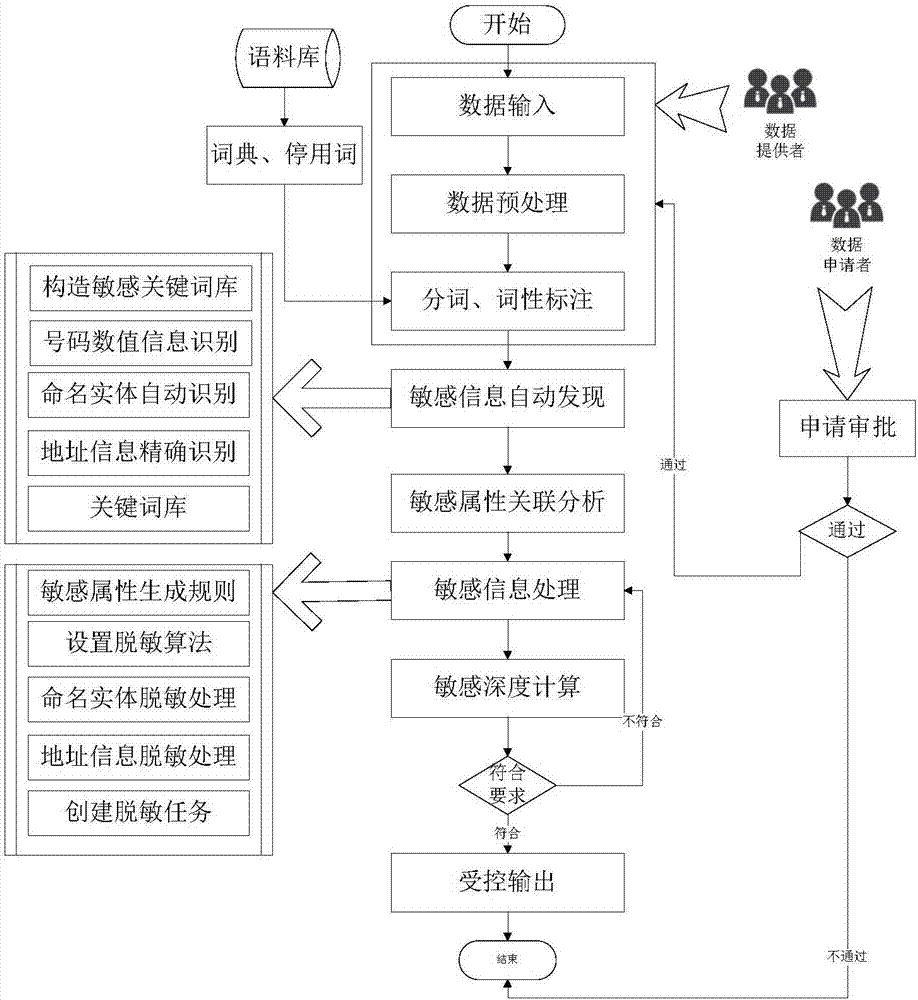
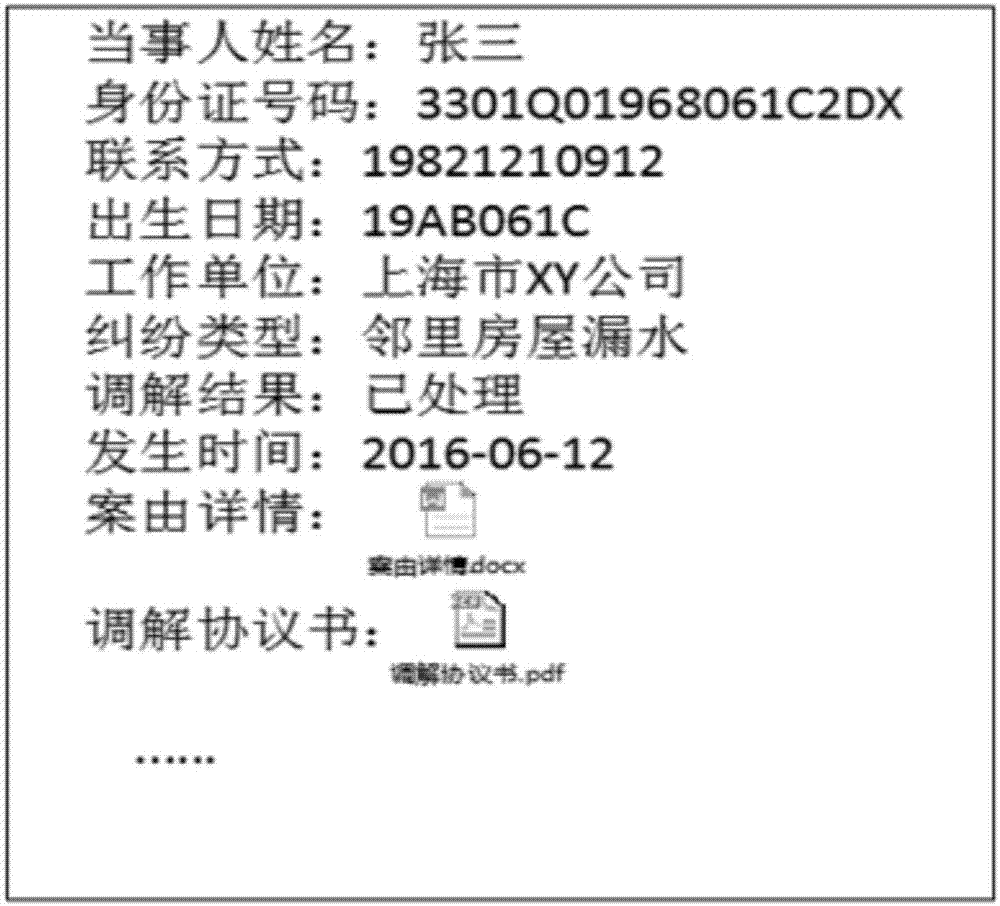
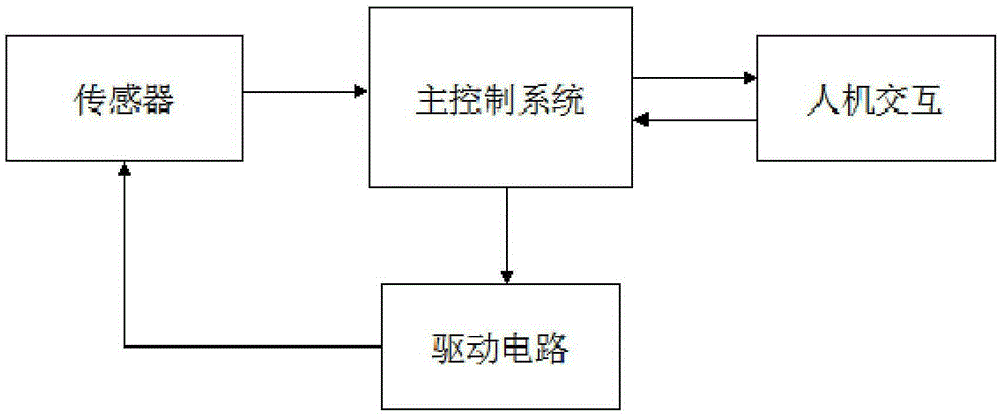
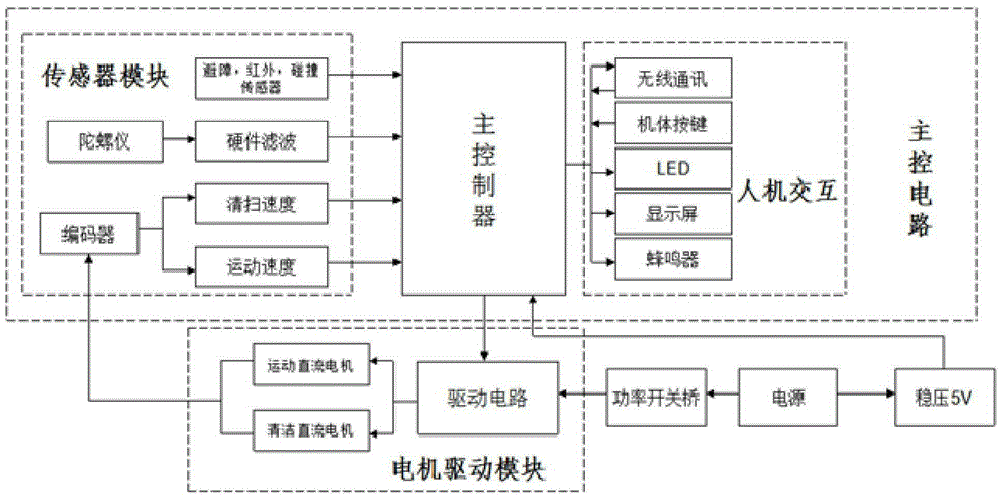
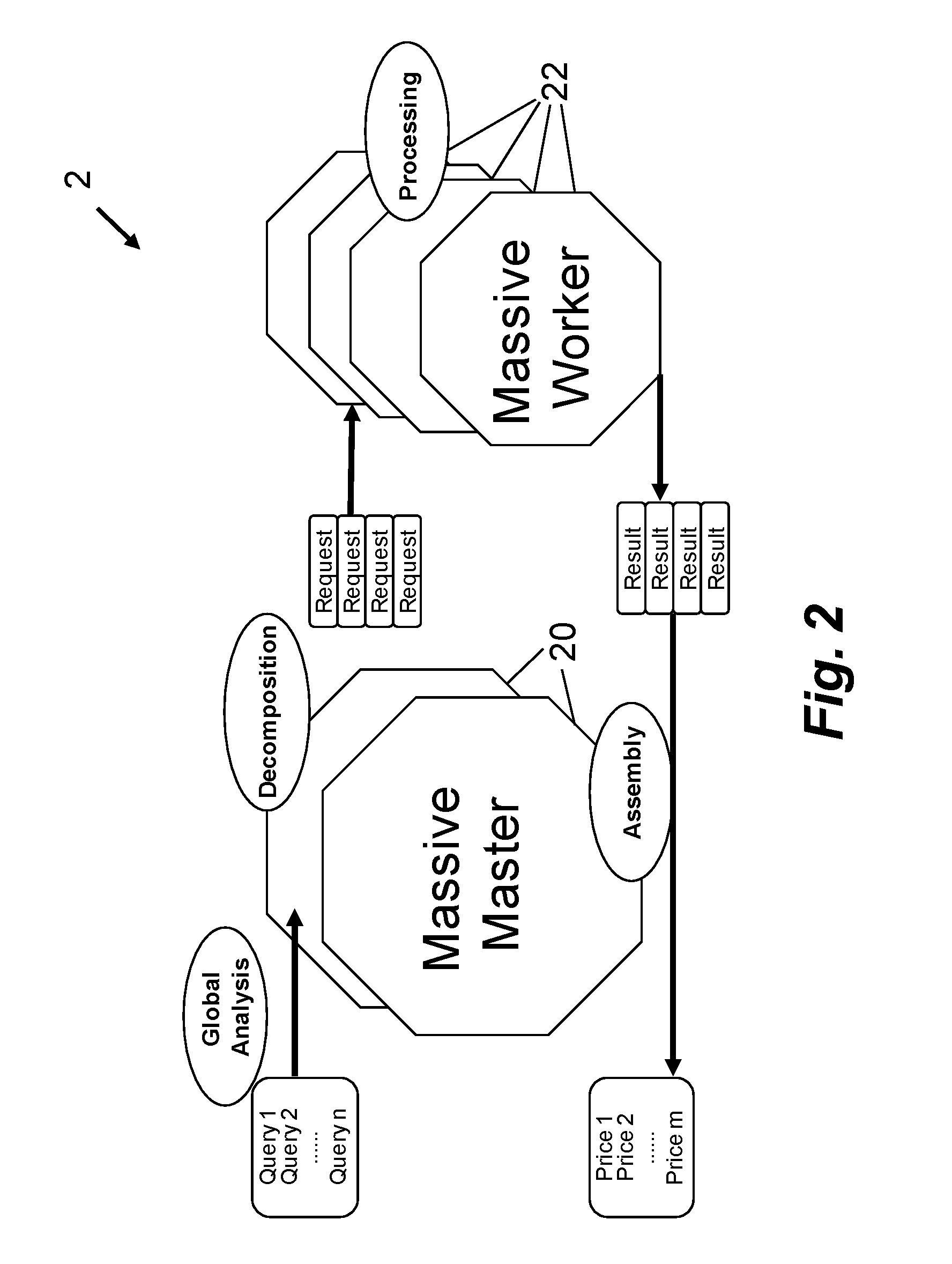
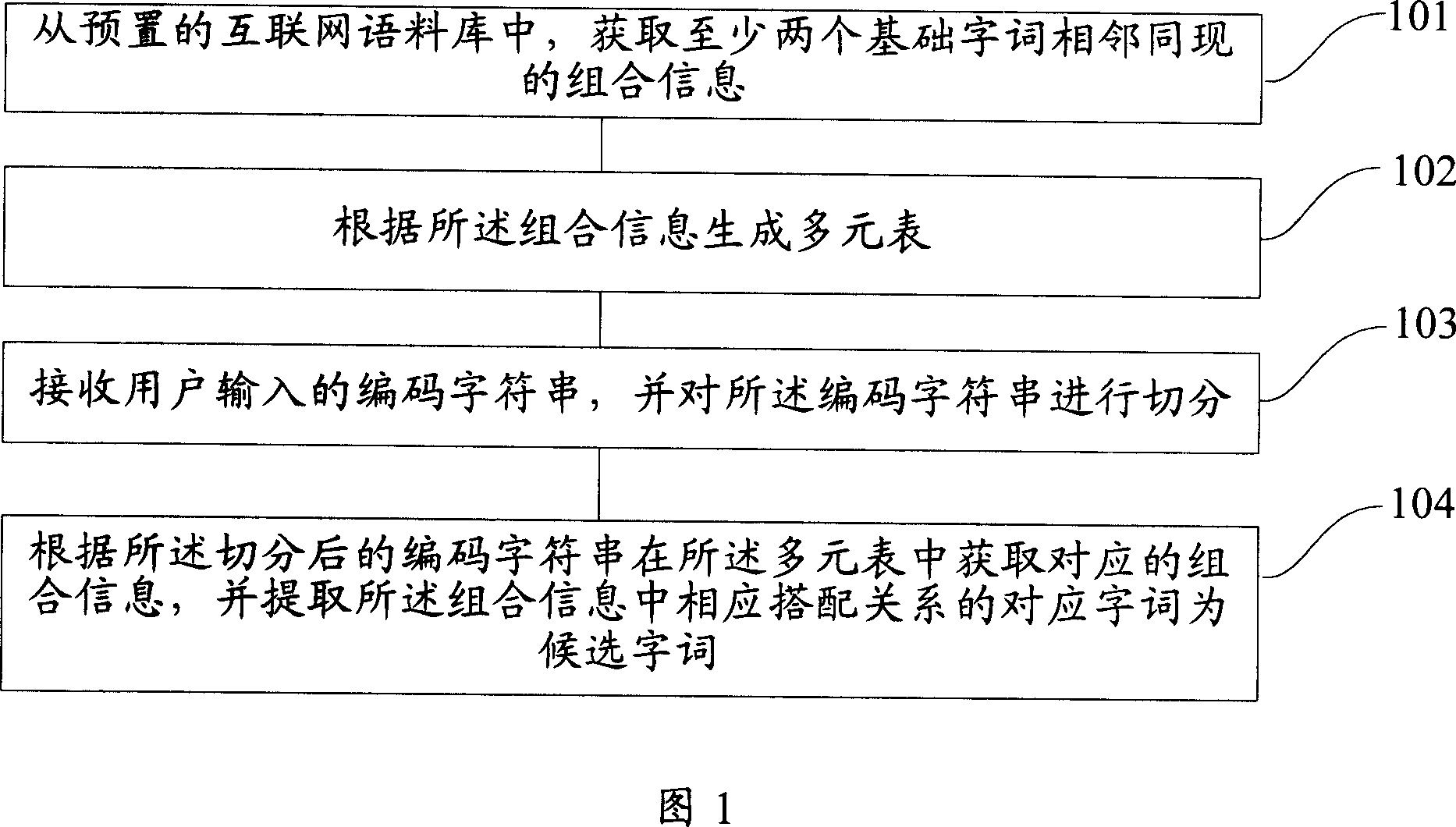
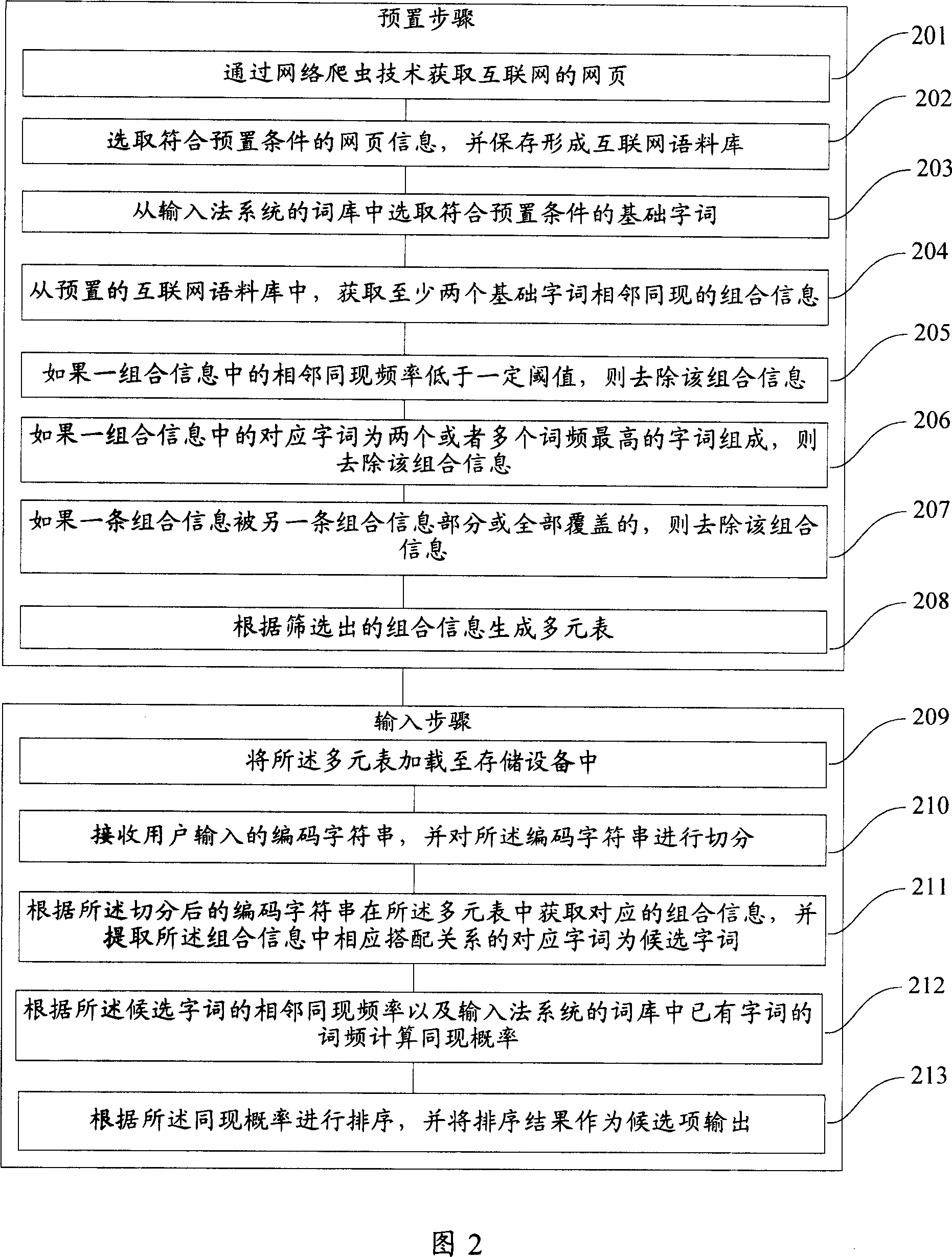
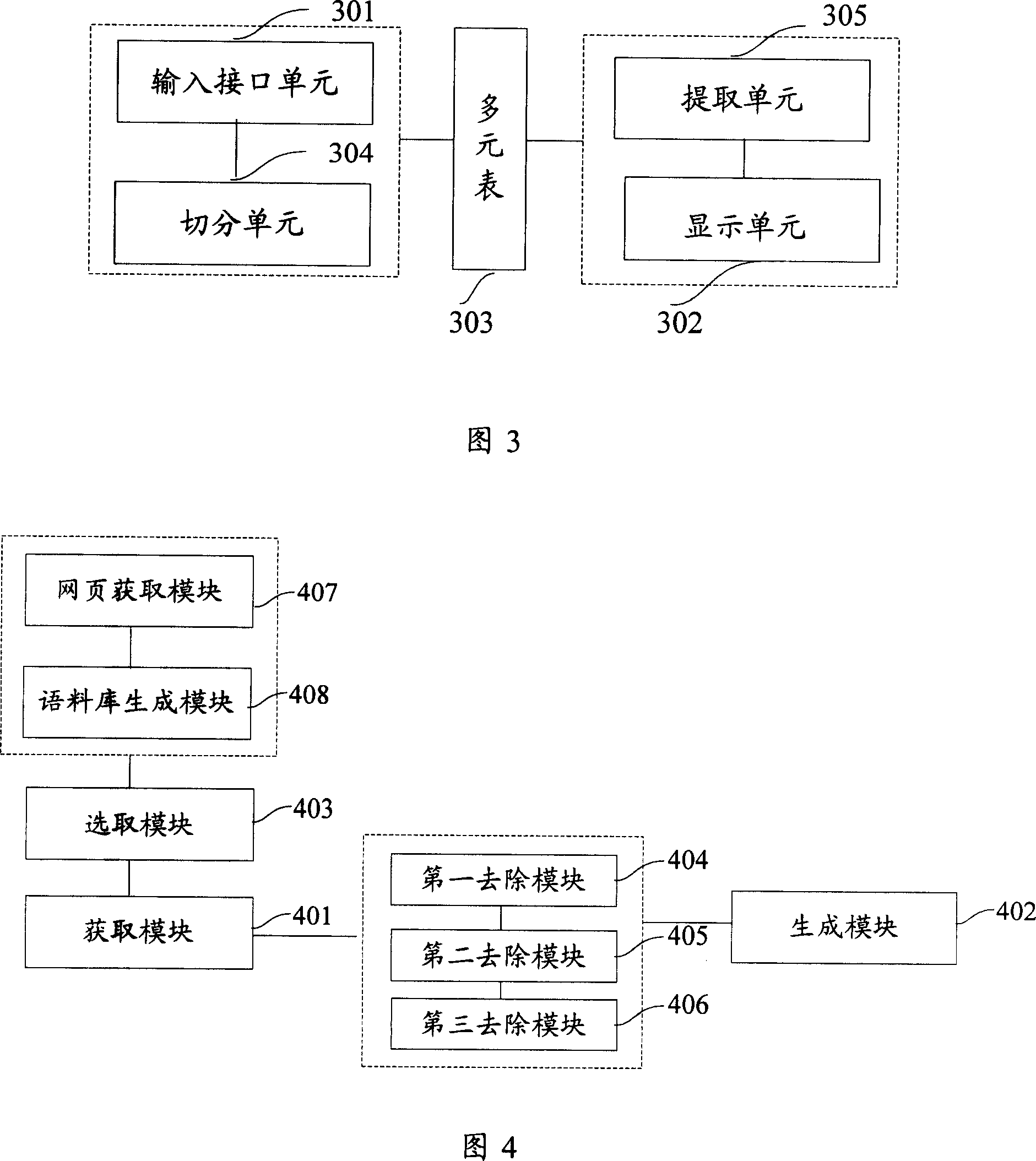
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2522results about How to "Avoid duplication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
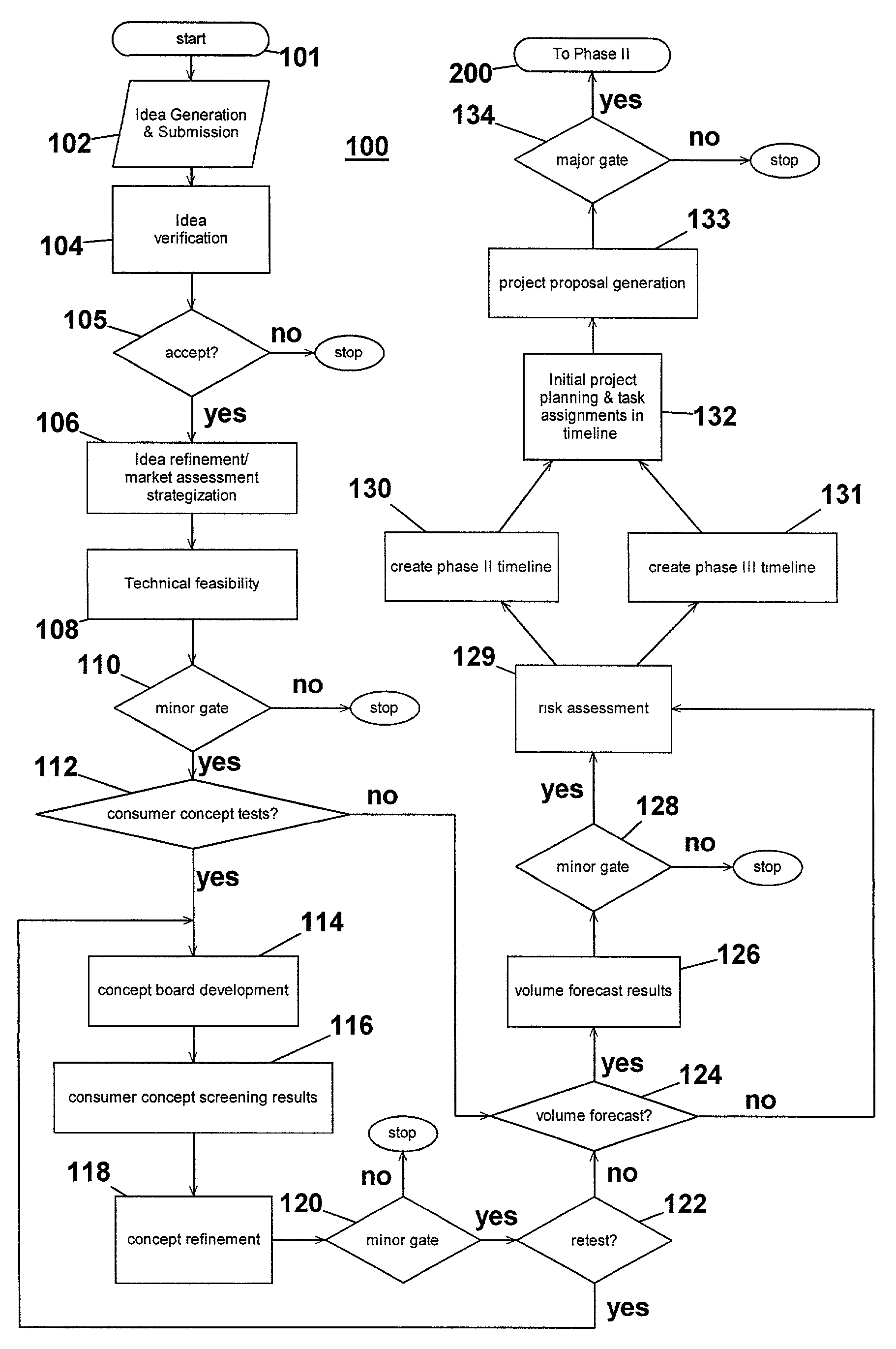
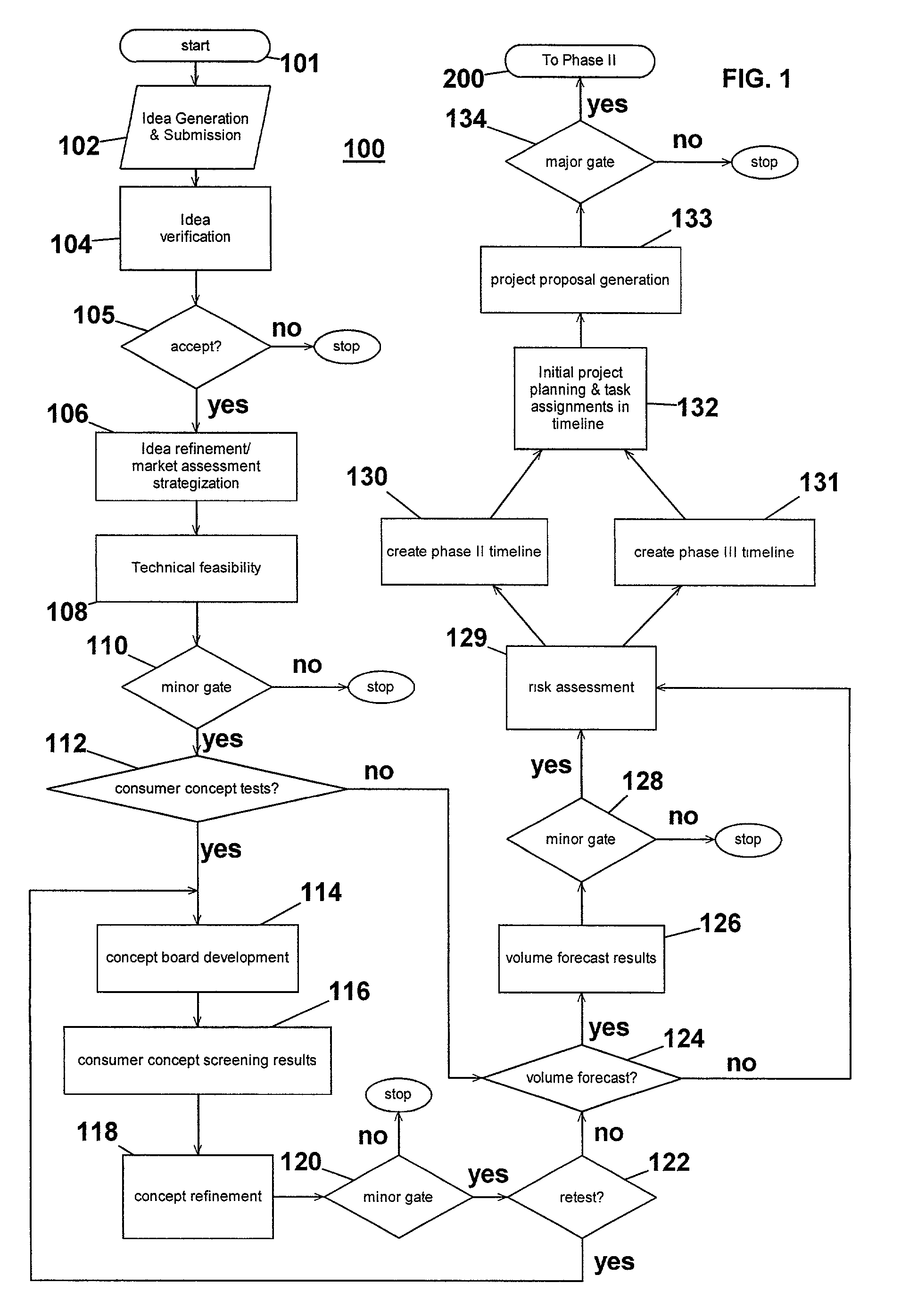
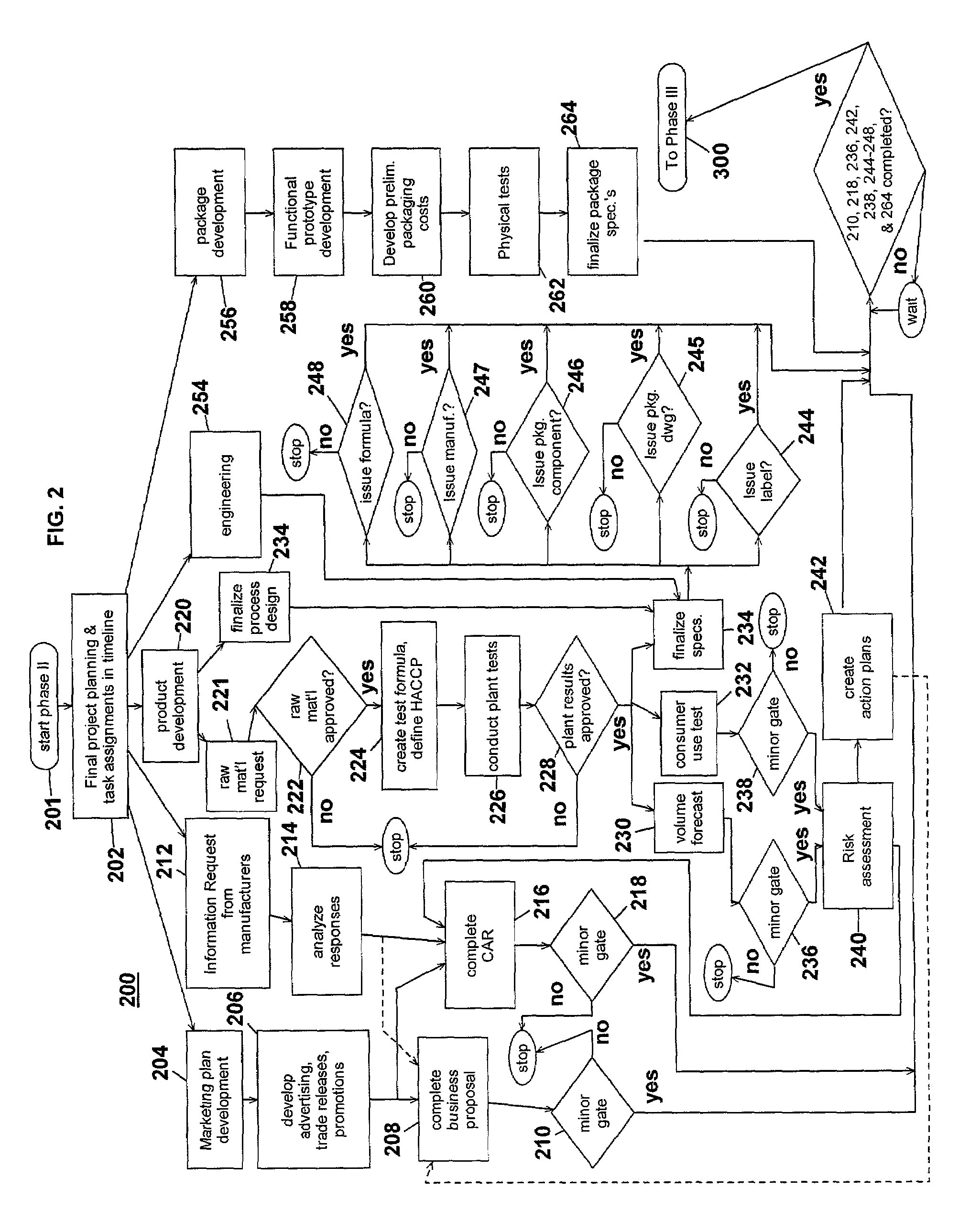
Computer-implemented system and method for project development
InactiveUS7051036B2Avoid repetitionPractical and convenientDigital data processing detailsResourcesProject proposalComputer science
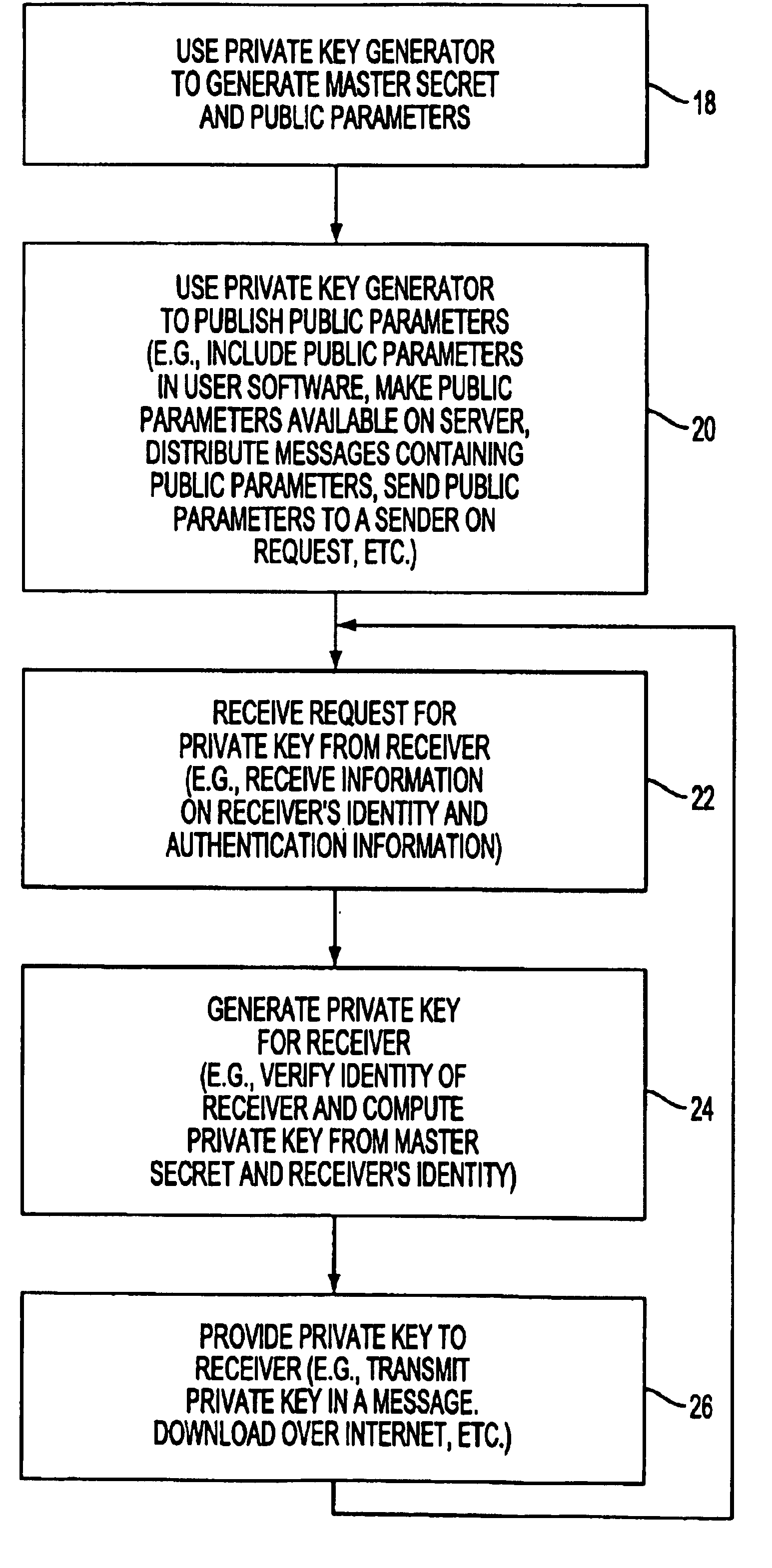
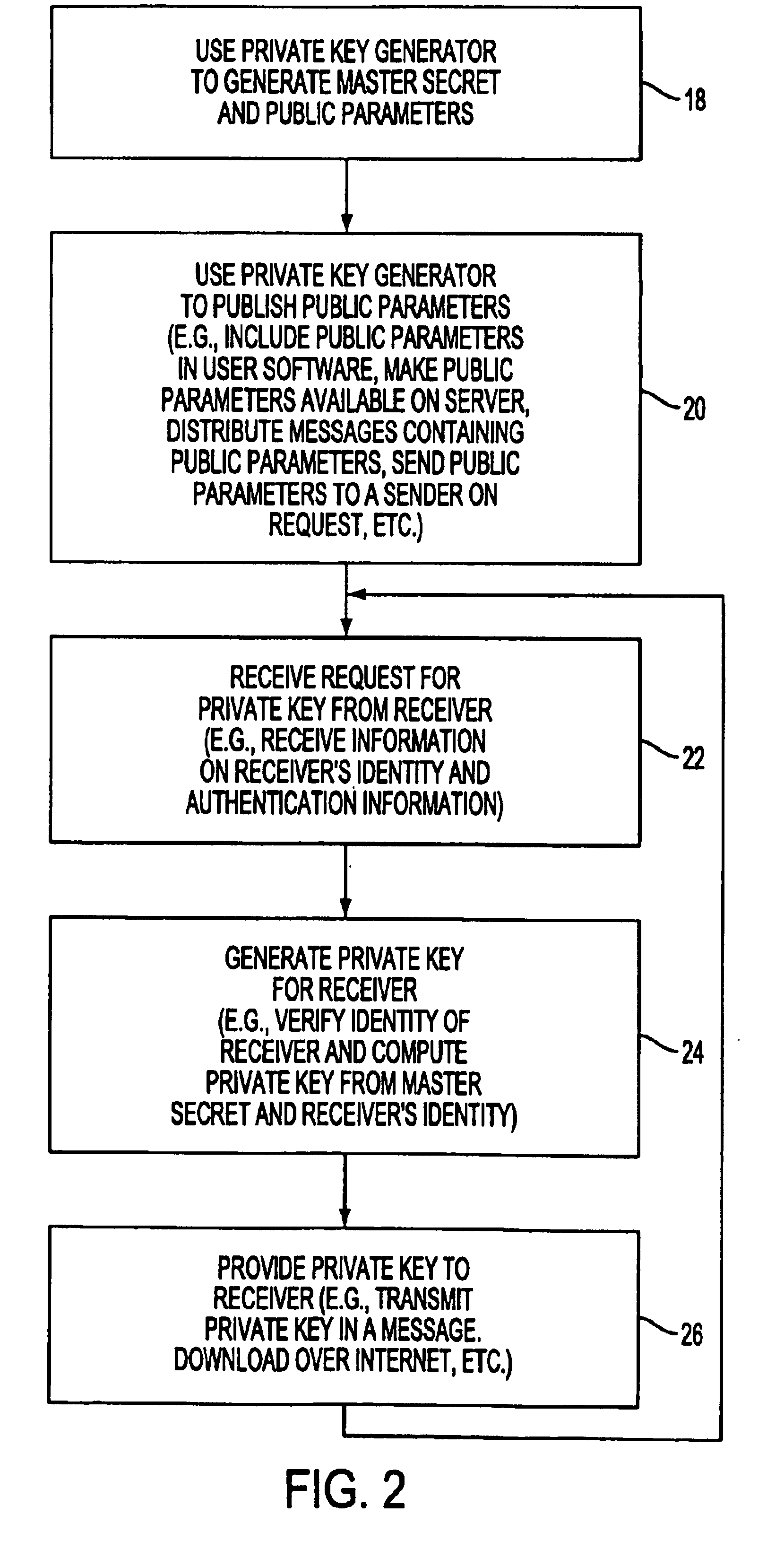
The present invention generally relates to an inventive automated system, and method for its use, including a computer having a computer program defining three development phases including project proposal development, business proposition development, and implementation for market introduction. The project proposal development phase includes a unique idea verification feature by automated reference to an internal