Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
735 results about "Environment variable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
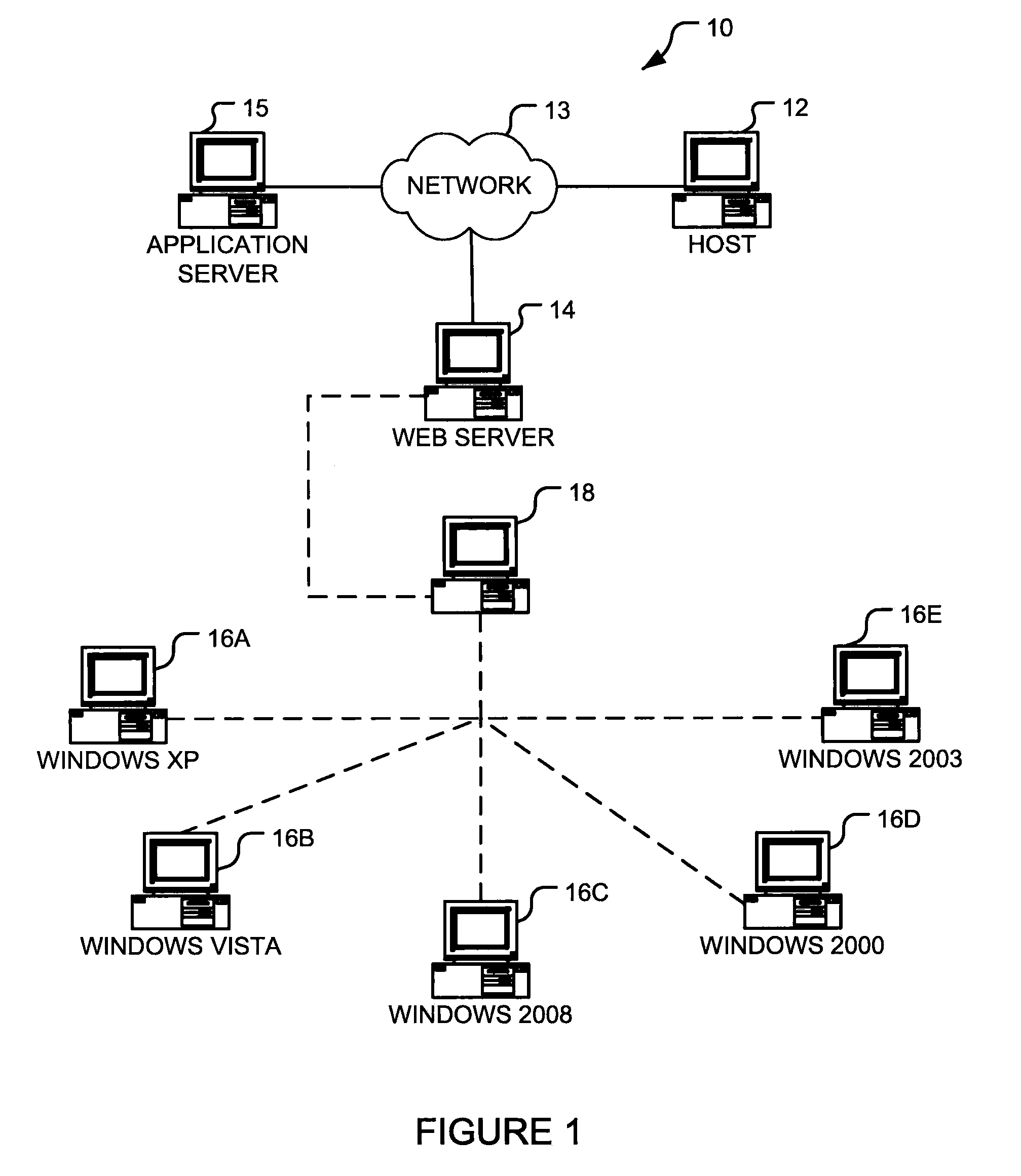
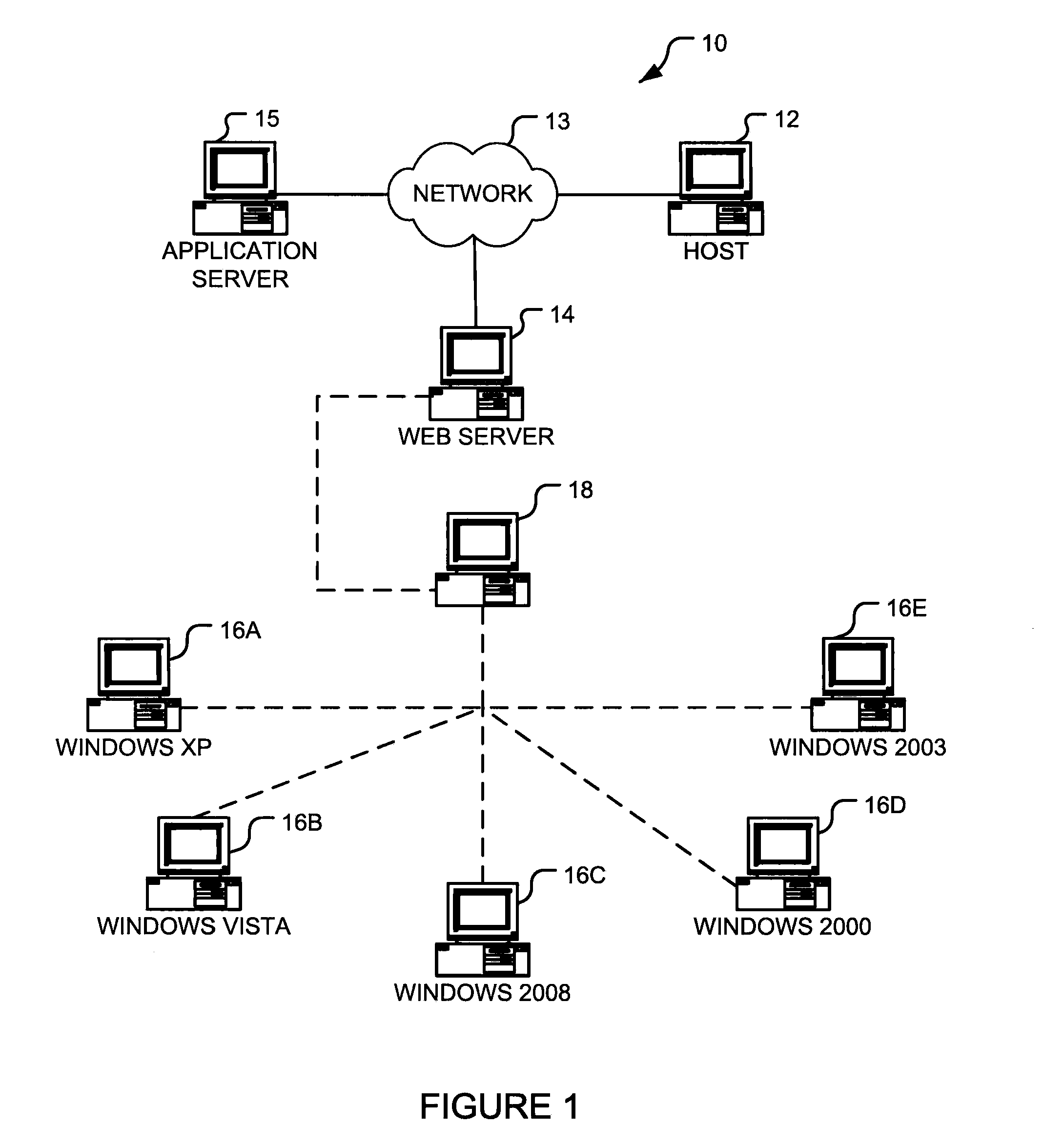
An environment variable is a dynamic-named value that can affect the way running processes will behave on a computer. They are part of the environment in which a process runs. For example, a running process can query the value of the TEMP environment variable to discover a suitable location to store temporary files, or the HOME or USERPROFILE variable to find the directory structure owned by the user running the process.
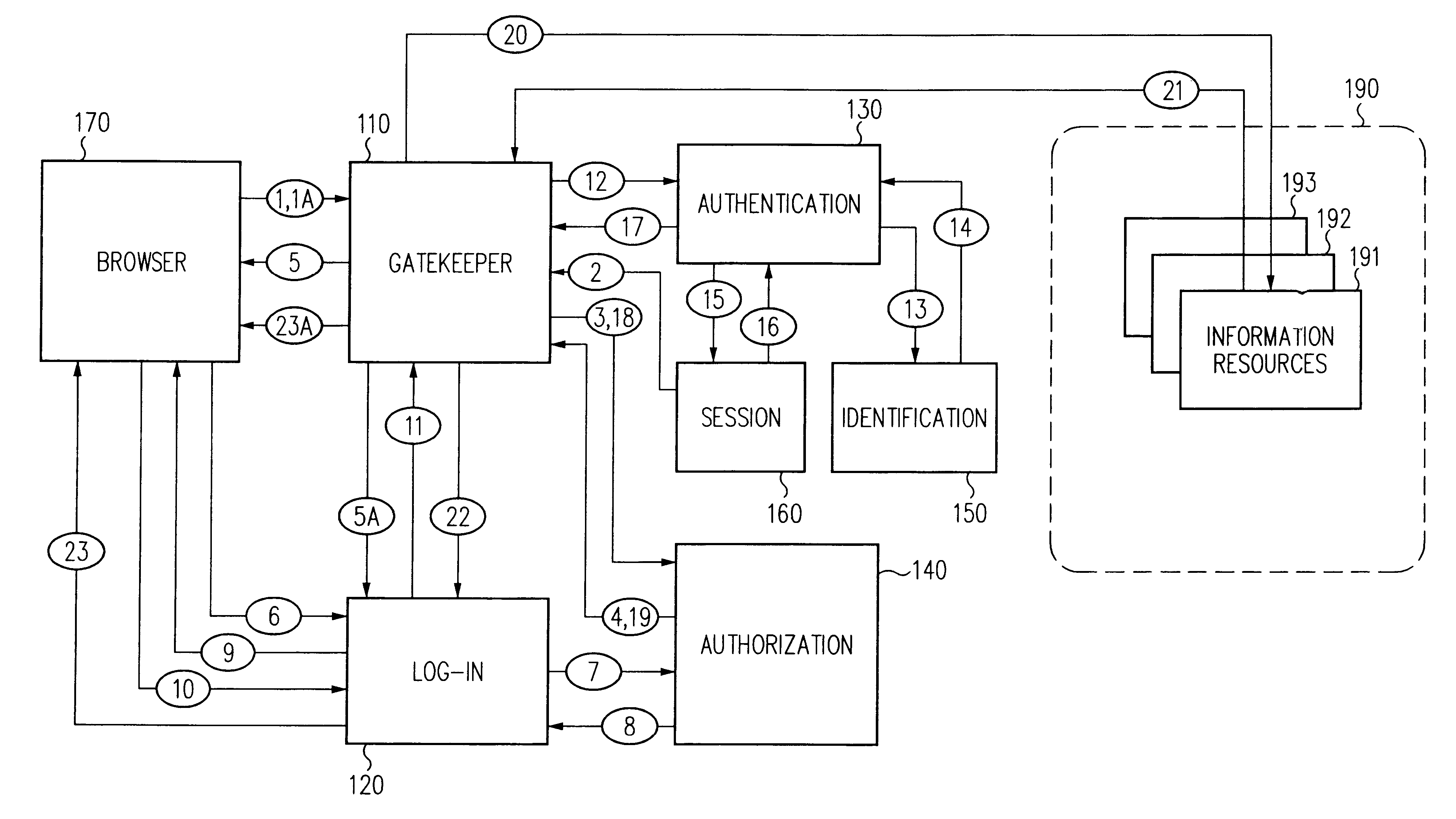
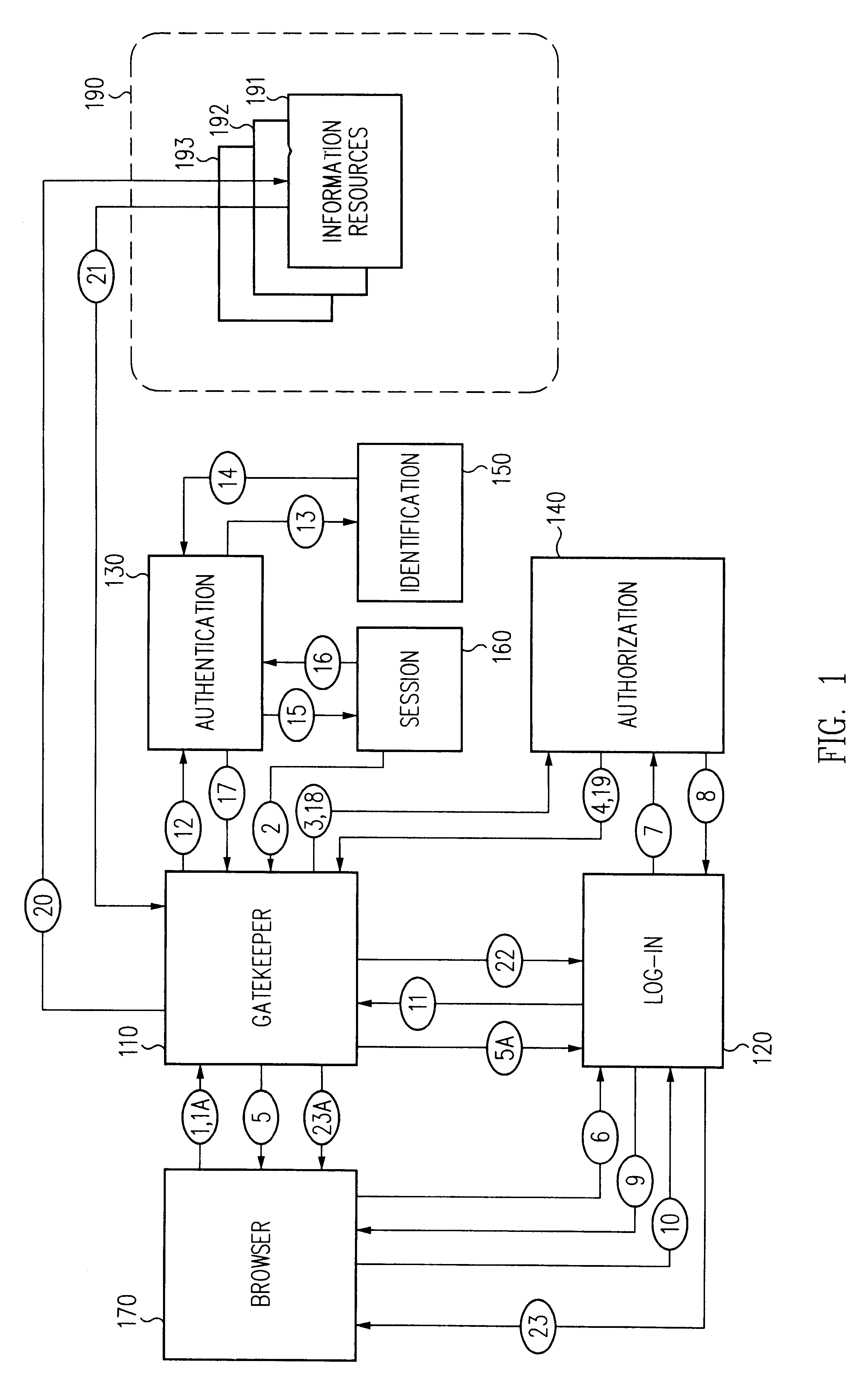
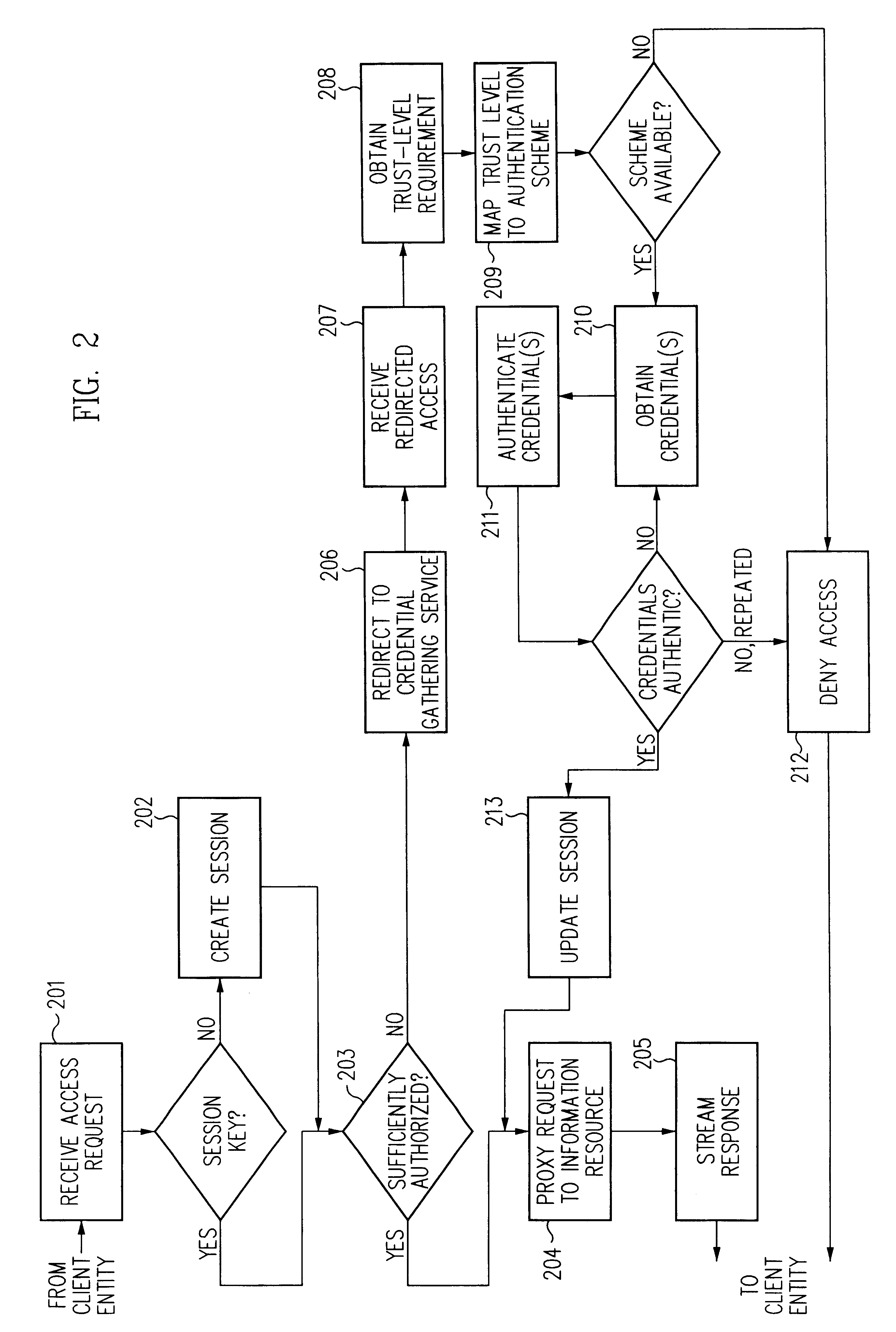
Log-on service providing credential level change without loss of session continuity
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
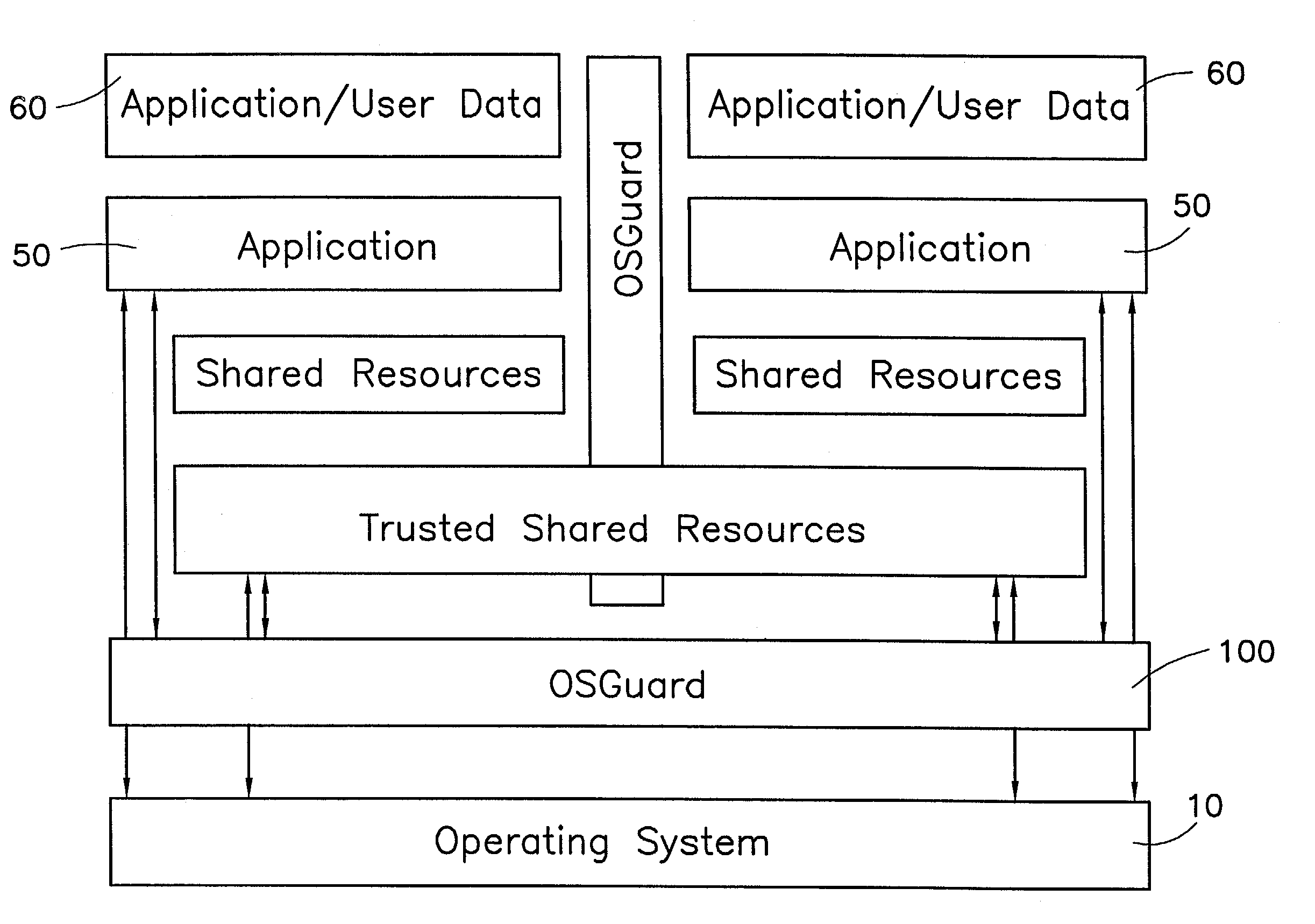
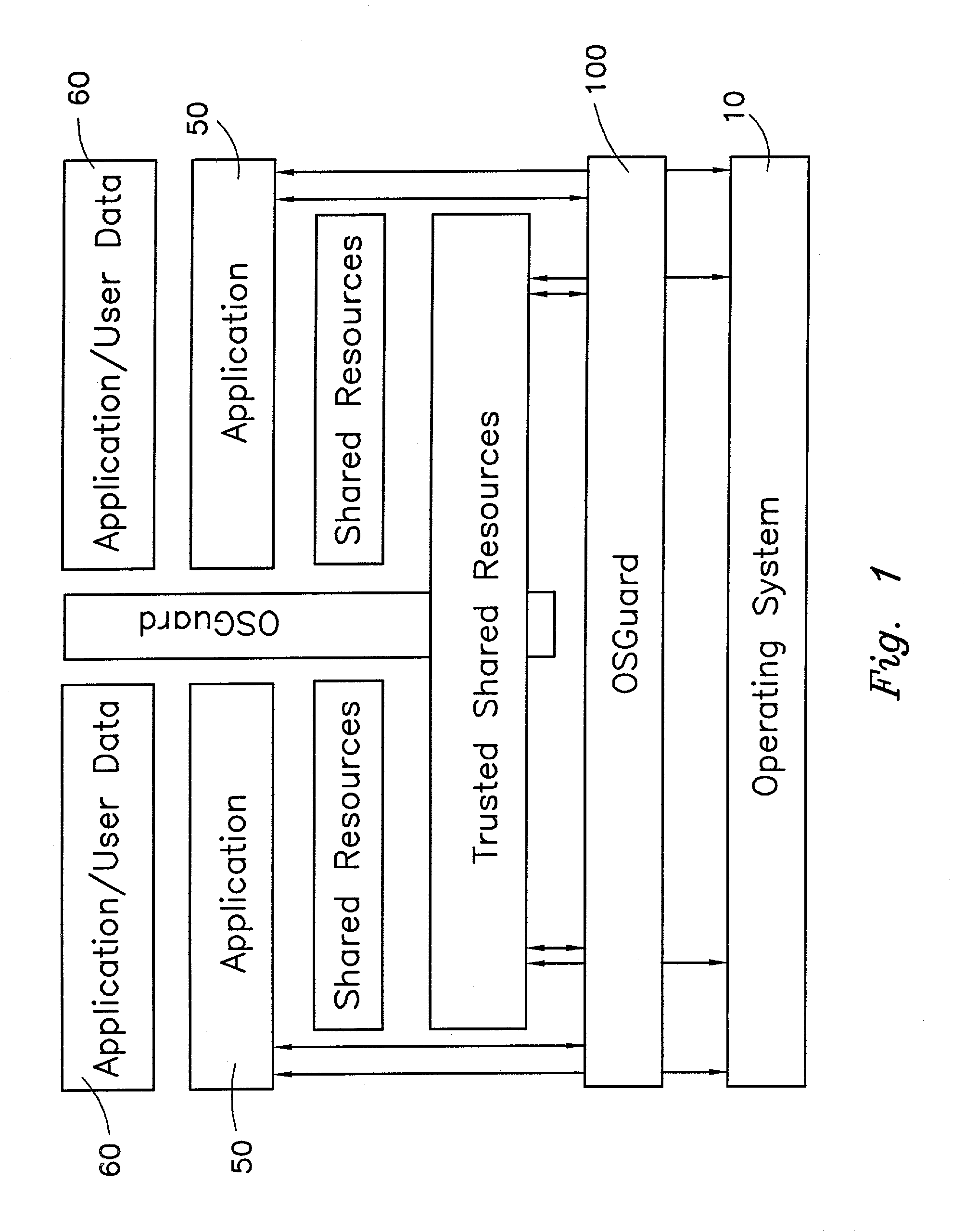
Operating system abstraction and protection layer
InactiveUS7028305B2Avoid changeInhibition of informationInterprogram communicationDigital computer detailsOperational systemConfiguration item
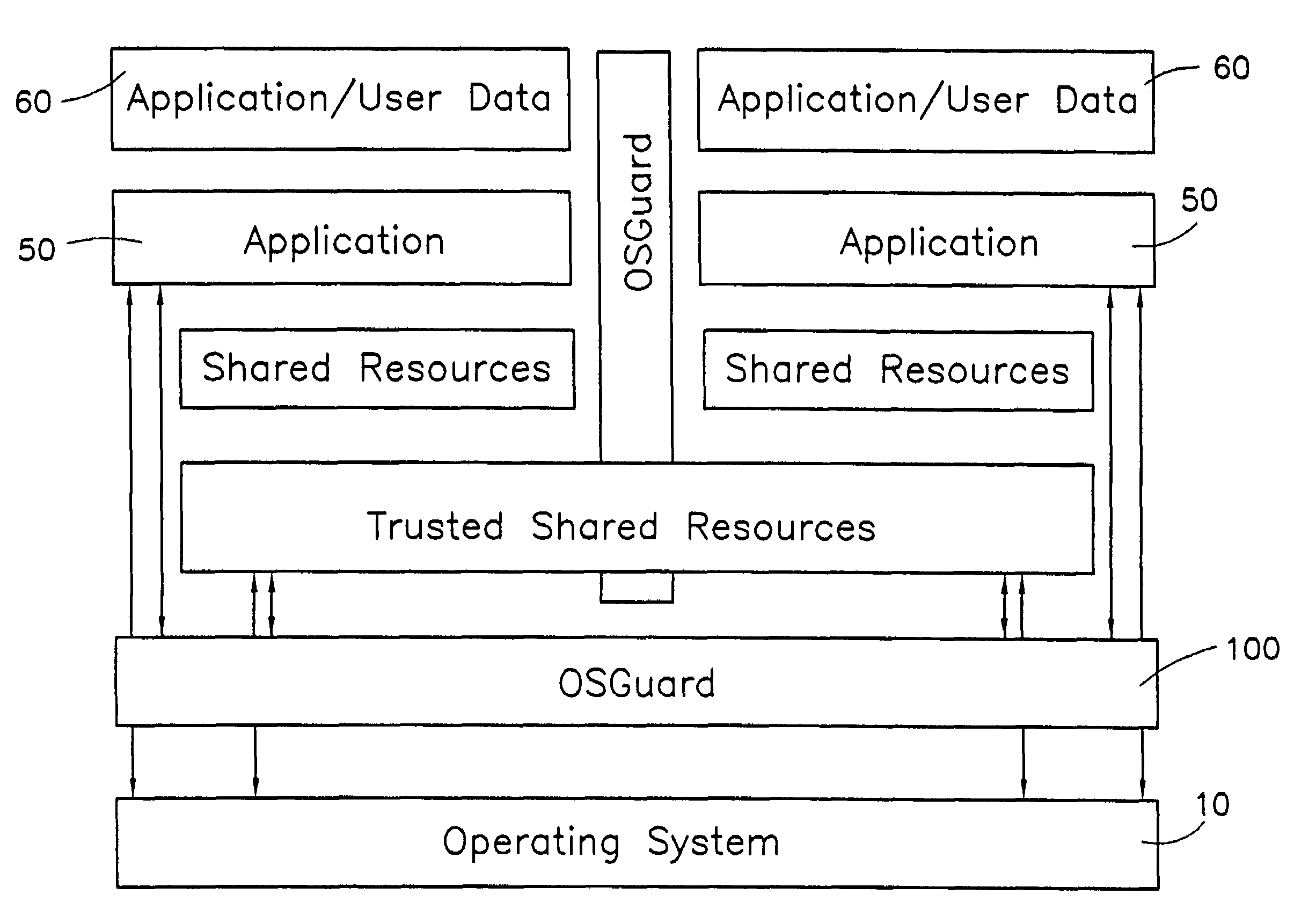
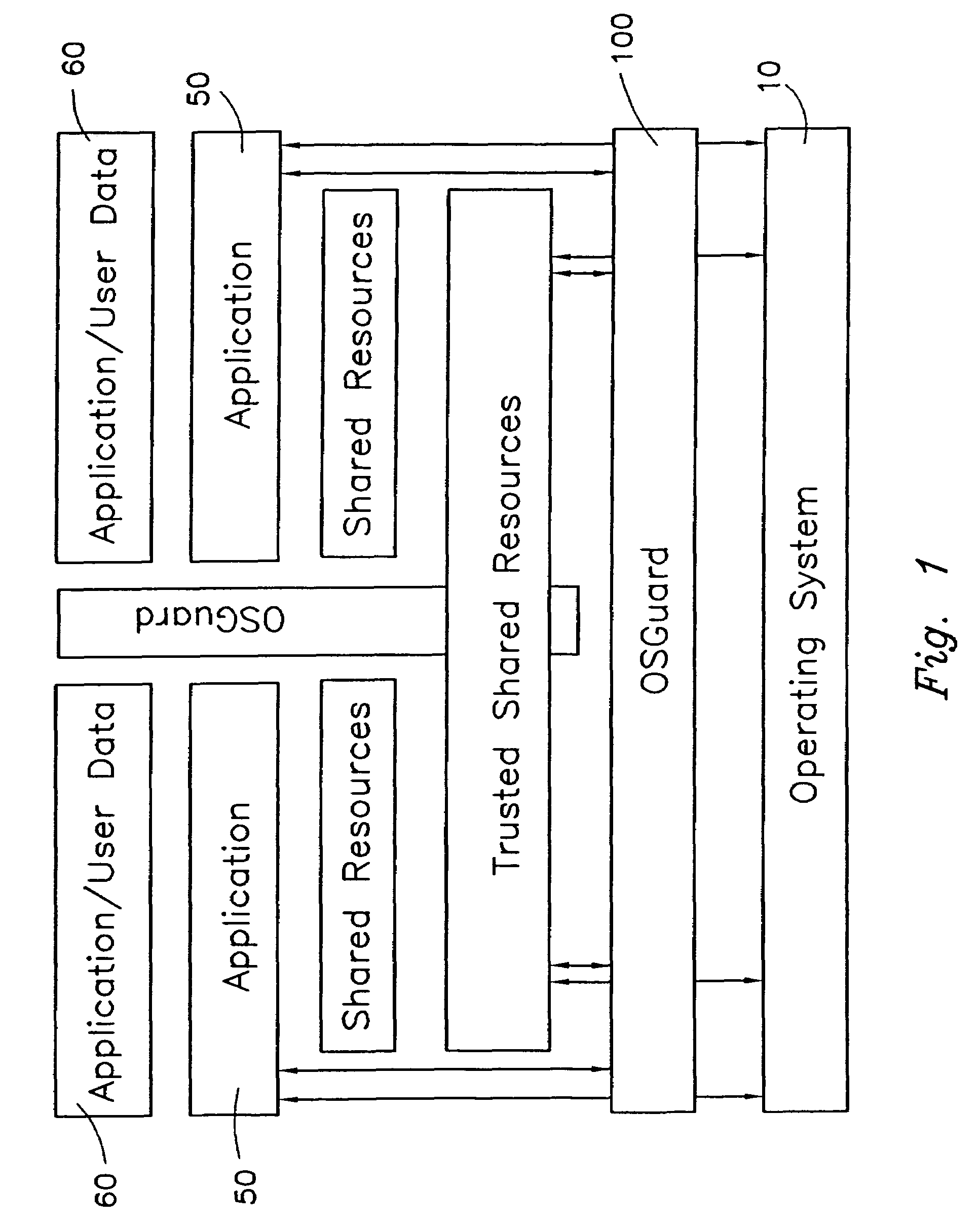
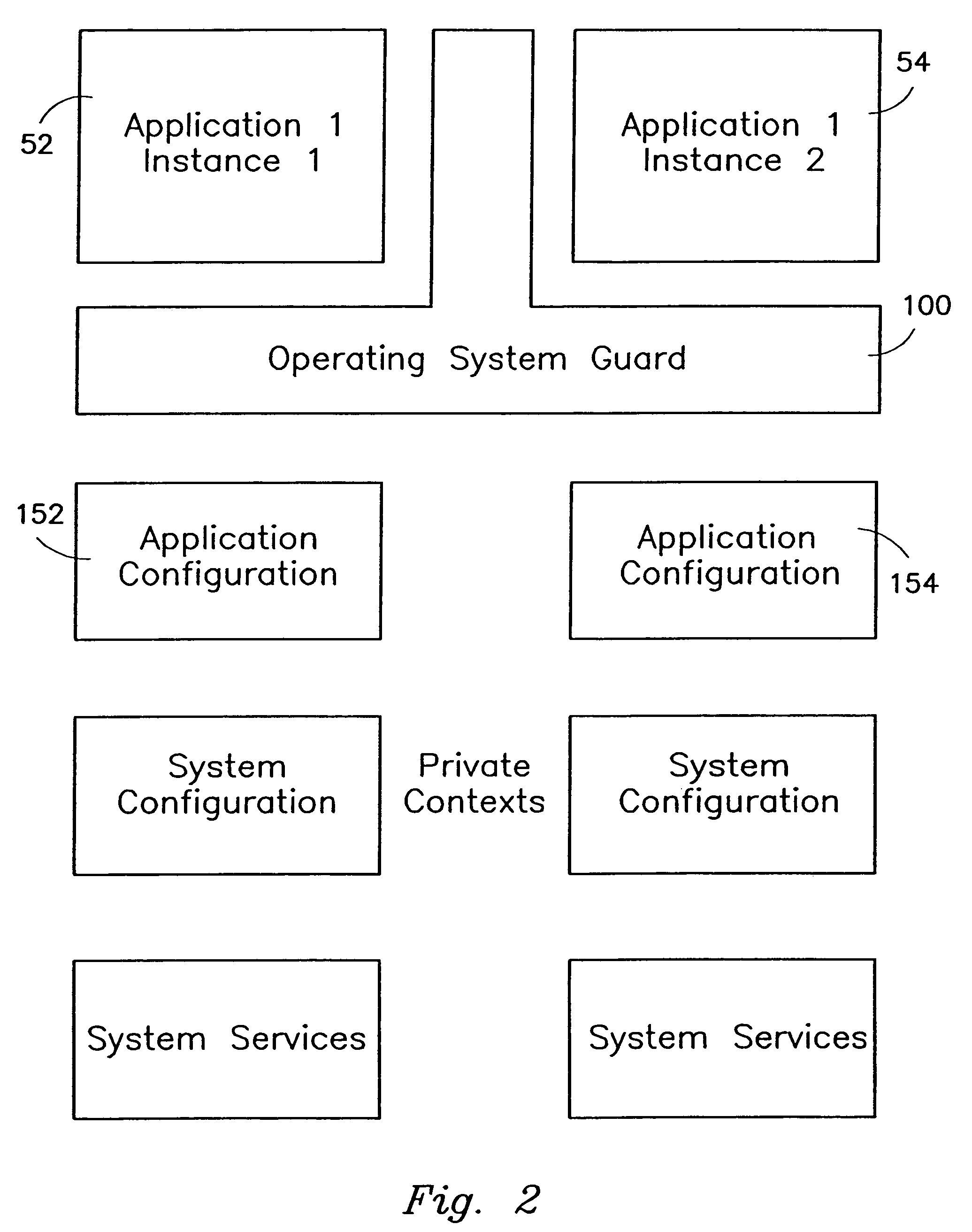
The present invention provides a system for creating an application software environment without changing an operating system of a client computer, the system comprising an operating system abstraction and protection layer, wherein said abstraction and protection layer is interposed between a running software application and said operating system, whereby a virtual