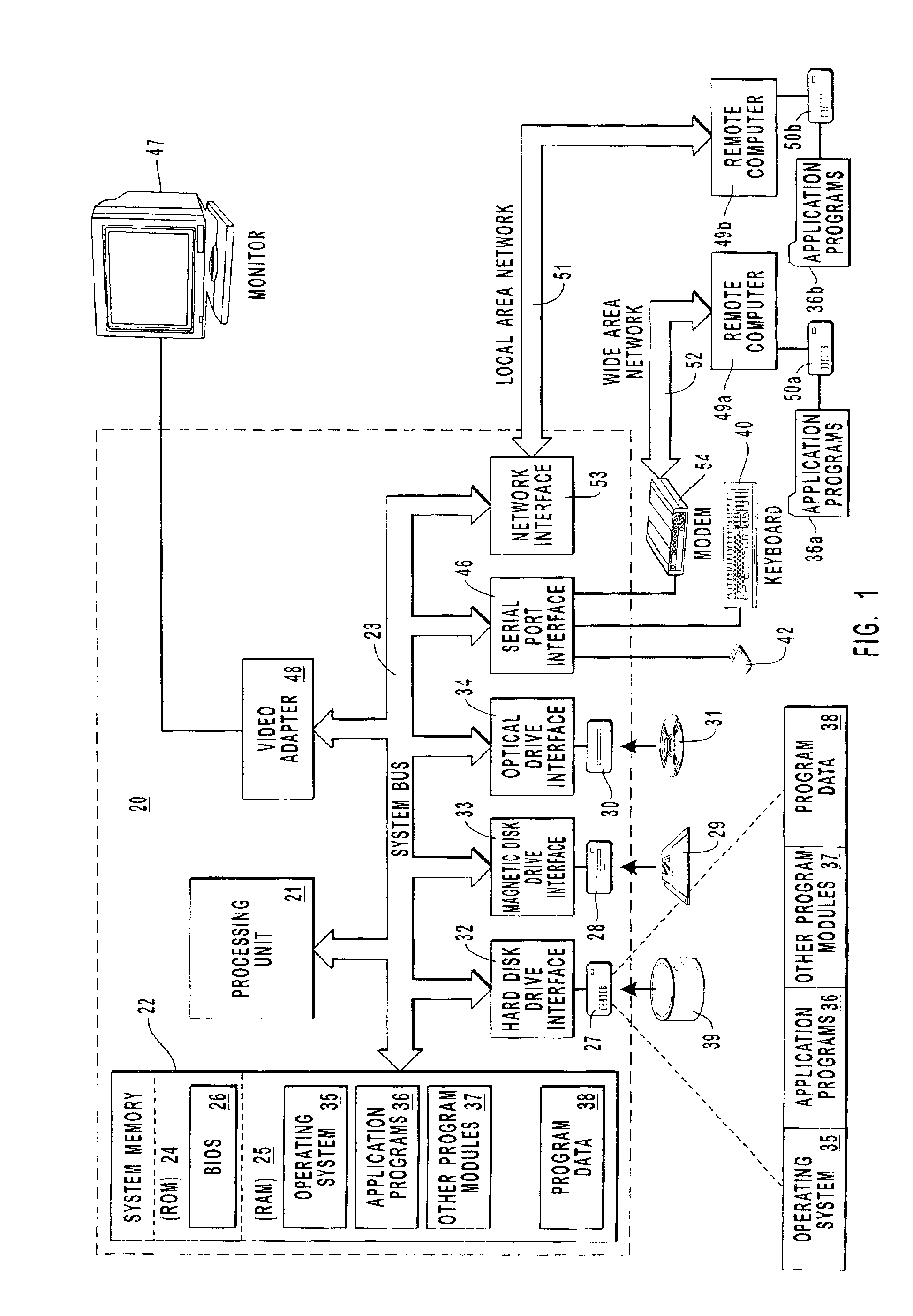
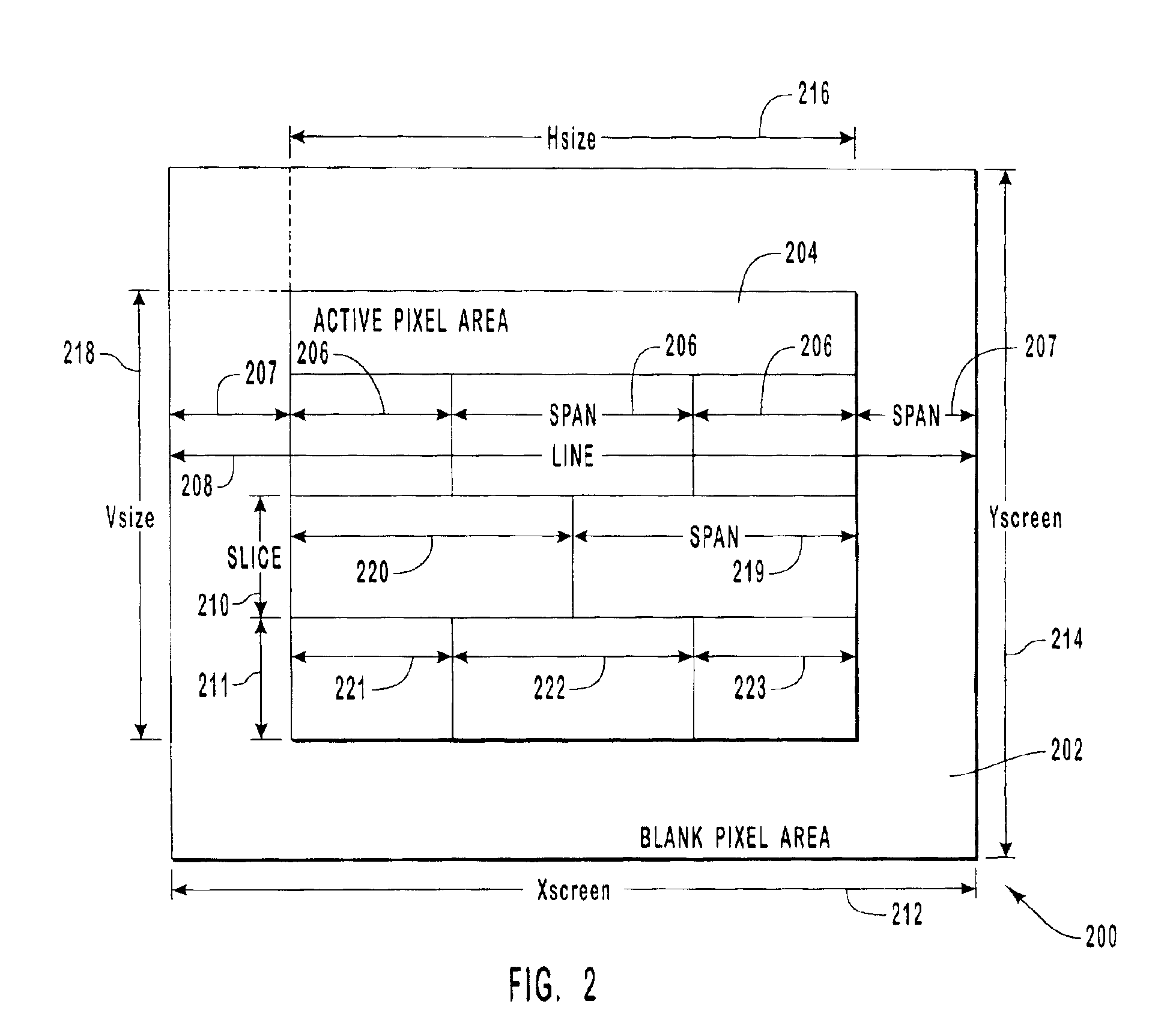
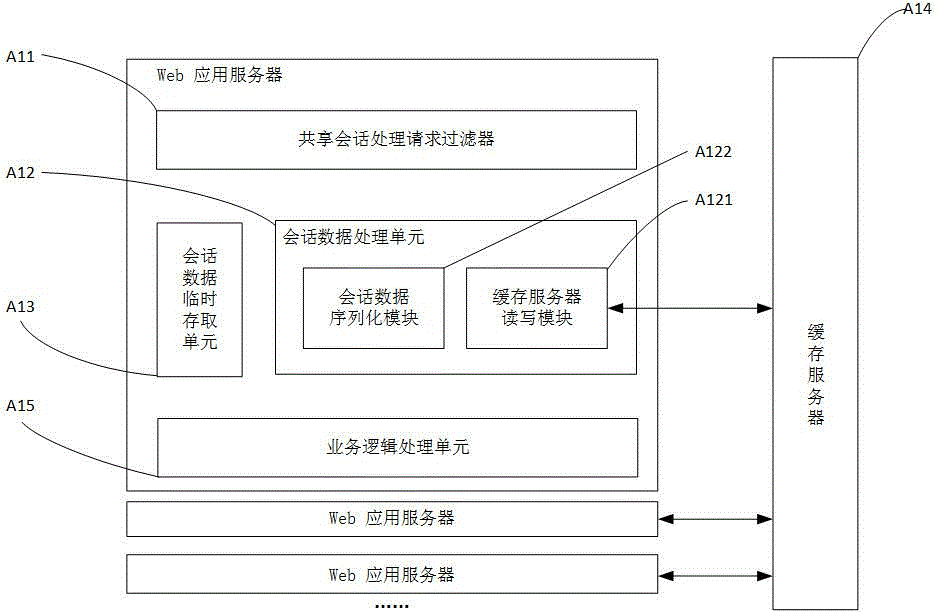
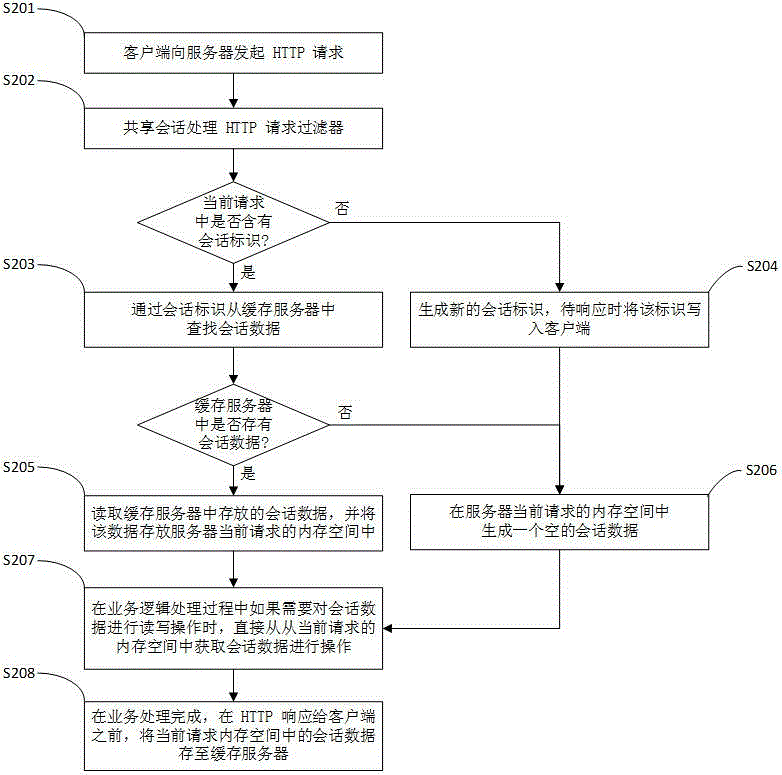
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1090 results about "Memory footprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
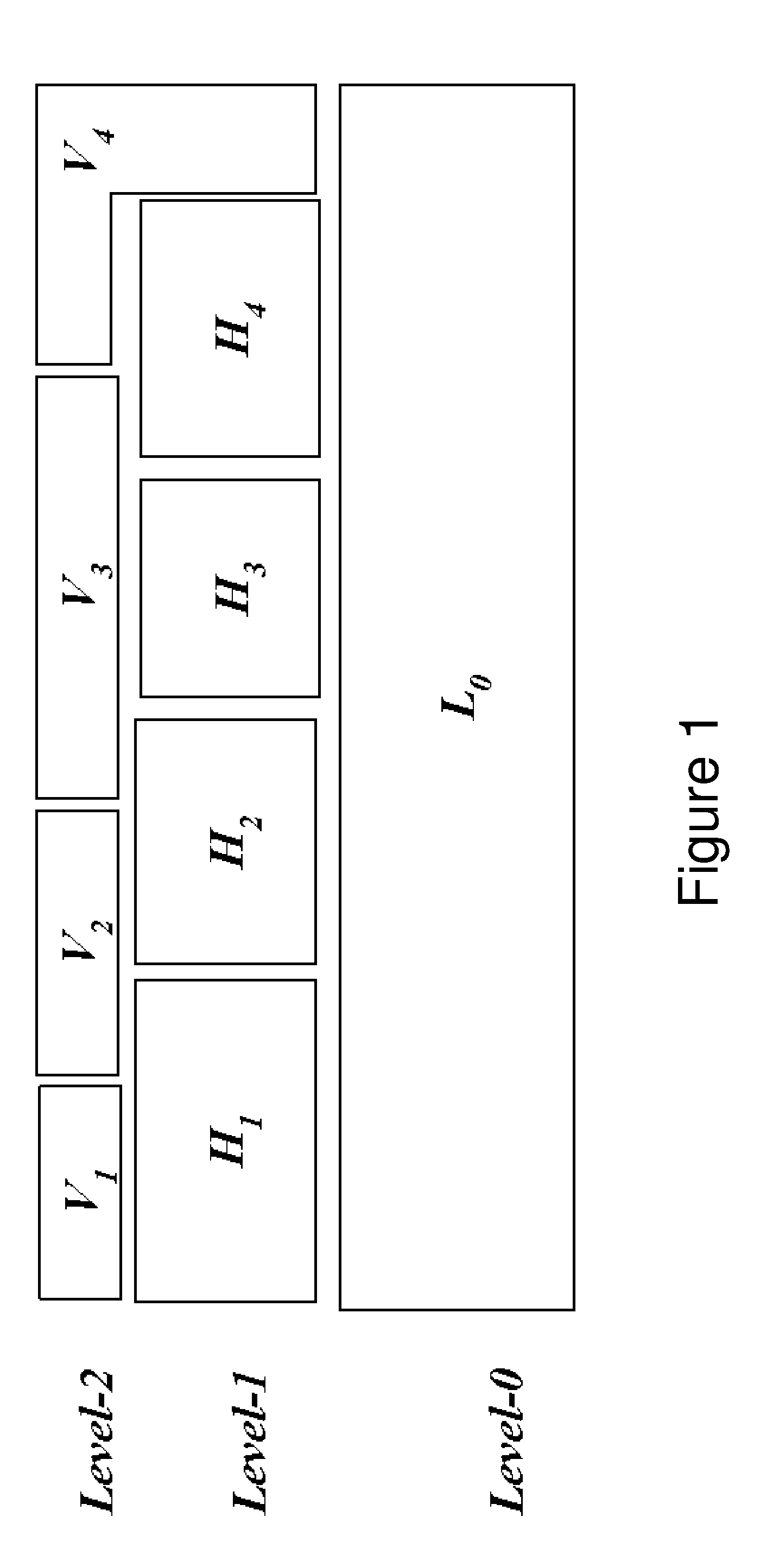
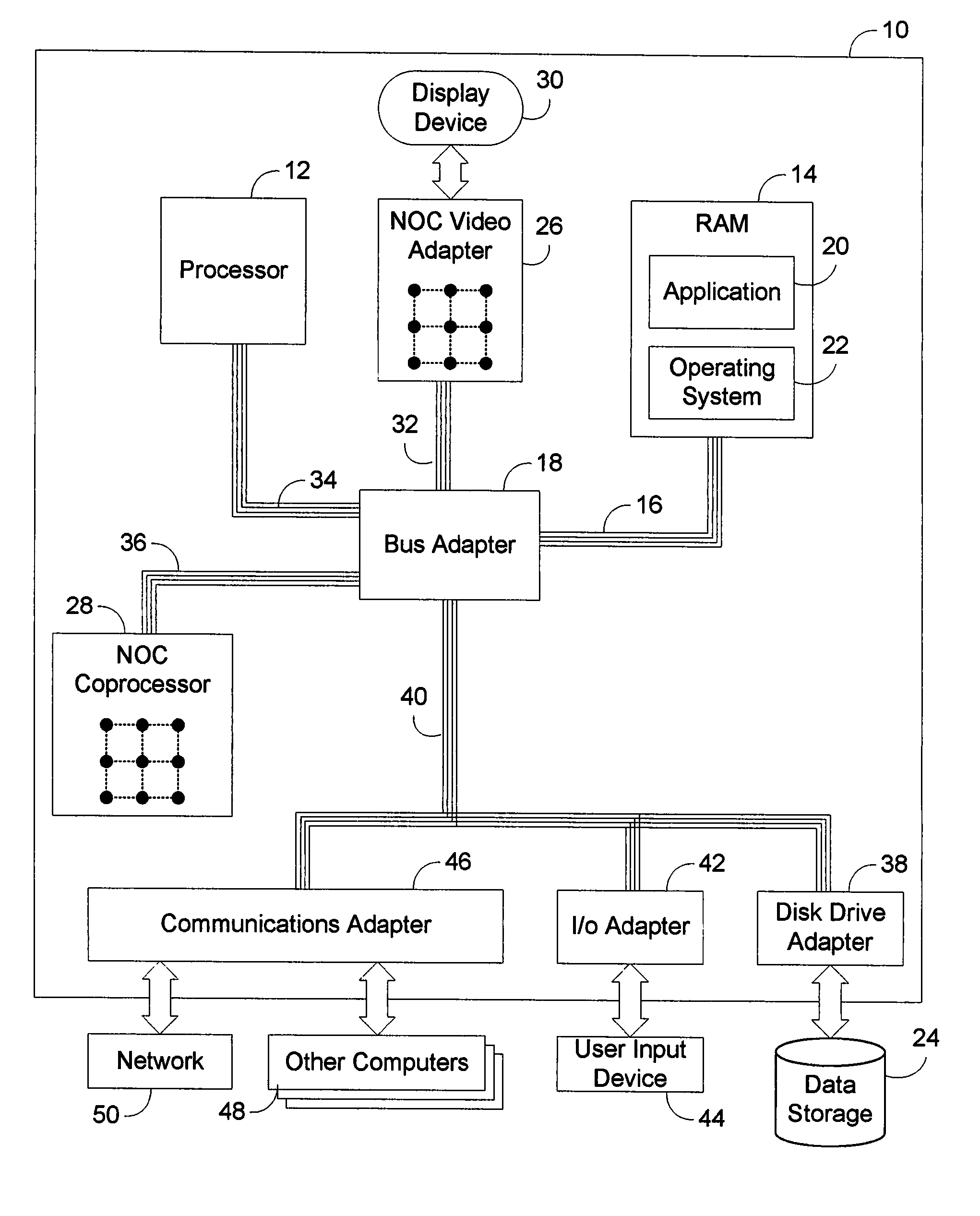
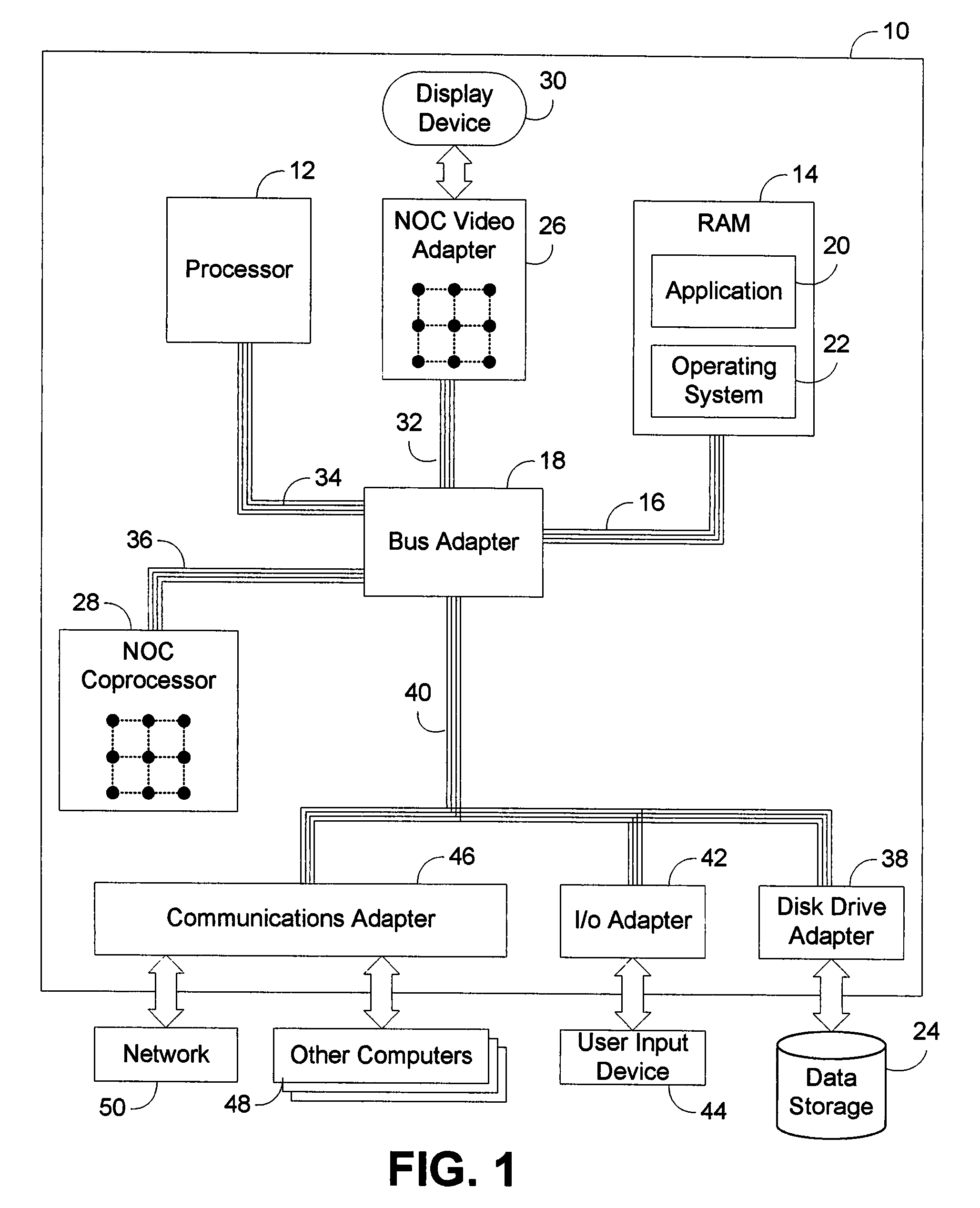
Memory footprint refers to the amount of main memory that a program uses or references while running. The word footprint generally refers to the extent of physical dimensions that an object occupies, giving a sense of its size. In computing, the memory footprint of a software application indicates its runtime memory requirements, while the program executes. This includes all sorts of active memory regions like code segment containing (mostly) program instructions (and occasionally constants), data segment (both initialized and uninitialized), heap memory, call stack, plus memory required to hold any additional data structures, such as symbol tables, debugging data structures, open files, shared libraries mapped to the current process, etc., that the program ever needs while executing and will be loaded at least once during the entire run.
Method for determining a close approximate benefit of reducing memory footprint of a Java application
InactiveUS20050160416A1Improve performanceData processing applicationsSoftware engineeringMemory footprintParallel computing
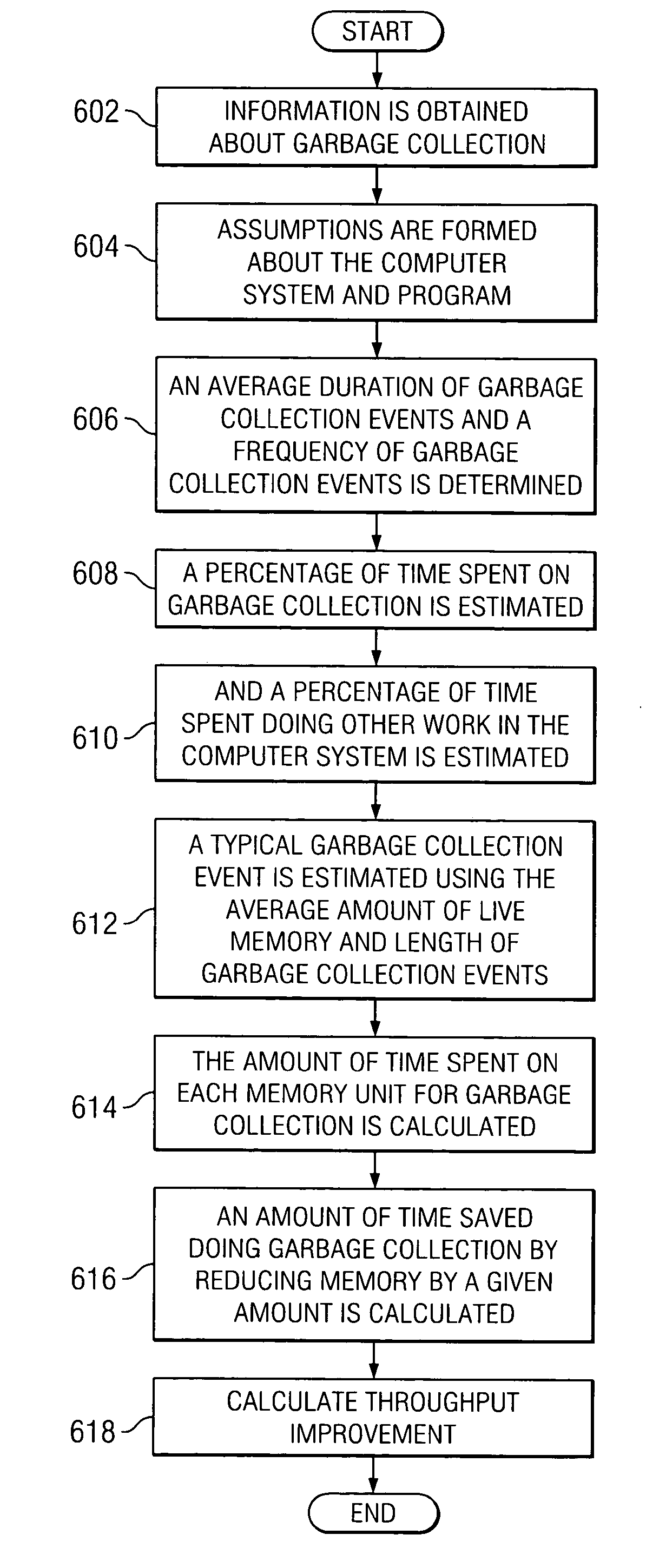
Changes in performance in a Java program are deduced from information related to garbage collection events of the program. Assumptions are made about the system, the application and garbage collection, and changes in performance that will result from modifying the program are deduced.
