Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
66 results about "OPEN protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
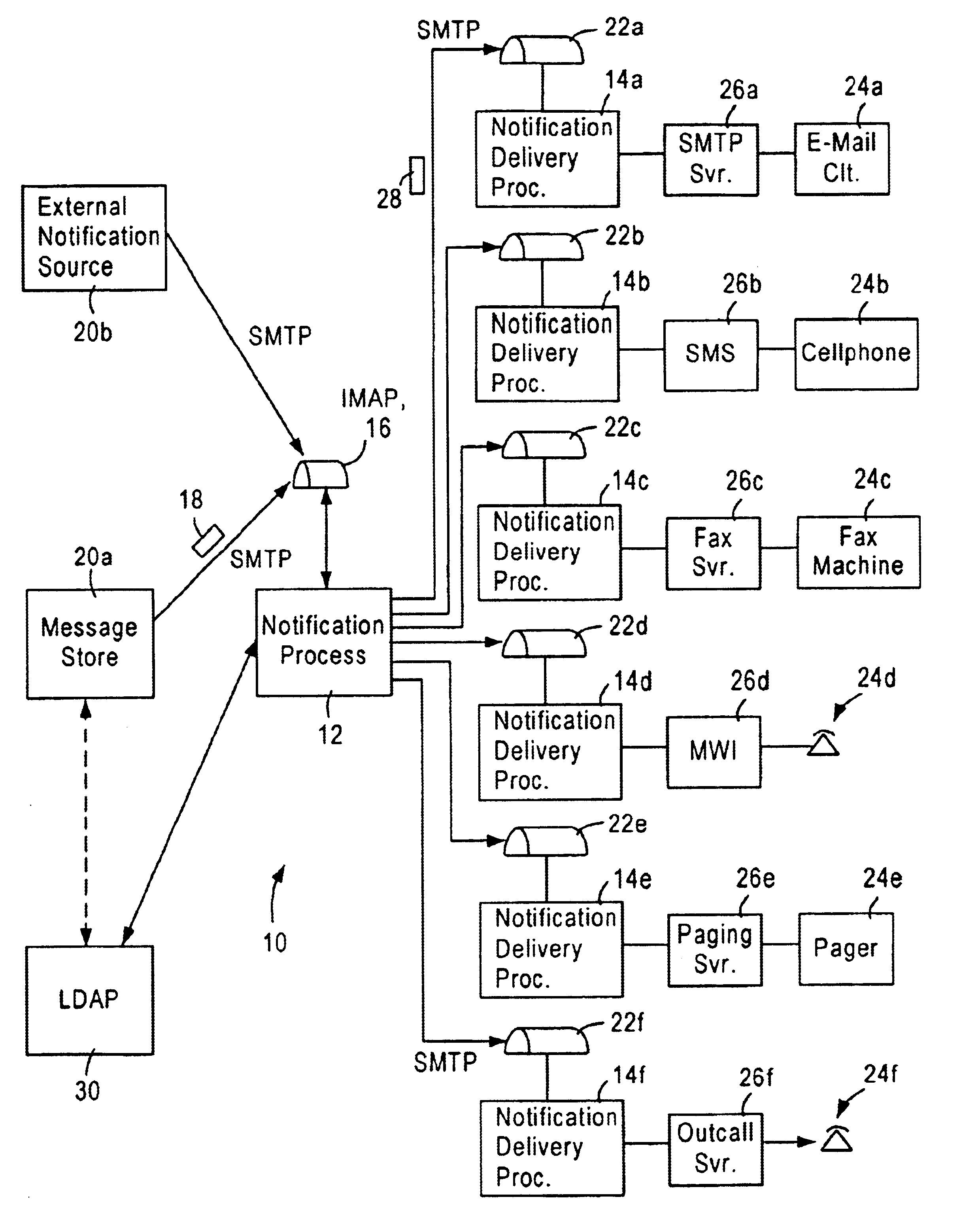
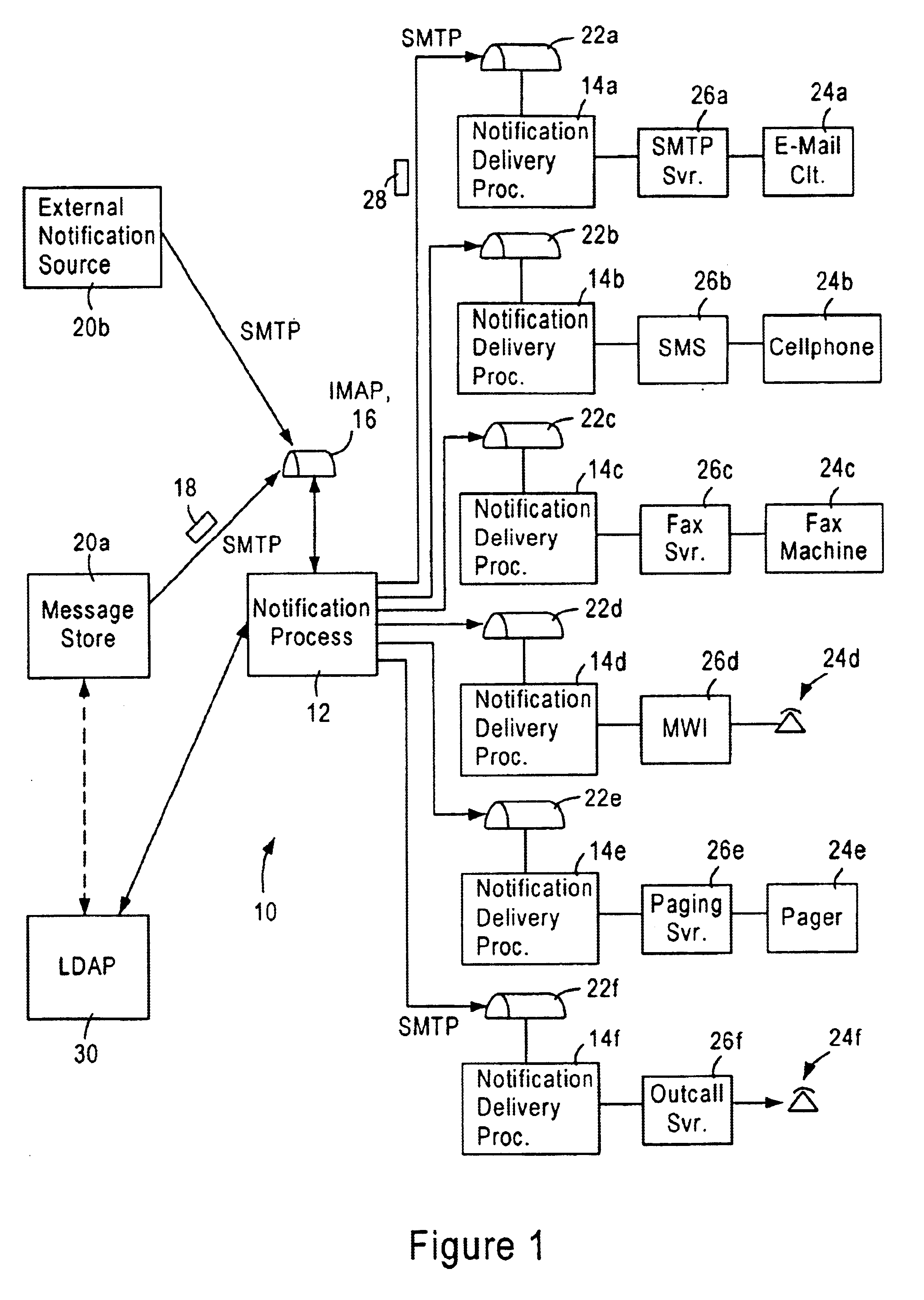
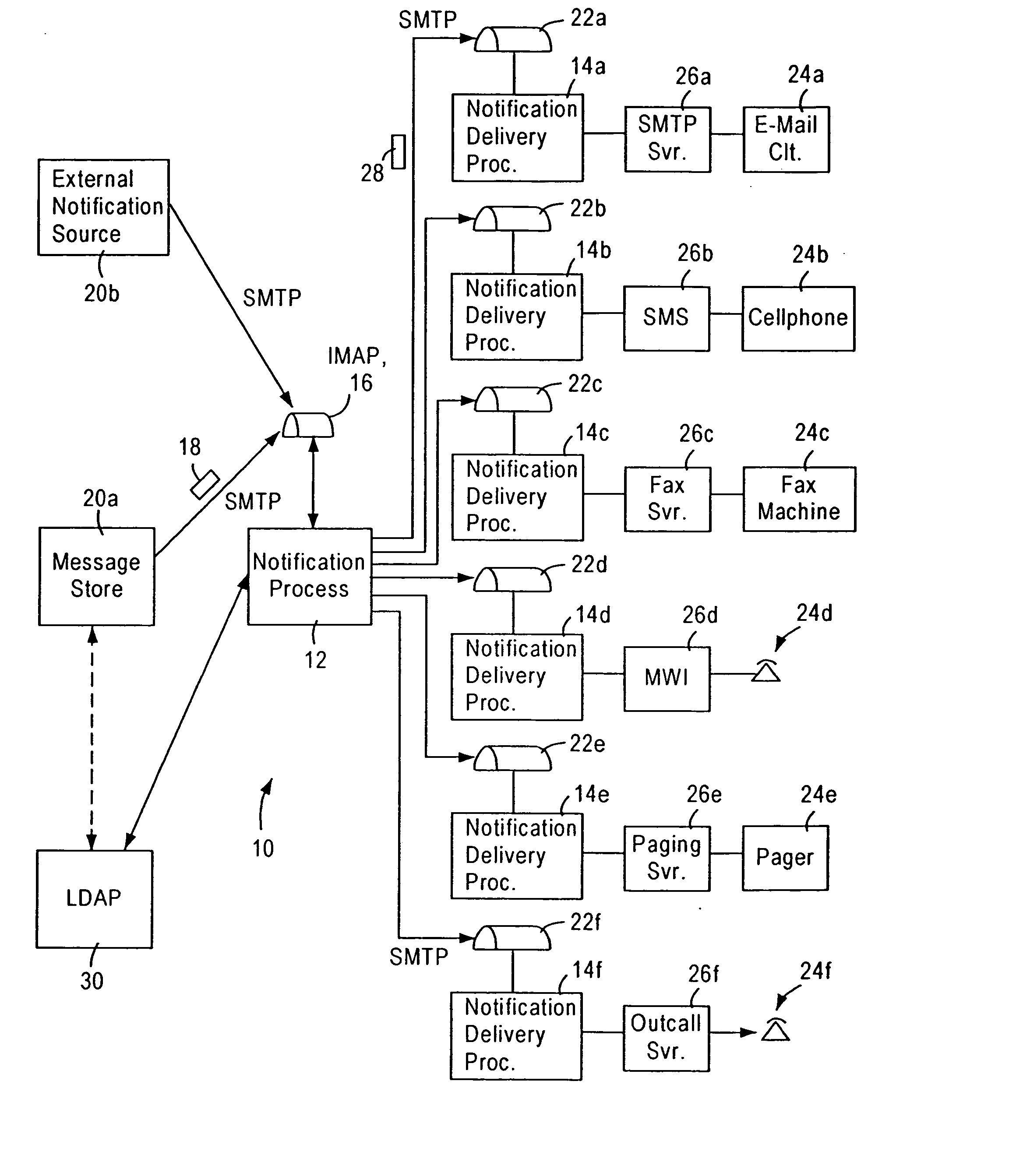
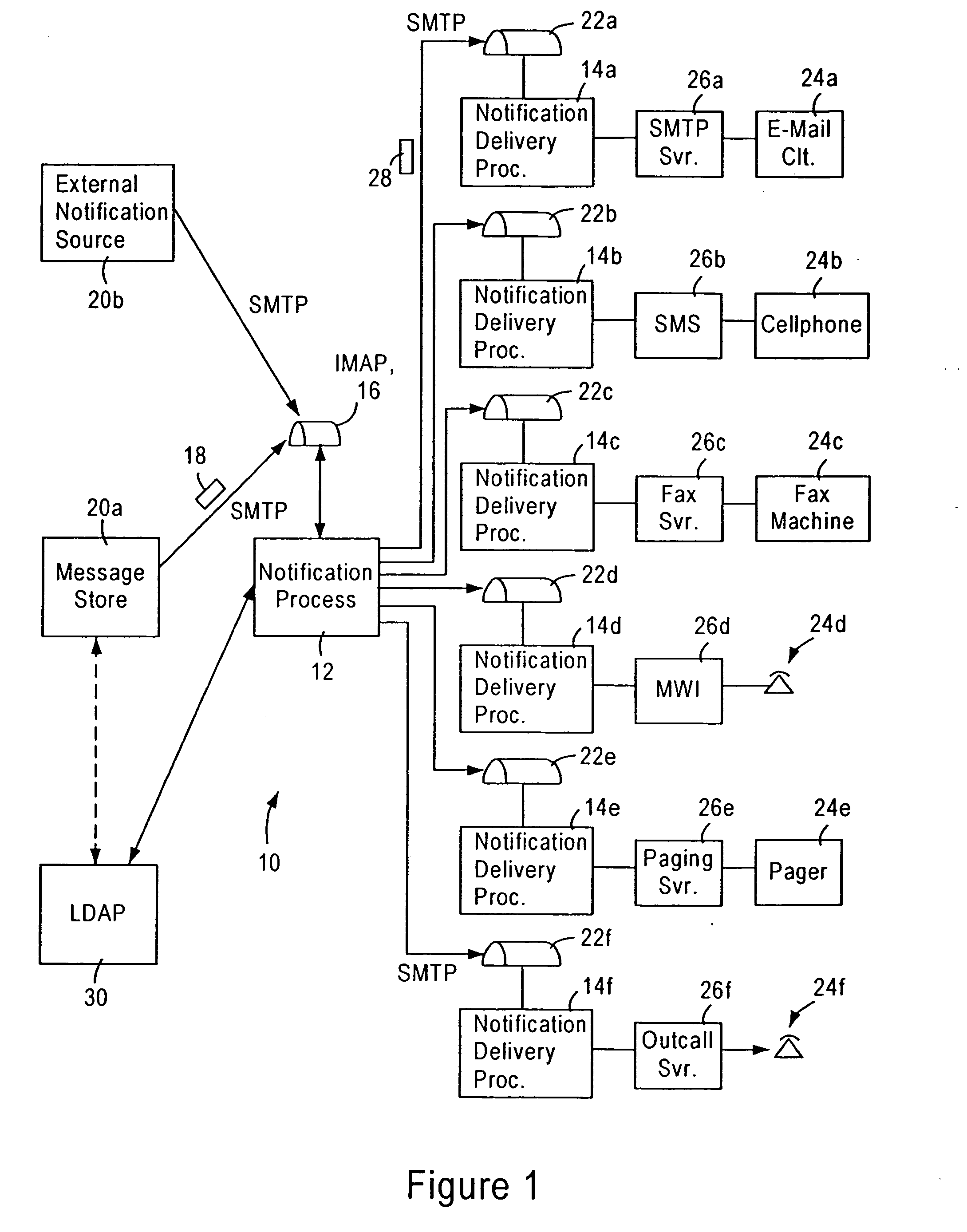
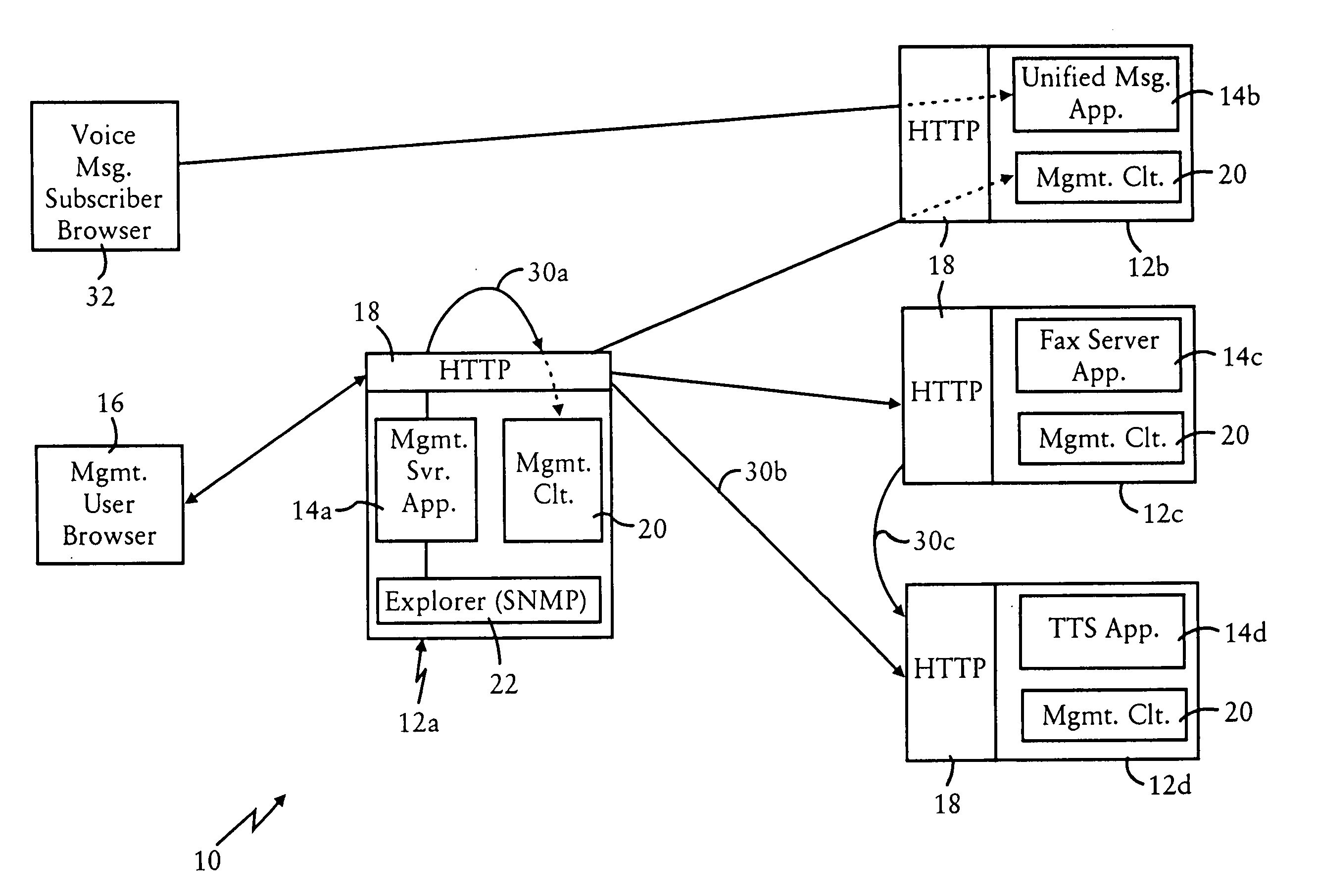
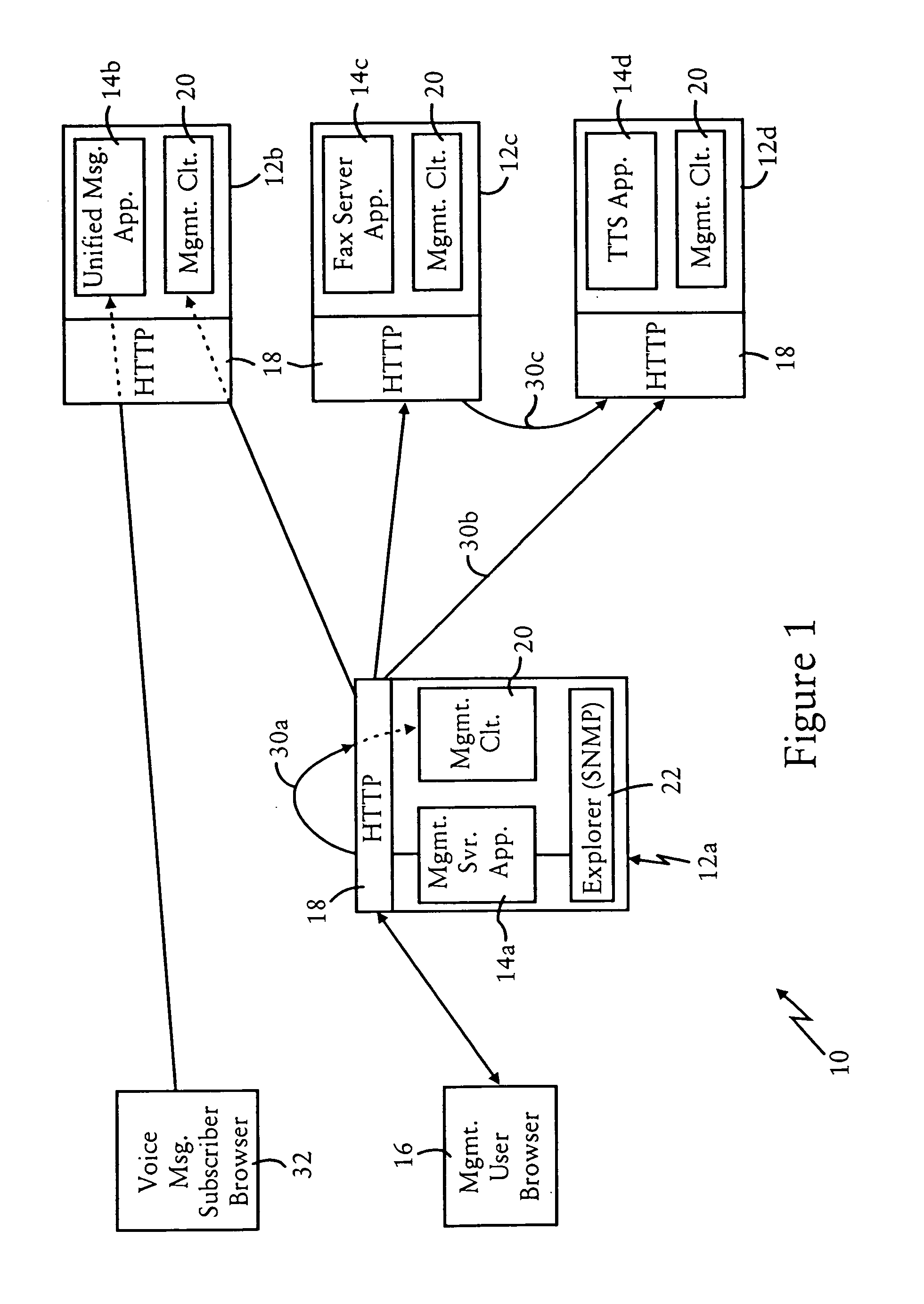
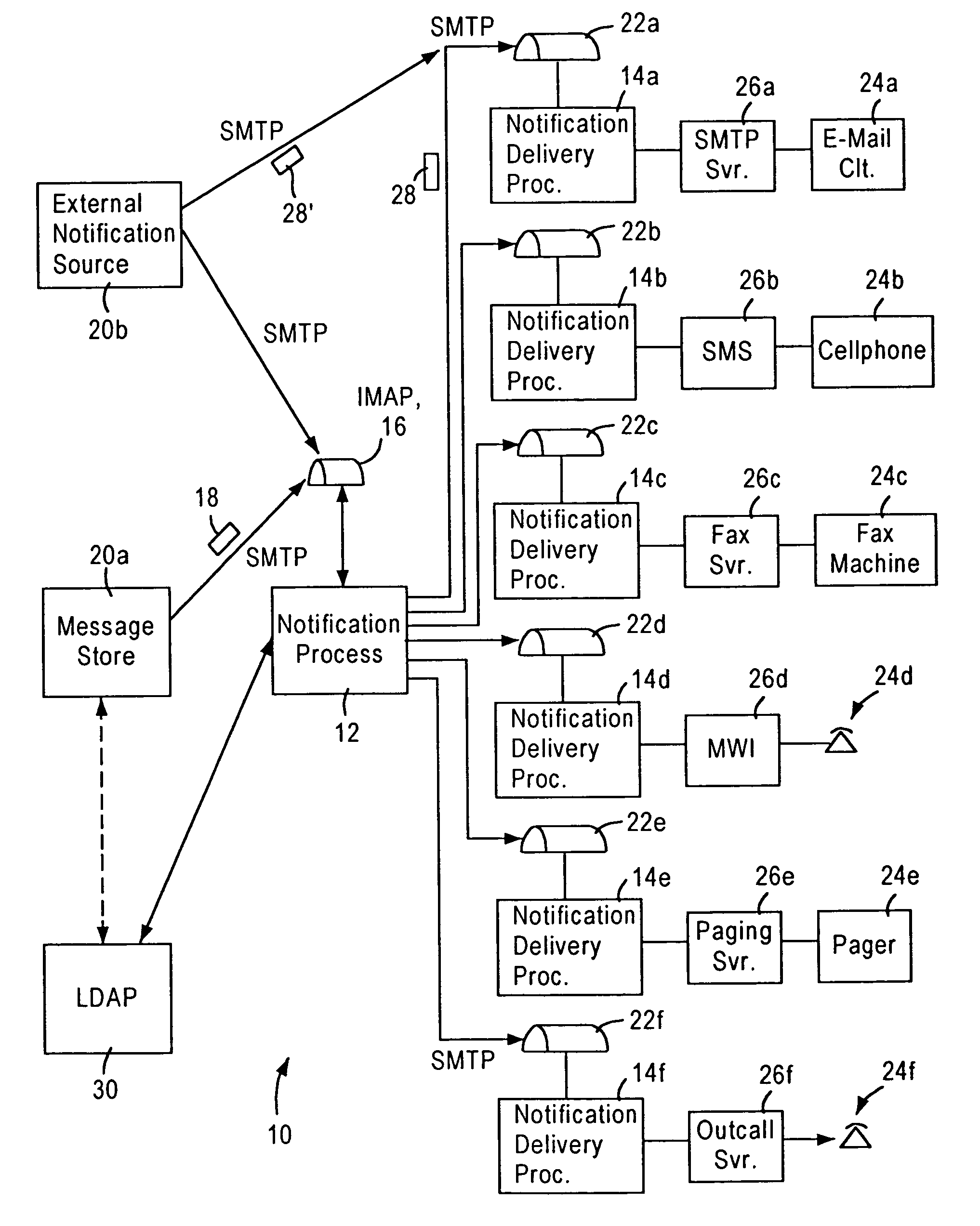
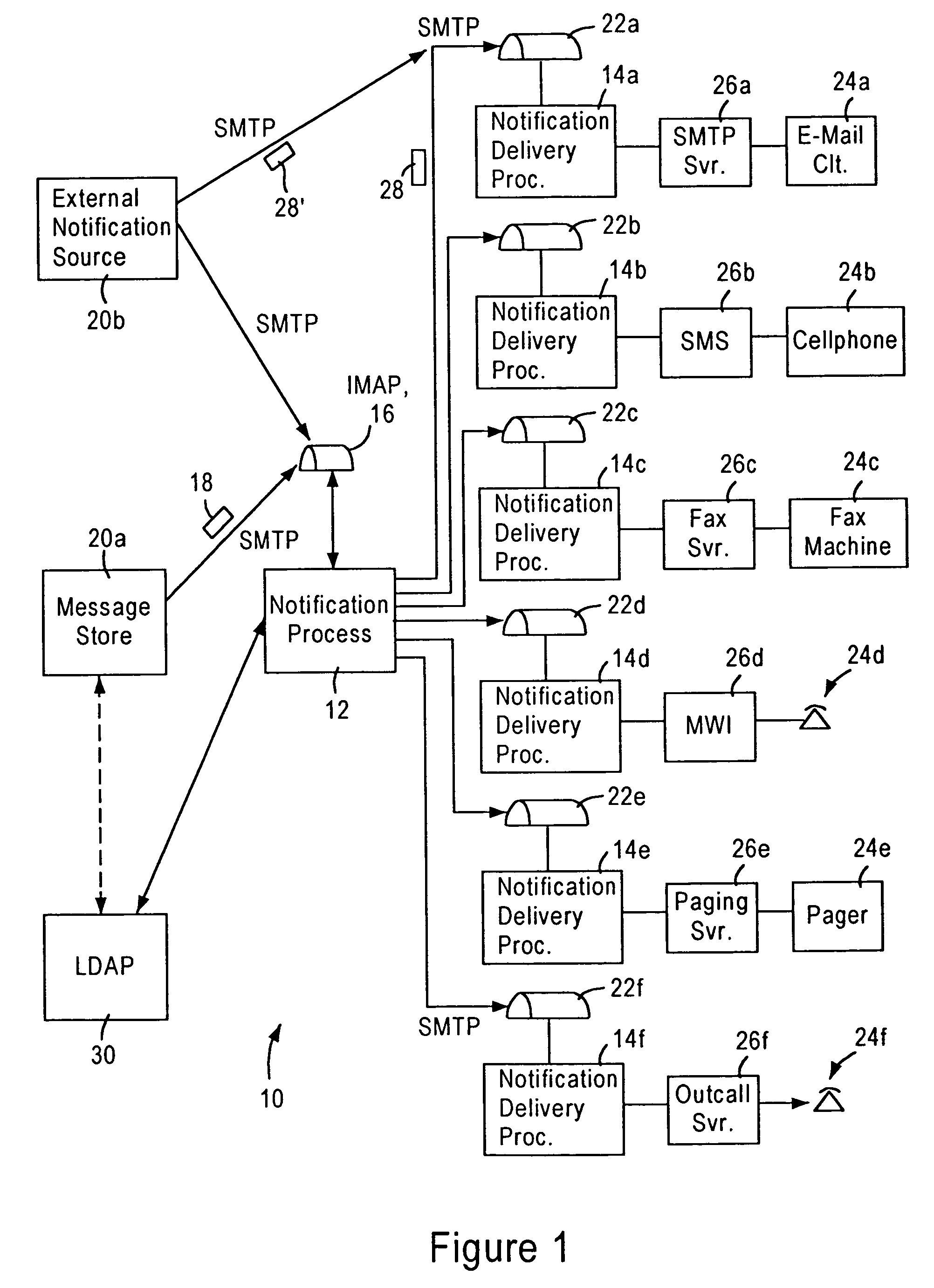
Scalable IP-based notification architecture for unified messaging
InactiveUS6874011B1Improve scalabilityIncrease capacityAutomatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsDevice typeOPEN protocol
A notification architecture utilizes multiple processes configured for managing notification operations based on reception of SMTP-based messages within IMAP based message stores. The notification architecture enables use of multiple instances of a notification process, each configured for receiving notification messages for respective subscribers from messaging sources according to a prescribed open protocol such as Internet Protocol. Each notification process accesses subscriber profile information from an open protocol-based subscriber directory based on the received notification messages. Each notification process determines, for each received notification message, the subscriber's notification preference based on the accessed profile information, and selectively outputs a notification delivery message according to a prescribed open protocol to at least one notification delivery process within the notification architecture based on the subscriber's notification preference. Each notification process may have access via the prescribed open protocol to multiple notification delivery processes, each configured for outputting a notification to a subscriber's notification device according to a corresponding device protocol. Multiple instances of each type of notification delivery process may also be utilized for increased capacity. Hence, subscribers may be notified of events according to their respective preferences, including subscriber device type, or time of notification. Moreover, the notification architecture can be scaled without adversely affecting any existing instances of the notification process or the notification delivery processes.
Owner:CISCO TECH INC
Scalable IP-based notification architecture for unified messaging
InactiveUS20050177622A1Improve scalabilityIncrease capacityTime-division multiplexMultiple digital computer combinationsDevice typeOPEN protocol
A notification architecture utilizes multiple processes configured for managing notification operations based on reception of SMTP-based messages within IMAP based message stores. The notification architecture enables use of multiple instances of a notification process, each configured for receiving notification messages for respective subscribers from messaging sources according to a prescribed open protocol such as Internet Protocol. Each notification process accesses subscriber profile information from an open protocol-based subscriber directory based on the received notification messages. Each notification process determines, for each received notification message, the subscriber's notification preference based on the accessed profile information, and selectively outputs a notification delivery message according to a prescribed open protocol to at least one notification delivery process within the notification architecture based on the subscriber's notification preference. Each notification process may have access via the prescribed open protocol to multiple notification delivery processes, each configured for outputting a notification to a subscriber's notification device according to a corresponding device protocol. Multiple instances of each type of notification delivery process may also be utilized for increased capacity. Hence, subscribers may be notified of events according to their respective preferences, including subscriber device type, or time of notification. Moreover, the notification architecture can be scaled without adversely affecting any existing instances of the notification process or the notification delivery processes.
