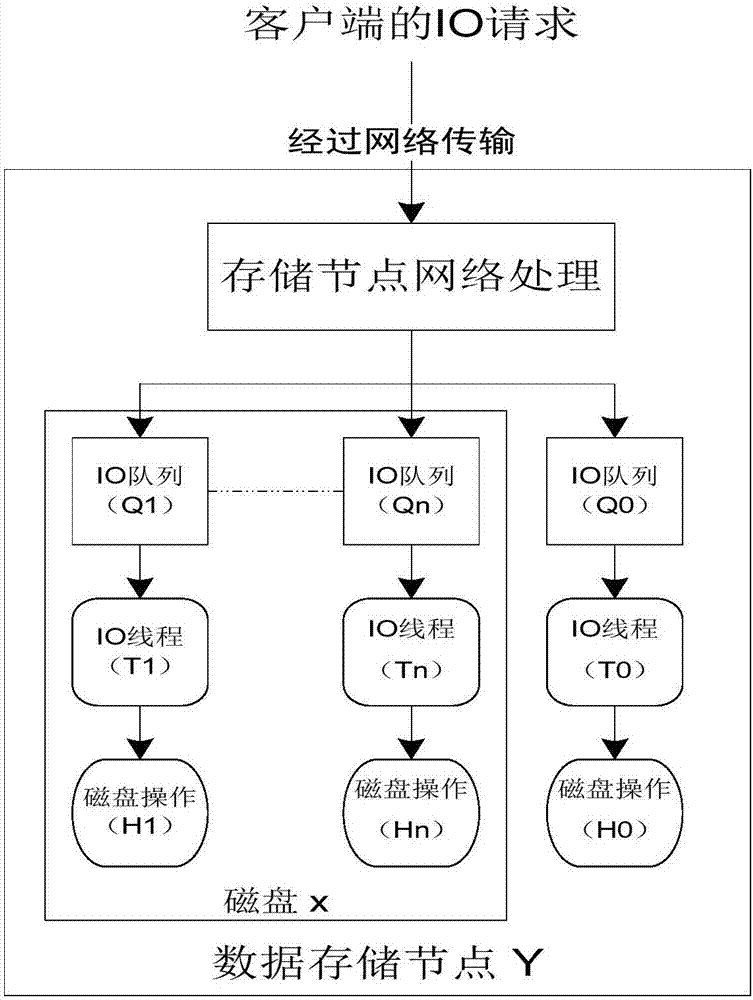
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
56results about How to "No access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
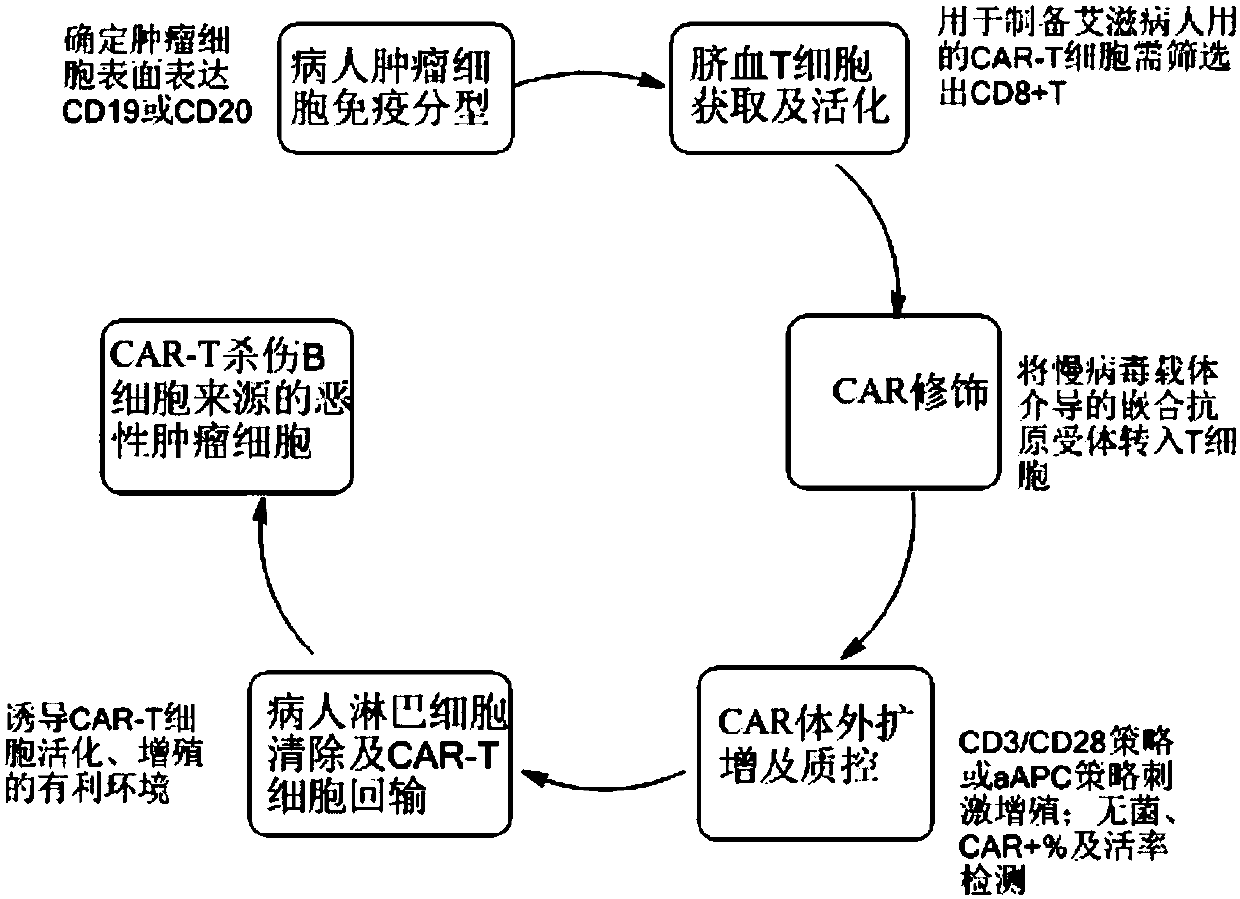
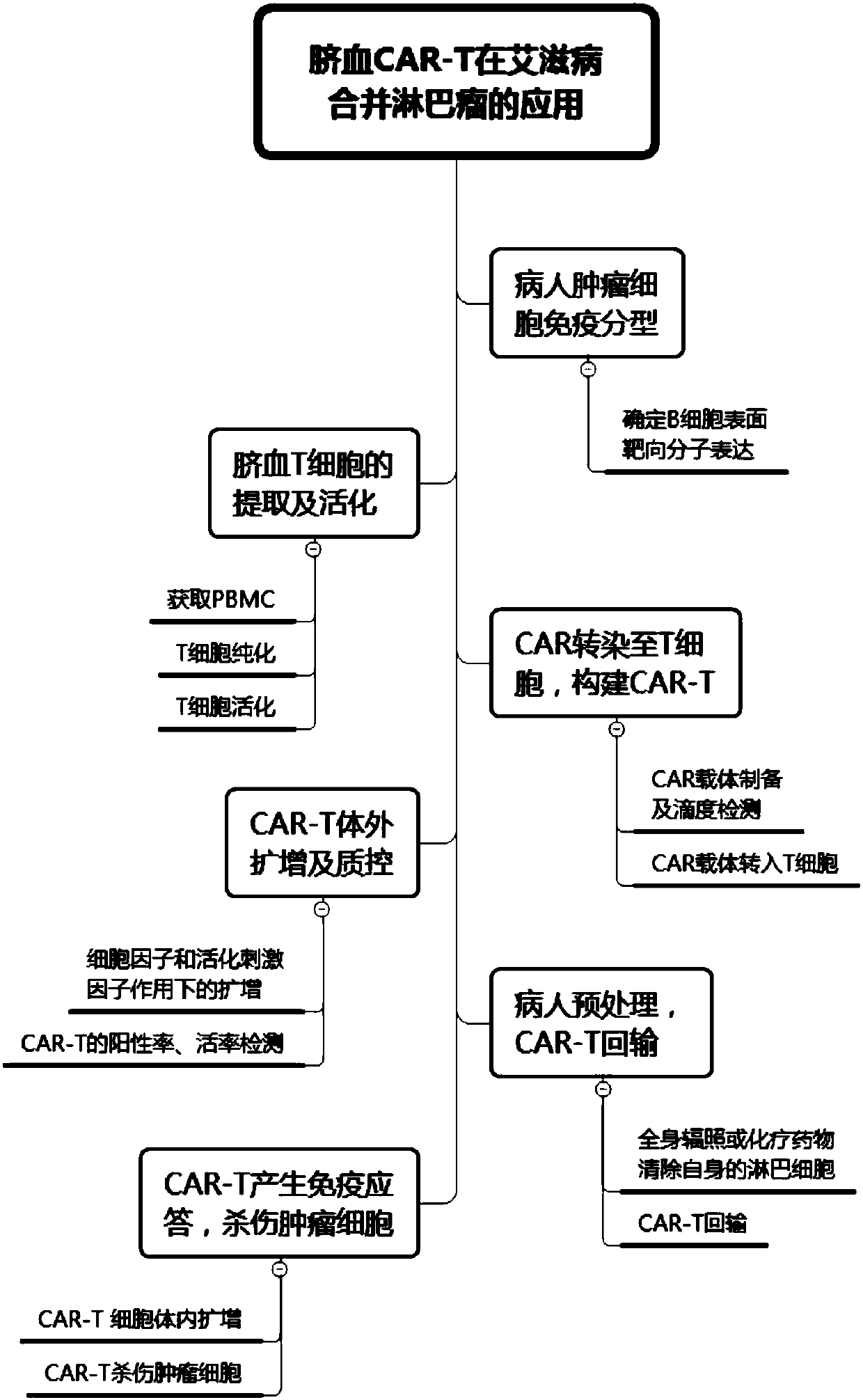
CAR-T cell for treating AIDS-associated lymphoma, and preparation method and application thereof
PendingCN107904259ALow storm riskSmall storm riskGenetically modified cellsAntiviralsAIDS-related lymphomaCord blood stem cell
The invention discloses a preparation method of a CAR-T cell for treating AIDS-related lymphoma. A CD8+ T cell is used to produce the CAR-T cell, and the CD8-T cell derives from a cord blood T cell. The method includes the following steps: preparing cord blood mononuclear cells from cord blood, removing tumors and other cells by using a human T cell purification kit to obtain T cells, and carryingout separation by using magnetic beads to obtain the CD8+ T cell; activating the CD8+ T cell by using an appropriate medium and appropriate stimulation conditions; transferring CAR to the CD8+ T cellby using lentivirus to prepare the CAR-T cell; and amplifying the CAR-T cell in vitro by using cytokines and activating stimulators to achieve the desired effective dose. The invention also relates to the CAR-T cell prepared by the method, and an application thereof. The CAR-T cell prepared in the invention has a good cell activity and a high proliferation speed, and reduces the attack risk of GVHD; and only the CD8+T cell of the umbilical blood T cells of AIDS patients is used to prepare the CAR-T cell for, so the risk of input CAR-T infected with in-vivo HIV is reduced.
Owner:SHANGHAI LONGYAO BIOTECH CO LTD
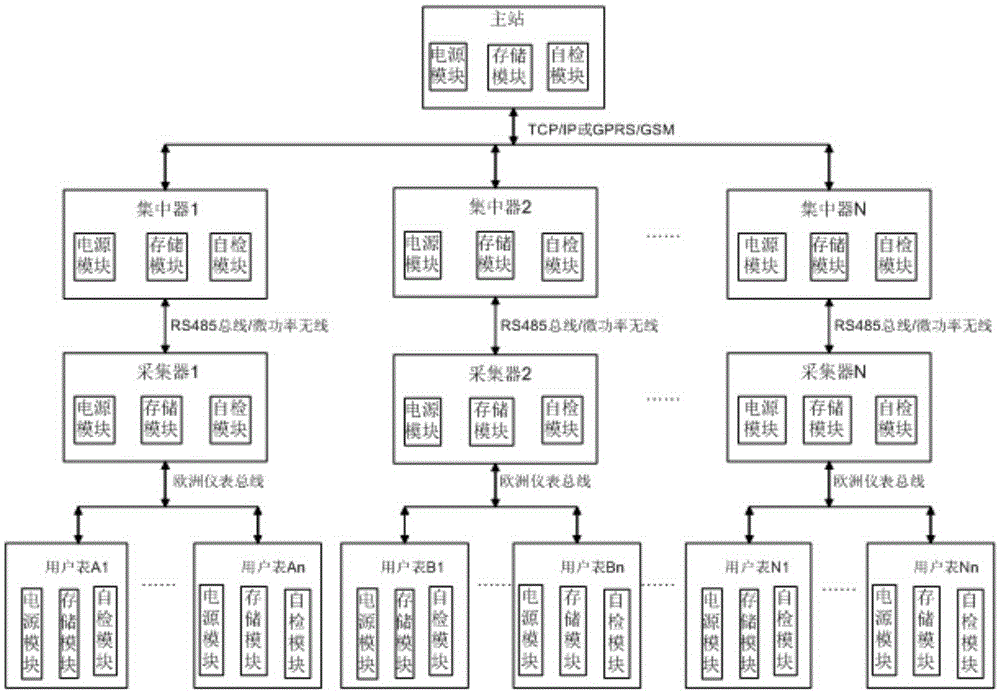
Binary channel communication remote meter reading monitoring and analysis system
InactiveCN105427571ANo AccessImprove anti-interference abilityElectric signal transmission systemsNetwork topologiesVIT signalsDirect reading
The invention provides a binary channel communication remote meter reading monitoring and analysis system. The system is characterized by comprising a user meter, a collector, a concentrator and a master station. Data are exchanged between the user meter and the collector through a Europe instrument bus. Data are exchanged between the collector and the concentrator through an RS485 bus or a micropower wireless channel. Data are exchanged between the concentrator and the master station through a GPRS / GSM or TCP / IP network. The system has the advantages that the binary channel communication scheme enables signal transmission not to be limited and interfered by the landform, building blocking and other factors, the transmission speed is high, real-time performance is high, data are safe, and interference resistance is high; micropower wireless channels are independent from each other; various communication network models are formed through optimization and integration in a heterogeneous network mode, complementary advantages are obtained, and communication blind points are eliminated; direct reading intelligent meters are adopted in the whole system, and the data accuracy is 100%; each device has the storage function and the self-checking function.
Owner:CHONGQING SAIMING TECH CO LTD
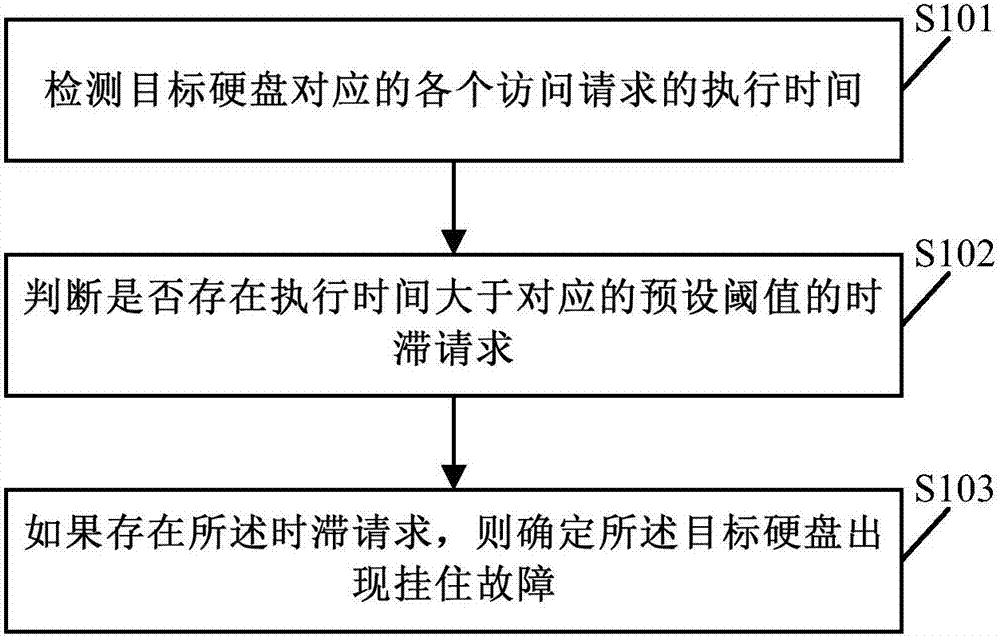
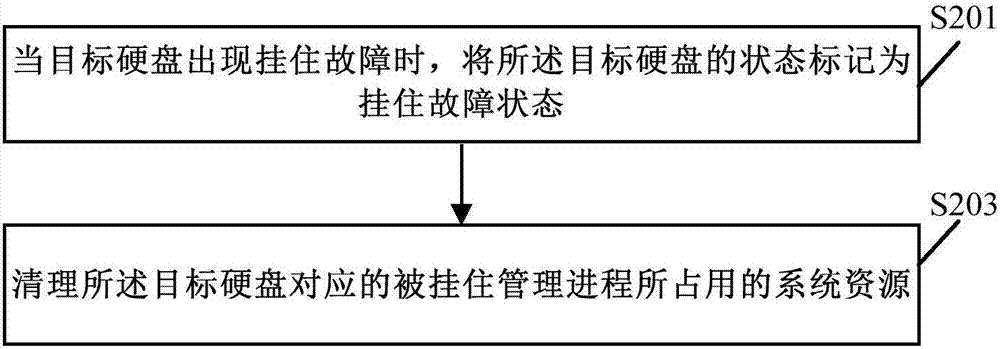
Hard disk hang-up fault detection and processing methods and apparatuses for distributed storage system
InactiveCN107273231AFind faults in timeDoes not affect production costsHardware monitoringNon-redundant fault processingComputer engineeringDistributed memory systems
The invention discloses hard disk hang-up fault detection and processing methods and apparatuses for a distributed storage system. Whether a target hard disk has a hang-up fault or not is judged by detecting executive time of an access request corresponding to the target hard disk, so that the hang-up fault of the target hard disk can be timely discovered; after it is discovered that the target hard disk has the hang-up fault, a faulted hard disk is prevented from being accessed again through a state tag on one hand and system resources occupied by the faulted hard disk are cleaned up on the other hand, so that other processes can reallocate and apply the system resources, negative influence possibly caused by the hang-up fault of the hard disk is reduced, and the purpose of stopping loss is achieved. According to the hang-up fault detection and processing schemes provided by the methods and the apparatuses, a detection tool can be provided without depending on a hard disk manufacturer, new hardware does not need to be added to the hard disk, and no manual intervention is needed, so that the simplicity and easiness are achieved, and the production and use costs of the hard disk are not influenced.