Owner:IBM CORP
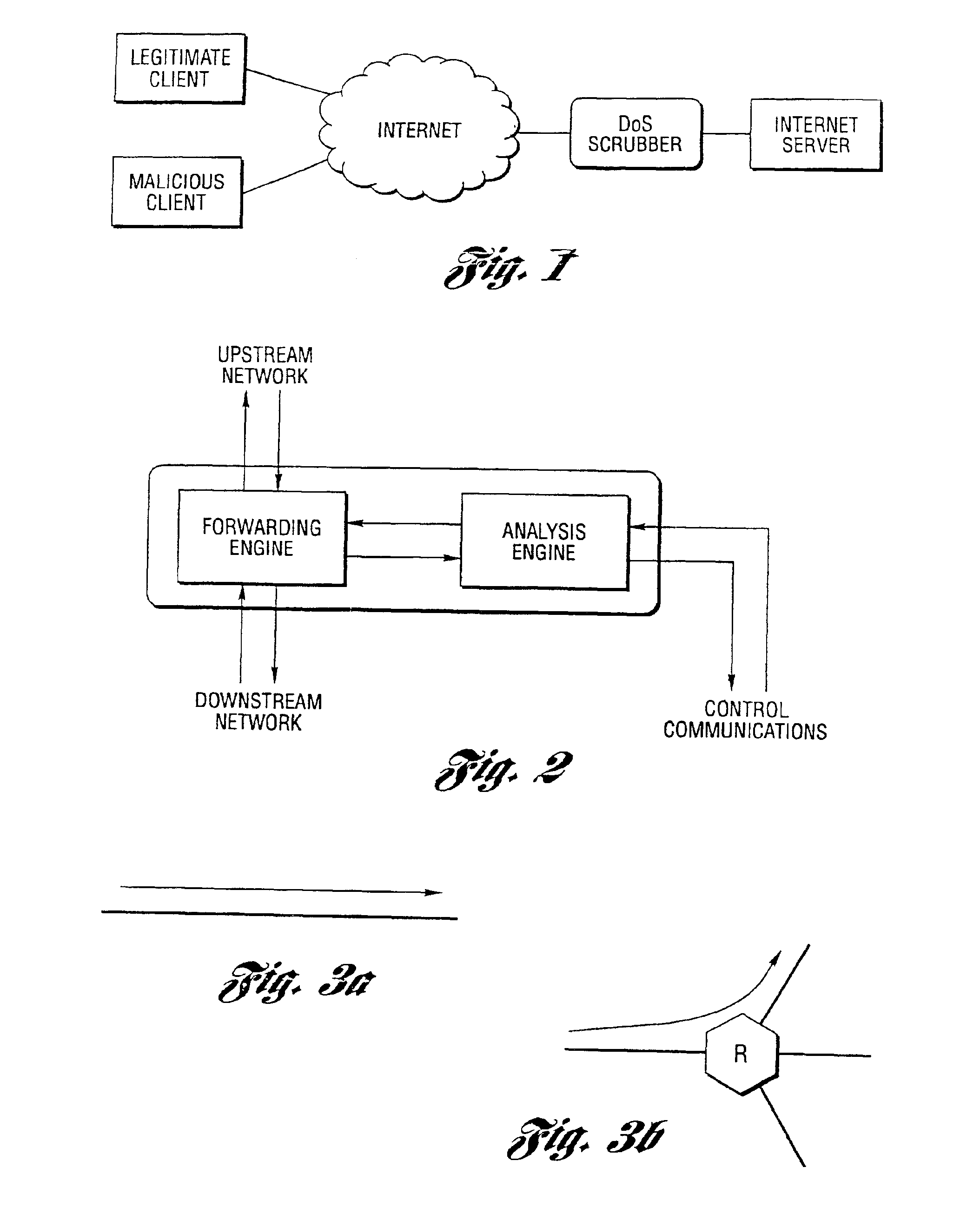
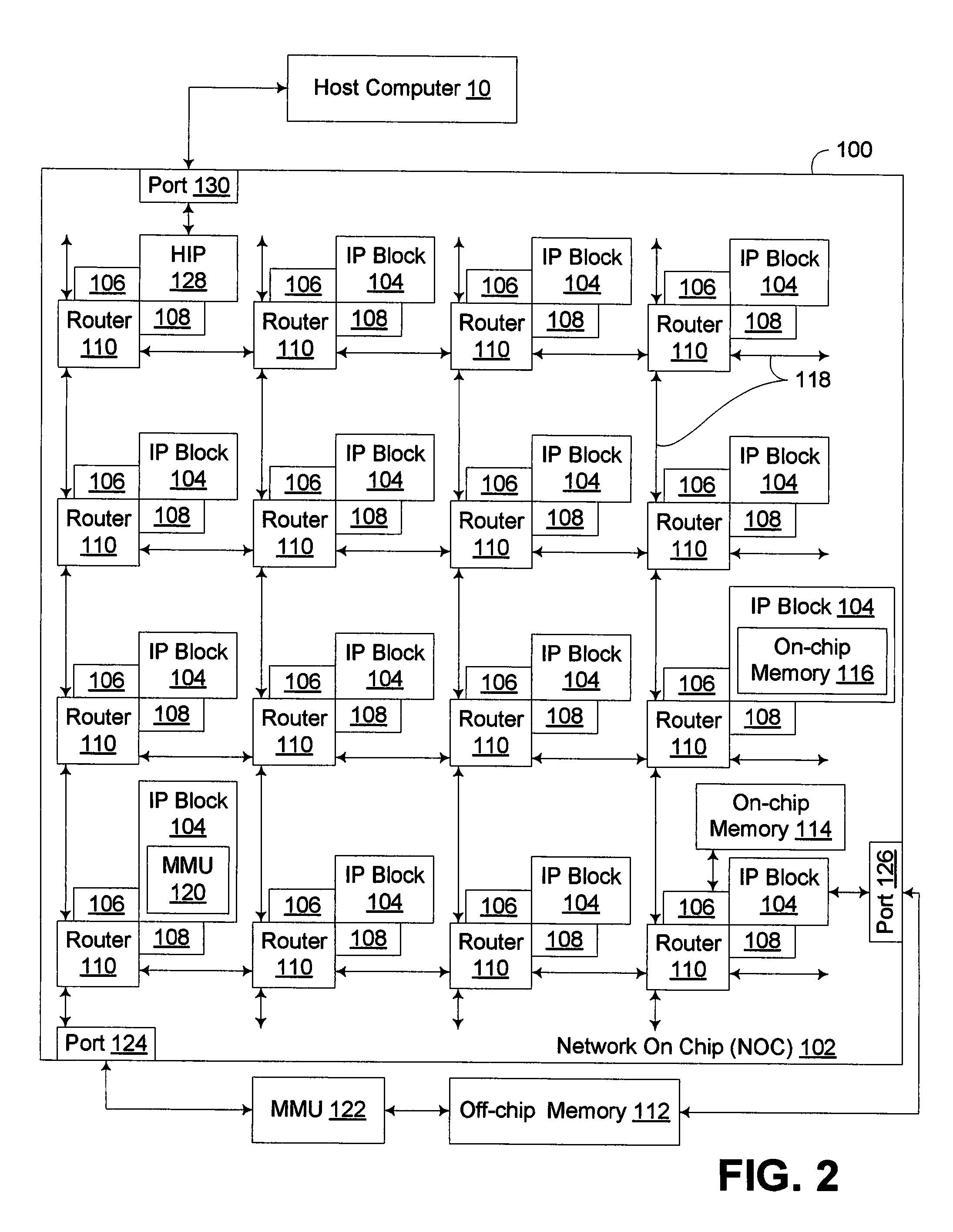
Method and system for profiling network flows at a measurement point within a computer network
InactiveUS6944673B2Multiple digital computer combinationsData switching networksTraffic characteristicMeasurement point
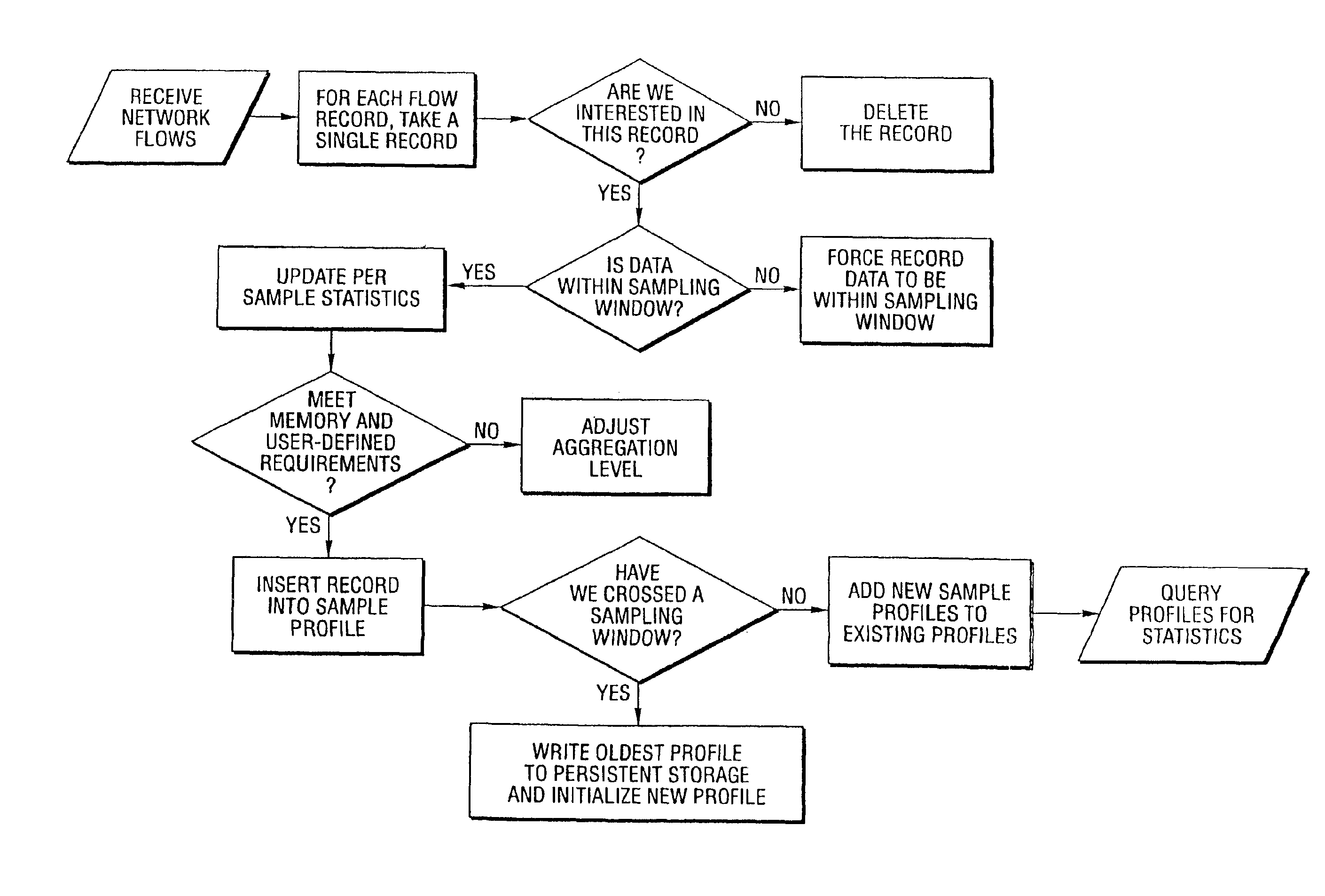
A method and system for profiling network flows at a measurement point within a computer network is provided. The method includes measuring network flows having invariant features at a measurement point located within routing infrastructure of the computer network to obtain flow statistics. The method also includes aggregating the flow statistics to obtain a traffic profile of the network flows at the measurement point. The method and system utilize the natural hierarchy in the Internet addressing scheme to provide a means for making tractable measurements of network traffic in high-speed networks. Moreover, the method and system adapt dynamically to the changing underlying traffic characteristics to maintain a maximum memory footprint for the profiles. The method and system adapt by adjusting the level of aggregation of the traffic endpoints along a scale from Interface to fully specified network address.
Owner:RGT UNIV OF MICHIGAN
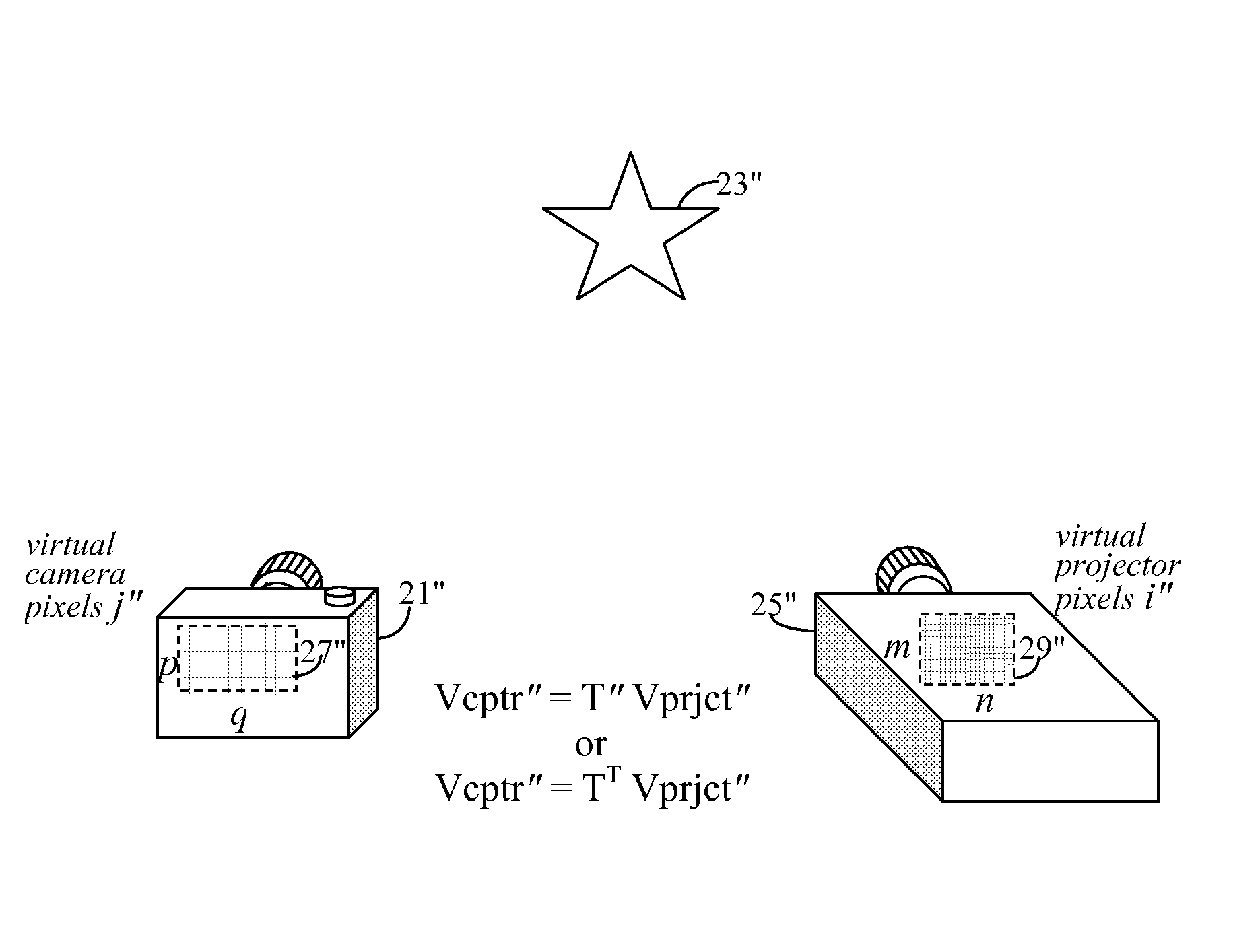
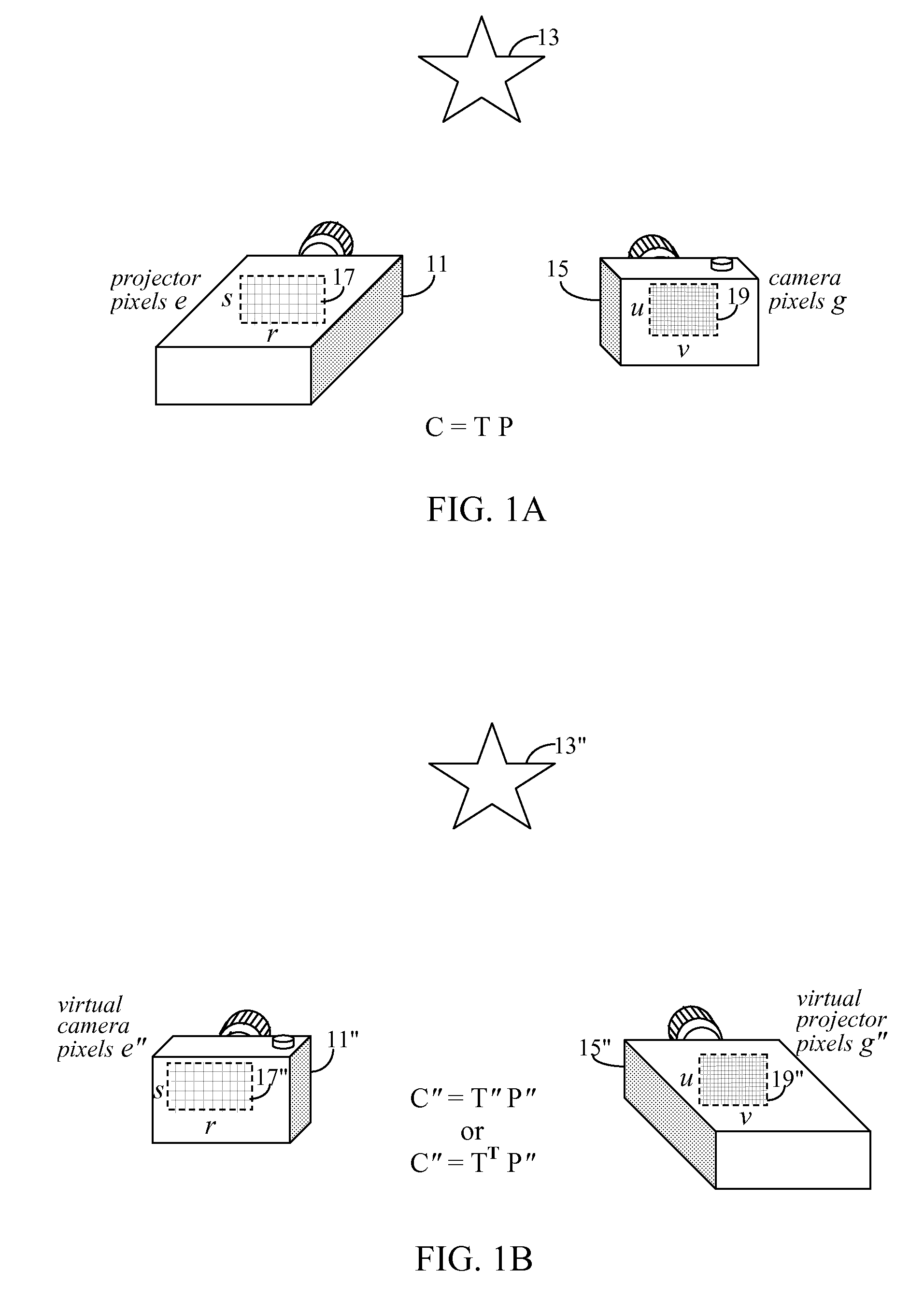
Small memory footprint light transport matrix capture
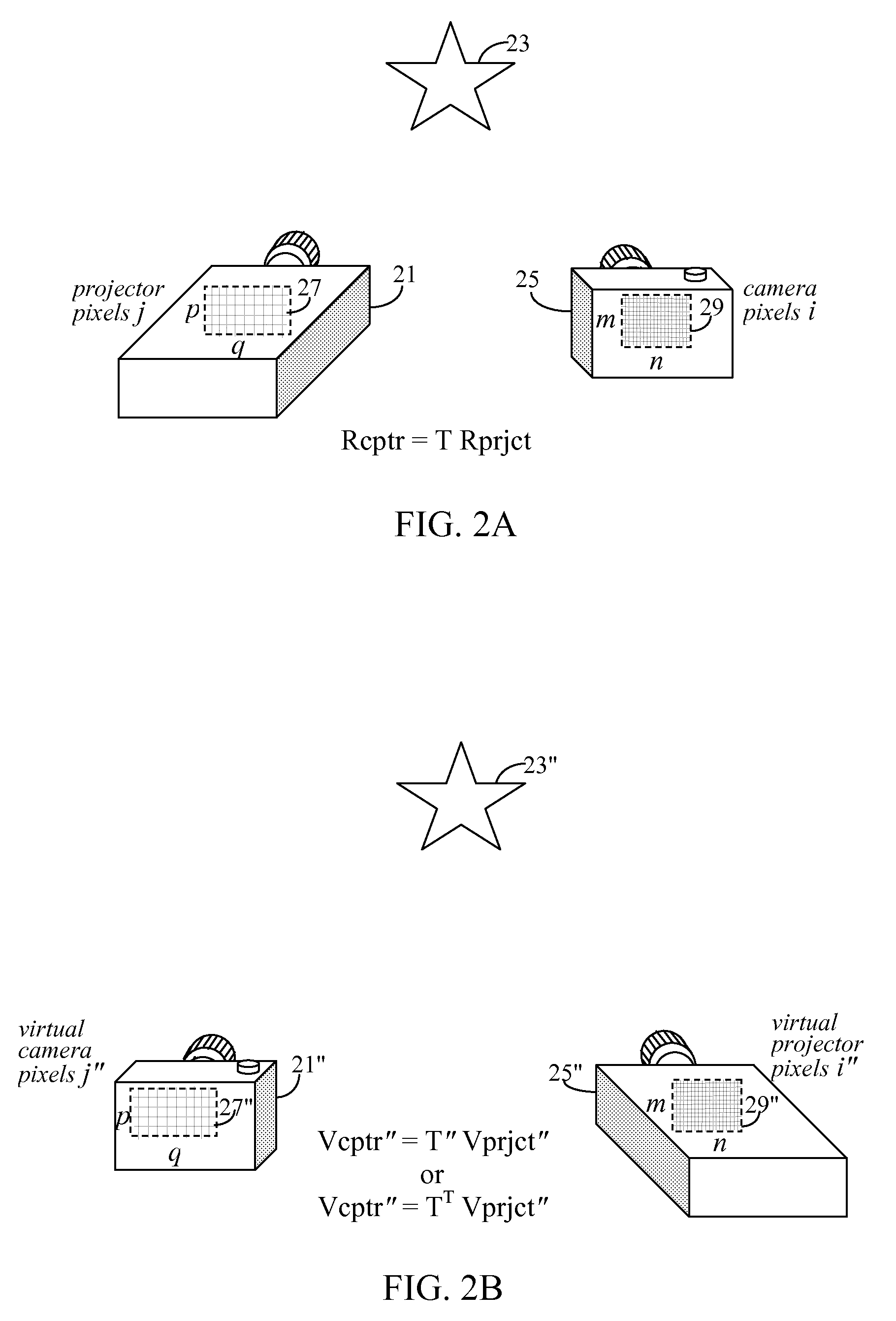
ActiveUS8106949B2Easy to shipEasy to implementTelevision system detailsTelevision system scanning detailsImaging processingProjection image
A projection system uses a transformation matrix to transform a projection image p in such a manner so as to compensate for surface irregularities on a projection surface. The transformation matrix makes use of properties of light transport relating a projector to a camera. A display pipeline of user-supplied image modification processing modules are reduced by first representing the processing modules as multiple, individual matrix operations. All the matrix operations are then combined with, i.e., multiplied to, the transformation matrix to create a modified transformation matrix. The created transformation matrix is then used in place of the original transformation matrix to simultaneously achieve both image transformation and any pre and post image processing defined by the image modification processing modules.
