A network transaction security system and method
A security system and network transaction technology, applied in transmission systems, payment architectures, instruments, etc., can solve the problems of limited coverage of third-party security clients, inability to cover phishing websites, and inability to completely block them, achieving high timeliness and low cost The probability of huge loss, the effect of improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
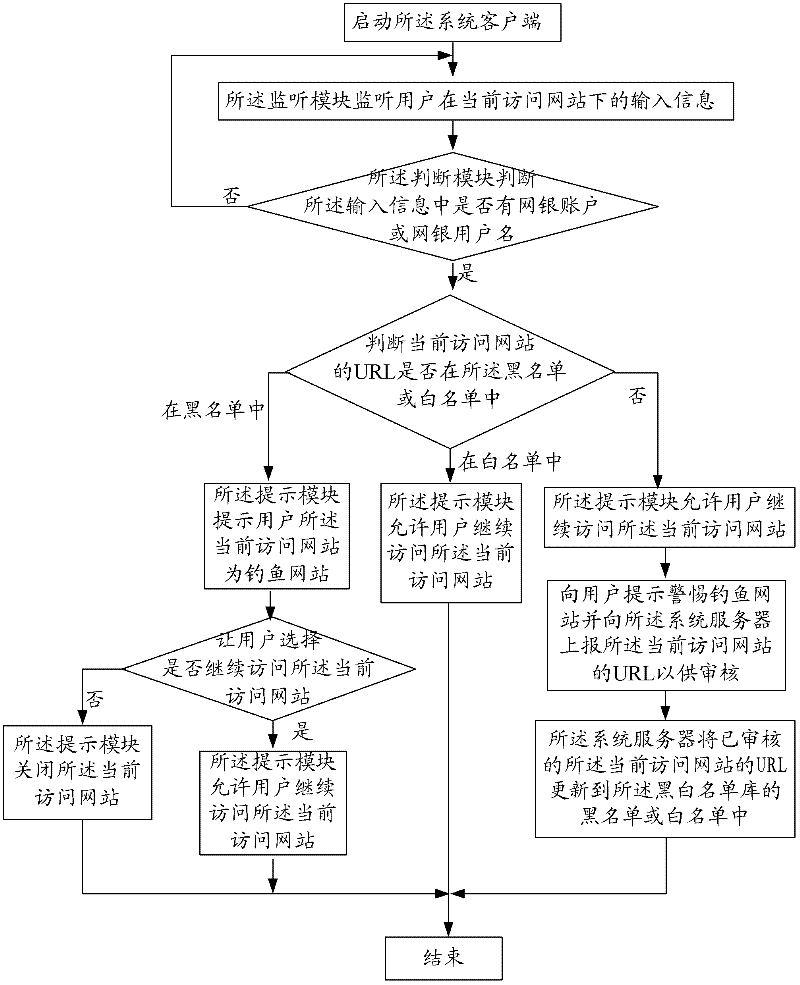
[0039] The network transaction security system and method proposed by the present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments.
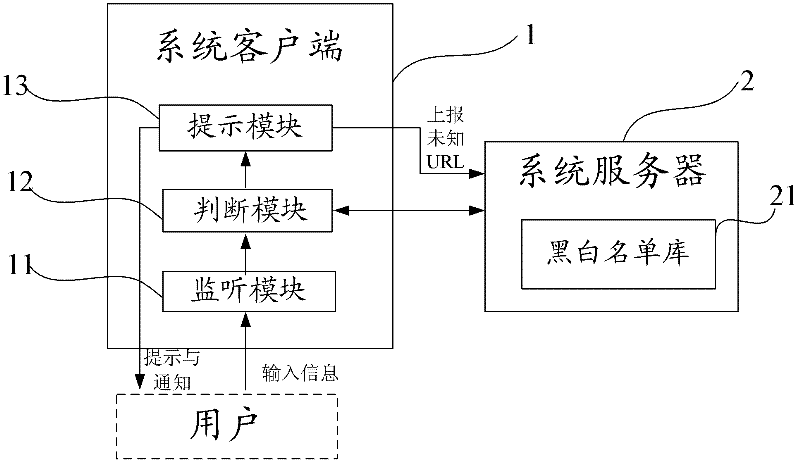
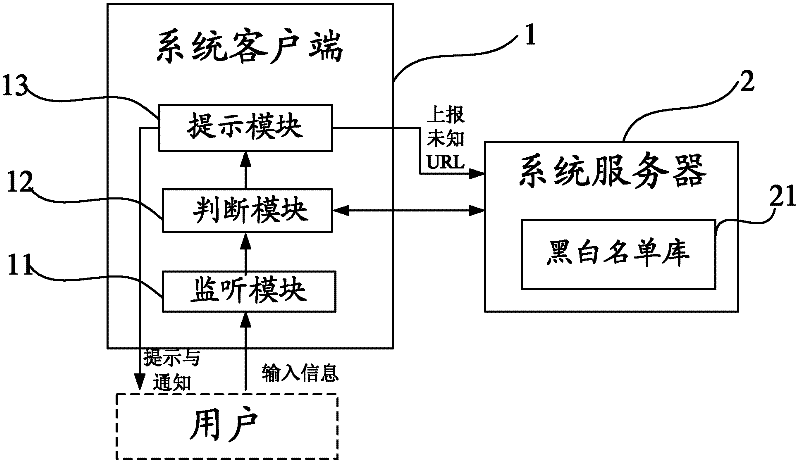
[0040] like figure 1 As shown, the present invention proposes a network transaction security system, including: a system client 1 installed in a user terminal device and a system server 2 interactively communicating with the system client 1 .
[0041] Wherein, the system server 2 is used to store and update the black and white list database 21 of the website, the black list in the black and white list database 21 contains the URLs of the audited phishing websites, and the white list in the black and white list database contains the audited phishing websites. The URL of the secure website.
[0042] The system client 1 includes a monitoring module 11 , a judging module 12 and a prompting module 13 .
[0043] The monitoring module 11 is used to monitor the input information o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com