knowledge repository and database. The computer is coupled for intercommunication to a plurality of stations or clients from which respective authorized users each have a browser-based interface with the computer.
Owner:KRAFT FOODS GRP BRANDS LLC
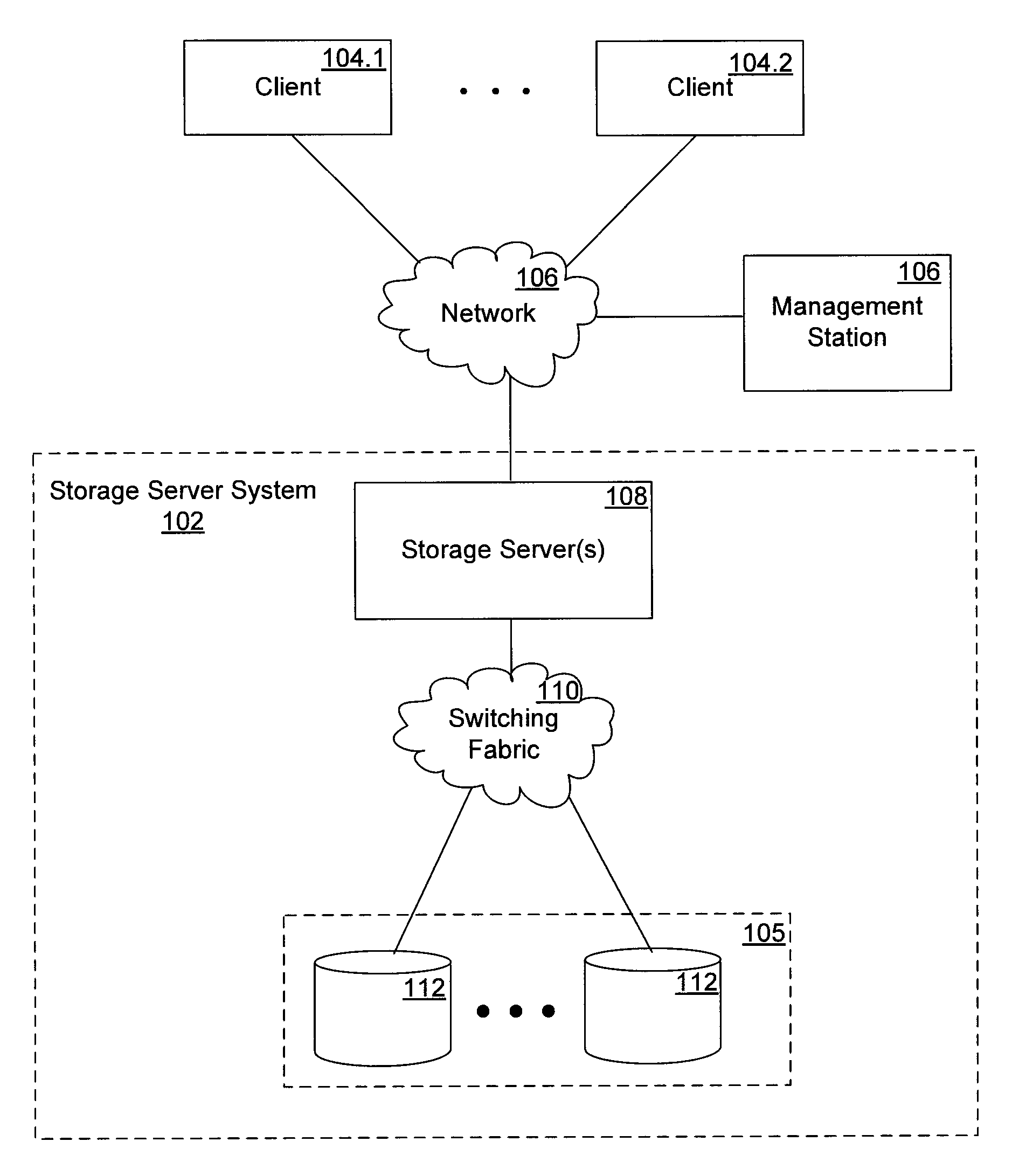
Use of Similarity Hash to Route Data for Improved Deduplication in a Storage Server Cluster
ActiveUS20110099351A1Efficiently routedAvoid duplicationMemory adressing/allocation/relocationTransmissionData miningData storing
A technique for routing data for improved deduplication in a storage server cluster includes computing, for each node in the cluster, a value collectively representative of the data stored on the node, such as a “geometric center” of the node. New or modified data is routed to the node which has stored data identical or most similar to the new or modified data, as determined based on those values. Each node stores a plurality of chunks of data, where each chunk includes multiple deduplication segments. A content hash is computed for each deduplication segment in each node, and a similarity hash is computed for each chunk from the content hashes of all segments in the chunk. A geometric center of a node is computed from the similarity hashes of the chunks stored in the node.