Owner:SEIKO EPSON CORP
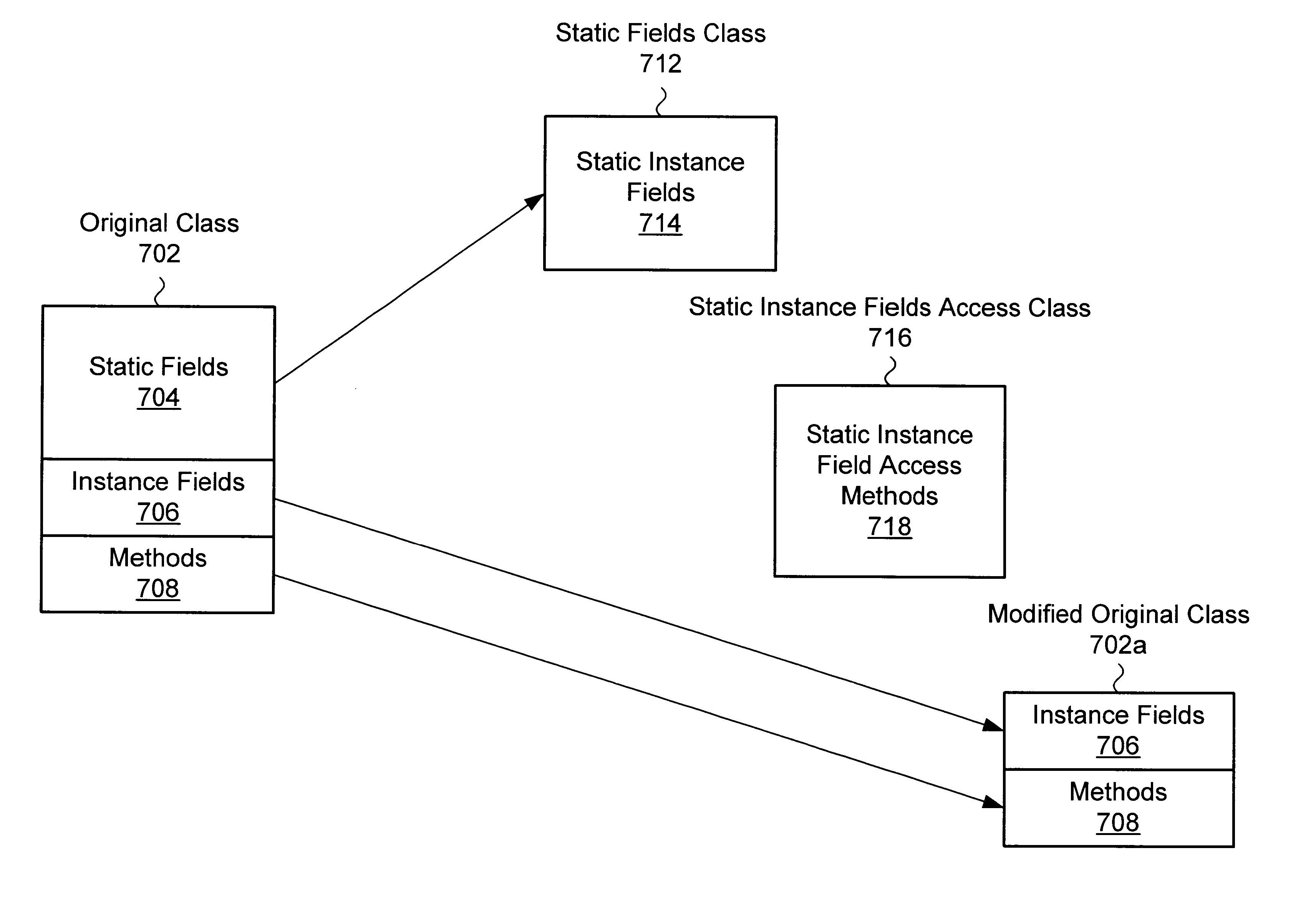
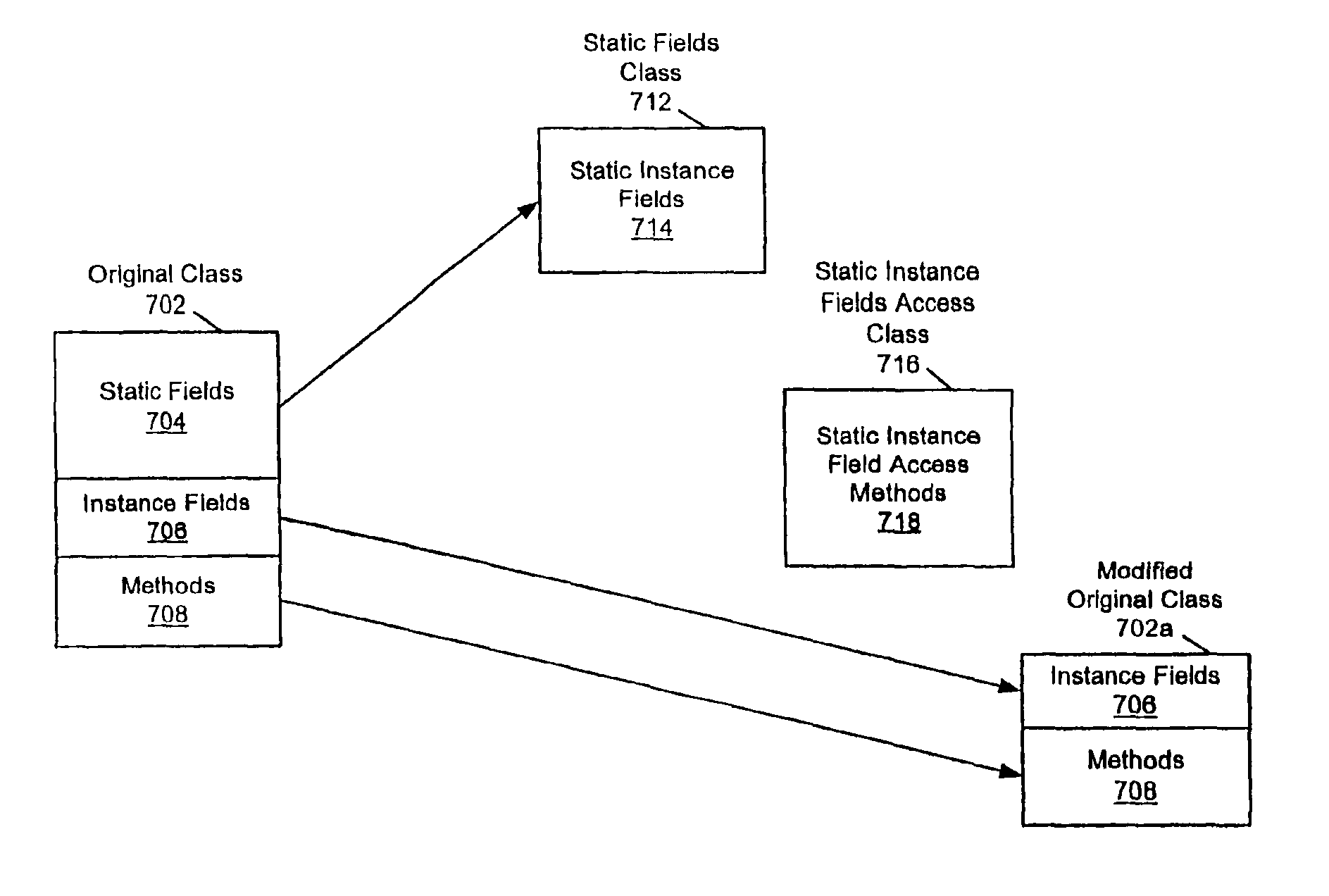
Small memory footprint system and method for separating applications within a single virtual machine
A system and method for isolating the execution of a plurality of applications. The applications may utilize or share one or more "original" classes. Only one copy of each original class is maintained, regardless of how many applications utilize it. Static fields are extracted from the original classes. A separate copy of the static fields is created for each of the utilizing applications. A static field class which includes instance fields corresponding to the static fields may be created, wherein each instance of the static field class corresponds to one of the utilizing applications. Access methods for the one or more static fields may be created, wherein the access methods are operable to access the corresponding separate copy of the static fields based upon the identity of the utilizing application. A single access methods class may be created for each original class, wherein the single access methods class includes the access methods for accessing the extracted fields from the original class. The method and system may be optimized by exempting from extraction static fields that are classified as secure for utilization by the plurality of applications without inter-application interference. The secure set of static fields may include final static fields of primitive types, final static strings, immutable arrays of primitive types, and / or other appropriate fields.
Owner:ORACLE INT CORP
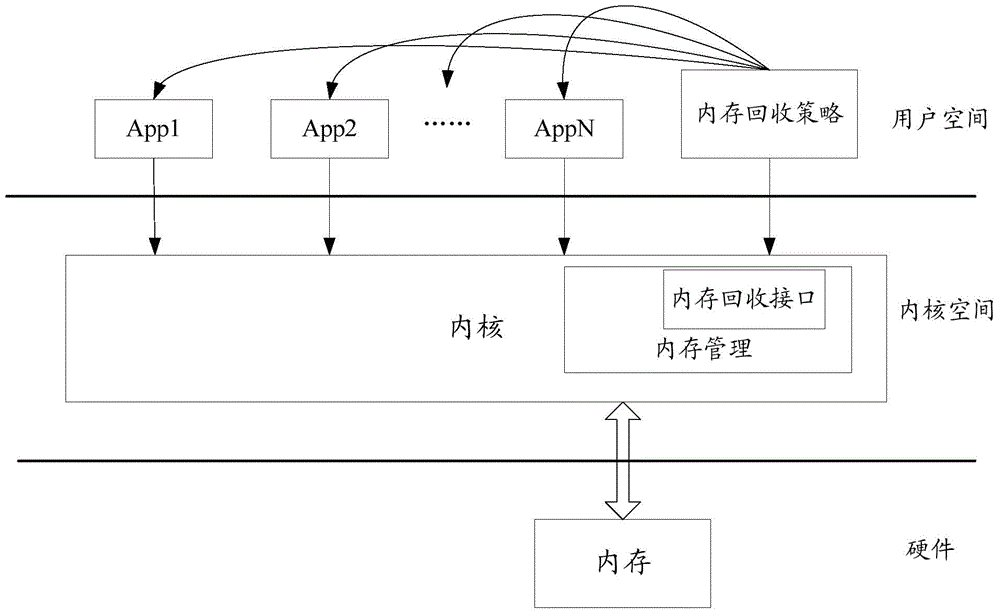
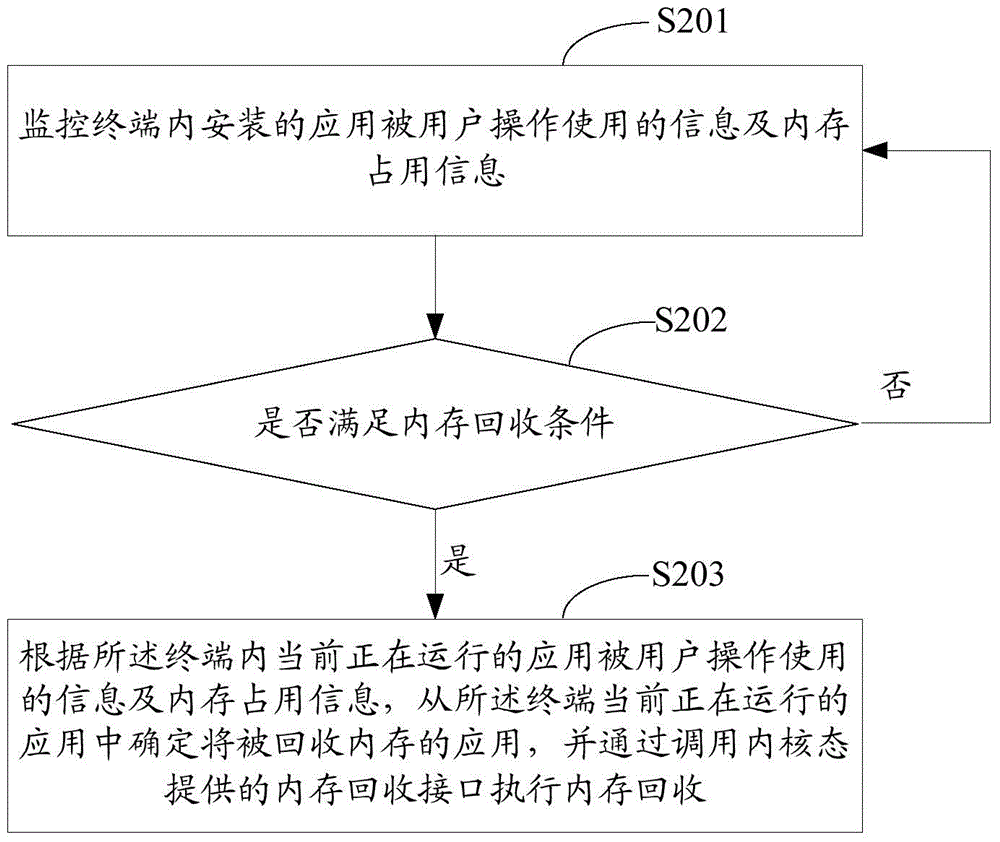
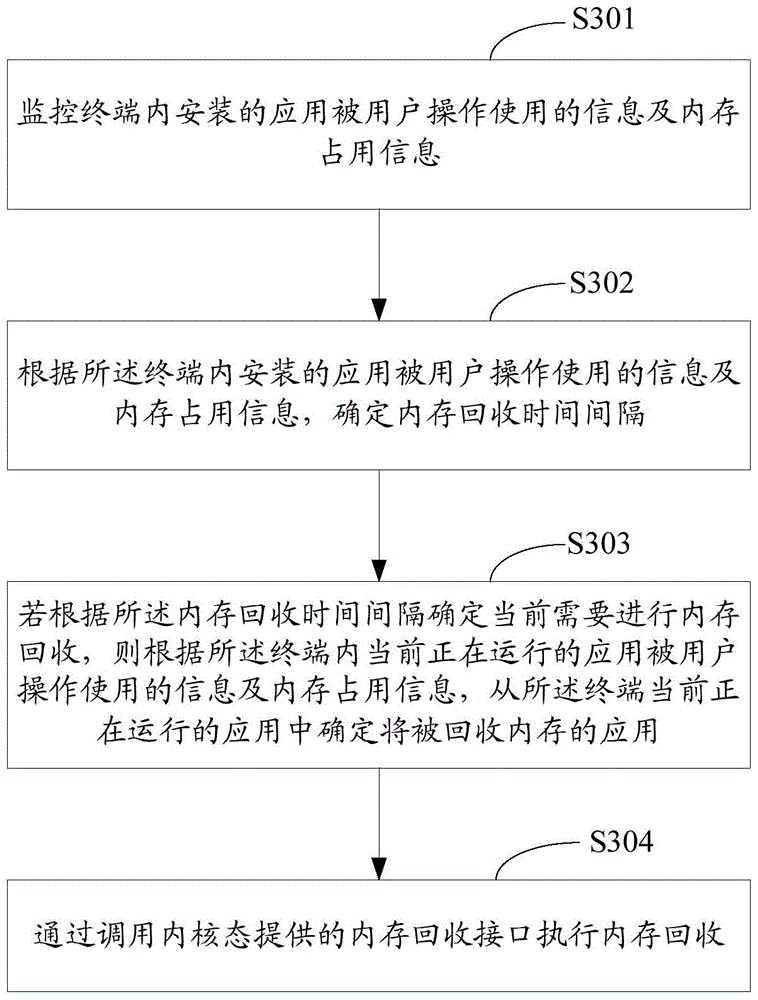
Memory recovery method and device
ActiveCN105701025AAccelerate collection frequencyEasy to useMemory architecture accessing/allocationResource allocationRecovery methodMemory footprint
The invention relates to the technical field of computers, and in particular relates to a memory recovery method and device, used for solving the problem that the application jamming problem is easily caused due to the fact that memory recovery is not in time. The memory recovery method provided by the invention comprises the following steps of: monitoring operation and use information of applications installed in a terminal by users and memory usage information; and determining that a memory recovery condition is satisfied currently according to at least one of the operation and use information of the applications installed in the terminal by users and the memory usage information, determining the application, the memory of which is to be recovered, in currently operated applications of the terminal according to the operation and use information of the currently operated applications in the terminal and the memory usage information, and performing memory recovery by invoking a memory recovery interface provided by a kernel mode.
Owner:HUAWEI TECH CO LTD
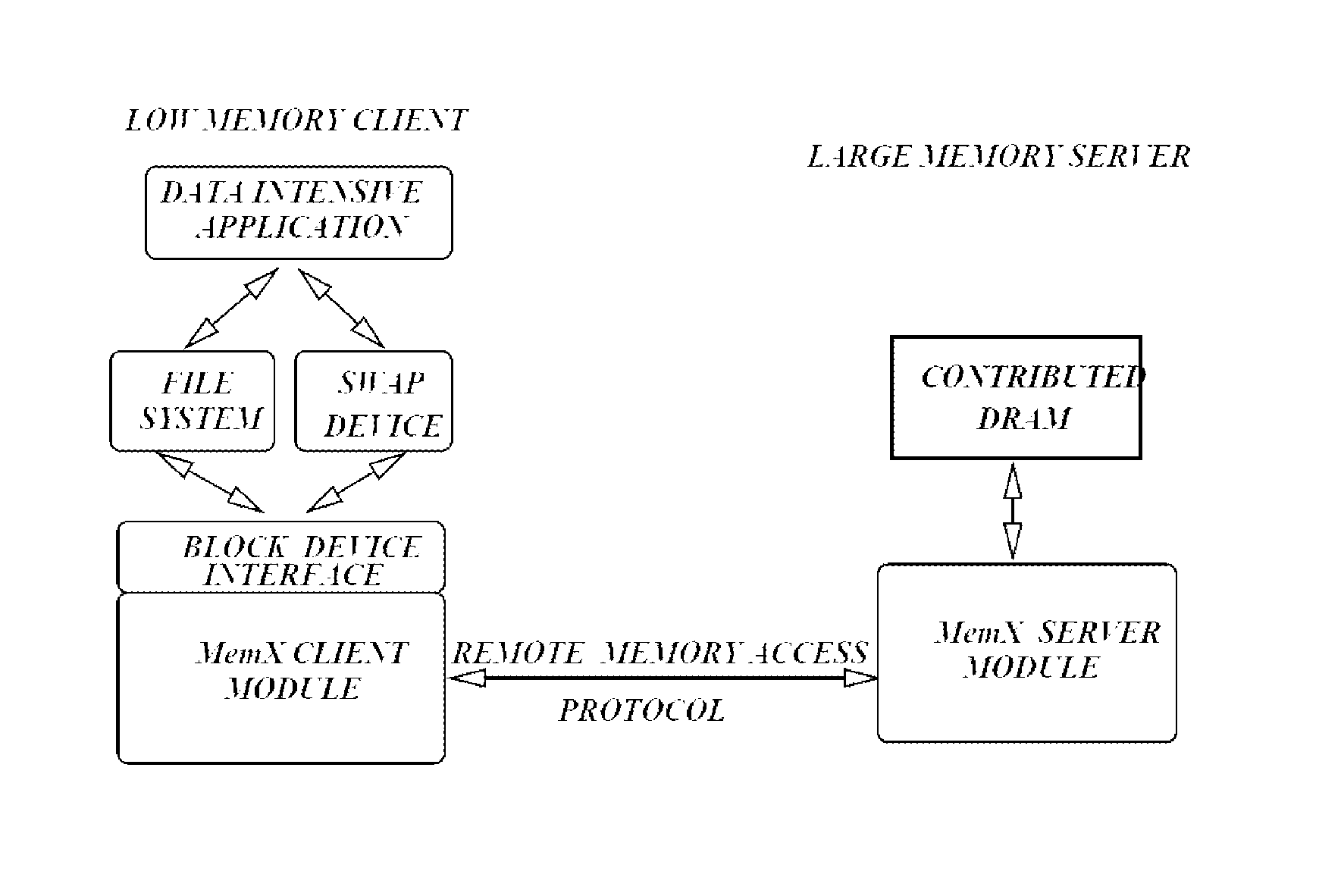
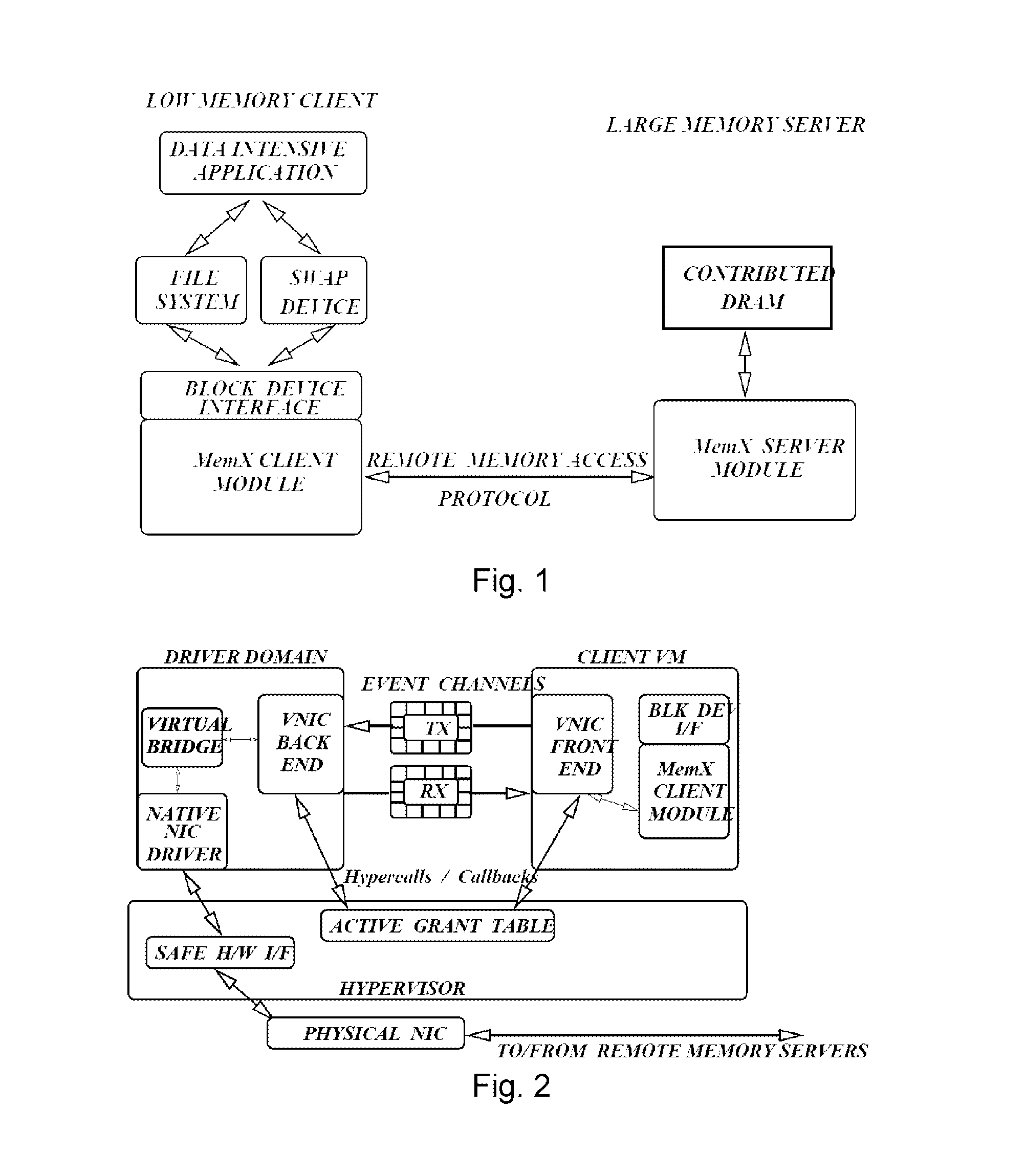
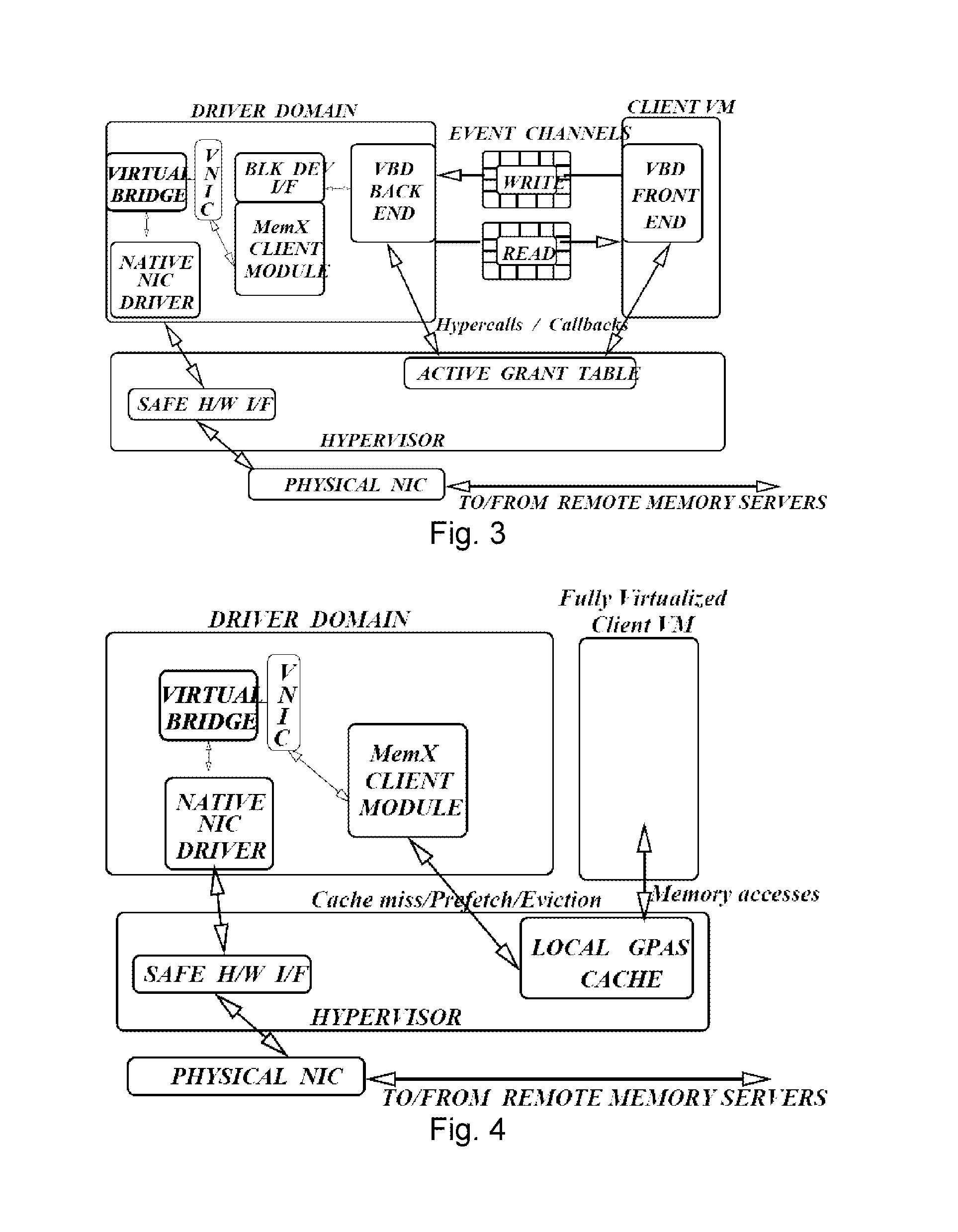
MemX: virtualization of cluster-wide memory
ActiveUS8935506B1Eliminate needReduced execution timeMemory systemsMicro-instruction address formationNODALData set
MemX provides a distributed system that virtualizes cluster-wide memory to support data-intensive and large memory workloads in virtual machines (VMs), and provides benefits in virtualized settings: (1) VM workloads that access large datasets can perform low-latency I / O over virtualized cluster-wide memory; (2) VMs can transparently execute very large memory applications that require more memory than physical DRAM present in the host machine; (3) reduces the effective memory usage of the cluster by de-duplicating pages that have identical content; (4) existing applications do not require any modifications to benefit from MemX such as the use of special APIs, libraries, recompilation, or relinking; and (5) supports live migration of large-footprint VMs by eliminating the need to migrate part of their memory footprint resident on other nodes. Detailed evaluations show that large dataset applications and multiple concurrent VMs achieve significant performance improvements using MemX compared against virtualized local and iSCSI disks.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
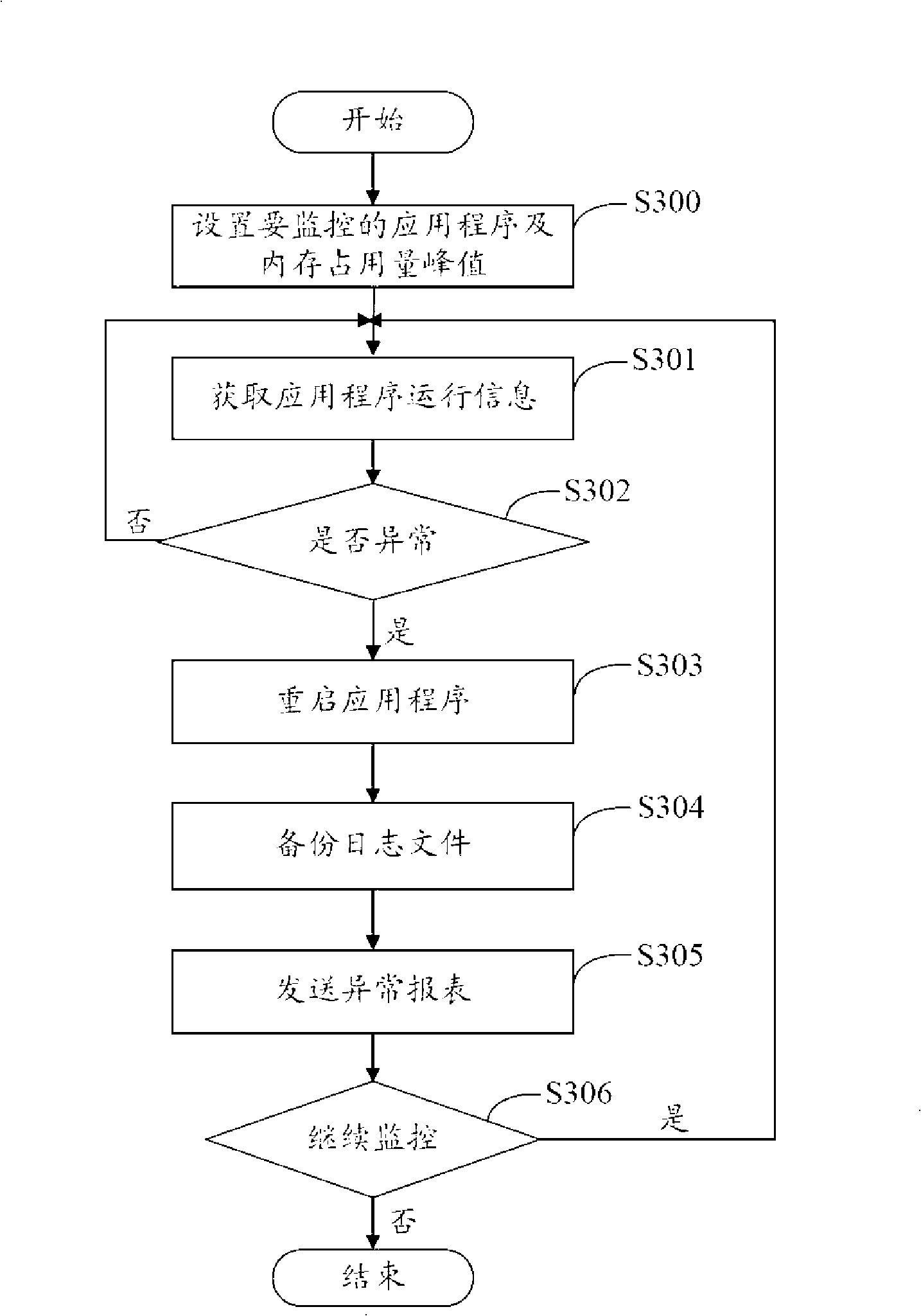
Real time monitoring system and method of application program
InactiveCN101408861AAutomatically monitor healthFix exceptions in timeHardware monitoringMemory footprintMonitoring system
The invention relates to an application real-time monitoring method, comprising the steps: setting the applications to be monitored and the memory occupancy amount peak value of each application; monitoring the CPU occupancy factor, memory occupancy amount and the operating state of each application; closing all monitored applications and restarting the applications when the CPU occupancy factor of any application reaches 100%, or the memory occupancy amount of any application reaches the peak value and or any application suspends; and returning to the monitoring step in need of proceeding the monitoring. The invention also provides an application real-time monitoring system, can automatically monitor the operating condition of applications, restore the application exception in time, improve the system operating efficiency and lower the system maintenance cost.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
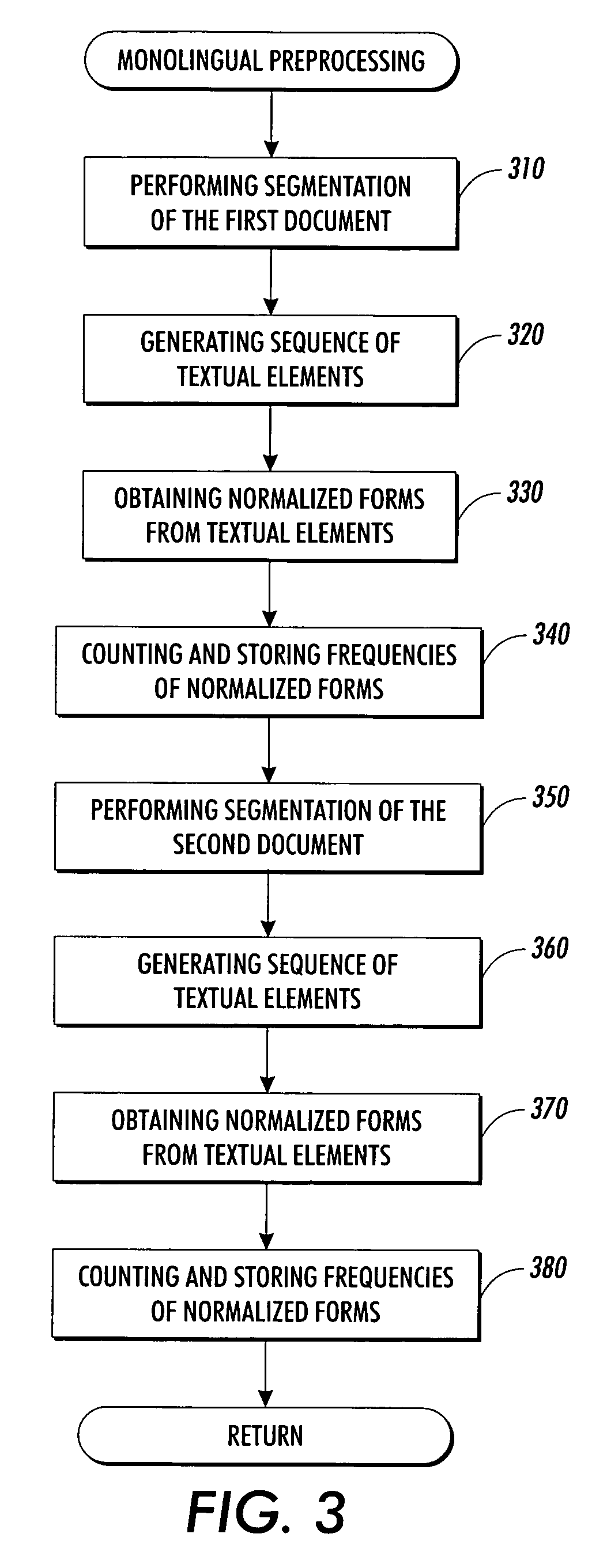
Extracting sentence translations from translated documents
InactiveUS7054803B2Efficient use ofReduce memory consumptionNatural language translationSpecial data processing applicationsKnowledge sourcesMemory footprint
A system extracts translations from translated texts, such as sentence translations from translated versions of documents. A first and a second text are accessed and divided into a plurality of textual elements. From these textual elements, a sequence of pairs of text portions is formed, and a pair score is calculated for each pair, using weighted features. Then, an alignment score of the sequence is calculated using the pair scores, and the sequence is systematically varied to identify a sequence that optimizes the alignment score. The invention allows for fast, reliable and robust alignment of sentences within large translated documents. Further, it allows to exploit a broad variety of existing knowledge sources in a flexible way, without performance penalty. Further, a general implementation of dynamic programming search with online memory allocation and garbage collection allows for treating very long documents with limited memory footprint.
