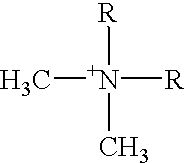Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1923results about How to "Maintain quality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
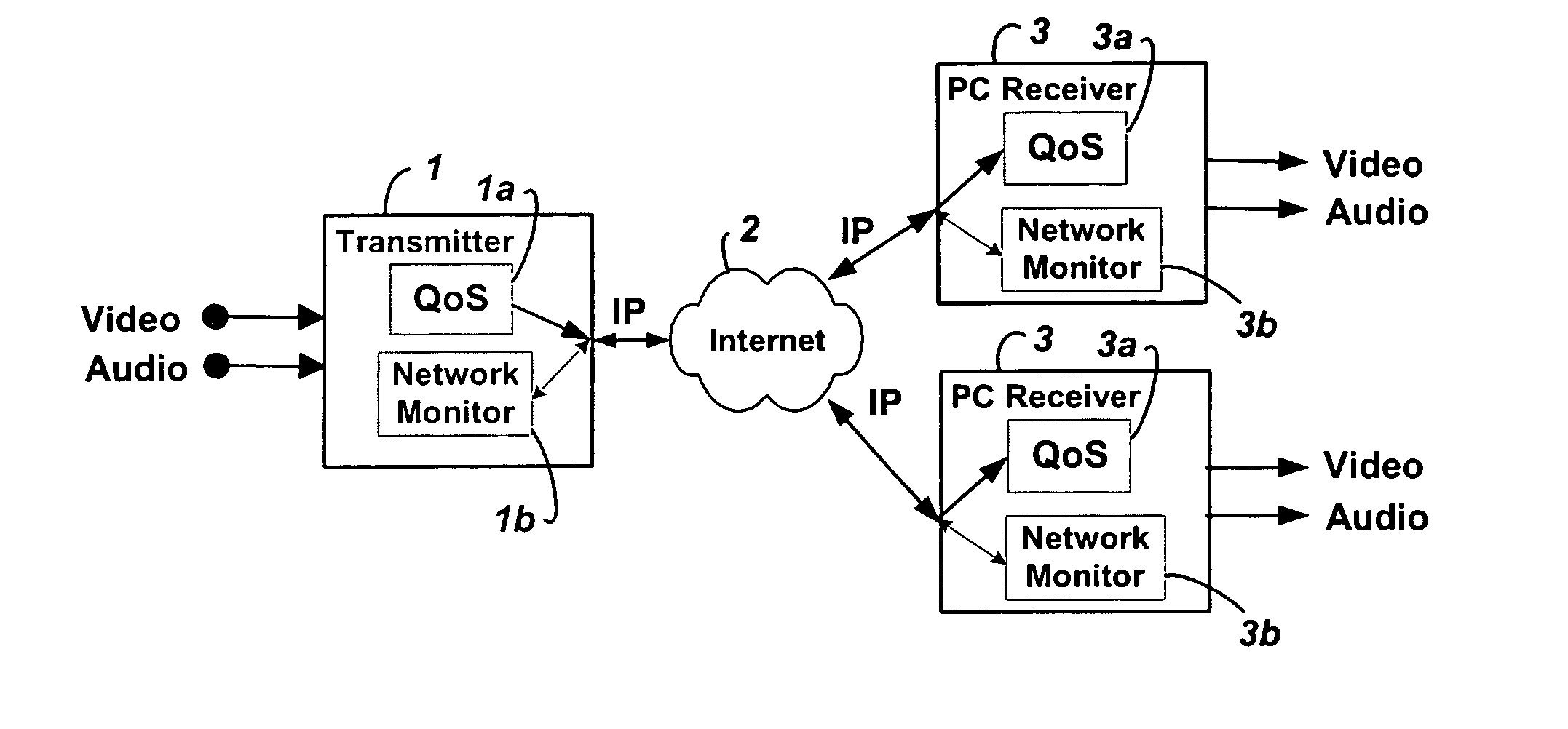
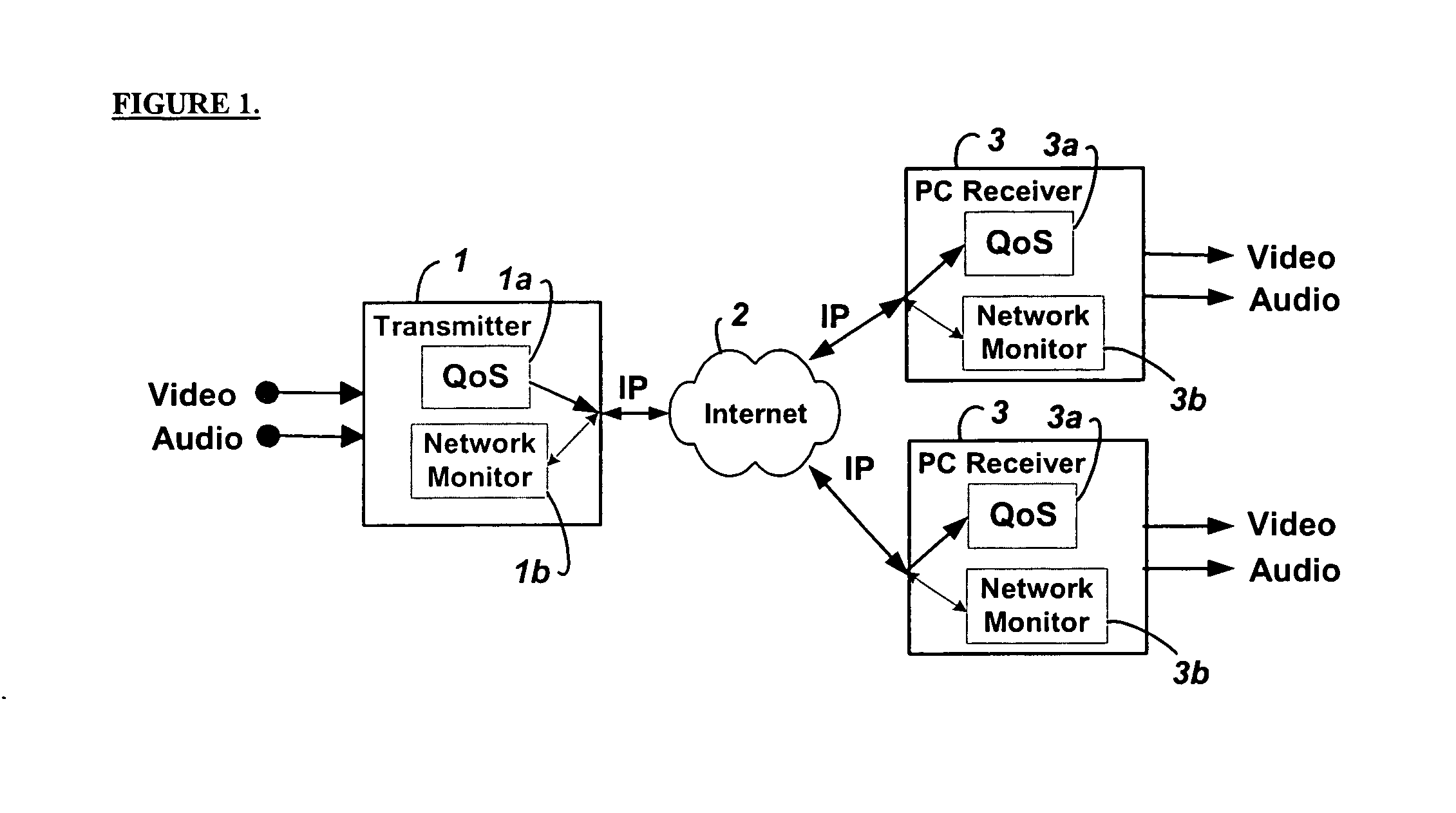
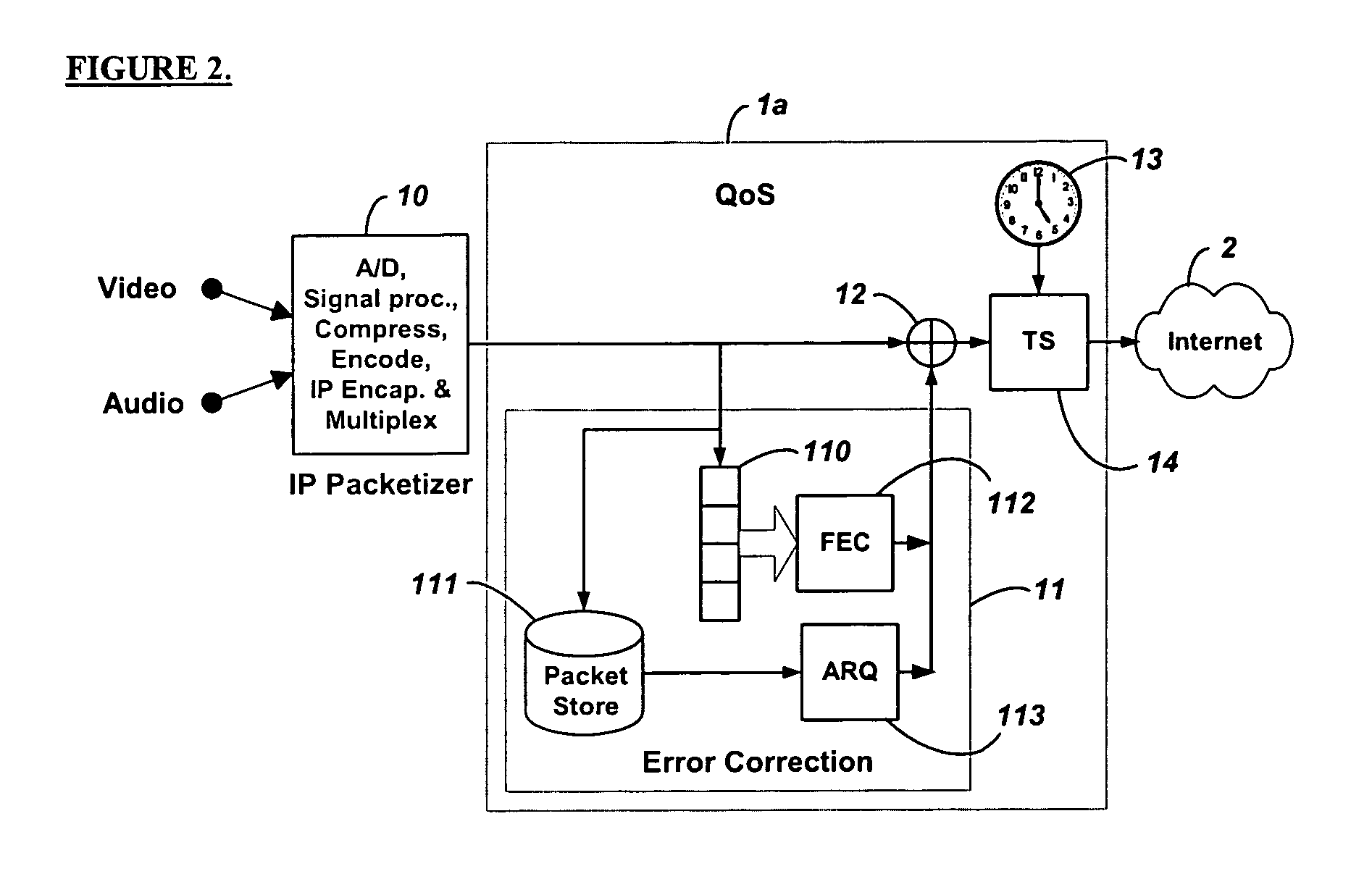
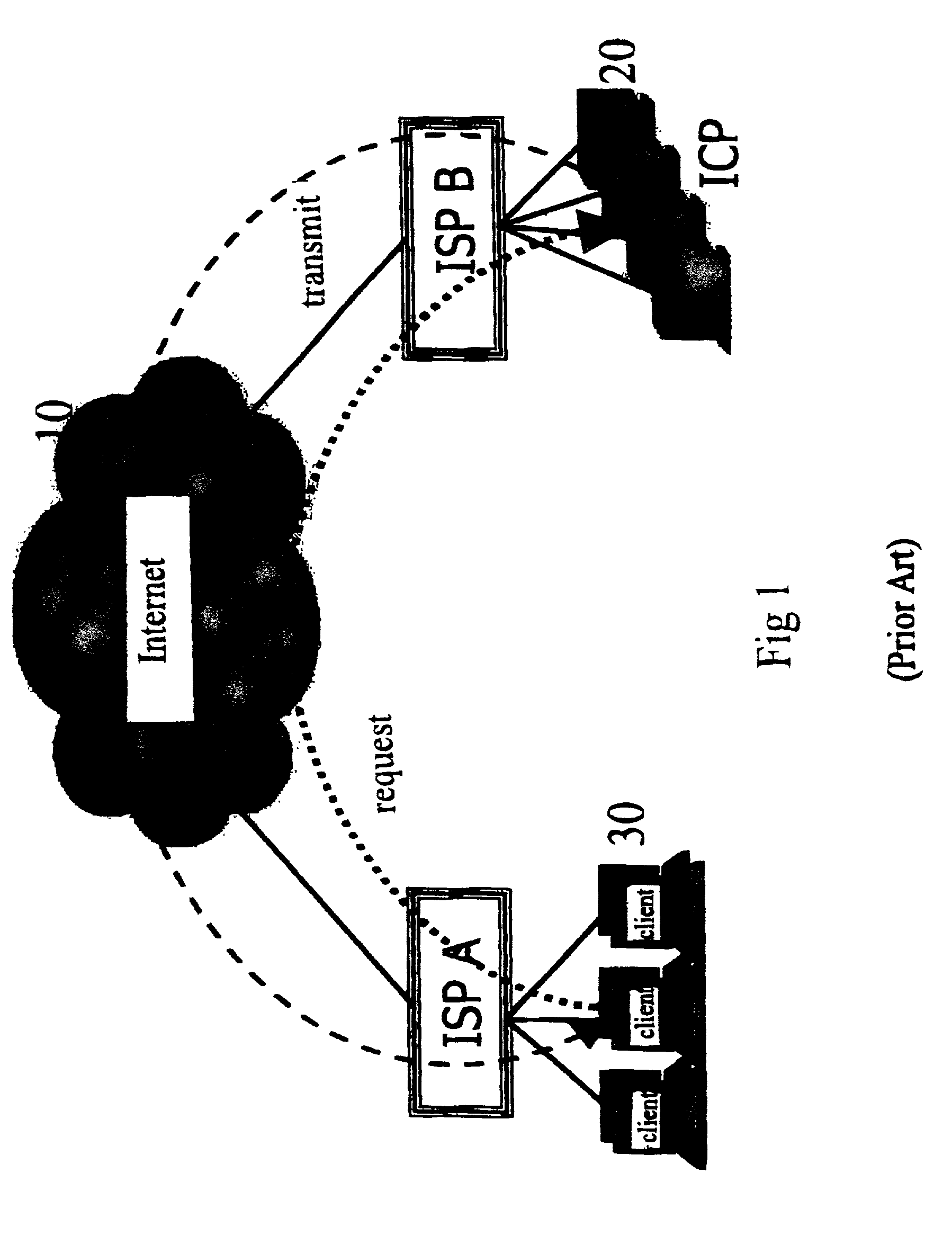
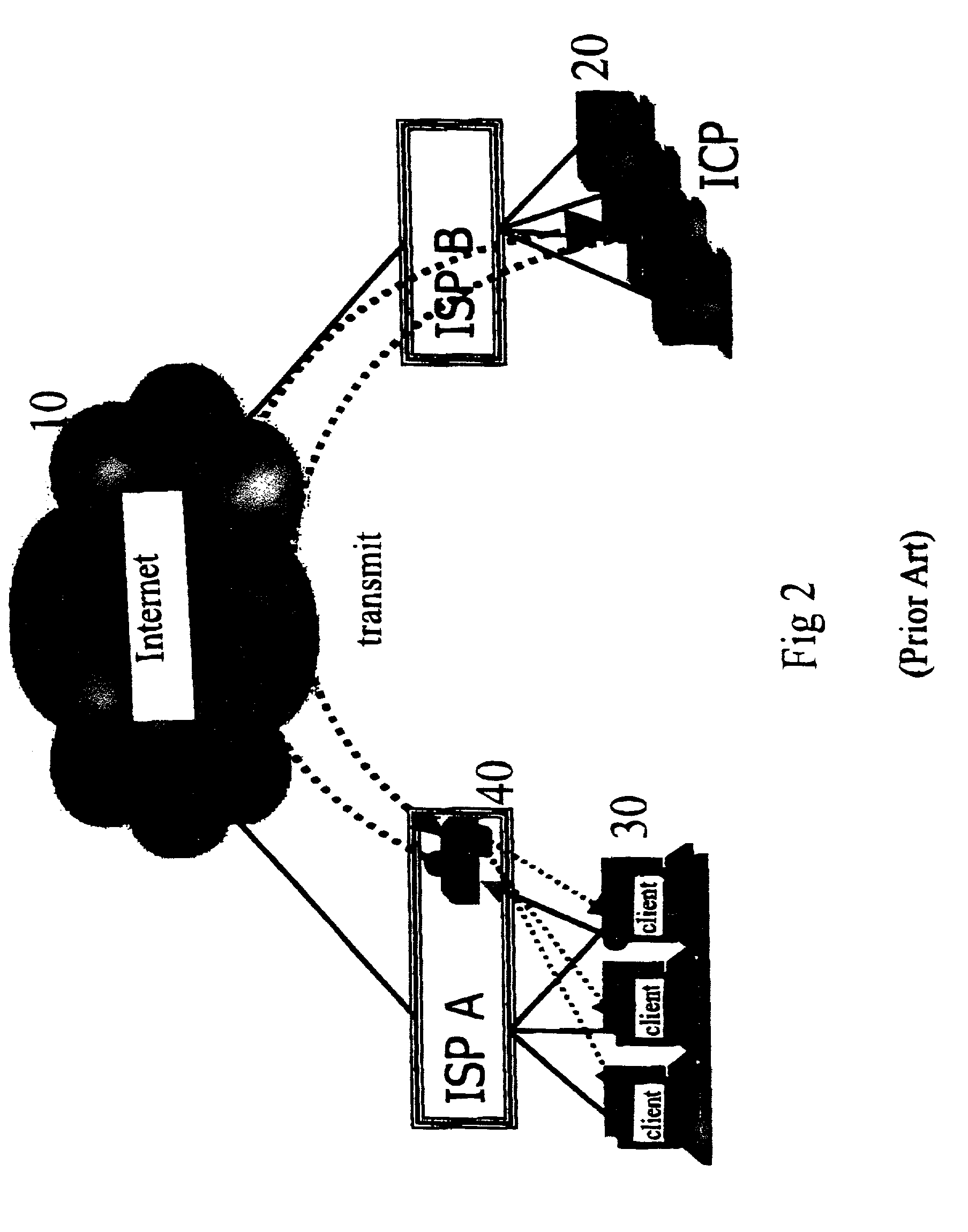
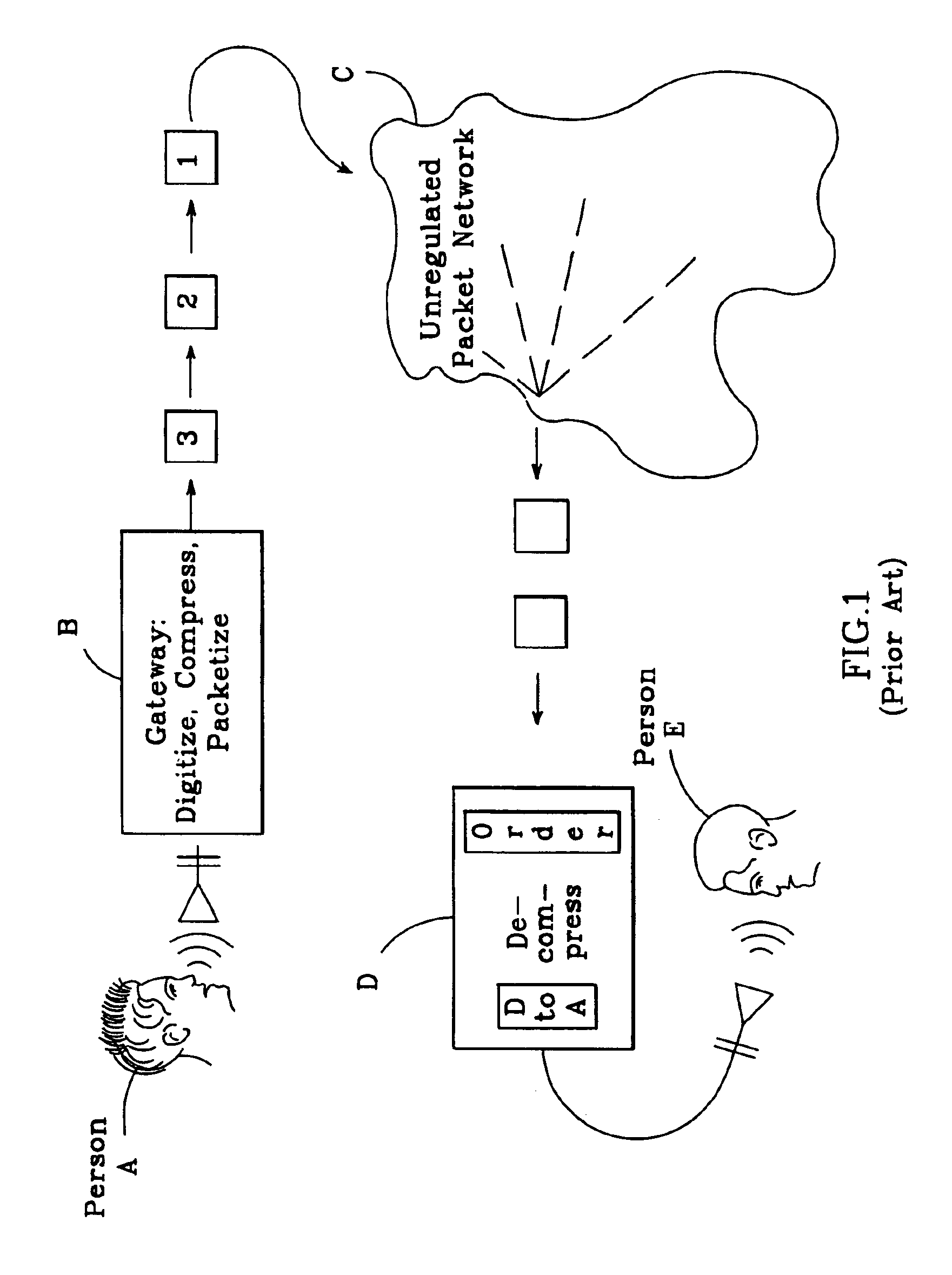
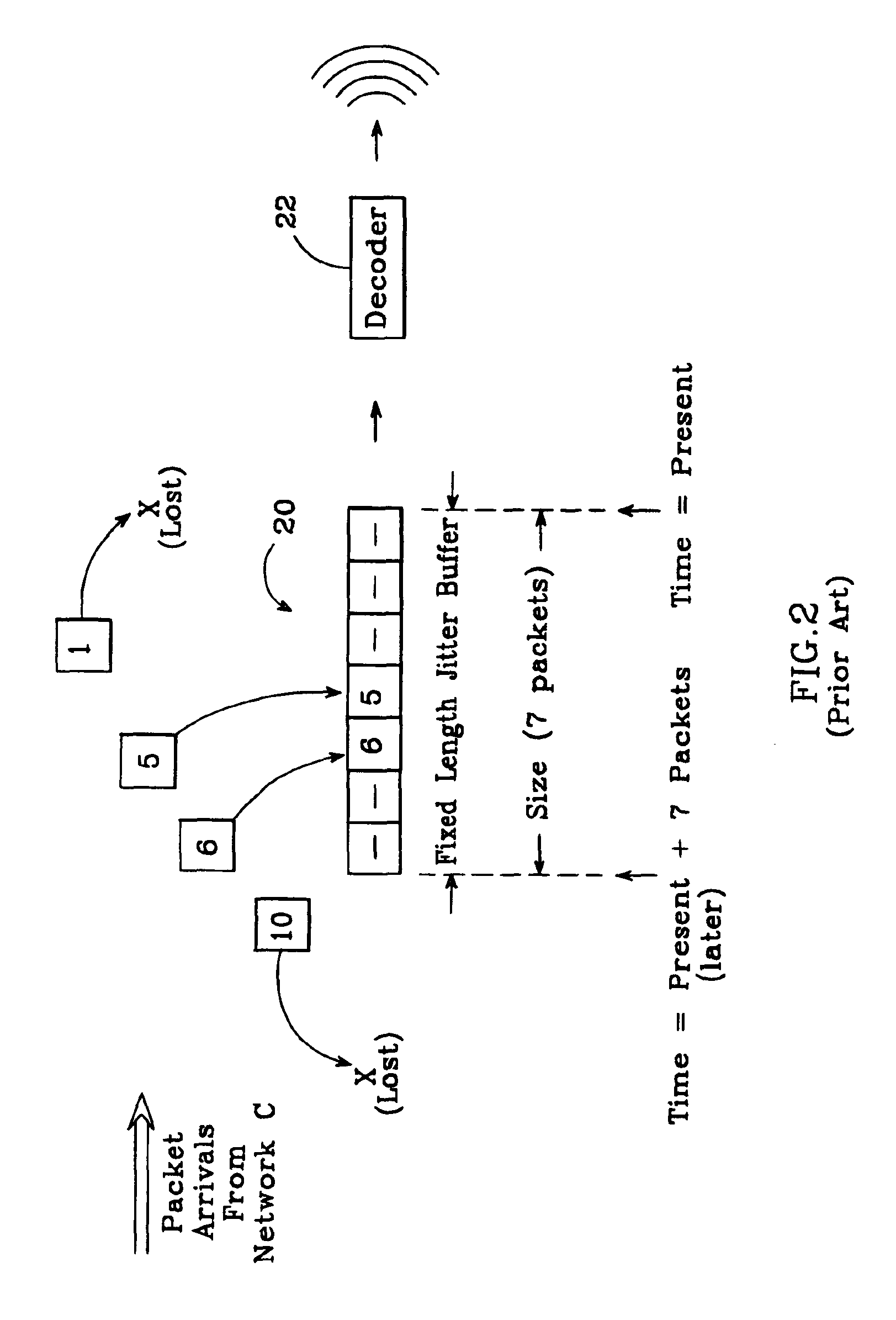
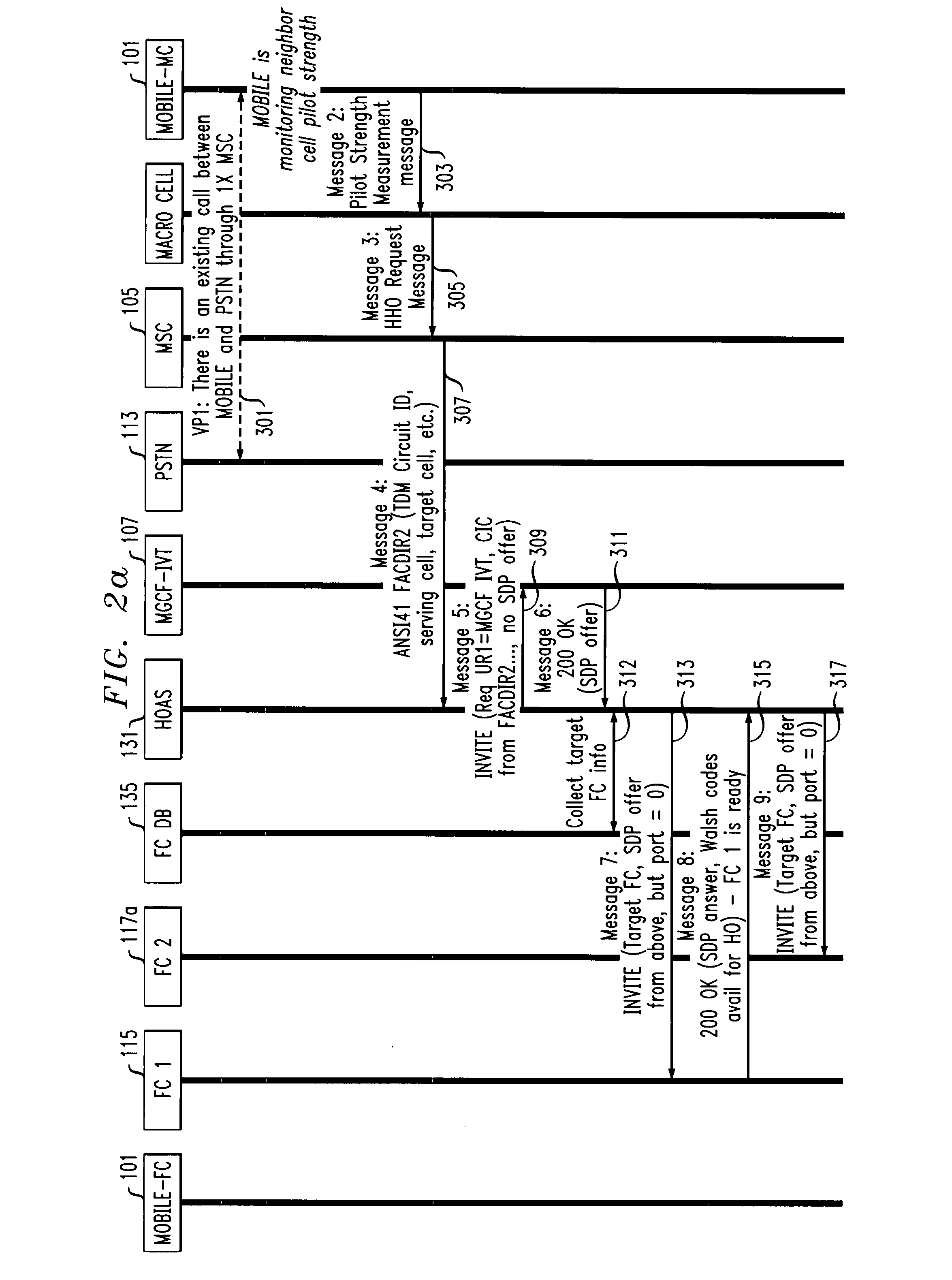
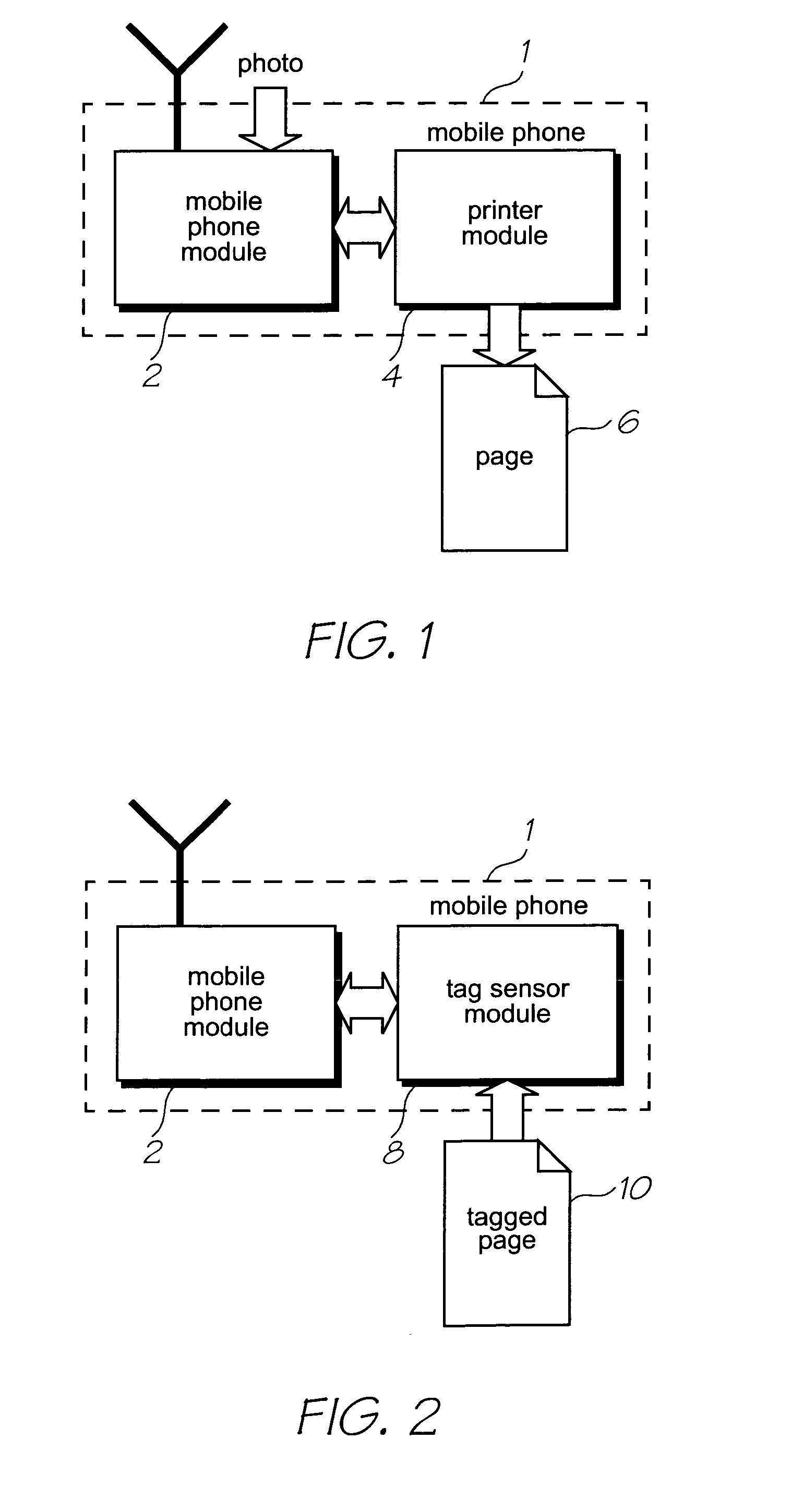
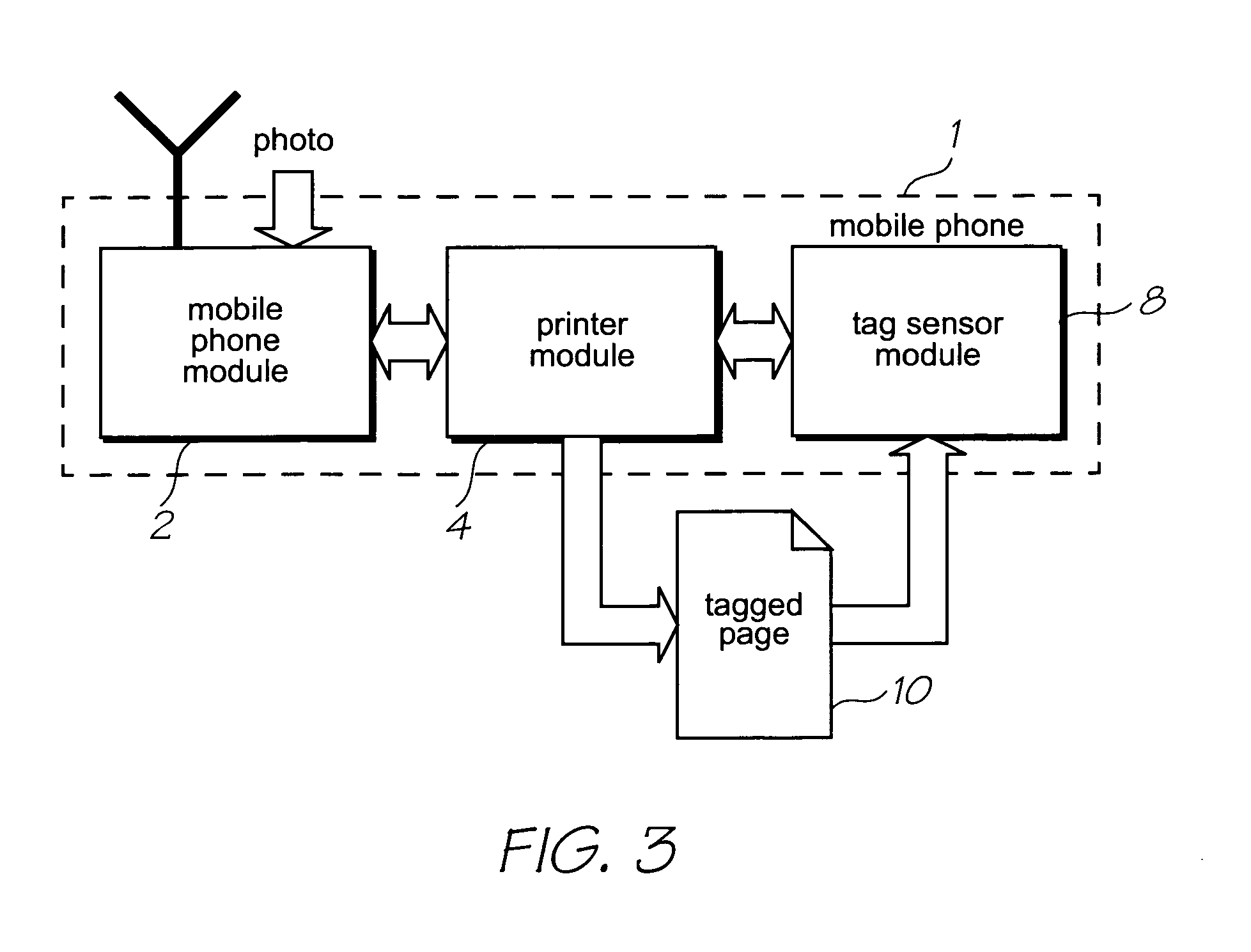
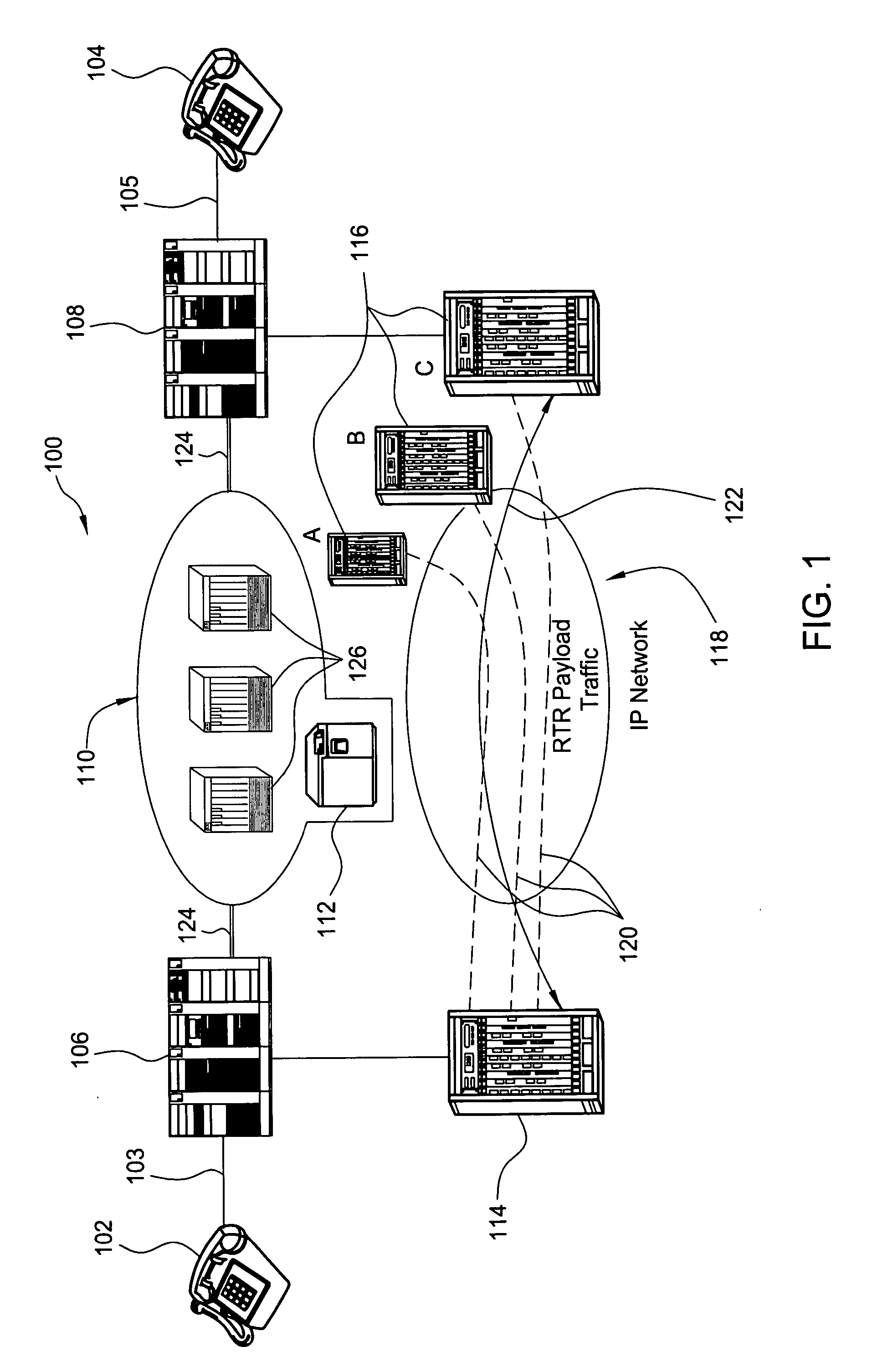
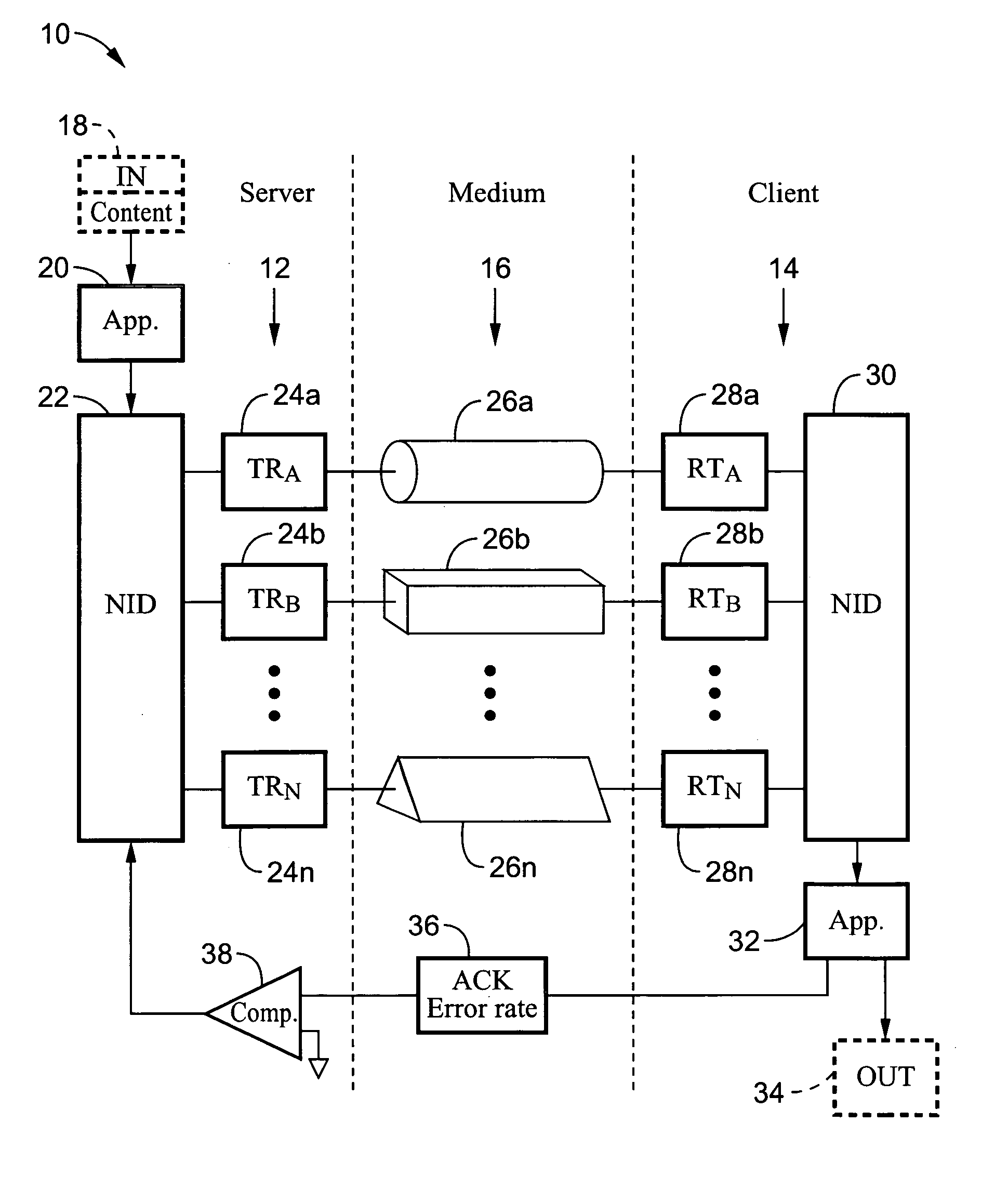
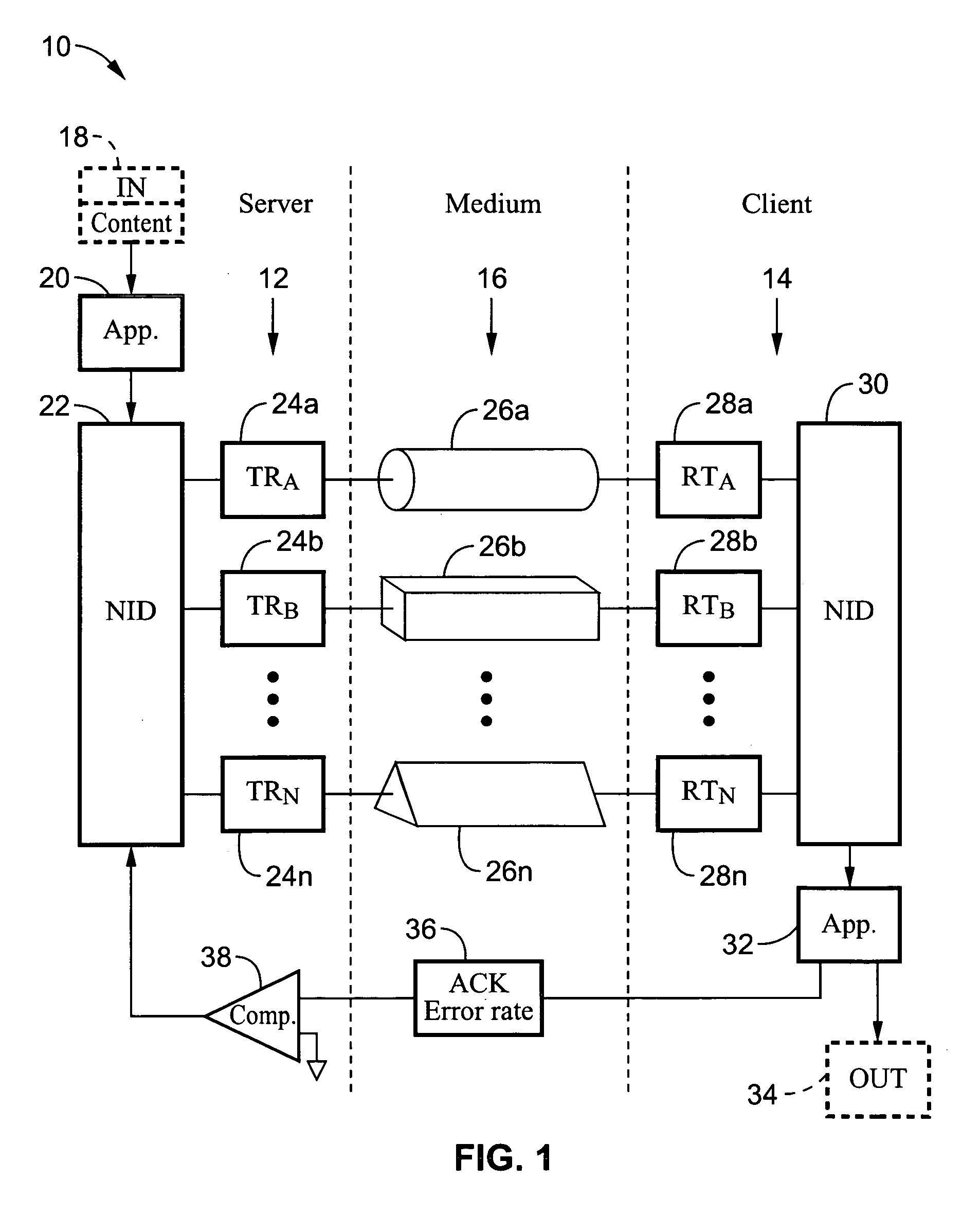
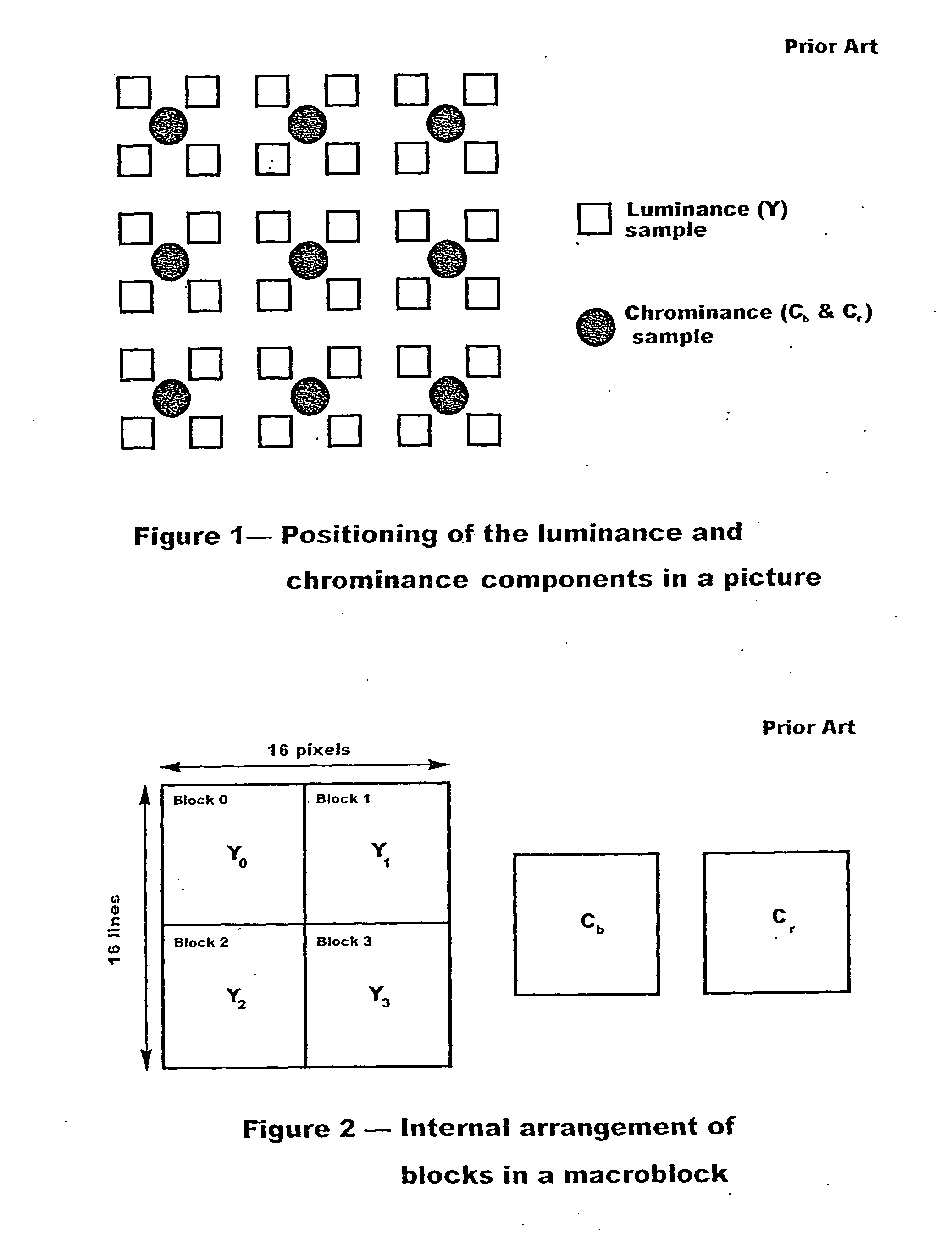
Method and system for providing site independent real-time multimedia transport over packet-switched networks
InactiveUS20060007943A1Minimal latency site-independenceAchieve independenceTime-division multiplexData switching by path configurationData packTimestamp
Embodiments of the invention enable minimum latency site independent real-time video transport over packet switched networks. Some examples of real-time video transport are video conferencing and real-time or live video streaming. In one embodiment of the invention, a network node transmits live or real-tine audio and video signals, encapsulated as Internet Protocol (IP) data packets, to one or more nodes on the Internet or other IP network. One embodiment of the invention enables a user to move to different nodes or move nodes to different locations thereby providing site independence. Site independence is achieved by measuring and accounting for the jitter and delay between a transmitter and receiver based on the particular path between the transmitter and receiver independent of site location. The transmitter inserts timestamps and sequence numbers into packets and then transmits them. A receiver uses these timestamps to recover the transmitter's clock. The receiver stores the packets in a buffer that orders them by sequence number. The packets stay in the buffer for a fixed latency to compensate for possible network jitter and / or packet reordering. The combination of timestamp packet-processing, remote clock recovery and synchronization, fixed-latency receiver buffering, and error correction mechanisms help to preserve the quality of the received video, despite the significant network impairments generally encountered throughout the Internet and wireless networks.
Owner:QVIDIUM TECH
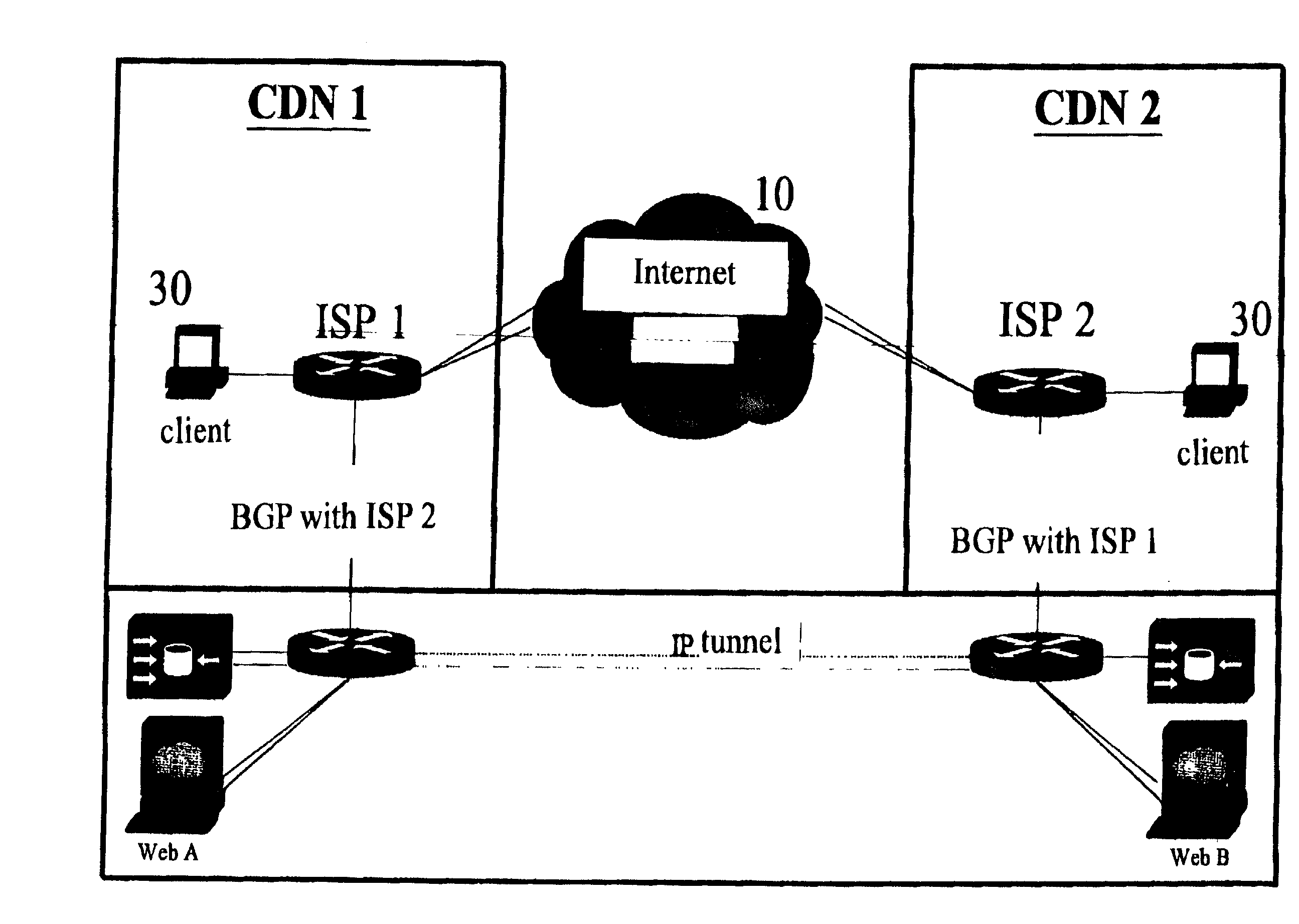
Content delivery network system and method for building the same
InactiveUS20020116481A1Optimize networkSolve the real problemData switching by path configurationMultiple digital computer combinationsClient-sideContent delivery network
