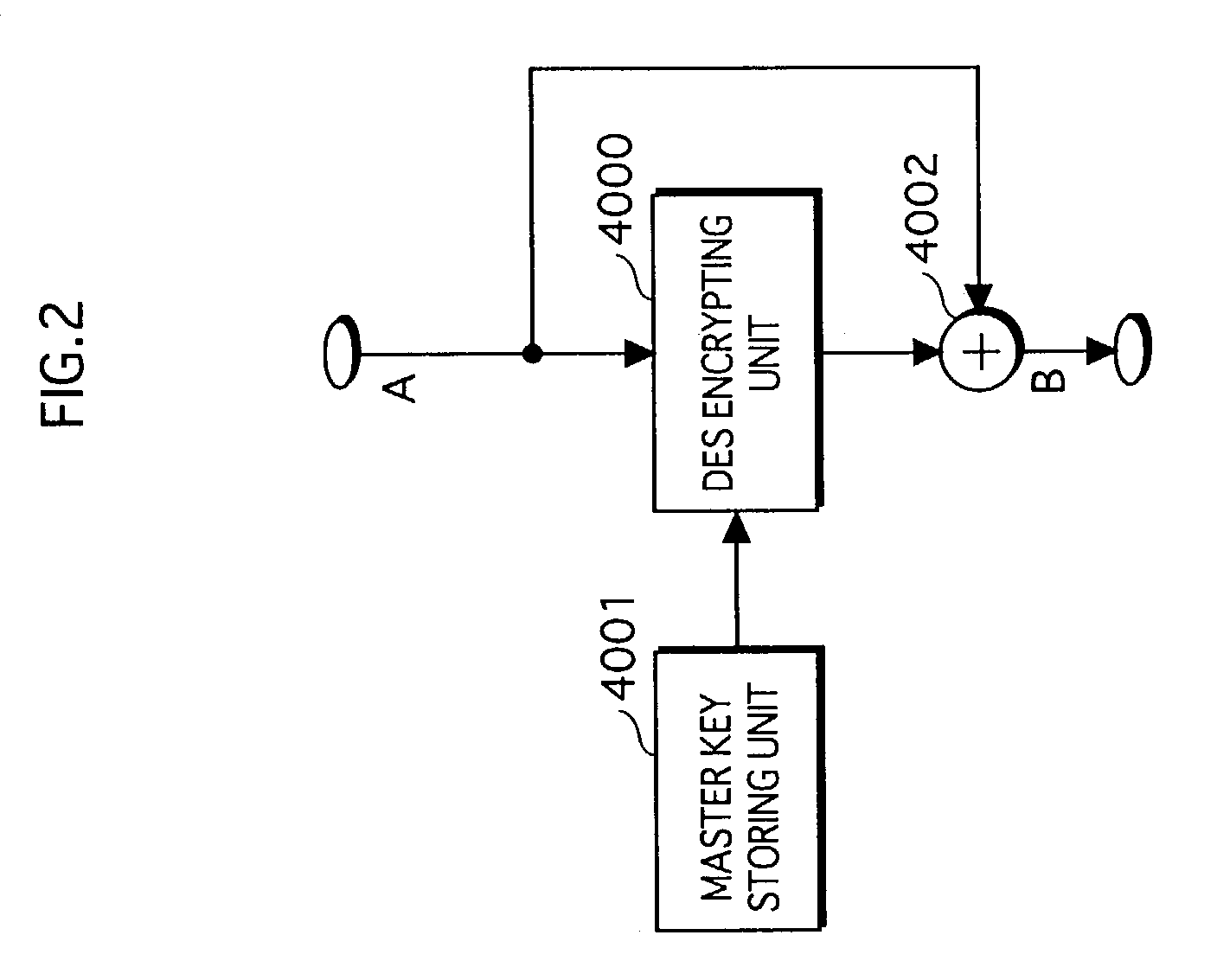
Copyright protection system, recording device, and reproduction device
ActiveUS7555779B2Avoid distributingPreclude obtainingDigital data processing detailsUser identity/authority verificationInternet privacyMediaFLO
A copyright protection system includes a recording device and a reproduction device. The recording device writes encrypted content, an encrypted content key for decrypting the encrypted content, and license information on a recording medium on which a unique media number has been recorded in an unrewritable state. The license information is generated using both the media number and the encrypted content key, and therefore reflects both values. The reproduction device reads the media number, the encrypted content key, and the license information from the recording medium, and judges whether the license information reflects both the media number and the encrypted content key. The reproduction device decrypts the encrypted content key, and decrypts the encrypted content using the content key only if the license information reflects both values. Thus, the copyright protection system allows only original recording media to be reproduced, and prohibits reproduction of copy recording media.
Owner:PANASONIC CORP
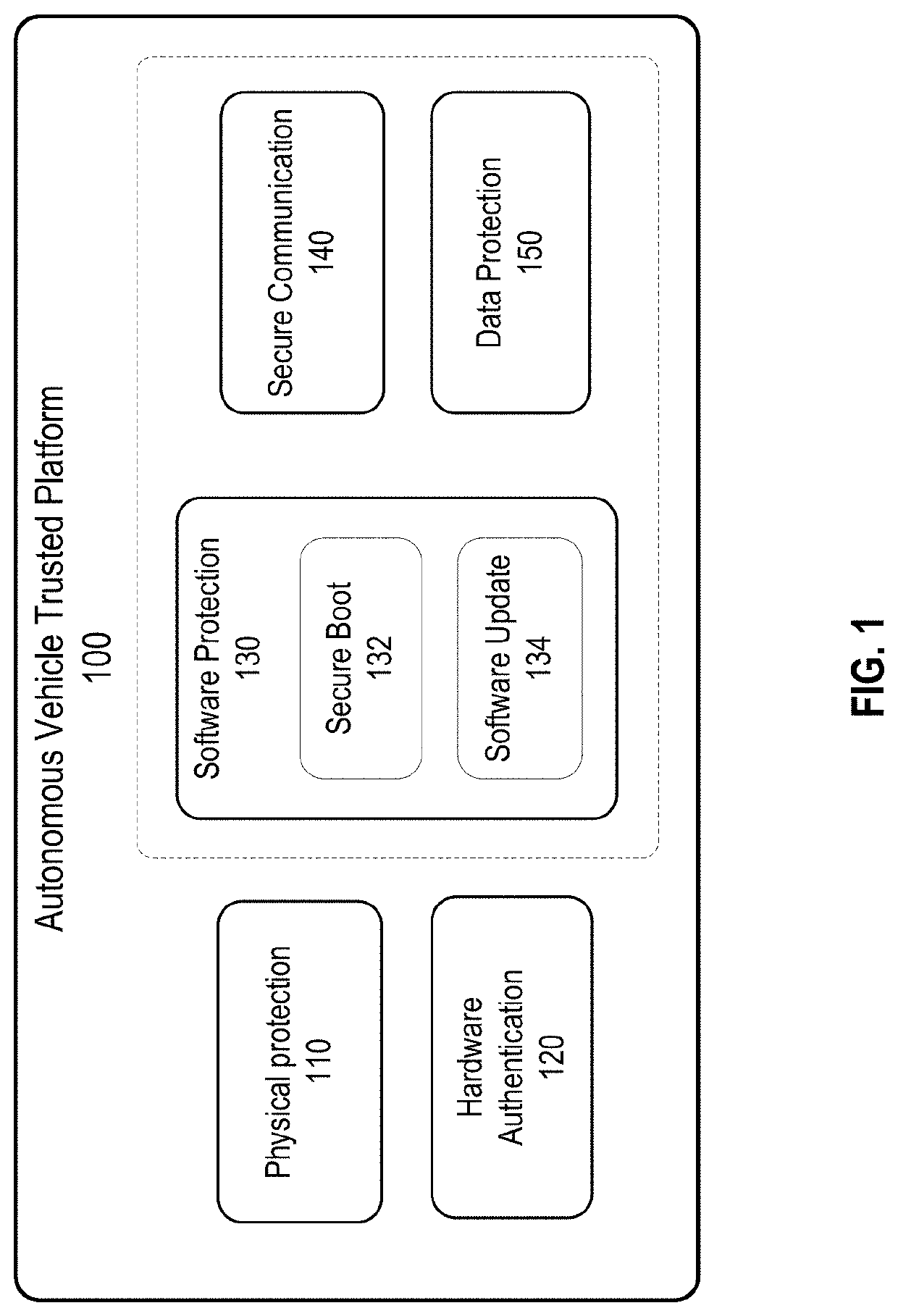
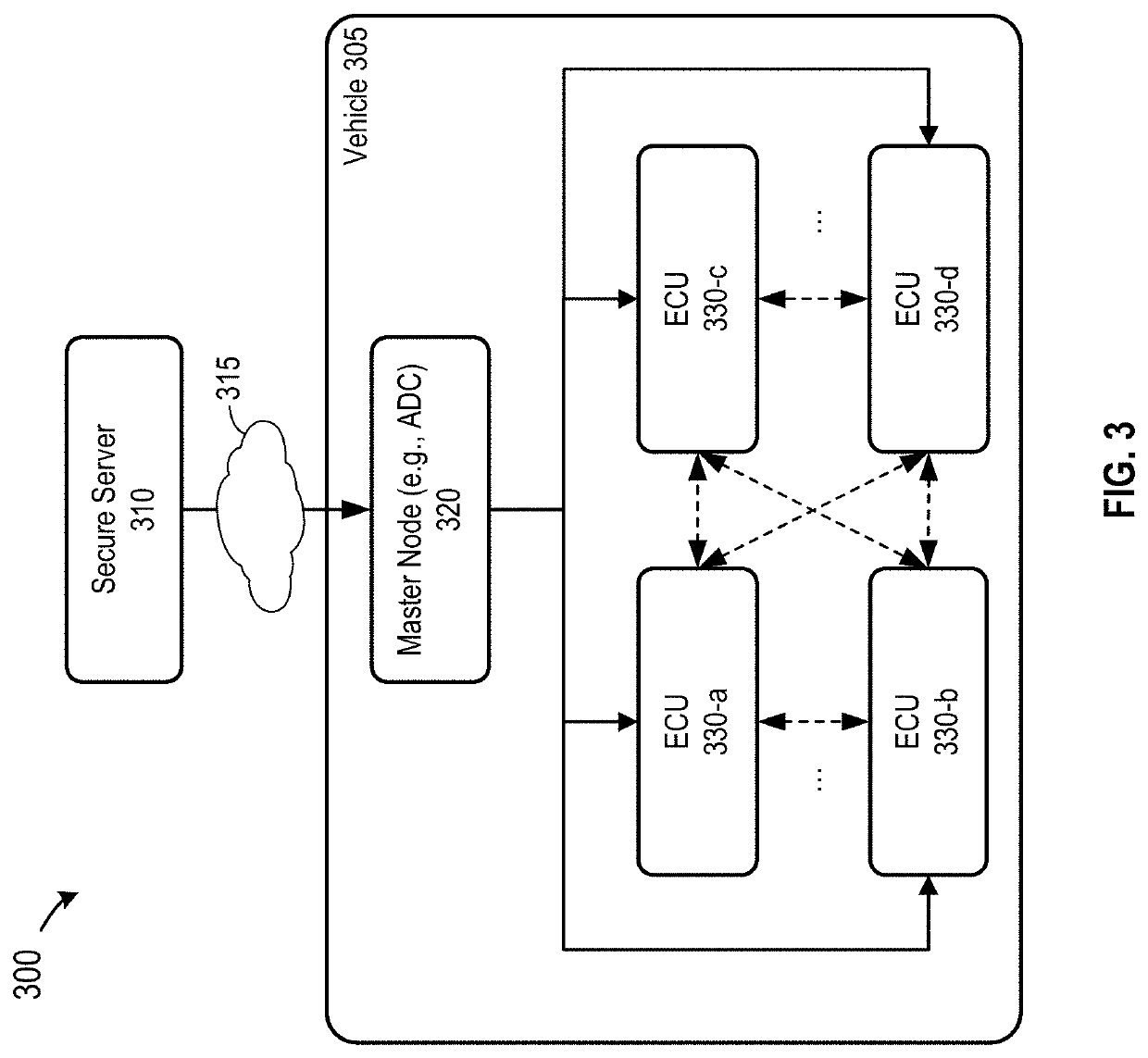
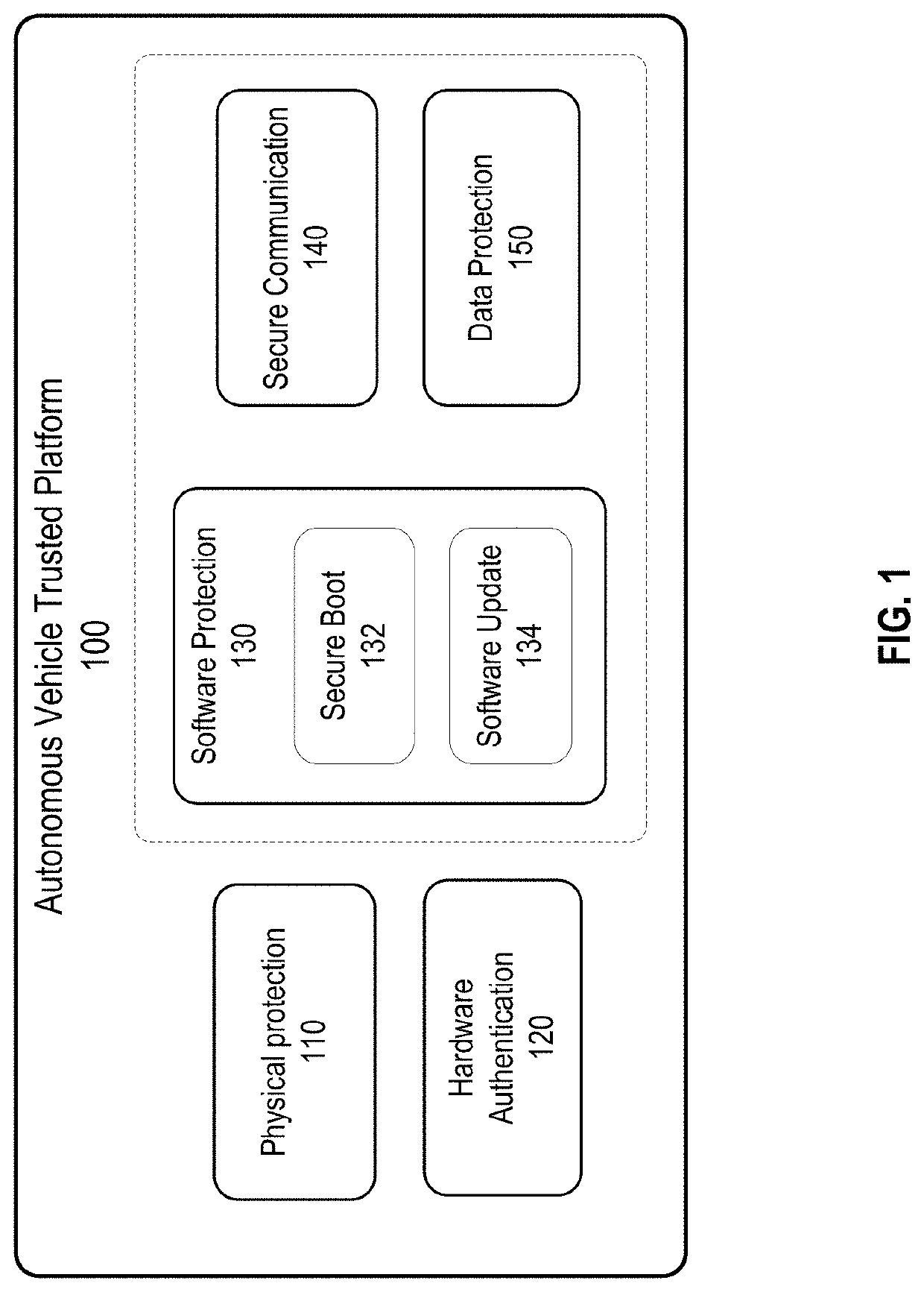
Trusted platform protection in an autonomous vehicle
ActiveUS20200213287A1Reduce and minimize safety and security issueSafety and security be improveParticular environment based servicesDigital data authenticationEmbedded systemSecure communication
Disclosed are techniques for securing electronic control units (ECUs) in a vehicle. A security platform for a vehicle includes a key distribution center (KDC) for the vehicle. The KDC is configured to verify that a digital certificate associated with a first electronic control unit (ECU) on the vehicle is a valid certificate, where the digital certificate indicates a first security level of the first ECU. The KDC is configured to generate, based on the first security level of the first ECU, one or more security keys for secure communication between the first ECU and a set of ECUs on the vehicle, and provision the one or more security keys to the first ECU and the set of ECUs. In some embodiments, the KDC uses the provisioned keys to authenticate each ECU when the vehicle is powered up.
Owner:BEIJING VOYAGER TECH CO LTD
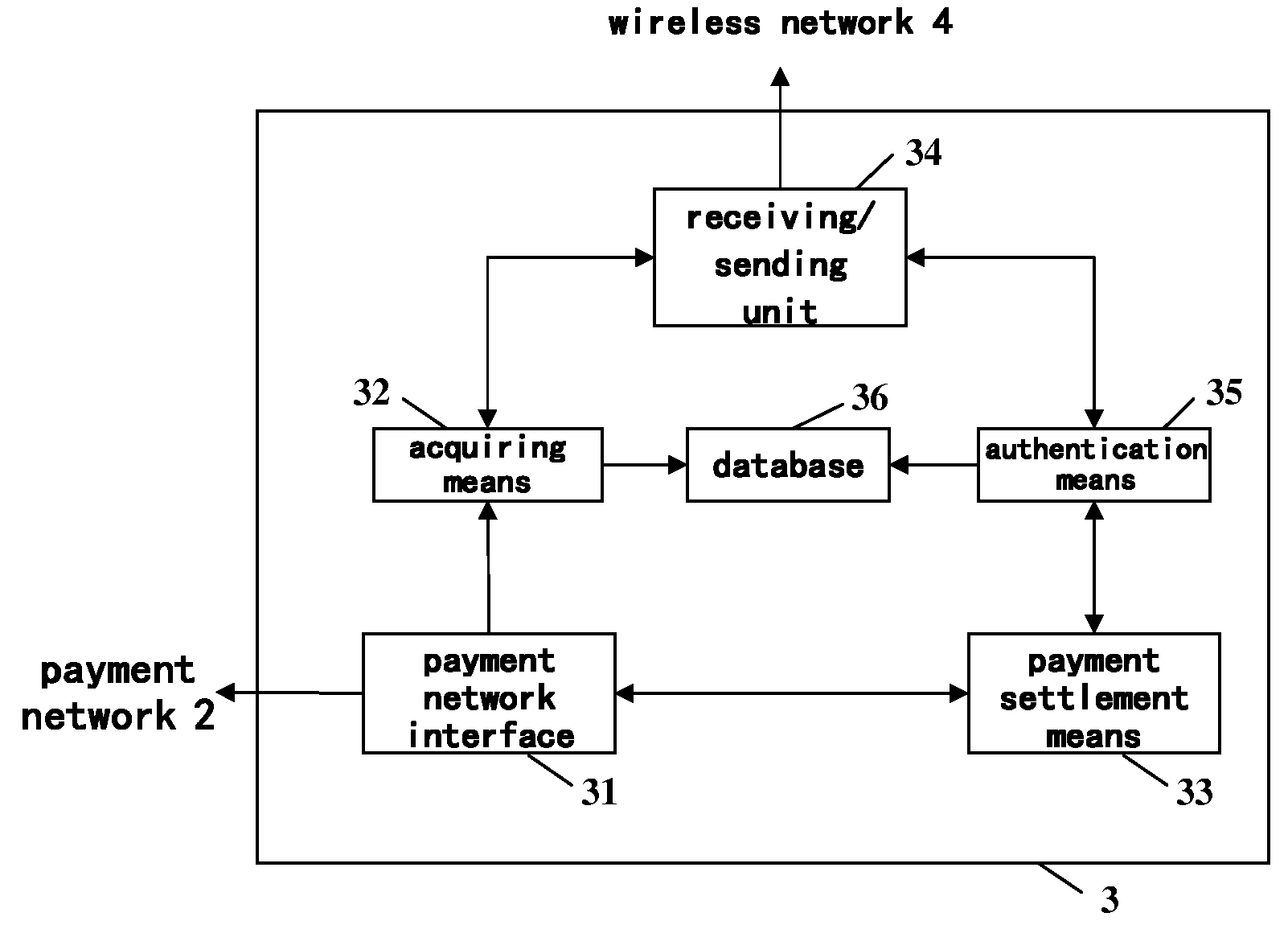
System for enhancing payment security, method thereof and payment center
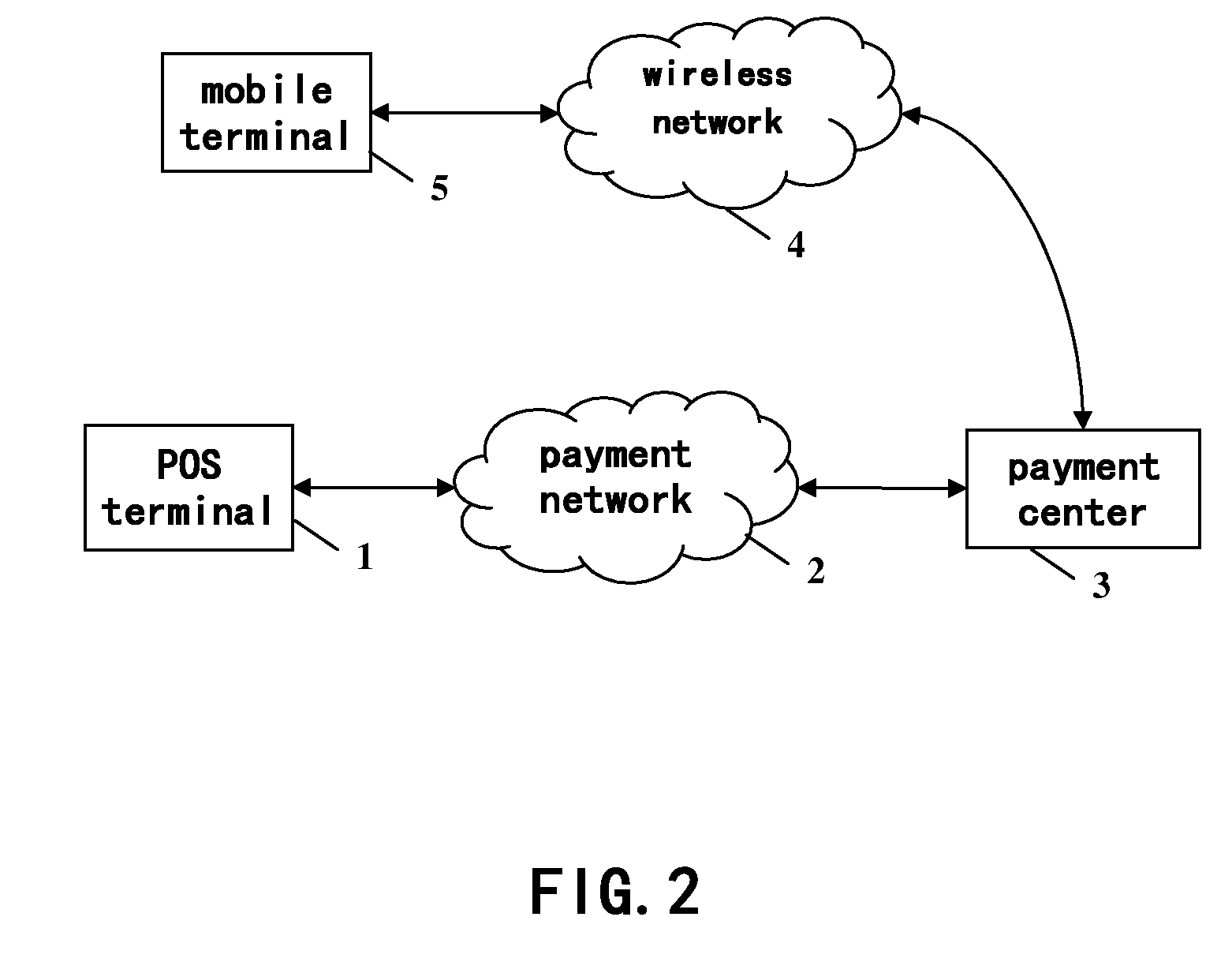
InactiveUS20090150248A1Improve payment securityPreclude obtainingPoint-of-sale network systemsPaymentPassword
A system for enhancing payment security includes a payment network interface unit for communicating with a POS terminal through a payment network; a database for storing a card number and password of a payment tool of a user and a number of a mobile terminal of the user associated with the card number; an acquiring means for searching in the database to obtain the number of the user's mobile terminal associated with the card number; a receiving / sending unit for sending, according to the obtained number of the user's mobile terminal, a request for a transaction password of the payment tool to the user's mobile terminal by means of a wireless network; and an authentication means for authenticating whether or not the transaction password of the user's payment tool returned from the user's mobile terminal matches with the password stored in the database.