Owner:NETWORK APPLIANCE INC
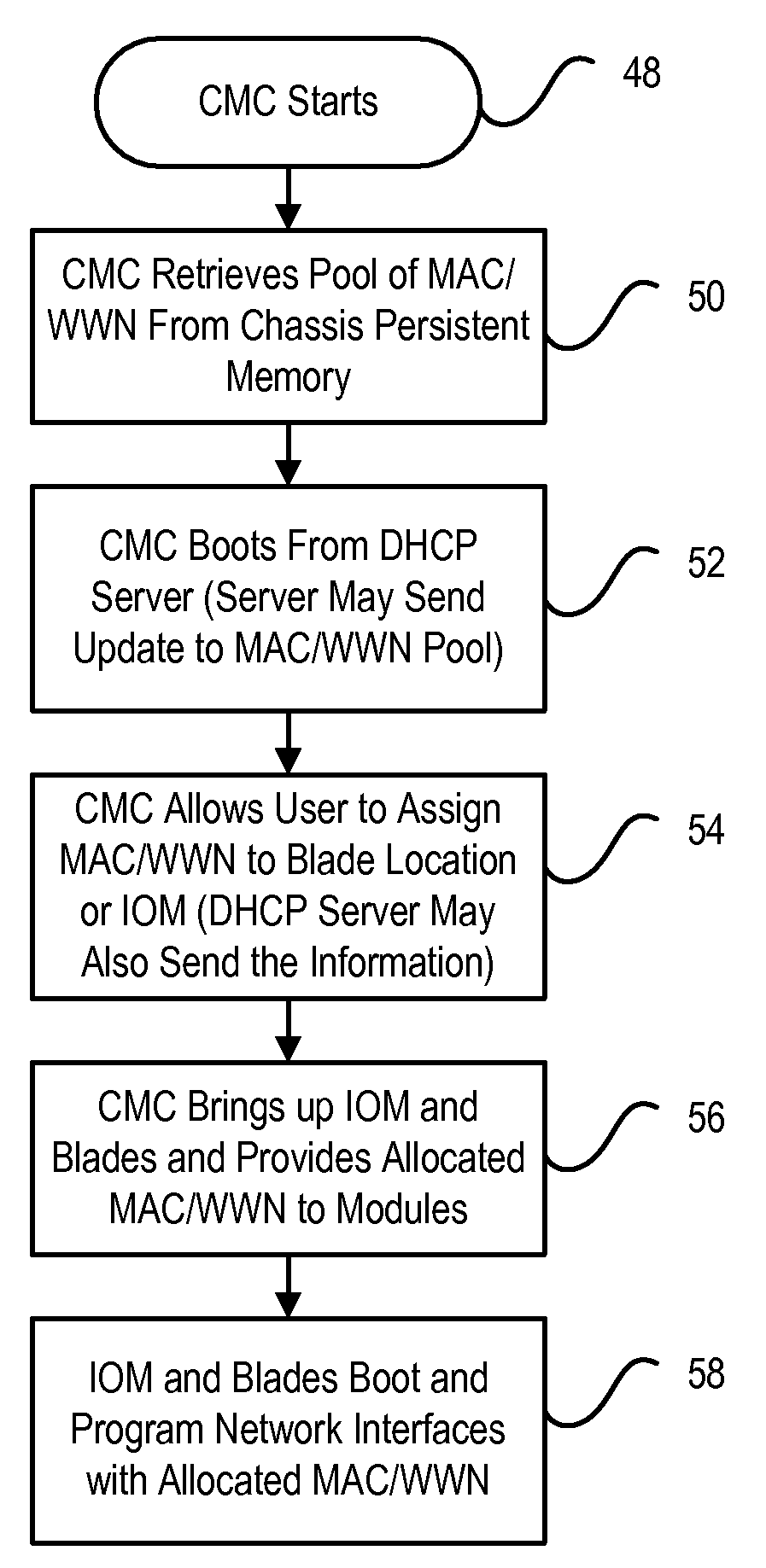
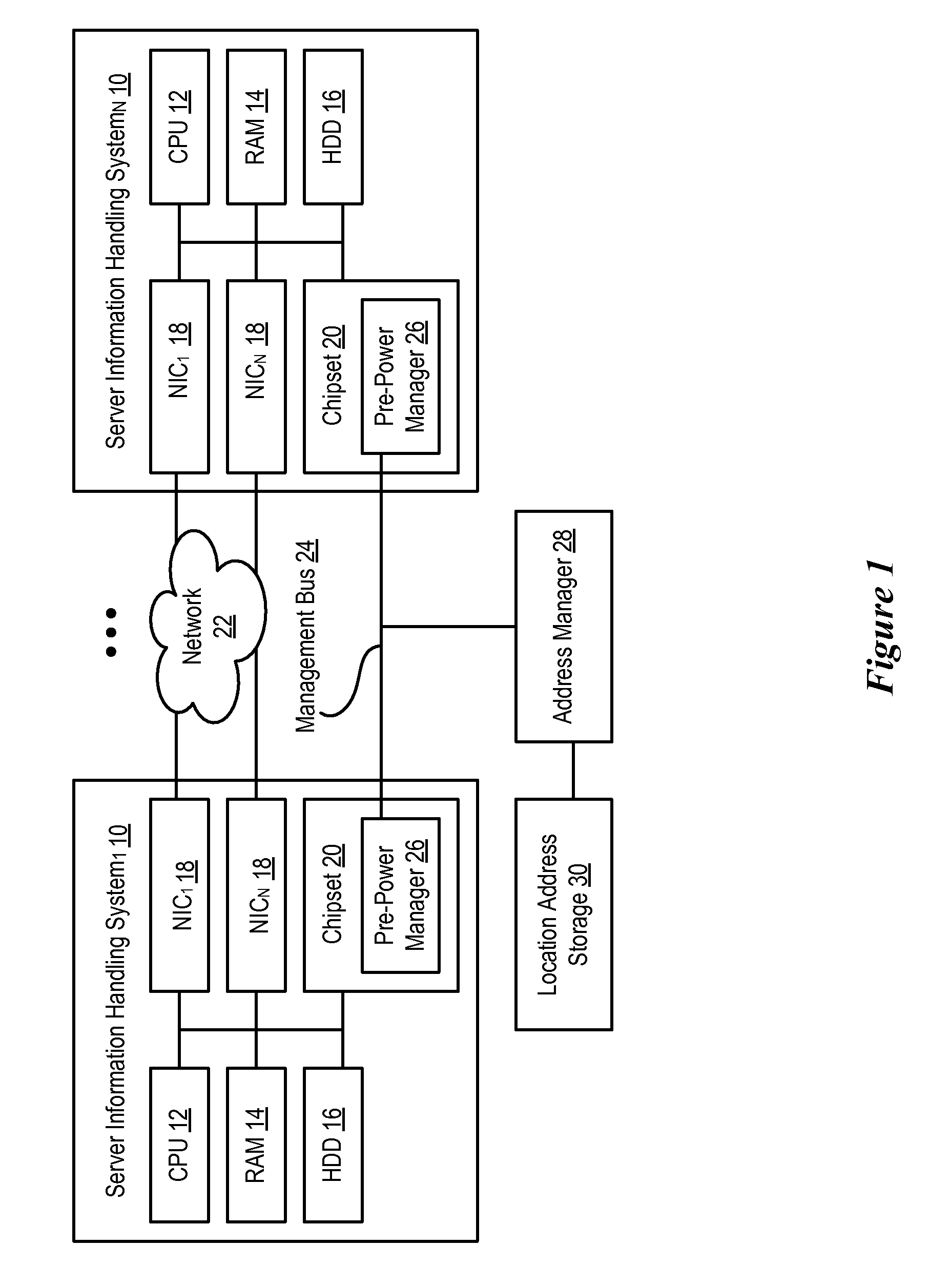
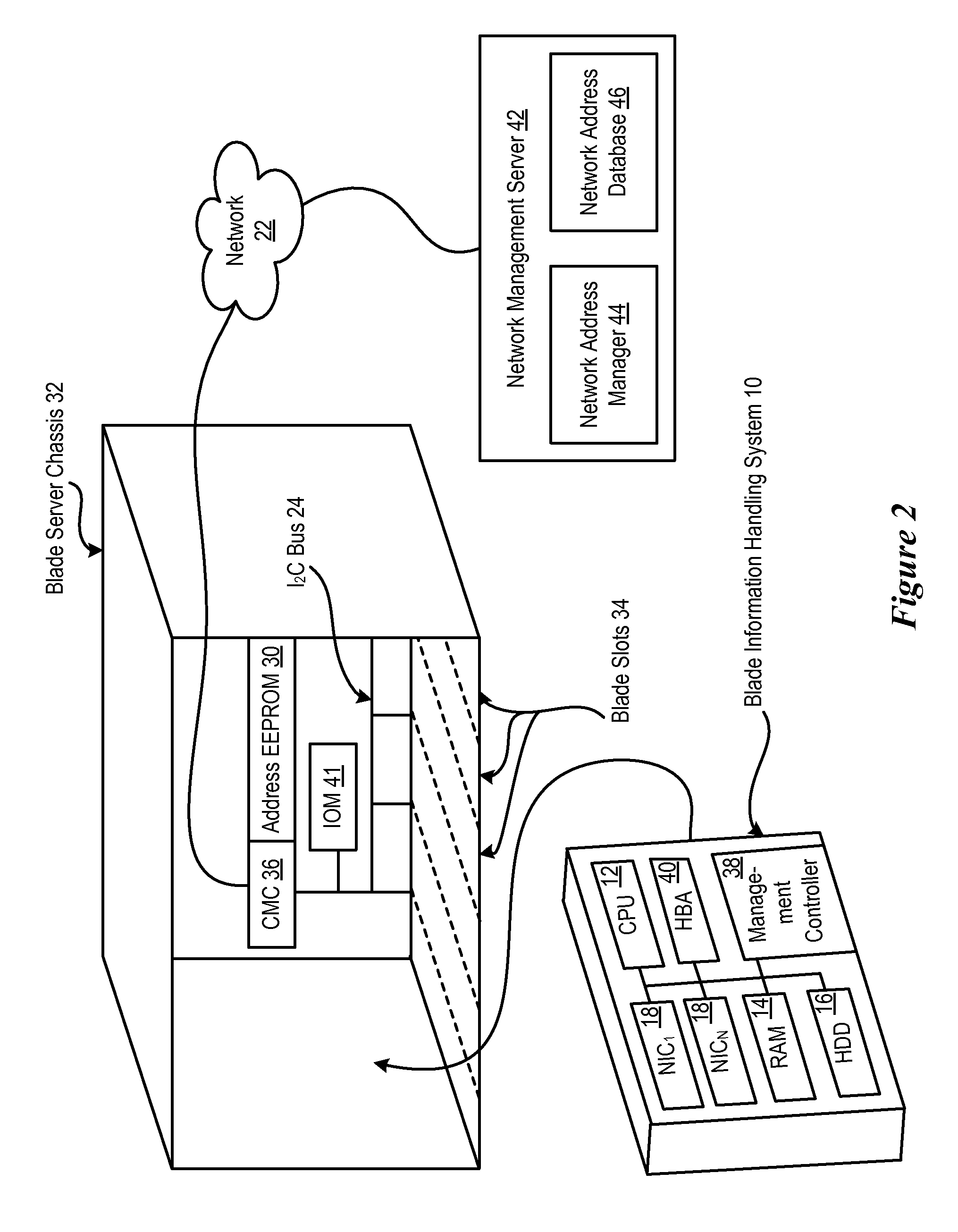
System And Method For Assigning Addresses To Information Handling Systems
ActiveUS20090077208A1Inadvertent duplication is preventedReduce disadvantagesError preventionFrequency-division multiplex detailsNetwork addressingNetwork communication
Information handling system network addresses are managed to support a consistent MAC address for iSCSI and fibre channel host bus adapter. For example, a management controller retrieves a MAC address from persistent memory, such as a network location, and assigns the MAC address to a non-persistent memory of a predetermined information handling system network component so that the MAC address remains consistent even if the network component is replaced. For example, an offload engine that supports network communications with iSCSI receives a MAC address from a network location and applies the MAC address for use by a host bus adapter. Alternatively, an offload engine supports Fibre Channel with World Wide Name or World Wide Identifier address assignments.
Owner:DELL PROD LP
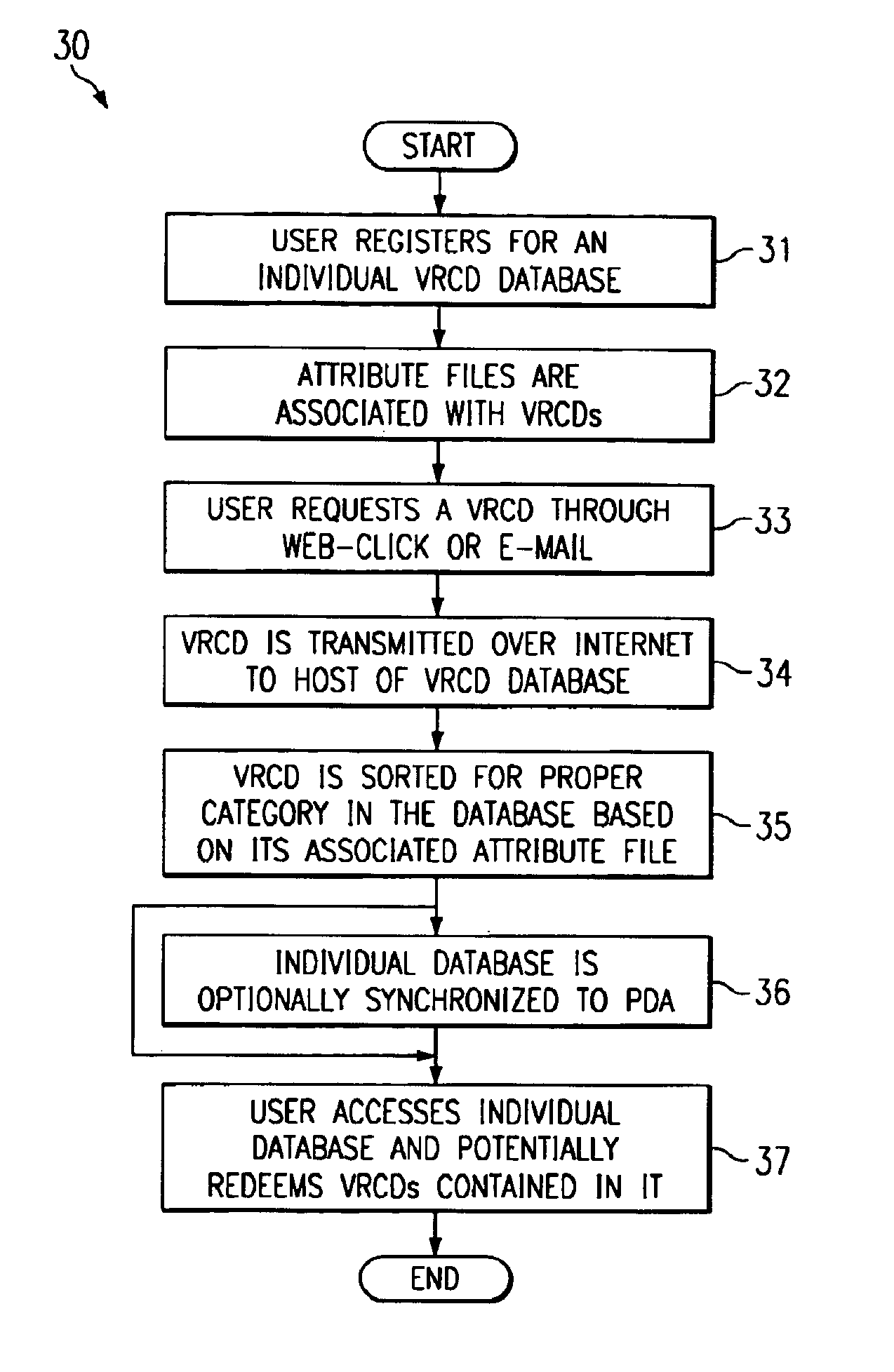
Virtual document organizer system and method
InactiveUS6868426B1Increase the challengeIncrease stickinessAdvertisementsOffice automationDocumentationDatabase
A system and method of managing virtual documents is described. In this approach, a user database is set up on a network-connected computer. There are a number of virtual documents that are created by on other network-connected computers. These virtual documents have associated with them an attribute file having known header and field information. The virtual documents and their associated attribute files are sent from the other network-connected computers to the network-connected computer, which then categorizes and stores information from the virtual documents according to the contents of the attribute file.
Owner:MANKOFF JEFFREY W
Identity-based encryption system
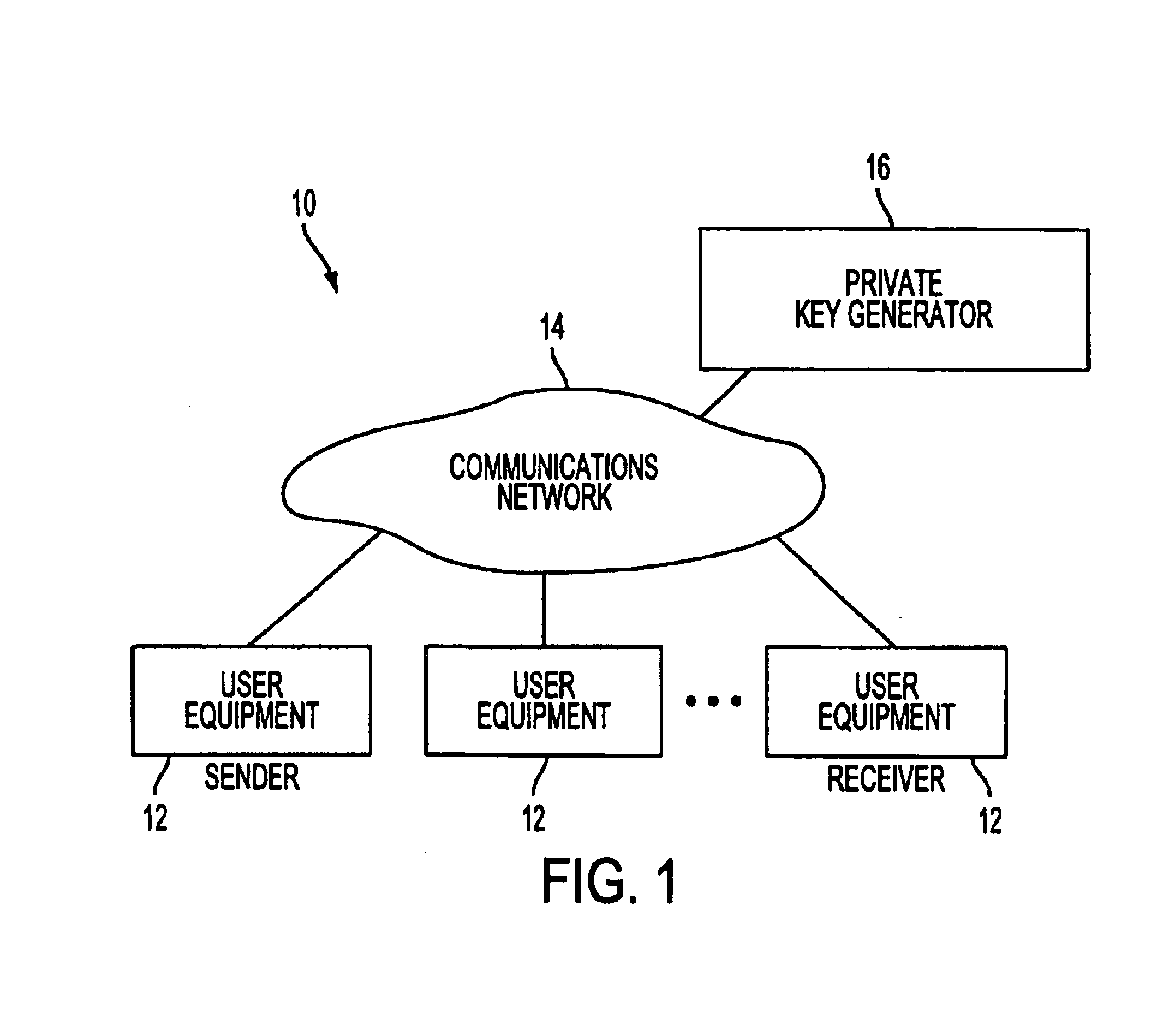
ActiveUS6886096B2Avoid duplicationAvoid repetitionPublic key for secure communicationUser identity/authority verificationSecure communicationKey generator
A system is provided that uses identity-based encryption to support secure communications. Messages from a sender to a receiver may be encrypted using the receiver's identity and public parameters that have been generated by a private key generator associated with the receiver. The private key generator associated with the receiver generates a private key for the receiver. The encrypted message may be decrypted by the receiver using the receiver's private key. The system may have multiple private key generators, each with a separate set of public parameters. Directory services may be used to provide a sender that is associated with one private key generator with appropriate public parameters to use when encrypting messages for a receiver that is associated with a different private key generator. A certification authority may be used to sign directory entries for the directory service. A clearinghouse may be used to avoid duplicative directory entries.