A content delivery network system is disclosed. The system comprises a communication network, a first network node for providing services for clients to access network, a second network node for managing hosts for network content providers and a third network node, wherein said third network node sets a default route and a VPN tunnel between the first and second network nodes, and provides a cache server at the bandwidth outlet of the first network node, said cache server stores a information content which has been requested and transmitted. When the client request an information content, the third network node searches the cache server. If the information content is found, the cache server provides said information content to the client directly. If the information content is not found, the cache server sends a request for catching the information content to the second network via the VPN tunnel, and transmits the information content to the client via the default route. The cache server records the data of the transmitted information content. The recorded data is provided to the second network node, so that the second network node can bill the network content provider accordingly.
Owner:LEE KIM MAN
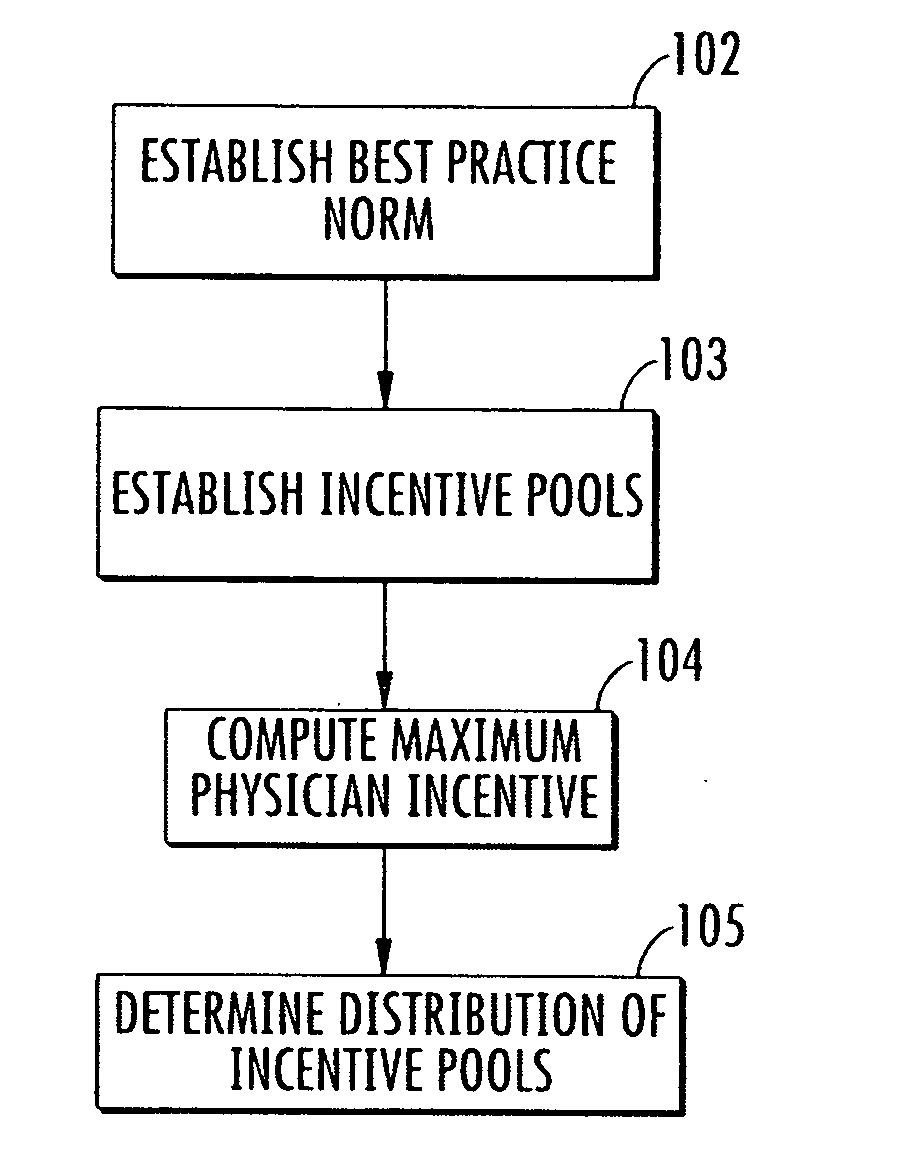
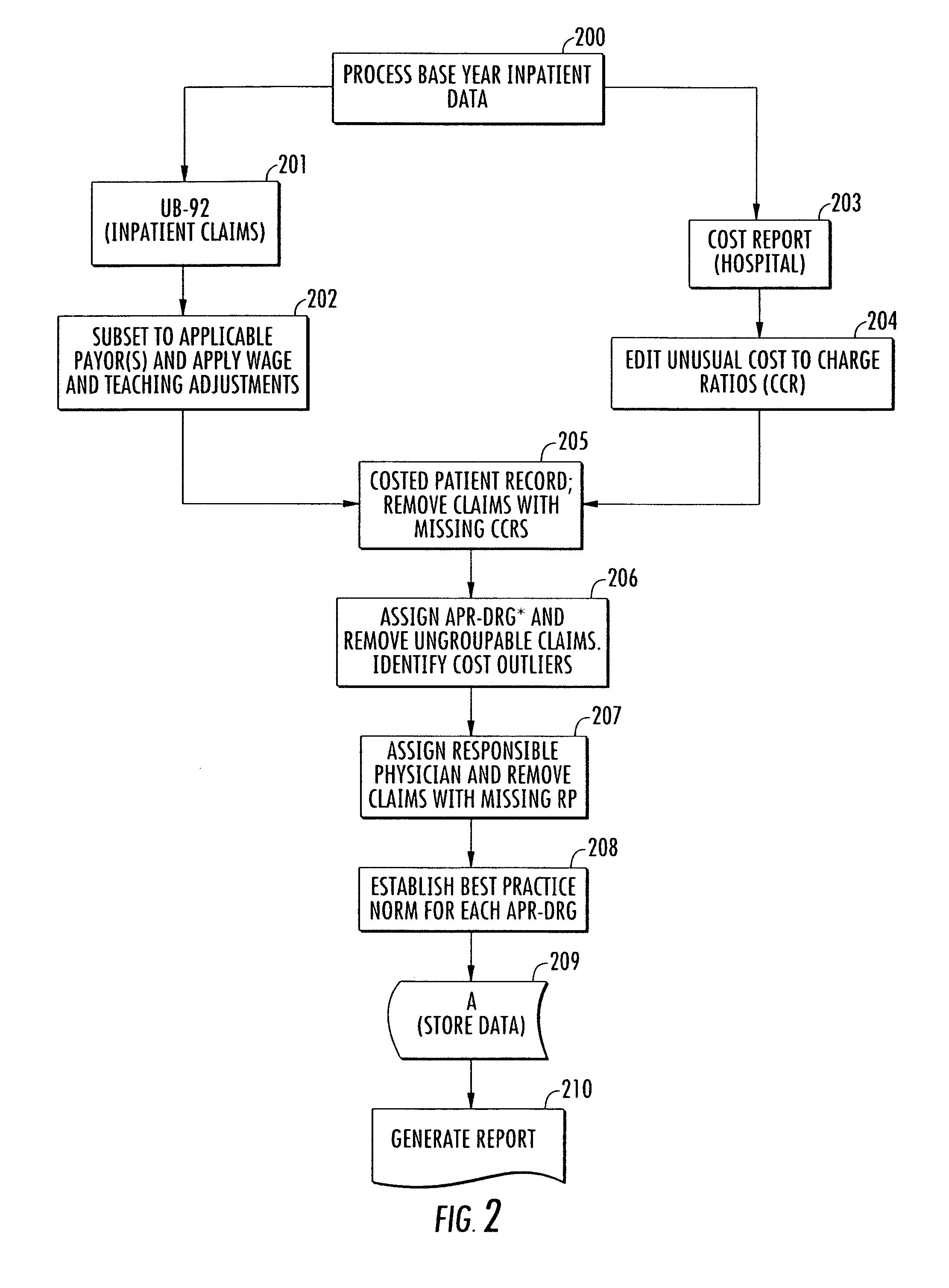
Method and system for evaluating a physician's economic performance and gainsharing of physician services
InactiveUS20080195417A1Impose significant, additional data collection burdens on providersEfficient and inexpensiveFinanceOffice automationPaymentDisease
The invention relates to a method and system of physician economic performance evaluation in which the relative medical difficulty associated with patients admitted by a particular physician is determined and, given that measurement, judgments made concerning the relative amount of inpatient resources that the physician required. Also, one application of the present invention relates to a method for gainsharing of physician services using a surplus allocation methodology for rewarding physicians in relation to their performance. An incentive pool is determined from previous patient claims and payments made to physicians in advance, such as in a base year. Best practice norms are established for a plurality of classified diagnosis groups. In one embodiment of the present invention, the classified diagnosis related groups are adjusted for severity of illness to compensate for actual clinical challenges faced by individual physicians. The best practice norms can be used in the surplus allocation method for determining physician performance. The incentive is established proportional to the relationship between a physician's individual performance and the best practice norm.
