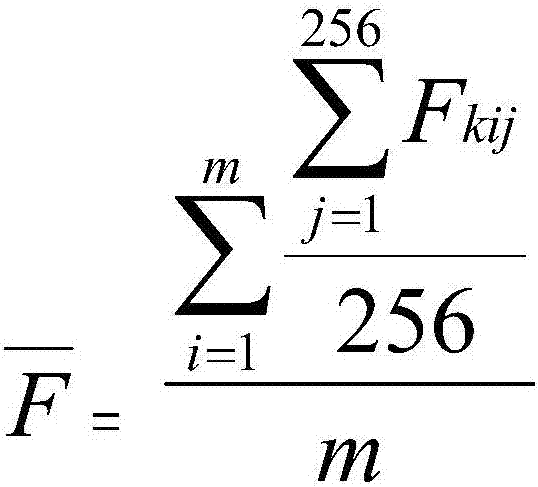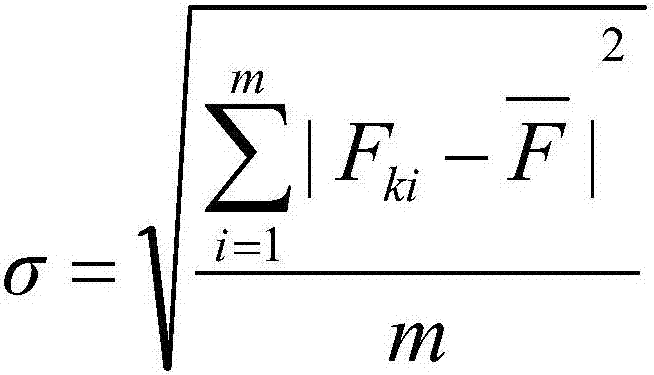Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
98 results about "Industrial security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Intelligent industrial security cloud gateway equipment system and method
InactiveCN107040459AUser identity/authority verificationNetwork connectionsData centerSecurity authentication
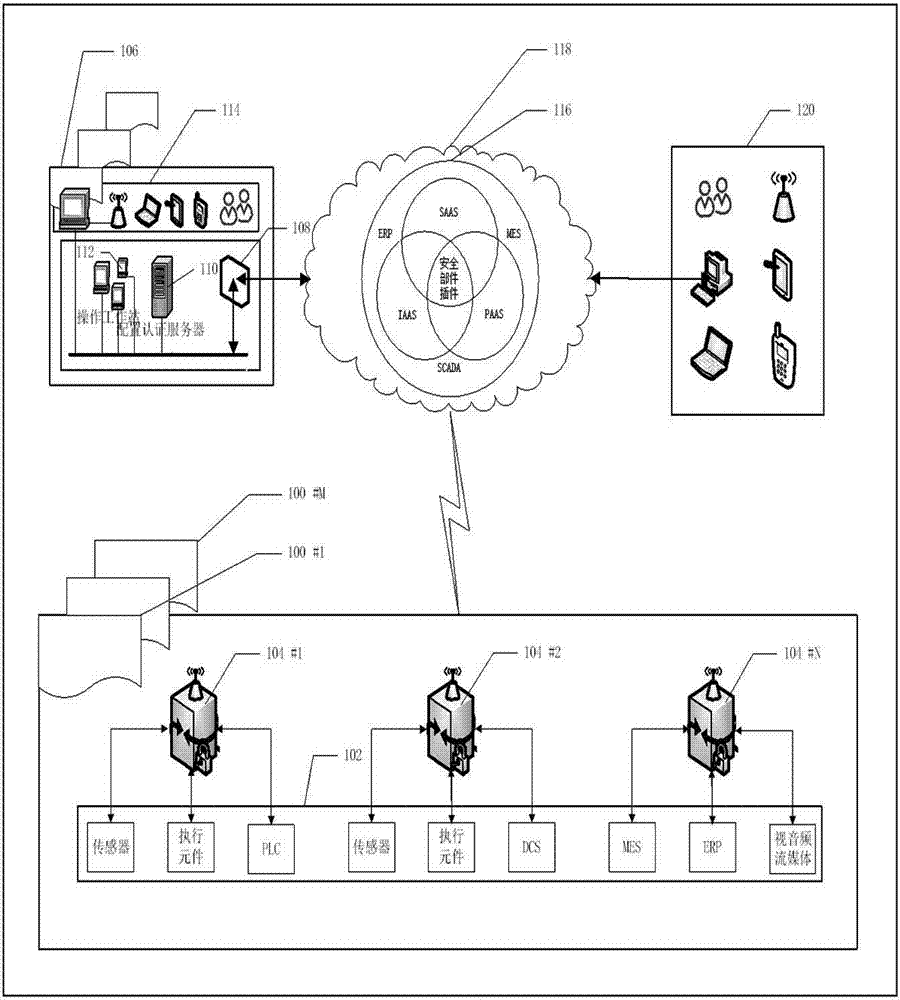
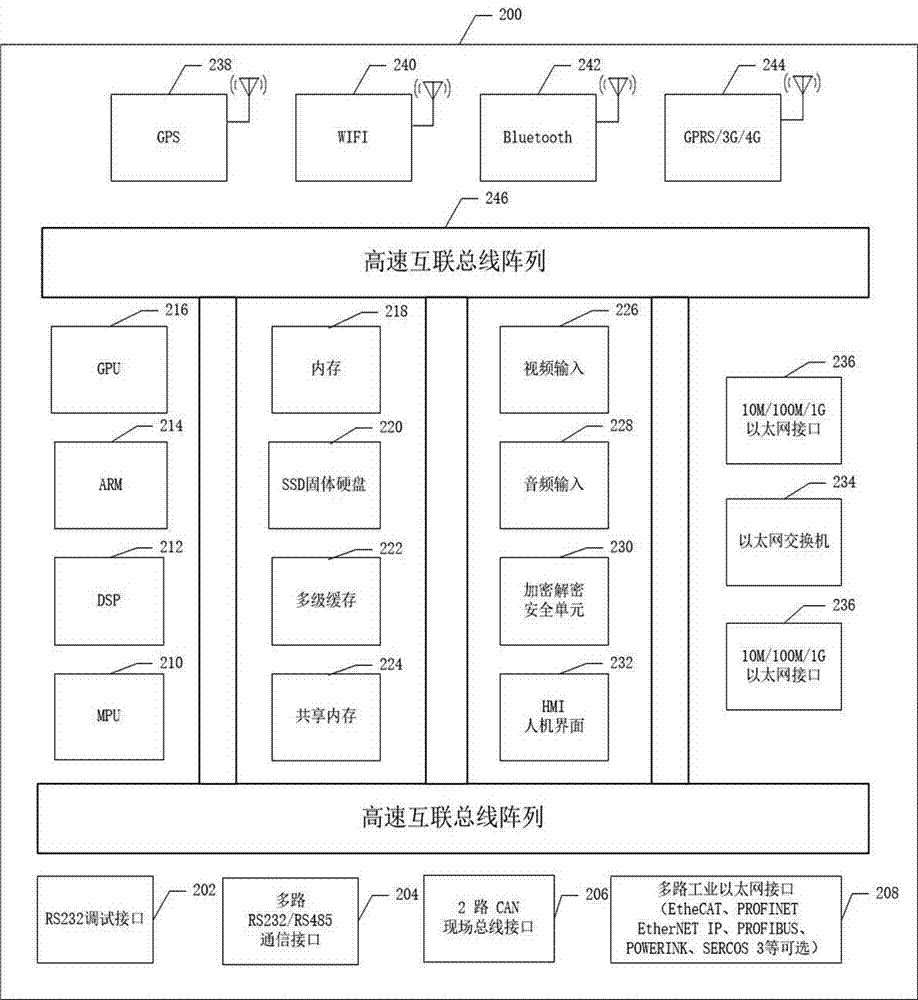
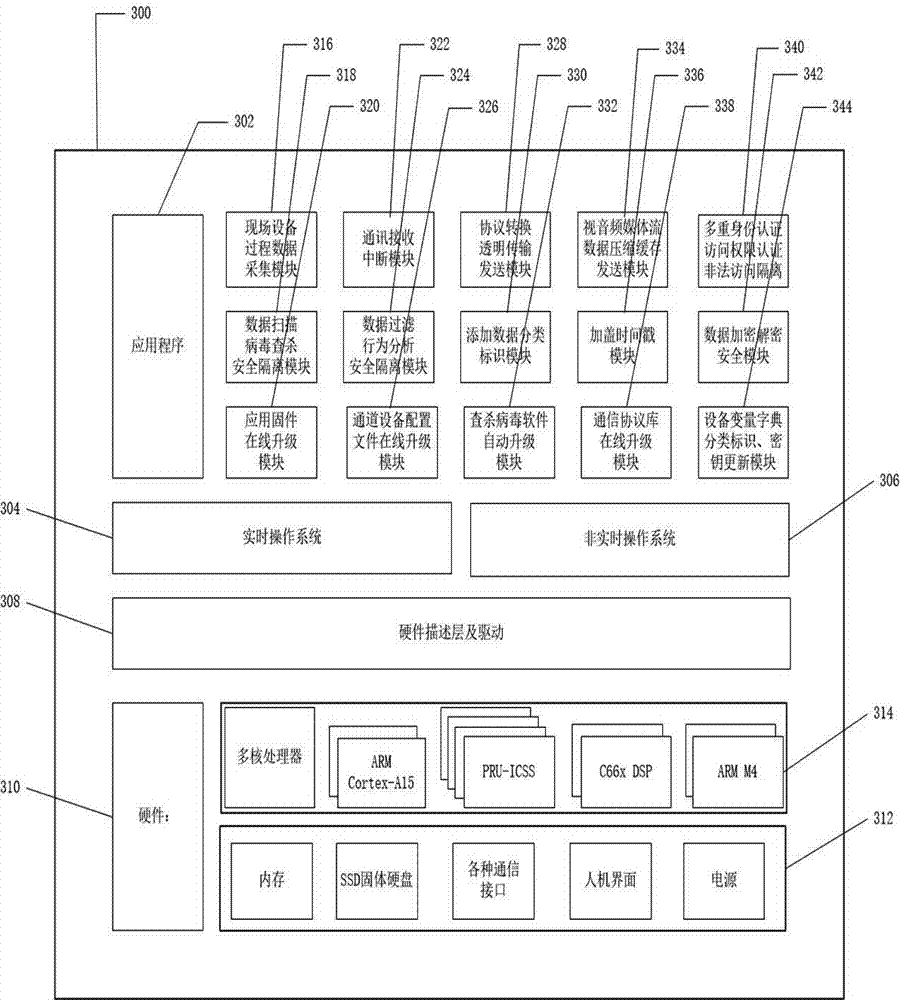
The invention discloses an intelligent industrial security cloud gateway equipment system and method. The industrial cloud security gateway equipment and method is characterized in that upper cloud data is encrypted and added with data classification identifiers and time stamps, and decryption, security scanning and multiple security authentication access control are carried out on data on downlink intelligent equipment, so that interconnection, protocol conversion, and multi-directional transparent and real-time transmission among cloud equipment, enterprise datacenter equipment and various intelligent equipment on an industrial field can be achieved. An intelligent industrial cloud security gateway is embedded intelligent equipment comprising various serial ports, communication interfaces for a field bus and field intelligent equipment such as the industrial Ethernet, communication interfaces for wireless mobile communication and wired Internet cloud equipment, wireless or wired local area network interfaces for Bluetooth, broadband and the like, an Ethernet switch, a GPS module, and embedded software. The intelligent industrial cloud security gateway can systematically prevent user data leakage and network virus attacks, is core equipment of a secure and reliable intelligent industrial cloud service system, and can serve intelligent industrial manufacturing.
Owner:高岩
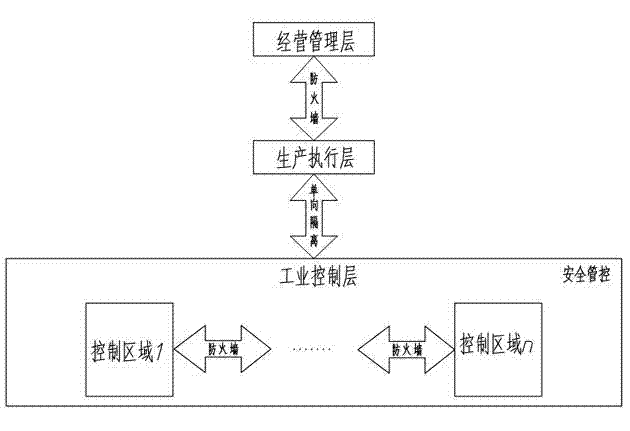
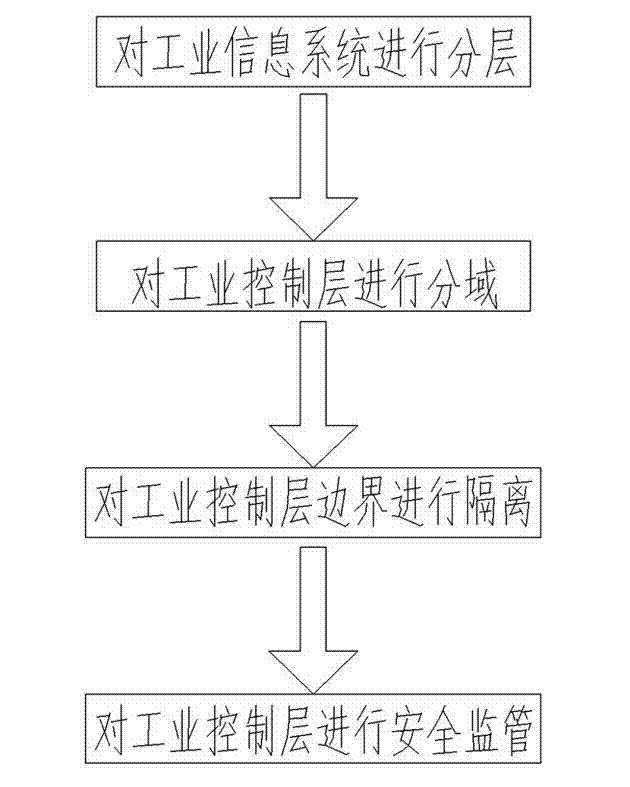
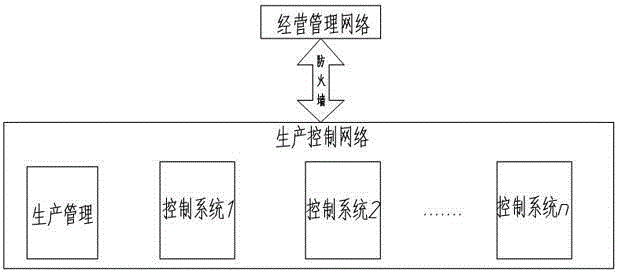
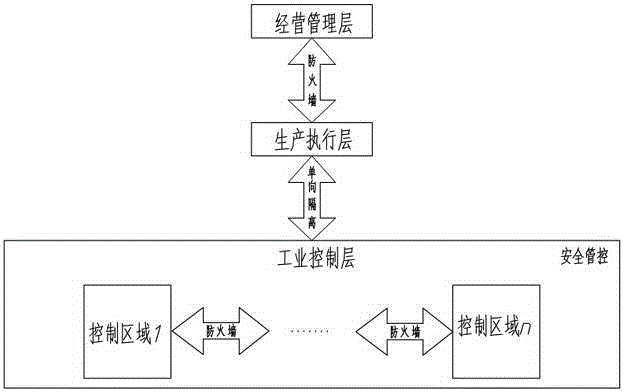
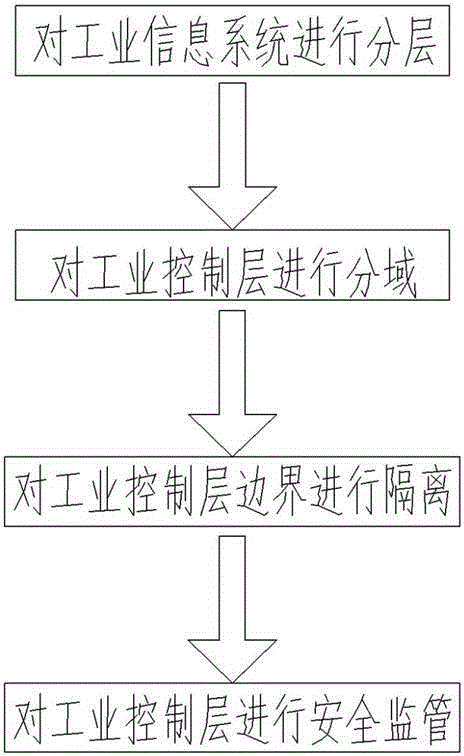
Industrial controlling network safety protecting method
ActiveCN103036886AGuaranteed real-time diagnosisReduce severityTransmissionIndustrial securityControl system
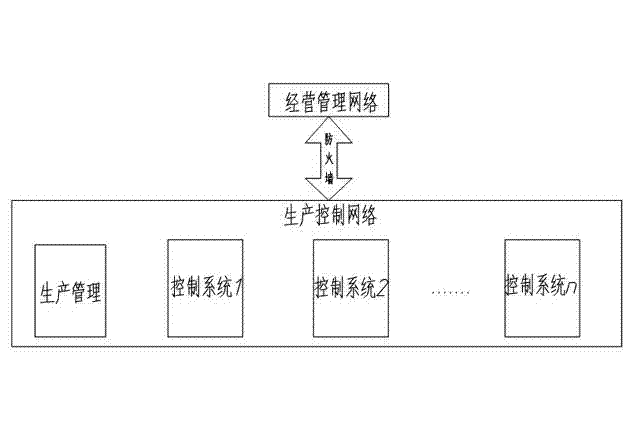
The invention discloses an industrial controlling network safety protecting method. The industrial controlling network safety protecting method is capable of improving industrial controlling network safety, convenient to communicate, capable of preventing external attack and invasion, and effectively protecting industrial controlling system and safety of industrial equipment. The industrial controlling network safety protecting method comprises the steps as below: processing an information system of an industrial enterprise in hierarchy; adopting safety protecting strategy procedures for data exchanging of the industrial controlling hierarchies; dividing the industrial controlling hierarchies into a plurality of automated unit regions and using a firewall for region separation; blocking potential communication ways of a production executive hierarchy to the industrial controlling hierarchy; adopting an industrial safety management platform module to build the center of configuration, management, analysis, warning and auditing of the industrial controlling hierarchy. The industrial controlling network safety protecting method is applied to the field of industrial controlling network.