Owner:CISCO TECH INC
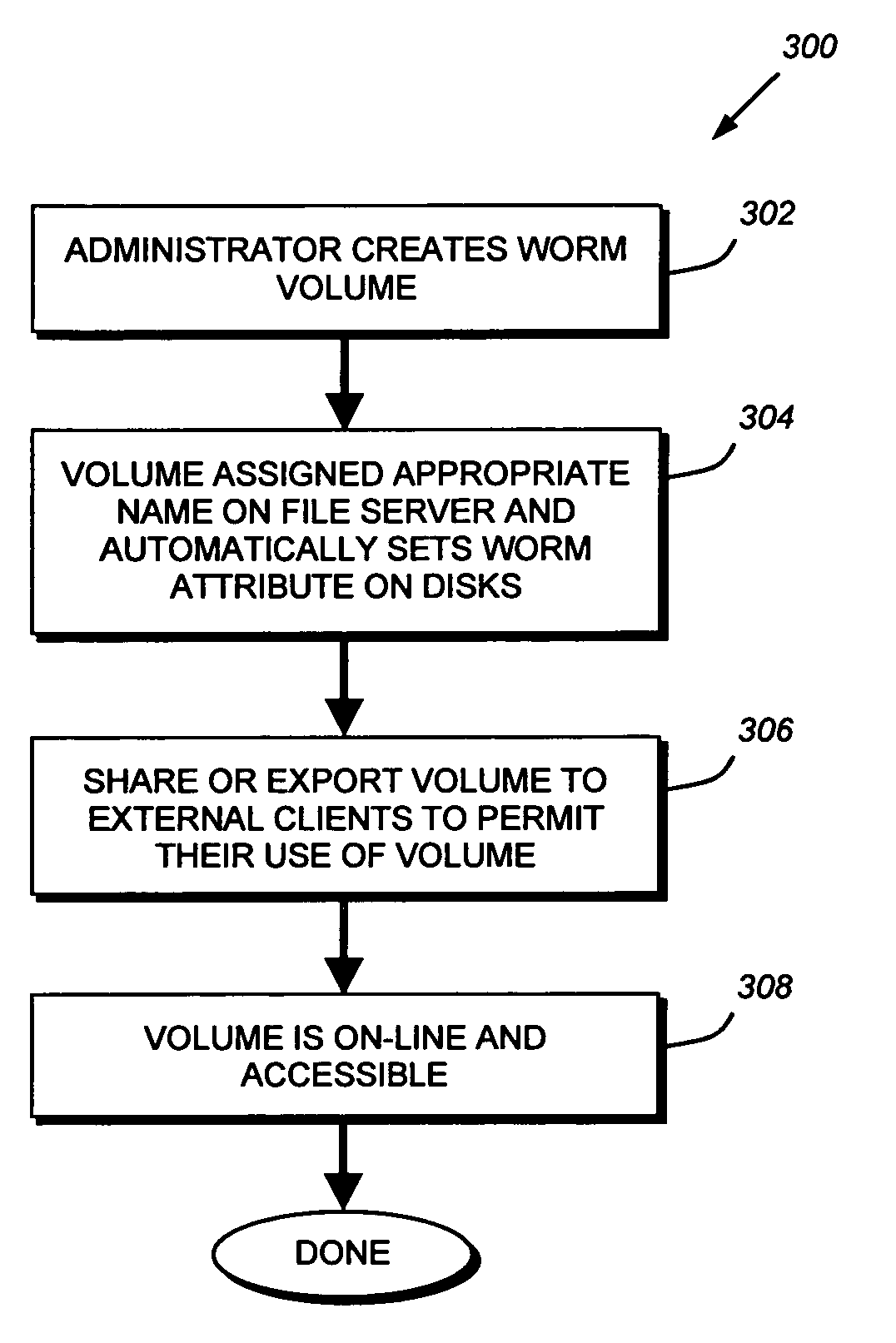
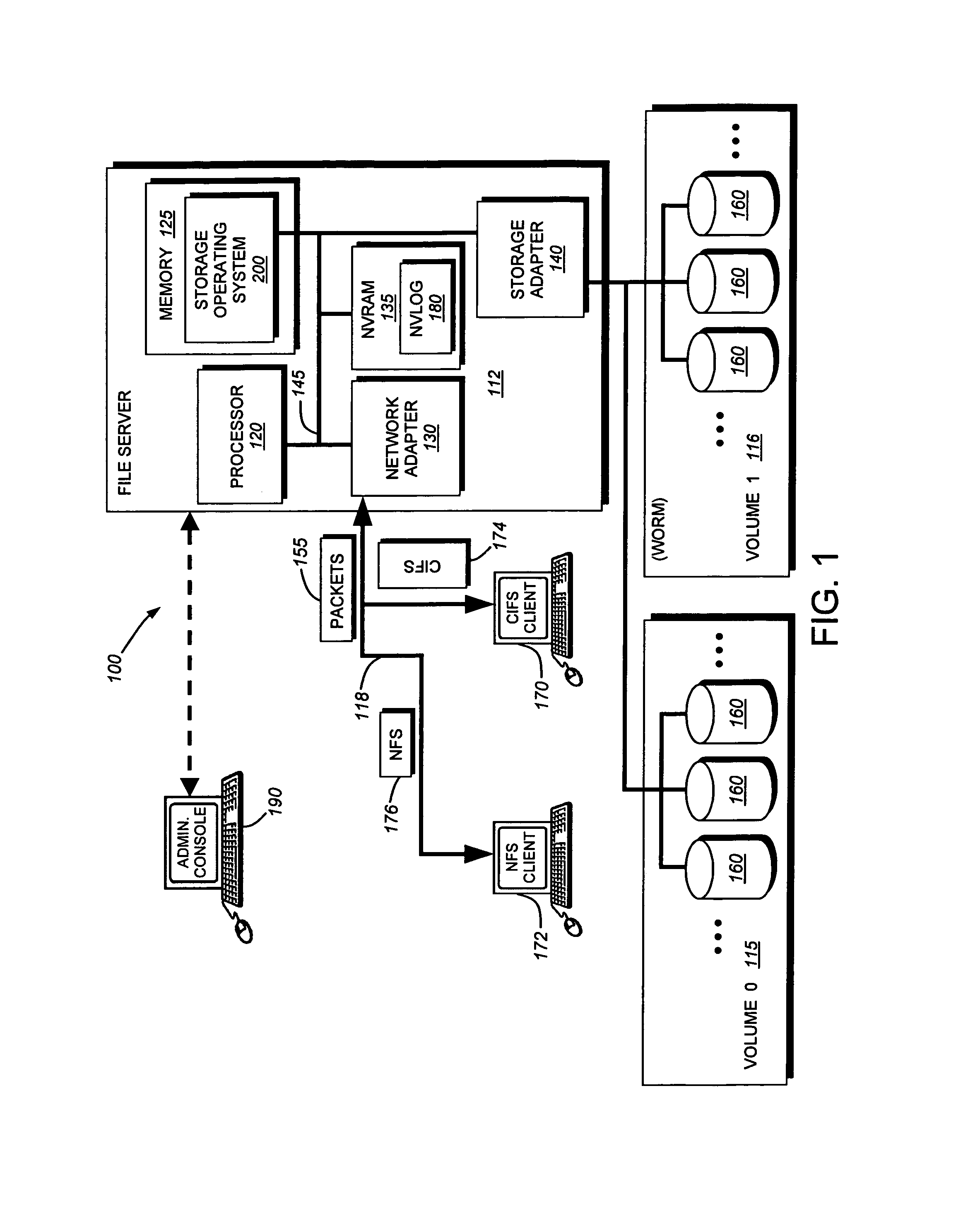
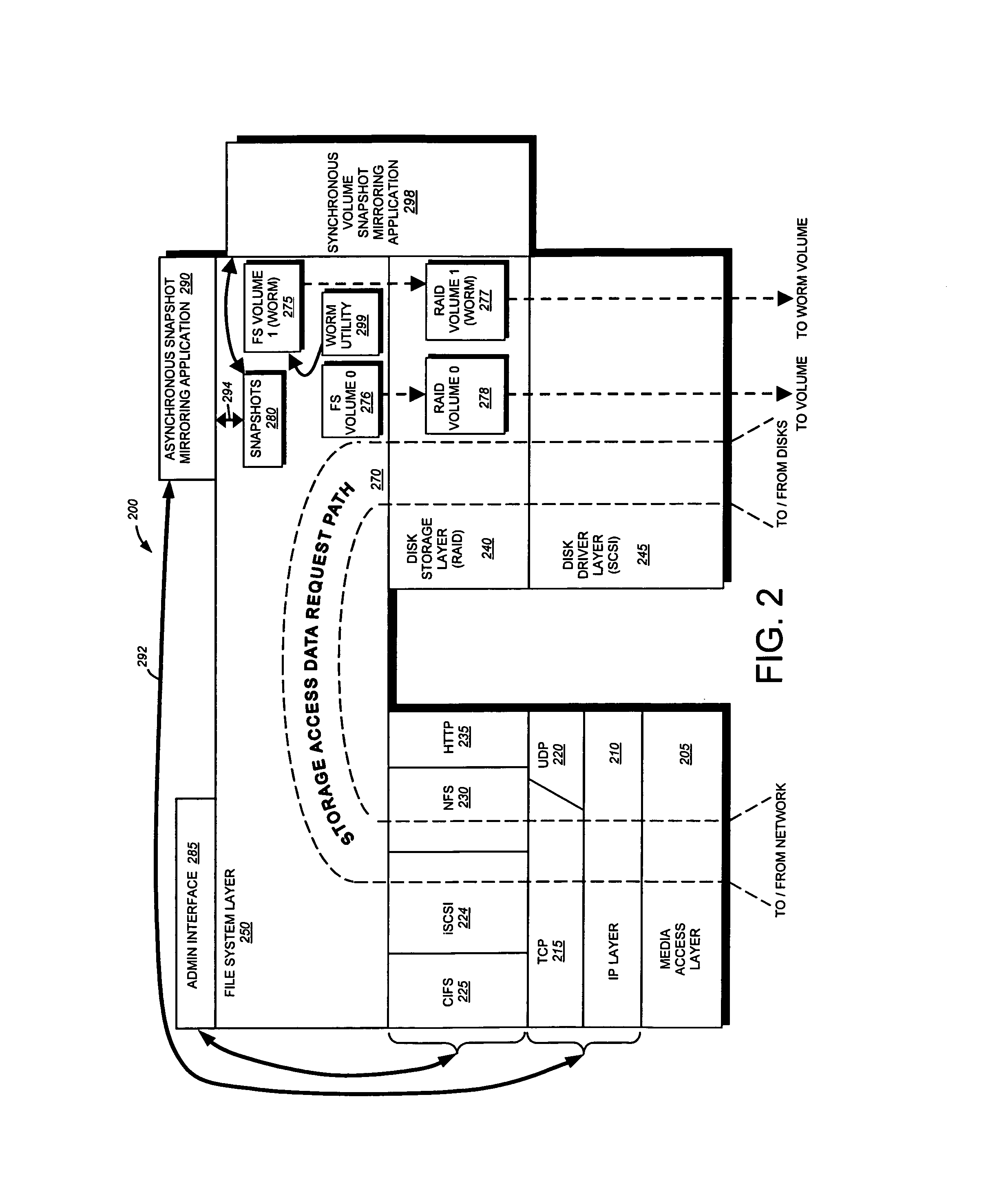
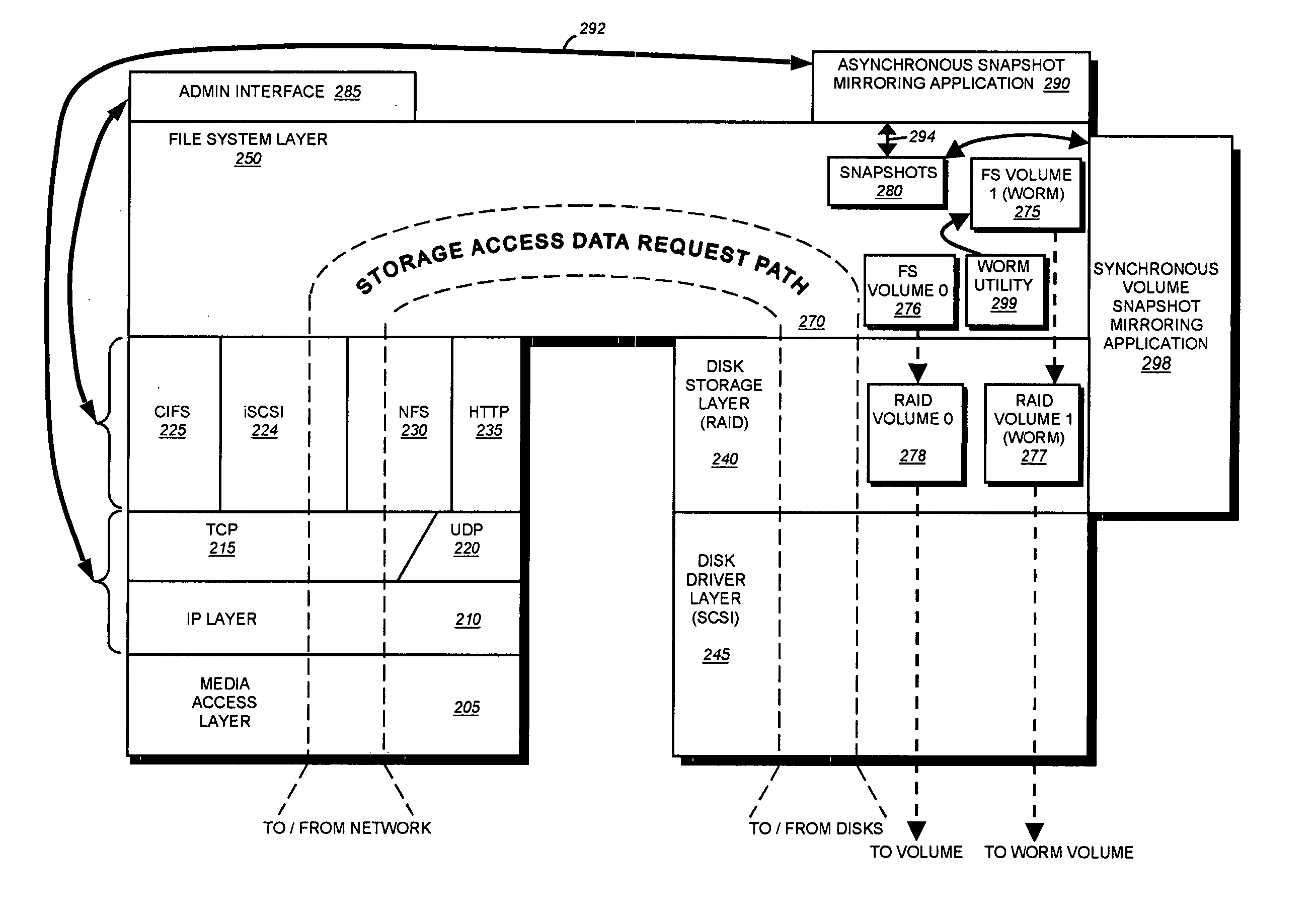
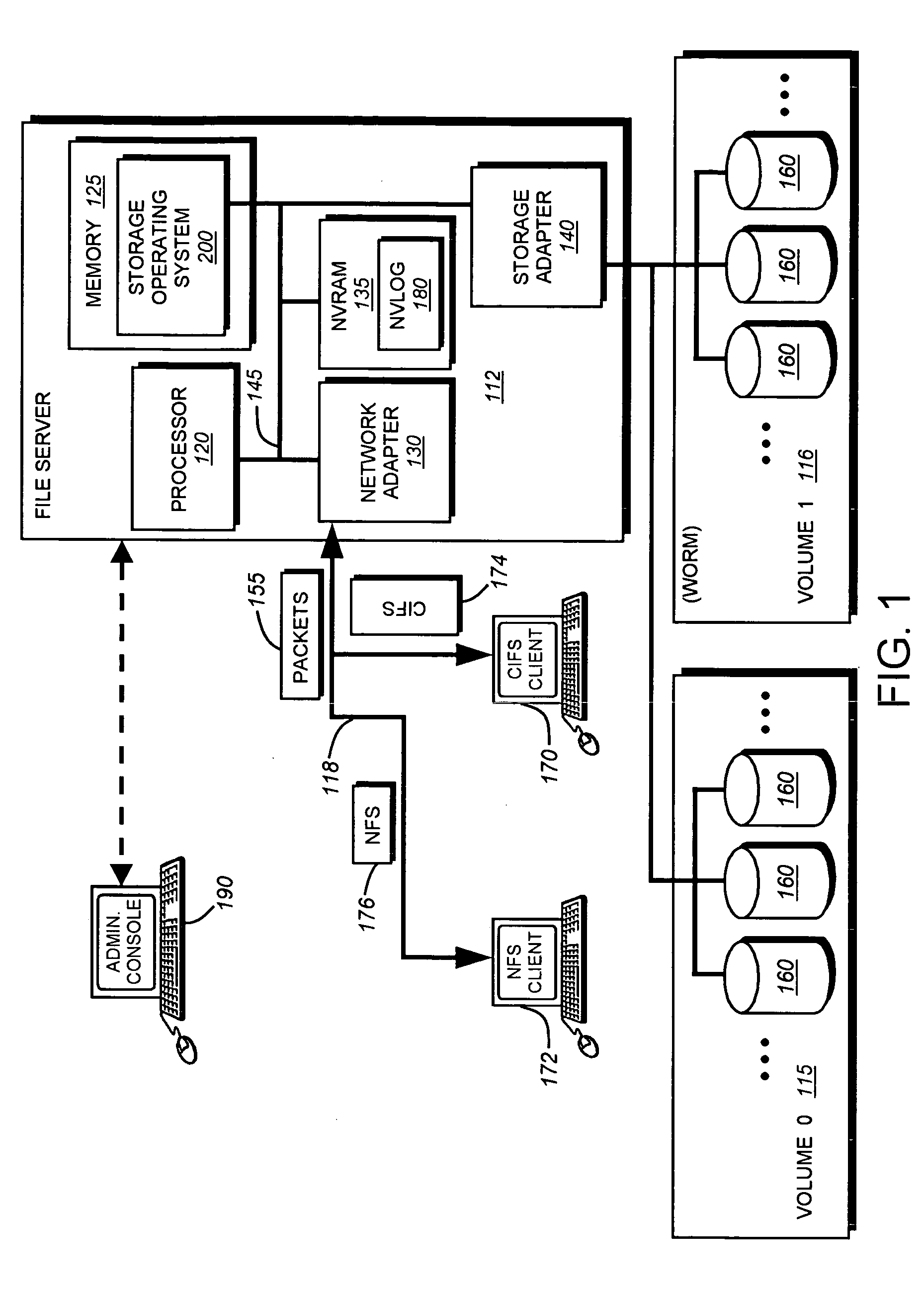
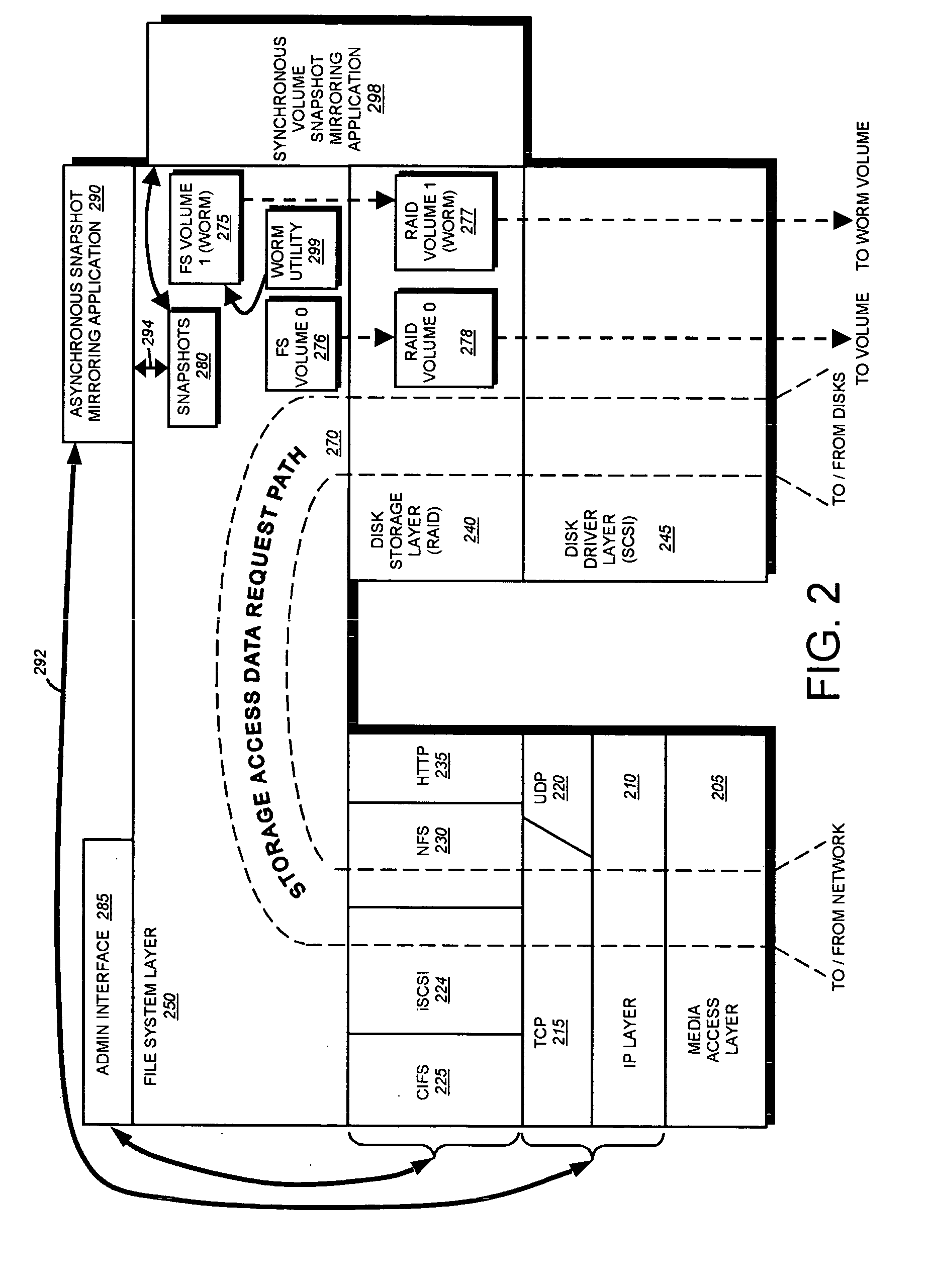
Write-once-read-many storage system and method for implementing the same
ActiveUS7155460B2Improve performanceInput/output to record carriersData processing applicationsOperational systemFile system
A write-once-read-many (WORM) storage system that employs large-capacity and relatively inexpensive disks in connection with a file system on a file server is provided. The file system contains most or all of the required WORM functionality so as to impose a minimal footprint on client applications, client operating systems and open protocols if desired. The system is organized around WORM storage volumes that contain files that, when committed to WORM storage, cannot be deleted or modified. Any file path or directory tree structure used to identify the file within the WORM volume is locked and cannot be deleted. In one embodiment, the administrator creates a WORM volume, capable of storing designated WORM files. The client then creates an appropriate WORM file using the appropriate protocol semantics. The file is written to the volume and committed by transitioning the file attributes from a not-read-only to a read-only state. The file system recognizes the persistently stored WORM attribute of any file in a WORM volume as WORM file. Henceforth, any attempt to modify the file attributes, write to the file, or delete the file, by clients, administrators or other entities is rejected and a request denied message is returned to the attempting party
Owner:NETWORK APPLIANCE INC
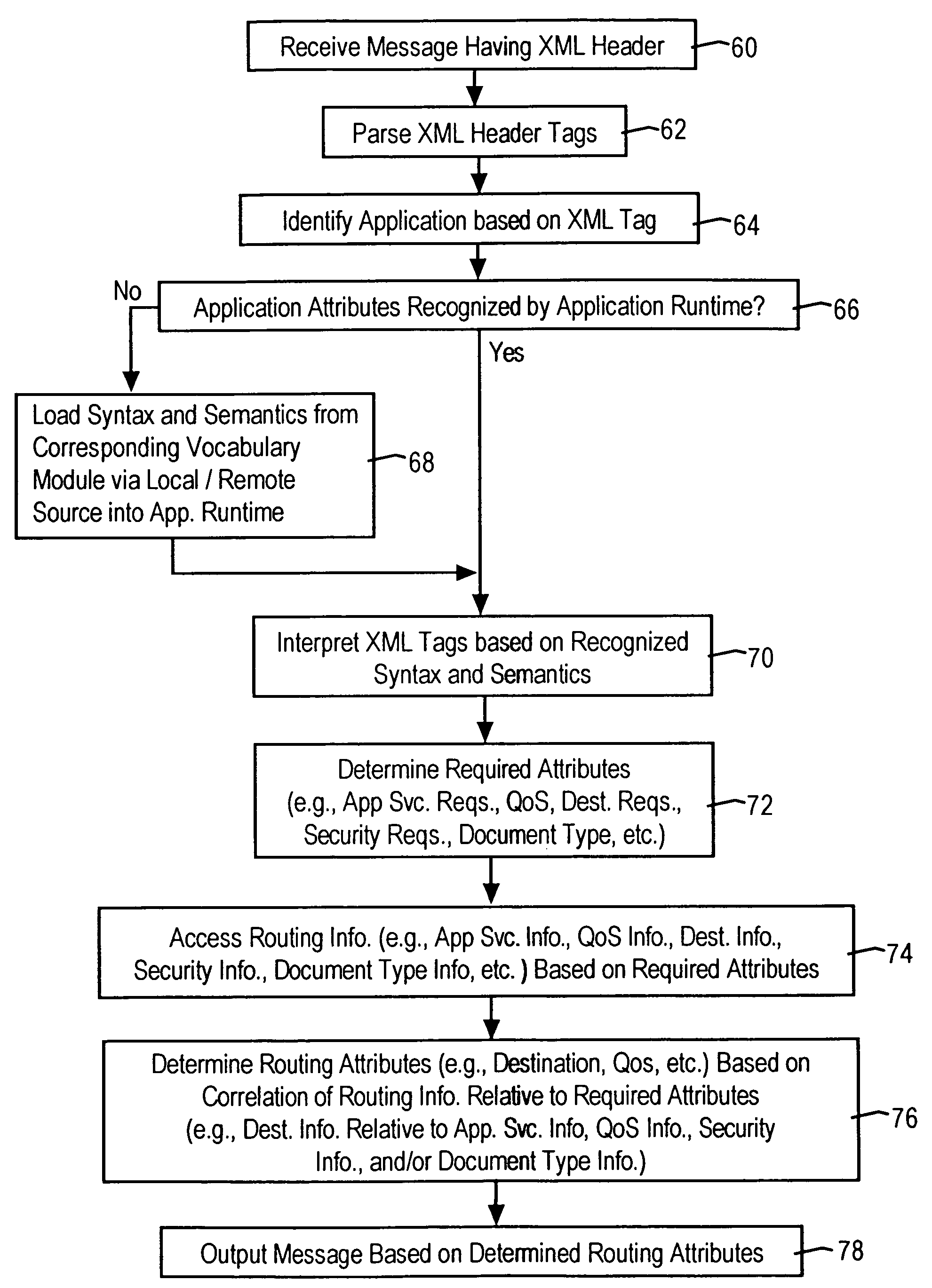
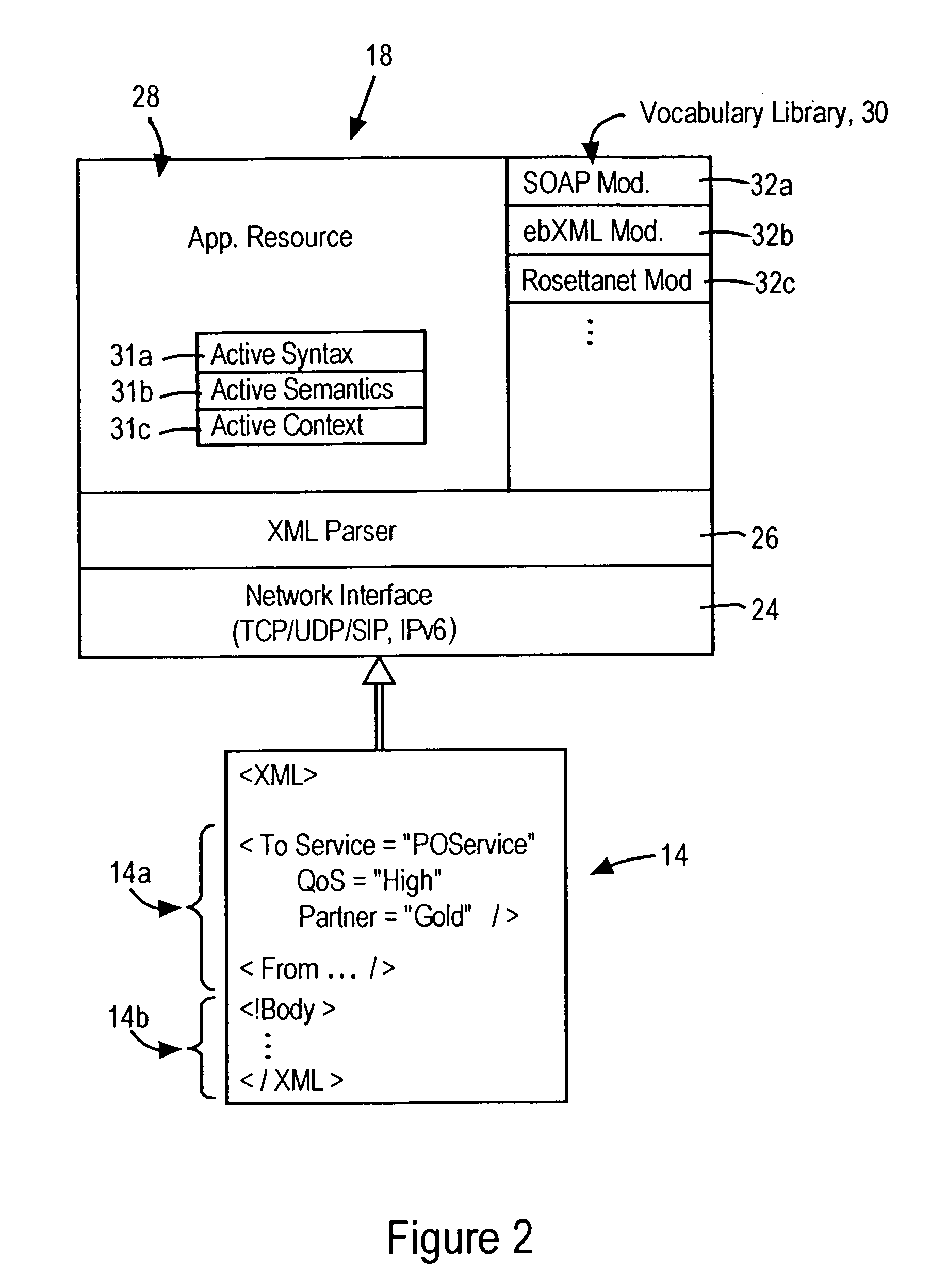
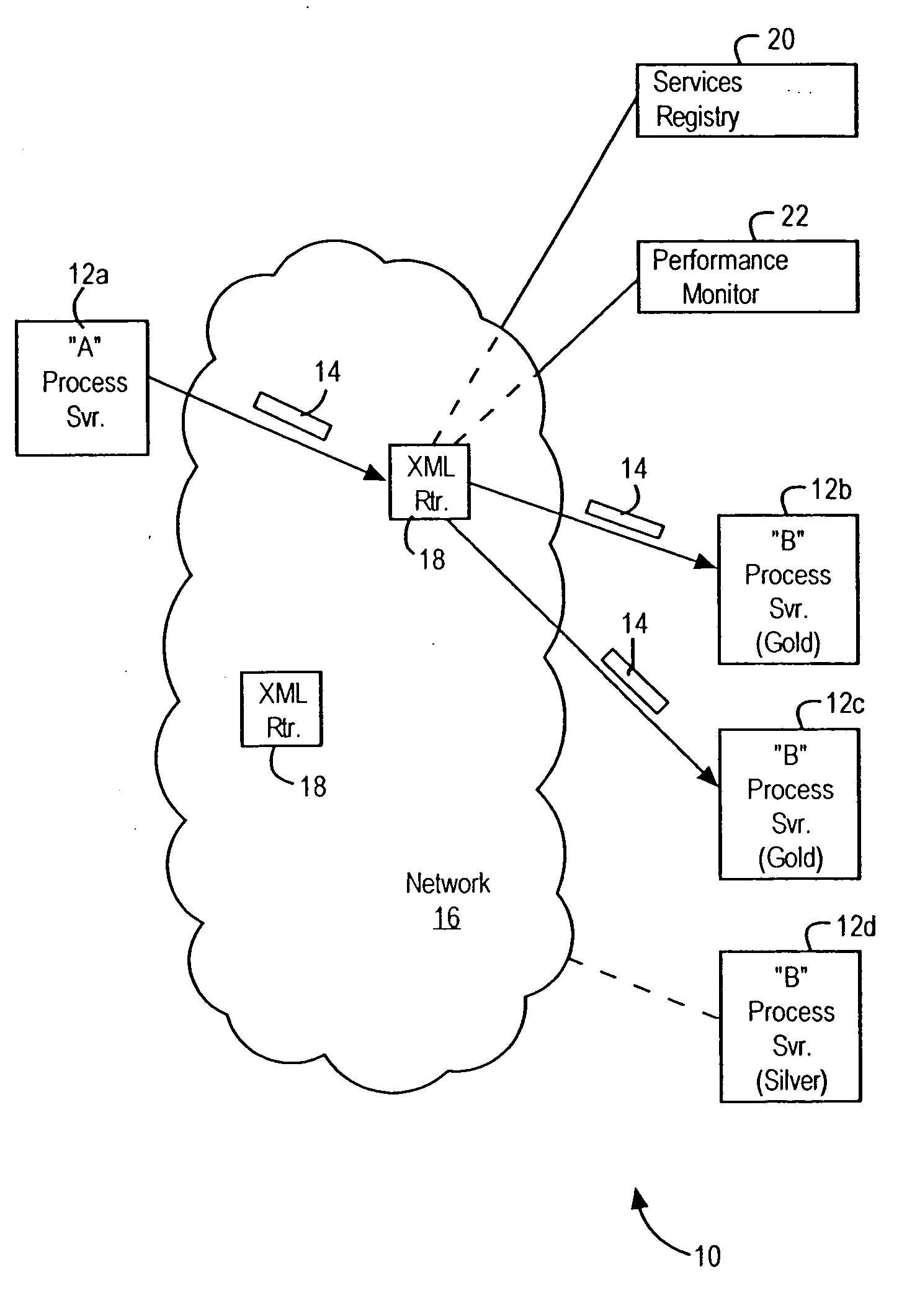
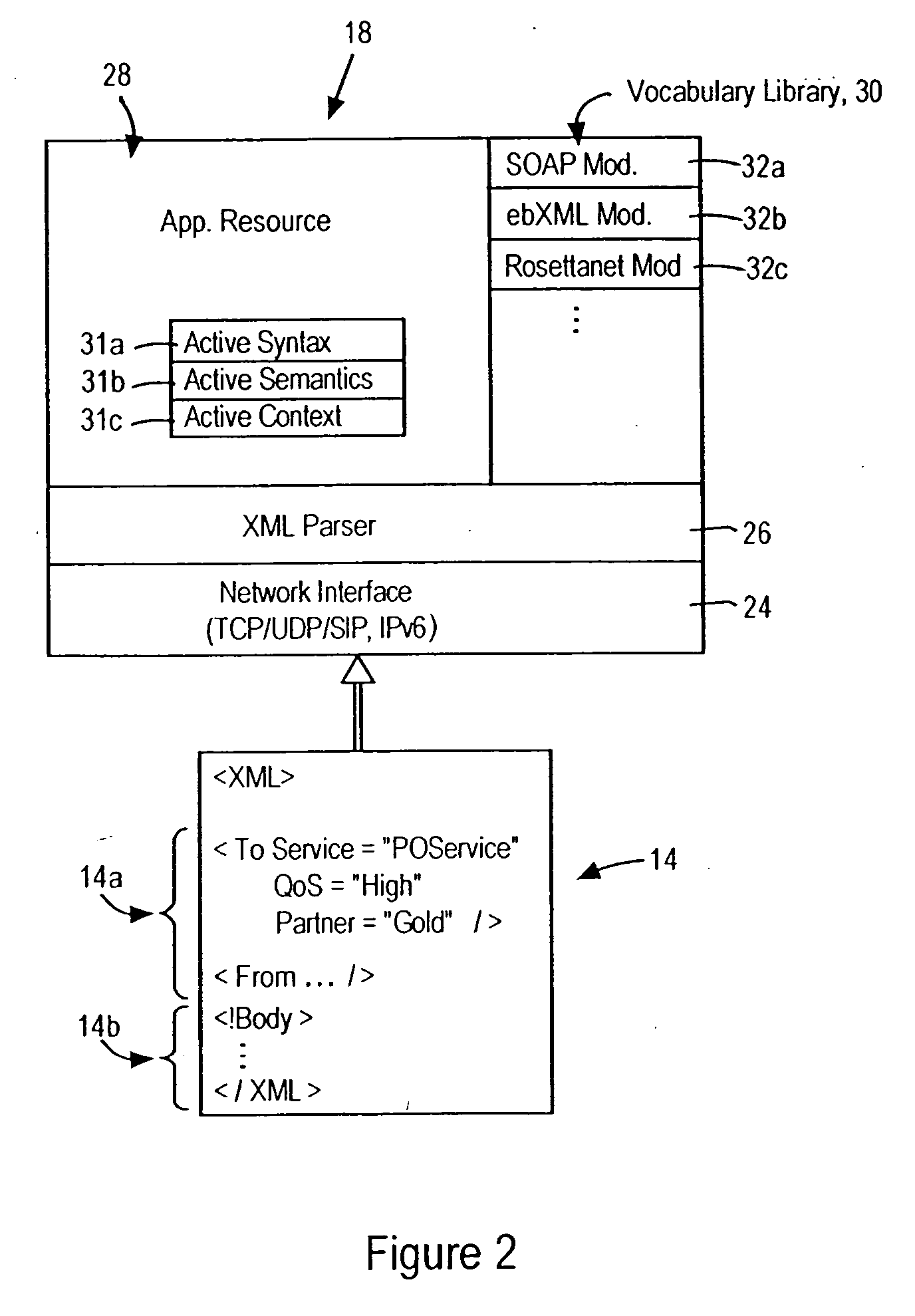
Network router configured for executing network operations based on parsing XML tags in a received XML document
InactiveUS7065706B1Good serviceIncreased “vocabularyDigital computer detailsTransmissionSemanticsMessage routing
A router is configured for routing, via an open protocol network, a received message to a destination node based on parsing an XML portion within the received message. The router includes an XML parser configured for parsing XML tags specifying prescribed attributes, and an application resource configured for interpreting the prescribed attributes for a determined service based on runtime execution of the application resource. In particular, the runtime execution of the application resource provides application-specific syntax and semantics enabling interpretation of the parsed XML tags. The application resource, in response to interpreting the prescribed attributes, initiates selected application operations, including outputting the received message to a prescribed destination, based on the execution of the prescribed application operations.
