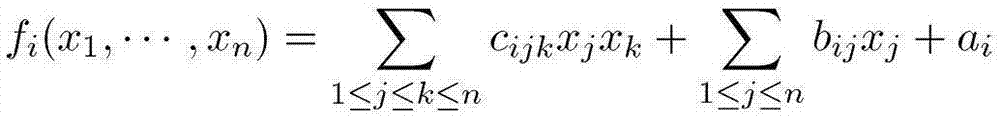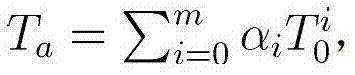Shared secret key establishment method under quantum computing environment
A shared key, quantum computing technology, applied in the field of information security, can solve the problems of incapable of quantum channel secure communication, less research on key exchange protocols, etc., and achieve high efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
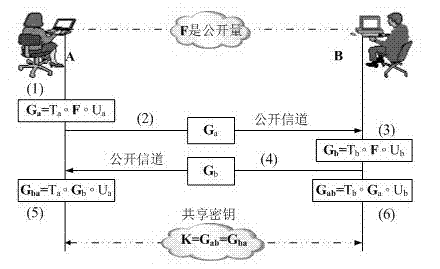
[0031] The method for establishing a shared key under the quantum computing environment proposed by the present invention will be described below in conjunction with the accompanying drawings and specific embodiments.
[0032] please see figure 1 , the method for establishing a shared key under the quantum computing environment of the present invention, comprising the following steps:
[0033] Step 1: Build the system:
[0034] Choose the finite field GF(2 16 ), randomly select CF(2 16 ) on the 10-dimensional square matrix T 0 and the 12-dimensional square matrix U 0 , and a nonlinear transformation F composed of 12 variables and 10 quadratic polynomials, F can be expressed as:
[0035] F(x 1 ,...,x 12 )=(f 1 (x 1 ,...,x 12 ),..., f 10 (x 1 ,...,x 12 ))
[0036] Here, f i is a quadratic polynomial function of 12 elements, the form is as follows:
[0037] f i ( x 1 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com