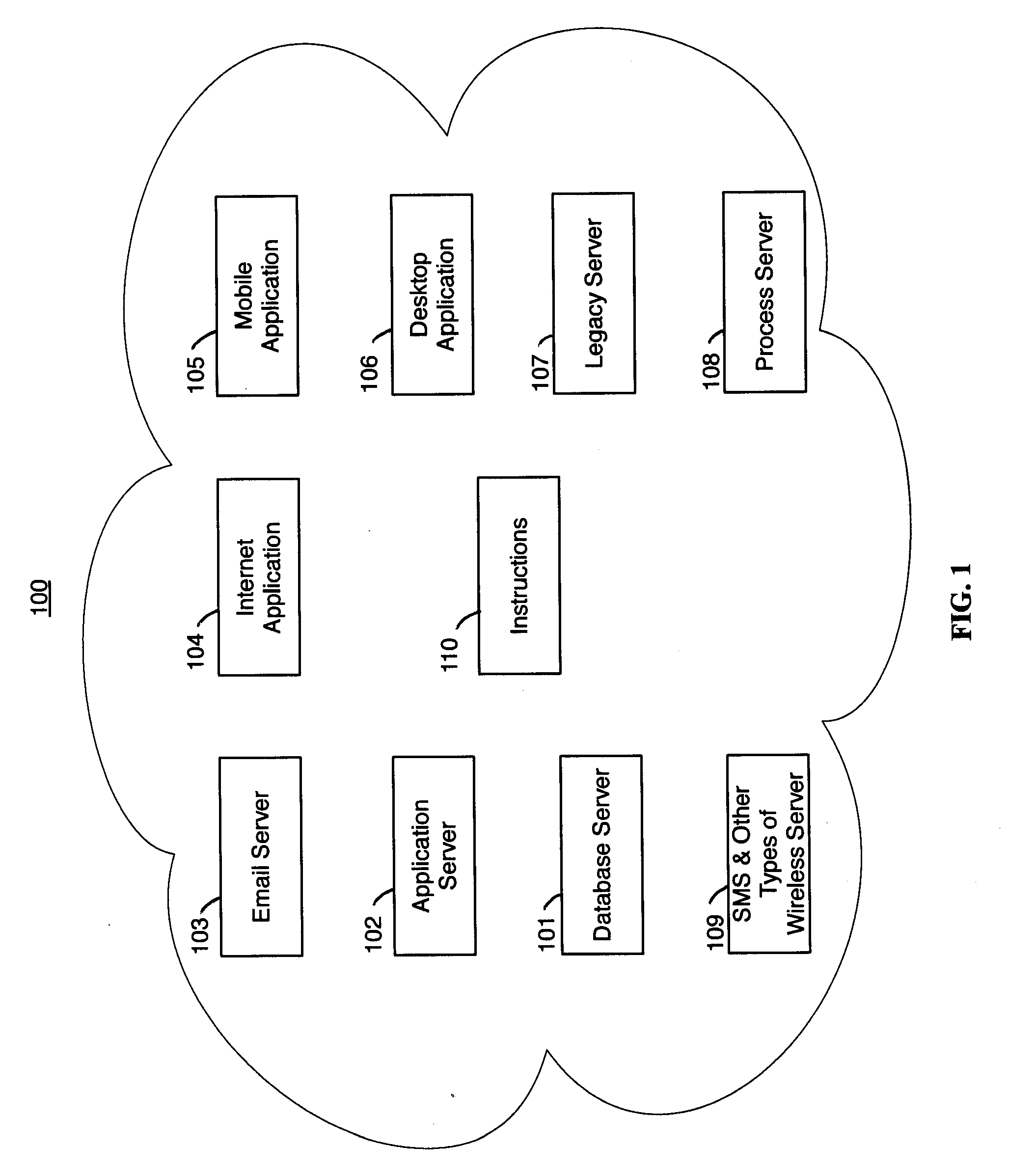
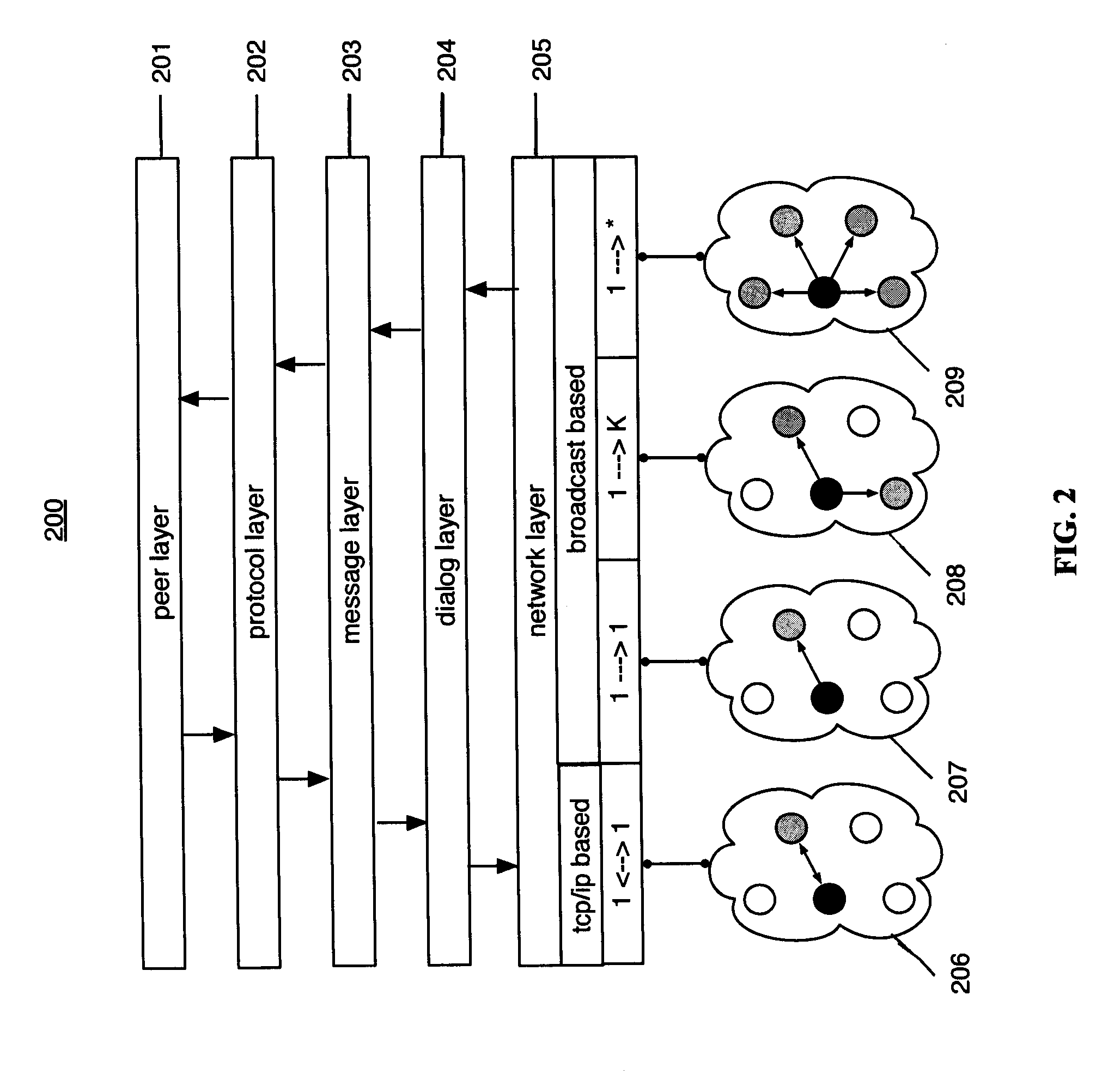
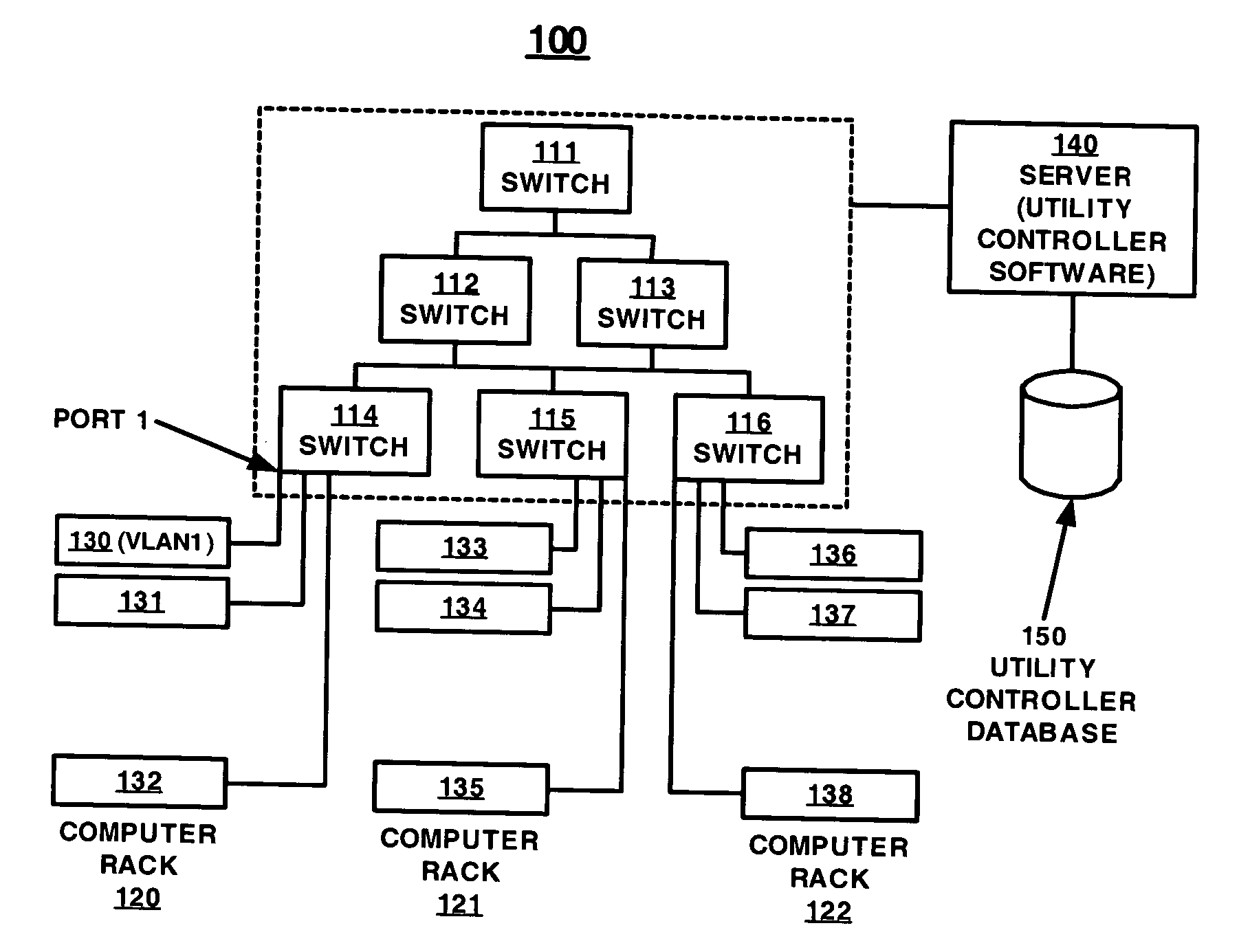
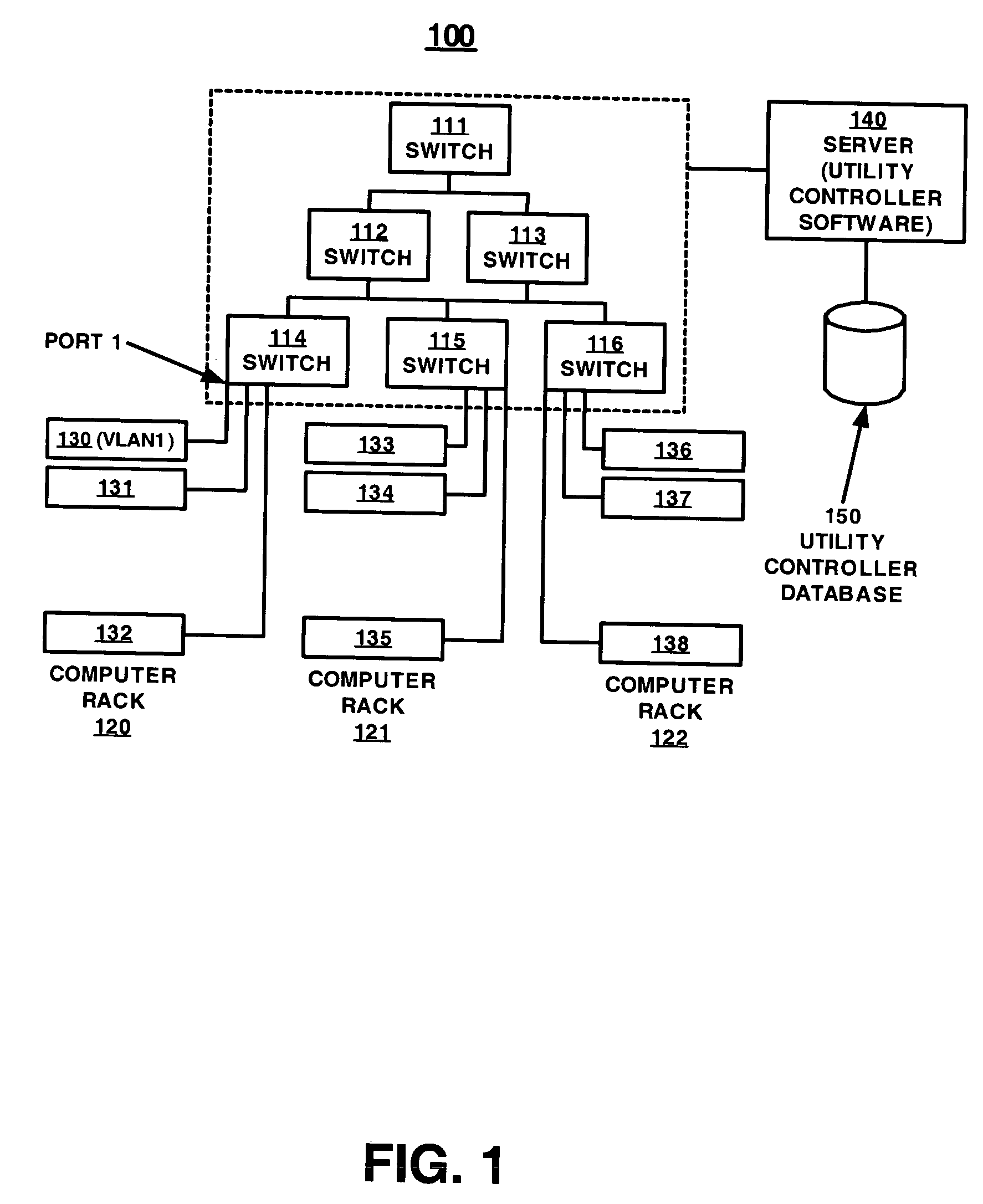
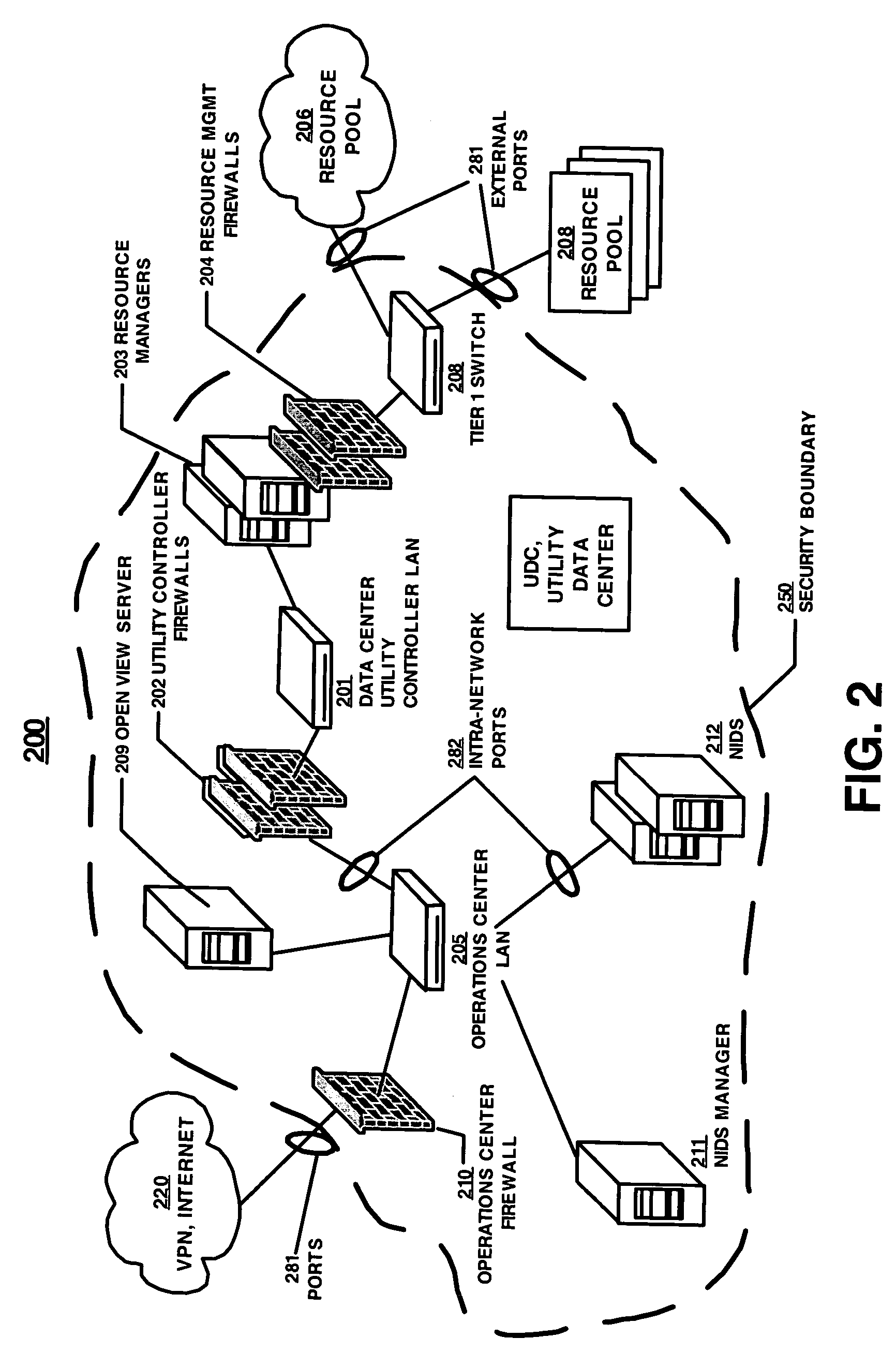
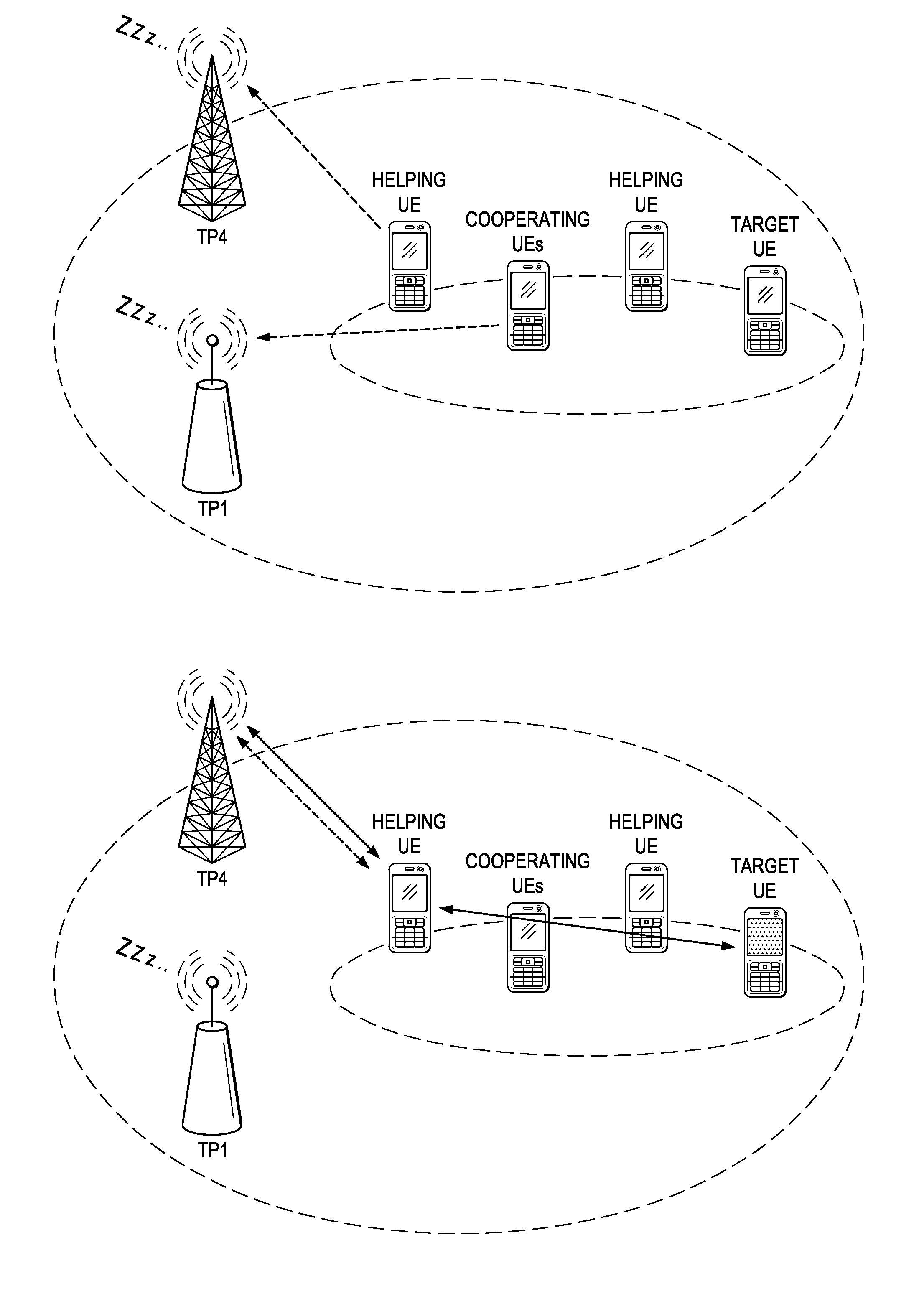
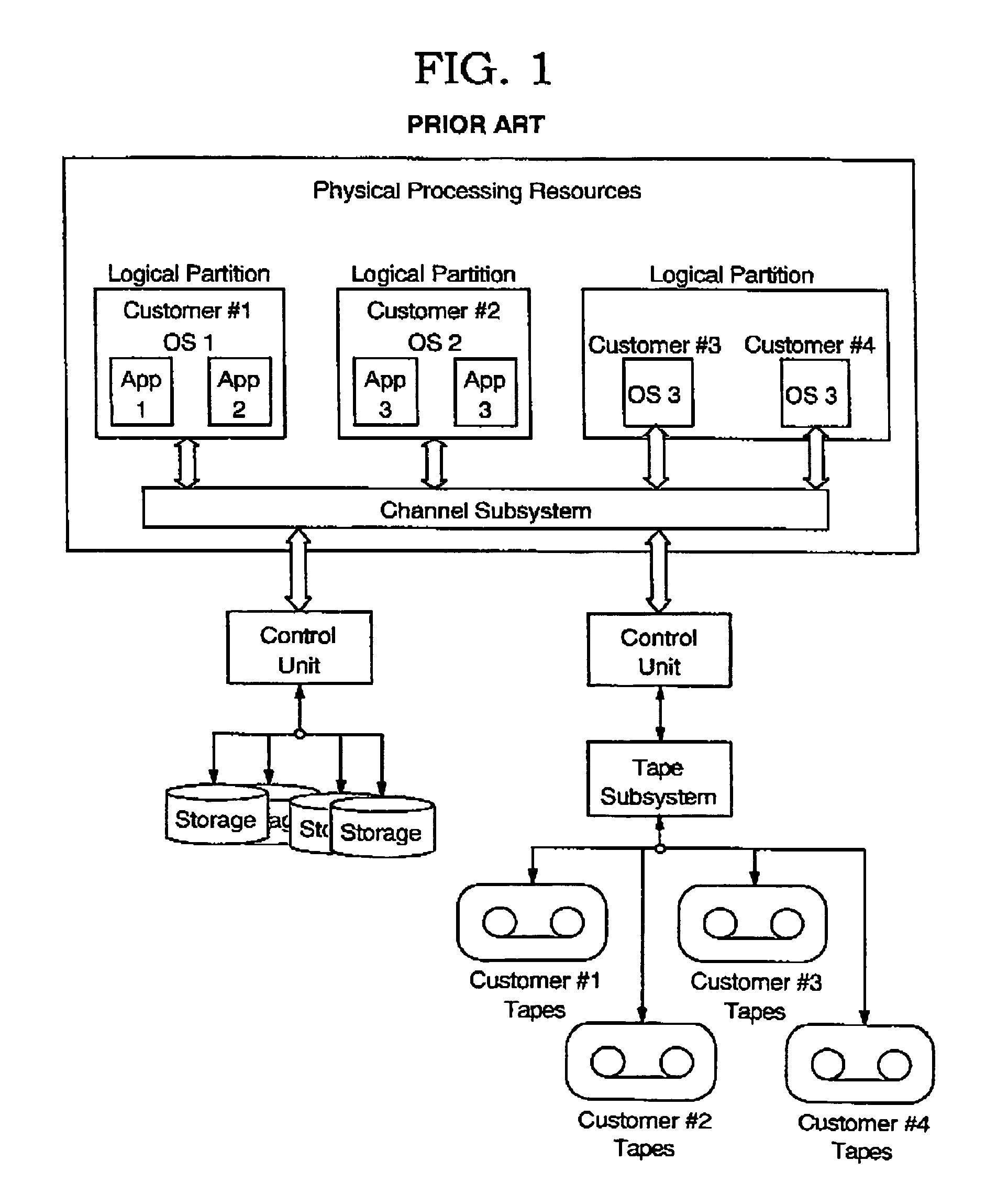
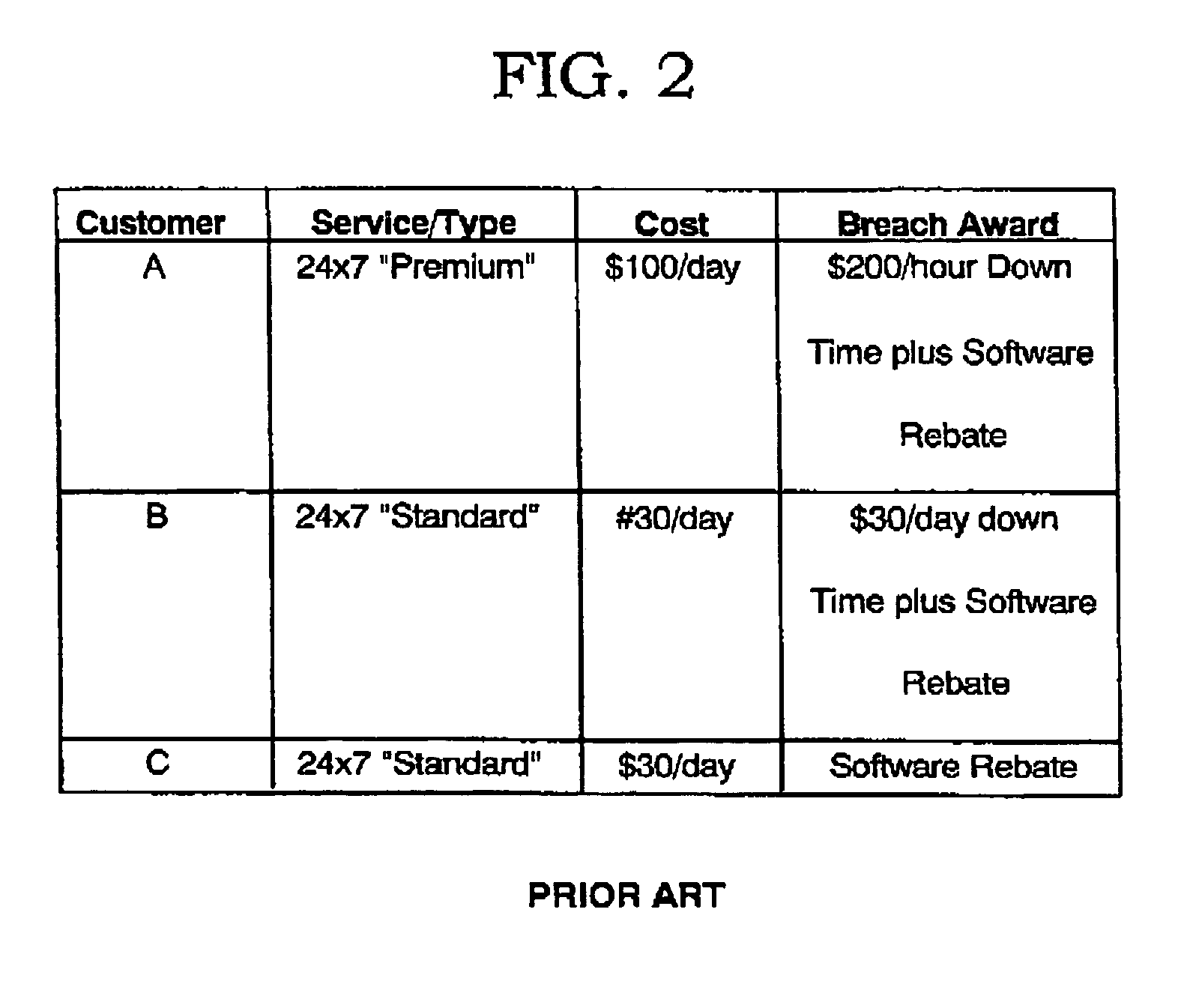
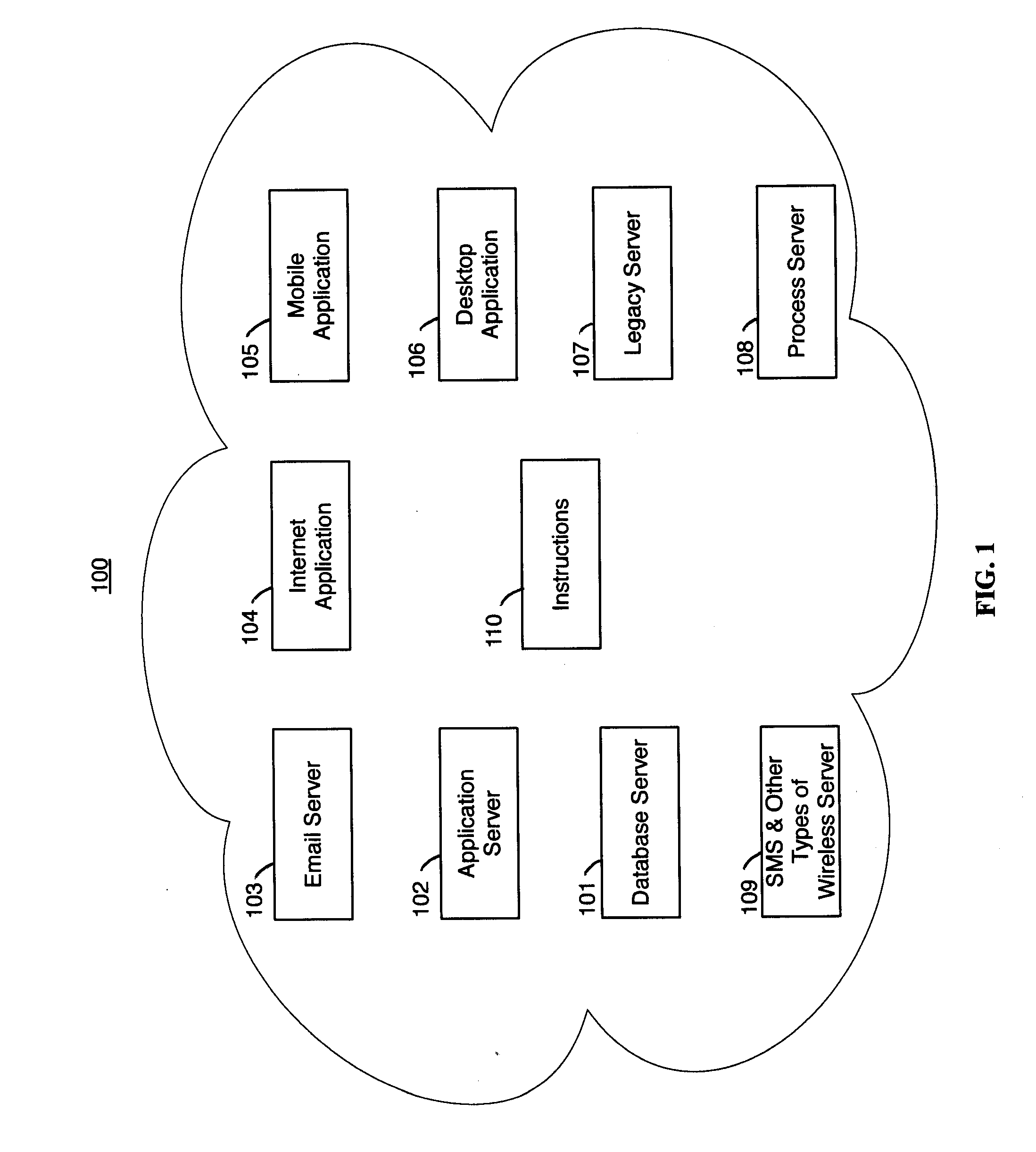
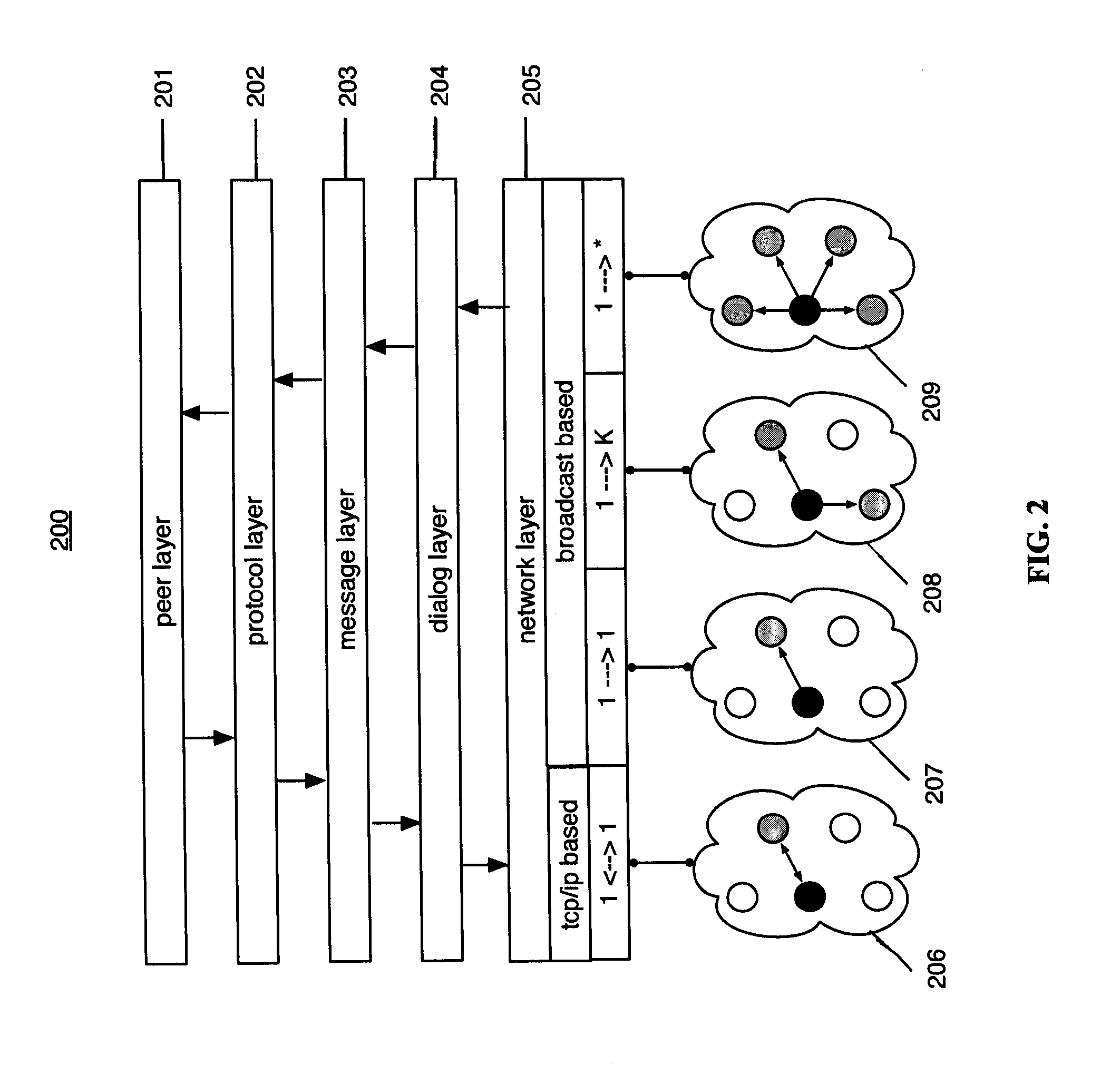
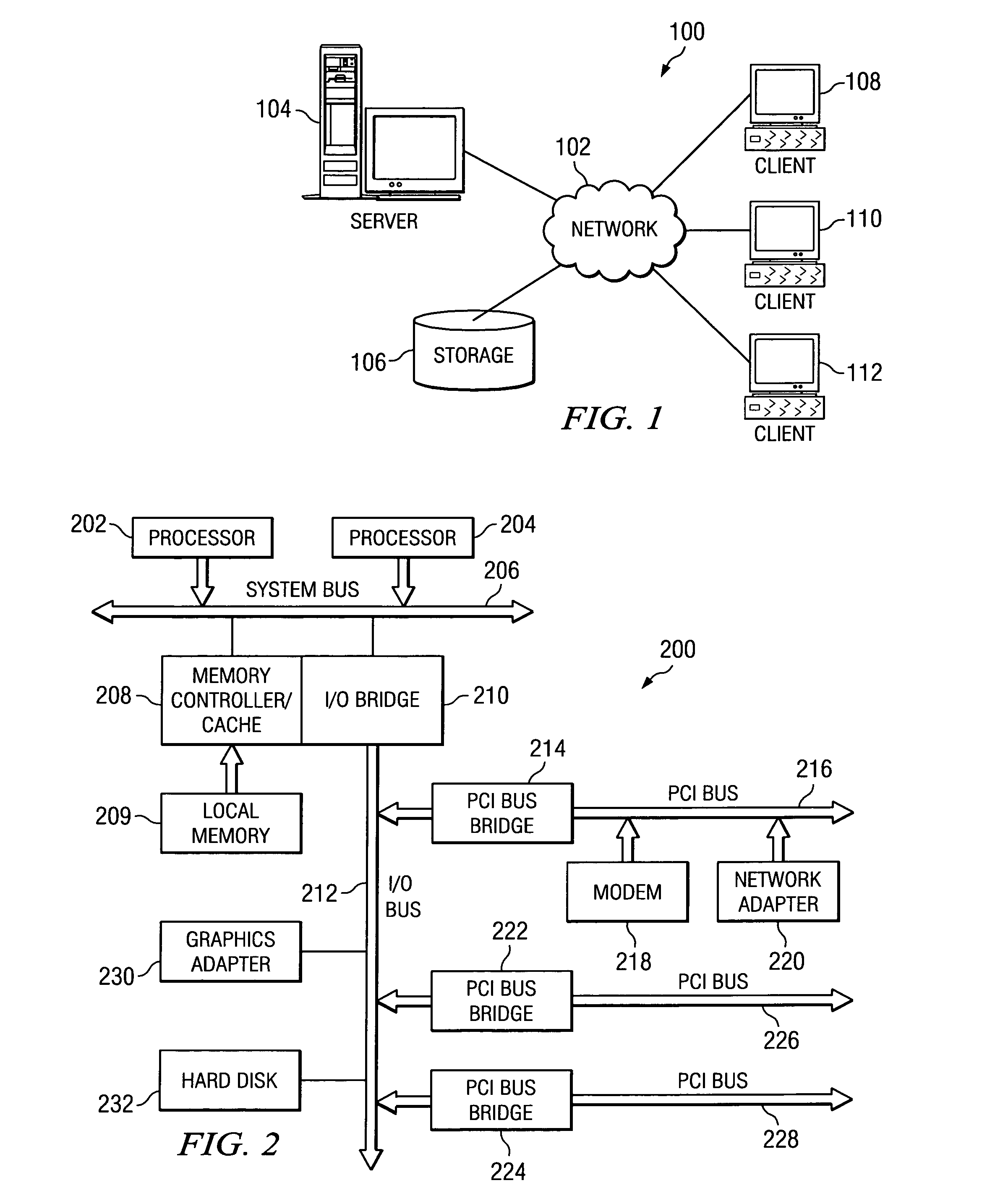