Owner:CISCO TECH INC
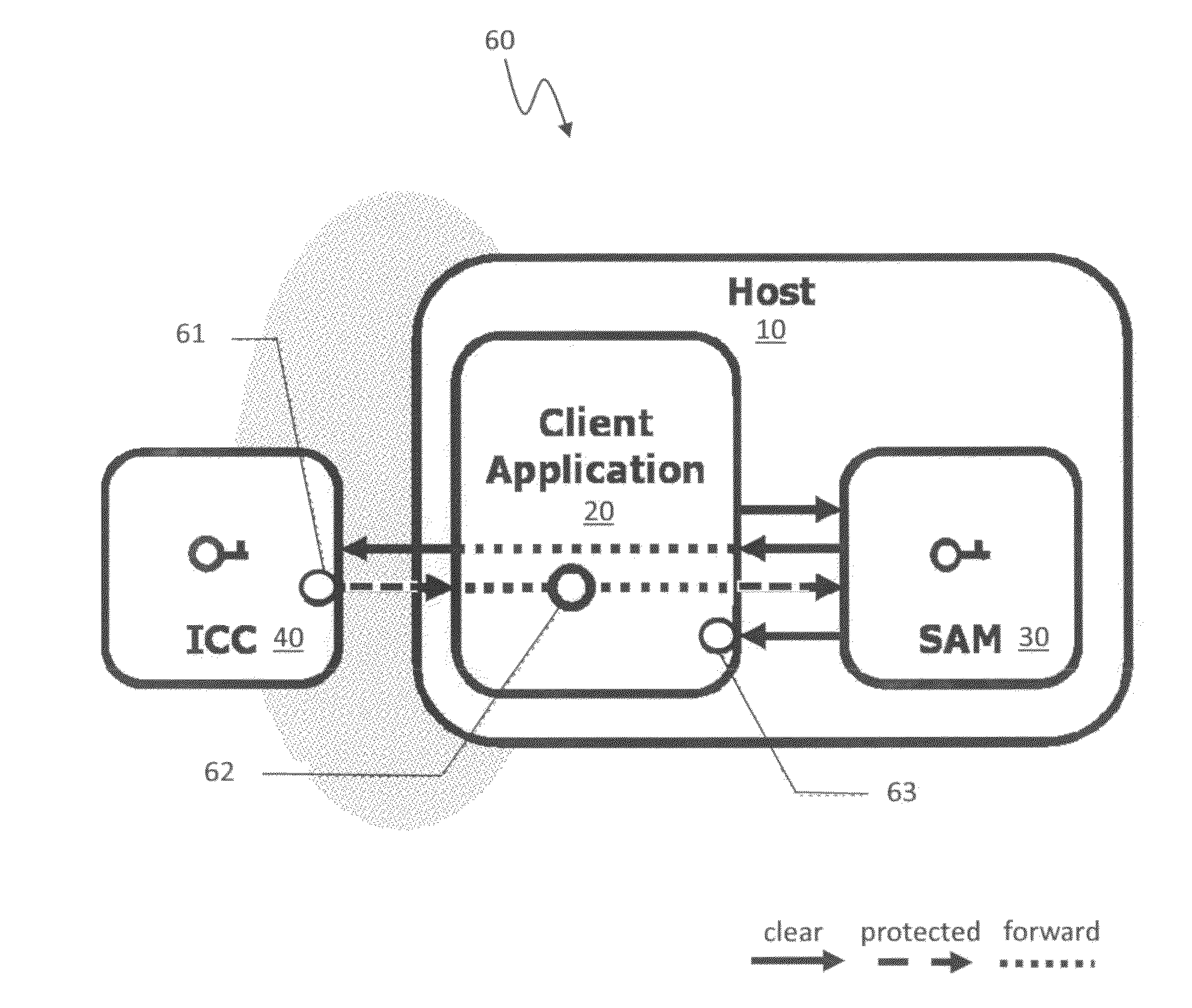
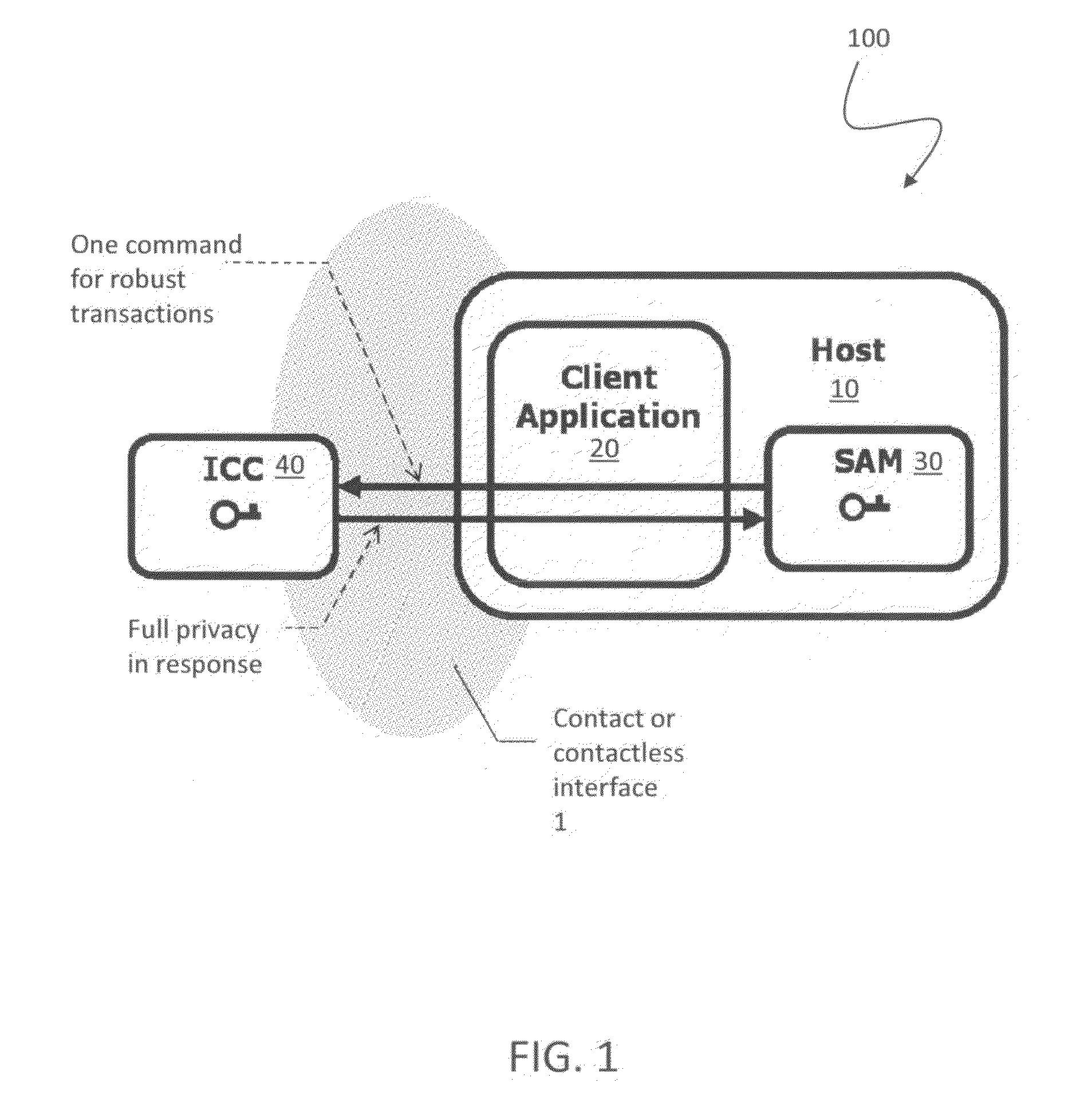
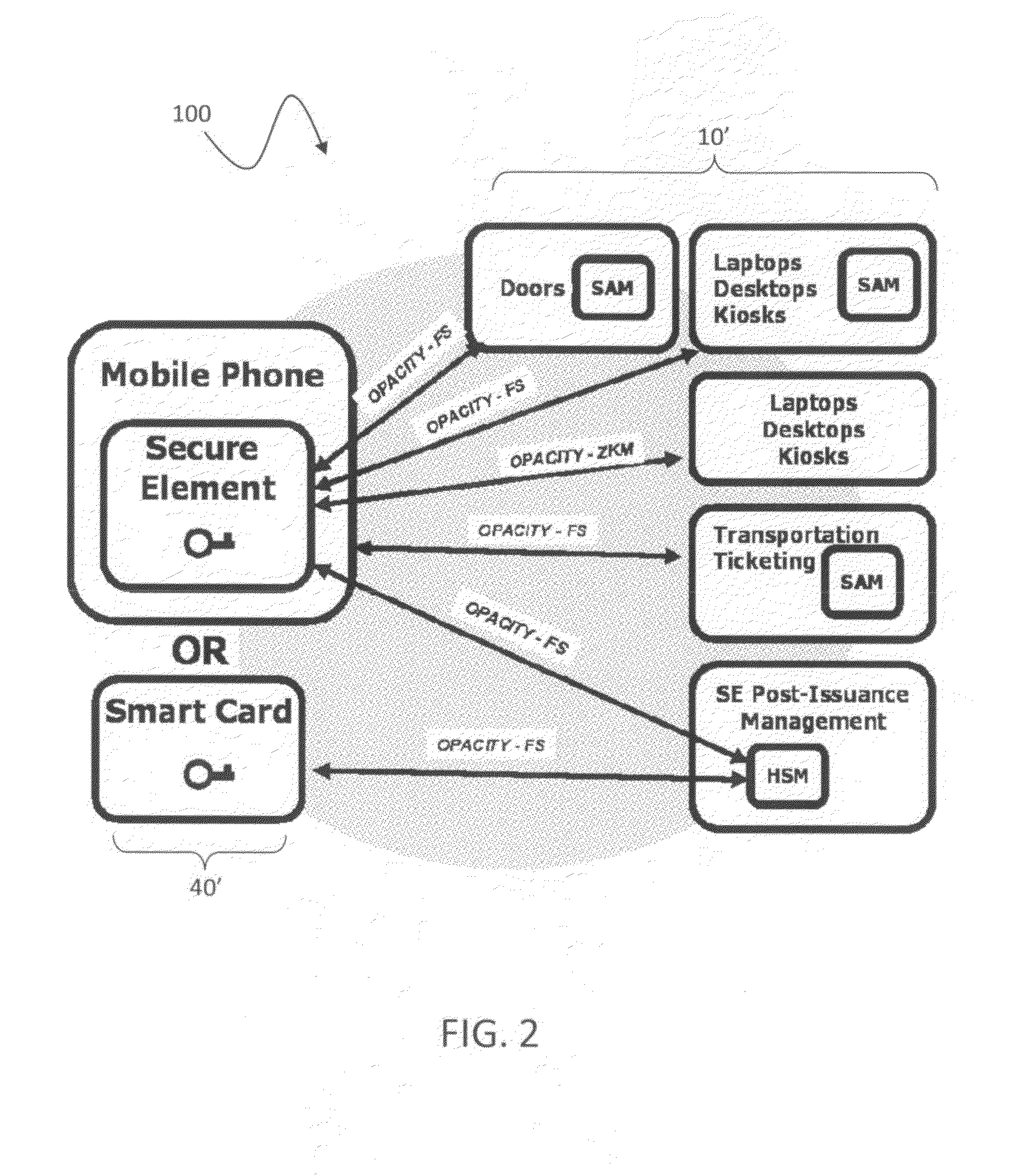
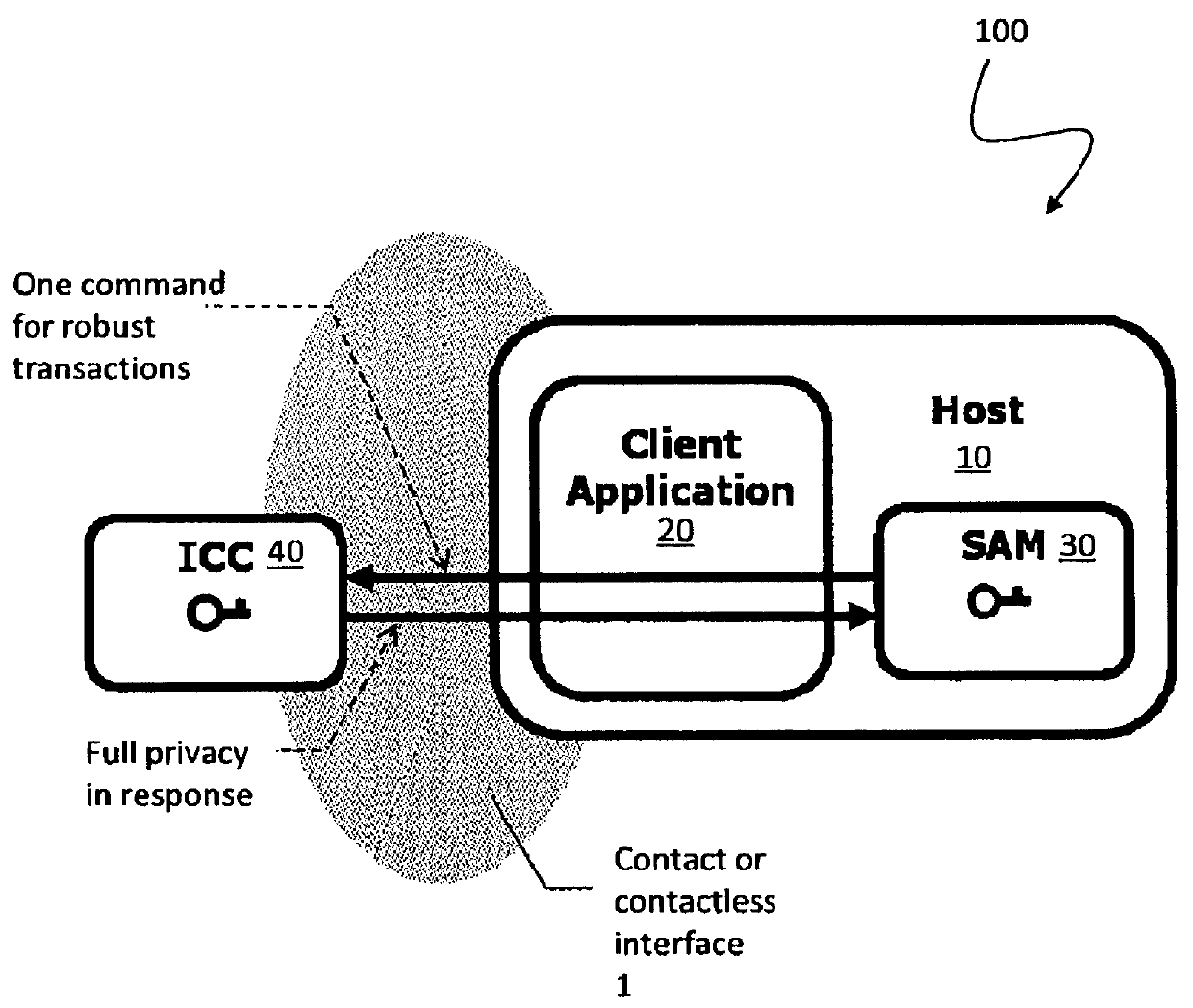
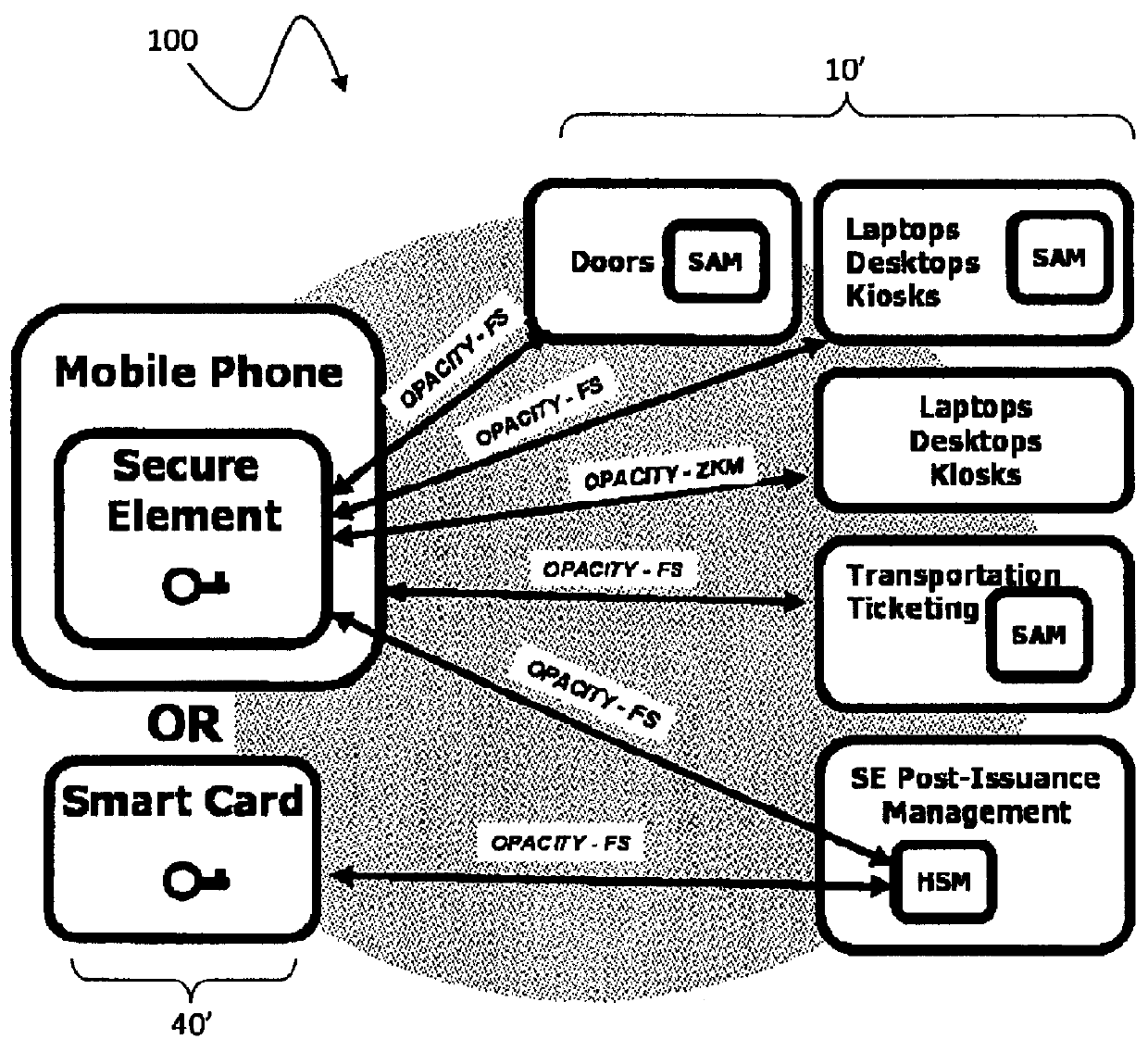
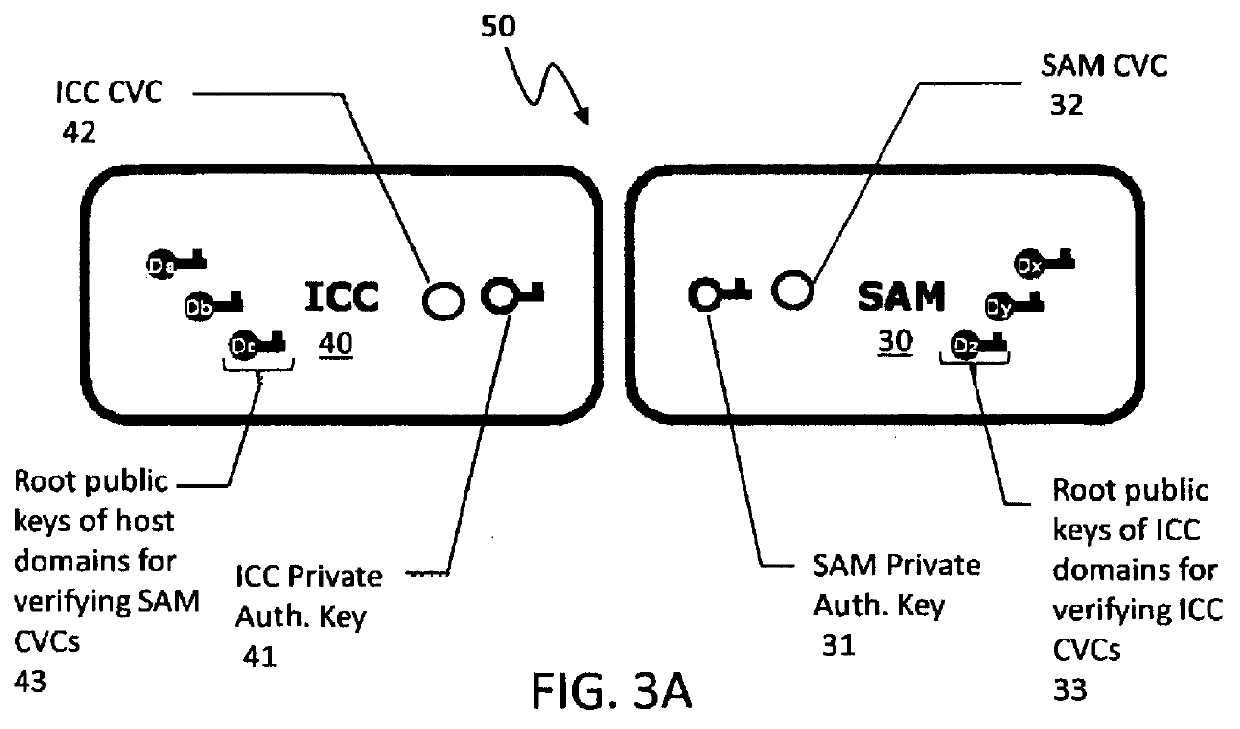
Open protocol for authentication and key establishment with privacy
ActiveUS20120144193A1Public key for secure communicationUser identity/authority verificationSmart cardPhysical access
A suite of efficient authentication and key establishment protocols for securing contact or contactless interfaces between communicating systems. The protocols may be used in secure physical access, logical access and / or transportation applications, among other implementations. The system authenticates a mobile device such as a smart card and / or mobile phone equipped with a secure element presented to one or more host terminals and establishes shared secure messaging keys to protect communications between the device and terminal. Secure messaging provides an end-to-end protected path of digital documents or transactions through the interface. The protocols provide that the device does not reveal identification information to entities different from a trusted host. The terminal may be a contactless reader at a door for controlling physical access, a desktop, laptop or kiosk for controlling logical access, and / or an access point for obtaining an encrypted digital ticket from an authenticated mobile device used for transit applications.
Owner:ASSA ABLOY AB
Open protocol for authentication and key establishment with privacy
ActiveUSH2270H1Public key for secure communicationUser identity/authority verificationSmart cardPhysical access
A suite of efficient authentication and key establishment protocols for securing contact or contactless interfaces between communicating systems. The protocols may be used in secure physical access, logical access and / or transportation applications, among other implementations. The system authenticates a mobile device such as a smart card and / or mobile phone equipped with a secure element presented to one or more host terminals and establishes shared secure messaging keys to protect communications between the device and terminal. Secure messaging provides an end-to-end protected path of digital documents or transactions through the interface. The protocols provide that the device does not reveal identification information to entities different from a trusted host. The terminal may be a contactless reader at a door for controlling physical access, a desktop, laptop or kiosk for controlling logical access, and / or an access point for obtaining an encrypted digital ticket from an authenticated mobile device used for transit applications.
