Network safety isolating and information exchanging system and method based on proxy mapping
An information exchange and network security technology, applied in the field of network security isolation and information exchange system based on proxy mapping, can solve the problems of increasing user cost, management complexity, poor real-time and scalability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
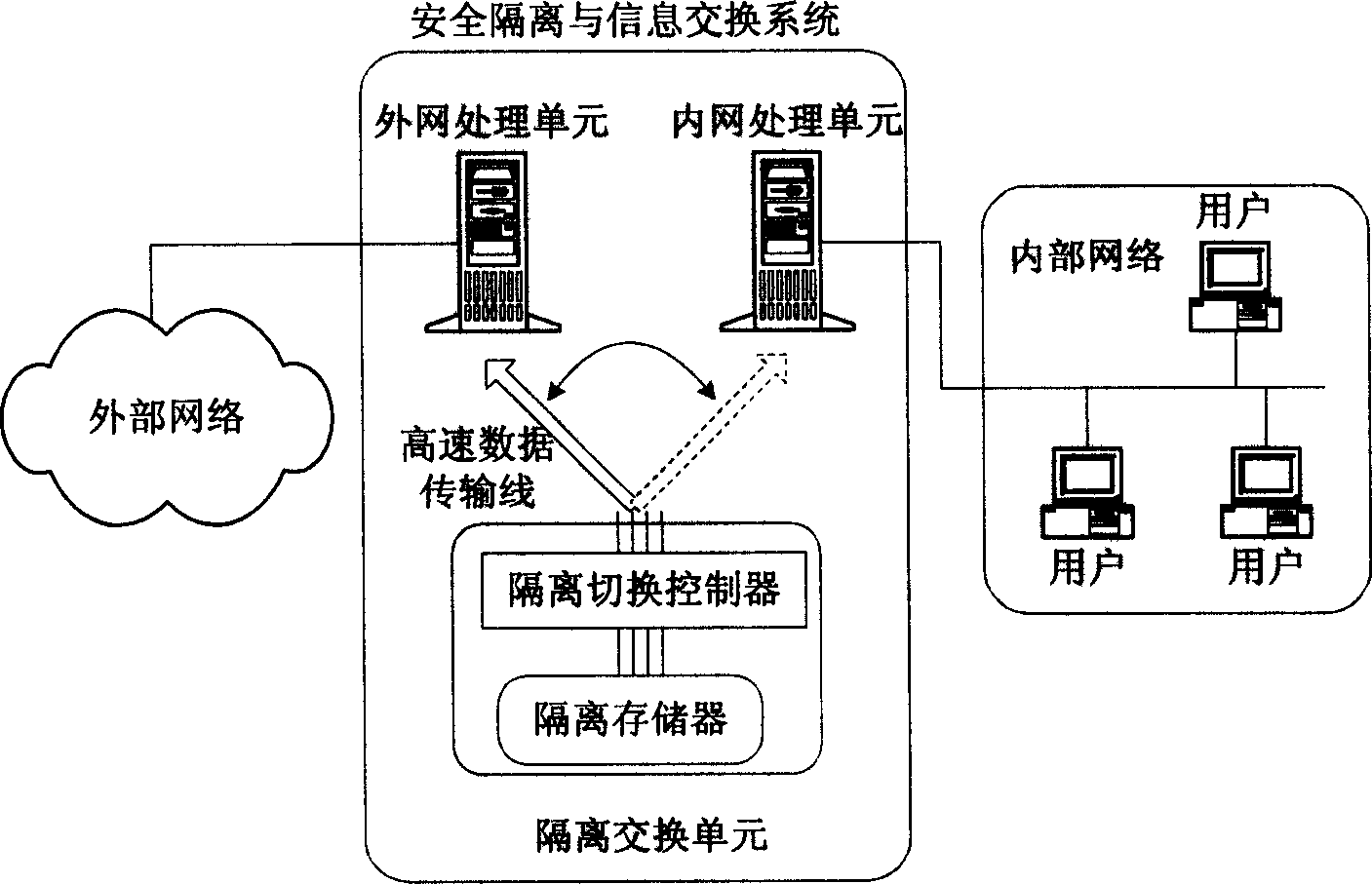
[0039] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings. figure 1 It is a structural block diagram of the security isolation and information exchange system. In the prototype system, the internal and external network processing units choose the X86-based industrial control system, and the high-speed data transmission line can use SCSI or USB buses. According to the different buses, different isolation switching control units can be realized, and the corresponding isolation memory can be selected, such as SCSI or USB interface hard disk.