Owner:珠海市鸿瑞信息技术股份有限公司
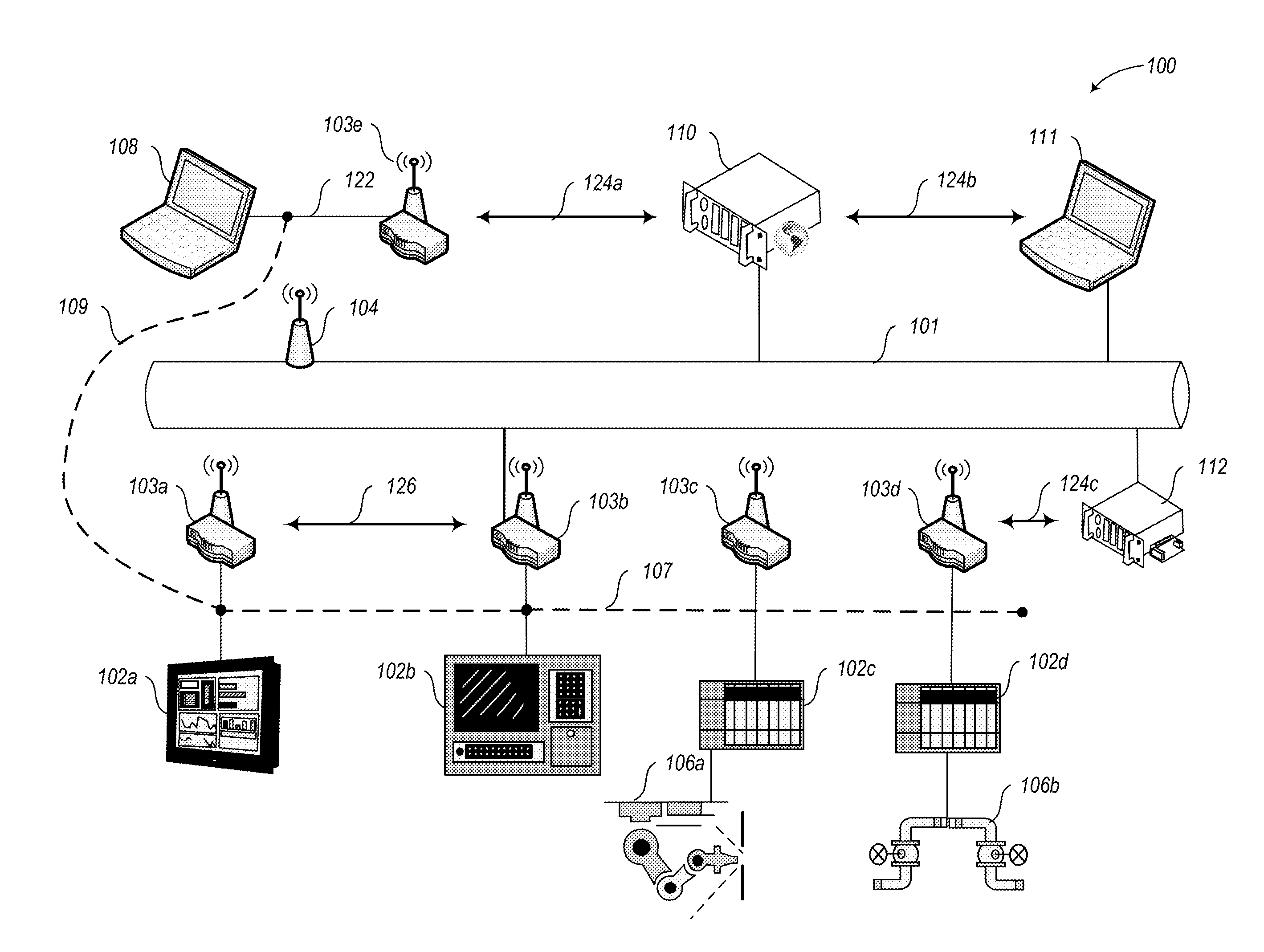
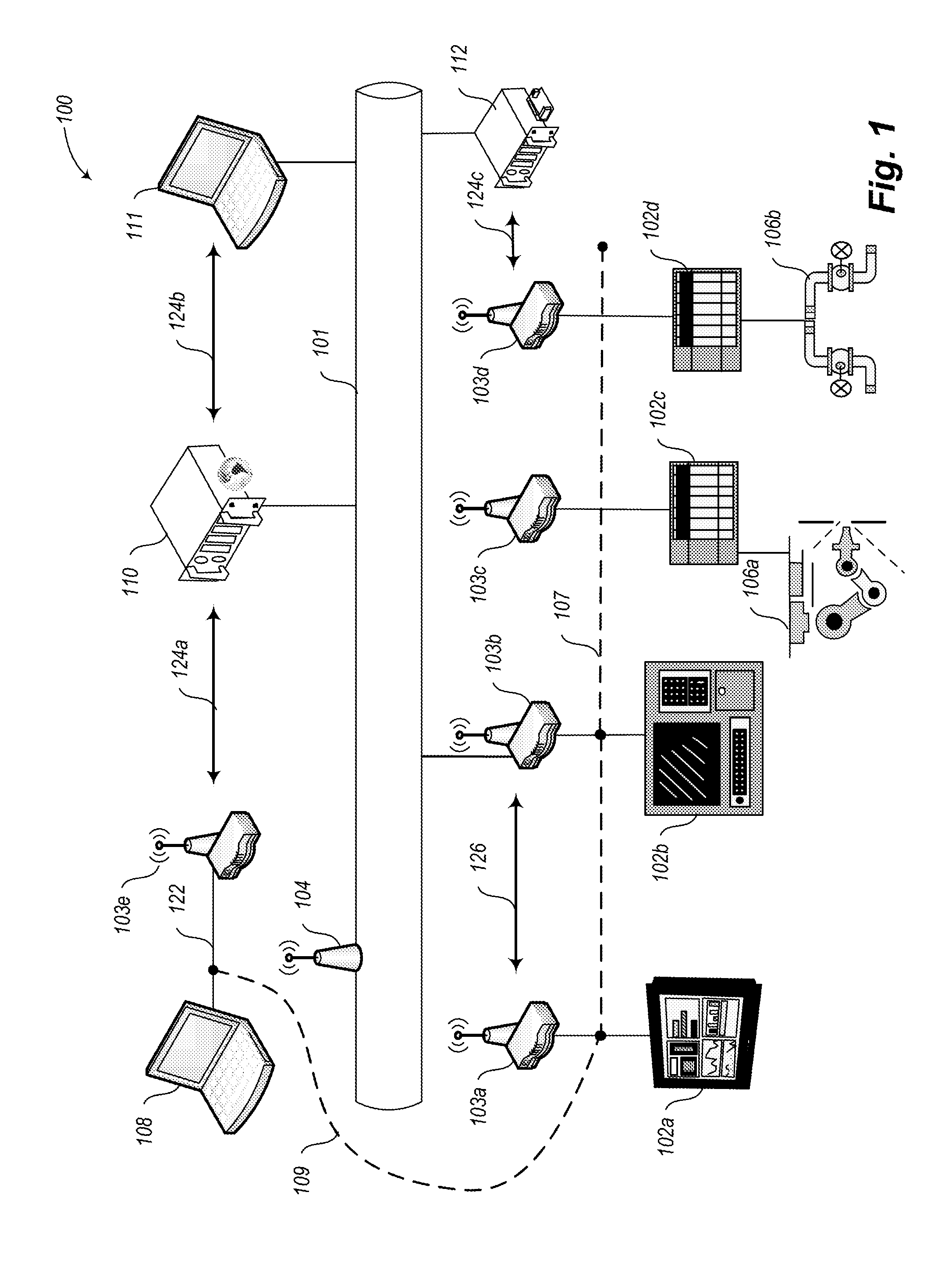
Industrial network security
ActiveUS20140282850A1Facilitate communicationImprove network securityTransmissionSpecial data processing applicationsIndustrial safety systemNetwork link
A private overlay network is introduced into an existing core network infrastructure to control information flow between private secure environments. Such a scheme can be used to connect a factory automation network linking operations devices to a corporate network linking various business units, with enhanced network security. Such a connection can be facilitated by introducing into the existing infrastructure a set of industrial security appliances (ISAs) that work together to create an encrypted tunnel between the two networks. The set of ISAs can be scalable to overlay differently sized core networks, to create the private overlay network. Connections to the private overlay network can be managed by the ISAs in a distributed fashion, implementing a peer-to-peer dynamic mesh policy. The industrial security system disclosed may be particularly advantageous in environments such as public utility systems, medical facilities, and energy delivery systems.
Owner:TEMPERED NETWORKS
Industrial security isolation gateway
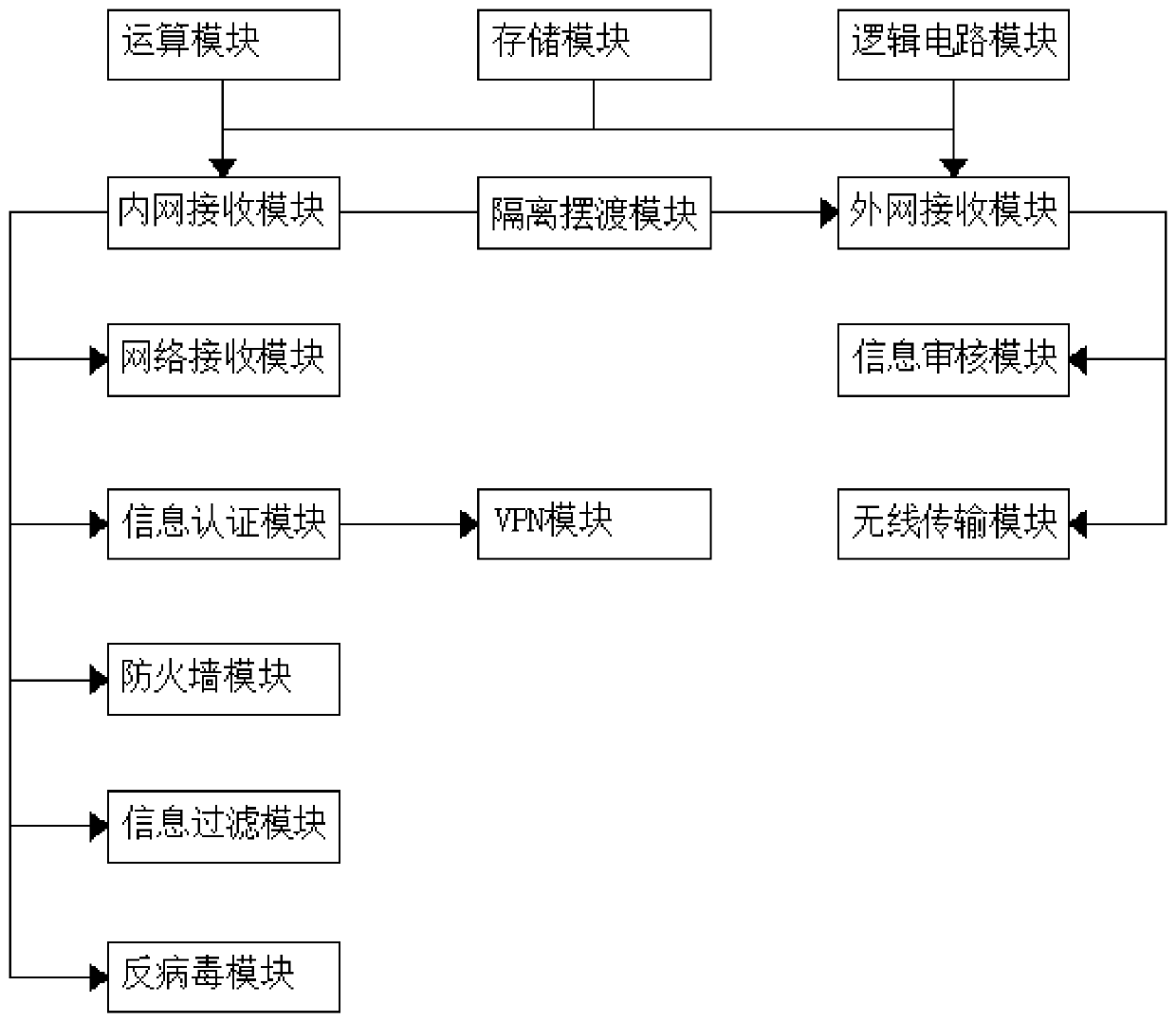
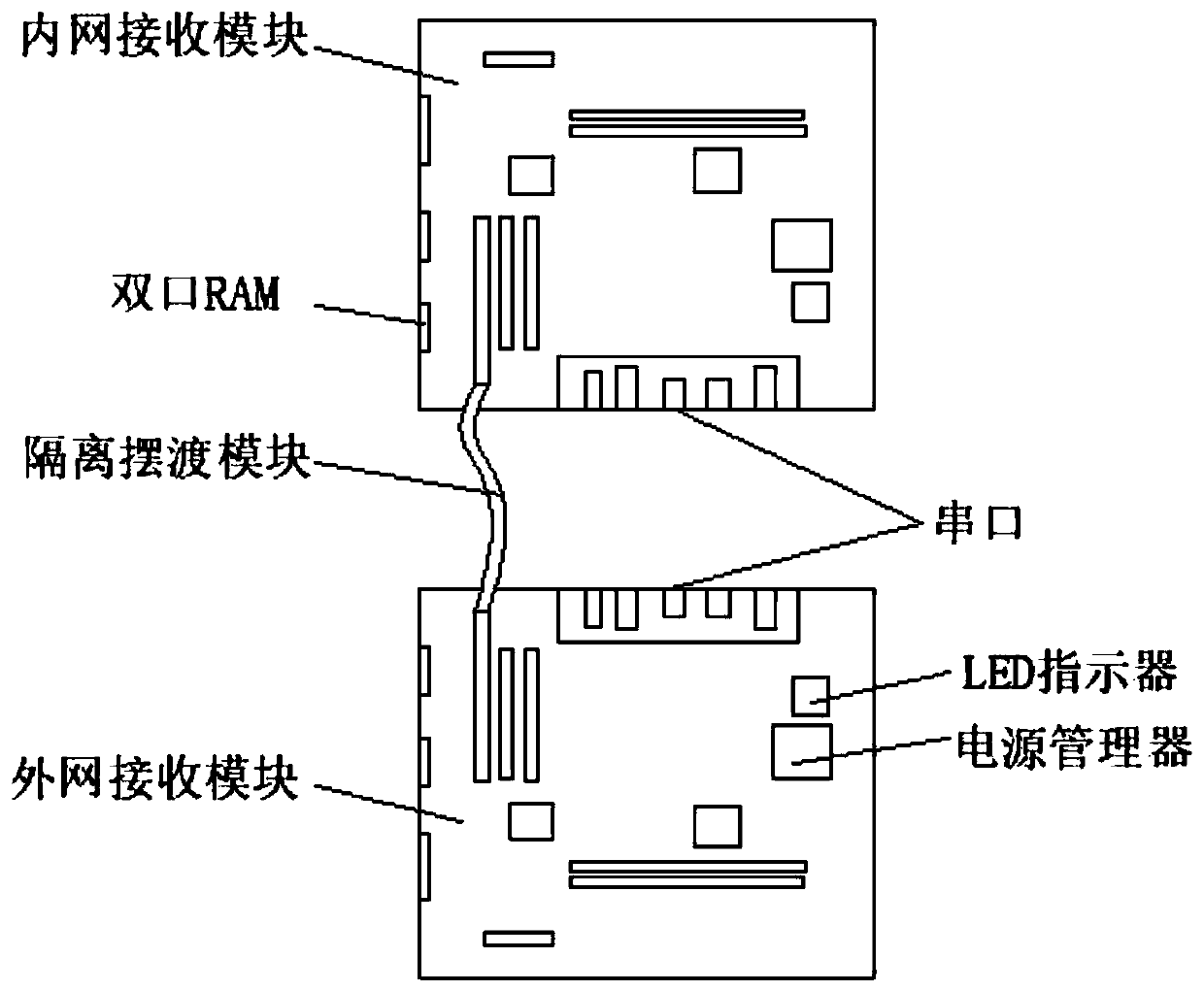
InactiveCN110943913ASafe and stable operationImprove reliabilityNetwork connectionsAnti virusInformation networks
The invention discloses an industrial security isolation gateway. The gateway comprises an external network receiving module, an internal network receiving module and an isolation ferry module. The external network receiving module and the internal network receiving module are two independent control systems. Each of the modules comprises an operation module, a storage module and a logic circuit module. Data transmission is carried out between the external network receiving module and the internal network receiving module through the isolation ferry module. The transmission process comprises protocol stripping, verification, encryption, decryption and storage processes, and the external network receiving module comprises a network receiving module, an information authentication module, a firewall module, an information filtering module and an anti-virus module. According to the invention, data security isolation between an industrial network and an information network can be realized,the reliability is improved by combining physical isolation and logic isolation, the functions of data encryption, virus prevention, network firewall, user authentication, intrusion prevention and thelike are supported, and the safe and stable operation of an industrial control system can be ensured.
Owner:广东互动电子有限公司
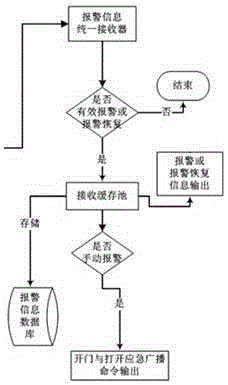
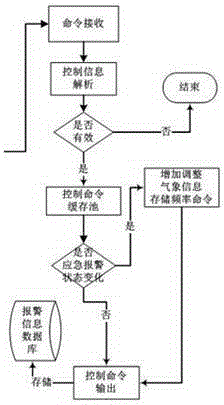
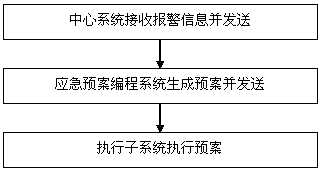
Industrial safety emergency command integrated system-based emergency plan control method
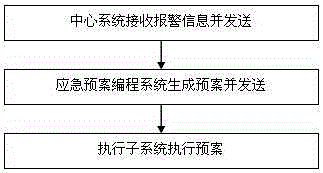
ActiveCN105159255AIncrease the data cache poolGuaranteed reception processing capacityAlarmsProgramme total factory controlIntegrated systemsEngineering
The invention discloses an industrial safety emergency command integrated system-based emergency plan control method. The method includes the following steps that: S1, a center system receives alarm information of an alarm subsystem, analyzes, stores and judges the alarm information, and forwards the alarm information to an emergency plan programming system; S2, the emergency plan programming system sends control commands to the center system, and the center system receives the information, and analyzes and stores the information, and then transmits the control commands to an execution subsystem through the center system; and S3, the execution subsystem executes a plan according to the received control commands. According to the control method of the invention, a plurality of systems are correlated, and therefore, a linkage effect can be realized, and video monitoring signals are controlled, and perimeter intrusion alarm signals are monitored in real time, and fire alarm signals are automatically received and are fed back to the center system in real time, and at the same time, different emergency plans can be started according to dangers.
Owner:CHENGDU GREATECH ELECTRICS
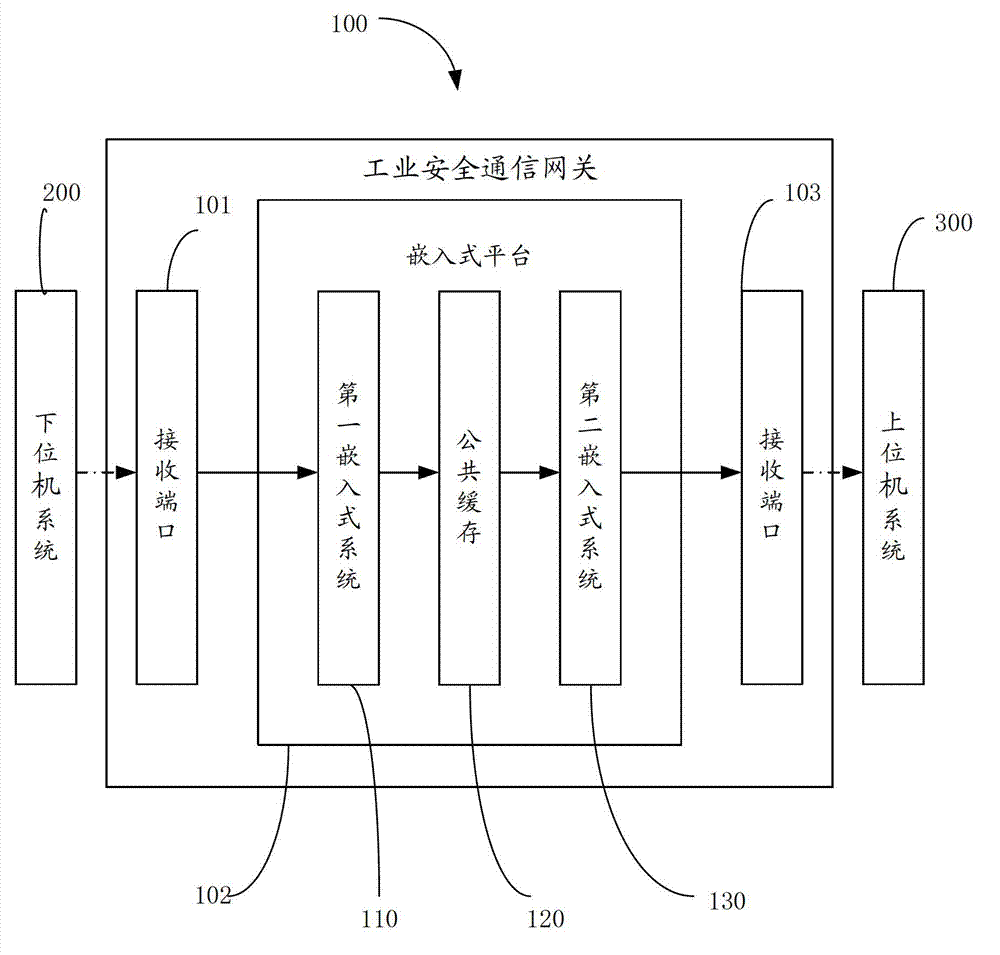
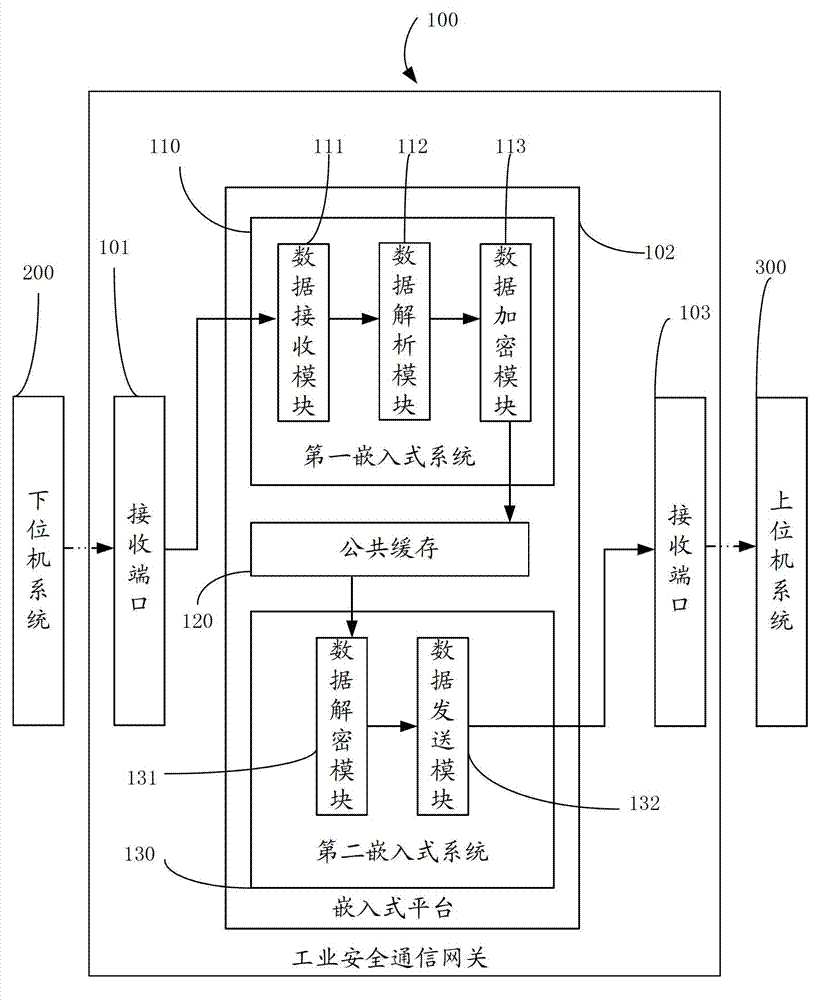
Industrial security communication gateway
The invention discloses an industrial security communication gateway, which comprises a data receiving port connected with a lower computer system, a data sending port connected with an upper computer system, and an embedded platform connected between the two ports. The industrial security communication gateway comprises two embedded systems and a public cache, wherein the two embedded systems have different functions; the first embedded system comprises a data receiving module, a data resolving module and a data encrypting module; and the second embedded system comprises a data decrypting module and a data sending module. By the industrial security communication gateway, the security of the industrial security communication gateway can be improved.