Owner:MICRO FOCUS LLC
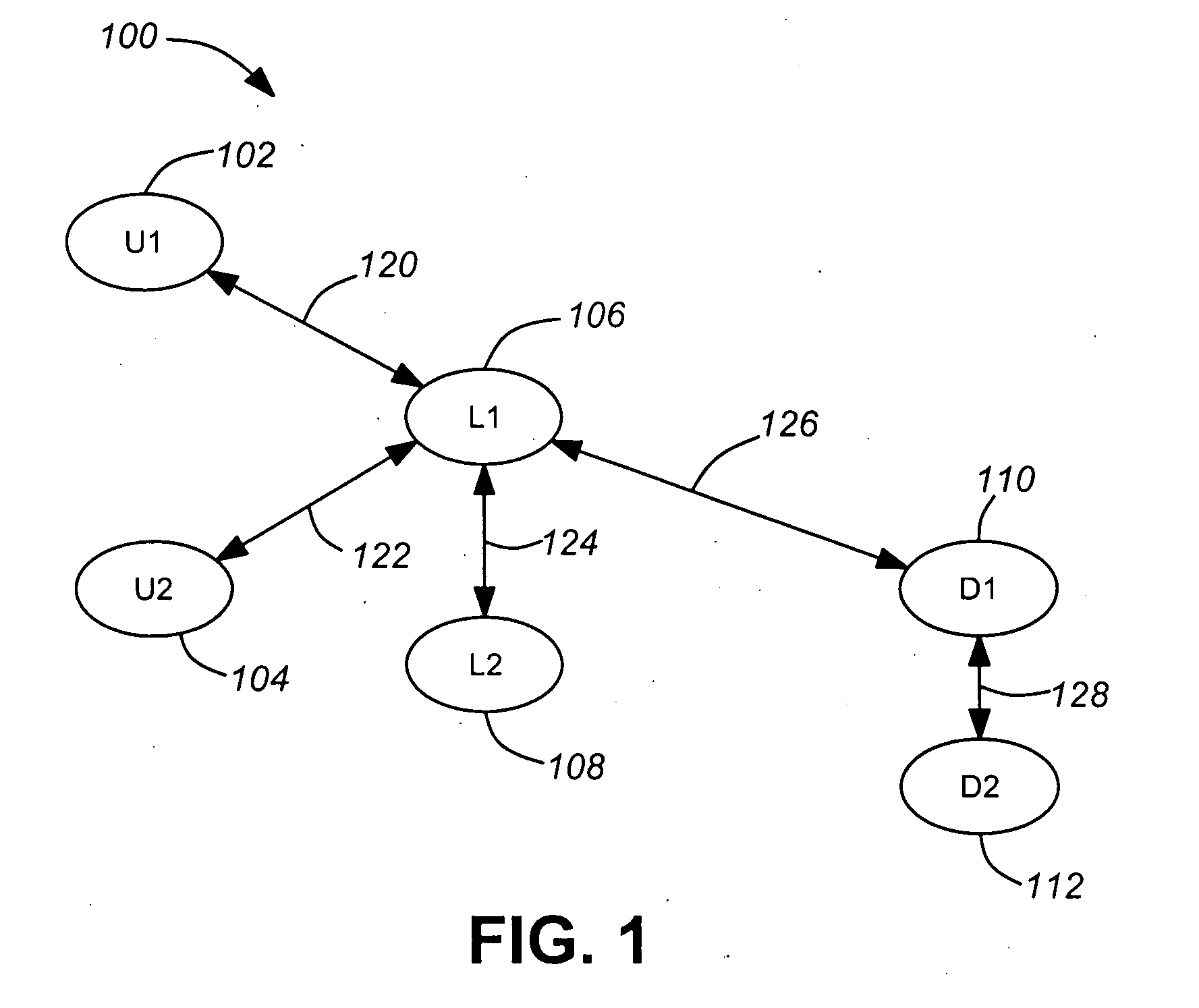
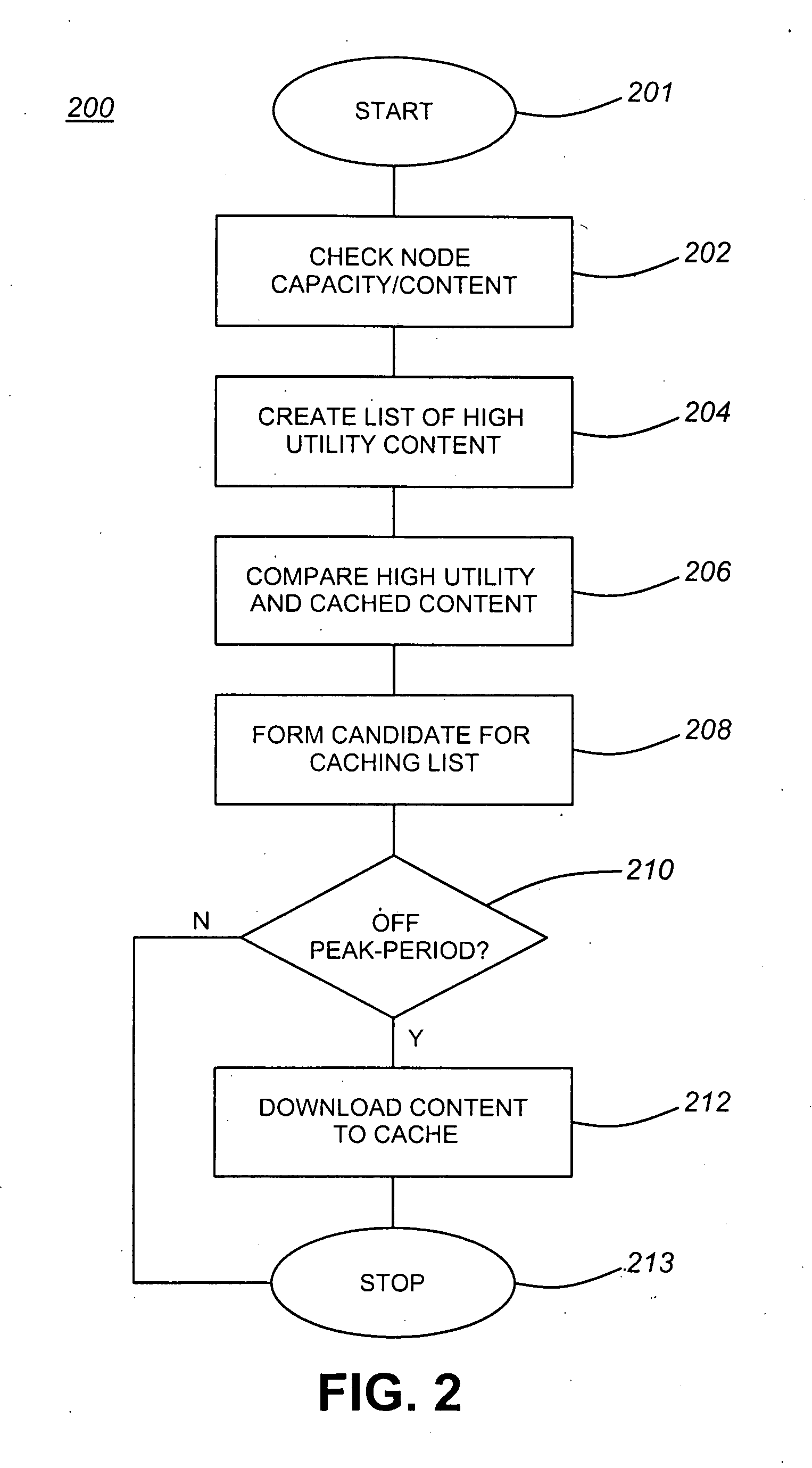
Predictive caching content distribution network
ActiveUS20090168795A1Minimization requirementsAvoid duplicationStore-and-forward switching systemsQuality of serviceContent distribution
In various exemplary embodiments, a method for the distribution of content within a network of constrained capacity uses distributed content storage nodes functioning to achieve optimal service quality and maximum service session capacity. The method, which functions in unicast, broadcast, switched broadcast, and multicast mode networks, uses predictions of the utility of particular content items to download or record the highest utility items to distributed content stores during periods and in modes that will not increase demand peaks. These predictions of utility may be based on, for example, the number of potential users, the likelihood of their use, and the value to the service provider. The method uses signaling between network nodes to identify the best source for particular content items based on which nodes hold that content and the nature of network constraints.
Owner:ALCATEL LUCENT SAS
Method and apparatus for end-to-end content publishing system using XML with an object dependency graph
InactiveUS7076728B2Avoid scatterAvoid duplicationDigital computer detailsNatural language data processingData integrityReusability
The system for end-to-end content publishing using XML with an object dependency graph is based on the following two design principles: First, separation of content and style: Information stored in the content management system is independent on how it is going to be presented. The presentation style is encapsulated elsewhere and can be used to customize the look and feel based on the end-user preferences as well as the delivery methods and devices. Second, reusability of information content: By encapsulating common information in fragments and subfragments and making these fragments insertable in other fragments, thereby avoid scattering and duplication of information. This enables a user to restrict the edit operations to a limited number of relevant fragments, to affect global changes. In addition, the present invention provides data consistency and data integrity in the content management.
Owner:IBM CORP
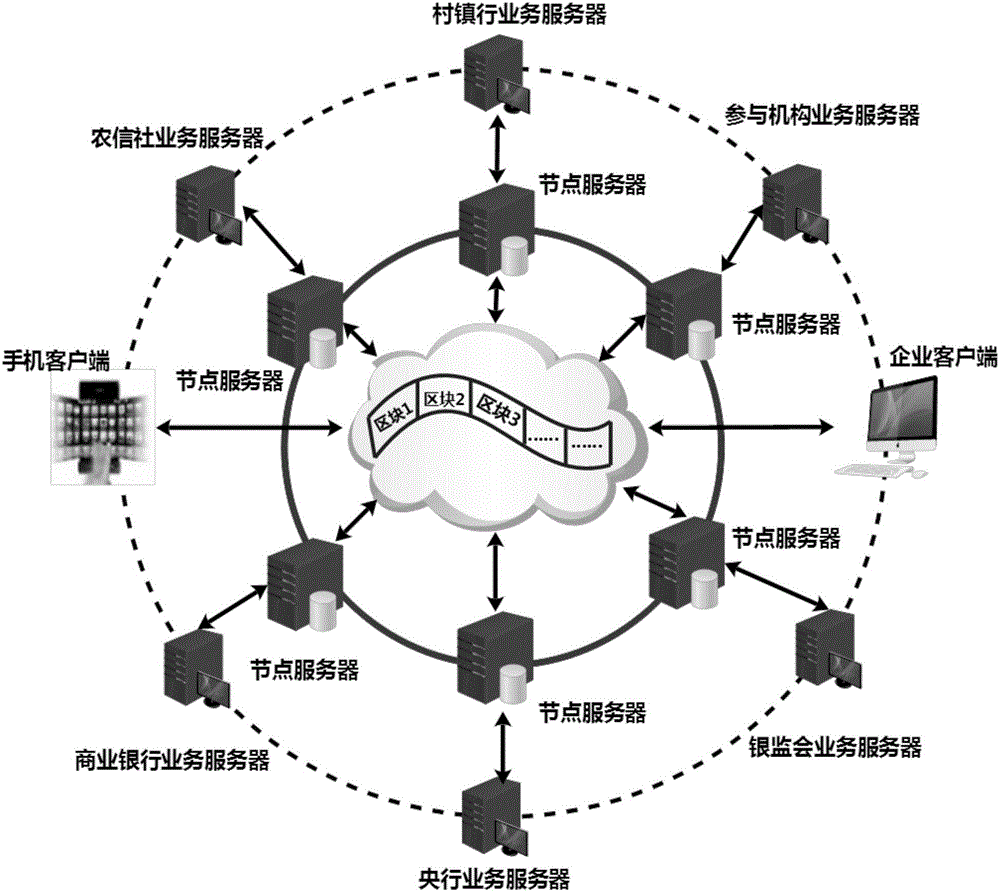
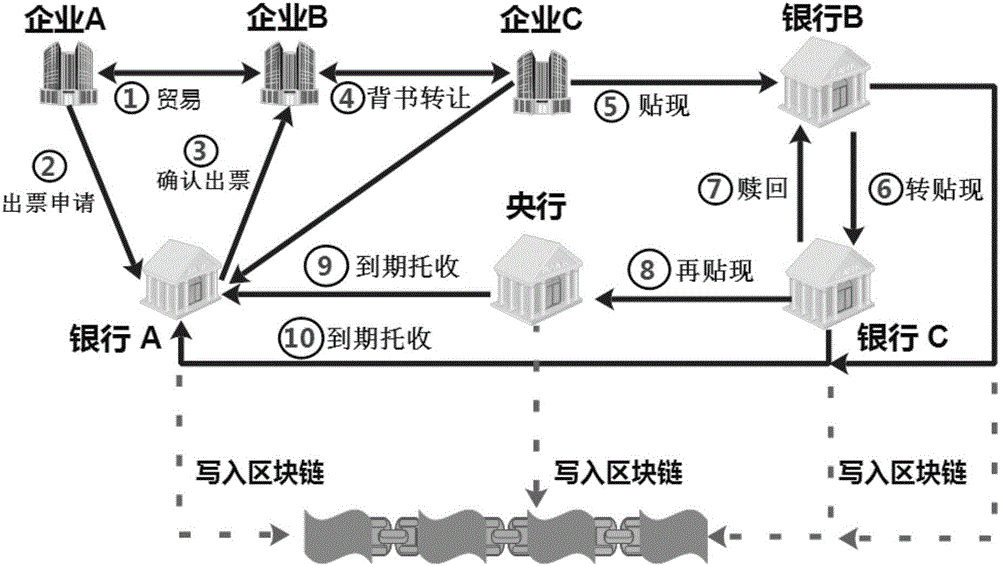
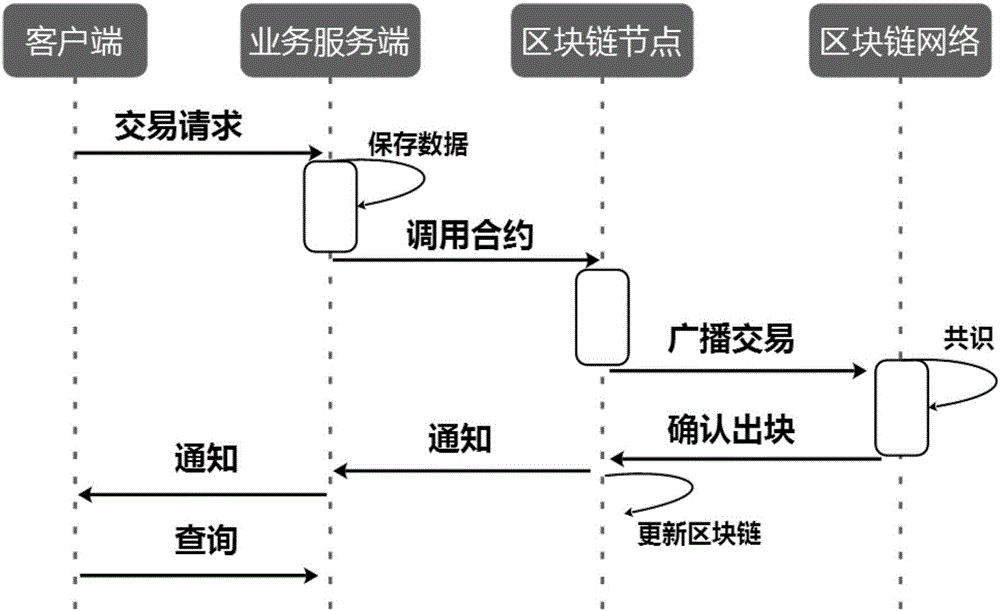
Consortium chain-based digital bill trading system construction method
InactiveCN106780033AImprove safety and reliabilityAvoid reconciliation workFinanceTechnical supportBlockchain
The invention discloses a consortium chain-based digital bill trading system construction method, which develops a brand-new bill display form, namely, a digital bill in combination with existing bill attributes, laws and regulations and market by taking a consortium chain as technical support. Compared with an existing electronic bill, the digital bill is totally different from the electronic bill in technical framework, not only has all functions and advantages of the electronic bill but also fuses the advantages of a block chain technology, and is a securer, more intelligent, more convenient and more promising bill form. In addition, the block chain technology is applied to the field of bill businesses for the first time; a unified standard bill trading platform is established; the problems of trade background forgery, bill authenticity authentication failure, paper bill multi-time selling, non-synchronous electronic bill discounting and bill endorsing, and the like are solved; and various risks are effectively managed, controlled and prevented.
Owner:HANGZHOU YUNXIANG NETWORK TECH
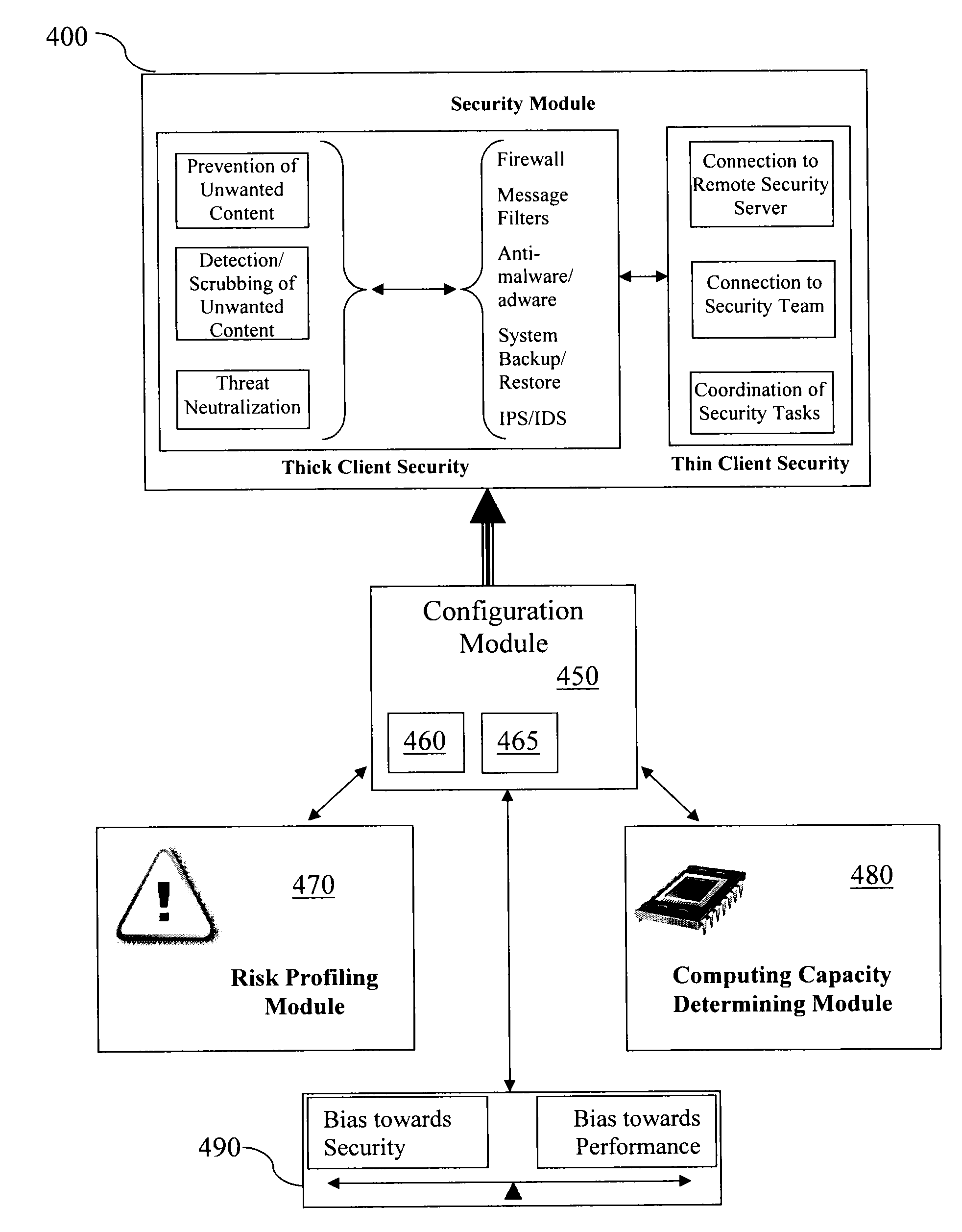
Team security for portable information devices
ActiveUS20110289308A1Avoid duplicationImprove intelligenceData resettingMultiple digital computer combinationsRelevant informationInformation device
A portable information device (PID) having a security module that conducts security-related functionality. At least some of the security-related functionality for the benefit of the PID is provided by a security team of at least one other PID. In one type of arrangement, when configured in a team processing mode, certain ones of the security functions or components operating for the benefit of the PID can be processed on one or more of the security team member devices. In another type of arrangement, the team of devices exchanges security-related information determined as a result of a single team member device's processing of one or more security-related tasks.
Owner:AO KASPERSKY LAB
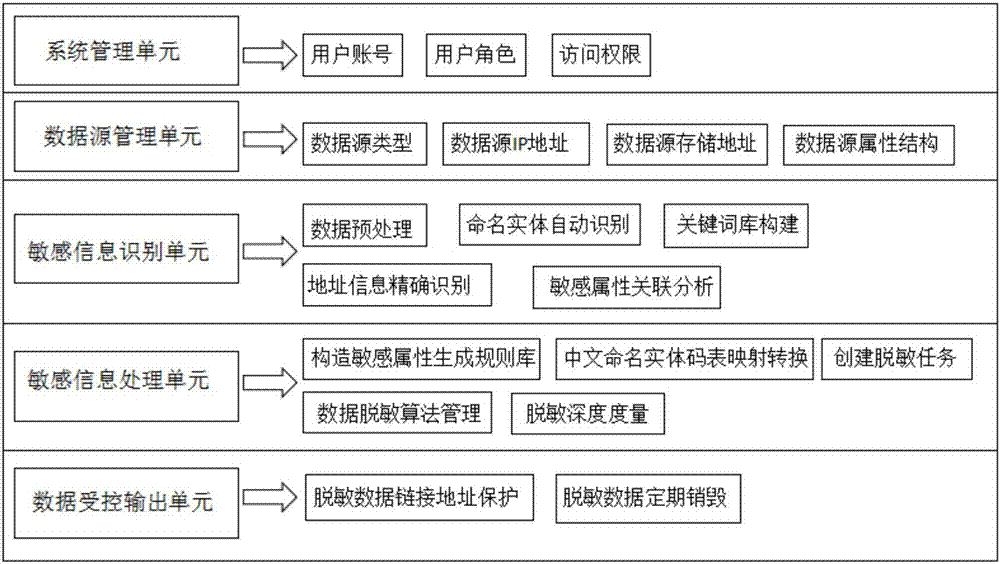
Sensitive information desensitization method and system for data sharing
ActiveCN107480549AAvoid duplicationAvoid rebuildingDigital data protectionSpecial data processing applicationsInformation processingData set
The invention relates to a sensitive information desensitization method and system for data sharing. According to the method, by adopting statistics, a natural language processing technology and a machine learning technology, the protection of sensitive data in the whole process from data publishing to data application and usage, and automatic identification of sensitive information of such as named entities and addresses is put forward on the basis of the establishment of a sensitive information keyword library, named entities, addresses and the like is put forward; a Sigmoid function is used for calculating the correlation degree of sensitive attributes; a desensitization strategy is carried out in a combined mode of establishing a sensitive attribute generation rule library and adopting a named entity desensitization rule and a core desensitization algorithm; deep desensitization calculation is conducted in combination with numerical sensitive attributes and classified sensitive attributes separately, the desensitization degree of a whole data set is obtained, and the controlled output of data and the like are achieved by downloading a link address hash; thus, the safety of data sensitive information and a sensitive information processing strategy which meets analysis and mining requirements to the maximize degree can be ensured, and the method and system have the advantages of being good in desensitization effect, high in reliability and the like.
Owner:ENJOYOR COMPANY LIMITED
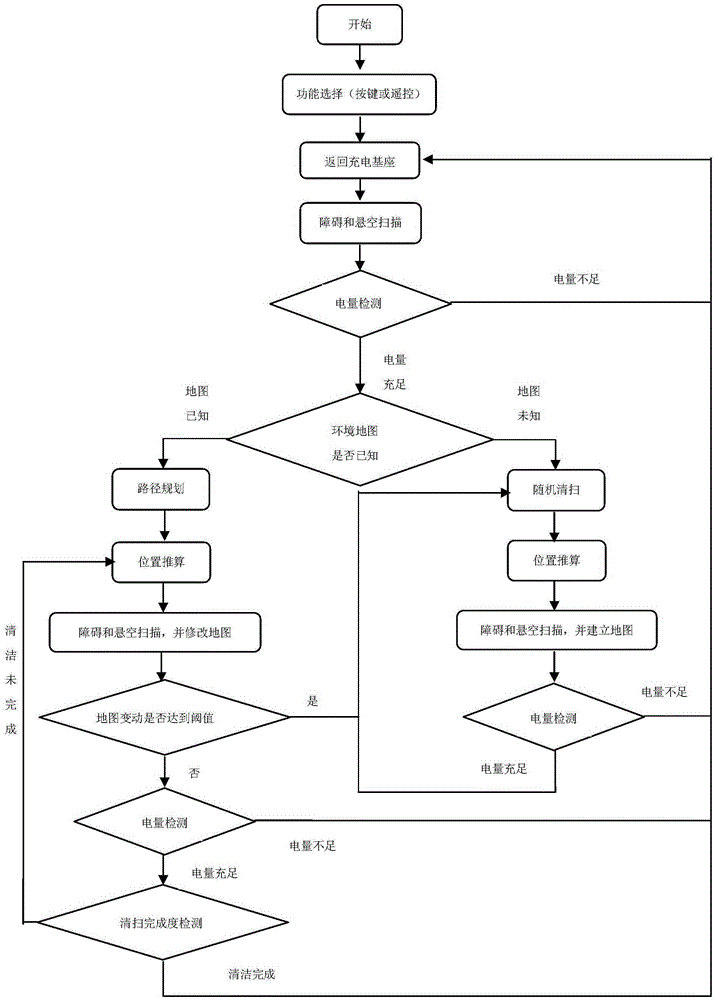
Intelligent cleaning robot based on advanced path programming technology and cleaning method thereof
InactiveCN105425801ASave cleaning timeAchieve maximum coveragePosition/course control in two dimensionsMotor driveControl system
The invention relates to an intelligent cleaning robot based on an advanced path programming technology and a cleaning method thereof. An external environment information detection system installed on a robot body, a real-time positioning system, a main control system, a motor driving module and a power supply are included. The external environment information detection system is used for detecting external environment information. The real-time positioning system is used for acquiring a real-time position where the robot is located. The main control system is used for acquiring external environment information and establishing a grid map. Through combining the grid map and the real-time position, a cleaning path is programmed. The motor driving module is used for driving the robot to operate according to the programmed cleaning path and clean. The power supply is used for providing power for the main control system and the motor driving module. A path programming technology of boundary cleaning, rectangular manufacturing, parallel paving and cleaning and obstacle consideration is used to design the cleaning path, a current position is determined in real time, cleaning time is saved and simultaneously a largest coverage rate to an cleaning environment is realized.