Owner:ASSA ABLOY AB
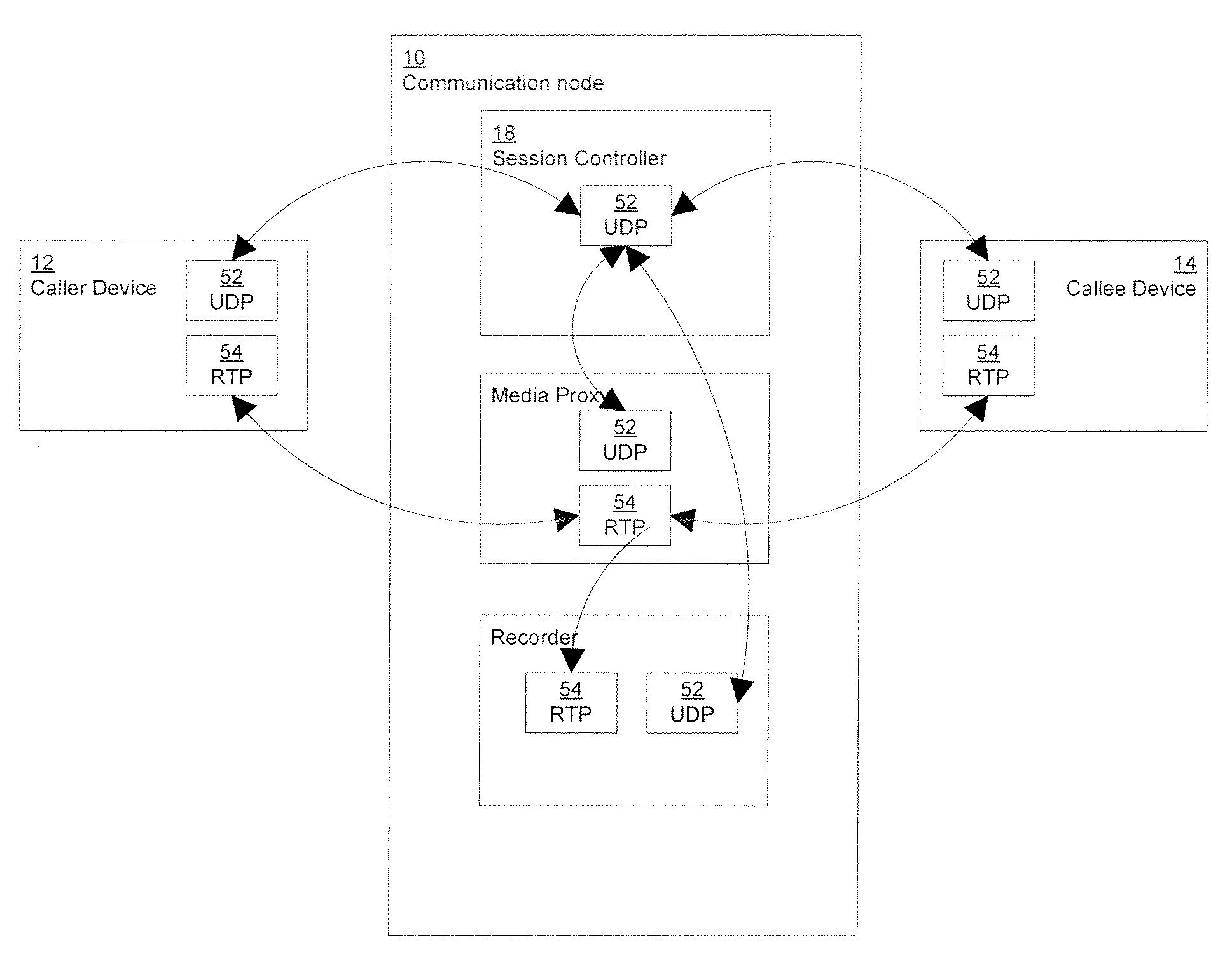
Communication node and method for handling sip communication
The present invention relates to a communication node and method for connecting and maintaining a call between a caller device and a callee device. The communication node comprises a session controller module and a plurality of internal SIP UA (Session Initiation Protocol User Agent) servers. The session controller module is adapted to remain in communication with the caller device and the callee device through a whole duration of the call. The plurality of internal SIP UA servers is adapted to communicate with the session controller module by open protocol.
Owner:PARAXIP TECH
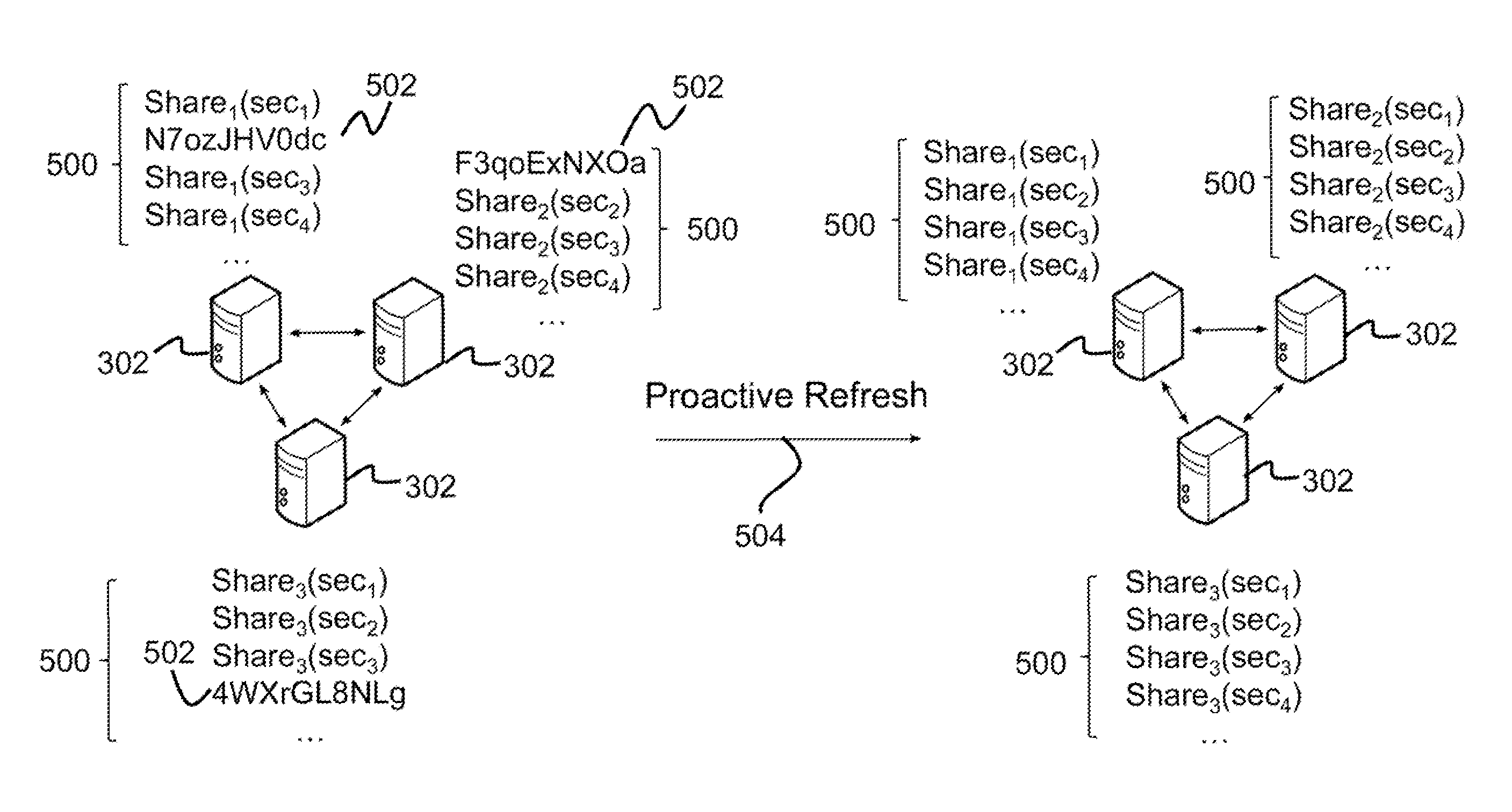
Method for secure and resilient distributed generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures with proactive security
ActiveUS9489522B1User identity/authority verificationDigital data protectionActive safetySecret share
Described is system for generation of elliptic curve digital signature algorithm (ECDSA) based digital signatures. A Secret-Share protocol is initialized between a client and a set of servers to share a set of shares of a private key s among the set of servers. The set of servers initializes a protocol to generate a digital signature on a message using the set of shares of the private key s without reconstructing or revealing the private key s. The set of servers periodically initializes a Secret-Redistribute protocol on each share of the private key s to re-randomize the set of shares. A Secret-Open protocol is initialized to reveal the private key s to an intended recipient, wherein the private key s is used to compute the digital signature.
Owner:HRL LAB
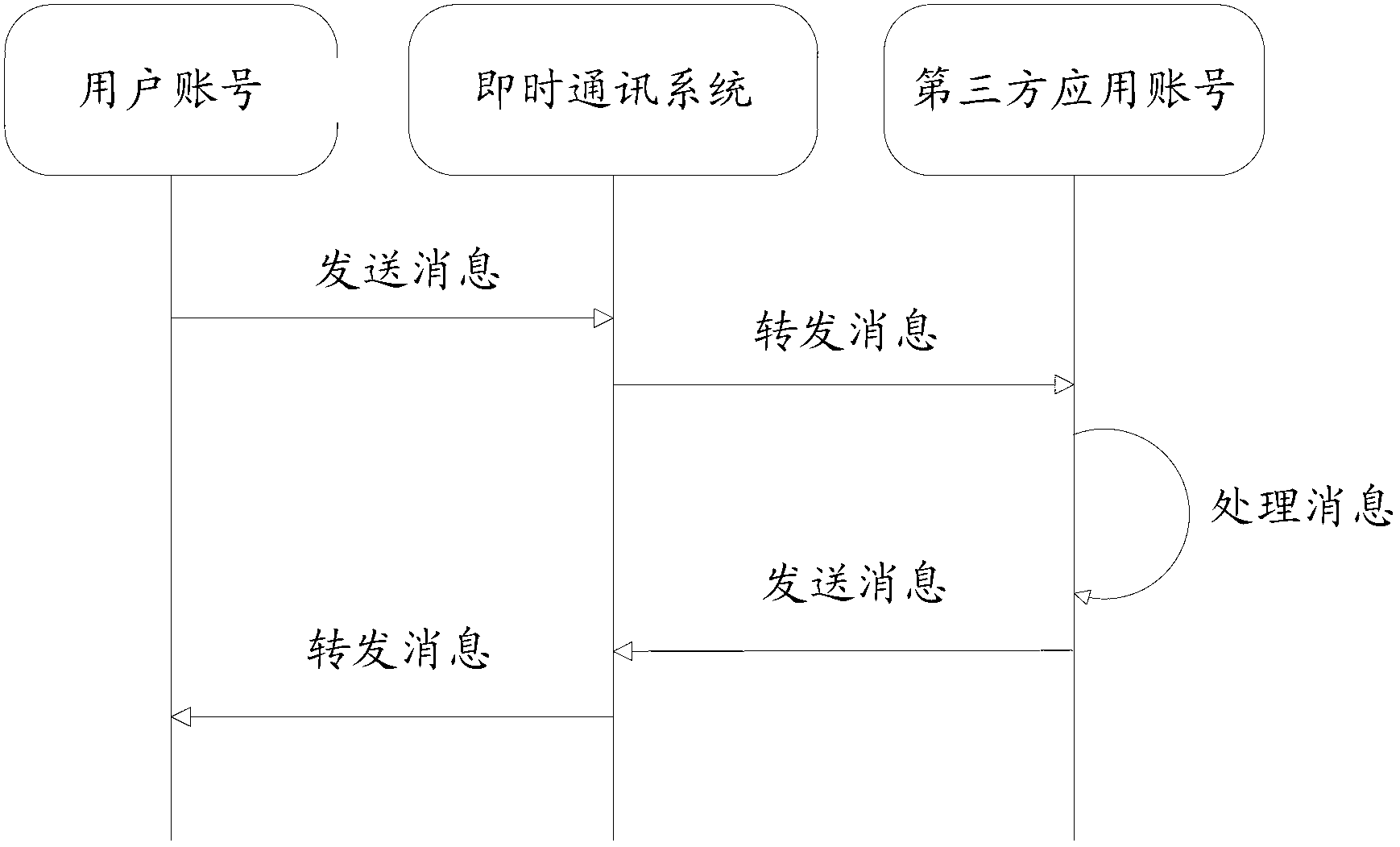
Method, device and equipment for interacting with third-party application in instant messaging system
ActiveCN103297325AVersatileMeet needsData switching networksSpecial data processing applicationsThird partyApplication programming interface
An embodiment of the invention provides a method for interacting with a third-party application in instant messaging system. The instant messaging system provides an open protocol for the third-party application, and the third-party application is provided with an API (application programming interface) generated according to the protocol. The method includes accessing to the second-party application through the API, and acquiring information sent by the third-party application. By the method, a user can invoke related services of the third-party application in the instant messaging system directly, complicated operations when the user acquires the services are decreased, occupancy of time resources is reduced, and services of the third-party application are acquired conveniently and quickly.
Owner:XIAOMI INC
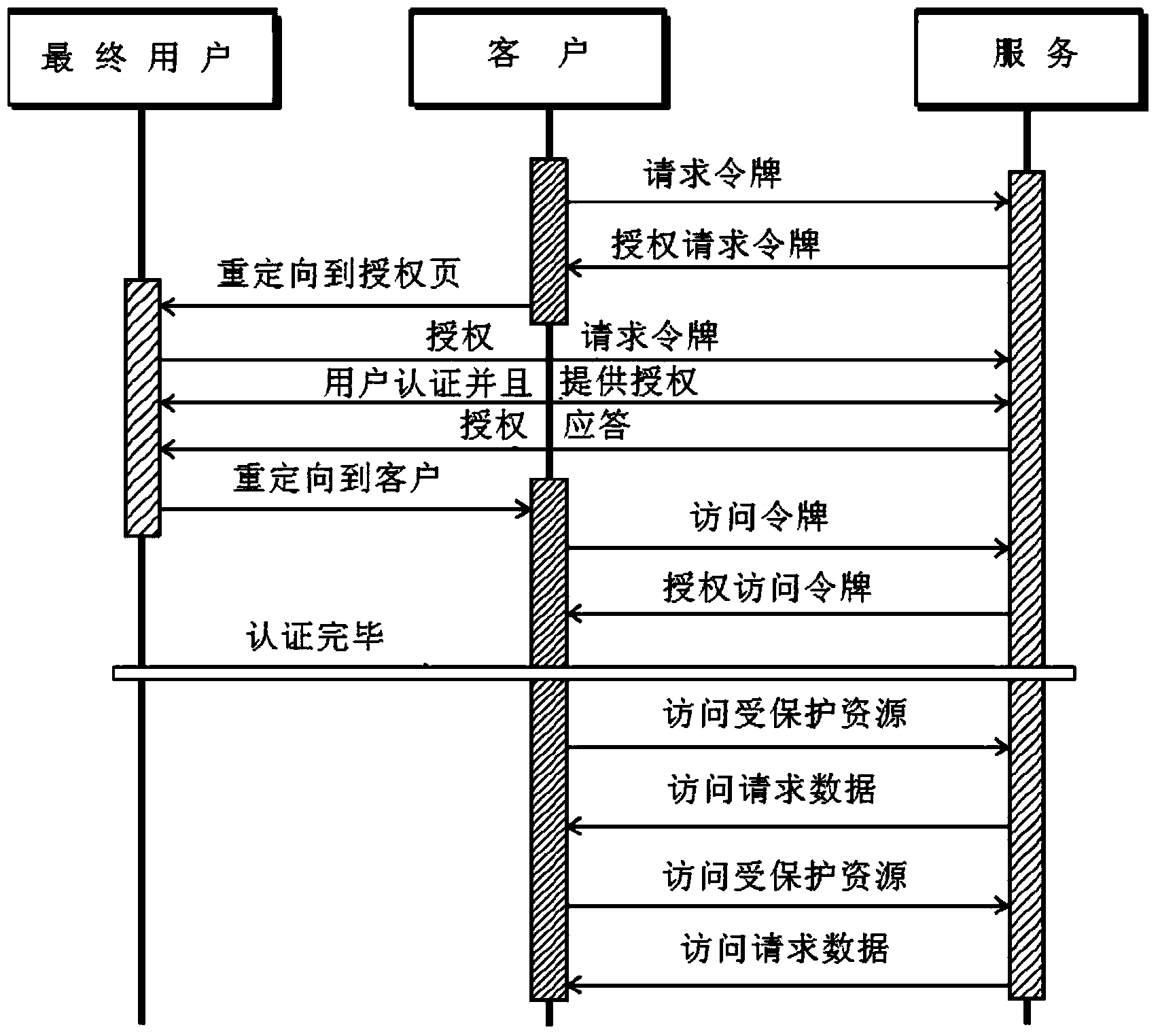
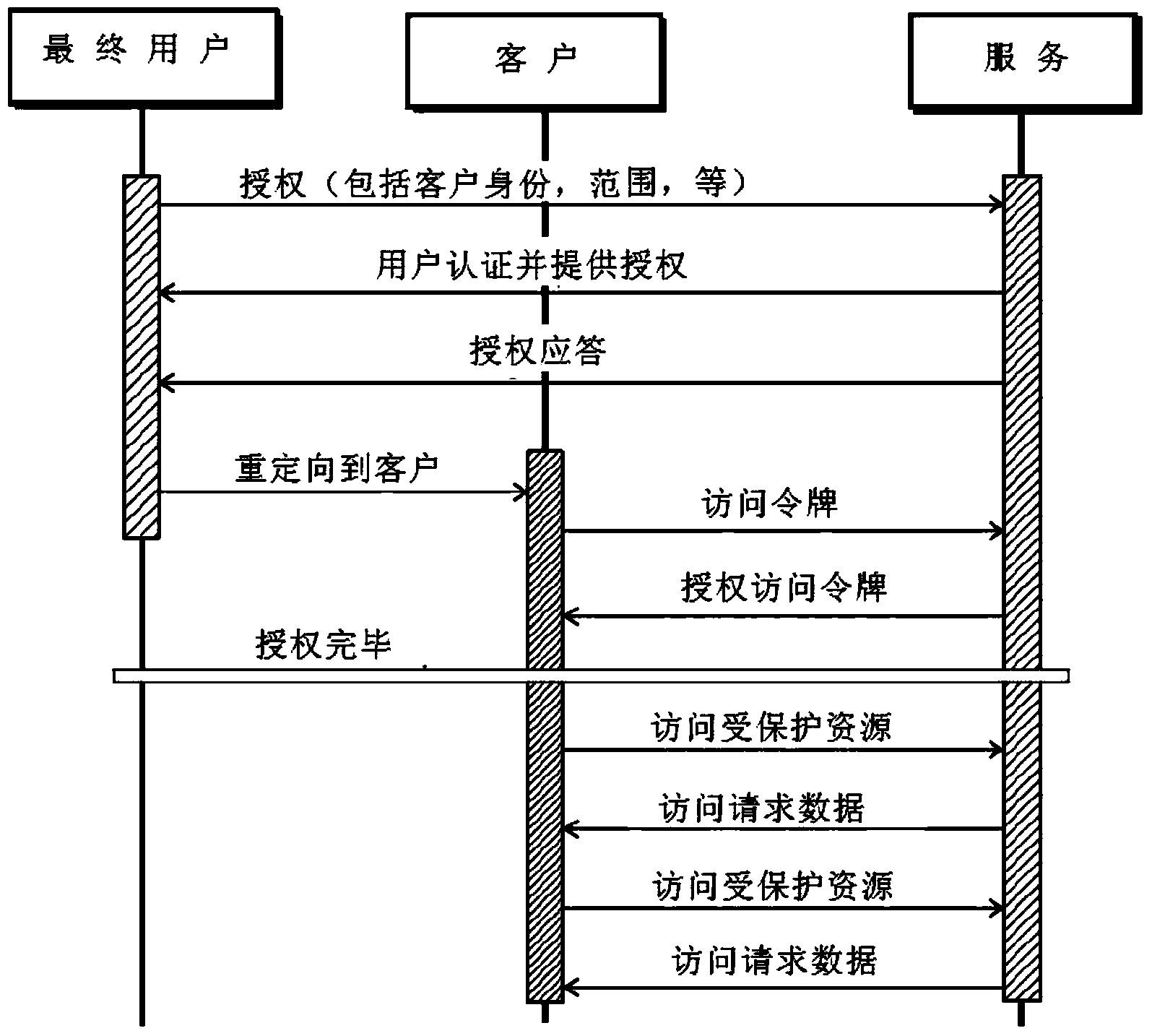
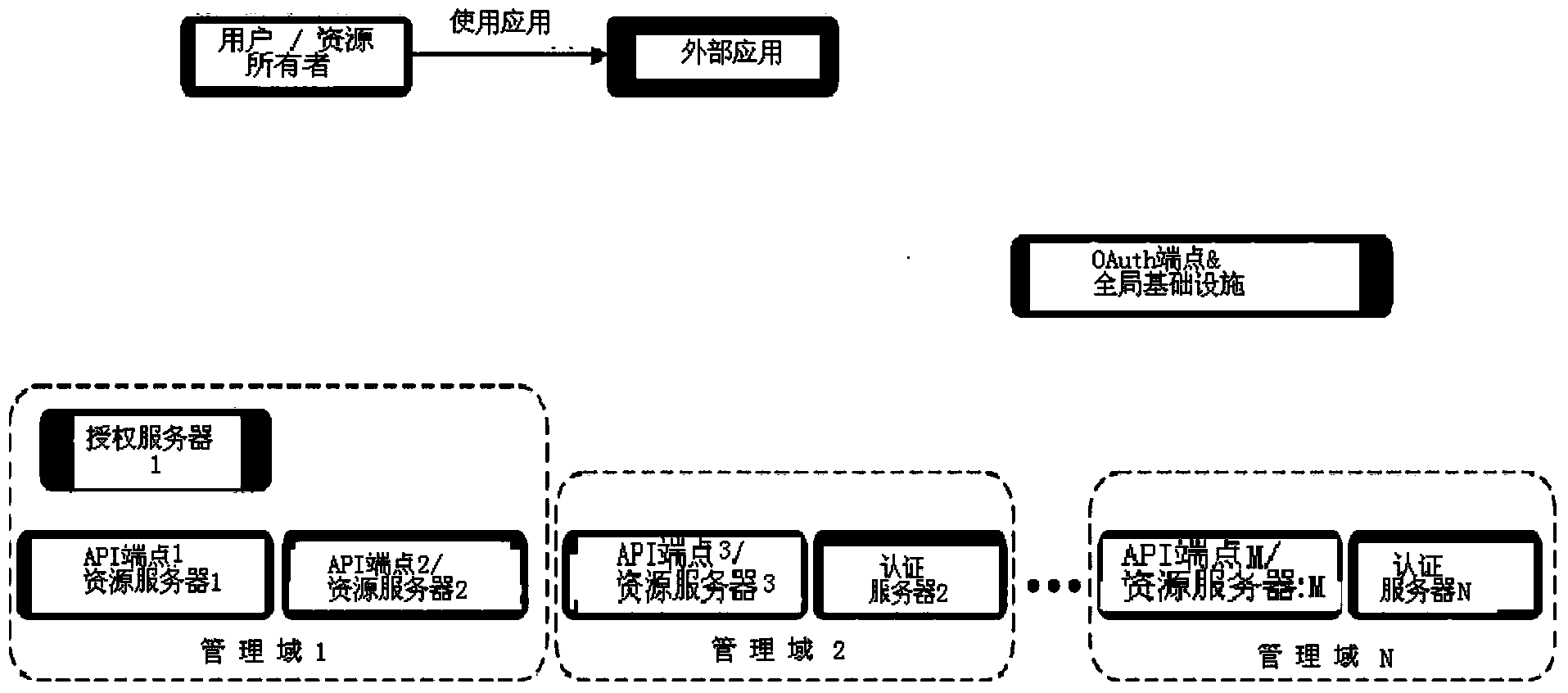
A method for providing authorized access to a service application in order to use a protected resource of an end user
InactiveCN103460215ADigital data protectionDigital data authenticationAdministrative domainComputer science
A method for providing authorized access to a service application in order to use a protected resource of an end user. The protected resource, typically an API, is exposed by endpoints of a plurality of administrative domains. The endpoints are previously unknown by said service application and the method further comprises: i. using an intermediate or global entity for: a) selecting one of said administrative domains based on flexible criteria (i.e. at least on the identity of said end user but also considering varying user or service preferences); and b) performing, said selected administrative domain, a secure authorization to grant access to said end user by means of an open protocol; and ii. providing, said selected administrative domain to said service application, once performed said secure authorization, direct or proxy access to said user's protected resource via the endpoint established by said intermediate entity.
Owner:电话有限公司
Write-once-read-many storage system and method for implementing the same
ActiveUS20070083568A1Input/output to record carriersData processing applicationsOperational systemState switching
A write-once-read-many (WORM) storage system that employs large-capacity and relatively inexpensive disks in connection with a file system on a file server is provided. The file system contains most or all of the required WORM functionality so as to impose a minimal footprint on client applications, client operating systems and open protocols if desired. The system is organized around WORM storage volumes that contain files that, when committed to WORM storage, cannot be deleted or modified. Any file path or directory tree structure used to identify the file within the WORM volume is locked and cannot be deleted. In one embodiment, the administrator creates a WORM volume, capable of storing designated WORM files. The client then creates an appropriate WORM file using the appropriate protocol semantics. The file is written to the volume and committed by transitioning the file attributes from a not-read-only to a read-only state. The- file system recognizes the persistently stored WORM attribute of any file in a WORM volume as WORM file. Henceforth, any attempt to modify the file attributes, write to the file, or delete the file, by clients, administrators or other entities is rejected and a request denied message is returned to the attempting party
Owner:NETWORK APPLIANCE INC
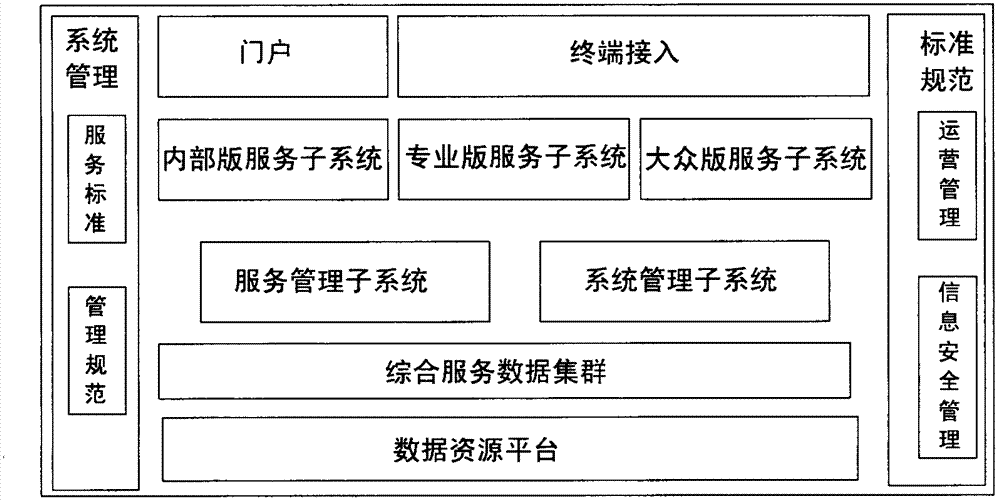
Cloud service based message queue stream processing method
ActiveCN103118138ALow costReduce complexityTransmissionSystems managementStructure of Management Information
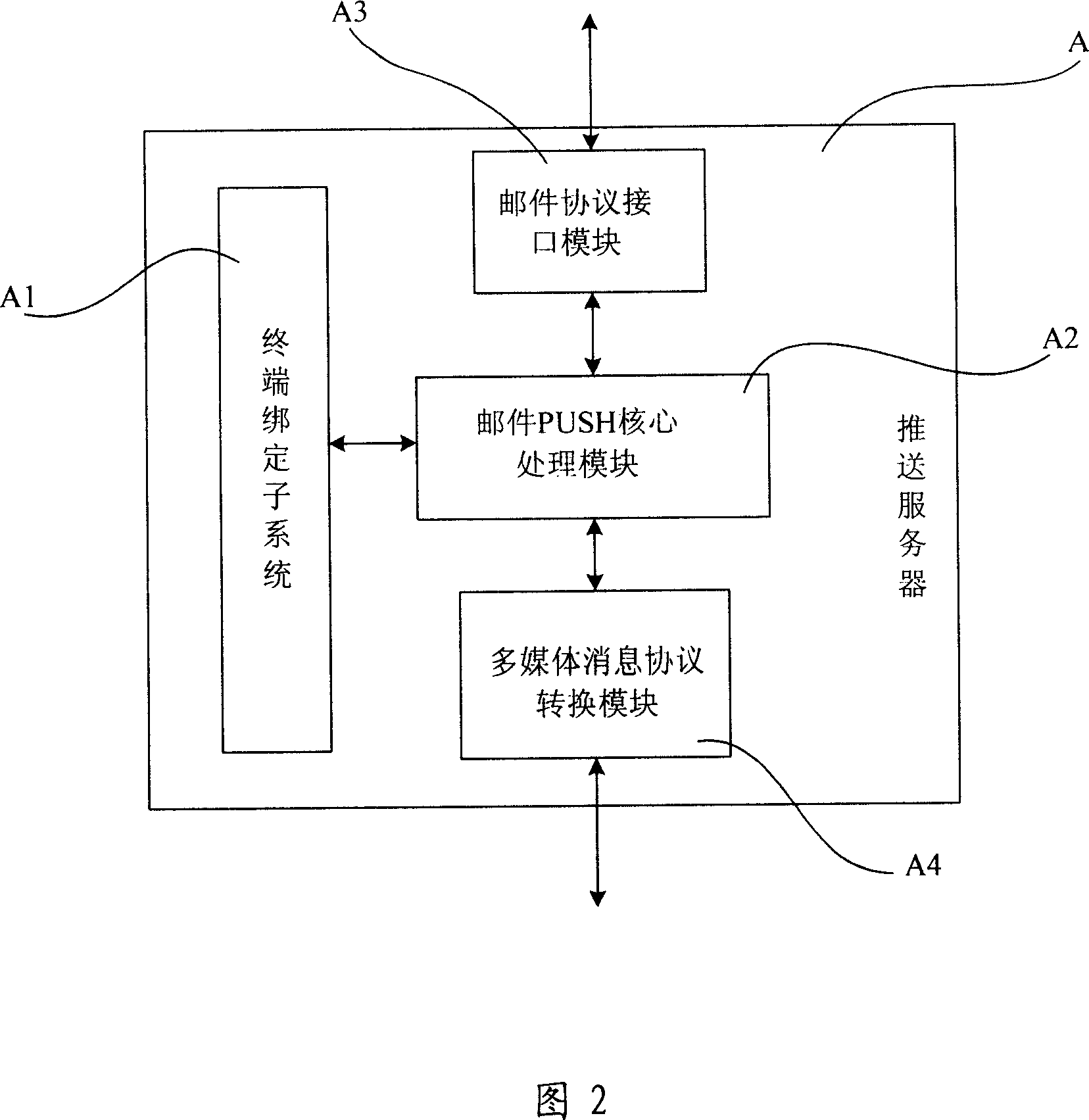
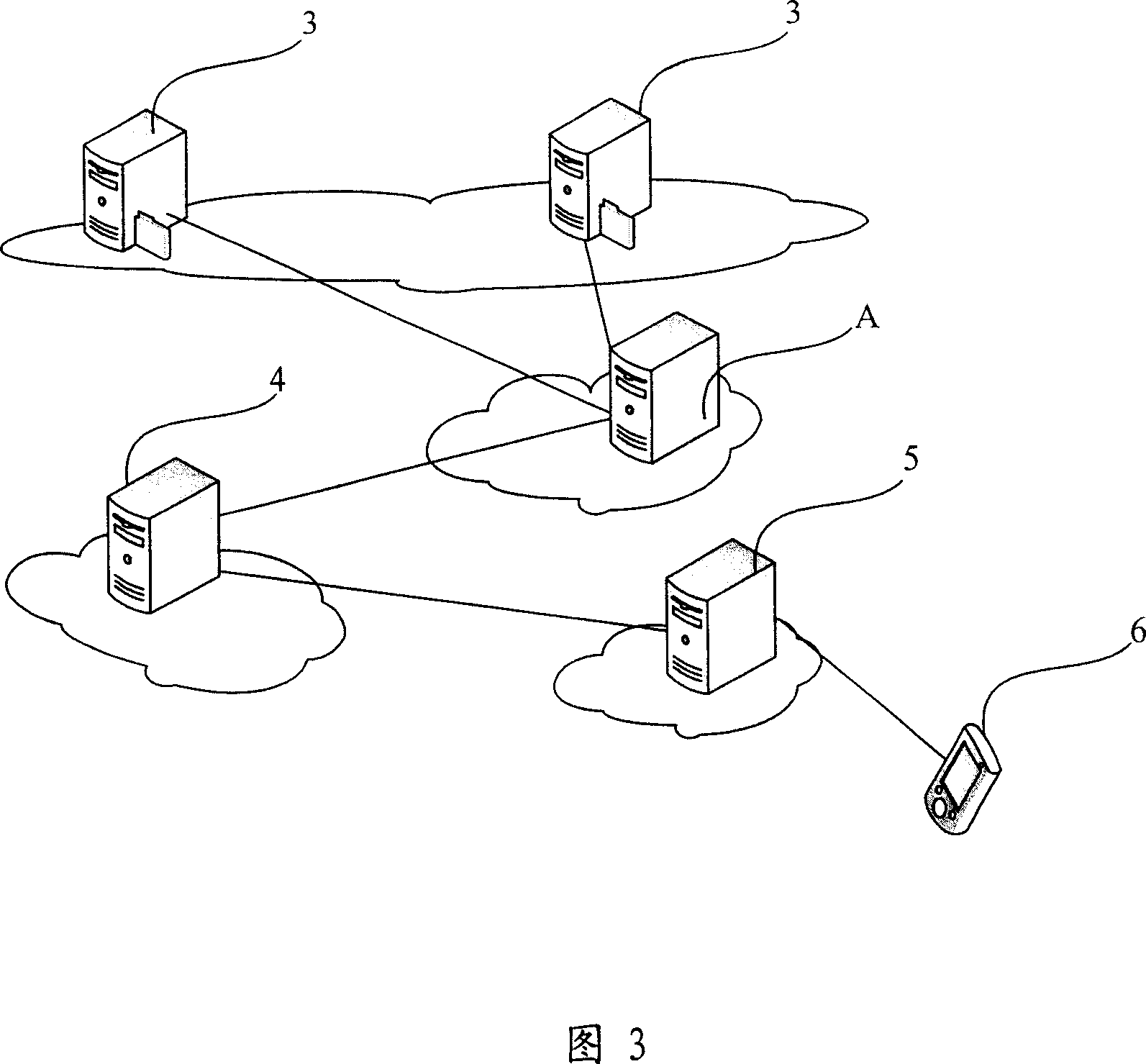
The invention relates to a cloud service based message queue stream processing method. The cloud service based message queue stream processing method mainly comprises the steps of: establishing eight sub-system structures, including, a portal sub-system, a terminal access sub-system, an internal edition service sub-system, a professional edition service sub-system, a public edition service sub-system, a service management sub-system, a system management sub-system and a comprehensive service database sub-system; and establishing a message queue structure to serve as a system core. The cloud service based message queue stream processing method has the beneficial effects of: enabling the message queue based cloud delivery as a service to develop a platform or a service for a final user, having an open protocol to define a user and a content model, allowing a third party to edit implementation of a federated server and a user client both of which can be operated mutually by two parties, realizing direct and in-time notice delivery for people, realizing delivery among devices at any time and at any place no matter the devices are movable devices, desktop computers or media devices, lowering cost and complexity for developers, and bringing about greater convenience and a value-added function for the final users.