Owner:AMS APPLIED MEDICAL SOFTWARE
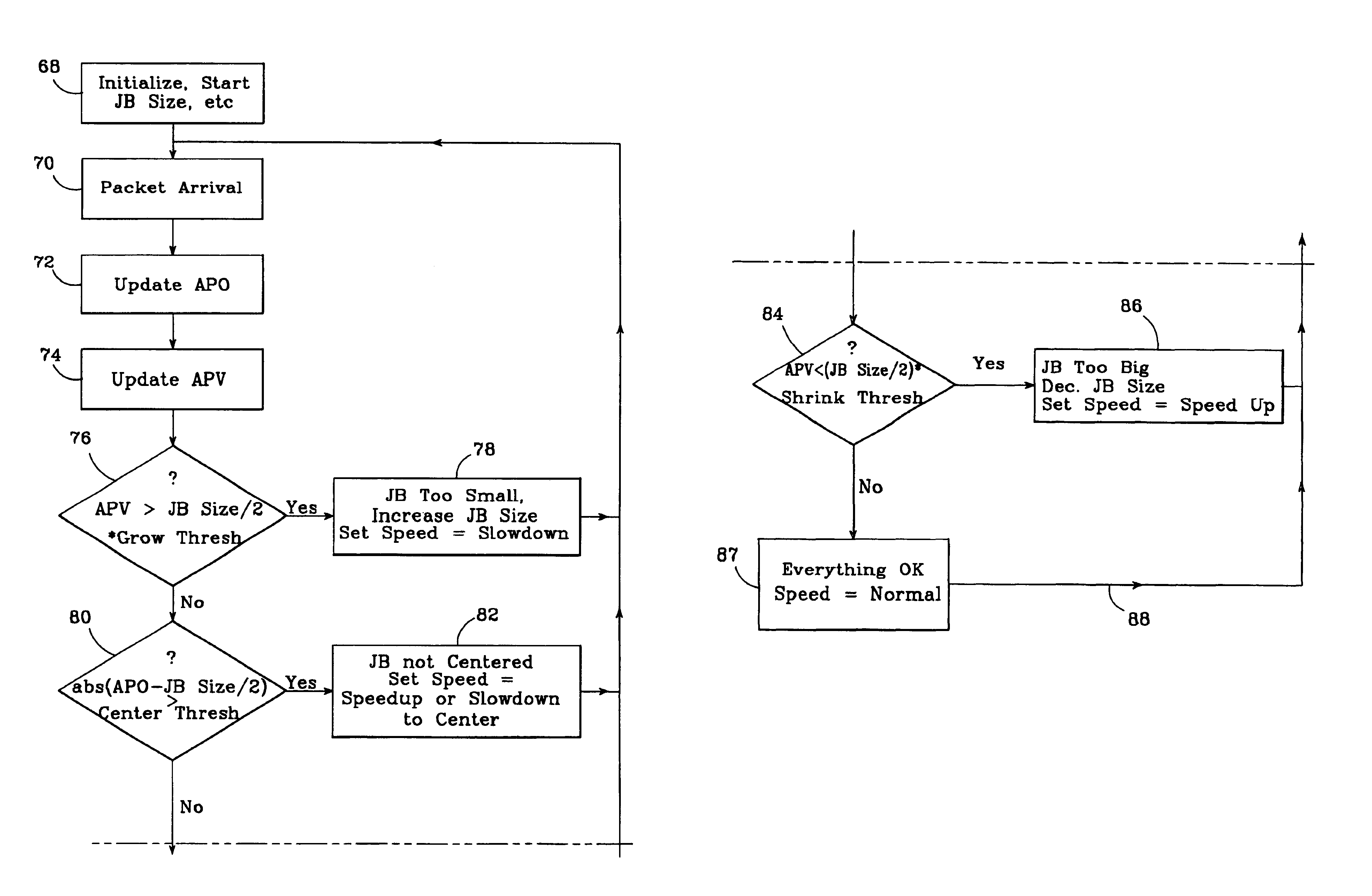
Adaptive jitter buffer for internet telephony
InactiveUS6862298B1Improve audio qualityTo overcome the large delayError preventionFrequency-division multiplex detailsPacket arrivalControl signal
In an improved system for receiving digital voice signals from a data network, a jitter buffer manager monitors packet arrival times, determines a time varying transit delay variation parameter and adaptively controls jitter buffer size in response to the variation parameter. A speed control module responds to a control signal from the jitter buffer manager by modifying the rate of data consumption from the jitter buffer, to compensate for changes in buffer size, preferably in a manner which maintains audio output with acceptable, natural human speech characteristics. Preferably, the manager also calculates average packet delay and controls the speed control module to adaptively align the jitter buffer's center with the average packet delay time.
Owner:GOOGLE LLC
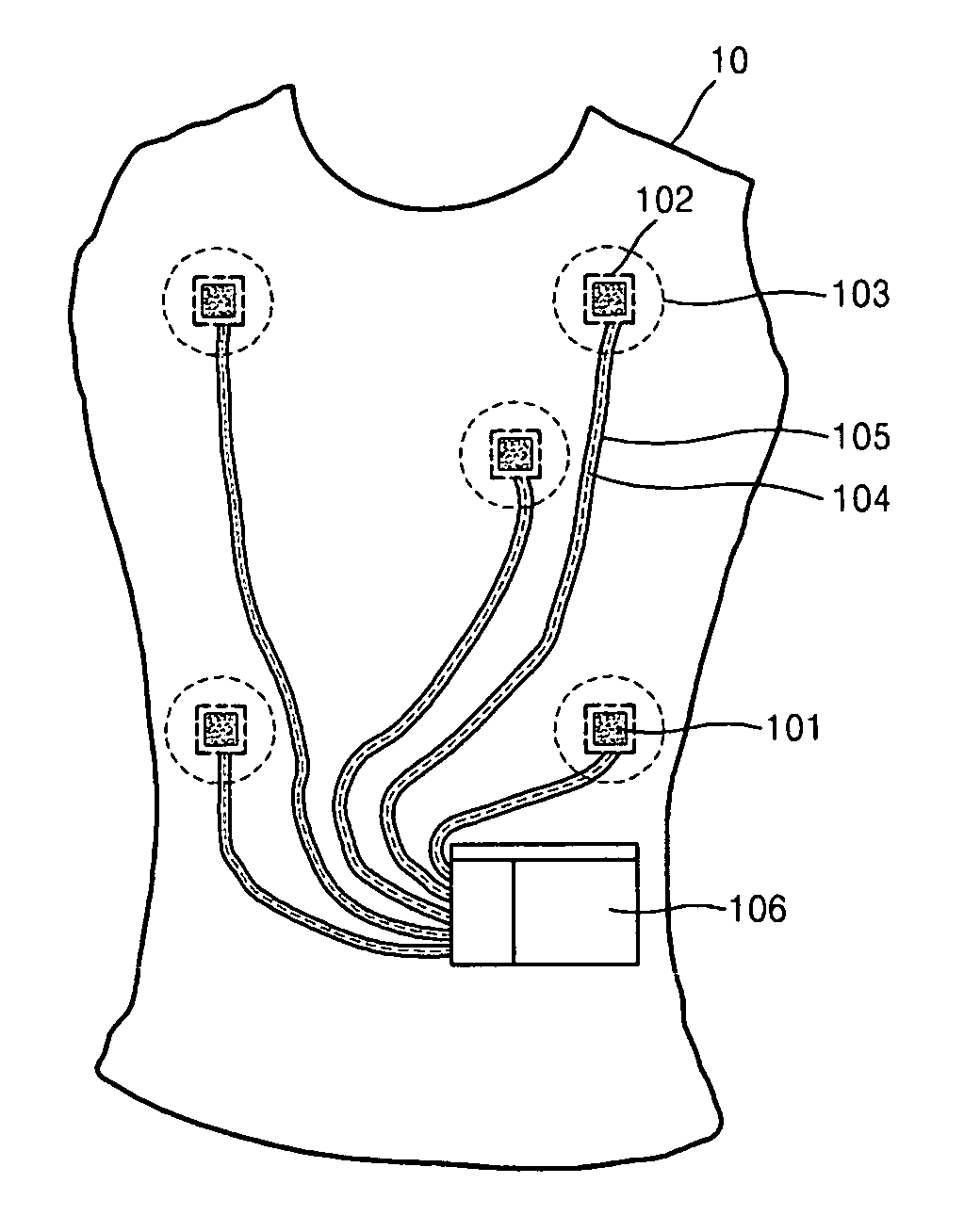
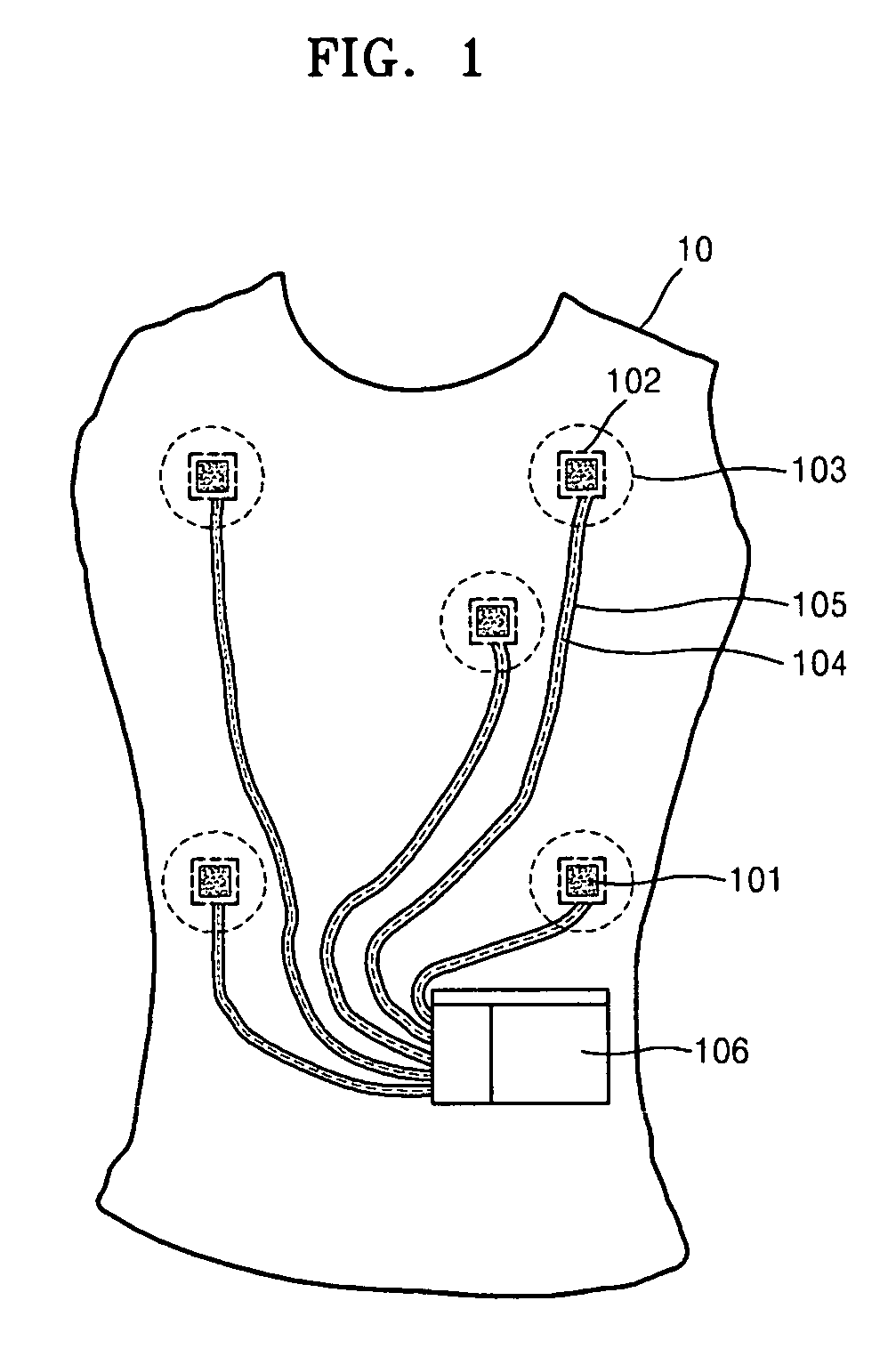
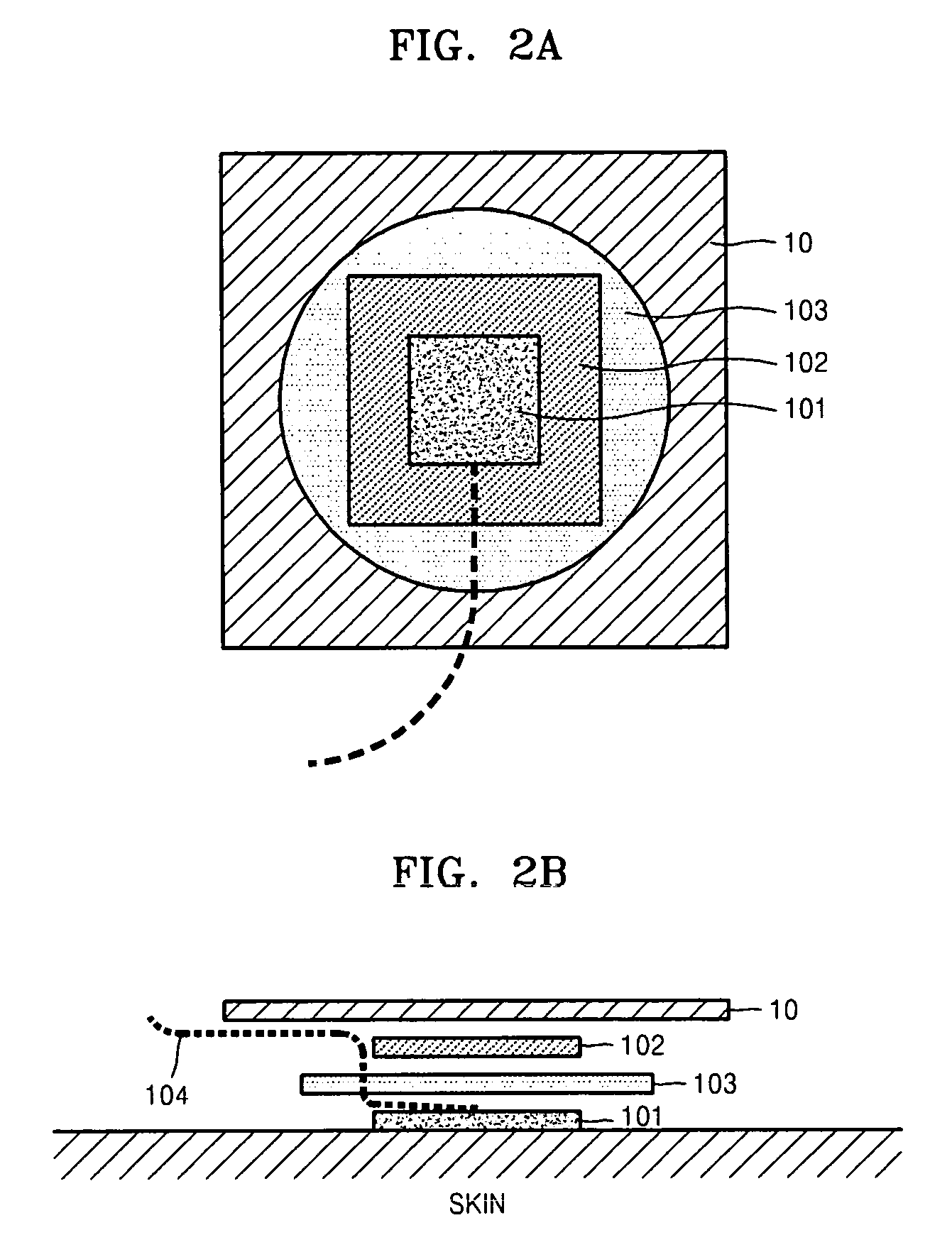
Garment for measuring physiological signal
InactiveUS20070038057A1Reduce contact resistanceReduce noiseElectrocardiographyNon-adhesive dressingsEngineeringBody condition
Provided is a smart garment for measuring a physiological signal which can improve comfort and convenience of wear and correctly measure a physiological signal. The smart garment for measuring physiological signals includes an electrode which is made of an electro-conductive fabric and detects a physiological signal, a physiological signal transmission line through which the detected physiological signal is transmitted, a physiological signal measuring unit which is connected to the transmission line, receives the physiological signal, and measures information regarding body conditions related to the physiological signal, and a pocket where the physiological signal measuring unit in inserted.
Owner:THE IND & ACADEMIC COOPERATION & CHUNGNAM NAT UNIV +1
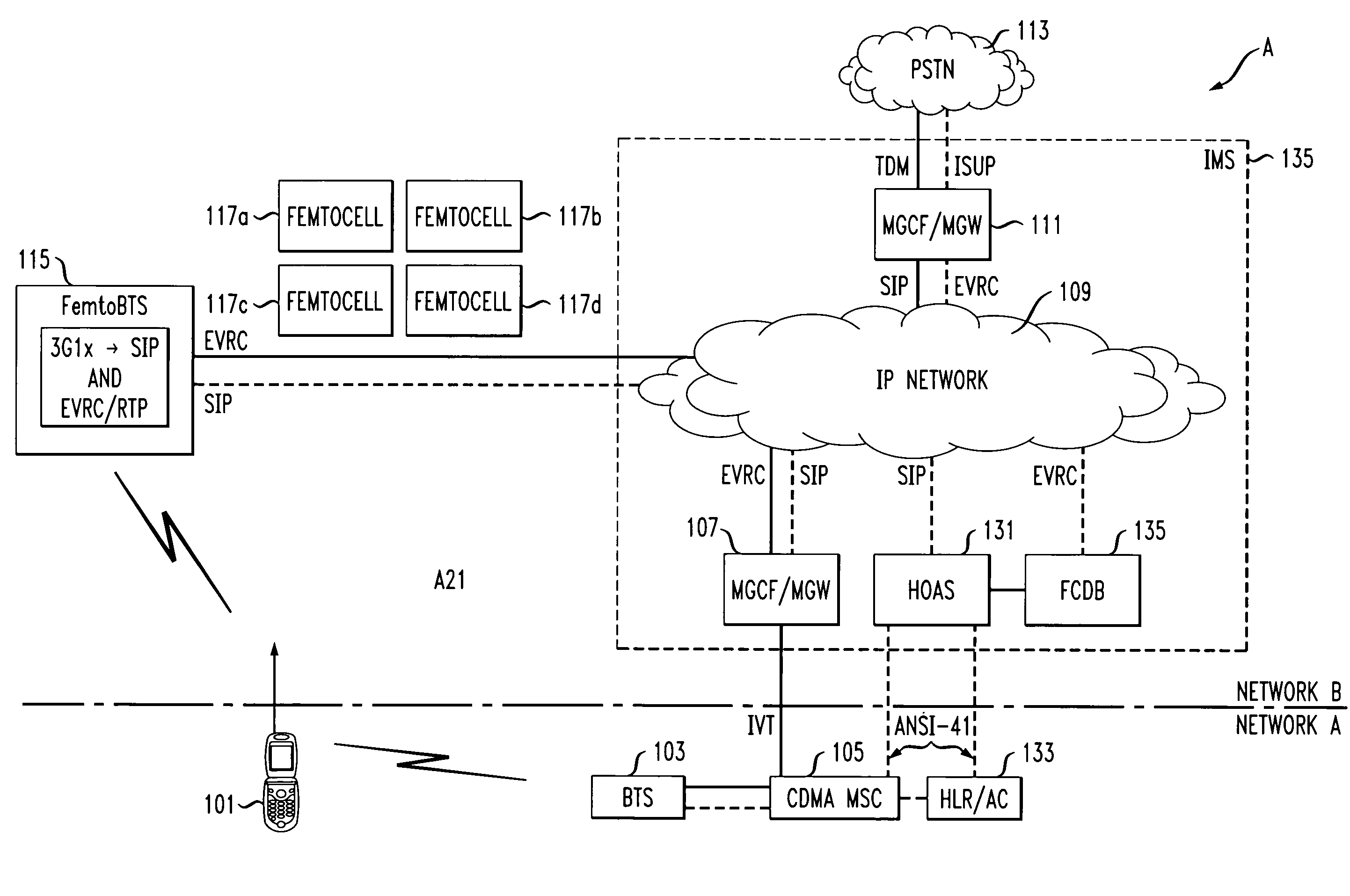
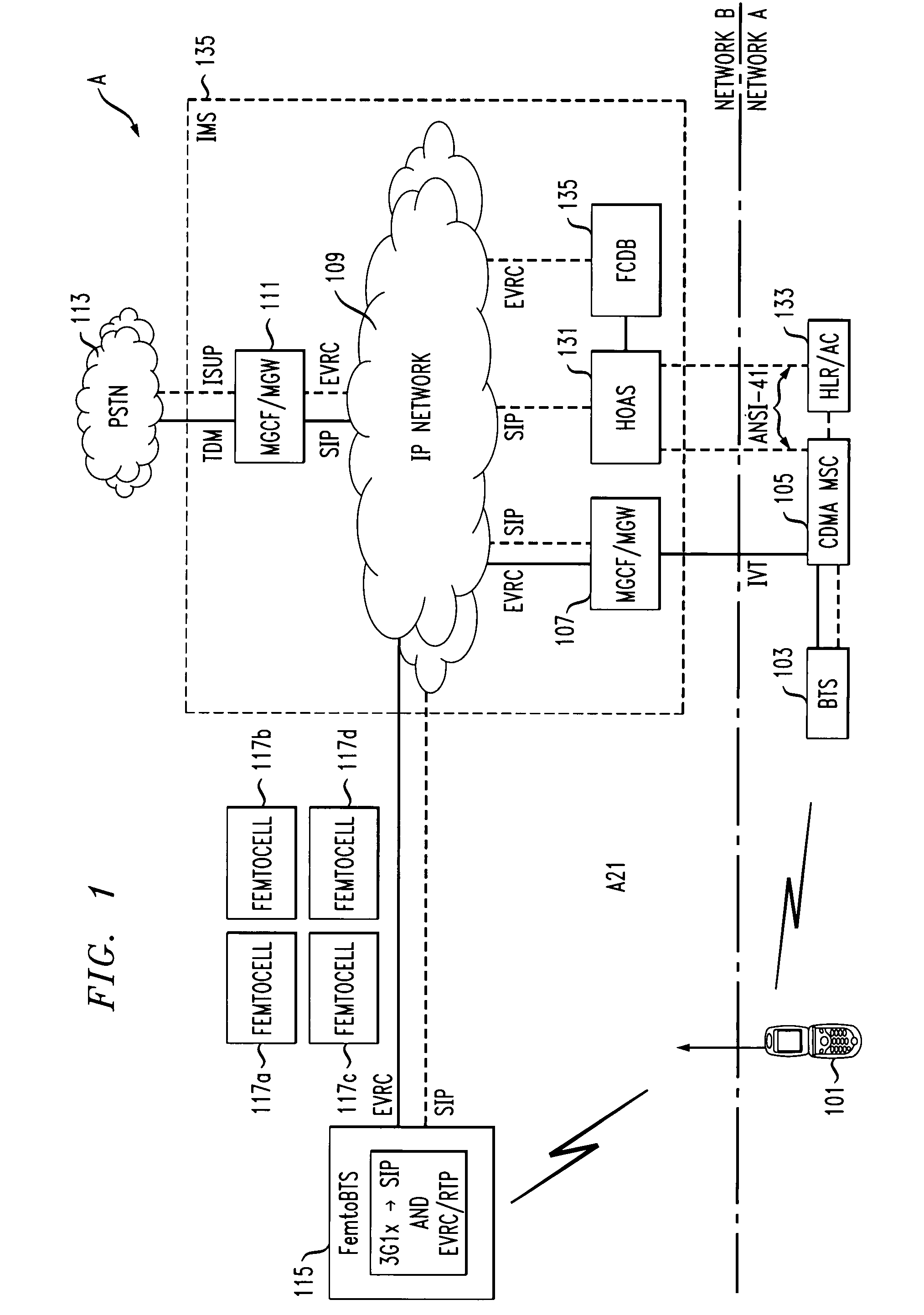
Method and apparatus to allow hand-off from a macrocell to a femtocell
InactiveUS20080305801A1Facilitates session controlBandwidth adjustableTransmission systemsNetwork topologiesTelecommunicationsMobile station
A method for hand-off of a CDMA access mobile from a macrocell to a femtocell is disclosed. The method includes tracking each femtocell which mobile stations have allowed access incorporating a mobile station identification for each of the mobile stations. The method continues with storing the mobile station identification for each femtocell. This may occur in a database or similar structure. The message continues on with requesting a hand-off from the macrocell to the femtocell via PN offset and the method concludes with querying all femtocells that have that PN offset that are within range of the macrocell's neighbor list. If only one femtocell fits that criteria the method is done. If more than one femtocell fits that criteria, a priority list may be set up based at least in part on the number of times and / or frequency that the mobile station has been allowed access on the femtocell. The method could include allocating resources for all high priority femtocells and cleaning up resources for the femtocells that do not send a hand-off complete message.