Owner:XEROX CORP
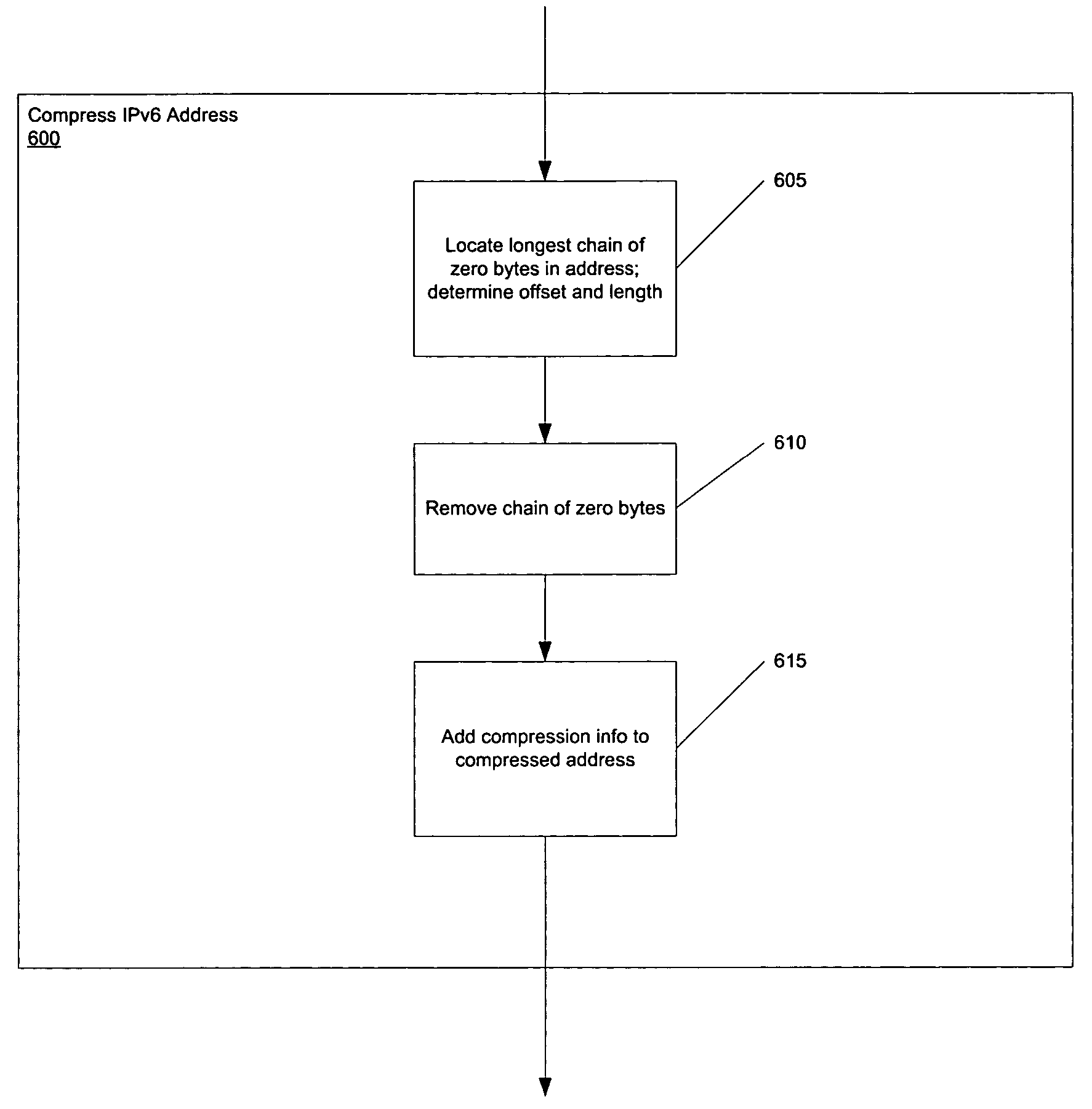
System and method for efficient sftorage and processing of IPV6 addresses
InactiveUS20050111494A1Eliminating compression informationTime-division multiplexData switching by path configurationRouting tableMemory footprint
A preferred method and algorithm of compressing IPv6 addresses is presented which ensures smaller memory occupancy for IPv6 routing tables and databases in general (applicability to particular case of databases of the routing protocol OSPF for IPv6 is described). A method and algorithm of comparison of such compressed IPv6 addresses without decompression is presented, a method of comparison that ensures in the majority of cases better comparison performance than for the case of comparing uncompressed IPv6 addresses. Also, a preferred method and algorithm of decompressing IPv6 addresses that were compressed using this preferred format is given, and a method and algorithm of comparison of an uncompressed IPv6 address with a compressed IPv6 address without decompression. The exemplary comparison methods may achieve or exceed comparable performance with the performance of comparing uncompressed addresses. Illustrations for the particular case of the routing protocol OSPF for IPv6 are presented for all cases.
Owner:WIND RIVER SYSTEMS
Small memory footprint system and method for separating applications within a single virtual machine
InactiveUS6938247B2Minimal collective footprintReliable isolationProgram loading/initiatingMemory systemsArray data structureAccess method
A system and method for isolating the execution of a plurality of applications. The applications may utilize or share one or more “original” classes. Only one copy of each original class is maintained, regardless of how many applications utilize it. Static fields are extracted from the original classes. A separate copy of the static fields is created for each of the utilizing applications. A static field class which includes instance fields corresponding to the static fields may be created, wherein each instance of the static field class corresponds to one of the utilizing applications. Access methods for the one or more static fields may be created, wherein the access methods are operable to access the corresponding separate copy of the static fields based upon the identity of the utilizing application. A single access methods class may be created for each original class, wherein the single access methods class includes the access methods for accessing the extracted fields from the original class. The method and system may be optimized by exempting from extraction static fields that are classified as secure for utilization by the plurality of applications without inter-application interference. The secure set of static fields may include final static fields of primitive types, final static strings, immutable arrays of primitive types, and / or other appropriate fields.
Owner:SUN MICROSYSTEMS INC
Binning predictors using per-predictor trees and MDL pruning
ActiveUS20070185896A1Reduce information lossReduces the introduction of false information artifactsDigital data processing detailsCharacter and pattern recognitionMemory footprintData selection
Binning of predictor values used for generating a data mining model provides useful reduction in memory footprint and computation during the computationally dominant decision tree build phase, but reduces the information loss of the model and reduces the introduction of false information artifacts. A method of binning data in a database for data mining modeling in a database system, the data stored in a database table in the database system, the data mining modeling having selected at least one predictor and one target for the data, the data including a plurality of values of the predictor and a plurality of values of the target, the method comprises constructing a binary tree for the predictor that splits the values of the predictor into a plurality of portions, pruning the binary tree, and defining as bins of the predictor leaves of the tree that remain after pruning, each leaf of the tree representing a portion of the values of the predictor.
Owner:ORACLE INT CORP
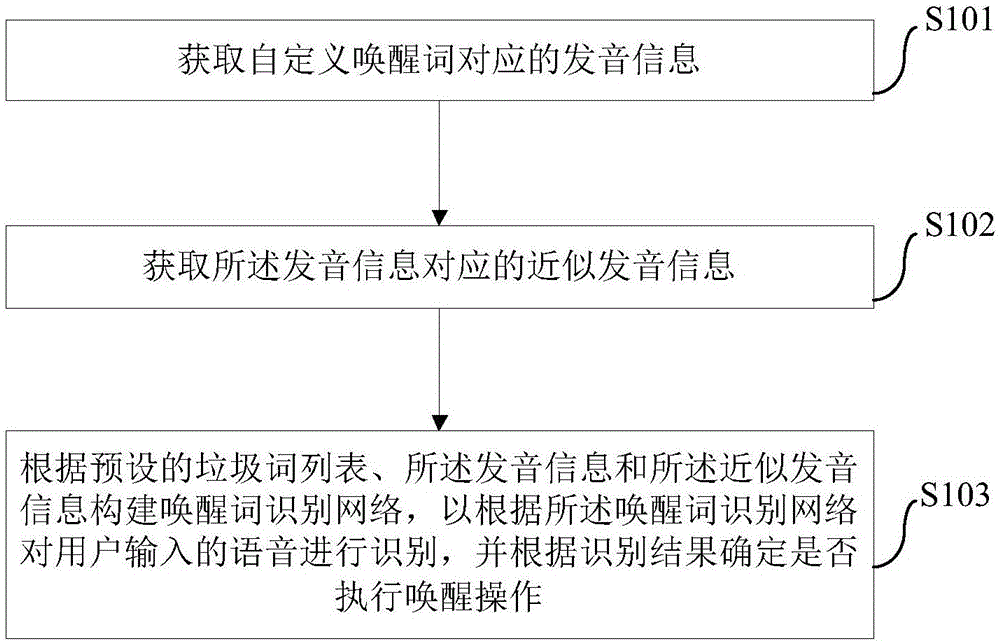
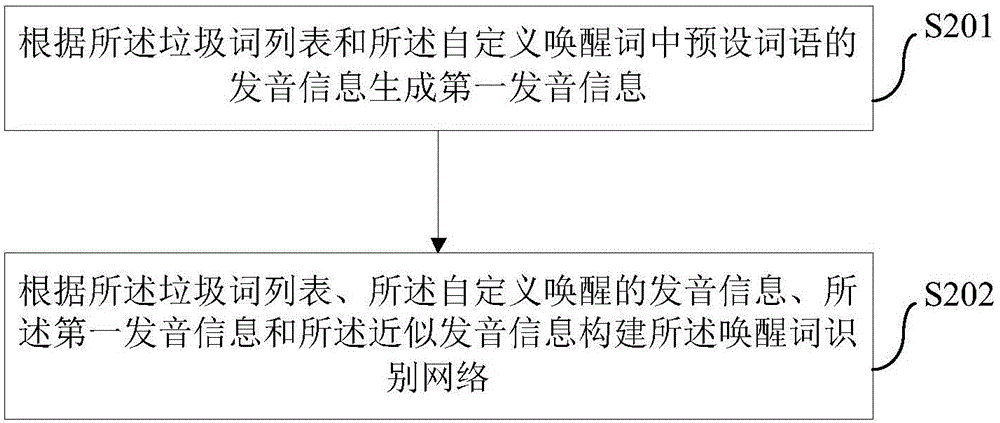
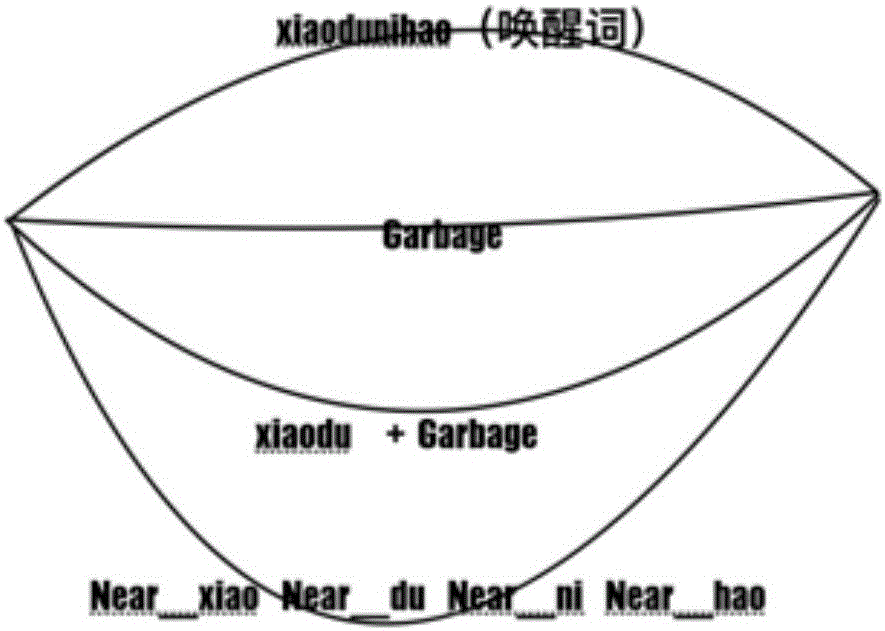
Voice wakeup method and voice wakeup device based on artificial intelligence
ActiveCN106611597AEasy to spread outReduce occupancySpeech recognitionSpeech synthesisMemory footprintWord list
The invention proposes a voice wakeup method and a voice wakeup device based on artificial intelligence. The voice wakeup method comprises the following steps: acquiring pronunciation information corresponding to a custom wakeup word; acquiring approximate pronunciation information corresponding to the pronunciation information; and building a wakeup word recognition network according to a preset spam word list, the pronunciation information and the approximate pronunciation information so as to recognize voice input by a user according to the wakeup word recognition network and determine whether or not need to perform a wakeup operation according to the recognition result. According to the embodiments of the invention, a wakeup word recognition network can be built dynamically for different custom wakeup, so that the accuracy of wakeup is enhanced effectively, the rate of false alarm is reduced, and the wakeup efficiency is improved. The device has smaller memory footprint and low power consumption.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
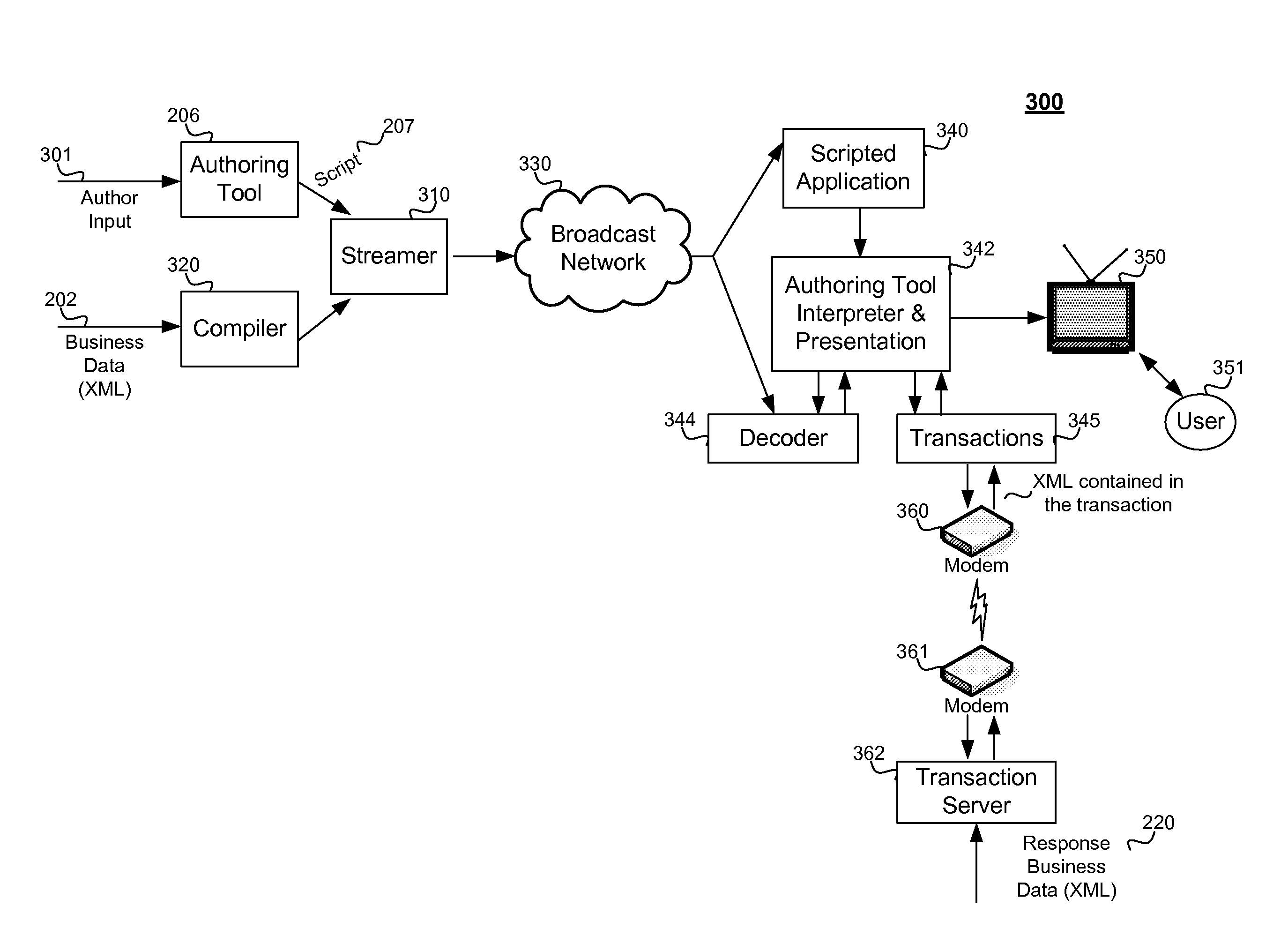
Interactive media presentation system for presenting business data over a digital television network
ActiveUS7516468B1Improve access speedReduce memory usageTelevision system detailsColor television detailsMemory footprintApplication software
The method includes steps for creating and updating an interactive television application, which includes business data and other interactive and dynamic data which changes frequently over time. The interactive television application and data is transmitted over a television broadcast network, and the method includes steps for presenting the data to the user. Business data is compiled into a binary form, the business data for example comprising descriptions of products. A description of an interactive application is generated using an authoring tool. The authoring tool allows a creative designer to create page layouts and use simple script to specify how to respond to user interactions. The compiled business data and the script are streamed to a receiver for generating video information for a user's television, wherein the receiver uses the script to access the compiled business data and generate a presentation of the data for the user. The receiver can be a set-top box for use with a cable television provider, a terrestrial television provider or a satellite television provider. The business data can be compatible with a version of XML (extensible markup language). The business data can be referenced within script created using an authoring tool without the instances of the business data being present at the time of authoring. The compiling can be configured to improve the access speed of the receiver to the business data and to reduce a memory footprint of the business data on the receiver. The business data can be updated and recompiled without requiring the application to be re-authored manually.