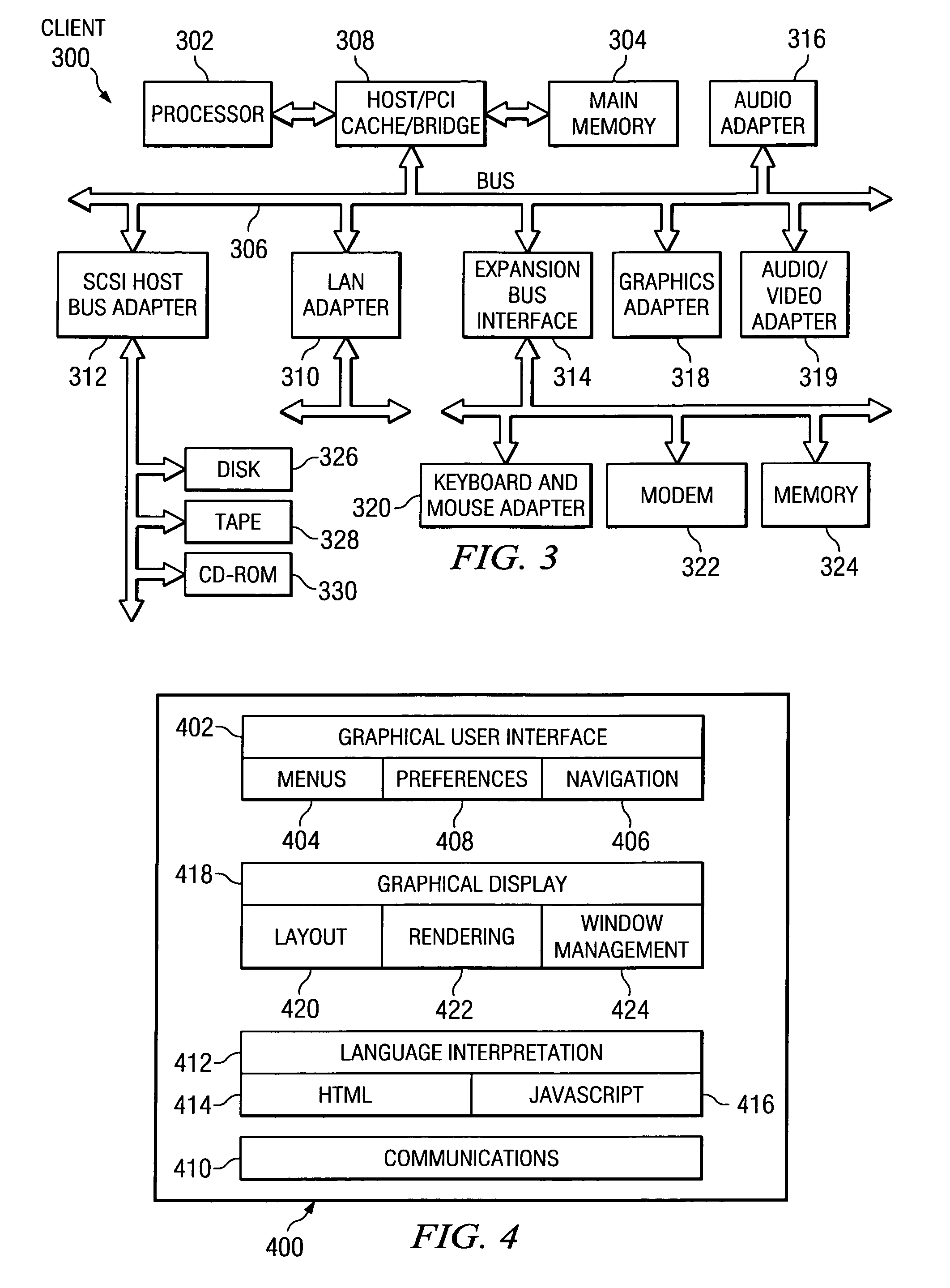
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
69 results about "Utility computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Utility computing, or The Computer Utility, is a service provisioning model in which a service provider makes computing resources and infrastructure management available to the customer as needed, and charges them for specific usage rather than a flat rate. Like other types of on-demand computing (such as grid computing), the utility model seeks to maximize the efficient use of resources and/or minimize associated costs. Utility is the packaging of system resources, such as computation, storage and services, as a metered service. This model has the advantage of a low or no initial cost to acquire computer resources; instead, resources are essentially rented.