Owner:CHINA INFORMATION TECH SECURITY EVALUATION CENT +1
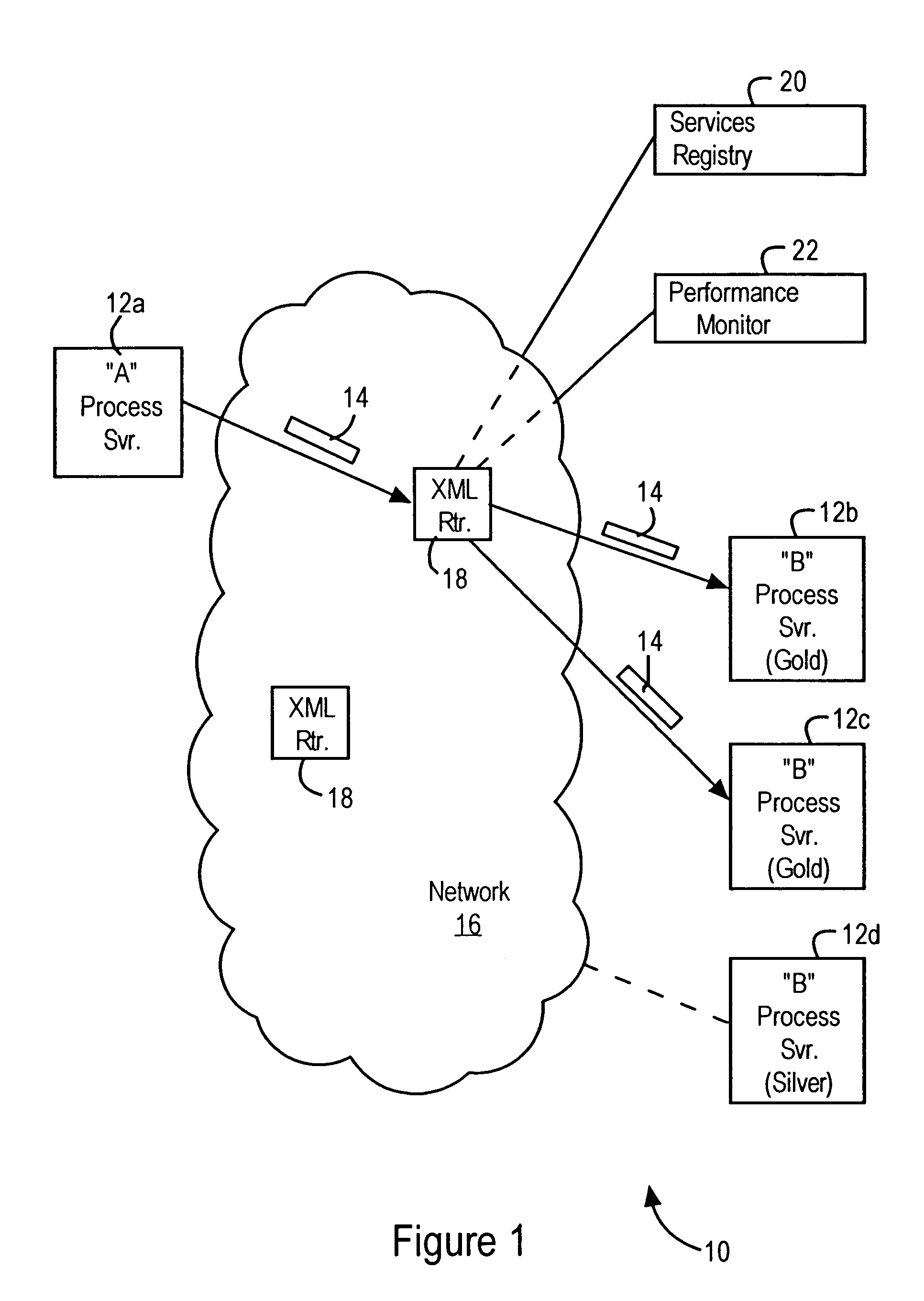
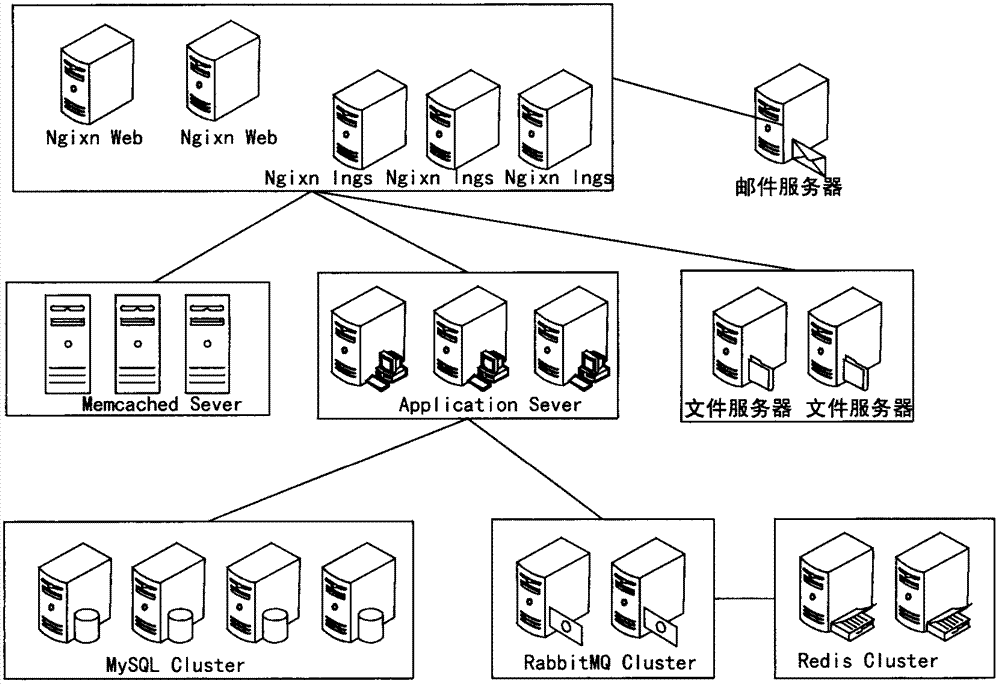
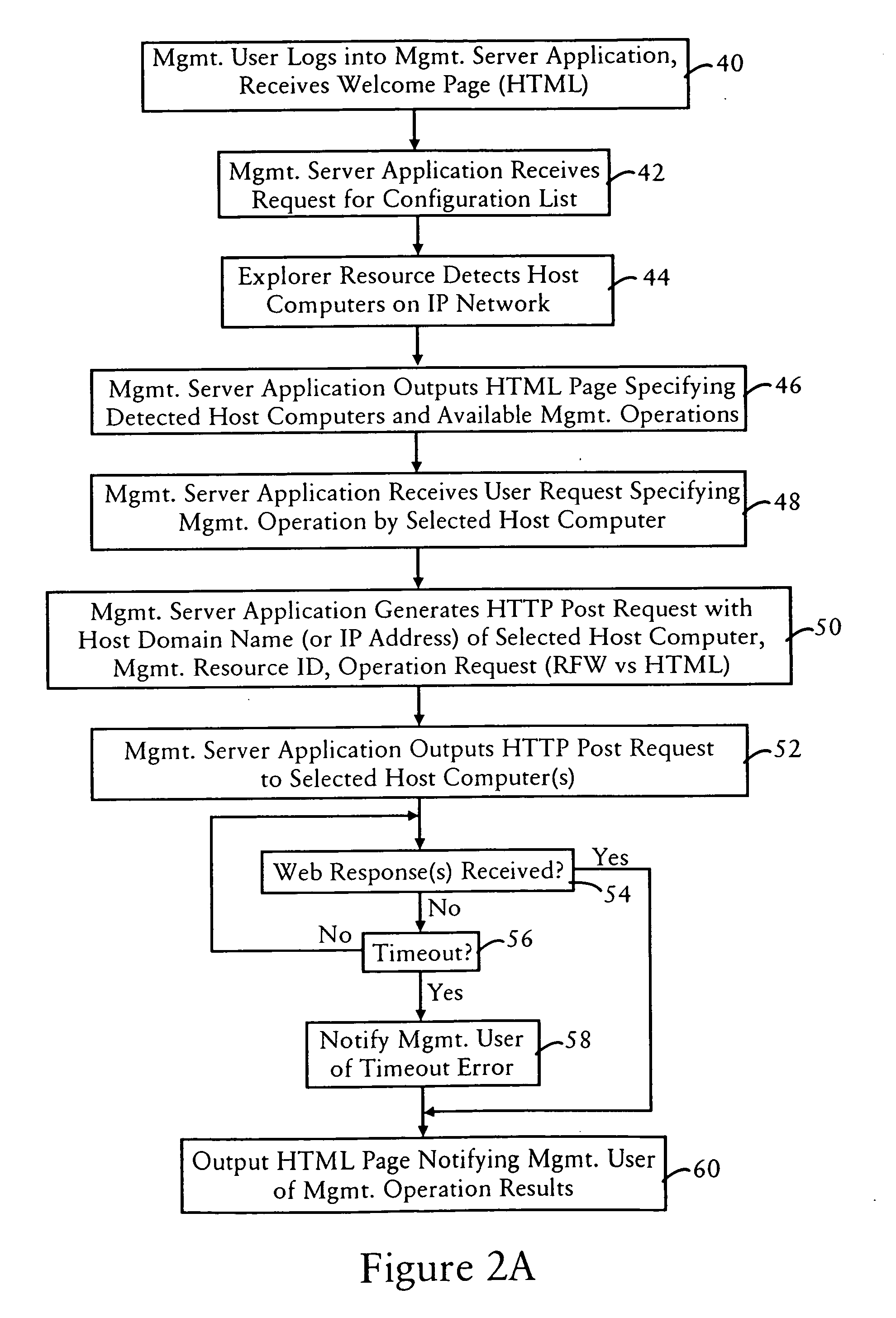
Web based management of host computers in an open protocol network
InactiveUS7082465B1Increase flexibilityMaintain scalabilityDigital computer detailsMultiprogramming arrangementsShort Message ServiceApplication software
Host computers in a distributed open standards-based computing system are configured for performing application operations and management operations, including sending and receiving configuration management messages according to a web based protocol across an Internet Protocol. Each host computer includes an application resource configured for executing the corresponding application operations, for example initiating a unified messaging session for a unified messaging subscriber, providing text to speech services, providing short message service operations, etc., in response to an application request received from the open standards interface. Each host computer also includes a management resource configured for executing prescribed configuration management operations based on a corresponding received management command from the open standards interface. The received management command may be an application-generated command output by a management server executing a management application for a user, or a host-generated command output by a host computer in response to execution of a corresponding management operation. Hence, the execution of the management resource on each of the host computers in the distributed open standards-based computing system enables deployment of a web based arrangement for managing the host computers, where any host computer can send a request to another host computer during execution of the corresponding management operation.
Owner:CISCO TECH INC
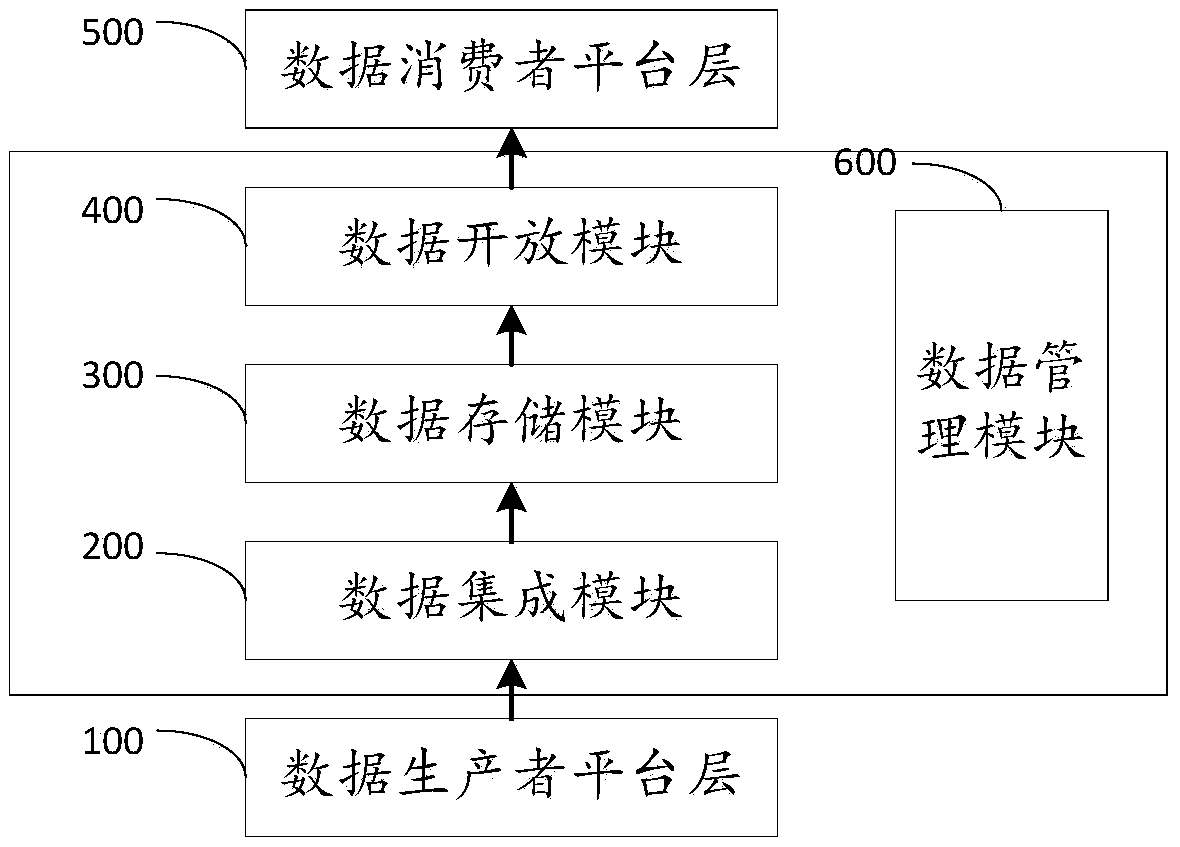
A data lake system oriented to all data morphology open sharing
InactiveCN109271382AOpen Share SupportDatabase management systemsSpecial data processing applicationsReal-time dataFull data
The invention discloses a data lake system oriented to full data form open sharing, which comprises a data producer platform layer, an intermediate layer and a consumer platform layer. The middle layer includes a data integration module, a data storage module and a data opening module. The data producer platform layer consists of one or more heterogeneous databases; The data integration module isused for automatically acquiring data from the data producer platform layer, and integrating the acquired data into the offline data lake and the real-time data lake of the data storage module for storage; The data opening module is used for opening the data stored in the data storage module to the consumer platform layer according to the preset unified data directory, the standard open protocol and the SDN network optimization strategy. The consumer platform layer is used for data interaction with the consumer terminal. The invention can provide a data lake system oriented to full data form open sharing, which supports cross-organization, cross-department and cross-industry data convergence and supports full data form open sharing.
Owner:GUANGDONG POLYTECHNIC NORMAL UNIV +1
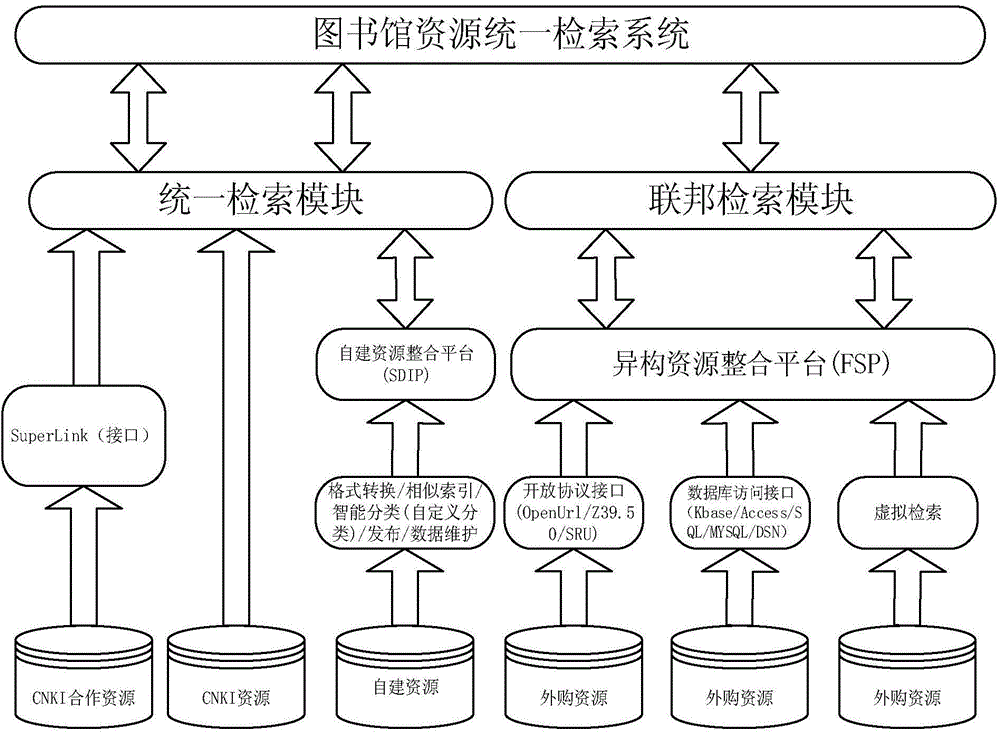
Digital library resource unified search system
InactiveCN104699849ARealize one-stop searchRealize discoveryResourcesSpecial data processing applicationsPersonalizationFederated search
The invention discloses a digital library resource unified search system. The system comprises a unified search module and a federated search module, the unified search module is provided with a self-established resource integration platform SDIP, the federated search module is provided with a resource integration platform, the self-established resource integration platform SDIP is used for conducting format translating on self-established resource, establishing a KBase database, establishing similarity indexing, establishing classification and grouping and issuing and maintaining the database, and the resource integration platform is used for integrating outsourcing resources through an open agreement connector and a database access connector and conducting virtual indexing on the outsourcing resources. By means of the digital library resource unified search system, integrating and searching CNKI resources, unit self-established resources, unit outsourcing resources and internet resources can be achieved simultaneously, and one-stop searching, finding and positioning of all resource are achieved. The management platform can be combined with a CNKI digital library, a digital cleaning research platform and the like, and various kinds of personalized services are provided.
Owner:同方知网数字出版技术股份有限公司 +1
Network router configured for executing network operations based on parsing XML tags in a received XML document
InactiveUS20060200458A1Increased “vocabularyGood serviceTransmissionSpecial data processing applicationsSemanticsApplication specific
Owner:CISCO TECH INC
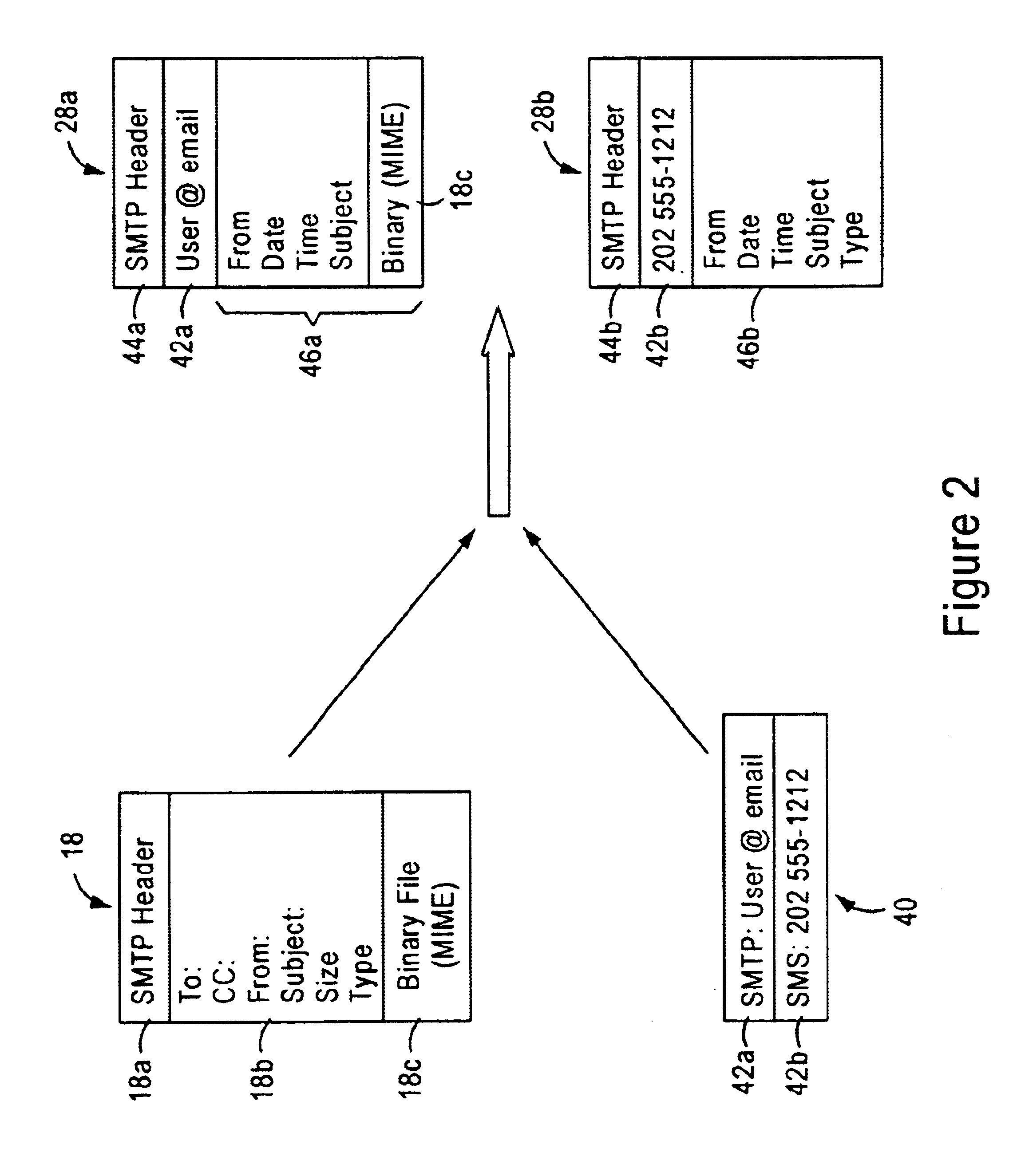
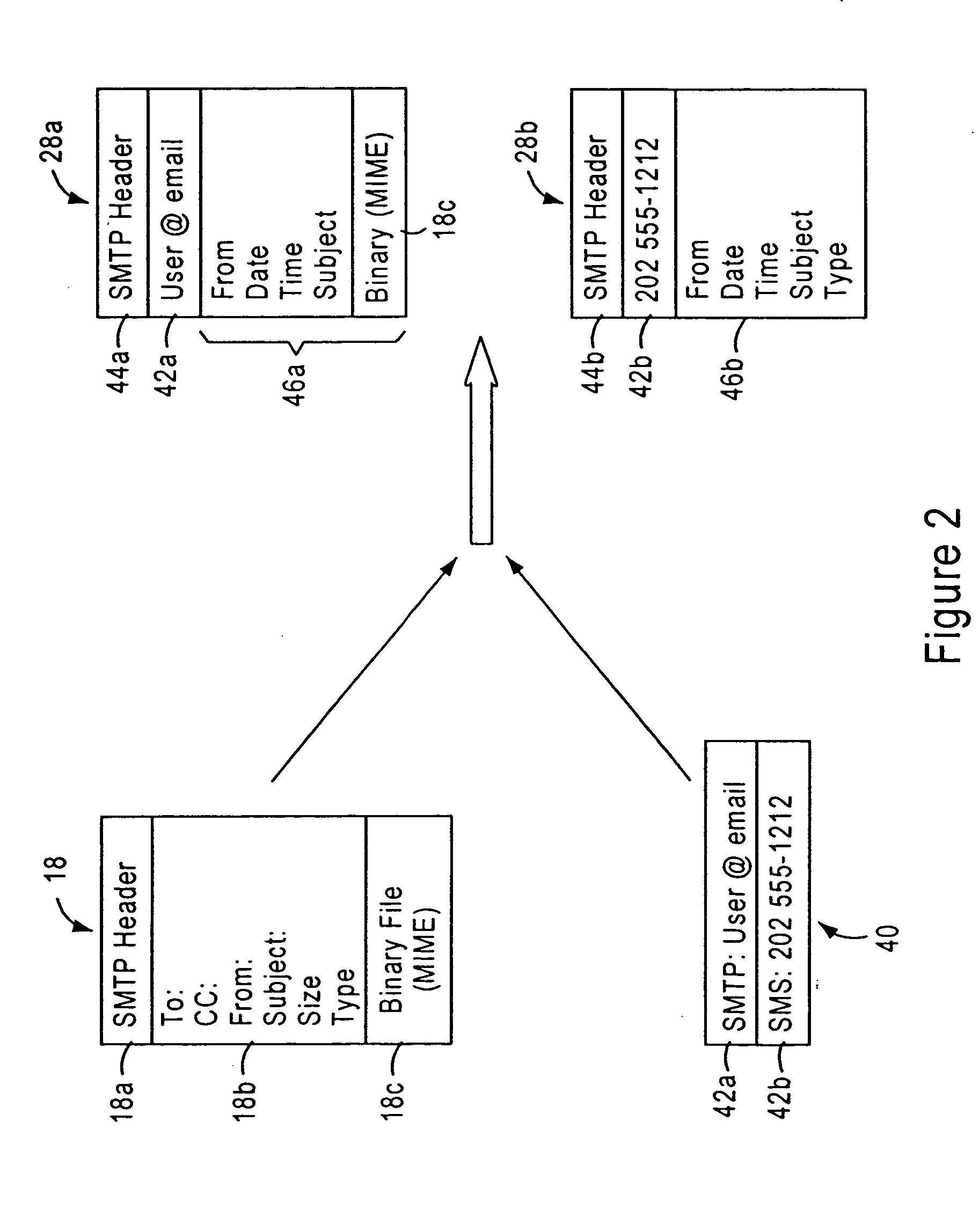
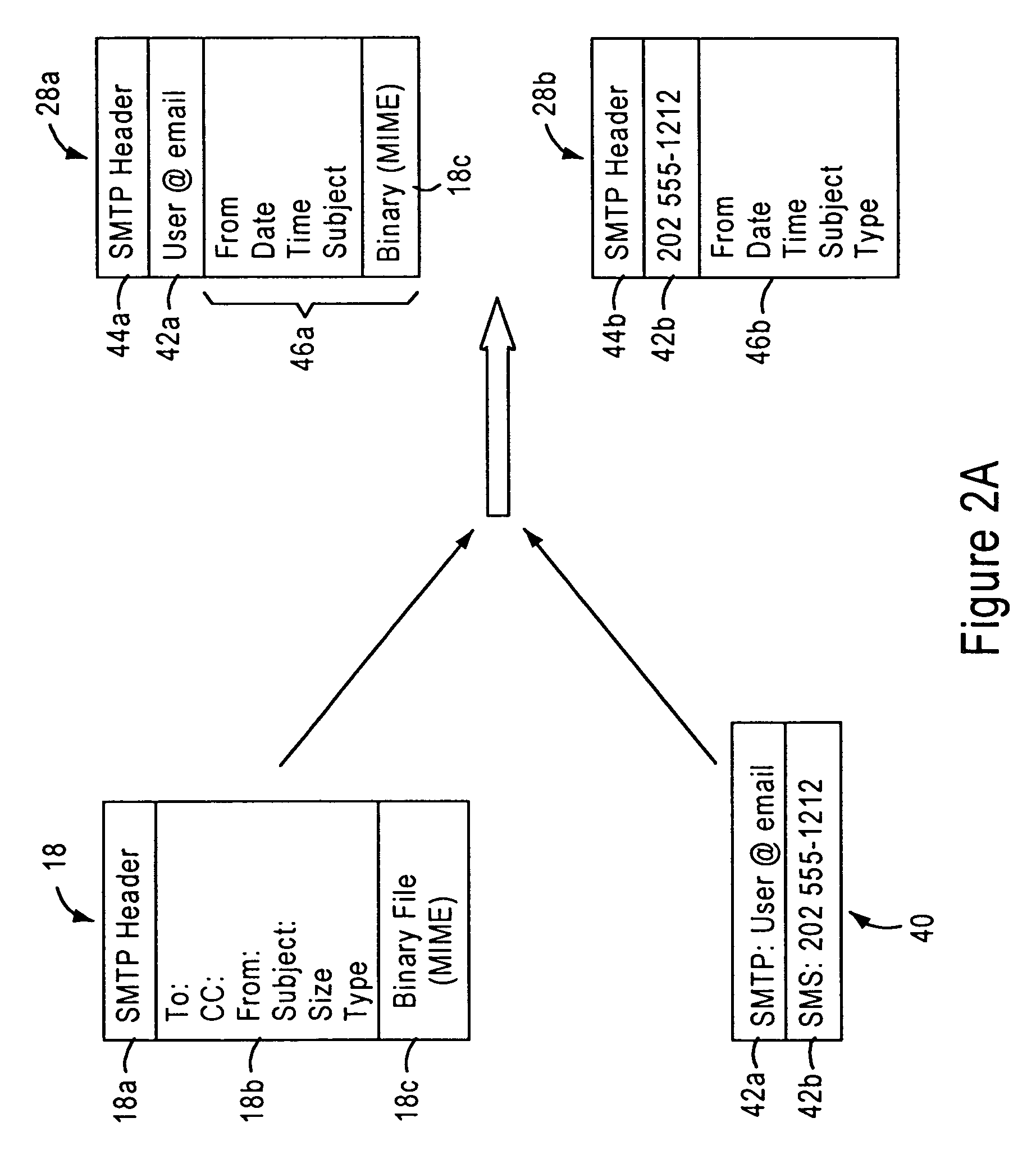
Arrangement for common-format notification delivery messages based on notification device type in an IP-based notification architecture
InactiveUS7092497B1Reduce necessityAutomatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsDevice typeOPEN protocol
A notification architecture utilizes multiple processes configured for managing notification operations based on reception of SMTP-based messages within IMAP based message stores. The notification architecture includes a notification process, configured for receiving notification messages for respective subscribers from messaging sources according to a prescribed open protocol such as Internet Protocol. The notification process accesses subscriber profile information from an open protocol-based subscriber directory based on the received notification messages. The notification process determines, for each received notification message, the subscriber's notification preference based on the accessed profile information, and selectively outputs a notification delivery message according to a prescribed open protocol to at least one notification delivery process within the notification architecture based on the subscriber's notification preference. The notification process may have access via the prescribed open protocol to multiple notification delivery processes, each configured for outputting a notification to a subscriber's notification device according to a corresponding device protocol. Hence, subscribers may be notified of events according to their respective preferences, including subscriber device type, or time of notification. The notification process also generates the notification delivery message using selected portions of the notification information and subscriber information based on the notification device type, providing a common format for device specific notification messages. Hence, each notification delivery process can receive device specific notification messages according to a common format from the notification process or another external process.