Owner:IBM CORP
Desiccant container structure
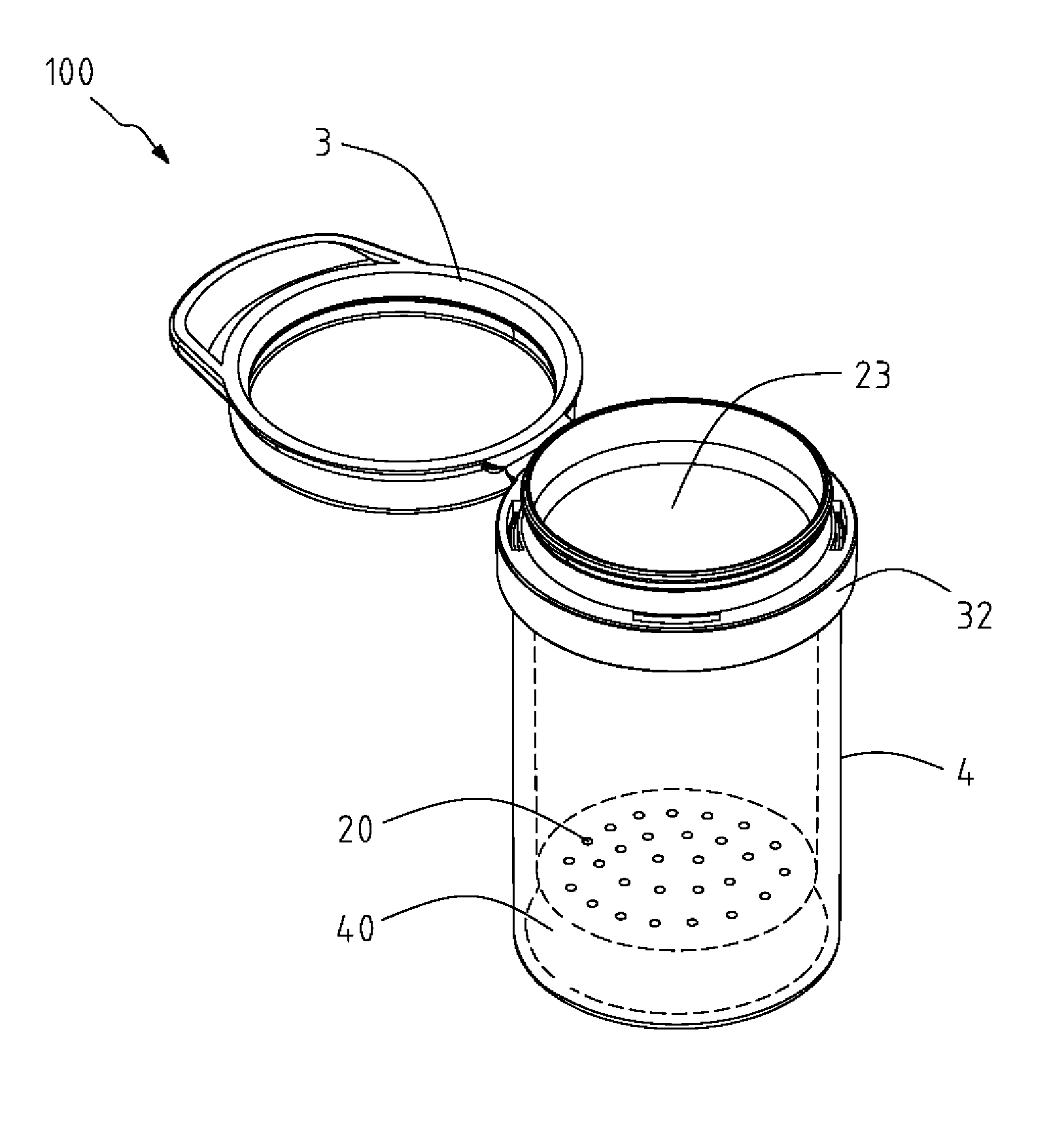
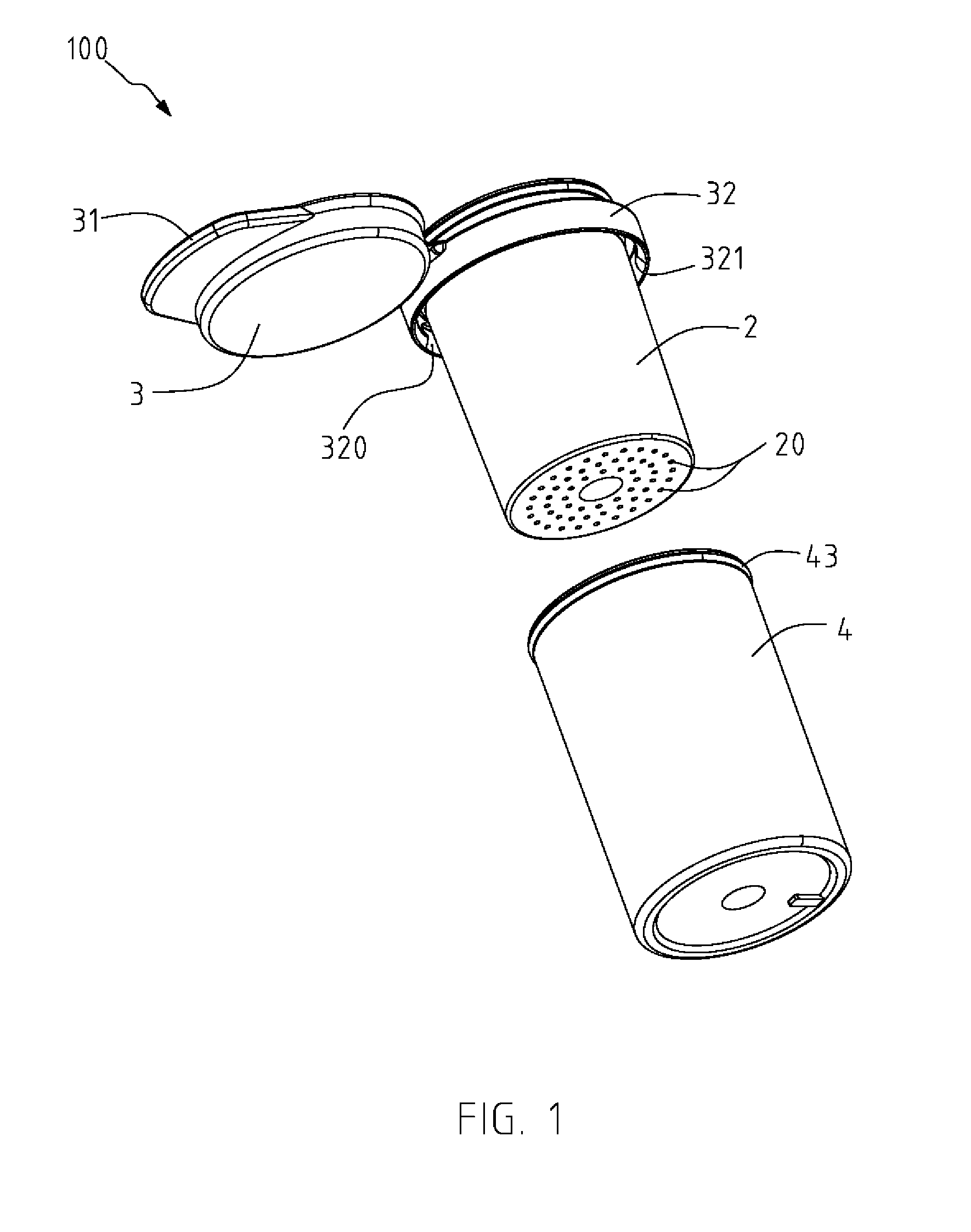
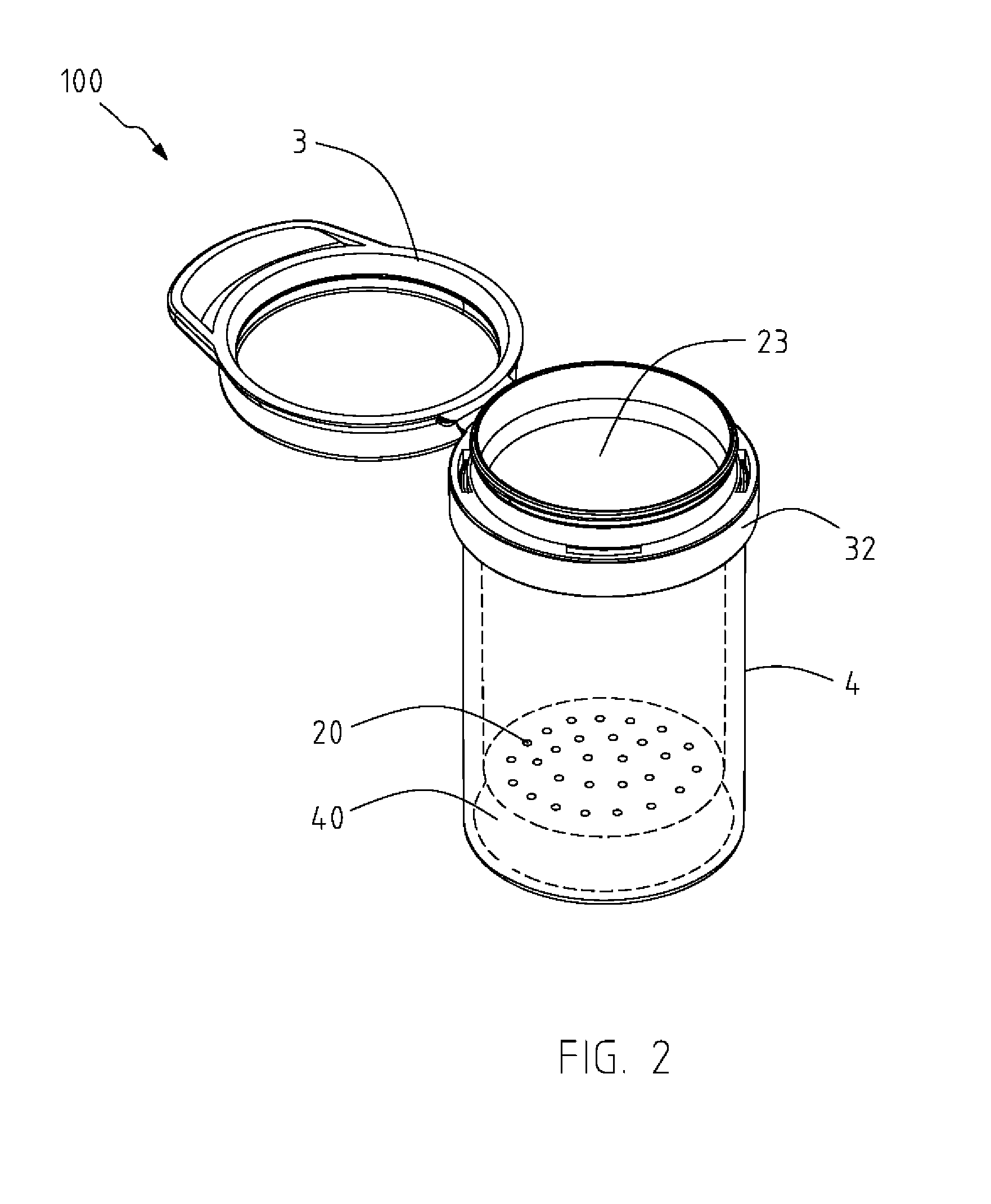
InactiveUS20150291338A1Preventing the objects from being affectedIncrease spaceClosures with oxygen absorbersContainer/bottle contructionDesiccantEngineering
A desiccant container structure includes a main body, a lid, and a desiccant storing element having at least a viewing portion made of a transparent material. The main body is formed with a plurality of through holes and an accommodation space for accommodating an object. The desiccant storing element is formed with a storing chamber for accommodating a desiccant and communicating with the main body through the plurality of through holes. The desiccant in the desiccant storing element is capable of absorbing moisture from the accommodation space through the plurality of through holes for maintaining the object in a dry state, and a state of the desiccant is capable of being viewed directly through the transparent viewing portion.
Owner:CHEN ERIK
Charging cable plug for electric vehicles
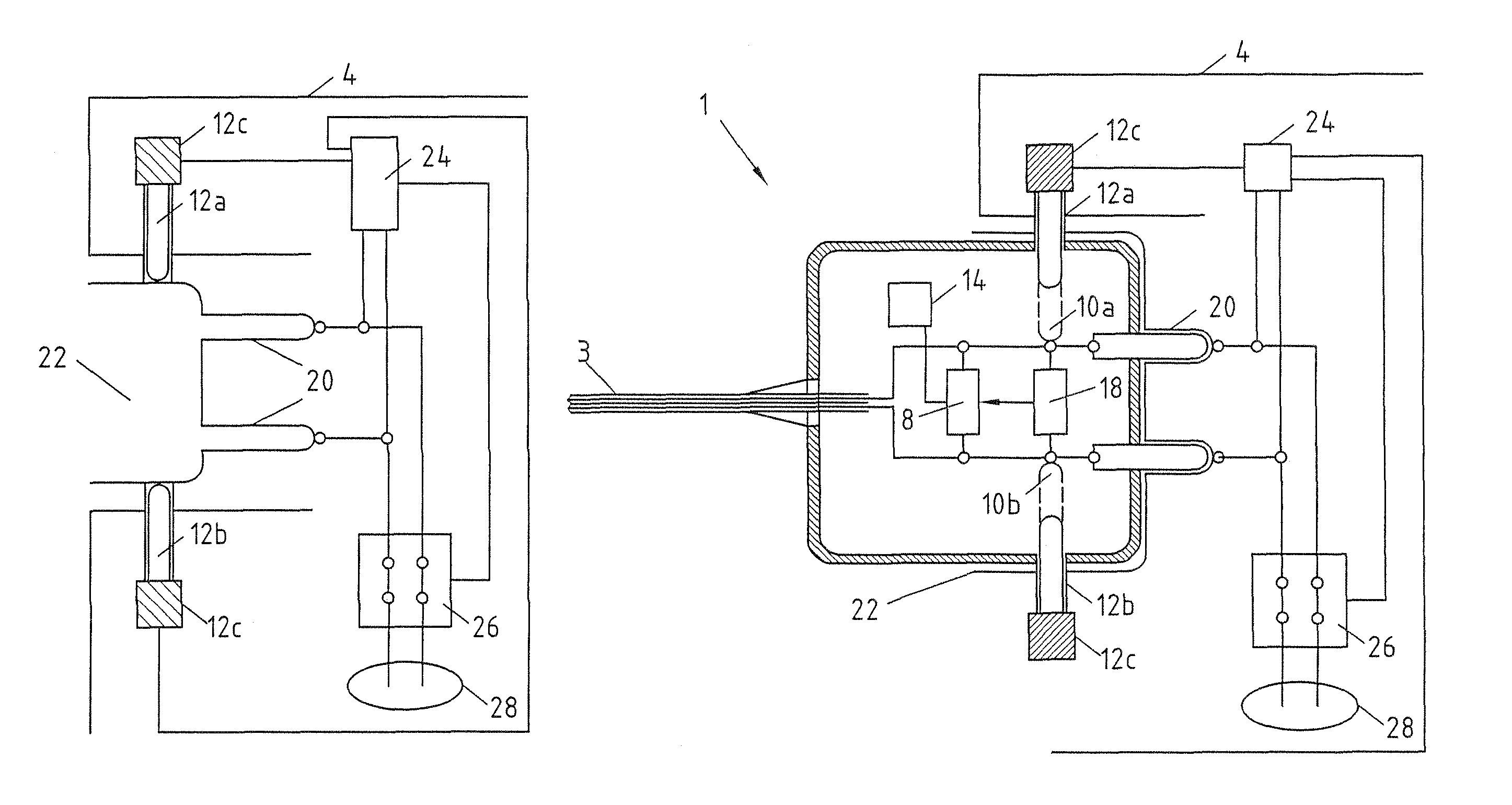
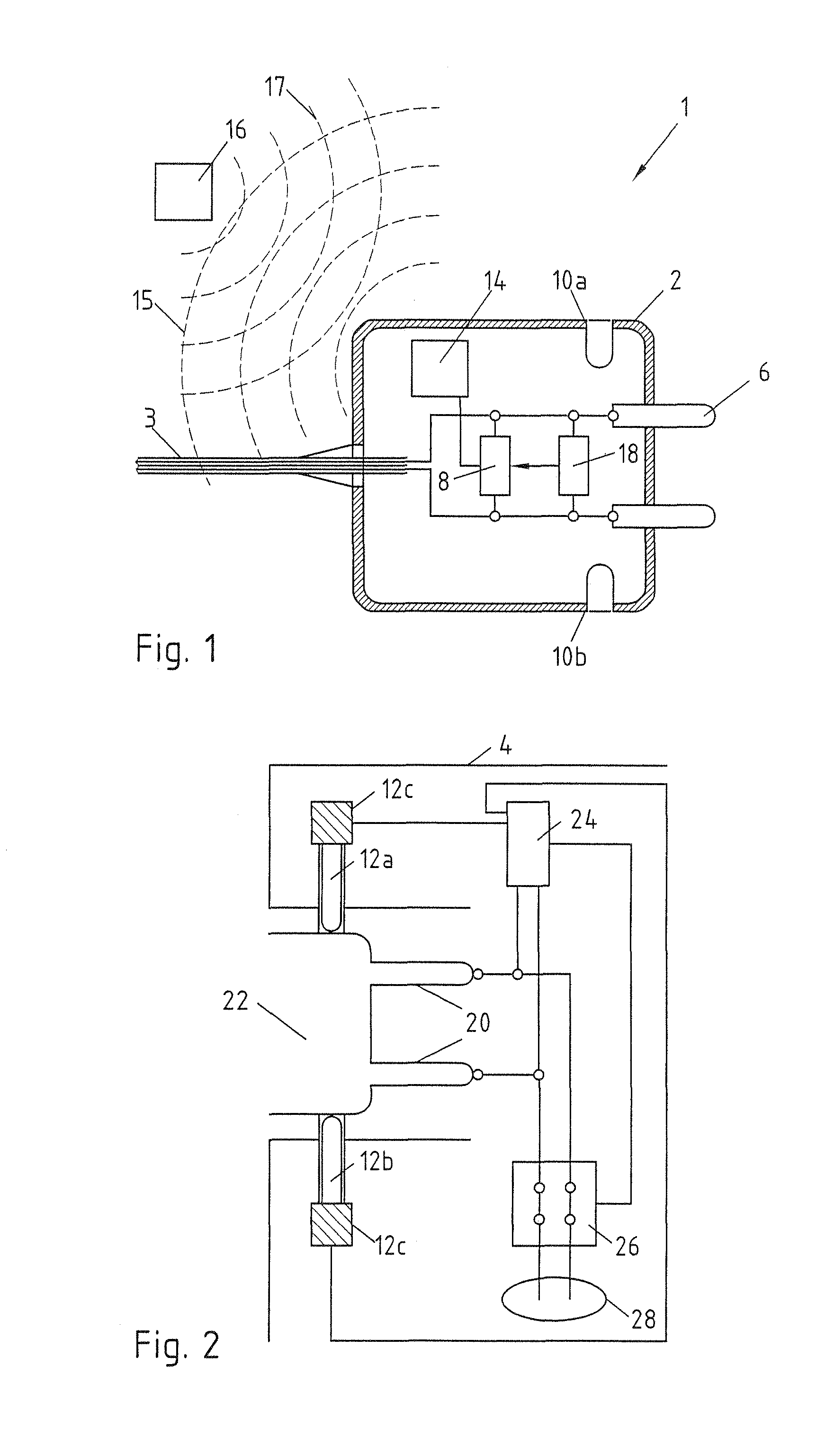
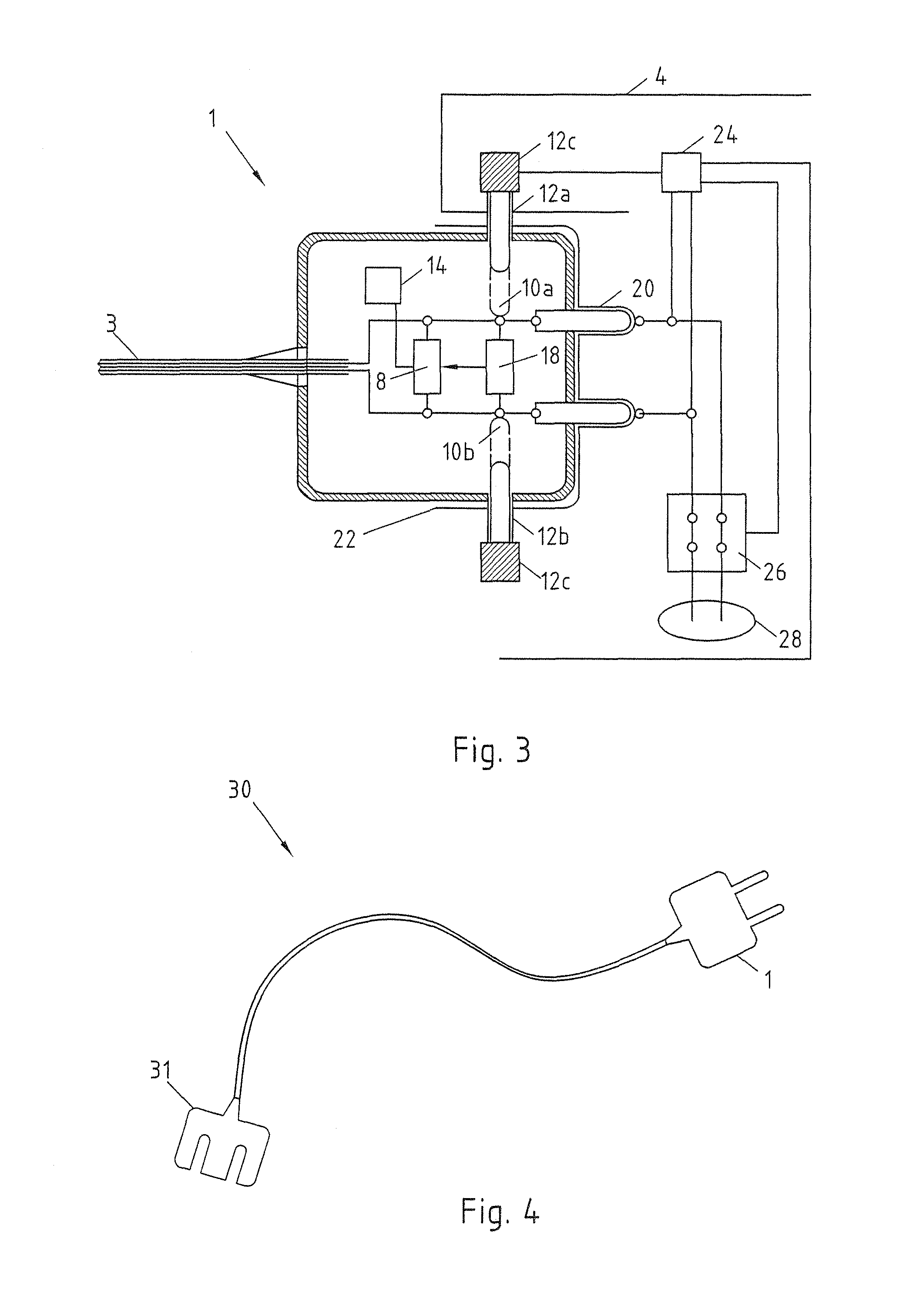
InactiveUS8900006B2Low costNot easy to changeElectrically conductive connectionsCharging stationsElectric carsIdentification device
Charging cable plug 1 for electric vehicles, with a housing 2 and electrical contacts 6, arranged in the housing 2, for connection to a charging station 4. For simple identification before a charging procedure, an identification means 8 is proposed, arranged in the housing 2 and communicating with the charging station 4 via the electrical contacts 6.