Owner:ORACLE INT CORP
Web page loading method and device
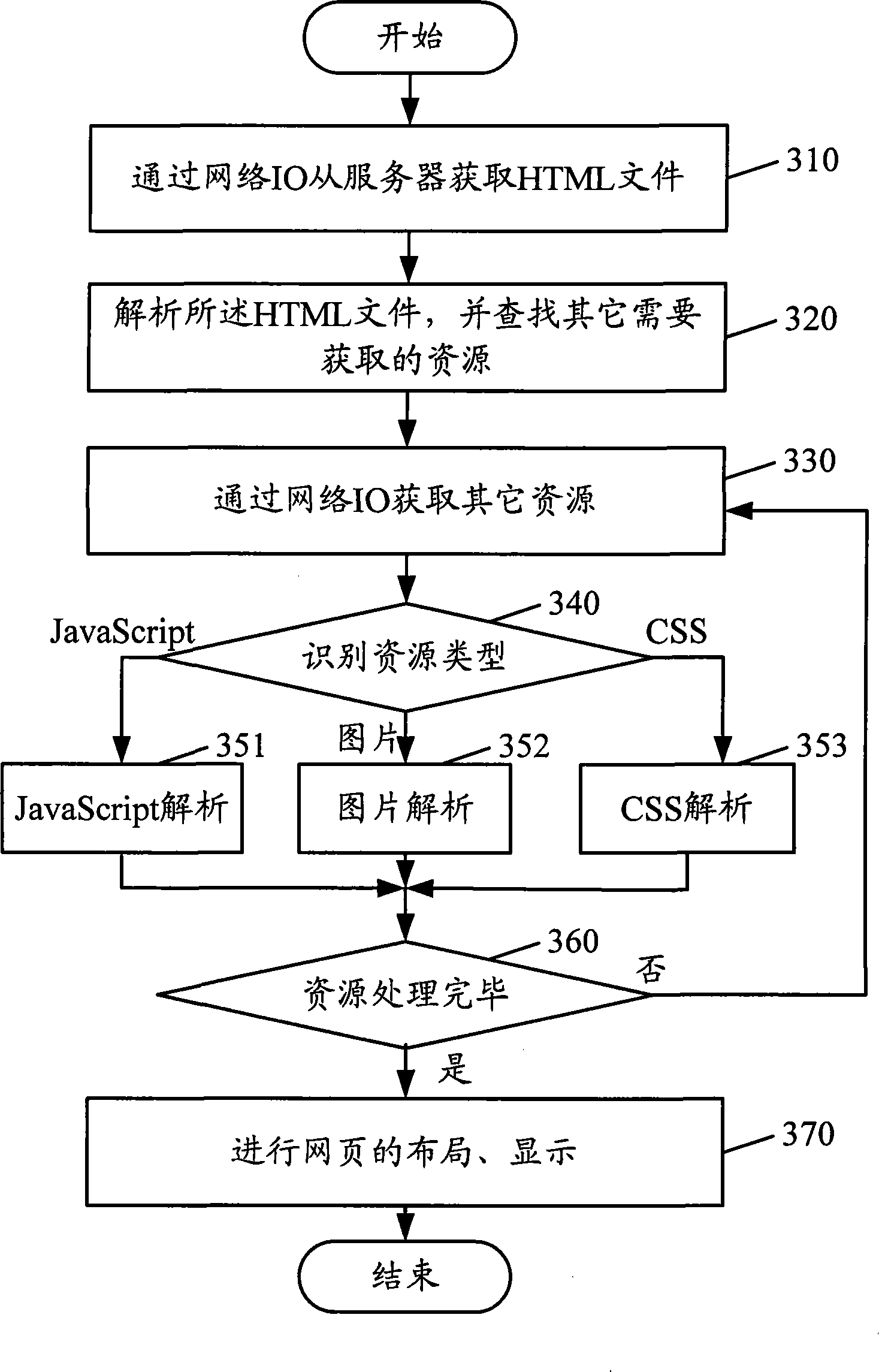
InactiveCN101382958AAvoid reparsingImprove loading timeWebsite content managementSpecial data processing applicationsMemory footprintWeb page
The embodiment of the invention discloses a webpage loading method and a webpage loading device. The method includes the following steps: whether resource analysis data corresponding to resources to be loaded exists is judged and the resource analysis data is directly loaded if so; otherwise, the original resource to be loaded is requested and analyzed to generate resource analysis data corresponding to the original resource to be loaded and the resource analysis data is loaded. Via the share of the resource analysis data after analysis, the re-analysis of shared resource is avoided, thereby saving loading time, improving loading speed and reducing the memory footprint.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
Mobile phone background program cleaning method and mobile phone
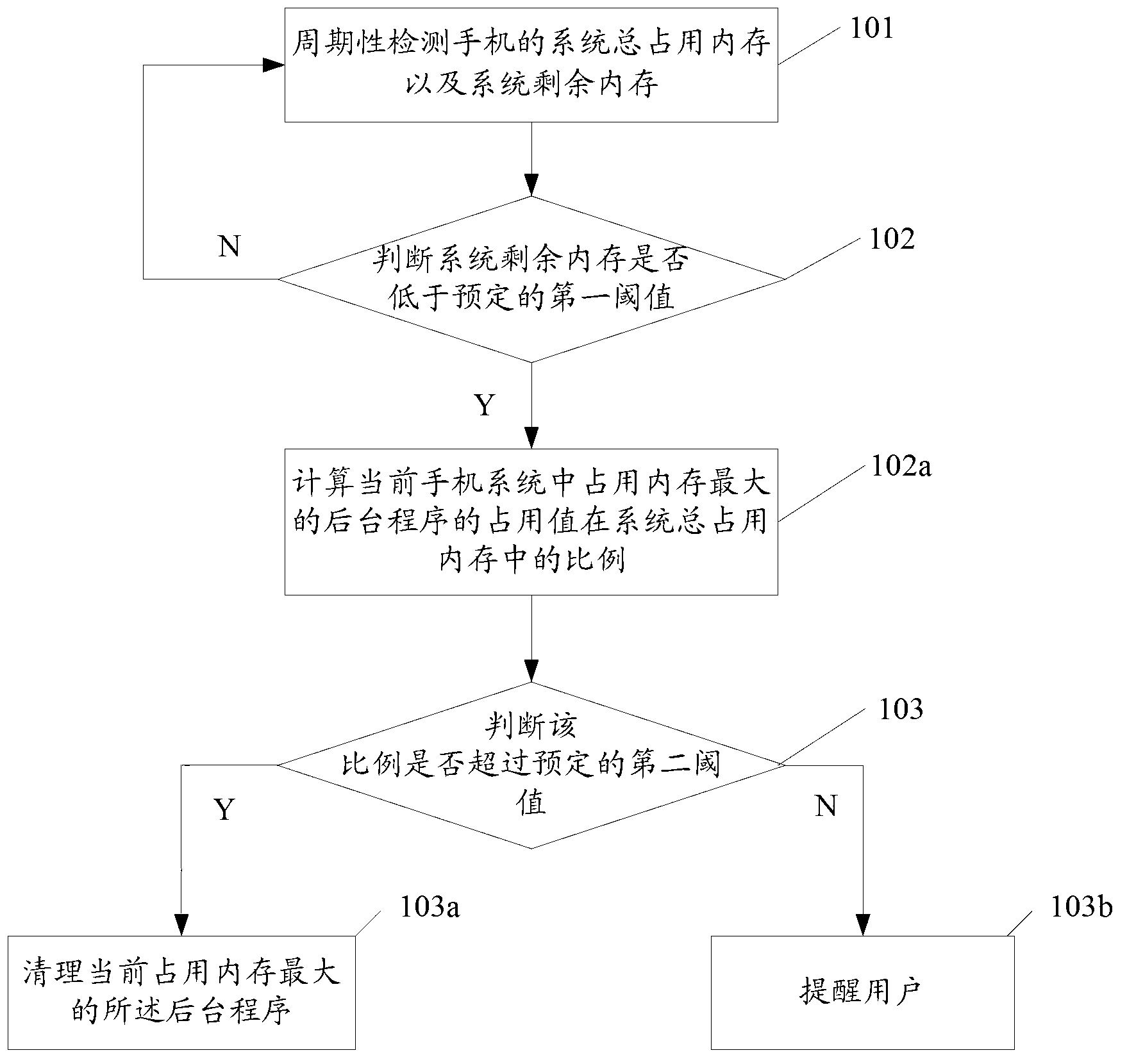
InactiveCN103220427AEasy to useDoes not affect running speedMultiprogramming arrangementsSubstation equipmentMemory footprintMobile phone
The invention discloses a mobile phone background program cleaning method. The mobile phone background program cleaning method includes the following steps: (1) periodically detecting total used system memory and remaining system memory of a mobile phone; (2) calculating the proportion of an usage value of a background program which uses maximum memory in a current mobile phone system in the total used system memory when the remaining system memory is lower than a preset first threshold value; and (3) detecting whether the proportion exceeds a preset second threshold value, if the proportion exceeds the preset second threshold value, cleaning the background program which uses the maximum memory in the current memory, and if the proportion does not exceed the preset second threshold, reminding a user. According to the mobile phone background program cleaning method, the background program which uses the maximum memory in the current memory can be cleaned or the user is reminded to manually clean a certain background program according to a mobile phone system memory usage state, and background programs which do not affect system operation speed are retained. The invention correspondingly discloses the mobile phone.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Method for quick finishing large data-handling and reporting system
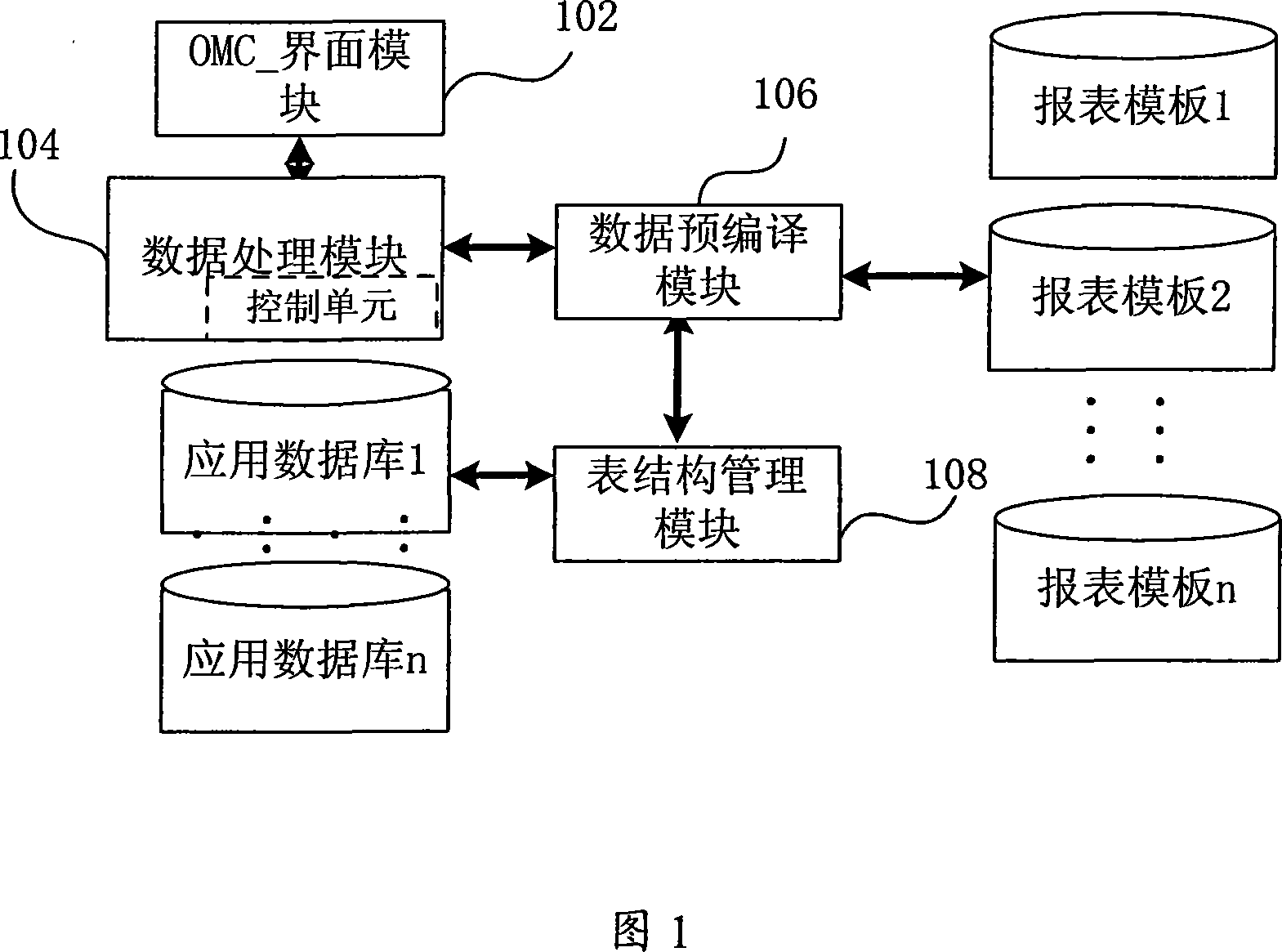
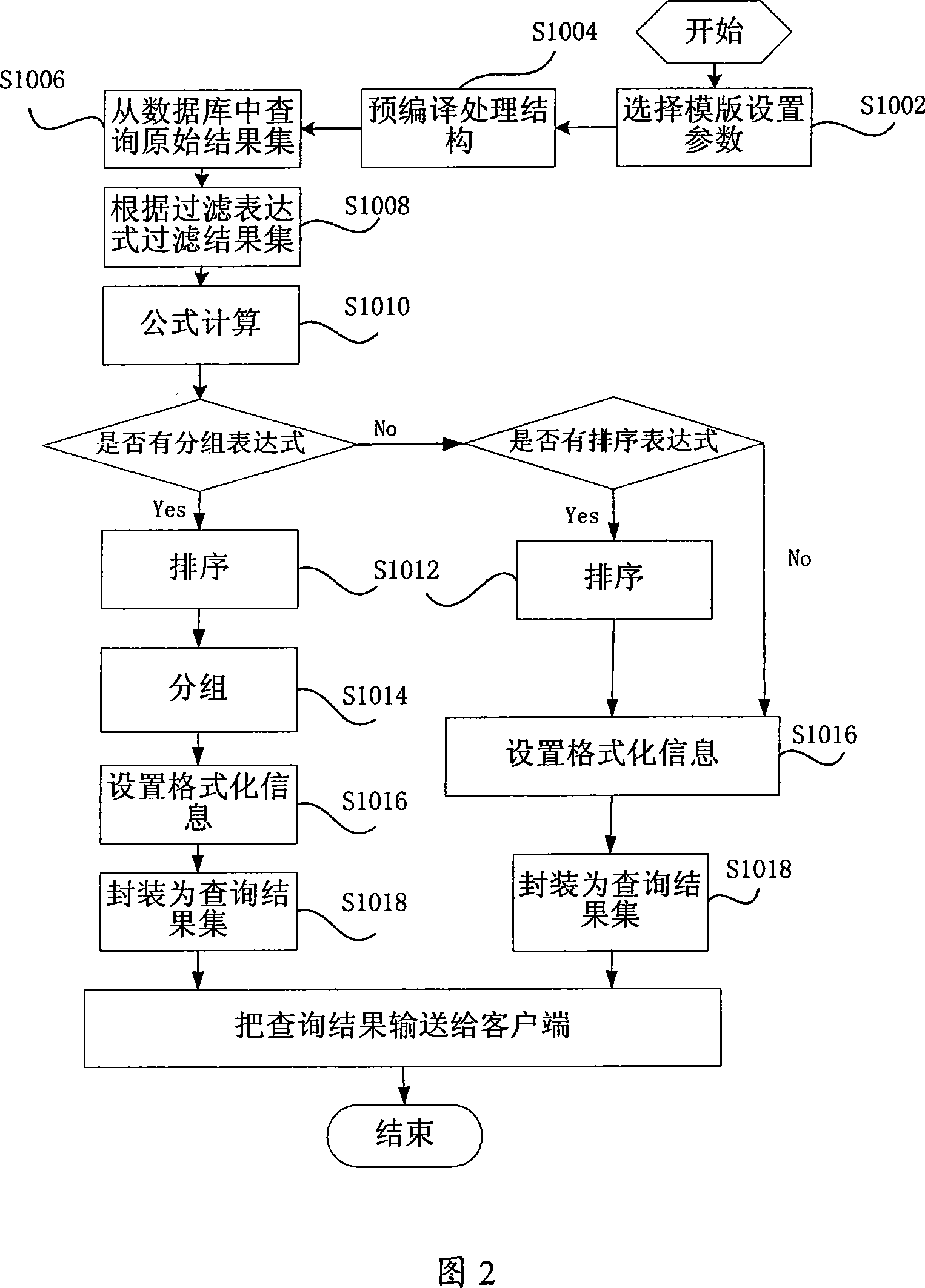
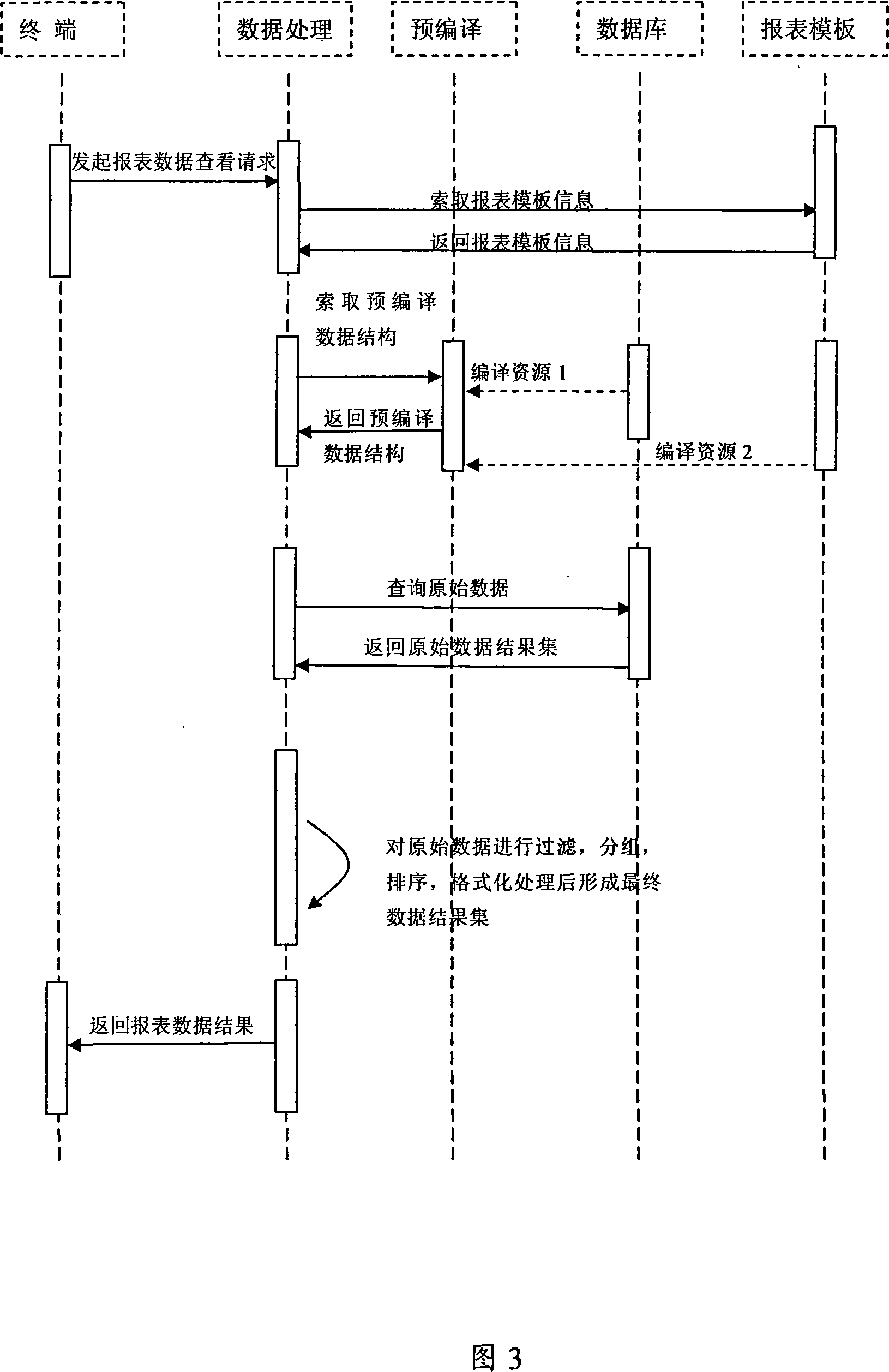
InactiveCN101183371AImprove data transfer efficiencySmall footprintData switching networksSpecial data processing applicationsMemory footprintFiltration
The invention discloses a report system and method for quickly completing large data processing. The method includes: selecting a report template and setting parameters for report query; forming a pre-compiled data structure according to the selected report template and parameter information; Query the original result set in , and filter the original result set according to the filter expression; the data processing module sorts and groups the filtered result set, and performs formatting according to the template information; the data processing module converts the report The resulting structure is encapsulated as a query result set and returned to the client for rendering. The system and method of the present invention are used to realize high-speed data generation because the format and data are completely separated. After the client receives the data, it does not need to analyze the data, which improves the efficiency of data transmission between the client and the server, greatly Improve the speed of querying a large amount of data in the report, reduce the memory usage of server-side data, and reduce the system load.
Owner:ZTE CORP
Compositing images from multiple sources
InactiveUS6903753B1Minimization requirementsDouble buffering requirements can be significantly reduced or eliminatedColor signal processing circuitsCharacter and pattern recognitionData streamColor transformation
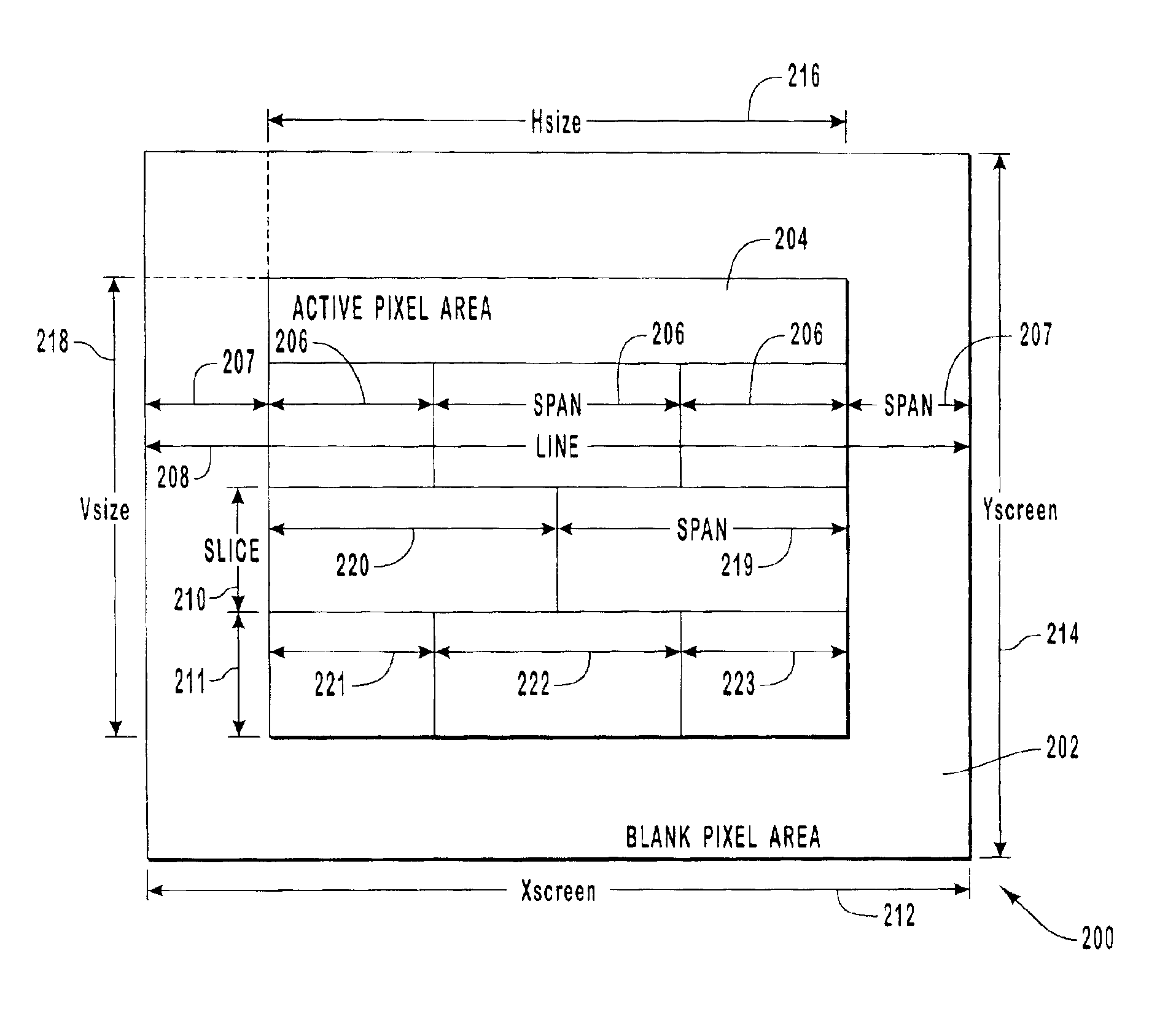
Systems and methods for compositing an image directly from multiple source image data for reducing system memory footprint and bandwidth and for improving color quality of the image. The image is divided into spans, lines, and slices. Each line includes at least one span and each slice includes at least one line. All lines in a slice have spans associated with identical sources. An image is composited by reading the image data directly from one or more sources of each span. If necessary, the sources are blended. A control structure is used to provide the image context and identifies the sources of the spans. The control structure includes headers for each data stream from each source of each span. Also, the color quality of the image is improved by reducing the number of color space conversions that occur as the image is composited. All sources in the same color space are blended before being blended with sources from other color spaces. Preferably, no more than a single color conversion is required.
Owner:MICROSOFT TECH LICENSING LLC
Session data sharing system and method
The invention belongs to the technical field of computer application and particularly provides a session data sharing system and method. The system comprises at least one Web application server and a cache server; the Web application servers are used for processing HTTP requests of client-sides and completing requested service logic, and each Web application server is a Servlet container based on Java and is composed of a session sharing processing request filter, a session data processing unit, a session data temporary storage unit and a service logic processing unit; the cache server is used for storing session data. According to the session data sharing system and method, the session data are stored into the cache server and can be shared by the Web application servers, so that memory occupation of the Web application servers is reduced; loss of the session data on the Web application servers can be avoided, the problems of loss of network performance and inconsistency of the session data caused by session data replication between cluster nodes can be avoided, the session data access speed is increased, and the session data processing performance is improved.