Owner:上海金自天正信息技术有限公司
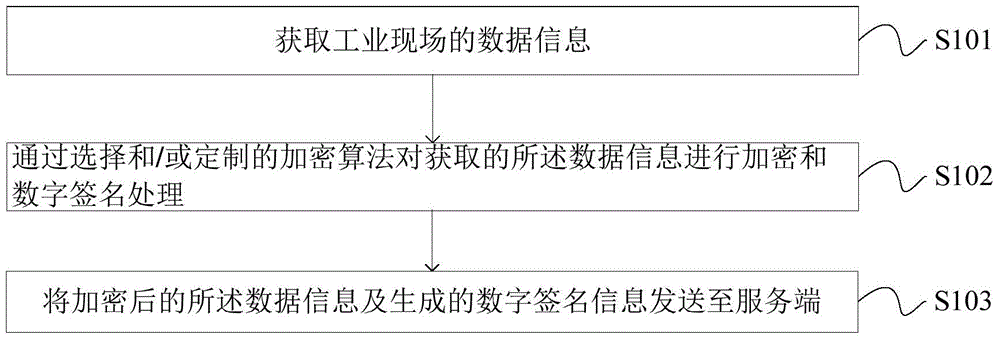
Communication method and device of industrial security gateway based on embedded system
ActiveCN104539573AImprove securityNo AccessUser identity/authority verificationIndustrial securityData information
The invention provides a communication method and device of an industrial security gateway based on an embedded system, and aims to enhance the security of data transmission in an industrial control network. The method comprises the following steps: acquiring data information of an industrial field; performing encryption and digital signature processing on the acquired data information through a selected and / or customized encryption algorithm; and transmitting the encrypted data information and generated digital signature information to a server side. The device comprises an acquisition unit for acquiring the data information of the industrial field, an encryption unit for performing encryption and digital signature processing on the acquired data information through the selected and / or customized encryption algorithm, and a first transmission unit for transmitting the encrypted data information and generated digital signature information to the server side. The communication method and device are suitable for the technical field of industrial automation information security.
Owner:UNIV OF SCI & TECH BEIJING
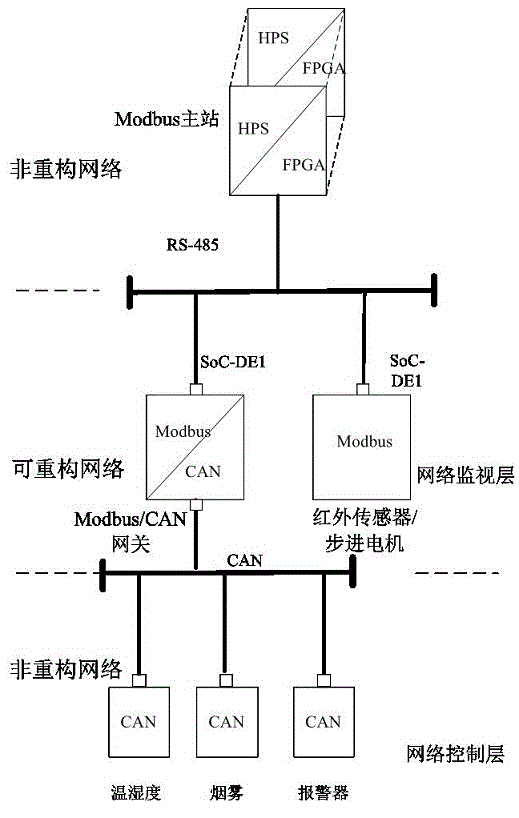
Network online reconfigurable industrial security monitoring system
InactiveCN104932472AThe measurement and control function is not affectedTotal factory controlProgramme total factory controlAutomatic controlNetwork communication
The invention discloses a network online reconfigurable industrial security monitoring system. The system includes a network monitoring man-machine interaction interface, a network monitoring unit and a network control unit; the network monitoring unit is composed of a Modbus monitoring master station which includes two monitoring master stations of different industrial control network types, and a Modbus slave station which includes two industrial control networks dynamically and partially-reconfigurable field apparatuses, wherein the monitoring master station can be put into operation in a switchable manner, and the field apparatuses are a gateway and a Modbus access control system control station respectively; the network monitoring unit is composed of a CAN control network; and the CAN control network includes three field control stations which are respectively used for monitoring field temperature and humidity, smoke concentration and warning. The network online reconfigurable industrial security monitoring system of the invention can automatically identify network types, plan reconfiguration plans, complete network communication dynamical local reconfiguration, and can automatically adapt to the change of different industrial control network types under the constraint that the continuous uninterrupted operation and the detection and control function of the whole system are not affected assuredly and control quality does not change; and the network online reconfigurable industrial security monitoring system has revolutionary significance in the industrial automatic control filed.
Owner:SOUTHWEST UNIVERSITY
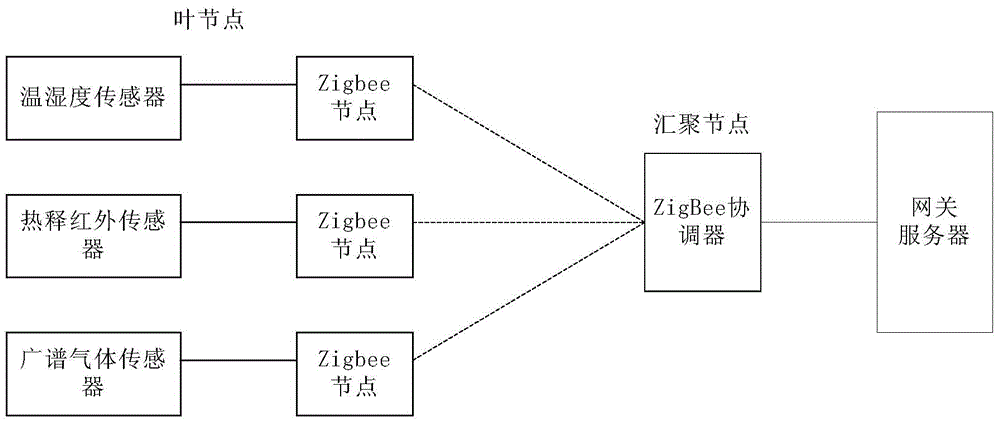
Zigbee-based multi-sensor Internet of Things monitoring method and equipment
ActiveCN104574898ATransmission performance will not be affected by overloadRealize remote monitoringTransmission systemsNetwork topologiesIndustrial securityMonitoring methods
The invention discloses a Zigbee-based multi-sensor Internet of Things monitoring method and equipment. The equipment is Zigbee communication network equipment which comprises leaf nodes and a convergence node, wherein the plurality of leaf nodes are connected with one convergence node; the leaf nodes comprise Zigbee nodes and sensors; the convergence node comprises a Zigbee coordinator; the Zigbee coordinator is connected with a gateway server; the Zigbee coordinator is used for detecting data of the identical and different types of sensors by using different coordination methods, and used for transmitting detected data to a background through a gateway. The method and the equipment are applicable to practical requirements of application scenes, and the stability of monitoring industrial security production monitoring data is improved.
Owner:WUHAN INSTITUTE OF TECHNOLOGY
Industrial safety control system and control method thereof
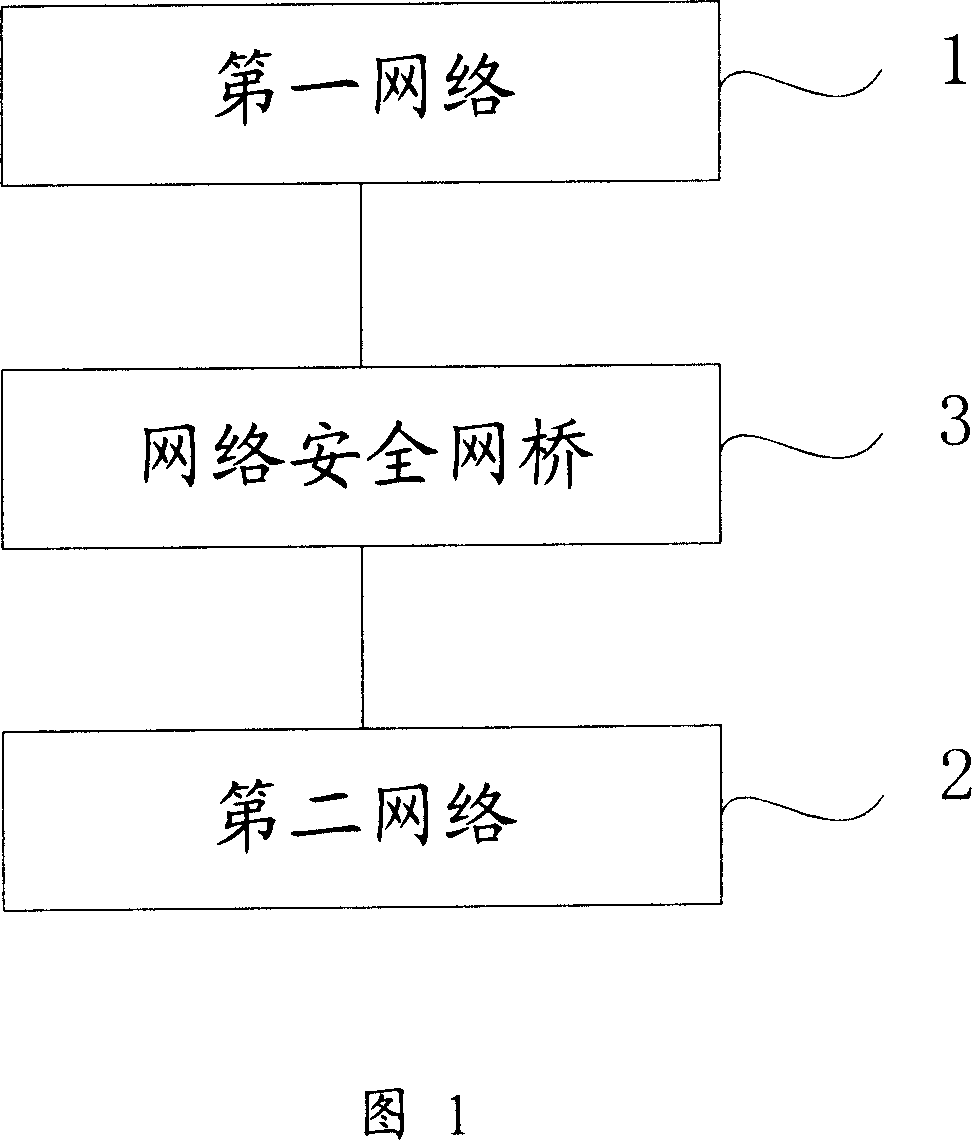
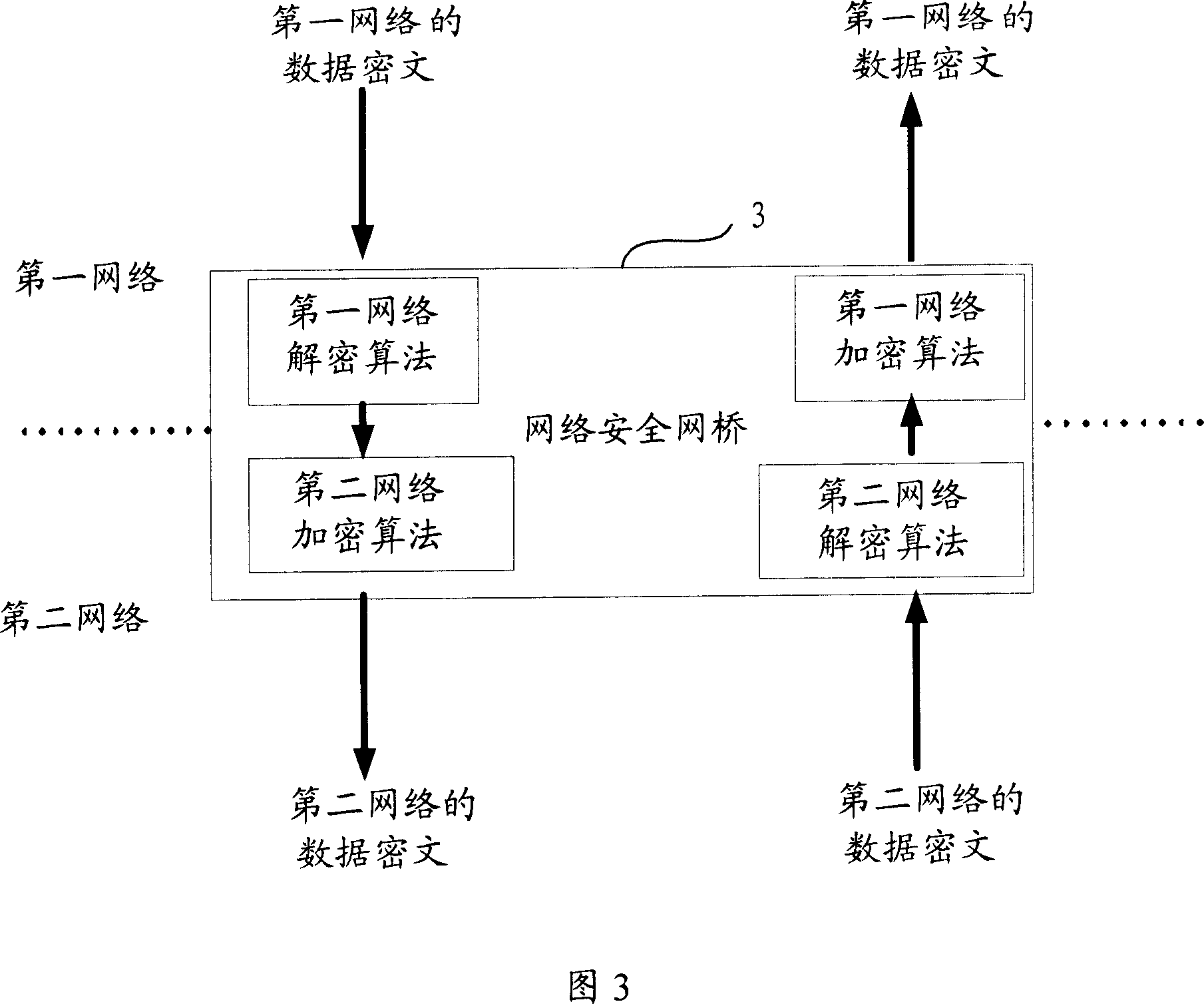
InactiveCN1929373AAvoid controlKey distribution for secure communicationCommunications securityIndustrial security
This invention discloses one industry safety control system, which comprises first and second networks and network safety bridge, wherein, the said network safety bridge is used to connect the said first and second networks to receive first network message as coded type to second network; receiving second network message to first network through set type.
Owner:SUPCON GRP +1
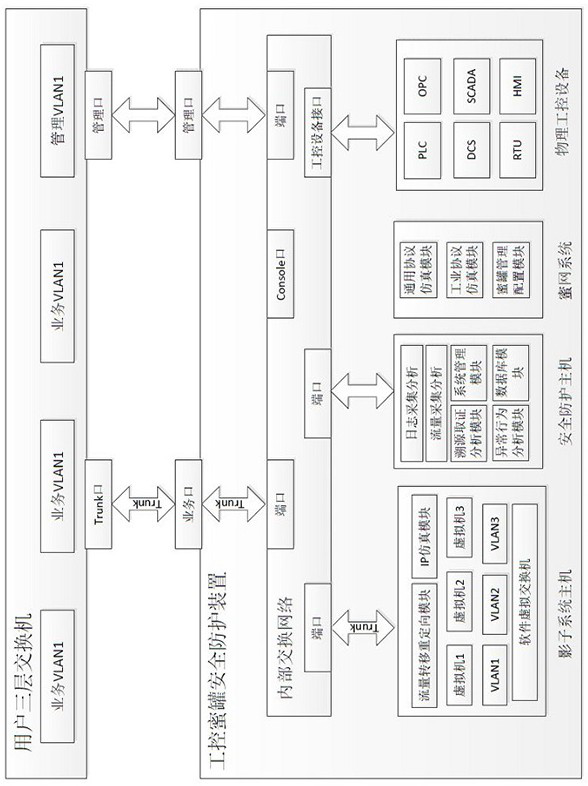
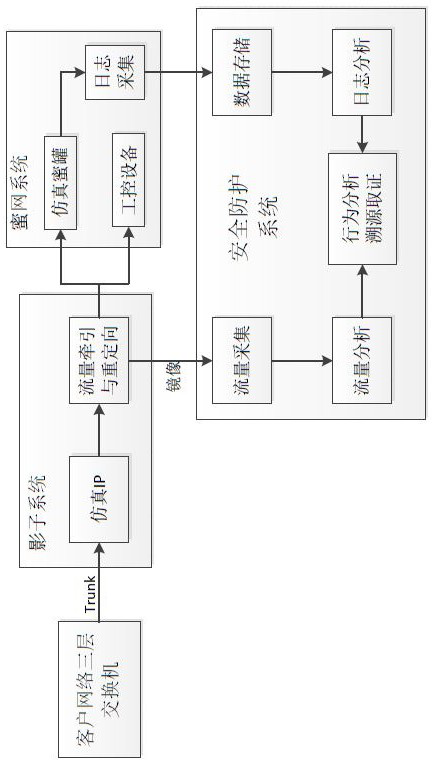
Industrial control honeypot safety protection device and method
ActiveCN112578761ADoes not change the physical network structureChange structureTotal factory controlProgramme total factory controlSystems managementEmbedded system
The invention relates to the technical field of industrial safety, in particular to an industrial control honeypot safety protection device and method. A shadow system comprises an IP simulation module, a flow transfer redirection module, virtual switch software and a plurality of virtual machine systems; a honeynet system comprises a general protocol simulation module, an industrial protocol simulation module and a honeypot management configuration module; an industrial control equipment interface provides access to a PLC module, a DSC module, an RTU module, an OPC service, SCADA equipment and HMI man-machine interaction system industrial control equipment; and a safety protection system comprises a log acquisition and analysis module, a flow acquisition and analysis module, an abnormal behavior analysis module, a traceability evidence obtaining analysis module, a system management module and a system database module. The beneficial effects are that the device does not need to connecta network in series, does not need to configure a port flow mirror image in a bypass manner, does not change the physical network structure of a user, does not affect the network operation environment of the user, achieves the flexible deployment of the environment, and achieves plug-and-play.