Owner:INNOGY SE
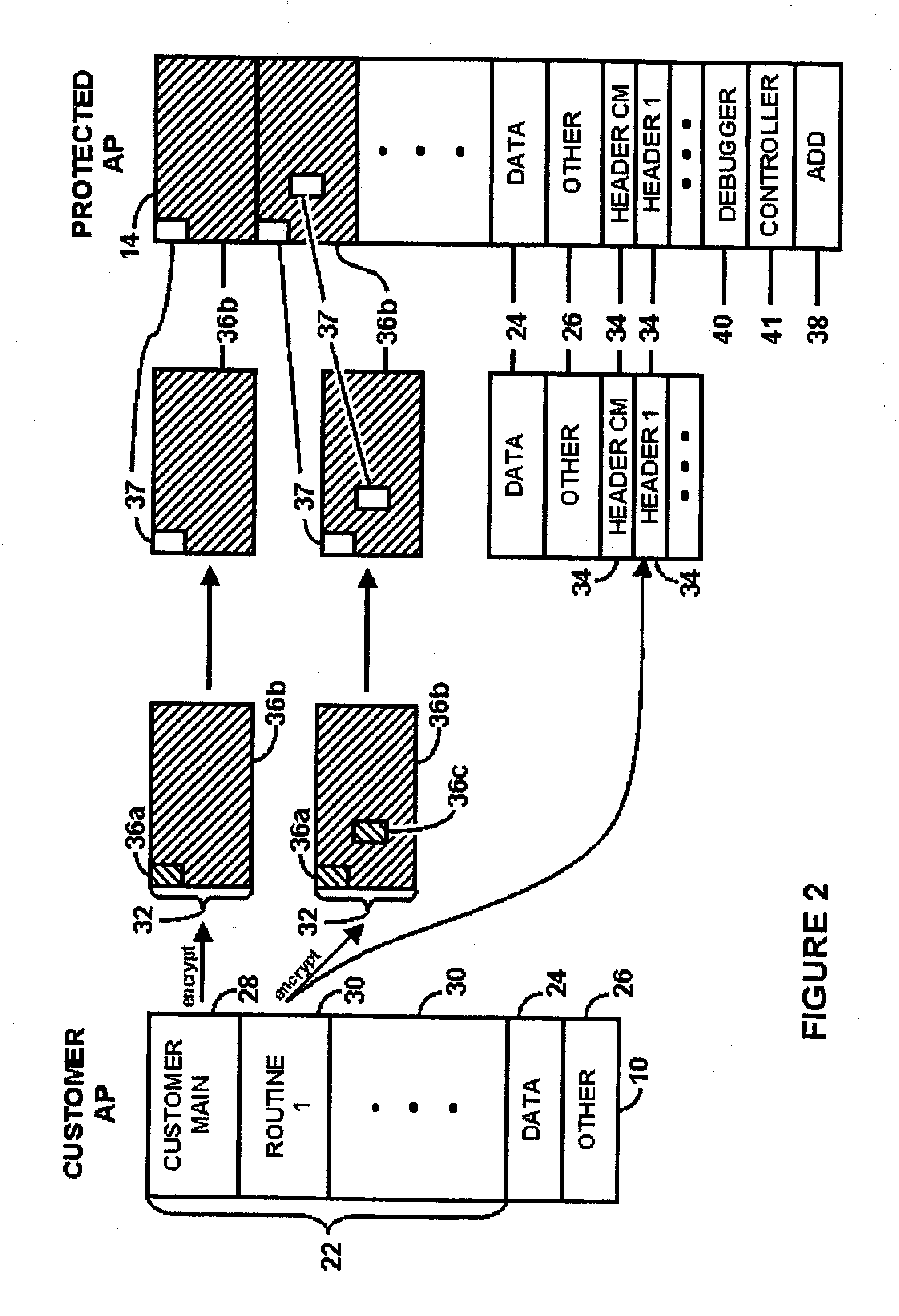
Systems And Methods For Regulating Execution Of Computer Software
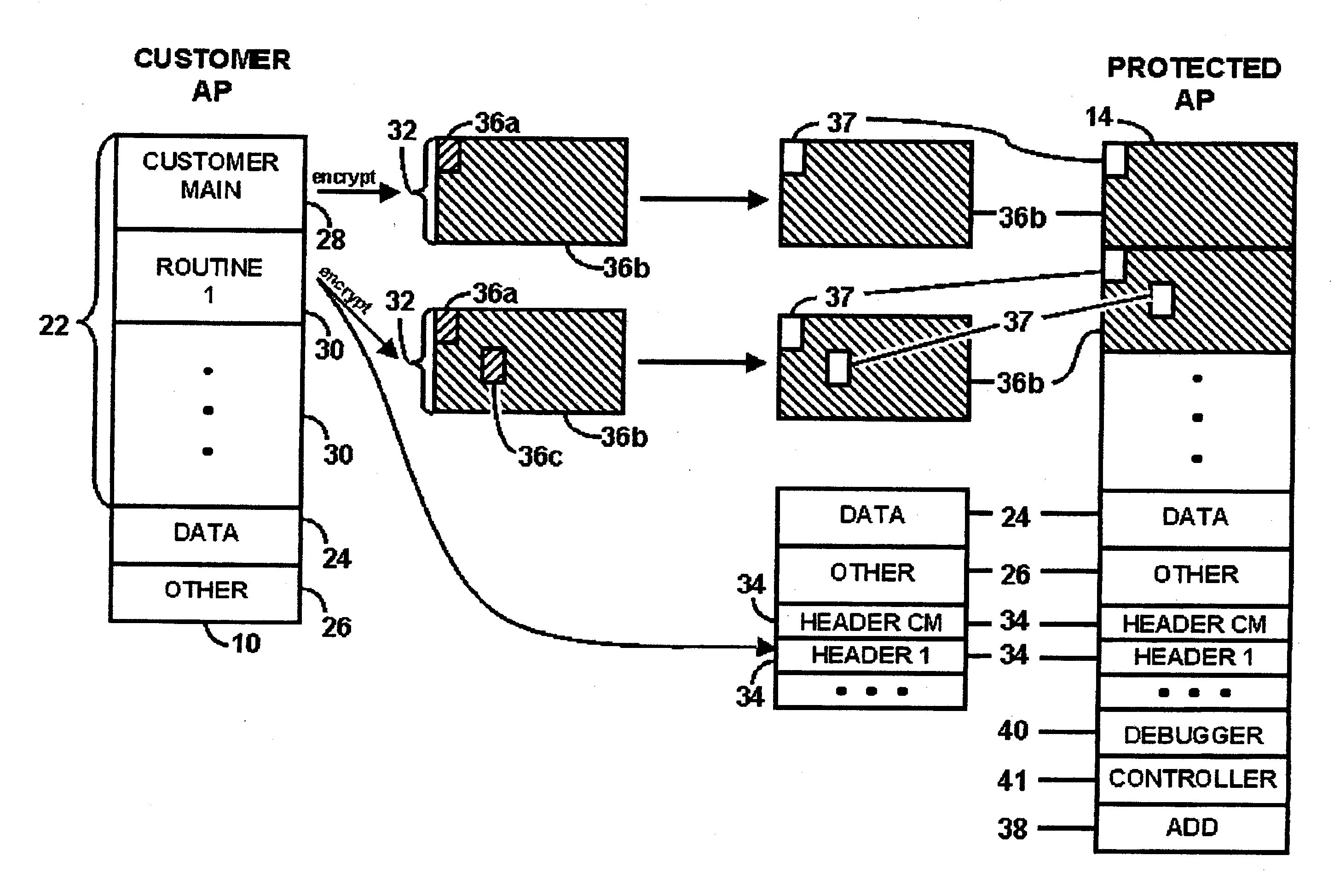
InactiveUS20090328003A1Access is deniedSacrificing protectionDigital computer detailsUnauthorized memory use protectionResponse processOperational system
A method for regulating execution of an application program includes a process for preparing the application and a process for executing the application. The preparation process divides the application program into related segments and encrypts instructions of at least one segment. The preparation process positions encrypted instructions in at least two discontiguous regions within an executable file and associates header information with at least one discontiguous region. The header identifies a decryption key and the location of the other discontiguous region. The resulting execution file thus has portions that would not execute and would cause an operating system to call a responsive process. The execution process initiates execution of the protected application when at least a portion of the application instructions are available to the computer only in encrypted form. The user is authenticated, after which the encrypted portions can be decrypted and execution resumed. The processes may also include capability to detect and respond to tampering, or the ability to block execution snooping via a debugger. Also provided are systems and methods to allow debugging of code extensions to protected applications without sacrificing protection of the application. A Secure Debugger allows extension developers to examine memory and set breakpoints in their own extensions, without permitting them to view information in the rest of the protected application.
Owner:REVULYTICS INC
Producing method of flexible wired circuit board
InactiveUS7323093B2Preclude obtainingAvoid pollutionPrinted circuit detailsDecorative surface effectsResistContamination
A producing method of a flexible wired circuit board that can prevent the formation of a gap between an elongate substrate and a stiffener sheet bonded thereto to prevent contamination of the flexible wired circuit board obtained. In the process subsequent to the process of forming a conductive pattern 3 on a surface of the elongate substrate 1 by the semi-additive process using electrolysis plating and then annealing the elongate substrate 1 with the conductive pattern 3 in its wound up state, a stiffener sheet 9 having a width narrower than the elongate substrate 1 is bonded to the back side of the elongate substrate 1. Thereafter, an oxidized film formed on a surface of the conductive pattern 3 is removed and then a solder resist 11 is formed thereon. This prevents the strip of the stiffener sheet 9 from the elongate substrate 1 and in turn prevents etching solution or developing solution from entraining in a gap therebetween.
Owner:NITTO DENKO CORP
Foil shaped electro-optical product, semi-finished product and method and apparatus for manufacturing the same
InactiveUS20130140528A1Strong curvatureAvoid structureFinal product manufactureSolid-state devicesConvex sideWork in process
A curved foil-shaped electro-optical product (1) is provided having at least a first region with a basis substrate layer (10) of a shrunken organic substance, having a convex side and a concave side and comprising at the convex side (12) of the basis substrate layer at least a further layer (20), the electro-optical product further comprising at least a second region with an electro-optical structure (20).
Owner:NEDERLANDSE ORG VOOR TOEGEPAST-NATUURWETENSCHAPPELIJK ONDERZOEK (TNO)
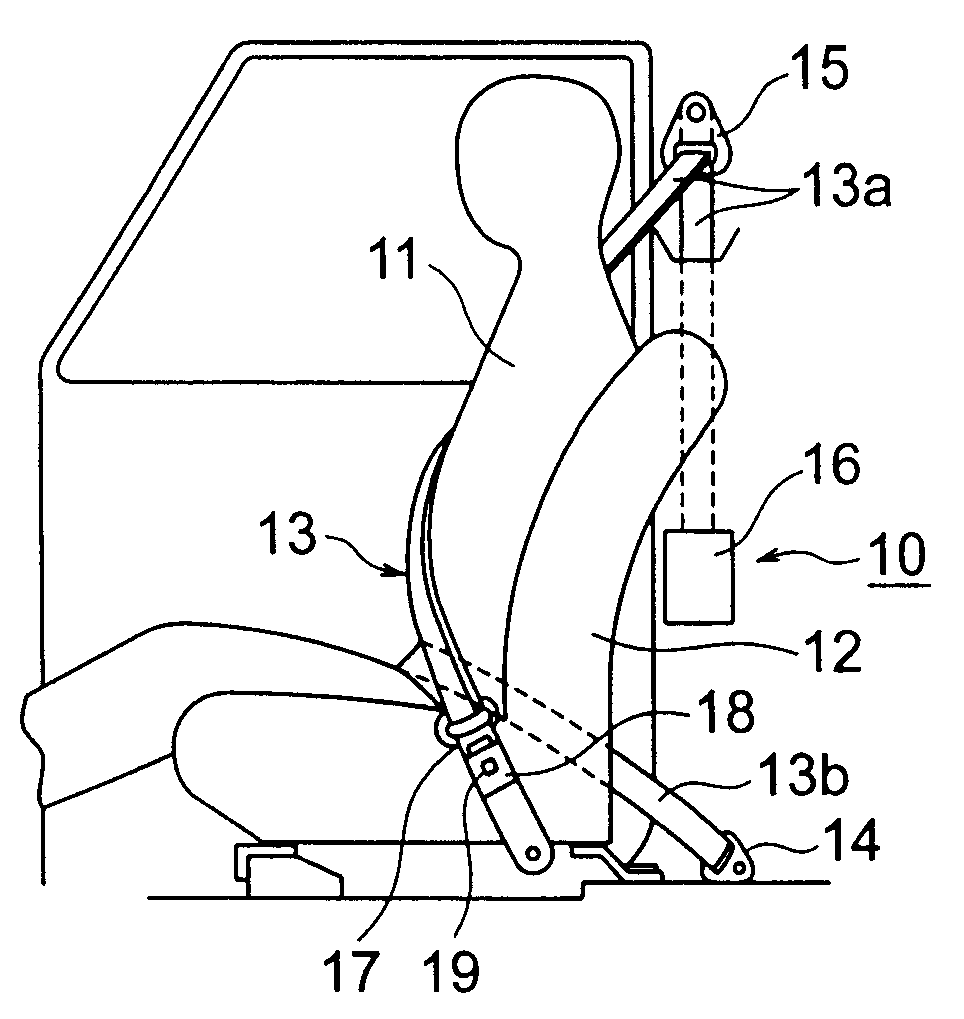
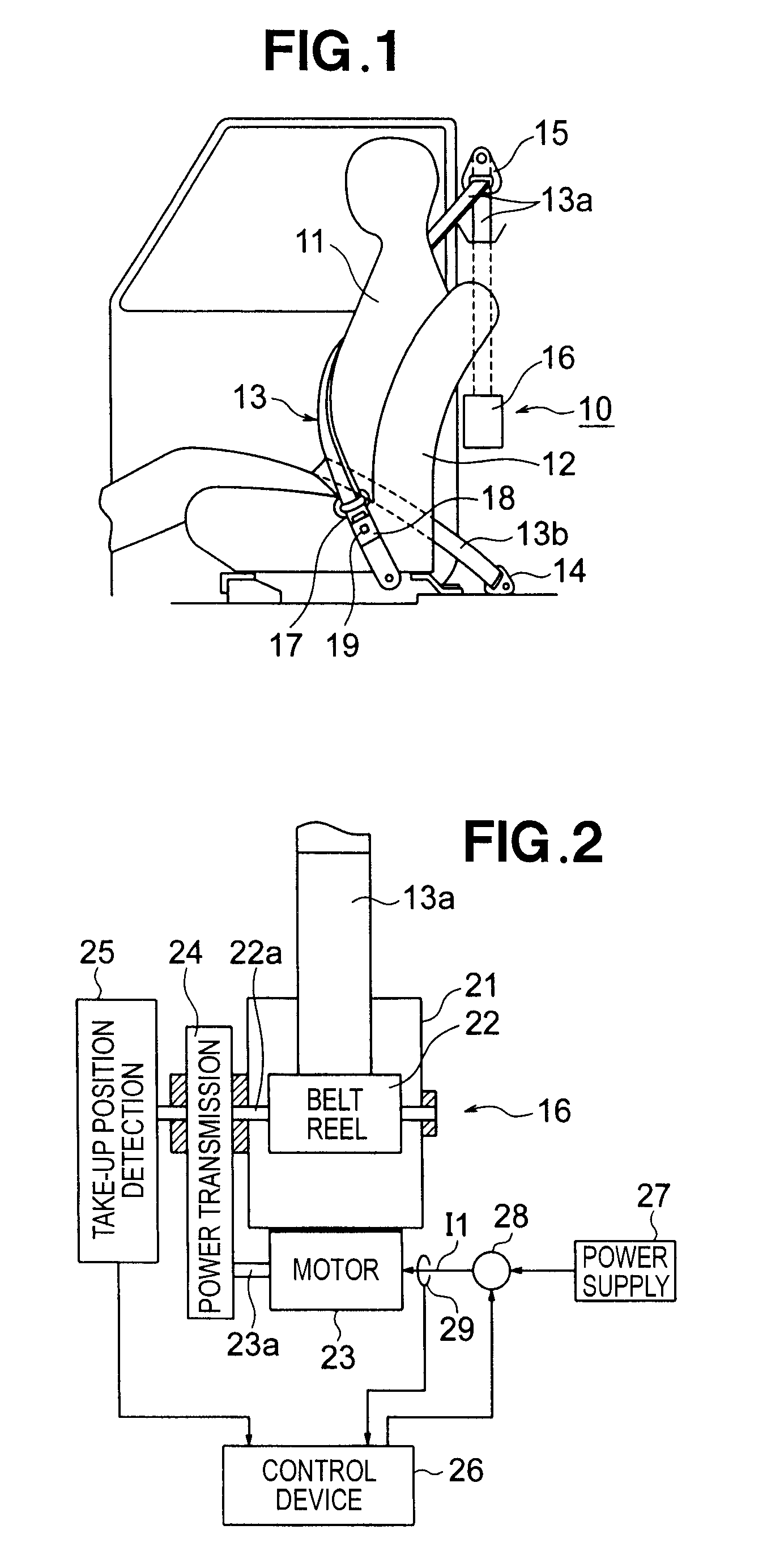
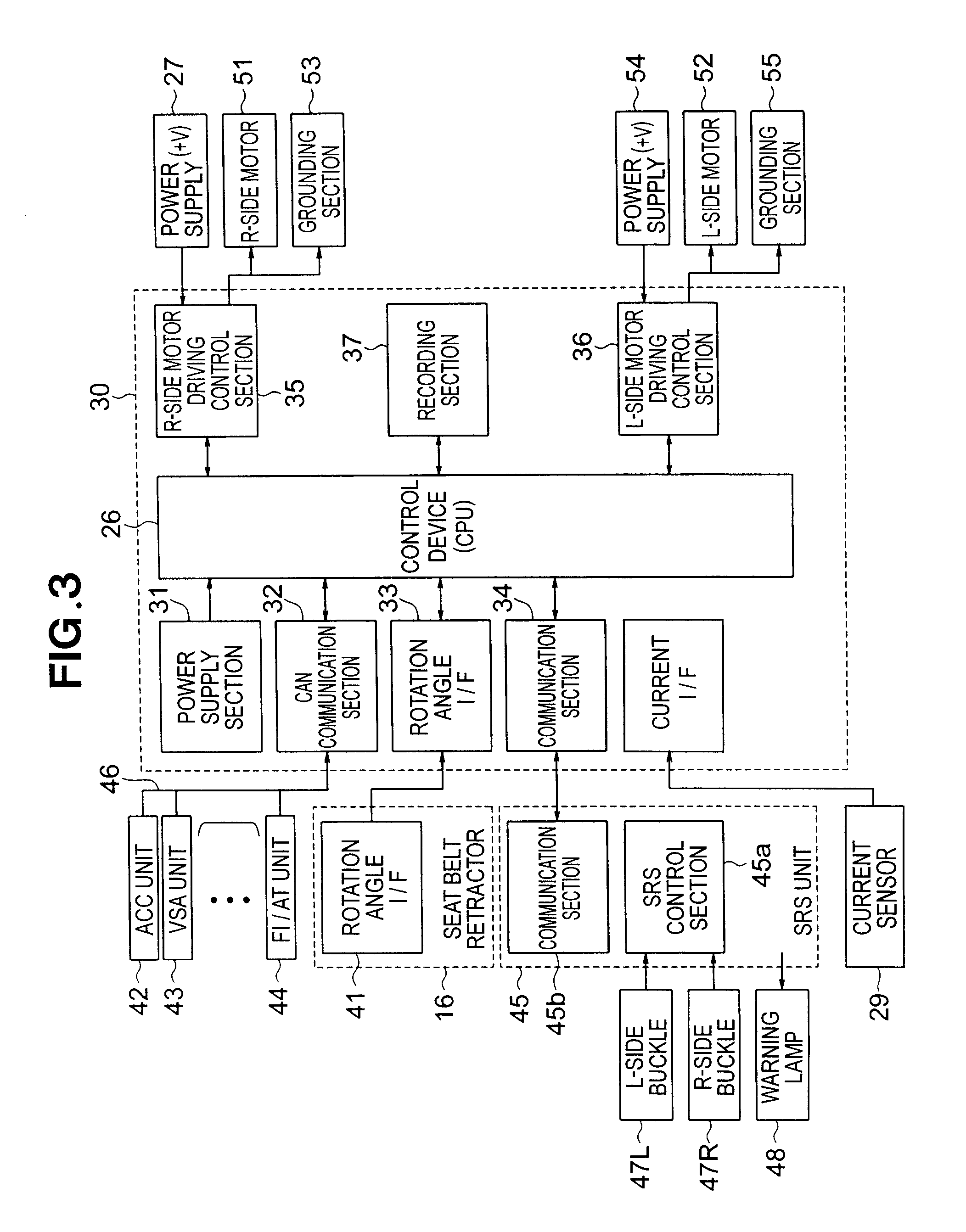
Vehicle seat belt apparatus
ActiveUS7664585B2Improve comfortStable tensionBelt retractorsDigital data processing detailsPower flowSeat belt
A seat belt apparatus includes a belt reel having a belt wound thereon, a motor for driving the reel to take up the belt; a control section for adjusting an amount of electric current supply to the motor to thereby control a belt-taking-up driving force of the motor, a current detection section for detecting the current supplied to the motor, and a rotation detection section for detecting a rotational position of the reel. The control section includes a constant current control section for executing a constant current control mode so that the current supply to the motor takes a target value, and a target current supply value change section for changing the target value when a detection signal from the rotation detection section has satisfied a predetermined condition in the constant current control mode.