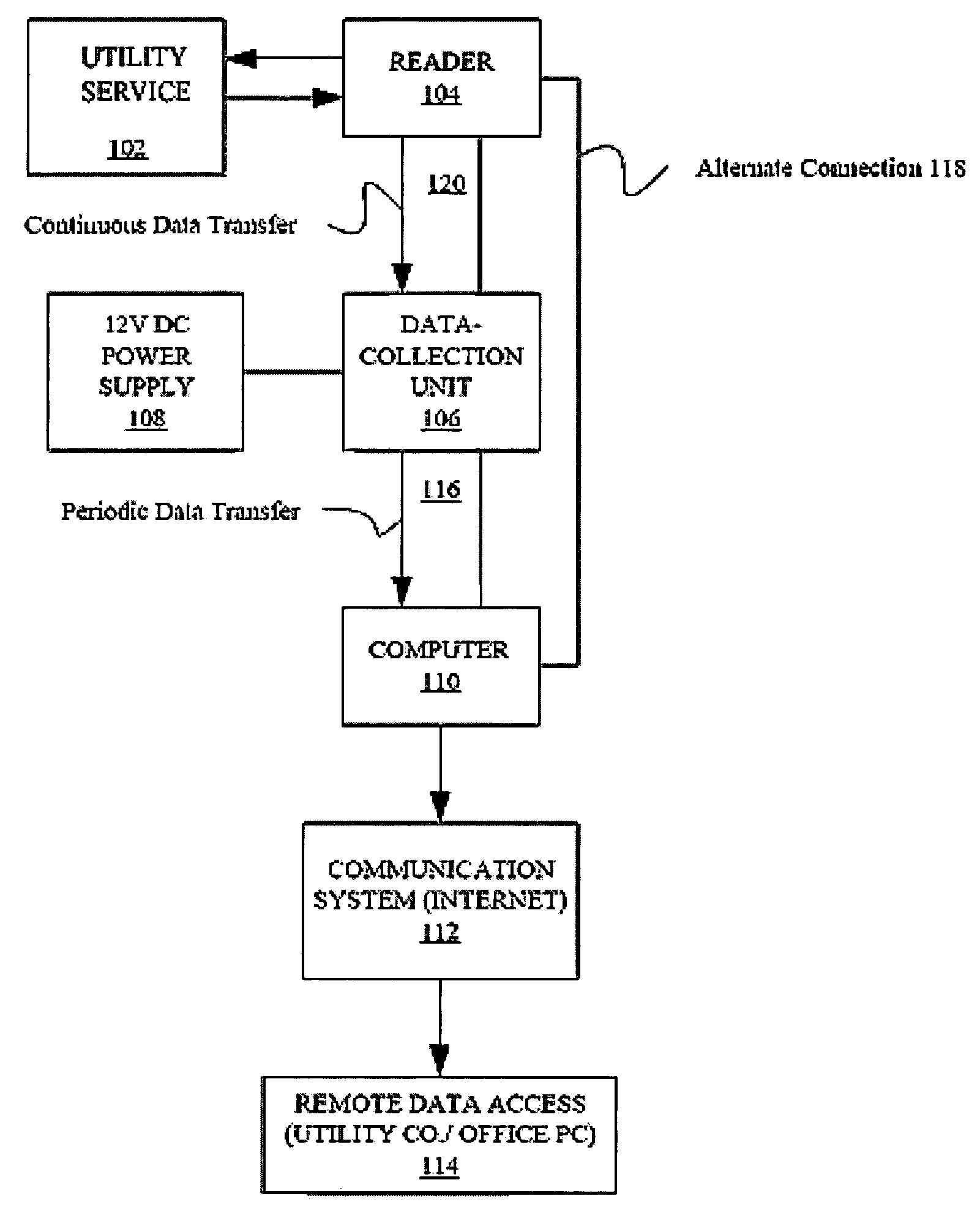
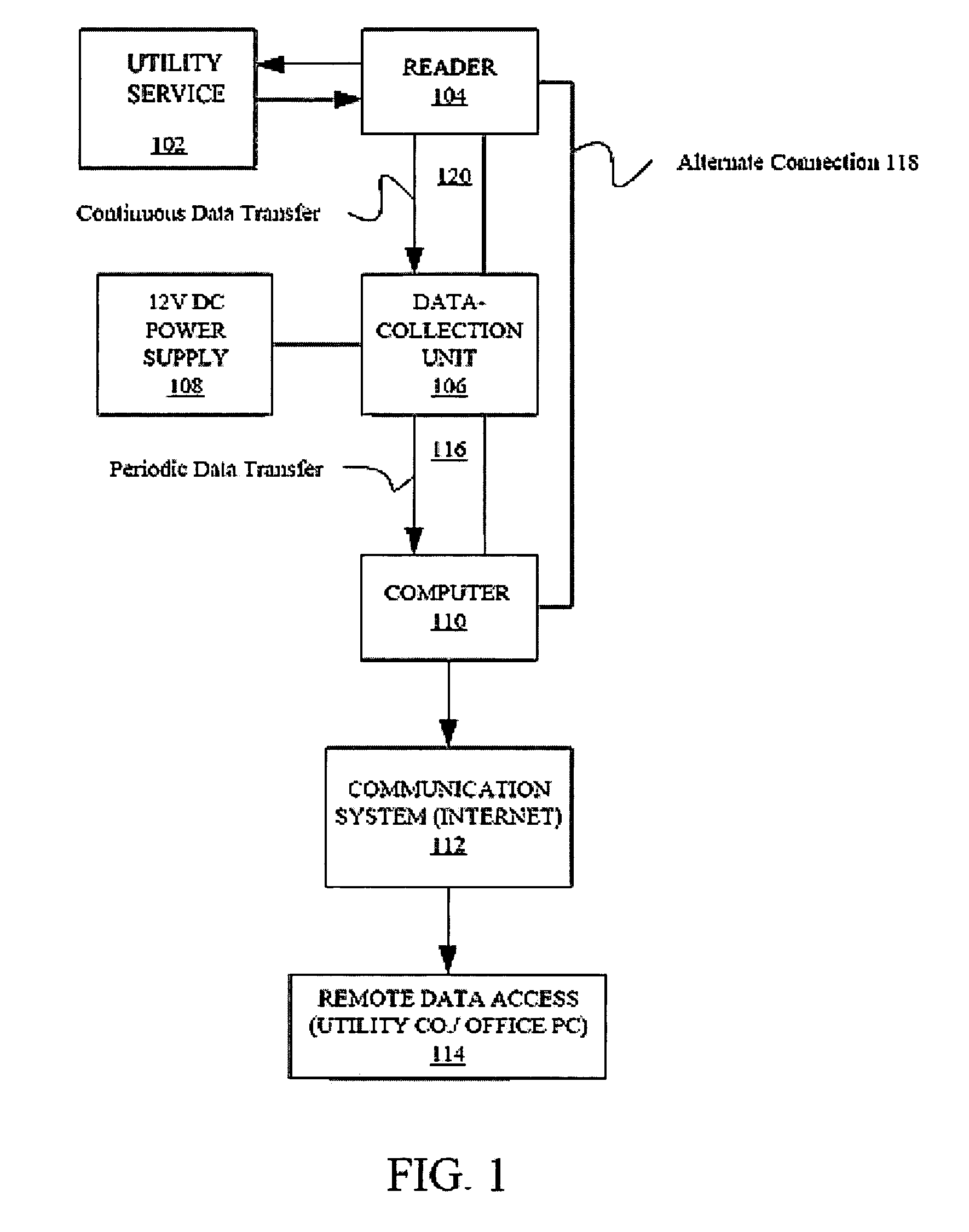
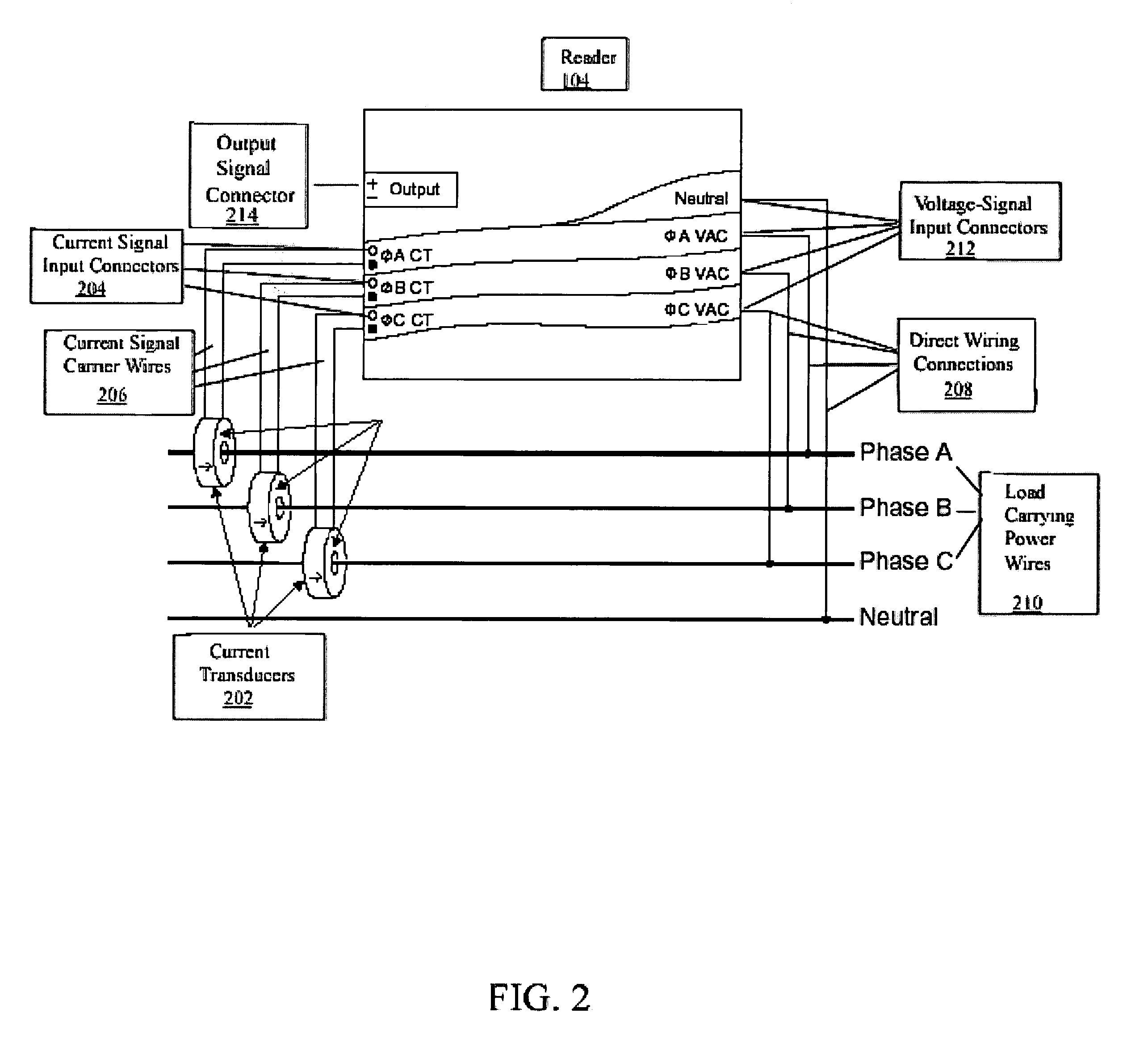
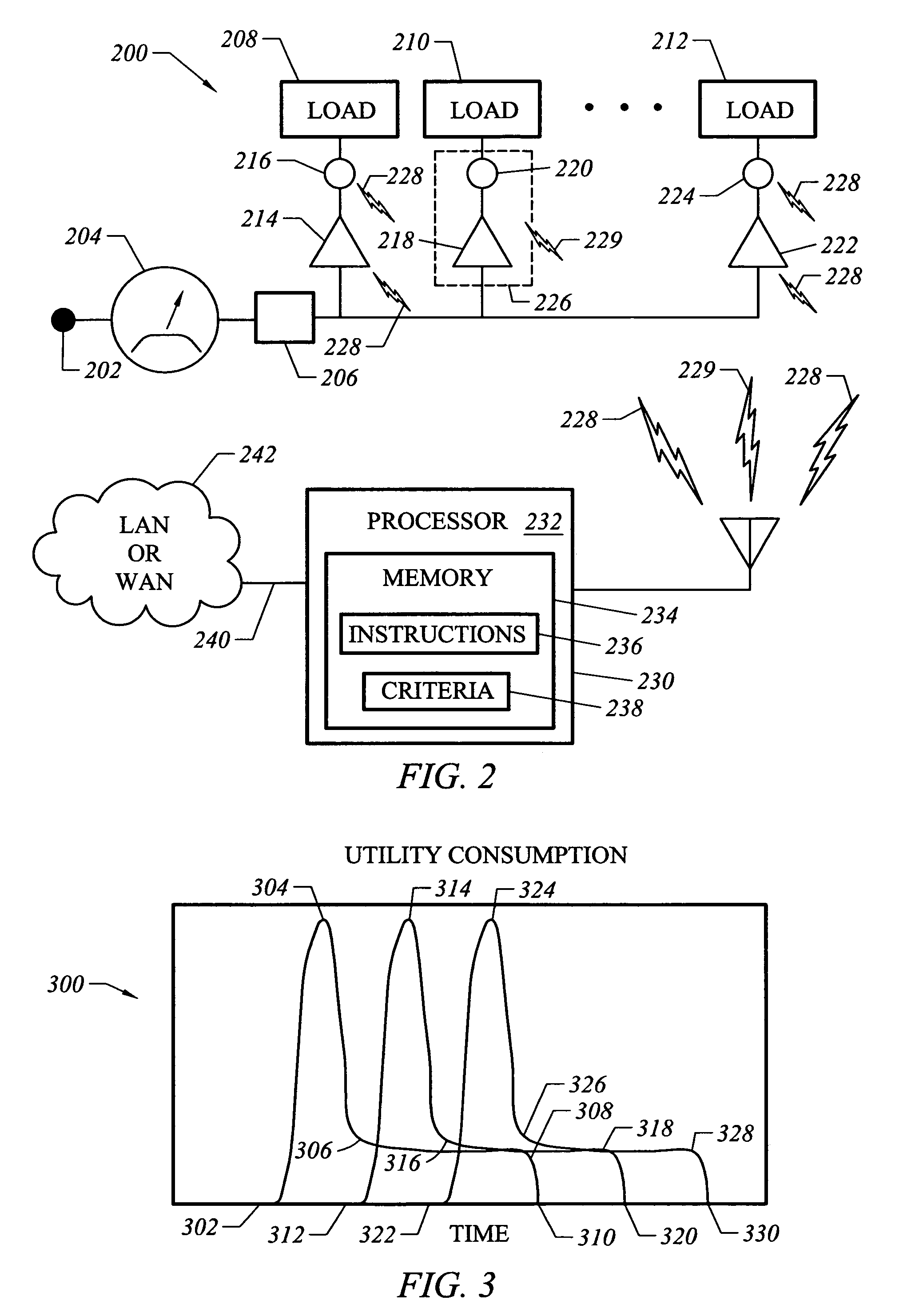
Method and apparatus for reading and controlling utility consumption
InactiveUS7039532B2Good energyElectric devicesElectric testing/monitoringElectricityUtility computing
A method and system for controlling electric power consumption using a computer to create a forecast and then controlling devices that use power based on the forecast. An automatic reader device is used to gather power consumption data from a point of utility service. The power consumption data is then provided to a computer. The computer is used to create a forecast of energy use for instantaneous demand and time-based usage. The computer then provides alerts based on the forecast for the manual or automatic control of devices that consume electricity. The system may be managed locally or remotely by a computer, PDA, cell phone or other network enabled device.