Owner:ALIBABA GRP HLDG LTD
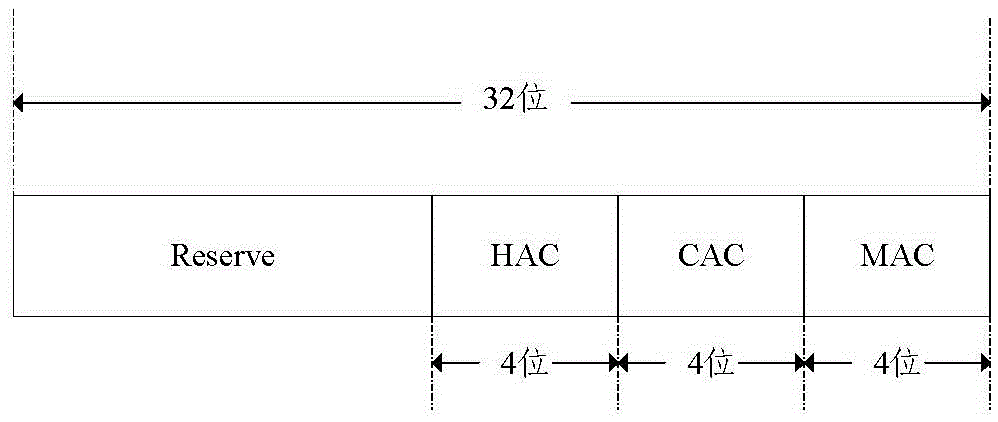
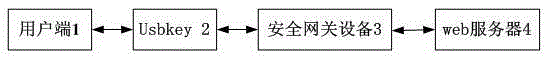
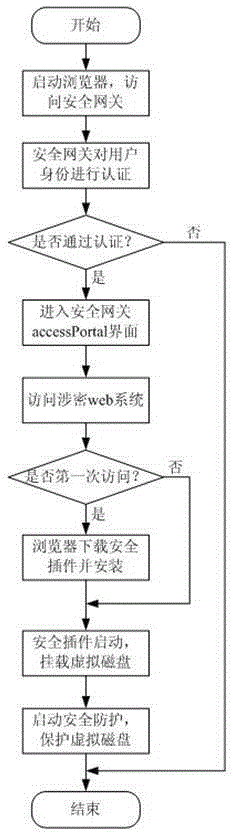
Traceless access controlling method and device based on protection of visual magnetic disc
ActiveCN103218573AProtection securityAvoid safety hazardsDigital data protectionInternal/peripheral component protectionWeb serviceTransfer procedure
The invention provides a traceless access controlling method and a device based on protection of a visual magnetic disc. The traceless access controlling method and the device based on protection of the visual magnetic disc are characterized in that a usbkey is used for setting up a visual magnetic disc in a system of a user terminal. A safety gateway device with a safety plug-in board is arranged between the user terminal and a web server. The usbkey is used for identifying a user identity by accessing a classified web system. The visual magnetic disc is mounted on the safety plug-in board to set up a visual accessing space. Files in the visual accessing space are oriented again to the visual magnetic disc. According to the traceless access controlling method and the device based on protection of the visual magnetic disc, only a user is allowed to access the files in the visual magnetic disc. Other progresses in the system are forbidden from accessing user files in the visual magnetic disc so that safety of the files in a transmission process is ensured and safety of local files of the user is ensured.
Owner:上海海加网络科技有限公司
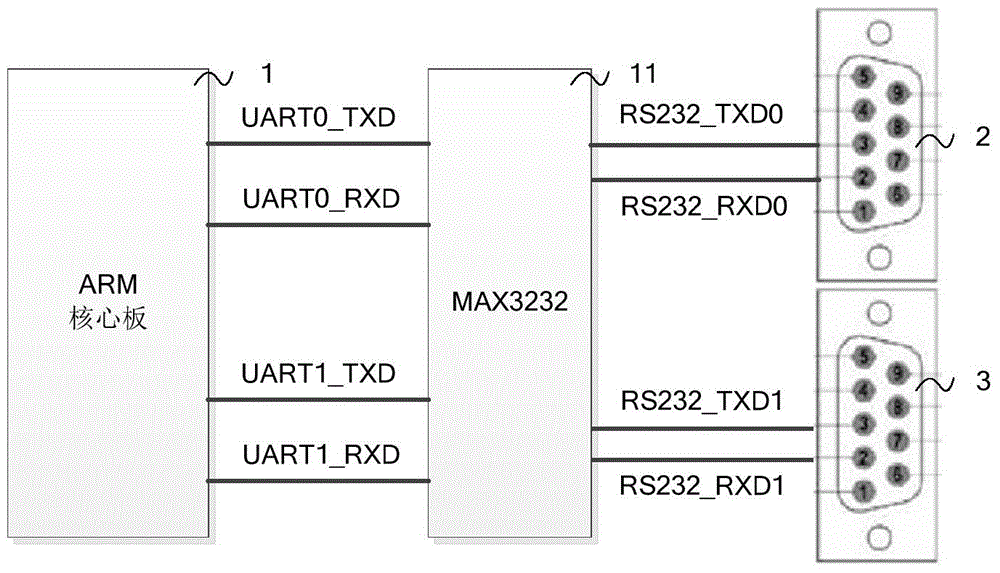
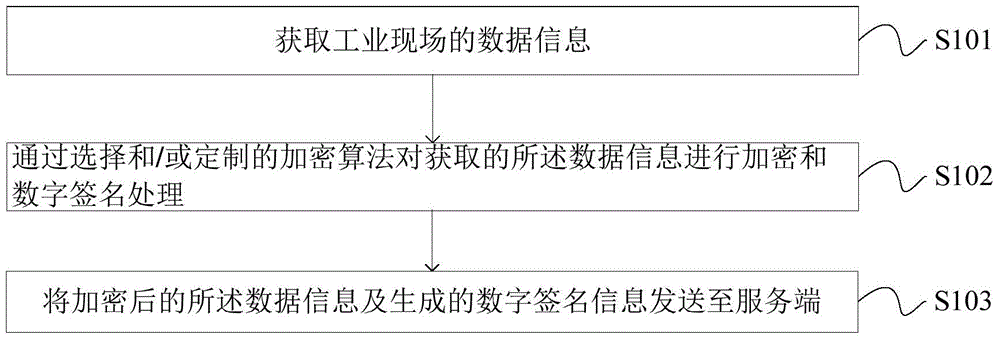
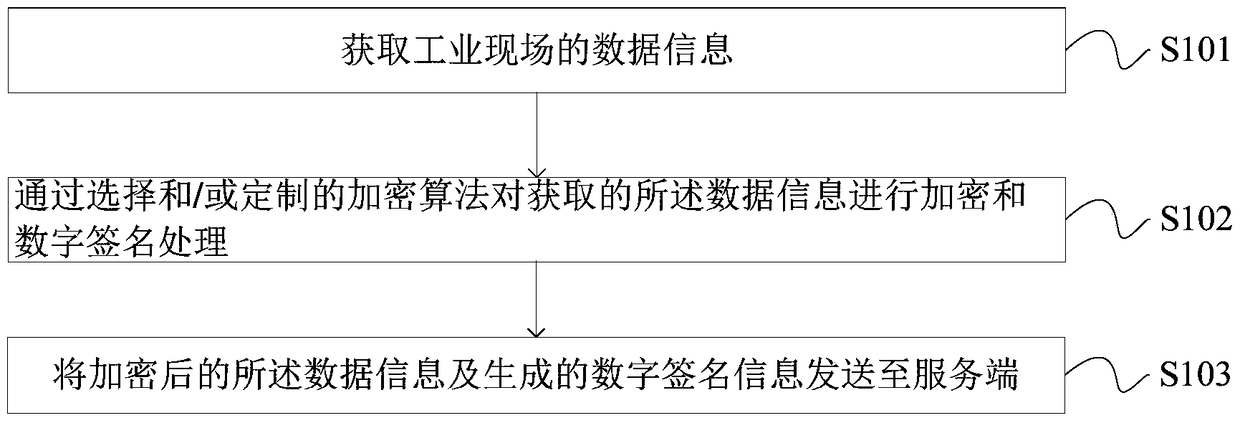
Communication method and device of industrial security gateway based on embedded system
ActiveCN104539573AImprove securityNo AccessUser identity/authority verificationIndustrial securityData information
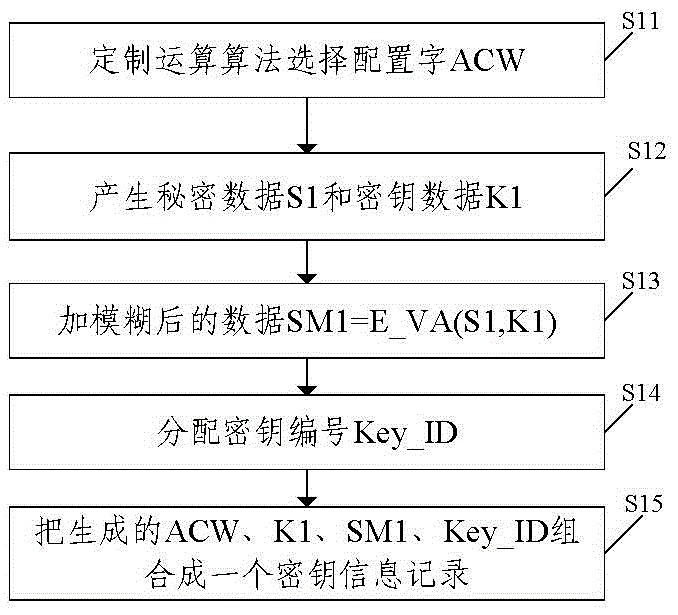
The invention provides a communication method and device of an industrial security gateway based on an embedded system, and aims to enhance the security of data transmission in an industrial control network. The method comprises the following steps: acquiring data information of an industrial field; performing encryption and digital signature processing on the acquired data information through a selected and / or customized encryption algorithm; and transmitting the encrypted data information and generated digital signature information to a server side. The device comprises an acquisition unit for acquiring the data information of the industrial field, an encryption unit for performing encryption and digital signature processing on the acquired data information through the selected and / or customized encryption algorithm, and a first transmission unit for transmitting the encrypted data information and generated digital signature information to the server side. The communication method and device are suitable for the technical field of industrial automation information security.
Owner:UNIV OF SCI & TECH BEIJING
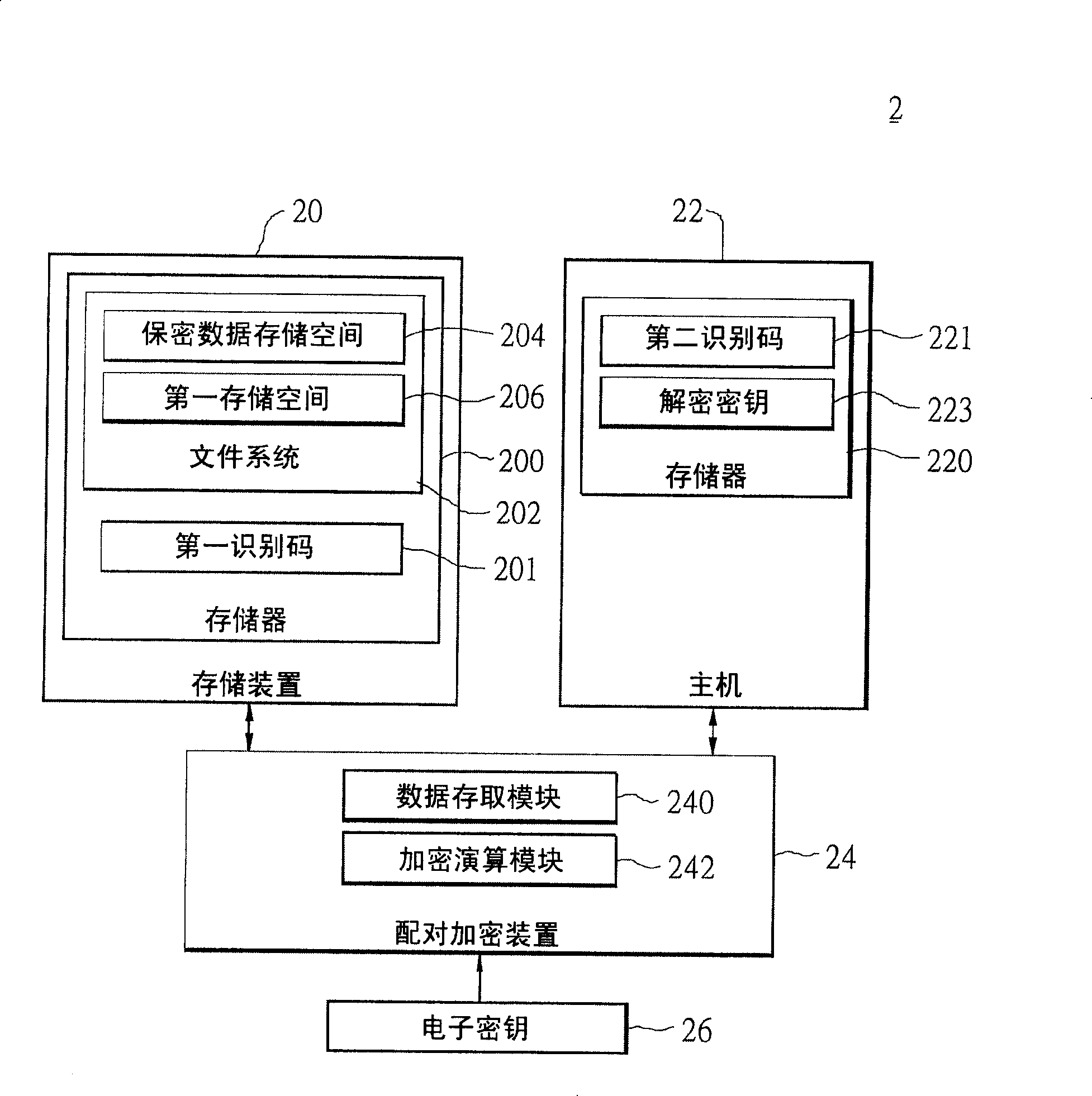
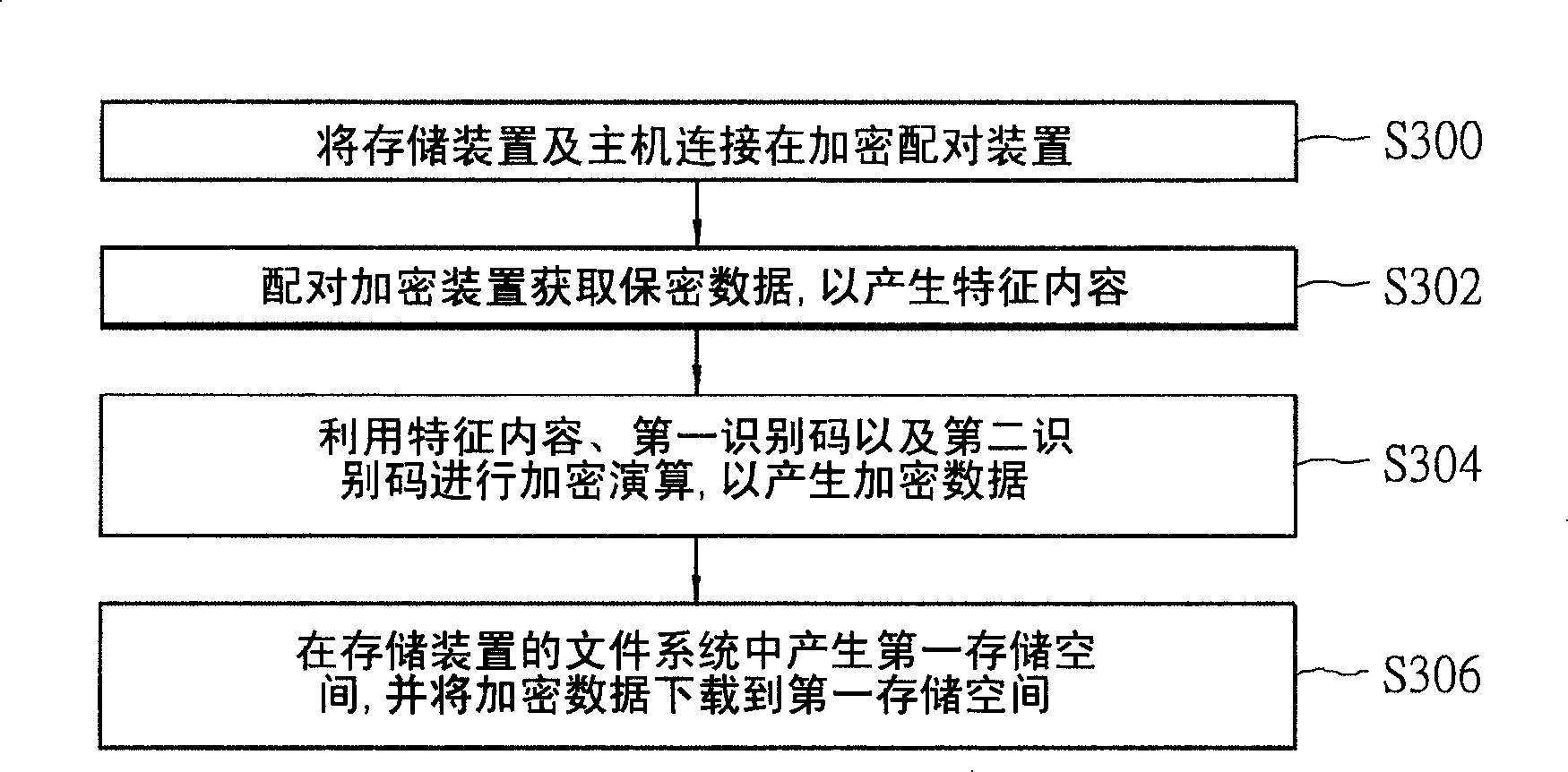
Security method and system as well as correlative pairing enciphering system thereof
InactiveCN101226507AAccess prohibitedNo accessUnauthorized memory use protectionInternal/peripheral component protectionData providerFile system
The invention relates to a security method for controlling the access of host on memory device, wherein the memory device comprises a memory storing a first recognition code and a file system, the structure of the file system is matched to store secure data and a first memory space. The host pre-stores a second recognition code. The inventive security method comprises sending the data of the first memory space to the host, while the first memory space is generated by match security program, decrypting the data in the first memory space to generate a decrypt data, judging the correct of the decrypt data that checks if the decrypt data meets the first recognition code and security data, referring the correct of the decrypt data, controlling the host to store the security data. The invention can improve the security of storing device to provide more security to data supplier and client.