Owner:HONDA MOTOR CO LTD
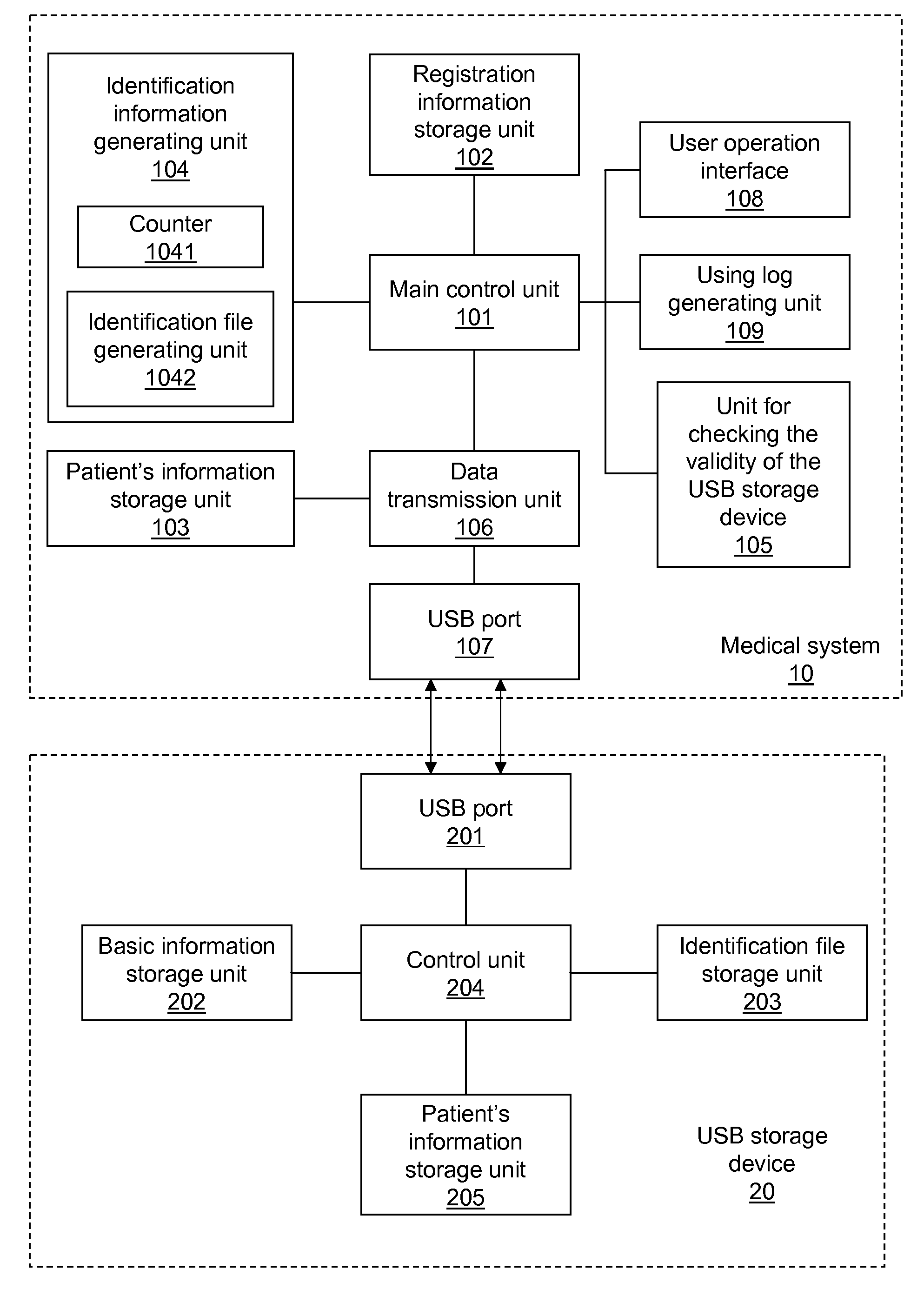
Method and system for protecting patient data
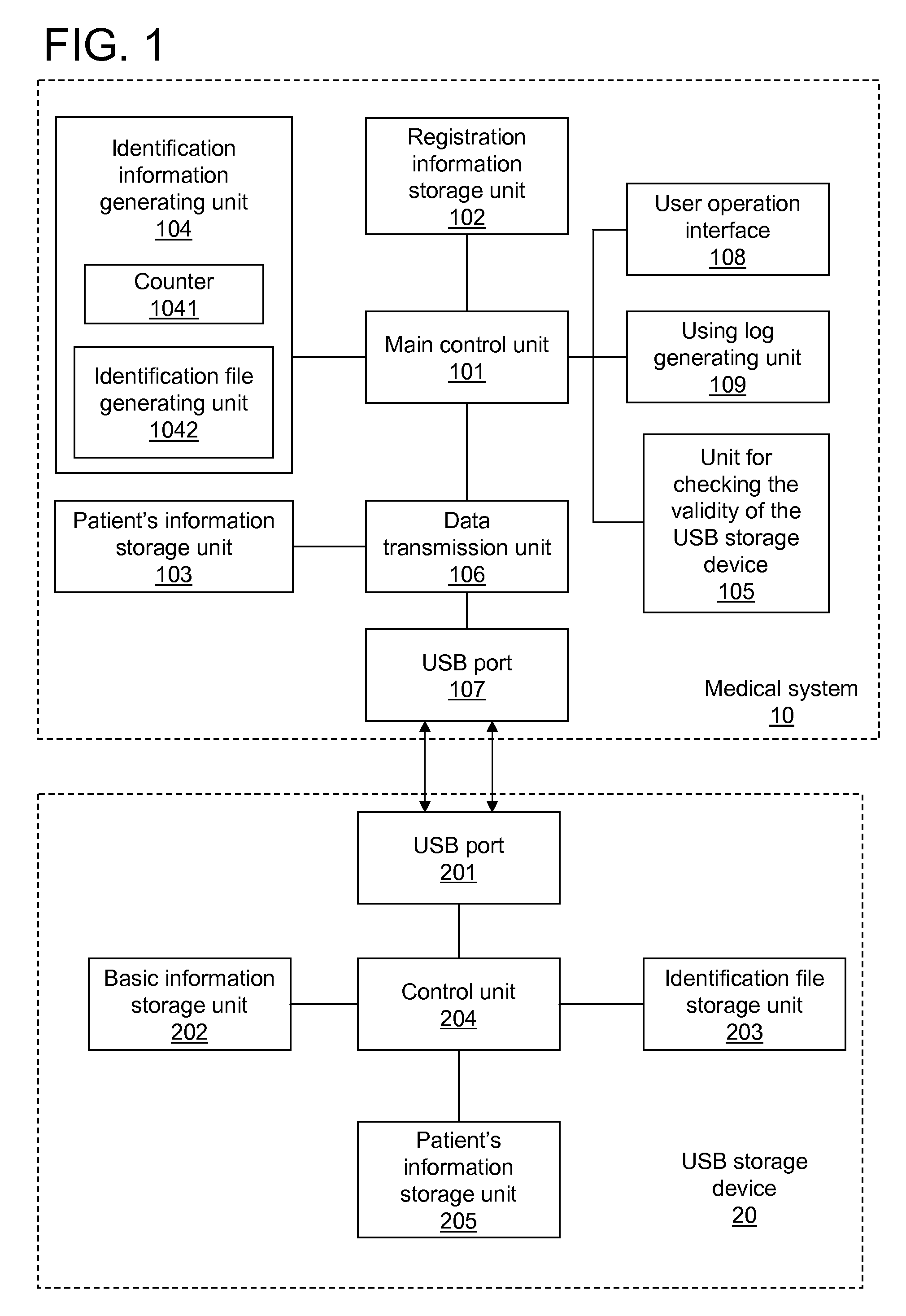
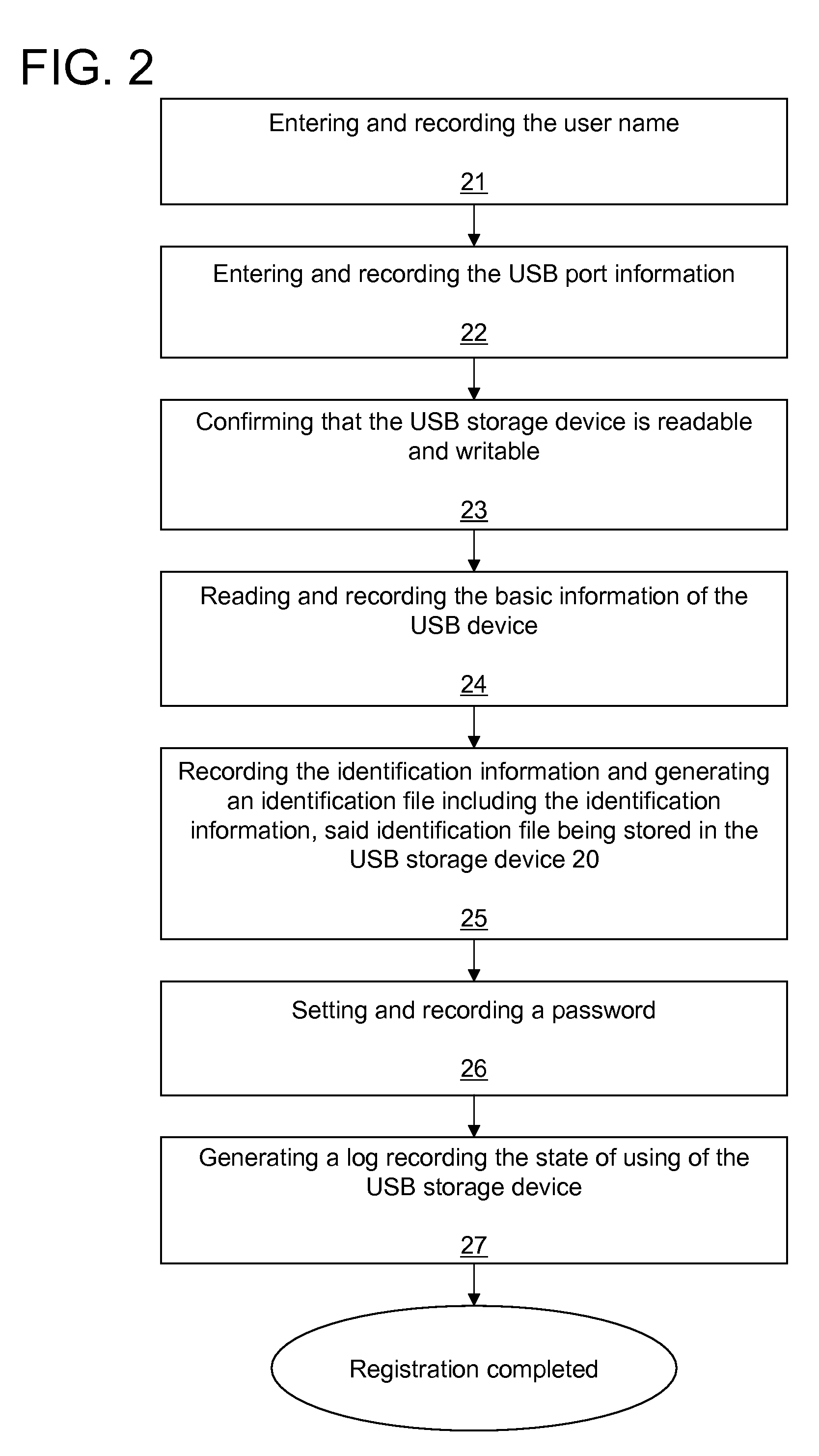
InactiveUS20090172406A1Effective protectionEnsuring security and confidentialityUser identity/authority verificationDigital data protectionPatient dataUSB
A method for a medical system to transmitting patient information to an external USB storage device includes checking the validity of the USB storage device according to the registered information therein, generating a new identification file according to a new times of using value that is incremented each time the validity checks are passed, and a unique ID number of the USB device, and writing the new identification file into the USB storage device to replace the old identification file.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
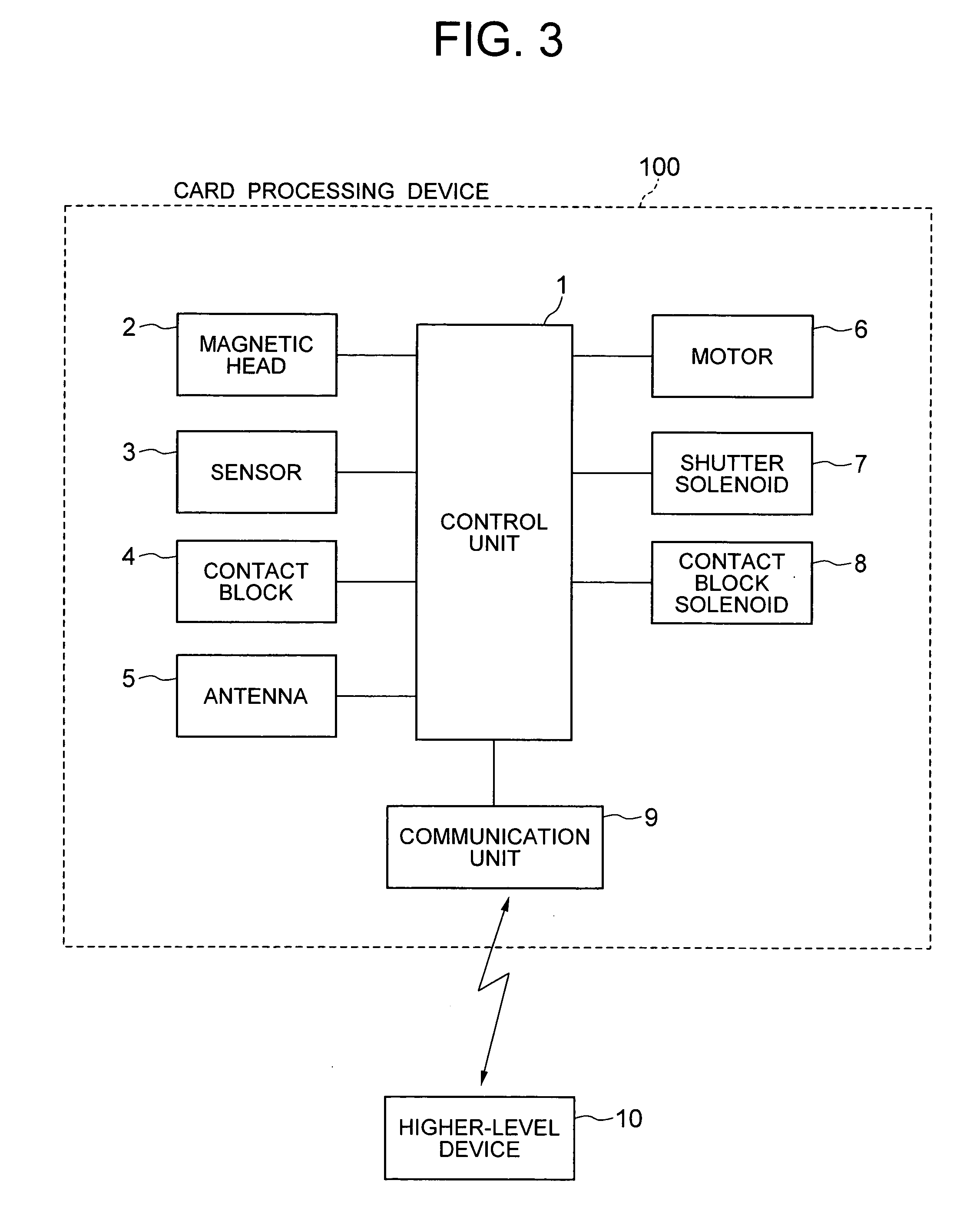
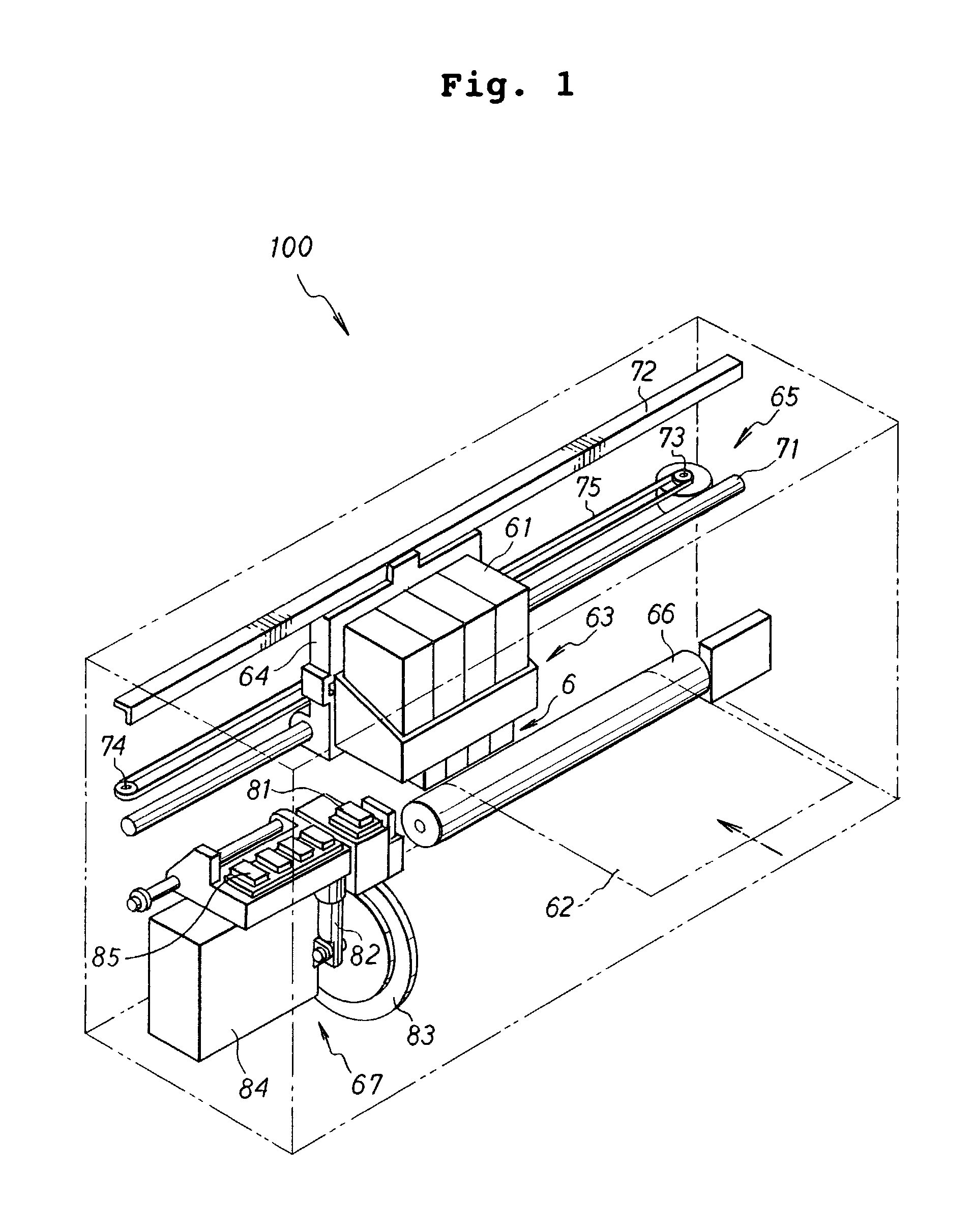
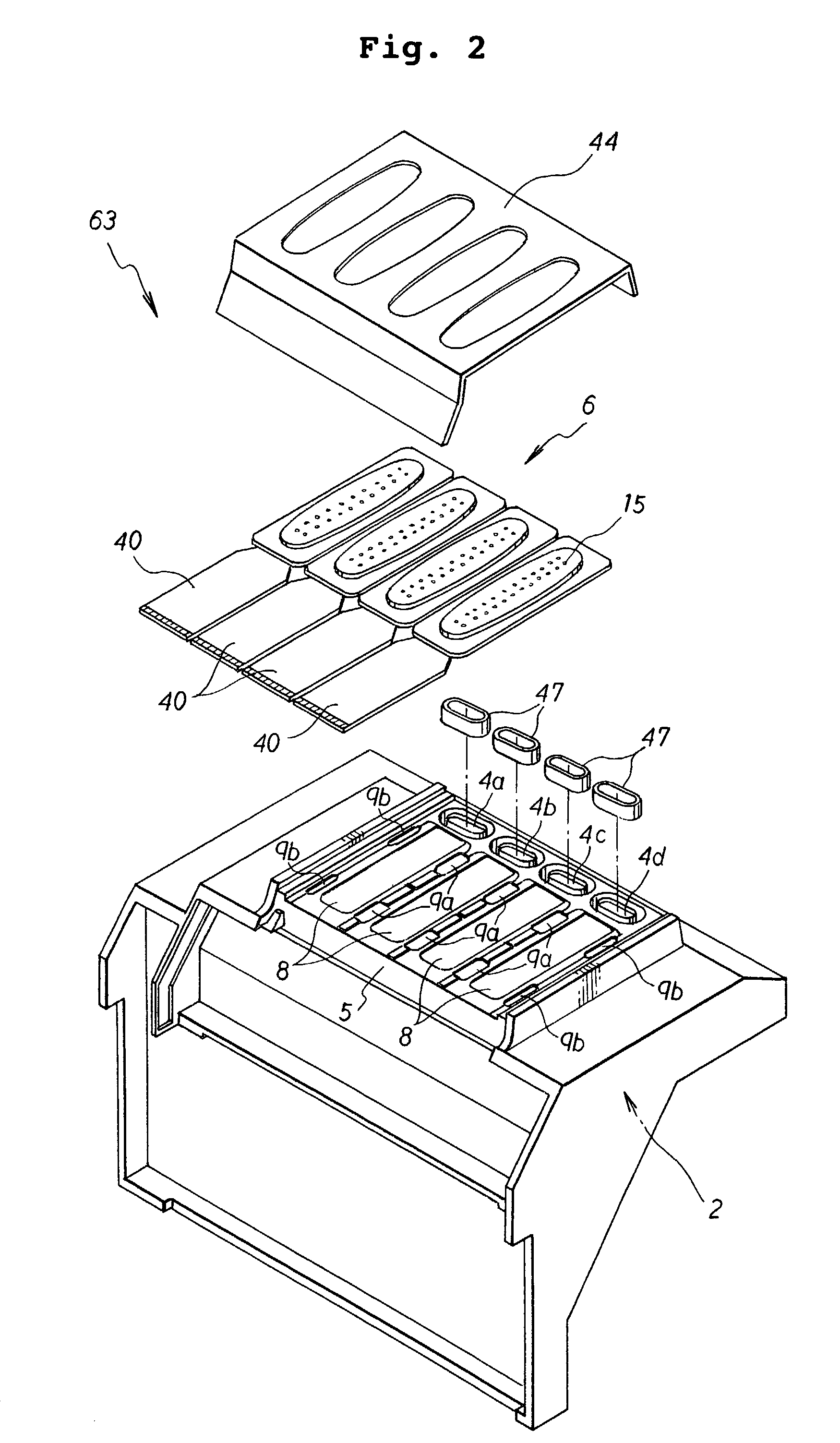
Card processing device
InactiveUS20070080231A1Prevents magnetic informationEasy to handleComplete banking machinesConveying record carriersComputer hardware
A card processing device (100) that handles a magnetic card and an IC card wherein, when a card (50) is taken into a main body (20) and if the card is a magnetic card, the inserted card (50) is taken in by intermittently transporting the card to a predetermined