Owner:SHANGHAI HANDPAL INFORMATION TECH SERVICE
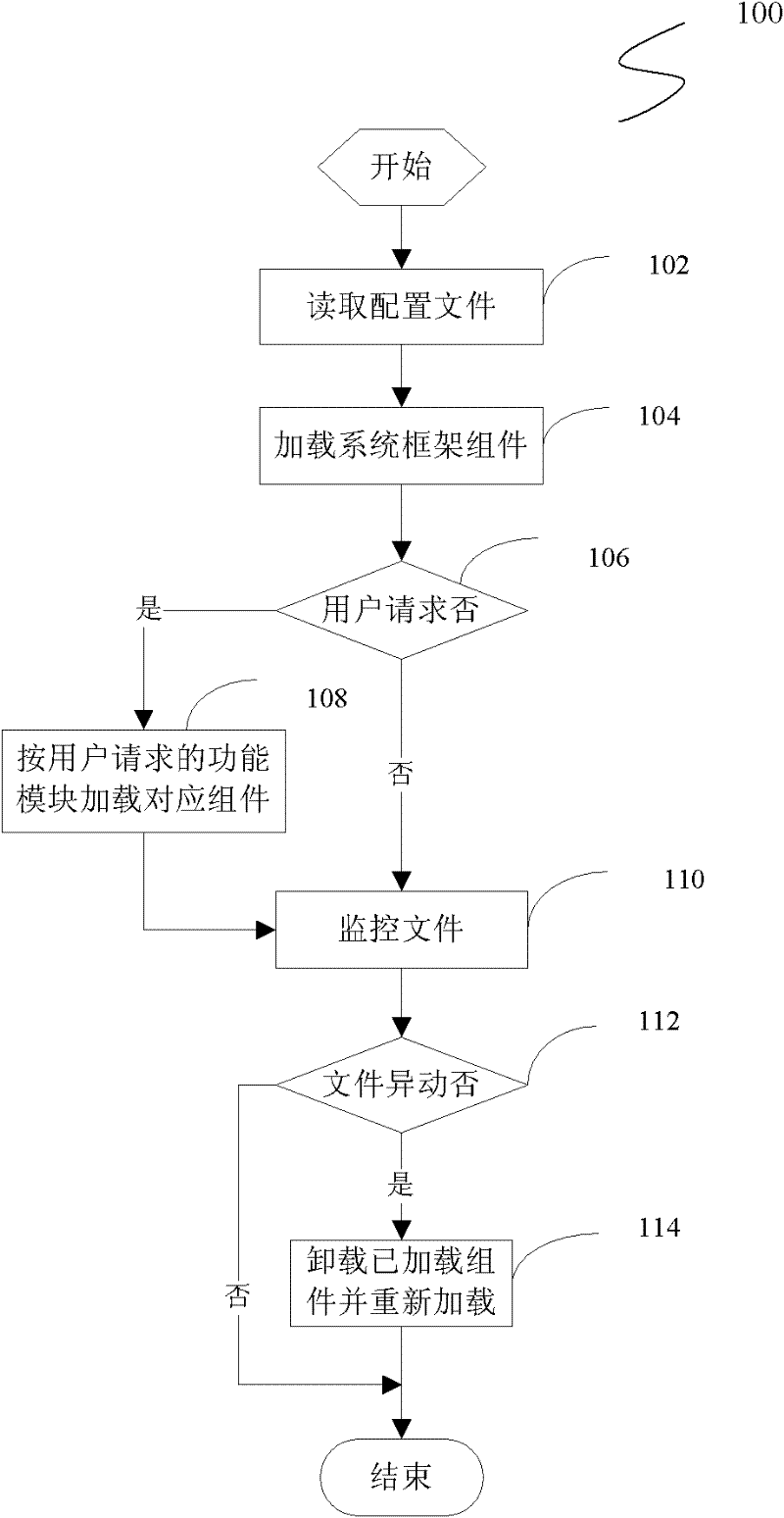
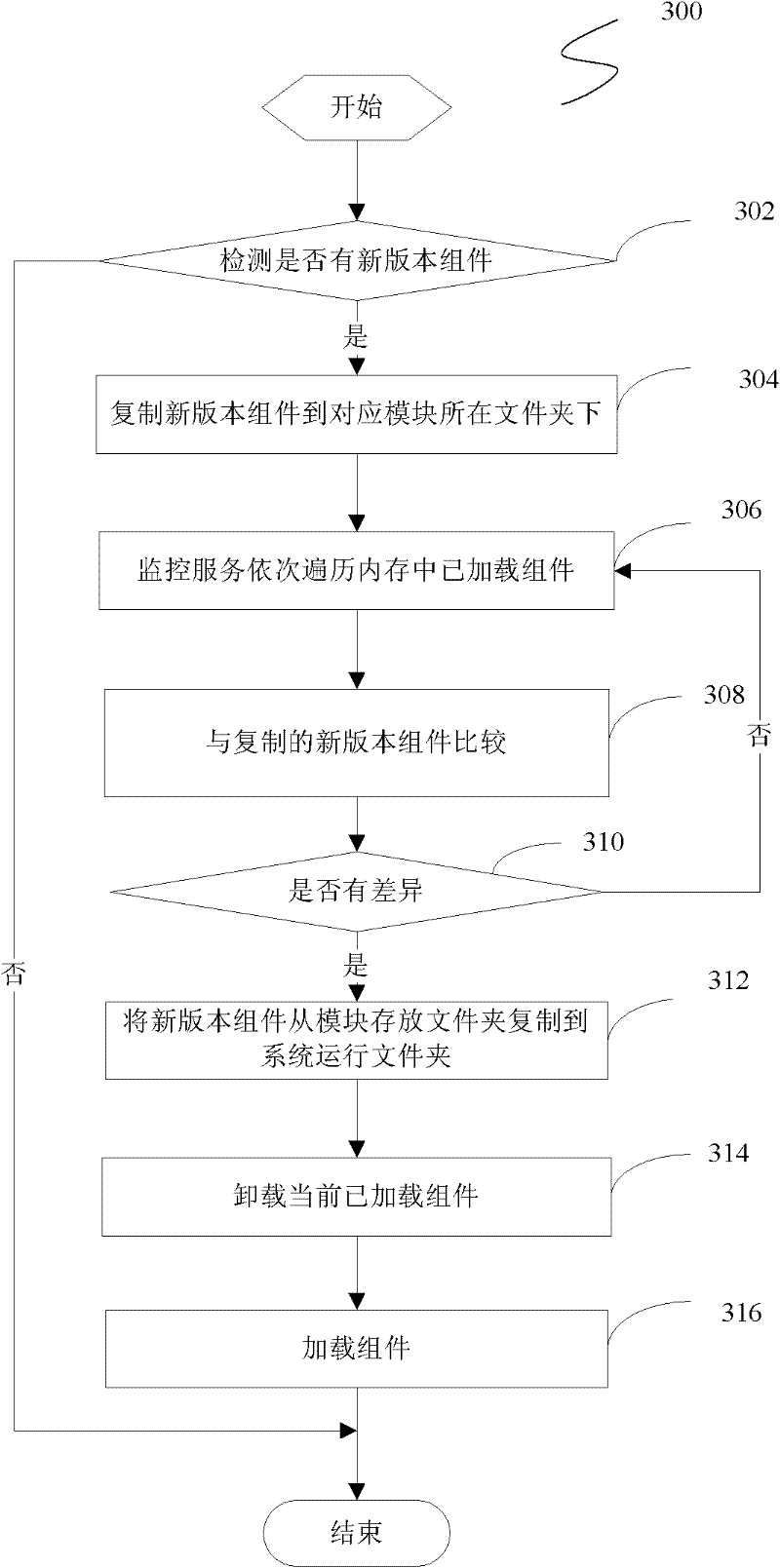
Method and system for dynamically loading component
ActiveCN102541598AFast startupImprove efficiencyProgram loading/initiatingMemory footprintComputer module
The invention discloses a method and a system for dynamically loading a component. The method comprises the following steps of: storing components of different functional modules under an application program into different file folders, and storing storage routes corresponding to the components into a configuration file; when the application program is started, reading the configuration file, loading necessary components of a system framework of the application program, loading the components of the functional modules according to the storage routes of the components of the functional modules in the configuration files when a request of a user for calling the functional modules under the application program is received, and caching the components in a memory. According to the method and the system, the components are divided according to the functional modules; when the application program is started, only the components required by the least number of users are loaded, so that the speed of initializing the system is increased, the memory occupancy is reduced, and the running efficiency of the system is improved.
Owner:SHENZHEN LAN YOU TECH
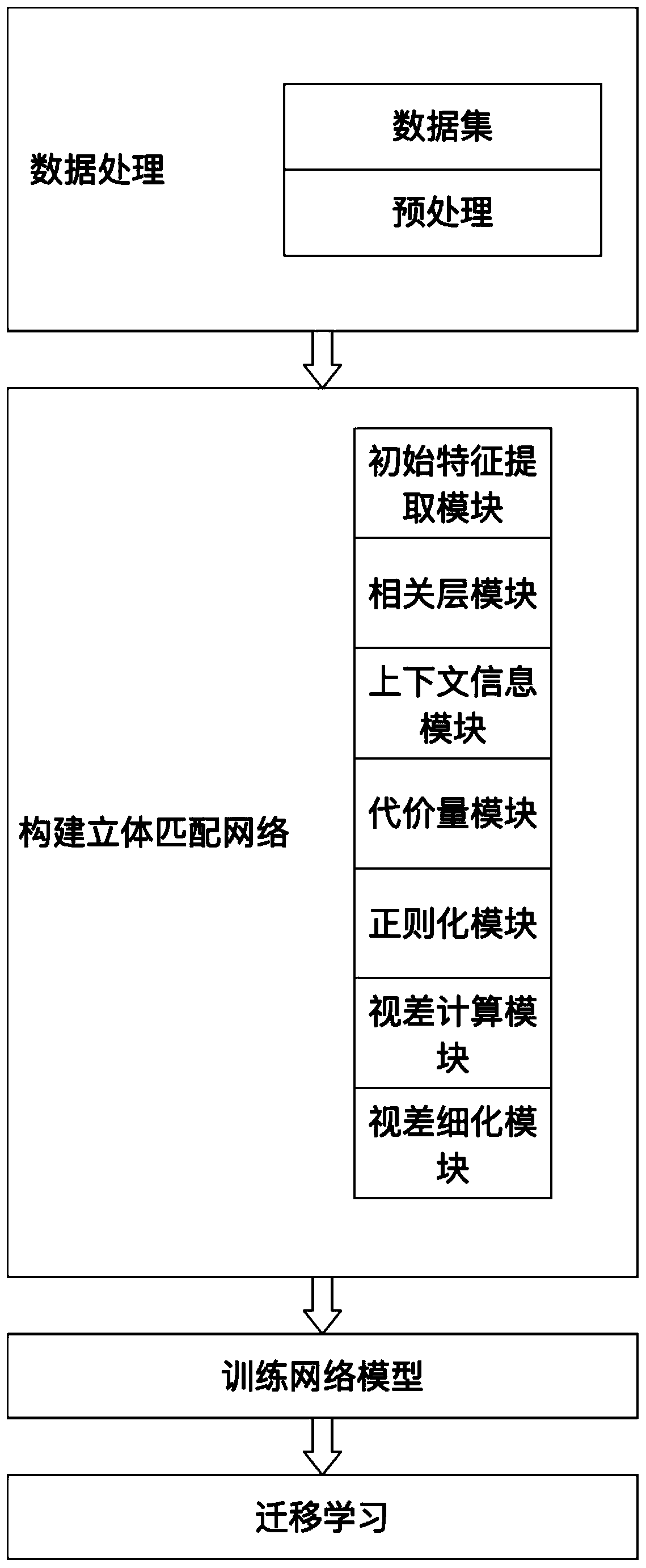
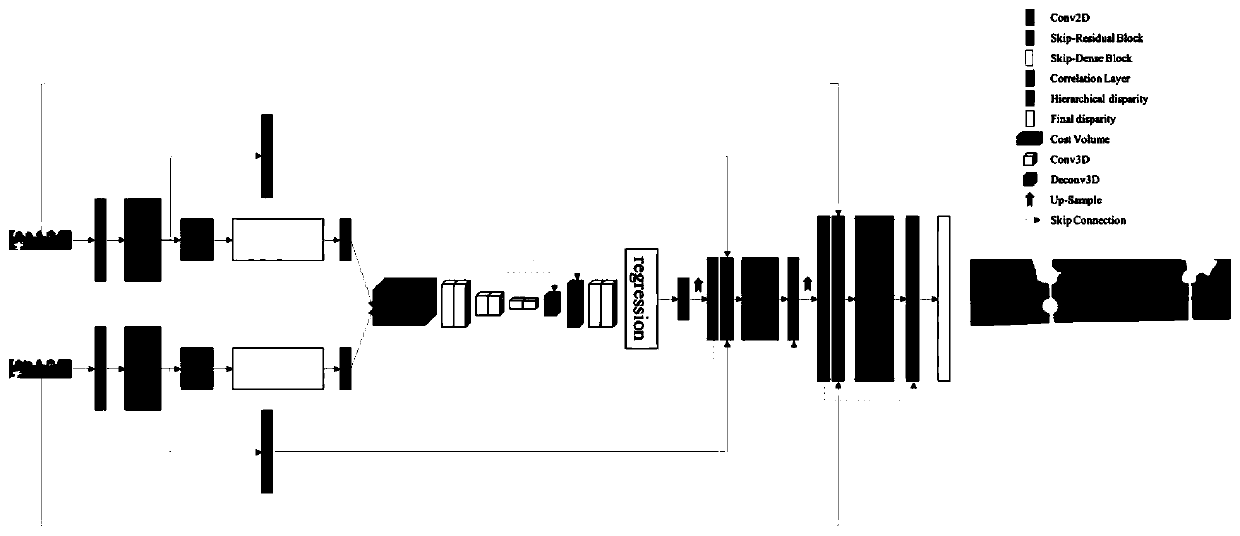
Binocular stereo matching method based on convolutional neural network
ActiveCN110533712AImprove forecast accuracyMitigation mismatchImage enhancementImage analysisParallaxCost aggregation
The invention discloses a binocular stereo matching method based on a convolutional neural network. For matching cost calculation, context information is integrated by using dense blocks on the basisof initial features. For matching cost aggregation, a regularization cost amount of a small coding and decoding structure is provided. And for parallax calculation, a differentiable soft argmin operation is executed on the parallax dimension of the cost quantity to obtain an initial parallax. For parallax refinement, the initial parallax is guided to be refined by taking a residual block as a mainpart and taking similarity measurement as an auxiliary part. According to the method, four stages of a stereo matching algorithm are strictly followed, and four steps are integrated into one network,so that the network can be trained end to end. According to the stereo matching method, contextual information is integrated in the feature extraction process, mismatching of pixel points in an ill-conditioned area is effectively relieved, memory occupation and running time in the network training / speculation period are remarkably reduced through small and medium coding and decoding structures inthe regularization process, and parallax prediction precision is improved.
Owner:BEIJING UNIV OF TECH
Method and device for detecting safety state of terminal device
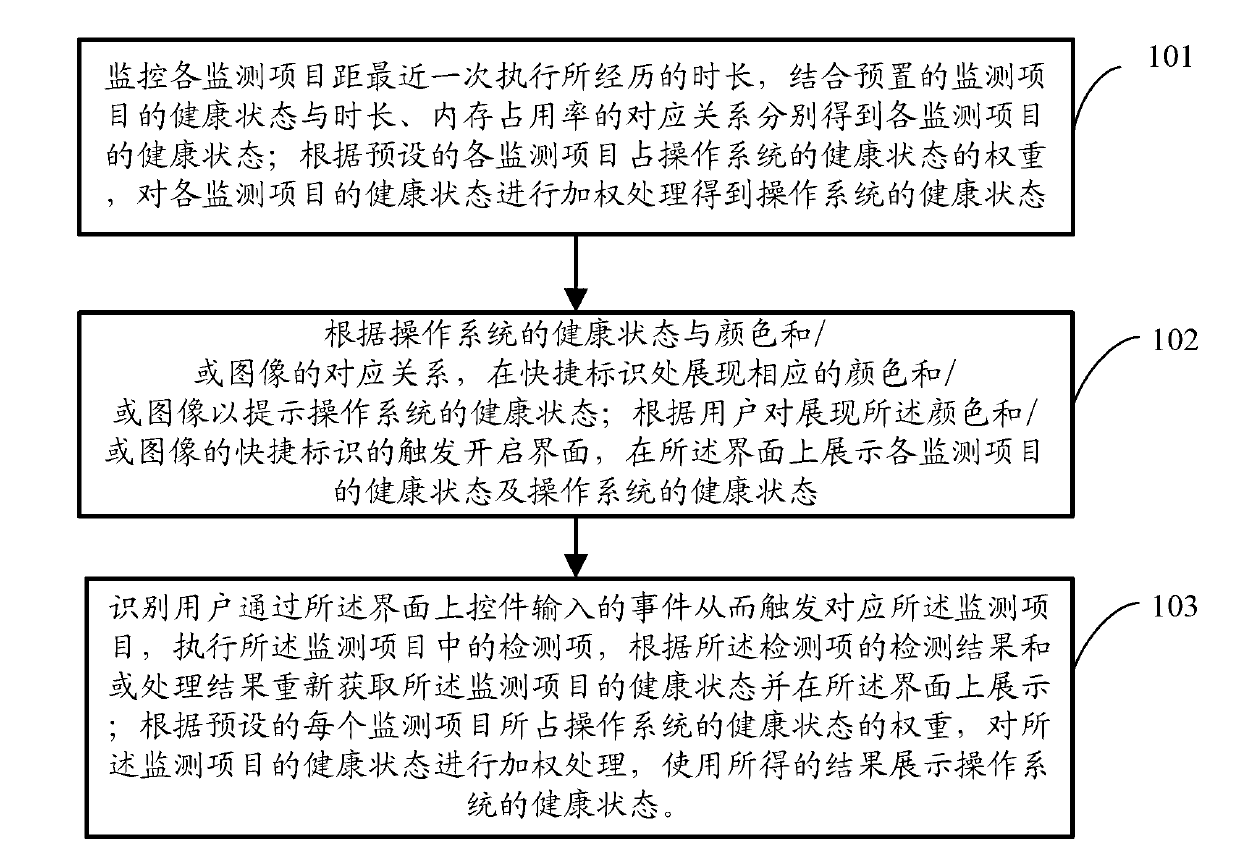
ActiveCN103136091AShow completionUnderstand business contentHardware monitoringOperational systemMemory footprint
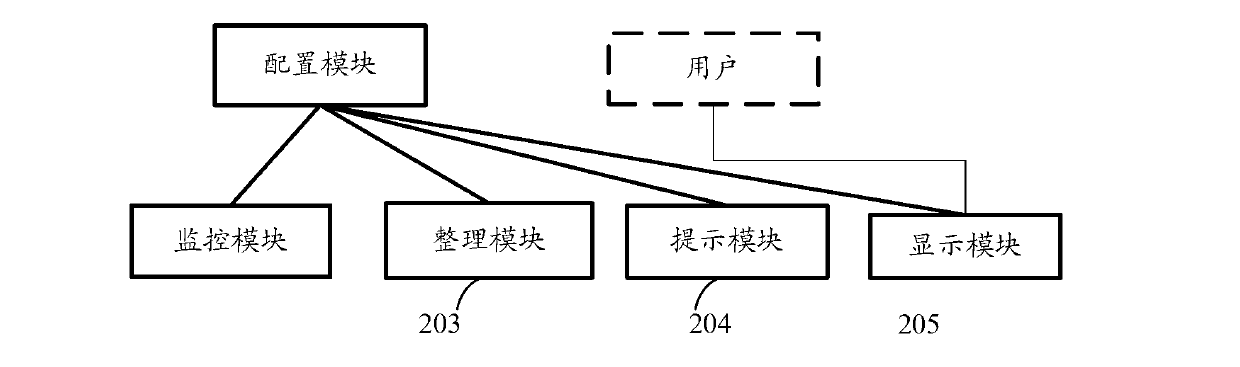
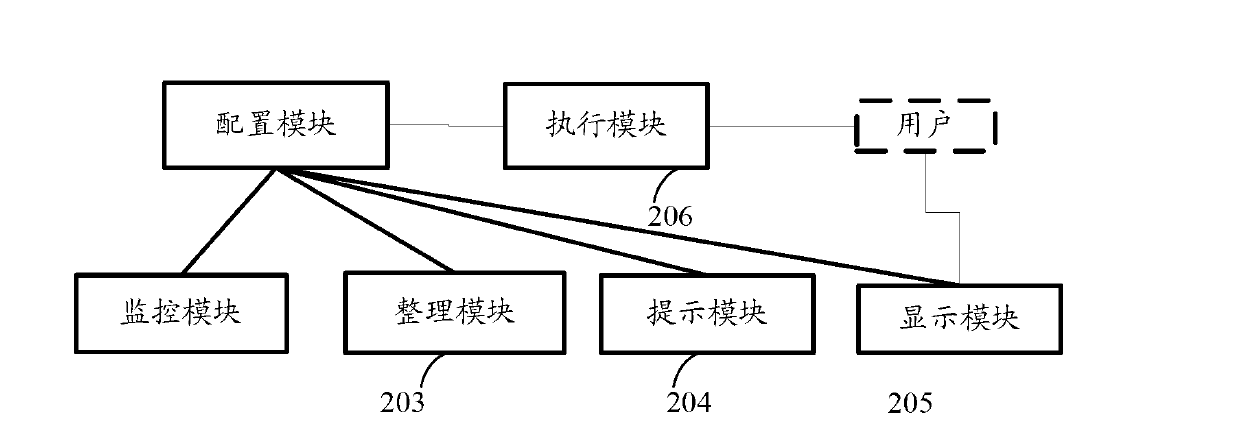
The invention discloses a method and device for detecting a safety state of a terminal device. The device comprises a configuration module, a monitoring module, a tidying module, a prompting module and a displaying module. The configuration module presets correspondence relation between healthy states and time interval and memory usage rate and weight of healthy states of monitoring programs occupying an operation system. The monitoring module monitors the time interval of the monitoring programs from the last-time execution and obtains the healthy states of the monitoring programs by combining the correspondence relation between the healthy states and the time interval and the memory usage rate. The tidying module performs weighted processing to the healthy states of the monitoring programs to obtain the healthy state of the operation system. The prompting module displays a color and / or an image corresponding to the obtained healthy state of the operation system. The displaying module opens an interface through triggering of a color and / or image quick icon operated by a user and displays the healthy states of the monitoring programs and the operation system. The method and device for detecting the safety state of the terminal device performs device testing, gives healthy state evaluation and finishes and displays the cleaning or optimizing work.
Owner:BEIJING QIHOO TECH CO LTD
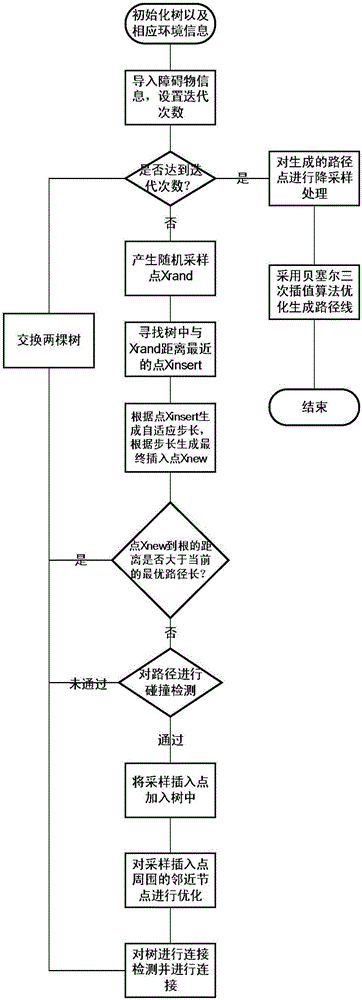
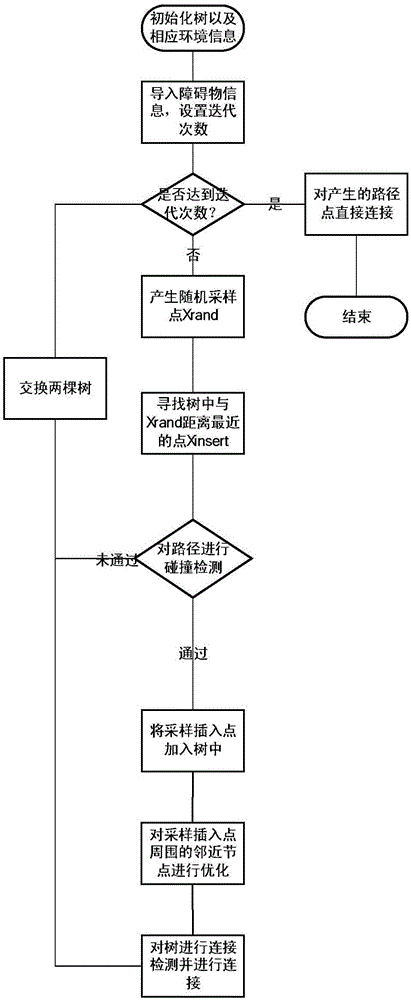
MB-RRT-based unmanned aerial vehicle two-dimensional track planning method
ActiveCN106444740AReduce memory usageAddress limitationsPosition/course control in two dimensionsPath lengthCollision detection
The invention discloses an MB-RRT-based unmanned aerial vehicle two-dimensional track planning method, comprising the steps of initializing a tree and environmental information; importing obstacle information, and setting a number of iterations; judging whether the number of iterations is arrived, if so, performing down-sampling on the generated path point and optimizing the generated path line by adopting an interpolation algorithm; otherwise, generating a random sampling point, looking for a point nearest to the random sampling point in the tree, generating an adaptive step length according to the point, generating a final interpolation point according to the step length, judging whether the distance between the interpolation point and the root is greater than the current optimal path length, if not, performing collision detection on the path, adding the interpolation point to the tree and optimizing adjacent nodes around the interpolation point; if not, performing connection detection and connection on the tree. The method is high in convergence rate and small in memory occupation space, solves the problem of limitation of growth nearby an obstacle, and can be directly applied to unmanned aerial vehicle control.
Owner:ZHEJIANG UNIV OF TECH
Hybrid-domain full wave form inversion method of central processing unit (CPU)/graphics processing unit (GPU) synergetic parallel computing
InactiveCN103135132ASolving Convergence ProblemsAvoid the problem of insufficient storage and occupancySeismic signal processingInternal memoryFull wave
The invention discloses a hybrid-domain full wave form inversion method of central processing unit (CPU) / graphics processing unit (GPU) synergetic parallel computing. Compared with a traditional method, the method can be adopted to conduct the CPU / GPU synergetic parallel computing so as to obviously improve computing efficiency. The method enables a forward part of full wave form inversion to be placed to a time domain, namely forward is conducted in the time domain, the forward is converted to be conducted as the inversion in a frequency domain by the discrete fourier transform (DFT) being utilized, namely the DFT is adopted to pick wave field components corresponding to inversion frequency, and the inversion is conducted in the frequency domain from low frequency to high frequency. The method effectively resolves the problem of astringency of a standard time domain method, and avoids the problem that internal memory of wave form inversion of a standard three-dimensional frequency domain and a Laplace domain cannot be satisfied. The method is few in step, reduces computing expenses, and due to the fact the method can be adopted to conduct the CPU / GPU synergetic parallel computing, largely improves speed-up ratio of the computing method.