Owner:CHANGAN UNIV
Video distribution system
InactiveUS20070234391A1Avoid conversionAvoid duplicationTelevision system detailsRecord information storageDistribution systemSubject matter
The disclosed subject matter relates to video distribution systems and, more particularly, to a system that blanket transmits video / audio content such as movies (for example, via satellite downlink transmission) to each customer's recording, storage and playback system. Customers may preselect from a list of available movies or other content in advance using an interactive screen selector, and pay for the video / audio content that is actually viewed.
Owner:OCHOA OPTICS
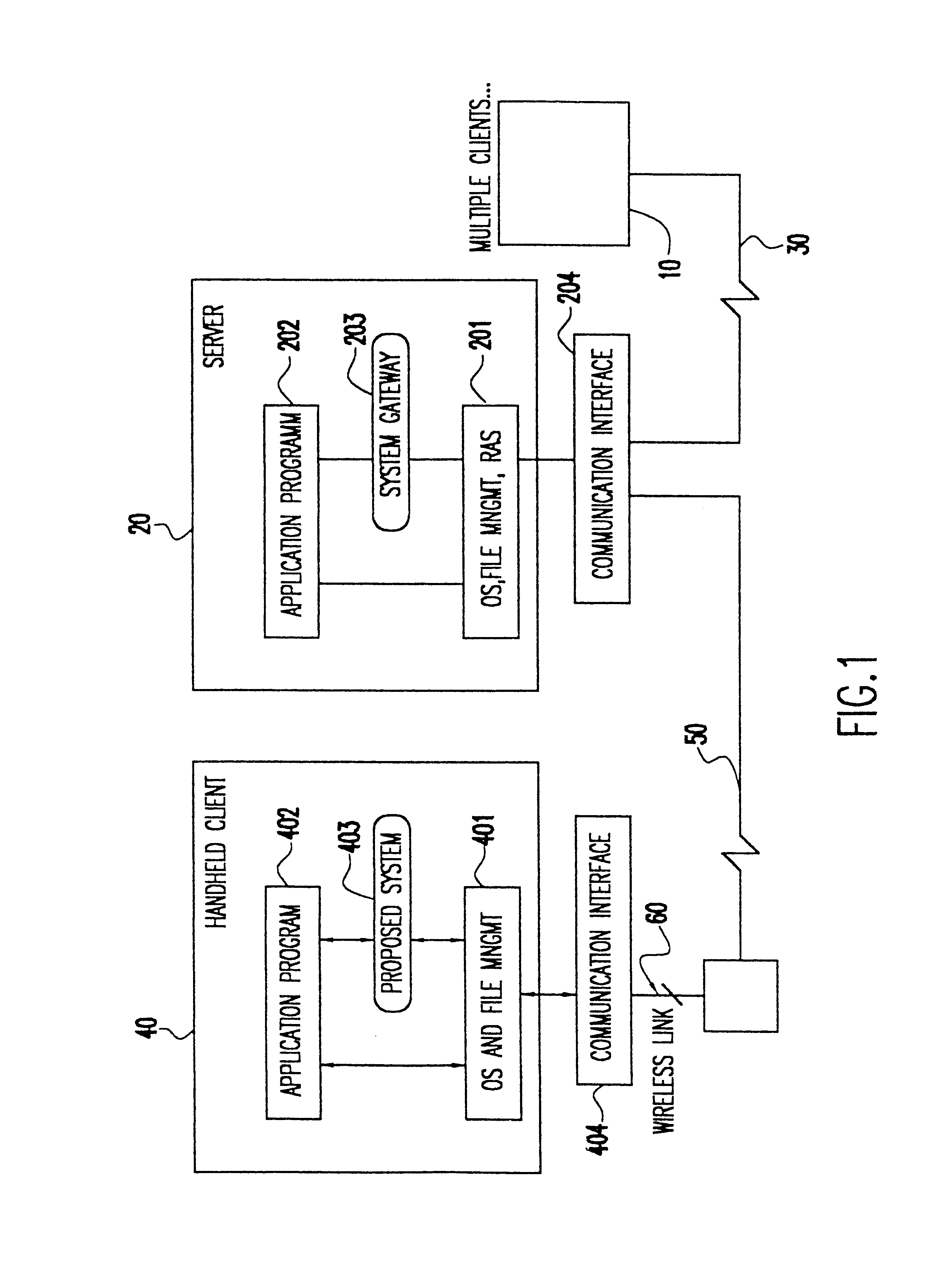
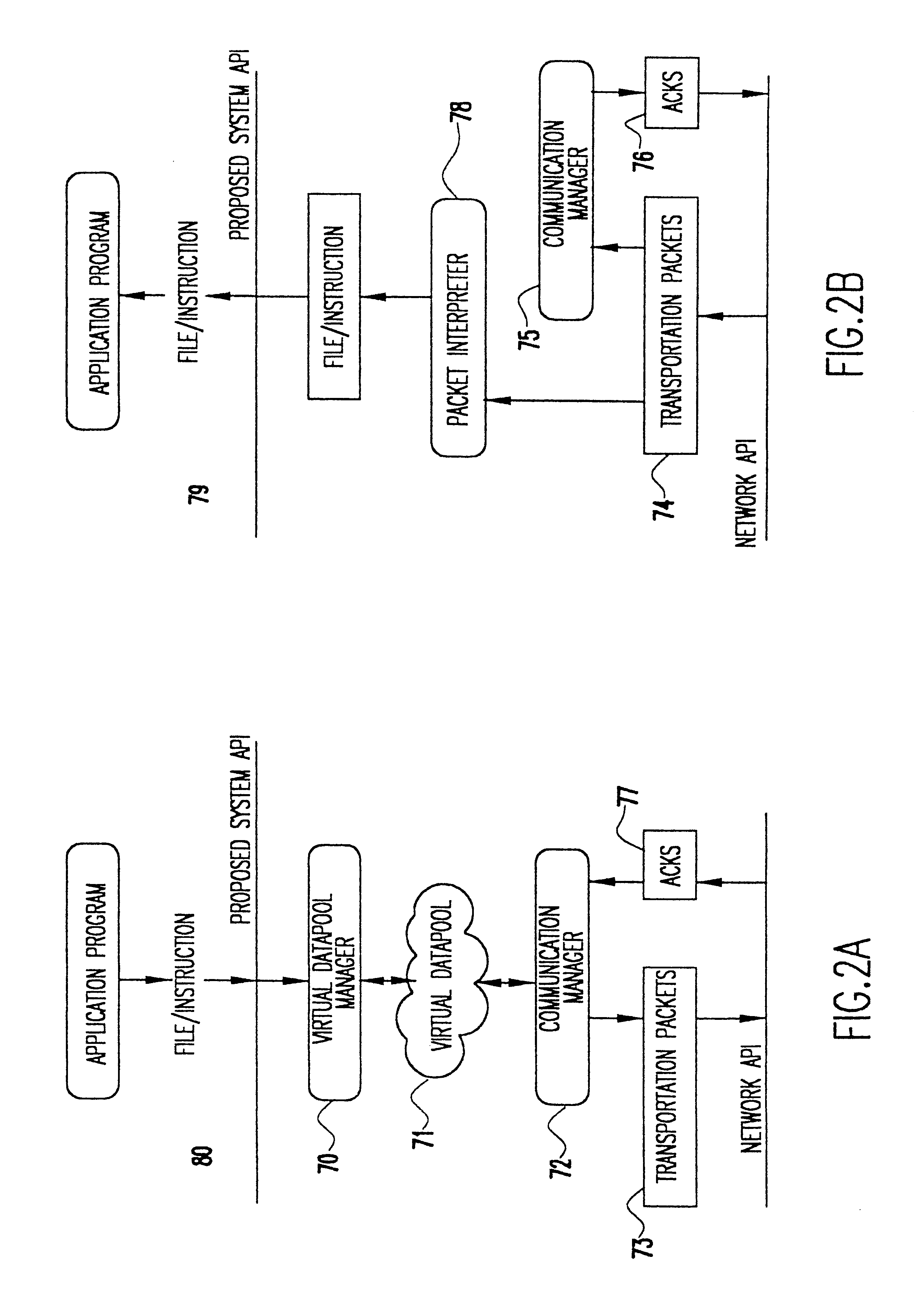
Data transfer mechanism for handheld devices over a wireless communication link
InactiveUS6775298B1Bandwidth is not as inexpensiveReduce battery power consumptionError preventionFrequency-division multiplex detailsTelecommunications linkNetwork packet
A method and apparatus for transferring data between a handheld device and a network over a wireless communications link. A datapool manager breaks files into virtual blocks and adds the virtual blocks to a datapool. A communications manager converts the virtual blocks into transportation packets and controls the transfer of the transportation packets between the handheld device and the network. After a transportation packet is transferred, an acknowledgment is returned indicating that the transfer was successful. If the transfer of a file is interrupted, then, upon reestablishing the wireless link, only those transportation packets for which an acknowledgment has not been returned are transferred. To properly reconstruct the file, a pointer indicates the location of each transportation packet in the file. Furthermore, to enable the use of a partially transferred file, a table of information is maintained indicating the validity of the partially transferred file. Transportation packets are identified as instruction packets or data packets. When determining the order of transfer, priority is placed on the transfer of instruction packets.
Owner:IBM CORP
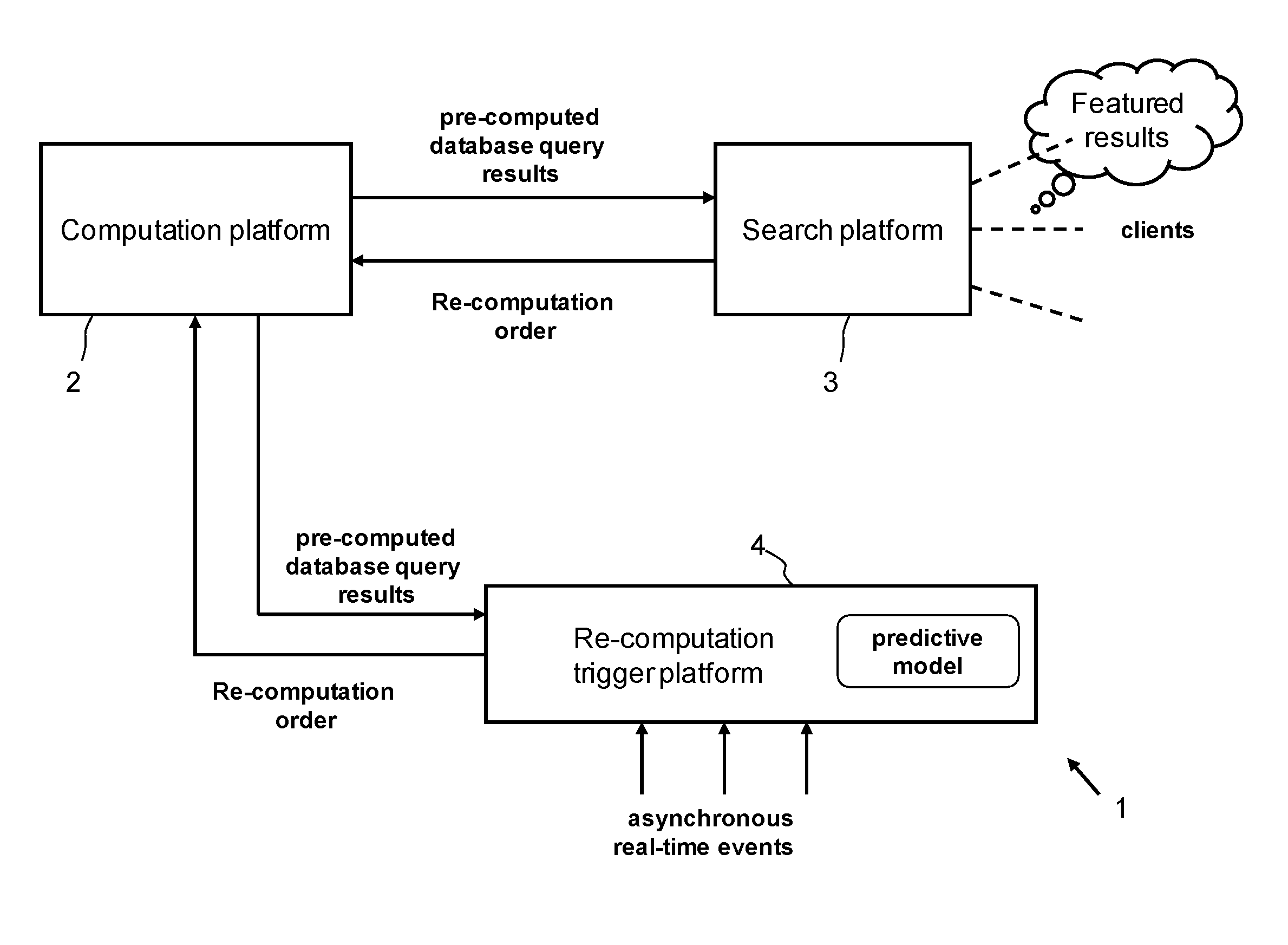
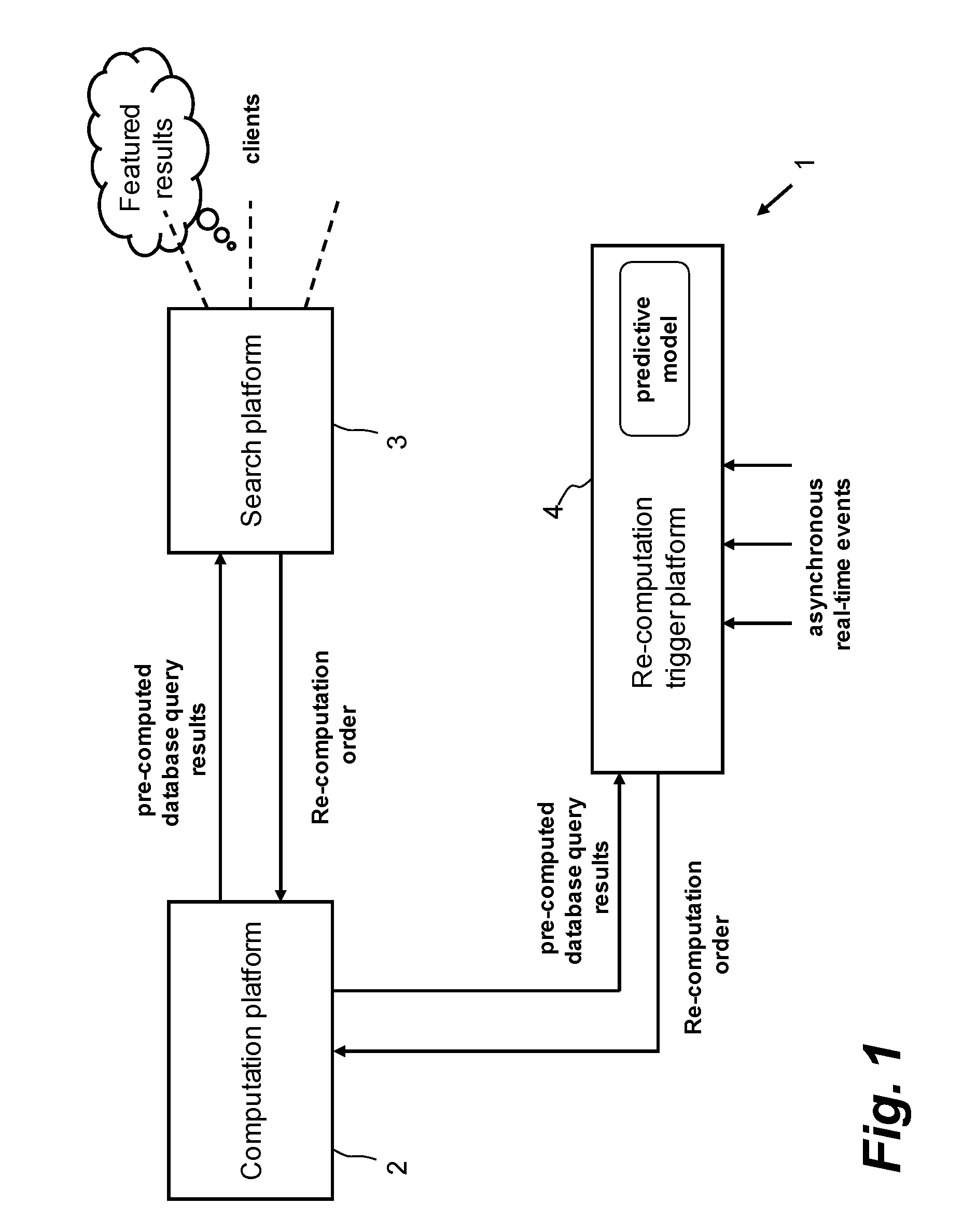
Database system using batch-oriented computation
InactiveUS20130073586A1Avoid duplicationHigh data volumeDigital data information retrievalDigital data processing detailsClient-sideTime frame
Systems, methods, and computer program for processing large volumes of data in travel and travel-related applications. A computation platform is configured to receive batch re-computation orders from the search platform, process a batch re-computation order by computing the plurality of database query results according to a batch processing schedule within a given time frame, and return the computed database query results resulting from the batch re-computation order to the search platform. Each batch re-computation order instructs the computation platform to compute a plurality of database query results. A search platform is configured to maintain the computed database query results in a memory, and to make the computed database query results available to clients connected to the search platform and to transmit the batch re-computation orders to the computation platform.
Owner:AMADEUS S
Intelligent word input method and input method system and updating method thereof
ActiveCN101013443AGuaranteed accuracyGuaranteed representationSpecial data processing applicationsInput/output processes for data processingUser inputThe Internet
The invention discloses an intelligent word-group input method in input system, including get the portfolio information between at least two basic words from the pre-set internet corpus, which including the combination relationship and adjacent same frequency of (the least two) words; generate multi-table according to the portfolio information; receive the user input encoding string, and segment the encoding string; get the combination information in the multi-table according to segmentation string, and extract the words with the corresponding relations in combination information as the candidate words. The invention can improve the first selected words hit rate of user input words, phrases, short sentences or long sentences to avoid ineffective repeat calculation process to improve the efficiency of the user input.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Interface generating method and system
ActiveCN105022615AEnsure consistencyGuaranteed flexibilitySpecific program execution arrangementsSoftware engineeringWorkload
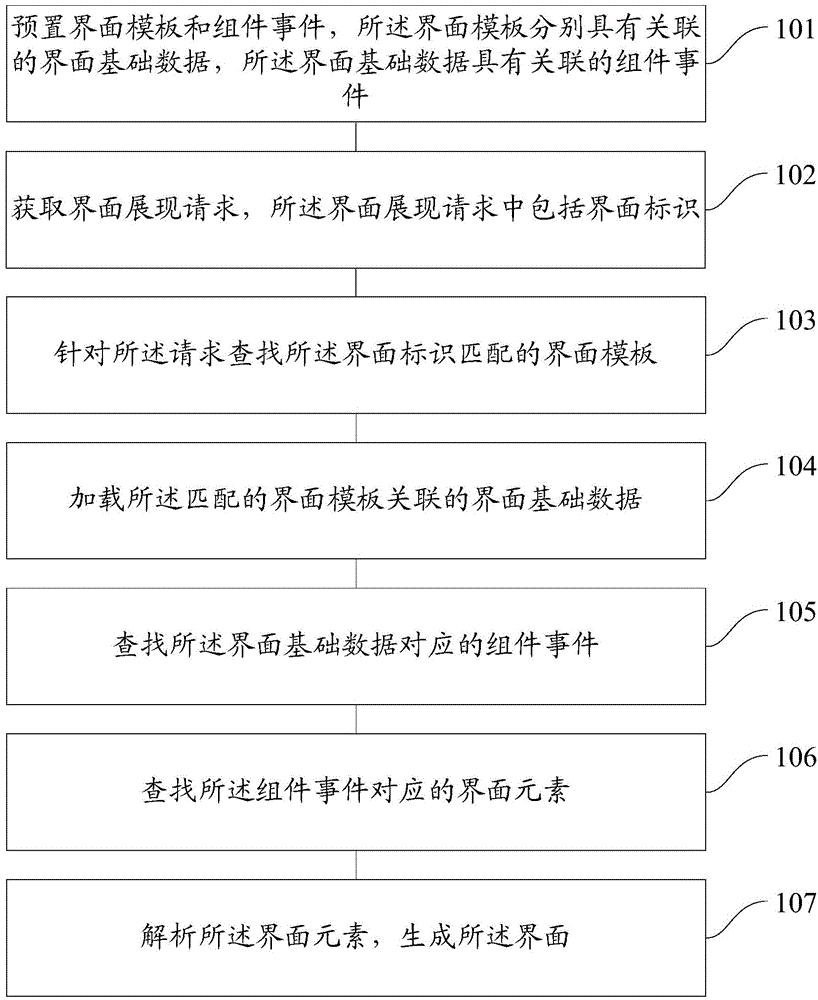
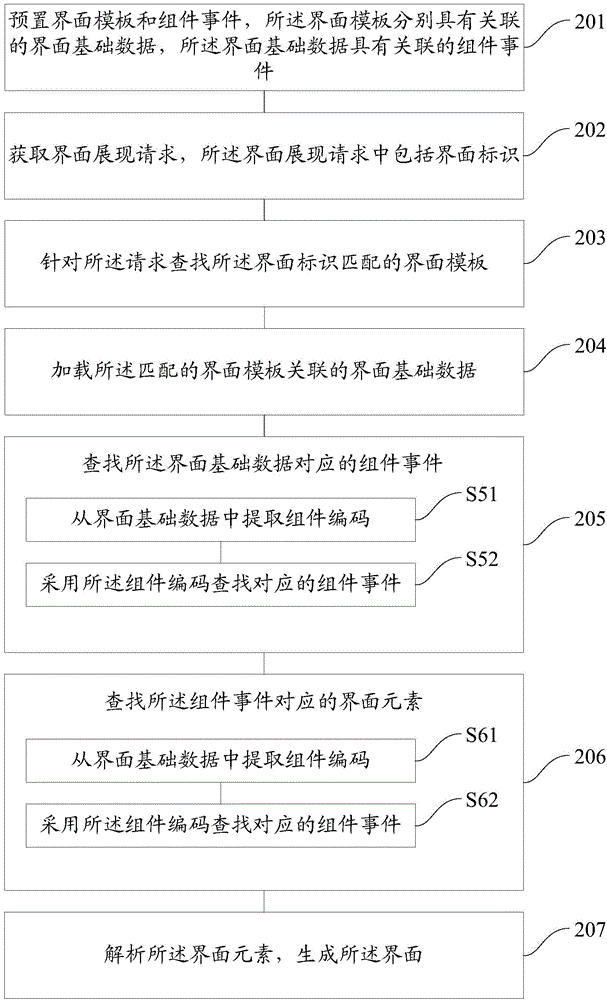
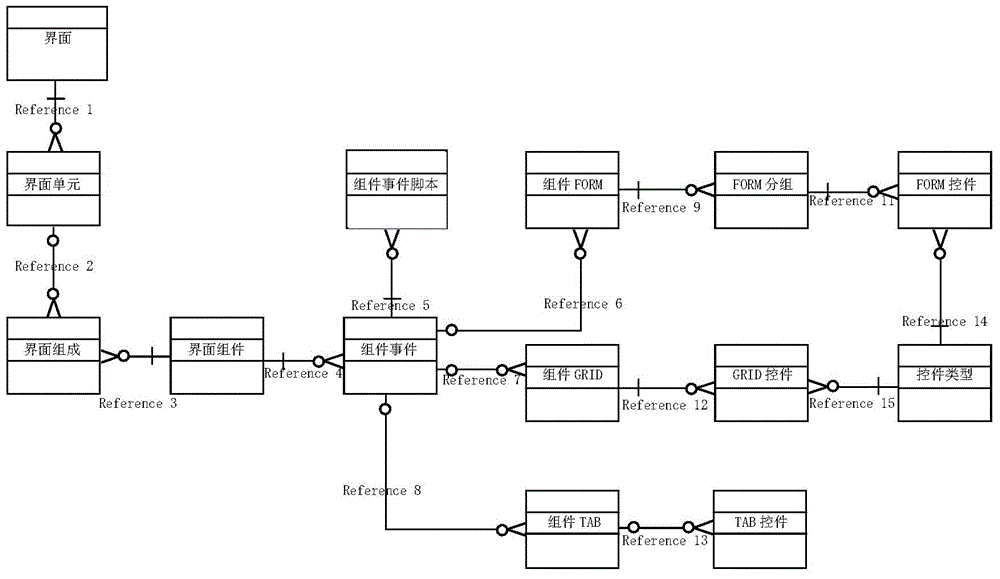
An embodiment of the present invention provides an interface generating method and system. The method comprises: presetting interface templates and component events, wherein the interface templates respectively have associated interface base data, and the interface base data has the associated component events; acquiring an interface presentation request, wherein the interface presentation request comprises an interface identifier; searching the interface template matched with the interface identifier for the request; loading the interface base data associated with the matched interface template; searching the component event corresponding to the interface base data; searching an interface element corresponding to the component event; and parsing the interface element and generating an interface. According to the interface generating method and system which are provided by the present invention, workload can be reduced, the consistency and flexibility of the interface are ensured, and the same set of service logic codes is adopted to meet different client demands, so that the complexity degree of the system is reduced, the workload of maintenance is reduced, the maintenance and extension of the system are facilitated, the error probability is reduced, the development cycle is shortened and the client demands are responded rapidly.