Owner:UNIVERSAL SCI IND CO LTD
A method for rapid development of NFV
InactiveCN109144673ANo accessReduce copyTransmissionSoftware simulation/interpretation/emulationIp addressSoftware development
The invention discloses a method for rapidly developing NFV. The method includes the following steps: S1, byte stream processing: firstly, data packets transmitted from the outside are received, and the received data packets are quickly packed; S2, data packet processing: data IP address, format and size of the data packets received in S1 are analyzed through a data packet analysis module in a data packet processing system, and the data IP address, format and size of the data packets are analyzed, which relates to the technical field of software development. The NFV rapid development approach,including development environments and libraries, we abstract the packet operations in the network, including byte stream operations, package operations, state operations, by abstracting these operations, an our library is built, users can use these abstract operations to construct complex NFV functions, through using reference counters and intelligent pointer technology, fast execution, the useof Unique-type packets encapsulation, the number of packets copied is reduced, execution efficiency is improved, and a flexible development framework and API can be provided.
Owner:上海飞旗网络技术股份有限公司
Routing device for intelligently controlling user connection number, and application method
InactiveCN105871843AControl quantityReduce in quantityData switching networksNetwork connectionThe Internet
The invention discloses a routing device for intelligently controlling the user connection number, and an application method. The device comprises a user interface, a local authentication server and an internet interface; the user interface is used for connecting a user terminal, judging the type of the user terminal, and judging whether wired network connection or wireless network connection is executed according to the type of the user terminal; the local authentication server is connected to the user terminal, and used for receiving a networking request instruction sent by the user terminal and performing networking authentication of the user terminal requesting for networking; the local authentication server is also used for judging whether a user terminal, which does not access to an internet at the pre-determined time for wireless network connection, exists or not; if the user terminal exists, wireless network connection of the user terminal is disconnected; otherwise, judgment is continuously carried out; the local authentication server is also connected to the internet interface and used for opening an internet connection channel to the user terminal passing authentication; and the user terminal passing authentication is allowed to access to the internet.
Owner:广州指点网络科技有限公司
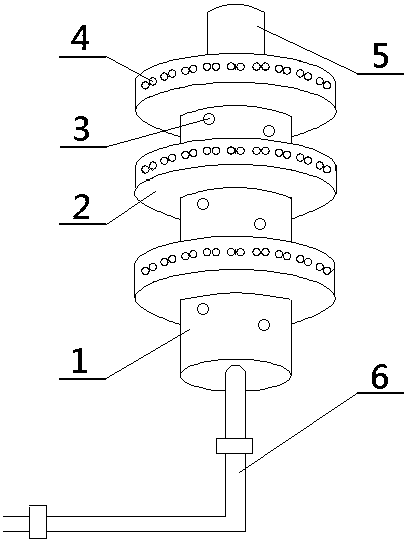
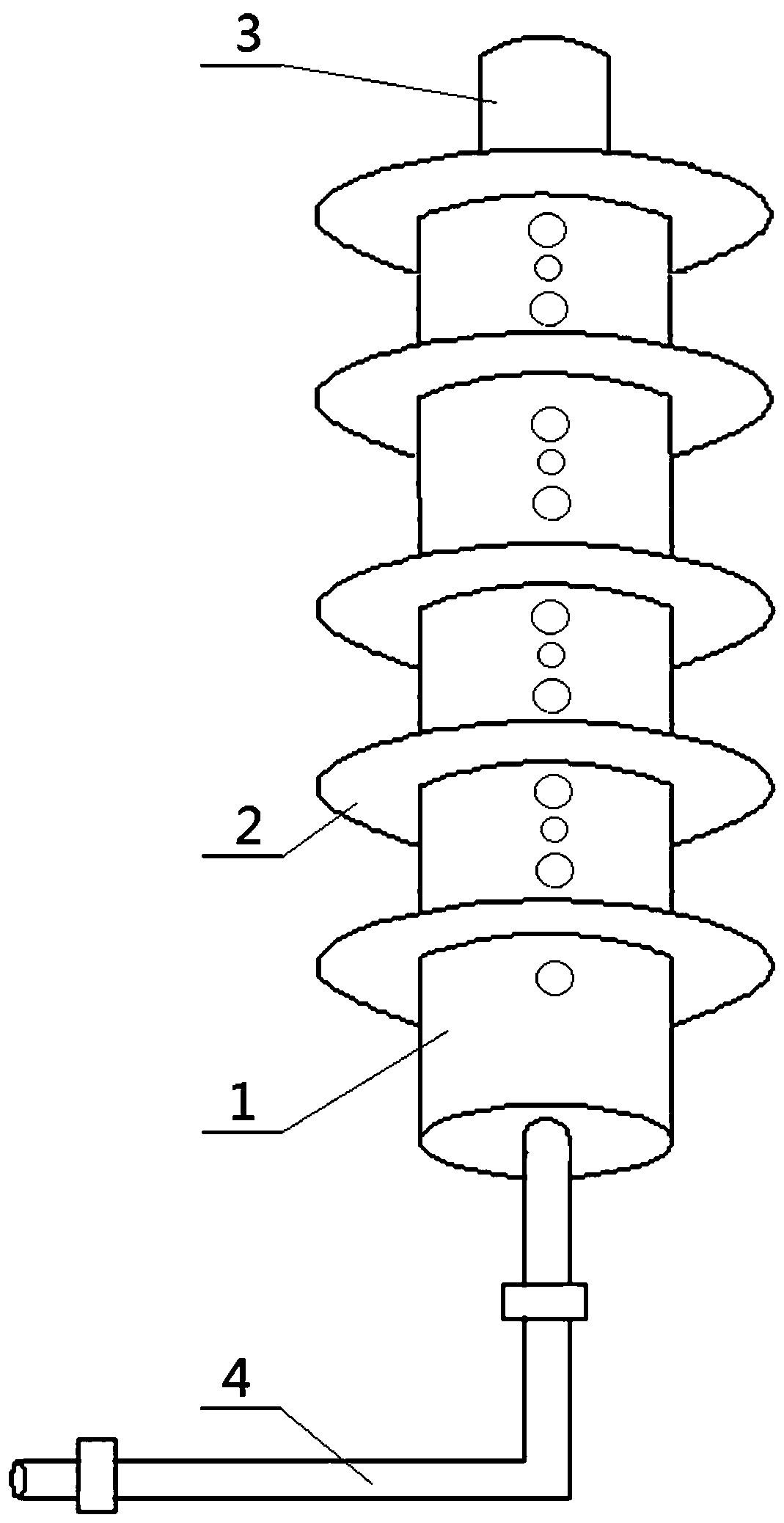
Zigzag sync compression arc extinction and lightning protection device of parallelly arranged arc extinction channels
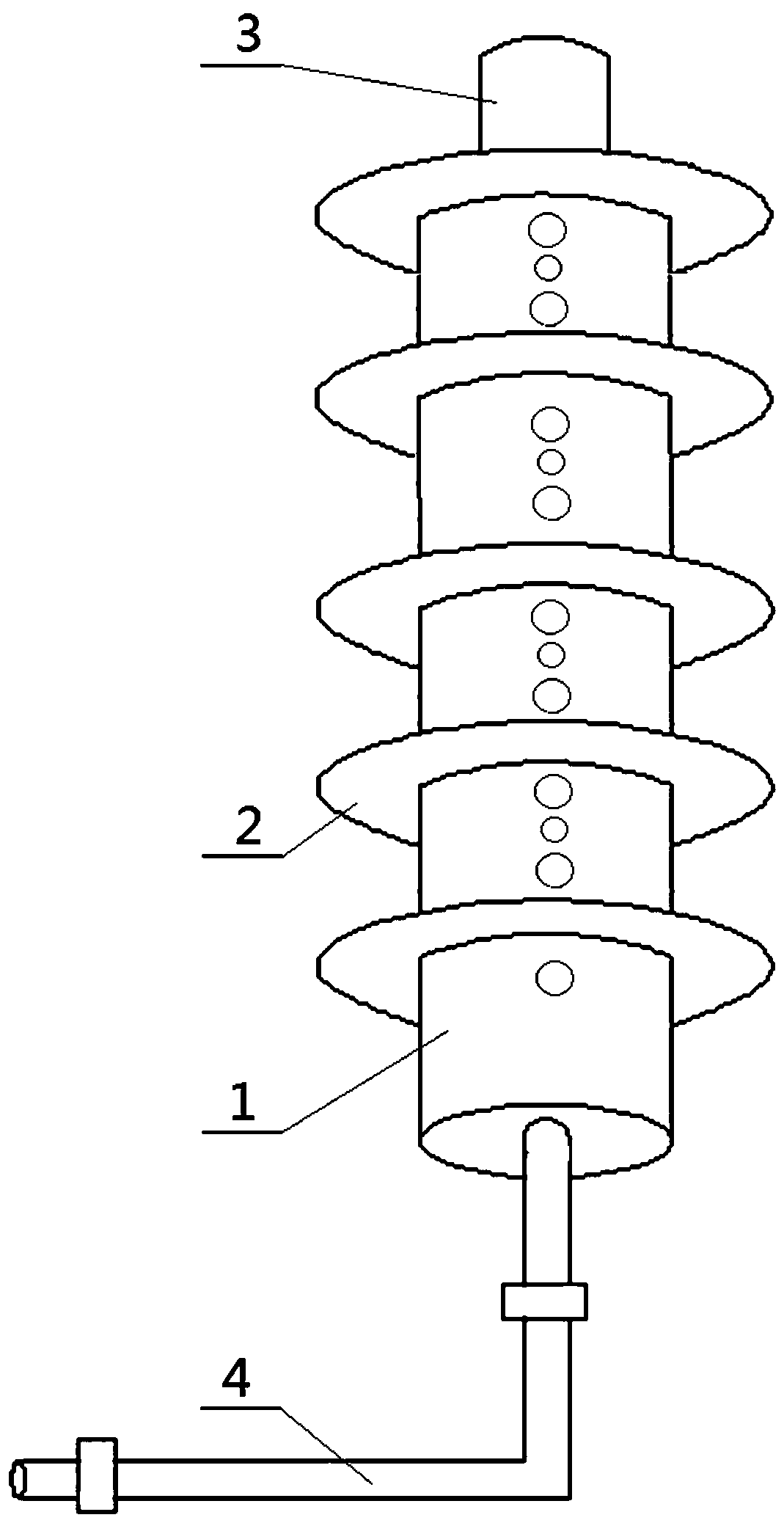
PendingCN107742559AAvoid damage to the lightning protection deviceRelieve pressureSpark gap detailsInsulatorsMeanderEngineering
The invention discloses a zigzag sync compression arc extinction and lightning protection device of parallelly arranged arc extinction channels. The zigzag sync compression arc extinction and lightning protection device comprises a lightning protection device body (1) and an arc striking electrode (3), wherein an arc extinction path composed of the several arc extinction channels parallelly arranged from top to bottom is arranged inside the lightning protection device body; arc extinction pipes (5) are placed in all the arc extinction channels, wherein the head end of the arc extinction pipe in the first arc extinction channel is electrically connected with the arc striking electrode (3), the tail end of the arc extinction pipe in the last arc extinction channel is electrically connected with a connecting hardware fitting (4), and the ends of every two adjacent arc extinction pipes are connected through a three-way pipe (6) and two T-shaped arc guide pipes (9); the transverse ends andthe longitudinal ends of the T-shaped arc guide pipes (9) are embedded in the arc extinction pipes (5) and the three-way pipes (6) respectively. The zigzag sync compression arc extinction and lightning protection device is simple in structure, reasonable in design, higher in arc extinction capability and stable and reliable in work.
Owner:王巨丰
Method for controlling access of clients to a service in a cluster environment
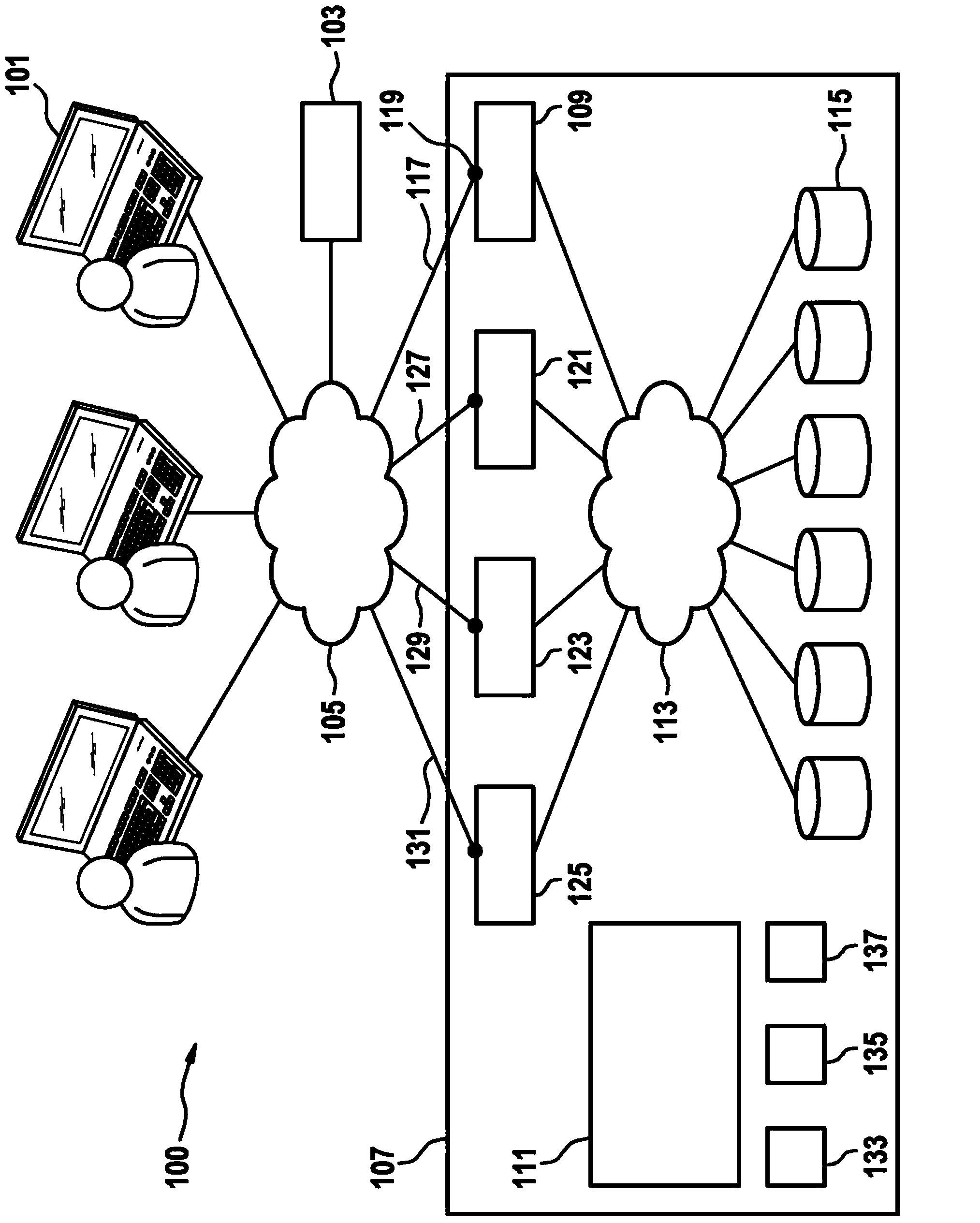
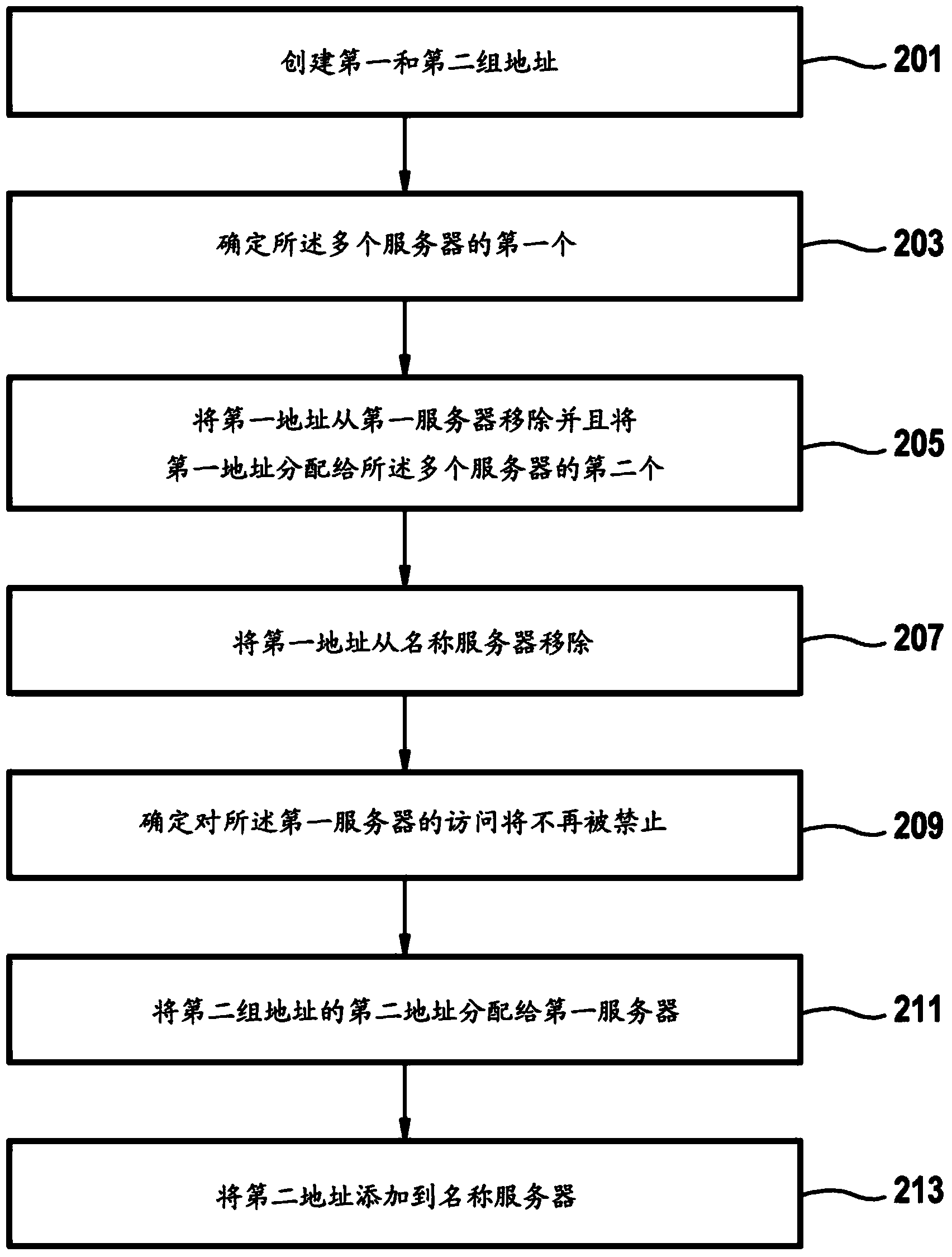
ActiveCN104137085AImprove usabilityNo AccessError detection/correctionTransmissionName serverEngineering
First, second, and third sets of addresses are created. The first set includes addresses registered in a name server; both the second and third sets include addresses not registered in the name server and that are disjoint. A first address of a first server that has failed and to which access is to be prohibited is moved from the first to the third set., is removed from the first server, assigned to a second server, and removed from the name server. Usage parameter values of the first address are monitored to determine whether at least one is below a value. If so, the first address is removed from the second server and moved from the third to the second set. Upon access to the first server no longer being prohibited, a second address of the second set is assigned to the first server and added to the name server.
