Timestamp technique-based industrial network security transmission method
A technology of network security and transmission method, which is applied in the field of industrial data network security transmission based on time stamp technology, and the field of industrial data security transmission. Good, low hardware requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
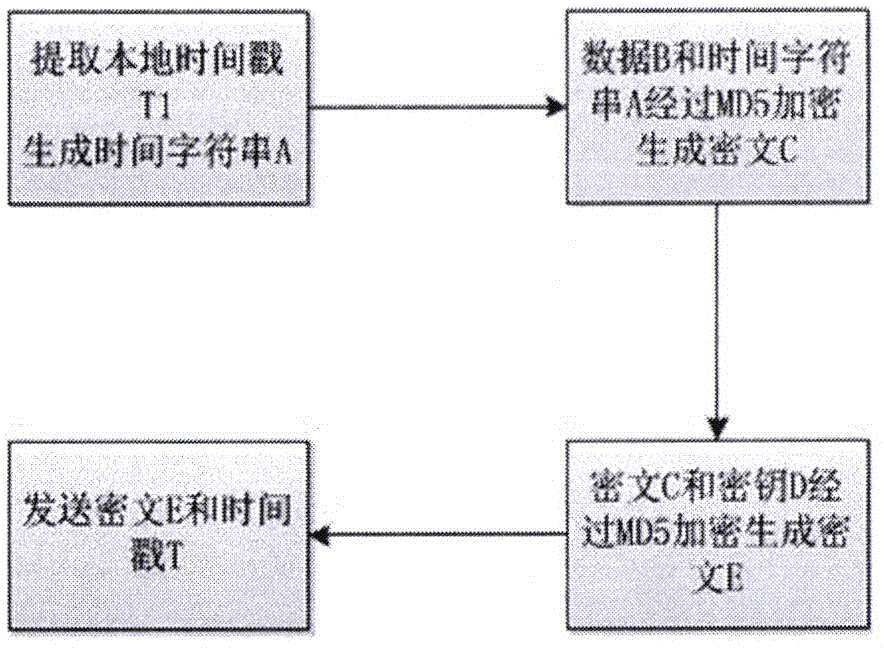
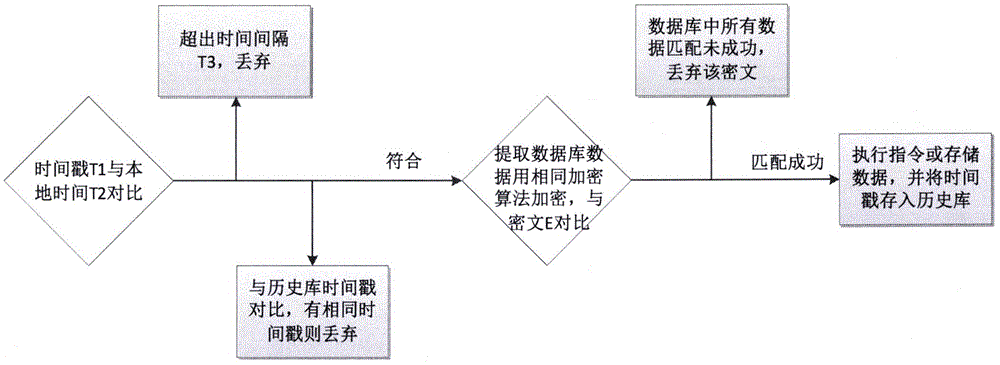
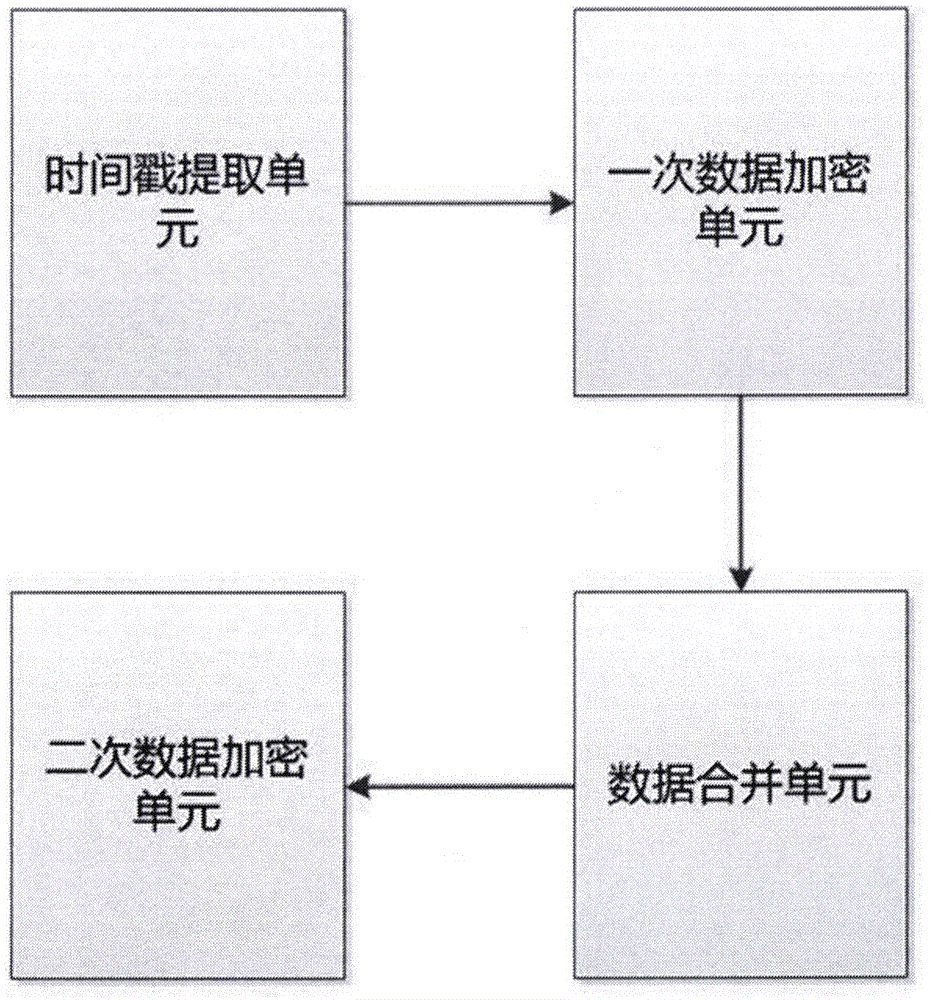
[0037] The present invention mainly relates to a method for sending data at the sending end and receiving data at the receiving end, and the data sending and receiving process is closely related to the local time. Therefore, as a prerequisite for the implementation of the present invention, the time of the sending end and the receiving end are required to be synchronized. The current relevant time There are many types of synchronization devices, which can be realized by adopting a suitable time synchronization scheme according to the actual application environment. In addition, in order to facilitate the transplantation of the method of the present invention, a list of data instruction libraries is preset at the receiving end to store all the data that may be sent by the sending end; in order to improve the efficiency of judging whether it is repeated data, a history is maintained for each sending end The library is used to store the time stamp of the data sent by the sender re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com