Owner:TRENDPOINT SYST
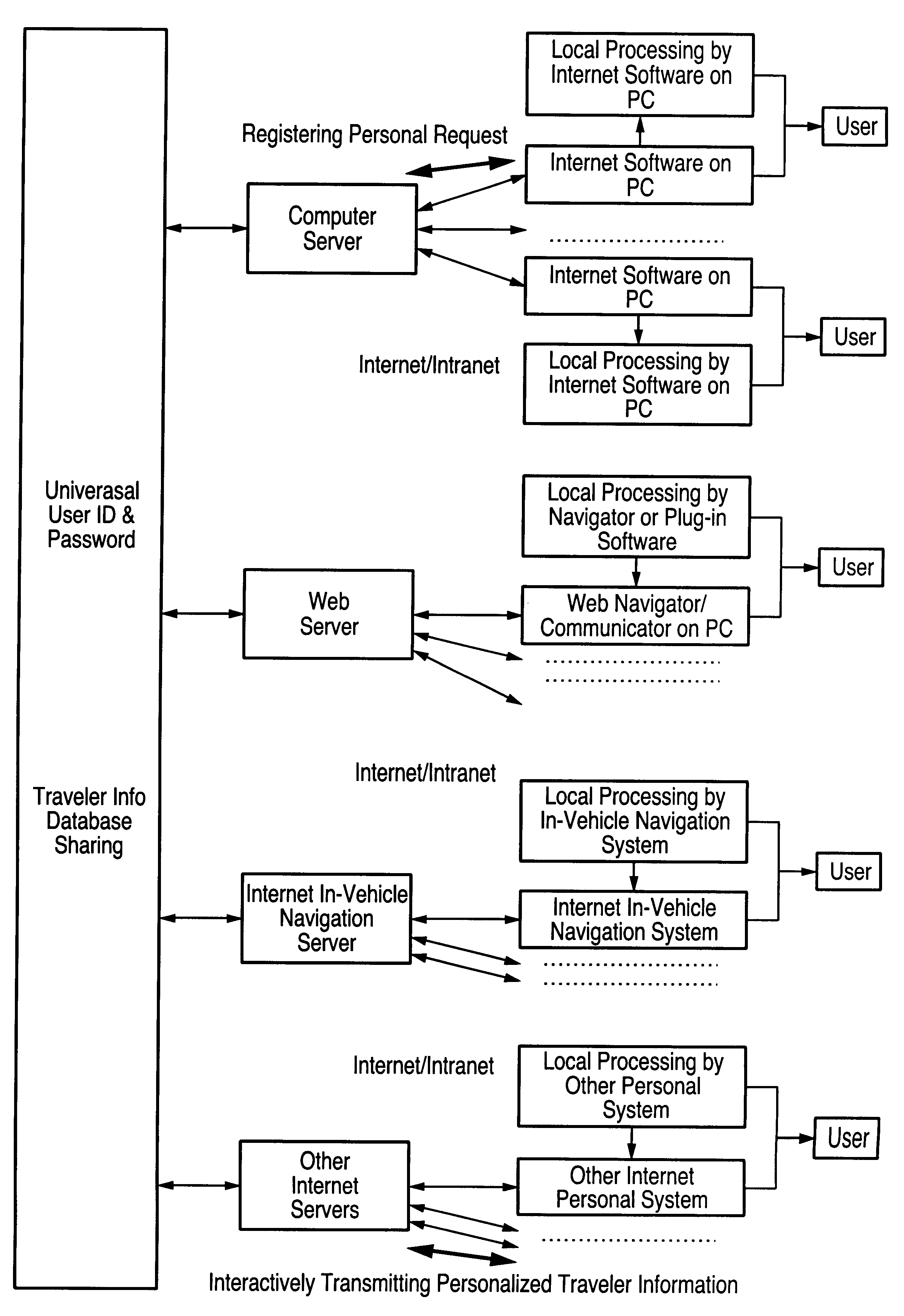
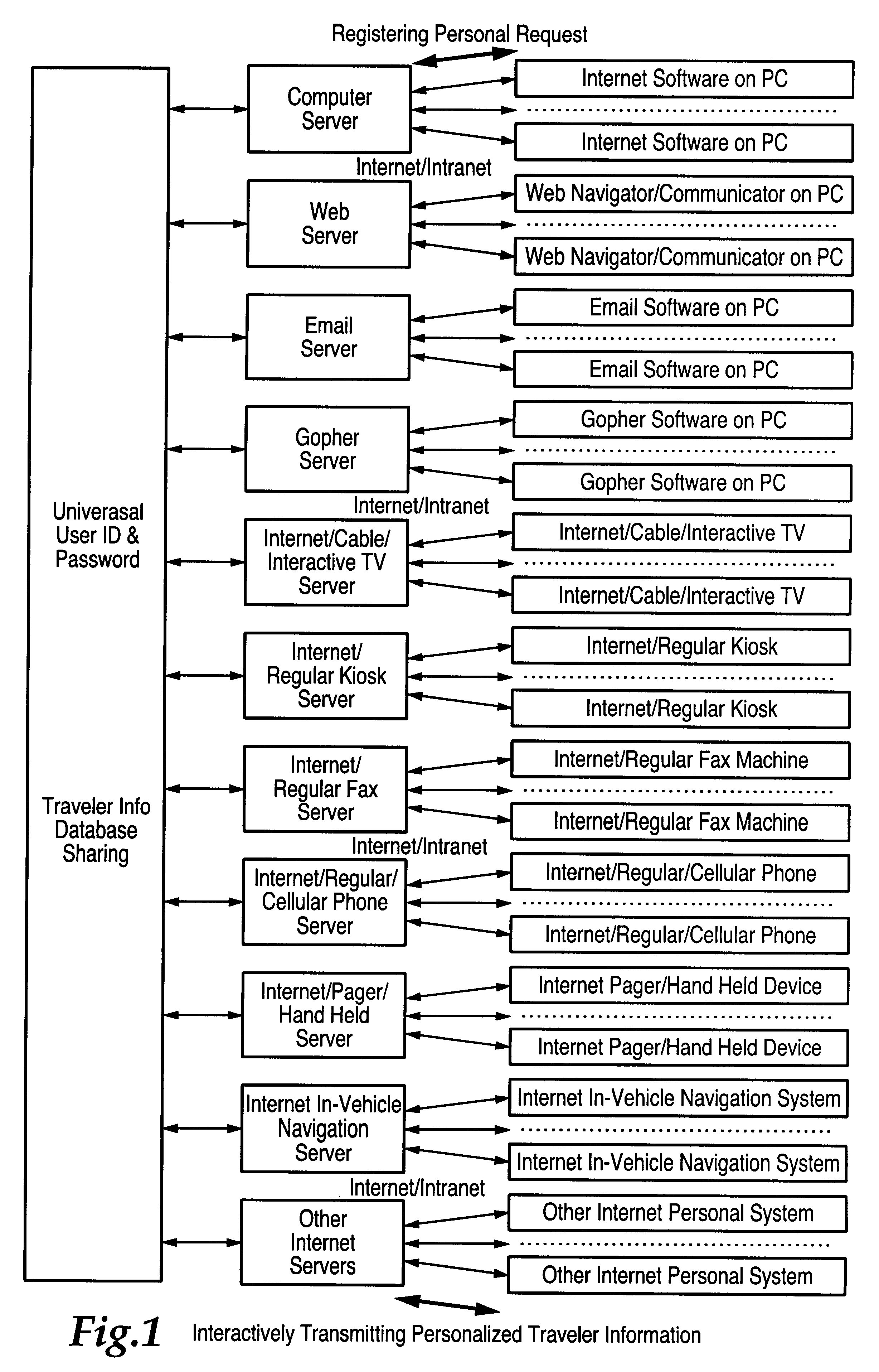
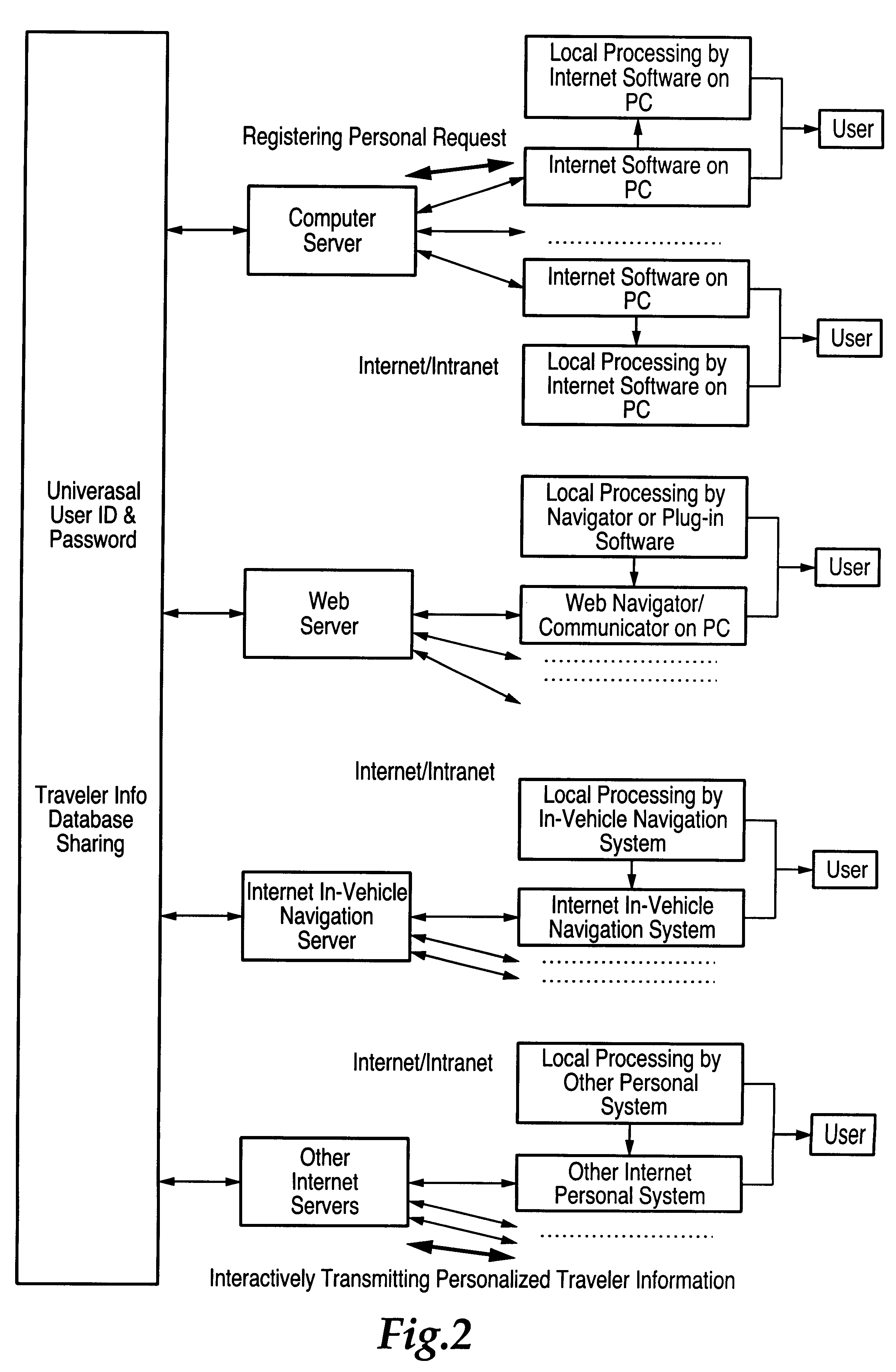
Central processing and combined central and local processing of personalized real-time traveler information over internet/intranet
InactiveUS6209026B1ForecastingMultiple digital computer combinationsUtility computingPersonalization
An Internet utility which receives information about a proposed trip, including trip origin, destination and time. The web based utility calculates at least one route and provides periodic automatic updates of information related to the route such as traffic and weather conditions. Other information which may be automatically periodically transmitted includes information about other transportation systems which may interface with a trip such as airline departure or arrival times. Specific information related to a trip or destination such as availability of parking at the destination also constitute the automatically transmitted information.
Owner:ITERIS INC
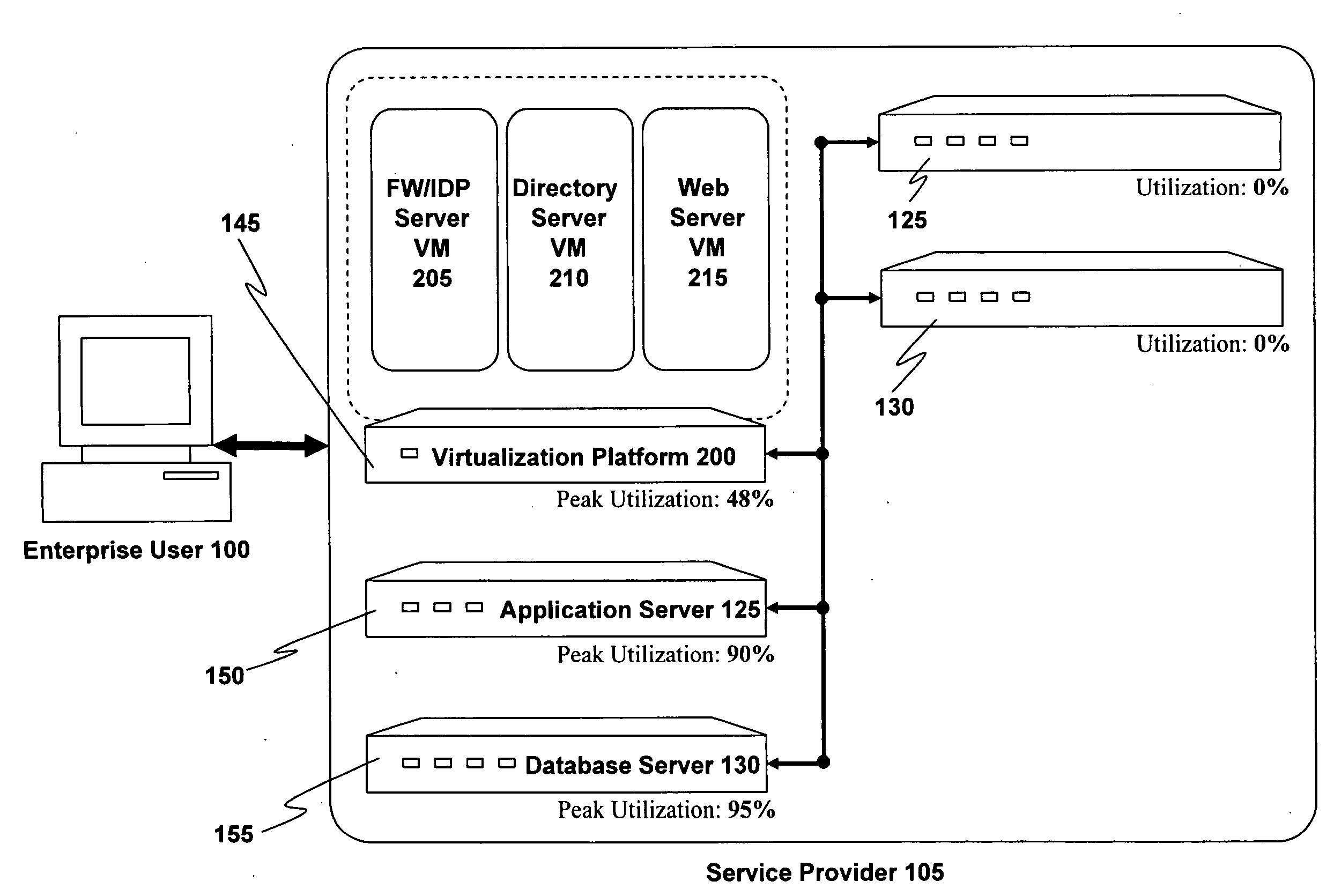
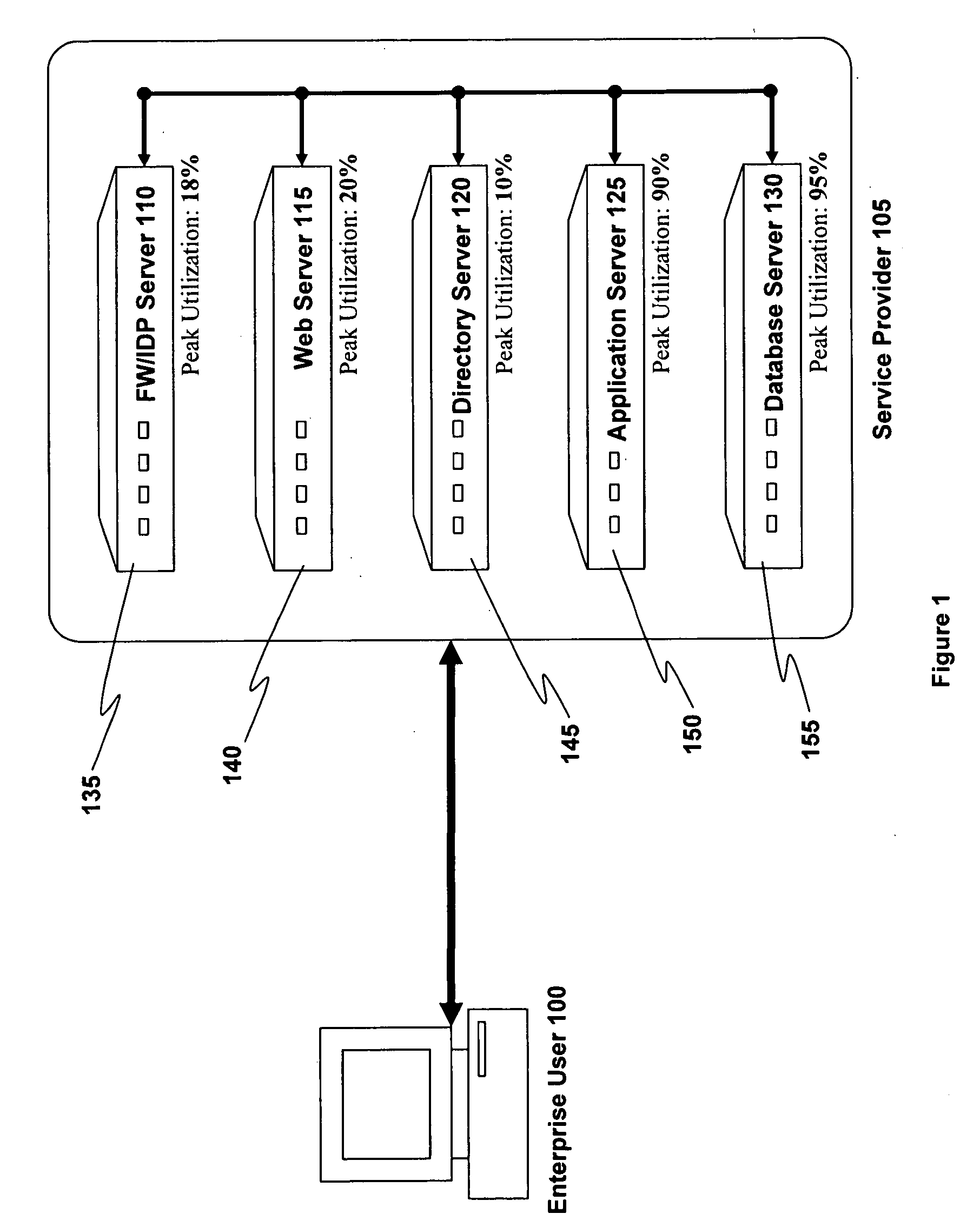
Virtual machine utility computing method and system
ActiveUS20100199285A1Realize automatic adjustmentComplete banking machinesResource allocationUtility computingResource utilization
An analytics engine receives real-time statistics from a set of virtual machines supporting a line of business (LOB) application. The statistics relate to computing resource utilization and are used by the analytics engine to generate a prediction of demand for the LOB application in order to dynamically control the provisioning of virtual machines to support the LOB application.