Owner:DATANG SOFTWARE TECH
Method and System for Preventing Unauthorized Access and Distribution of Digital Data
InactiveUS20080295174A1Prevent tampering and unauthorized accessAvoid accessMemory loss protectionError detection/correctionDigital dataMonitoring system
A system and method for preventing tampering and unauthorized access to digital data stored on a device. The system can include 1) a data store for containing digital data to be protected and a listing of processes permitted to access the digital data, 2) a filter driver for intercepting a request issued from a process to access the digital data, 3) a central processor, in communication with the data store, upon receipt of a notification of the intercepted request from the filter driver, deciding to grant or deny the request by determining whether the process issuing the request is on the listing of processes permitted to access the digital data, and 4) a monitor process for monitoring one or more software components of the system including the central processor, filter driver, and data store, and for identifying and preventing any unauthorized processes from accessing and tampering with the software components of the system.
Owner:FAHMY ANDREA ROBINSON +2
Sewage purifier and sewage purification method
ActiveCN101928069AIncrease reproductive rateImprove purification effectSustainable biological treatmentBiological water/sewage treatmentPurification methodsMetal salts
The invention discloses a sewage purifier, which comprises polyhydroxyalkanoate, diatomite, humic acid, a bioactivator, inorganic metal salt and other substances. The invention also discloses a sewage purification method by utilizing the sewage purifier. A completely biodegradable material polyhydroxyalkanoate is used as a sustained material of the bioactivator, and the completely biodegradable material is slowly degraded and releases the bioactivator so as to realize the long-term high-efficiency purification function of the bioactivator; and by combining the effects of aquatic plants, phosphorus, nitrogen, polycyclic aromatic hydrocarbon and heavy metals in the sewage are purified and treated, so the sewage purifier has better sewage treatment effect.
Owner:SHENZHEN ECOMANN BIOTECH
Trouble correlation analytic system and method
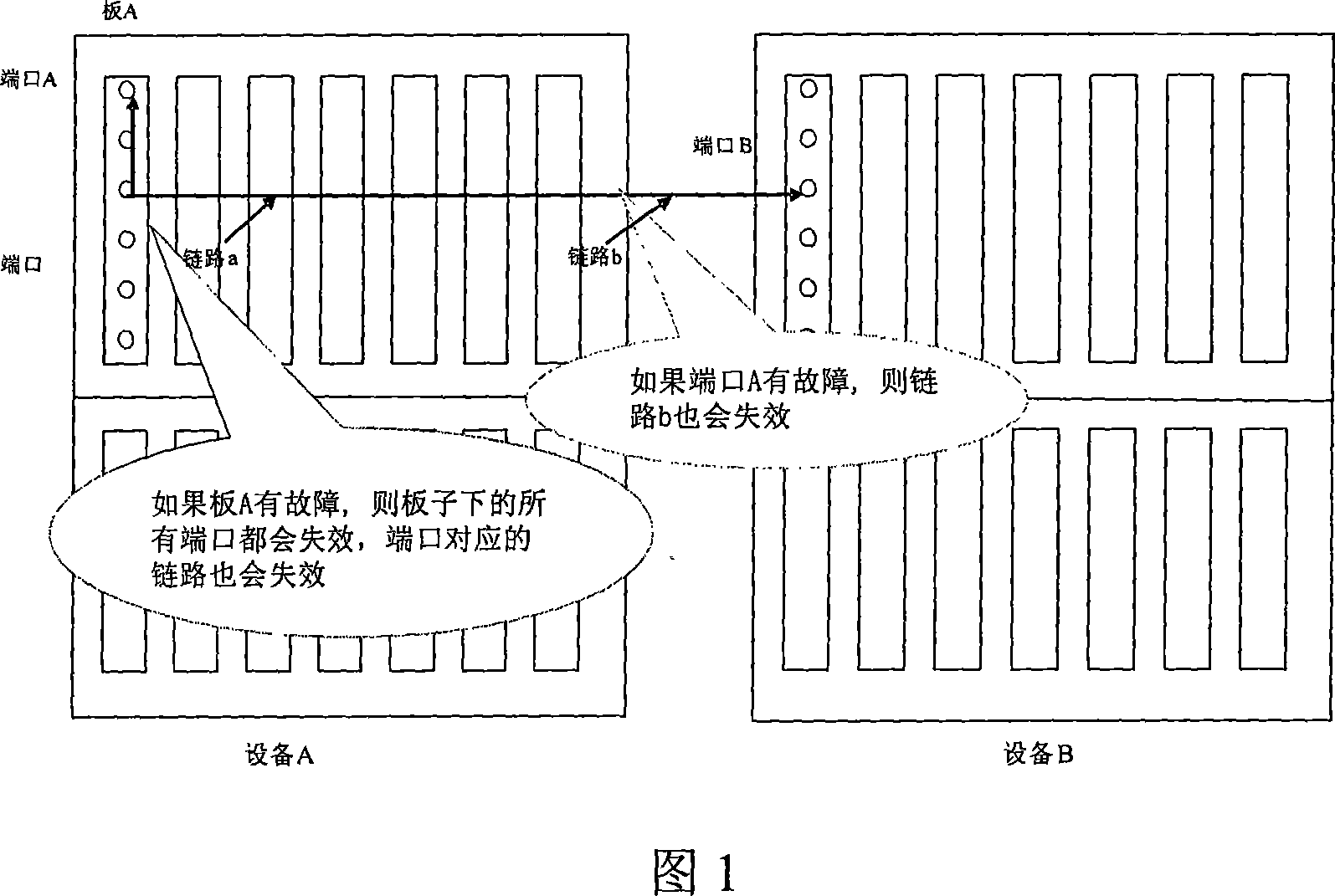
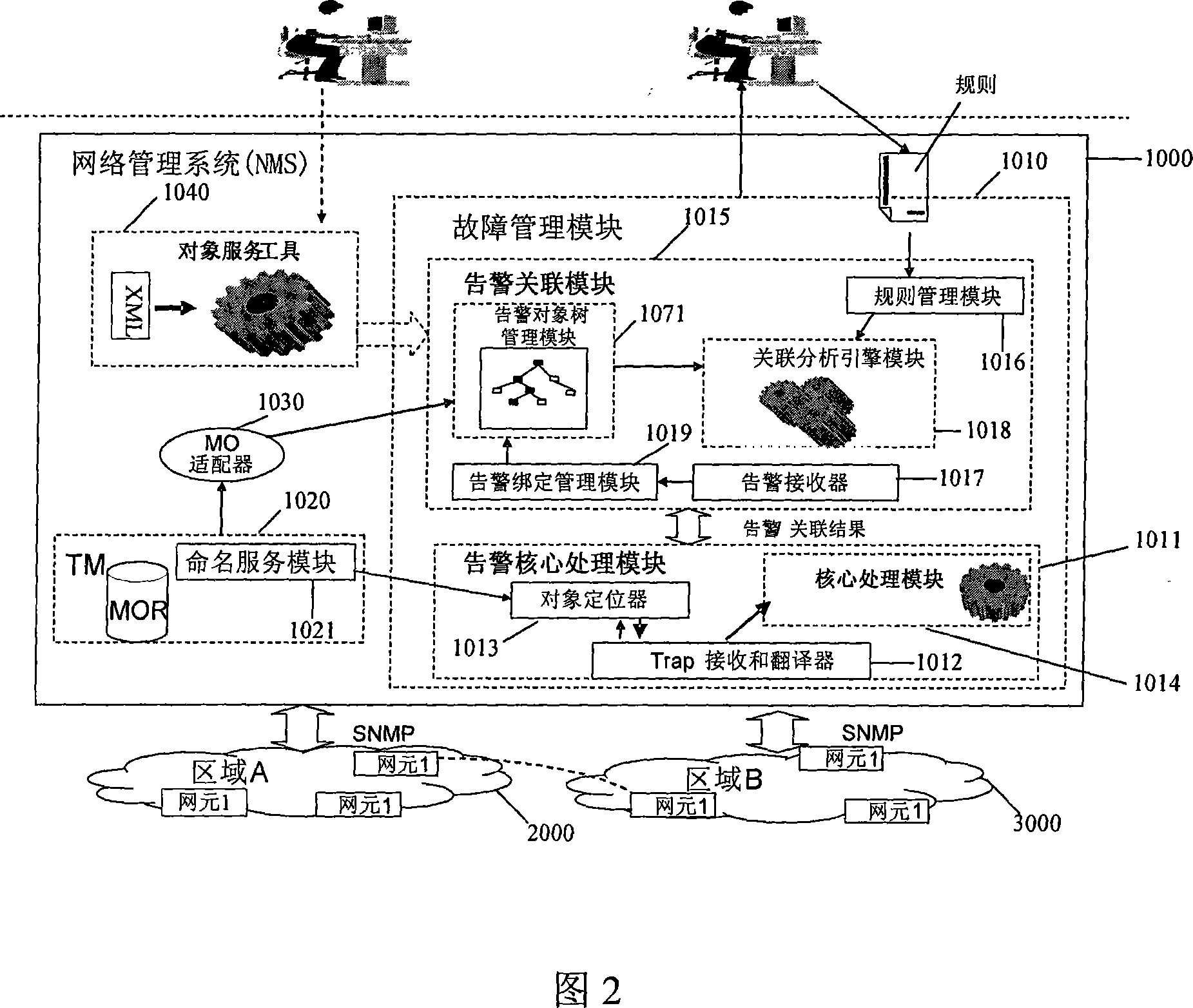
InactiveCN101022366AIntuitive and efficient managementAvoid duplicationData switching networksCorrelation analysisNetwork management
A fault correlation analysis system comprises fault management module for carrying out fault management and network topology management module for maintaining managed network. It is featured as forming said fault management module by warning kernel treatment module for making kernel treatment on fault warning and warning correlation module for finding out fault reason by carrying out correlation analysis based on specific logic relation according to obtained warning.
Owner:UTSTARCOM TELECOM CO LTD
Method and apparatus for resource provisioning
InactiveUS20100100878A1Avoid duplicationAvoid repetitionTransmissionSoftware simulation/interpretation/emulationNPIVComputer device
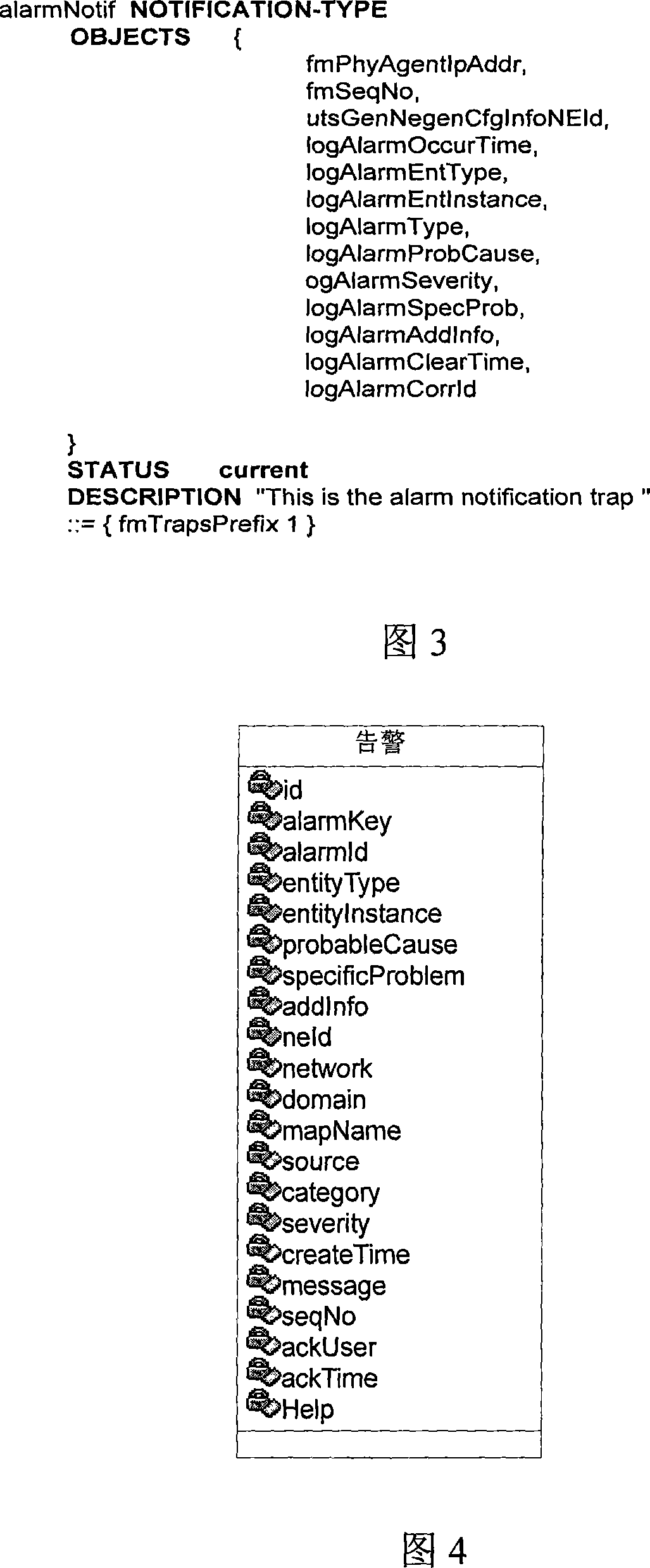
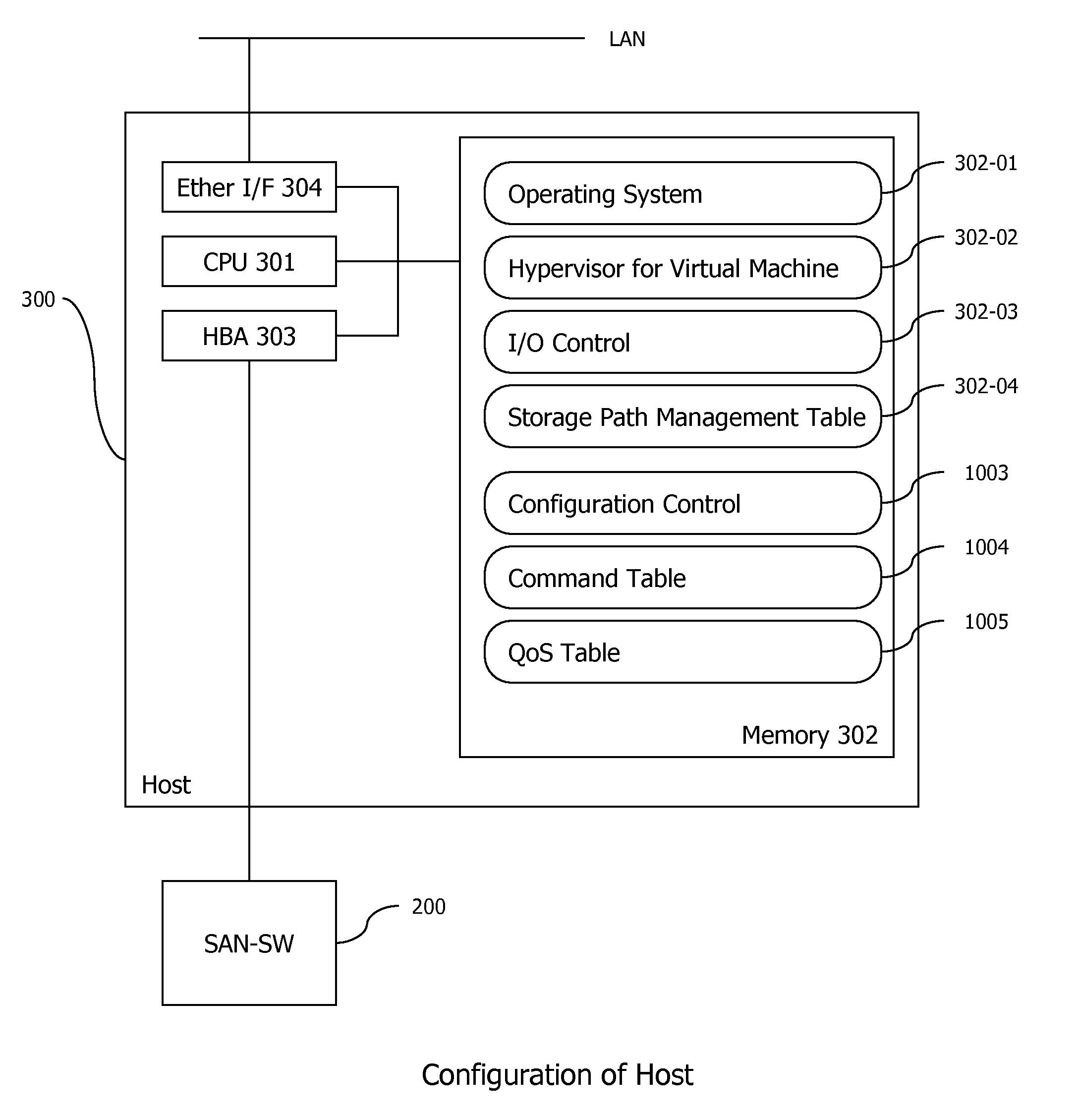
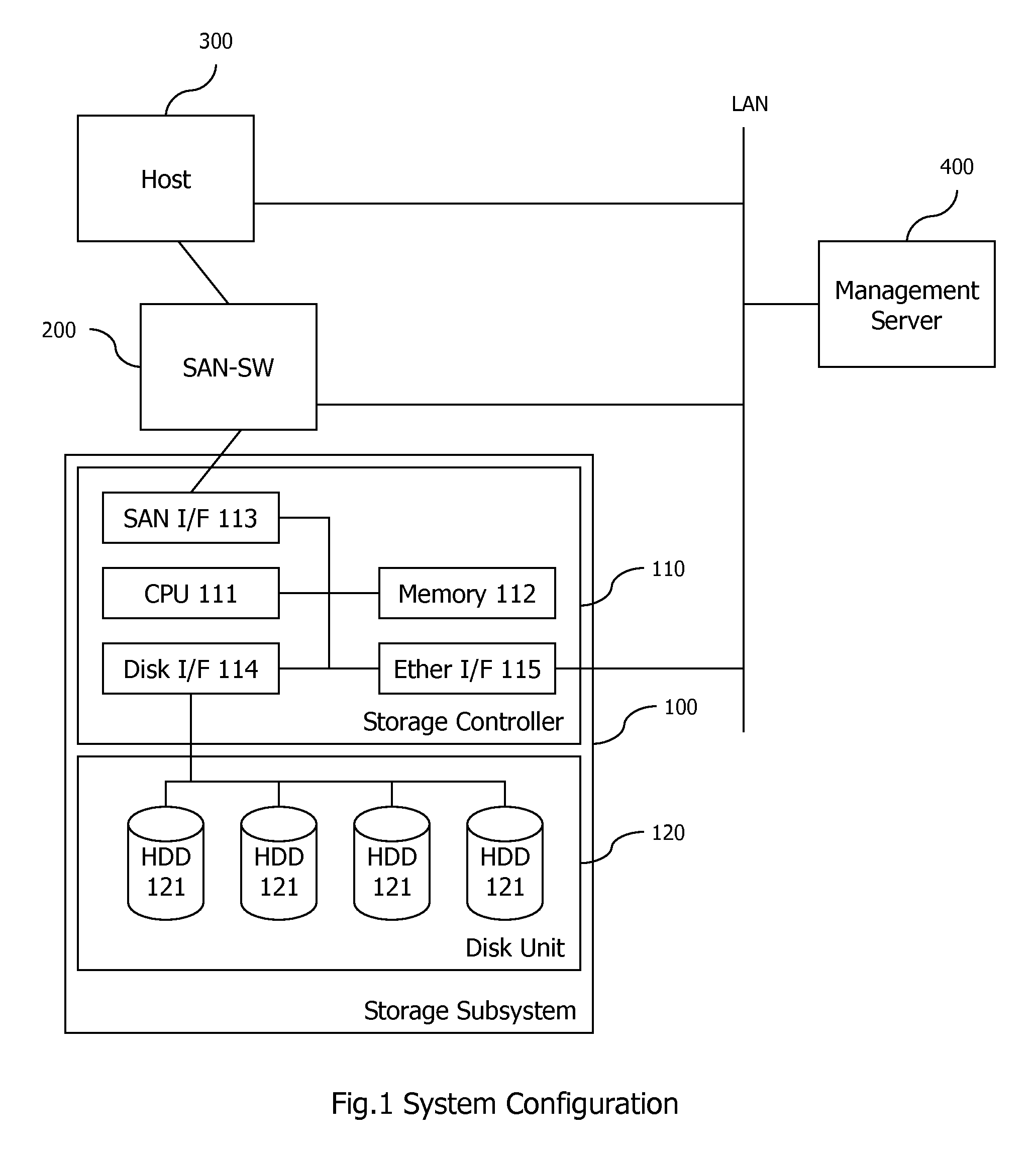
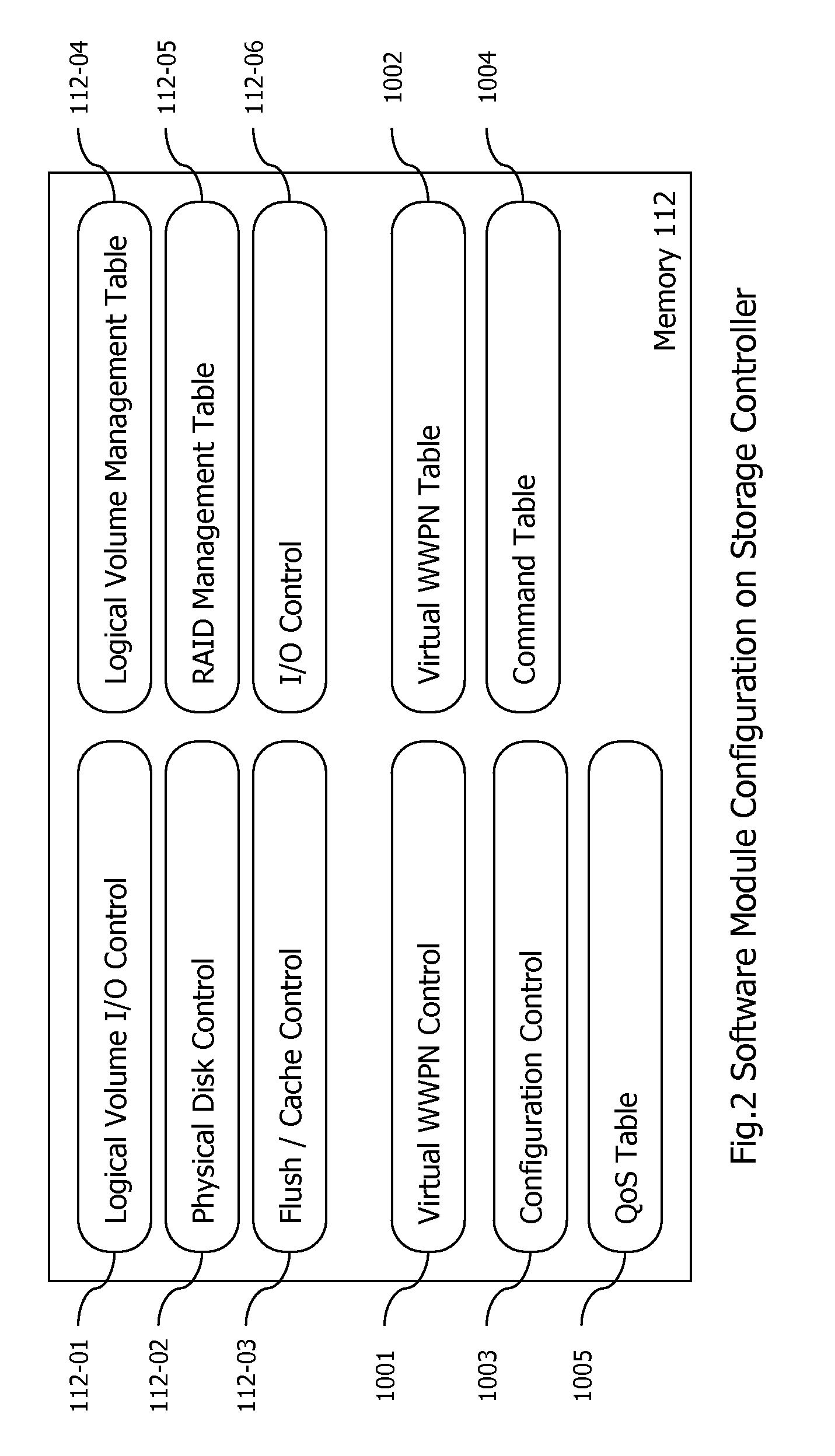
Embodiments of the invention provide a method and apparatus for resource provisioning for a new virtual machine to be provided in a computer device. In one embodiment, at least one storage subsystem, the computer device, and a storage management server are connected via a network. A unique virtual port name for the new virtual machine is created by one of a first storage subsystem of the at least one storage subsystem or the storage management server. A volume for the new virtual machine is provided in the first storage subsystem. The first storage subsystem includes a unique port name for a port through which the volume for the new virtual machine has I / O connection via the network. The unique virtual port name is assigned to the new virtual machine in the computer device under NPIV (N_Port ID Virtualization).
