A traceless access control method and device based on virtual disk protection
A virtual disk and virtual access technology, applied in the field of network security, can solve problems such as security risks, and achieve the effect of preventing security risks, avoiding security risks, and protecting security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
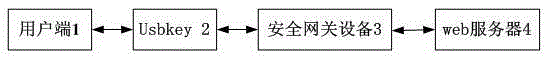
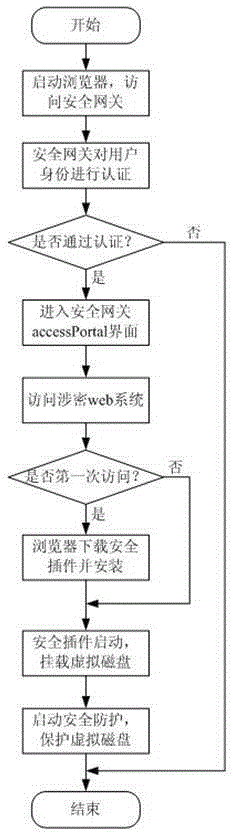
[0037] Such as figure 1 , figure 2 As shown, a non-trace access device based on virtual disk protection includes a client terminal 1 and a web server 4, and the client terminal 1 and the web server 4 are interactively connected through a security gateway device 3; the client terminal 1 is provided with USB interface, described USB interface is plugged with usbkey 2. Described usbkey 2 comprises single-chip microcomputer 2-1, and described single-chip microcomputer 2-1 is interactively connected with memory module 2-2, safety protection module respectively, and described single-chip microcomputer 2-1 carries out interactive connection with security gateway equipment 3. The safety protection module comprises the file filtering driver module 2-3 that prevents the application program or process that visits by usbkey from saving, the copy operation and its cache directory is forced to be redirected to the orientation module 2-4 in the memory module 2-2; The file filtering driver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com