position and, after that, by continuously transporting the card and, if the card is an IC card, the inserted card (50) is taken in by continuously transporting the card. When the card (50) is ejected out of the main body (20) and if the card is a magnetic card, the card is ejected by continuously transporting the card to a predetermined position and, after that, by intermittently transporting the card and, if the card is an IC card, the card is ejected by continuously transporting the card.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
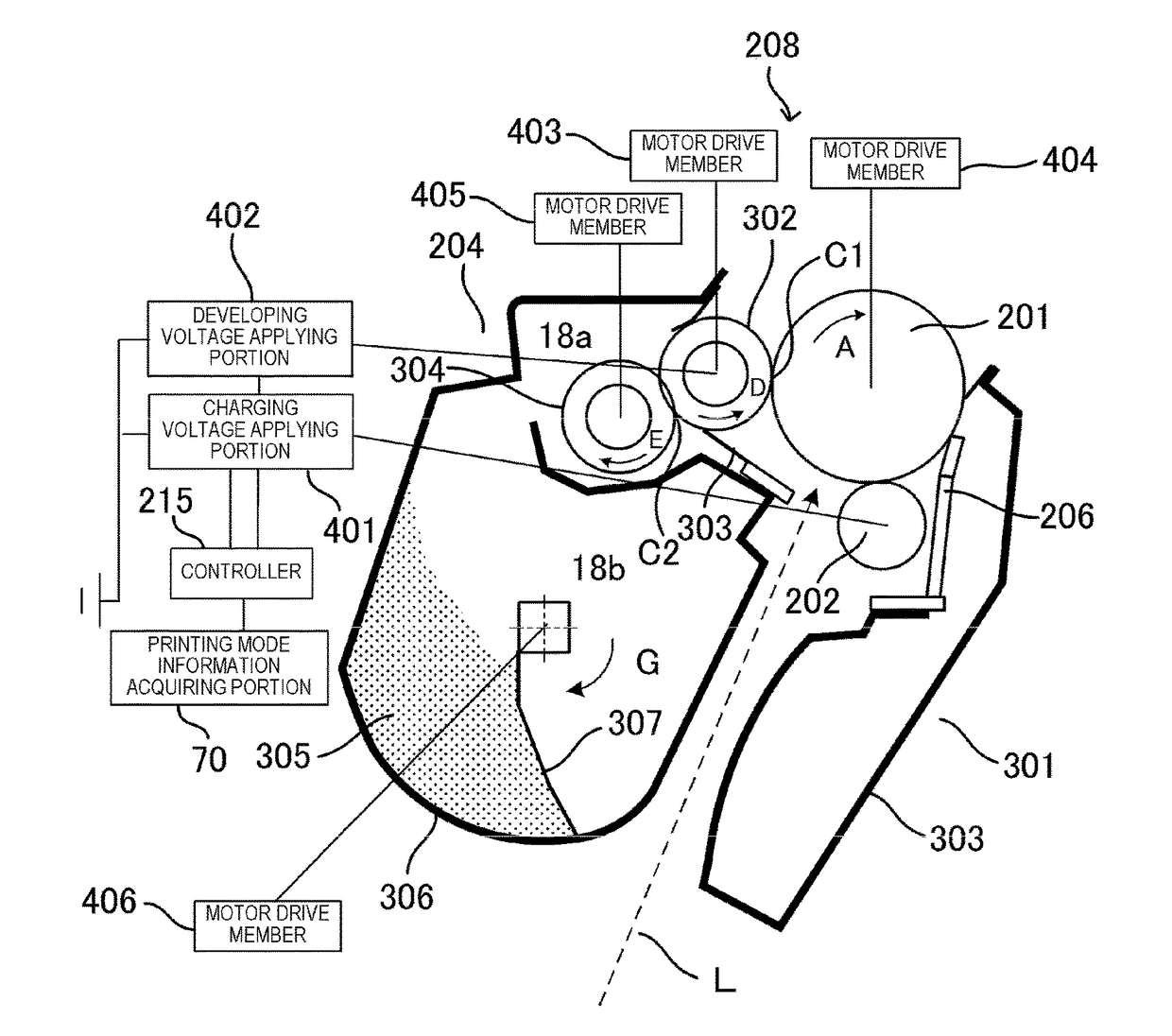
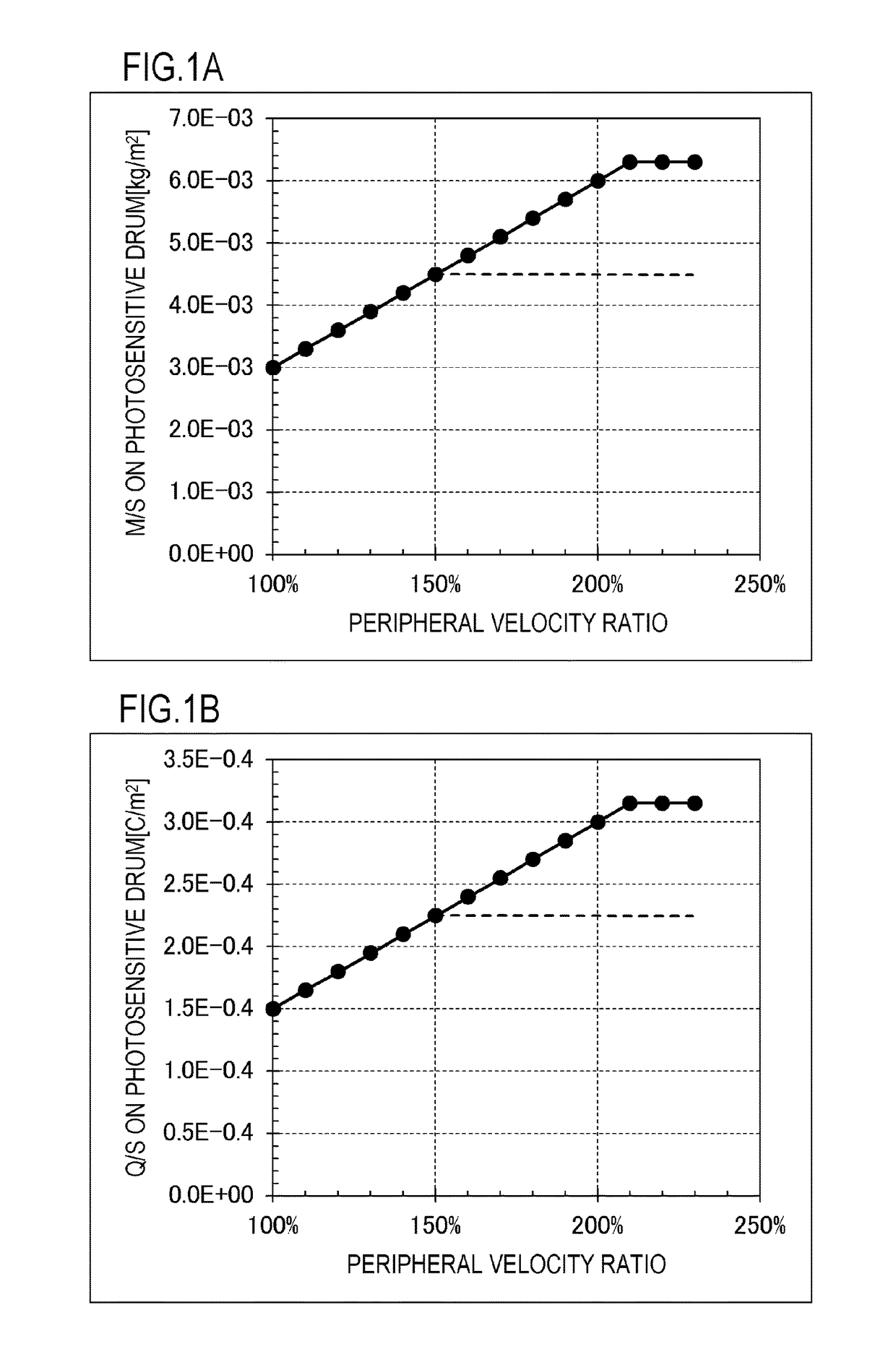
Image forming apparatus
ActiveUS20170277068A1Tinge selection range be increasedSupply amount is increasedElectrographic process apparatusCapacitanceImage formation
When, in a state where a developer borne by a developer bearing member is sandwiched by an opposing portion of an image bearing member and the developer bearing member, C denotes capacitance between the image bearing member and the developer bearing member, ΔV denotes a development contrast, Q / S denotes a charge amount per unit area of the developer borne by the developer bearing member, and Δv denotes a peripheral velocity ratio which is a ratio of a peripheral velocity of the developer bearing member to a peripheral velocity of the image bearing member, a first peripheral velocity ratio is set so that |Q / S×Δv|≦|C×ΔV| is satisfied, and a second peripheral velocity ratio which is larger than the first peripheral velocity ratio is set so that |Q / S×Δv|>|C×ΔV| is satisfied.