Owner:WSOU INVESTMENTS LLC
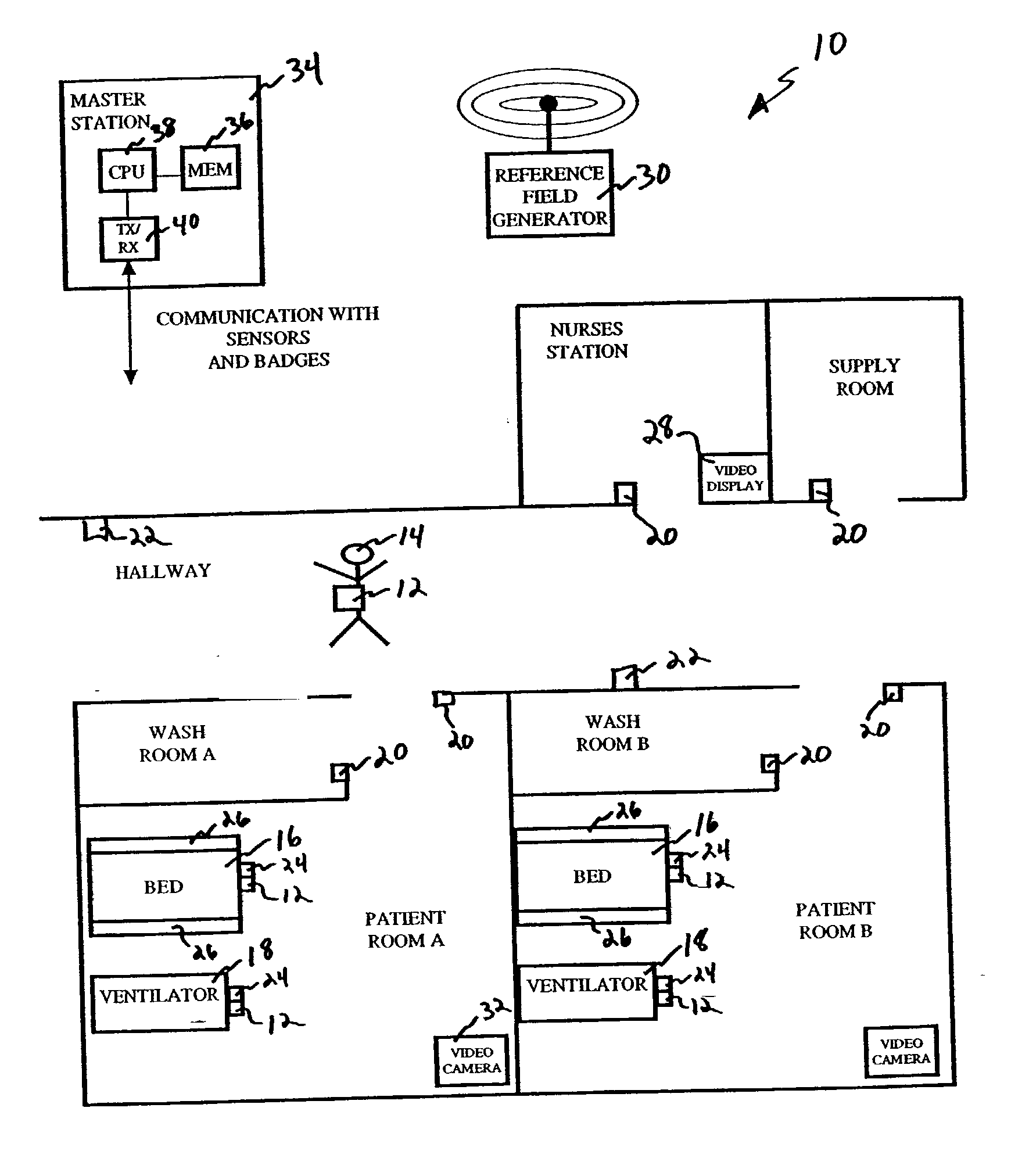
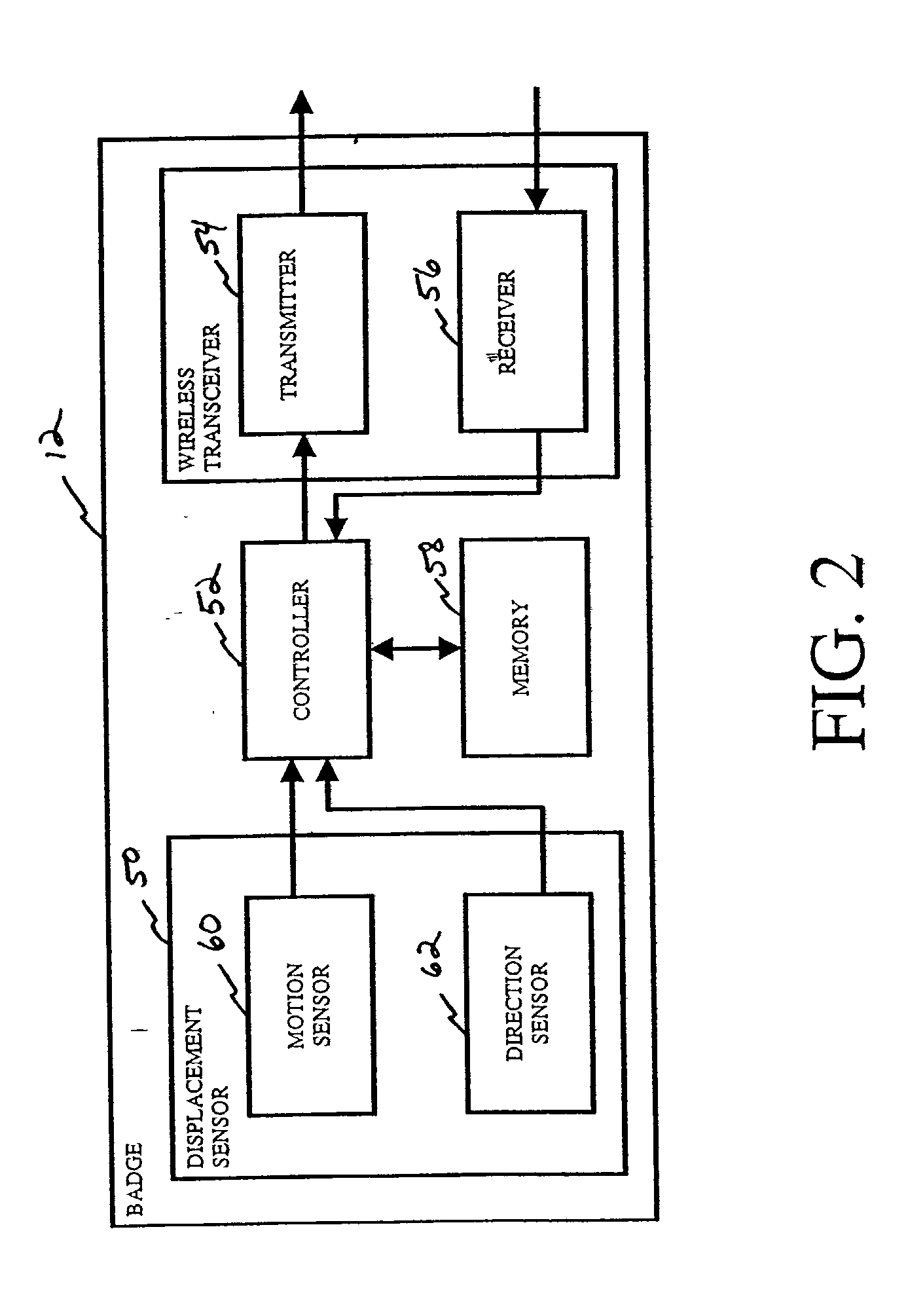
Article locating and tracking system
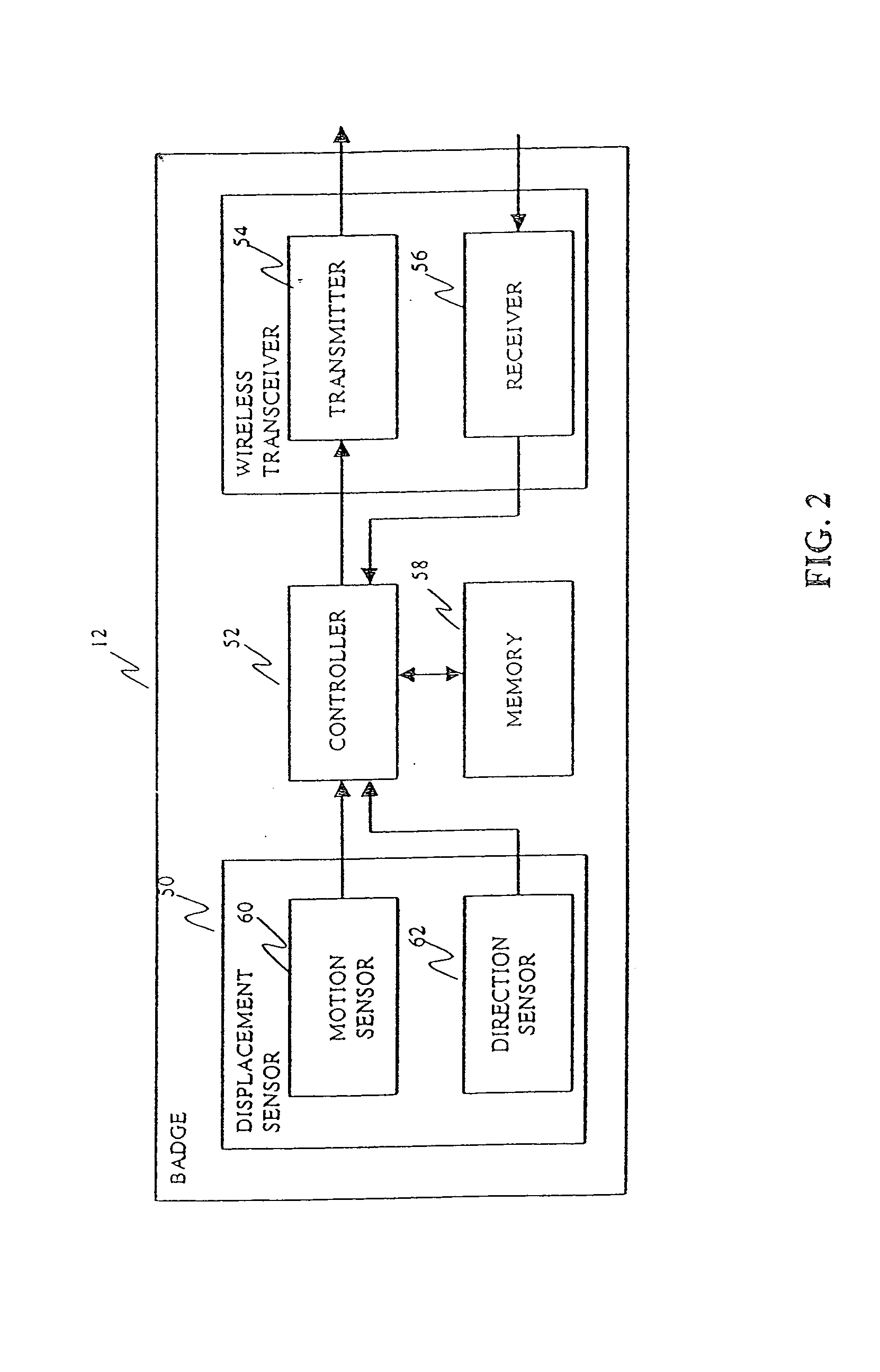
ActiveUS20020183979A1Reduce non-value added activityReduce in quantityRegistering/indicating time of eventsError detection/correctionTransceiverPosition dependent
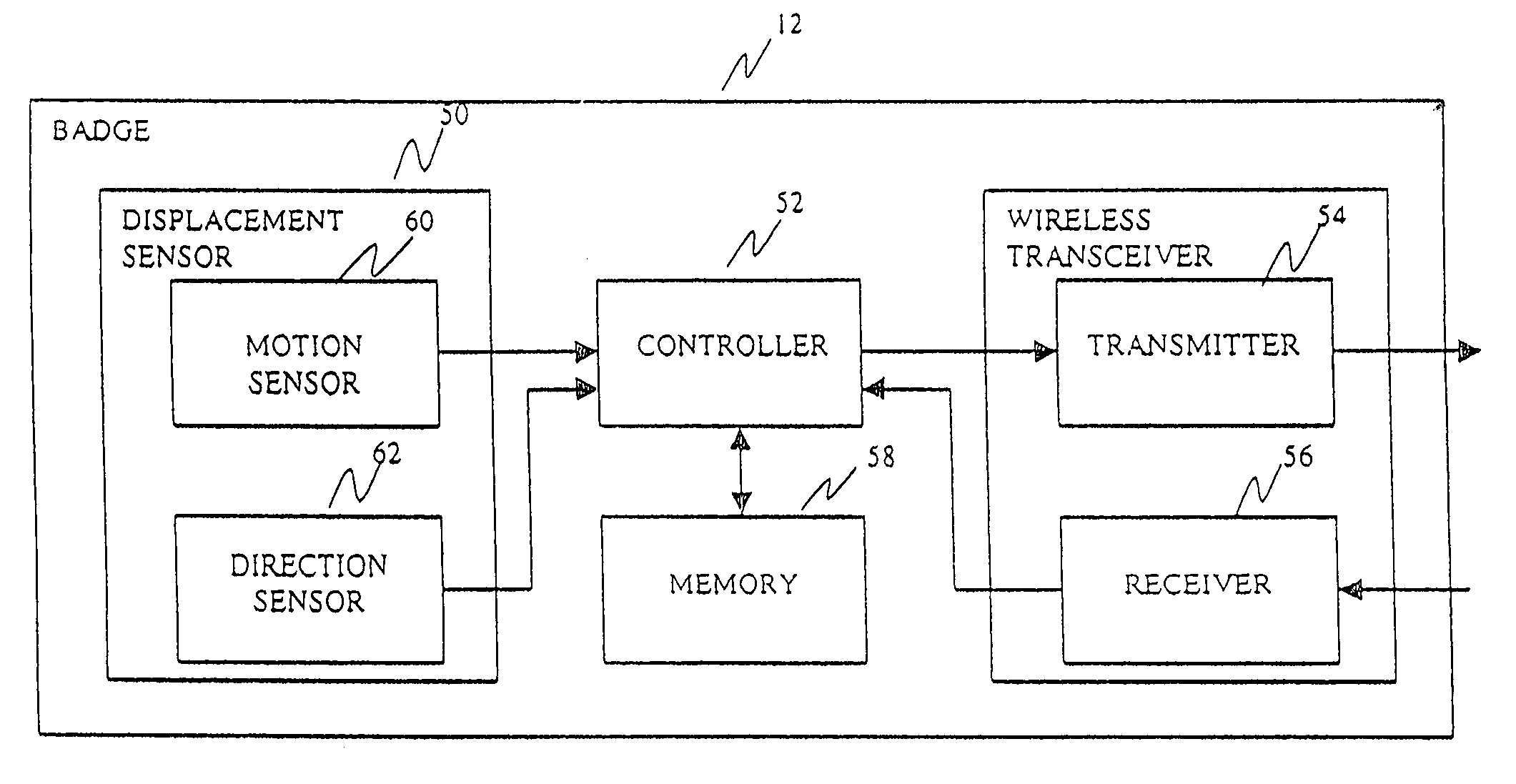
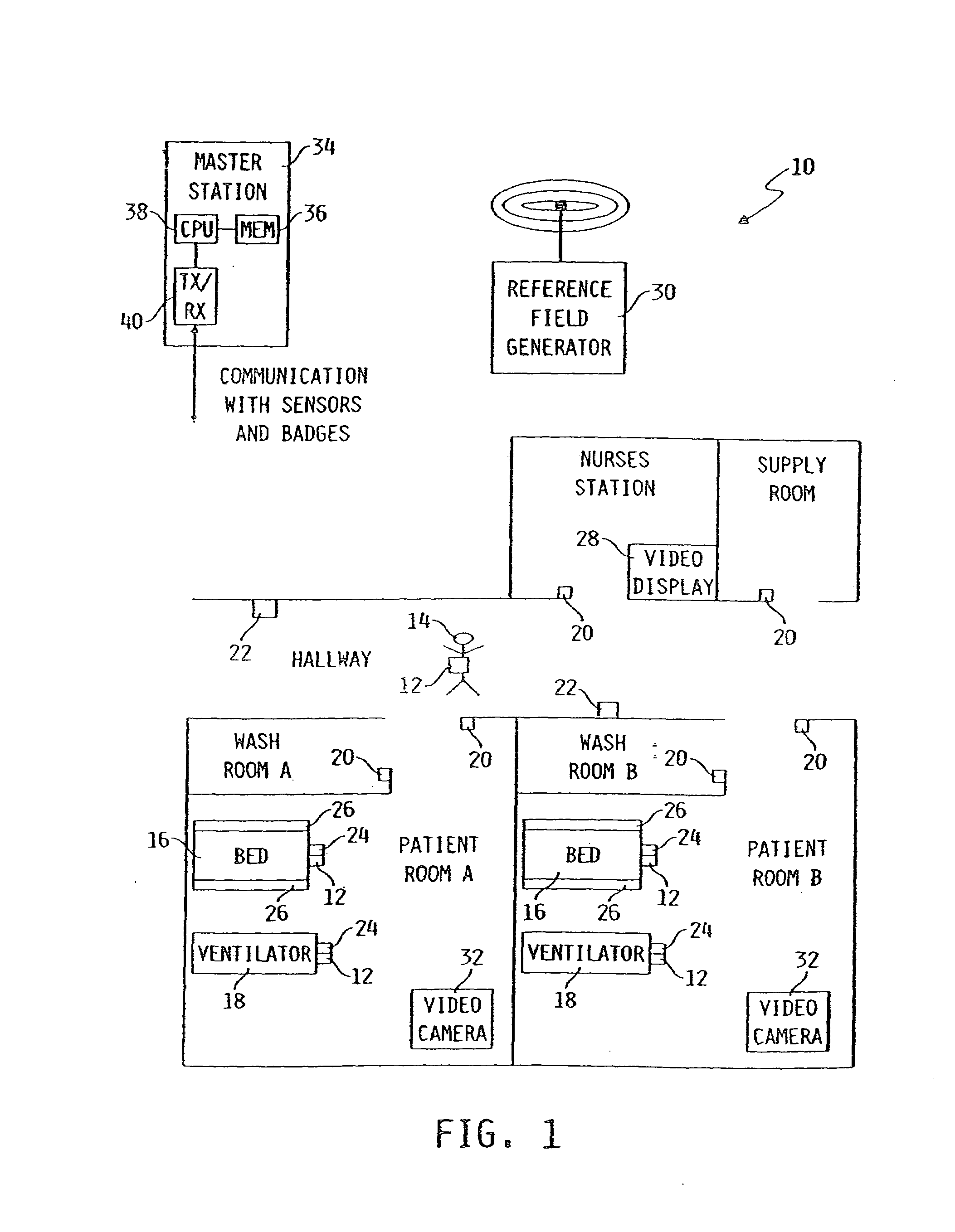
A system for tracking an activity in a healthcare environment includes a master station having a processor, a memory, and a transceiver, badges coupled to objects, each transmitting a unique badge ID, and sensors disposed throughout the environment, each including a transceiver for receiving badge IDs and transmitting to the master station transceiver the badge IDs and a unique sensor ID that relates the sensor to a location. The master station processor determines object locations from the badge and sensor IDs by identifying the badge associated with the object, relating the sensor ID to the sensor location, and storing object location information in memory. Each badge also includes a displacement sensor that generates signals indicating object movement and direction for transmission to the sensor transceivers which forward displacement information to the master station. The master station processor uses the information to update the stored object location information.
Owner:HILL ROM SERVICES
Communication system
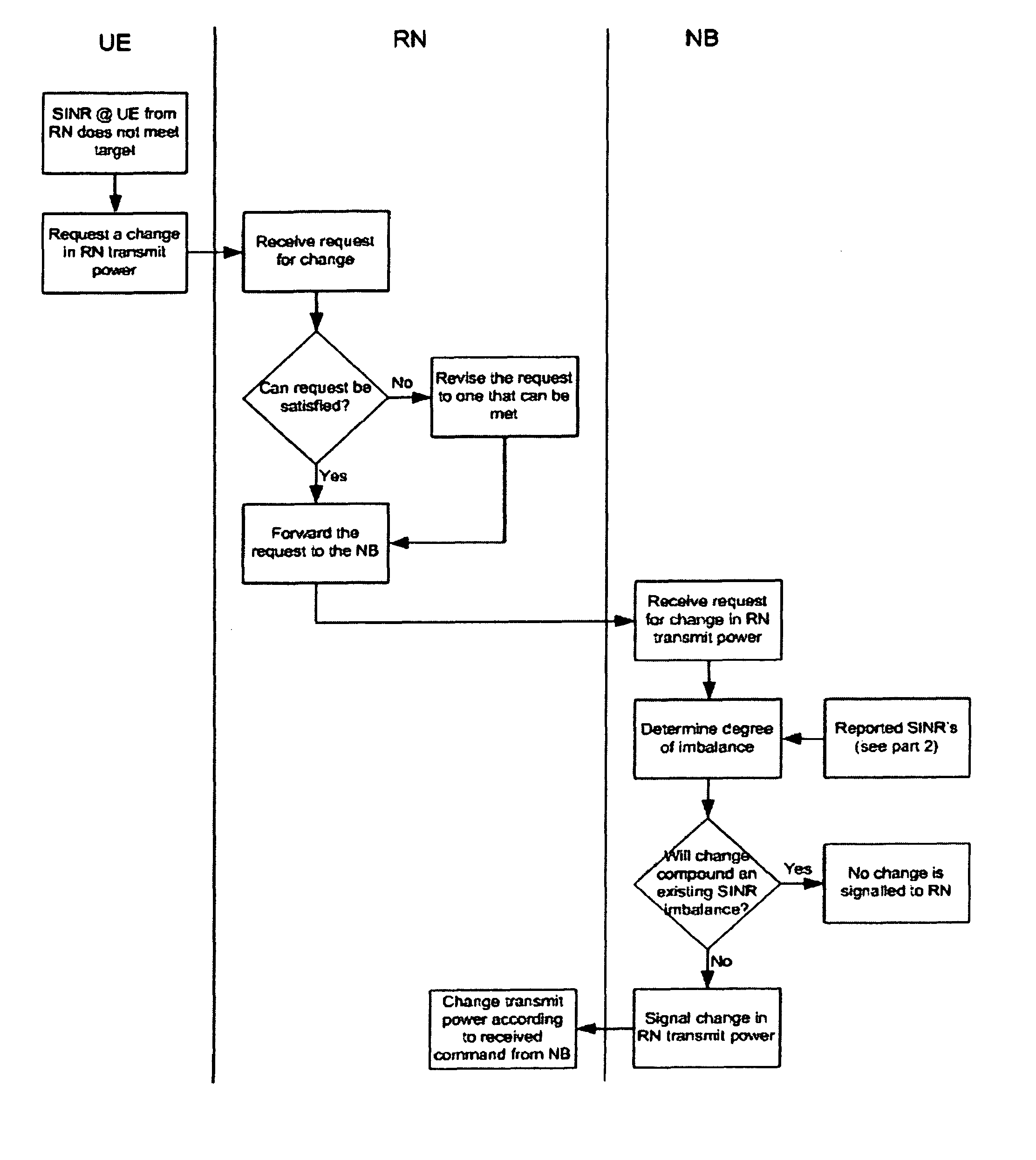
ActiveUS8150311B2Reduce or prevent substantial imbalanceMaintain qualityEnergy efficient ICTPower managementTelecommunicationsCommunications system
The present application relates to a wireless communication system and related methods and apparatuses for transmitting a signal from a source apparatus to a destination apparatus, via at least one intermediate apparatus. In particular, the present invention relates to techniques which seek to improve the throughput of data in multi-hop communication systems.
Owner:FUJITSU LTD
Computer resource allocating method
InactiveUS7062559B2Reduce loadMaintain qualityResource allocationMultiple digital computer combinationsComputer resourcesServer allocation
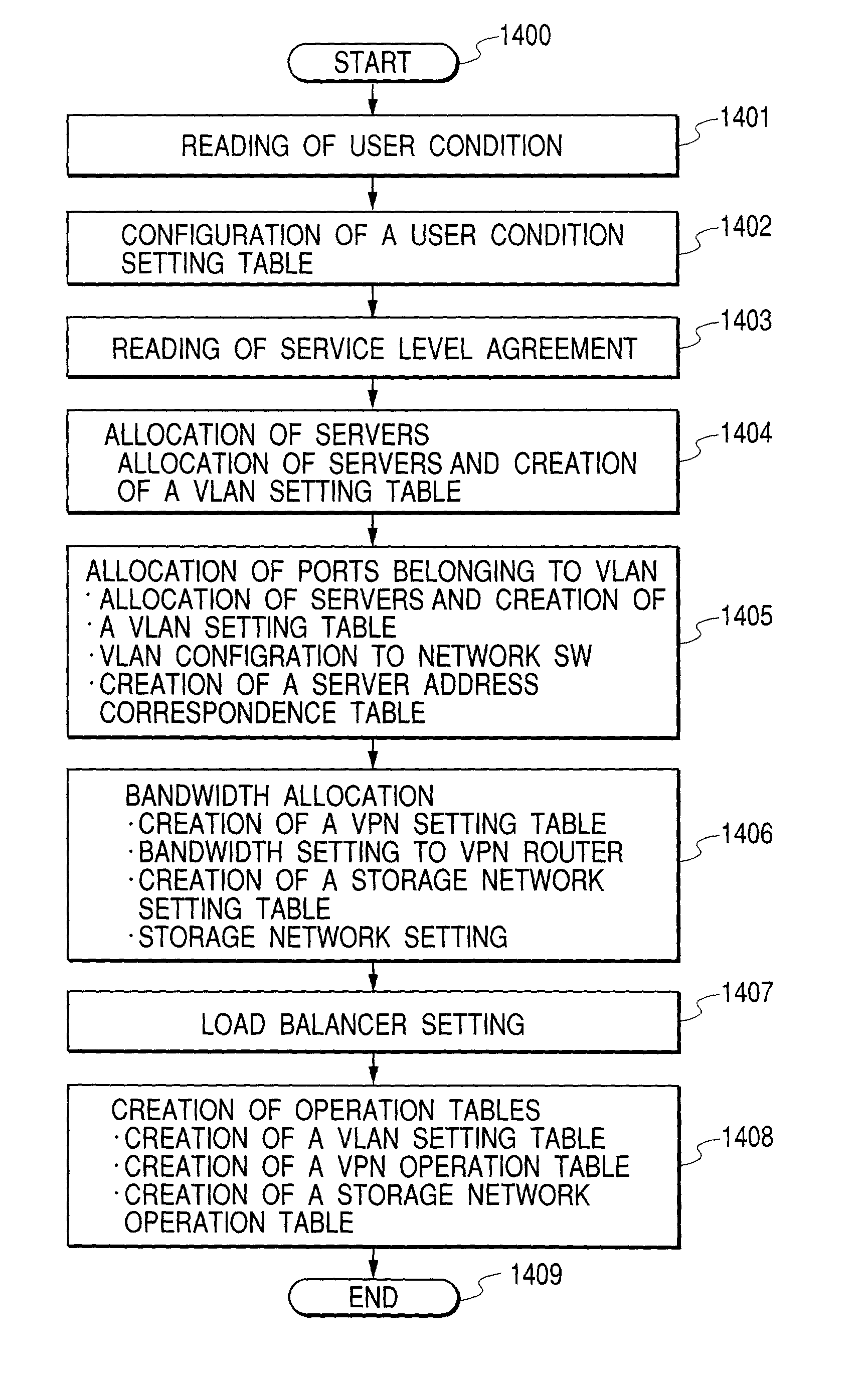
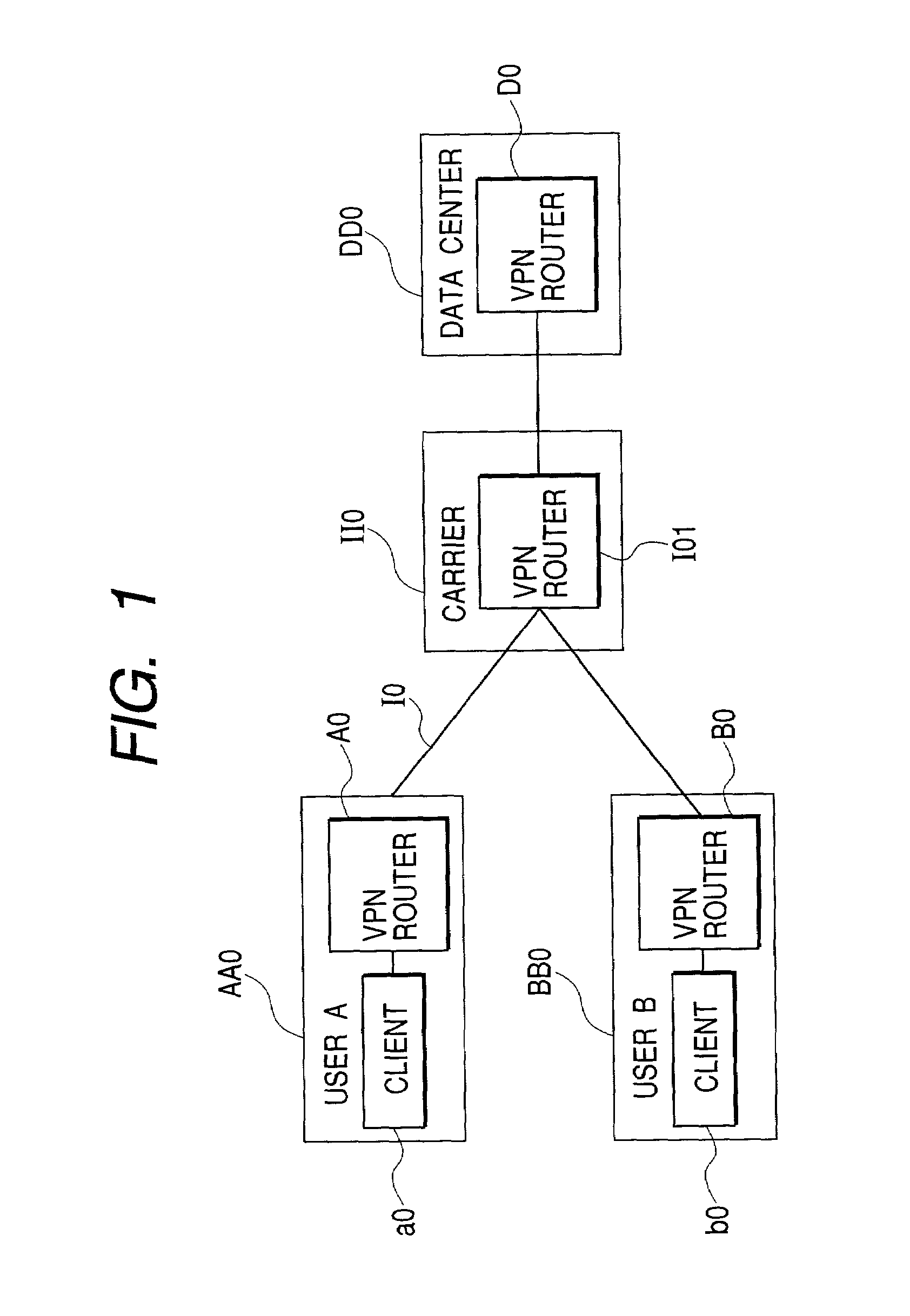
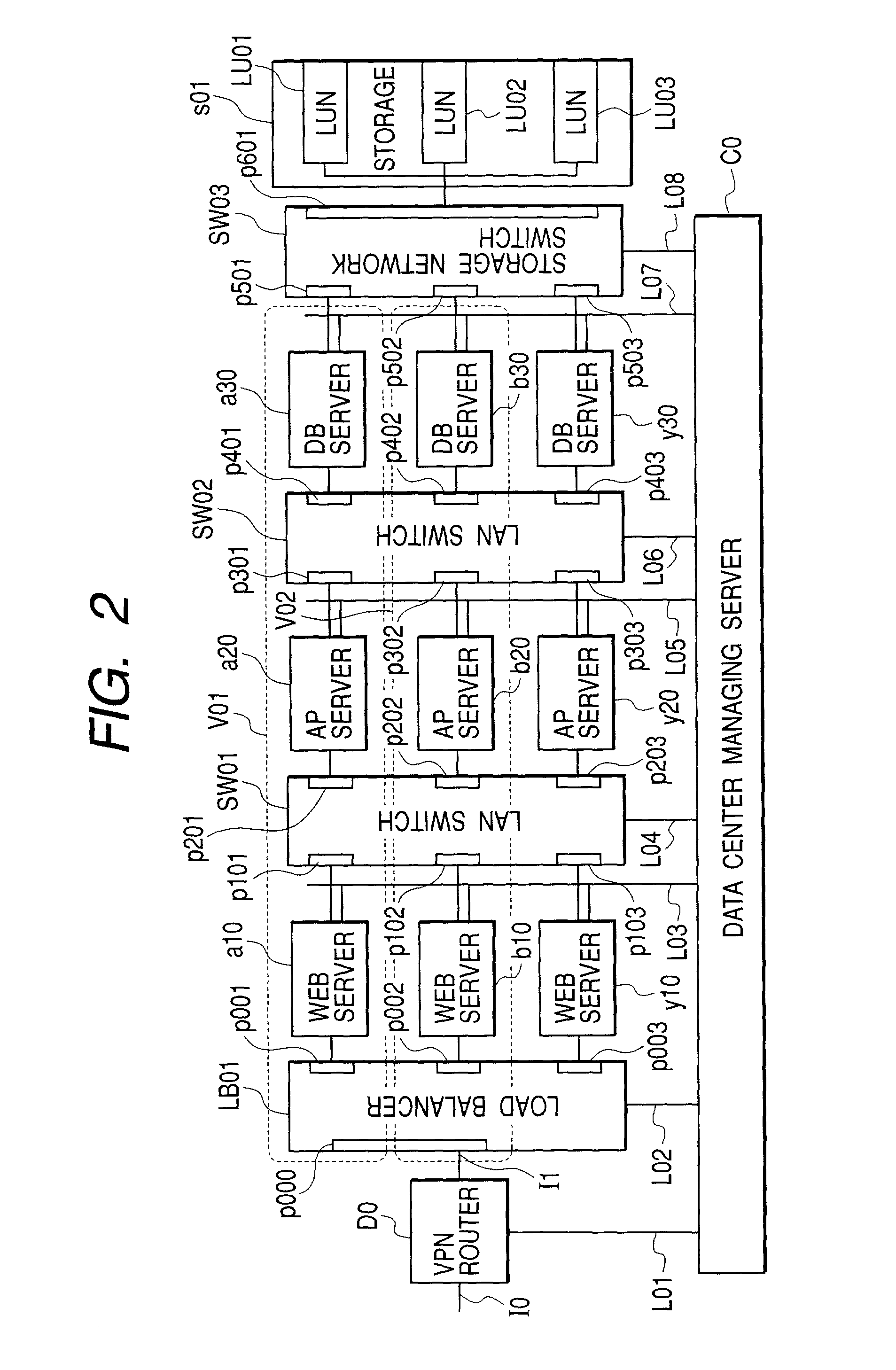
When a load of a user is fluctuated, a data center dynamically changes resource allocation to the user according to the load and holds security for each user.A control program on a data center managing server creates a VLAN configuration table so as to allocate a user-dedicated VLAN including plural network switches for each user company, thereby configuring the ports of a load balancer and network switches allocated to a user to the user-dedicated VLAN. A VPN is configured from the user to the data center, whereby a VLAN tagging technique is used to hold security of the user from the user to the data center. The control program compares a user condition setting table created along the service level agreement for each user with the monitoring result of the computer operating state (the CPU utilization history in a VLAN operation table) to dynamically change the computer allocation and VLAN configuration at unsatisfied agreement. Specifically, the VLAN configuration table and the VLAN operation table are changed to change the VLAN configuration in the load balancer and the network switches (in the case of the Web layer). The control program changes the parameter (the sever allocation history in the VLAN operation table) related to charge information based on that.
Owner:HITACHI LTD
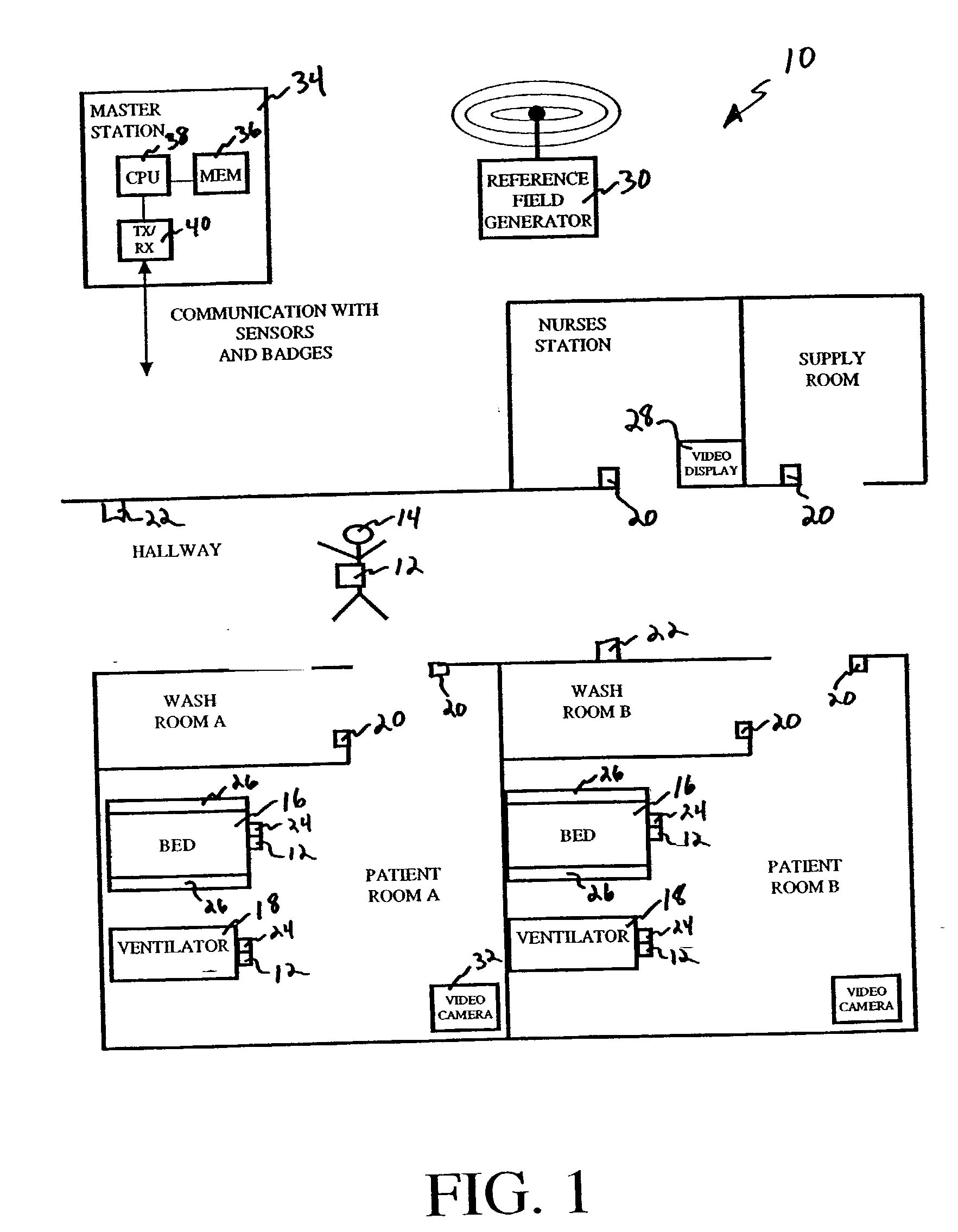
Article locating and tracking system
ActiveUS7248933B2Reduce non-value added activityReduce in quantityRegistering/indicating time of eventsError detection/correctionTransceiverMaster station
A system for tracking an activity in a healthcare environment includes a master station having a processor, a memory, and a transceiver, badges coupled to objects, each transmitting a unique badge ID, and sensors disposed throughout the environment, each including a transceiver for receiving badge IDs and transmitting to the master station transceiver the badge IDs and a unique sensor ID that relates the sensor to a location. The master station processor determines object locations from the badge and sensor IDs by identifying the badge associated with the object, relating the sensor ID to the sensor location, and storing object location information in memory. Each badge also includes a displacement sensor that generates signals indicating object movement and direction for transmission to the sensor transceivers which forward displacement information to the master station. The master station processor uses the information to update the stored object location information.