environment in which an application may run is provided and application level interactions are substantially removed. Preferably, any changes directly to the operating system are selectively made within the context of the running application and the abstraction and protection layer dynamically changes the virtual environment according to administrative settings. Additionally, in certain embodiments, the system continually monitors the use of shared system resources and acts as a service to apply and remove changes to system components. The present thus invention defines an “Operating System Guard.” These components cover the protection semantics required by .DLLs and other shared library code as well as system device drivers, fonts, registries and other configuration items, files, and environment variables.
Owner:MICROSOFT TECH LICENSING LLC
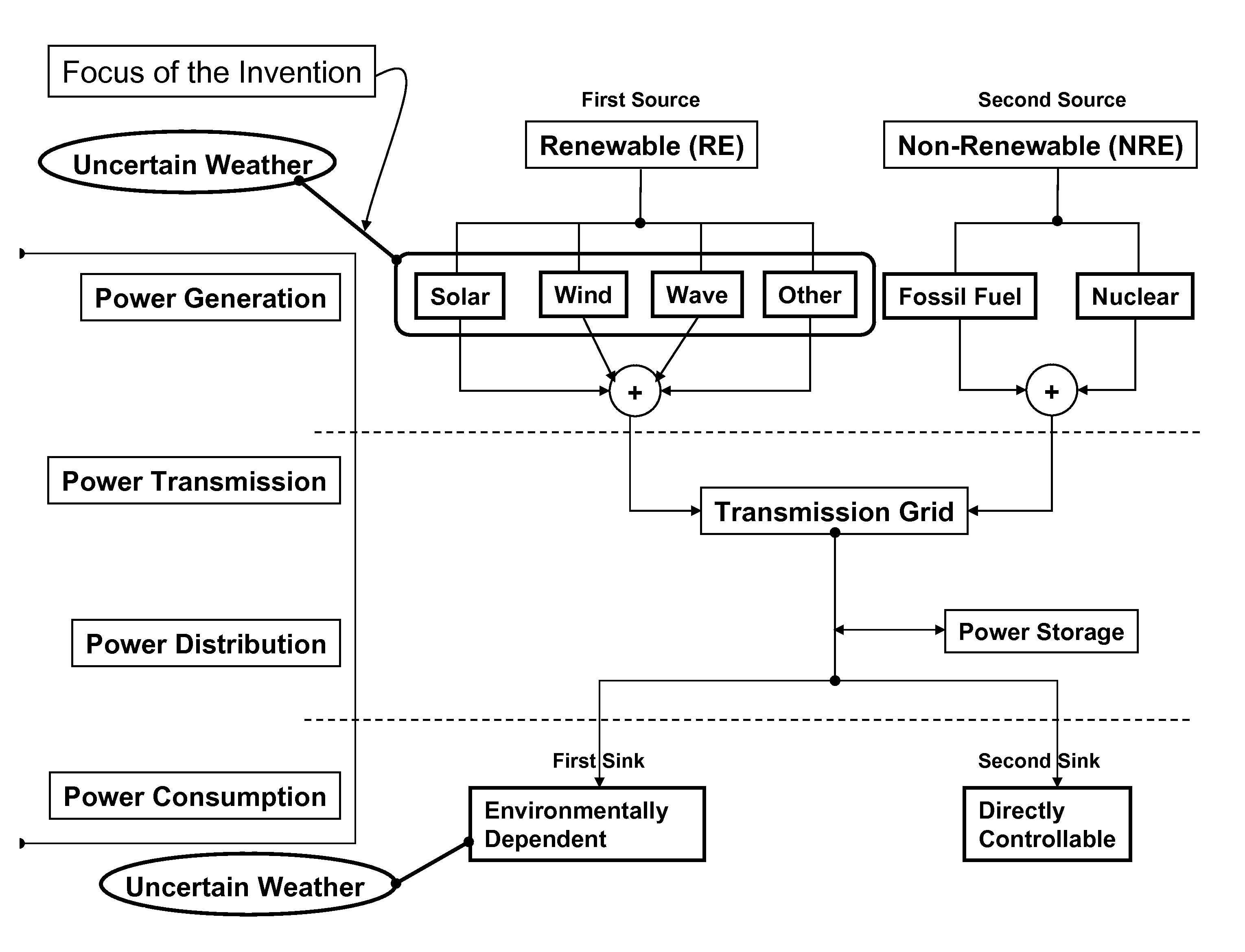
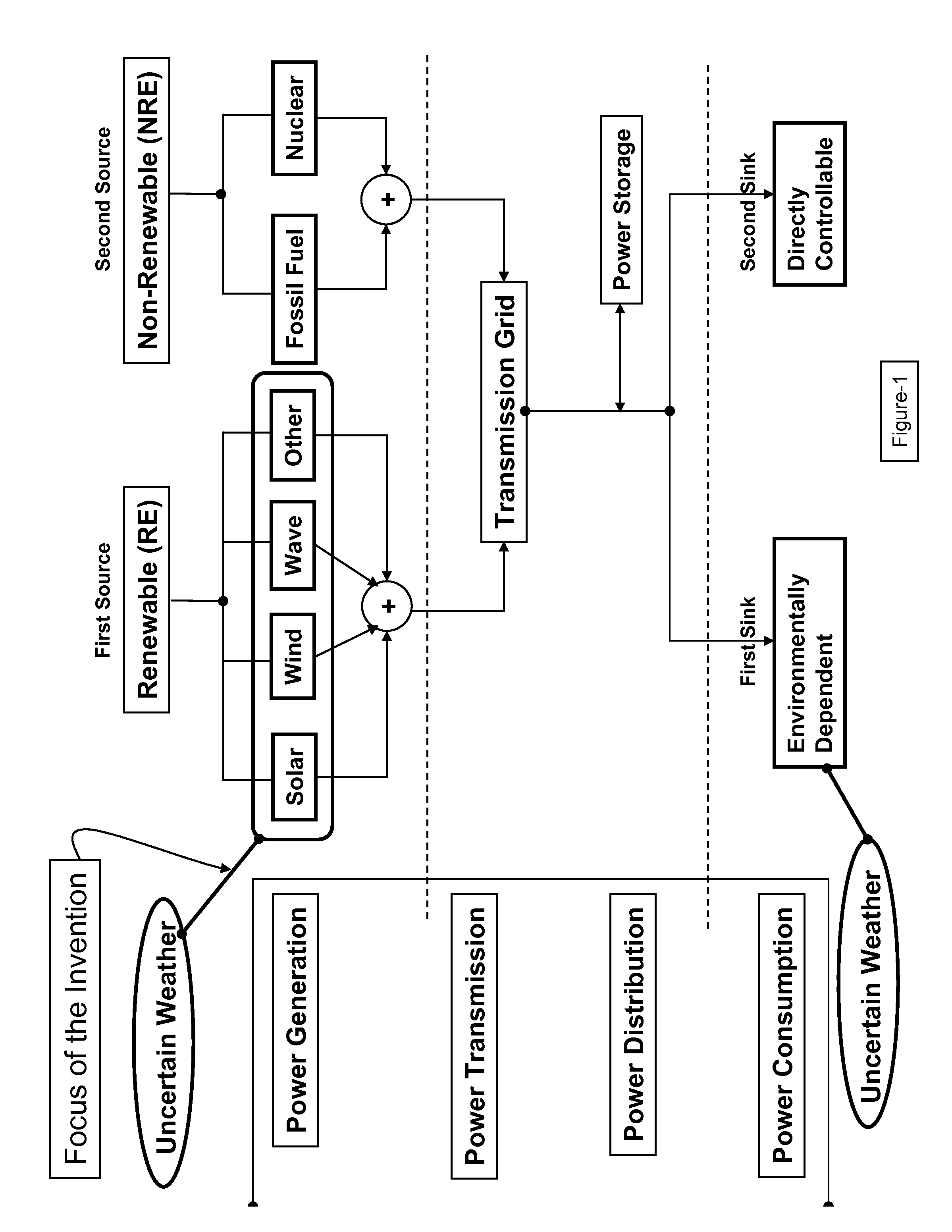
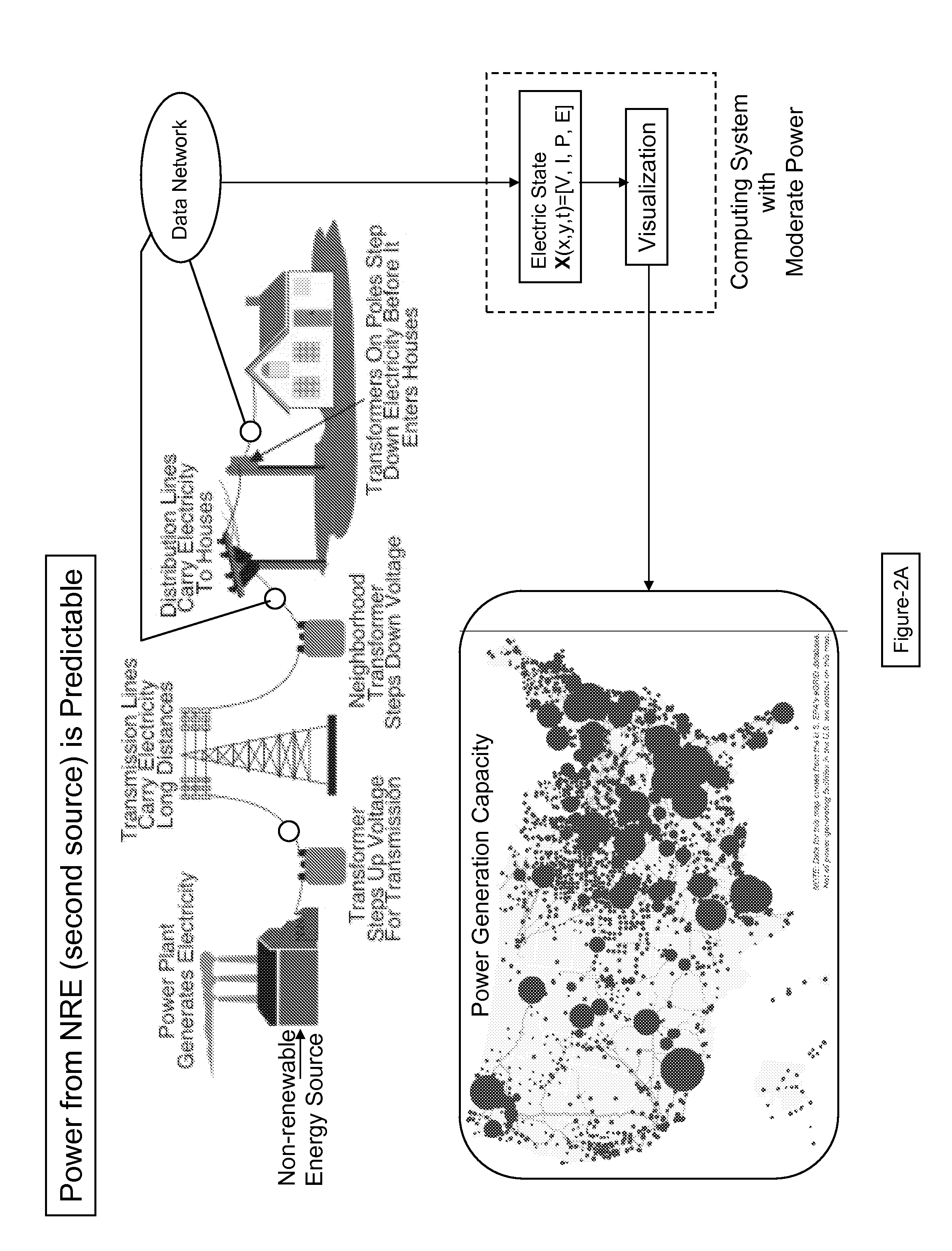
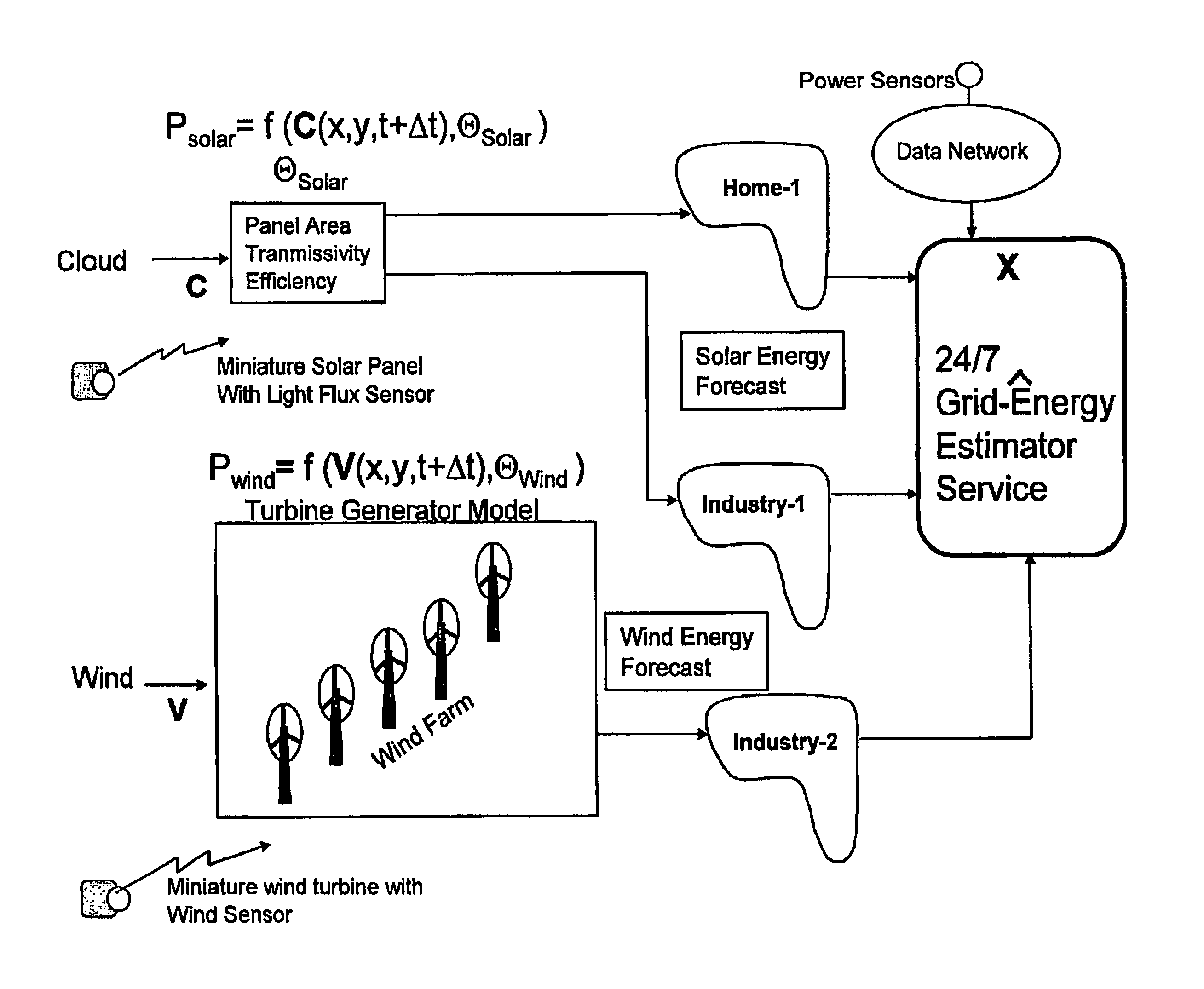
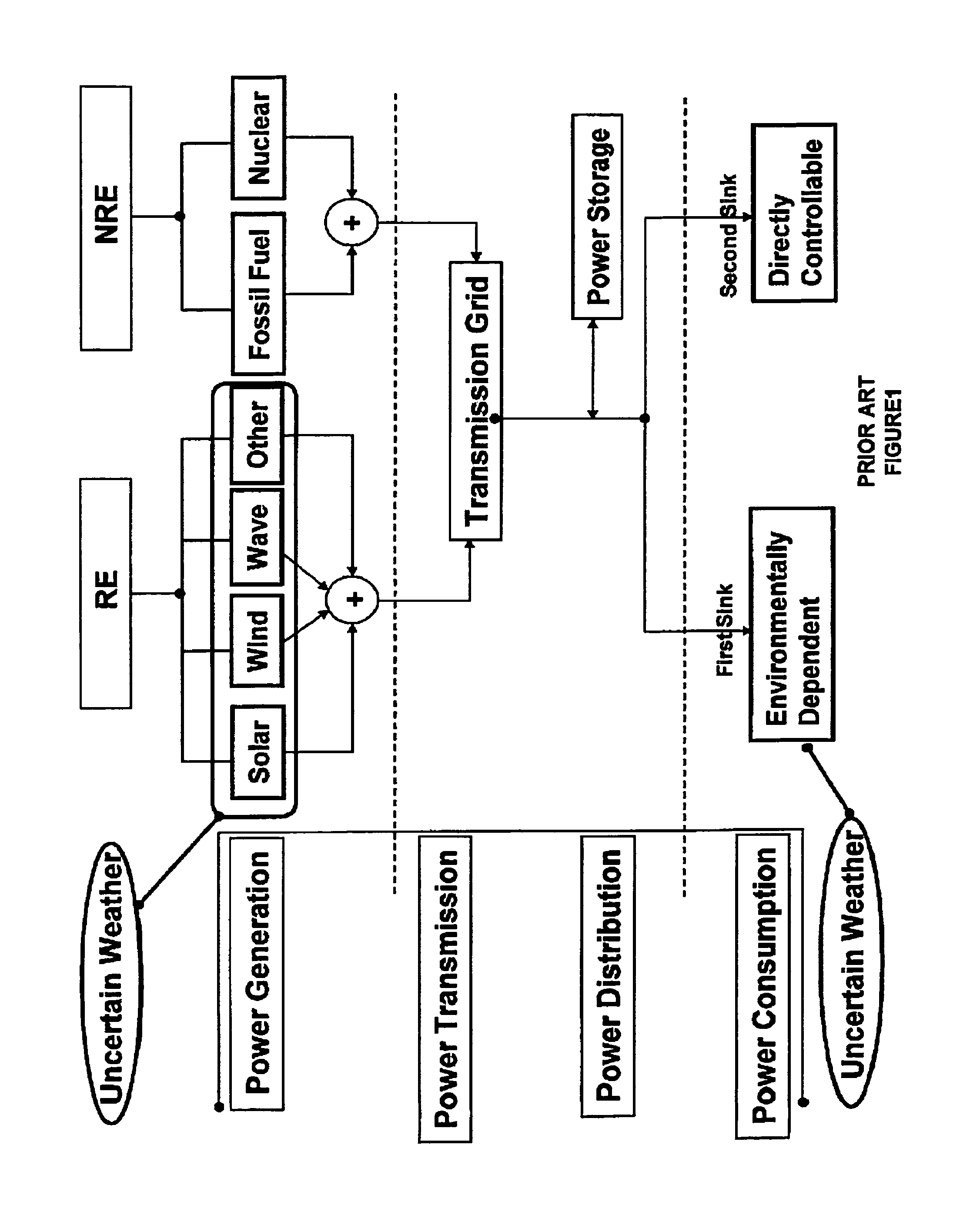
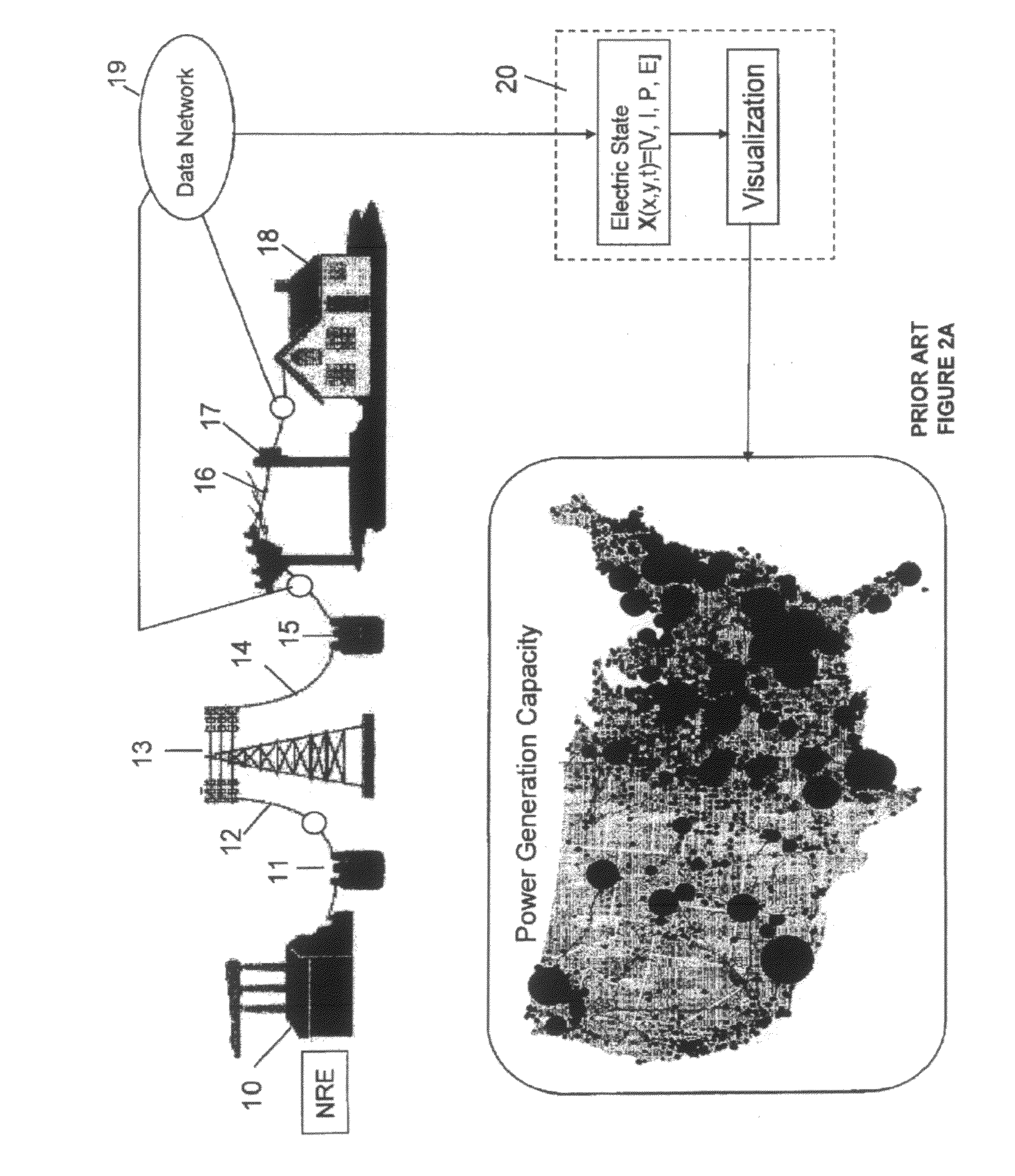
Smarter-Grid: Method to Forecast Electric Energy Production and Utilization Subject to Uncertain Environmental Variables
InactiveUS20110307109A1Improve accuracyMechanical power/torque controlLevel controlSmart gridEngineering
A method to forecast the energy sources and energy sinks to facilitate continuous capacity planning, regulation and control of energy state of an entity under variable weather condition is established. Energy sources of specific focus are related to renewable energy forms from wind, solar and wave that are highly dependent on prevailing weather conditions.