Owner:VMWARE INC
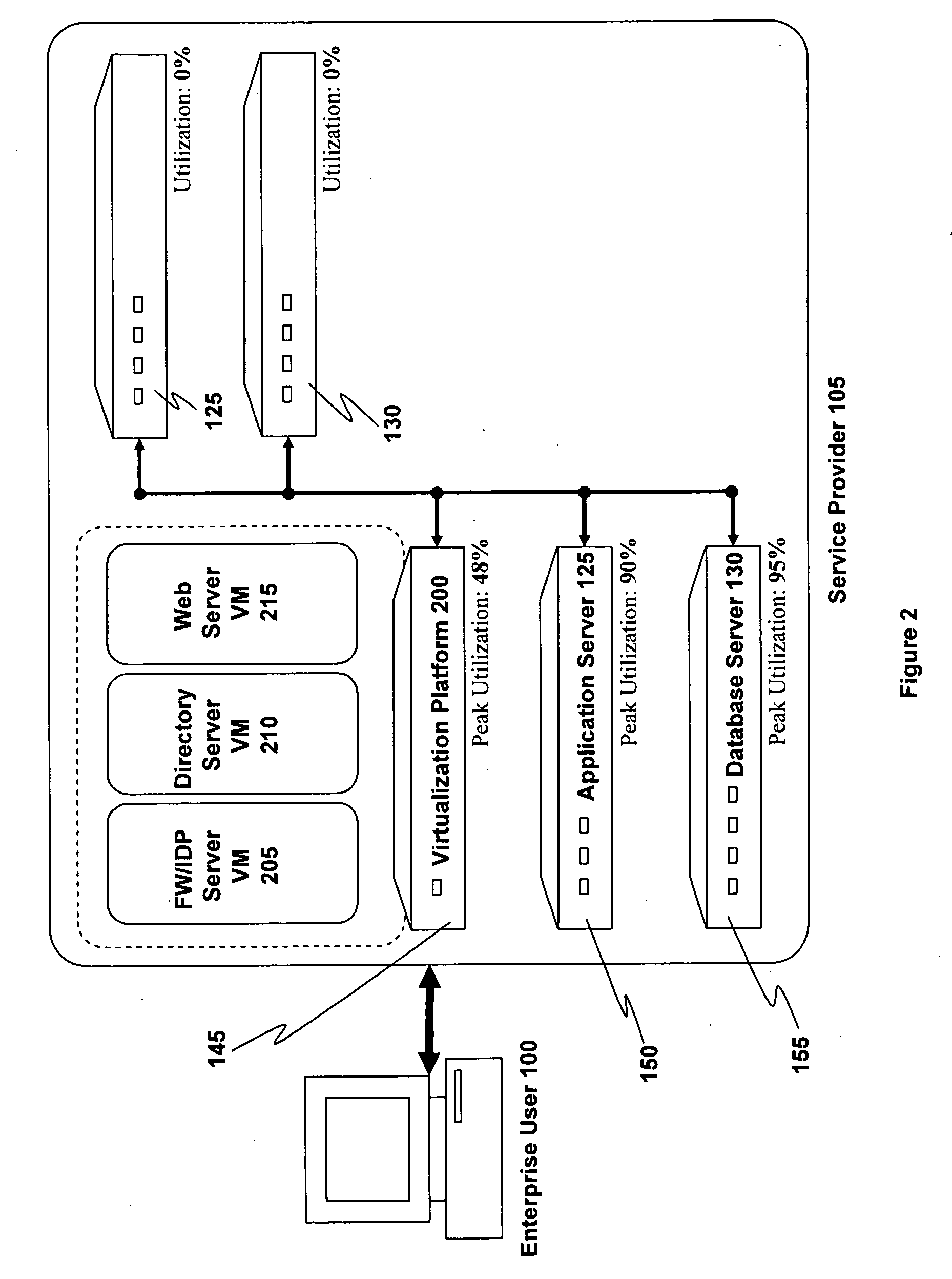
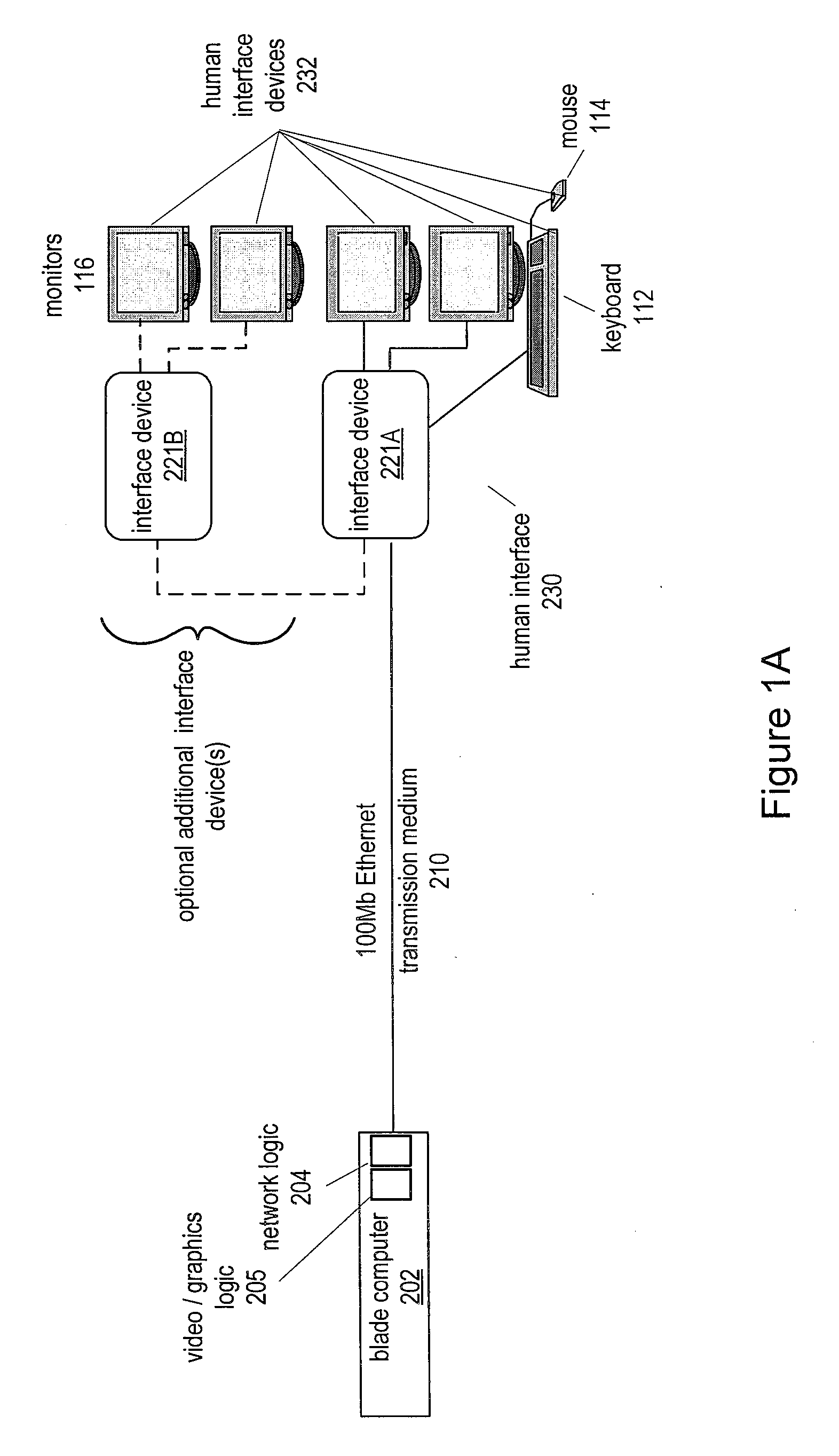
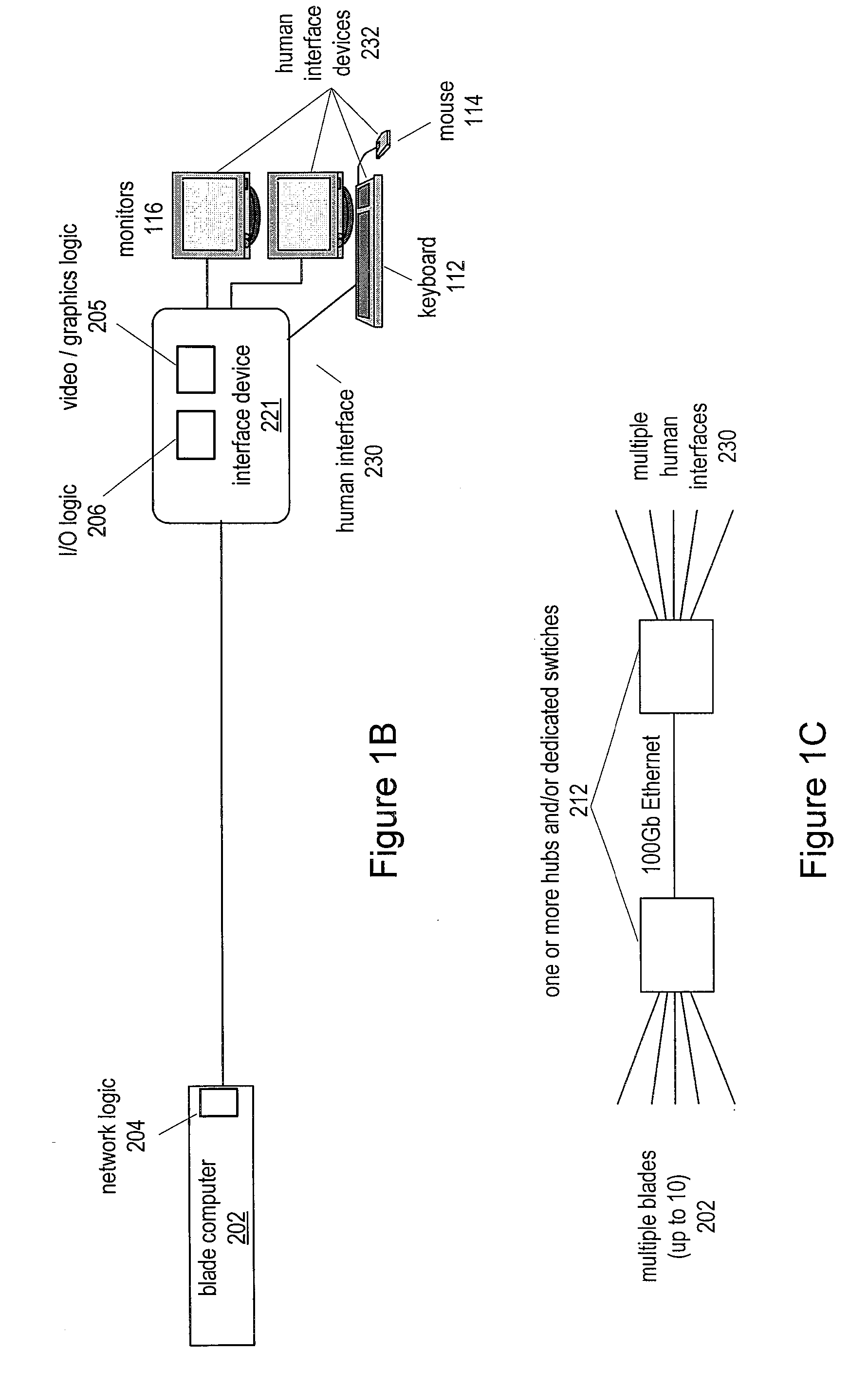
Utility Computing System Having Co-located Computer Systems for Provision of Computing Resources
System and method for providing computer resources to users. The system includes a plurality of co-located computing systems, e.g., blade computers, comprising a hierarchy of computer resources based on performance, and located at a first location, each computing system including a processor, a memory medium coupled to the processor, and a plurality of human interface systems, each located at a second location remote from the first location, and each including an interface device, and one or more human interface devices coupled to the interface device, where each human interface system is coupled to the co-located computing systems over a network, such as a LAN or a WAN, via the interface device. Computer resources are provided to users of the plurality of remote human interface systems over the network in accordance with the computer resource performance needs of the users. Charges may be assessed for usage of the computer resources.