Owner:IBM CORP
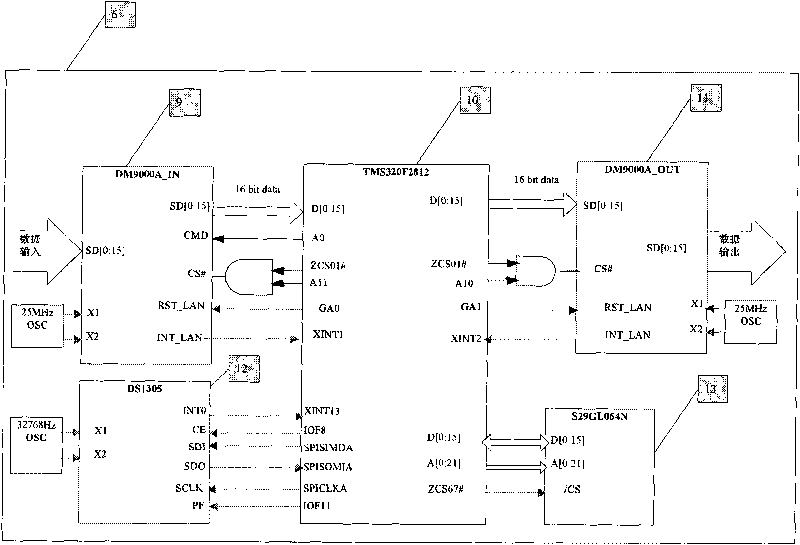
Computer network monitoring system using chip TMS320F2812
InactiveCN101741636AGuaranteed circulationAchieve viewData switching networksComputer network technologyThe Internet
The invention discloses a computer network monitoring system using a chip TMS320F2812 and relates to a network monitoring system, belonging to the technical field of computer networks. The invention aims to solve the problem of providing the computer network monitoring system using the chip TMS320F2812. The computer network monitoring system comprises a personal computer 5, a computer network supervision system 6, an internet interface 7 (such as an ADSL (asymmetrical digital subscriber loop) modem) and an internet 8; the input end of the computer network supervision system 6 is connected with the personal computer 5; the output end of the computer network supervision system 6 is connected with the input end of the internet interface 7; and the output end of the internet interface 7 is connected with the internet 8. The invention can ensure normal flow of network data, provide the identity authentication function, can control net play time, record access websites and provide the blacklist function.
Owner:CHANGCHUN INST OF OPTICS FINE MECHANICS & PHYSICS CHINESE ACAD OF SCI
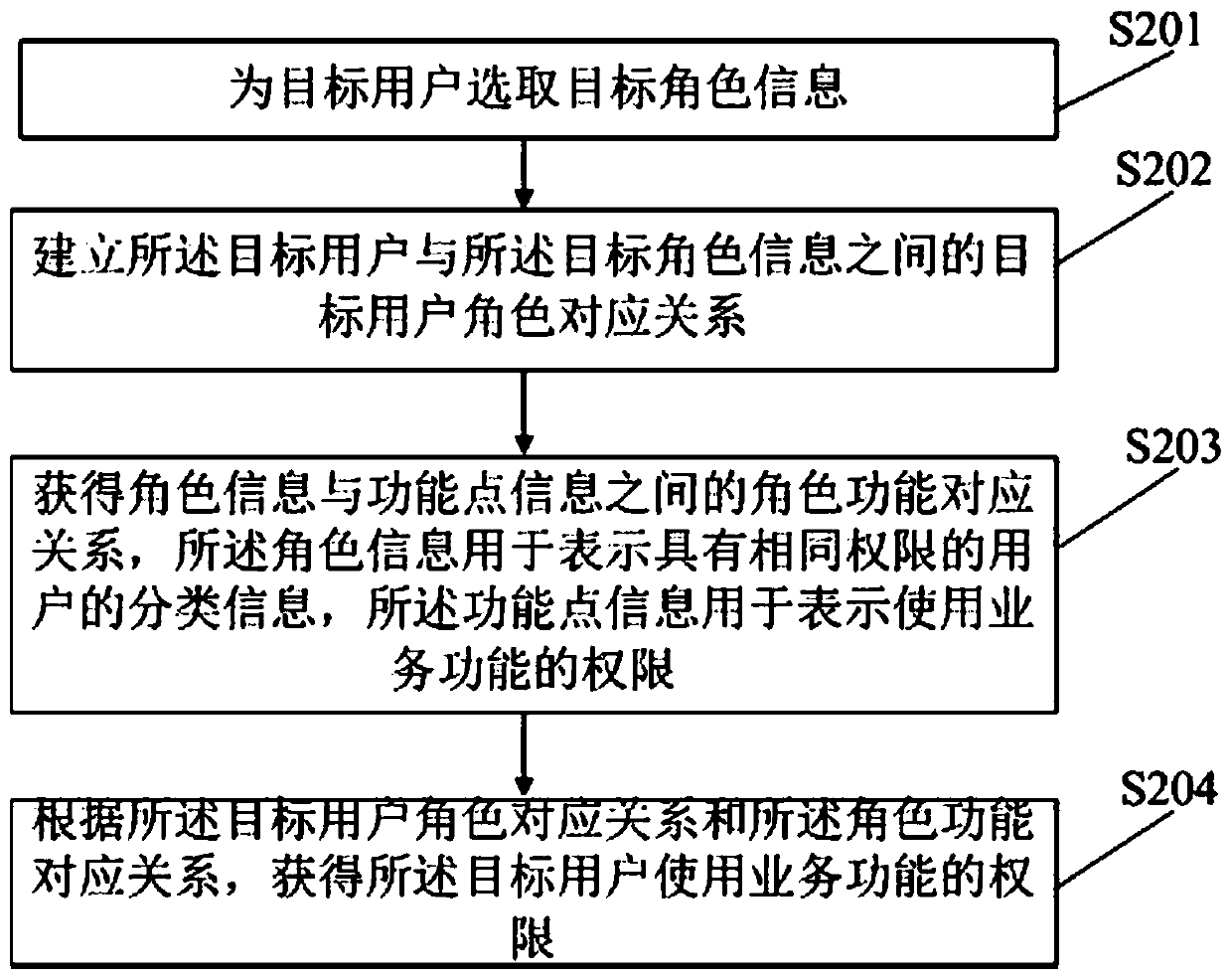
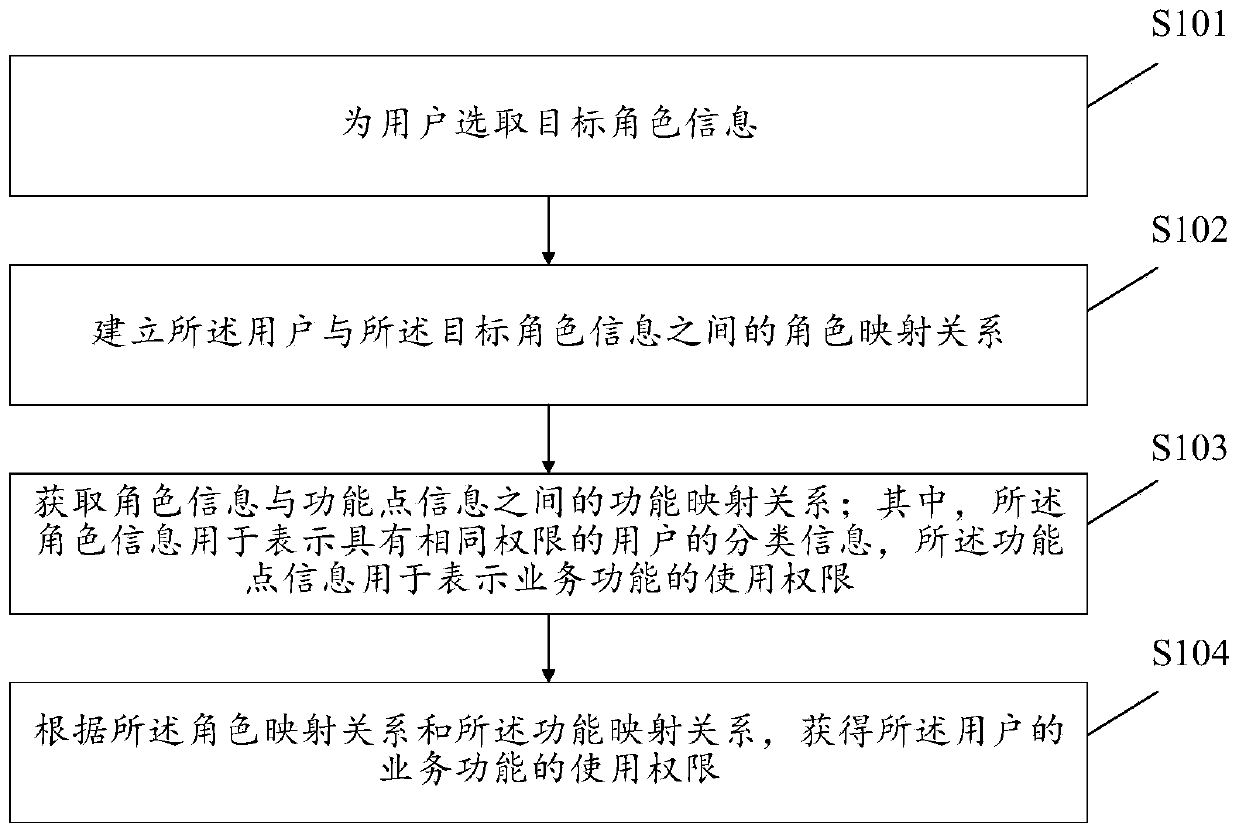
Permission processing method and device and permission control method and device
InactiveCN110457629ANo AccessFlexible permission control methodDigital data authenticationWebsite content managementRole functionAuthority control
The invention discloses an authority processing method. The method comprises the steps of selecting target role information for a target user; establishing a target user role corresponding relationship between the target user and the target role information; obtaining a role function corresponding relationship between role information and function point information, with the role information beingused for representing classification information of users having the same permission, and the function point information being used for representing permission of using a service function; and according to the role corresponding relationship of the target user and the role function corresponding relationship, obtaining the permission of the target user to use the service function. By adopting themethod, authority control with finer authority granularity is provided.
Owner:KOUBEI SHANGHAI INFORMATION TECH CO LTD
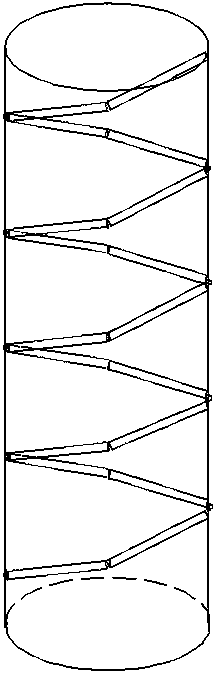
Deflection sync compression arc extinguishing and lightning protecting device
InactiveCN107732659AImprove arc extinguishing performanceWith basic arc extinguishing functionSpark gap detailsInsulatorsEngineeringInjection air
The invention discloses a meandering synchronous compression arc extinguishing and lightning protection device, which comprises a main body of a lightning protection device and an arc striking electrode. The outer surface of the main body of the lightning protection device is provided with a skirt; The arc extinguishing path II composed of circular arrangement; the head end of the first arc extinguishing tube II in the skirt is electrically connected with the end of the arc extinguishing tube I in the main body of the lightning arrester above the skirt and closest to the skirt, and finally The end of one arc extinguishing tube II is electrically connected to the head end of arc extinguishing tube I in the main body of the lightning arrester below the skirt and closest to the skirt; the ends of two adjacent arc extinguishing tubes II are directly contacted or connected. Connected by connecting piece II; there is an air flow outlet channel II at the junction of two adjacent arc extinguishing tubes II, and the air flow outlet channel II extends to the outer surface of the skirt, that is, the outer surface of the skirt is provided with air flow Outlet II. The invention has the advantages of simple structure, reasonable design, stronger arc extinguishing ability and stable and reliable operation.