Owner:IBM CORP +1
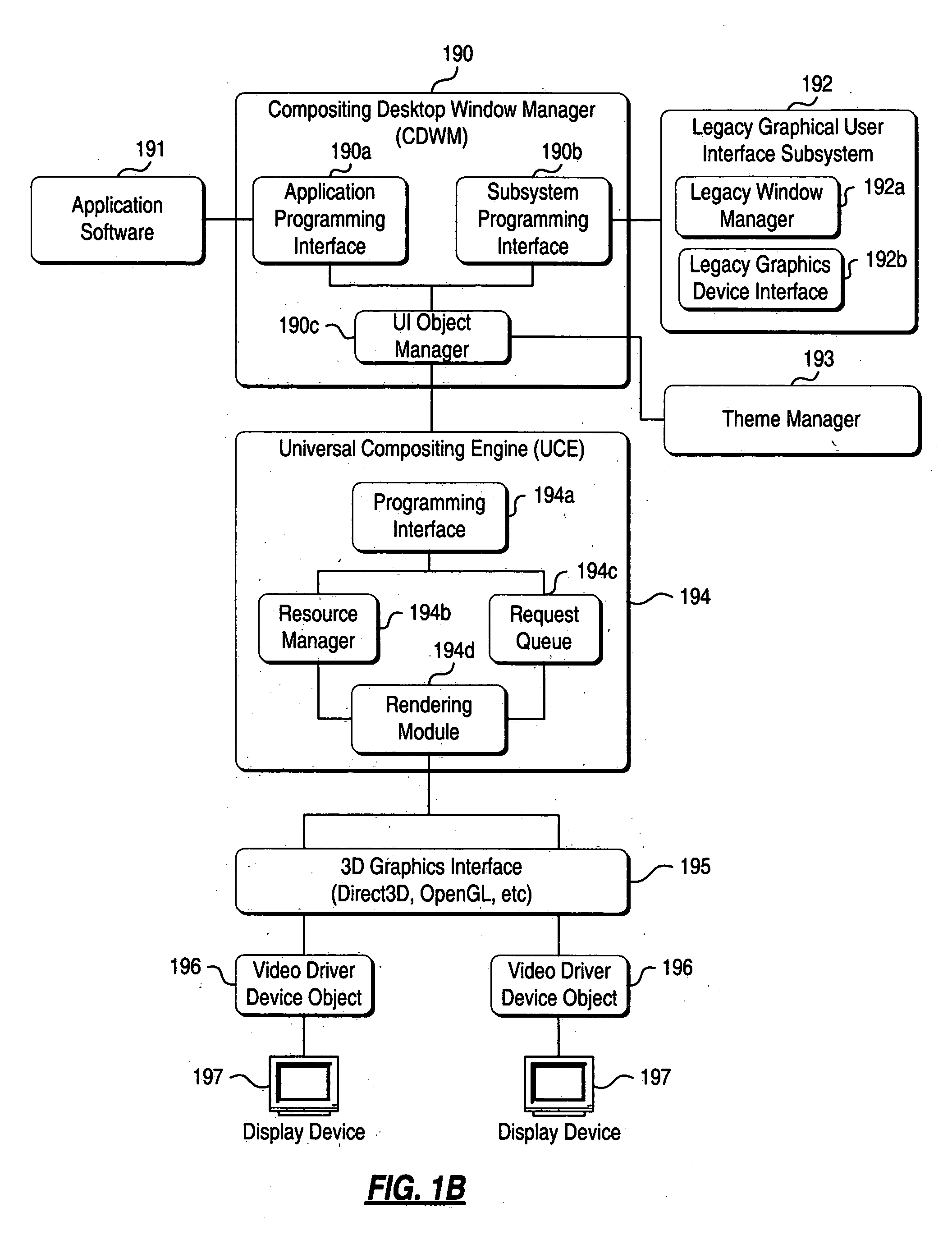
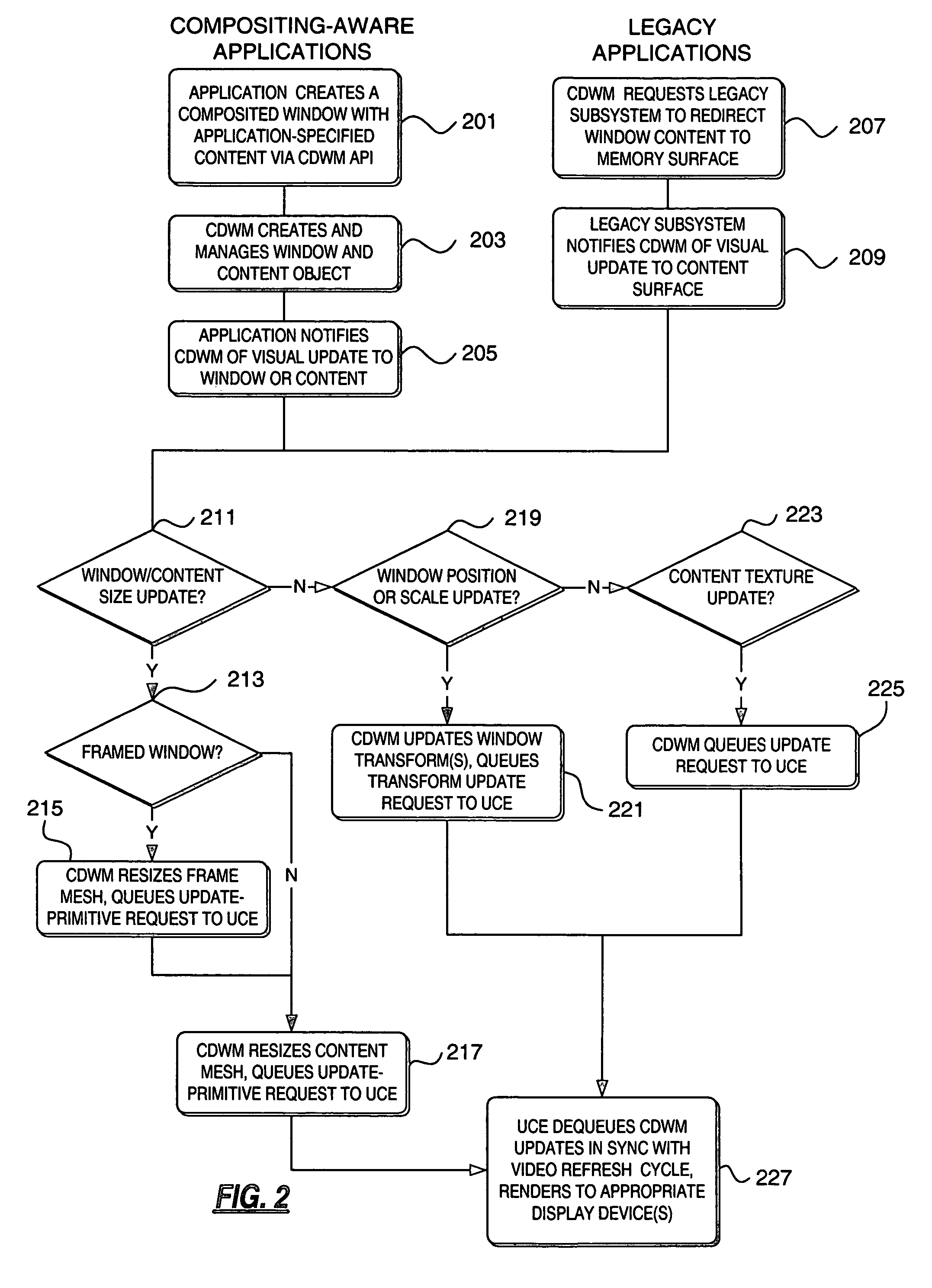
Compositing desktop window manager
InactiveUS20050088447A1Improve abilitiesMemory adressing/allocation/relocationDigital computer detailsWindow managerOperational system
A method and system for rendering a desktop on a computer using a composited desktop model operating system are disclosed. A composited desktop window manager, upon receiving content information from application programs, draws the window to a buffer memory for future reference, and takes advantage of advanced graphics hardware and visual effects to render windows based on content on which they are drawn. The windows may also be rendered based on environment variables including virtual light sources. The frame portion of each window may be generated by pixel shading a bitmap having the appearance of frosted glass based on the content of the desktop on top of which the frame is displayed. Legacy support is provided so that the operating system can draw and render windows generated by legacy applications to look consistent with non-legacy application windows.
Owner:MICROSOFT TECH LICENSING LLC
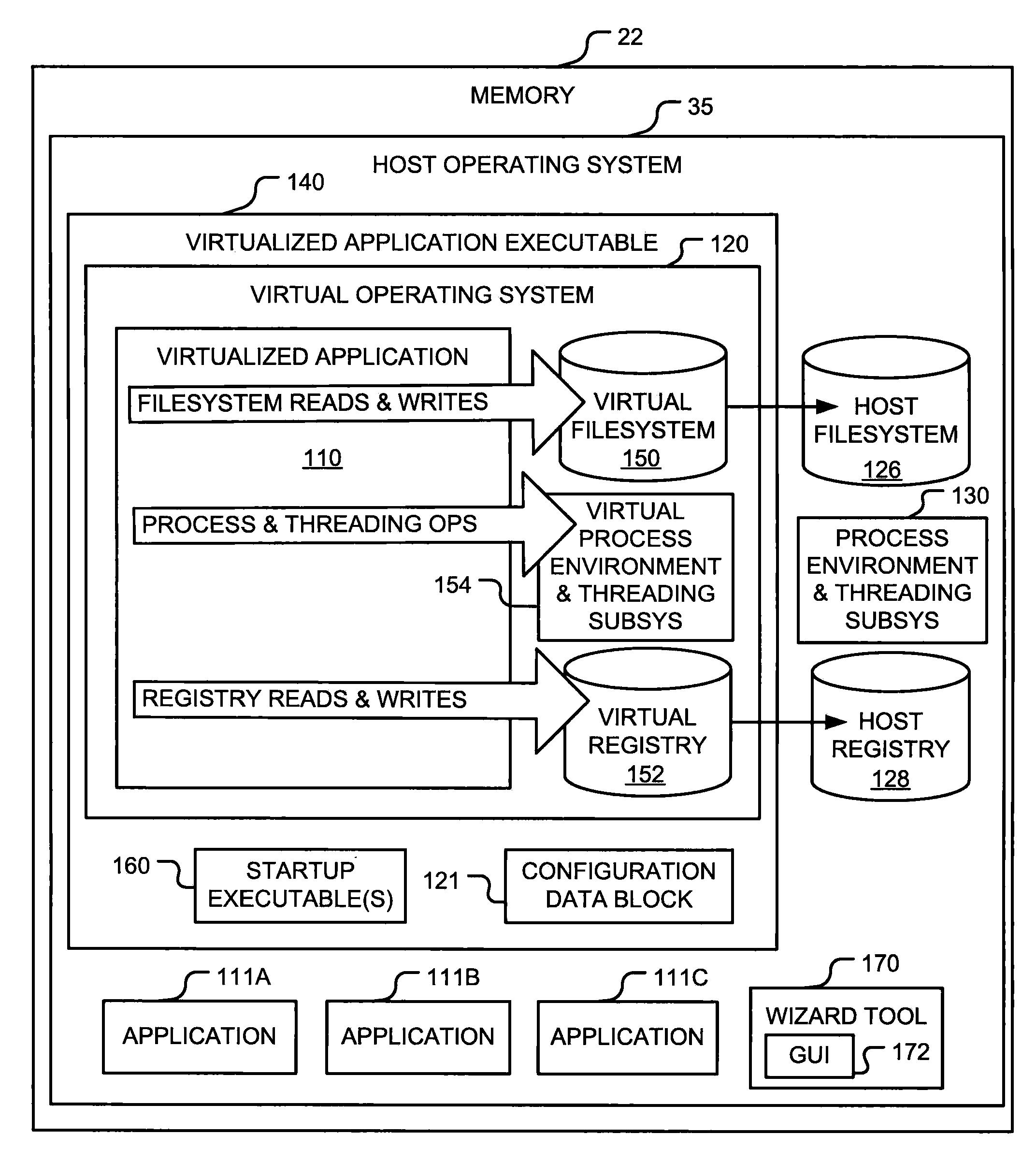
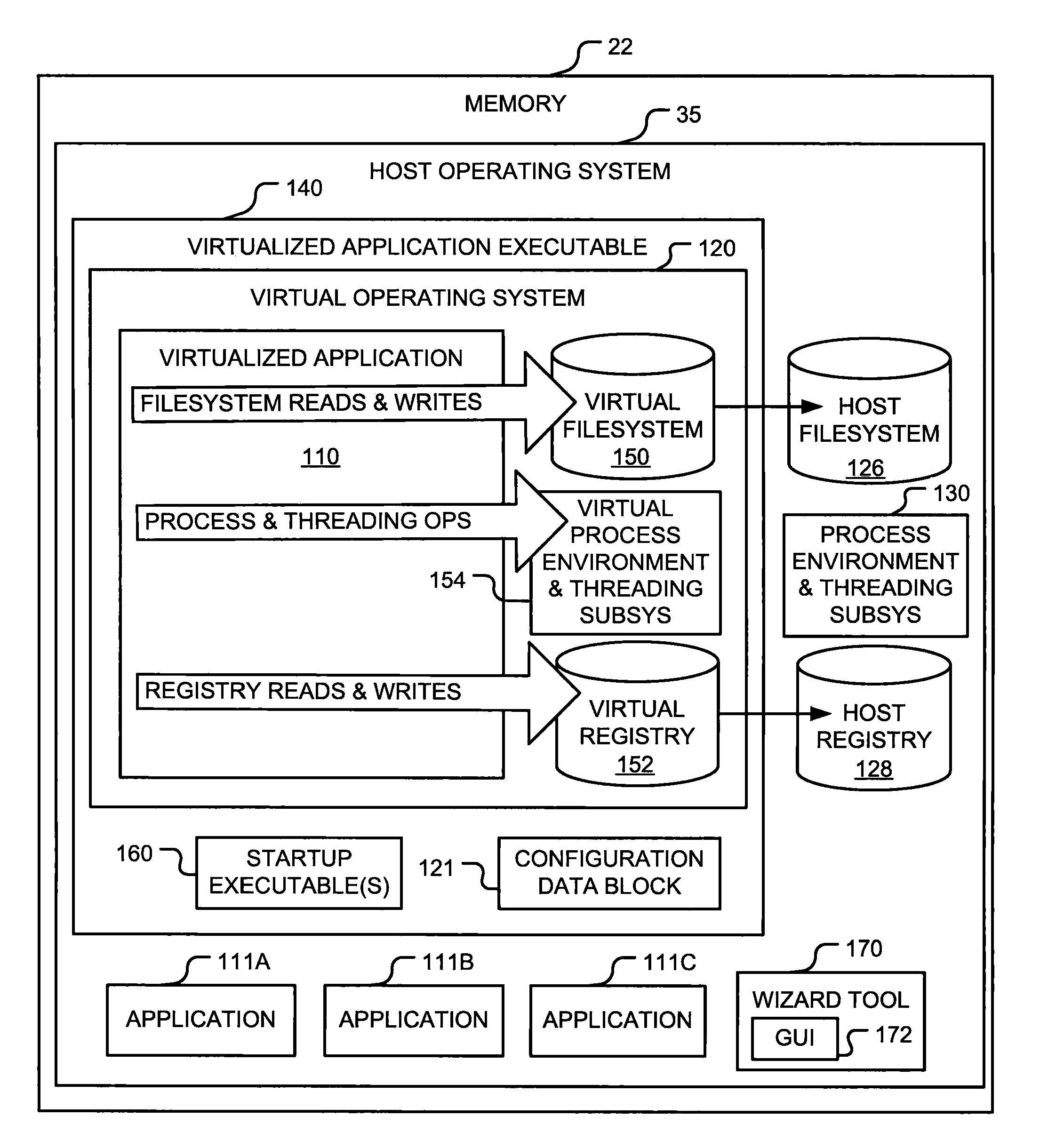
Method and system for virtualization of software applications
A method of virtualizing an application to execute on a plurality of operating systems without installation. The method includes creating an input configuration file for each operating system. The templates each include a collection of configurations that were made by the application during installation on a computing device executing the operating system. The templates are combined into a single application template having a layer including the collection of configurations for each operating system. The collection of configurations includes files and registry entries. The collections also identifies and configures environmental variables, systems, and the like. Files in the collection of configurations and references to those files may be replaced with references to files stored on installation media. The application template is used to build an executable of the virtualized application. The application template may be incorporated into a manifest listing other application templates and made available to users from a website.