Owner:山东云天安全技术有限公司
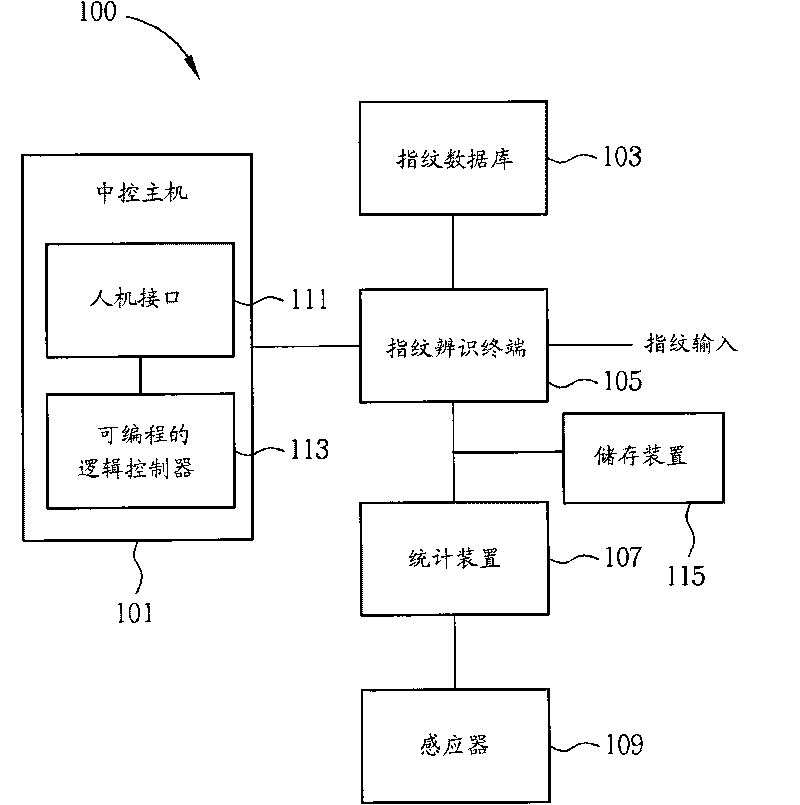
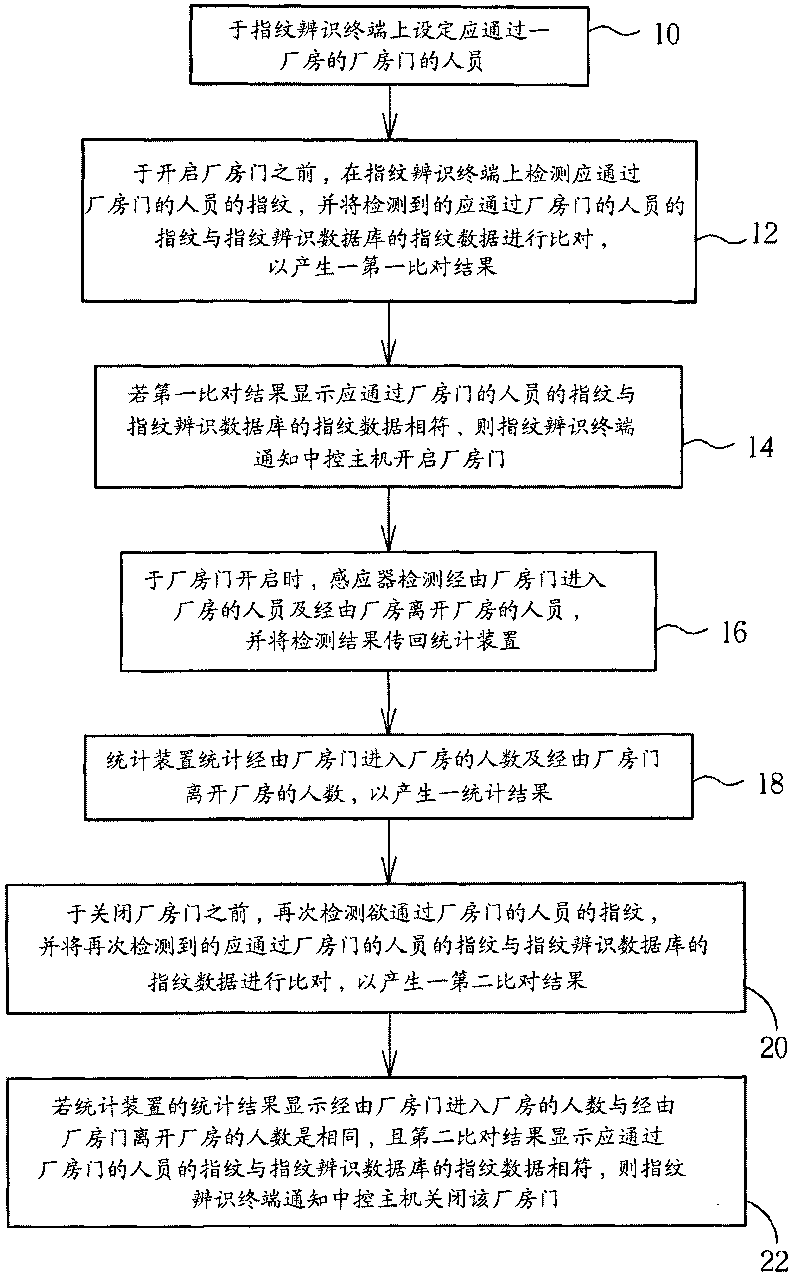
Method for managing and controlling industry safety and related access control system
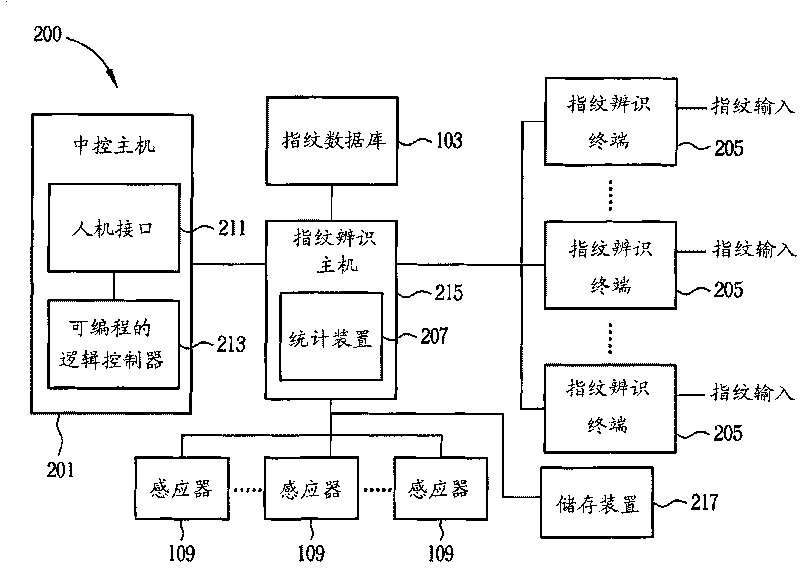
When a factory building is installed with a factory door, staffs going in / out the factory door are detected by using a group of sensors and biological characteristics of the staffs going in / out the factory door are identified by a biological identification terminal, thereby effectively and assuredly executing the management and control of the industry safety. When the factory building is installed with plurality of factory doors, a plurality of staffs going in / out the factory door are detected by using a plurality of groups of sensors; the detected results are transmitted to a biologic identification host, and biological characteristics of the staffs going in / out the factory door are identified through a plurality of biological identification terminals; the identified results are transmitted to the biological identification host capable of effectively and assuredly executing the management and control of the industry safety according to the transmitted identified results and the detection results of the plurality of groups of sensors.
Owner:SUNVISION TECH
Inspection method for early warning system of industrial security
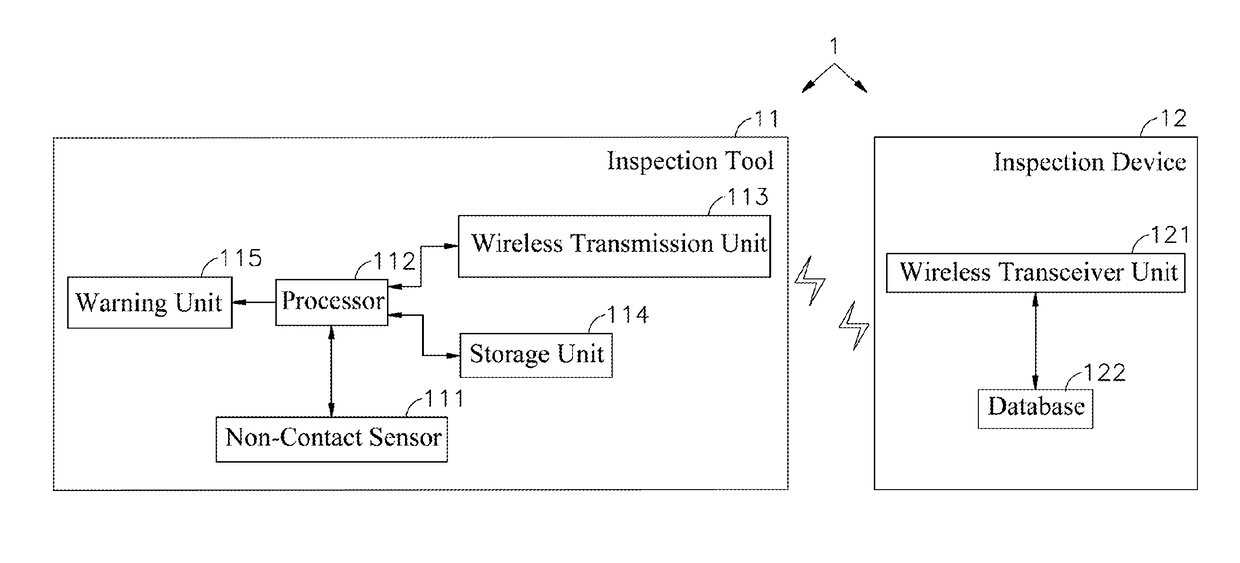
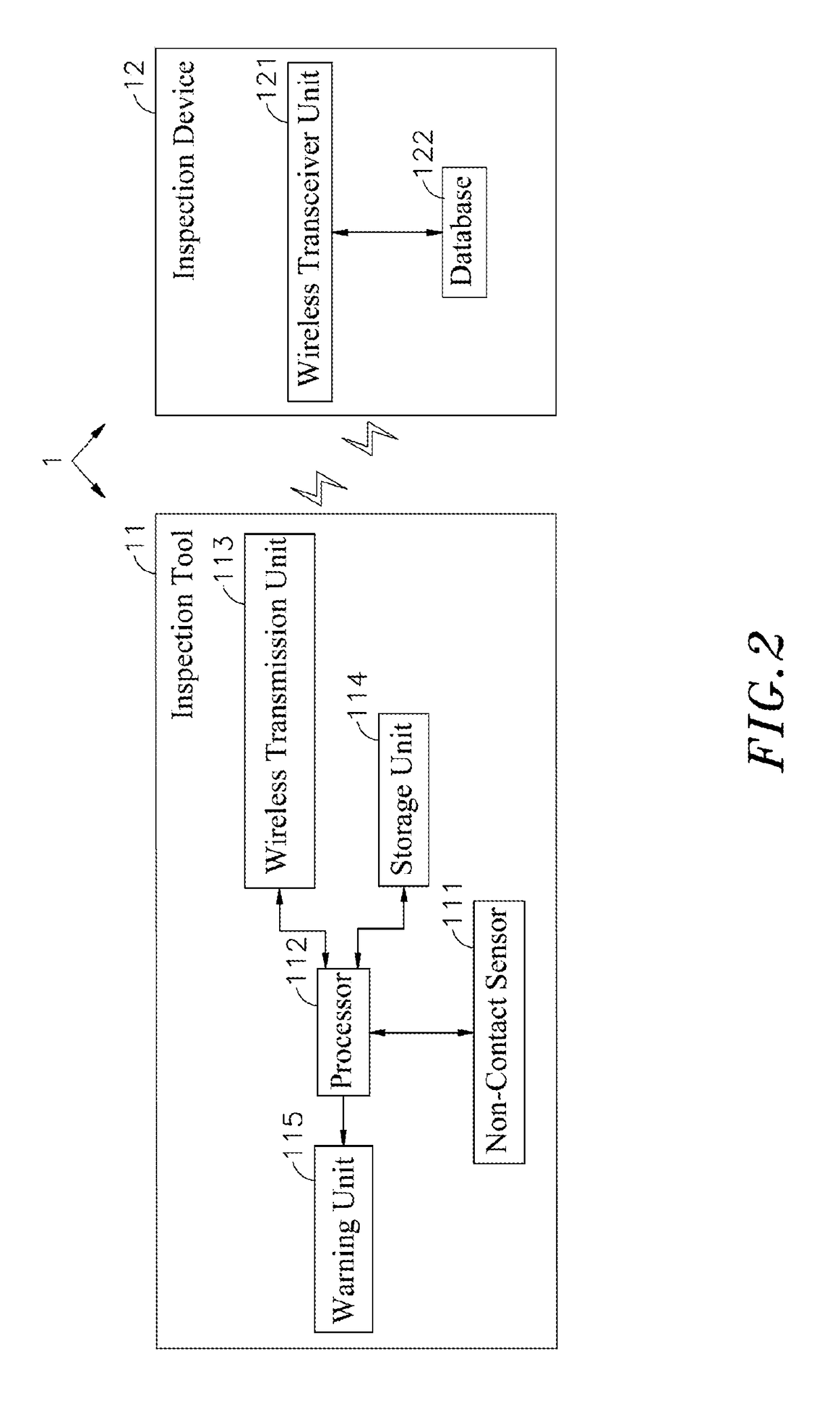
InactiveUS20170176313A1Improve accuracyReduce the possibilityProgramme controlSafety arrangmentsEarly warning systemWireless transceiver
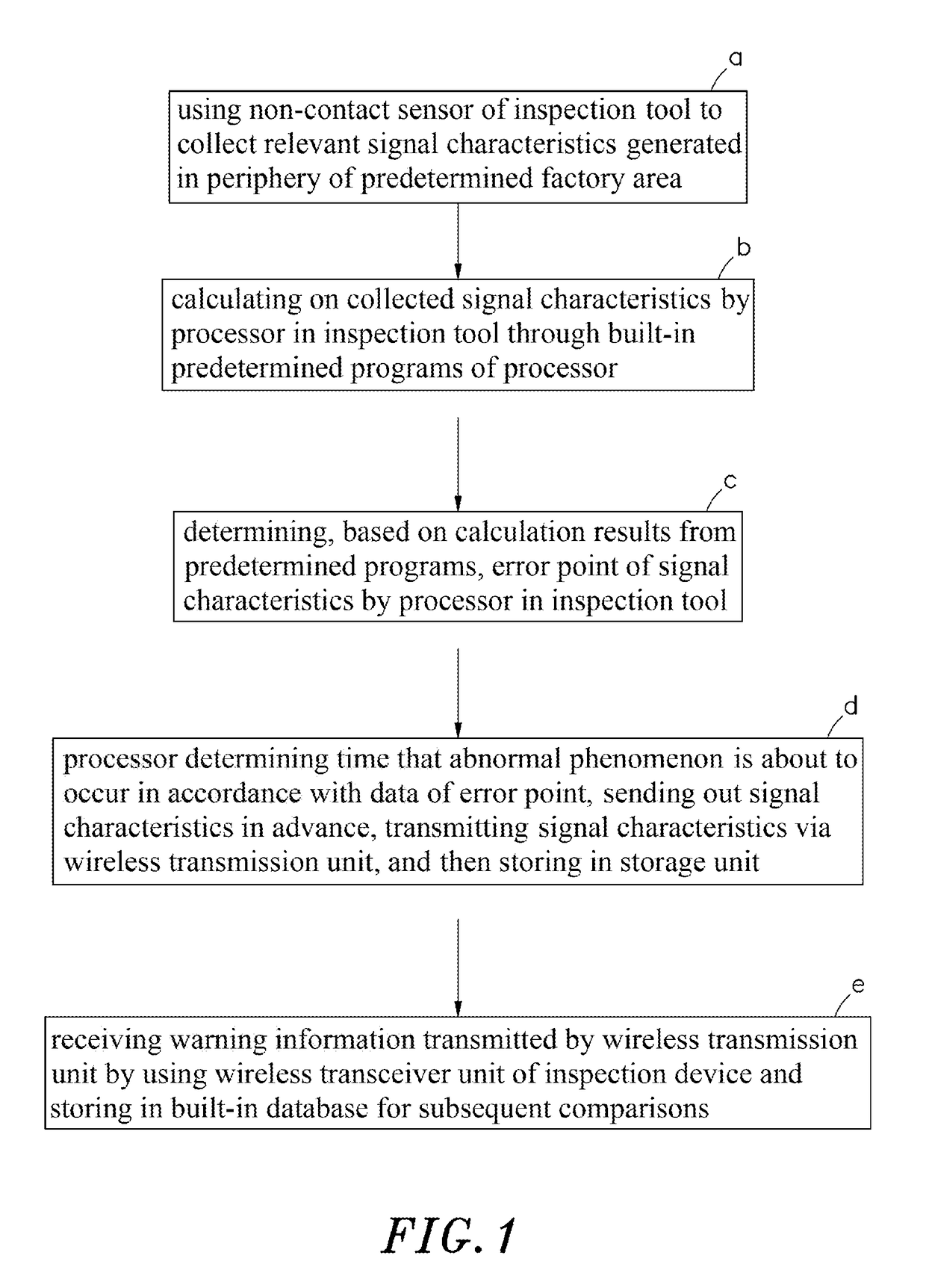
The present invention discloses an inspection method for early warning system of industrial security, in which the inspection steps for early warning system comprises: using inspection tool to collect signal characteristics regarding periphery of predetermined area; calculating on collected signal characteristics by means of processor in inspection tool through predetermined programs; determining, based on calculation results, error point of signal characteristics by means of processor in inspection tool; determining the time that abnormal phenomenon is about to occur by means of processor in accordance with data of error point, sending out warning information, and also transmitting collected signal characteristics via wireless transmission unit; and receiving characteristics information transmitted by wireless transmission unit by using wireless transceiver unit and then storing in built-in database for subsequent comparisons. The purposes of early and accurate factory security inspections as well as reduction in possibility for occurrence of accidents can be successfully achieved.
Owner:WIDAX TECH
OT system monitoring method, device and system and storage medium
InactiveCN109922026AImprove visibilityPrecise positioningInterprogram communicationData switching networksVisibilityApplication programming interface
The invention relates to the technical field of industrial safety, in particular to a monitoring method, device and system for an operation technology OT system and a storage medium so as to improve the visibility of one OT system and effectively prevent safety risks. The OT monitoring system provided by the embodiment of the invention comprises at least one network sensor, which is configured toobtain at least one data packet transmitted in an OT system and send the data packet to an OT monitoring device; an OT monitoring device, which is configured to extract information of at least one asset included in an OT system from at least one acquired data packet, and providing a first application programming interface API according to the extracted information of the at least one asset, generating an asset directory of the OT system when the first API is called, or determining the asset directory of the OT system according to the extracted information of the at least one asset. And the asset directory of the OT system can improve the visibility of the OT system, so that the security risk positioning is more accurate.