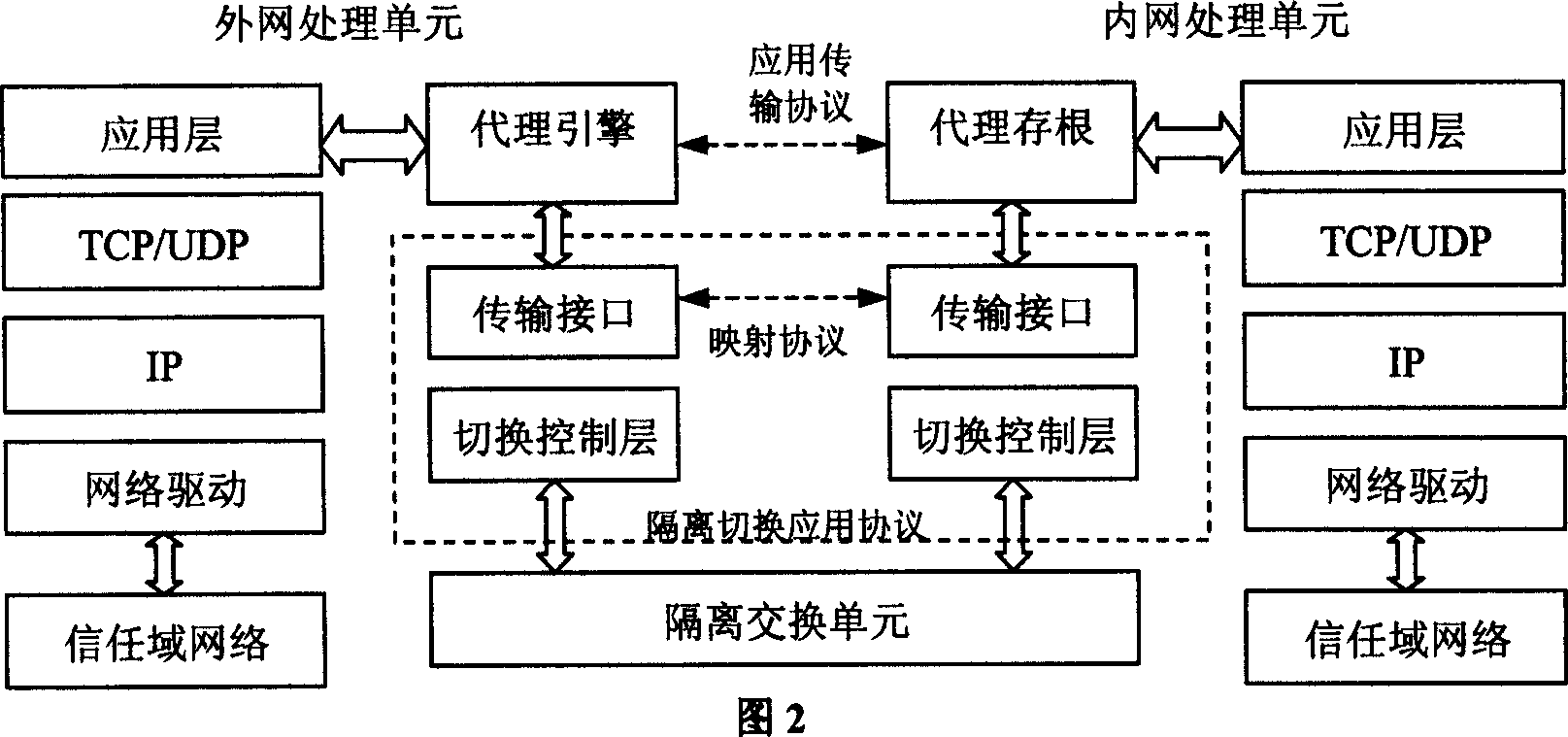
[0040] The operating system of the internal and external network processing units selects the Linux operating system, and the protocol stack in the system is shown in Figure 2. The proxy engine communicates with the intranet processing unit through the isolation switching unit, and performs virus filtering and security inspection on the data. The internal network p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com