Owner:INST OF GEOLOGY & GEOPHYSICS CHINESE ACAD OF SCI
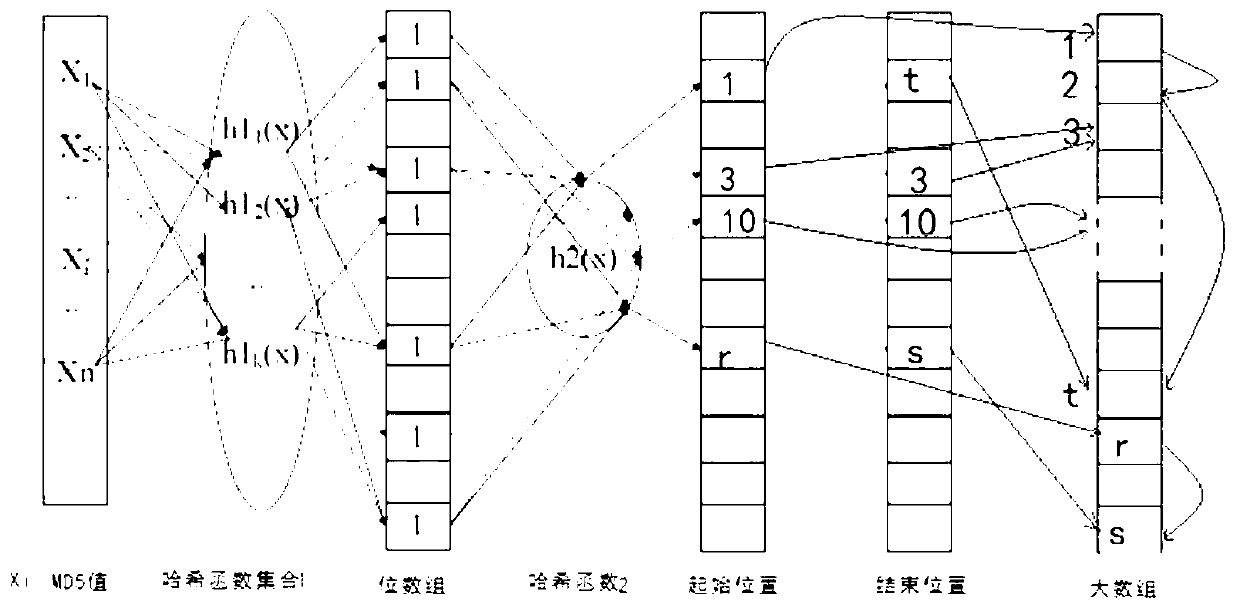
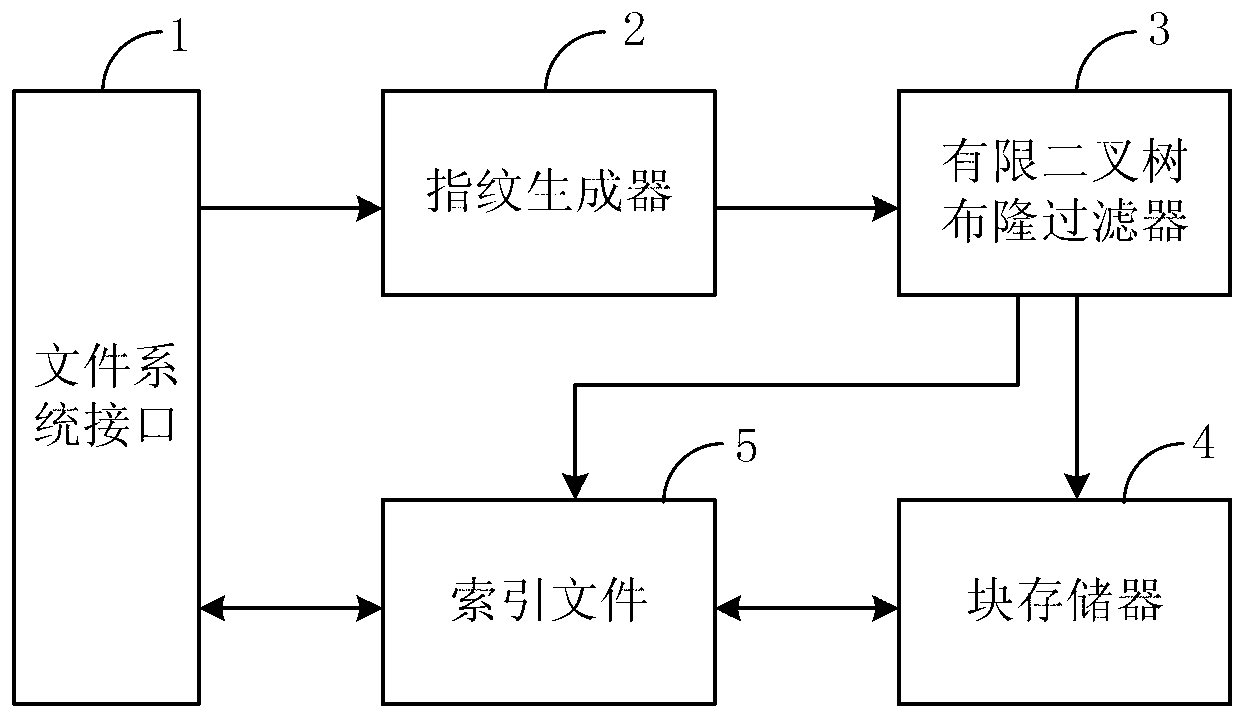
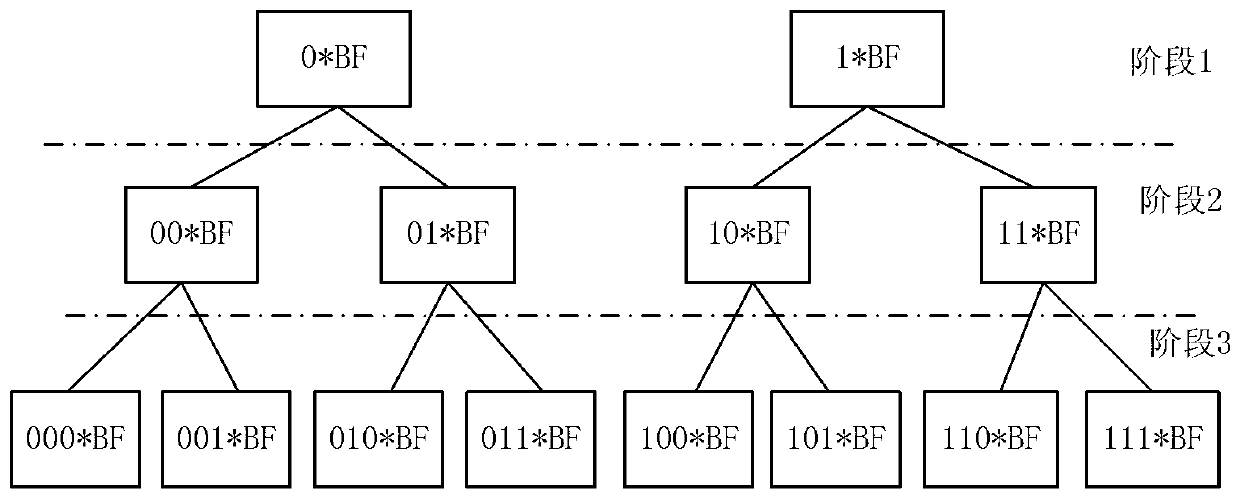
Redundancy removal file system based on limited binary tree bloom filter and construction method of redundancy removal file system
InactiveCN103345472AReduce misjudgmentHigh Deduplication Rate AccessSpecial data processing applicationsMemory footprintFile system
The invention provides a limited binary tree bloom filter, a redundancy removal file system based on the limited binary tree bloom filter, and a construction method of the redundancy removal file system based on the limited binary tree bloom filter. According to the limited binary tree bloom filter, an upper limit is arranged for the number of nodes of each layer, each node is a two-stage bloom filter, and each two-stage bloom filter comprises a standard bloom filter body and a second portion which contains fingerprints and addresses of data blocks in a stored mode. Firstly, a fingerprint of each data block is searched in the standard bloom filter bodies; when the fingerprint of each data block is not found, a node misses, otherwise, search is continuously carried out in the second portions, the node hits the target when a completely matched fingerprint is found in the second portions, and otherwise the node misses. The redundancy removal file system and the construction method of the redundancy removal file system achieve write-in, reading and deletion of files on the basis of the limited binary tree bloom filter. Misjudgment is reduced through a secondary query, and the limited binary tree bloom filter, the redundancy removal file system based on the limited binary tree bloom filter, and the construction method of the redundancy removal file system based on the limited binary tree bloom filter have the advantages of being low in occupation of the memory, low in usage of a CPU, low in occupation of additional space, high in redundancy removal ratio, and excellent in access performance and extensibility.
Owner:BEIHANG UNIV
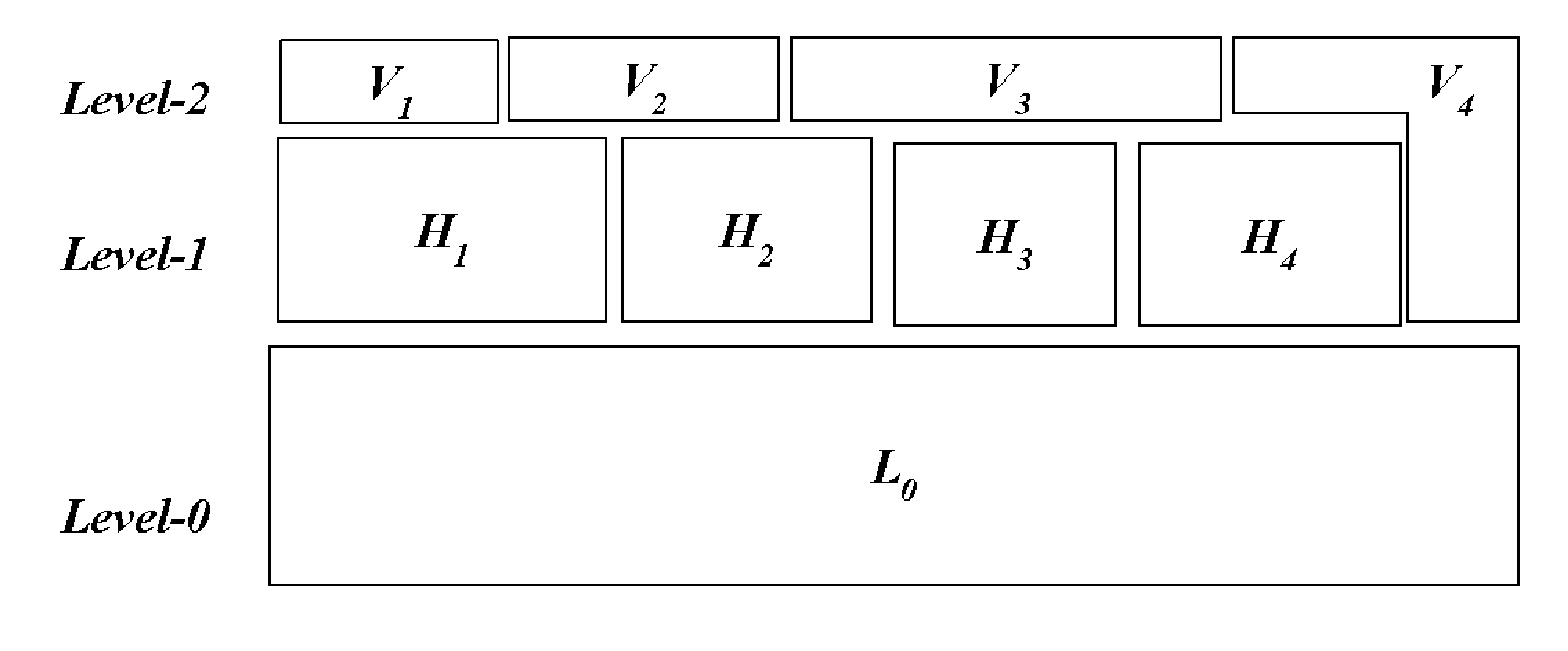
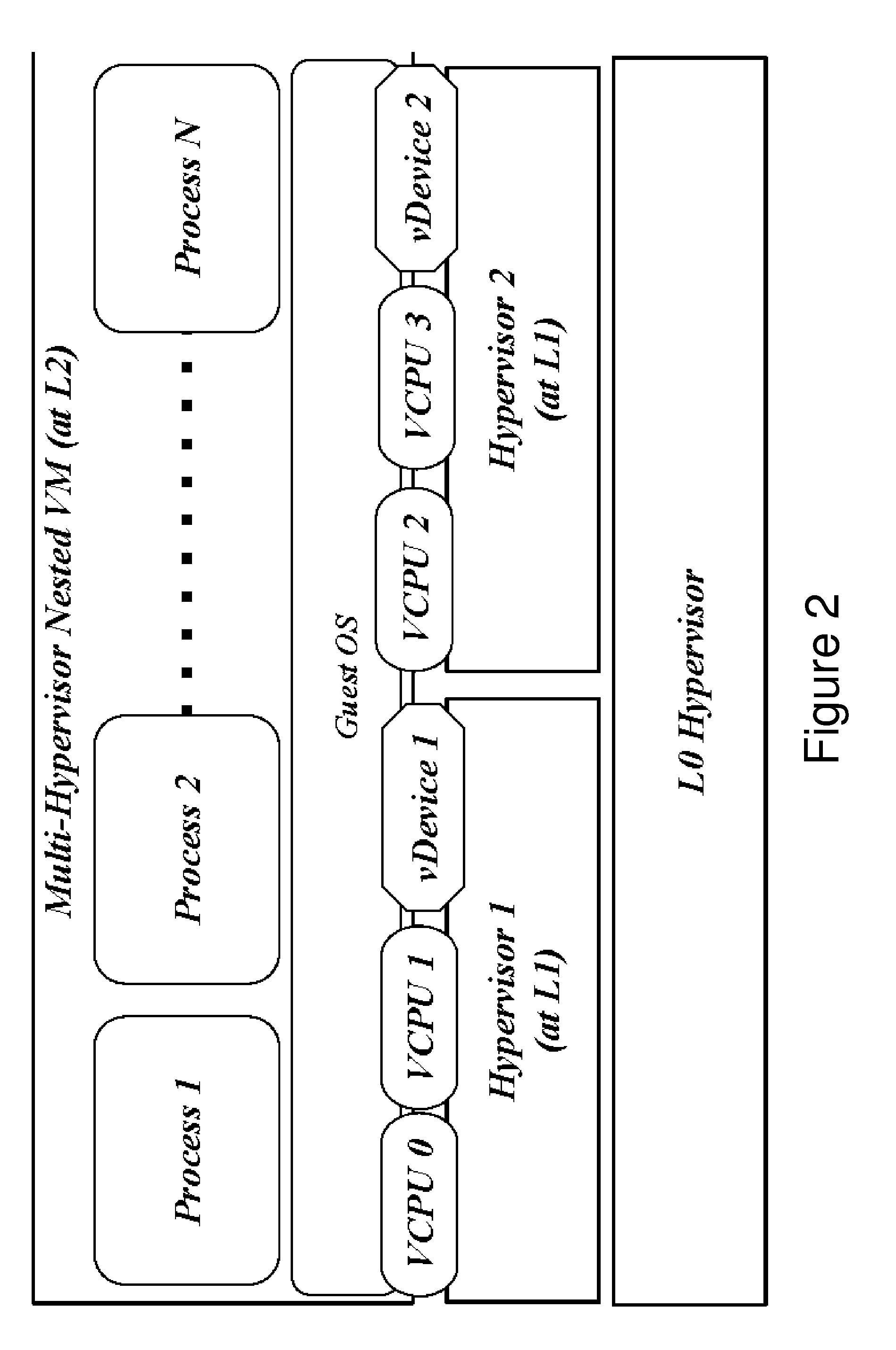
Multi-hypervisor virtual machines
ActiveUS20160147556A1Improve performanceNegatively impacts the I/O performance of the benchmarked systemSoftware simulation/interpretation/emulationMemory systemsMemory footprintNested virtualization
Standard nested virtualization allows a hypervisor to run other hypervisors as guests, i.e. a level-0 (L0) hypervisor can run multiple level-1 (L1) hypervisors, each of which can run multiple level-2 (L2) virtual machines (VMs), with each L2 VM is restricted to run on only one L1 hypervisor. Span provides a Multi-hypervisor VM in which a single VM can simultaneously run on multiple hypervisors, which permits a VM to benefit from different services provided by multiple hypervisors that co-exist on a single physical machine. Span allows (a) the memory footprint of the VM to be shared across two hypervisors, and (b) the responsibility for CPU and I / O scheduling to be distributed among the two hypervisors. Span VMs can achieve performance comparable to traditional (single-hypervisor) nested VMs for common benchmarks.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Method of implementation of audio codec
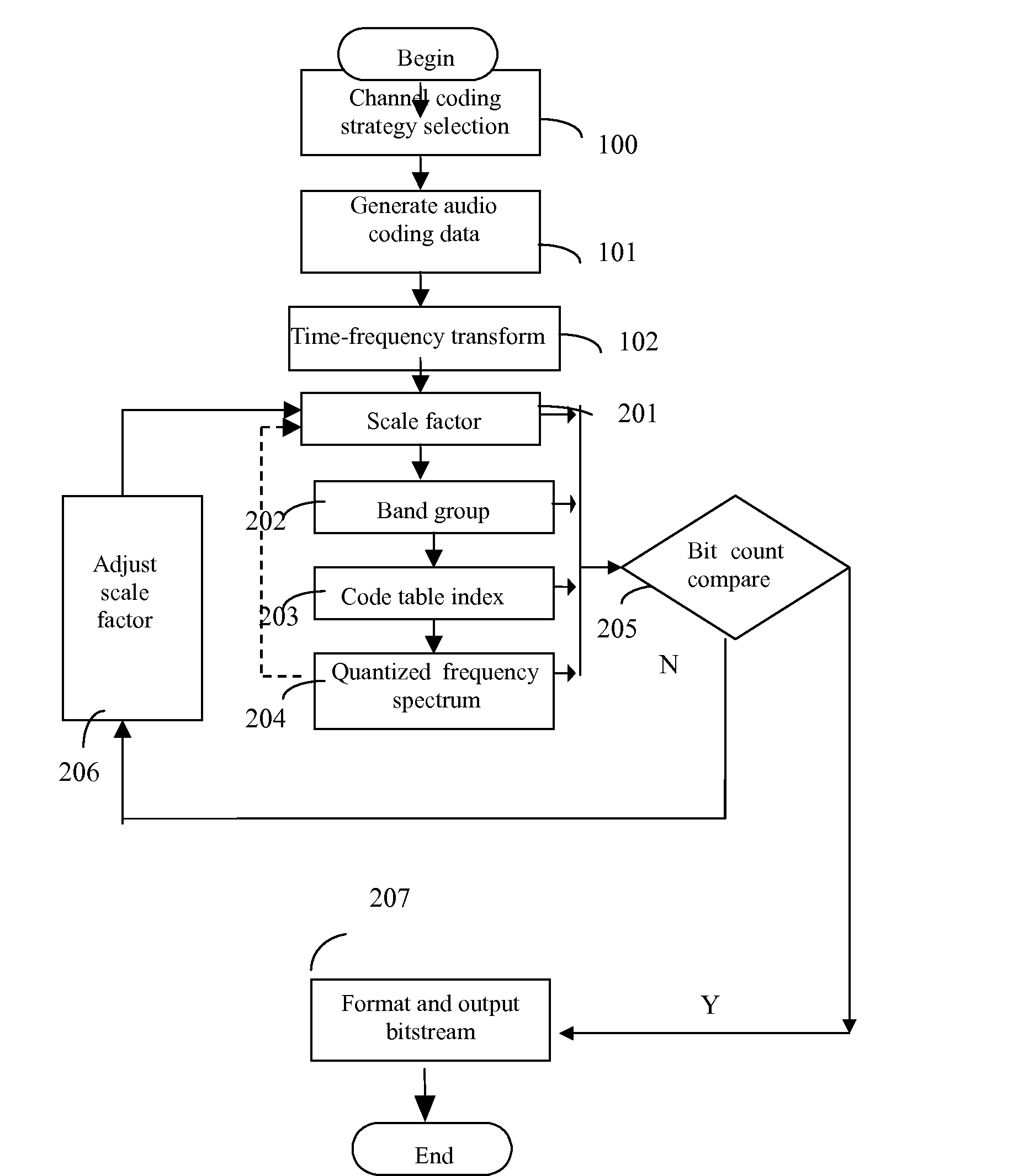
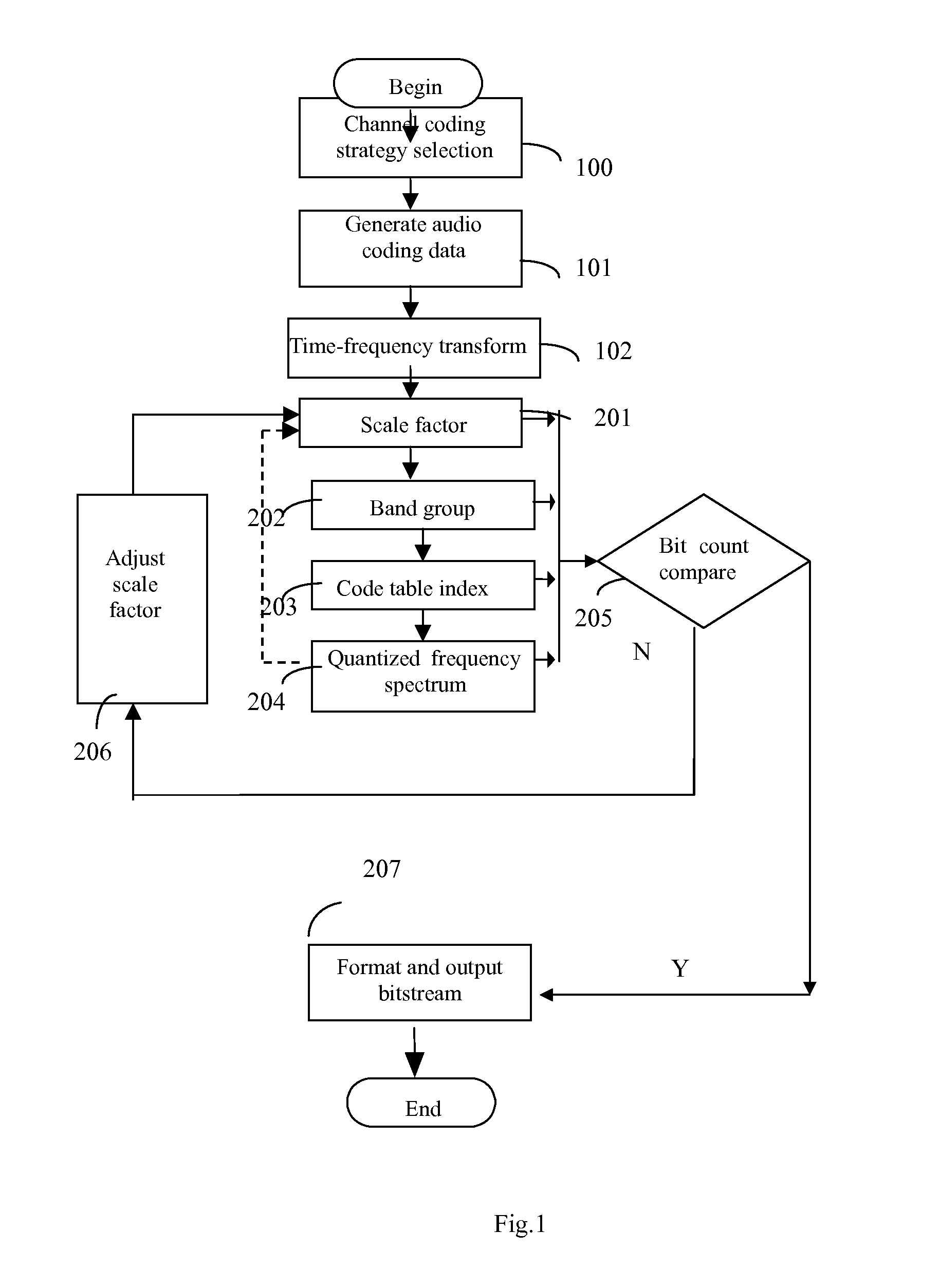
InactiveUS20070027677A1Easily identifiableReduce complexitySpeech analysisFrequency spectrumComputation complexity
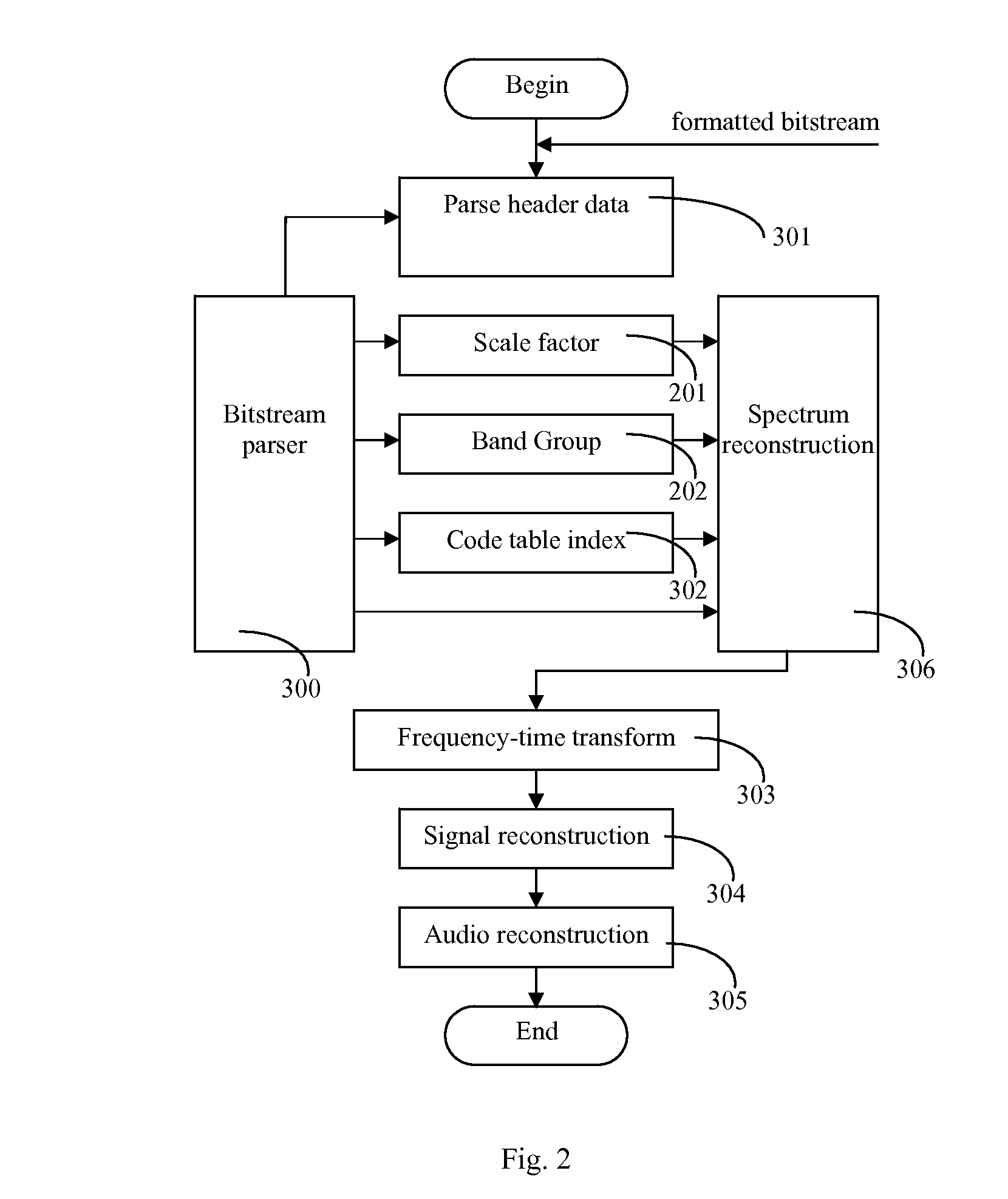
This invention discloses an implementation of audio codec, which has low computational complexity, small memory footprint and high coding efficiency. It can be used in handheld devices, SoC or ASIC products and embedded systems. At the encoder side: first, apply time-to-frequency transform to audio signals, obtaining un-quantized spectrum data; second, based on the un-quantized spectrum data and target bit count, calculate the corresponding information of optimal scale factor, frequency band group, code table index and quantized spectrum by iteration; third, calculate and format bit-stream; fourth, output formatted bit-stream. At the decoder side: parse the formatted bit-stream, apply decoding and inverse quantization to the spectrum of each frame, reconstruct temporal audio data by frequency-to-time transform, and reconstruct the time-domain signals of each channel.