Owner:王巨丰
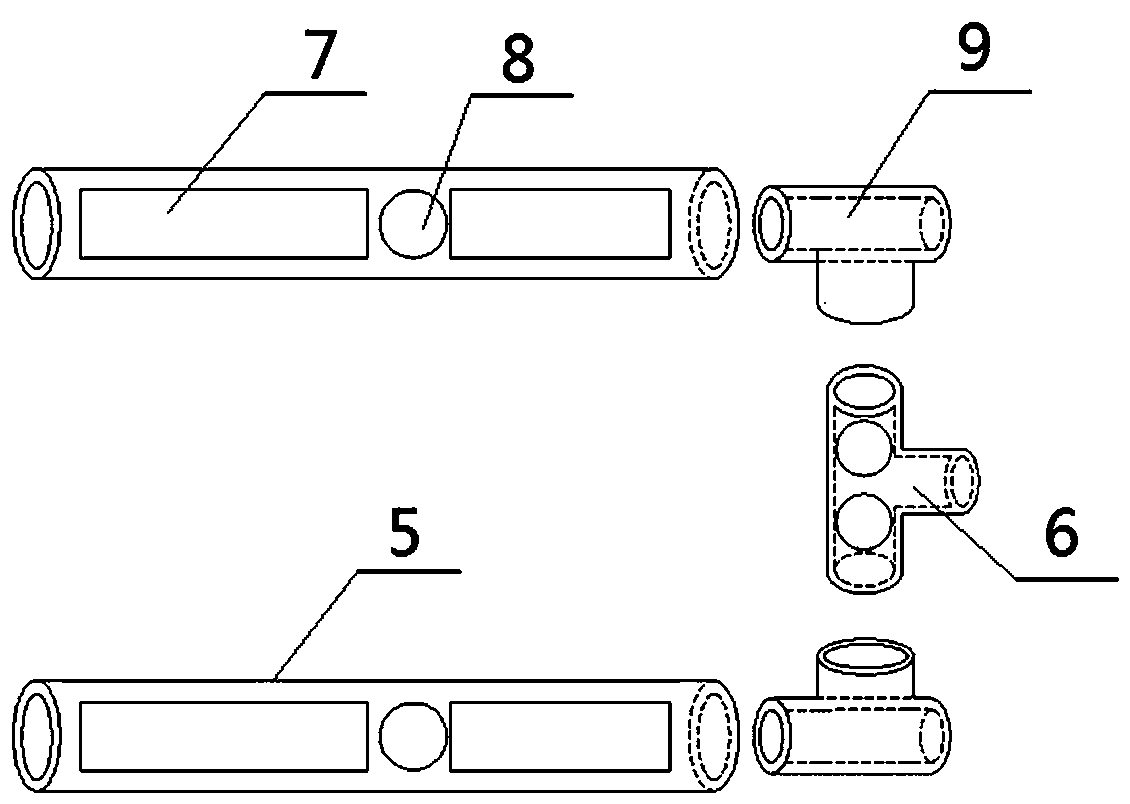
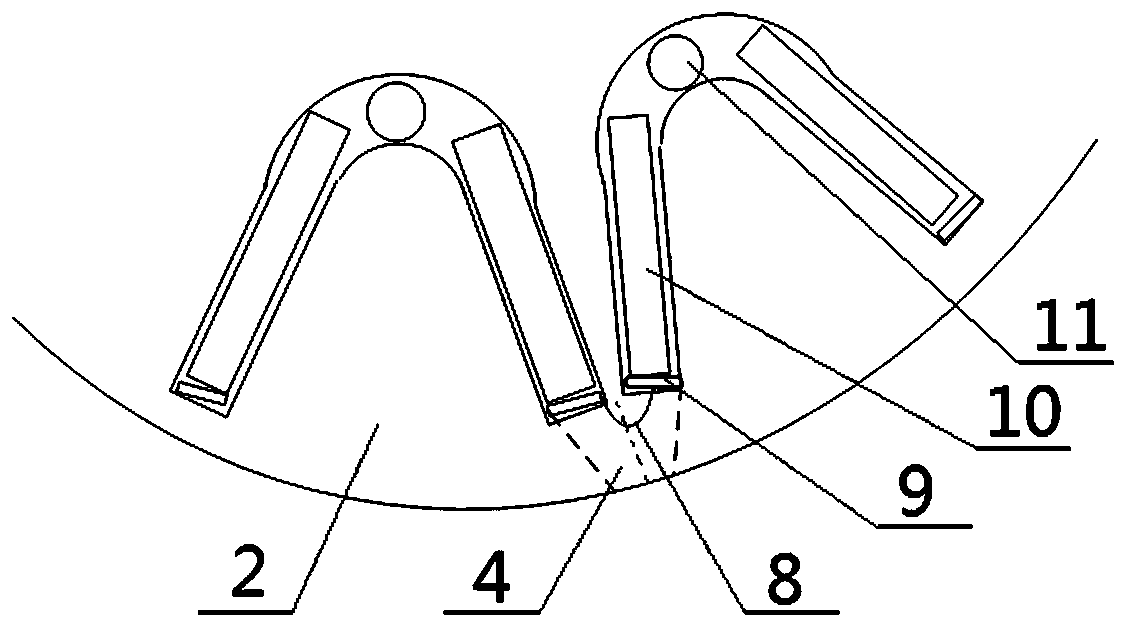
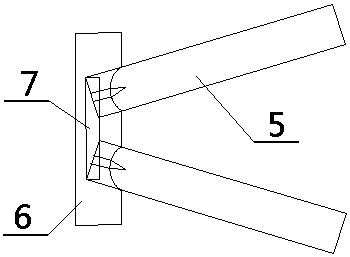
Deflection sync compression arc extinguishing and lightning protecting device with protection side
PendingCN107732661AAvoid burnsImprove arc extinguishing performanceSpark gap detailsInsulatorsStructural engineeringMechanical engineering
The invention discloses a deflection sync compression arc extinguishing lightning protection device, comprising a lightning protection device body (1) and an arc ignition electrode (3). The internal part of the lightning protection device body (1) is provided with an arc extinguishing path formed by a plurality of arc extinguishing channels arranged from top to bottom in a spiral manner. An arc extinguishing pipe (5) is disposed in each arc extinguishing channel. Two adjacent end parts of the arc extinguishing pipe at one side of the lightning protection device body (1), facing towards an insulator chain are connected through a casting ceramic block (6), and an iron nail base (7) is disposed in the ceramic block (6). The iron nail base (7) is provided with two iron nails, which respectively insert into the internal part of the arc extinguishing pipe. Two adjacent end parts of the other arc extinguishing pipes are connected through a t-branch pipe (9) and two arc-guiding electrode (8).The invention is advantageous in the structure is simple, design is reasonable, arc extinguishing capability is strong, and work is stable and reliable.
Owner:王巨丰
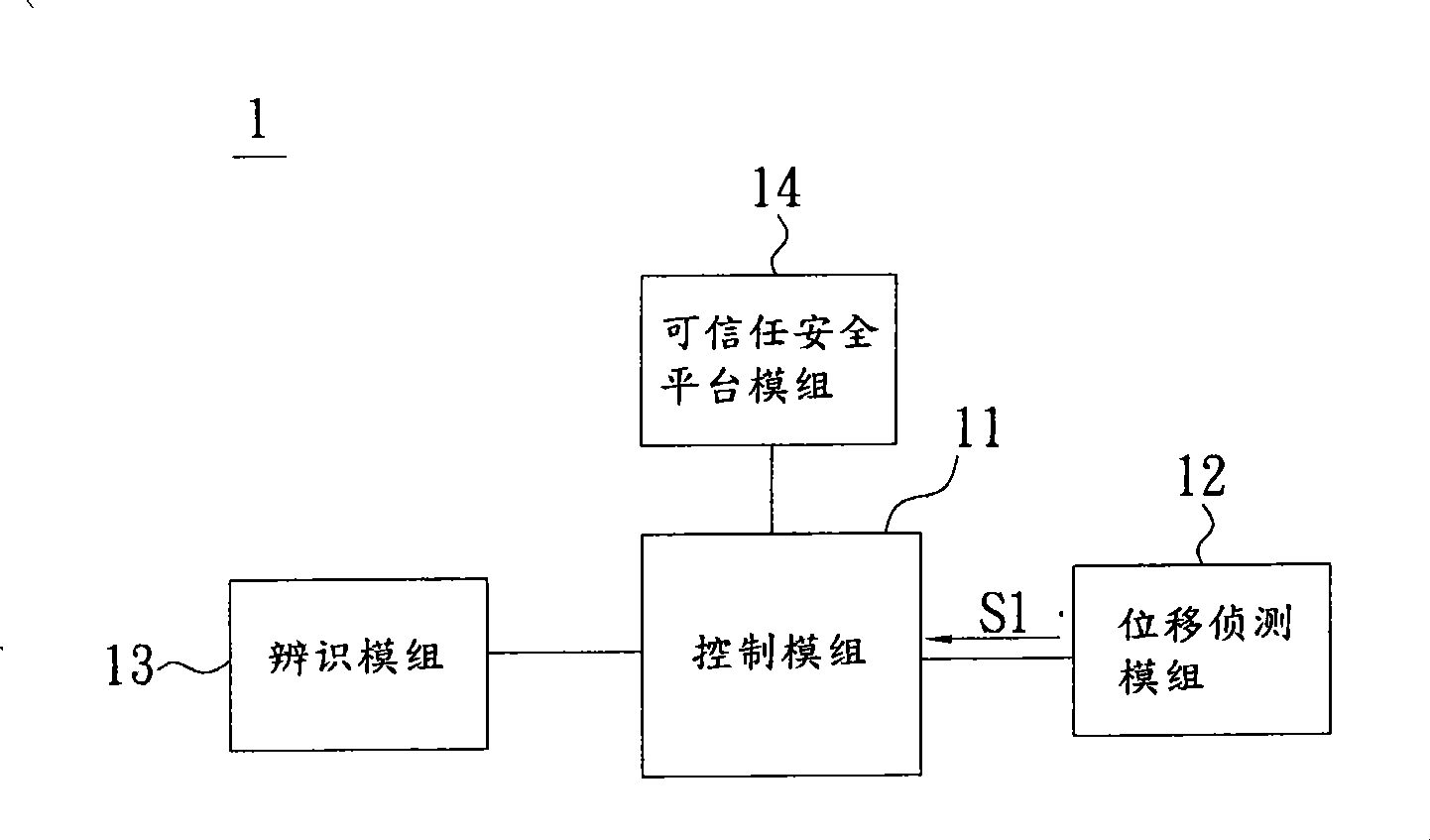
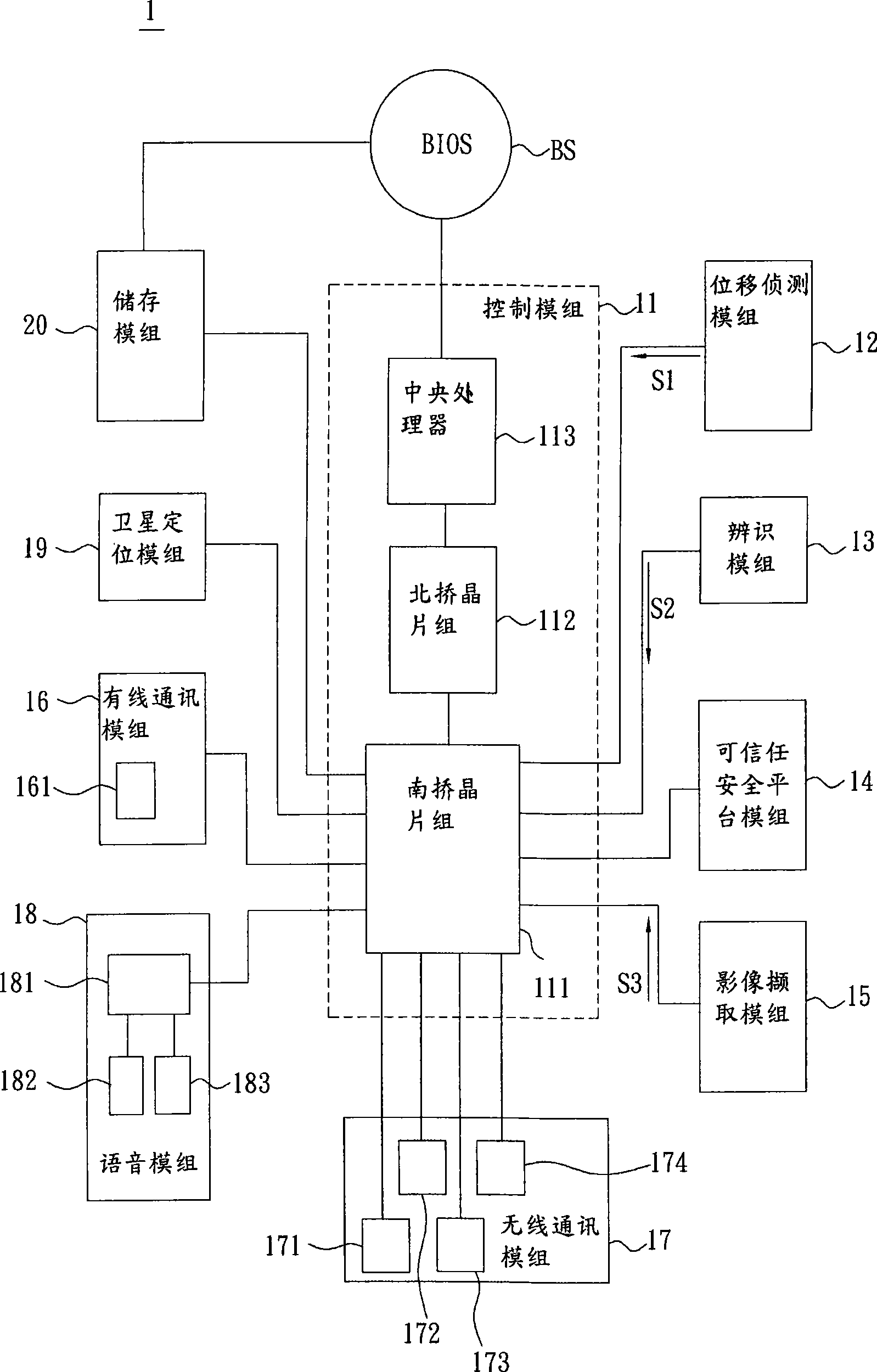
Portable computer with anti-theft function and control method thereof
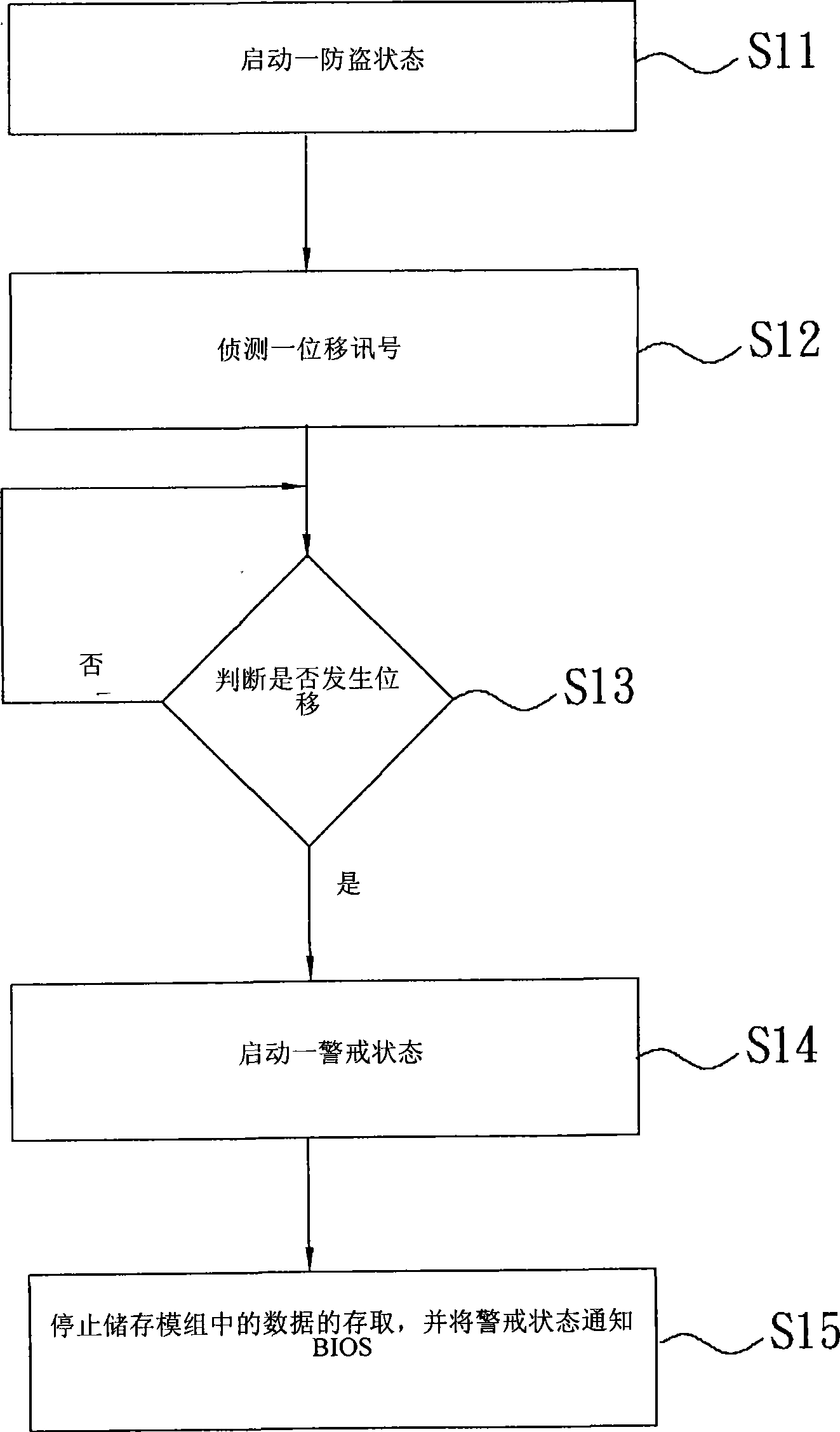
InactiveCN101414331ANo accessReduce lossesInternal/peripheral component protectionBurglar alarm by hand-portable articles removalMemory moduleAnti theft
The invention relates to a portable computer and a control method thereof; wherein, the portable computer is provided with a basic input and output system and a memory module; while the memory module stores a plurality of groups of data. The control method comprises the following steps: starting an anti-theft state; sensing a displacement signal under the anti-theft state so as to judge whether the portable computer generates displacement or not; starting a warning state when the portable computer is judged to generate displacement; and stopping the accessing of the data in the memory module and informing the warning state of the basic input and output system.