Owner:CODE SYST CORPOATION
Method and system for configuration of virtualized software applications
ActiveUS20100037206A1Digital data information retrievalSoftware simulation/interpretation/emulationVirtualizationWeb site
Owner:CODE SYST CORPOATION
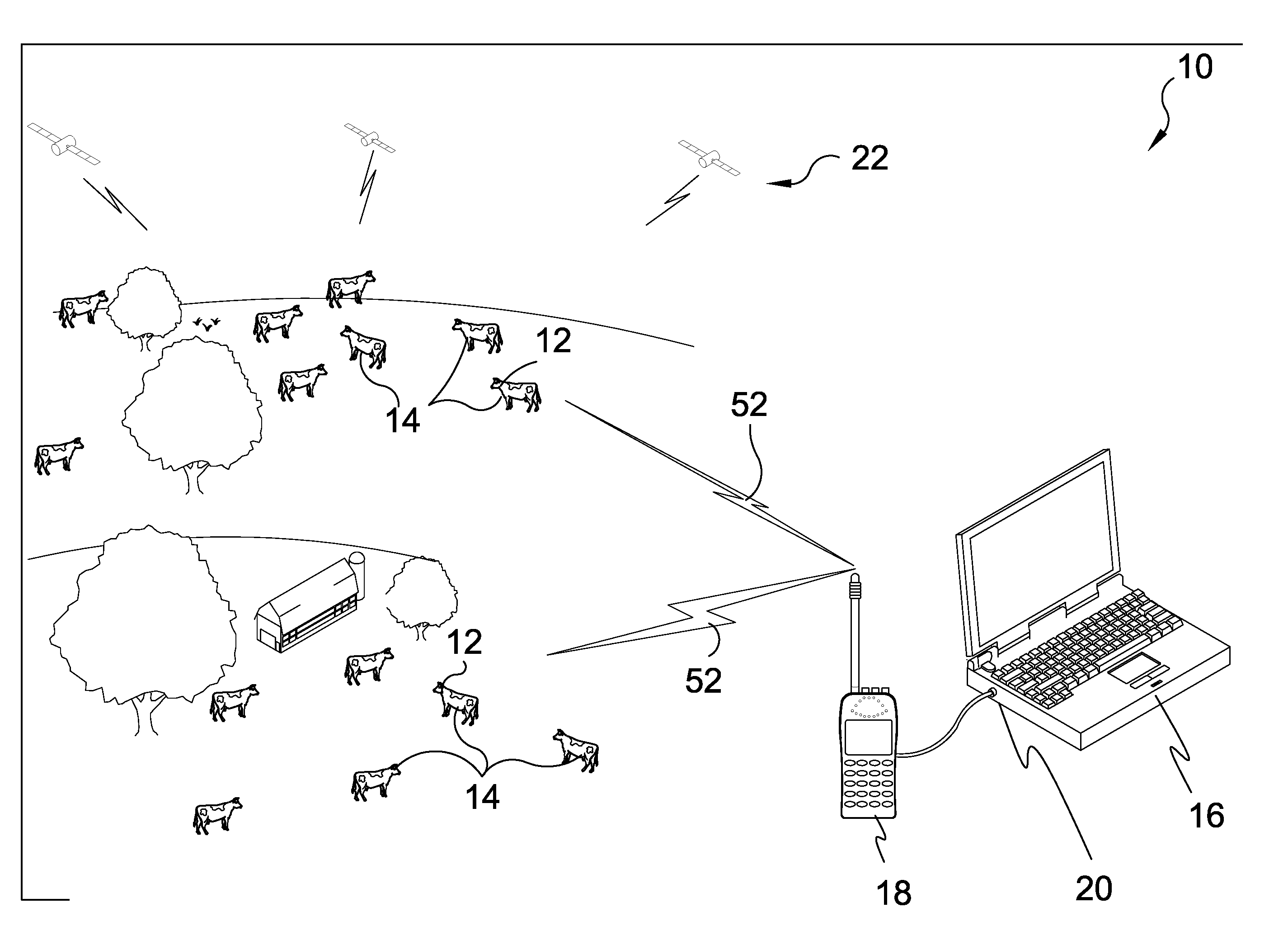
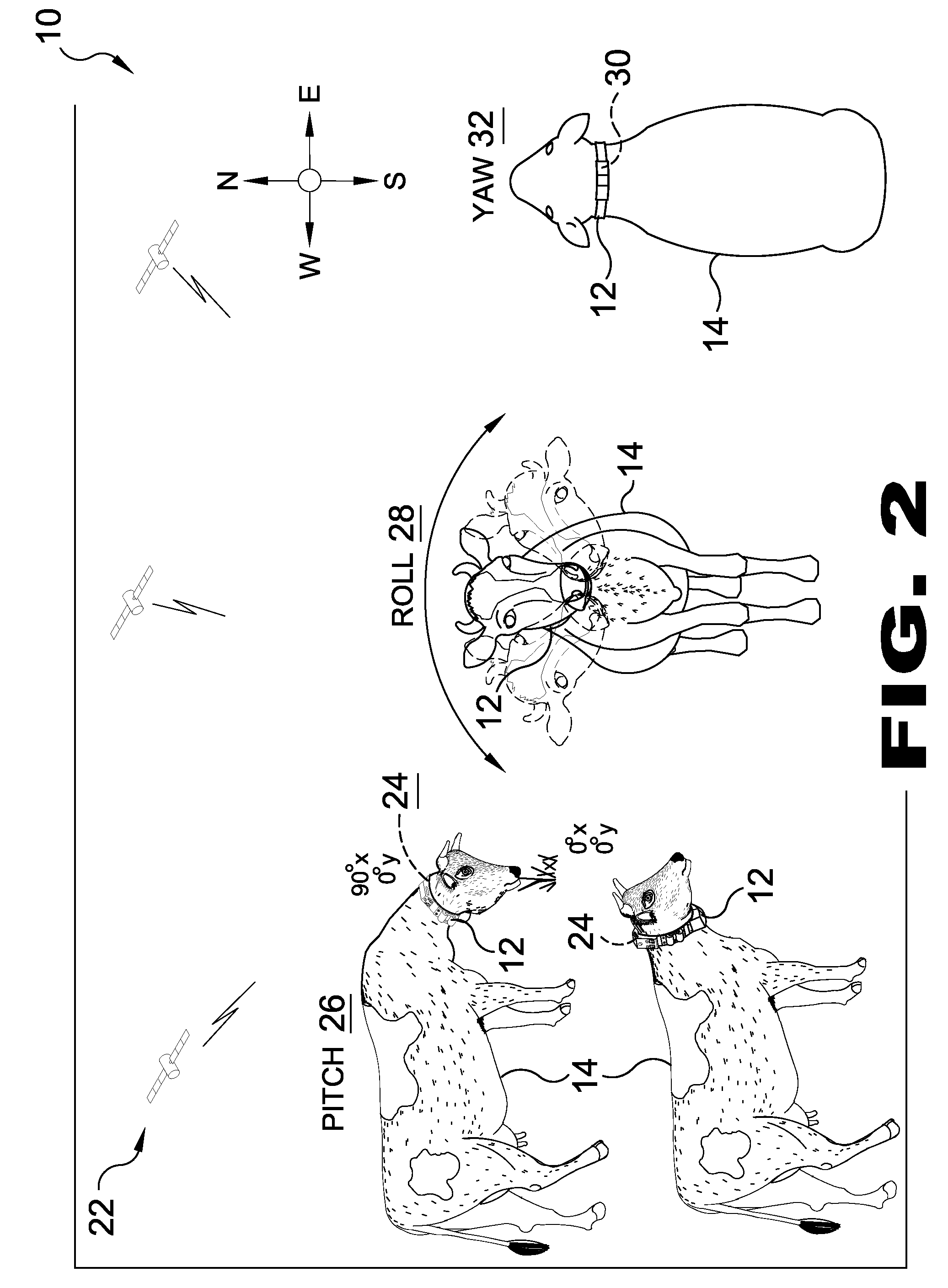
Method and apparatus for data logging of physiological and environmental variables for domestic and feral animals
A GPS data acquisition collar incorporating an individualized rugged watertight collar that monitors factors including GPS location, gazing patterns, elevation, feeding patterns, temperature, movement speed, sleep patterns and signaling or beacon tracking options. Additionally the present invention provides options for visual representation or programming alerting of factors that may affect an animal or herd of animals in a monitored and recorded environment.
Owner:KEDZIORA JOHN
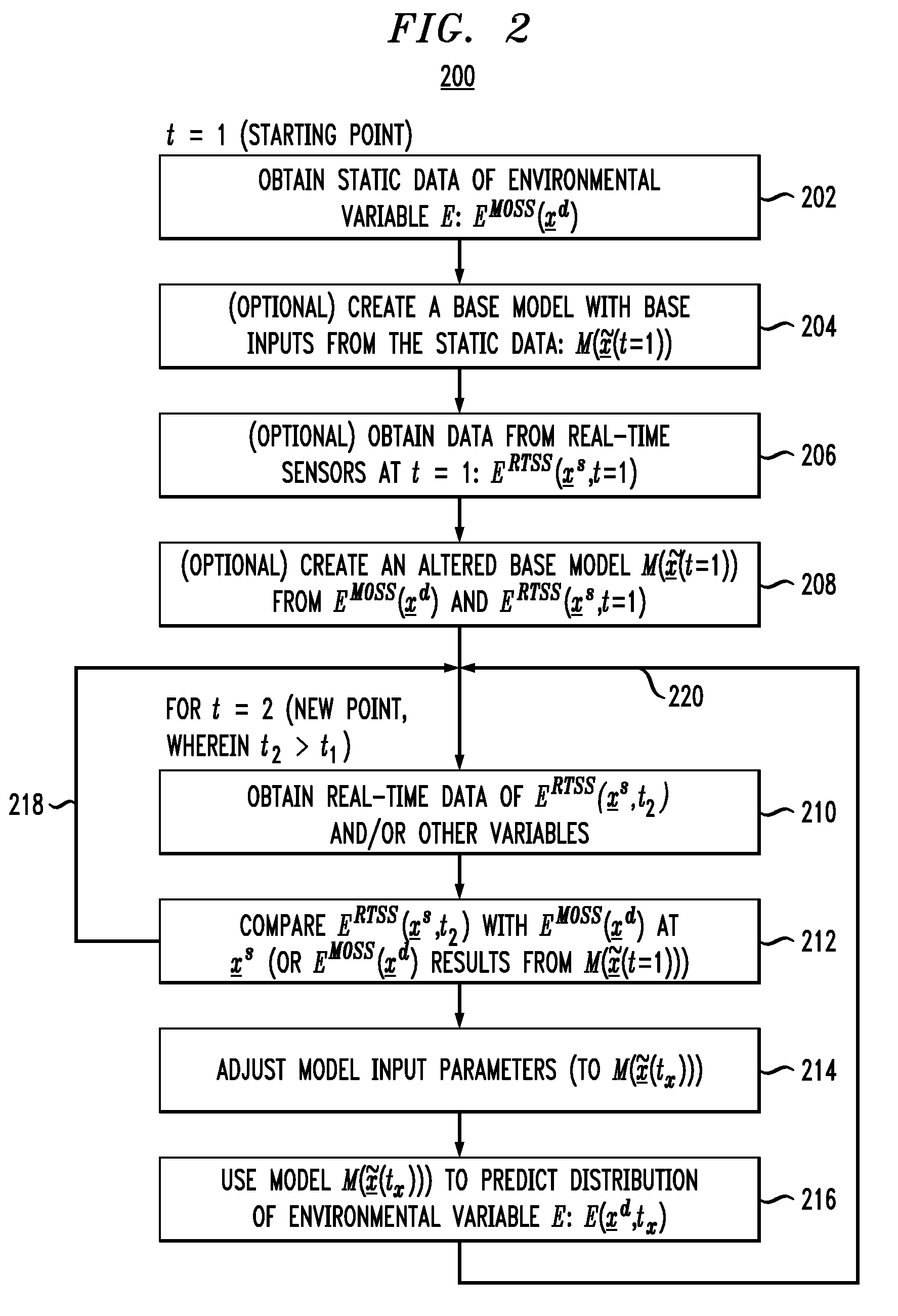
Techniques to Predict Three-Dimensional Thermal Distributions in Real-Time
ActiveUS20090326884A1Improve spatial resolutionMeasurement resolutionEnergy efficient ICTComputation using non-denominational number representationImage resolutionHigh spatial resolution
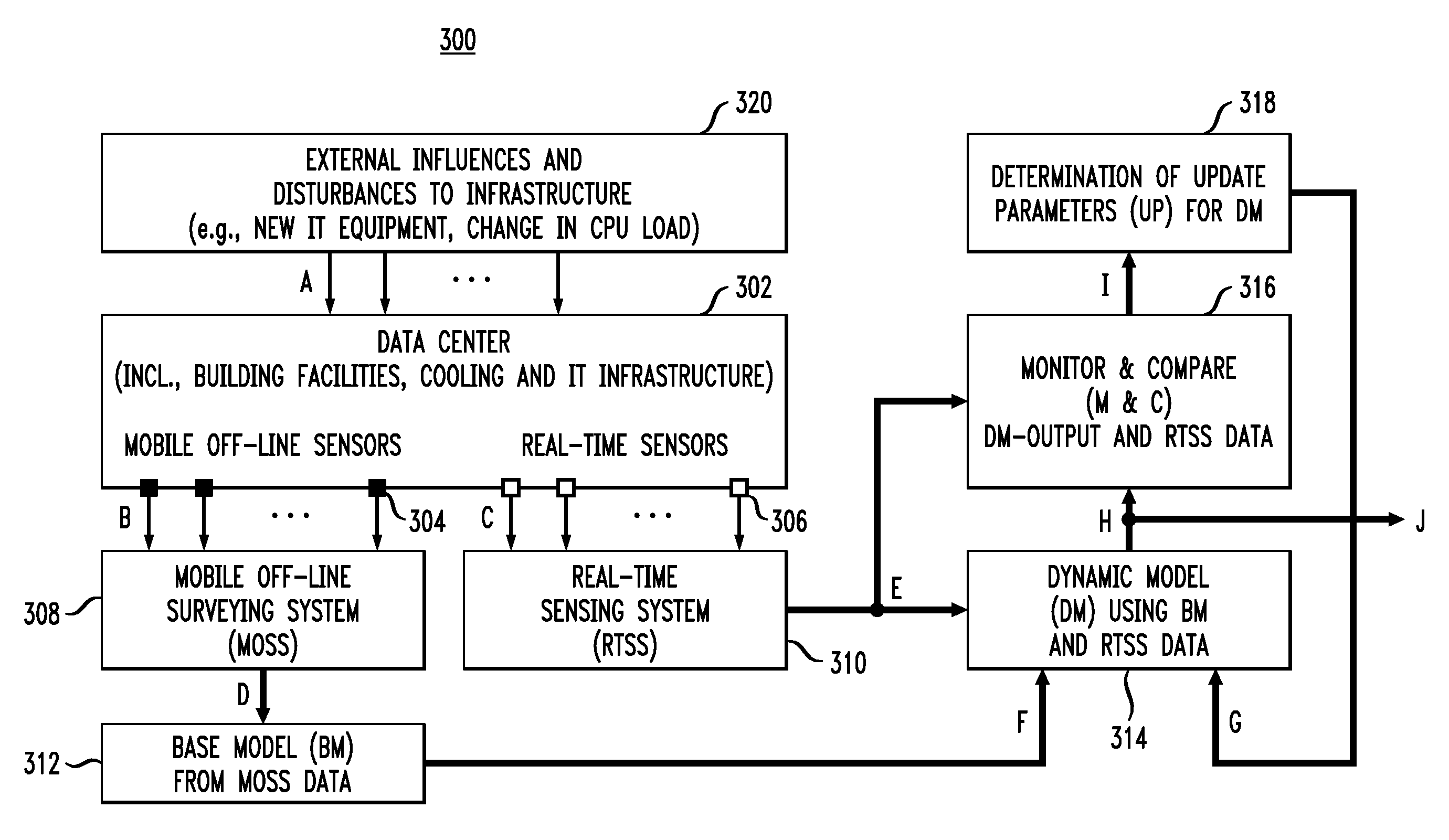
Techniques for monitoring and predicting environmental operating conditions in a data center are provided. In one aspect, a method for real-time, three-dimensional analysis of environmental operating conditions in a data center includes the following steps. High spatial resolution three-dimensional measurements of one or more environmental variables in the data center made at a time t1 are obtained. Real-time measurements of the environmental variables in the data center made at a time t2, wherein t2 is later in time than t1, are obtained. The high spatial resolution three-dimensional measurements are combined with the real-time measurements to derive a model for the environmental variables in the data center at the time t2. The model is used to predict three-dimensional distributions of the environmental variables in the data center at the time t2. A base model can be created and used to derive the model for the data center at the time t2.
Owner:IBM CORP
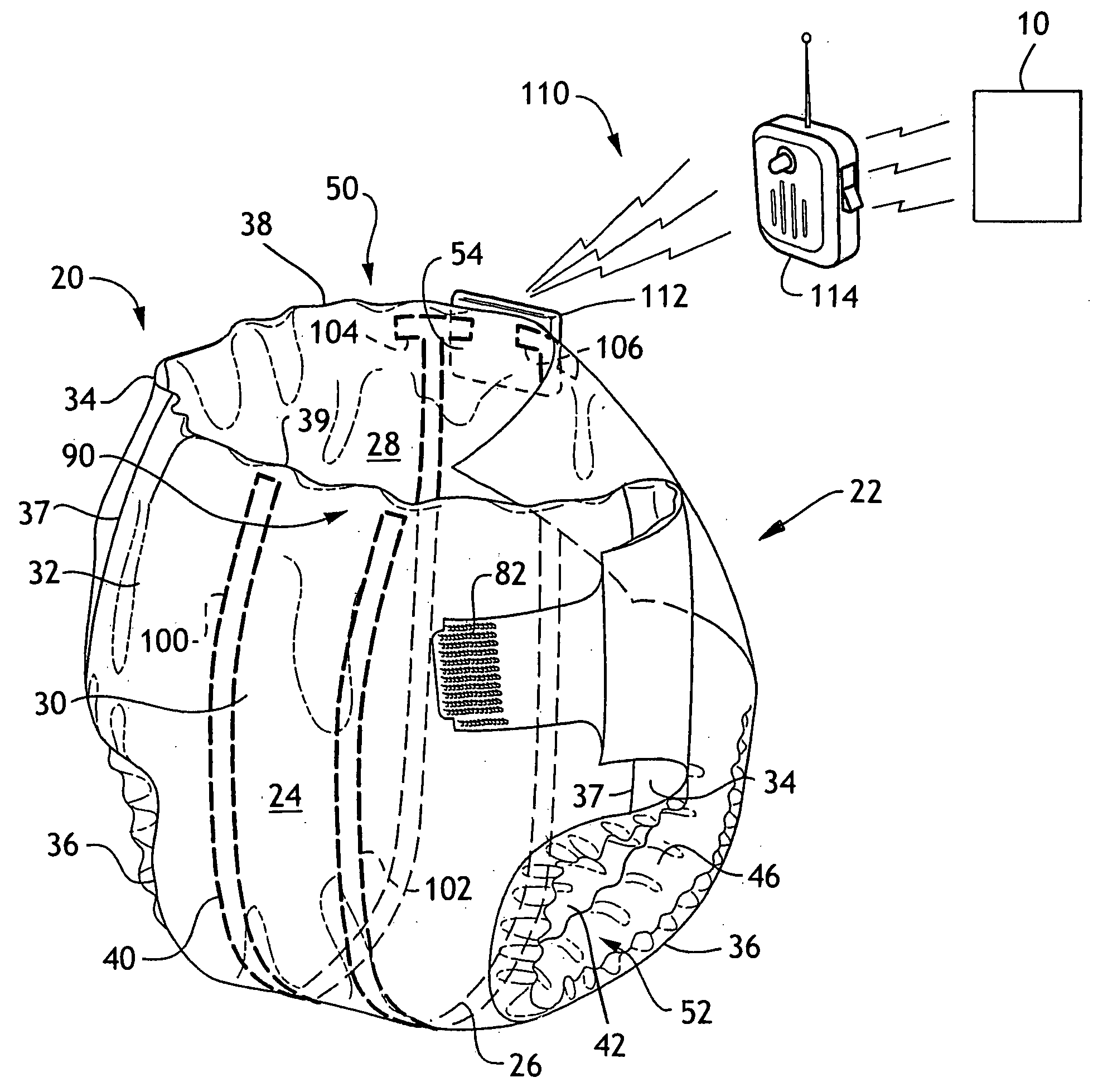
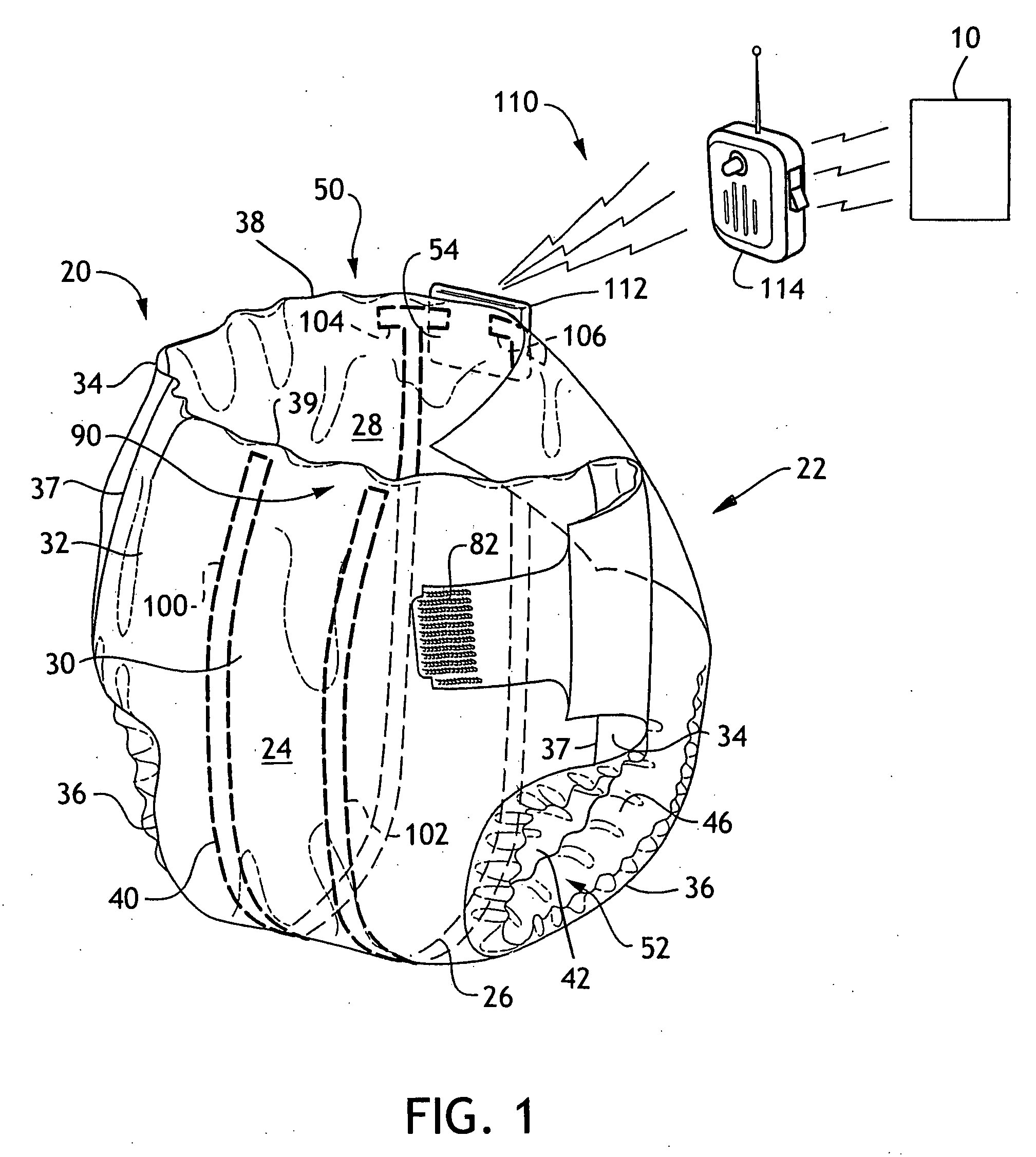
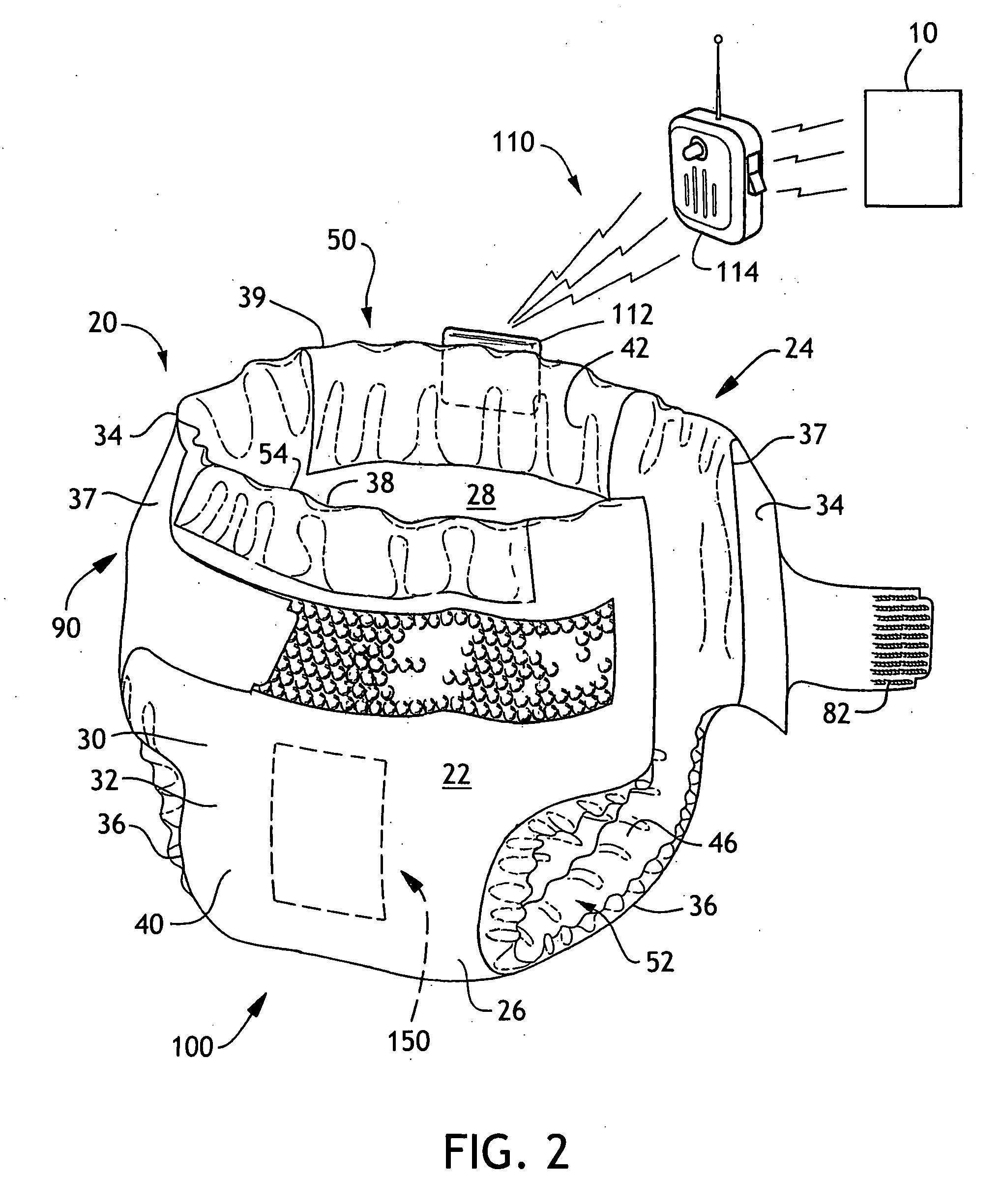
Sensing article for a home automation network
InactiveUS20080058740A1Improve convenienceEnhance interestNetwork topologiesAudible advertisingNetwork controlCombined use
Provided is a sensing system for use in conjunction with a home automation network controlling an environmental variable in a home, the system including a transmitter adapted to be used with an absorbent article having a sensor, wherein the transmitter is adapted to communicate with the sensor and directly with the home automation network. Also provided is a physiological event notification system including an absorbent article including a physiological event sensor; a home automation network controlling an environmental variable in a home; and a transmitter associable with the absorbent article and in signal communication with the physiological event sensor and with the home automation network.
Owner:KIMBERLY-CLARK WORLDWIDE INC
Method and system for virtualization of software applications
A method of virtualizing an application to execute on a plurality of operating systems without installation. The method includes creating an input configuration file for each operating system. The templates each include a collection of configurations that were made by the application during installation on a computing device executing the operating system. The templates are combined into a single application template having a layer including the collection of configurations for each operating system. The collection of configurations includes files and registry entries. The collections also identifies and configures environmental variables, systems, and the like. Files in the collection of configurations and references to those files may be replaced with references to files stored on installation media. The application template is used to build an executable of the virtualized application. The application template may be incorporated into a manifest listing other application templates and made available to users from a website.
Owner:CODE SYST CORPOATION
Method and system for tracking client software use
A method and system for tracking client software use is disclosed. User data, specifically user interaction with a client-installed software application, is collected in data files and the data files are dynamically uploaded over a global computer system, such as the Internet, to a remote analysis system. The data files are parsed for on-going analysis of feature usage. Typically, for any action that a user performs in the software application, several items are recorded in a data file, such as a user ID, an absolute time-stamp, the method invoked including application source (if the software application includes more than one application), and details such as the dialog invoked, button pressed, menu used, menu item selected, application launch, application termination, as well as environment variables, such as operating system, screen resolution, etc.
Owner:MICROSOFT TECH LICENSING LLC
Environmental monitoring and control system
A wireless environmental monitoring system is disclosed comprising at least one monitor unit in wireless communication with a remote monitoring centre by way of the Internet and a server unit wherein the server unit is in wireless communication with both the monitor unit and the remote monitoring centre. The monitor unit comprises at least one sensor configured to detect an anomalous environmental condition such as the presence of or undesirable change in environmental variables. The monitor unit further comprises an alarm system and a relay output wherein the relay output is configured to trigger an event in response to the anomalous environmental condition to mitigate damage that may be caused by the anomalous environmental condition. The remote monitoring centre is configured to receive and monitor the operational parameters of the monitor unit to interpret an anomalous environmental condition detected by the monitor unit in light of operational variations which may affect the accuracy of the monitor unit. The remote monitoring centre is also configured to receive and communicate environmental data to the monitor unit to establish the base threshold level used to determine an anomalous environmental condition.