Owner:CISCO TECH INC
Blind exchange of keys using an open protocol
InactiveUS20050044379A1User identity/authority verificationComputer security arrangementsAuthentication serverField service
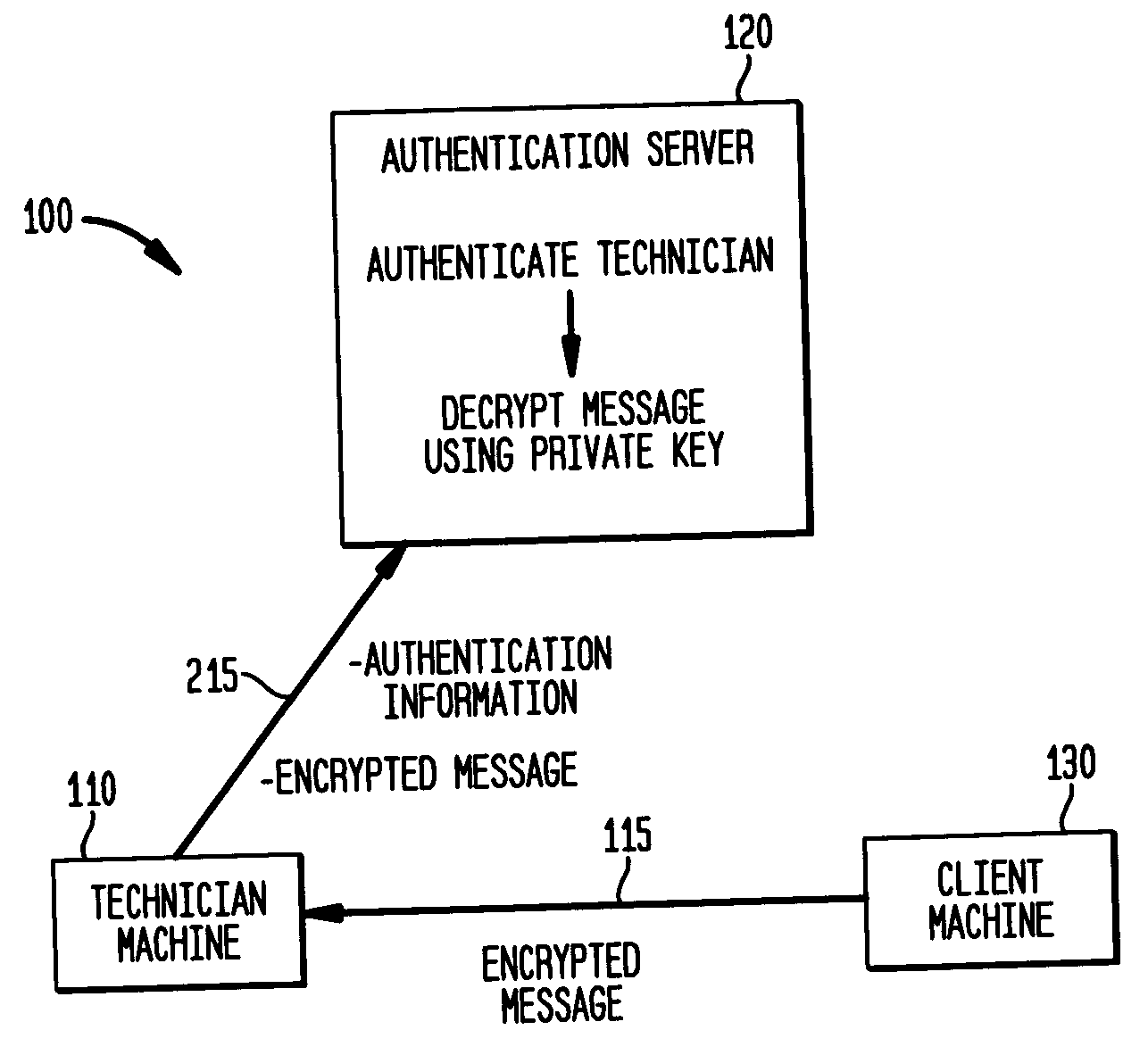
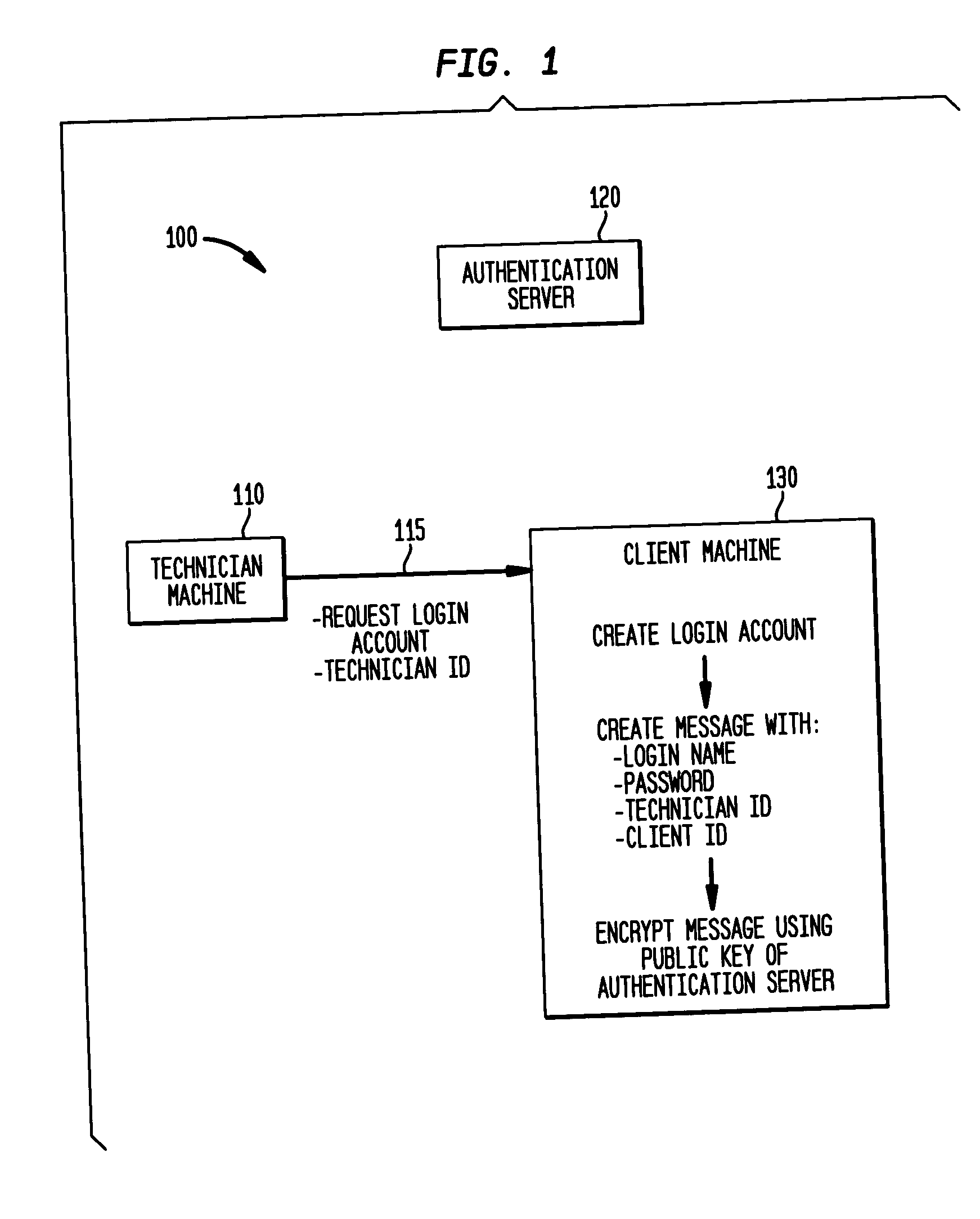
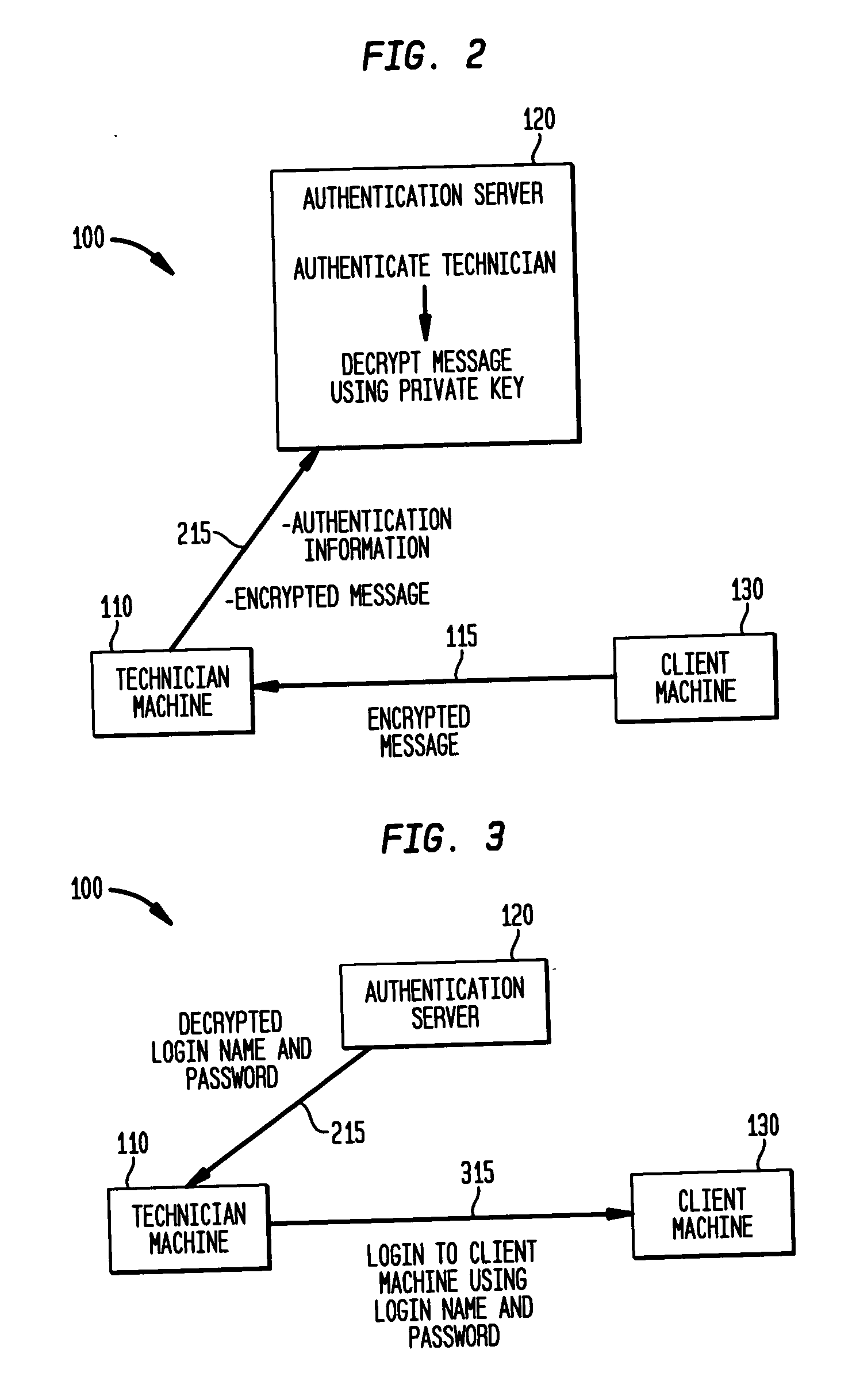
A computer system and method where a user is authenticated to both an authentication server and to a client machine, but no link between the client machine and authentication server is needed. Login information is provided from the client machine to the technician machine in an encrypted format using a public key so that the technician machine cannot access the login information. The technician machine communicates the encrypted login information to an authentication server, which decrypts the login information using a private key and provides the decrypted login information to the technician machine if the technician machine can authenticate itself to the authentication server. The invention is particularly useful in enabling field service technicians to access client computer systems from remote locations such as field offices, hotel rooms, airports and the like.
Owner:IBM CORP
230MHz Mobitex master-slave redundancy wireless data terminal special for electric power
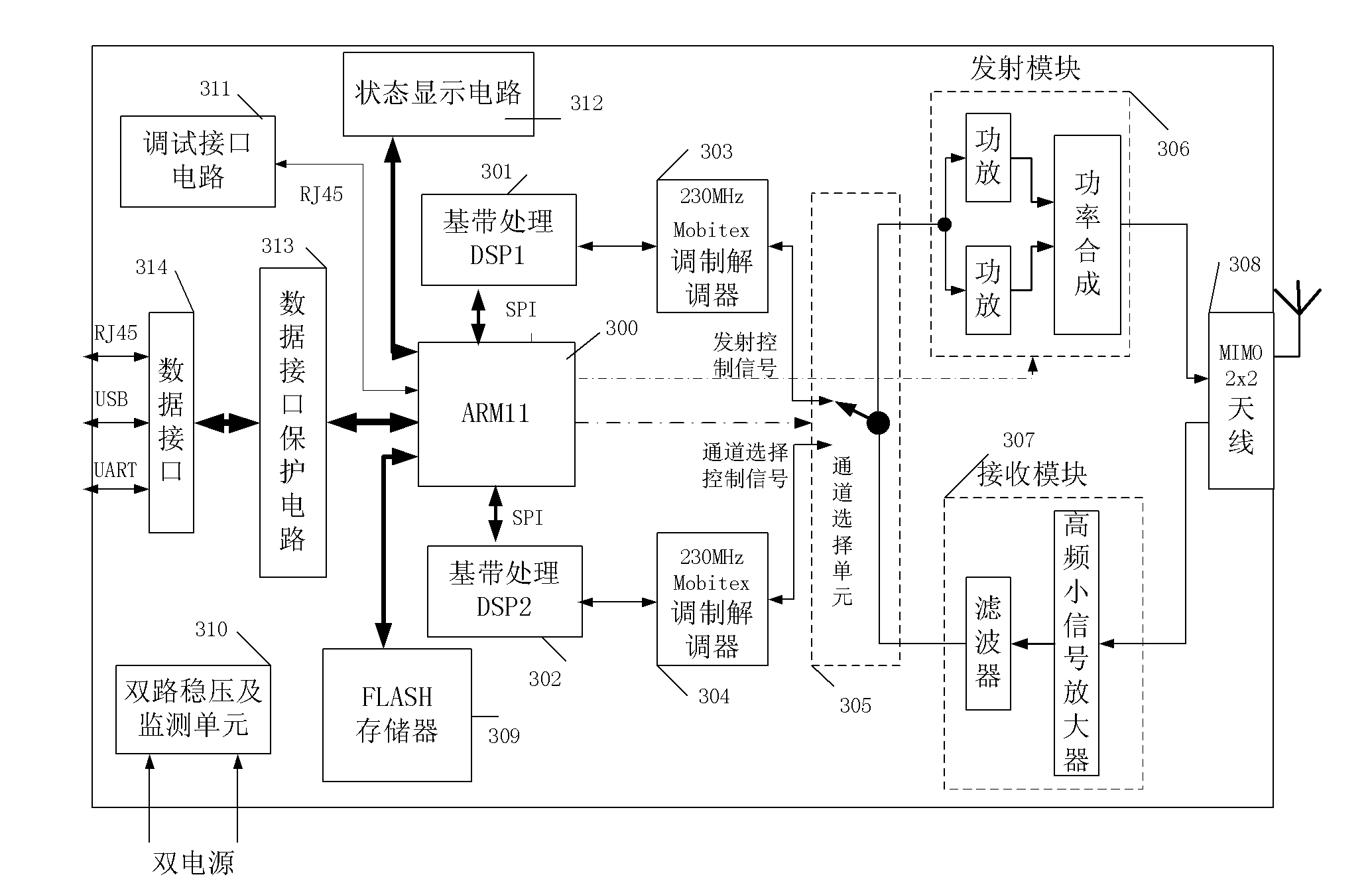
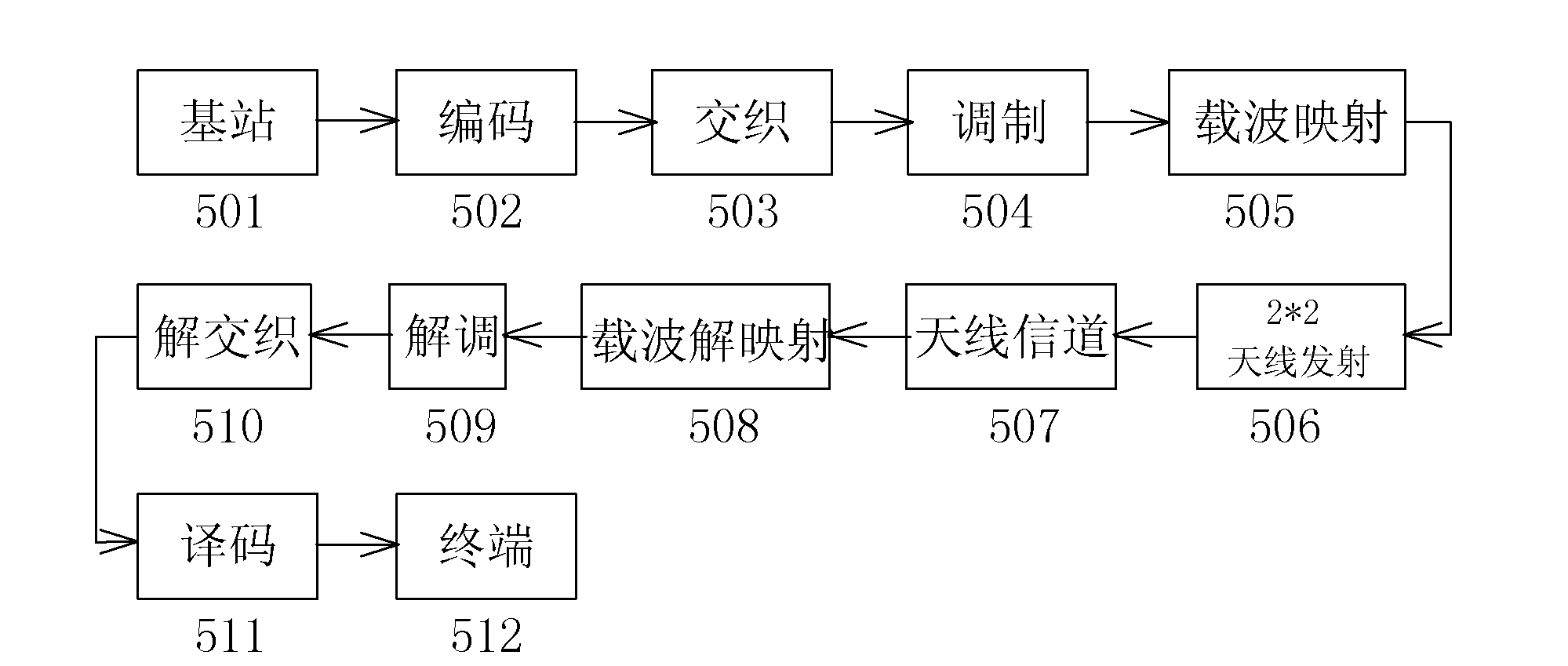
ActiveCN102361470ACompliant with data transferConforms to data transmission characteristicsError preventionCircuit arrangementsModem deviceElectric power system
The invention relates to the technical field of electric power wireless data terminals, in particular to a 230MHz Mobitex master-slave redundancy wireless data terminal special for electric power. The wireless data terminal is characterized by comprising an advanced RISC (reduced instruction set computer) machines (ARM) main processor, a first baseband processing digital signal processor (DSP) chip, a second baseband processing DSP chip, a first radio frequency modem, a second radio frequency modem, a channel selection unit, a transmitting module, a receiving module and an MIMO2*2 antenna, wherein the ARM main processor, the first baseband processing DSP chip and the second baseband processing DSP chip form a master-slave structure, and the first baseband processing DSP chip and the second baseband processing DSP chip backup each other. Compared with the prior art, the 230MHz Mobitex master-slave redundancy wireless data terminal has the advantage that: based on a Mobitex open protocol stack and existing 230MHz frequency band resources of an electric power system, the 230MHz Mobitex master-slave redundancy wireless data terminal is favorable for upgrading and reconstructing the existing 230MHz data radio station and an 800MHz Mobitex wireless communication system of the electric power system.
Owner:ANSHAN POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER COMPANY +1
Push-mail system based on mobile network and receiving/sending method for mails
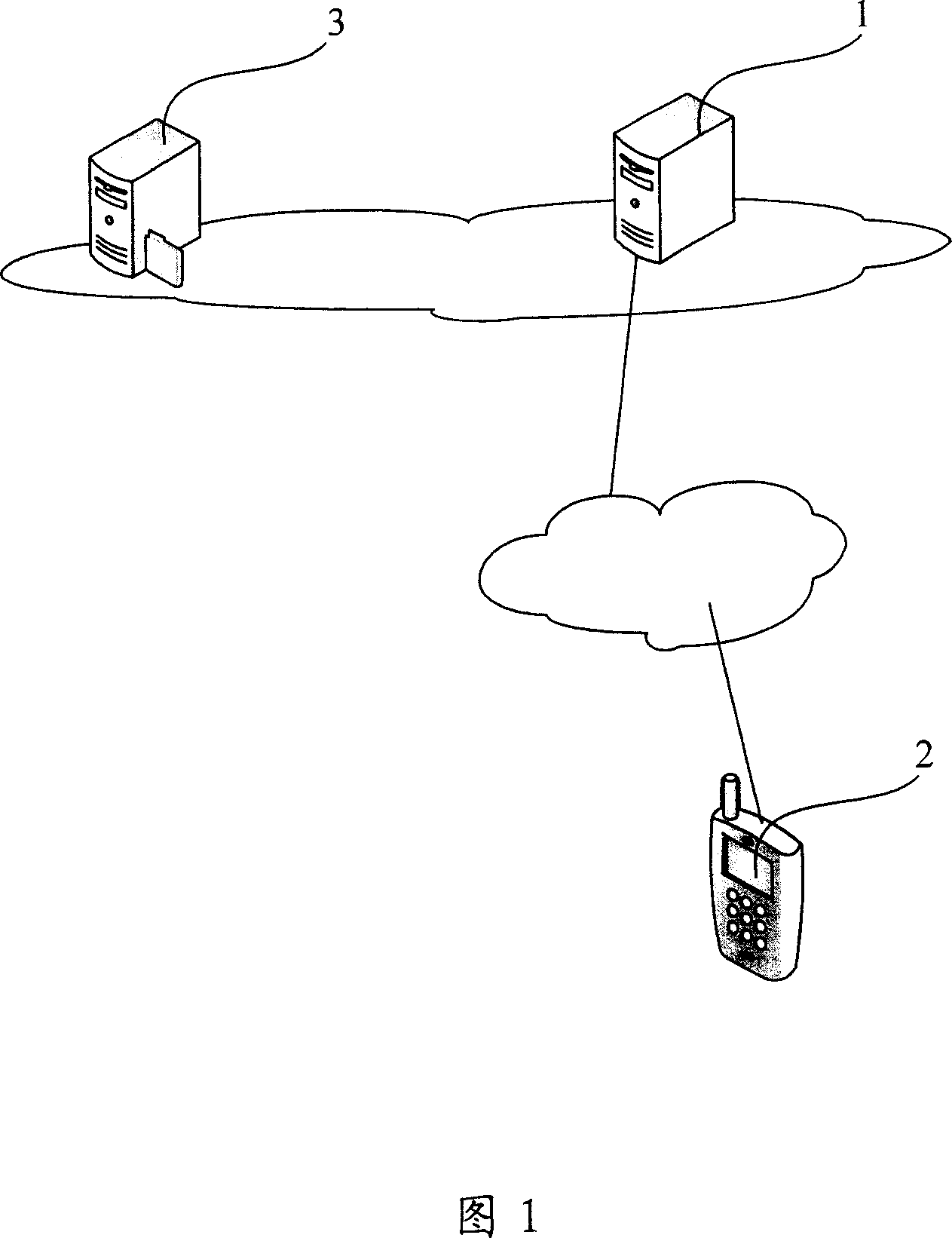
InactiveCN1929459AIncrease opennessMultiple digital computer combinationsRadio/inductive link selection arrangementsTransfer systemMobile Web
This invention relates to mobile mail transfer system and its send method, wherein the system comprises mail servo, transfer servo, mobile terminal to book mails and multi-media message center. The mail receive method comprises the following steps: transfer servo inquires main servo change information; sending indication information to mobile terminal; converting mail into multi-media information form to service center for mobile terminal. The mail send method comprises steps of sending multi-media information form mails to transfer servo through multi-media message servo center and converting mails into main form to mail servo.
Owner:HUAWEI TECH CO LTD
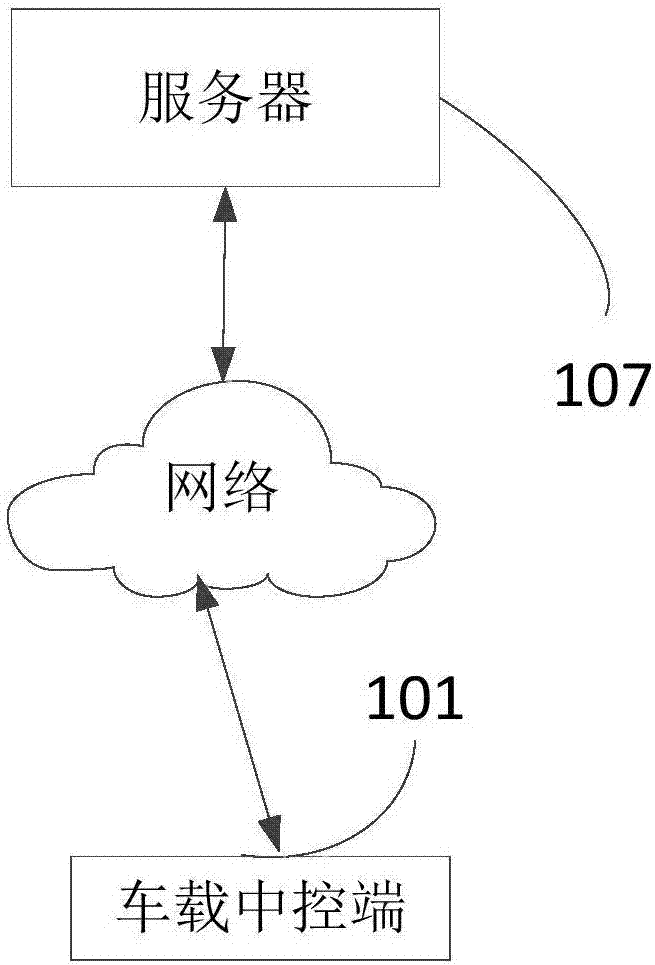
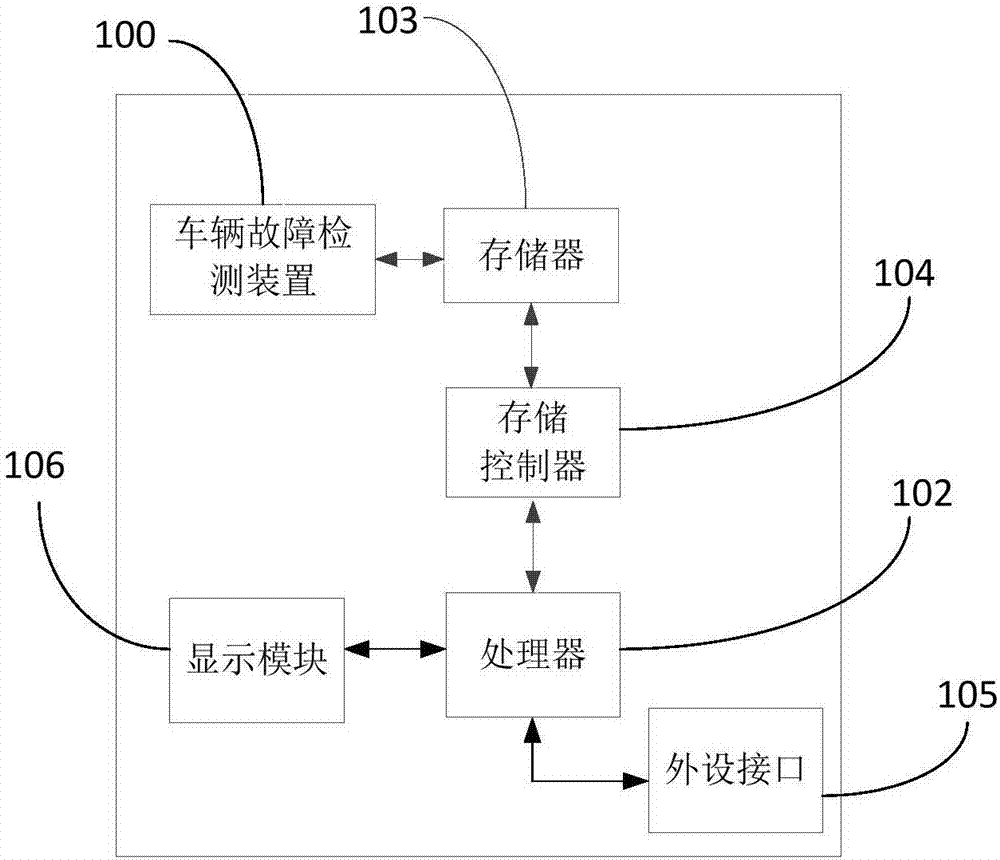
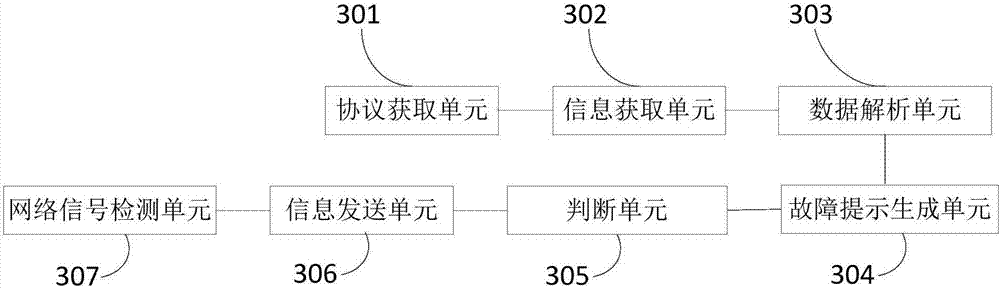
Vehicle fault detection device and method
InactiveCN107450525AReduce manufacturing costLow costProgramme controlElectric testing/monitoringComputer scienceOPEN protocol
The invention provides a vehicle fault detection device and method, and relates to the field of vehicle on-line detection. The vehicle fault detection device and method first obtains an open protocol of a current vehicle from a prestored configuration file; then monitors and obtains vehicle running state information according to the prestored configuration file carrying a data protocol ID; then analyzing the vehicle running state information according to the open protocol so as to obtain vehicle running data; and finally, generating a fault prompt according to fault judging rules contained in the configuration file and the obtained vehicle running data. The vehicle fault detection device is installed in a vehicle-mounted center control terminal, detects a vehicle fault through system software, does not need hardware research personnel and a hardware manufacturer to jointly participate, during volume production, saves a large amount of production cost, can extend and upgrade the vehicle fault detection device and make the device flexibly adaptive to open protocols of various manufacturers without developing and manufacturing again, thus the vehicle fault detection device is very convenient, and cost is also saved.