Owner:HITACHI LTD
Method for improving page layout display performance of embedded browser
InactiveCN101221580AImprove the display effectImprove hit rateMemory adressing/allocation/relocationSpecial data processing applicationsUniform resource locatorComputer science
The invention discloses a method for improving page display performance of an embedded browser. The method comprises the following steps that: when a picture needs to be displayed in the page, whether a uniform resource locator (URL), which the picture corresponds to, exists in a memory buffer area is inquired; if the uniform resource locator exists, the data of the picture is called to display to picture; or the data of the picture is downloaded and decoded, then the URL that the picture corresponds to and the decoded data of the picture are stored in the memory buffer area, finally the picture is displayed. The method of the invention can remarkably improve the page display performance of the embedded browser.
Owner:ZTE CORP
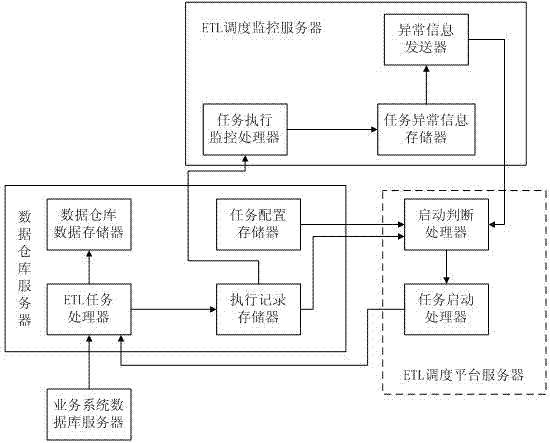
ETL (Extraction-Transformation-Loading) dispatching system and method for error-correction restarting and automatic-judgment starting
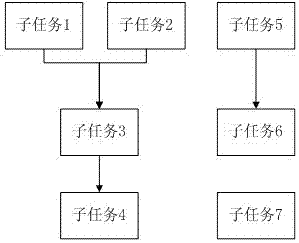
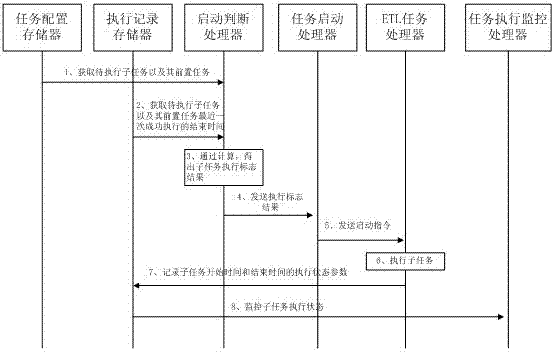
ActiveCN103034554AEasy to troubleshootReduce rescheduling task timeProgram initiation/switchingFault responseData warehouseDatabase server
The invention discloses an ETL (Extraction-Transformation-Loading) dispatching system and method for error-correction restarting and automatic-judgment starting. The ETL dispatching system structurally comprises a business system database server, a data warehouse server, an ETL dispatching and monitoring server and an ETL dispatching platform server. The ETL dispatching method disclosed by the invention comprises the following steps of: dividing a data warehouse ETL task into a plurality of subject tasks, wherein each subject task comprises a plurality of sub-tasks; configuring information according to a preset executing sequence and automatically judging the end time for successfully executing the pre-posed associated sub-tasks; executing follow-up sub-tasks, stopping the execution of the associated follow-up sub-tasks according to the sub-task correlation after the execution of the sub-tasks has exception faults, and recording the exceptional sub-tasks; and only processing the exceptional sub-tasks and the associated follow-up sub-tasks in a way of automatically restarting for many times. According to the ETL dispatching system and method disclosed by the invention, the problem that the follow-up sub-tasks are continuously executed when the pre-posed sub-tasks have faults in the ETL task dispatching is solved; the task executing efficiency is improved; the manual intervention is reduced; and the operation loss is reduced.
Owner:FOCUS TECH
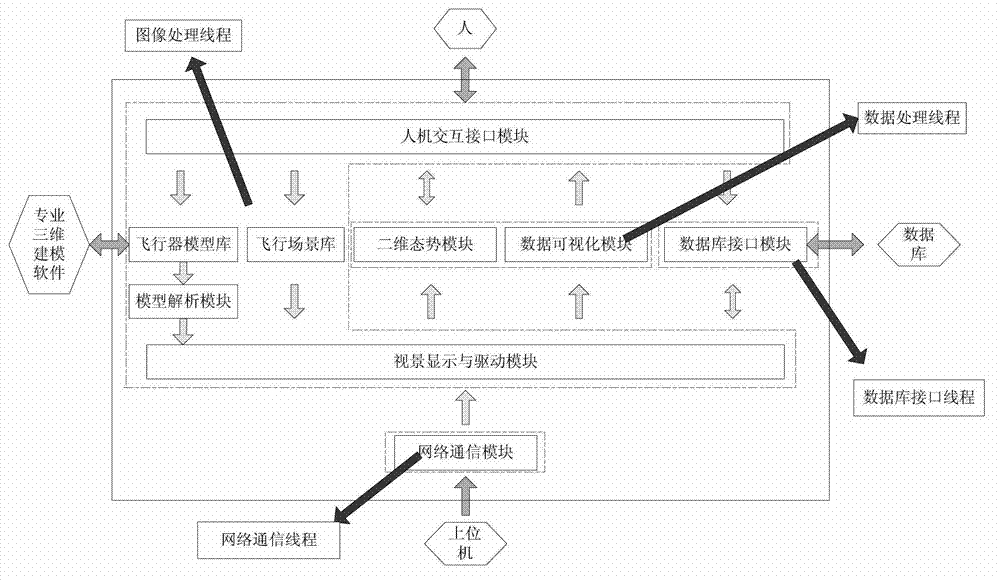
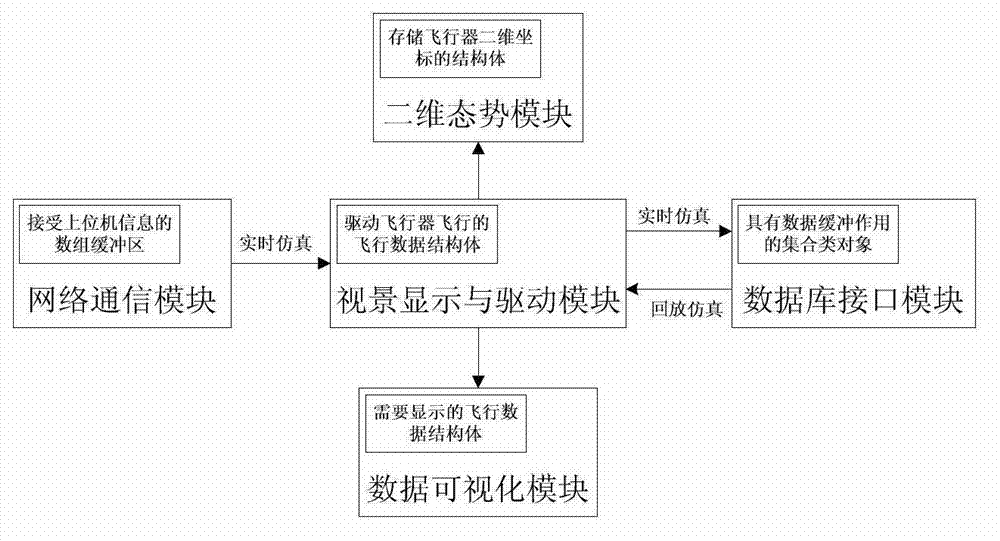
Typical aircraft visual simulation system
ActiveCN103093047ARealize the loadAchieve intelligenceSpecial data processing applicationsDatabase interfaceNetwork communication
The invention relates to the technical field of computer simulation. In order to design a visual simulation system applicable for typical aircrafts including hypersonic aerocrafts, unmanned planes and satellites, analysis for flight data by researchers includes that pure digital information is converted into three-dimensional image-based information which can be better understood by people through posture changes of virtual aircrafts. Visual simulation can performed on all of the hypersonic aerocrafts, the unmanned planes and the satellites, and the purpose that a same system is shared by a plurality of the aircrafts is achieved. Single-computer simulation or multiple-computer group control simulation can be performed. The overlapping development problem of the visual system is solved. The technical scheme includes that the typical aircraft visual simulation system comprises an aircraft model base module, a flight scene base module, a network communication module, a visual display and drive module, a data base interface module, a data visualization module, a two-dimensional state module, a model parse module and a man-machine interactive interface module. The typical aircraft visual simulation system is mainly applied to computer flight simulation.
Owner:TIANJIN UNIV
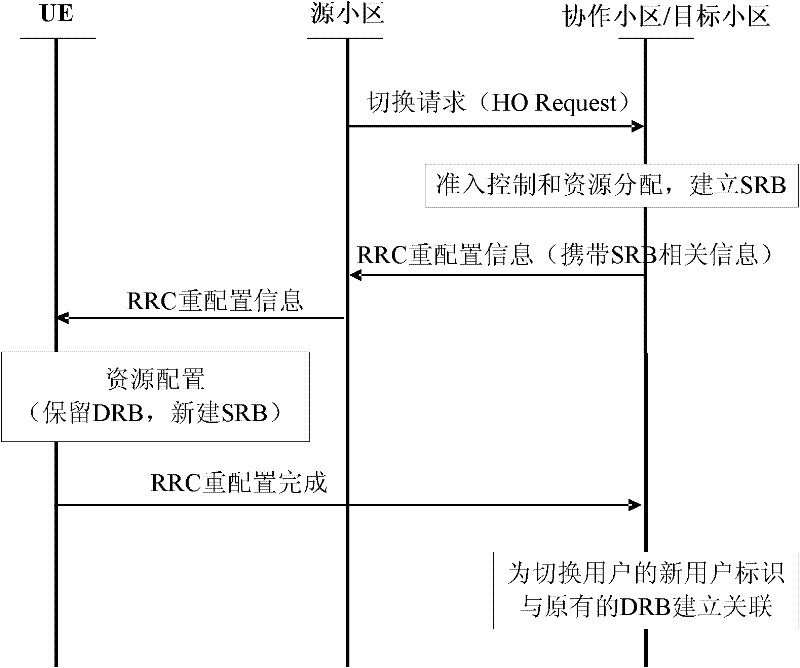
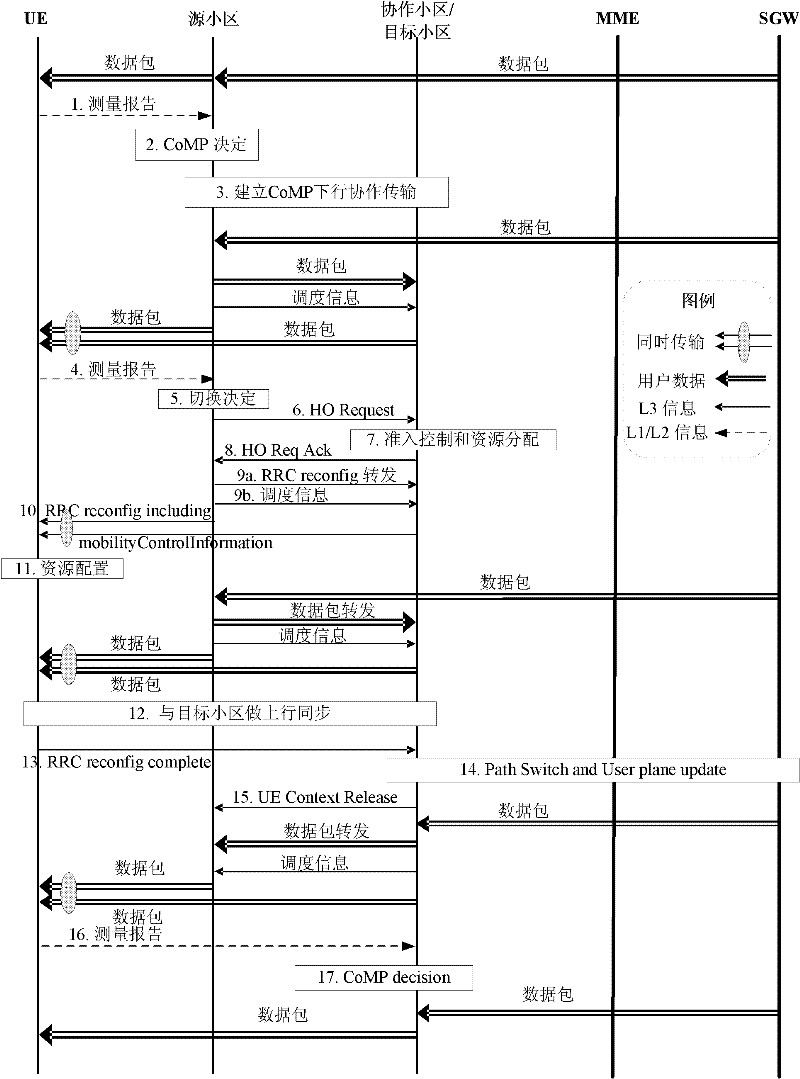
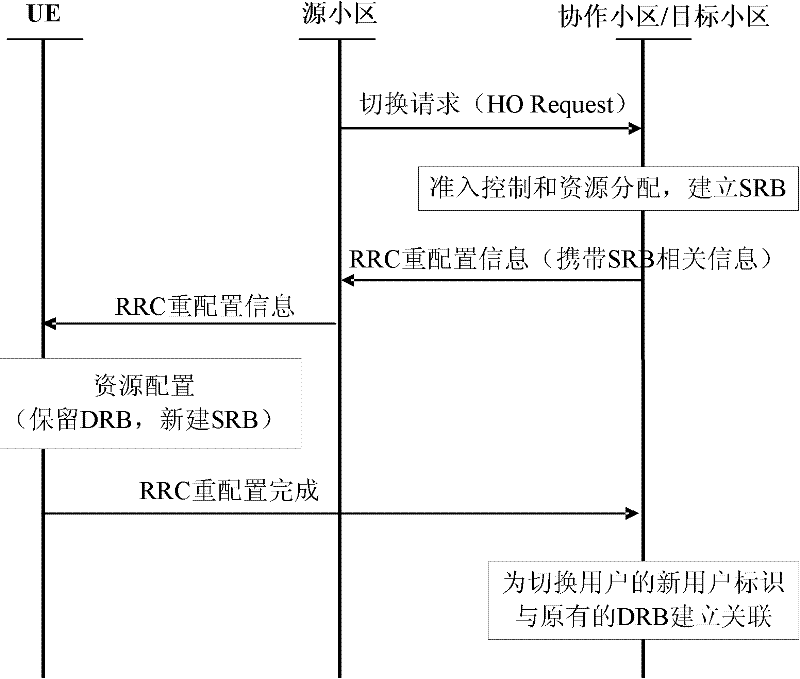
Radio communication system and method of resource configuration optimization during switching in coordination set
ActiveCN102457970AAvoid duplicationImprove efficiencyConnection managementConfiguration optimizationData radio bearer
The invention discloses a radio communication system and a method of resource configuration optimization during switching in a coordination set in the system, used for carrying out resource configuration optimization during switching in the coordination set. In the process of switching in a joint processing coordination set, when a target cell learns that a switched user is a coordinated user, the switched user is directly judged to be accessed and only a signalling radio bearer is established; after finishing the resource configuration, the target cell generates a radio resource control connection reconfiguration message comprising the signalling radio bearer and transmits the message to user equipment through a source cell; the user equipment carries out resource configuration, maintains a data radio bearer established in the coordinated process and establishes the signalling radio bearer. According to the invention, unnecessary steps are omitted, operations of repeated establishment and resource deletion are avoided and the efficiency of a terminal and a base station is improved.
Owner:XUZHOU JIANGMEI TECH
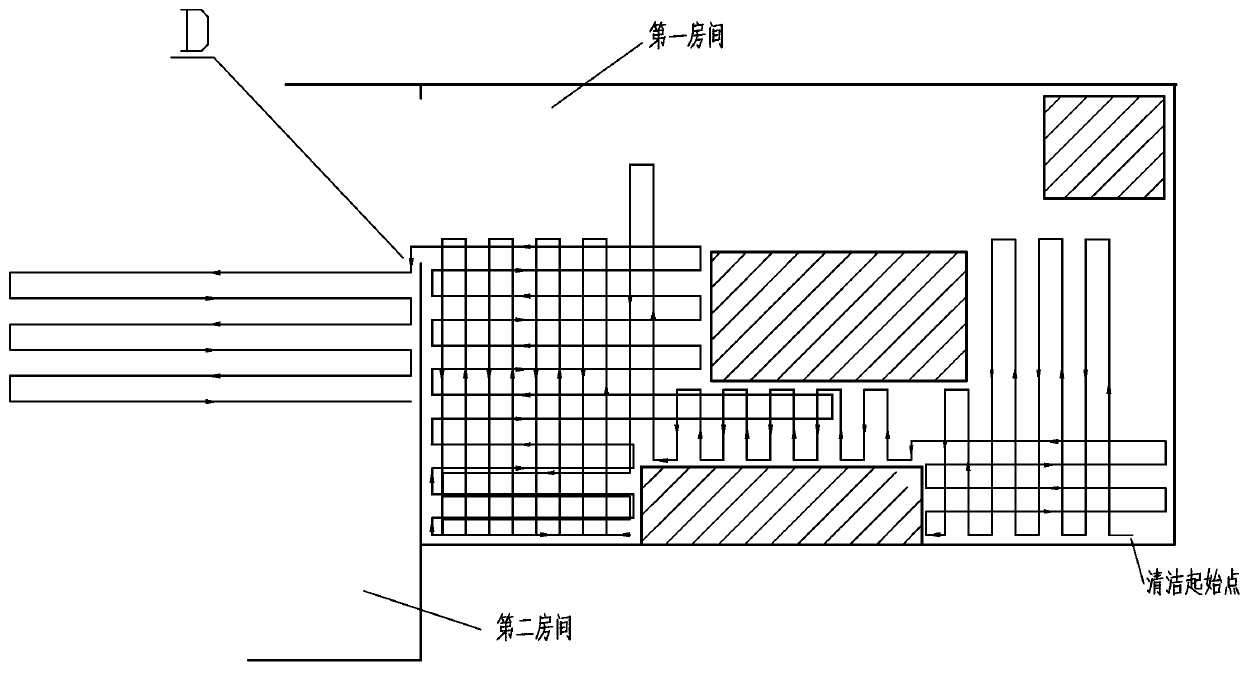
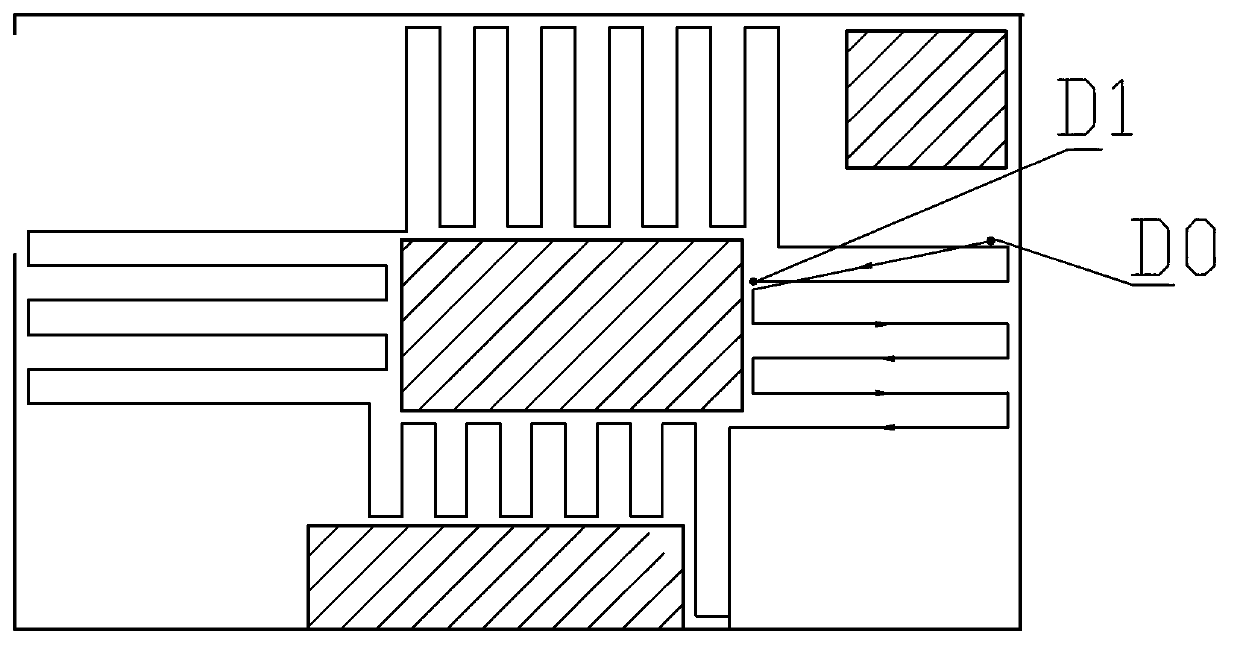
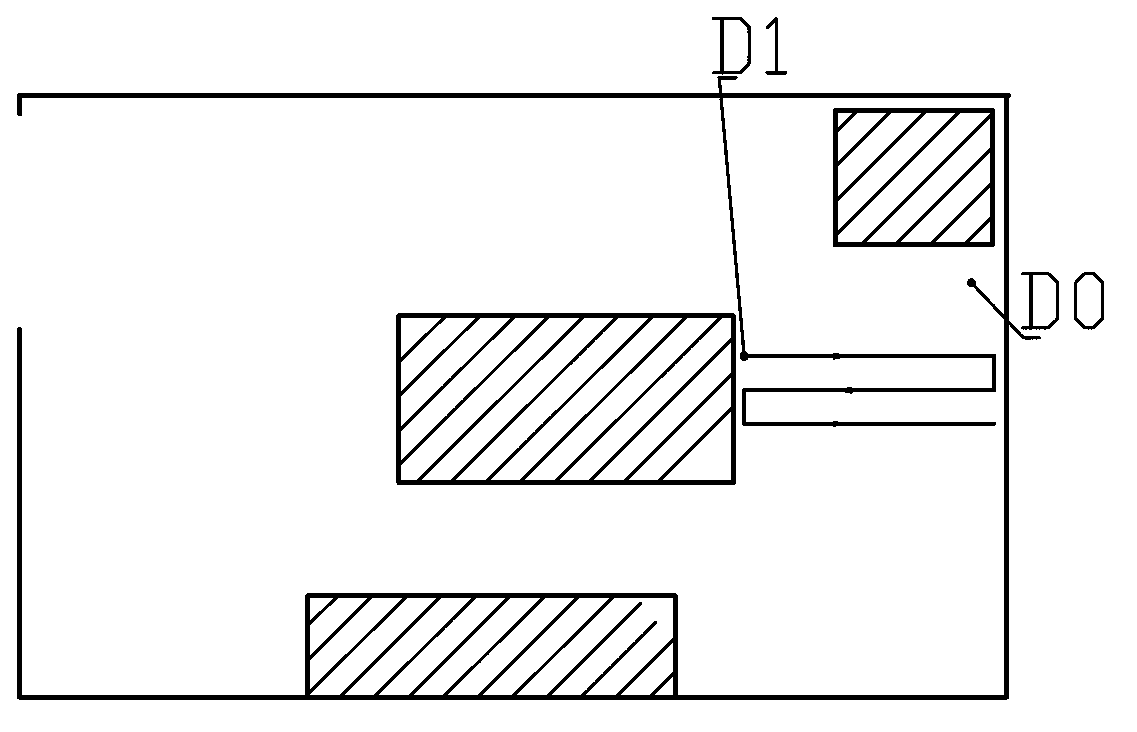
Cleaning method using cleaning robot by means of edgewise navigating and intro-expanding
ActiveCN103099586AAvoid missed or repeated cleaningsImprove cleaning efficiencyAutomatic obstacle detectionTravelling automatic controlStructural engineeringMechanical engineering
The invention aims at providing a cleaning method by using a cleaning robot, which can traverse regions which need to be cleaned in a plurality of rooms, and can reduce a repeated forwarding route, i.e., a cleaning method using the cleaning robot by means of edgewise navigating and intro-expanding. The cleaning robot advances along the outer wall of a wall body of the room, and the cleaning robot leaves away from the outer wall of the wall body for a plurality of times to move to the direction which is far away from the outer wall of the wall body to clean the ground. After the cleaning robot leaves away from the outer wall of the wall body at a certain distance or encounters a barrier every time, the cleaning robot firstly rotates for a preset angle, advances at a section of preset distance, and returns to the outer wall of the wall body, so that the traversing and the cleaning of the region which needs to be cleaned can be realized.