Owner:ASUSTEK COMPUTER INC
Data protection method and device
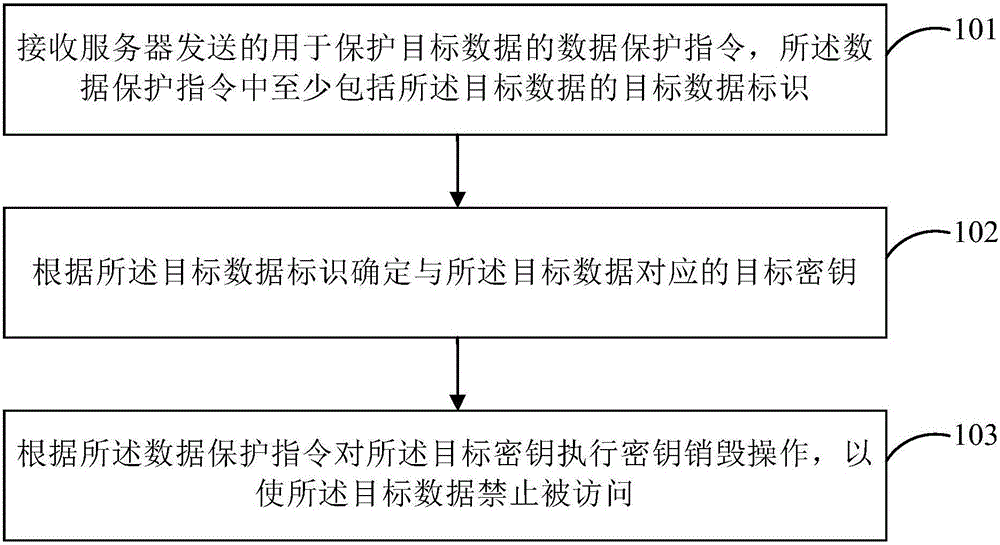
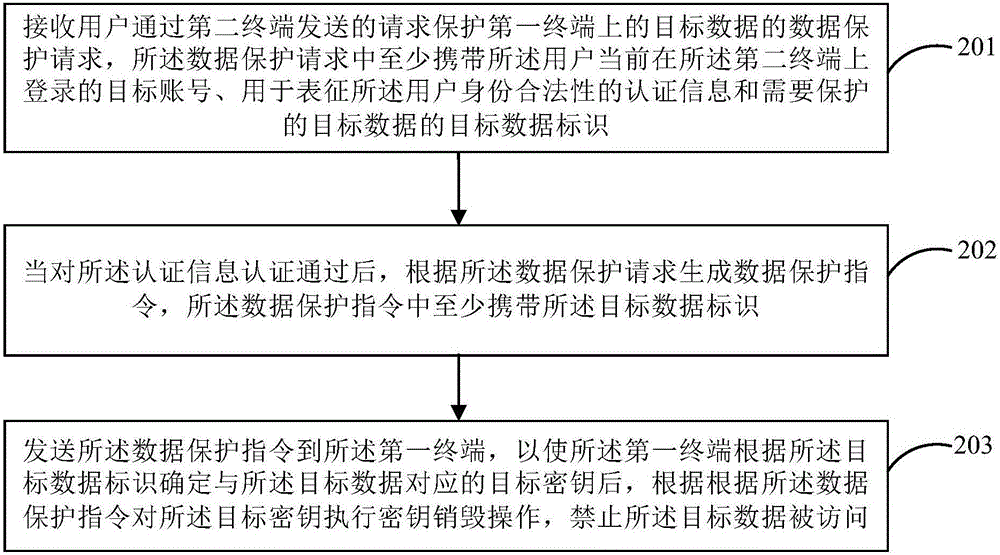
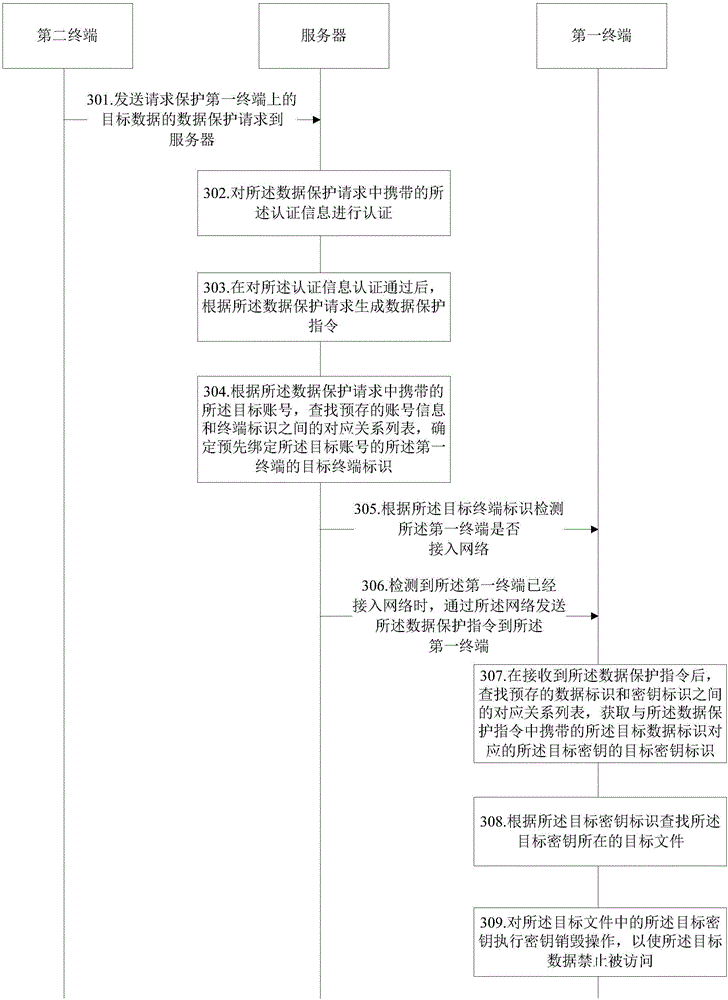
InactiveCN106066968AEnsure safetyNo AccessKey distribution for secure communicationDigital data protectionComputer securityComputer terminal
The disclosure provides a data protection method and device; the method comprises the following steps: receiving a data protection order sent by a server and used for protecting target data, wherein the data protection order at least comprises a target data ID of the target data; determining a target secret key corresponding to the target data according to the target data ID; destroying the target secret key according to the data protection order, thus preventing the target data from being accessed. In the disclosure, the first terminal receives the data protection order sent by the server, and destroys the target secret key; the method and device can fast ensure the target data on the first terminal not to be accessed, thus ensuring user data safety, and improving user data safety protection speed.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Group authentication method and system in asynchronous group communication of LTE network machine type communication equipment
ActiveCN112118569AComplete refactoringNo AccessUser identity/authority verificationSecurity arrangementAuthentication systemData messages
Related technologies of the Internet-of-things are developed rapidly and widely applied. Machine type communication (MTC) can complete data information exchange and sharing between equipment without active participation of a user, has the characteristics of low cost, low power consumption and capability of transmitting information on a large scale, and is one of the most important communication modes in the Internet-of-things. Therefore, the security of the MTC needs to be emphasized, and the data security of the user needs to be protected. The invention provides a group authentication methodand a group authentication system in asynchronous group communication of machine type communication equipment in an LTE network, which construct a group authentication scheme by utilizing a (t, n) secret sharing scheme of Shamir, authenticate m (m is greater than or equal to t) machine type communication equipment (MTCD) at one time, and ensure the legality of MTCD identity of an access network. Meanwhile, in the token transmission process, an ElGamal encryption algorithm is used to ensure the security of the authentication token in the transmission process. By utilizing the method and the system, the group authentication can be completed only by one-time calculation, the confidentiality can reach the calculation security, and each group member only needs to carry one authentication token.
Owner:LANZHOU UNIVERSITY
Communication method for mobile terminal, and mobile terminal
ActiveCN106211144AImprove securityPrevent communicationAssess restrictionEavesdropping prevention circuitsCommunications securityOperational system
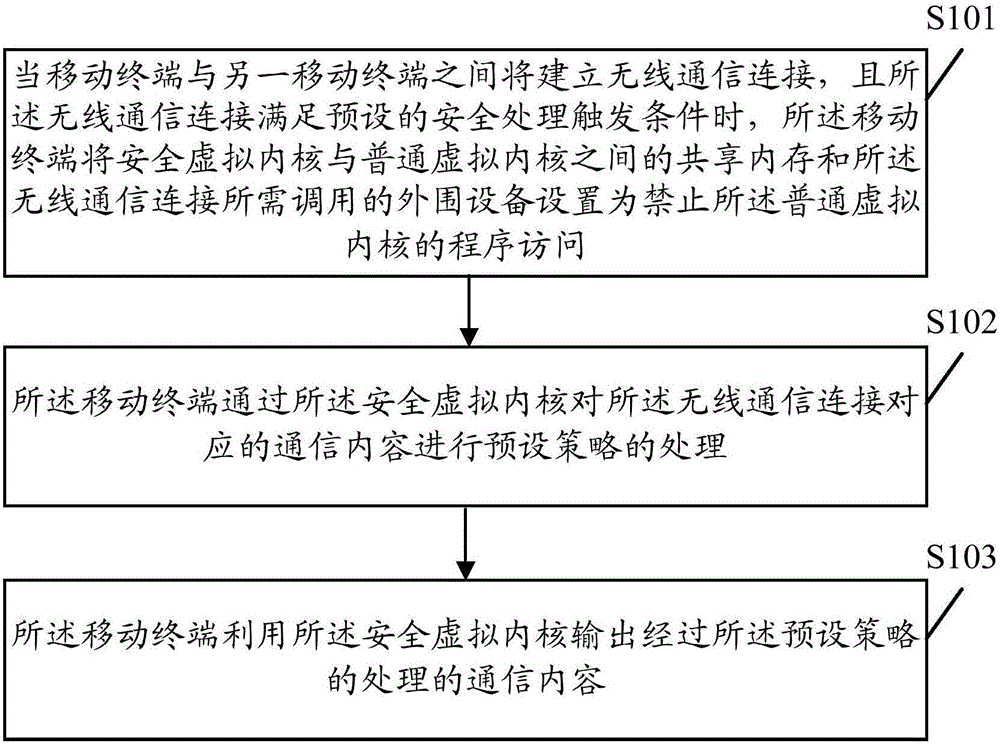
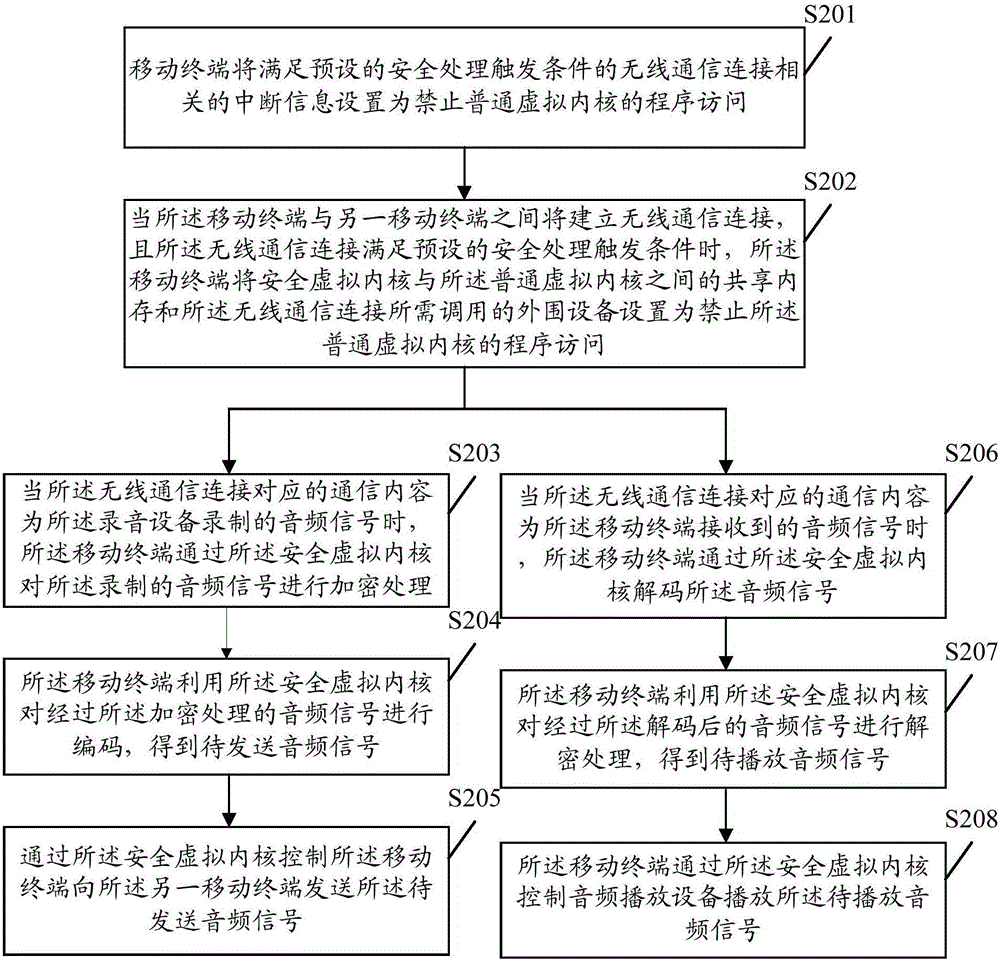
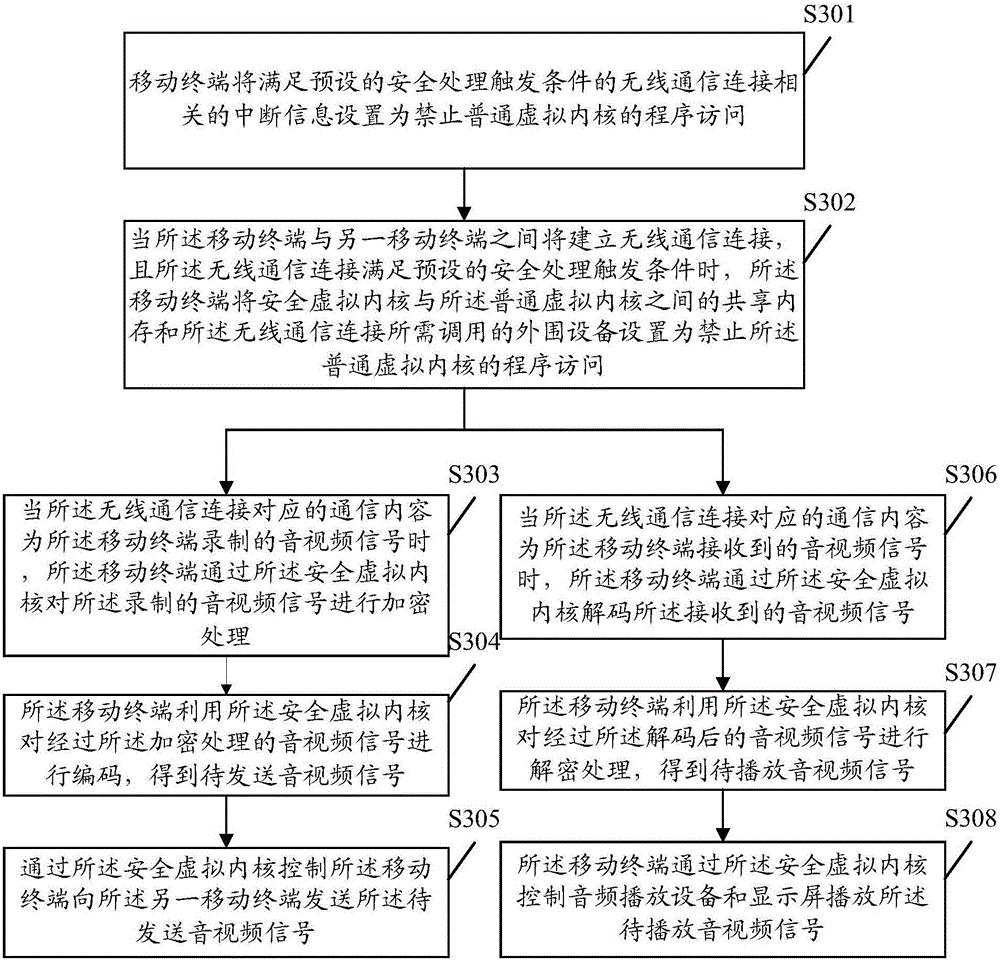
The embodiment of the invention discloses a security communication method for a mobile terminal, and the mobile terminal, wherein the security communication method can comprise the following steps of: setting a shared memory between a security virtual kernel and a normal virtual kernel and peripheral equipment called by the wireless communication connection to forbid program access of the normal virtual kernel when wireless communication connection between a mobile terminal and another mobile terminal is established and the wireless communication connection satisfies a pre-set security processing triggering condition; performing pre-set strategy processing of a communication content corresponding to wireless communication connection through the security virtual kernel; and outputting the communication content after being subjected pre-set strategy processing by utilizing the security virtual kernel. By means of the embodiment of the invention, an operating system and a program operated in the normal virtual kernel can be prevented from obtaining the communication content before being processed; the operating system can also be prevented from eavesdropping the communication content through the shared memory or related peripherals; and thus, the communication security of the mobile terminal is improved.
Owner:HUAWEI TECH CO LTD
Resource and energy recovery-based sewage treatment method
InactiveCN109160686AEasy to handleImprove separation efficiencyTreatment using aerobic processesWaste based fuelEnergy balancingEnergy recovery
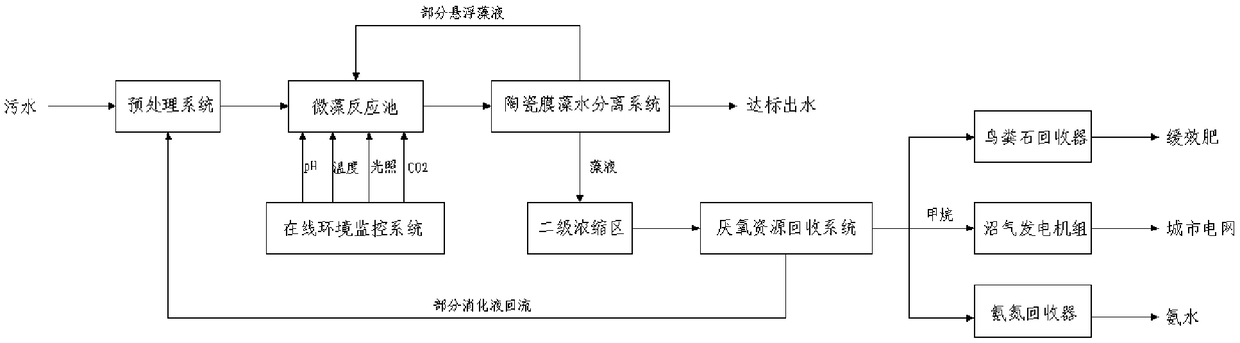
The invention relates to a resource and energy recovery-based sewage treatment method, and provides a sewage treatment system. The sewage treatment system comprises a pre-treatment system, a microalgae reaction tank, an online environment monitoring system, a ceramic membrane and algae separation system and an anaerobic resource recovery system. The method for carrying out sewage treatment by utilizing the sewage treatment system comprises the following steps of: enabling pre-treated sewage to enter the microalgae reaction tank, and reducing the concentrations of nitrogen, phosphorus and organic matters in the sewage through biochemical reaction of microalgae under a controlled environment condition; and carrying out separation on algae-water mixed solution through the ceramic membrane andalgae separation system, discharging qualified effluent, enabling a little suspension algae solution to flow back, carrying out secondary concentration on most of the algae solution to enter the anaerobic resource recovery system so as to carry out anaerobic digestion reaction, and respectively generating electric energy, fertilizer and ammonium hydroxide from generated methane and residual digestion solution through a marsh gas generating set, a struvite recovery device and an ammonia nitrogen recovery device. The system is good in sewage treatment effect and high in nitrogen and phosphorusrecycle rate, and is capable of realizing resource and energy balance of sewage treatment.