Owner:CANON KK
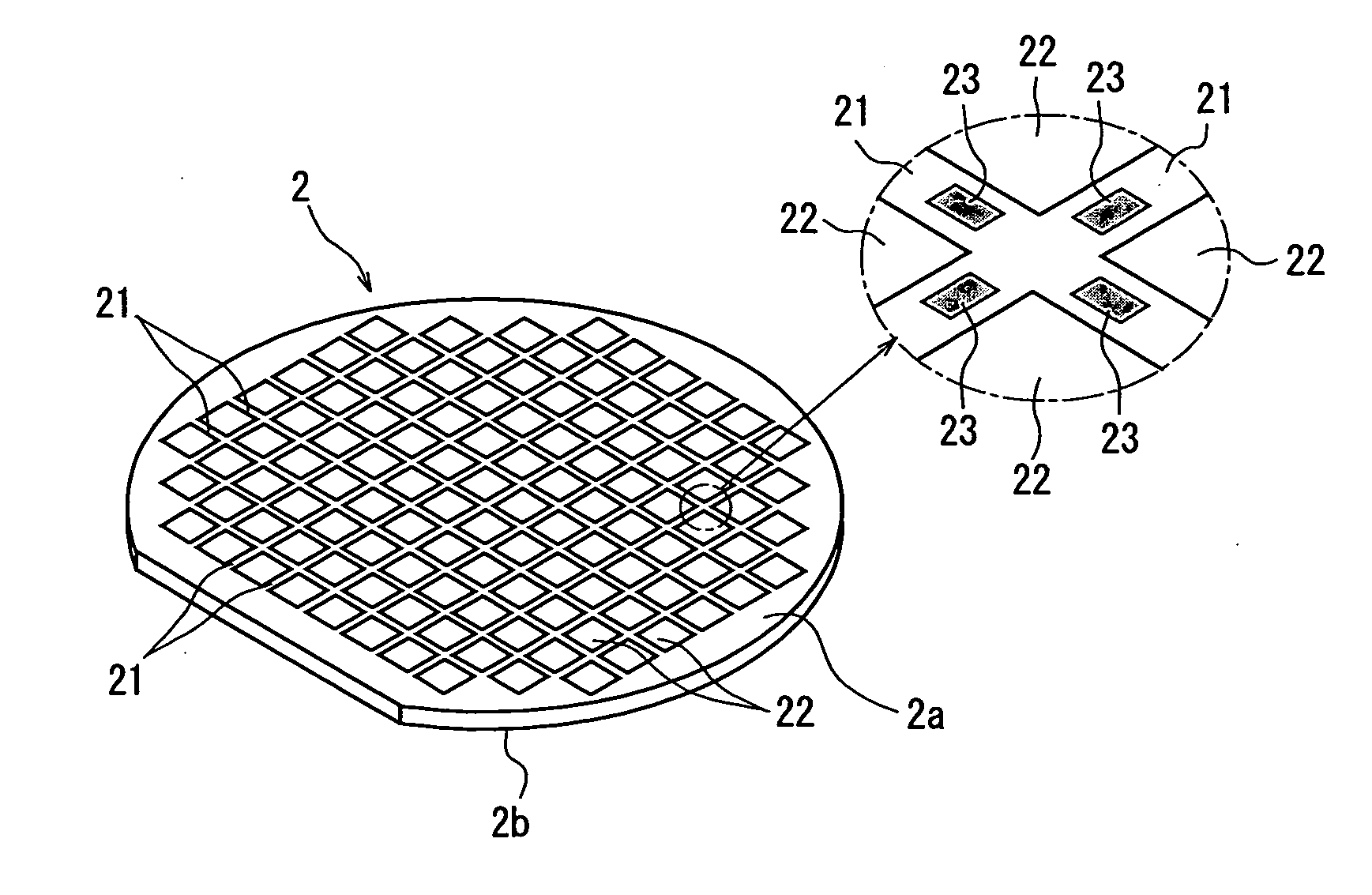
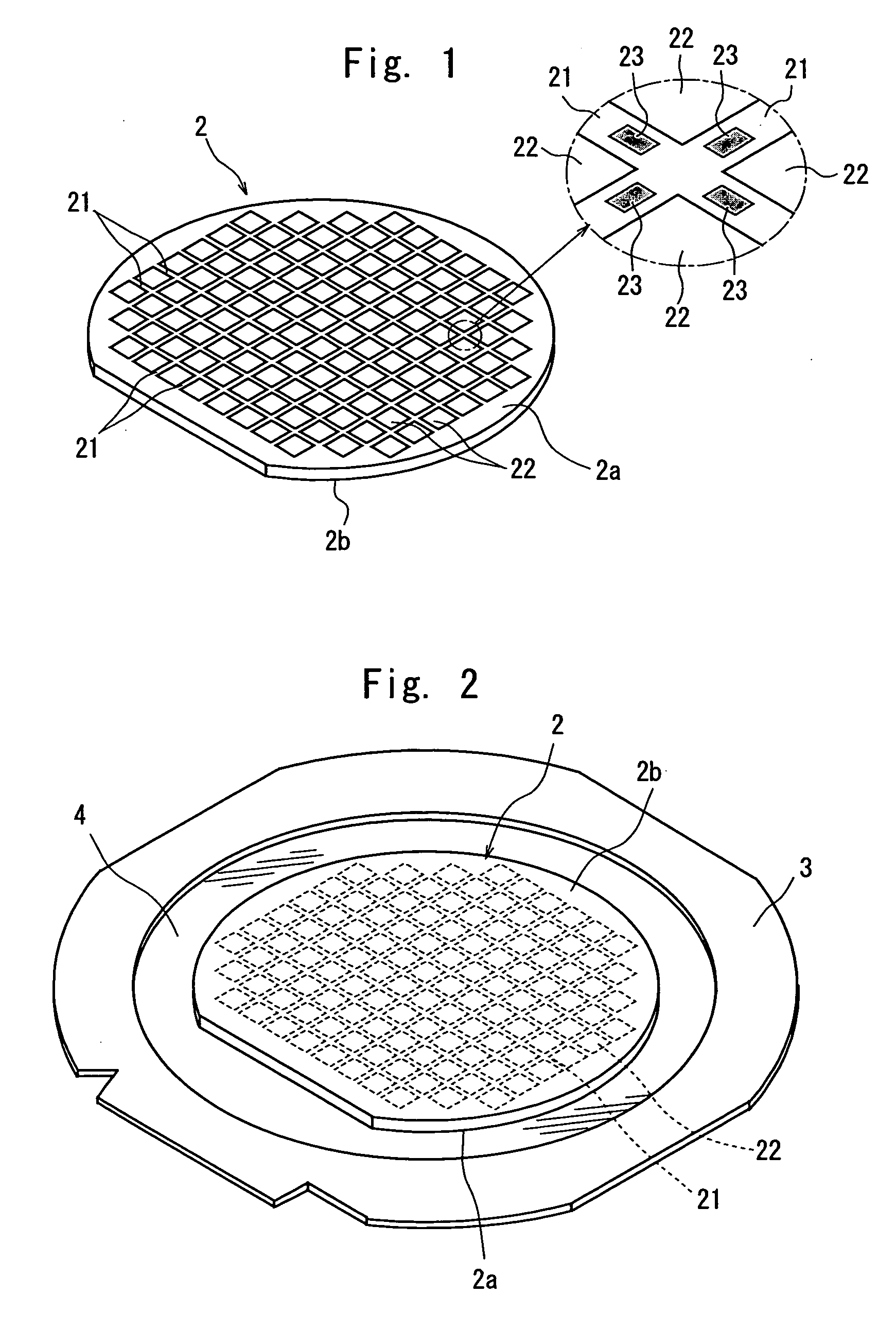
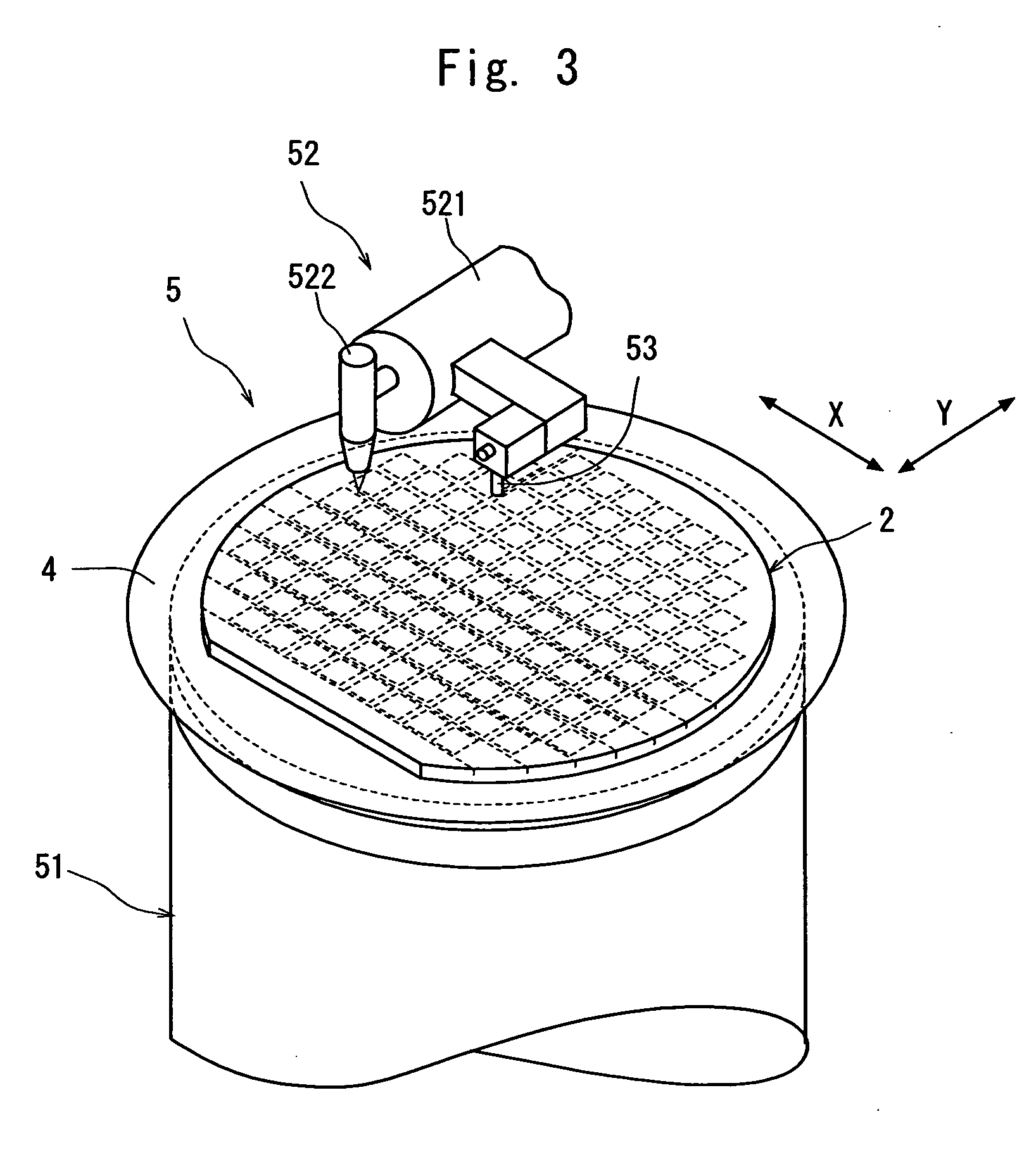
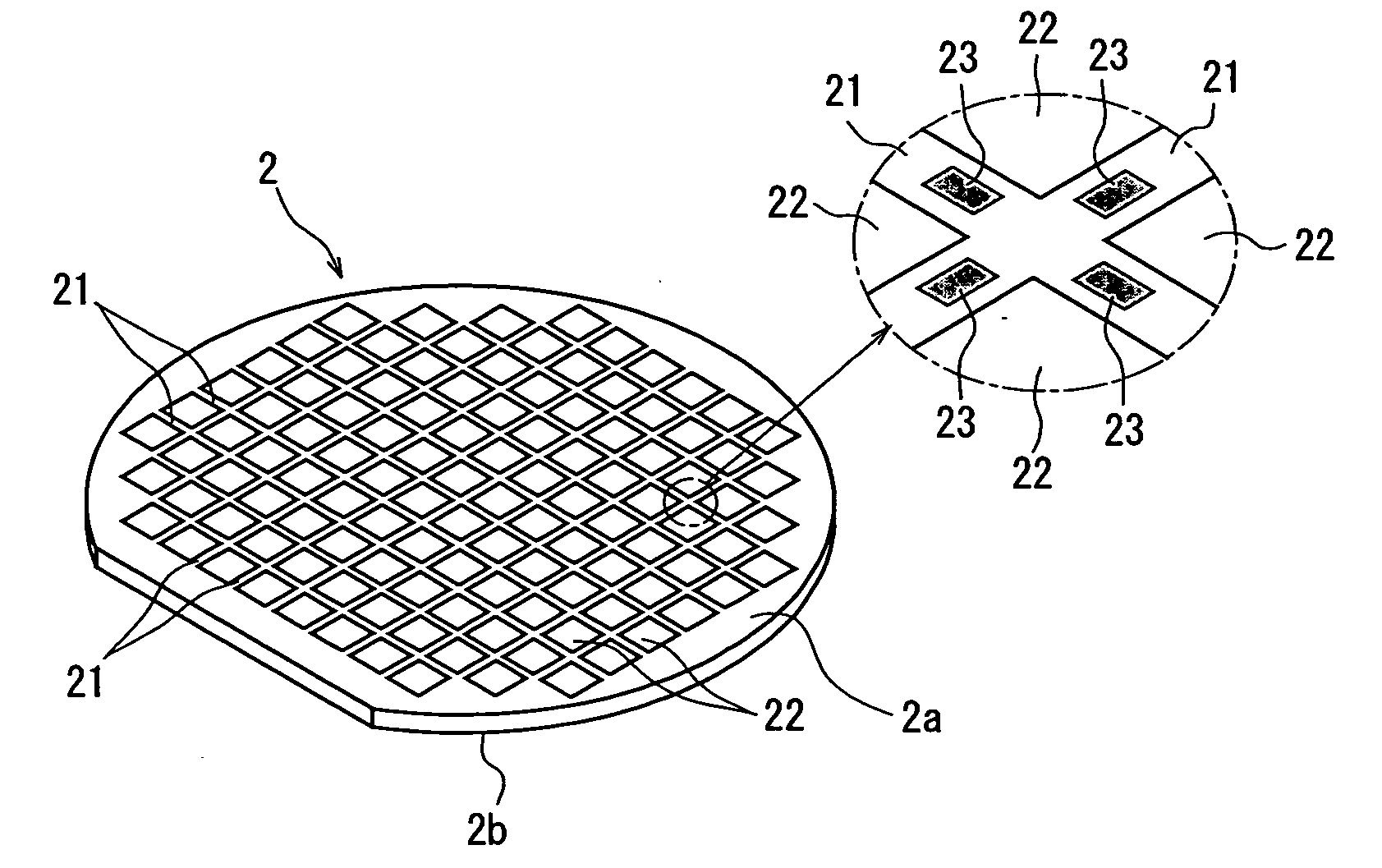
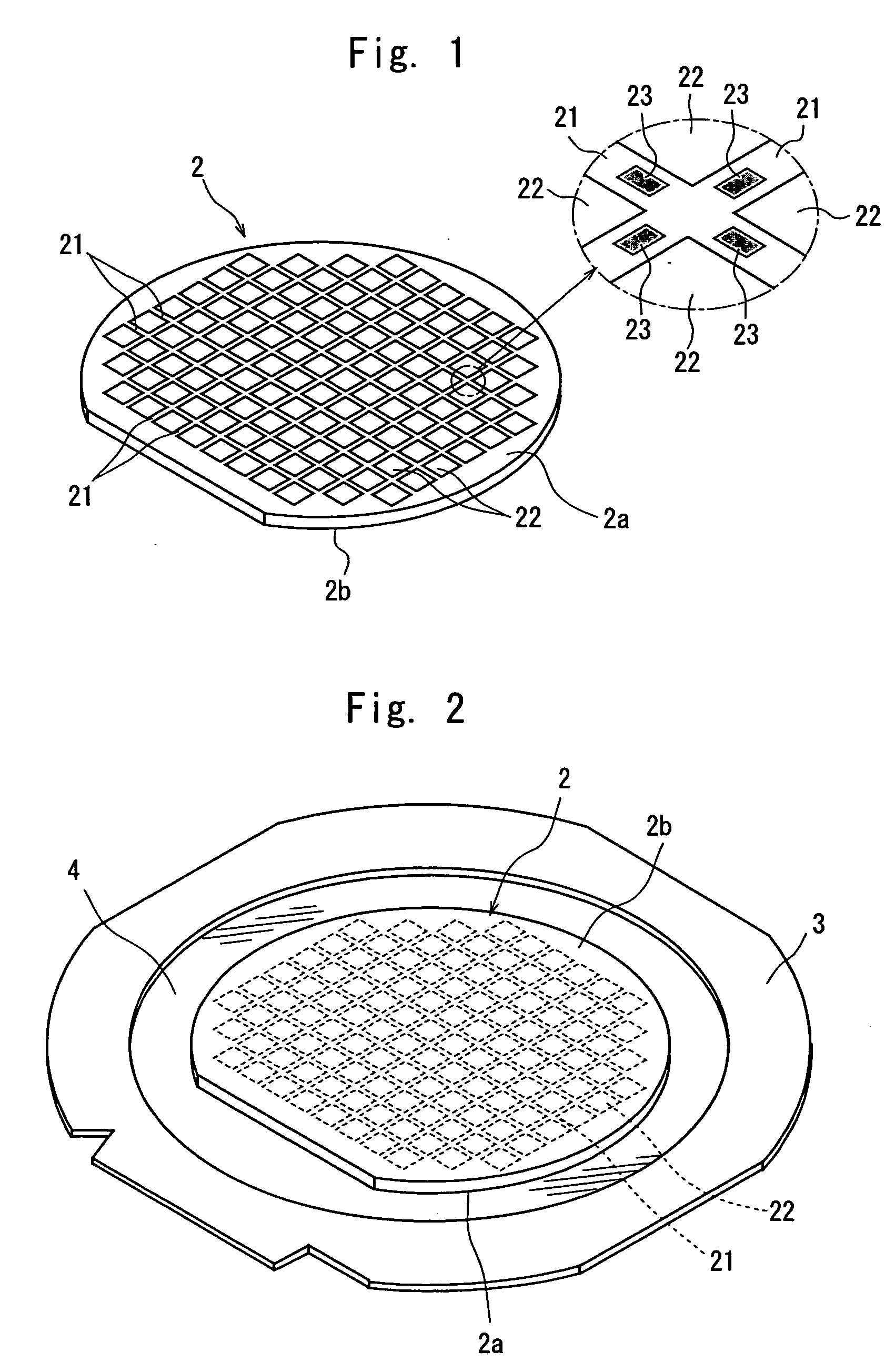
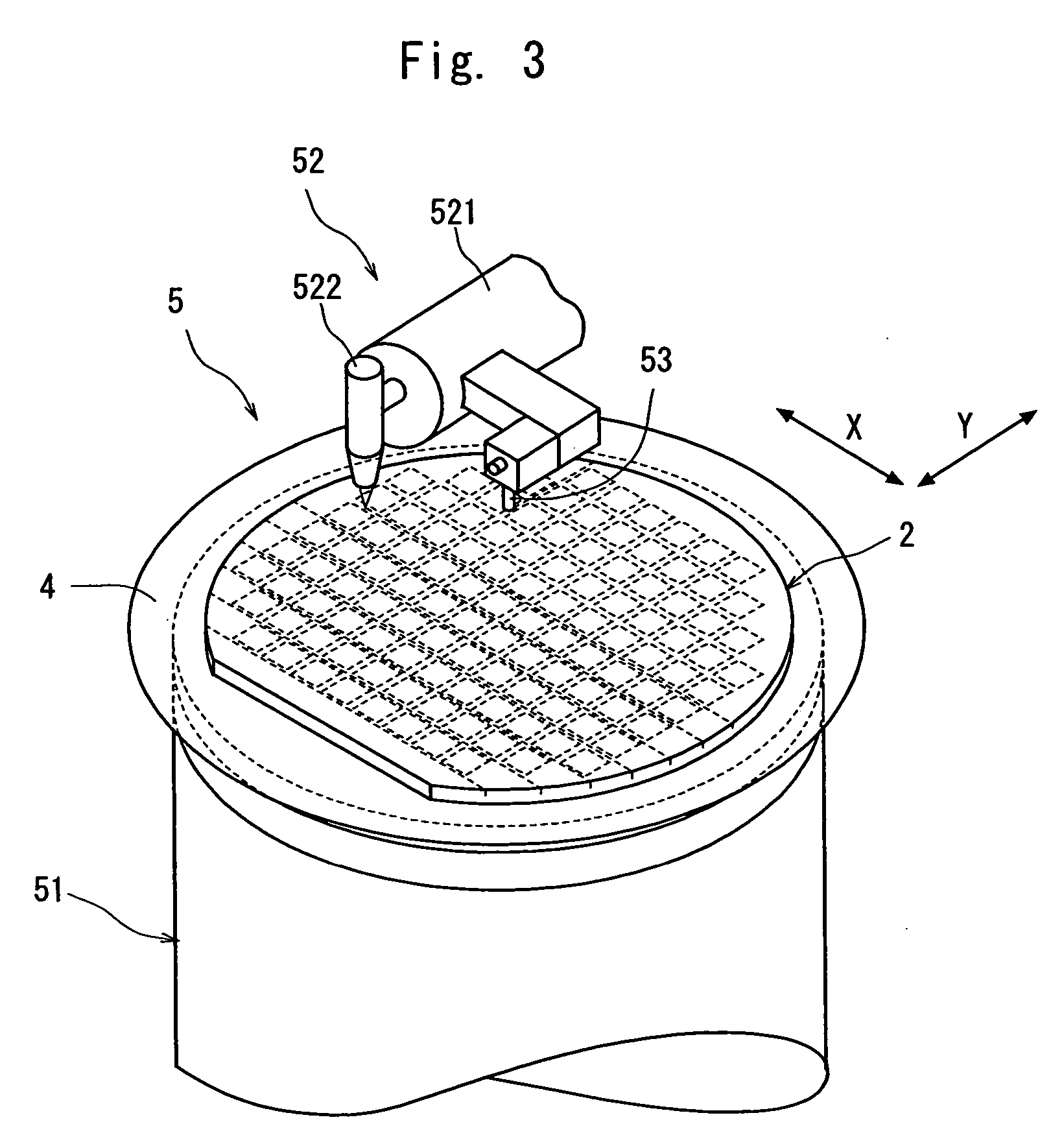
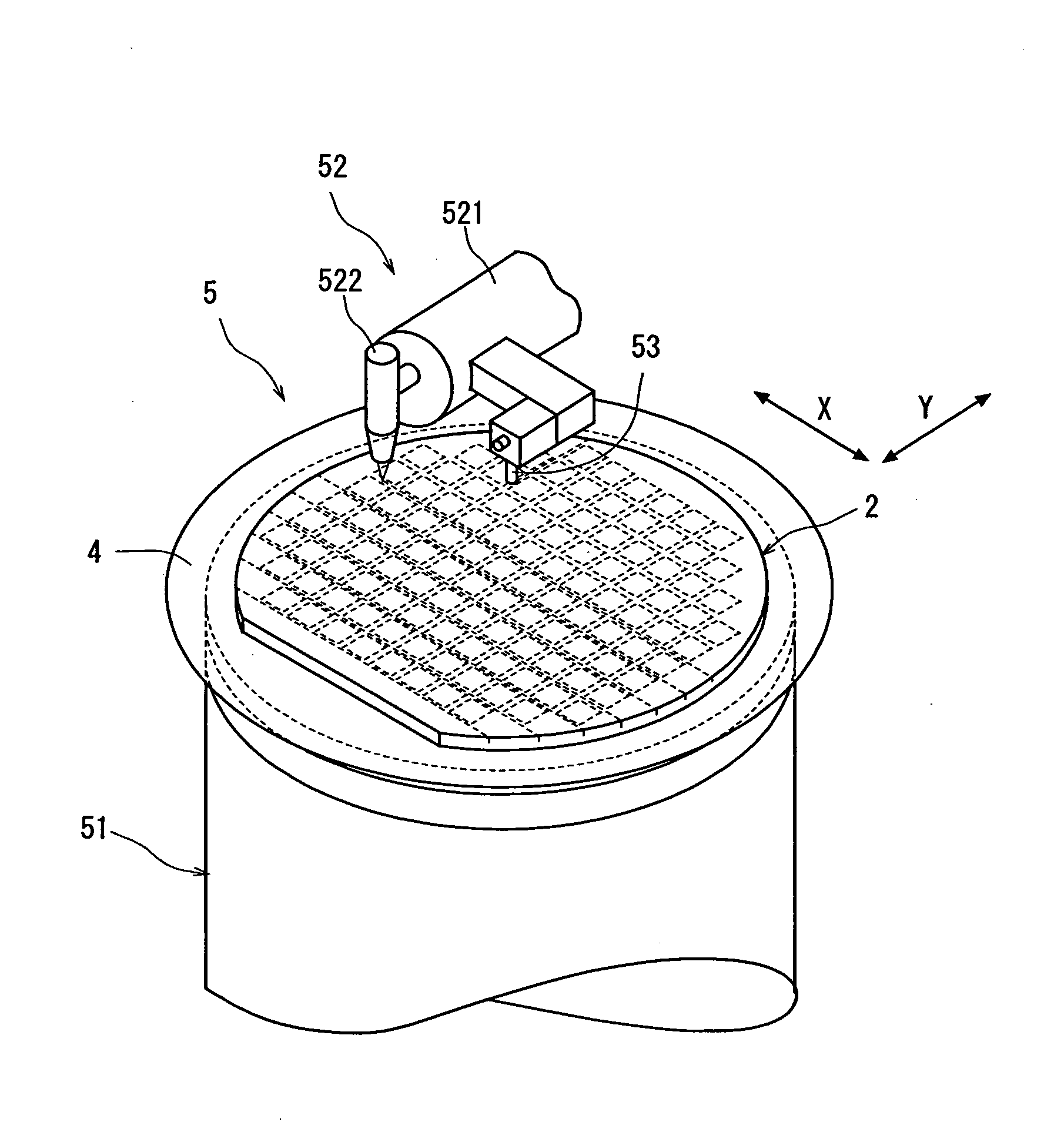
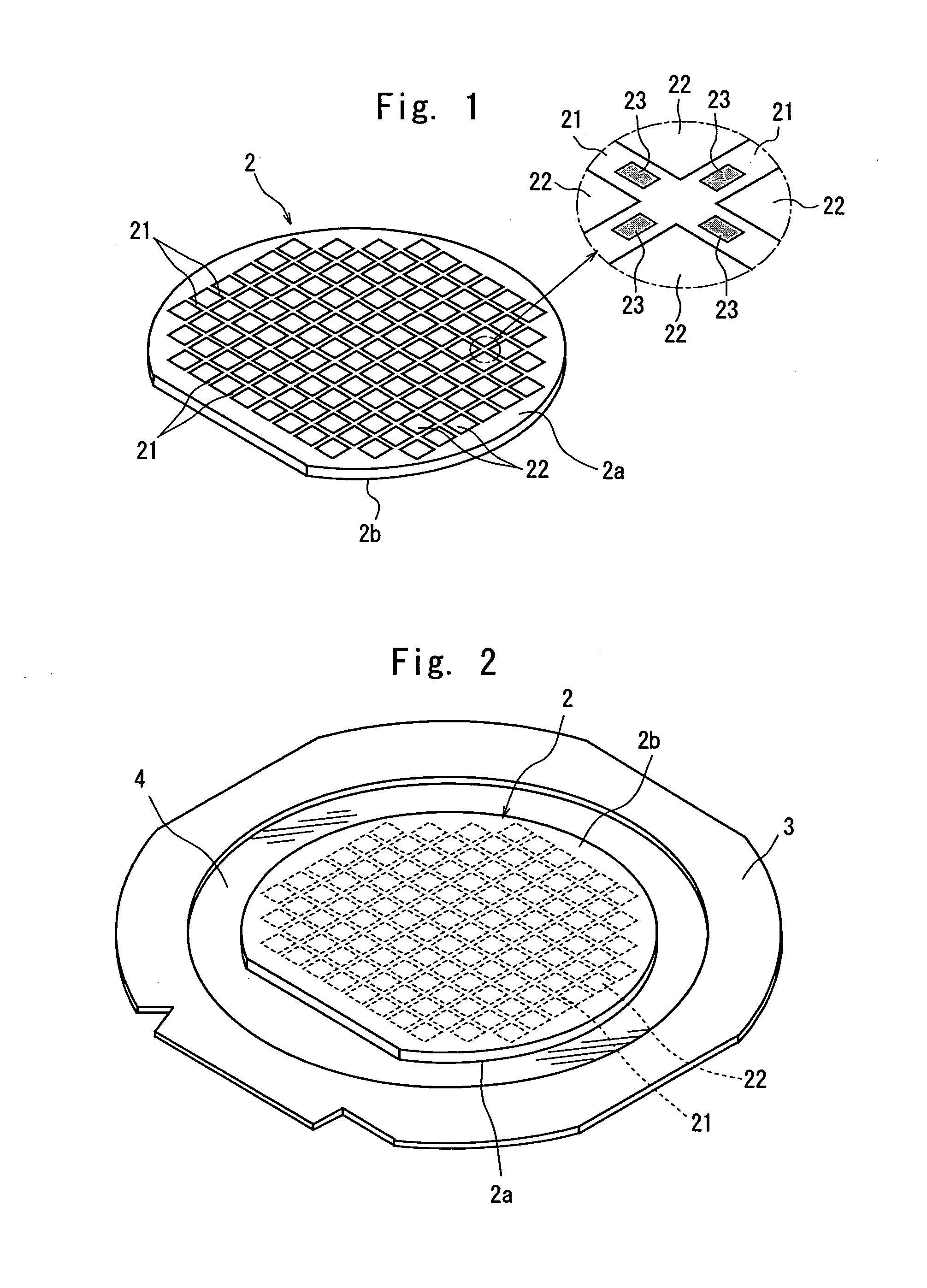
Wafer dividing method
ActiveUS20060281226A1Prevent detectionPreclude obtainingSemiconductor/solid-state device detailsSolid-state devicesPhysicsMetal
A method of dividing a wafer having a plurality of devices, which are formed in a plurality of areas sectioned by streets formed in a lattice pattern on the front surface, and having test metal patterns which are formed on the streets, comprising the steps of: a laser beam application step for carrying out laser processing to form a dividing start point along a street on both sides of the test metal patterns by applying a laser beam along the street on both sides of the test metal patterns in the street formed on the wafer; and a dividing step for dividing the wafer which has been laser processed to form dividing start points along the dividing start points by exerting external force to the wafer, resulting in leaving the streets having the test metal patterns formed thereon behind.
