Software protection method based on virtual machine
A technology of software protection and virtual machine, applied in the direction of platform integrity maintenance, computer security devices, program control design, etc., can solve the problems of weak storage and computing capabilities of secure smart card chips, running complex algorithms, poor user experience, etc., to achieve strong Anti-illegal tampering function, anti-use, anti-piracy effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings.
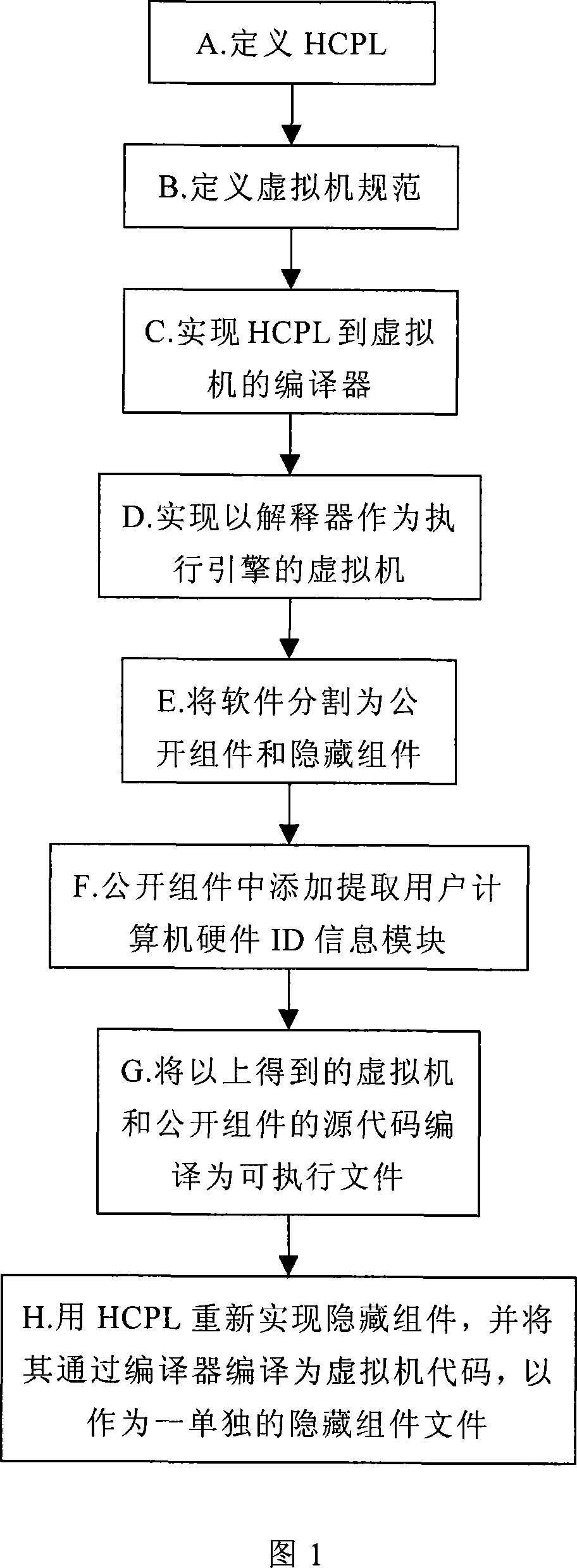
[0040] As shown in FIG. 1 , the software developer can divide the software through the following steps A to H, so that the software can be effectively protected.
[0041] A. Define a high-level programming language HCPL for writing hidden components. High-level programming language HCPL is a writing language defined by software developers themselves. This HCPL can adopt the grammatical rules in existing programming languages, such as the grammatical rules similar to JAVA language. Of course, HCPL can also be completely composed of Software developers specify a new set of grammatical rules different from existing programming languages.
[0042] B. Define a virtual machine specification, which includes a non-public virtual machine-specific instruction set and a virtual machine file format.
[0043] C. A compiler that implements high-level programming language HCPL to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com