Owner:SIEMENS AG
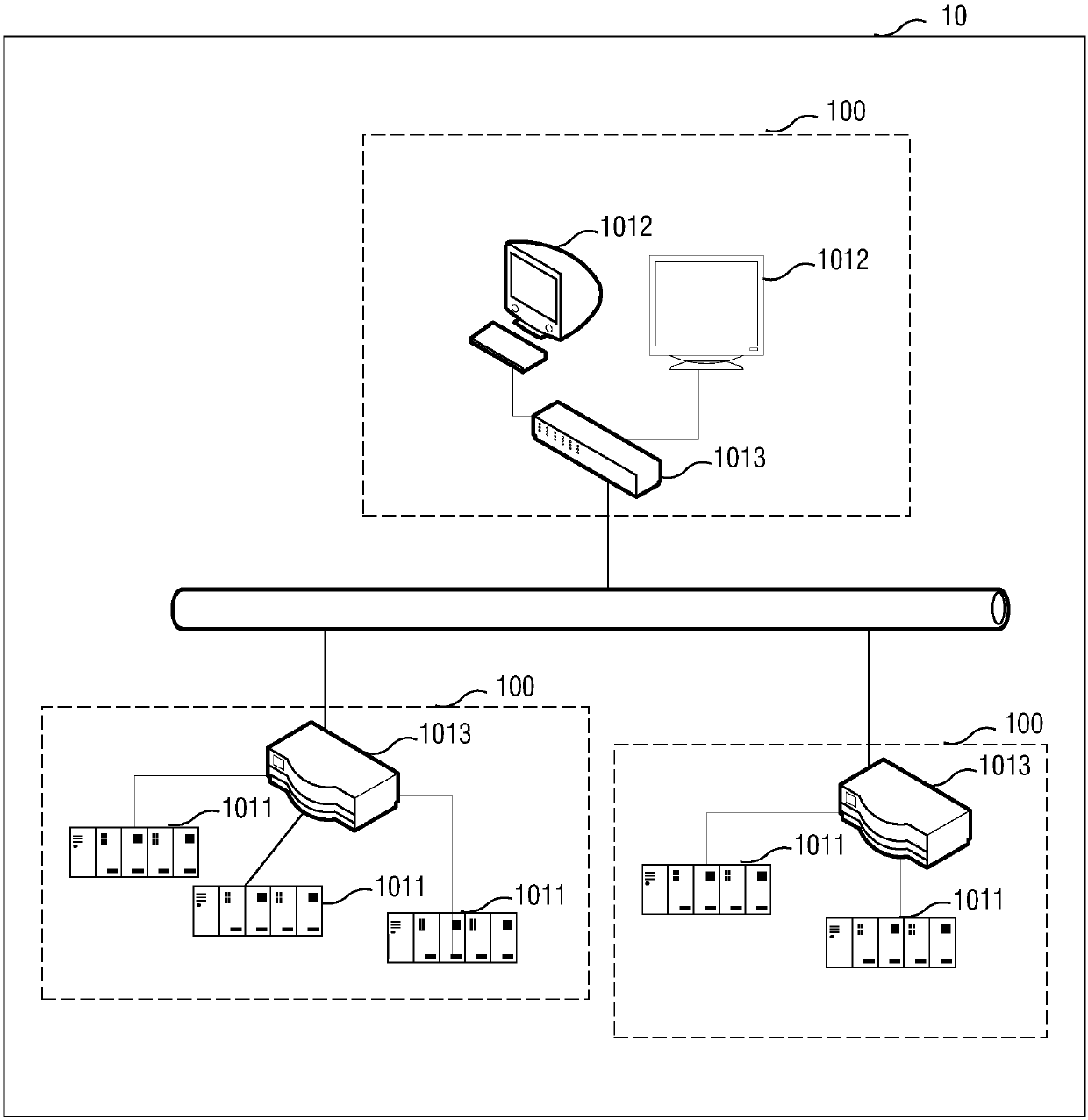
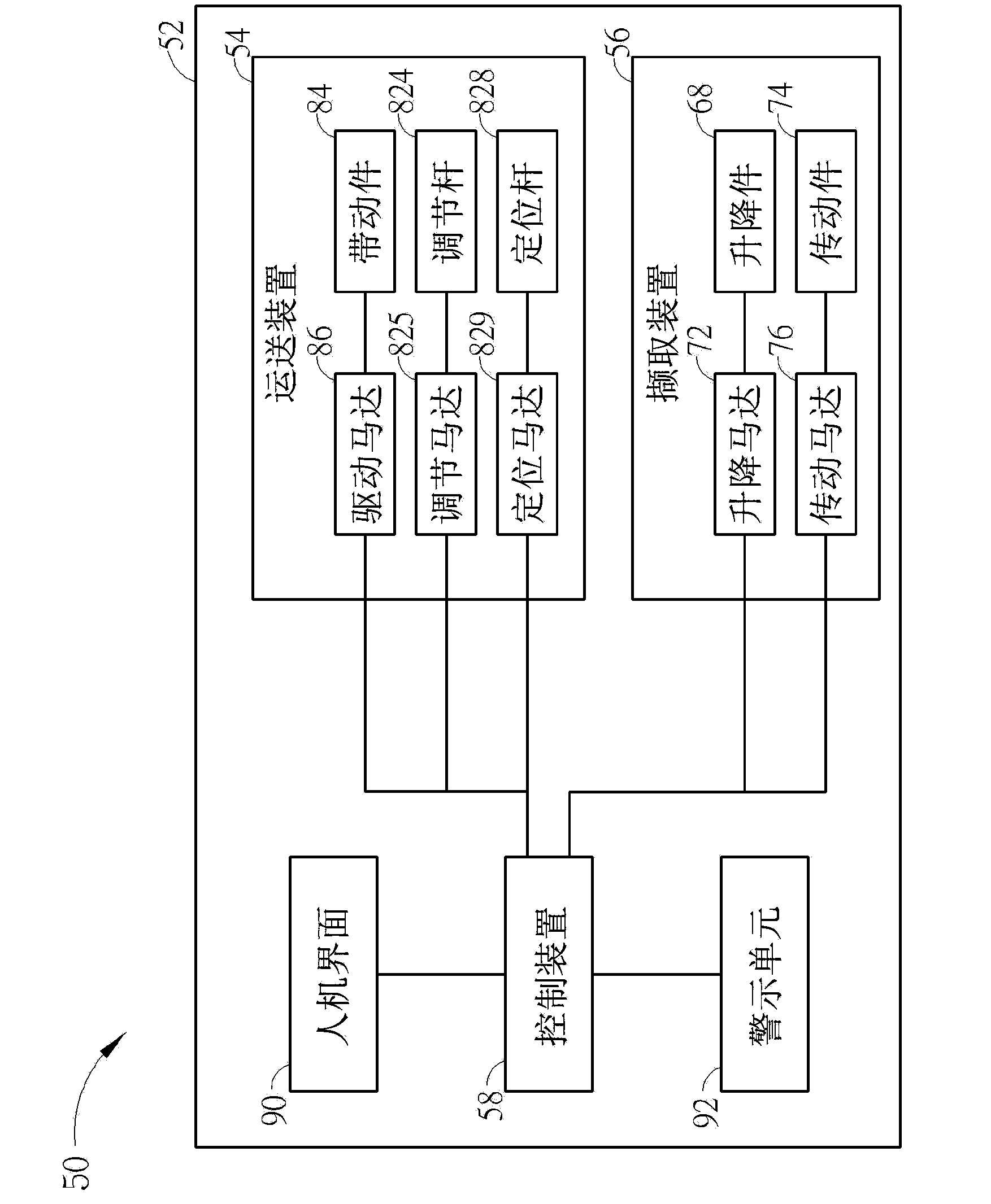
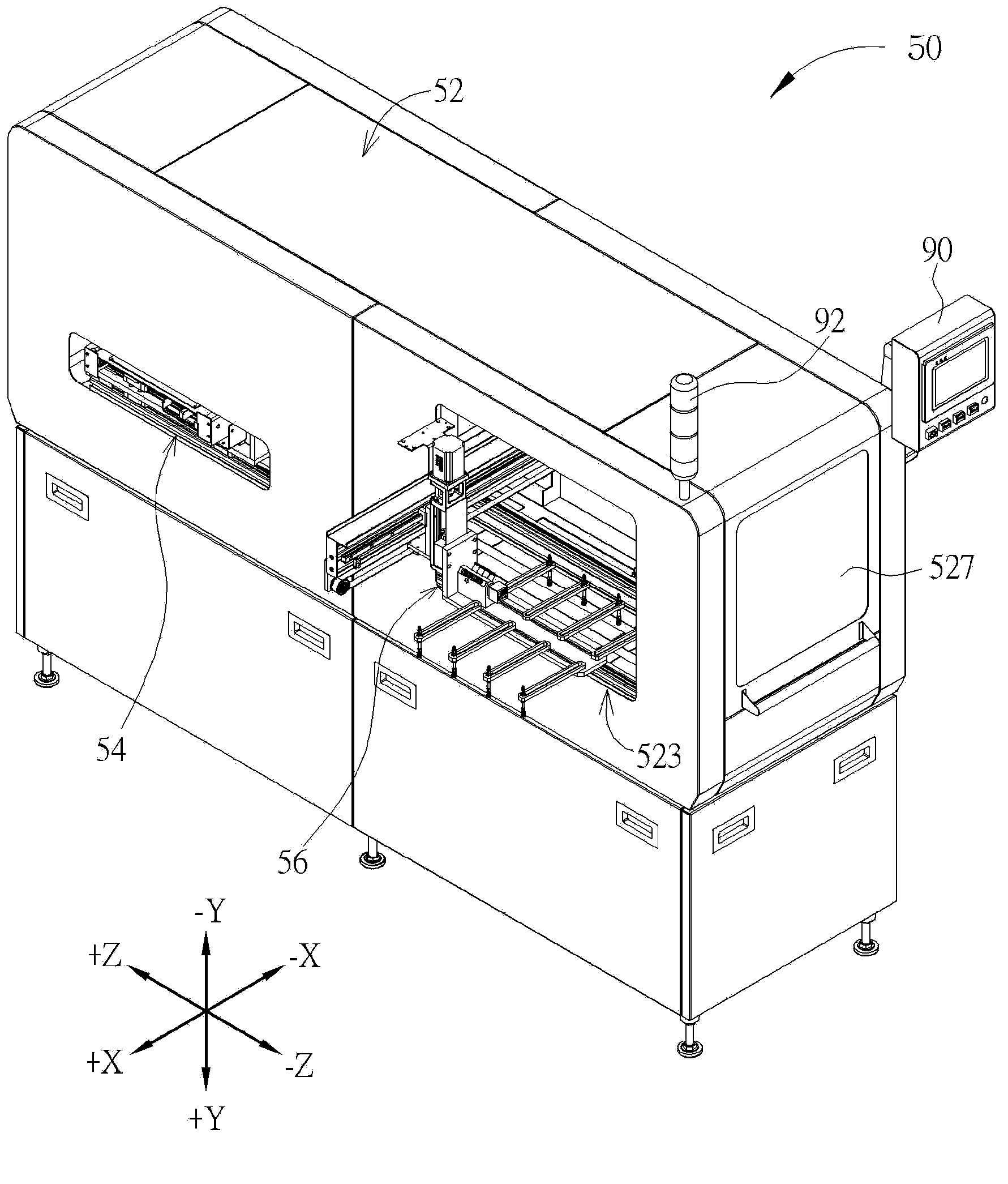
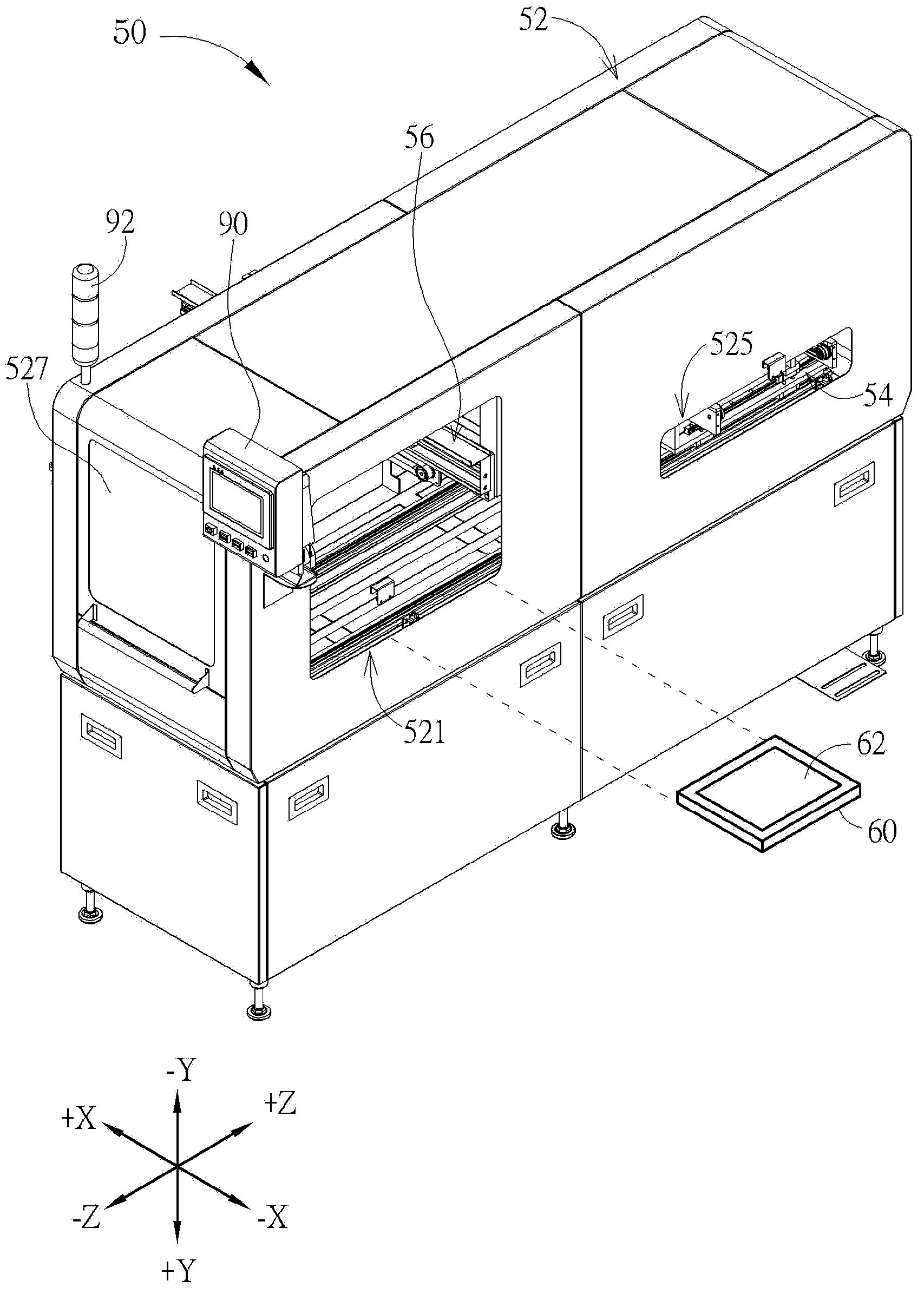
Unloading system used for automatically unloading circuit board
An unloading system includes a casing, a conveying device, a capturing device and a control device. A first entrance, a first exit and a second exit are formed on the casing. The conveying device is for conveying a carrying component and a circuit board disposed on the carrying component from the first entrance. The capturing device is for capturing the circuit board and then conveying the circuit board to the first exit. The control device is electrically connected to the conveying device and the capturing device. The control device is for controlling the capturing device to capture the circuit board entering from the first entrance and then to convey the circuit board to the first exit. The control device is further for controlling the conveying device to convey the carrying component from which the circuit board is unloaded to the second exit.
Owner:WISTRON KUSN +1
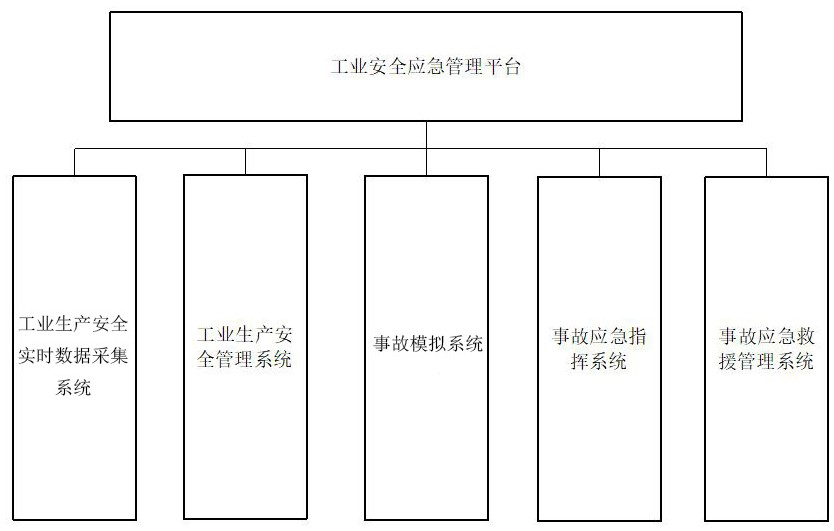
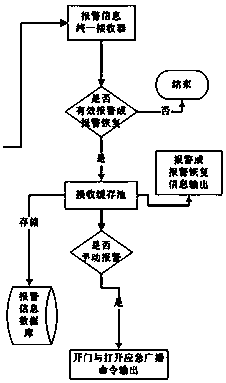
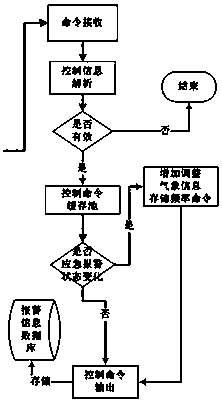
Industrial safety emergency management platform based on big data analysis technology
PendingCN111626636AAchieve securityRealize monitoring and early warning systemOffice automationResourcesSafety management systemsLarge screen
The invention discloses an industrial safety emergency management platform based on a big data analysis technology. The industrial safety emergency management platform based on the big data analysis technology comprises an industrial production safety real-time data acquisition system, an industrial production safety management system, an accident simulation system, an accident emergency command system and an accident emergency rescue management system. After the emergency command data monitoring server is controlled to monitor an alarm, the camera related to the alarm is automatically rotatedto the vicinity of an alarm point instantly, and a corresponding video is displayed on a large screen and the map of the emergency command data monitoring server immediately; meanwhile, the system supports automatic opening and closing of the fireproof roller shutter door, opening of an escape channel, automatic pushing of emergency broadcast, automatic sending of short messages and the like after certain conditions are met. Through configuration intelligent linkage, all emergency operations are completed in the shortest time, the casualty rate of accidents is greatly reduced, and meanwhile continuous production is guaranteed.
Owner:CHENGDU GREATECH ELECTRICS
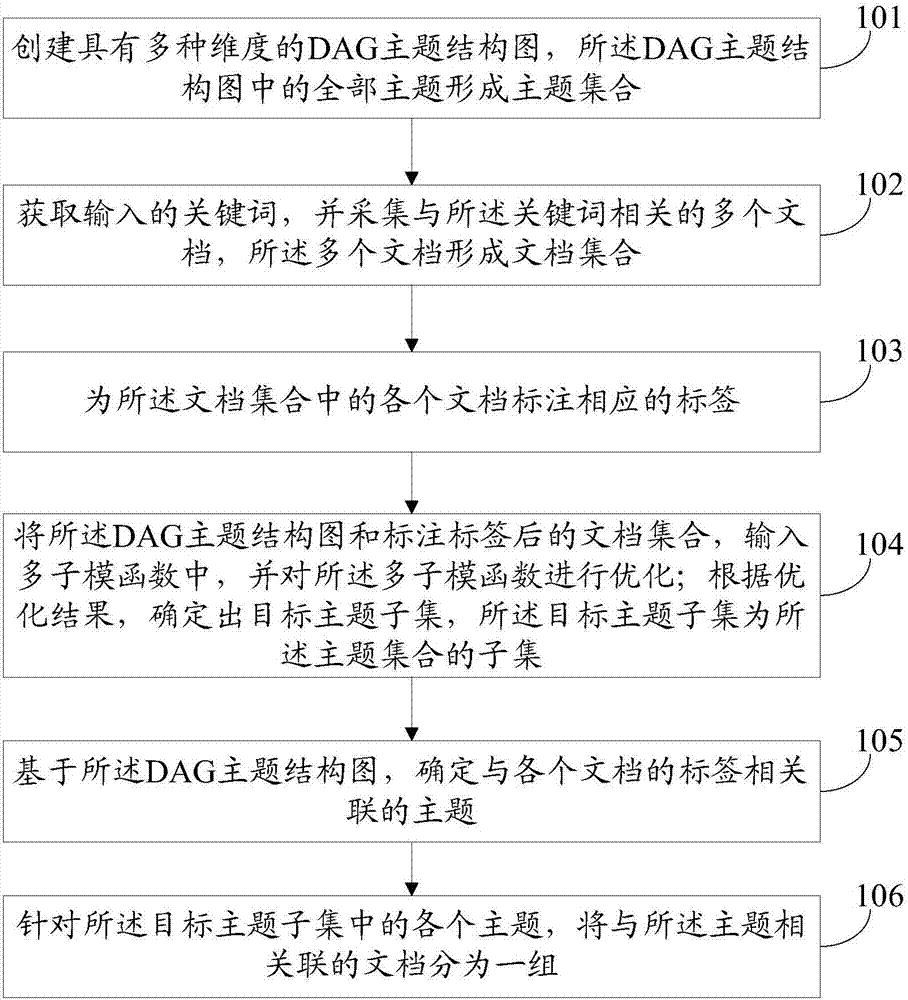
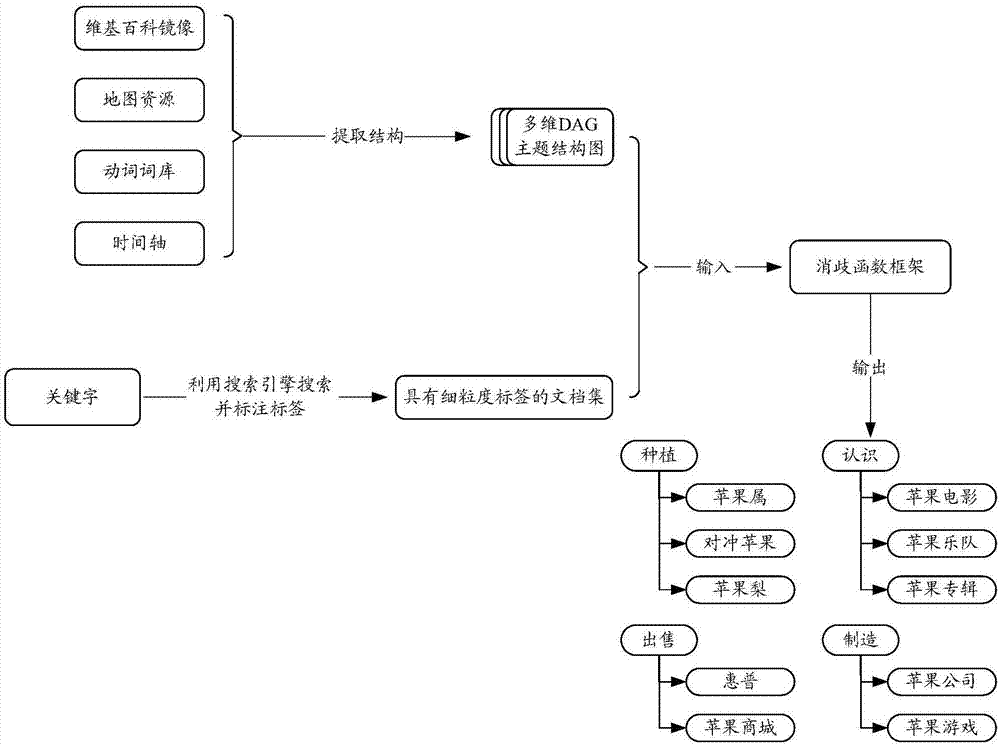
Method and device for automatic disambiguation of multiple documents of industrial safety topics
ActiveCN107391613AImprove inheritance structureEnhanced description abilitySemantic analysisSpecial data processing applicationsIndustrial securitySubject matter
The invention discloses a method and device for automatic disambiguation of multiple documents of industrial safety topics. The method includes the steps that a DAG topic structure chart with multiple dimensions is created, and a topic set is formed by all topics in the DAG topic structure chart; input keywords are acquired, the multiple documents corresponding to the keywords are collected, and a document set is formed by the multiple documents; each document in the document set is tagged with a corresponding tag; the DAG topic structure chart and the document set tagged with the tags are input into a multi-sub-modular function, and the multi-sub-modular function is optimized; according to an optimization result, a target topic subset is determined, and the target topic subset is a subset of the topic set; based on the DAG topic structure chart, topics corresponding to the tags of the documents are determined; aiming at the topics of the target topic subset, the documents corresponding to the topics are classified as a group.