Owner:DISCO CORP
Wafer dividing method
ActiveUS20070004179A1Preclude obtainingSemiconductor/solid-state device testing/measurementSemiconductor/solid-state device manufacturingOptoelectronicsPulsed laser beam
A method of dividing a wafer having a plurality of devices, which are formed in a plurality of areas sectioned by streets formed in a lattice pattern on the front surface and test metal patterns which are formed on the streets, comprising: a metal pattern breaking step for forming a break line in the test metal patterns by applying a pulse laser beam having permeability to the wafer to the rear surface of the wafer with its focal point set to a position near the test metal patterns; a deteriorated layer forming step for forming a deteriorated layer along the streets above the break lines in the inside of the wafer by applying a pulse laser beam having permeability to the wafer to the rear surface of the wafer with its focal point set to a position above the break lines in the inside of the wafer; and a dividing step for dividing the wafer into individual chips along the deteriorated layers of the wafer by exerting external force to the wafer having the deteriorated layers formed therein.
Owner:DISCO CORP
Wafer dividing method
ActiveUS20080153264A1Preclude obtainingSemiconductor/solid-state device detailsSolid-state devicesLaser processingMetal
A method of dividing a wafer having a plurality of devices, which are formed in a plurality of areas sectioned by streets formed in a lattice pattern on the front surface, and having test metal patterns which are formed on the streets, comprising the steps of: a laser beam application step for carrying out laser processing to form a dividing start point along a street on both sides of the test metal patterns by applying a laser beam along the street on both sides of the test metal patterns in the street formed on the wafer; and a dividing step for dividing the wafer which has been laser processed to form dividing start points along the dividing start points by exerting external force to the wafer, resulting in leaving the streets having the test metal patterns formed thereon behind.
Owner:DISCO CORP
Valve security device
InactiveUS6920894B1Preclude obtainingPrevent insertionBuilding locksAnti-theft devicesFree rotationValve actuator
A valve security device for releasably securing a fluid flow valve in an inoperable position including an inner body adapted to be disposed about the valve actuator such that rotation of the inner body effects corresponding rotation of the actuator to open and close the valve and an outer body rotatably mounted about the inner body. A valve cap defining a secondary actuator is mounted on the outer body. An operating pin assembly is carried by the outer body which, in an extended position, operatively couples the outer body to the inner body such that the valve can be controlled by the secondary actuator. In a retracted position, the pin assembly uncouples the outer and inner bodies such that the outer body is freely rotatable on the inner body. A lock secures the operating pin assembly in the retracted position thereby releasably securing the valve in an inoperable position.
Owner:FLOW SECURITY SYST
Display Device
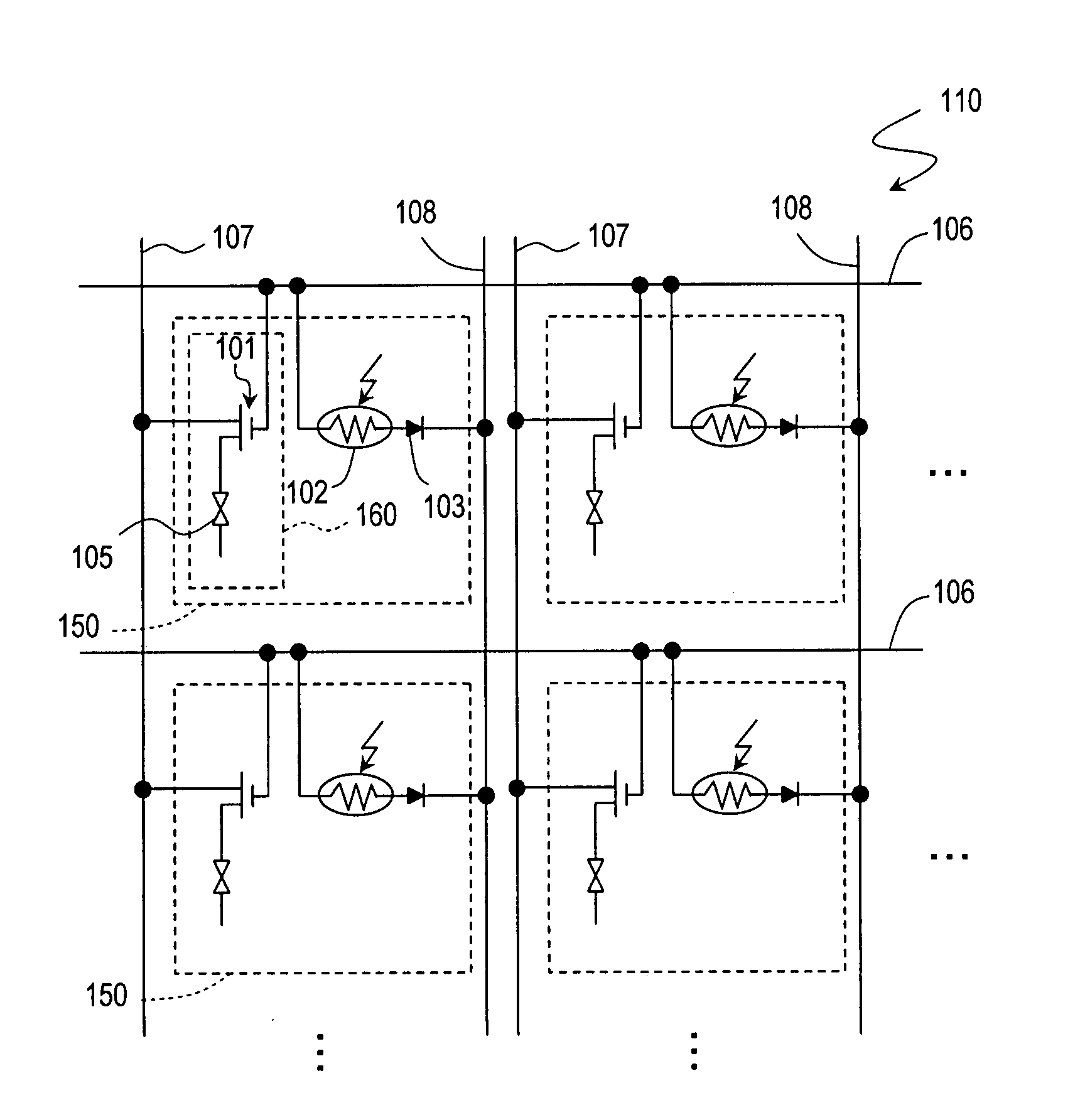
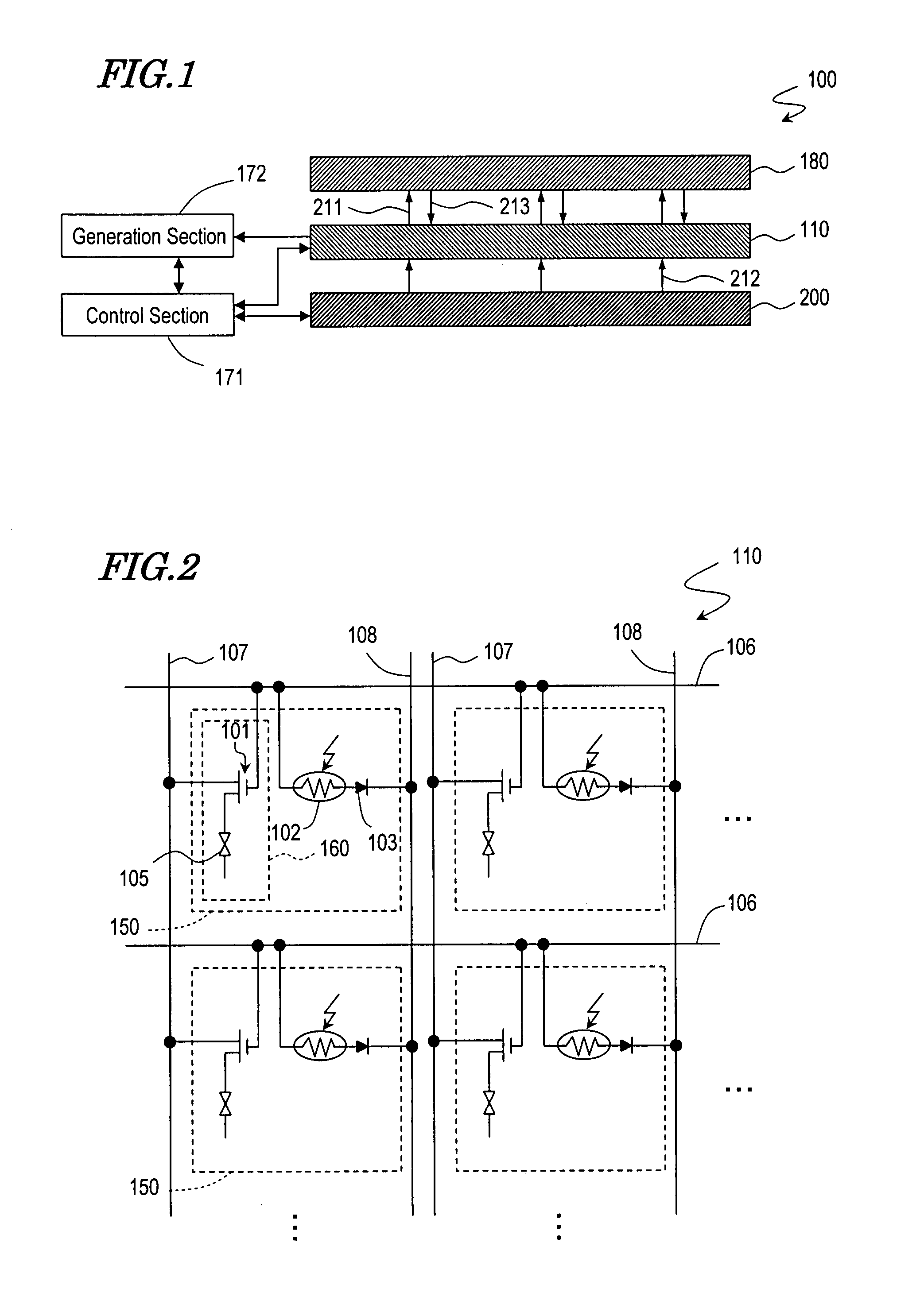
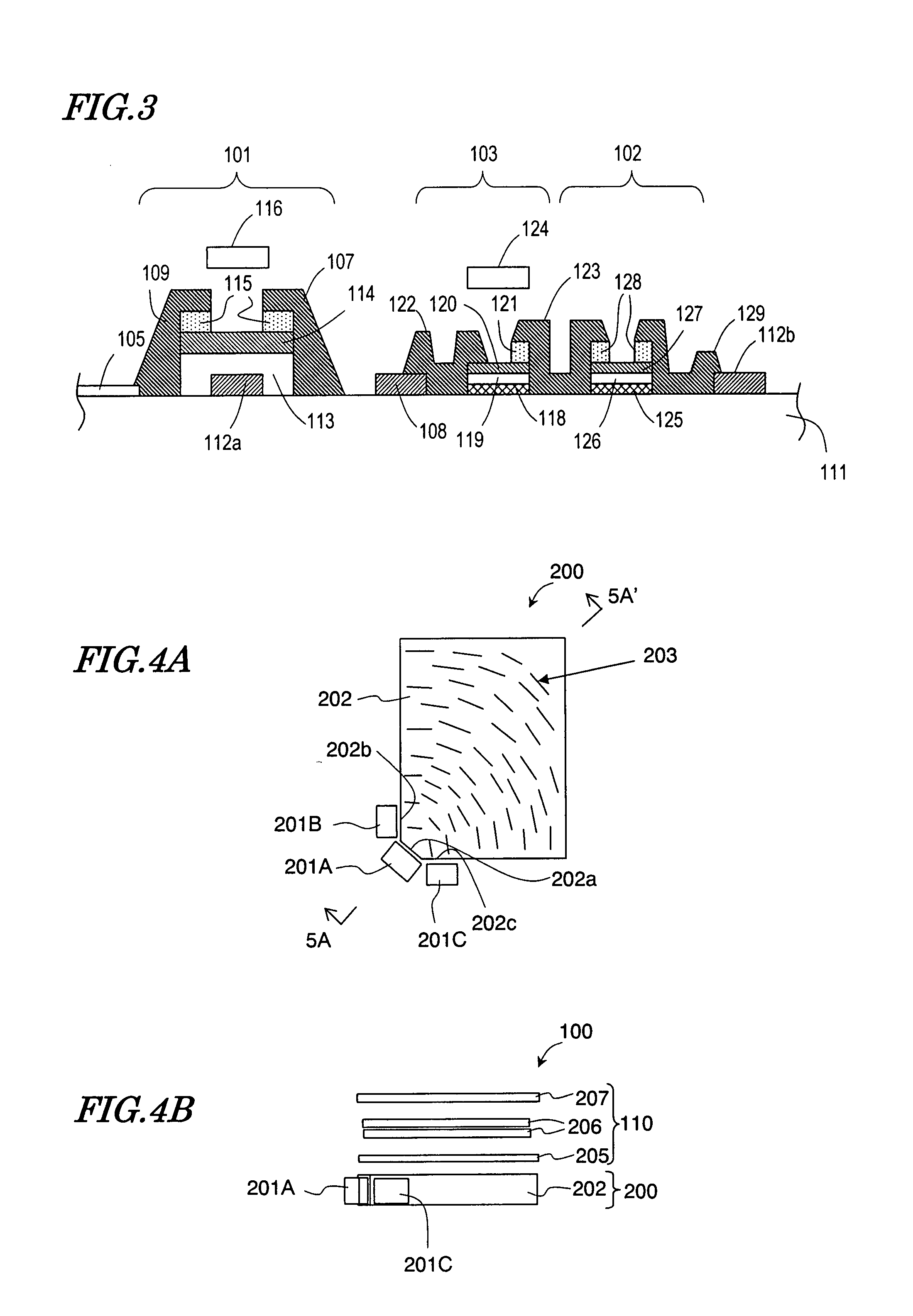
InactiveUS20080252939A1Improve directivityHigh operating requirementsStatic indicating devicesNon-linear opticsDisplay deviceComputer science
A display apparatus according to the present invention comprises a plurality of pixel sections 150 and performs an image display operation and an image reading operation. The plurality of pixel sections 150 each include a light output section 160 for outputting first light, and a light receiving section 102 for receiving reflected light obtained as a result of an imaging subject being irradiated with the first light. The apparatus further comprises a directivity adjusting section for adjusting a directivity of the first light. The plurality of pixel sections 150 are divided into a plurality of groups. The light output section 160 outputs the first light and the light receiving section 102 receives the reflected light on a group-by-group basis.
Owner:SHARP KK
Water base ink set for ink-jet recording
InactiveUS7159976B2Avoid color bleedStrong spreading forceMeasurement apparatus componentsDuplicating/marking methodsWater basedEngineering
An ink set for ink-jet recording of the present invention includes a black ink which has a surface tension of not less than 40 mN / m at 25° C., and a color ink which has a surface tension of not less than 40 mN / m at 25° C. The viscosity ratio of the color ink with respect to the black ink is not less than 1.3. The feathering of the ink is avoided, and the bleeding, which would otherwise appear at the boundary between the black ink and the color ink, is avoided.
Owner:BROTHER KOGYO KK
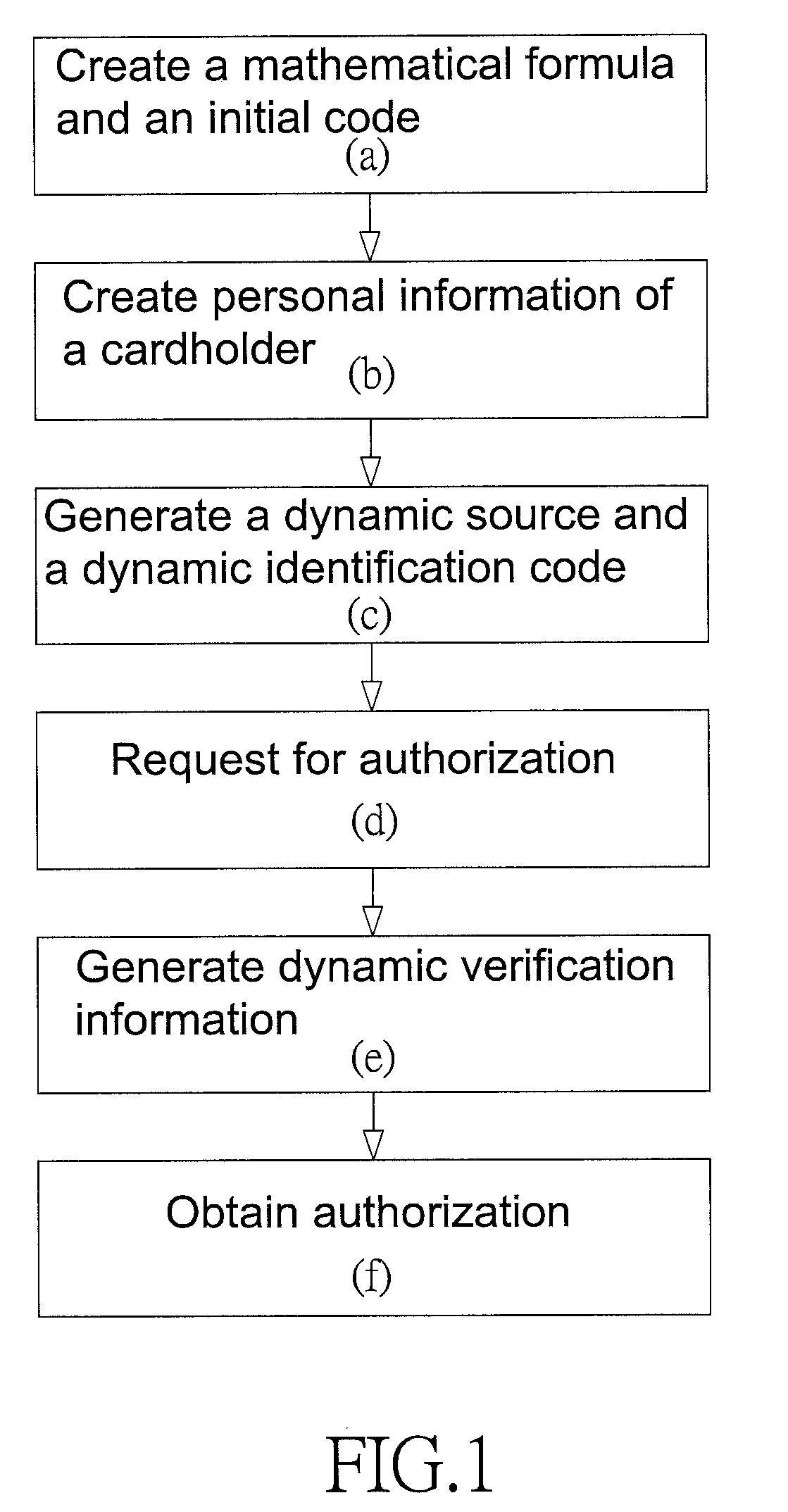
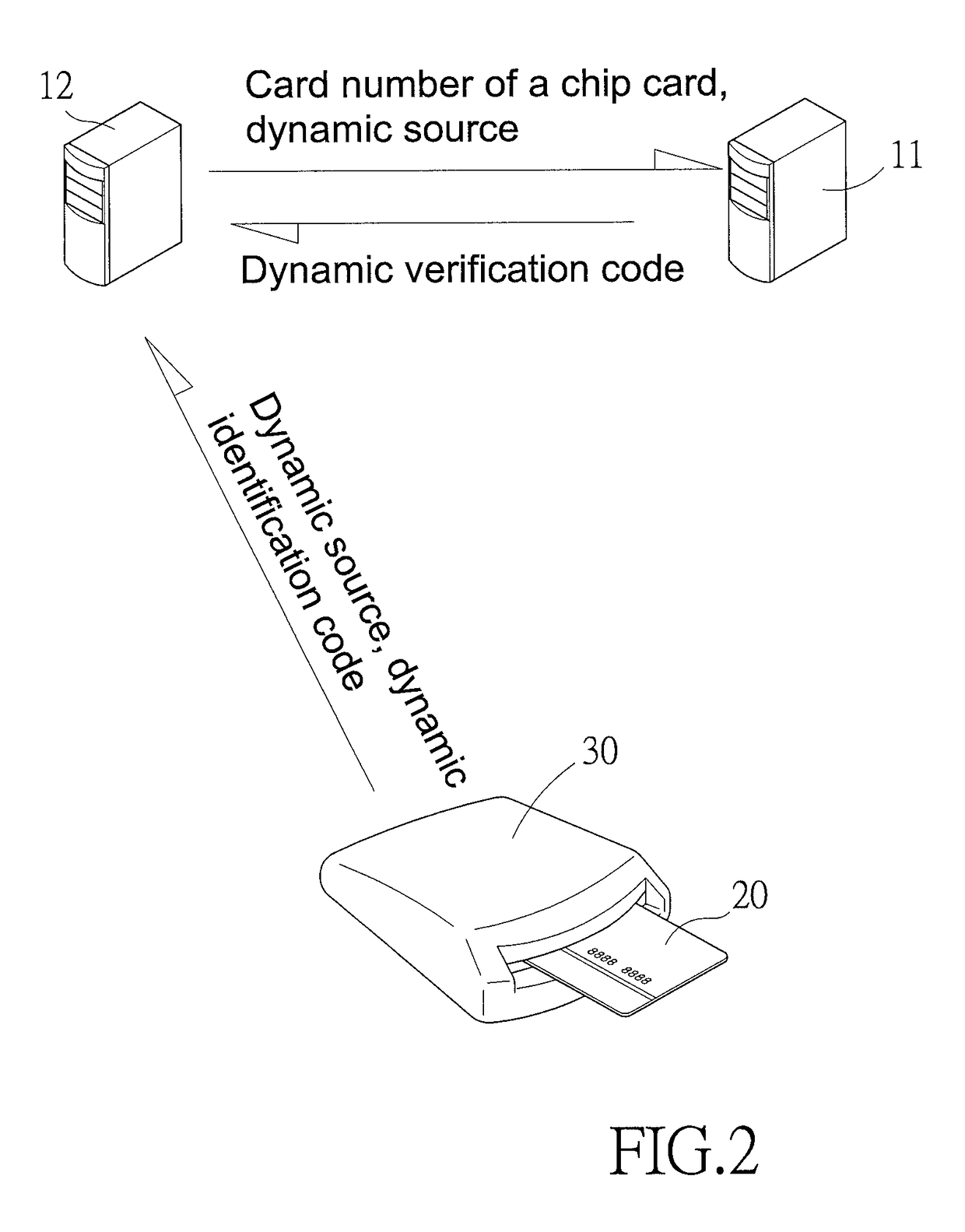
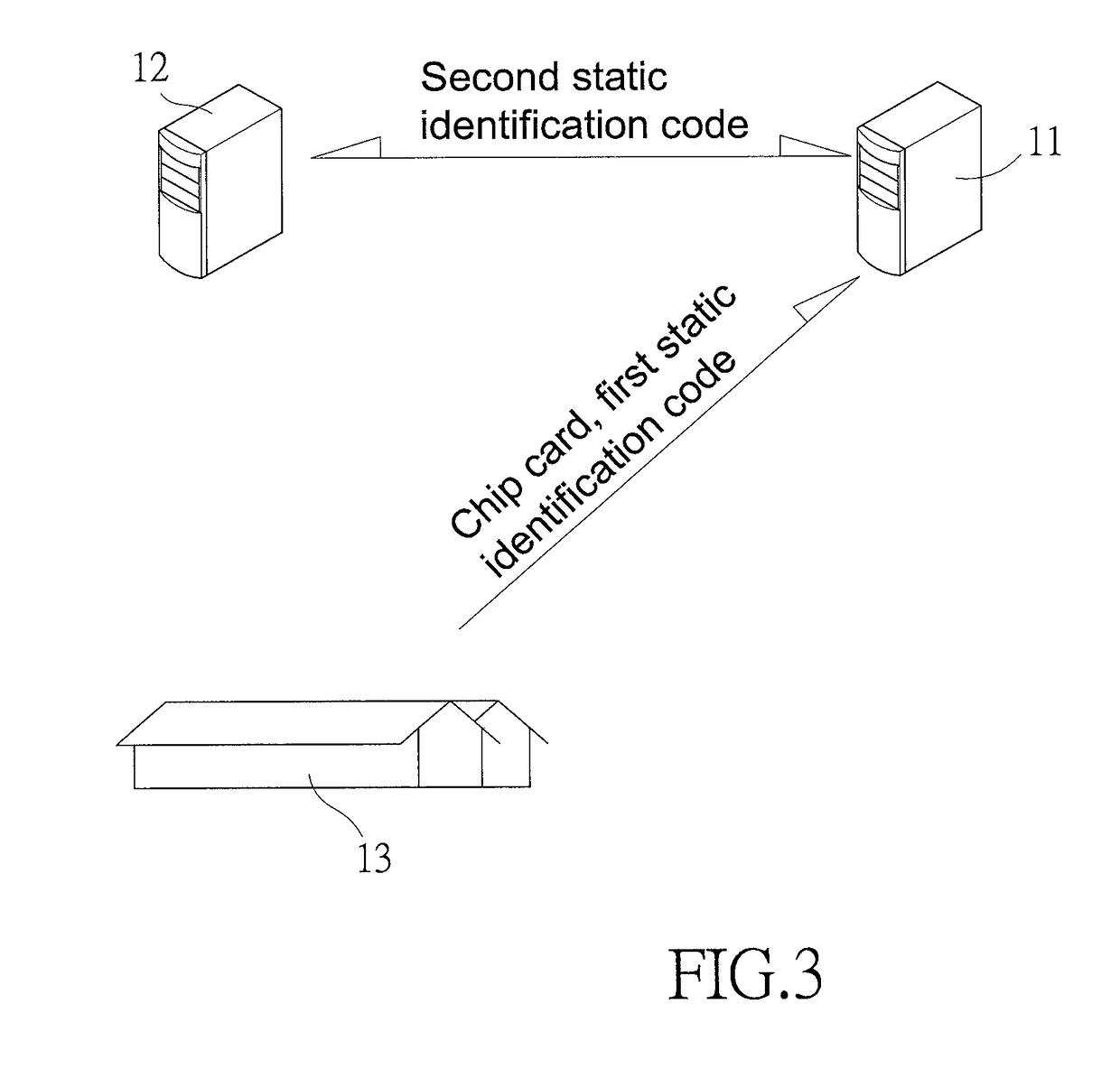
Method for verifying transactions in chip cards
InactiveUS20190005495A1Facilitate transmissionPromote disseminationAcutation objectsProtocol authorisationMinutiaeData storing
The present invention provides a method for verifying transactions in chip cards which effectively protects a chip card from being copied and facilitates transmission of transactional messages or transactional information over open networks. Consequently, personal information of a particular account and data stored in a chip card thereof cannot be obtained by intercepting the transmitted transactional details, effectively protecting the chip card from being copied, and facilitating the transmission of transactional messages or transactional information over open networks.