Owner:SINKEVICIUS VYTAS +1
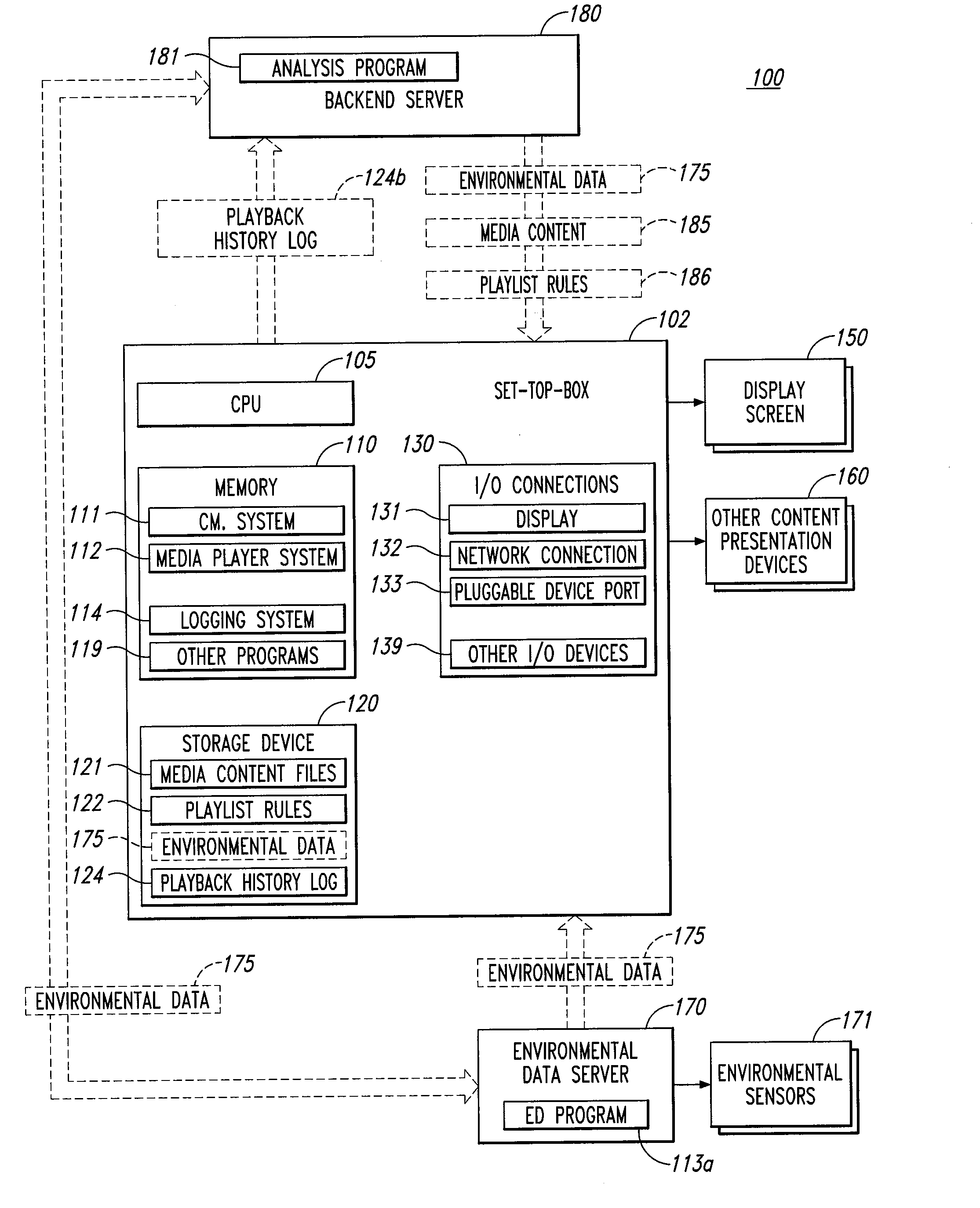
Media delivery system
A media delivery system that may be used for tracking the number and type of human impressions of media content rendered by the system during the time the media was rendered is provided. The media delivery system includes a rendering device for rendering media content, an environmental sensor for sensing impressions and other environmental variables and a computing device configured to gather data related to the external states detected by the environmental sensor. The data may be provided to a backend server for correlating the data to the rendered media content. The system may include rules that interpret that data and may cause the system to custom select, tailor or control future playback of media on the system.
Owner:VULCAN IP HLDG
Compositing desktop window manager
InactiveUS7839419B2Memory adressing/allocation/relocationDigital computer detailsWindow managerOperational system
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatus for automated mangement of software
InactiveUS20060010425A1Reduce and avoidSimple methodVersion controlSpecific program execution arrangementsSoftware development processSoftware configuration management
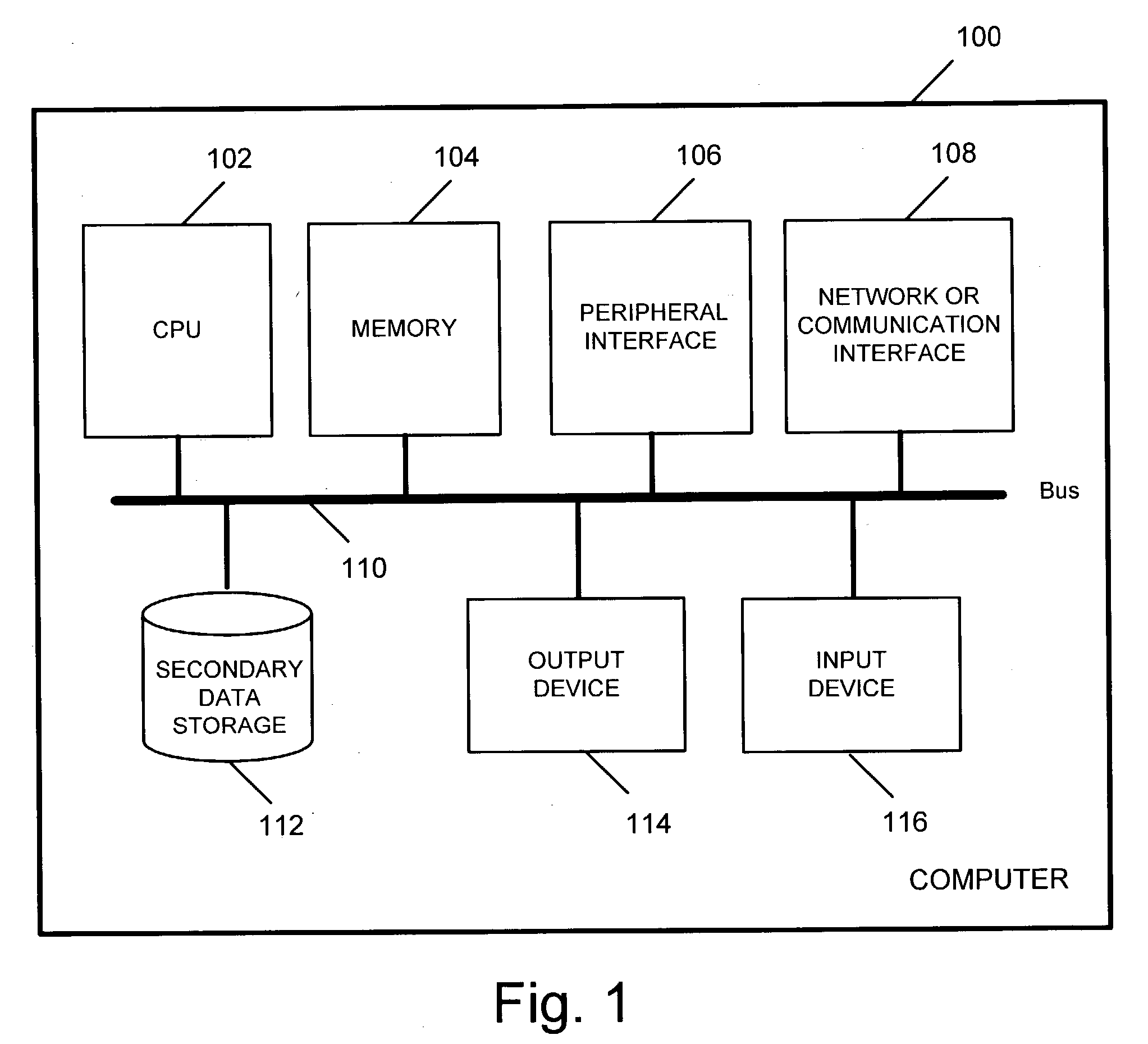
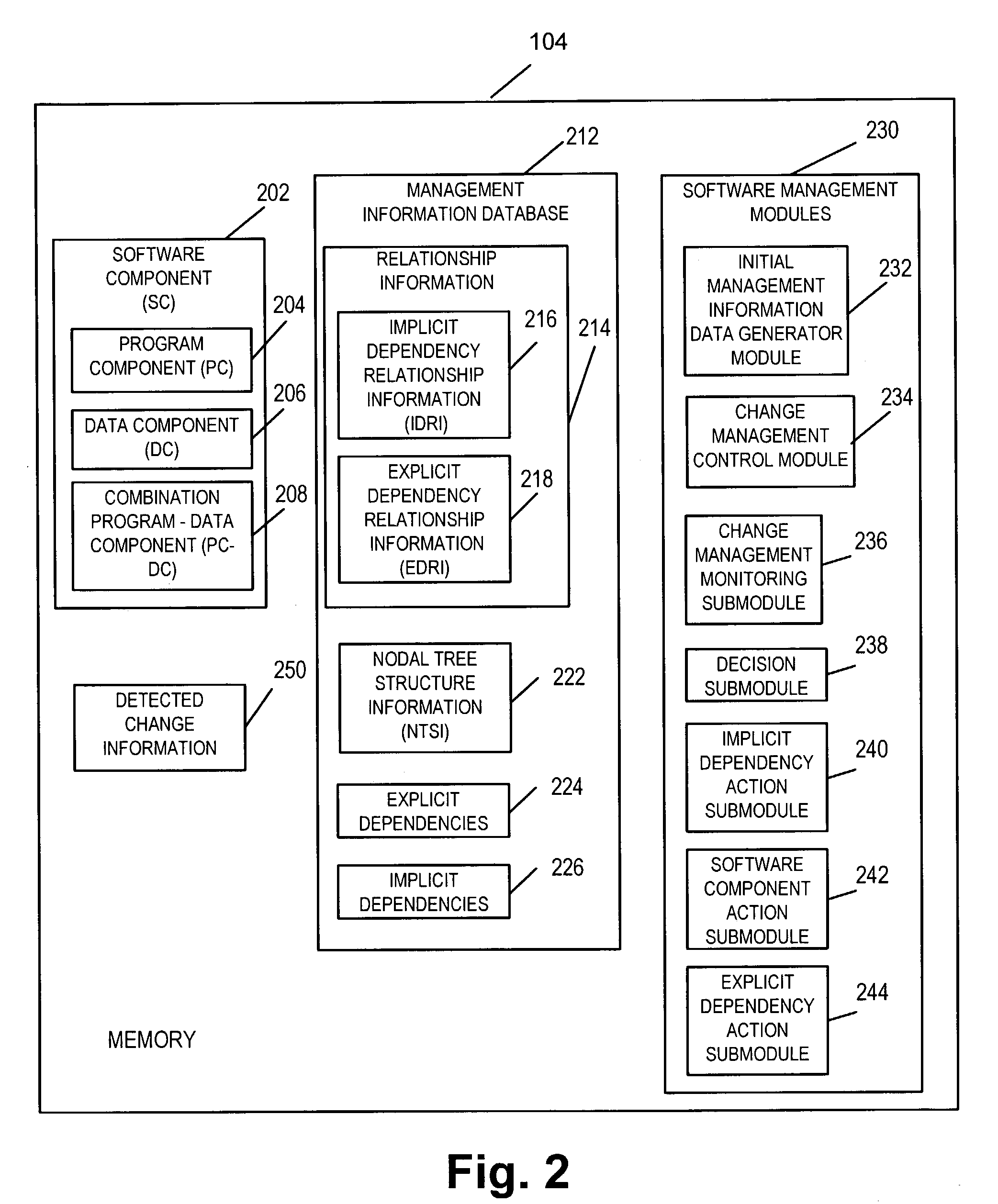
Software management methods and apparatus for performing software configuration management operations and for supporting build processes are described. Both implied and explicit dependency relationship information is captured and intelligently used in an automated fashion avoiding or reducing the need for human tracking of such relationships. Temporary or non-persistent data elements used during various phases of the software development process are automatically detected, including for example environment variables and their values and the versions of tools used to operate on the software components. A persistent association is created and stored between the normally temporary data element(s) and the software component(s) they affect. Implicit dependencies between data elements and software components are also automatically updated and revision-controlled, making historical and current implicit dependencies persistent. A software management information data base including implicit dependency relationship and explicit dependency relationship information is created. The information reflects explicit or implied relationships between various software components.
Owner:AAVIOM
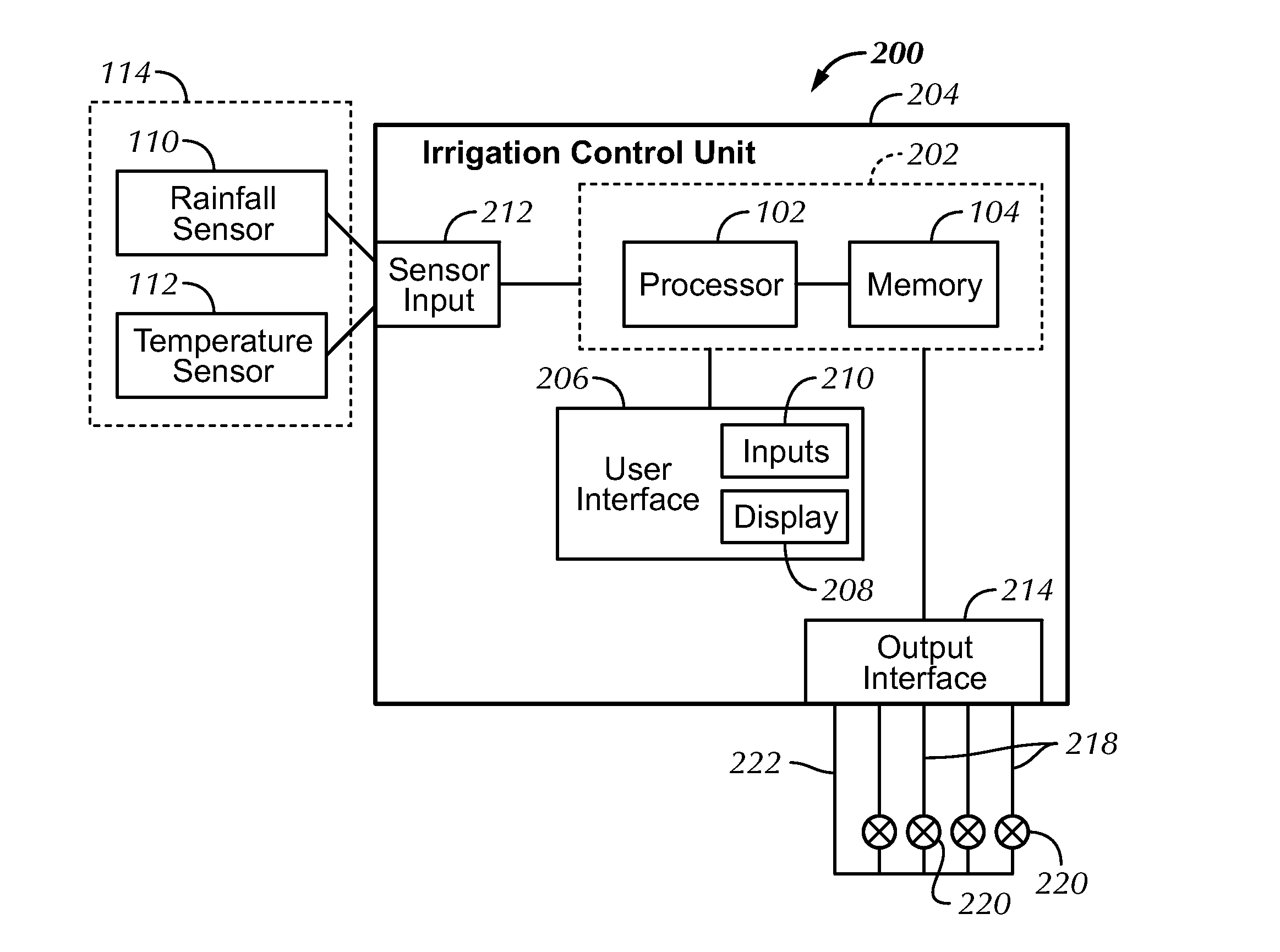
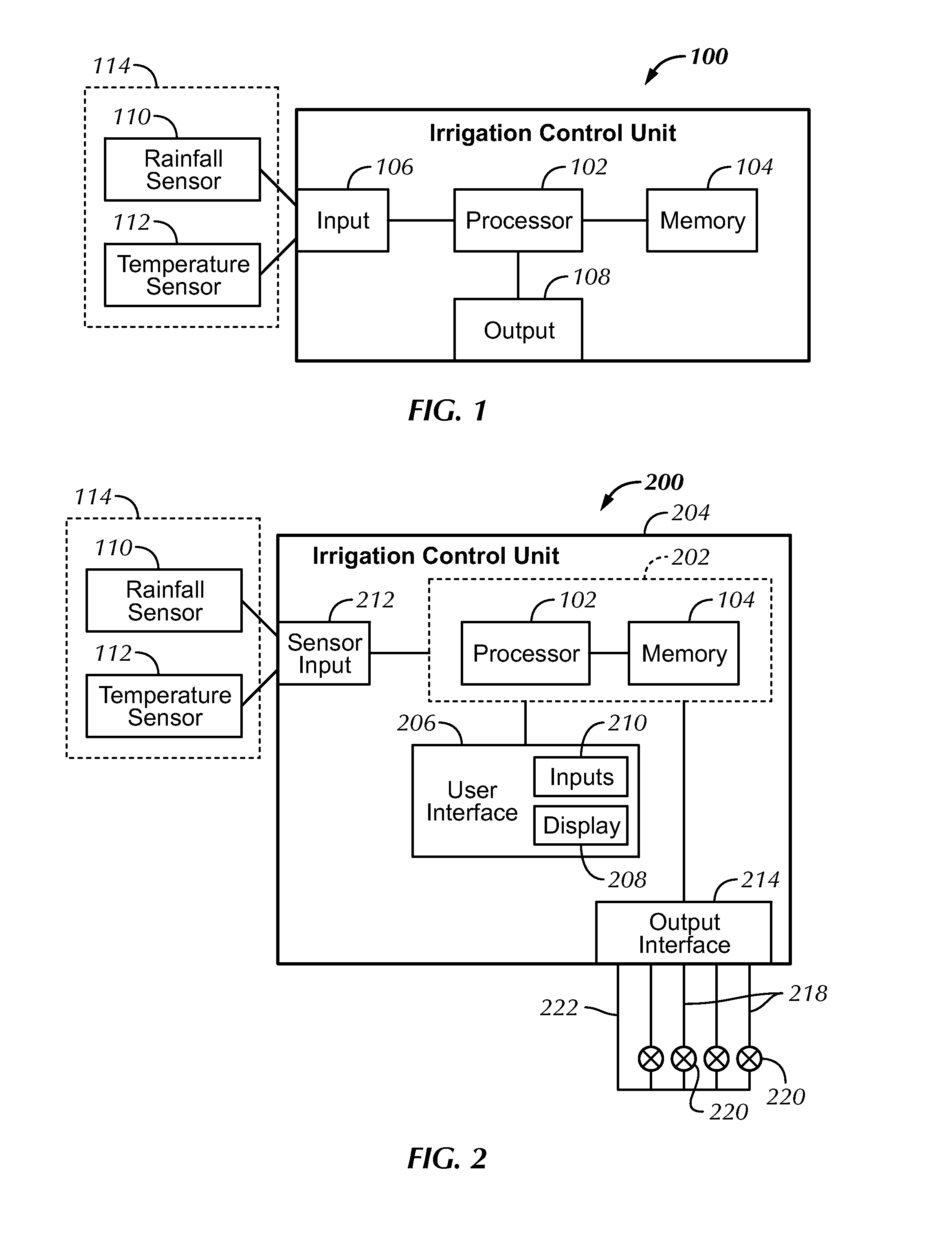
Automatically Adjusting Irrigation Controller
Methods and devices are provided to automatically determine plant water requirements and adjust irrigation in order to make efficient use of water. In one implementation, the invention may be characterized as a method comprising: receiving, user entered historical values of one or more environmental variables, wherein the historical values correspond to a geographic region and storing the historical values in a memory; receiving current values of one or more environmental variables useful in determining the plant water requirements from one or more sensors, the values corresponding to a geographic region and the other environment variables being different from the one or more environmental variables and storing the current values in the memory; and determining the plant water requirements based at least in part on the user entered historical values and the current values of the one or more other environmental variables.
Owner:RAIN BIRD CORP
Smarter-grid: method to forecast electric energy production and utilization subject to uncertain environmental variables
InactiveUS8600572B2Improve accuracyMechanical power/torque controlLevel controlSmart gridEngineering
A method to forecast the energy sources and energy sinks to facilitate continuous capacity planning, regulation and control of energy state of an entity under variable weather condition is established. Energy sources of specific focus are related to renewable energy forms from wind, solar and wave that are highly dependent on prevailing weather conditions.