Owner:BEIHANG UNIV
Intelligent video box equipment for safety management and corresponding intelligent video analysis method
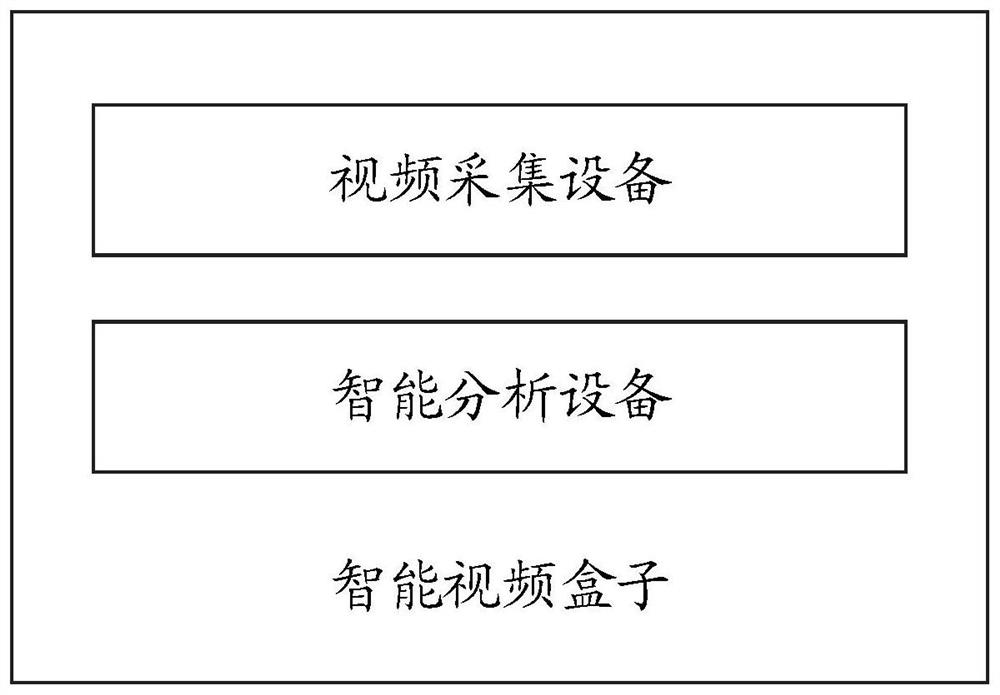
ActiveCN112153334AQuick collectionQuick solveCharacter and pattern recognitionClosed circuit television systemsAcquisition apparatusIndustrial security
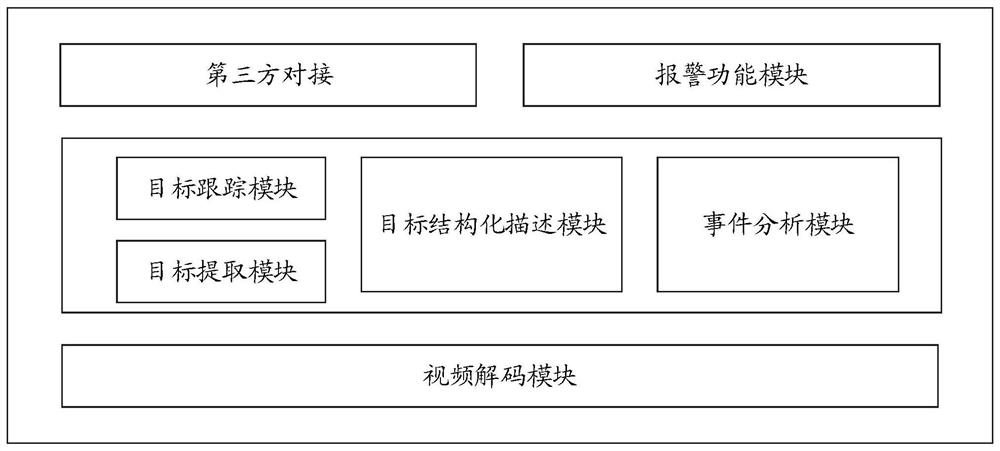
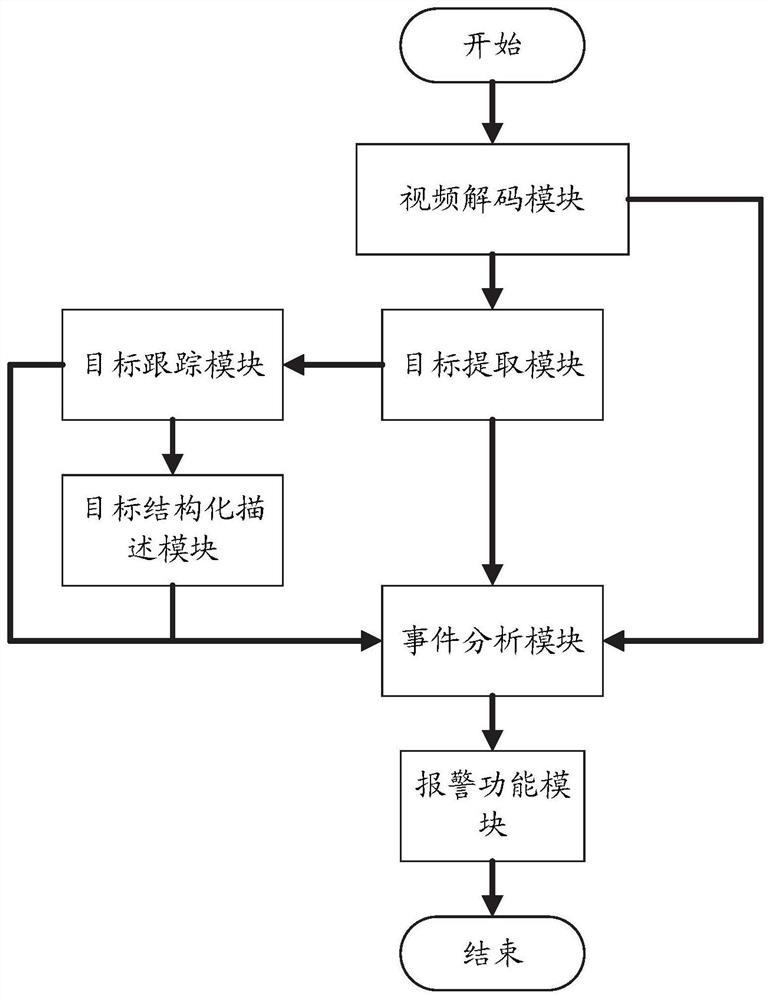
The invention relates to intelligent video box equipment for safety management, and the equipment comprises video collection equipment which comprises a video collection module which is used for obtaining a real-time video stream and transmitting collected video data to intelligent analysis equipment; and the intelligent analysis equipment is connected with the video acquisition equipment and is used for operating a plurality of intelligent video module methods. The invention also relates to an intelligent video analysis method for safety management based on the equipment. By adopting the intelligent video box equipment for safety management and the corresponding intelligent video analysis method, hardware calculation is marginalized by combining the intelligent analysis equipment and thevideo acquisition module, the advantages of edge calculation are brought into full play, and multiple algorithm modules are integrated on the intelligent analysis equipment. The method achieves the quick collection of target behaviors, events, attributes and other information, achieves the filing and collection of the information to an alarm system, and provides an efficient, quick and flexible solution for industrial safety management.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Detection method for network abnormality attacks
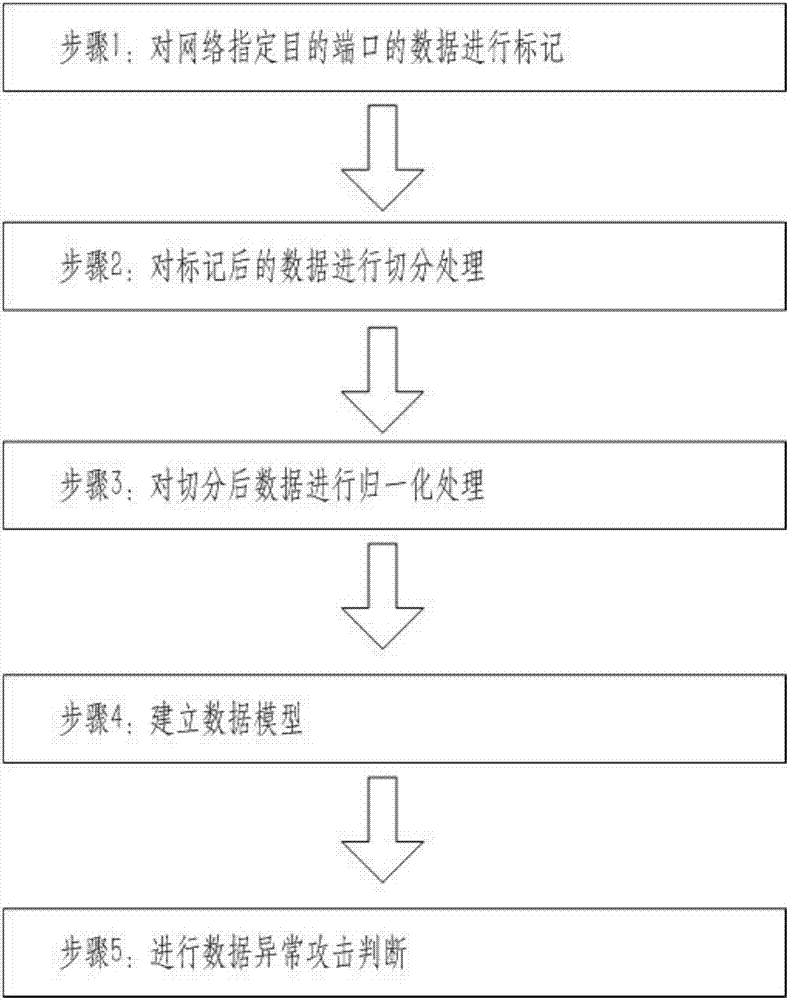
ActiveCN107995193ASolving Attack Detection ProblemsSolve the problems of high maintenance cost, high threshold, and real-time updateMachine learningTransmissionIndustrial securityData modeling
The invention aims at providing a detection method for network abnormality attacks. Efficient detection on the network abnormality attacks is achieved by cooperatively using the steps of data marking,data mark splitting, normalization processing, data modeling, data abnormality attack judging and the like, the problems that a traditional rule-based detection method is high in maintenance cost andthreshold and needs real-time updating are solved, and meanwhile the private protocol attack detection problem which cannot be solved by existing industrial security manufactures generally is solved.
Owner:宝牧科技(天津)有限公司
Fiber web for gas sensor, method for manufacturing same, and gas sensor comprising same
ActiveUS20190391082A1High sensitivityImprove spin performanceMaterial analysis by observing effect on chemical indicatorNon-woven fabricsFiberIndustrial security
Provided is a fiber web for a gas sensor. In one exemplary embodiment of the present invention, there is provided a fiber web for a gas sensor including nanofibers including a fiber-forming material and a sensing material for reacting with a target substance in a test gas. According to the exemplary embodiment, the fiber web for a gas sensor is capable of identifying the presence or absence of a target substance in a test gas and quantitatively determining the concentration of a target substance, and exhibits improved sensitivity due to having an increased area of contact and reaction with a target substance contained in a test gas. In addition, the fiber web for a gas sensor facilitates the detection of a target substance in a test gas at a low cost and thus can be widely used for the detection of various volatile organic compounds (VOCs) in households, the diagnosis of asthma or esophagitis or the identification of a patient suffering from the same, and the detection of hazardous materials in other fields of industrial safety.
Owner:AMOGREENTECH CO LTD
Information security protection system for DCS (Distributed Control System)
PendingCN113225313AAchieve isolationRealize controllableData switching networksData acquisitionInformation security
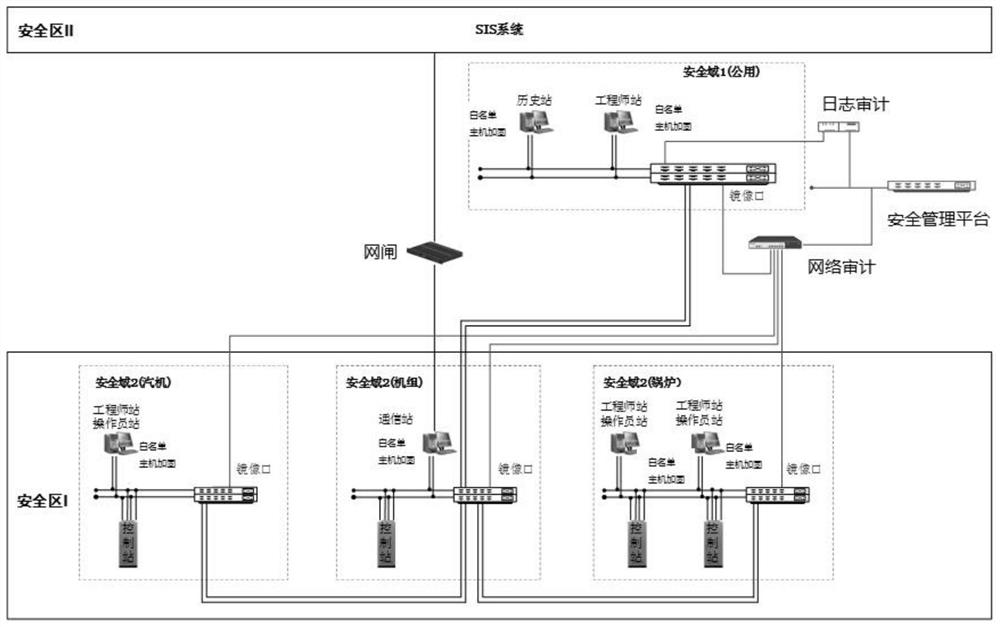
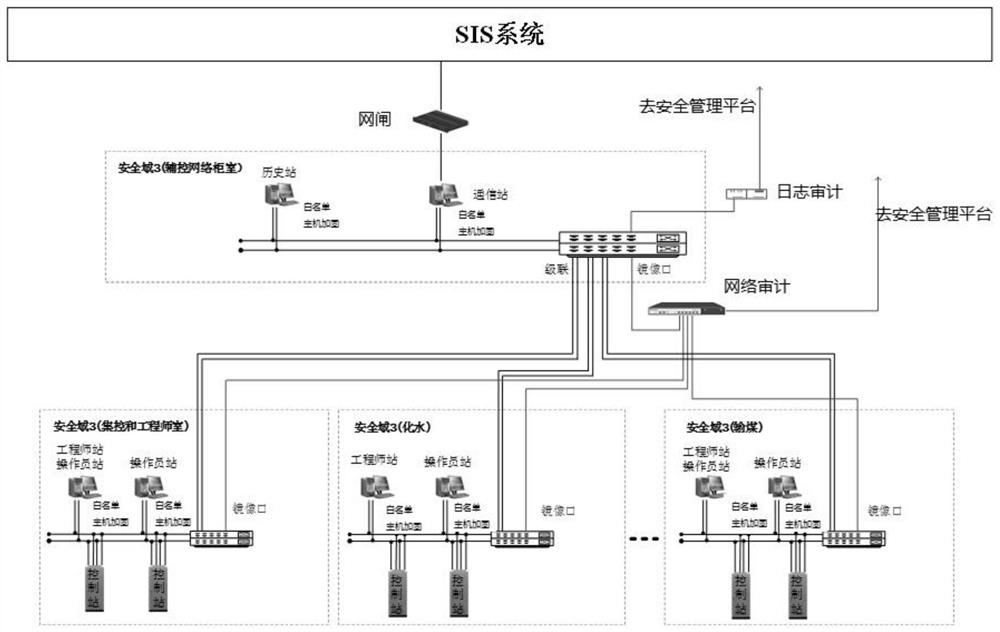
The invention relates to an information security protection system for a DCS system, and the system comprises an industrial security isolation gatekeeper which is disposed at the network boundary of a DCS network and an SIS system, and is used for isolating the DCS system from the SIS system, and protecting the security of the network boundary of the DCS system; an industrial network auditing system which is deployed in a main switch bypass of the DCS system and is used for network full-flow auditing, alarming and analyzing; an industrial log auditing system which is deployed in the DCS and is used for carrying out log data acquisition, classification and analysis on the safety equipment, the network equipment, the host system and the database; and an industrial intrusion detection system which is deployed at a bypass of the SIS three-layer core switch and is used for monitoring industrial network transmission data in real time and performing intrusion detection and alarm on network data traffic. According to the invention, safe and stable operation of the DCS system information network can be ensured.
Owner:DATANG SANMENXIA POWER GENERATION
Intelligent industrial safety lock
InactiveCN111899383APrevent private entryResume normal operationIndividual entry/exit registersIndustrial securitySafety knowledge
The invention relates to an intelligent industrial safety lock which comprises a controller, a locking actuator and a personal IC card. The controller is used for completing the functions of identifying an operator, checking entering and withdrawing personnel information and performing unlocking; the locking actuator is used for completing locking and unlocking functions and a self-checking function of automatic equipment; company identifier information, employee ID codes, employee authority information and IC card special encrypted data information are stored in the personal IC card; and thecontroller is connected with the locking actuator through a communication bus. The beneficial effects of the intelligent industrial safety lock are that the system can effectively prevent a person whodoes not have related safety knowledge and operation skills from entering privately; other irrelevant personnel or other accidents can be prevented from closing the safety door, and the automatic equipment is reset to operate; the self-checking function is achieved, and safety accidents caused by failure of the safety lock function can be prevented; an operator can be reminded to standardize operation, and some accidental unsafe factors are effectively avoided.