Owner:SUN YAT SEN UNIV
Video recorder and video server system
InactiveCN1610396ANo AccessProper internet connectionTelevision system detailsPulse modulation television signal transmissionVideocassette recorderNetwork connection
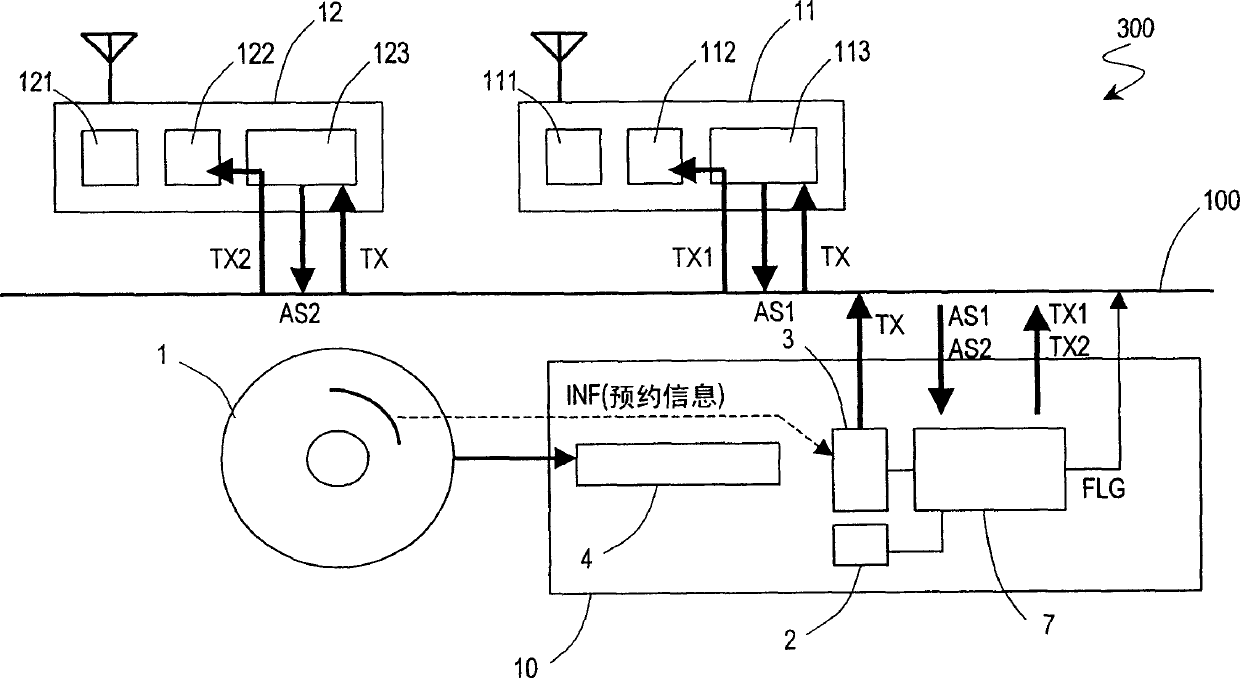
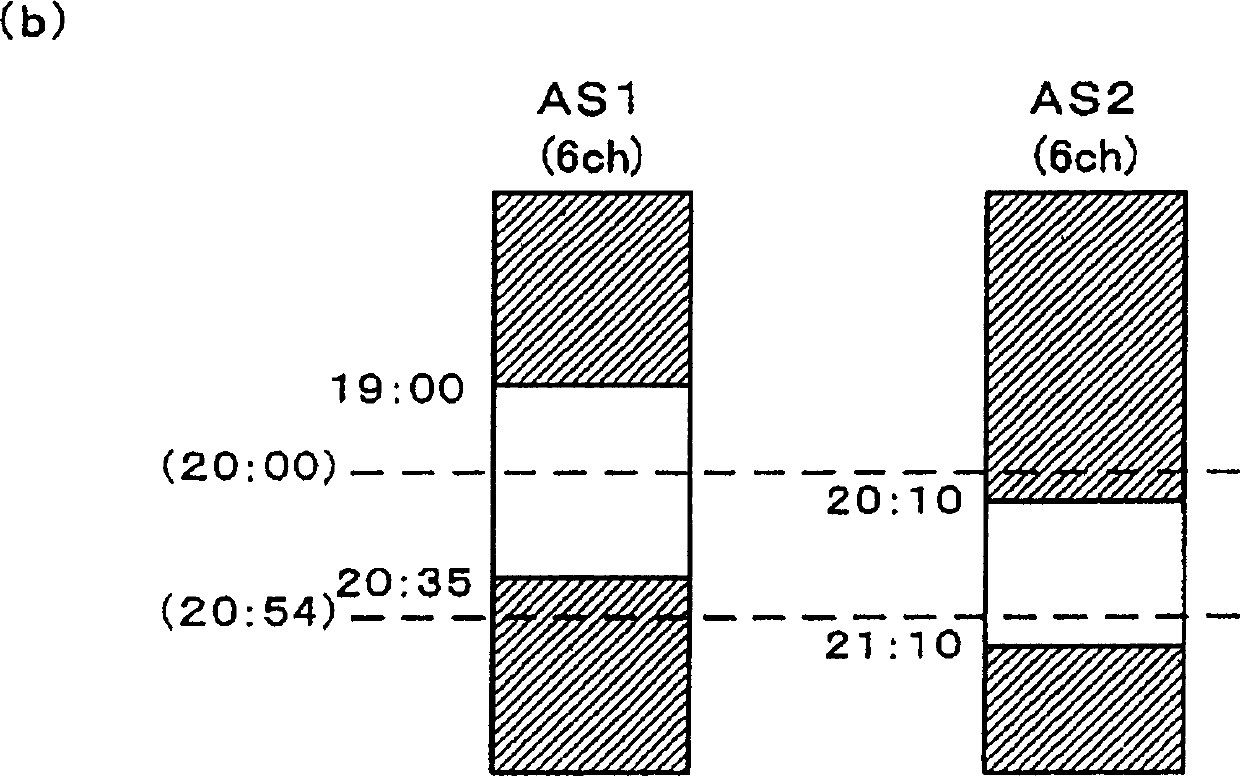
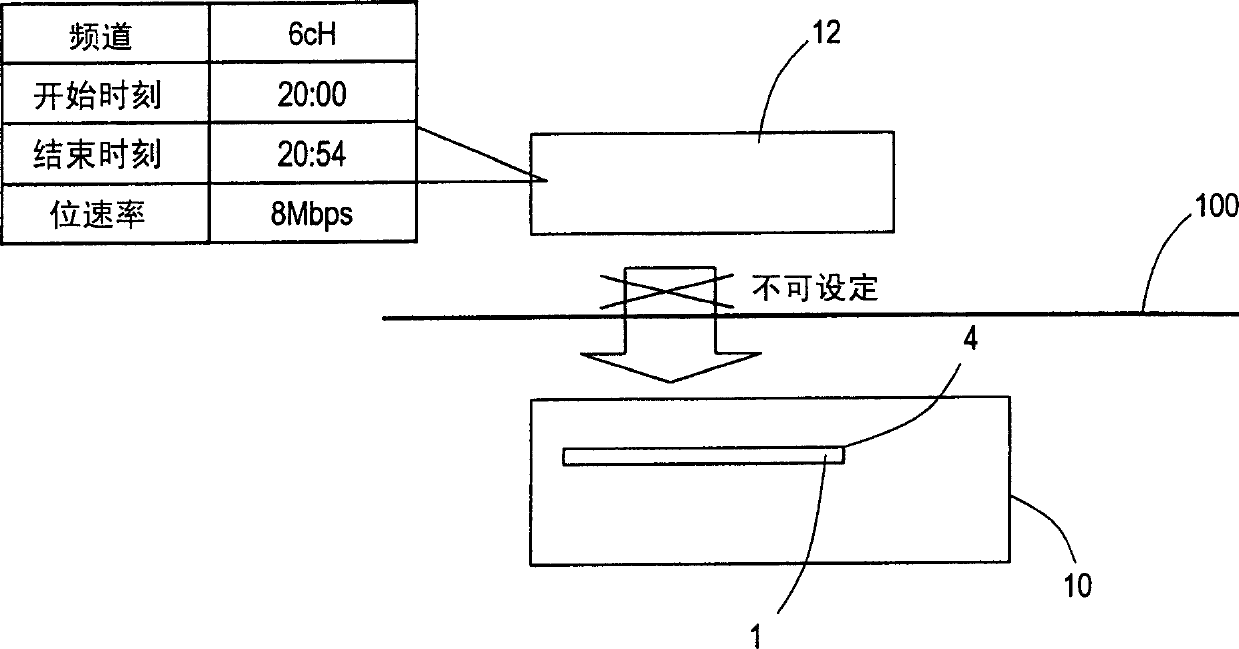
The invention is aimed to provide a video recorder which can record a broadcast program through a network without causing network failure or the like, maintaining an advantage of the interchangeability of an information recording medium. This video recorder connectable with the network is provided with a reservation management section which manages broadcast program reservation information, a recording drive which records on an interchangeable information recording medium and which records broadcast program data on the information recording medium, and a controller which controls the reservation management section and the recording drive. When the recording drive is loaded with the information recording medium, and such a setting that the recording drive records the broadcast program data is performed, the controller prohibits other apparatus from accessing the recording drive through the network.
Owner:PANASONIC CORP
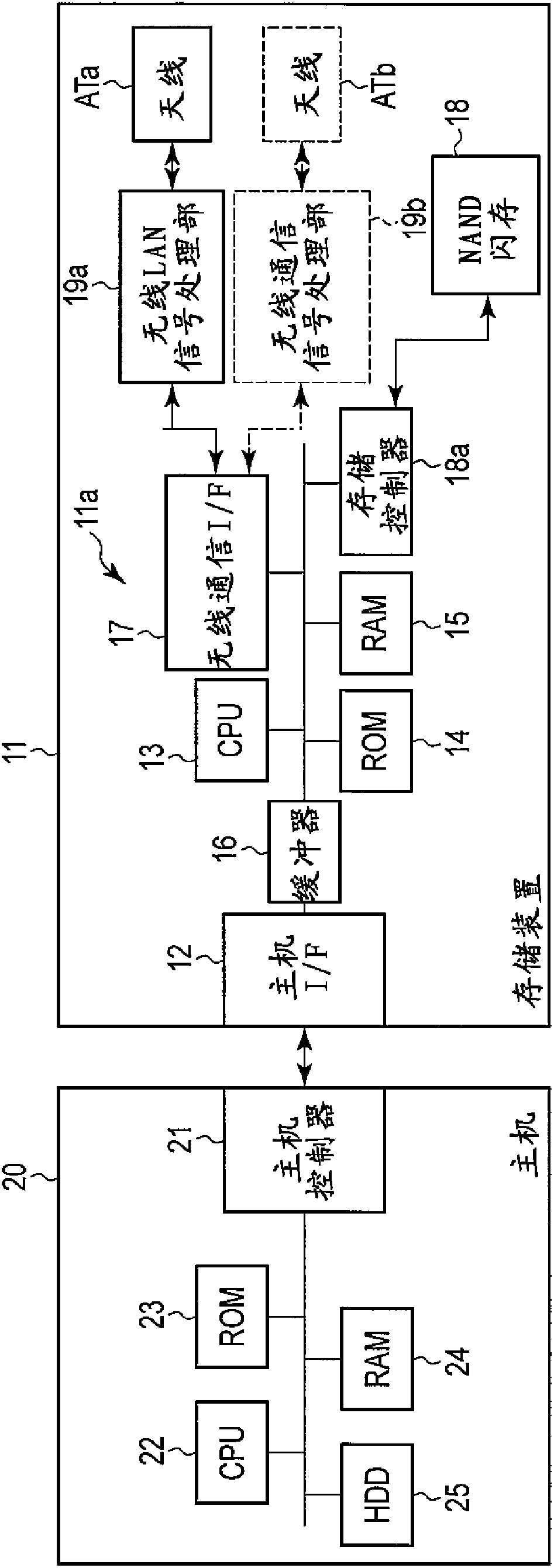
Memory system capable of prohibiting access to application software and system software
InactiveCN102650973ANo AccessMemory loss protectionInternal/peripheral component protectionApplication softwareApplication module
According to one embodiment, a memory system includes an application module, a storage module, and a control module. The storage module stores user data, application software configured to control operation of the application module, and management information used to manage the user data and the application software. The control module controls writing and erasing of the storage module. The control module masks information indicating an access-prohibited area included in the management information read from the storage module, the access-prohibited area includes the application software.
Owner:TOSHIBA MEMORY CORP
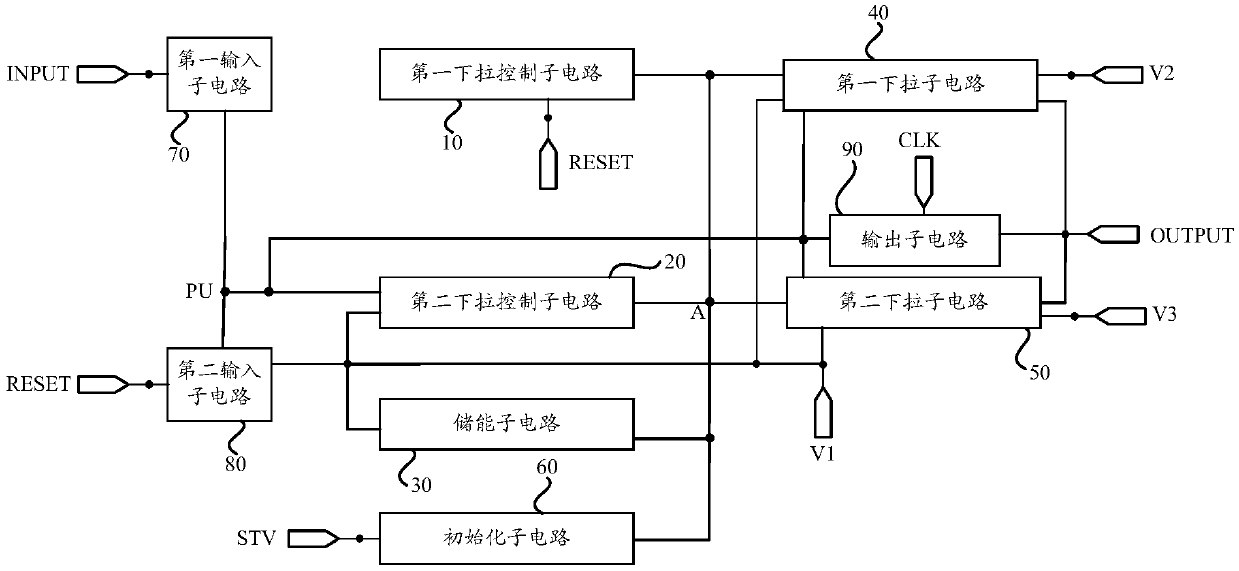
Shift register units, drive method thereof, gate driver circuits and display device
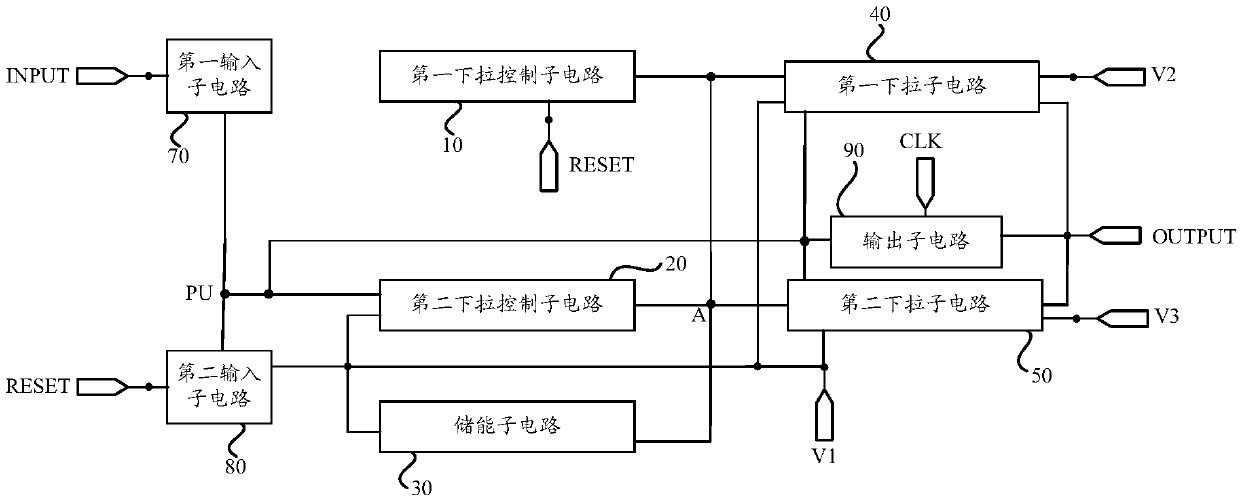
ActiveCN109616048ANo accessReduce power consumptionStatic indicating devicesDigital storageDriver circuitShift register
The invention provides shift register units, a drive method thereof, gate driver circuits and a display device, relates to the technical field of display and is used for solving the problem that a GOA(Gate Driver on Array) generates additional power consumption. A shift register unit comprises a first pull-down control subcircuit which is configured to transmit a signal of a reset signal end to an energy storage subcircuit and a selection node; a second pull-down control subcircuit which is configured to transmit the signal of a first voltage end to the energy storage subcircuit and the selection node under the control of a pull-up node; the energy storage subcircuit which is configured to store the signal transmitted to the energy storage subcircuit and transmit the signal stored in theenergy storage subcircuit to the selection node; a first pull-down subcircuit which is configured to transmit the signal of the first voltage end to the pull-up node and a signal output end; a secondpull-down subcircuit which is configured to transmit the signal of the first voltage end to the pull-up node and the signal output end; and an output subcircuit which is configured to transmit the signal of a clock signal end to the signal output end.