Owner:IBM CORP +1
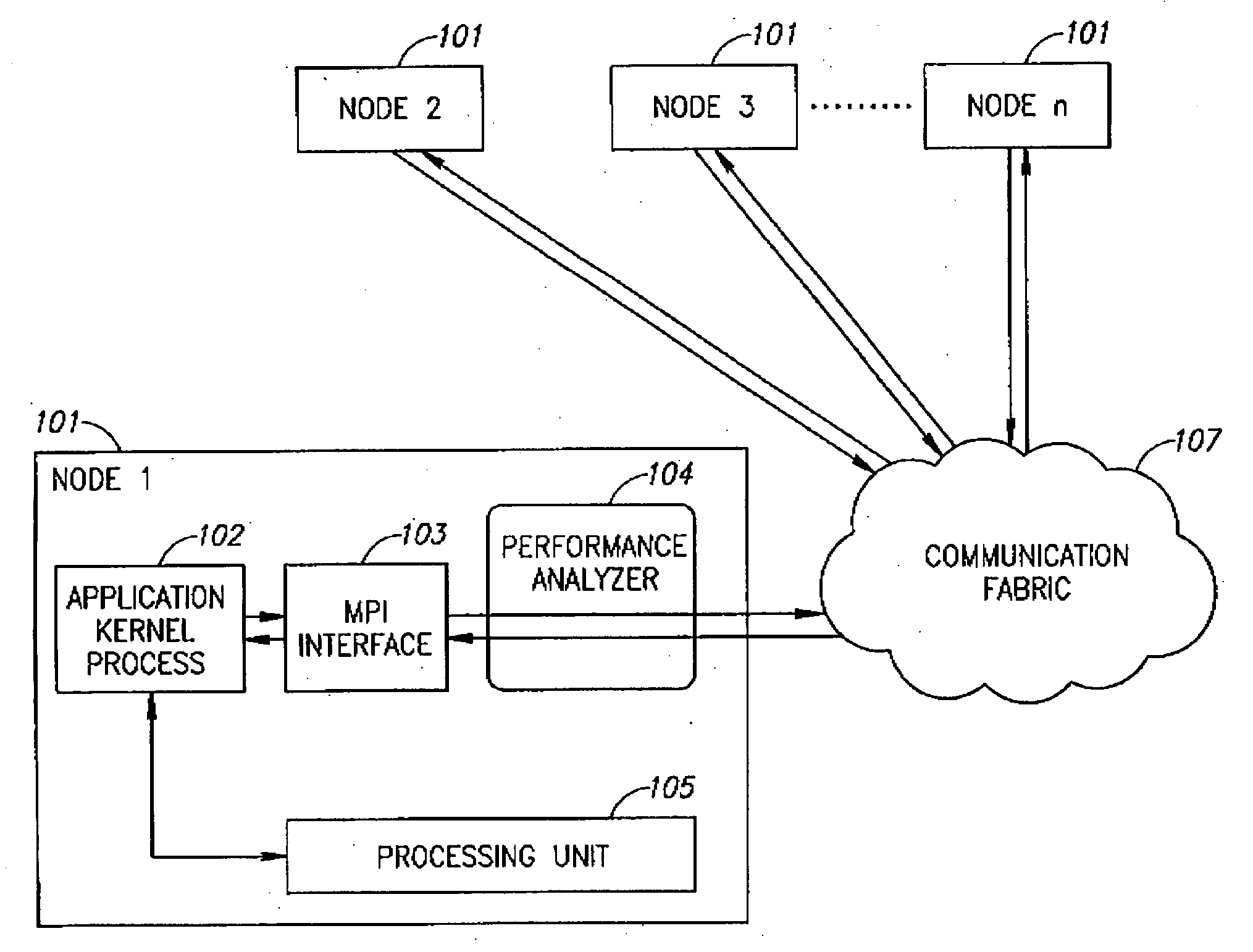
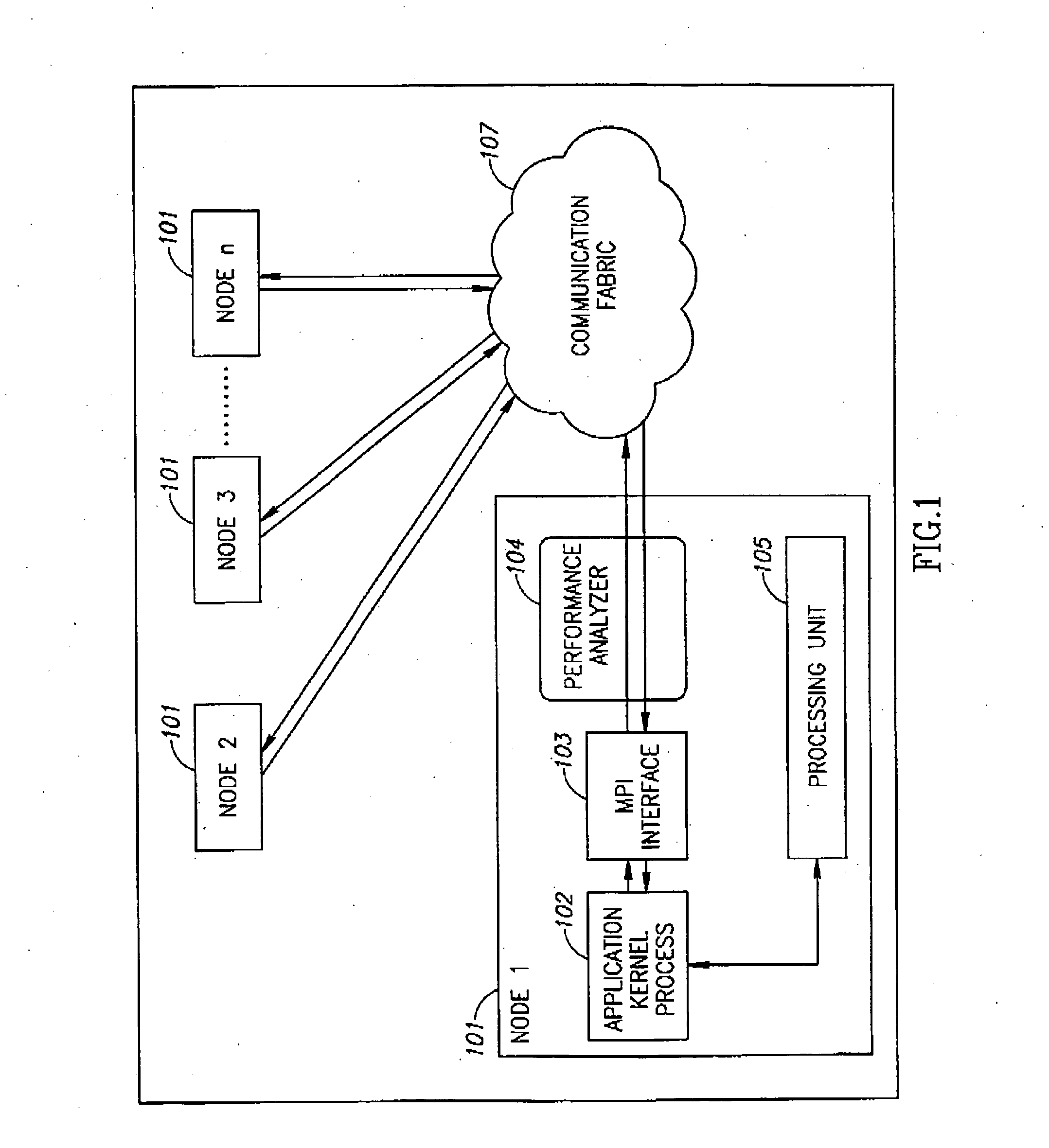
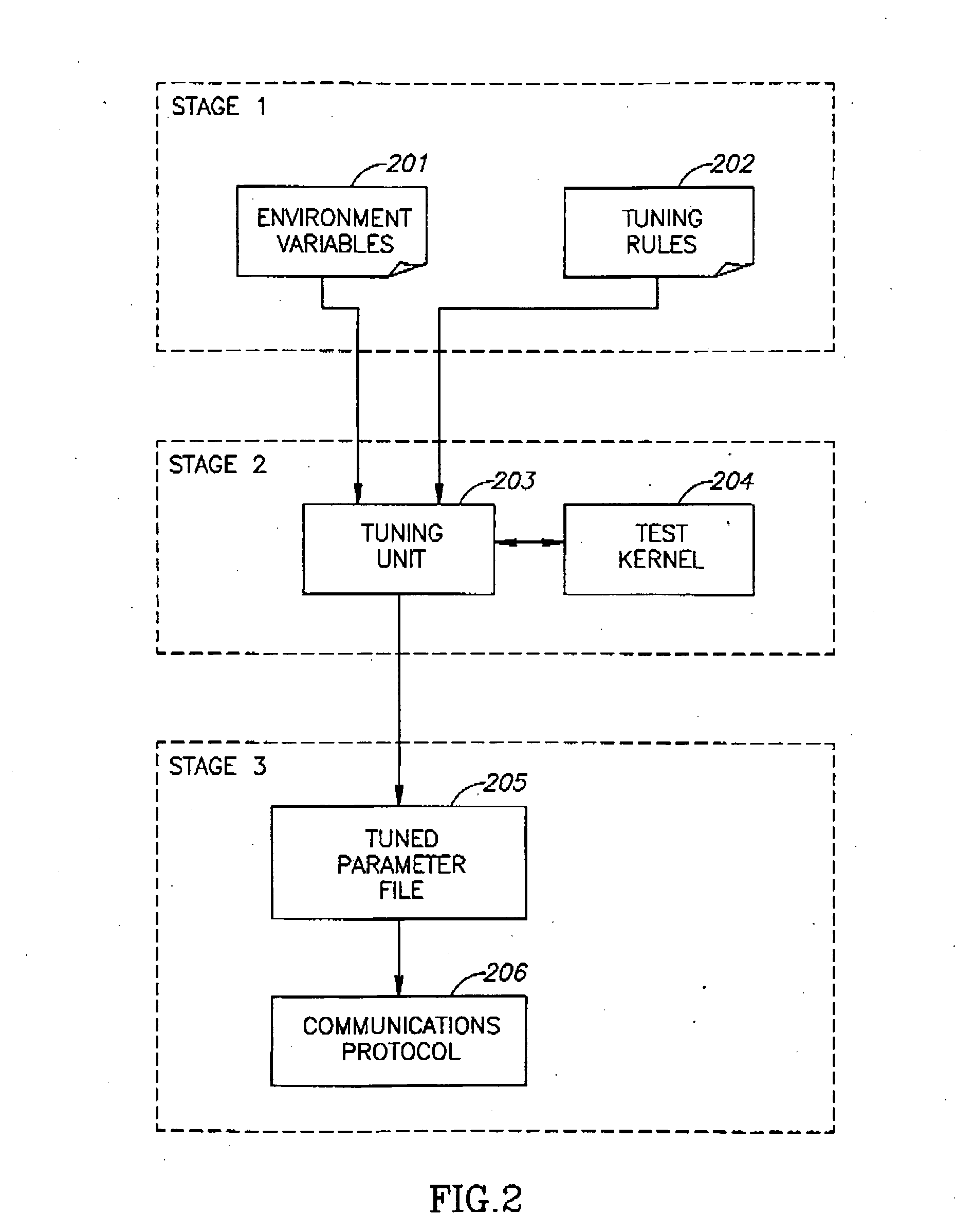
Automatic tuning of communication protocol performance
InactiveUS20090129277A1Error preventionFrequency-division multiplex detailsMessage Passing InterfaceApplication software
A method or device may optimize applications on a parallel computing system using protocols such as Message Passing Interface (MPI). Environment variables data may be used as well as a test kernel of an application to optimize communication protocol performance according to a set of predefined tuning rules. The tuning rules may specify the output parameters to be optimized, and may include a ranking or hierarchy of such output parameters. Optimization may be achieved through use of a tuning unit, which may execute the test kernel on the parallel computing system, and may monitor the output parameters for a series of input parameters. The input parameters may be varied over a range of values and combinations. Input parameters corresponding to optimized output parameters may stored for future use. This information may be used to adjust the application's communication protocol performance “on the fly” by changing the input parameters for a given usage scenario.
Owner:INTEL CORP
Systems and methods for adjusting a sighting device
Systems and methods usable to facilitate adjustments to a sighting device, such as a scope. In one example, an adjustment calculator associated with the scope receives data relating to a distance to a target and relating to at least one environmental variable, such as for example, wind and / or humidity, which may affect the trajectory of a projectile. The adjustment calculator processes the data and calculates a recommended scope adjustment. For instance, the adjustment calculator may output a number of adjustment “clicks” for a rifle scope in order to at least partially compensate for the distance and / or the environmental variable(s). In another example, the adjustment calculator receives data relating to properties of ammunition that may affect the trajectory of the ammunition.
Owner:MEADE INSTRUMENTS
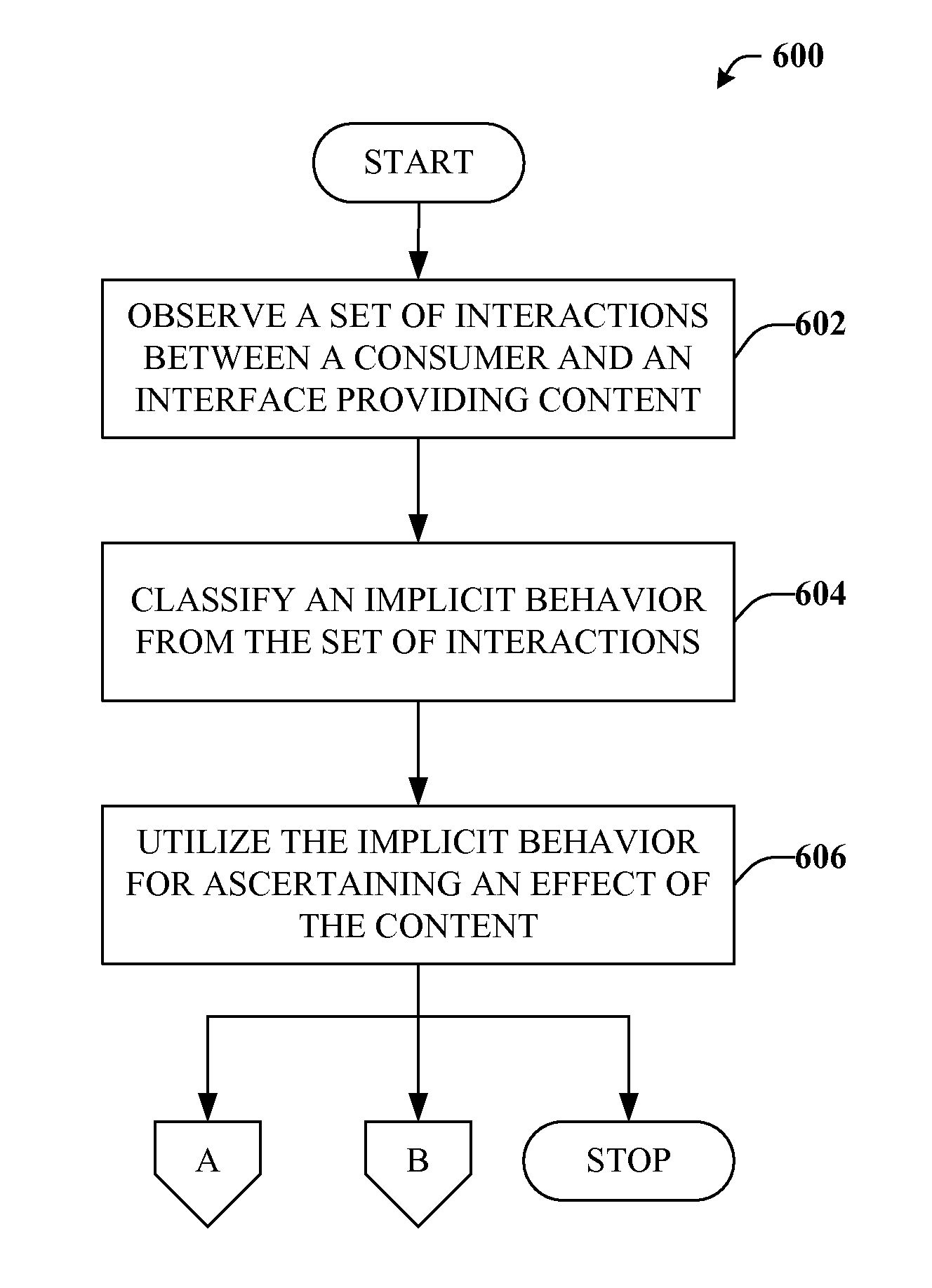
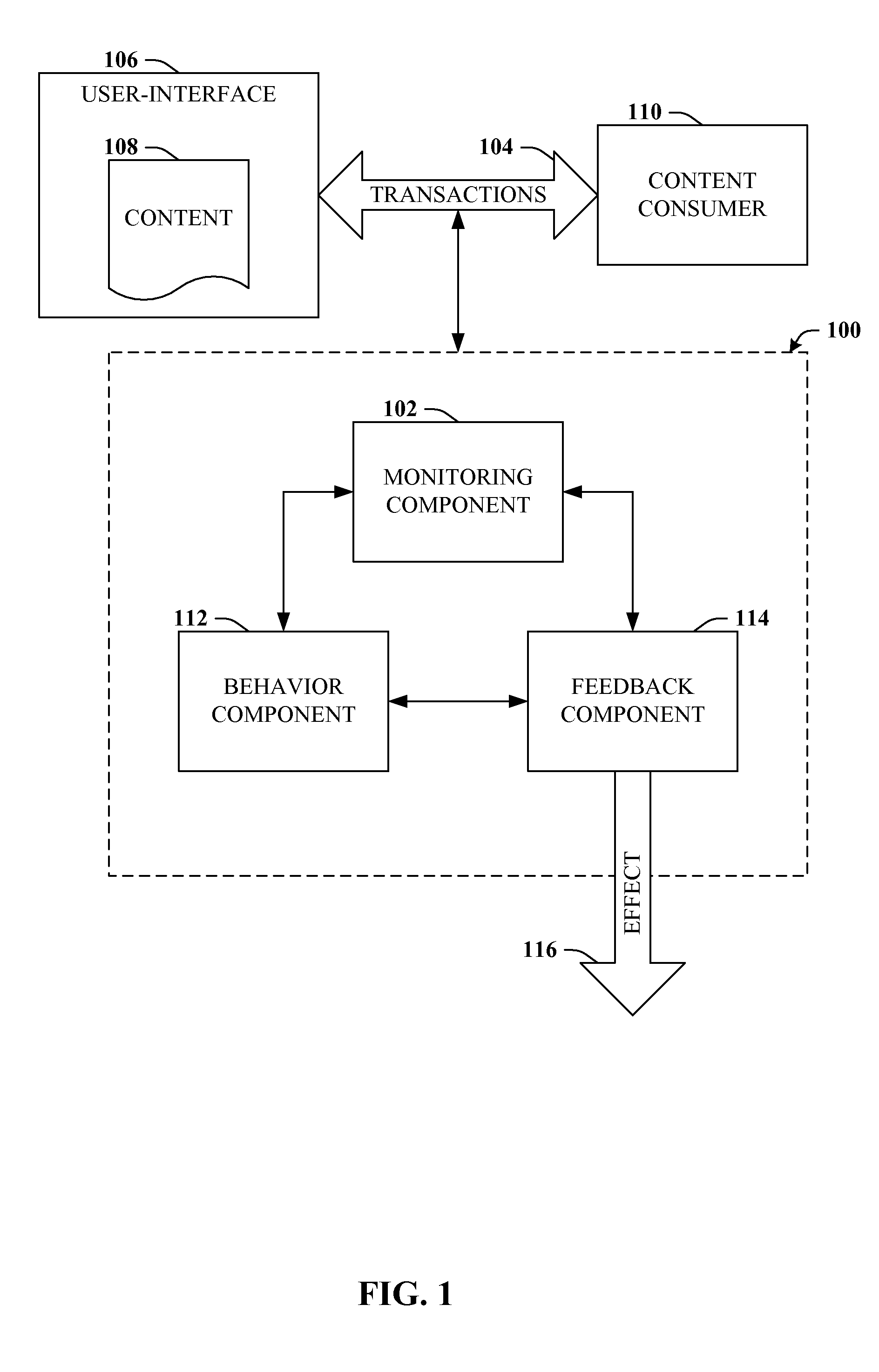
Mining implicit behavior
InactiveUS20080319827A1Special data processing applicationsMarket data gatheringSubject matterUser interface
The claimed subject matter relates to an architecture that can monitor transactions between a content consumer and a user-interface that provides the content. The architecture can also monitor environment variables that relate to a content consumption environment. From one or both of these potential sources, the architecture can identify implicit behavior on the part of the content consumer that relates to the consumption of the content. The implicit behavior can be employed to determine or infer effects of the consumed content, which can supplement, enhance, or replace conventional explicit consumer feedback.
Owner:MICROSOFT TECH LICENSING LLC
Operating system abstraction and protection layer
InactiveUS7451451B2Inhibition of informationInterprogram communicationMemory systemsOperational systemConfiguration item
Owner:MICROSOFT TECH LICENSING LLC +1
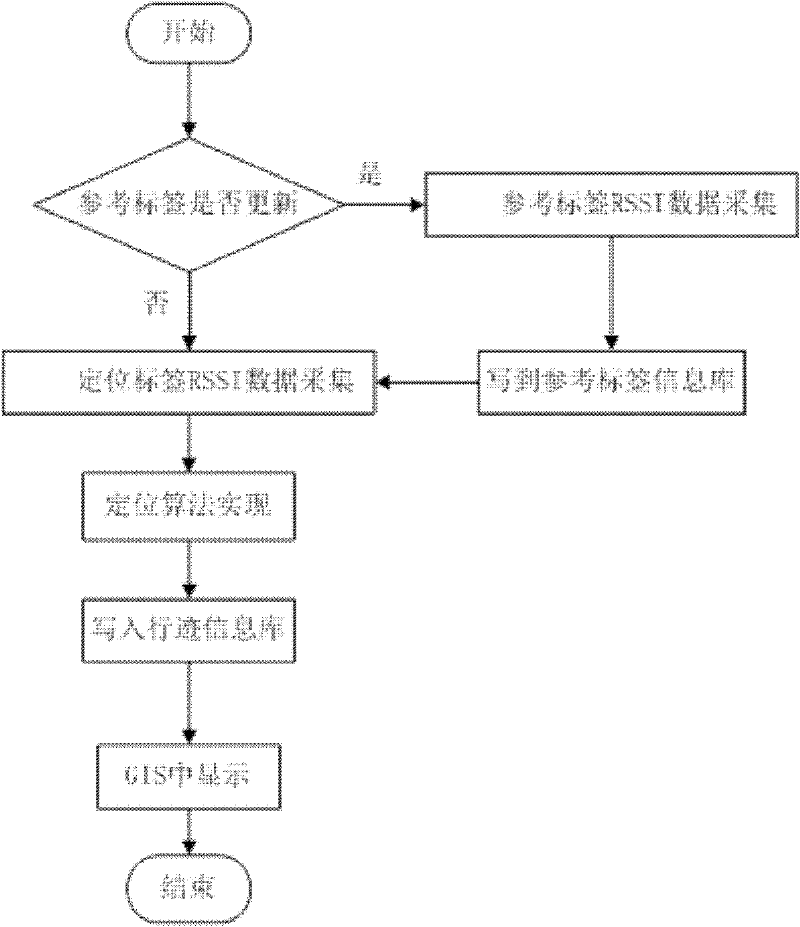
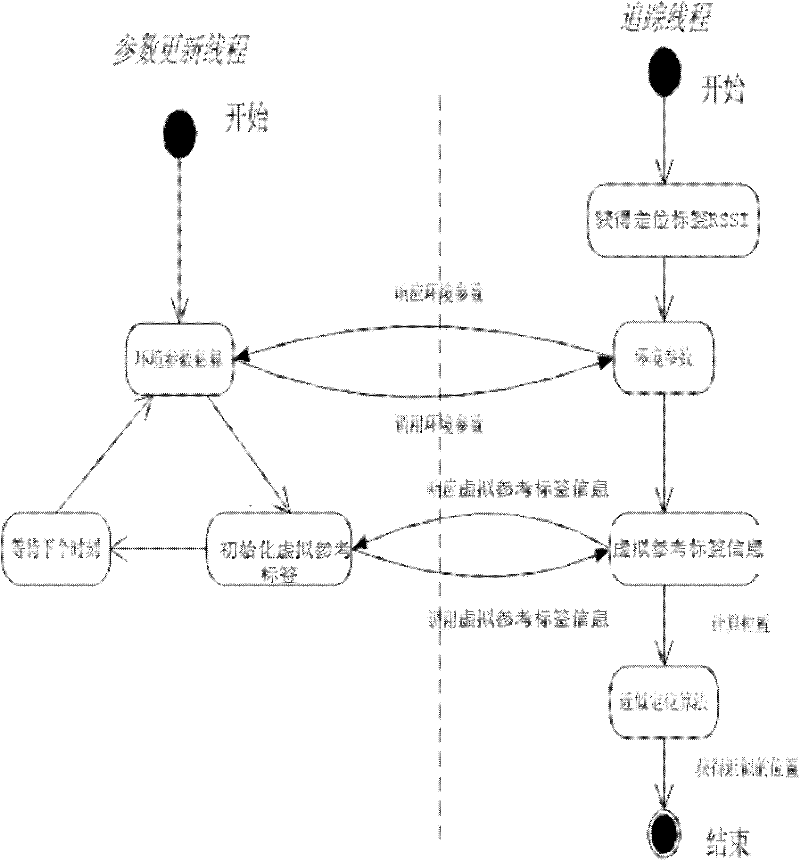
Radio frequency indoor positioning method based on virtual tag algorithm
InactiveCN102338866ACounteracts the defect of mutual interference of intensitiesOvercoming the problem of positioning accuracy distortionPosition fixationHigh densityPath loss exponent
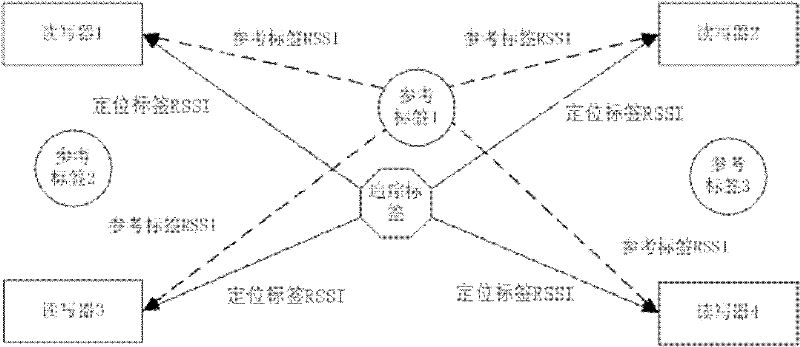
The invention discloses a radio frequency indoor positioning method based on a virtual tag algorithm. A reference tag is fixed at a proper position in a positioning area; the coordinate of the proper position is measured in a relatively easy way; the signal intensity of the reference tag is read through an arranged RFID (Radio Frequency Identification Device) reader / writer every a section of time so as to adapt to the influence of the environment factor variation on the positioning error; and the positioned tag is attached to a target to be positioned; estimating the position of the tag in the space through the positioning tag signal received by the RFID reader / writer, wherein the method is implemented according to the following steps of: first, estimating an environment variable, wherein the estimation includes path consumption index estimation and normal distribution standard deviation estimation; and then constructing a virtual reference tag; and finally, realizing the positioning algorithm according to the virtual reference tag. By using the indoor positioning method disclosed by the invention, the problem of radio frequency signal interference brought by the setting of the high-density reference tag in the prior art is overcome, and flexible layout of the reference tag is obtained; meanwhile, the range of the positioning area is expanded and the indoor positioning precision is improved.