Owner:苏争练
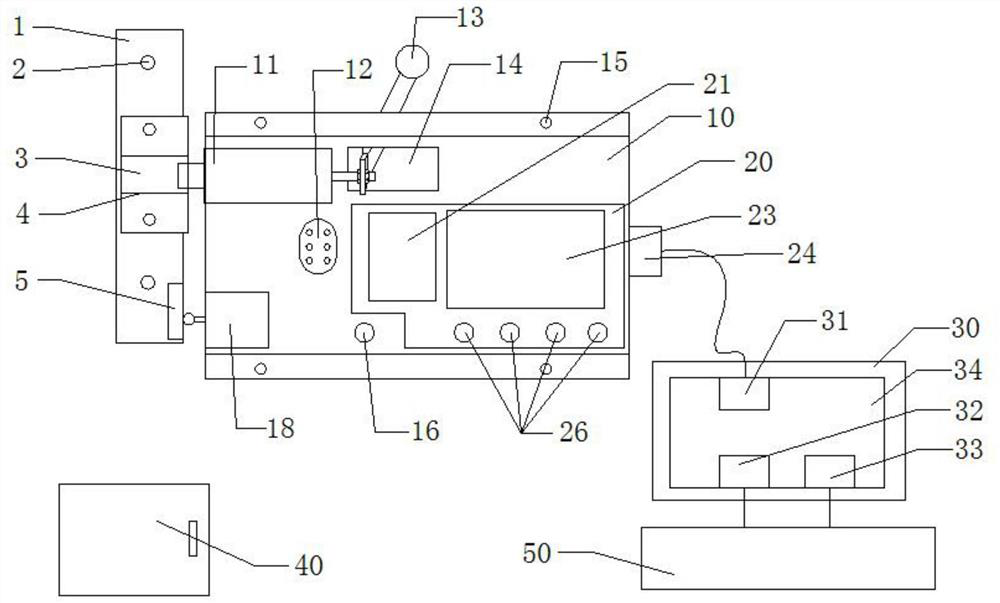
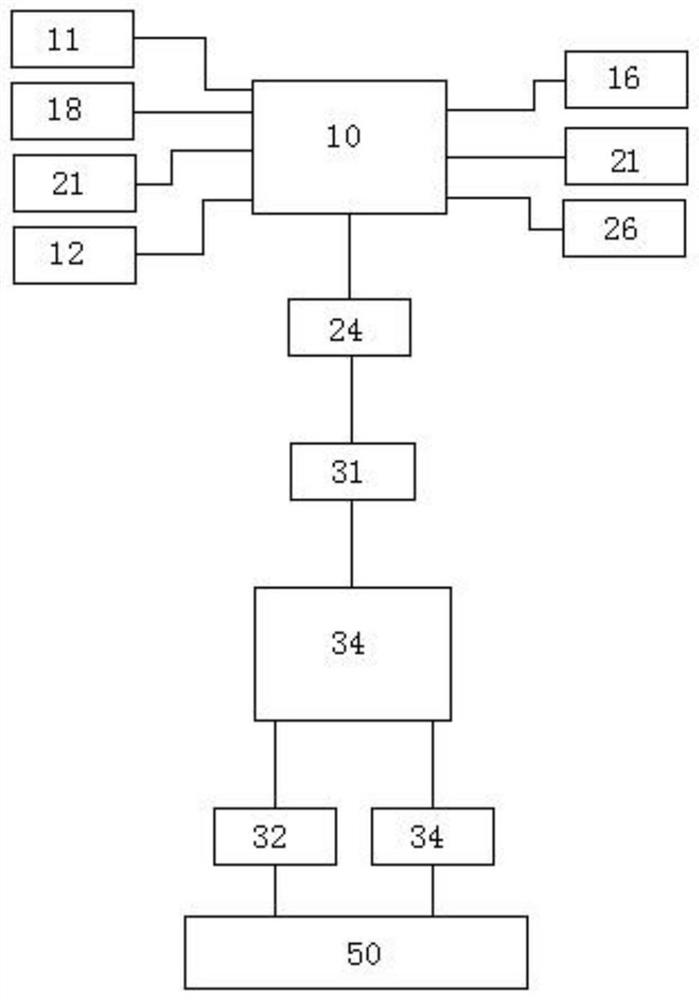
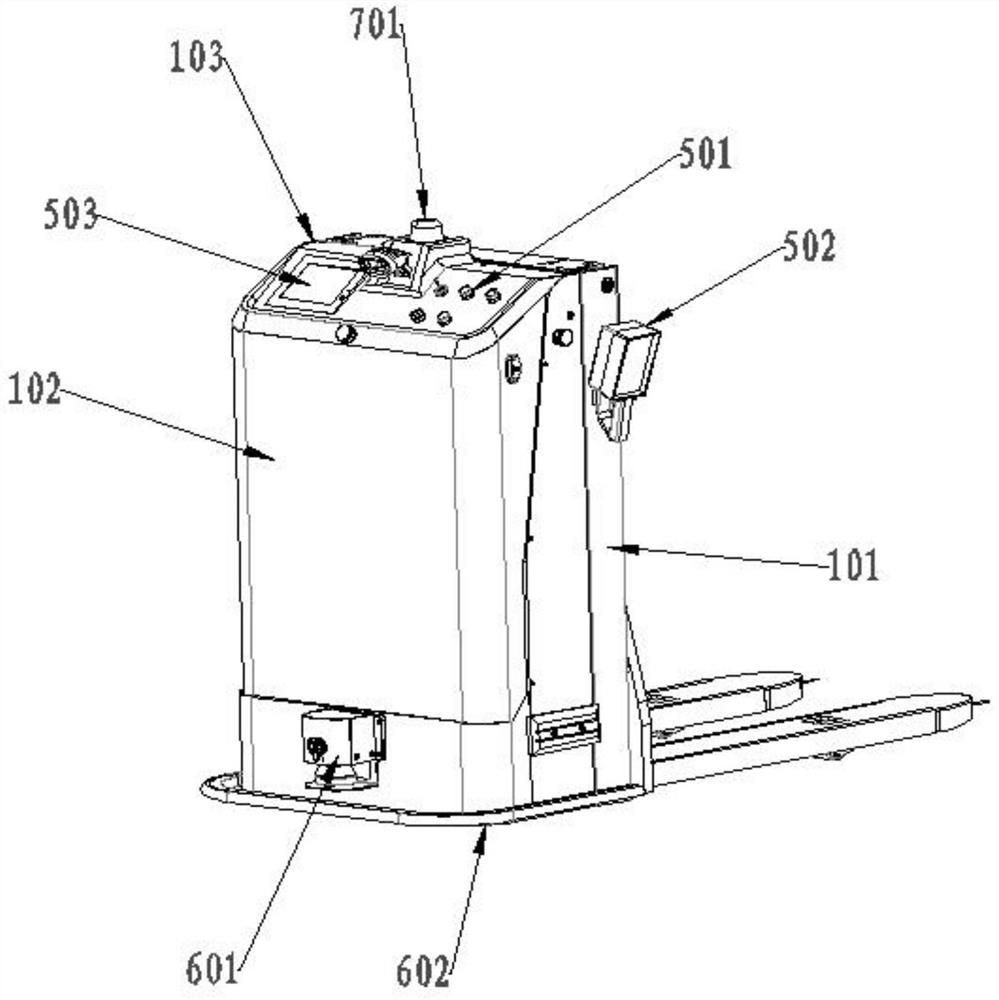
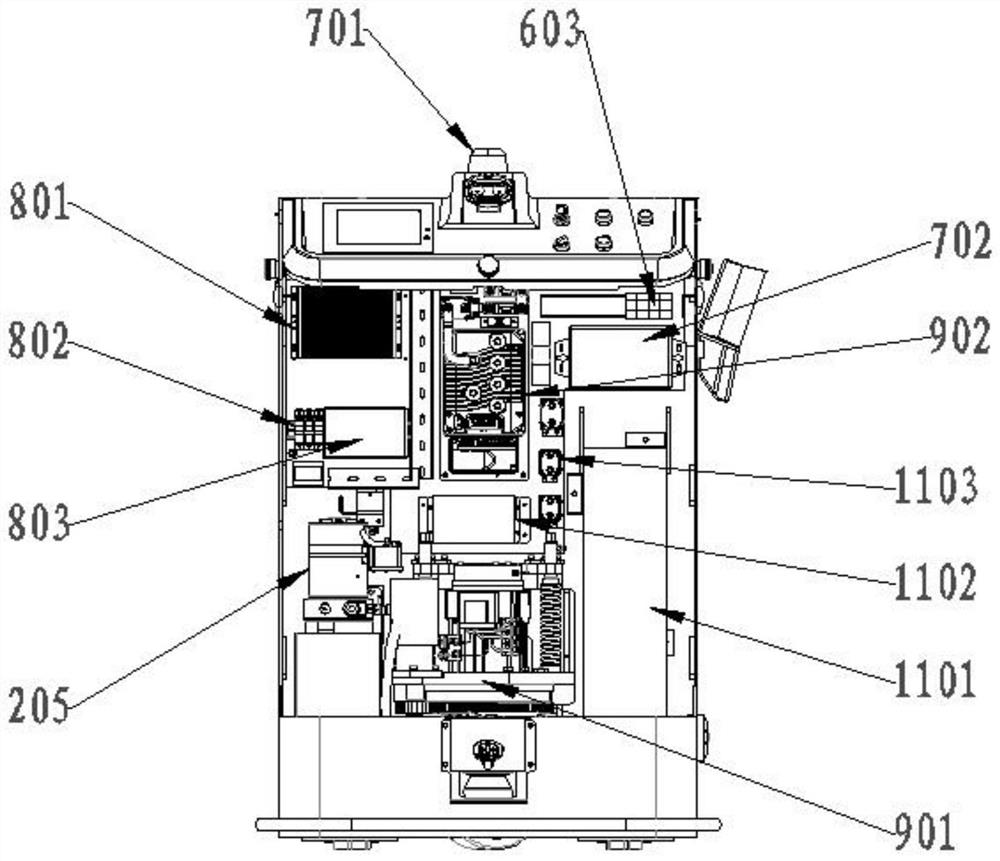
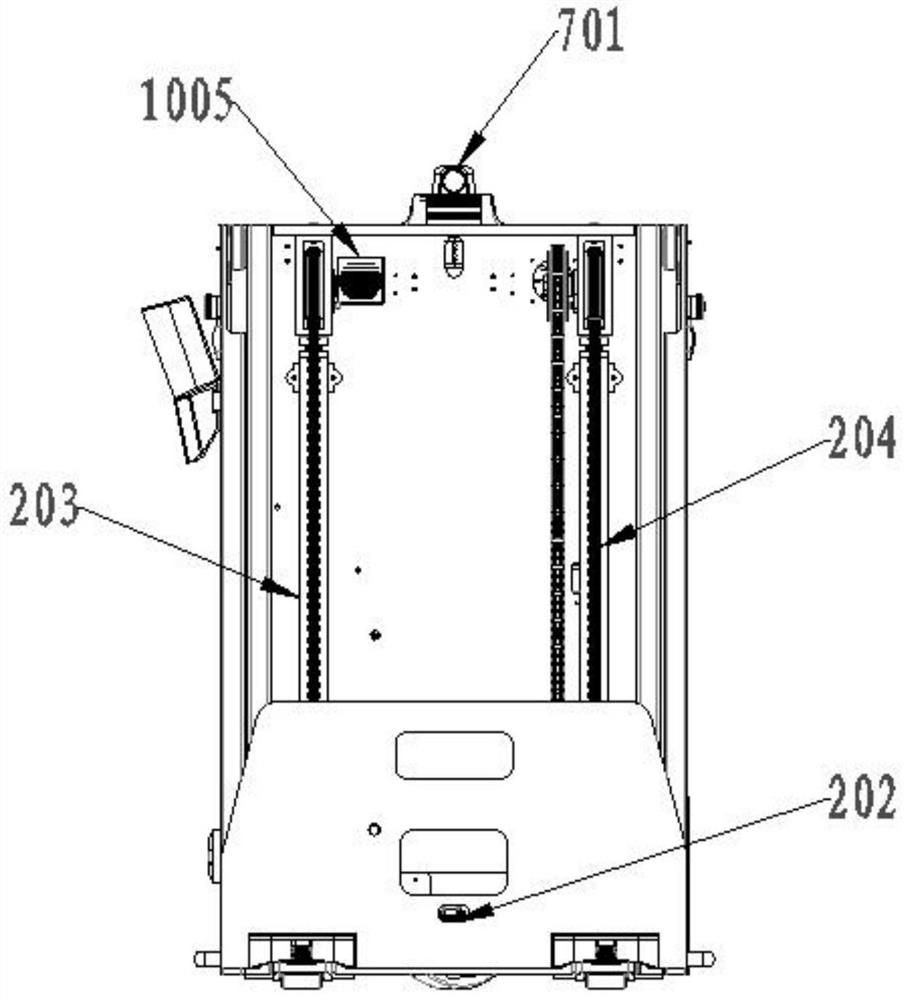
Industrial safety laser simultaneous localization and mapping (SLAM) navigation pallet stacking automated guided vehicle (AGV)
InactiveCN111717844AEnsure safetyImprove parking accuracySafety devices for lifting equipmentsSimultaneous localization and mappingVehicle frame
The invention relates to an automated guided vehicle (AGV) trolley, in particular to an industrial safety laser simultaneous localization and mapping (SLAM) navigation pallet stacking AGV. The industrial safety laser SLAM navigation pallet stacking AGV includes a frame, a lower covering part fixed to the front end of the frame, an upper covering part fixed between the top of the frame and the topof the lower covering part, a laser SLAM navigation system and a vehicle driving system, a vehicle controller is arranged inside the lower covering part, a fork mechanism is arranged at the rear of the frame, the fork mechanism is driven by a fork lifting system, the fork lifting system includes a pumping station, a lifting cylinder and a driving chain, and an obstacle avoidance system is furtherincluded. The obstacle avoidance system includes a front obstacle avoidance unit, a rear obstacle avoidance unit and a safety relay component connected between a vehicle power supply and the vehicle driving system. The front obstacle avoidance unit includes a laser obstacle avoidance module arranged at the bottom of the lower covering part and a safety edge contact module arranged at the bottom ofthe lower covering part. The technical scheme can overcome the defects of the low AGV parking accuracy and ineffectiveness in obstacle avoidance function in the prior art.
Owner:安徽安歌机器人有限公司
Industrial network security
ActiveUS9344403B2Facilitate communicationImprove network securityTransmissionIndustrial safety systemNetwork link
A private overlay network is introduced into an existing core network infrastructure to control information flow between private secure environments. Such a scheme can be used to connect a factory automation network linking operations devices to a corporate network linking various business units, with enhanced network security. Such a connection can be facilitated by introducing into the existing infrastructure a set of industrial security appliances (ISAs) that work together to create an encrypted tunnel between the two networks. The set of ISAs can be scalable to overlay differently sized core networks, to create the private overlay network. Connections to the private overlay network can be managed by the ISAs in a distributed fashion, implementing a peer-to-peer dynamic mesh policy. The industrial security system disclosed may be particularly advantageous in environments such as public utility systems, medical facilities, and energy delivery systems.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
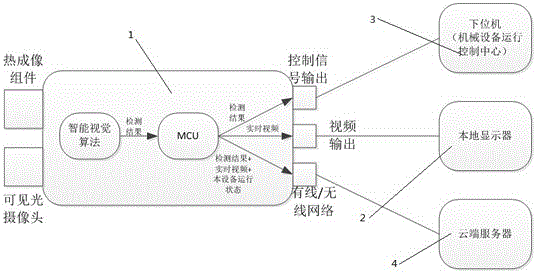
Industrial safety monitoring system based on intelligent thermal imaging
ActiveCN106204998AReduce casualtiesIntelligent RecognitionClosed circuit television systemsBurglar alarm short radiation actuationIndustrial securityStructure of Management Information
The invention provides an industrial safety monitoring system based on intelligent thermal imaging. The system comprises a safety monitor correspondingly arranged for an operator, an independently arranged display unit, a lower-layer control unit used for sending a stopping instruction to machining equipment, and a cloud server used for collecting, analyzing and classifying violation data recorded on the safety monitor. The safety monitor is provided with a communication port and a thermal imaging assembly. The communication port is connected with the cloud server, the lower-layer control unit and the display unit through a wireless network. The system is simple in structure, long in service life and high in working efficiency. The production process is monitored in real time through the thermal imaging assembly. Compared with the prior art, the monitoring is more accurate. Furthermore, the cloud server is used for carrying out data sampling on the safety monitor correspondingly arranged for the operator. Therefore, the adaptability of operators to various devices is analyzed, so that an optimal operator for each device can be found out for users.
Owner:南京南工应急科技有限公司
Industrial control network security protection method
ActiveCN103036886BGuaranteed real-time diagnosisReduce severityTransmissionIndustrial securityControl system
Owner:珠海市鸿瑞信息技术股份有限公司
An emergency plan control method based on an industrial safety emergency command integrated system
ActiveCN105159255BPlay a linkage roleAutomatically receive perimeter intrusion alarm signalsAlarmsProgramme total factory controlVideo monitoringEmergency plan
The invention discloses an industrial safety emergency command integrated system-based emergency plan control method. The method includes the following steps that: S1, a center system receives alarm information of an alarm subsystem, analyzes, stores and judges the alarm information, and forwards the alarm information to an emergency plan programming system; S2, the emergency plan programming system sends control commands to the center system, and the center system receives the information, and analyzes and stores the information, and then transmits the control commands to an execution subsystem through the center system; and S3, the execution subsystem executes a plan according to the received control commands. According to the control method of the invention, a plurality of systems are correlated, and therefore, a linkage effect can be realized, and video monitoring signals are controlled, and perimeter intrusion alarm signals are monitored in real time, and fire alarm signals are automatically received and are fed back to the center system in real time, and at the same time, different emergency plans can be started according to dangers.
Owner:CHENGDU GREATECH ELECTRICS
Engineering-based industrial safety monitoring equipment and using method thereof
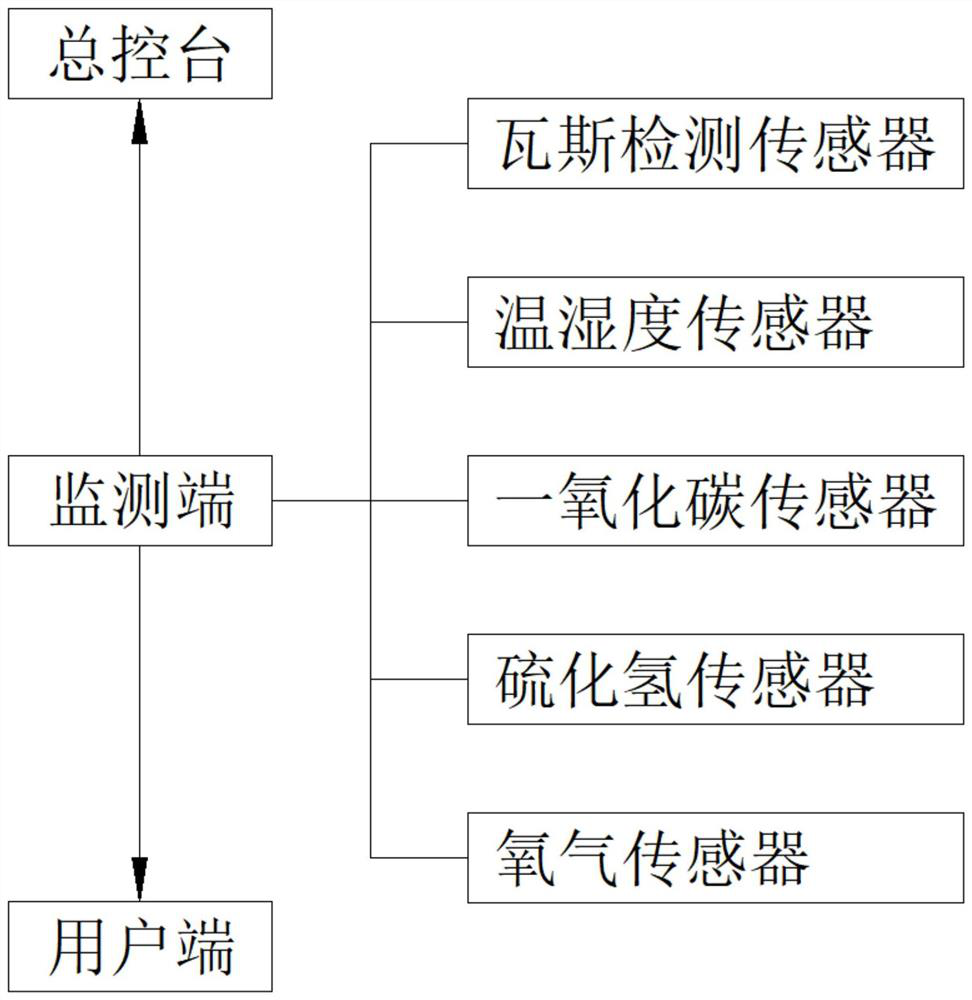
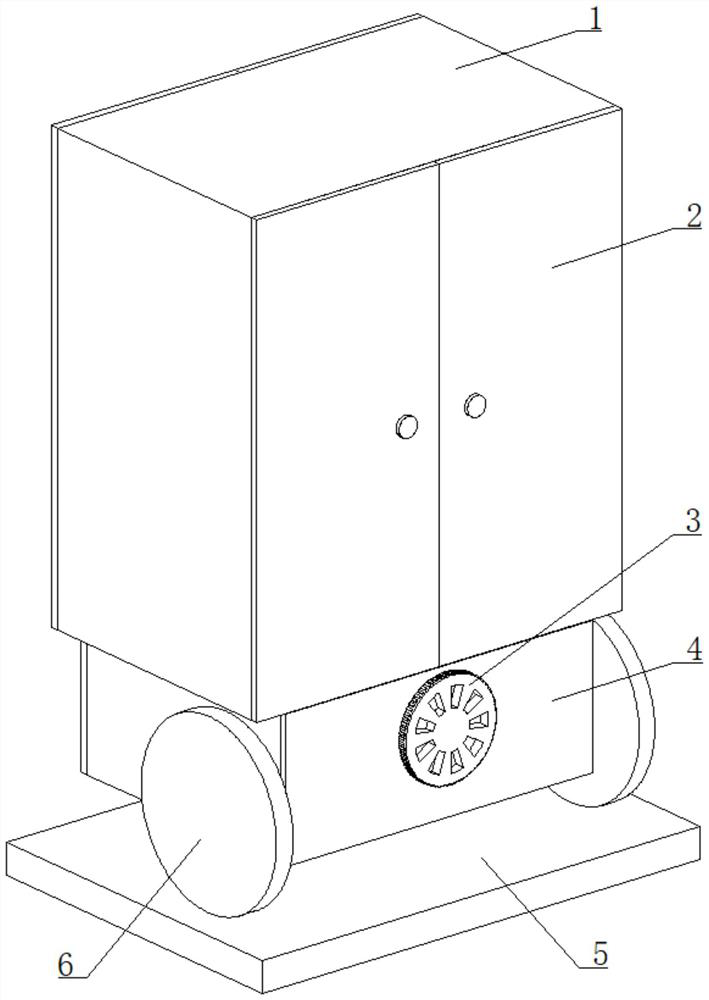
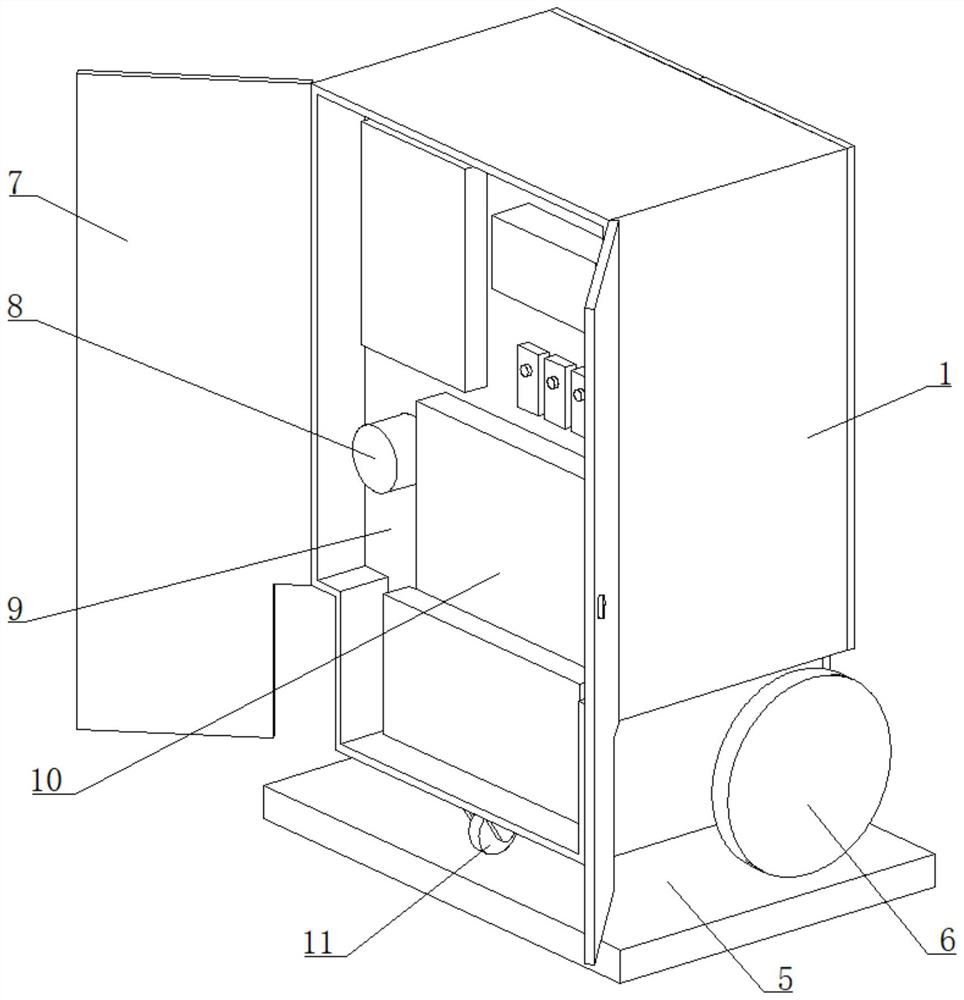
InactiveCN112212914AEasy to understand in real timeGuarantee working conditionsMeasurement apparatus componentsIndustrial securityInformation assurance
The invention relates to the field of safety monitoring, and particularly discloses engineering-based industrial safety monitoring equipment, which comprises a monitoring end, a user end and a masterconsole, and a monitor is arranged in the monitoring end, the monitoring end sends monitoring data of the monitor to the user end and the master console, the monitoring end comprises a cabinet body capable of being fixed on the ground, and the user end comprises a shell, one side of the shell is rotatably connected with a rotating plate, a gap is formed between the rotating plate and the shell, and the invention further discloses a use method of the detection equipment, and the use method comprises the following steps: S1, arranging the monitoring end; S2, enabling the user side to receive thesafety monitoring information; S3, when the monitoring data exceeds a safety threshold, enabling the user side to give an alarm. According to the invention, the monitoring terminal is arranged at theconstruction site, the monitor is arranged in the monitoring terminal, a constructor carries the user terminal, and the monitoring terminal can send the monitoring data of the monitor to the user terminal and the master console, so that the constructor can know the safety monitoring information in real time and guarantee the labor operation conditions, and safety accidents are avoided.