Owner:CHEN JOE CHI +2
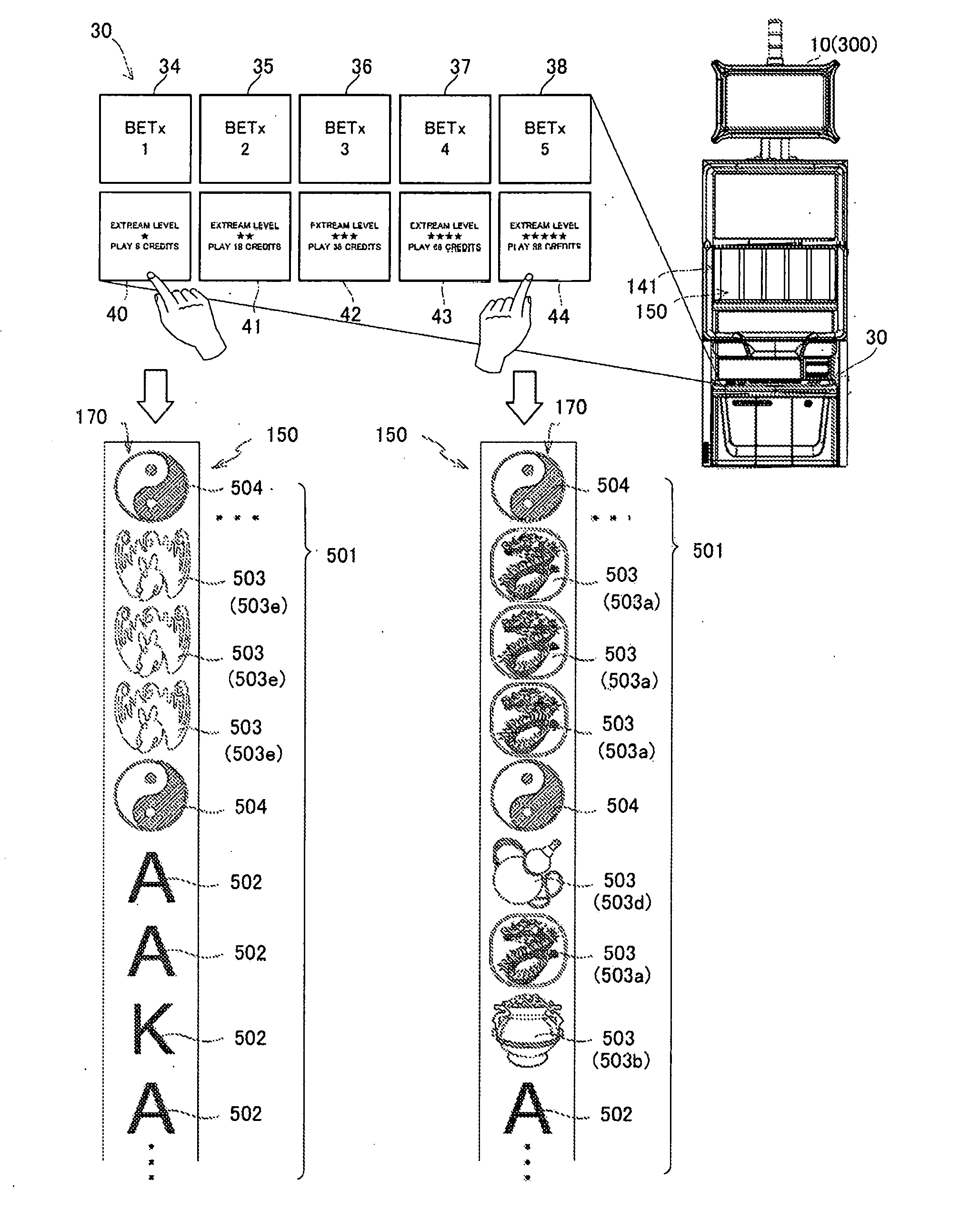
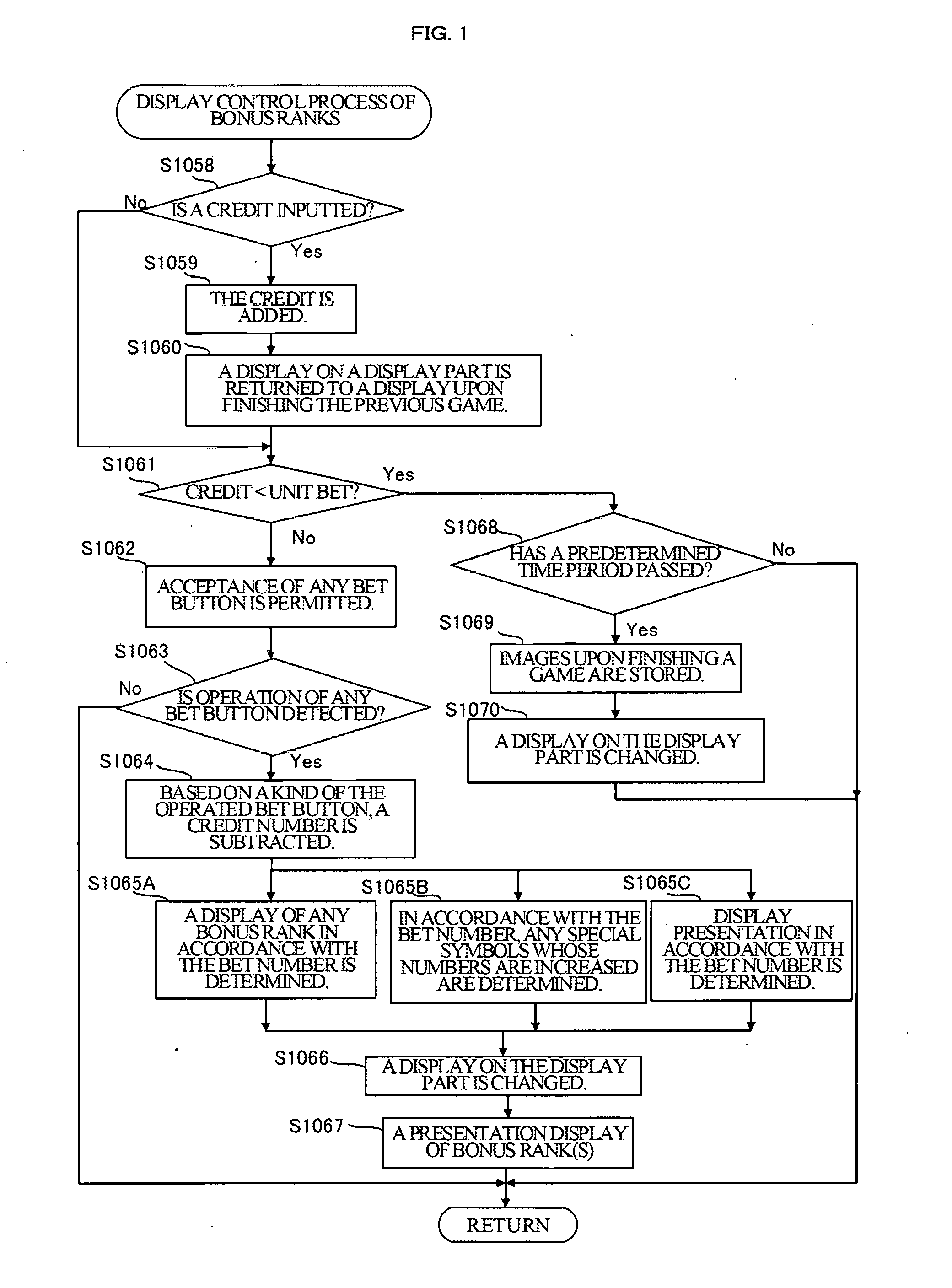
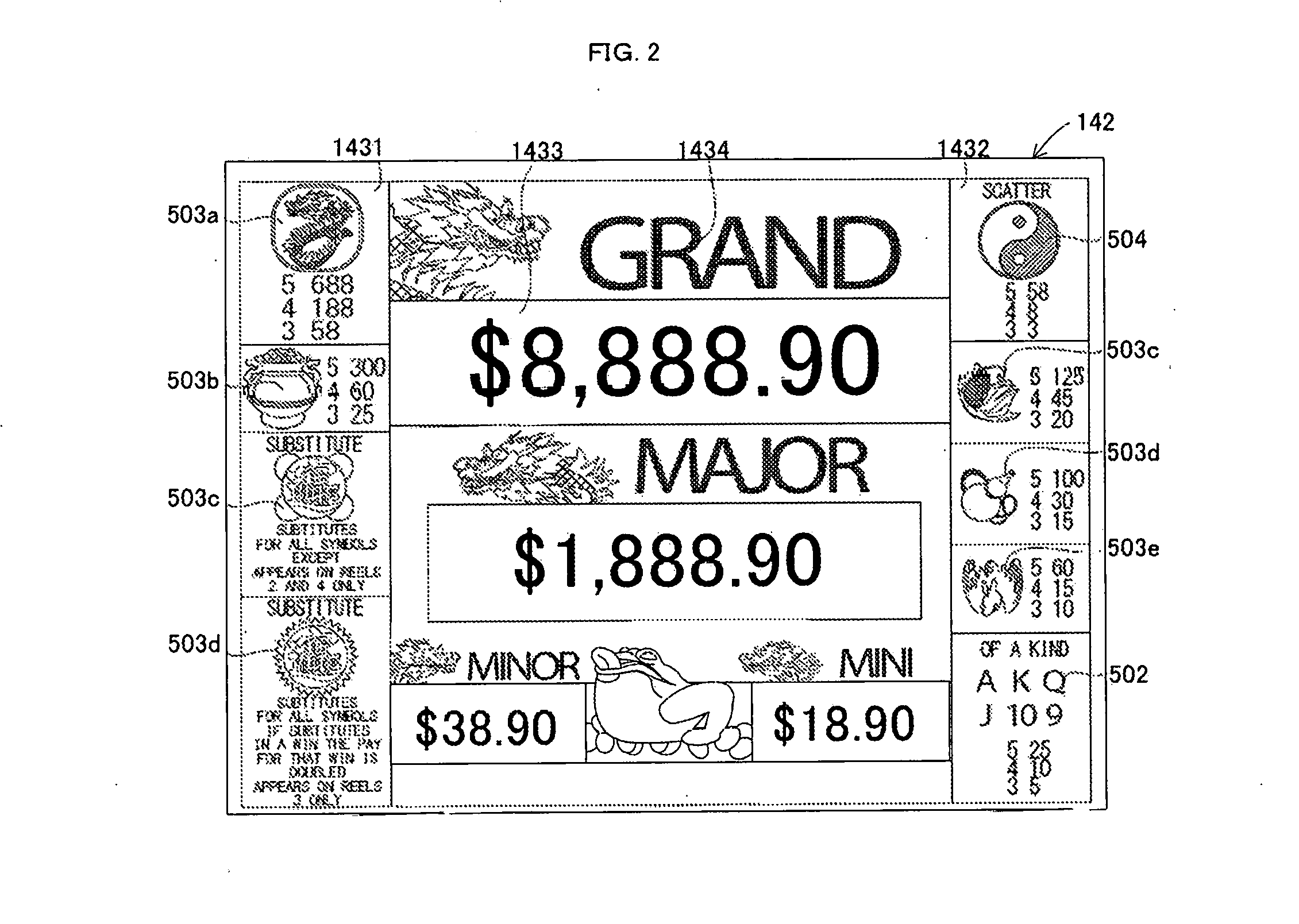
Gaming machine
ActiveUS20160343202A1Preclude obtainingImprove operating rateApparatus for meter-controlled dispensingIntermediate imageComputer graphics (images)
After determining that a game state is a non-play state, it is determined whether or not a credit required for a play has been inputted within a predetermined time period. When the credit has not been inputted within the predetermined time period, a display mode in which a plurality of different bonus ranks are displayed on a middle image display panel in a first state in which a bonus or bonuses are likely to be obtained by a drawing and in a second state in which the bonus or bonuses are not obtained thereby is switched to a display mode in which all of the plurality of bonus ranks displayed in display areas are displayed in either of the first state or the second state.
Owner:INTERBLOCK DOO +1
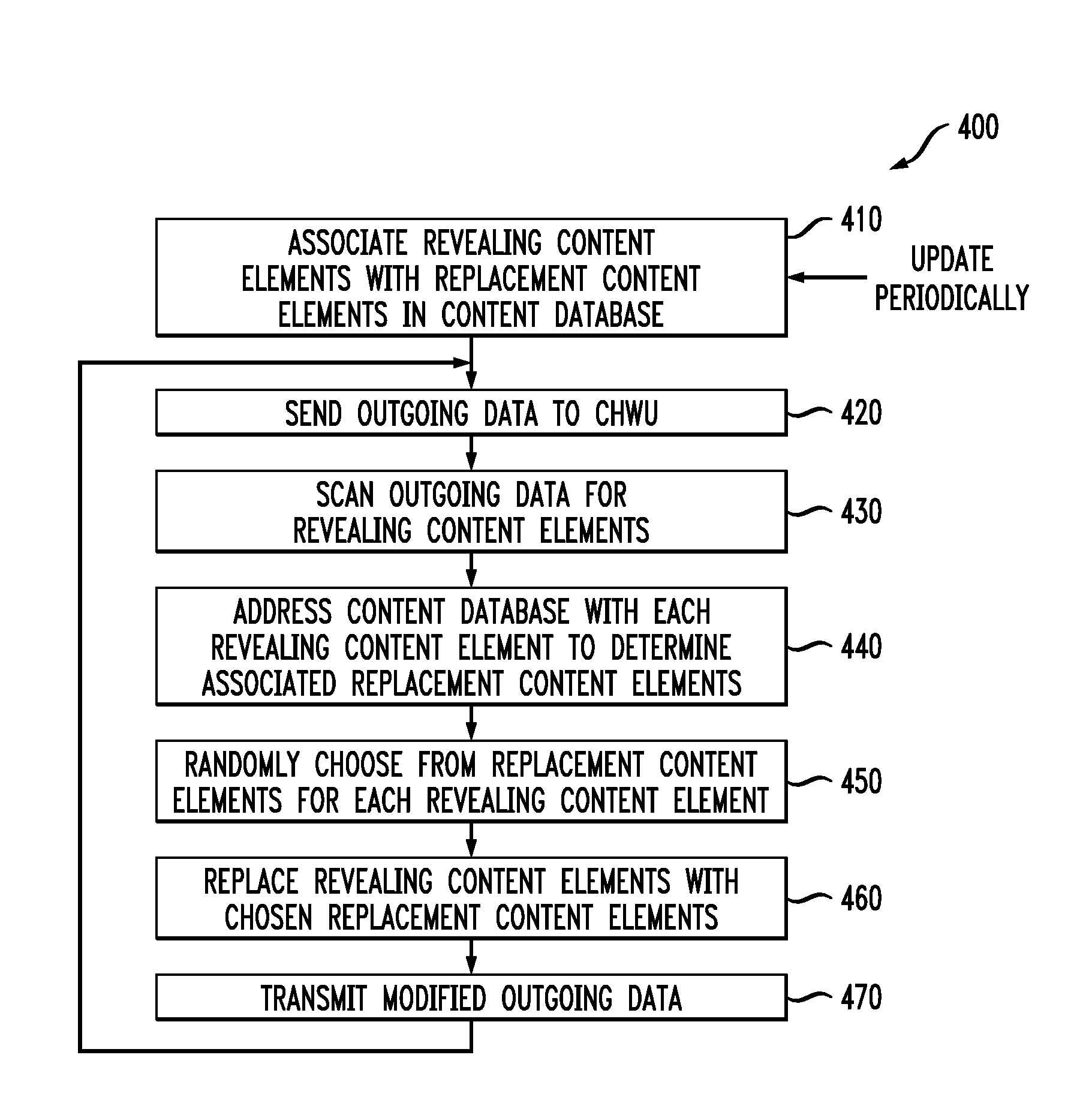
Networked Computer System with Reduced Vulnerability to Directed Attacks
ActiveUS20090055927A1Reduce vulnerabilityPreclude obtainingMemory loss protectionError detection/correctionComputerized systemComputer science
An attacker is prevented from obtaining information about the configuration of a computer system. Each of one or more revealing content elements that may be found in outgoing data transmitted by the computer system and that are capable of being used by the attacker to obtain the information about the configuration of the computer system is associated with one or more respective replacement content elements. Outgoing data to be transmitted by the computer system are then scanned for these one or more revealing content elements. A revealing content element found in the outgoing data is replaced by a replacement content element from the one or more replacement content elements associated with that revealing content element. This is done before the outgoing data is transmitted.
Owner:AVAGO TECH INT SALES PTE LTD
Foil shaped electro-optical product, semi-finished product and method and apparatus for manufacturing the same
InactiveUS9076970B2Preclude obtainingFinal product manufactureSolid-state devicesConvex sideEngineering
Owner:NEDERLANDSE ORG VOOR TOEGEPAST NATUURWETENSCHAPPELIJK ONDERZOEK TNO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com