Owner:XIAN UNIV OF TECH
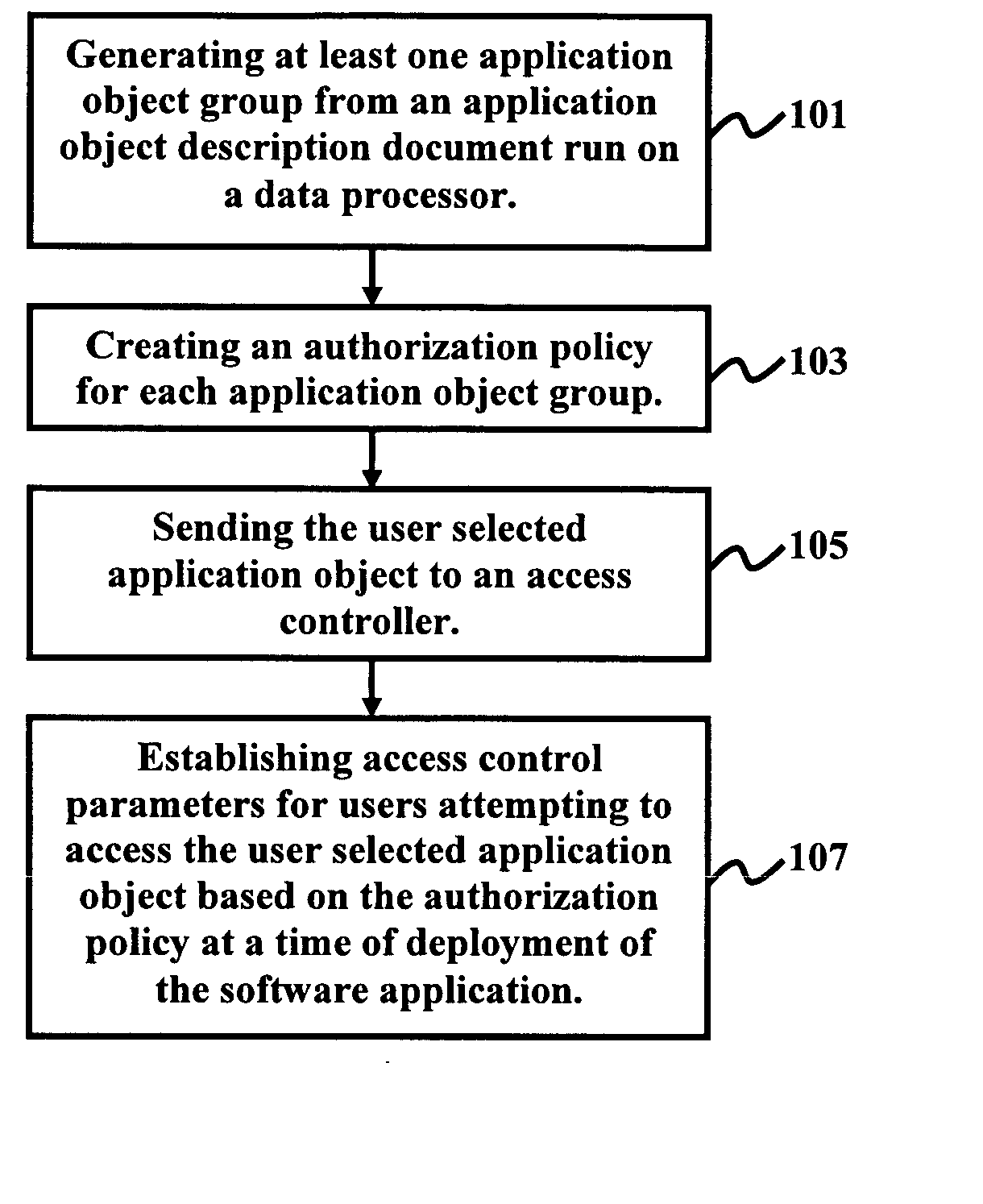
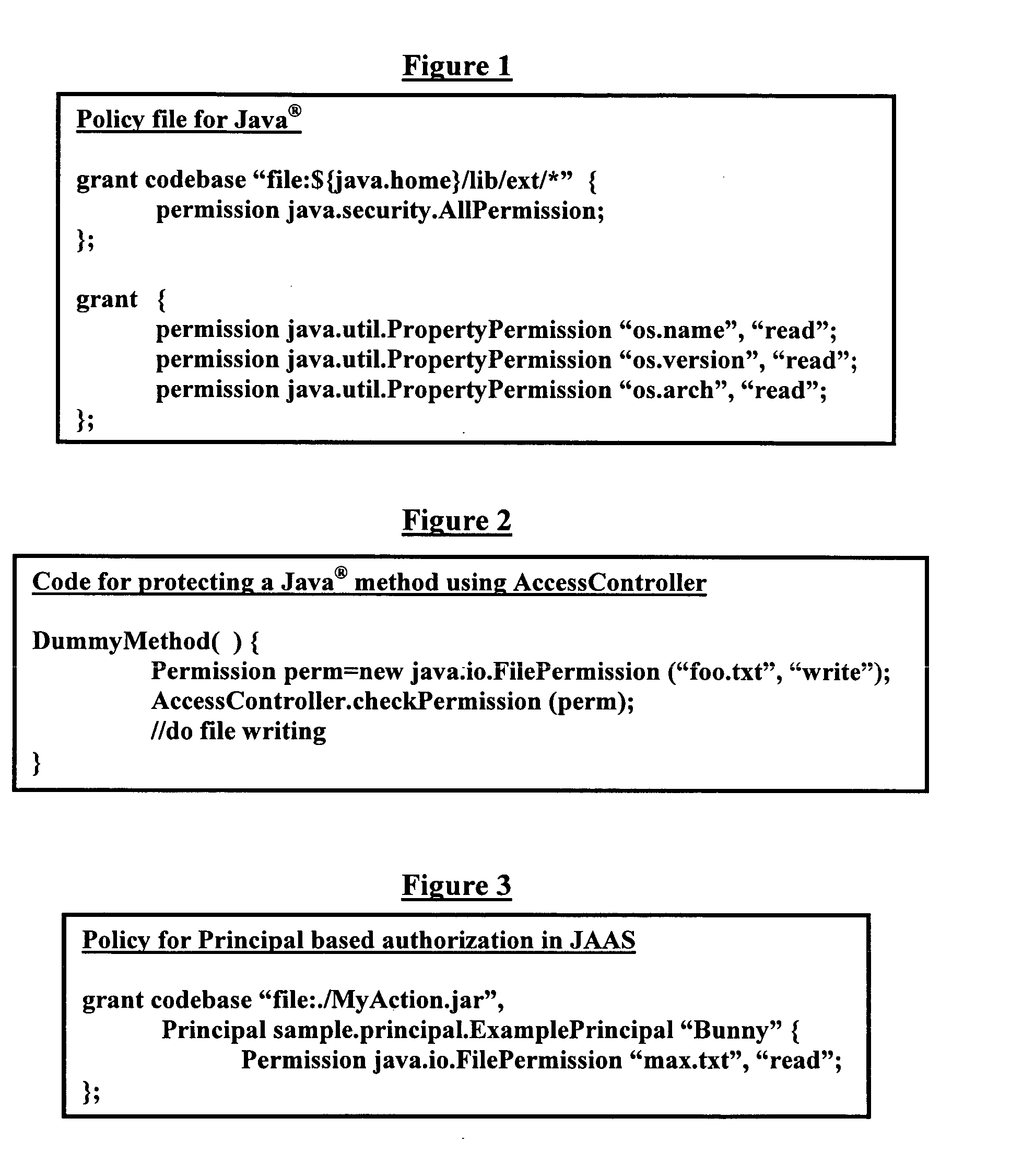
Generic declarative authorization scheme for Java
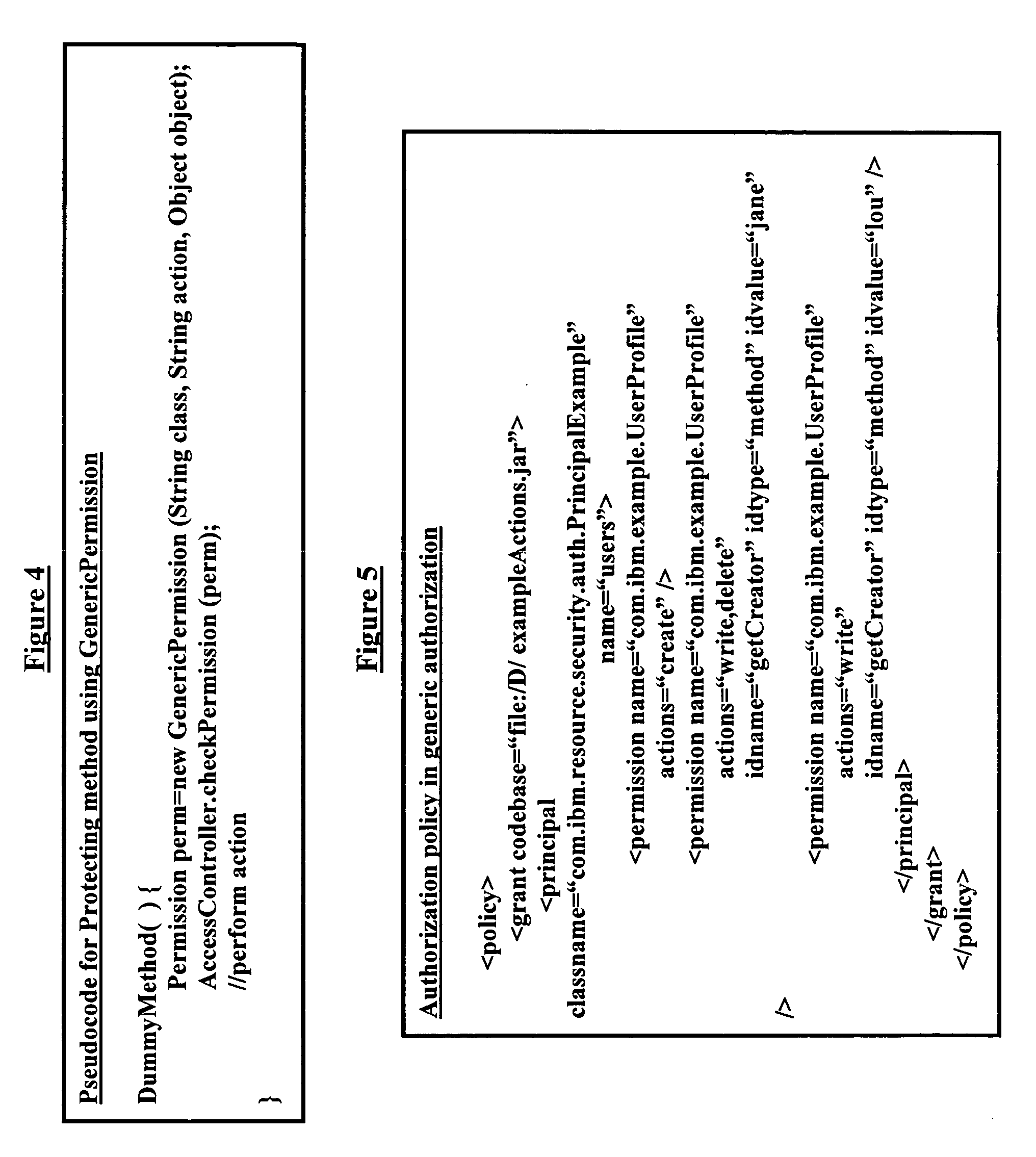
InactiveUS20060026667A1Digital data protectionProgram/content distribution protectionPaper documentDocument preparation
A method, system, and program storage device for establishing security and authorization policies for users accessing a software application, wherein the method comprises generating at least one application object group from an application object description document comprising an XML format run on a data processor; creating an authorization policy for each application object; sending a selected application object group to an access controller; and establishing access control parameters at a time of deployment of the software application for users attempting to access the selected application object group based on the authorization policy. The method further comprises specifying environmental variables for the authorization policy; changing the authorization policy by modifying a declarative specification of the environmental variables and modifying constraints defined on attributes of an application object; implementing varied classes of authorization policies using a same authorization policy classifier; and specifying the application object group using grouping parameters.
Owner:IBM CORP
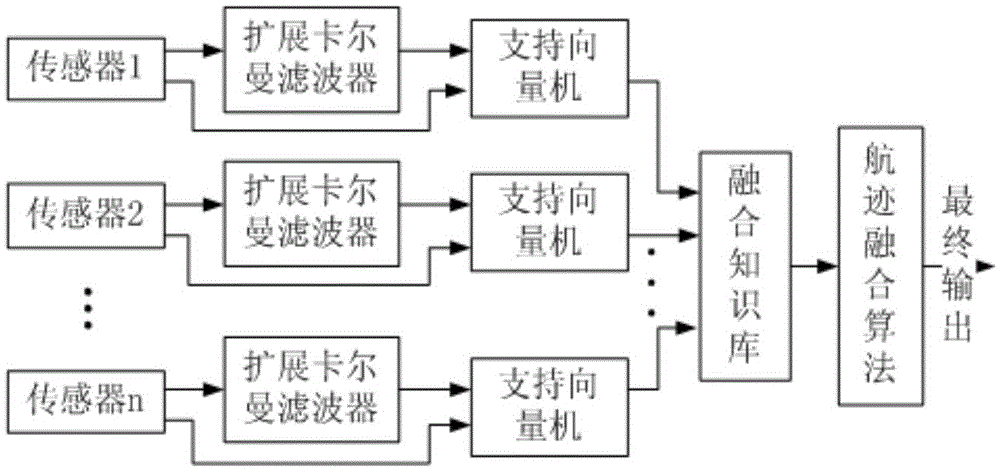
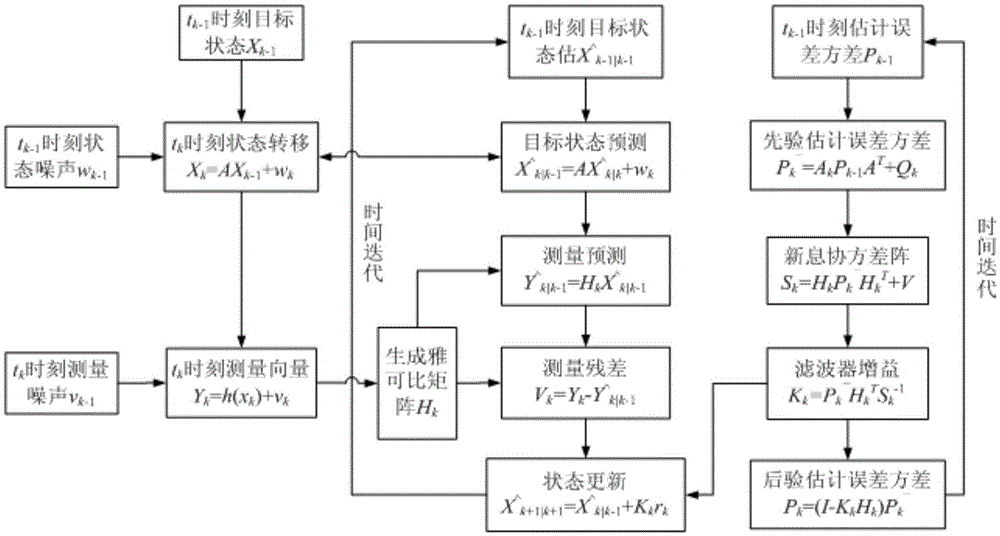
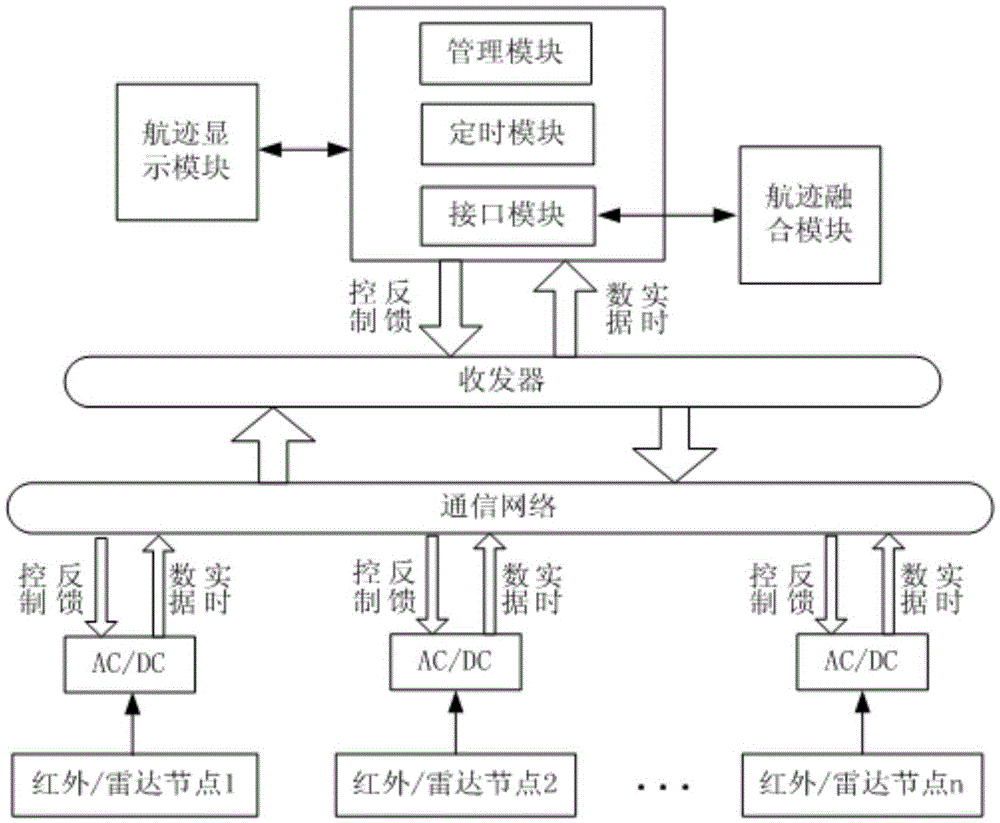
SVM (Support Vector Machine)-based multi-sensor target tracking data fusion algorithm and system thereof
InactiveCN105467382AReduce complexityReduce uncertaintyRadio wave reradiation/reflectionFault toleranceObjective information
The invention discloses a SVM (Support Vector Machine)-based multi-sensor target tracking data fusion algorithm. According to target information acquired by sensors, a compact combination mode is adopted, the SVM serves as a middle layer, an environmental variable and a measurement variance normalized vector serve as input of the SVM, output of the SVM serves as trust of the sensor, a known training sample is used for offline training, real-time filter information is used for online estimation, and a fusion knowledge base performs track fusion through real-time weighting according to the obtained trust of the sensor. According to the SVM-based multi-sensor target tracking data fusion algorithm and the system thereof, the SVM principle is adopted, the algorithm complexity is low, the environmental variable and the measurement variance normalized vector are introduced, the biological robustness and the fault tolerance are strong, extension is easy, and the algorithm and the system thereof are applicable to the field of multi-sensor tracking.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
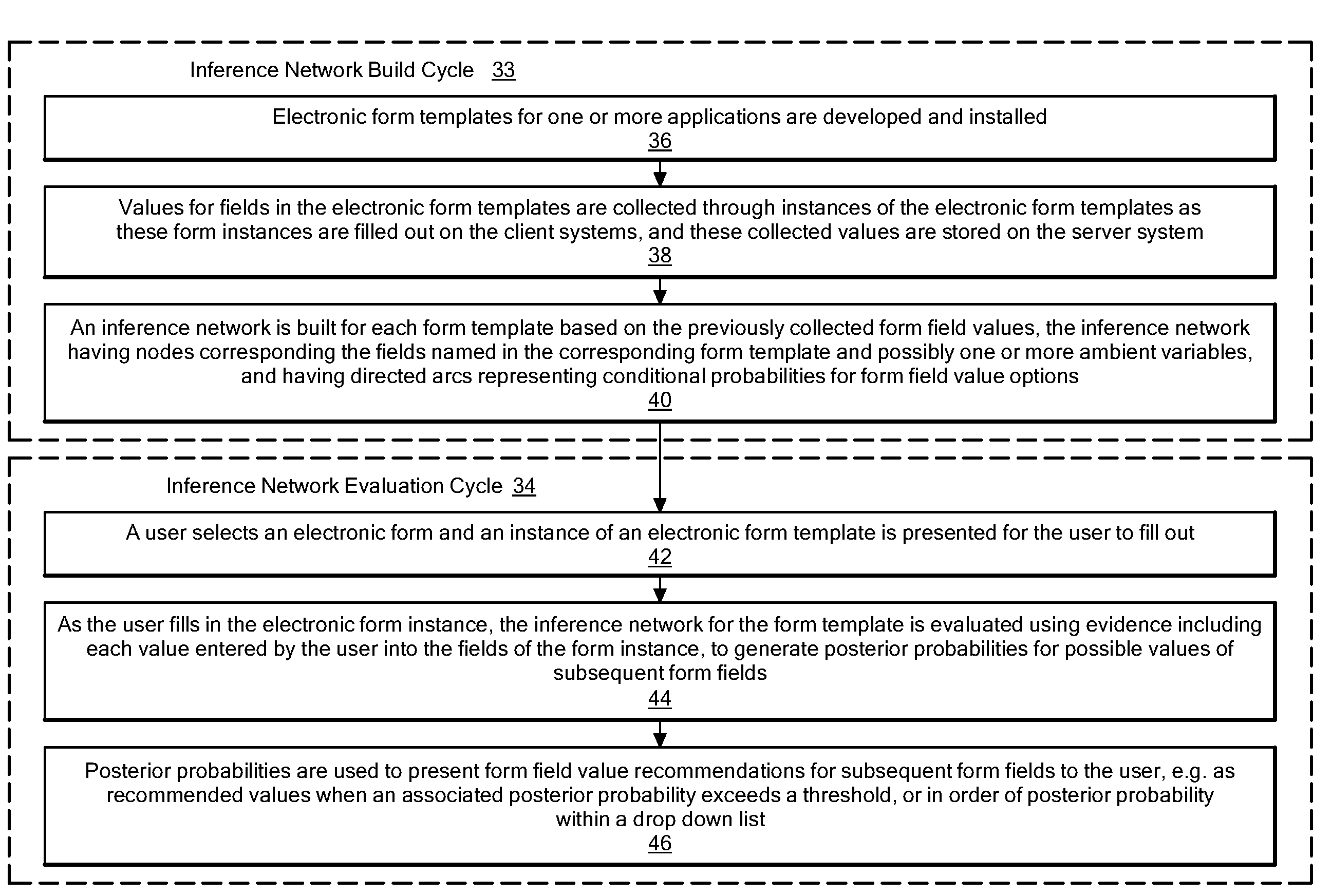
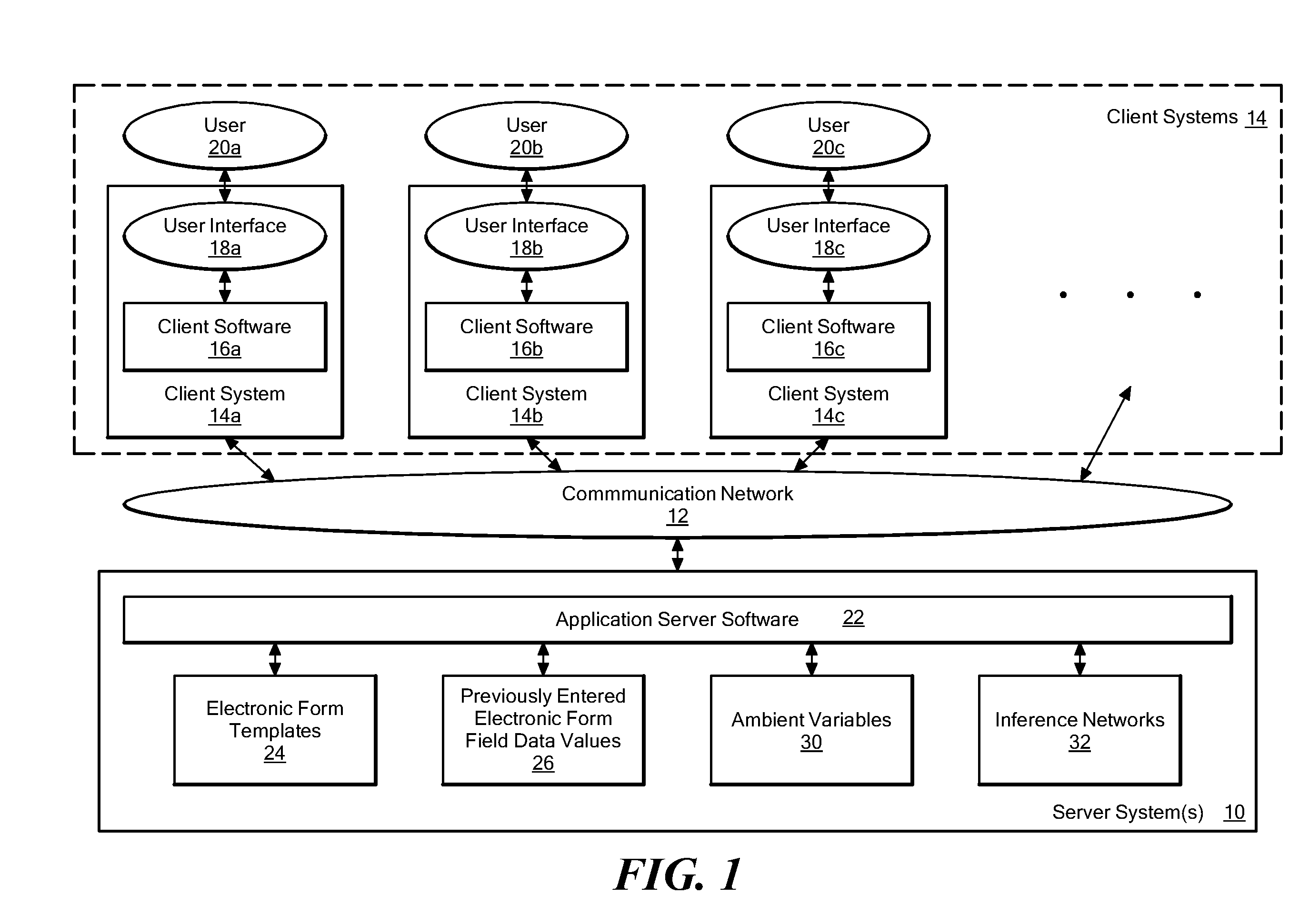
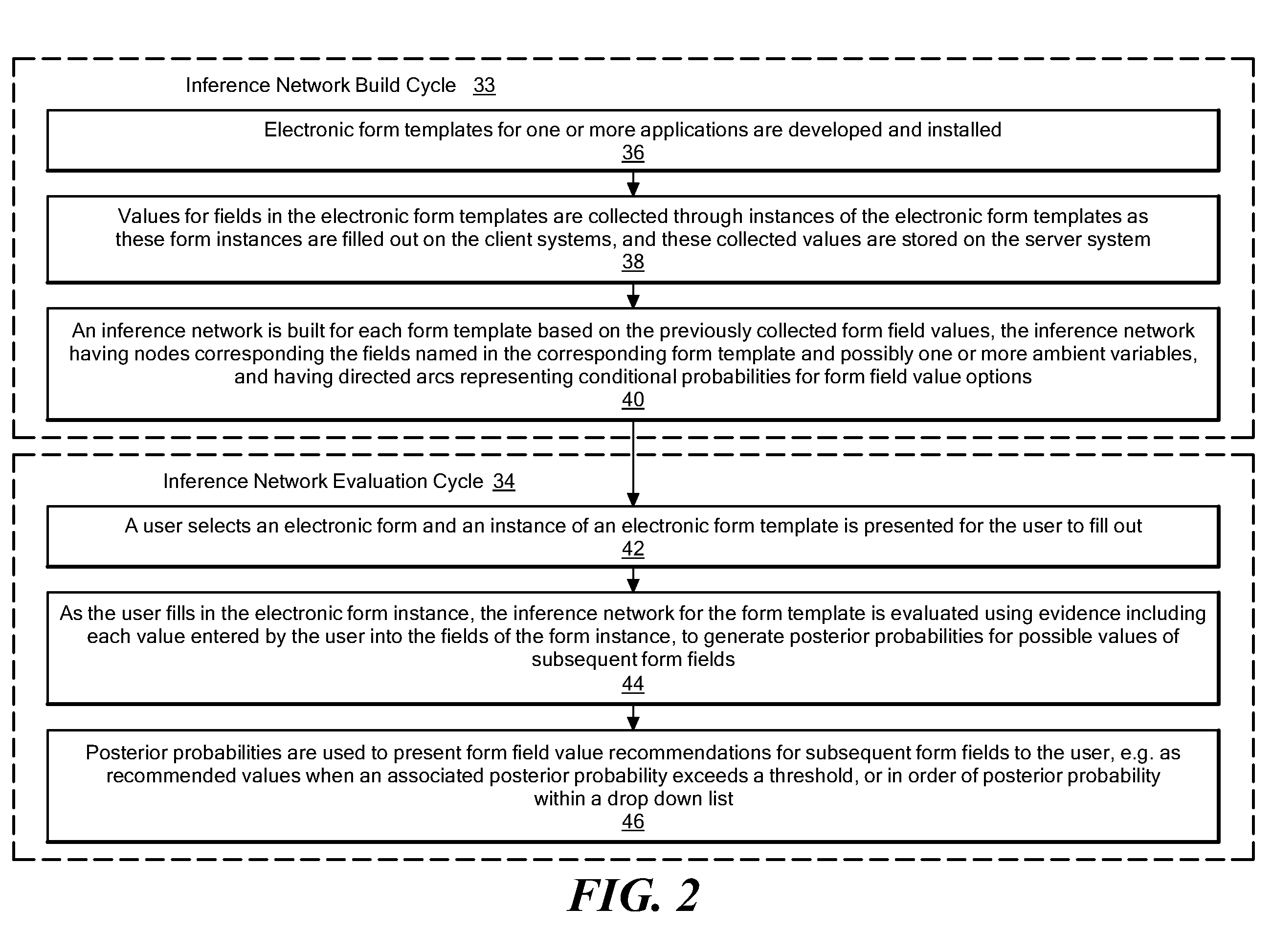
Method and system for autocompletion of multiple fields in electronic forms
InactiveUS20080154824A1Good choiceAccurate valueProbabilistic networksKnowledge representationElectronic formData mining
A method and system for autocompletion of multiple fields in electronic forms that generates “inference networks” (Bayesian networks), and evaluates them to suggest likely options for user selection while filling out fields in corresponding electronic forms. The disclosed Bayesian networks are generated and evaluated based on a broad set of information. The information used by the disclosed system for generating an inference network includes form previously selected field values. The information used in the disclosed system to evaluate an inference networks while a current instance of a given form is being filled out includes values previously entered by a current user into preceding form fields, and values of ambient variables that are external to the forms, such as current day of the week, current time of day, etc. When the inference network is evaluated in this way, posterior probabilities are determined for values of fields not yet filled out in the current form instance. These posterior probabilities are used to present value options for the unfilled fields in a way that makes selection of the most-probable options convenient to the user.