Owner:CLEARCUBE TECHNOLOGY INC
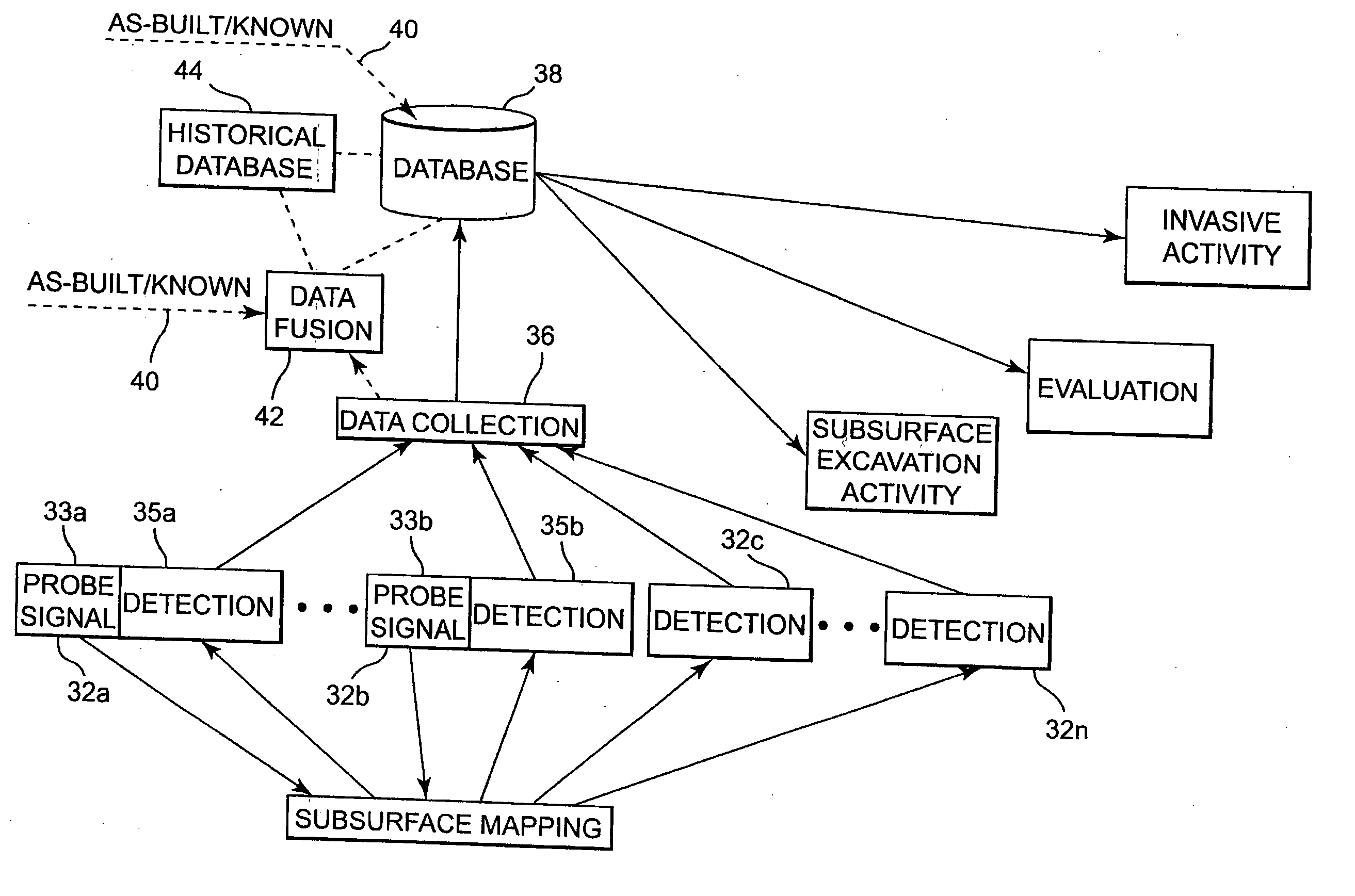
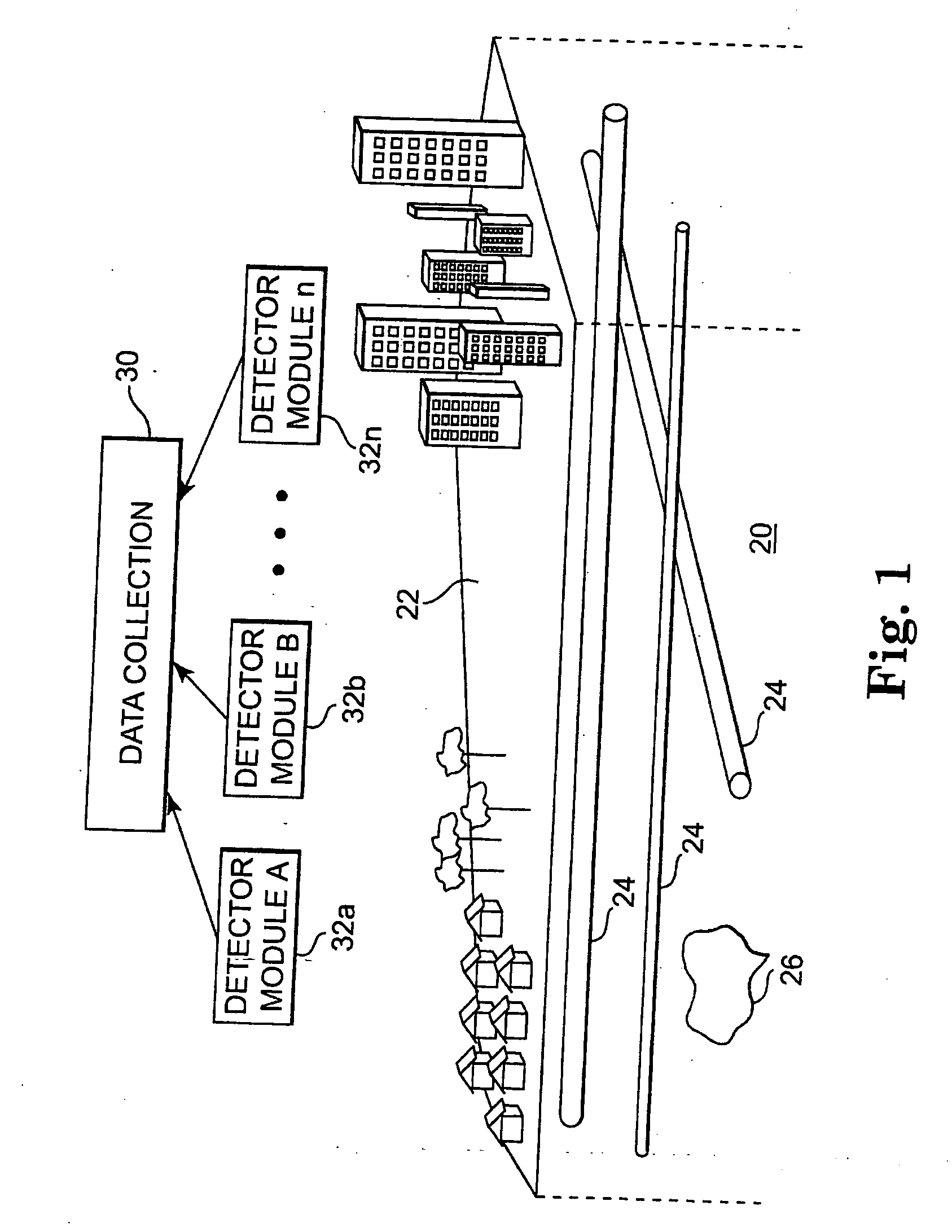
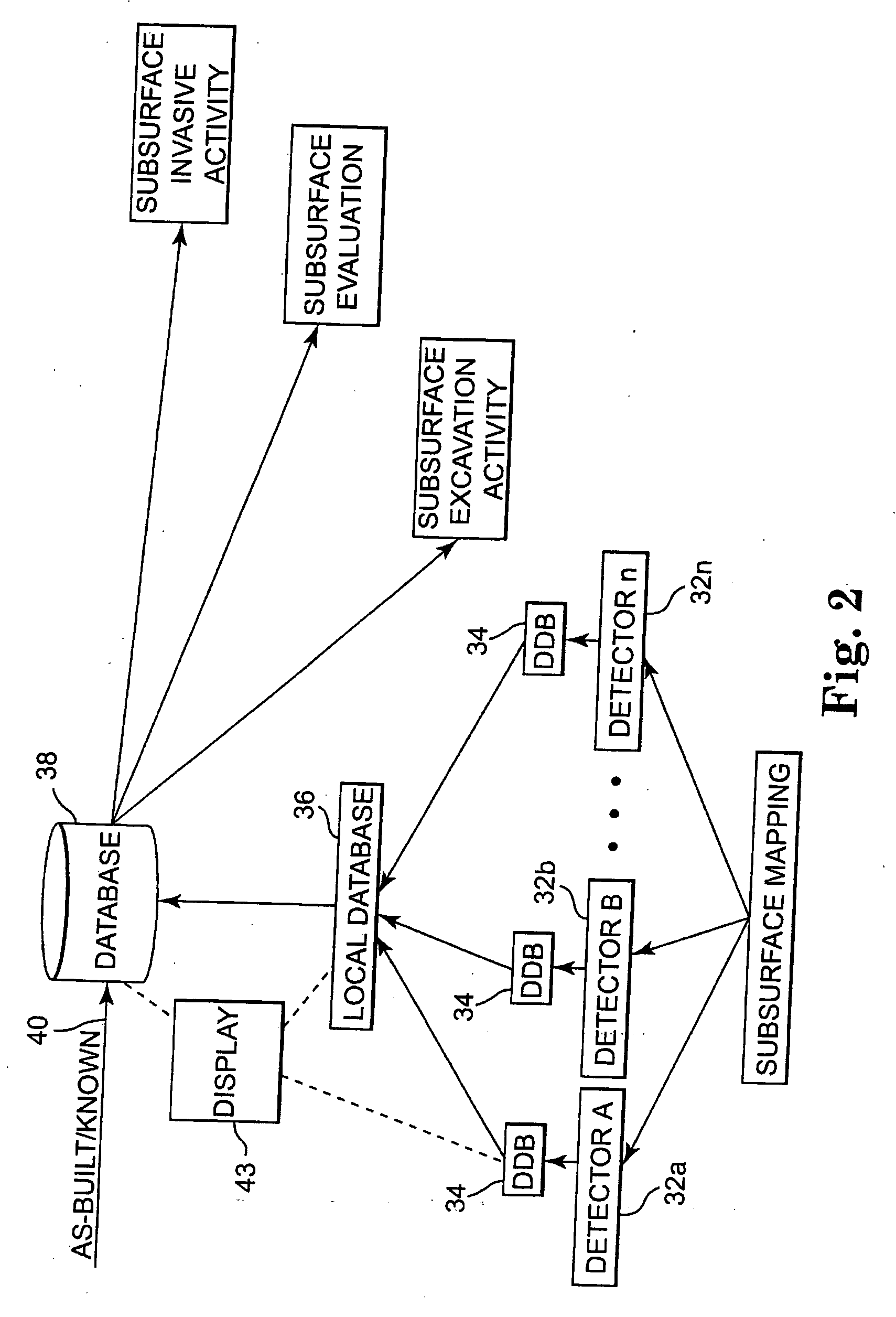
Utility mapping and data distribution system and method
InactiveUS20060085133A1Improve accuracySeismologySpecial data processing applicationsUtility computingDistribution system
A system and method of mapping underground utilities and other subsurface objects involves one or more of acquiring utility location data using a number of different detectors and sensors, processing the multiple detector / sensor output data to produce mapping data, storing the mapping data in a database, and providing access to and use of the stored mapping data by subscribing users on a usage fee basis.
Owner:VERMEER MFG CO
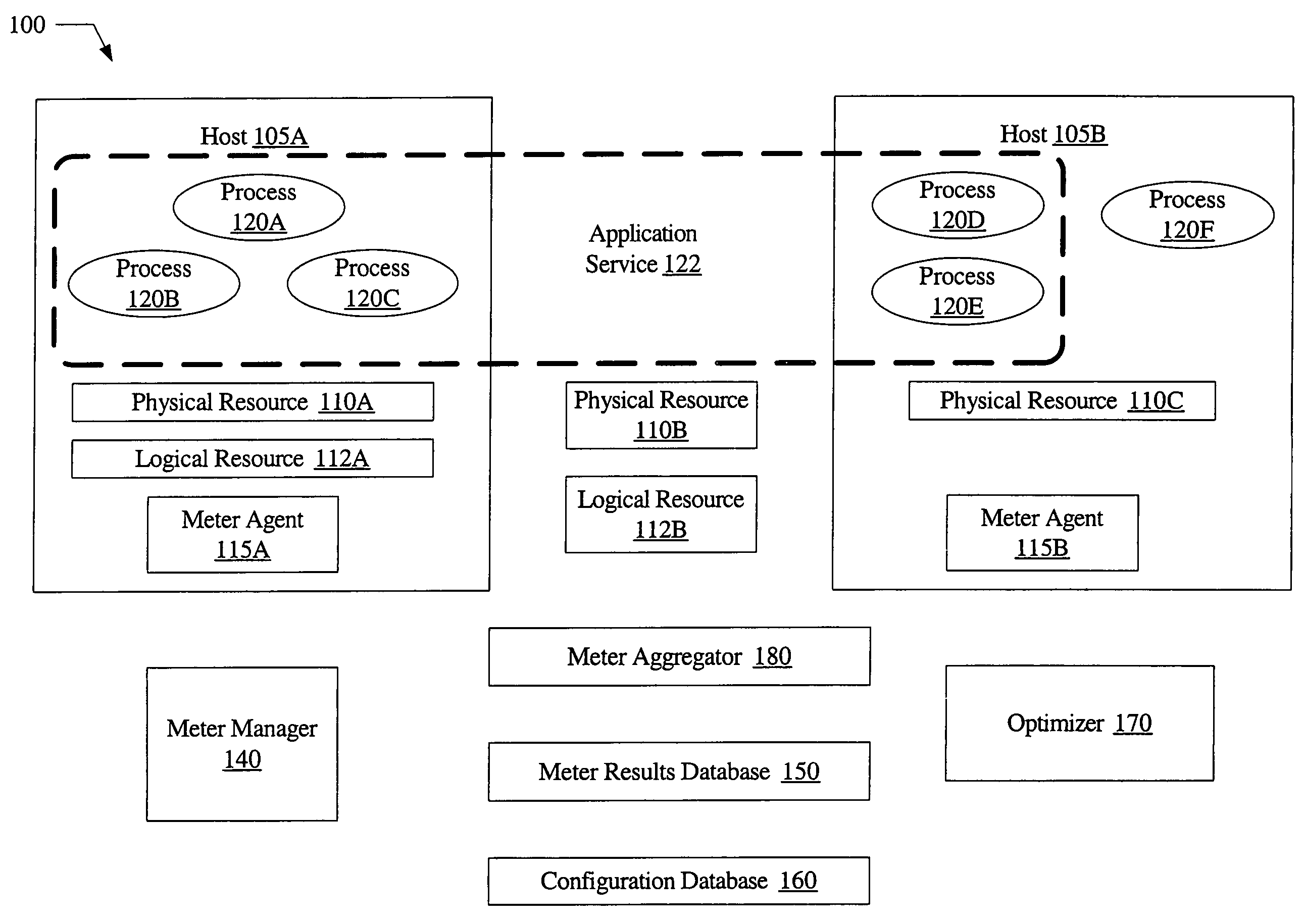
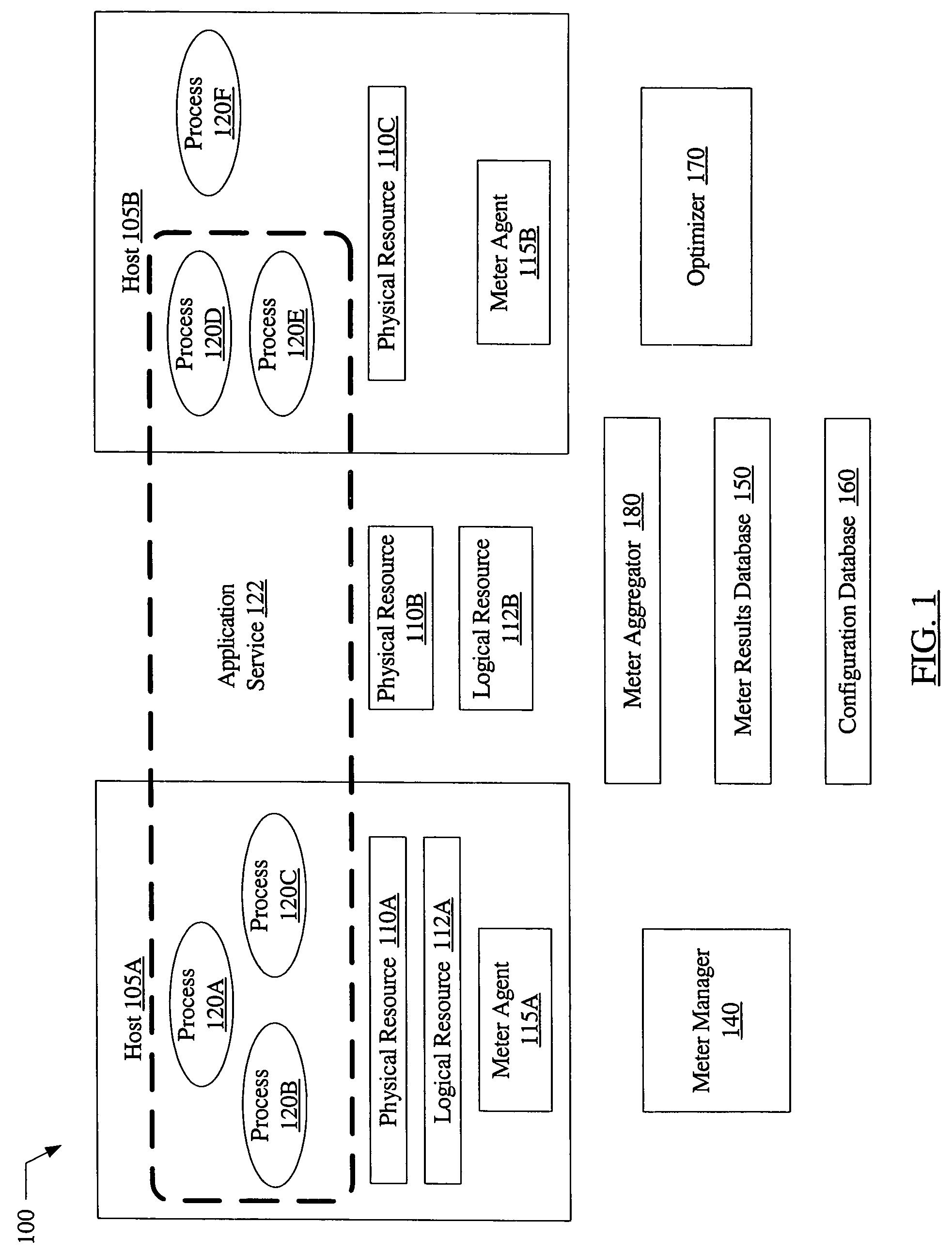
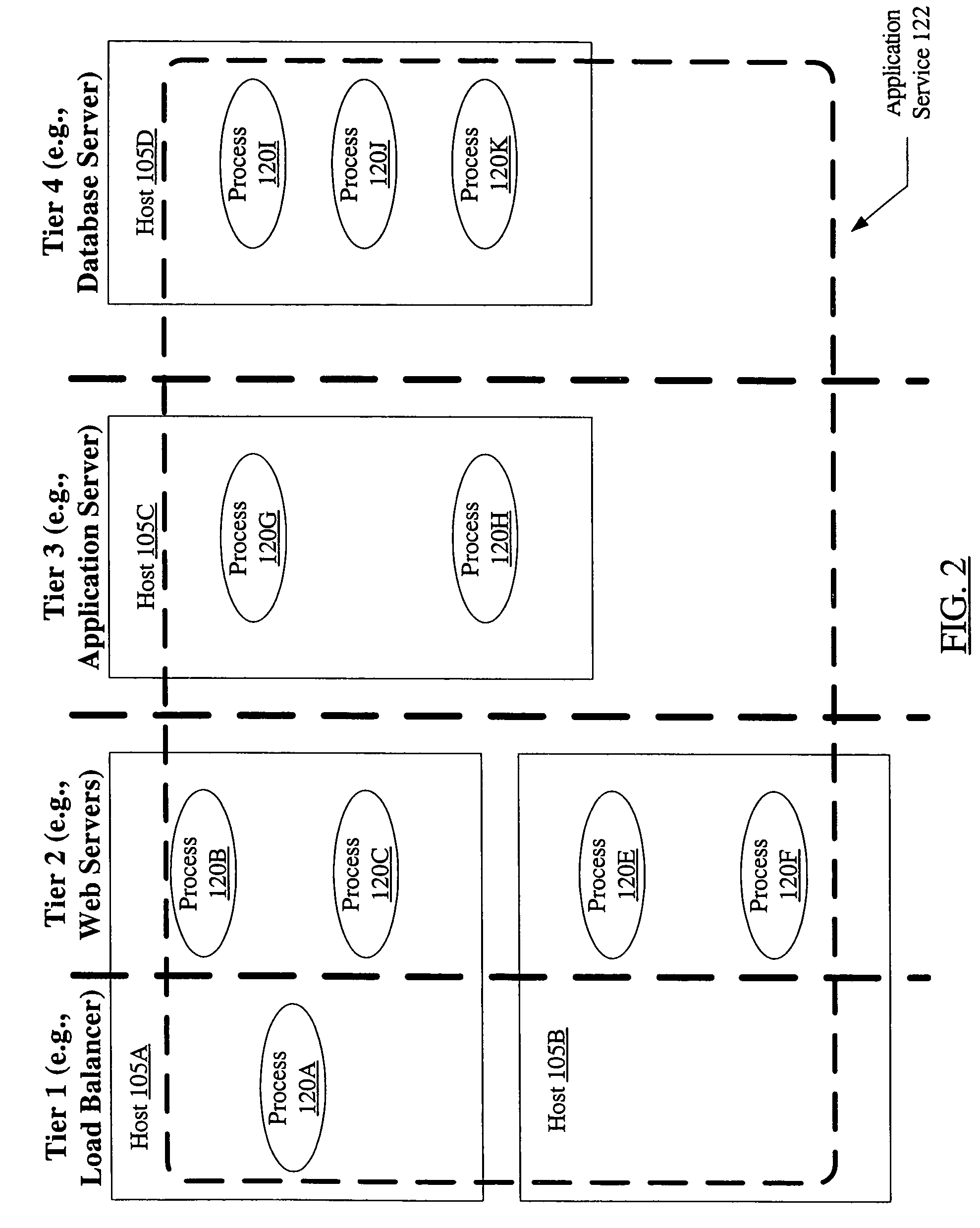