Owner:HILL ROM SERVICES
Online personalized apparel design and sales technology with associated manufacturing and fulfillment techniques and processes
The present invention relates to systems and methods for the customized and personalized design of school, team, club, class and event branded apparel and merchandise online via dealer, client-branded and business-to-business websites without minimum orders. The invention further comprises customized design ordering, order fulfillment, image text positioning, image curing, image cutting, and pixilation methods.
Owner:MYGARB
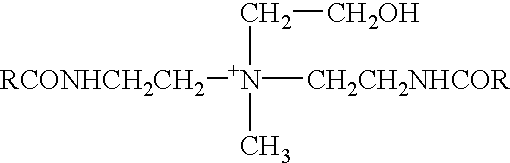
Composition and method for preparing biocompatible surfaces
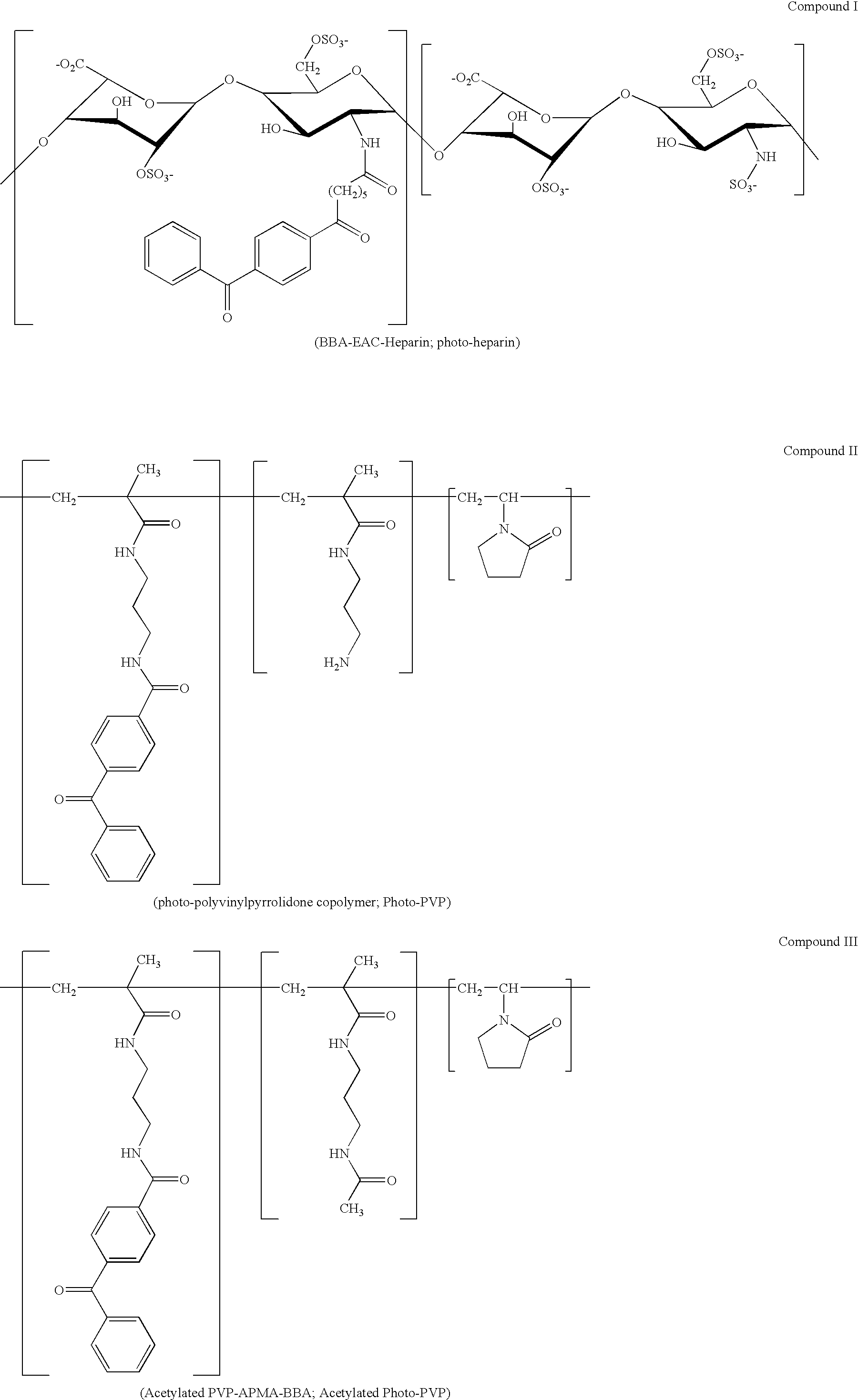
ActiveUS20050244453A1Reduced throughput timeEfficient and cost-effectiveBiocideOrganic active ingredientsPre irradiationActive agent
The invention provides methods and compositions for providing biocompatible surfaces to medical articles. In particular the invention provides biocompatible coatings with heparin activity. In some aspects, the biocompatible coatings of the invention are able to release a bioactive agent. The coatings can be formed using biostable or biodegradable polymeric material and photoreactive groups. The invention also provides methods for improving the quality of bioactive agent-containing coatings by performing pre-irradiation of biocompatible coating compositions.
Owner:SURMODICS INC
Apparatus for processing an audio signal and method thereof
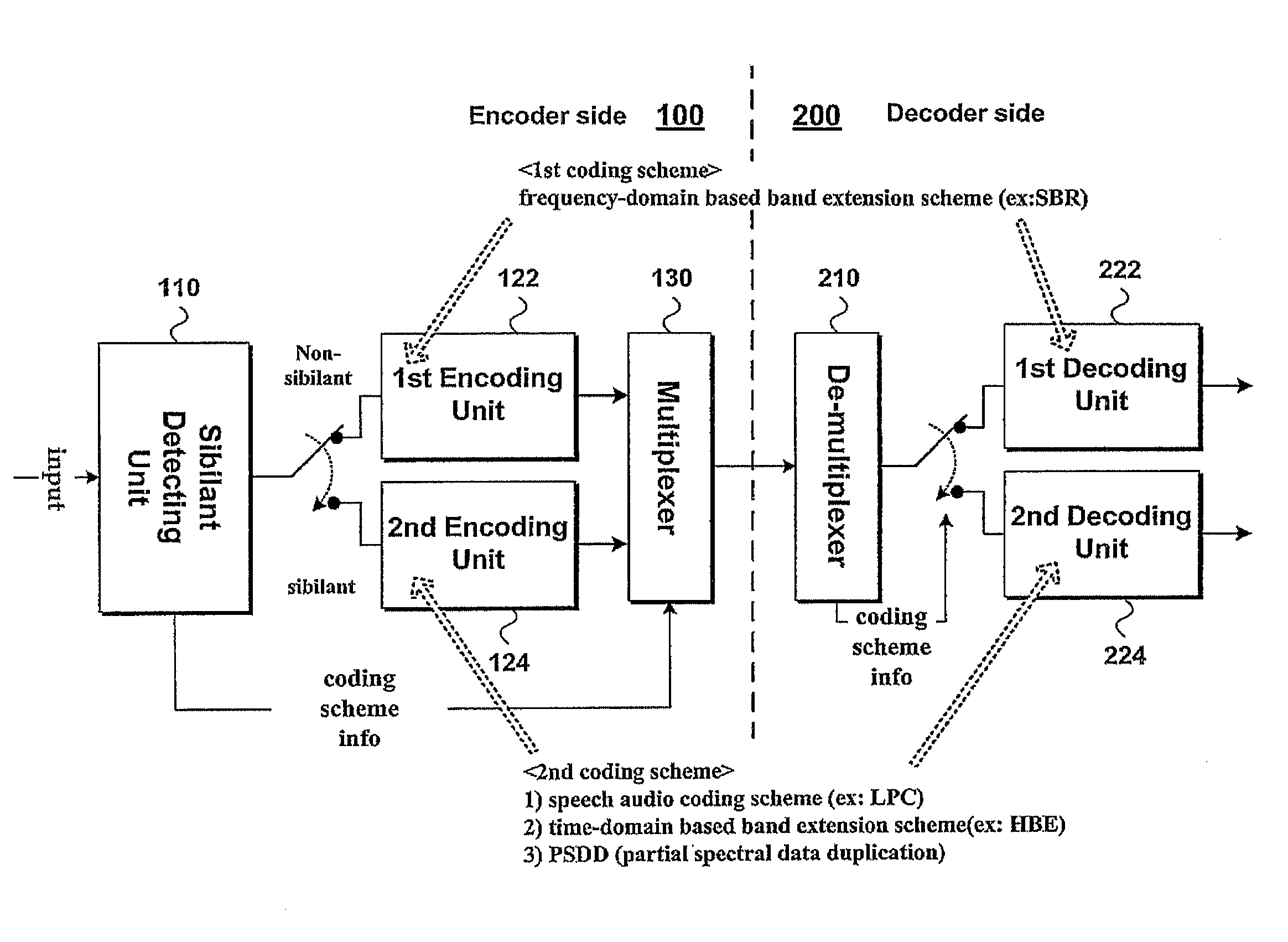
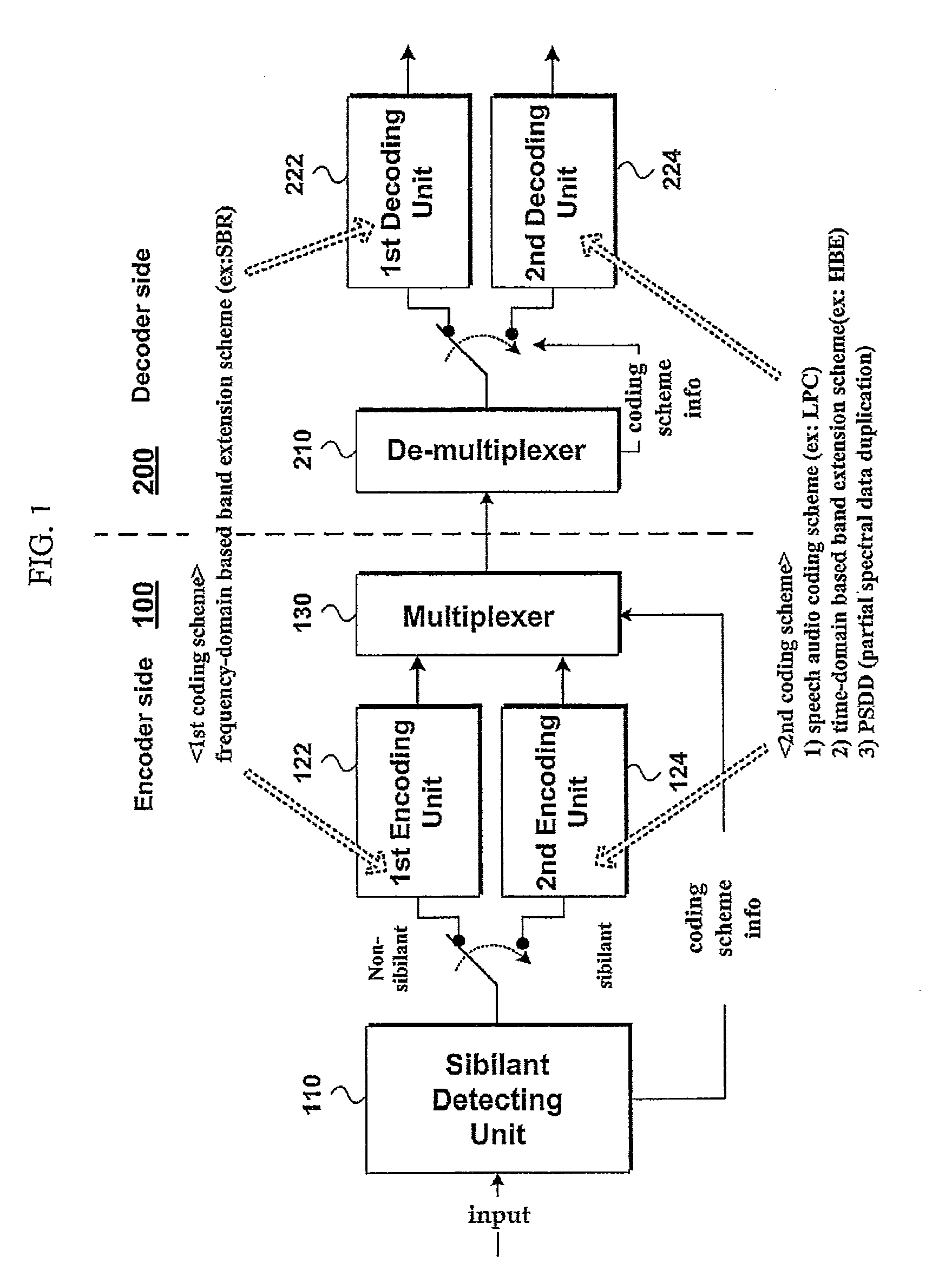
ActiveUS20100114583A1Maintain sound qualityMaintain qualitySpeech analysisFrequency spectrumComputer science
An apparatus for processing an audio signal and method thereof are disclosed. The present invention includes receiving a spectral data of lower band and type information indicating a particular band extension scheme for a current frame of the audio signal from among a plurality of band extension schemes including a first band extension scheme and a second band extension scheme, by an audio processing apparatus; when the type information indicates the first band extension scheme for the current frame, generating a spectral data of higher band in the current frame using the spectral data of lower band by performing the first band extension scheme; and when the type information indicates the second band extension scheme for the current frame, generating the spectral data of higher band in the current frame using the spectral data of lower band by performing the second band extension scheme, wherein the first band extension scheme is based on a first data area of the spectral data of lower band, and wherein the second band extension scheme is based on a second data area of the spectral data of lower band.
Owner:LG ELECTRONICS INC
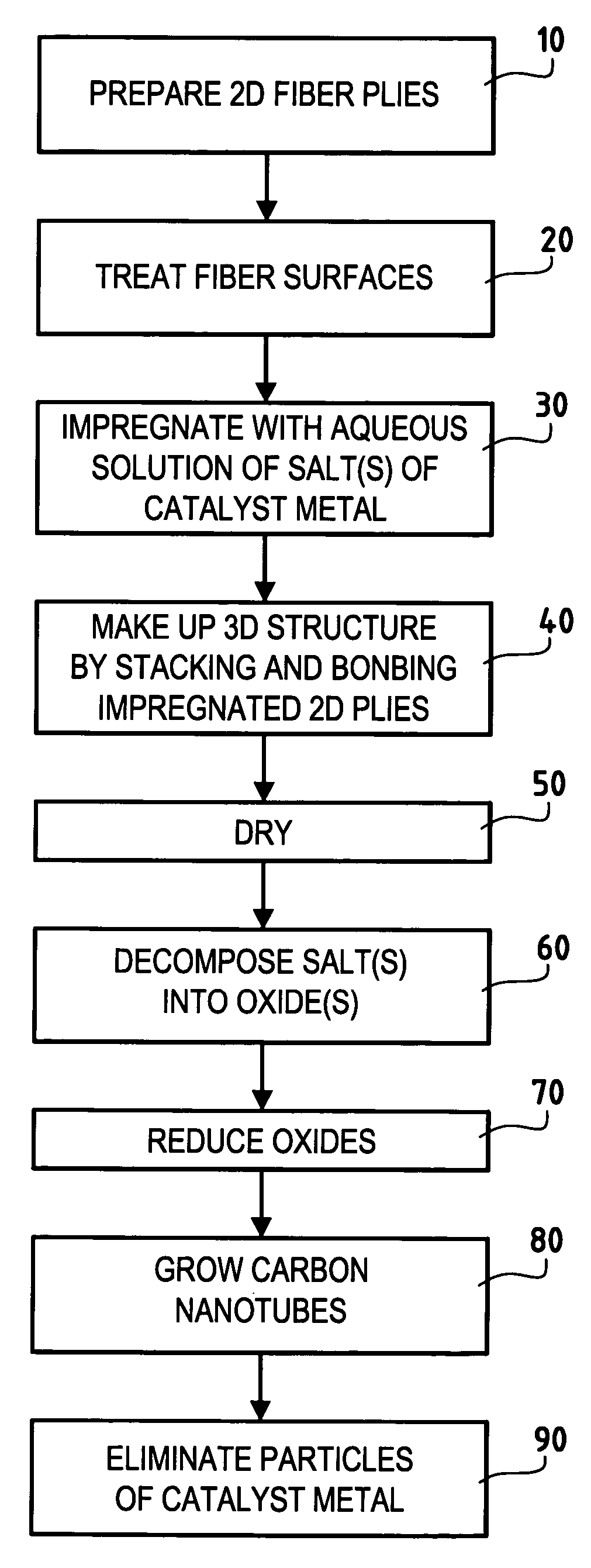
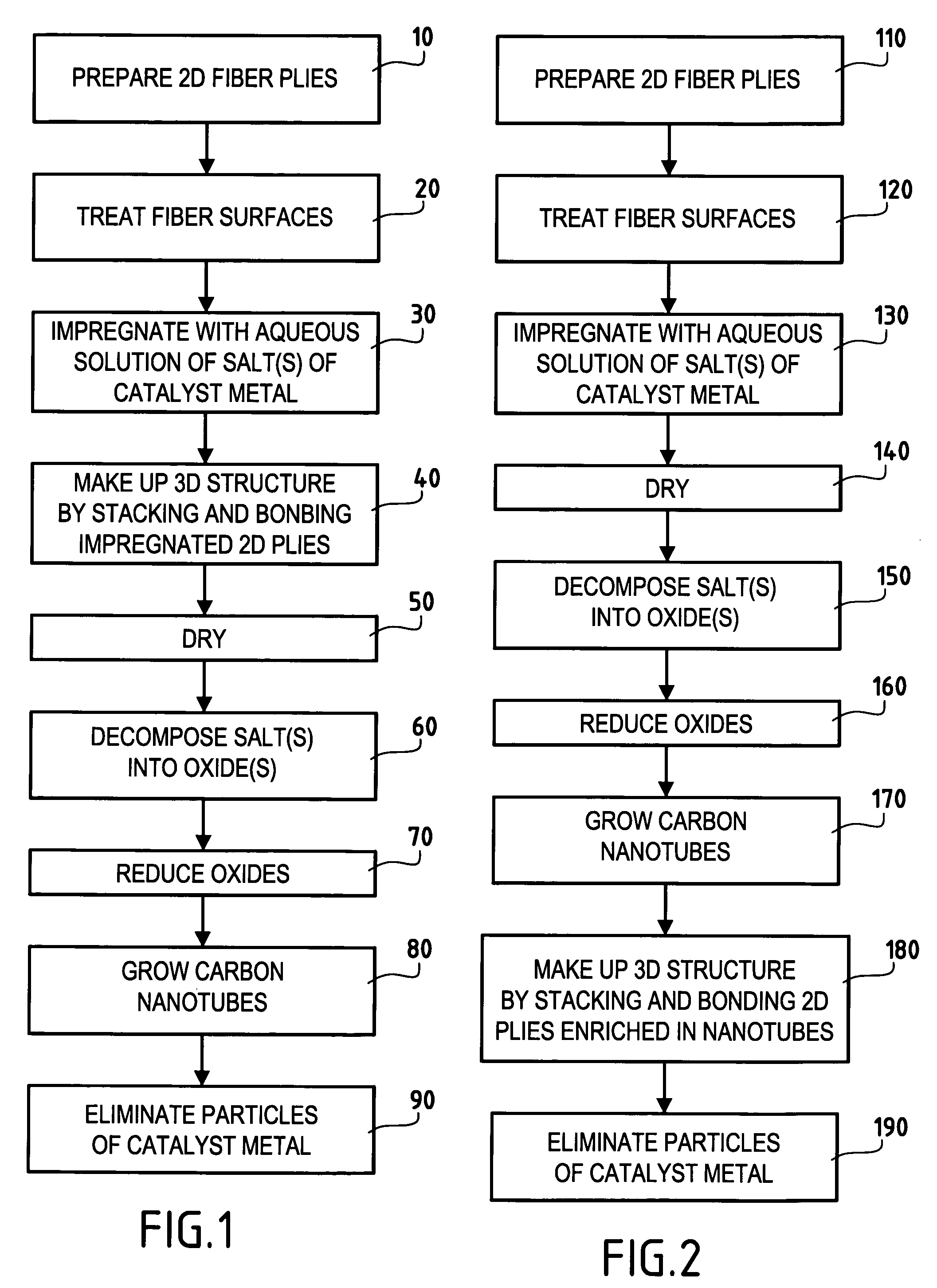
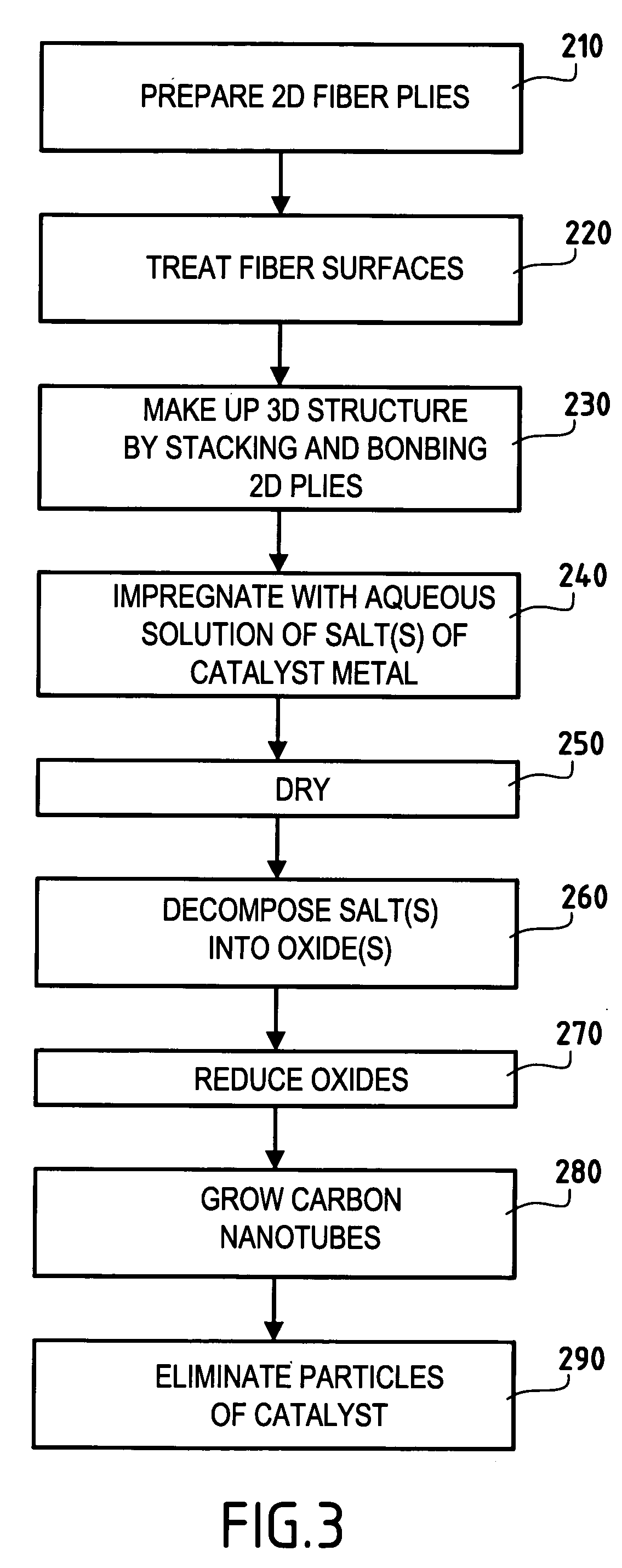
Three-dimensional fiber structure of refractory fibers, a method of making it, and thermostructural composite materials, in particular friction parts, made therefrom
ActiveUS20050176329A1Improve propertiesEasy to prepareMaterial nanotechnologyCarbon fibresMetallurgyCarbon nanotube
Carbon nanotubes are incorporated in the fiber structure by growing them on the refractory fibers of the substrate so as to obtain a three-dimensional substrate made of refractory fibers and enriched in carbon nanotubes. The substrate is densified with a matrix to form a part of composite material such as a friction part of C / C composite material.
Owner:CENT NAT DE LA RECHERCHE SCI
Cartridge with printhead and media feed mechanism for mobile device
InactiveUS20060250461A1Maintain print qualityLimit contaminationTypewritersSubstation equipmentPrint mediaEngineering
A cartridge for use in a mobile device including: (a) an inkjet printhead; (b) a print media feed path for directing print media past the printhead in a feed direction during printing; and (c) a drive mechanism for driving the print media past the inkjet printhead for printing.
Owner:SILVERBROOK RES PTY LTD
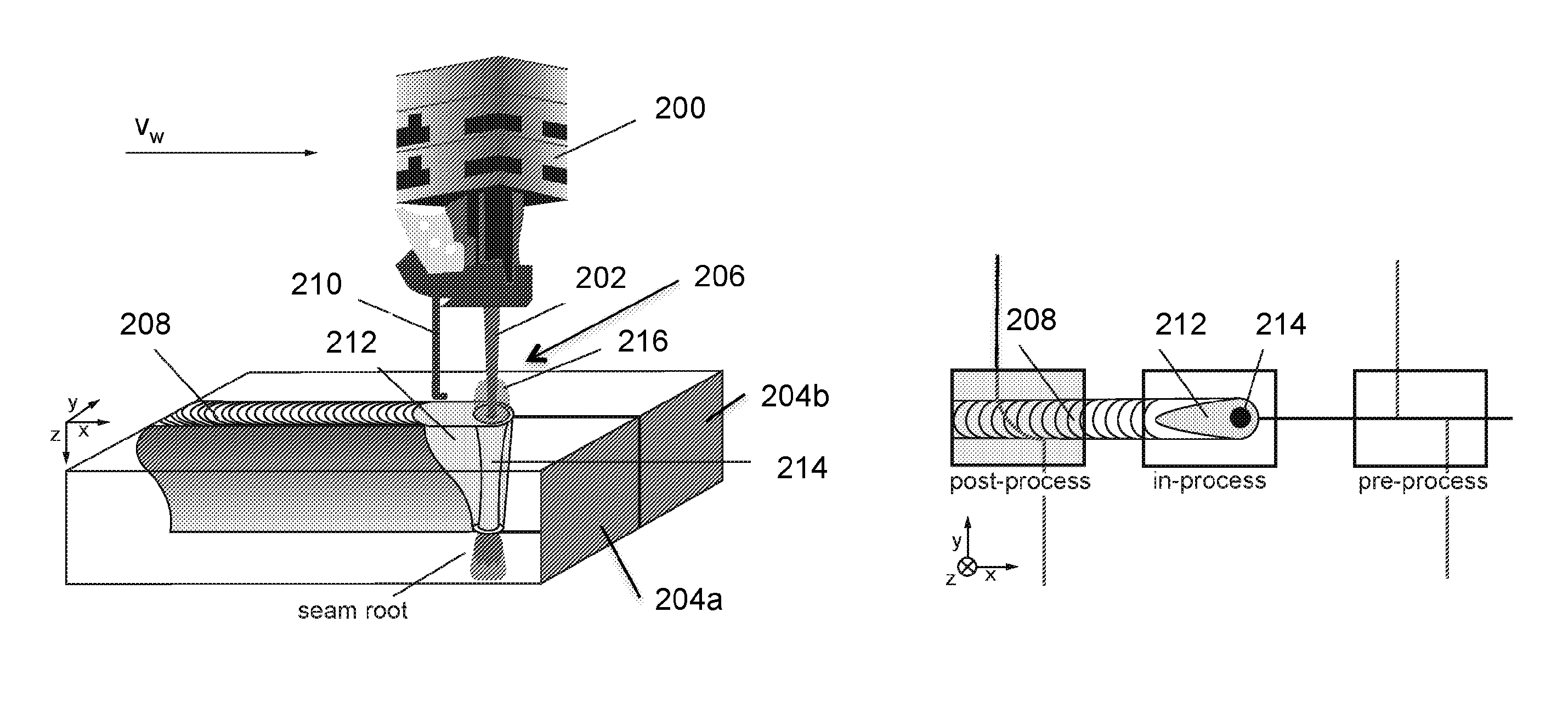
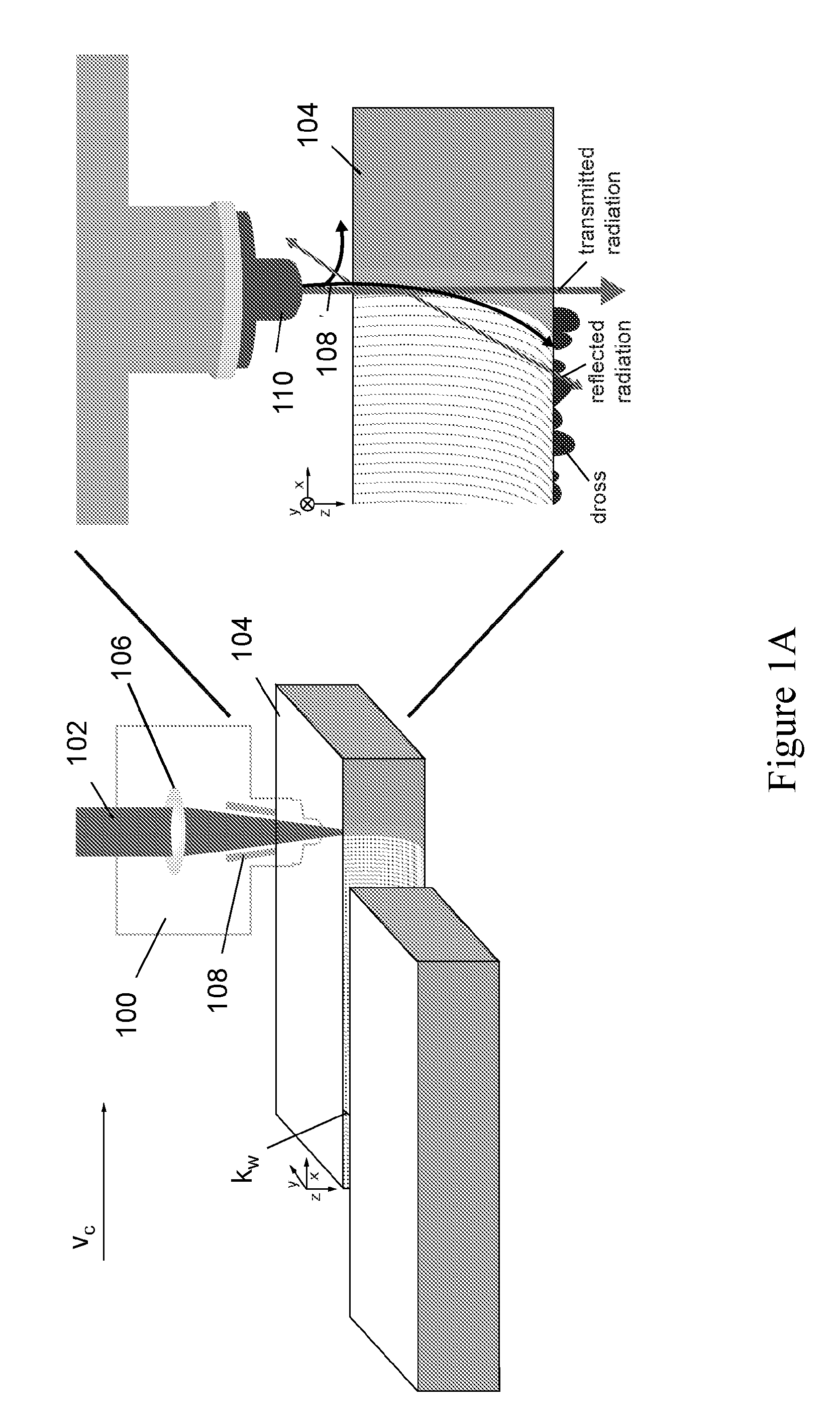
Method for closed-loop controlling a laser processing operation and laser material processing head using the same
ActiveUS20130178952A1Reliable detectionSimilar levelImage analysisSoldering apparatusLaser processingAlgorithm
The present invention relates to a method for closed-loop controlling a processing operation of a workpiece, comprising the steps of: (a) recording a pixel image at an initial time point of an interaction zone by means of a camera, wherein the workpiece is processed using an actuator having an initial actuator value; (b) converting the pixel image into a pixel vector; (c) representing the pixel vector by a sum of predetermined pixel mappings each multiplied by a corresponding feature value; (d) classifying the set of feature values on the basis of learned feature values into at least two classes of a group of classes comprising a first class of a too high actuator value, a second class of a sufficient actuator value and a third class of a too low actuator value at the initial time point; (e) performing a control step for adapting the actuator value by minimizing the error et between a quality indicator ye and a desired value; and (f) repeating the steps (a) to (e) for further time points to perform a closed-loop controlled processing operation.