Owner:SHANGHAI JADE TECH
Method for matching in speedup regular expression based on finite automaton containing memorization determination
InactiveCN101201836AReduce development difficultyReduce time spentSpecial data processing applicationsMemory footprintPattern matching
The invention discloses a matching and accelerating method of a regular expression based on a deterministic finite automaton with memory, including a rule compiler of the regular expression and a pattern matching engine; the rule compiler of the regular expression firstly transforms the regular expression into an analytic tree, and then transforms the analytic tree into a nondeterministic finite automaton with memory and the deterministic finite automaton with memory respectively; the pattern matching engine can accelerate pattern matching by using the deterministic finite automaton with memory generated by the rule compiler. The invention has the advantages that: 1) by directly supporting repeat operators, the compiler does not need to unfold the repeat expression, thus the difficulty of the development of the compiler is greatly reduced and the memory occupation and the compile time of the compiler are decreased as well; 2) for the same reason, the volume of a rules database generated by the compiler can be reduced, so the cost and complexity of the pattern matching engine can be lowered.
Owner:ZHEJIANG UNIV
Physical Rendering With Textured Bounding Volume Primitive Mapping
InactiveUS20100238169A1Reduce overheadReduce memory usageImage data processing detailsSpecial data processing applicationsComputer graphics (images)Memory footprint
A circuit arrangement, program product and circuit arrangement utilize a textured bounding volume to reduce the overhead associated with generating and using an Accelerated Data Structure (ADS) in connection with physical rendering. In particular, a subset of the primitives in a scene may be mapped to surfaces of a bounding volume to generate textures on such surfaces that can be used during physical rendering. By doing so, the primitives that are mapped to the bounding volume surfaces may be omitted from the ADS to reduce the processing overhead associated with both generating the ADS and using the ADS during physical rendering, and furthermore, in many instances the size of the ADS may be reduced, thus reducing the memory footprint of the ADS, and often improving cache hit rates and reducing memory bandwidth.
Owner:IBM CORP
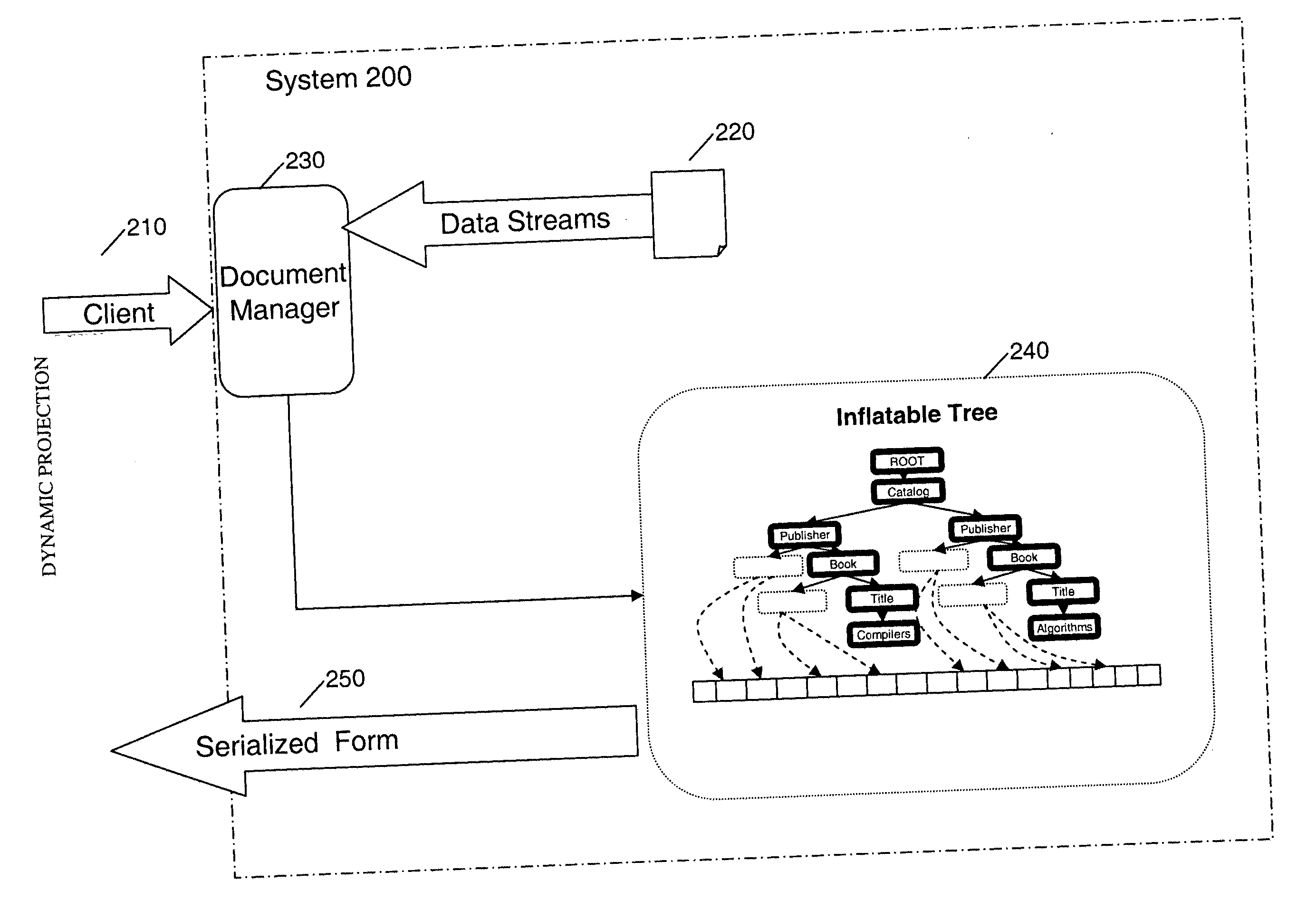
Method and apparatus for lazy construction of XML documents
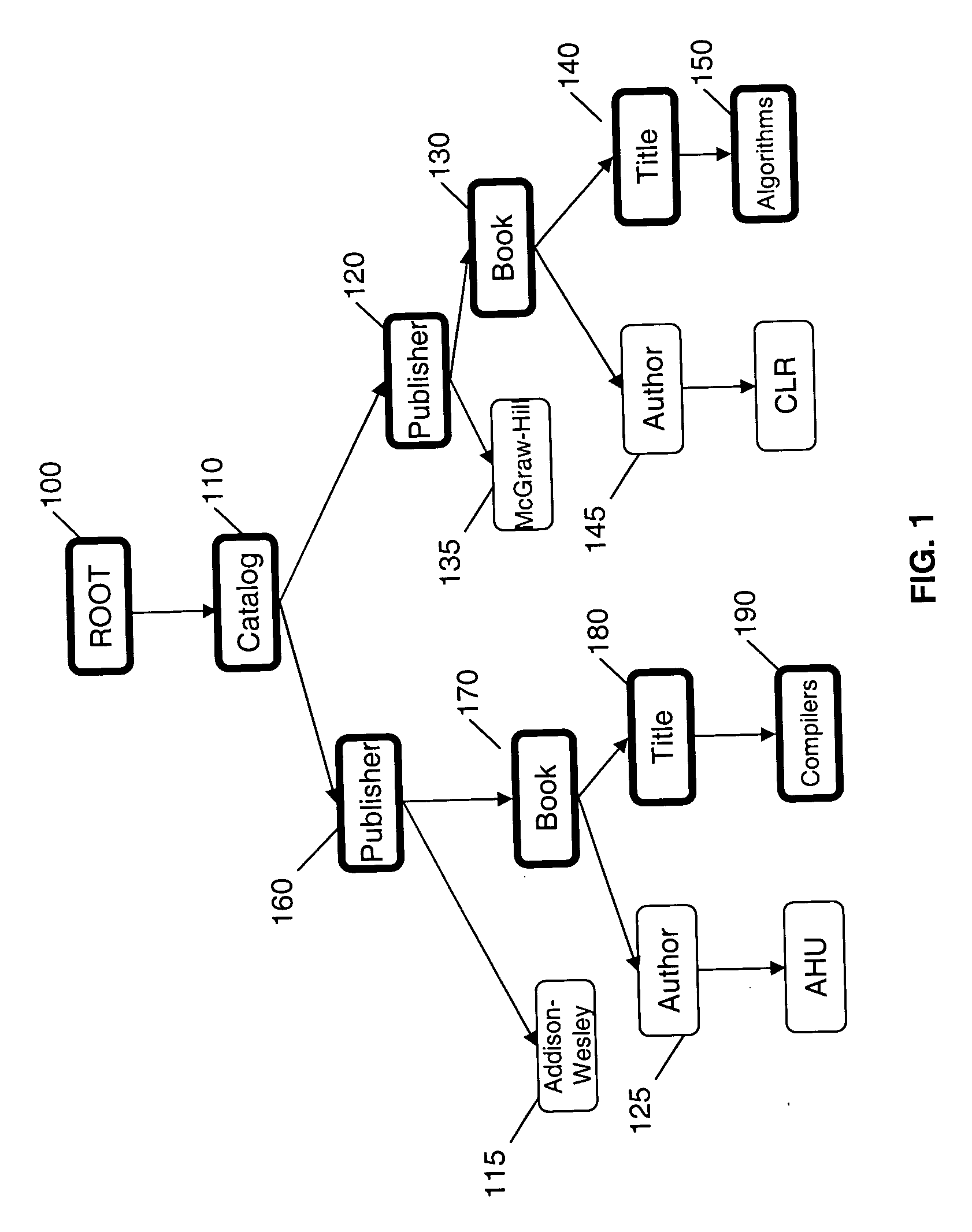
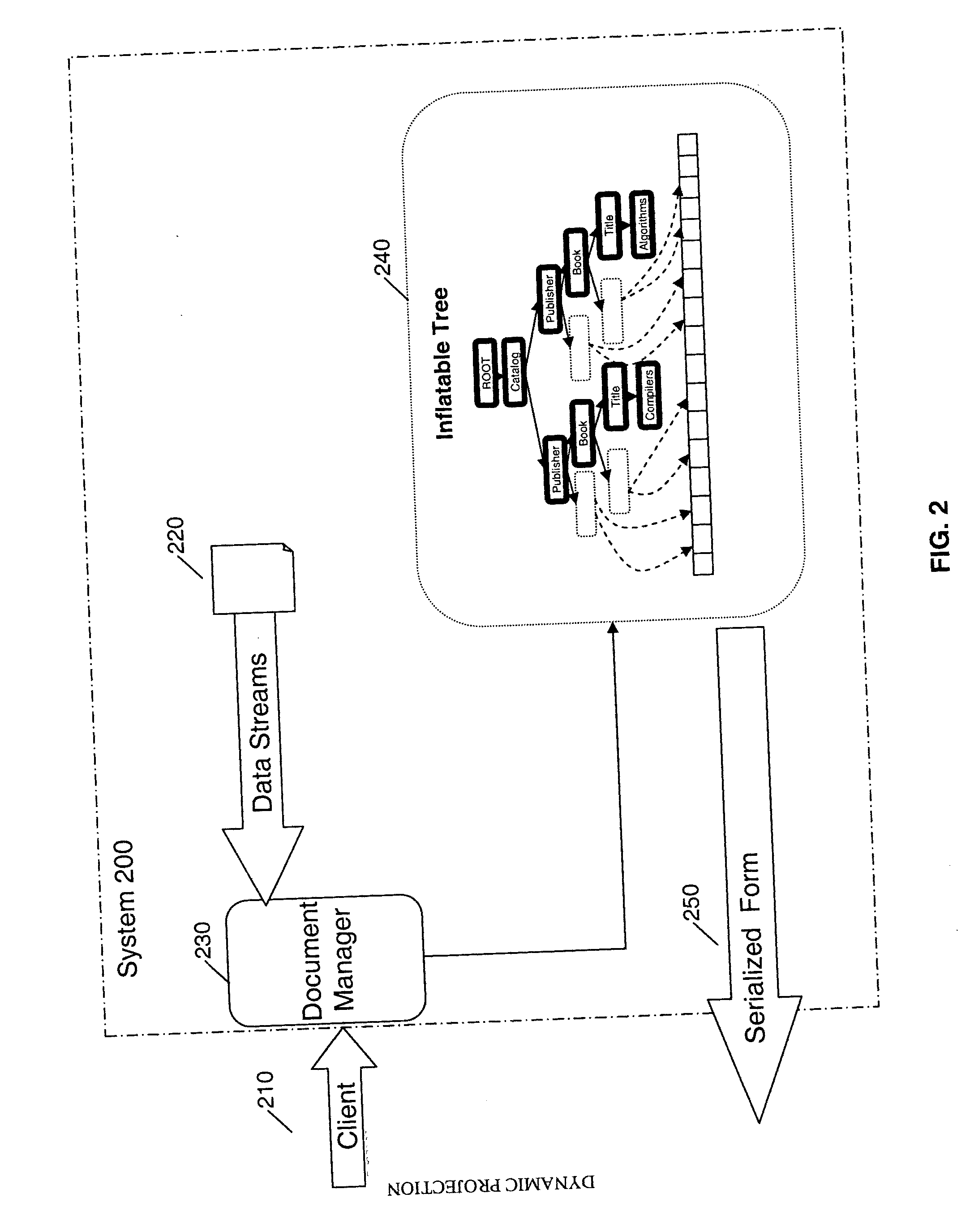
InactiveUS20070005622A1Digital data processing detailsNatural language data processingInformation processingMemory footprint
A method, information processing system, and computer readable medium for improved representation of hierarchical documents, particularly a document encoded in Extended Markup Language (XML). The method loads a hierarchical document and stores into an addressable data structure such as a byte array. It then expands the addressable data structure lazily in response to navigations requested by a client. Nodes requested by the client are materialized, that is, they are created in memory, whereas other nodes are left unmaterialized in byte form. The method reduces the memory footprint of an XML document, as well as, improves query evaluation time and serialization time.
Owner:IBM CORP
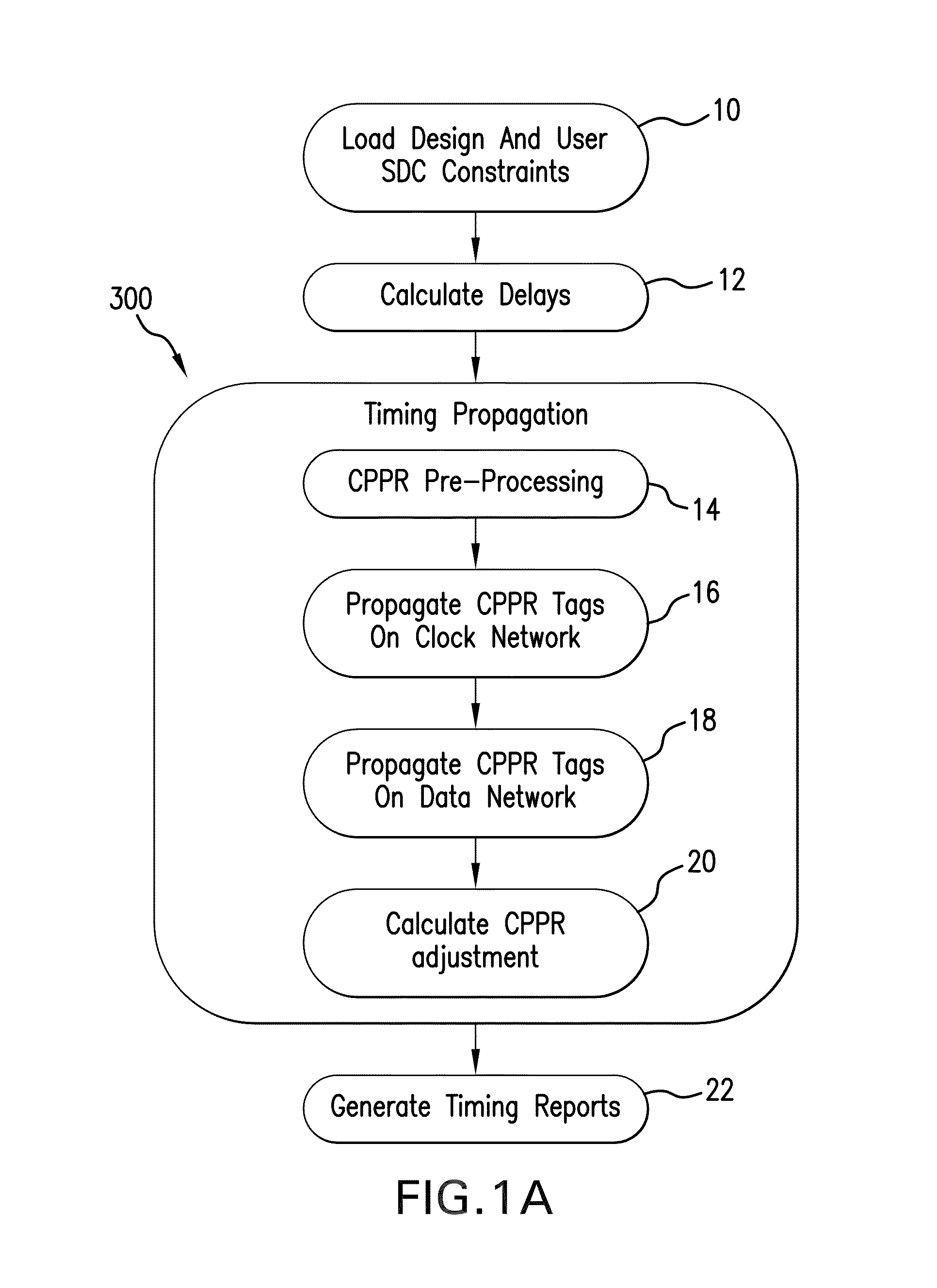
System and method for common path pessimism reduction in timing analysis to guide remedial transformations of a circuit design
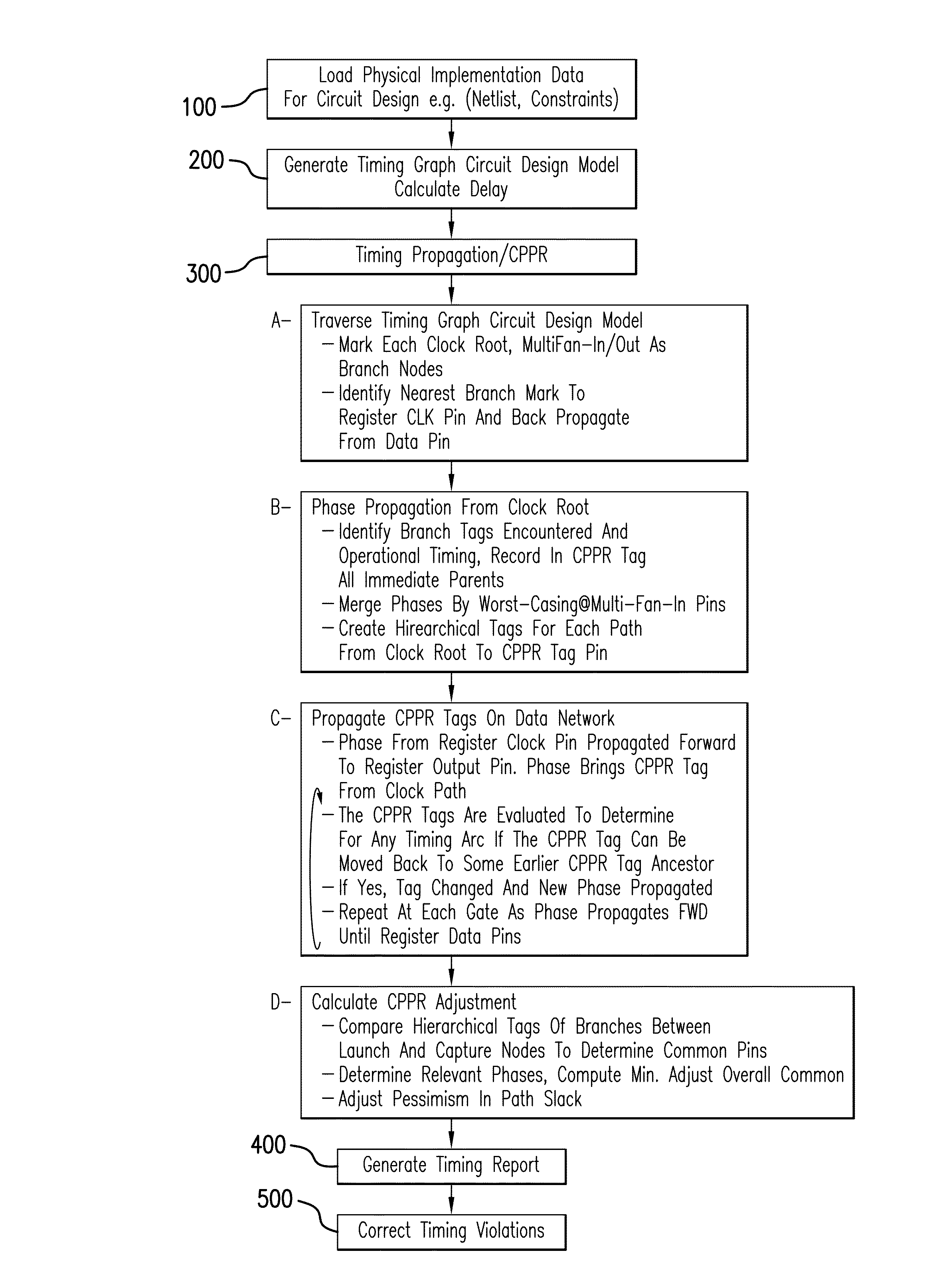
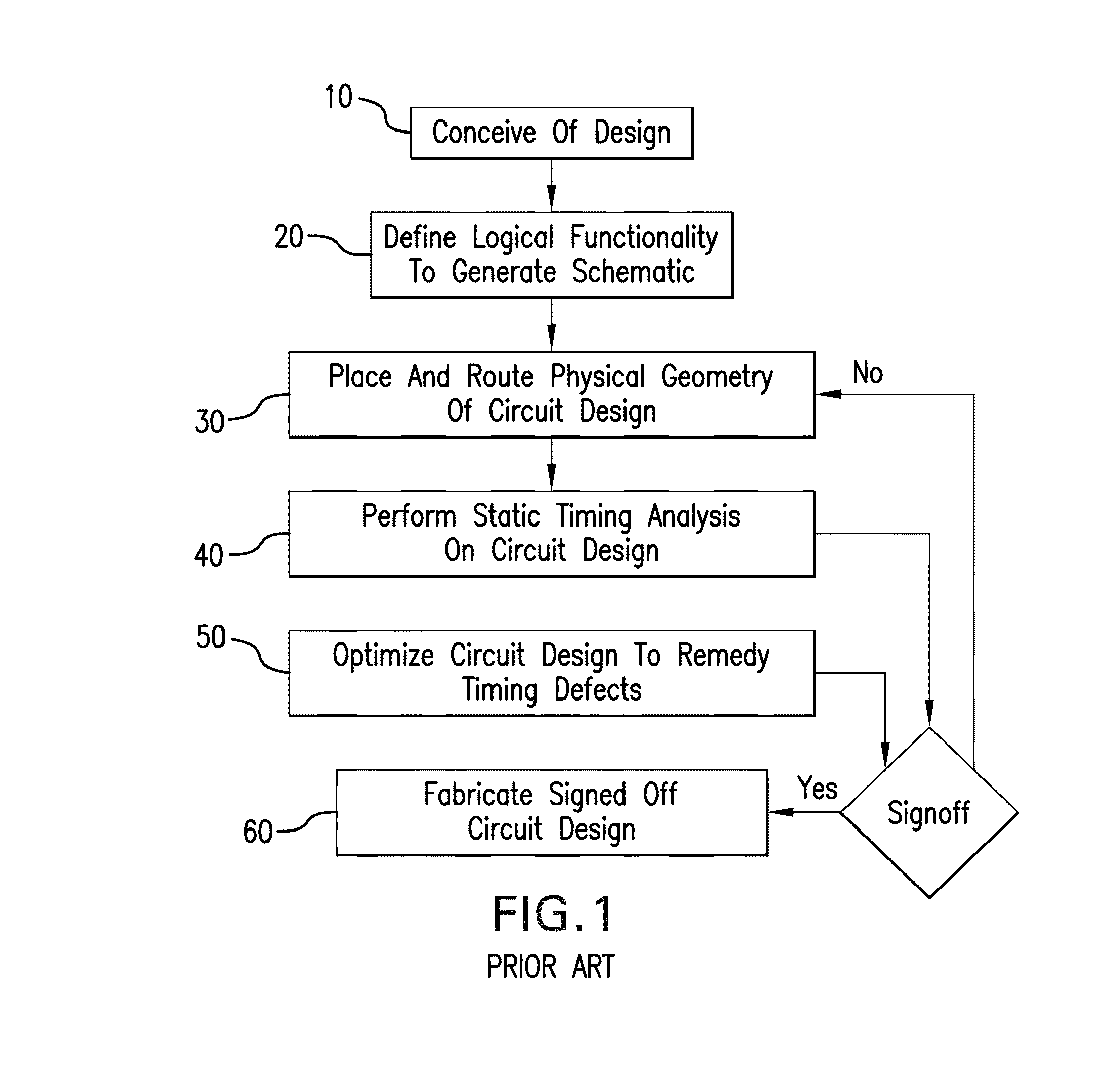
ActiveUS8745561B1Reduce unnecessaryGood correlationDetecting faulty computer hardwareCAD circuit designSystems designMemory footprint
A system and method are provided for common path pessimism removal or reduction (CPPR) in a timing database provided to guide transformative physical optimization / correction of a circuit design for an IC product to remedy operational timing violations detected in the circuit design. Pessimism is reduced through generation of a common path pessimism removal (CPPR) tree structure of branching nodes, and operational timing characteristics of each node. The CPPR tree structure is used to avoid exponential phases propagating in an exploratory manner through the system design, as well as the resultant memory footprint thereof. Additionally, back-tracing node-by-node through the circuit design for each and every launch and capture flip flop pair end point through each possible path thereof is avoided.
Owner:CADENCE DESIGN SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com