Owner:重庆艾亿佳智能技术有限公司
Organization and management and using method and system for cloud manufacturing service
InactiveCN105635283AEffective organizational managementActive service registrationTransmissionResource utilizationManagement efficiency
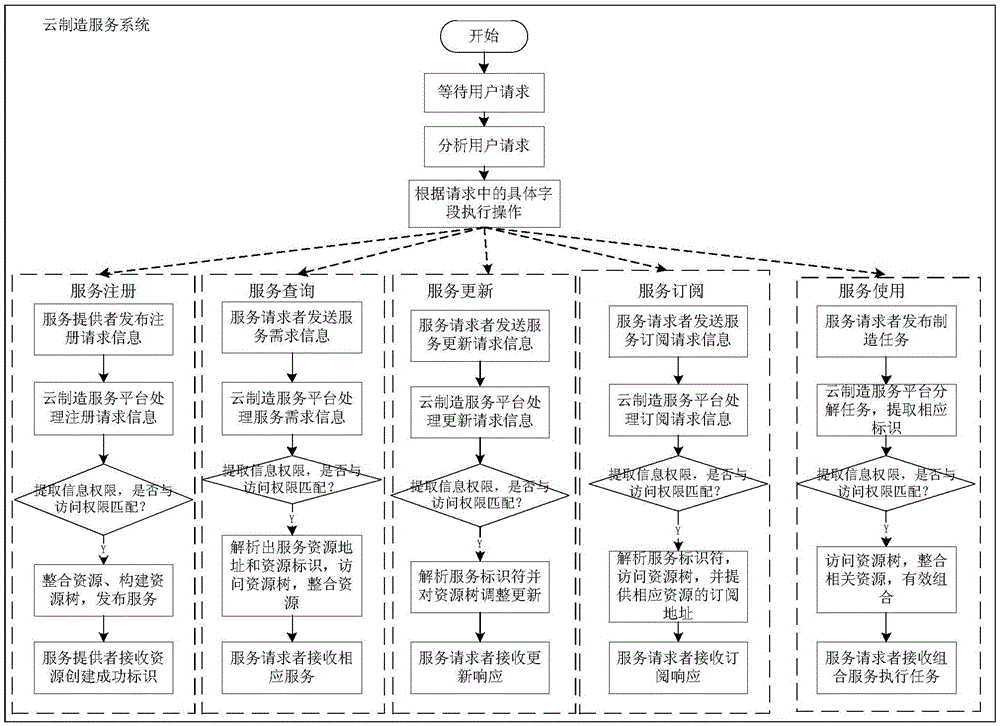
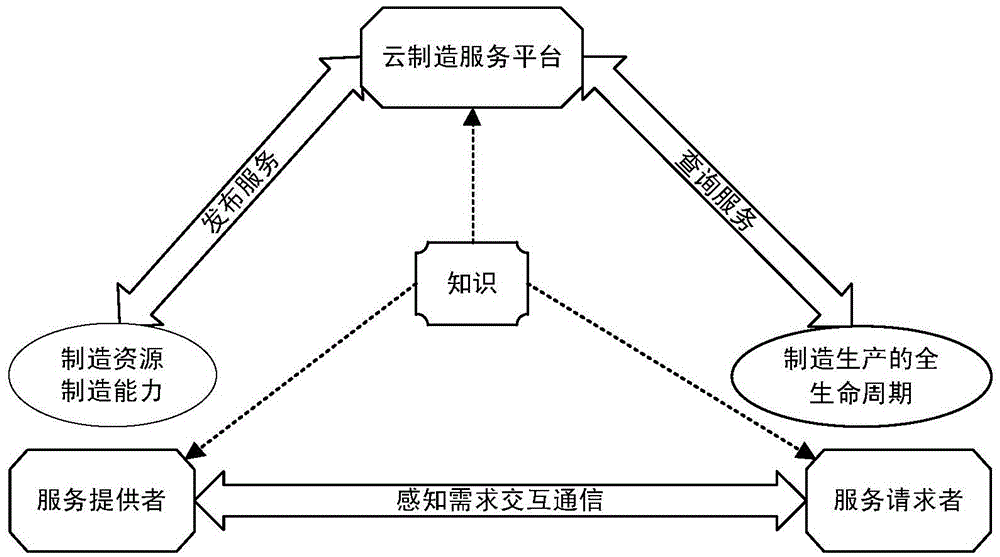
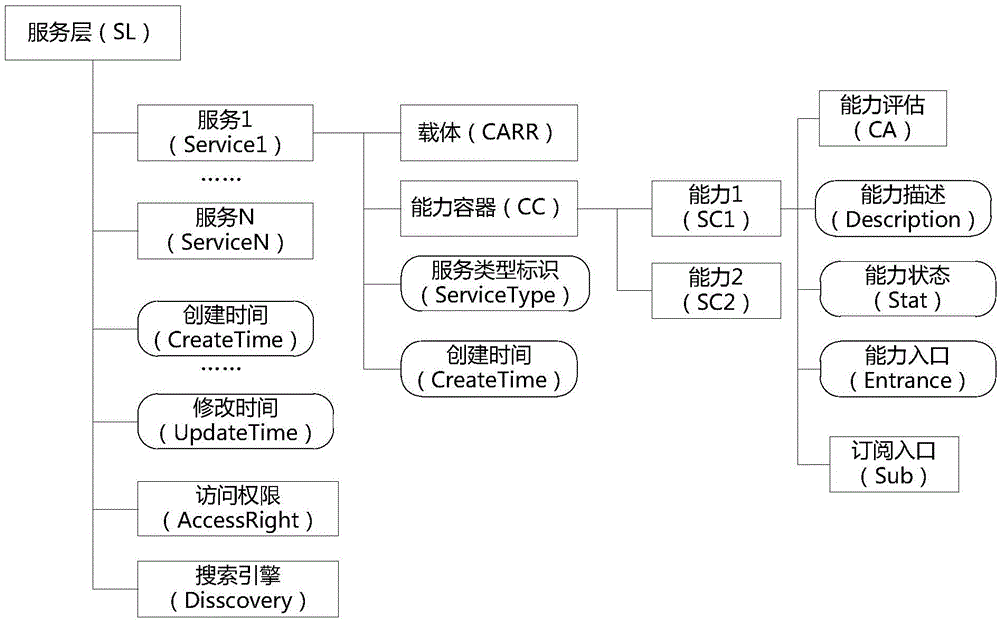
The invention discloses an organization and management and using method and system for a cloud manufacturing service. According to the method, on the basis of the internet of things technology and the cloud computing technology, interaction among a service provider, a service requester, and a cloud manufacturing service platform is described by using correlated network technologies like an XML language or an HTTP protocol; and modeling is carried out on the service based on description of the network technologies and a resource tree is constructed, so that the management efficiency and the resource utilization rate are effectively improved. Therefore, high-efficiency sharing of the resources and capabilities is realized; repeated building of the same kind of manufacturing resources and capability can be avoided; and the manufacturing energy and cost can be effectively saved. In a cloud manufacturing service system, a server is set to be in a user request waiting state; when a user request is received, the user request is analyzed; and corresponding operations of service registration, querying, updating, subscription, and usage are executed based on specific fields in the request.
Owner:NANJING UNIV OF POSTS & TELECOMM
Operation recording and playback method for interactive software
InactiveCN102799428AImprove space utilizationImprove space efficiencySpecific program execution arrangementsInteractive softwareGraphics
The invention relates to an operation recording and playback method for interactive software. The method comprises the following steps of: 1) recording playback semantic information operation on the interactive software when a user starts executing an operation task, and setting correspondence rules among user operation events, graphical user interface (GUI) events and operation types; 2) recording all operation parameters for finishing the task by the user, and sequencing according to the time to acquire a playback operation sequence; 3) after the user finishes the task, determining GUI object characteristic attributes according to a characteristic similarity technology, and determining whether objects capable of executing operation playback exist in the playback operation sequence or not under different user environments based on a characteristic threshold value; and 4) performing playback on the operation for the objects capable of executing operation playback according to the correspondence rules between the operation types and the events. Playback semantic records are extracted, and time semantics are extracted to form the reusable operation sequence, so that the method has high space utilization rate and time efficiency.
Owner:PEKING UNIV
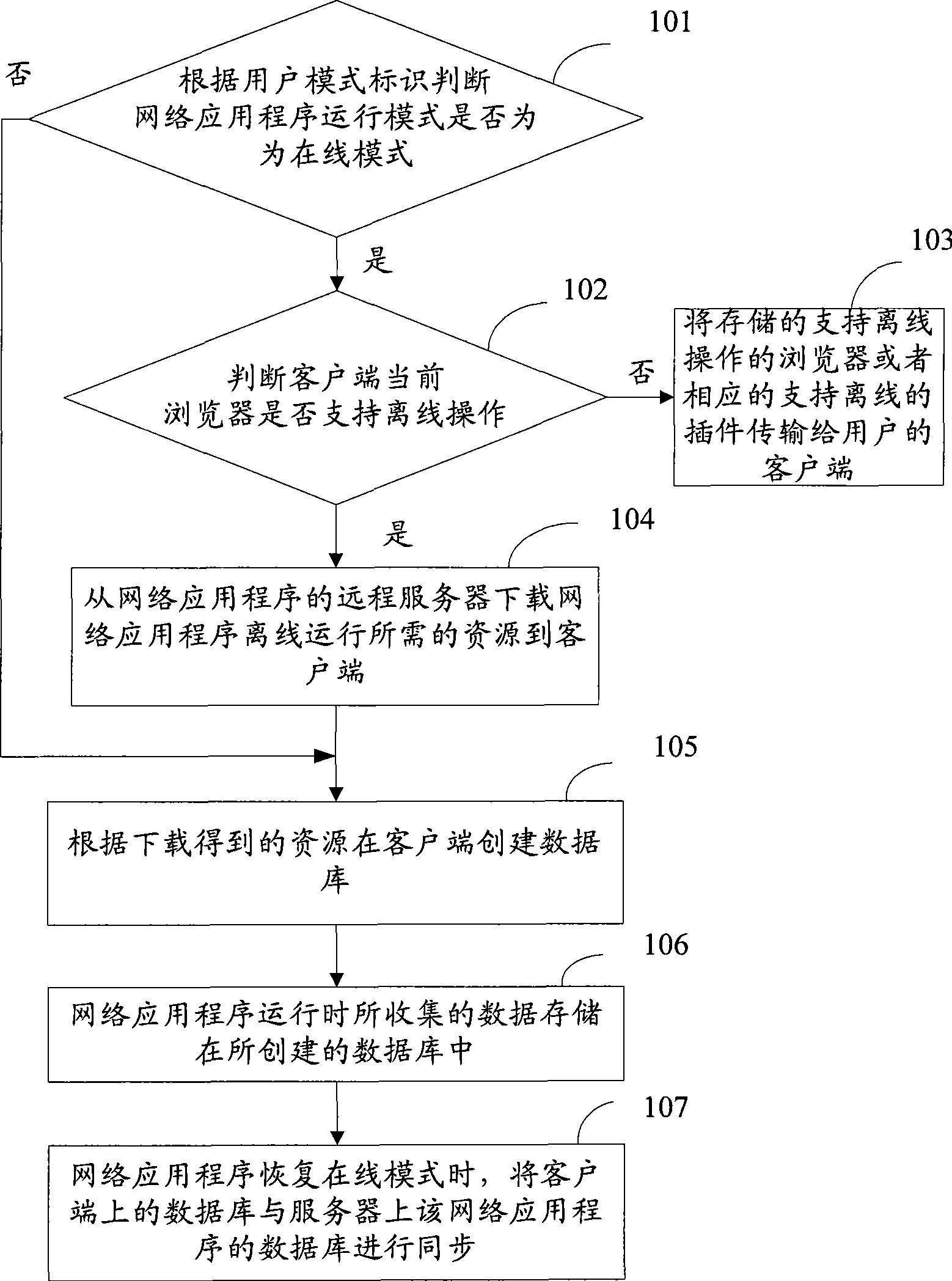
Off-line data collecting method for network application program
InactiveCN101388911ARealize data collectionEasy to operateMultiprogramming arrangementsTransmissionData acquisitionApplication software
The invention provides a network application program off line data acquisition method, which comprises: A. the server transfers the resources needed by the network application program operation under off line mode to the client end; B. the client end creates a data base according to the received resources; C. accessing the network application program under off line mode through the client end browser; D. when the network application program returns to on line mode, synchronizing the data base on the client end the data base of the network application program on the server. The invention can realize data acquisition under the network application program off line mode without installing any extra off line tool software.
Owner:YONYOU NETWORK TECH
Supply chain management system of one-stop integrated logistic service
InactiveCN103366263ASimple and efficient process managementReal-time alert responseLogisticsInformatizationLogistics management
The invention provides a supply chain management system of one-stop integrated logistic service. The supply chain management system comprises a customer management module, a customs declaration and inspection module, a logistic distribution module, a storage module, a process module and a balance account module, wherein the customer management module is used for carrying out customer management operation to customer service staff; the customs declaration and inspection module is used for carrying out customs clearance operation on enterprise import and export practices; the logistic distribution module is used for carrying out the operation of dispatch, order supervision, order acknowledgement and the like for transportation business; the storage module is used for carrying out warehouse in / out and inventory management of cargos; the process module is used for carrying out real-time management and control, reminding and early warning on the processes of all businesses; and the balance account module is used for carrying out charge balance account for all the businesses. The supply chain management system is not only a set of informatization management software of a third logistic enterprise, but also a set of supply chain solution scheme providing the one-stop integrated logistic service for a cargo owner enterprise; the supervisory control and management are realized for the whole supply chain links; the execution performance of the whole supply chain is improved; the cost is reduced; and the supply chain value is created.
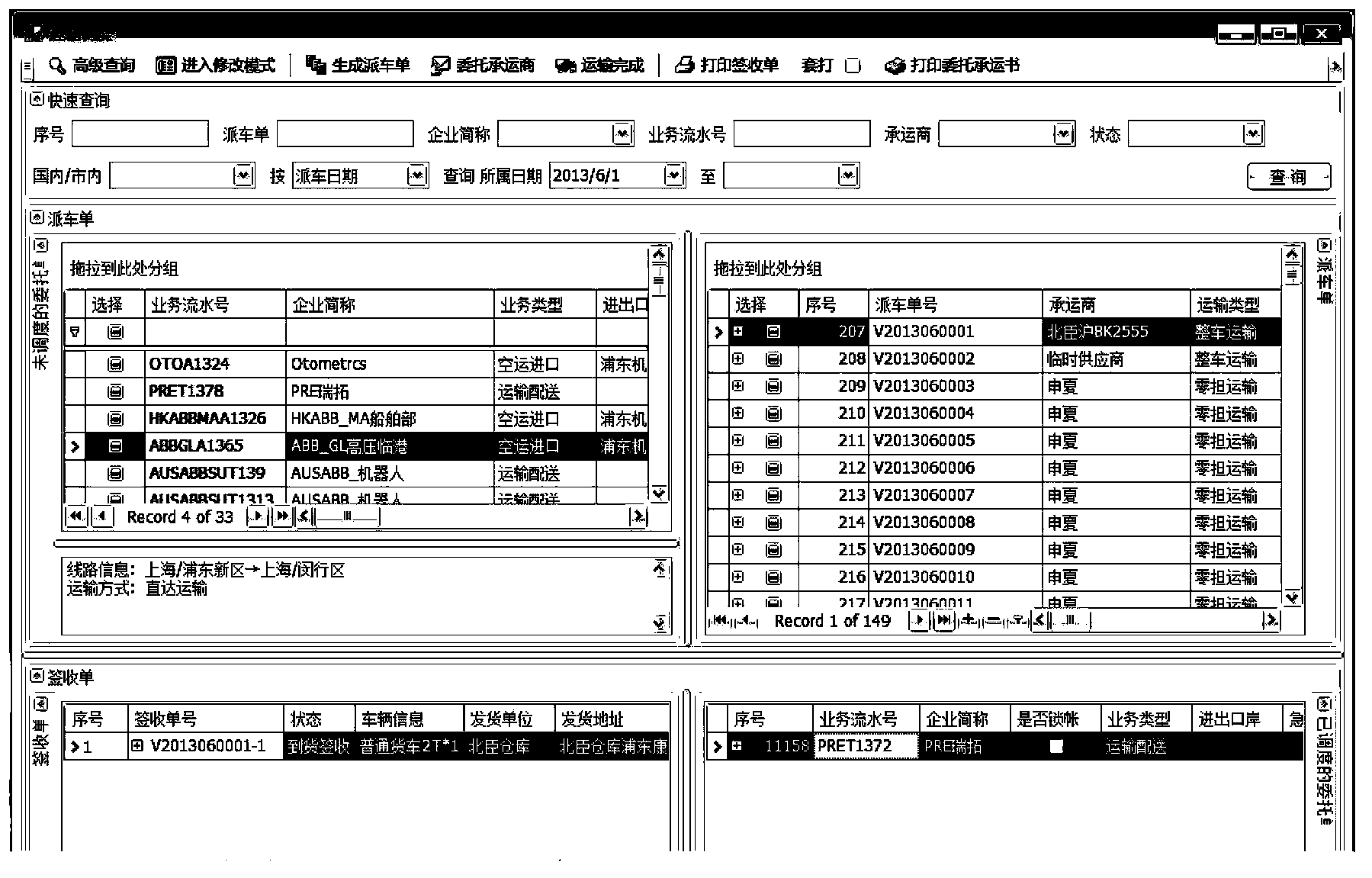
Owner:SHANGHAI BEICHEN IND
Transmission tower modal parameter identification method based on improved subspace algorithm
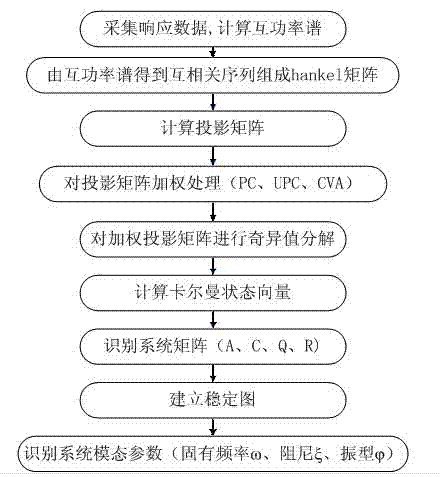
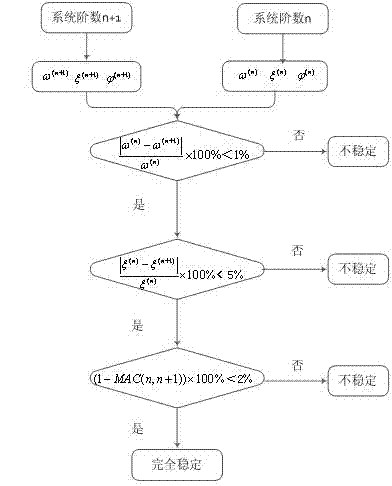
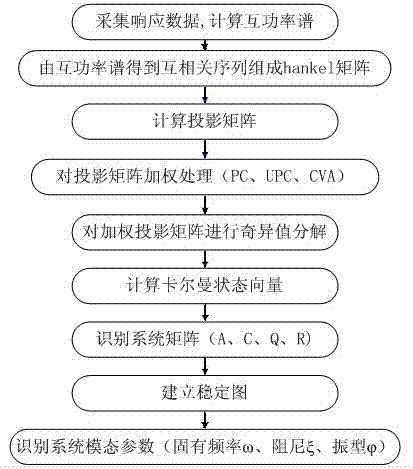
ActiveCN102520071ASolve the ordering problemAvoid Fitting ErrorsAnalysing solids using sonic/ultrasonic/infrasonic wavesProcessing detected response signalTransmission towerPeak value
The invention discloses a transmission tower modal parameter identification method based on an improved subspace algorithm and used for completing the modal parameter identification of a large span transmission tower structure through individually utilizing response data under the excitation of a field environment. According to the identification process, multi-group packet response data are integrated into synchronous pulse response data based on a random subspace identification principle; the integrated data avoid fitting errors caused by the packet identification, so the synchronous integrated identification of the data is realized; and a stable graph is constructed by utilizing modal parameter identification results under different system orders, so a modal parameter identification order determination problem under the environment excitation is solved, modal omission and repetition phenomena of traditional methods of a peak value method and the like are avoided, the obtained identification result is accurate and stable, and bases are established for subsequent structure damage detection and life estimation.
Owner:JIANGSU FRONTIER ELECTRIC TECH +3
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com