Owner:CHONGQING BOE OPTOELECTRONICS +1
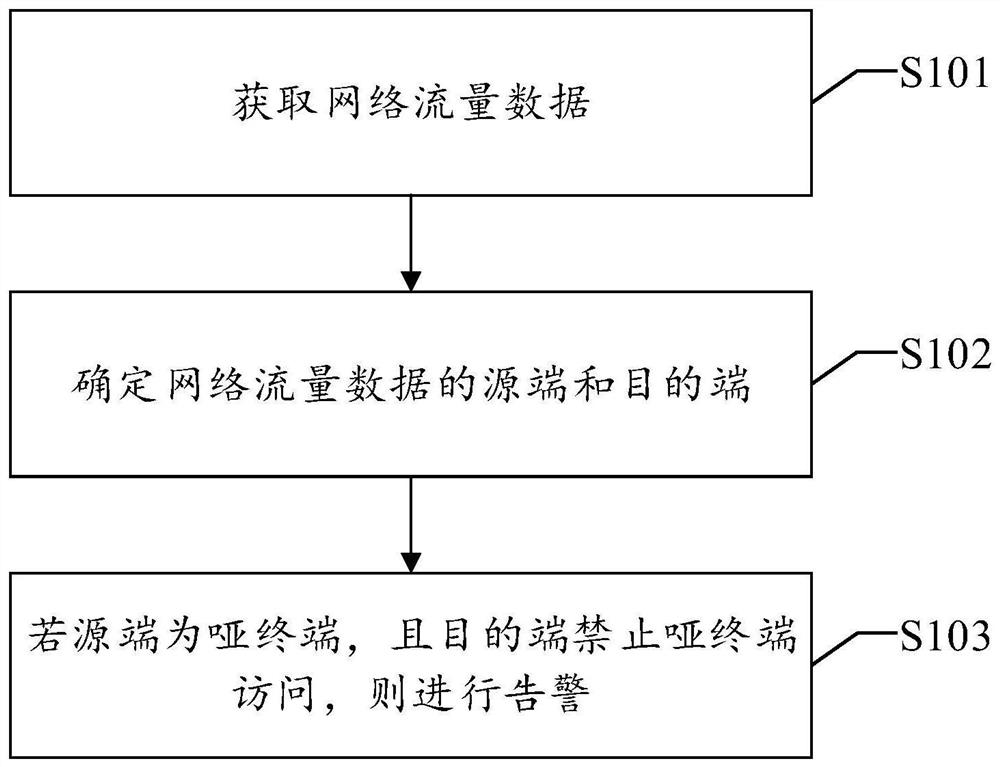
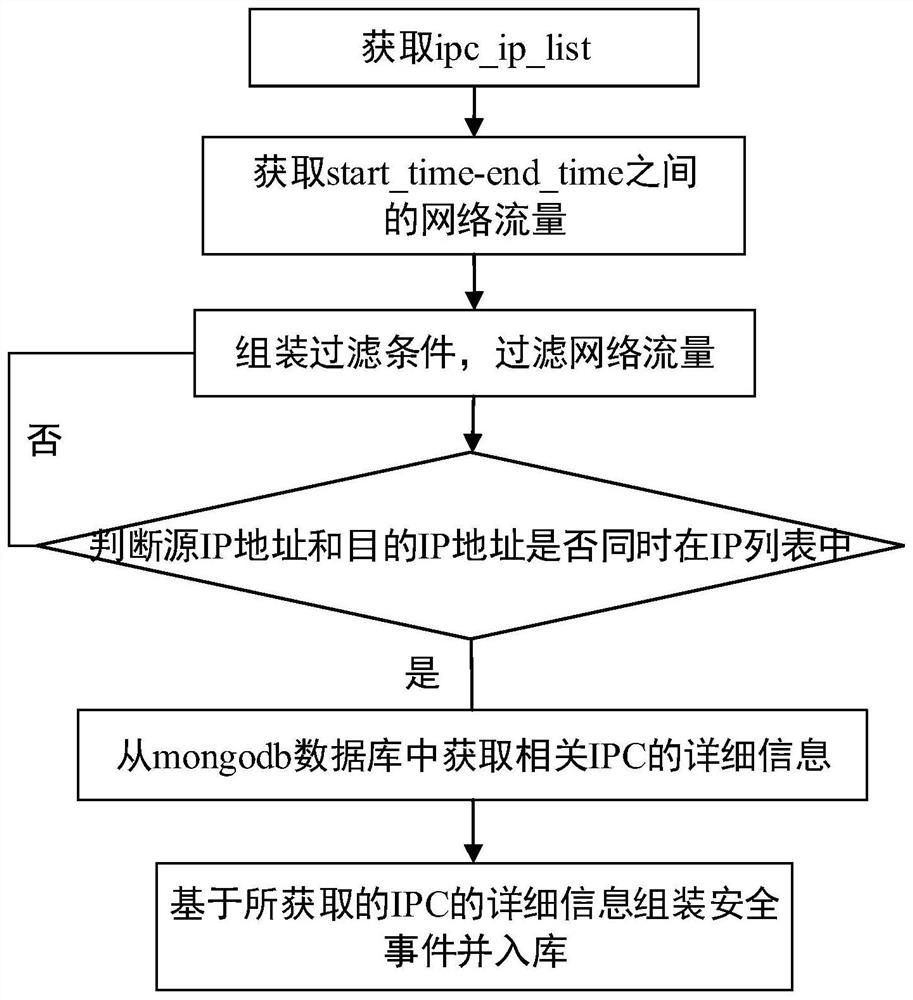
Dumb terminal security detection method and device, equipment and readable storage medium
Owner:SANGFOR TECH INC
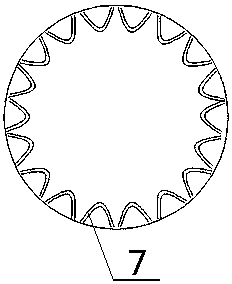
Skirt having arc extinguishing path
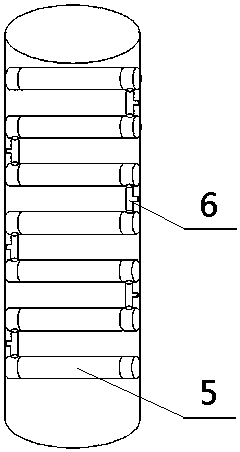
PendingCN107732657AImprove arc extinguishing abilitySimple structureSpark gap detailsInsulatorsAirflowEngineering
The invention discloses a skirt having an arc extinguishing path, which is disposed at the outer surface of a lightning protection device. The internal part of the skirt is provided with an arc extinguishing path I formed through arranging a plurality of arc extinguishing pipes along the circumferential direction, and the arc extinguishing path I is in series connection with an arc extinguishing path II of the lightning protection device. The end parts of two adjacent arc extinguishing pipes in the arc extinguishing path I are directly connected to each other in a contacting manner or are connected to each other through a connecting piece. A connecting part of two adjacent arc extinguishing pipes close to the outer edge of the skirt is provided with an airflow spraying channel. The airflowspraying channel extends to the outer surface of the skirt, which means that the outer surface of the skirt is provided with an airflow spraying outlet. The invention is advantageous in the structureis simple, design is reasonable, arc extinguishing capability is strong, and work is stable and reliable.
Owner:王巨丰
A method for authentication and key agreement between devices
ActiveCN103647653BProtection securityNo AccessKey distribution for secure communicationUser identity/authority verificationDependabilitySerial code
The invention discloses a certification and key agreement method between devices. The certification and key agreement method between the devices comprises that the same key information records are pre-established in a primary device and a slave device; when the primary device determines whether the slave device possesses the same key serial number, the slave device generates a random number RA; the primary device and the slave device calculate result data A1, B1 and C1 according to the key information records and the random number RA of the primary device and the slave device; when the primary device determines that the calculated result data A1 and B1 is equal to the calculated data A1 and B1 of the slave device, the slave device generates a random number RB; the primary device and the slave device calculate result data A2, B2 and C2 according to the key information records, the result data C1 and the random number RB of the primary device and the slave device; when the primary device determines that the calculated result data A2 and B2 is respectively equal to the result data A2 and B2 calculated by the slave device, the key between the primary device and the slave device is C2. The certification and key agreement method between the devices is safe and reliable and is beneficial to guaranteeing safety and reliability of data interaction between devices.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Shared big data on-site protection platform
ActiveCN110472378BReasonable designNo AccessDigital data authenticationProgram/content distribution protectionEngineeringIdentification device
The invention relates to a shared big data field protection platform, which comprises a depth-of-field identification device used for carrying out face feature analysis on a face object with the nearest depth of field in a morphologically processed image to determine whether the face object is an authorized user or not, and sending a first identification command when the face object is determinedto be the authorized user, otherwise, sending a second identification command; and a access control signal which is arranged in the desktop computer and is used for prohibiting access to the shared document address when the second identification command is received. The shared big data field protection platform is reasonable in design, safe and reliable. The face feature analysis is made on the face object with the nearest depth of field of the environment where a computer is located to determine whether the user is the authorized user or not, and when the user is determined to be the unauthorized user, the access to the currently requested shared document address is forbidden, so that the shared document content is prevented from being leaked.
Owner:SHANDONG HUIJIA SOFTWARE TECH
A traceless access control method and device based on virtual disk protection
ActiveCN103218573BProtection securityAvoid safety hazardsDigital data protectionInternal/peripheral component protectionWeb serviceTransfer procedure
The invention provides a traceless access controlling method and a device based on protection of a visual magnetic disc. The traceless access controlling method and the device based on protection of the visual magnetic disc are characterized in that a usbkey is used for setting up a visual magnetic disc in a system of a user terminal. A safety gateway device with a safety plug-in board is arranged between the user terminal and a web server. The usbkey is used for identifying a user identity by accessing a classified web system. The visual magnetic disc is mounted on the safety plug-in board to set up a visual accessing space. Files in the visual accessing space are oriented again to the visual magnetic disc. According to the traceless access controlling method and the device based on protection of the visual magnetic disc, only a user is allowed to access the files in the visual magnetic disc. Other progresses in the system are forbidden from accessing user files in the visual magnetic disc so that safety of the files in a transmission process is ensured and safety of local files of the user is ensured.
Owner:上海海加网络科技有限公司
User authority management method and device and storage medium
PendingCN111353145ANo AccessImprove management efficiencyDigital data authenticationClassified informationUser Privilege
The invention discloses a user permission management method. The method comprises the steps: selecting target role information for a user; establishing a role mapping relationship between the user andthe target role information; obtaining a function mapping relationship between the role information and the function point information, wherein the role information is used for representing classification information of users with the same authority, and the function point information is used for representing use authority of a service function; according to the role mapping relationship and thefunction mapping relationship, obtaining the use permission of the service function of the user. According to the user permission management method disclosed by the invention, permission control withfiner permission granularity can be provided, and the management efficiency and accuracy of the user permission are improved. The invention further provides a user permission management device and a storage medium.
Owner:广东特惟嘉科技发展有限公司
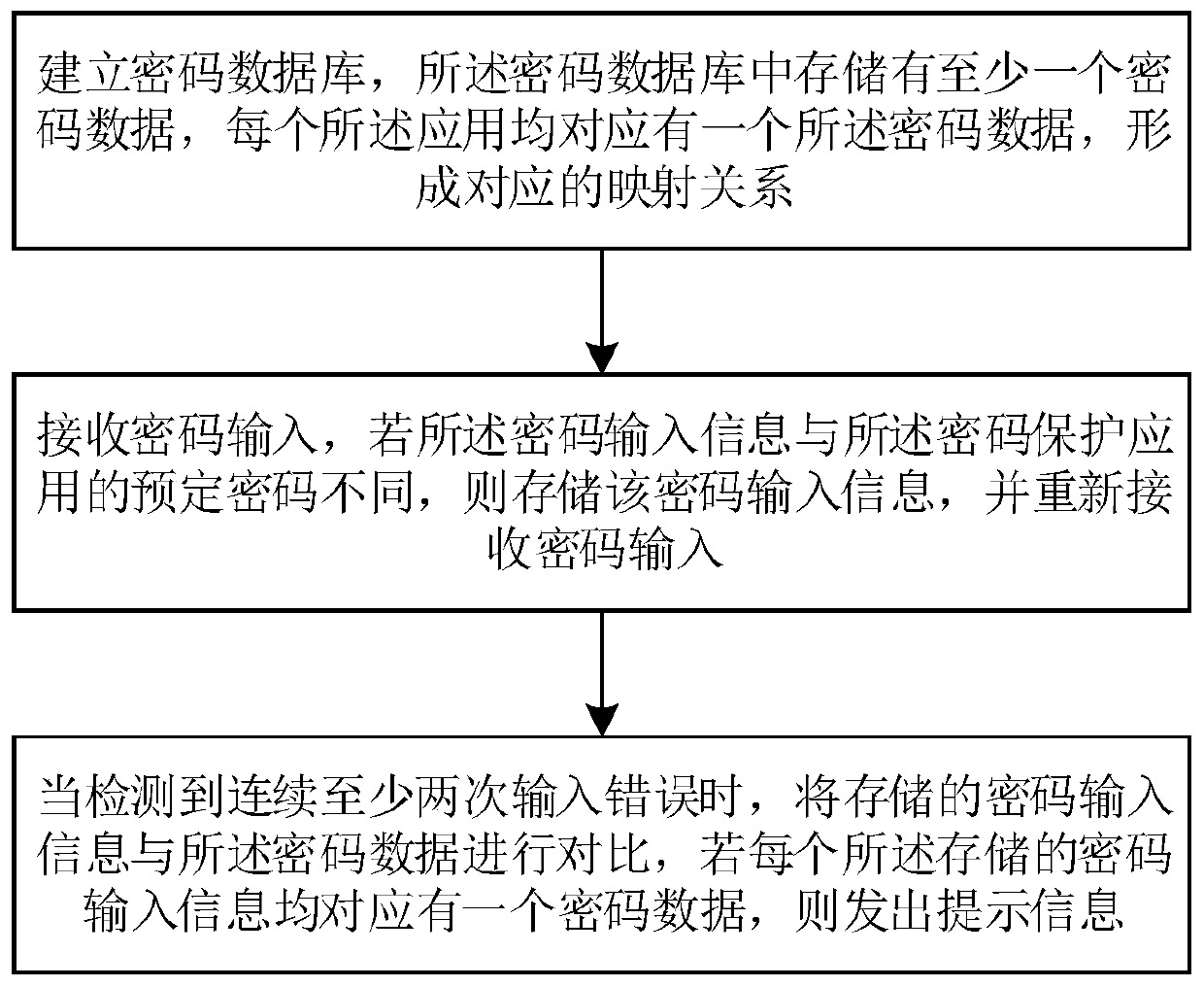
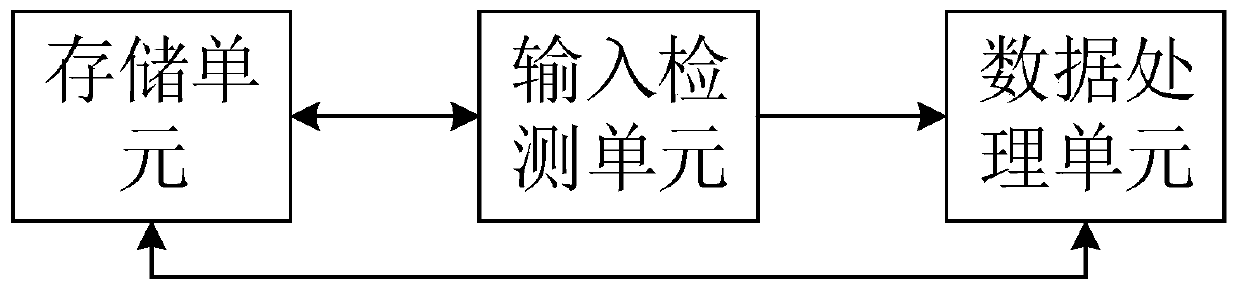
Password management method, system and intelligent terminal
The invention discloses a password management method. The password management method comprises the following steps of establishing a password database, wherein at least one piece of password data is stored in the password database, each application corresponds to one of the password data to form a corresponding mapping relationship; receiving password input, when password input information is different from a preset password of a password protection application, storing the password input information, and receiving the password input again; when at least two times of continuous false inputting are detected, comparing the stored password input information and the password data; when each stored password input information corresponds to one piece of password data, sending prompting information. The password management method has the advantages that the mapping relationship of the password and the corresponding application is pre-stored; when the password is falsely input for multiple times, the false inputting of a user is judged according to the input false password by the user; when the user falsely inputs the password, a correct password prompt is provided for the user, so as to facilitate the user to correctly input.
Owner:THUNDER SOFTWARE TECH
A communication method and device for an industrial security gateway based on an embedded system
ActiveCN104539573BNo AccessImprove securityUser identity/authority verificationIndustrial securityData information
The invention provides a communication method and device of an industrial security gateway based on an embedded system, which helps to improve the security of data transmission in an industrial control network. The method includes: obtaining data information on an industrial site; performing encryption and digital signature processing on the obtained data information through a selected and / or customized encryption algorithm; sending the encrypted data information and the generated digital signature information to to the server. The device includes: an acquisition unit, used to acquire data information on an industrial site; an encryption unit, used to encrypt and digitally sign the acquired data information through a selected and / or customized encryption algorithm; a first sending unit, It is used to send the encrypted data information and the generated digital signature information to the server. The invention is applicable to the technical field of industrial automation information security.
Owner:UNIV OF SCI & TECH BEIJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com