Owner:IBM CORP
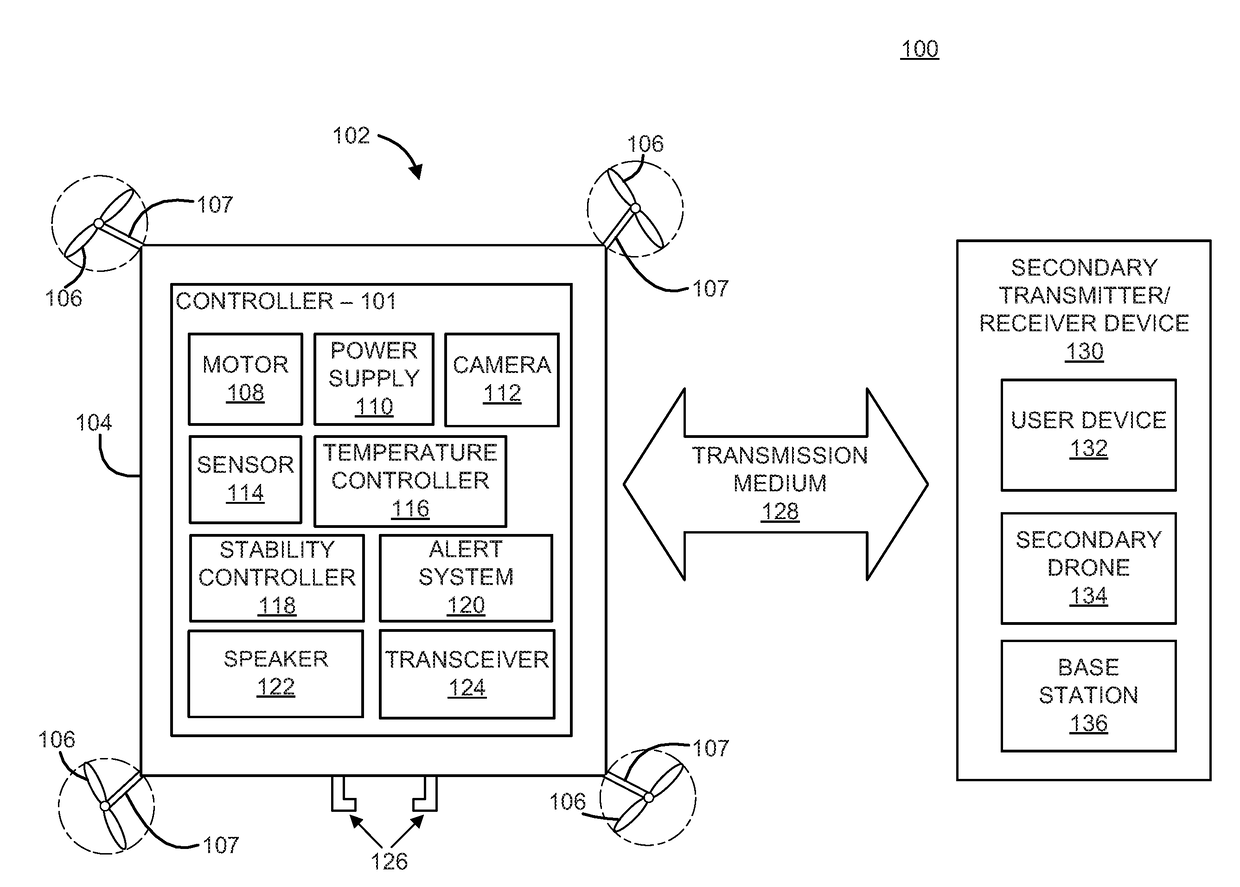
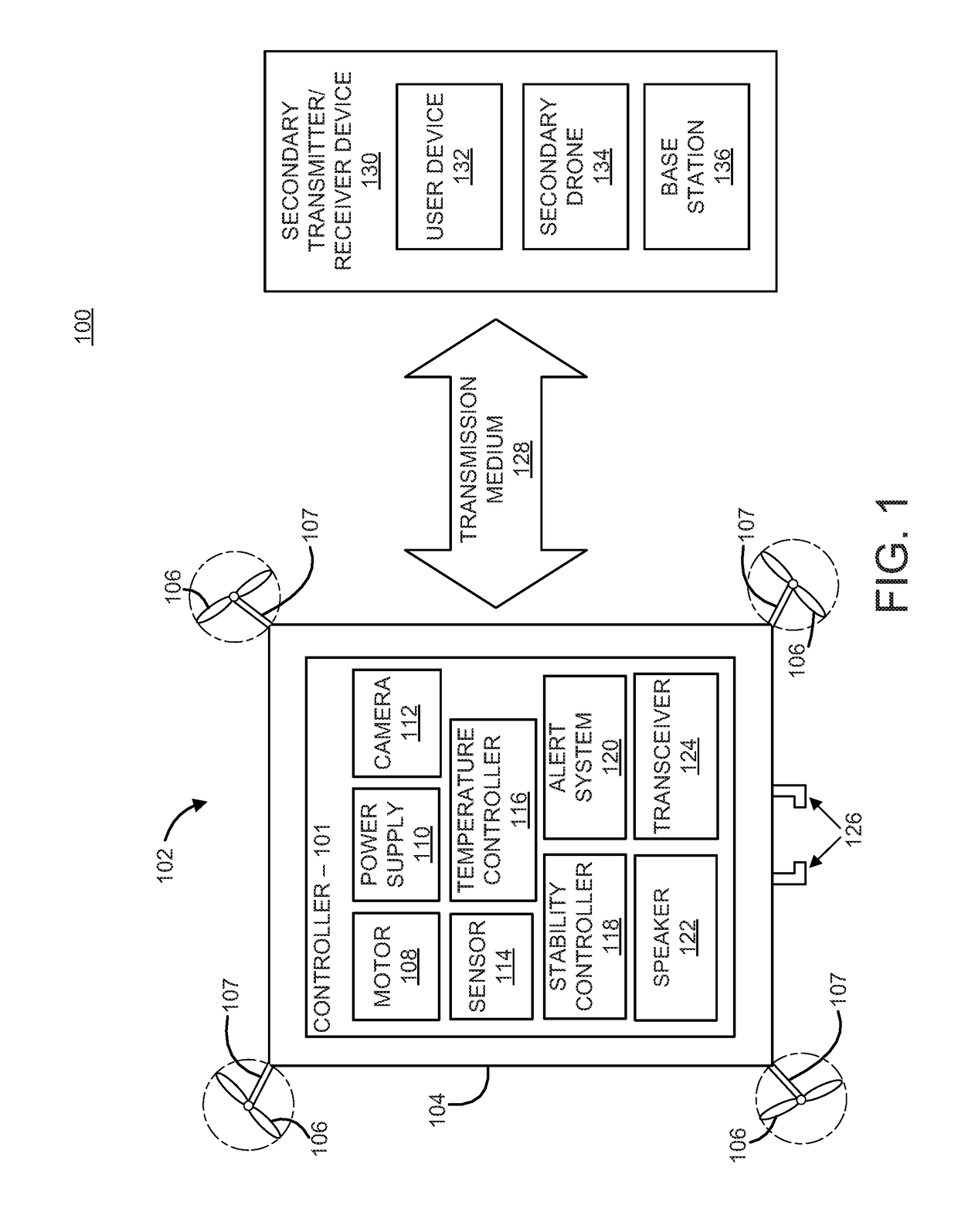
Alert system for an unmanned aerial vehicle
An unmanned aerial vehicle for aerial transportation of delivery items. The unmanned aerial vehicle includes an attachment device to fasten and unfasten one or more delivery items to the unmanned aerial vehicle, a motor to aerially transport the one or more delivery items along a delivery route, a sensor mounted on the unmanned aerial vehicle to detect at least one environmental variable during the delivery route, and an alert system to generate a status associated with the unmanned aerial vehicle along the delivery route to an observer when the environmental variable exceeds a predetermined threshold.
Owner:NEC CORP
Malware automated removal system and method using a diagnostic operating system
ActiveUS20090217258A1Automate operationImprove software performanceMemory loss protectionError detection/correctionOperational systemEvent trigger
The present invention automates the operation of multiple malware removal software products using a computerized system that systematically operates the multiple selected software products. These products are executed within a customized Diagnostic Operating System, which is different from the Normal Operating System in which the computer normally operates. Thus, any malware that may be attached to any of the programs, shells, drivers, services, or data files associated with the Normal Operating System cannot corrupt the malware removal process performed under the Diagnostic Operating System. Preferably, the Diagnostic Operating System is accessed from a read-only device prepared on a secure computer separate from the computer that is the target of the malware removal process, and the Diagnostic Operating System executes in a read-only environment. Because many malware removal products rely upon the environment provided by the Normal Operating System, the Diagnostic Operating System must provide redirection to ensure such products perform as expected. Event-triggered redirection of environment variables may be done by either injection of values, or by interception of name / key invocations.
Owner:BBY SOLUTIONS
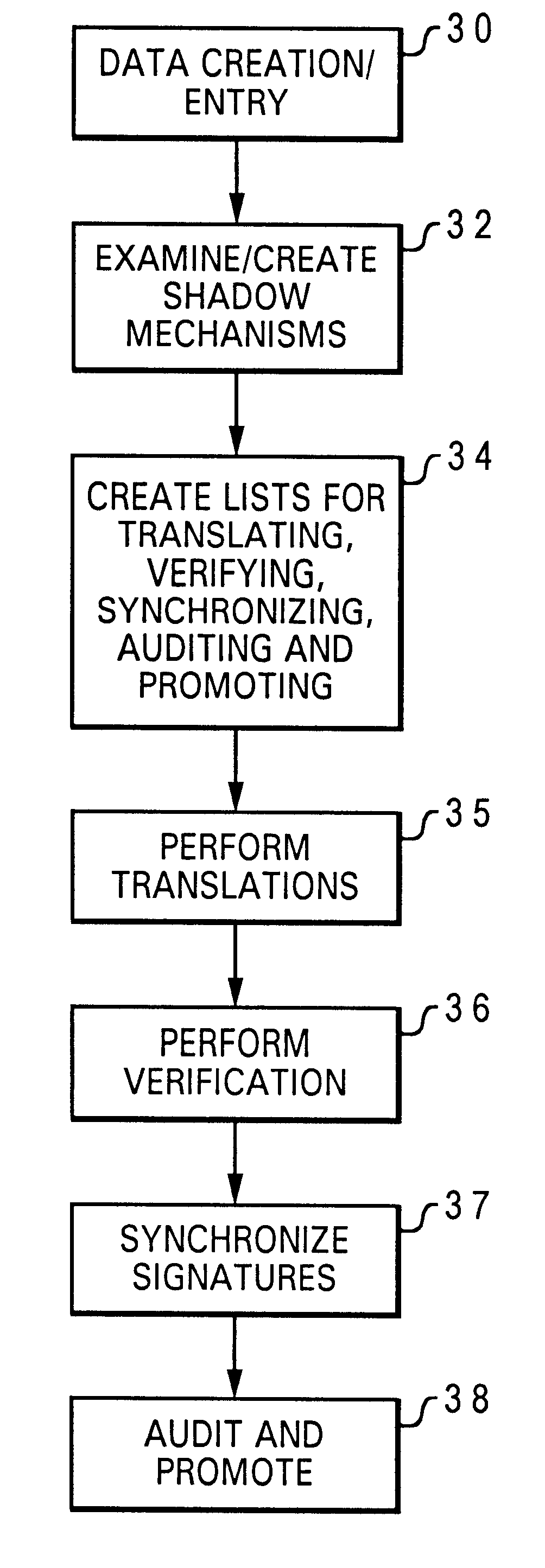
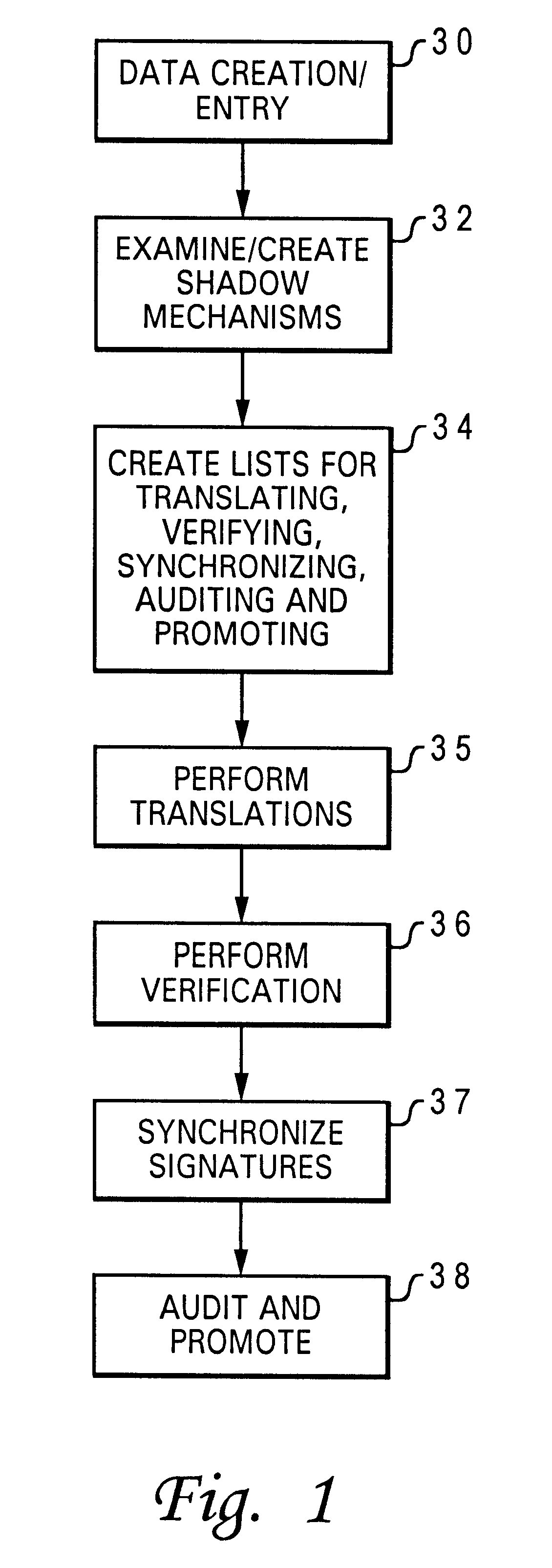
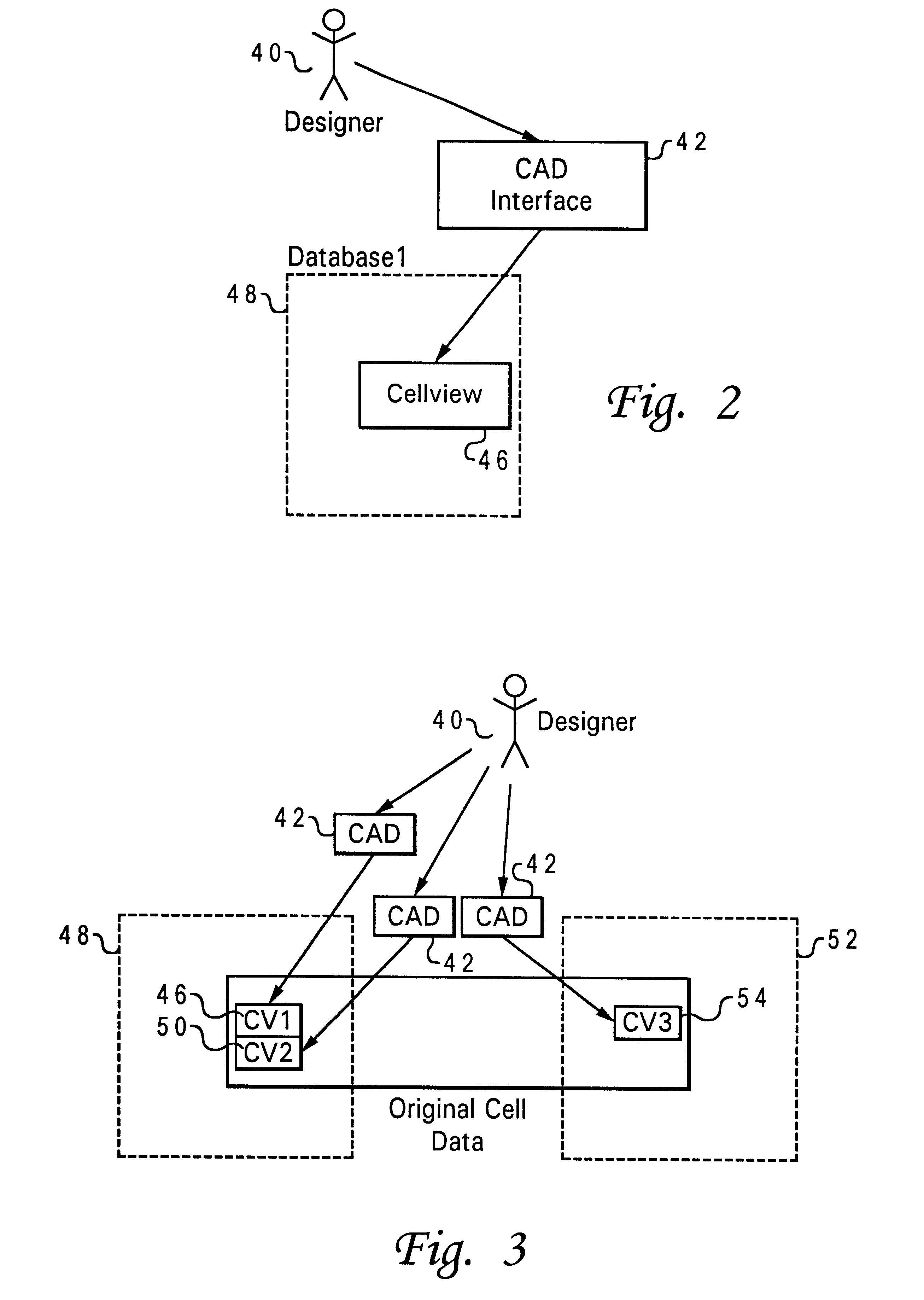
Method and system for automatically maintaining data consistency across various databases
InactiveUS6253213B1Data processing applicationsDigital data information retrievalShadowingsData file
A method and system for automatically maintaining data consistency across two or more hierarchically arranged databases is disclosed. A master list and an environmental variable file are created for use in maintaining the data consistency of a cell view. A cell view in a selected database is then checked to see if it has been modified by performing date-time stamp shadowing. If the cell view is modified, the cell view is then retrieved by derivative lists created from the master list and the environmental variable file and translated based on criteria from the environmental variable file. Verification is then performed on the translated cell view once again based on criteria from the environmental variable file. This verification creates a signature for the translated cell view. Signatures are then checked for being out of date with respect to any dependency listing contained internally. Any signature found to be out of date triggers an automatic re-verification of the pertinent data file. The translated and verified cell view is then checked to see if it or any of its dependencies have been altered by performing an audit based on criteria from the environmental variable file using the signature. The translated and verified cell view is then promoted to a higher quality database based on the results of the audit.
Owner:IBM CORP
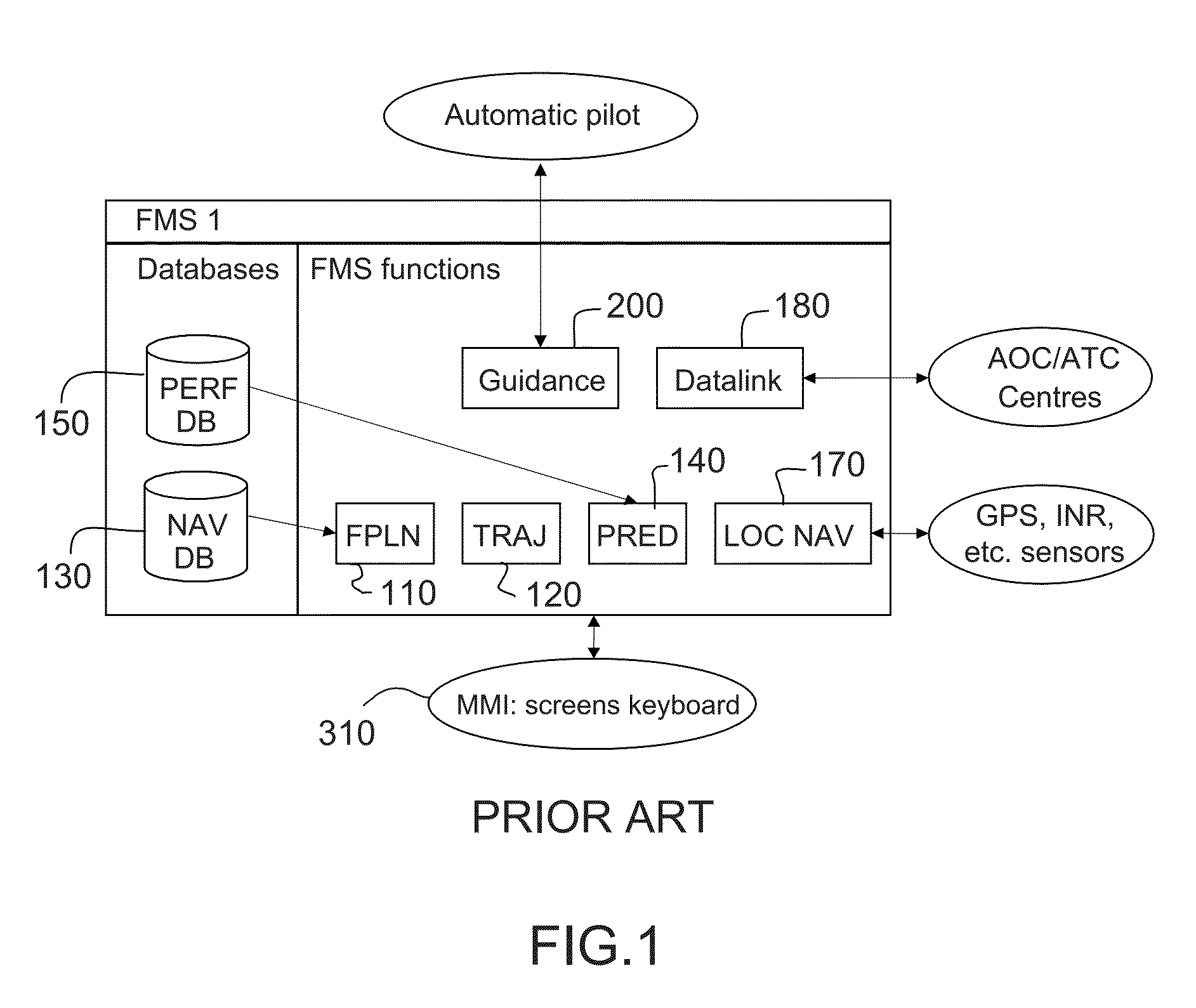
Method of adapting a segment of an aircraft trajectory with constant ground gradient segment according to at least one performance criterion
ActiveUS20160085239A1Optimization pathEasy to useEnergy efficient operational measuresDigital data processing detailsState variableEngineering
A method for adapting an aircraft constant-gradient descent segment comprises: an acquisition step in which state variables characterizing the aircraft, environment variables characterizing the environment thereof and path variables characterizing the predicted path thereof at one of the initial and final points of the segment are acquired; a calculation step whereby a limit ground gradient for at least one performance criterion is calculated from the state variables, environment variables and path variables; a validity verification step checking the validity of the path initially predicted against the most restrictive limit ground gradient; and when the path initially predicted is not valid: a feasibility verification step checking the feasibility of a command to modify at least one state variable; if feasibility is verified, a prediction of executing the command; otherwise, a prediction of modifying one of the initial and final points of the segment with respect to constraints of the flight plan.
Owner:THALES SA
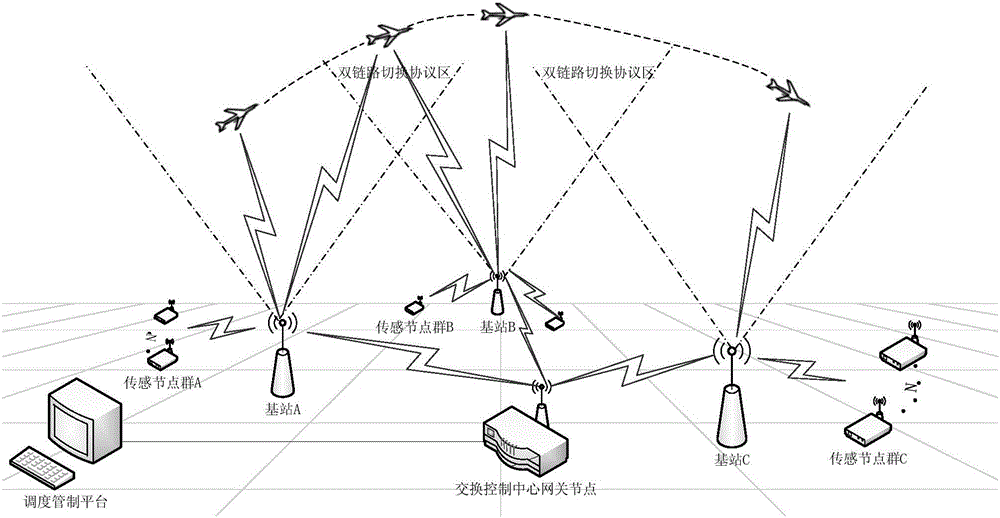
Ground-air wireless sensor network communication device and method compatible with UAV
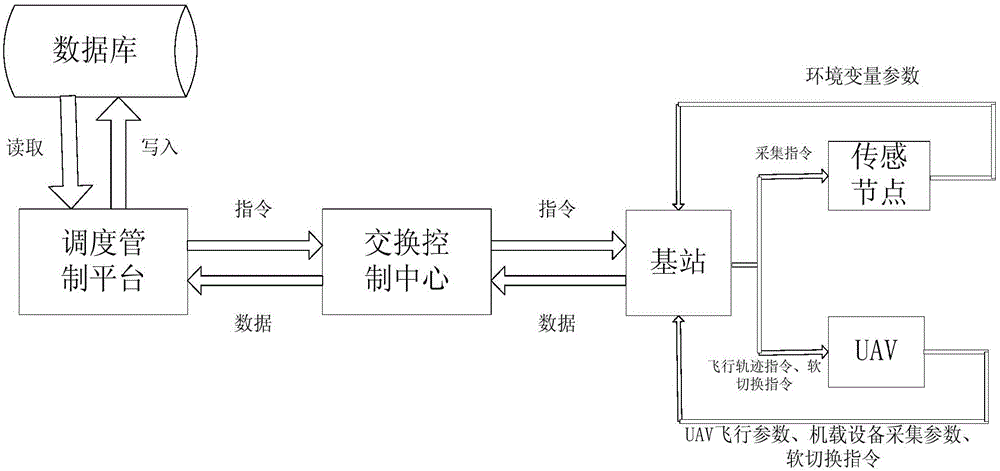
ActiveCN105828345AExpandable and flexibleEliminate signal blind spotsNetwork topologiesTransmissionGrid networkNetwork communication
The invention discloses a ground-air wireless sensor network communication device compatible with a UAV. The device comprises a sensing monitoring system, a mobile platform system, an integrated Wi-Fi network communication system and a dispatching control platform. The sensing monitoring system indicates that in a sensor network, sensor nodes randomly scattered in a monitored region monitor specific variable objects in a target region in real time. The mobile platform system comprises UAVs for mounting Wi-Fi network communication modules, wherein the controllability of the flying speeds and the paths of the UAVs is realized by using rotor vertical lifting platforms. The integrated Wi-Fi network communication system indicates a structure which takes a Wi-Fi communication mode as the main and refers to a cellular mobile communication network. The dispatching control platform is a set of software platform which is used for controlling flying paths of the unmanned aerial vehicles and collecting wireless network topology control information and environment variable information. According to the device, grid network development demands can be satisfied; and through establishment of the UAV communication network taking the network as the center, sufficient stability and reliability and high interconnection and interoperability can be realized.
Owner:SOUTH CHINA AGRI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com