Owner:PRECITEC GMBH +1
Method, Apparatus and Computer Program Product For Handover Failure Recovery
ActiveUS20100238799A1Fail to recoverImprove handoverError preventionFrequency-division multiplex detailsRadio link failuresComputer science
An apparatus for facilitating handover failure recovery may include a handover management element configured to receive, at a target node, a handover request from a source node regarding the handover of communications with a mobile terminal. The handover request may include identity information indicative of the mobile terminal. The identity information may be the identity information used to identify the mobile terminal to the source node during establishment of the original connection between the source node and the mobile terminal. The handover management element may be further configured to receive a request for a connection from the mobile terminal subsequent to a radio link failure and prior to handover completion. Based on matching the identity information from the request for connection and the identity information received from the source node, the target node may establish communication with the mobile terminal based on access stratum configuration information used by the source node.
Owner:NOKIA TECHNOLOGLES OY
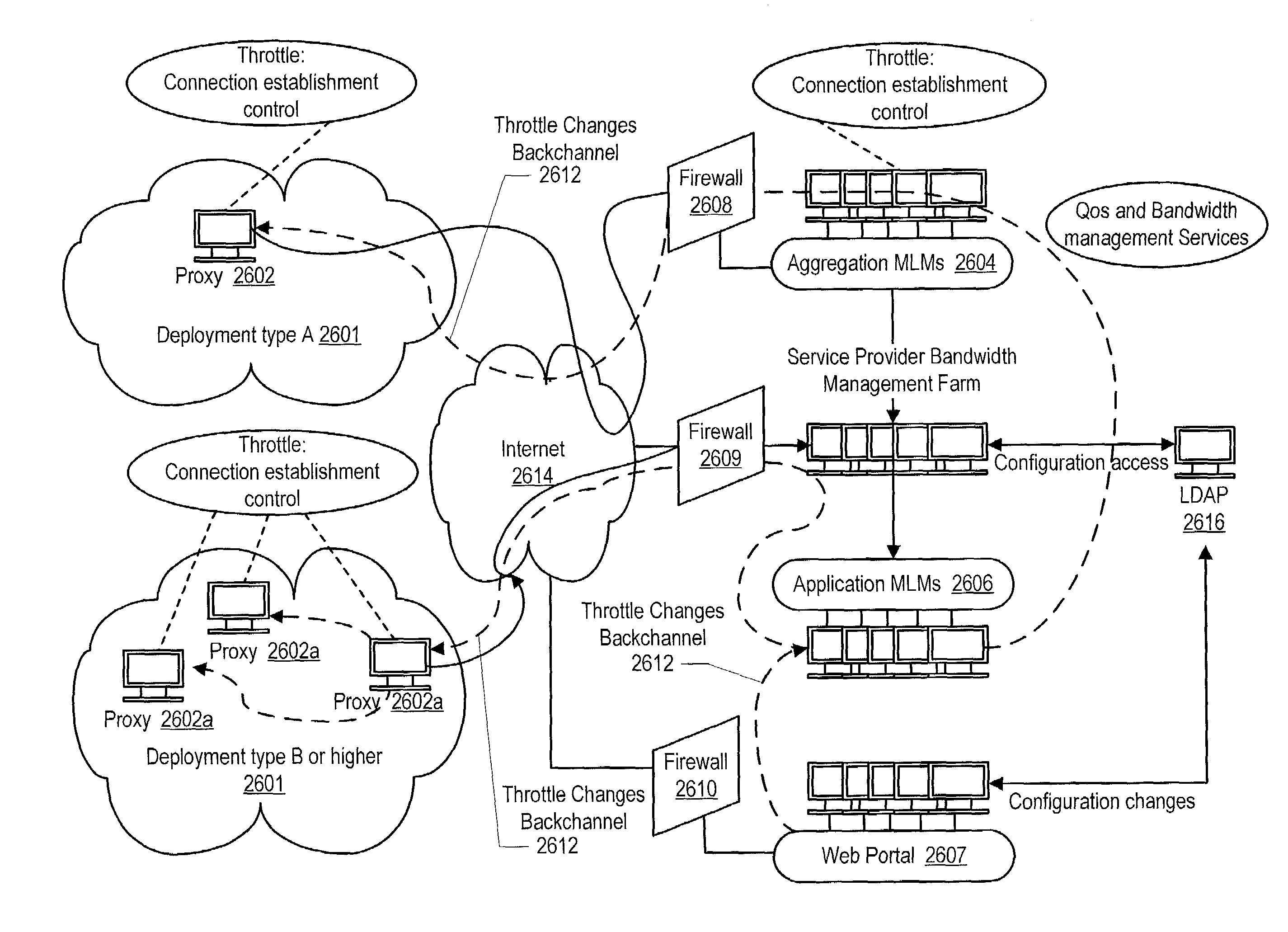
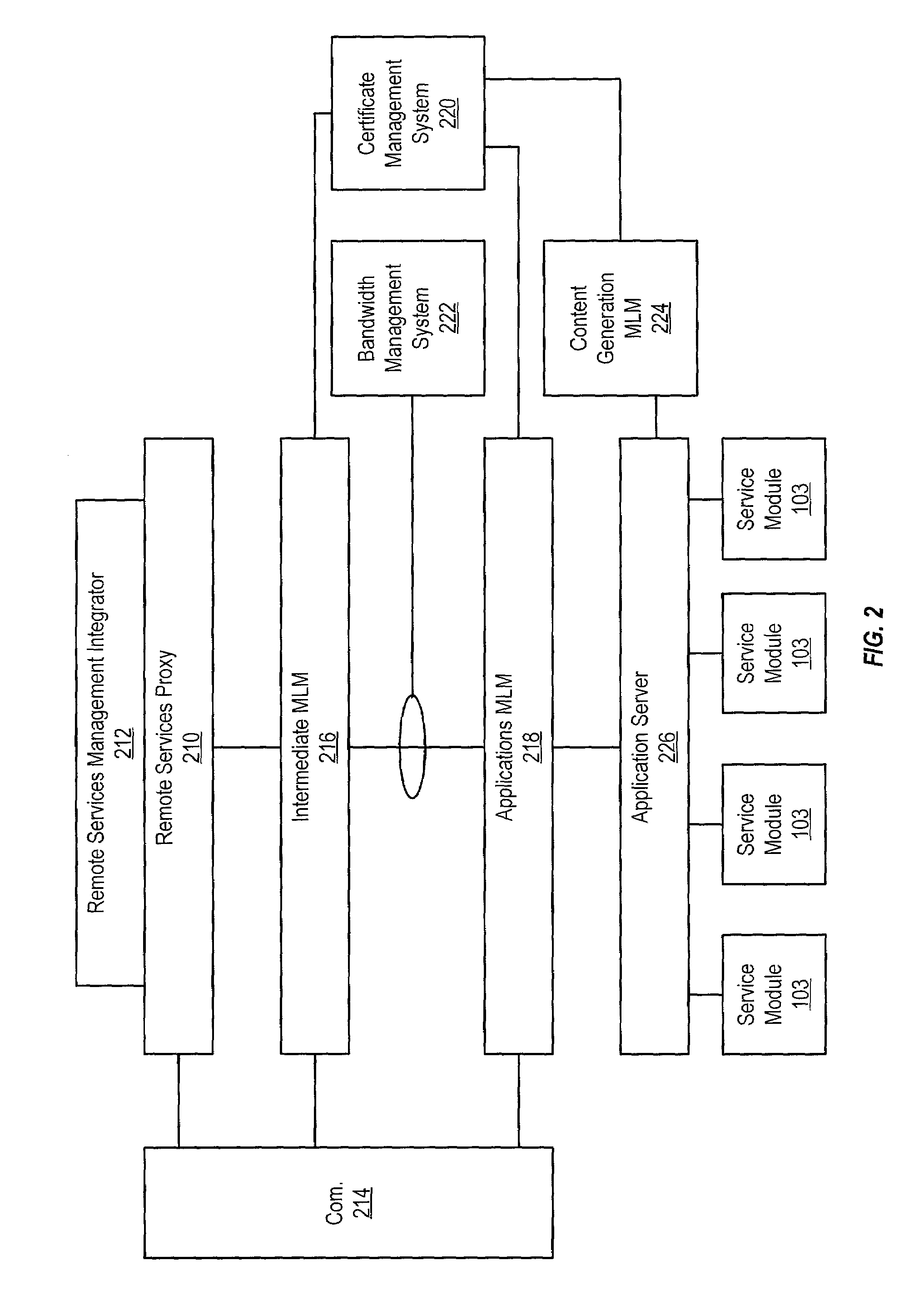
Bandwidth management for remote services system
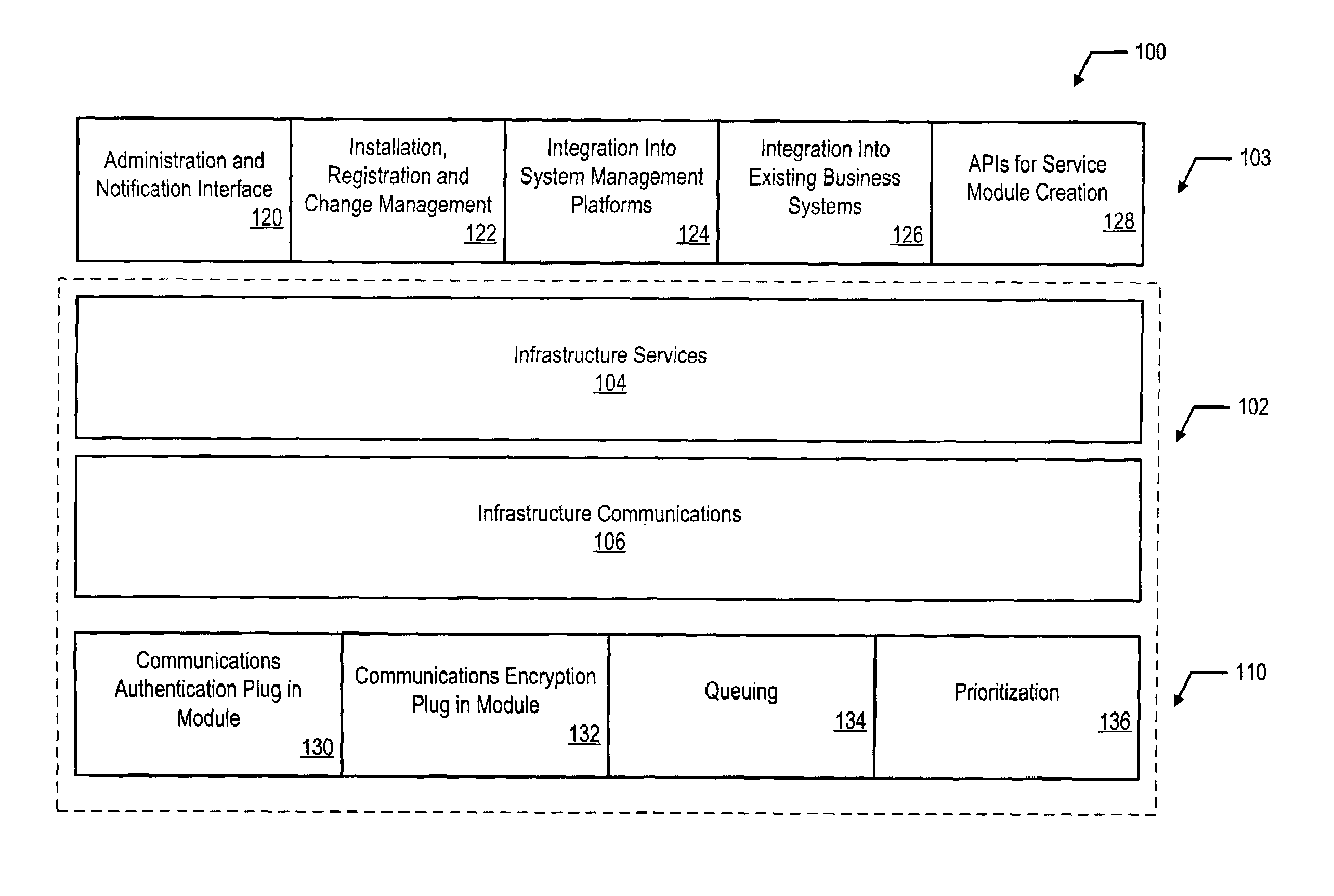
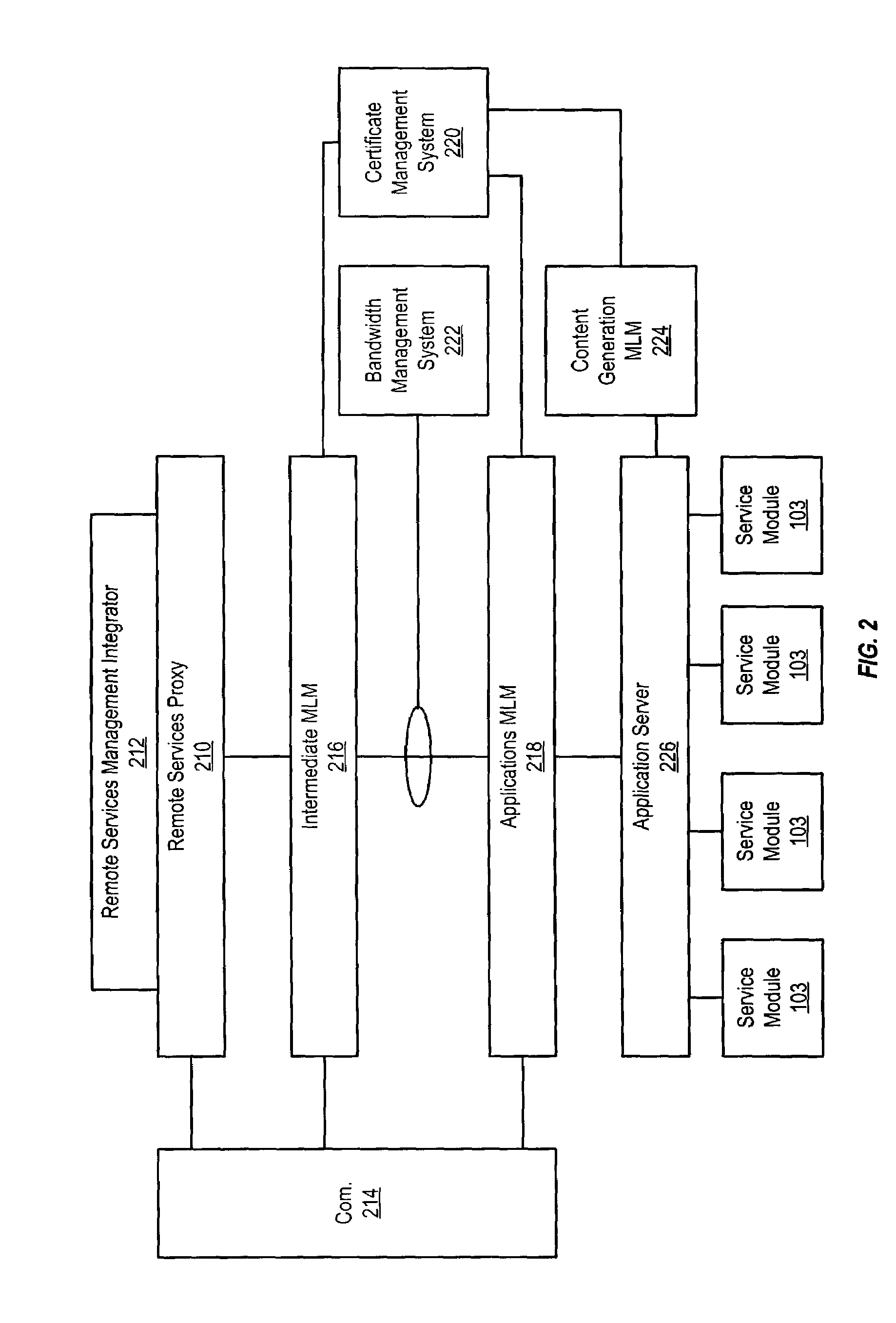
ActiveUS7181455B2High bandwidthMaintain qualityError preventionTransmission systemsBandwidth managementDistributed computing
The system for managing bandwidth in a remote services system provides an infrastructure that enables a customer to control bandwidth utilization in accordance with specified network performance criteria. The architecture is broadly comprised of a bandwidth management system that operates in conjunction with aggregation Mid-level Manager and application Mid-level Managers controlled by the service provider. The customer deployment can be implemented using a single proxy or a plurality of proxies. Customer access to system resources is controlled by a service provider web-access portal controlled by the service provider.
Owner:ORACLE INT CORP
Bluetooth sniff mode power saving
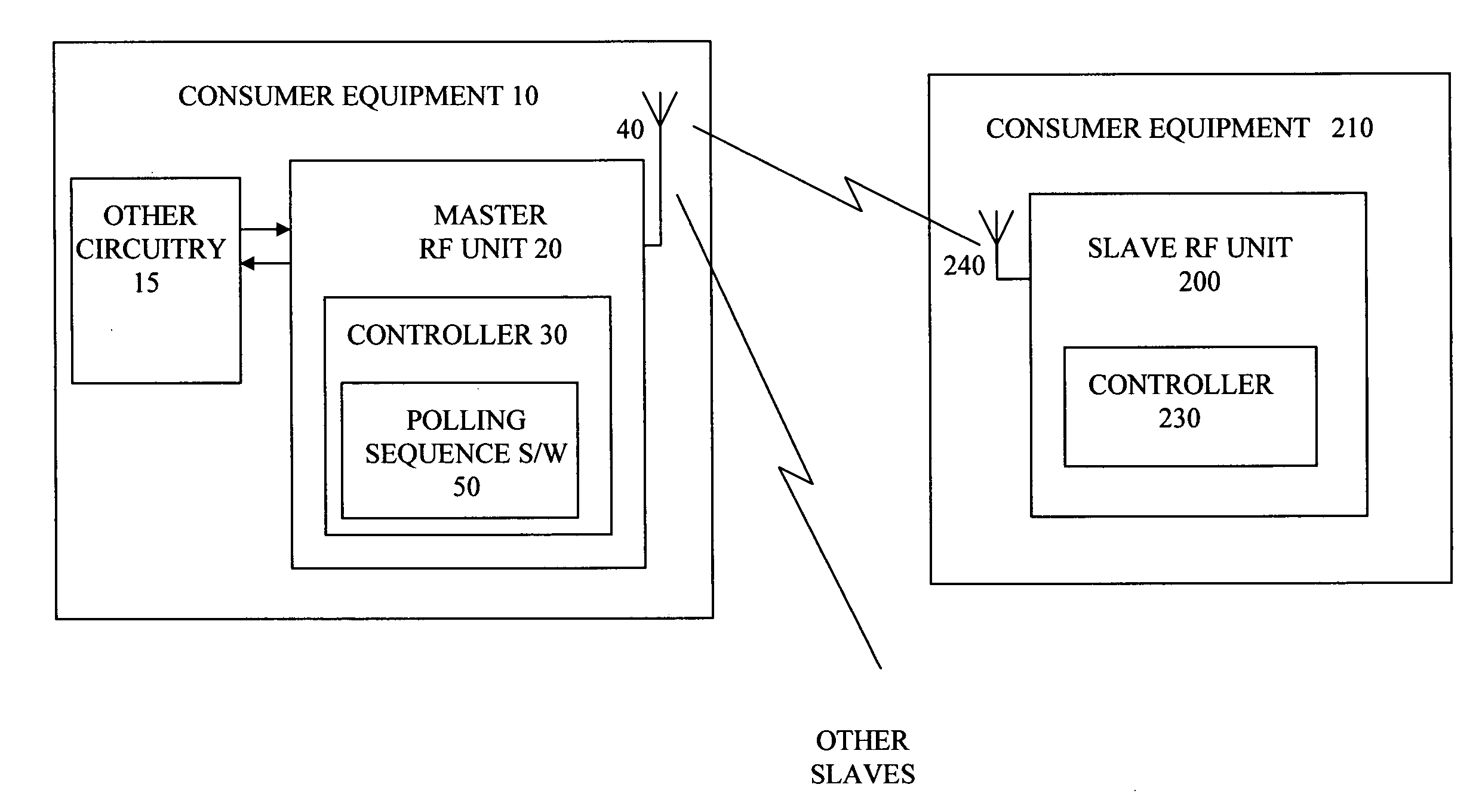
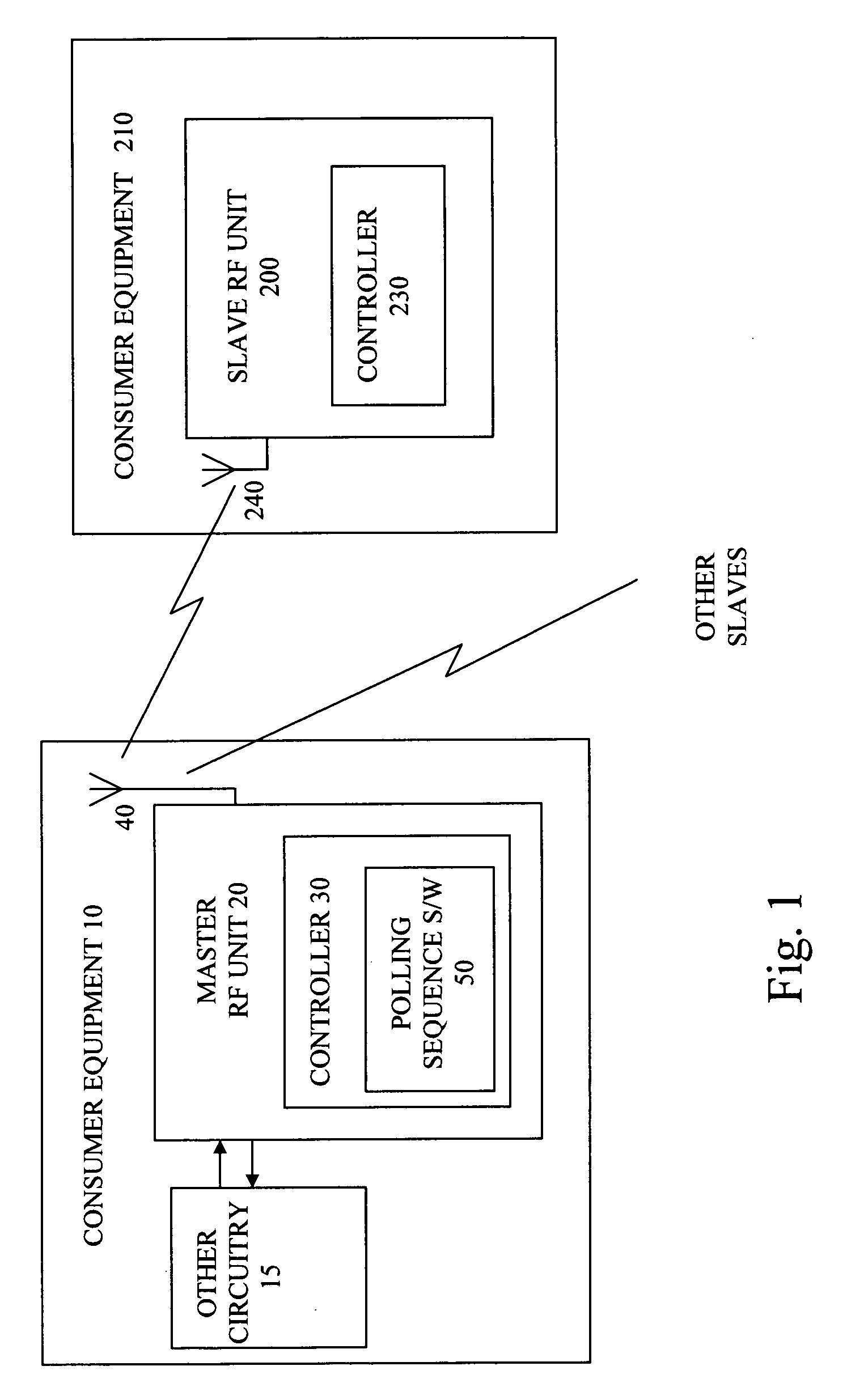
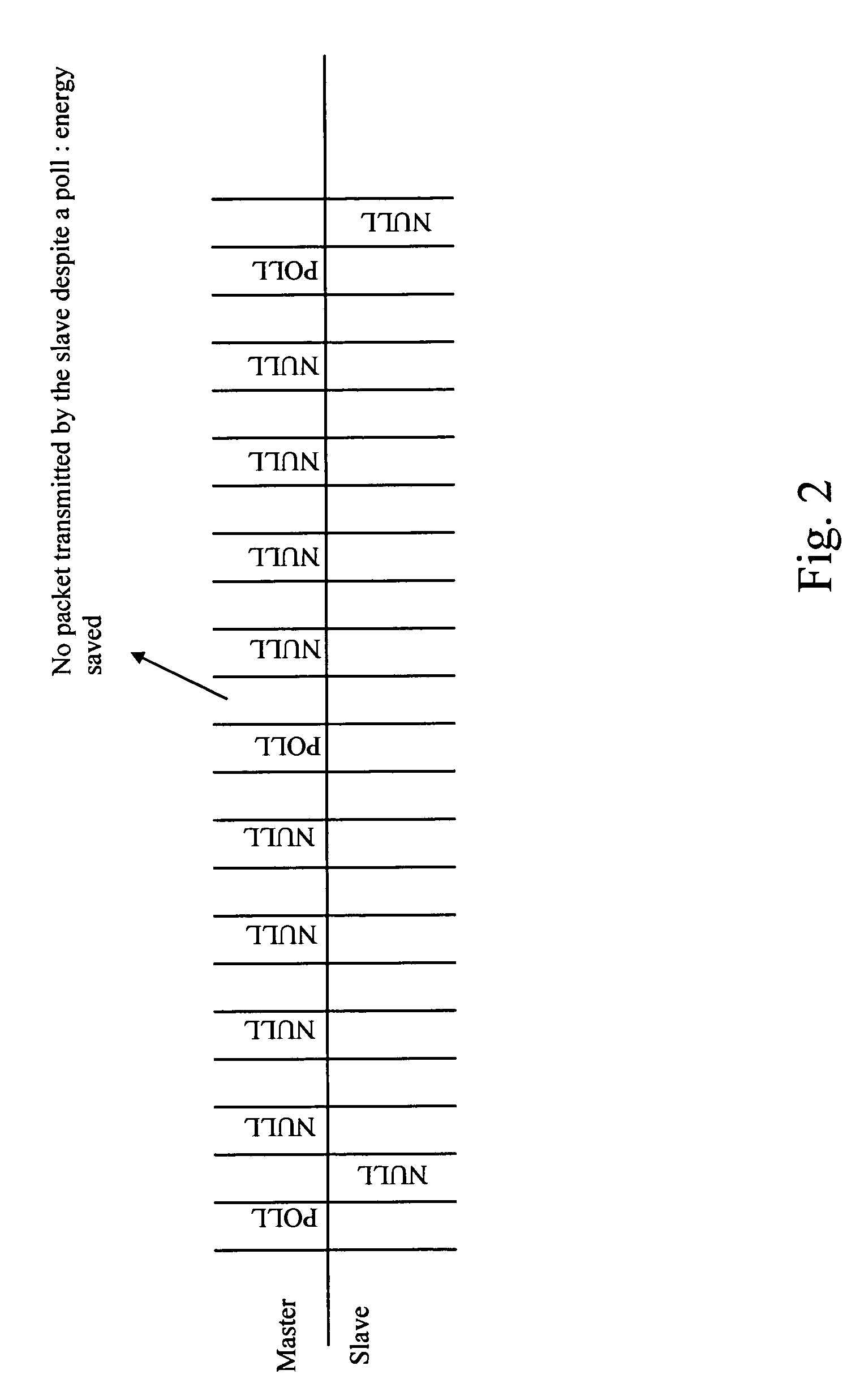
ActiveUS20050169201A1Save powerConvenient and accuratePower managementSynchronisation arrangementPrimary stationBluetooth
A Bluetooth master radio frequency unit addresses a slave radio frequency unit, to enable the slave to synchronize to the master, by sending poll packets and optionally null packets over an active link, the master being arranged so that receipt of a response from the slave unit to a poll packet is sufficient to maintain the active link. The slave unit does not have to respond to all of the poll packets. This approach can allow the slave to preserve more (transmit) power by going into a deep sleep mode in which a low power oscillator may be used while still allowing the master unit to detect whether the slave has resynchronized or not (and thus to update a Link Supervision Timer, for example).
Owner:SNAPTRACK
Prioritization of remote services messages within a low bandwidth environment
ActiveUS7167448B2High bandwidthMaintain qualityError preventionFrequency-division multiplex detailsData streamData file
The system for prioritizing data flow in a low bandwidth environment provides an infrastructure for ensuring that urgent data, such as messages, can be rapidly communicated to system components while also ensuring that the system bandwidth is optimized to accommodate the transfer of larger, less urgent data files. The architecture is broadly comprised of a bandwidth management system that operates in conjunction with aggregation Mid-level Manager and application Mid-level Managers controlled by the service provider. The customer deployment can be implemented using a single proxy or a plurality of proxies. Customer access to system resources is controlled by a service provider web-access portal controlled by the service provider.