Owner:四川驹马企业管理有限公司
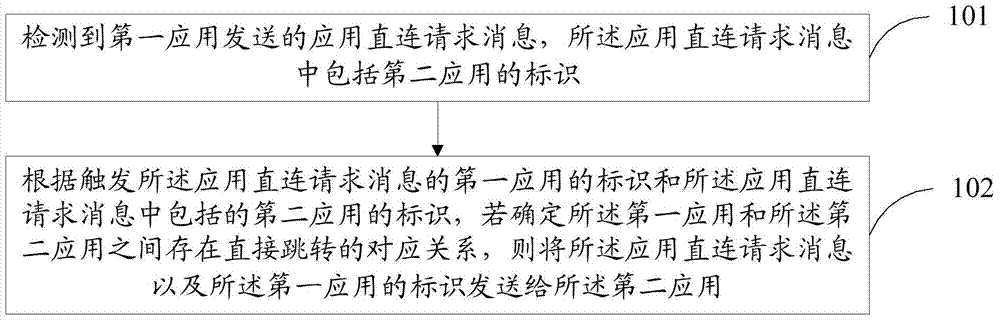
Application processing method and device and smart television
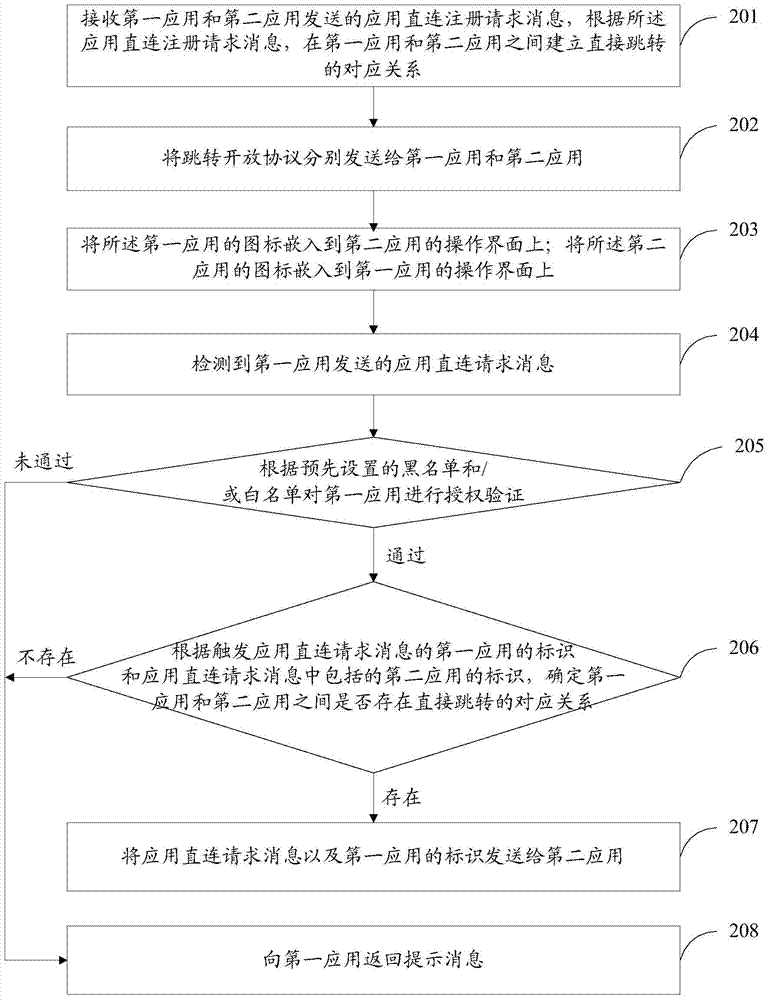
InactiveCN104333807AImprove experienceEasy to operateSelective content distributionOperating systemOPEN protocol
The invention provides an application processing method and device and a smart television so as to solve the problems of complex operation process and poor user experience in operating another application while one application is operated. The method comprises detecting an application direct-connection request message sent by a first application; and through triggering an icon of the first application of the application direct-connection request message and an icon of a second application contained in the application direct-connection request message, and if determining that the first application and the second application have direct skipping correspondence relationship, sending the application direct-connection request message and the icon of the first application to the second application, so that the second application is allowed to open an API of the second application and call a skipping open protocol to establish a direct connection channel between the first application and the second application according to the application direct-connection request message and the icon of the first application. According to the method and device, the second application can be directly entered while the first application is operated, thereby simplifying operation process of operating the second application and greatly improving user experience.
Owner:LETV INFORMATION TECH BEIJING
Communication Control System
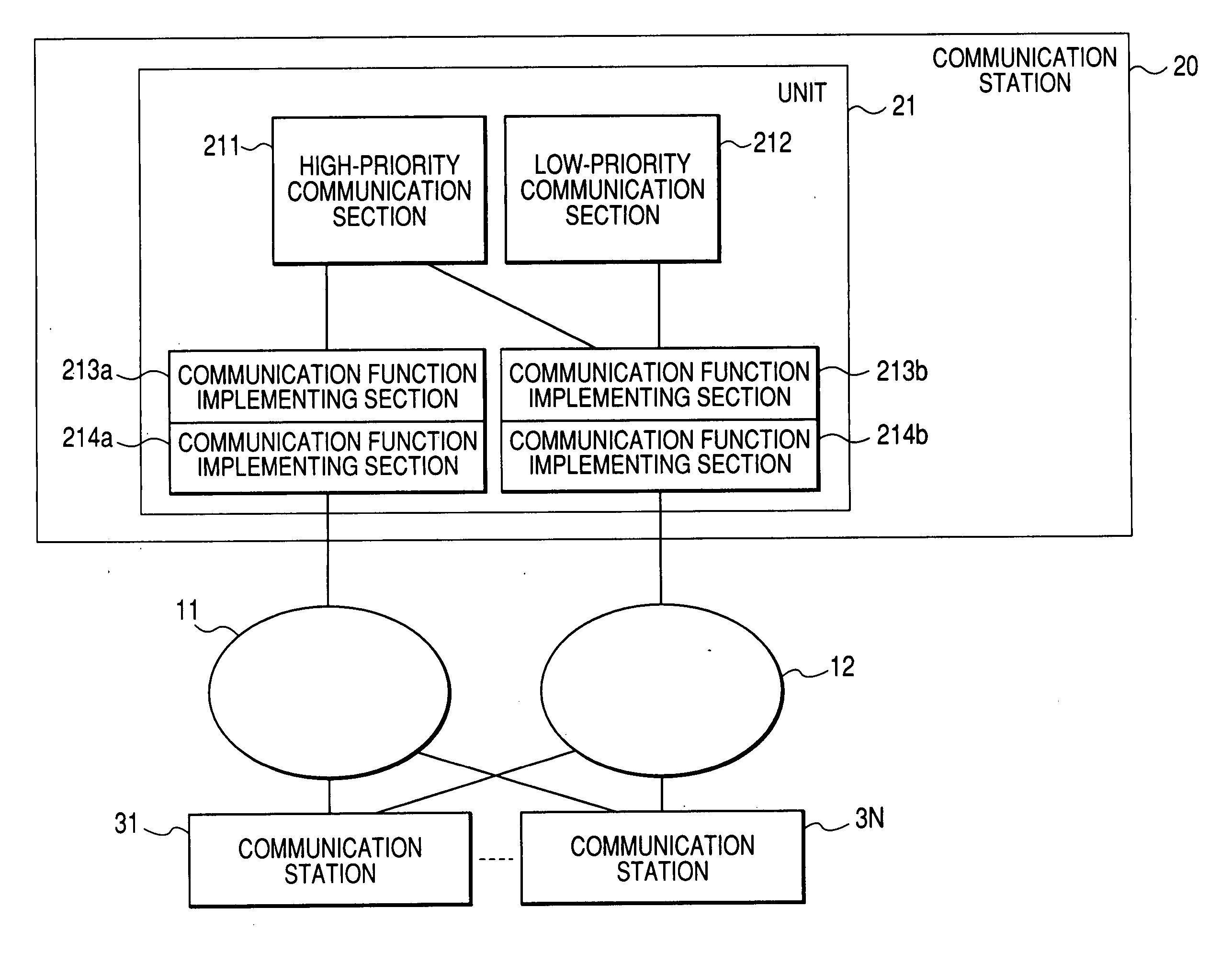
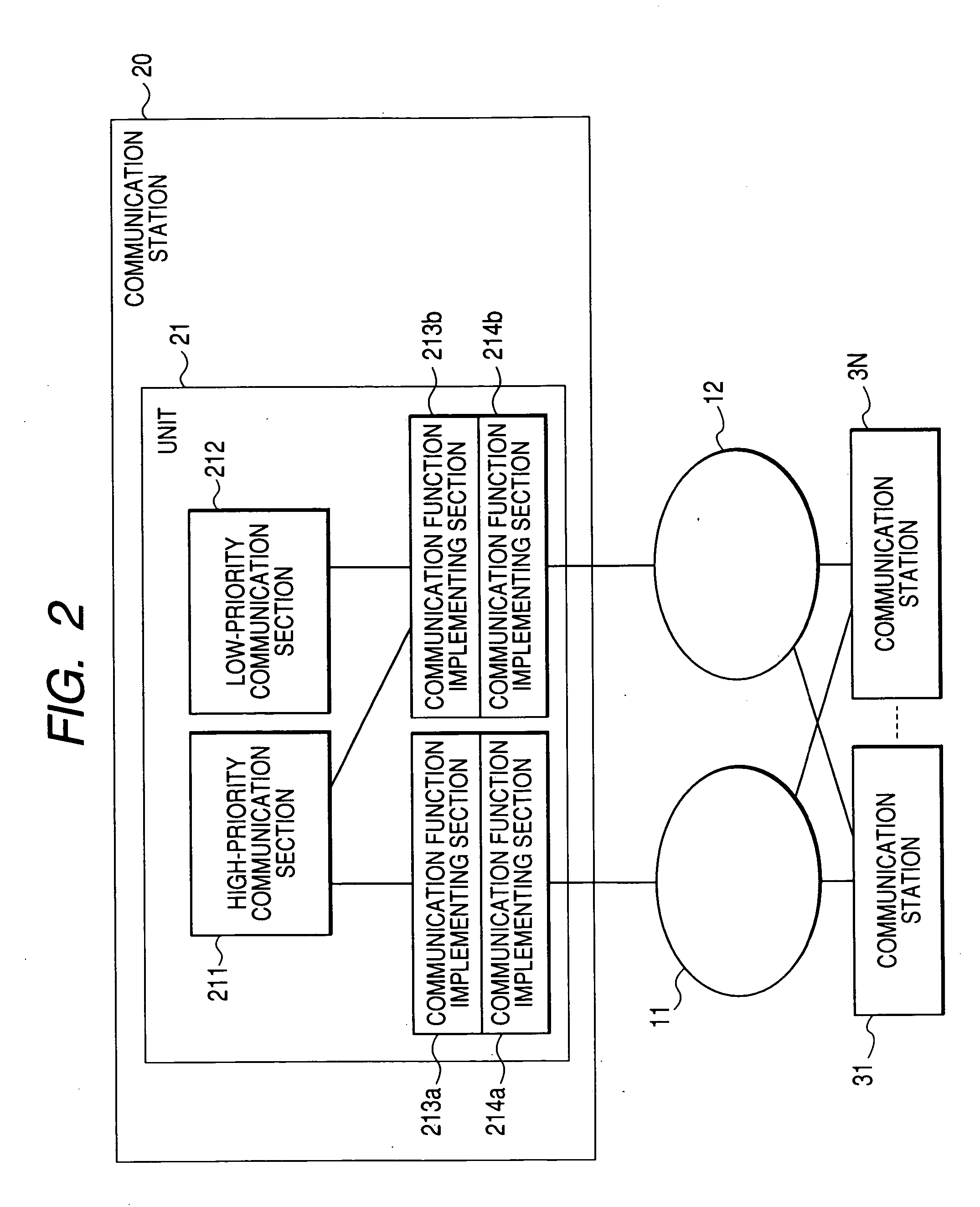
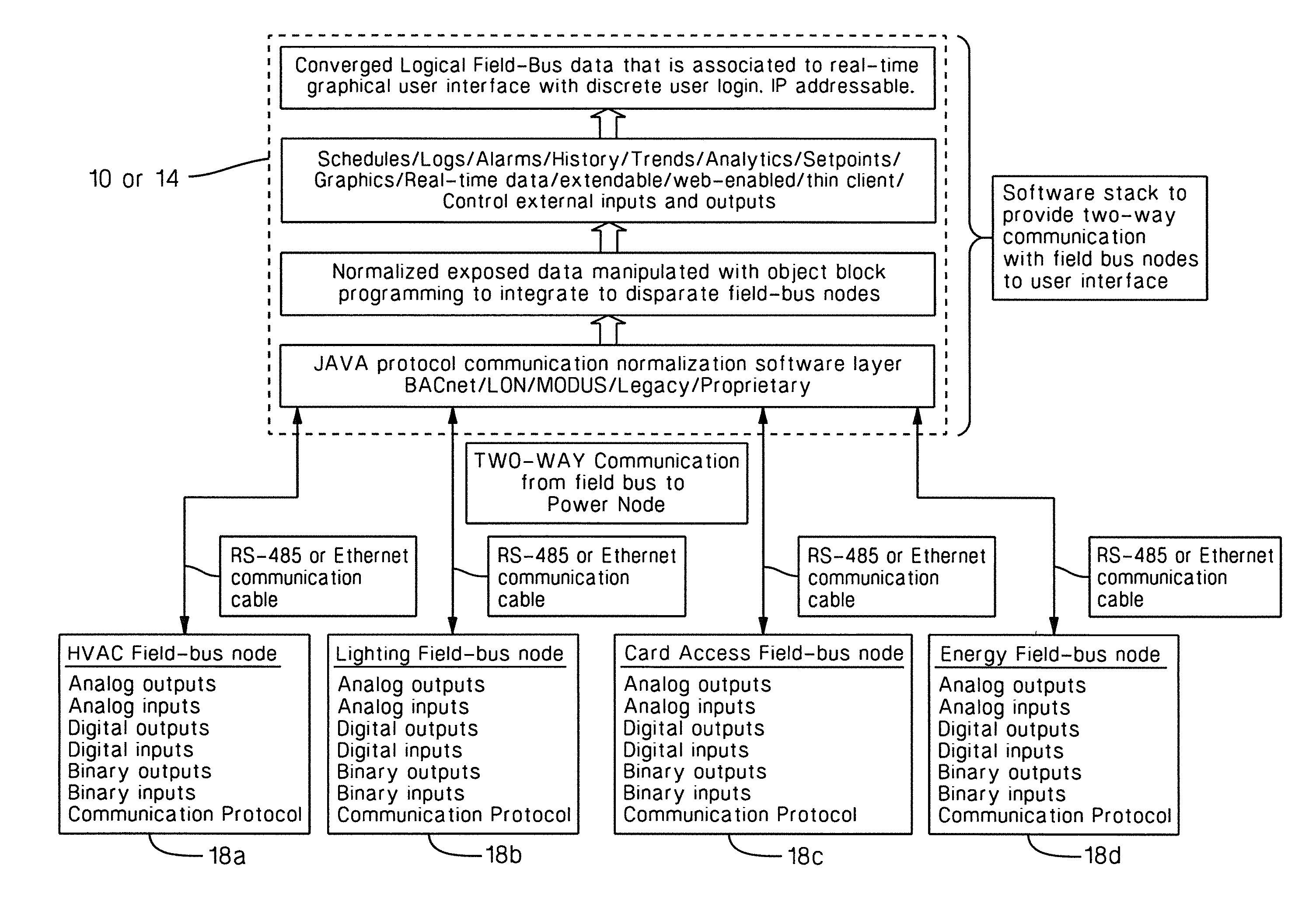
ActiveUS20070250182A1Avoid disturbancePrevent security attacksComputer controlSimulator controlControl systemCommunication control
A communication control system is provided that performs communications satisfying a request for industrial applications and a request for open protocol communications at the same time. To this end, in the invention, a high-priority communication section performing critical communications to provide real time property and reliability, and a low-priority communication section performing communications based on an open standard protocol coexist in a same communication station.
Owner:YOKOGAWA ELECTRIC CORP
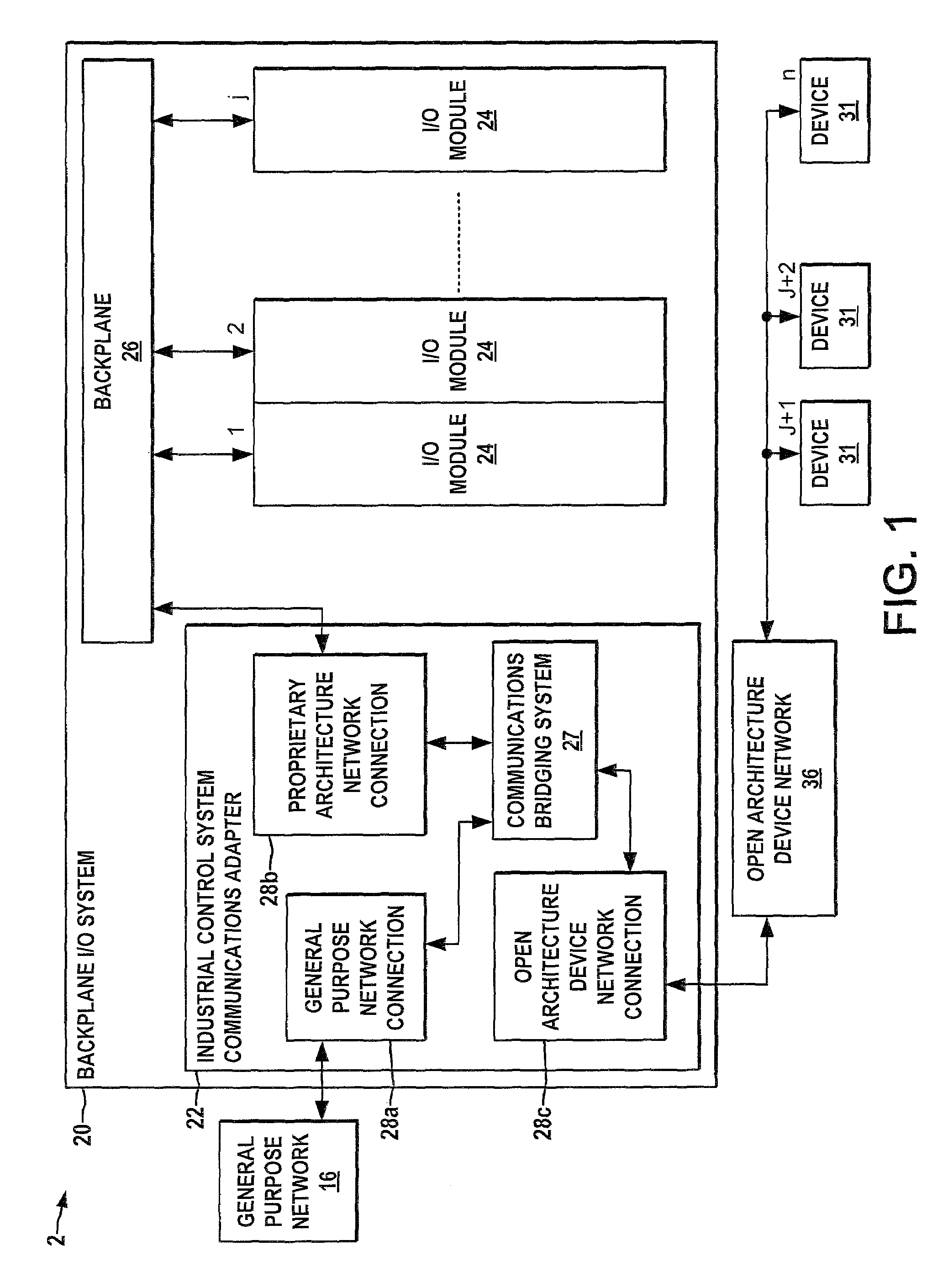
Industrial ethernet communications adapter
ActiveUS7719961B2Easy to understandIntegrated cost-effectivelyError preventionFrequency-division multiplex detailsGeneral purposeComputer module
Communications adapters and methods are provided for interfacing communications for an EtherNet / Ip or other general purpose industrial network, a Fieldbus or other open protocol device network, and a PointBus or other proprietary network. The adapter may be integrated in a module of a backplane system with connections to the general purpose, proprietary, and open protocol device networks, and provides a bridging for communications across the networks to make devices on the proprietary and open protocol networks accessible as if they were on a single device network and with sequential addressing capabilities.
Owner:ROCKWELL AUTOMATION TECH
Communication control system
ActiveCN1894901AMeet the requirements of industrial applicationsImprove reliabilitySecuring communicationBus networksControl systemCommunication control
A communication control system is provided that performs communications satisfying a request for industrial applications and a request for open protocol communications at the same time. To this end, in the invention, a high-priority communication section performing critical communications to provide real time property and reliability, and a low-priority communication section performing communications based on an open standard protocol coexist in a same communication station.
Owner:YOKOGAWA ELECTRIC CORP
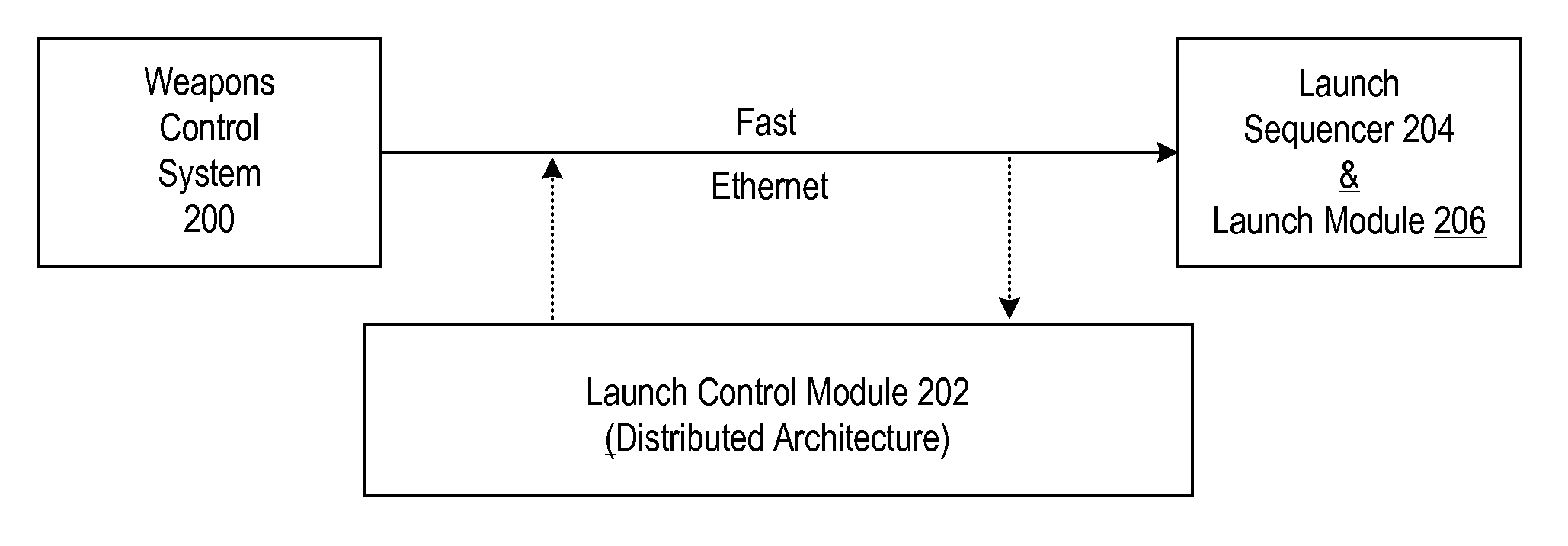
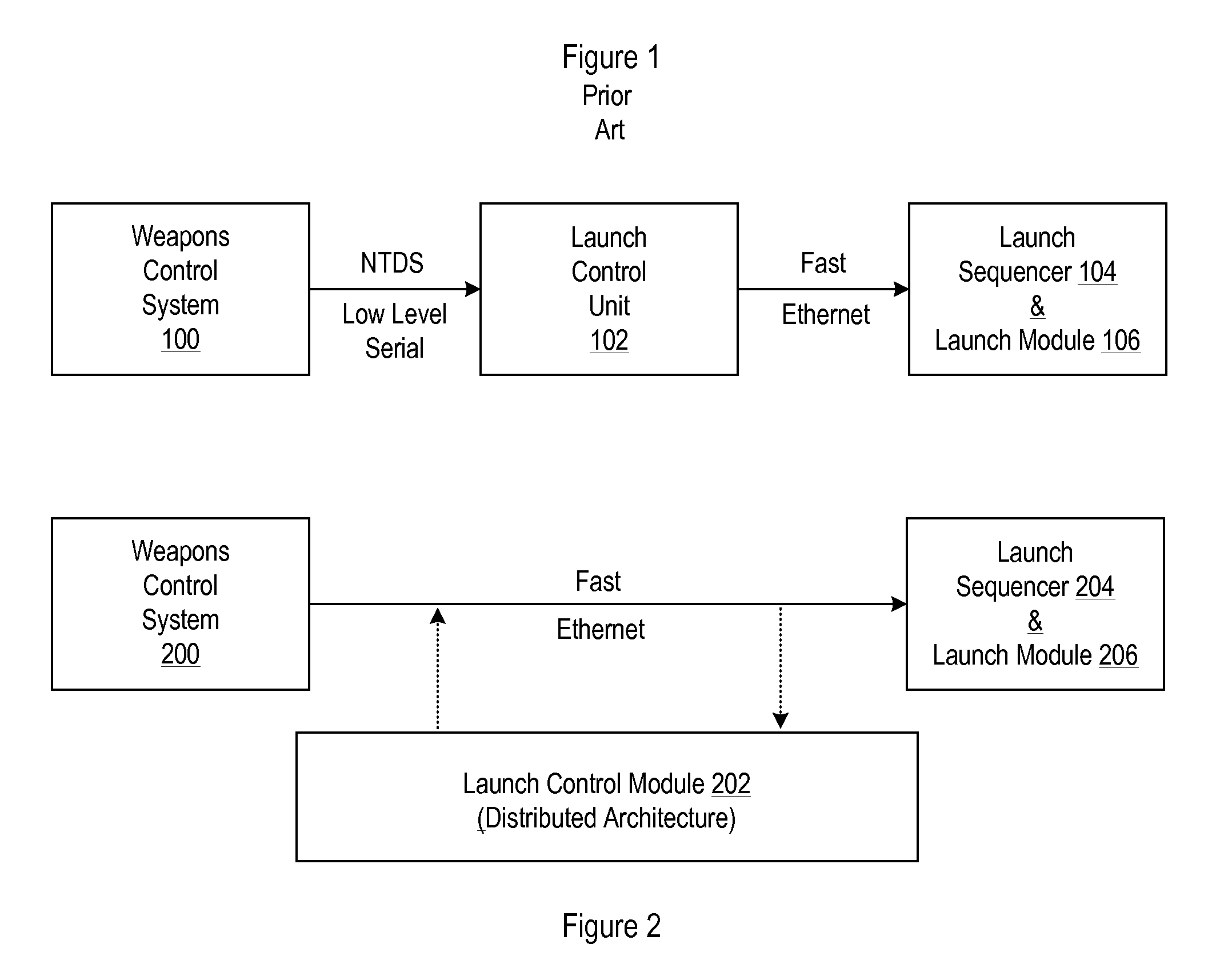
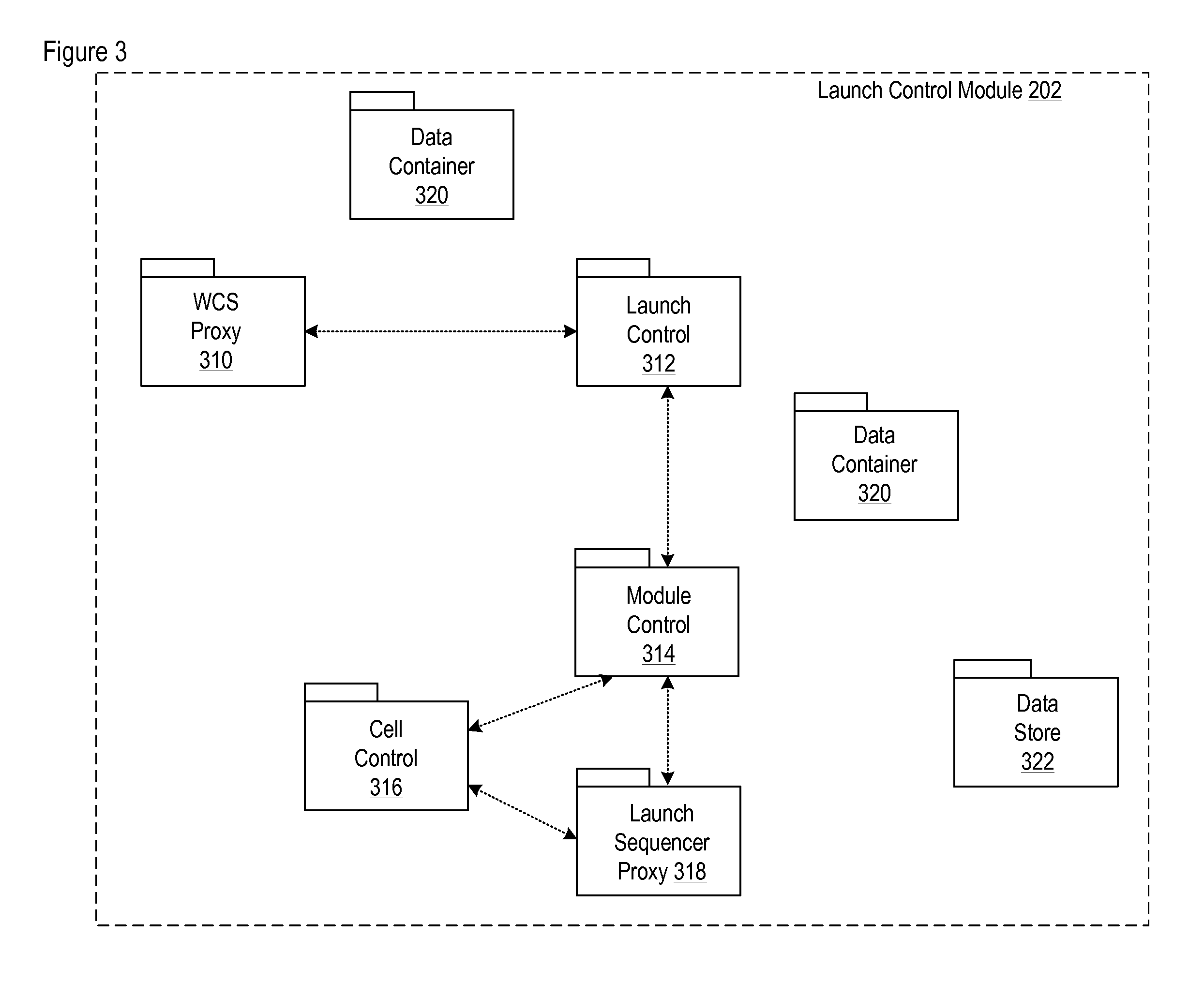
Architecture for a launch controller
InactiveUS20110049237A1Eliminate needTightly coupledRocket launchersDirection controllersControl systemSoftware architecture
A scalable and distributable software architecture for use in conjunction with various different weapons control system and launch systems is disclosed. The architecture discards the proprietary and non-open protocols and services that characterize in favor of open source adaptive and middleware components. In the illustrative embodiment of the invention, the inventive architecture is implemented as a Launch Control Module that separates different layers of responsibility within a launch controller (e.g., LCU) and exposes its variation points.