Owner:QUZHOU UNIV
Workshop production task label configuration method based on industrial safety emergency management
PendingCN114548580AIncrease productivityForecastingGeographical information databasesIndustrial securityTimestamping
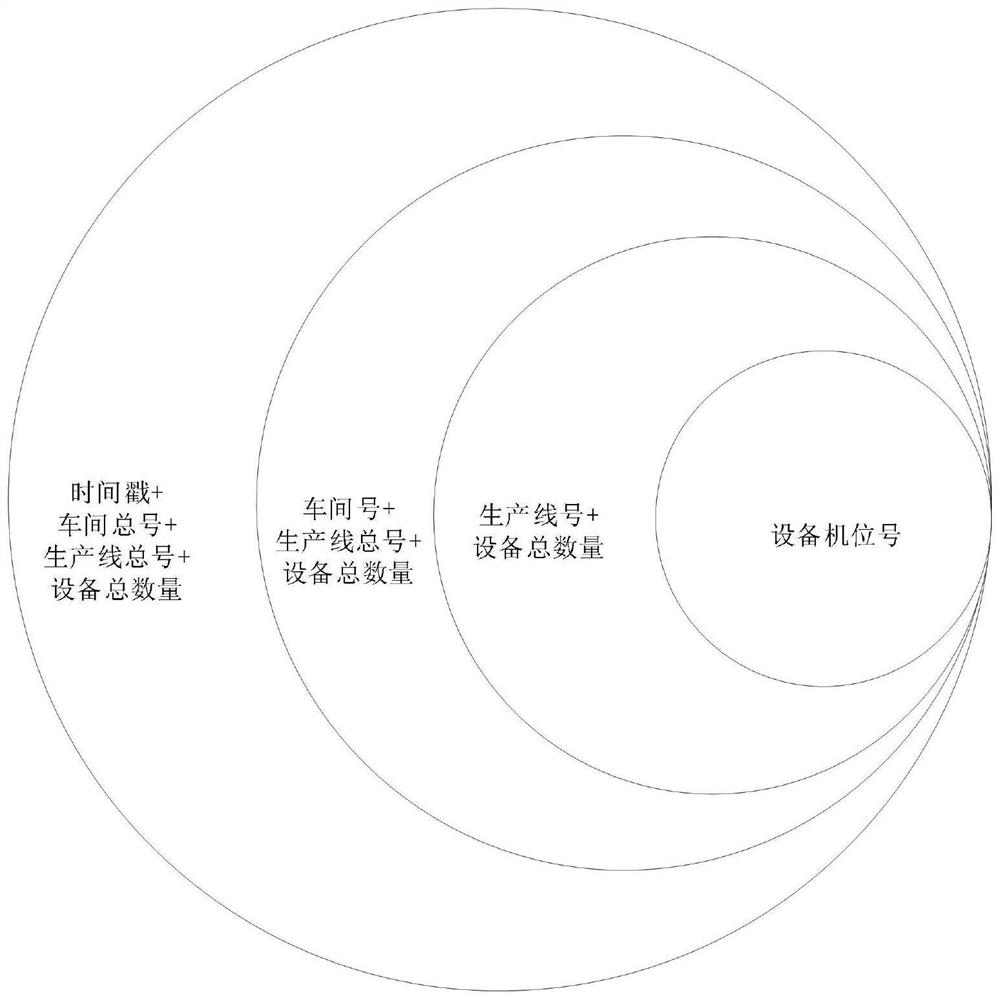
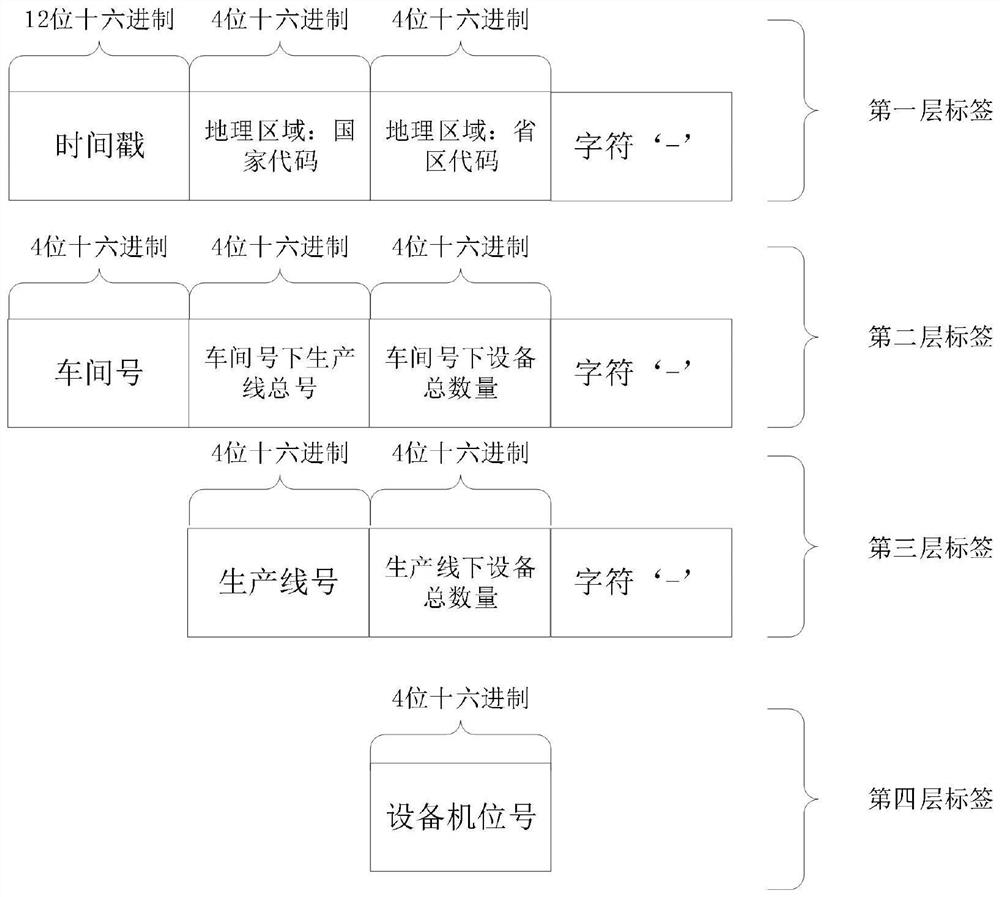
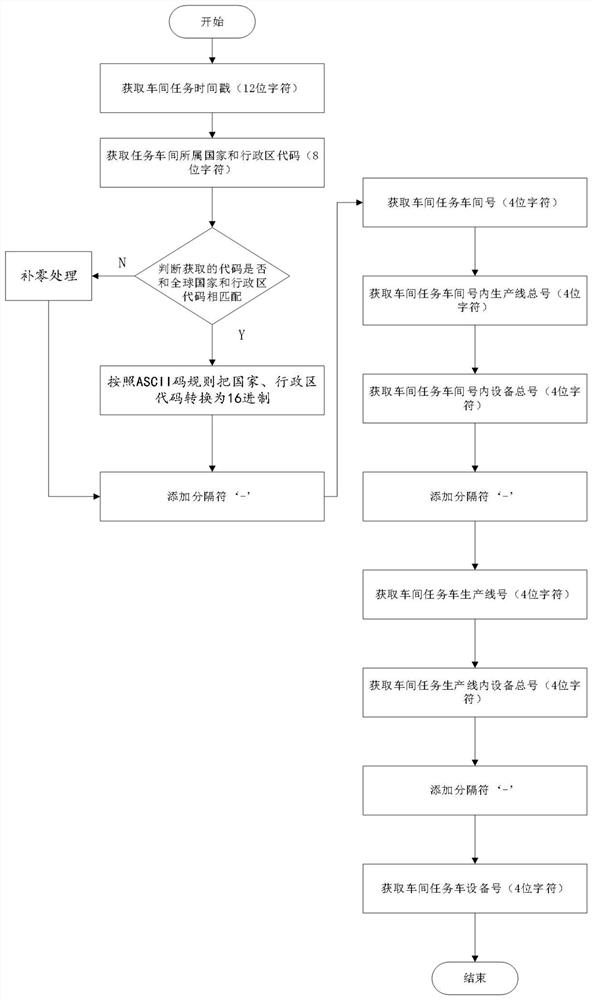
The invention discloses a workshop production task label configuration method based on industrial safety emergency management, and relates to the technical field of cloud computing containers. The method comprises the following steps: 1, obtaining workshop task data information, configuring a corresponding data label according to the workshop task data information, and adding a separator; 2, obtaining workshop data of the workshop task, correspondingly configuring a data label according to the workshop data, and adding a separator; and 3, obtaining production data of the workshop task, configuring a corresponding data label according to the production data, and adding a separator. According to the workshop task label obtained through the industrial workshop production task configuration method using the cloud host, a user can conveniently and clearly know the timestamp, the geographic area, the workshop number, the total number of production lines in the workshop, the total number of equipment in the workshop, the production line number, the total number of equipment in the production line and the equipment number information, and therefore the workshop production efficiency is improved.
Owner:南京信大安全应急管理研究院有限公司
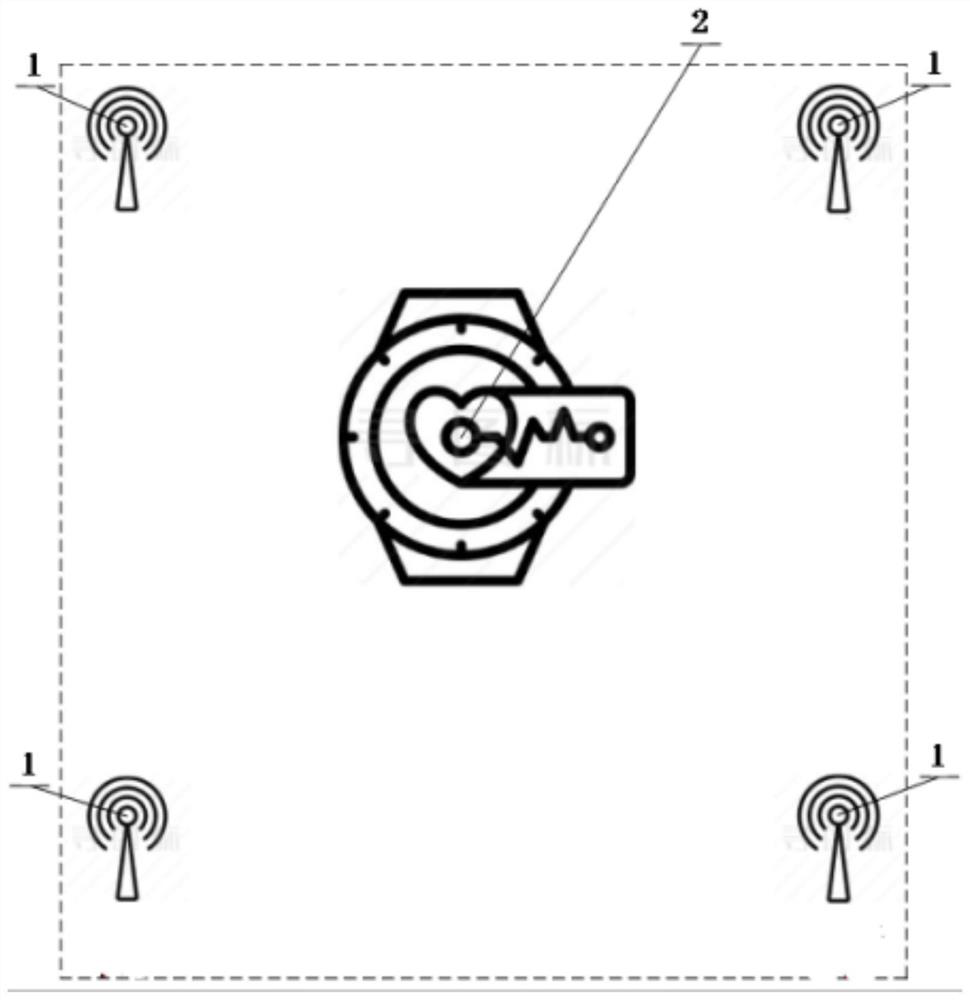
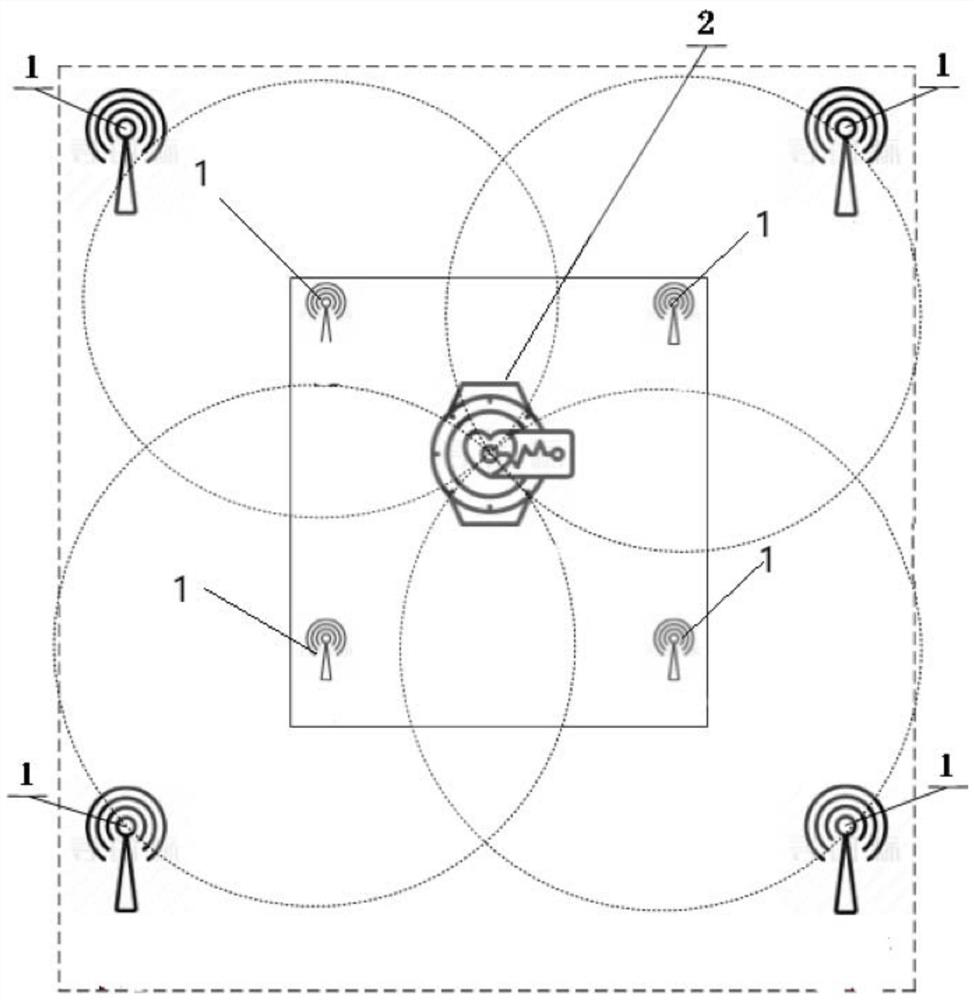
Security monitoring device based on wearable equipment and personal security method thereof
ActiveCN111711463AReduce system complexityReduce system costNear-field systems using receiversDiagnostic recording/measuringEmbedded systemReliability engineering
The invention discloses a security monitoring device based on wearable equipment and a personal security method thereof. The security monitoring device comprises a plurality of Bluetooth Beacon terminals and a Bluetooth scanning terminal. The Bluetooth scanning terminal captures, identifies and processes specific data messages periodically broadcasted by the plurality of Bluetooth Beacon terminals. Wearing person positioning is achieved through the Bluetooth receiving signal intensity and the positioning technology, and personal health and security monitoring of enterprise operation personnelis achieved through the NB-IOT communication technology, a heart rate and blood oxygen sensor, a motion step counting detection sensor, a body temperature sensor and other related technical means. Active alarm and abnormal state automatic alarm are realized through an SOS alarm module. The security monitoring device is combined with the development experience of wearable equipment, is wearable andmoves along with a wearer. The personal health safety of the wearer is brought into the security monitoring category, so that the combination of consumer life electronics and industrial security andprotection electronics is realized, and the personal security of the wearer is better guaranteed.
Owner:上海邑佰工业设备有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com