Owner:ORACLE INT CORP
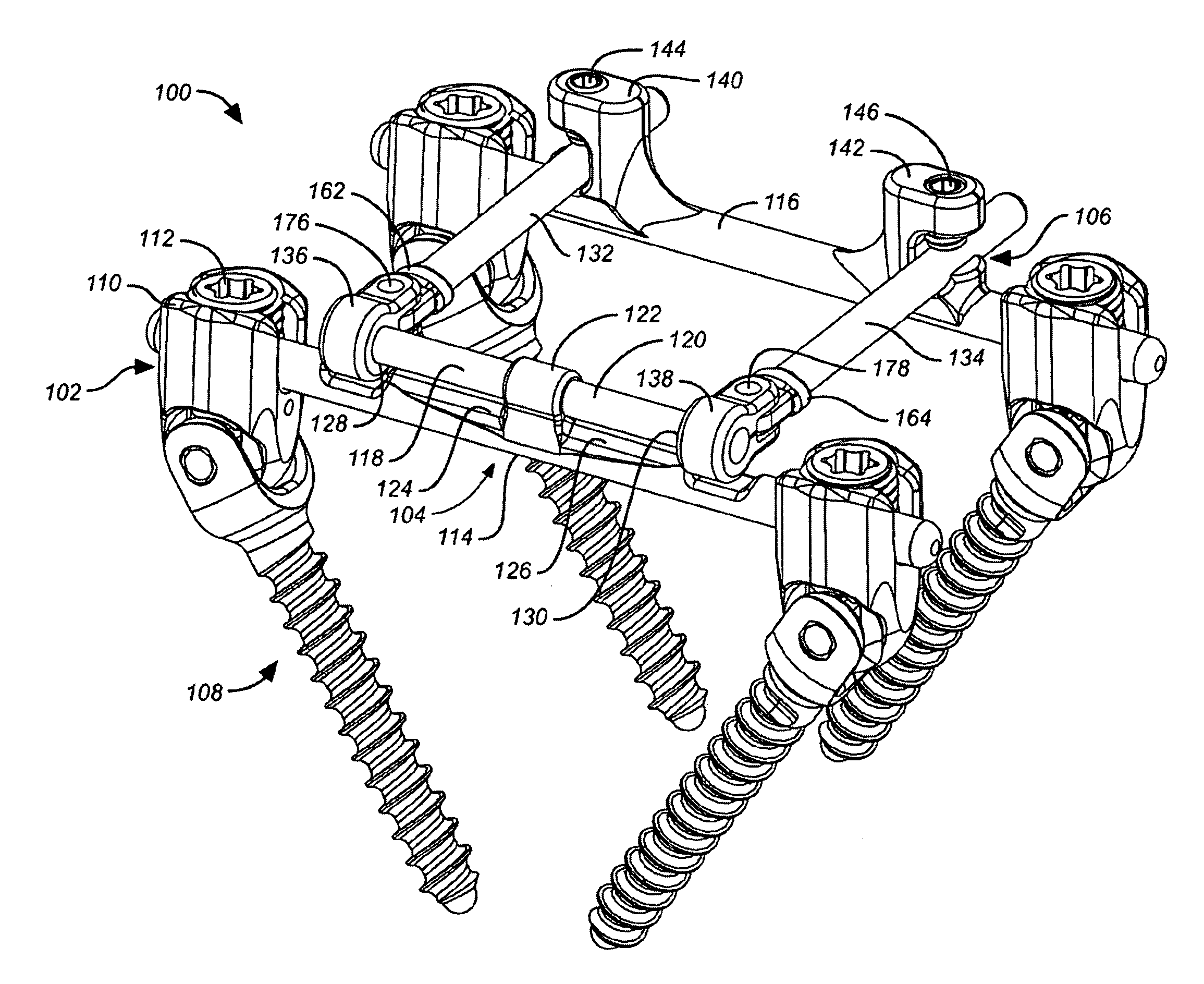
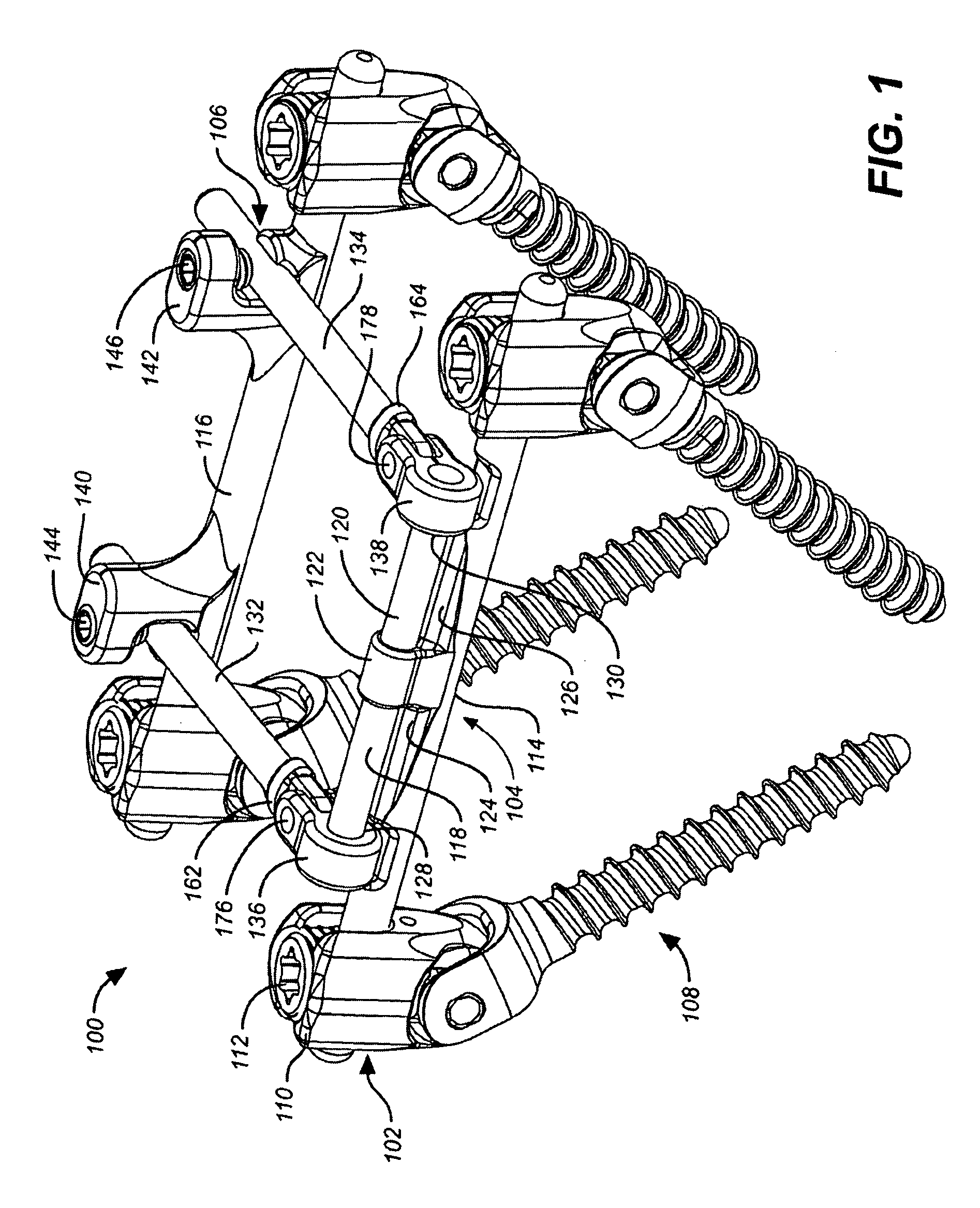
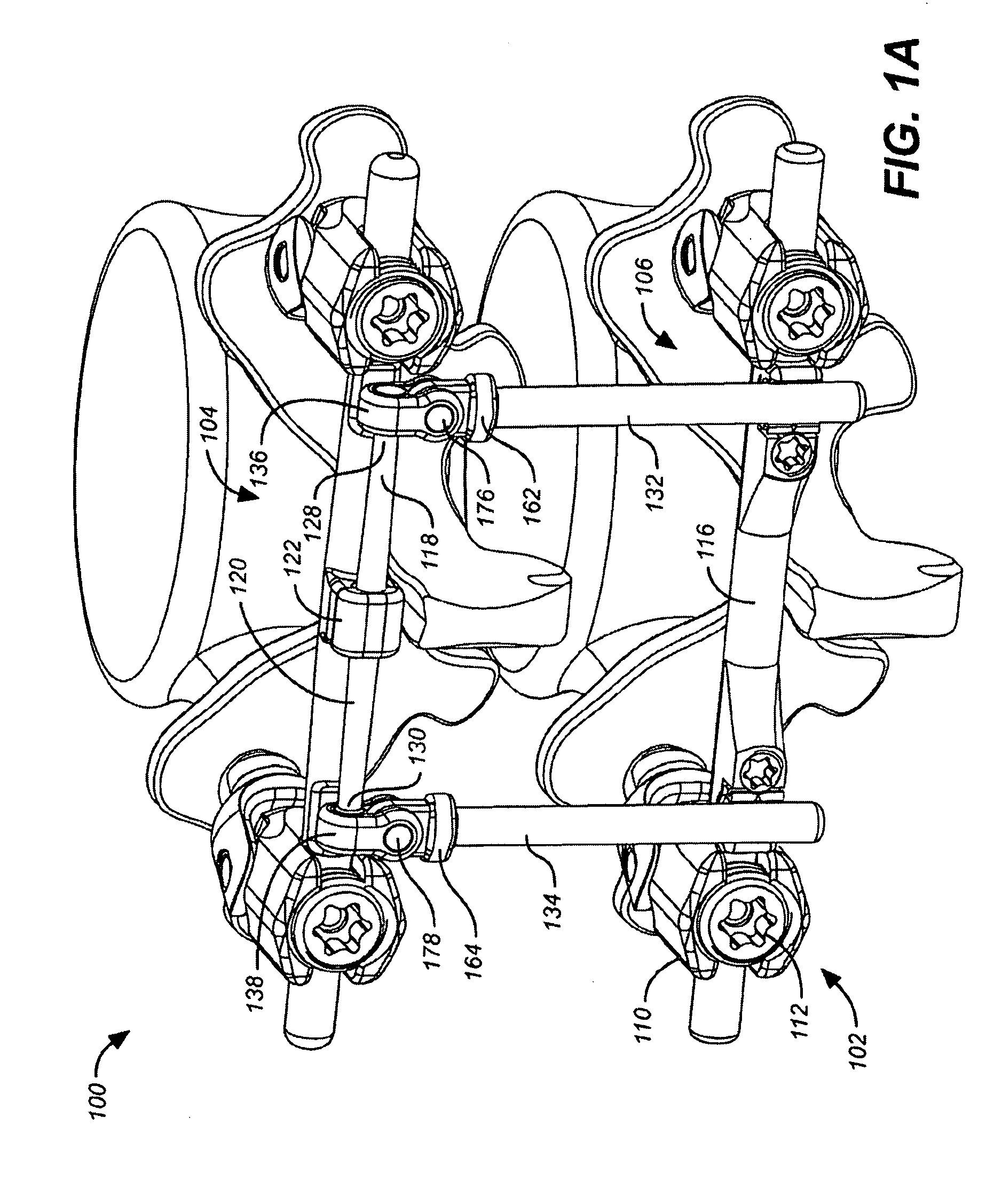
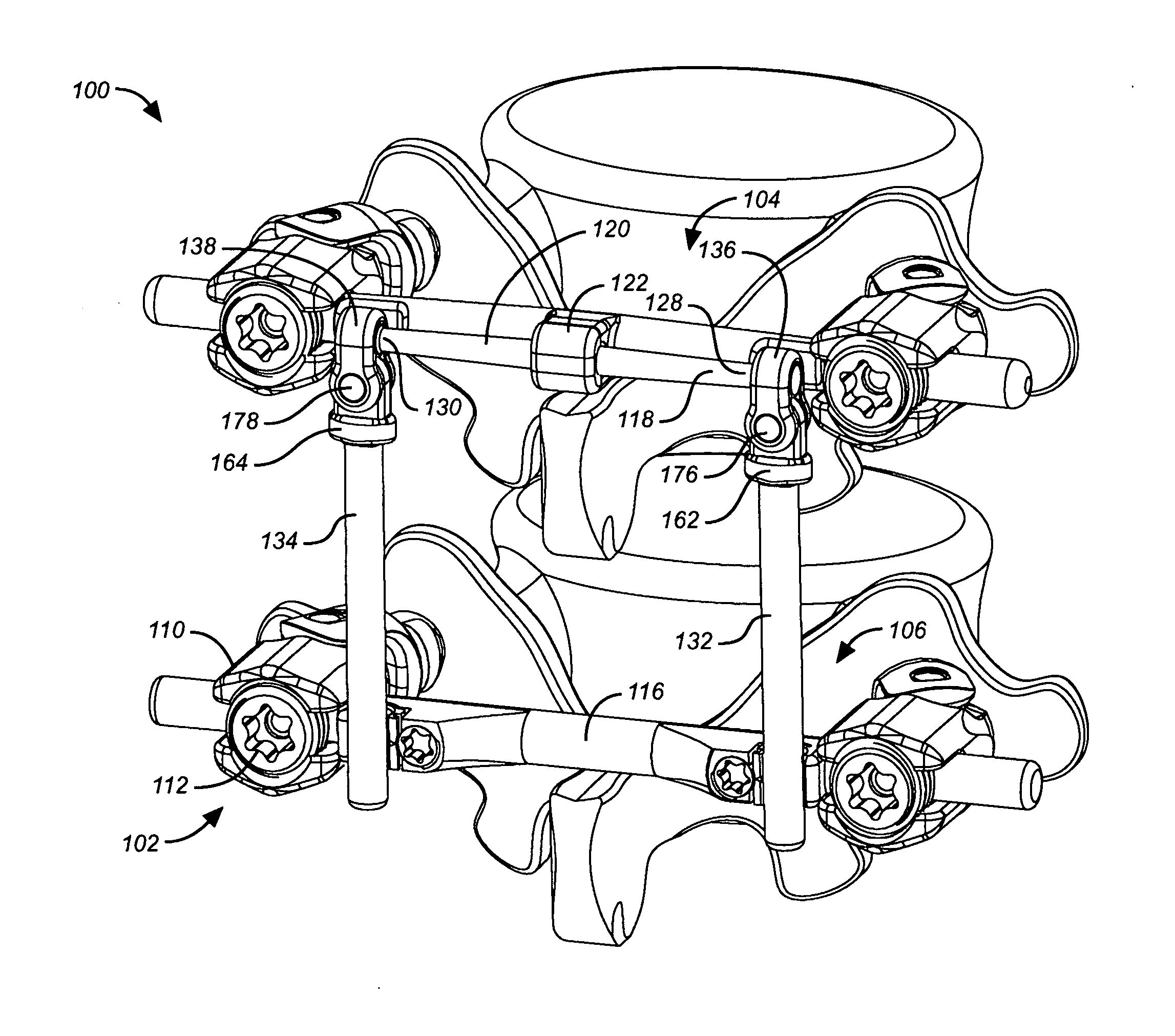
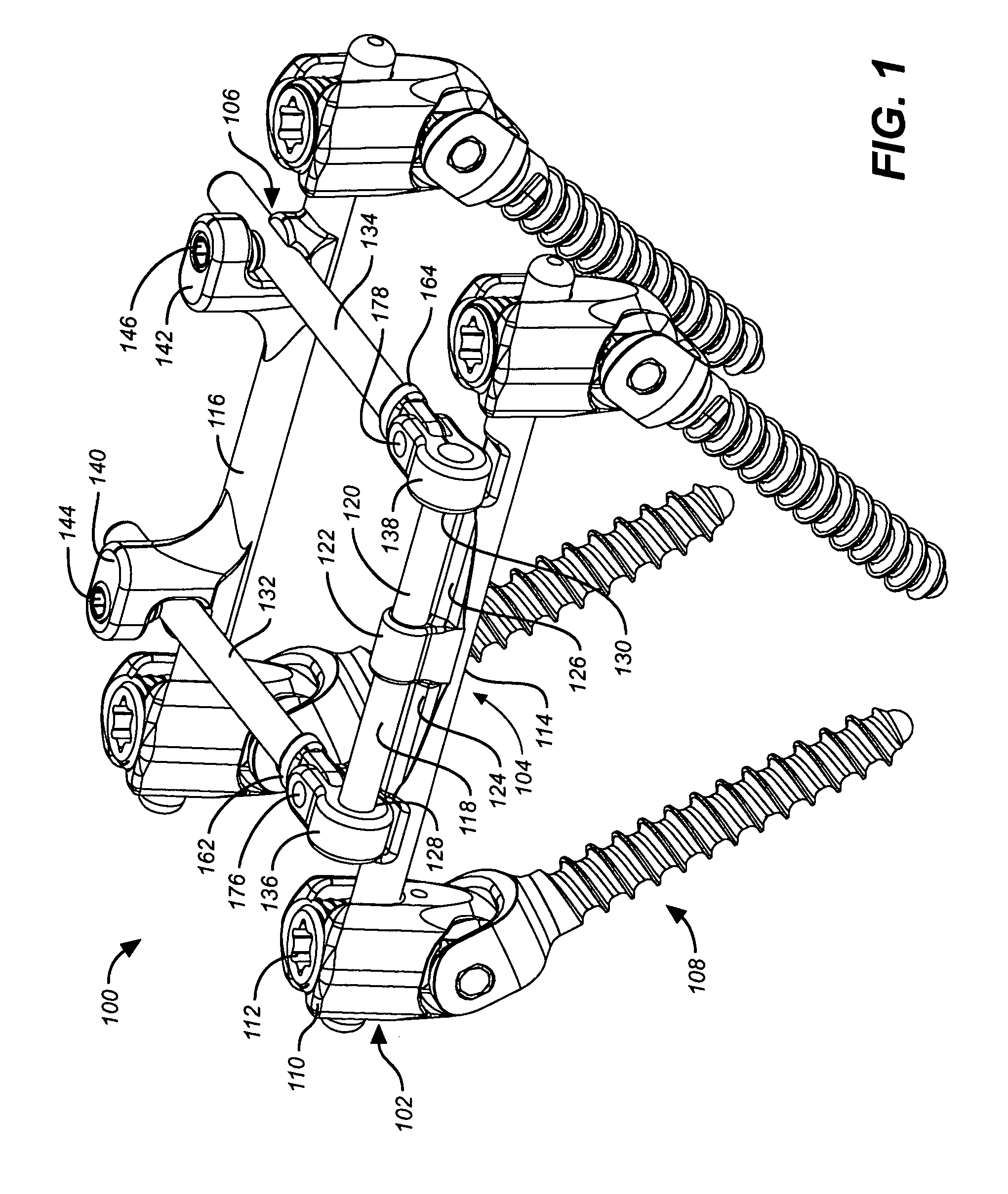
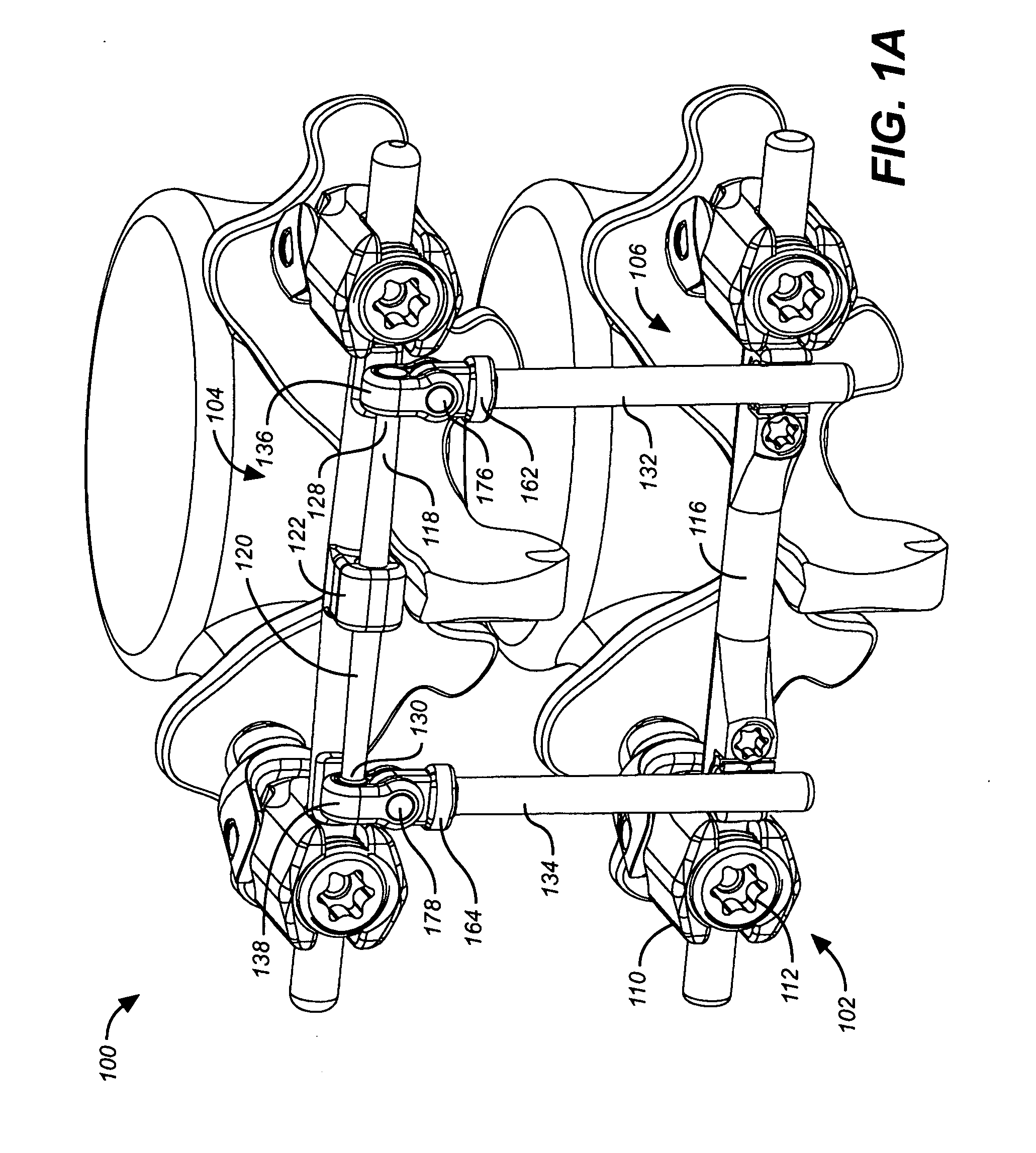
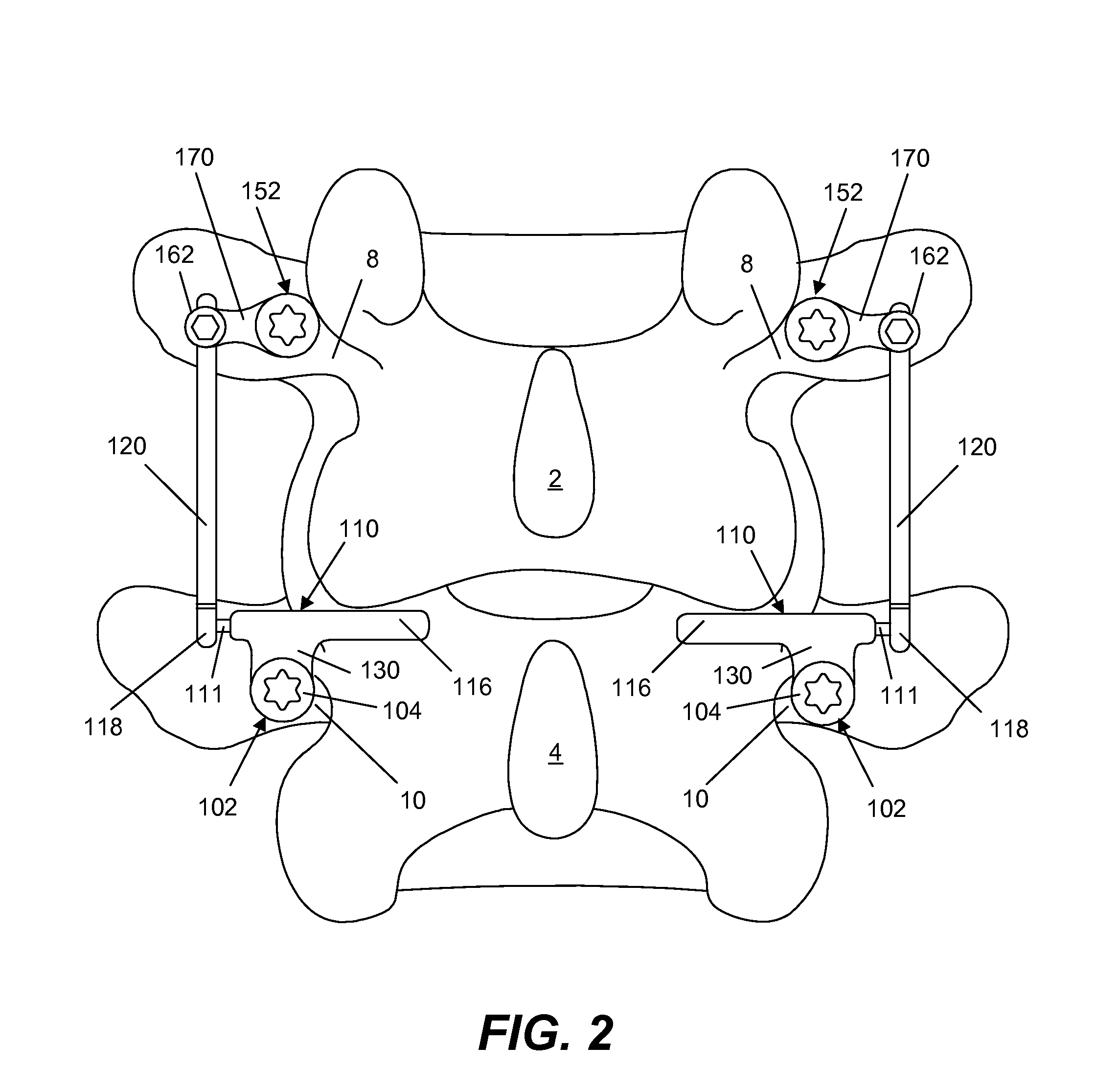
Deflection rod system for use with a vertebral fusion implant for dynamic stabilization and motion preservation spinal implantation system and method
InactiveUS20080306533A1Maximize range of motionMaintain qualitySuture equipmentsInternal osteosythesisSpinal columnSpinal implant
A dynamic stabilization, motion preservation spinal implant system includes an anchor system, a horizontal rod system and a vertical rod system. The systems are modular so that various constructs and configurations can be created and customized to a patient.