Owner:LOCKHEED MARTIN CORP
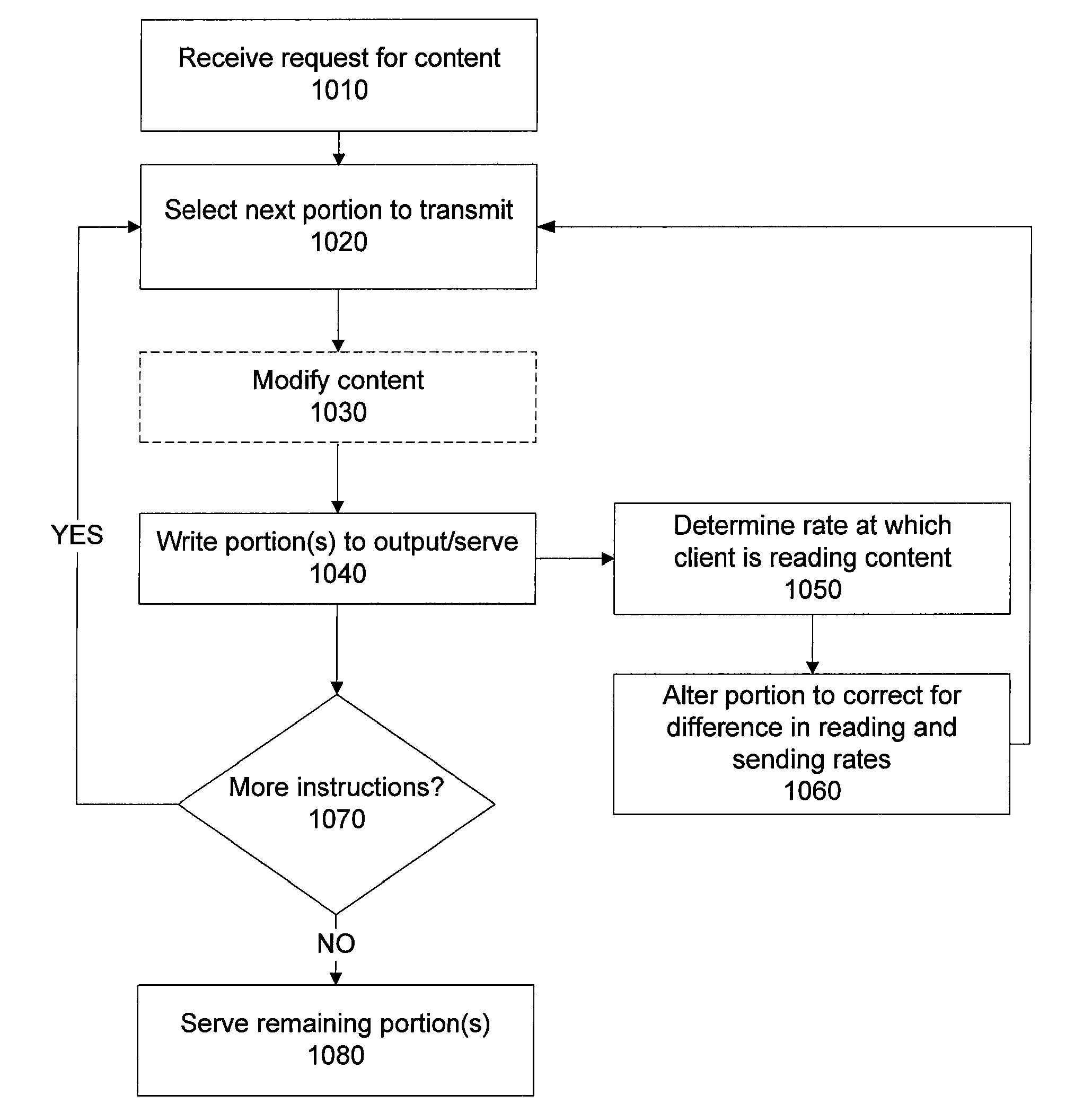
Media article adaptation to client device
ActiveUS8060641B2Monitors the reception rate of the content sentColor television detailsData switching by path configurationClient systemOPEN protocol
Systems and methods provide for on-the-fly adaptation of a send rate for content sent to a client based on a detected read rate of the client system for data previously sent. The system and method work within the bounds of simple, existing, open protocols and the media files served are playable by standard media playback clients. The method is driven by a request for media content from a client, in response to which the server provides portions of the media content and monitors the reception rate of the content as it is sent to the client. This method allows for dynamic modification of the send rate of the content after the server has calculated an adjustment to correct for the difference between the reading rate and sending rate, thereby allowing for a send rate most compatible with the client.
Owner:GOOGLE LLC
Intelligent Building Automation Node
InactiveUS20120254475A1Easy to convergeEasy to integrateData switching current supplyHome automation networksMonitoring and controlEngineering
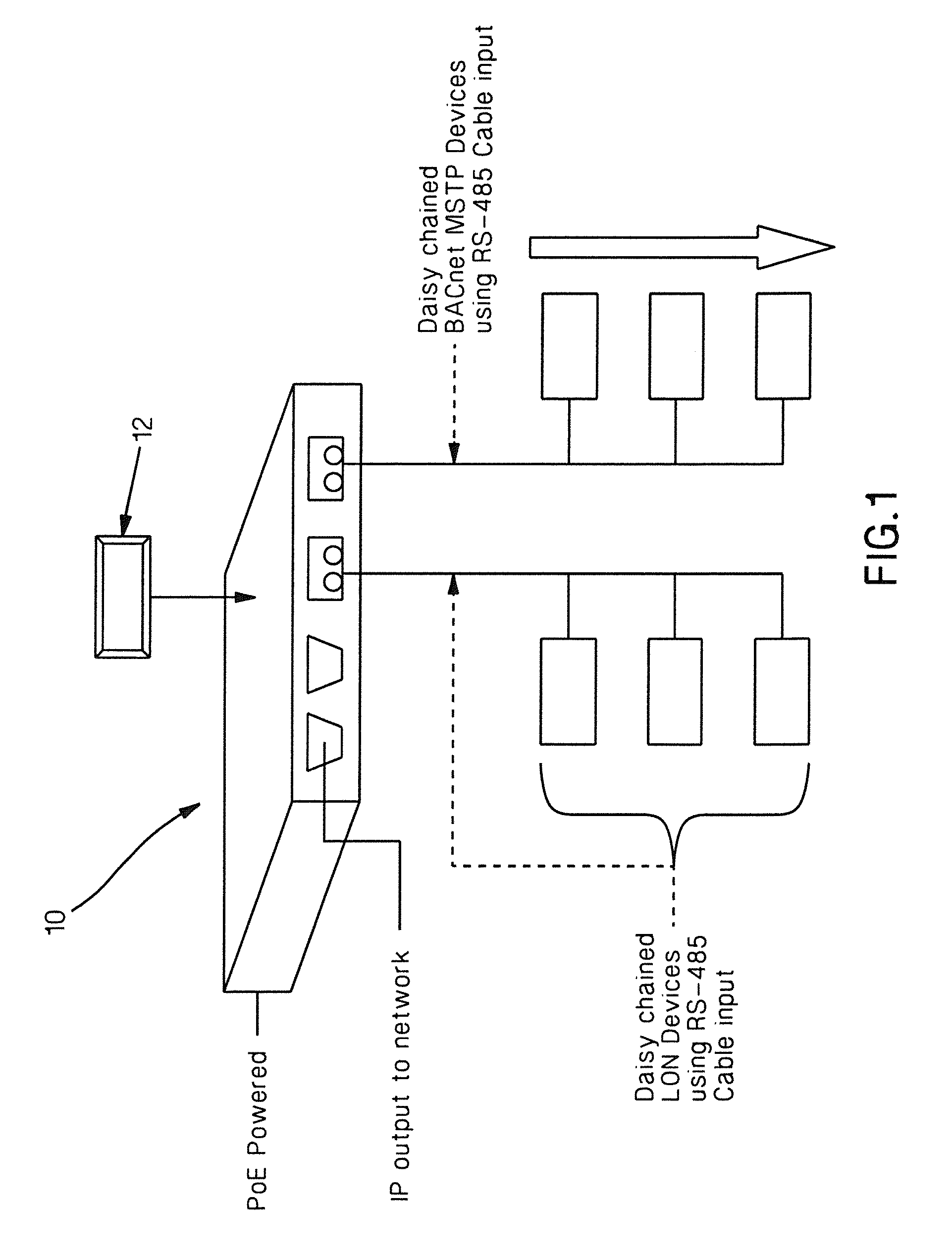
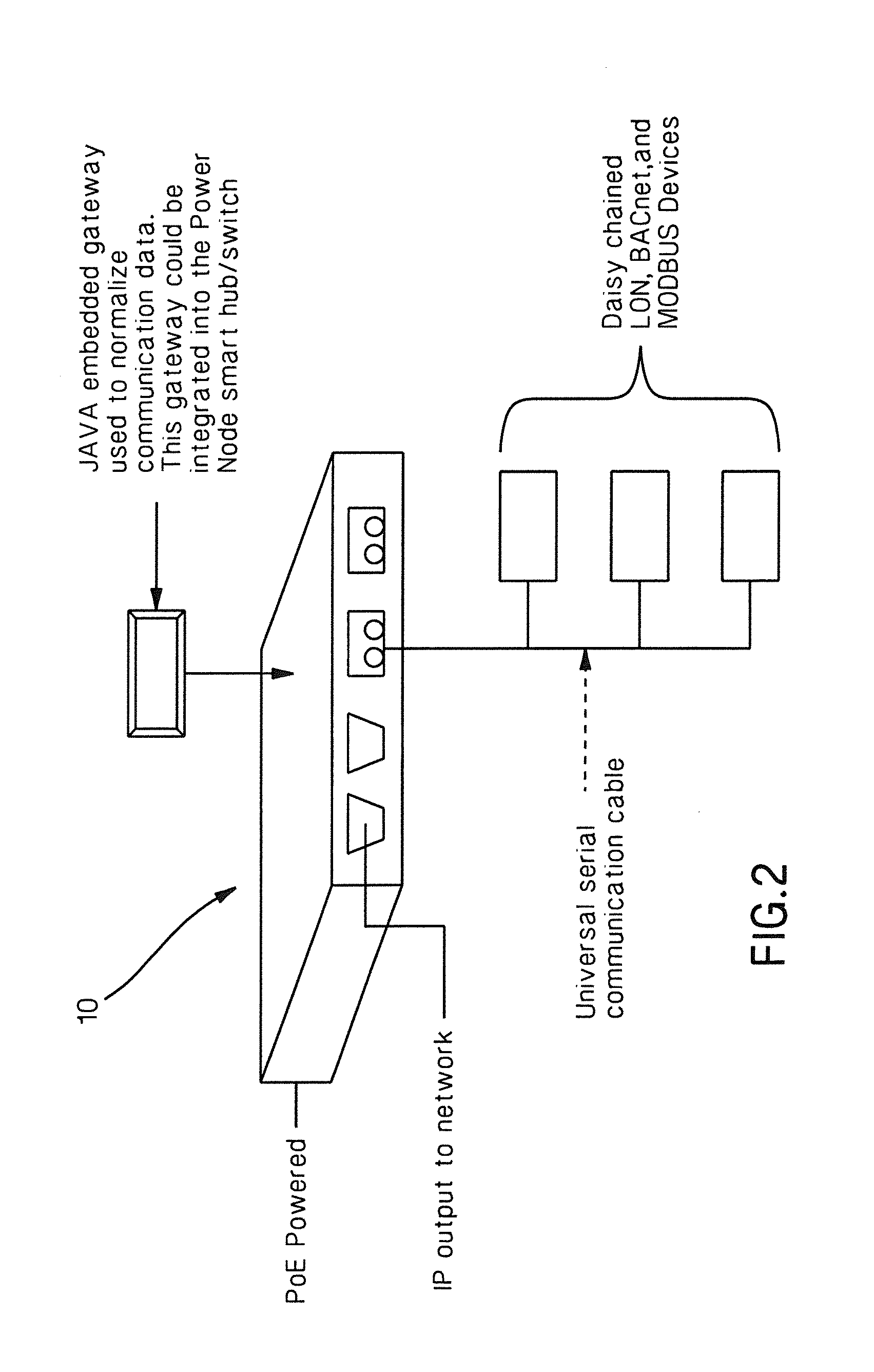
Apparatuses and methods for use in connection with a Building Automation System (BAS) are disclosed herein. In one embodiment, the present invention comprises an intelligent power node comprising a JAVA-enabled device and serial communication cable that provide a seamless open protocol and aggregation point to broadcast internet protocol communications. In another embodiment, the present invention enables energy monitoring and control of individual ports and outlets. In yet another embodiment, the present invention is a method of configuring and operating fieldbus devices.
Owner:PANDUIT
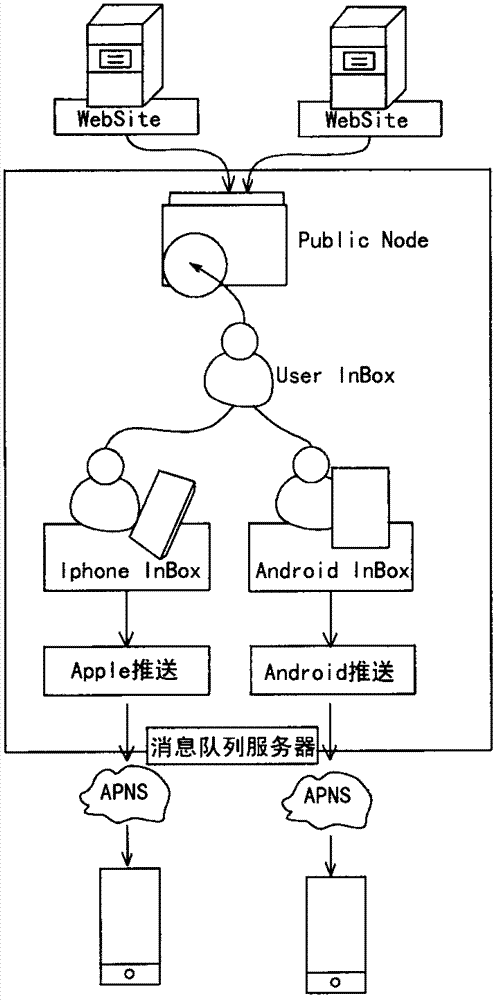
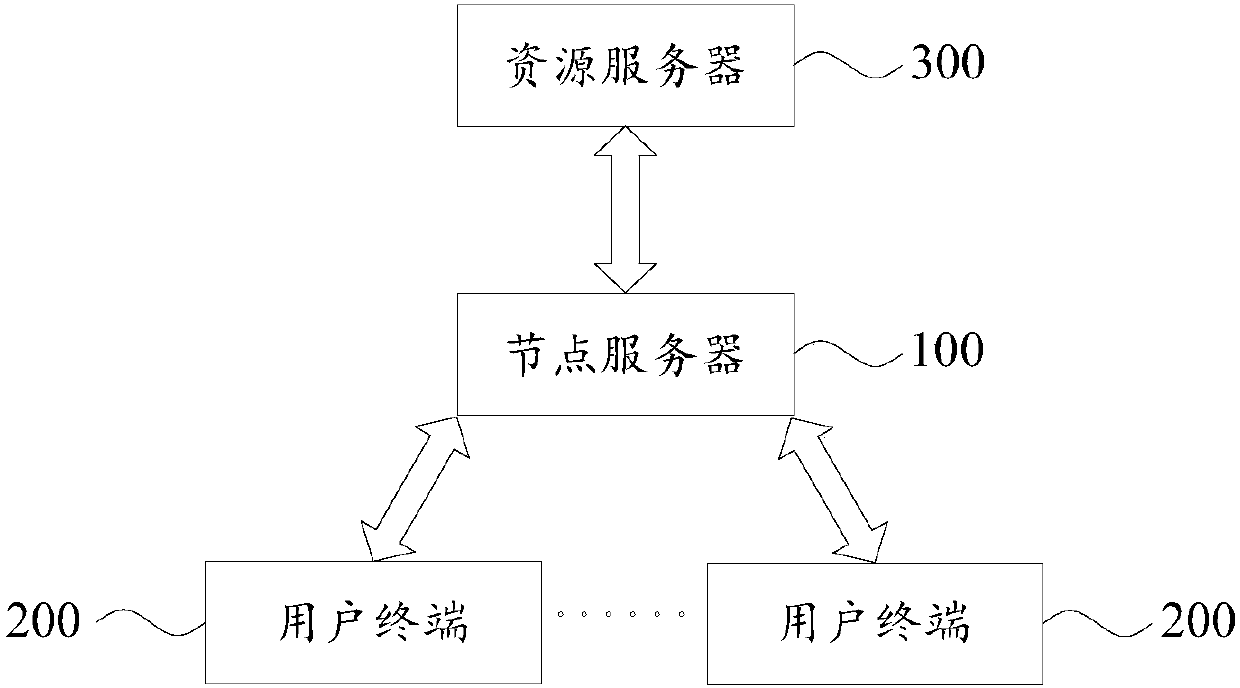
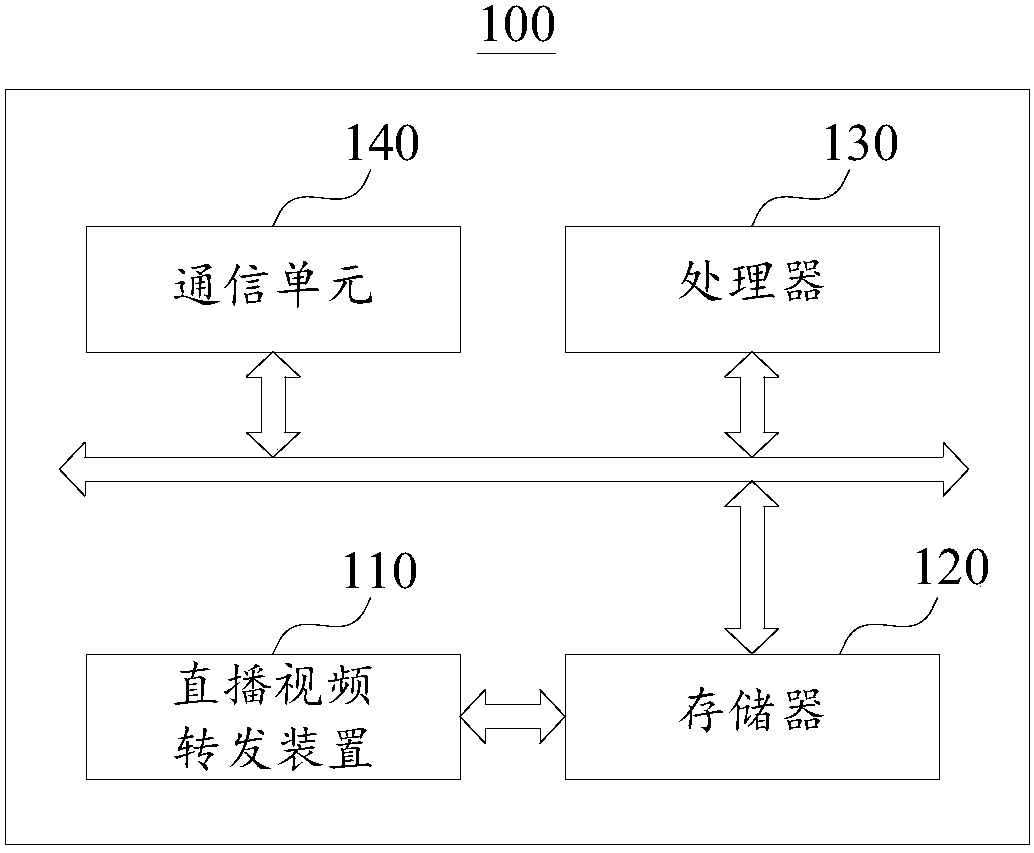
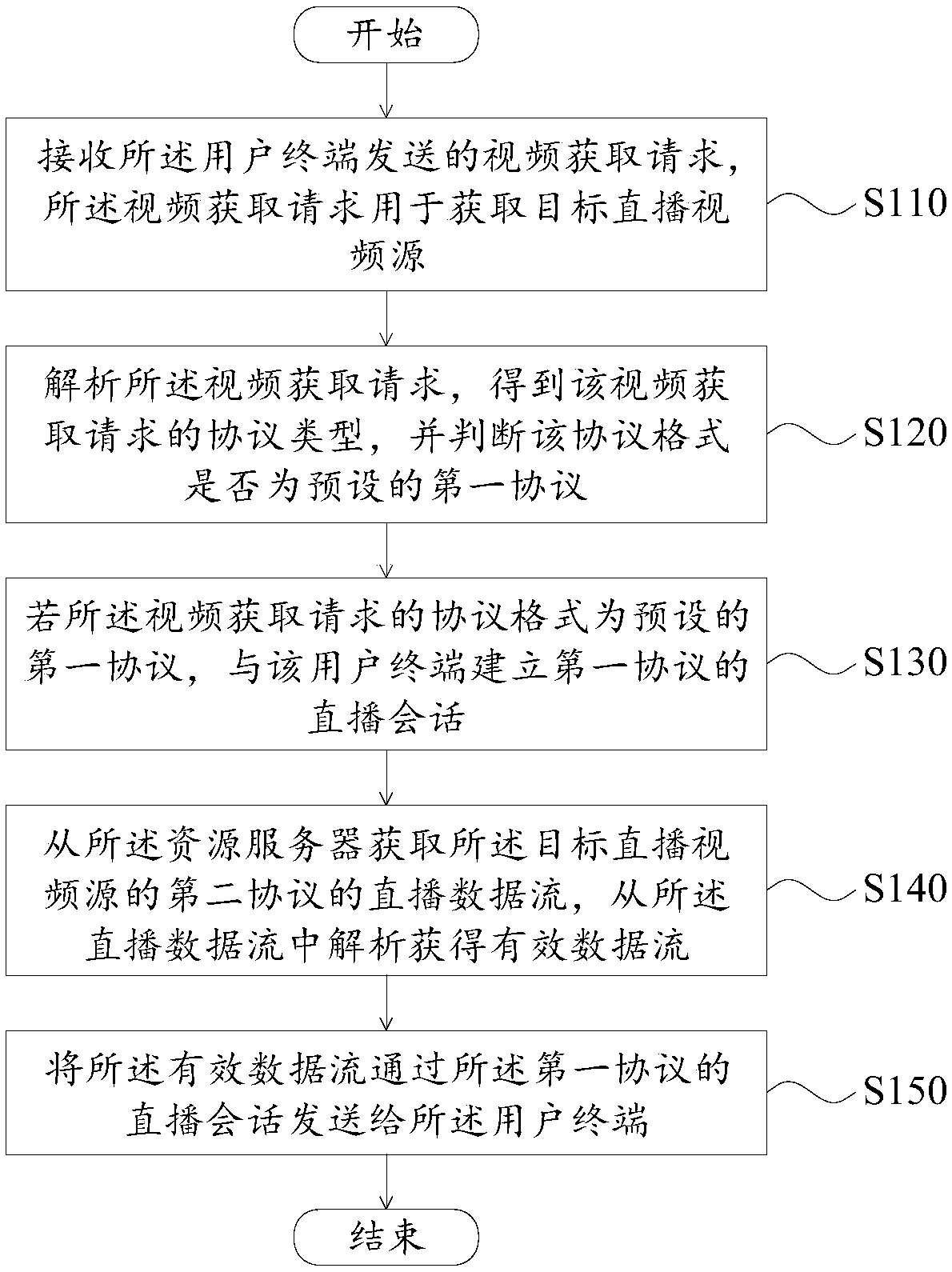
Live-broadcasting video forwarding method and device
The invention provides a live-broadcasting video forwarding method and device, applied to a node server that is communicated with a resource server and a user terminal. The method comprises the following steps: receiving a video acquisition request sent by the user terminal, wherein the video acquisition request is used to acquire a target live-broadcasting video source; parsing the video acquisition request, and if a protocol of the video acquisition request is a preset first protocol, establishing a live-broadcasting session of the first protocol with the user terminal; acquiring a live-broadcasting data stream of a second protocol of the target live-broadcasting video source from the resource server, and parsing the live-broadcasting data stream to obtain an effective data stream, wherein the second protocol is a non-open protocol; and sending the effective data stream to the user terminal through the live-broadcasting session of the first protocol. Thereby, the effect of switchingthe transmission mode of a live-broadcasting video stream from the non-open second protocol to the open first protocol can be implemented without changing the phenomenon that node services obtain live-broadcasting video stream subscription modes from the resource server, and the failure rate that the user terminal receives live-broadcasting videos can be reduced.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
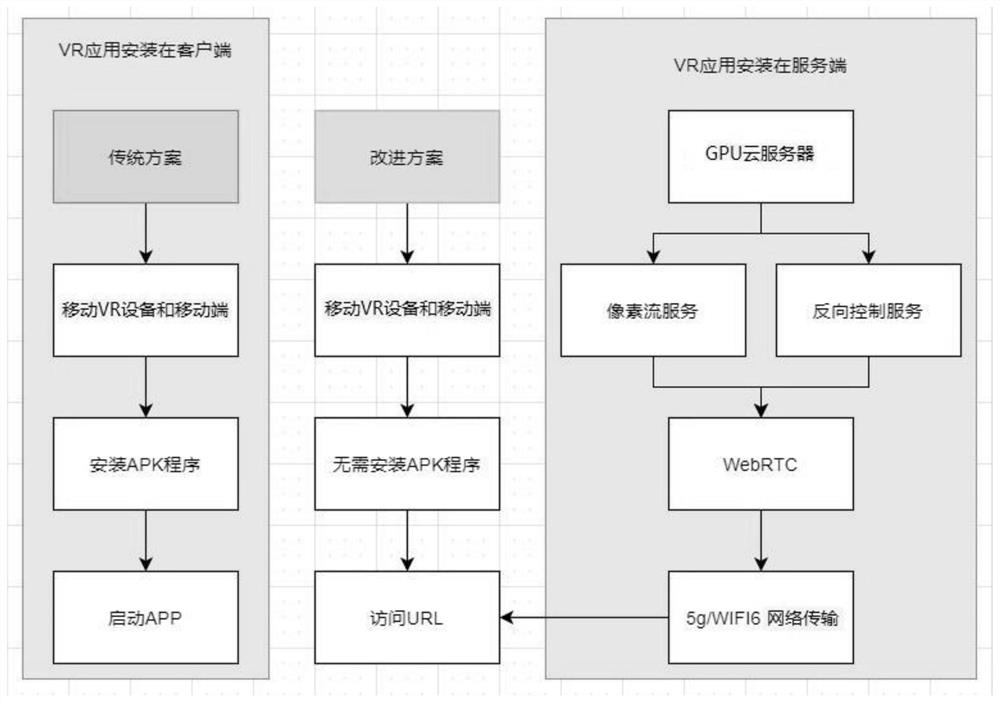
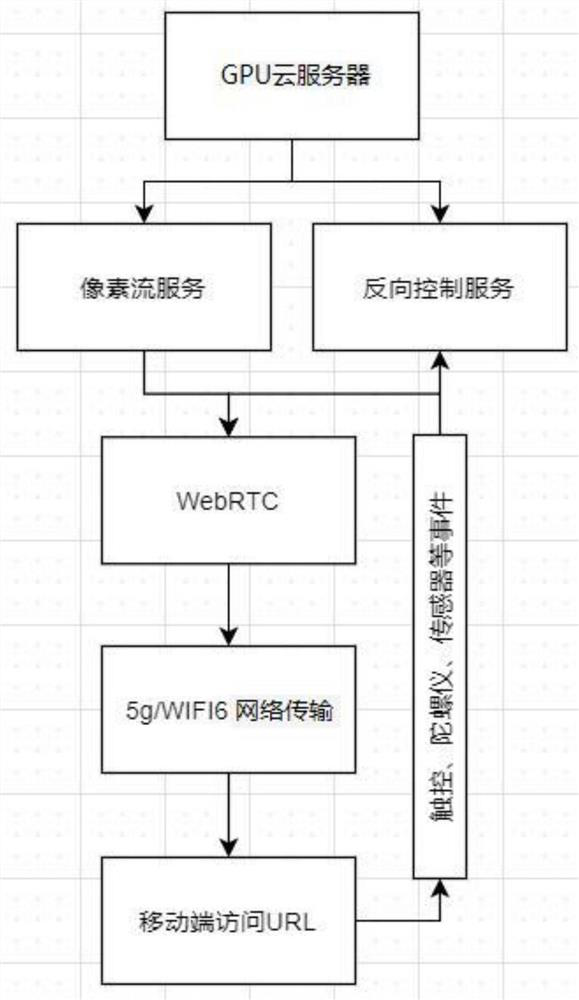
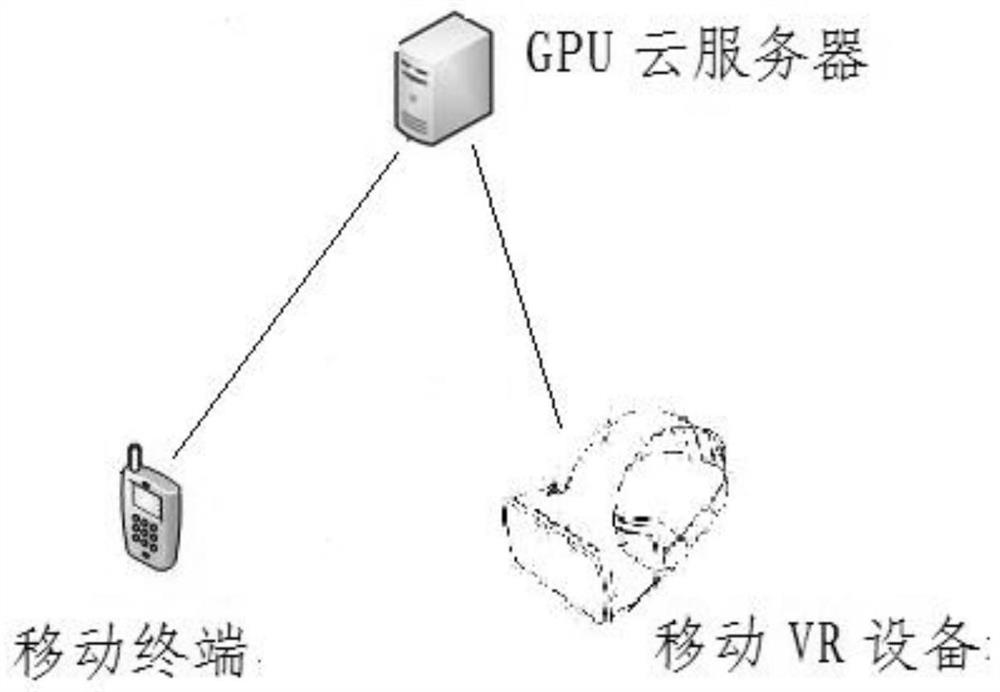
Mobile VR development method based on GPU cloud server and 5G/WIFI6 network transmission technology, and system and medium
InactiveCN112770295AImprove the display effectReduce lossInput/output for user-computer interactionService provisioningTransmission technologyWebRTC
The invention discloses a mobile VR application development method based on a GPU cloud server and a 5G / WIFI 6 network transmission technology, and a system and a computer readable storage medium. The method comprises the following steps: preparing a hardware environment and a network environment; issuing the mobile VR application to the GPU cloud server, and adjusting configuration parameters of the GPU cloud server to meet the operation requirements of the mobile VR application; respectively deploying a pixel flow service module and a reverse control service module on the GPU cloud server; configuring a network environment, a domain name and an open port; pushing the mobile VR application through a WebRTC proxy server, and opening a UDP for receiving reverse control parameters; and using the mobile terminal and the mobile VR device to access the mobile VR application running on the GPU cloud server. According to the invention, limitations of various aspects of a mobile phone terminal during development of the mobile VR application are mainly solved, and the mobile VR application is realized by adopting a new mode and a new technology.
Owner:BEIJING ZHIU TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com