Owner:SPARTEK MEDICAL
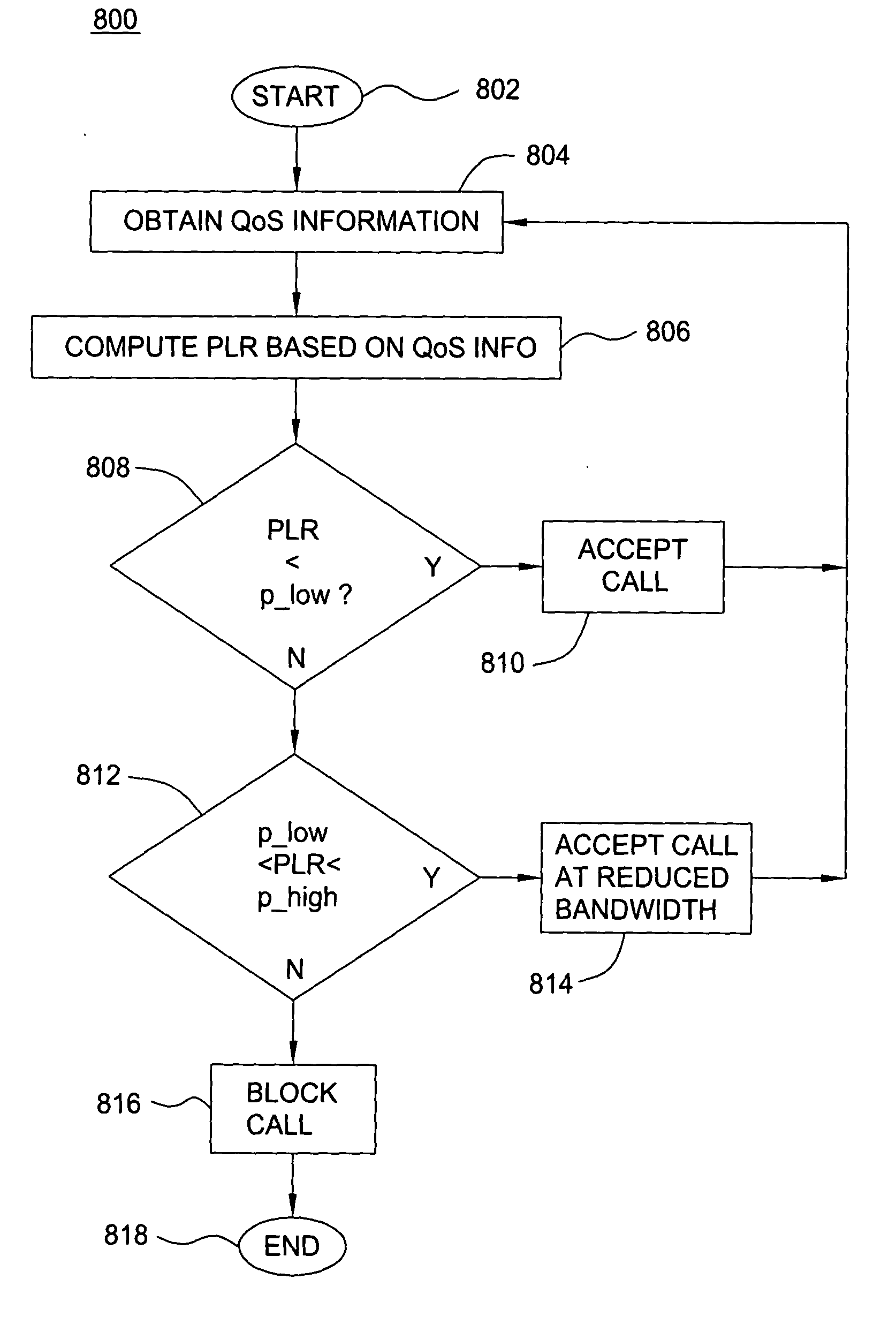
Arrangement in an IP node for preserving security-based sequences by ordering IP packets according to quality of service requirements prior to encryption
ActiveUS7389357B2Guaranteed service qualityMinimizes packet lossMultiple digital computer combinationsData switching networksQuality of serviceService level requirement
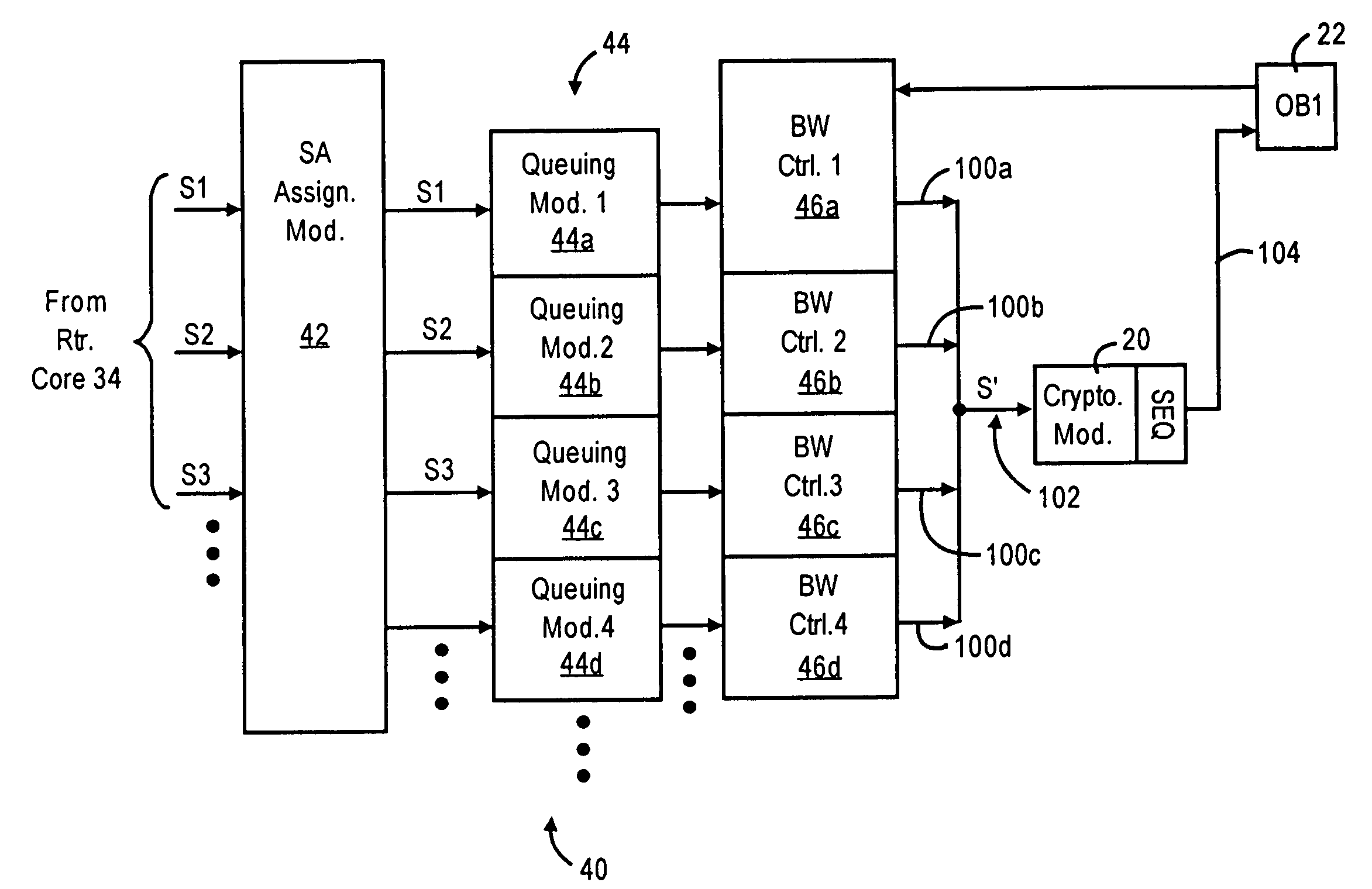
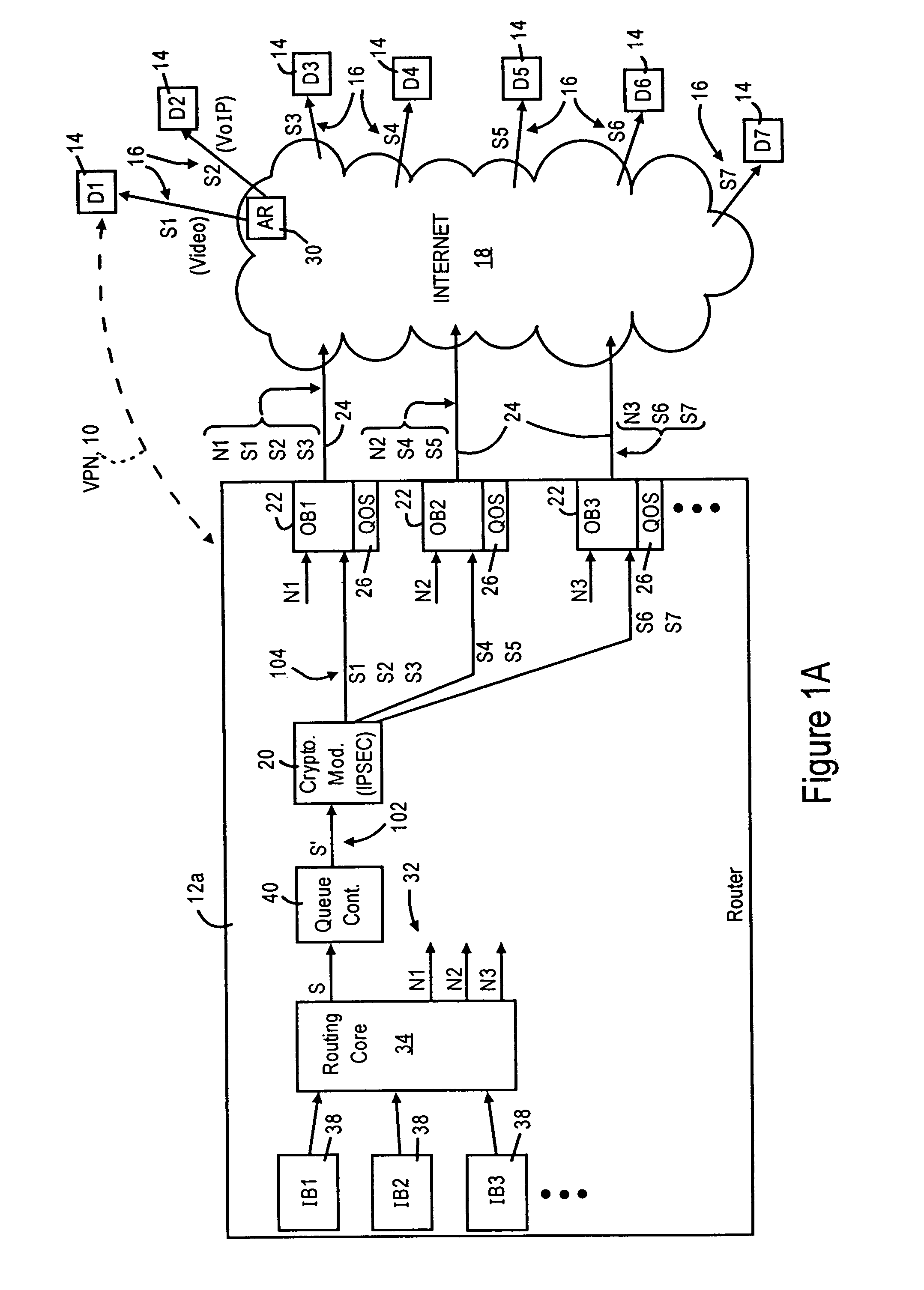
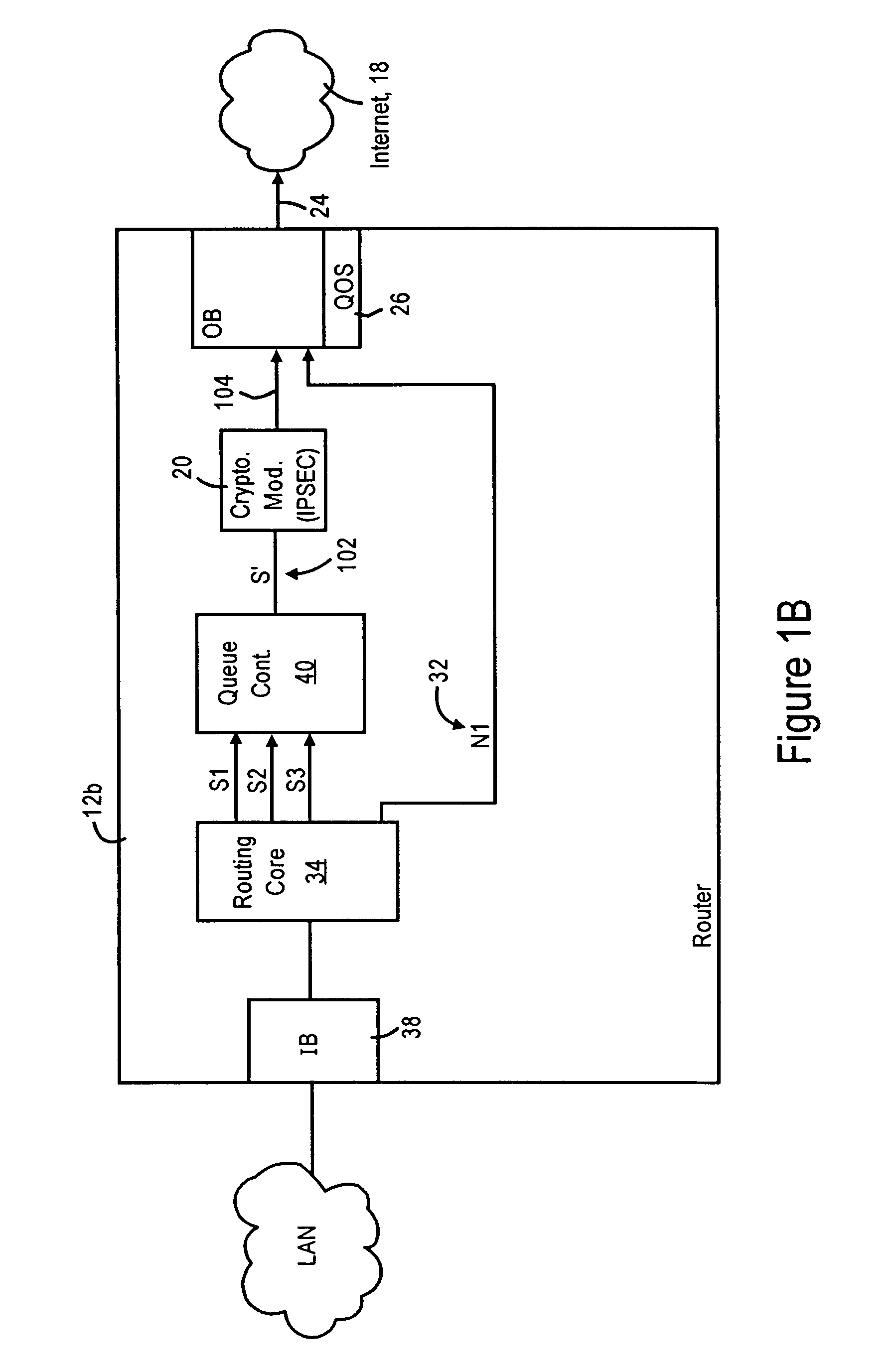
A router has at least one outbound interface configured for establishing multiple IP-based secure connections (i.e., tunnels) with respective destinations based on transmission of encrypted data packets via the IP-based secure connections. The encrypted data packets are generated by a cryptographic module, where each encrypted packet successively output from the cryptographic module includes a corresponding successively-unique sequence number. The supply of data packets to the cryptographic module is controlled by a queue controller: the queue controller assigns, for each secure connection, a corresponding queuing module configured for outputting a group of data packets associated with the corresponding secure connection according to a corresponding assigned maximum output bandwidth. Each queuing module also is configured for reordering the corresponding group of data packets according to a determined quality of service policy and the corresponding assigned maximum output bandwidth.
Owner:CISCO TECH INC
Deflection rod system for spine implant with end connectors and method
InactiveUS20080306528A1Maximize range of motionMaintain qualityInternal osteosythesisJoint implantsSpinal columnModularity
A dynamic stabilization, motion preservation spinal implant system includes an anchor system, a horizontal rod system and a vertical rod system. The systems are modular so that various constructs and configurations can be created and customized to a patient.
Owner:SPARTEK MEDICAL
Method and apparatus for management of voice-over IP communications
InactiveUS20050052996A1Attenuation bandwidthMaintain qualityError preventionFrequency-division multiplex detailsComputer networkVoice over IP
Owner:LUCENT TECH INC
Stabilization of cells and biological specimens for analysis
InactiveUS20050181353A1Improve stabilityMaintain qualityOrganic active ingredientsBiocideAbnormal tissue growthIn vivo
Compositions and methods for stabilizing rare cells in blood specimens, preserving the quality of blood specimens, and also serving as cell fixatives are disclosed which minimize losses of target cells (for example, circulating tumor cells) and formation of debris and aggregates from target cells, non-target cells and plasma components, thereby allowing more accurate analysis and classification of circulating tumor cells (CTC) and, ultimately, of tumor burdens in cancer patients. Stabilization of specimens is particularly desirable in protocols requiring rare cell enrichment from blood specimens drawn from cancer patients. Exposure of such specimens to potentially stressful conditions encountered, for example, in normal processing, mixing, shaking, delays due to transporting the blood, has been observed to not only diminish the number of CTC but also to generate debris and aggregates in the blood specimens that were found to interfere with accurate enumeration of target cells, if present. Stabilizers are necessary to discriminate between in vivo CTC disintegration and in vitro sample degredation.
Owner:VERIDEX LCC
Spine implant with a defelction rod system anchored to a bone anchor and method
InactiveUS20080306540A1Maximize range of motionMaintain qualitySuture equipmentsInternal osteosythesisModularitySpinal implant
A dynamic stabilization, motion preservation spinal implant system includes a deflection rod system implant. The system is modular so that various constructs and configurations can be created and customized to a patient.
Owner:SPARTEK MEDICAL
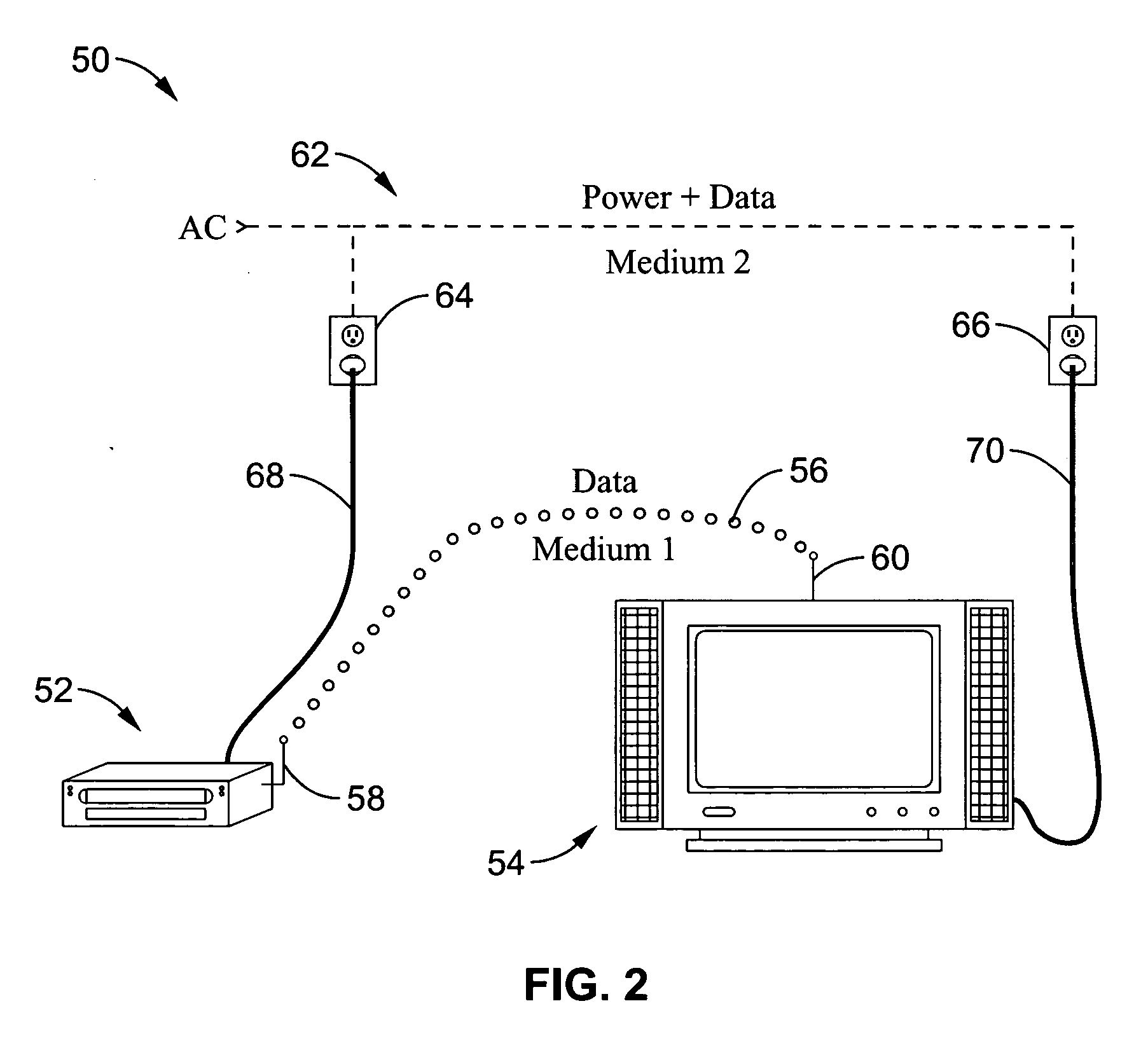
Reliable audio-video transmission system using multi-media diversity
InactiveUS20060062242A1Maintaining service qualityMaintain qualityNetwork traffic/resource managementTime-division multiplexQuality of servicePower line network
A system and method for switching data packet traffic distribution across diverse transmission medium according to detected quality of service characteristics for a given data packet rate from server to client. It should be recognized that diverse medium are not interdependent with regard to fading or signal strength considerations. One mode of switching comprises switching all the data packets from transmission on a first medium to transmission over a second diverse medium. In a second mode of switching the distribution is changed according to a media-time coding mechanism in which typically data is being transmitted simultaneously across more than one of the multiple diverse medium. The data packet transmissions preferably comprise audio-video data packet streams, such as MPEG-2 streams. By way of example, the diverse transmission medium may comprise a wireless connection (i.e. WiFi) used in combination with a power-line network connection, such as within a home network.
Owner:SONY CORP +1
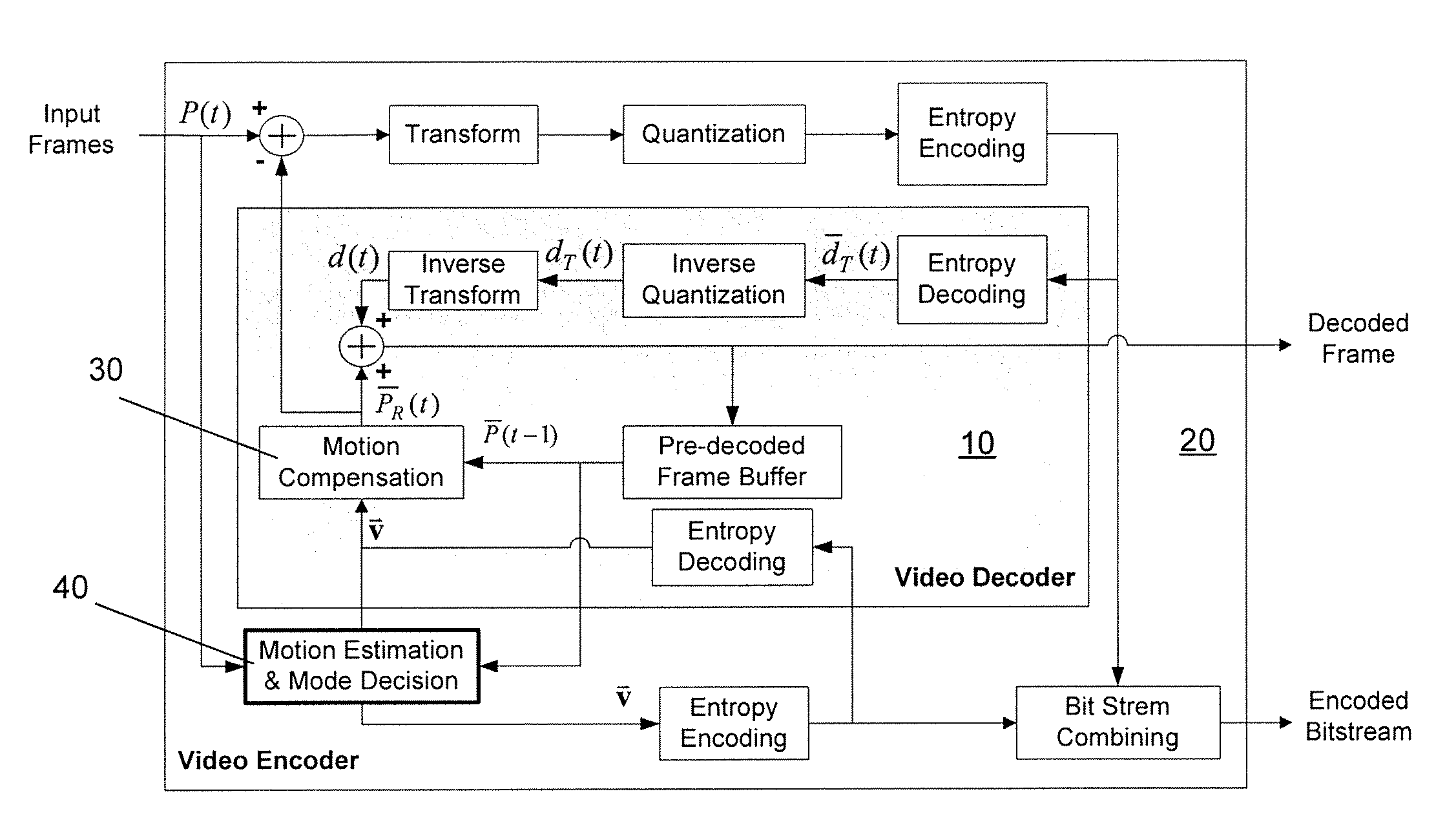
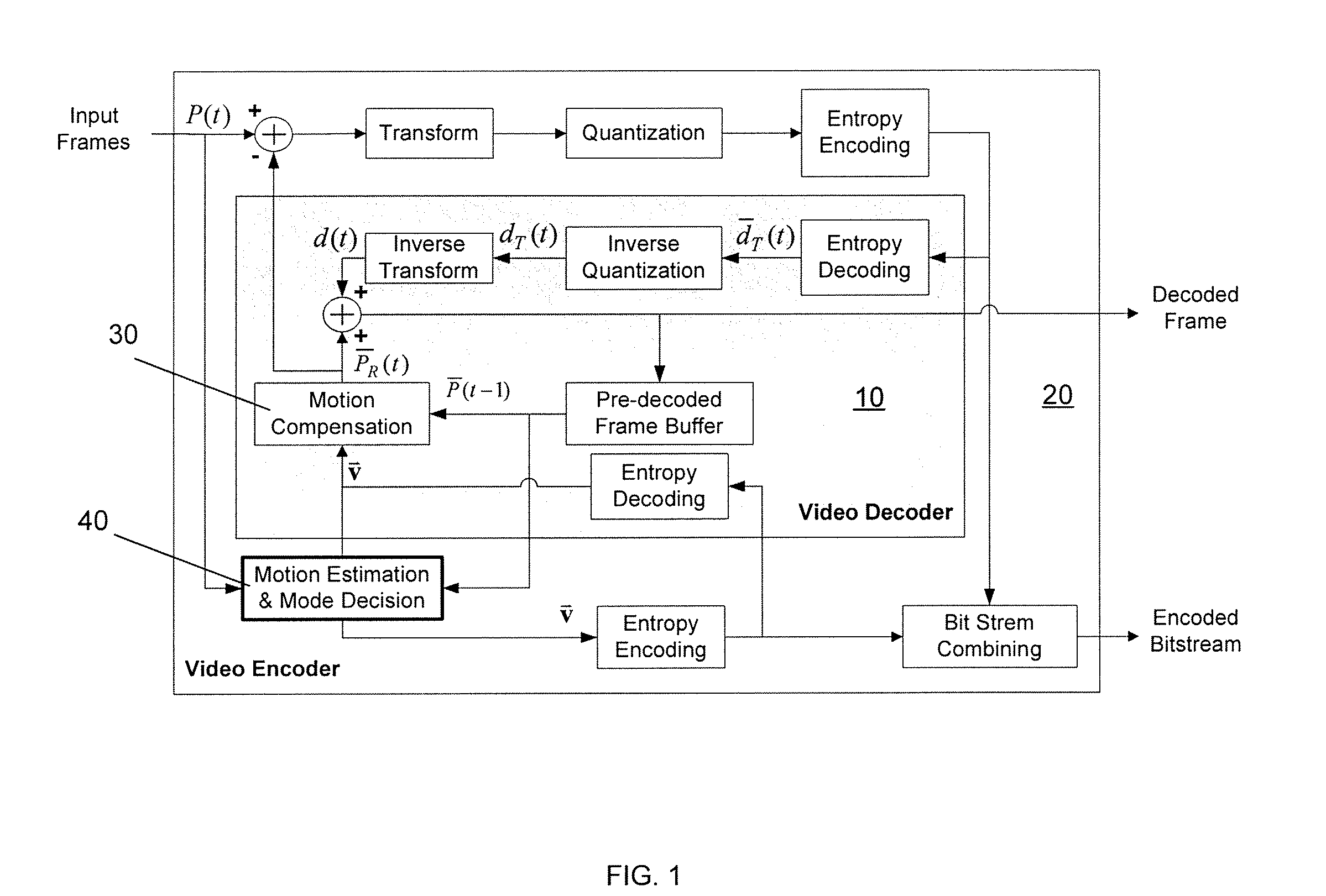
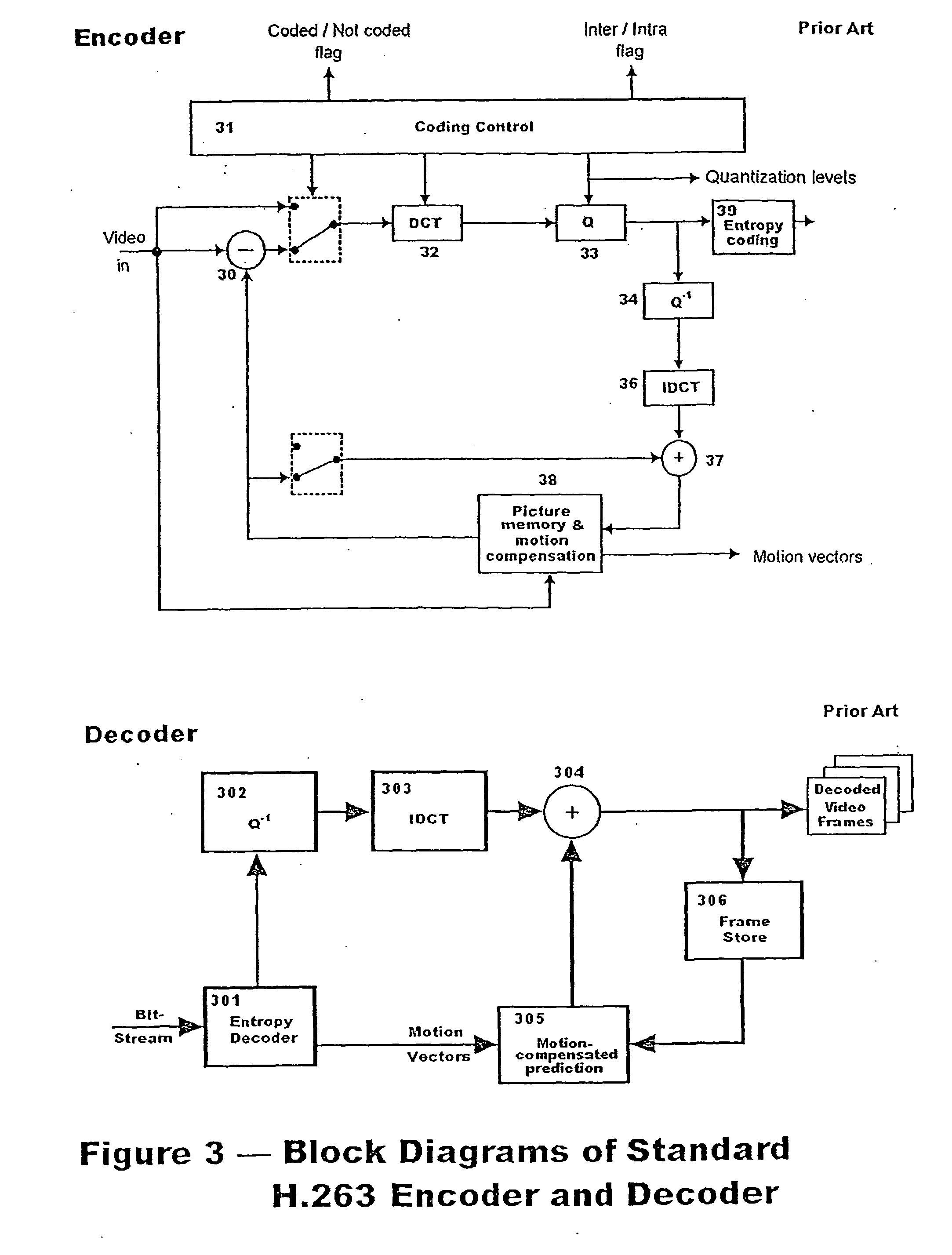
System and method for motion estimation and mode decision for low-complexity h.264 decoder
InactiveUS20080181308A1Reduce computing costMaintaining video qualityColor television with pulse code modulationColor television with bandwidth reductionRound complexityVideo encoding
The present invention relates to systems and methods for motion estimation and mode decision for low-complexity H.264 standard decoders. The present invention includes a method for optimizing the selection of motion vectors and motion compensation block modules in a video encoder in order to decrease the complexity of the video upon decoding. The novel method of the present invention may include novel steps for selecting motion vectors, block modes, and for applying a complexity-control algorithm to encode the received input video data sequence in accordance with the identified target complexity level. The present invention may be implemented in accordance with current and future video decoding standards to optimize decoding by reducing decoding complexity and thereby reducing required resources and power consumption.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
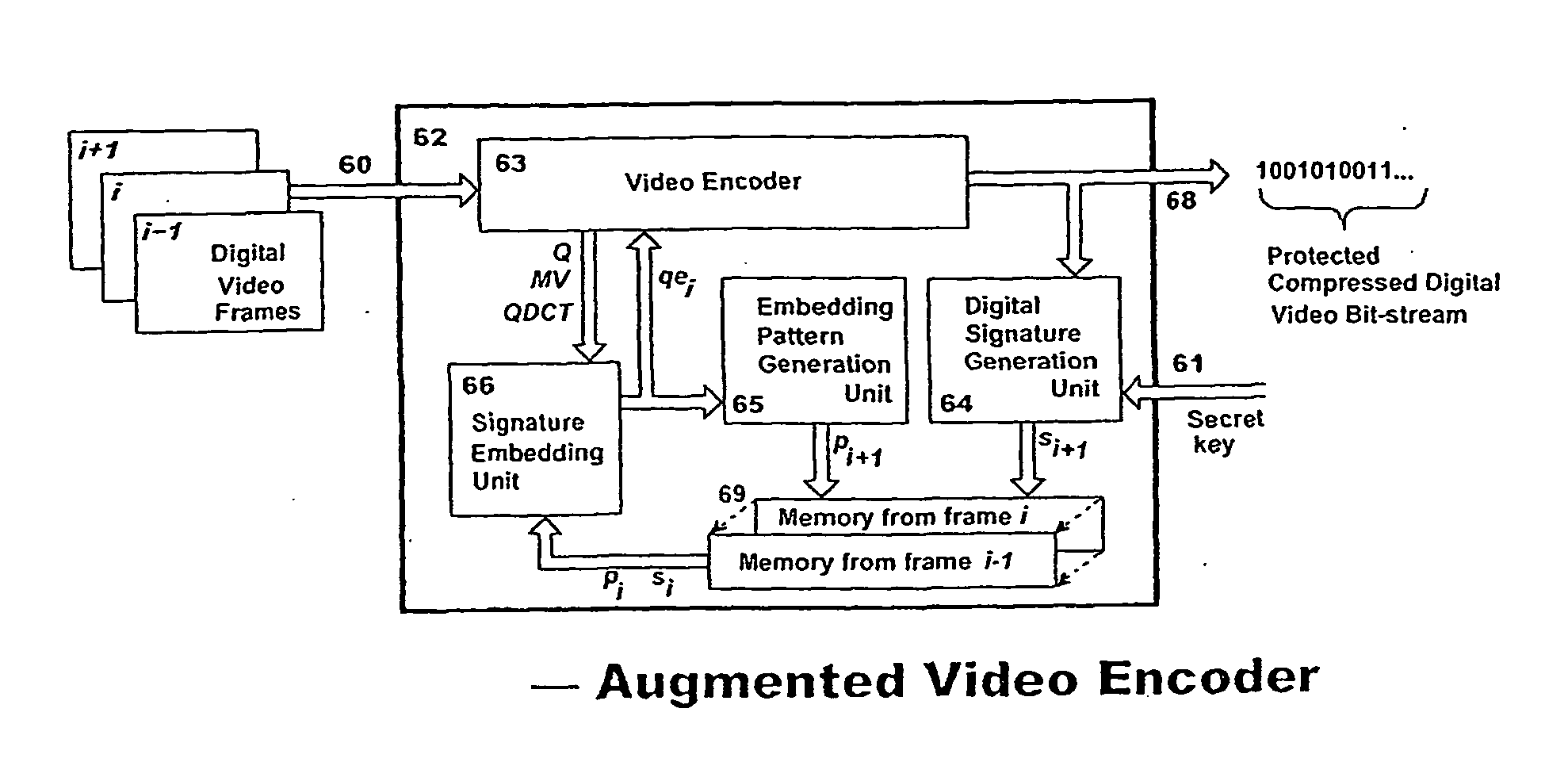
Digital video protection for authenticity verification
ActiveUS20100177891A1Reduce calculationShorten the timeTelevision system detailsPicture reproducers using cathode ray tubesDigital videoDigital signature
A method and apparatus for verifying the authenticity and integrity of an ordered sequence of digital video frames, without having access to the original recording, by embedding therein a respective series of digital signatures based on a secret key, or keys, and on the video content of respective frames. Signatures are camouflaged by embedding in transform coefficients of a transformed representation of the video data in parts of the frame corresponding to motion. If there is sufficient motion to contain all of the signature bits, a supplementary technique embeds in high-texture areas of a frame. A final fall-back is to embed in a pre-defined default zone. A method of predicting when supplementary embedding is needed enables the process to be applied in a single pass allowing real-time operation. Verification is done during decoding by comparing, for identity, embedded signatures with signatures calculated anew using the method employed to embed.
Owner:QOGNIFY
Wet crepe throughdry process for making absorbent sheet and novel fibrous products
InactiveUS20020148584A1Big cost advantageReduce air permeabilityNon-fibrous pulp additionNatural cellulose pulp/paperFiberEngineering
An improved process for making sheet from a fibrous furnish includes: depositing the furnish on a foraminous support; compactively dewatering the furnish to form a nascent web; drying the web on a heated cylinder; creping the web therefrom and throughdrying the web to a finished product. The microstructure of the web is controlled so as to facilitate throughdrying. The product exhibits a characteristic throughdrying coefficient of from 4 to 10 when the airflow through the sheet is characterized by a Reynolds Number of less than about 1. The novel products of the invention are characterized by wet springback ratio, hydraulic diameter and an internal bond strength parameter.
Owner:GPCP IP HLDG LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com