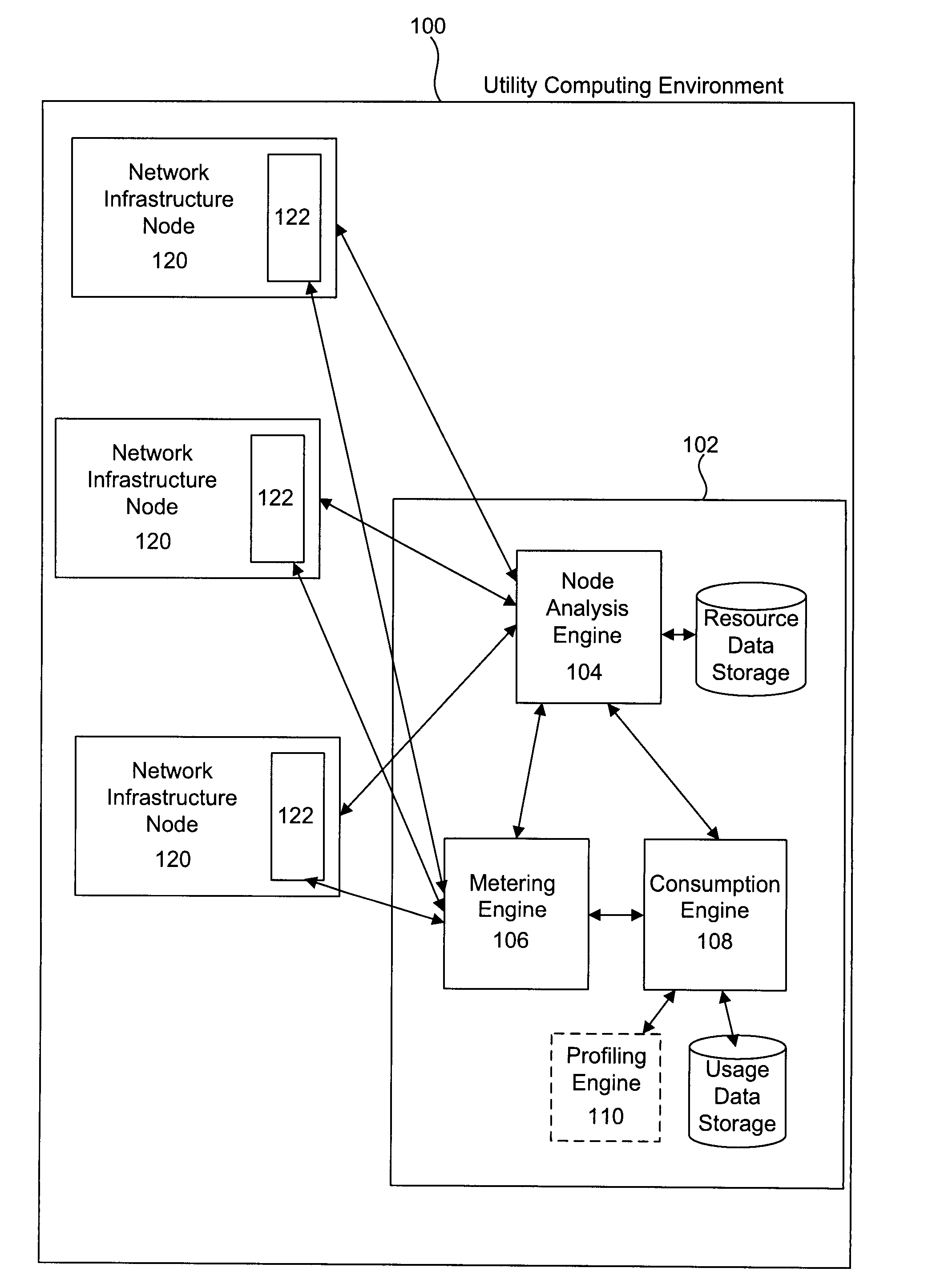
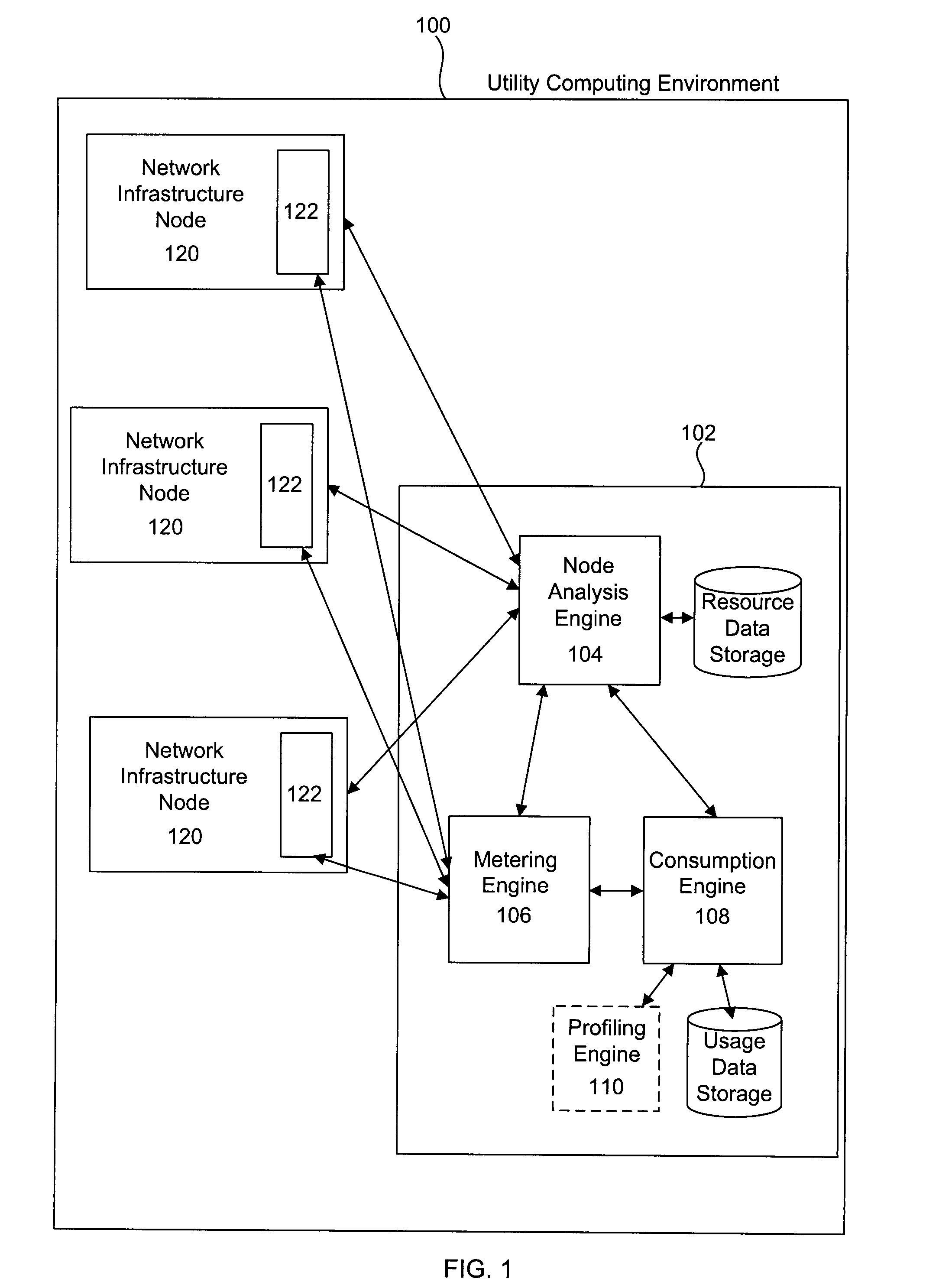
System and method for metering of application services in utility computing environments
A system for metering of application services in utility computing environments includes one or more meter agents and a meter aggregator. A meter agent may be configured to periodically collect usage data corresponding to one or more resources, and provide the usage data to the meter aggregator. The meter aggregator may be configured to aggregate the usage data associated with an application service, where the application service includes a plurality of application processes. In addition, the meter aggregator may be configured to compute a billing amount based on an aggregate resource usage by the application service over a specified time period.
Owner:SYMANTEC OPERATING CORP
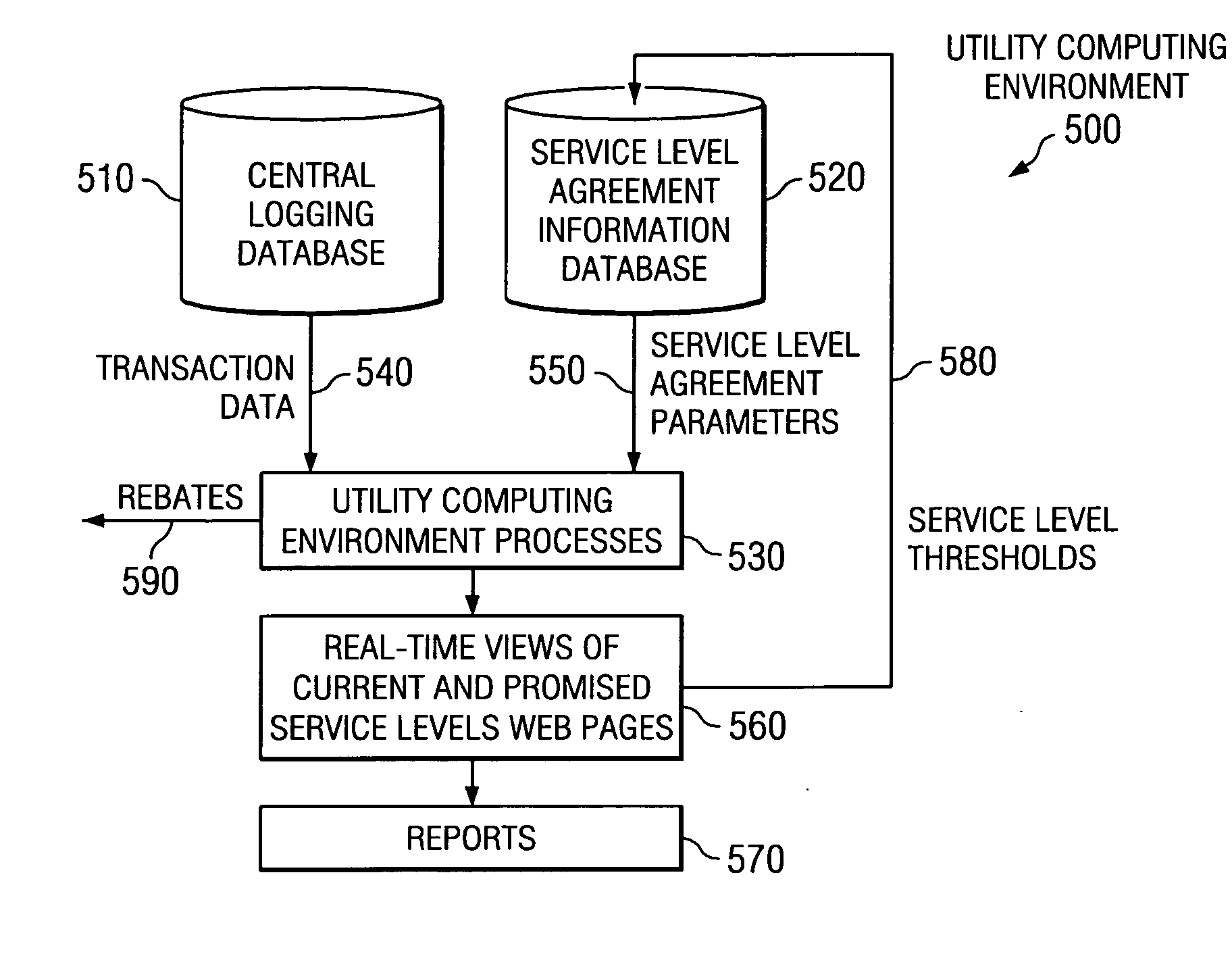
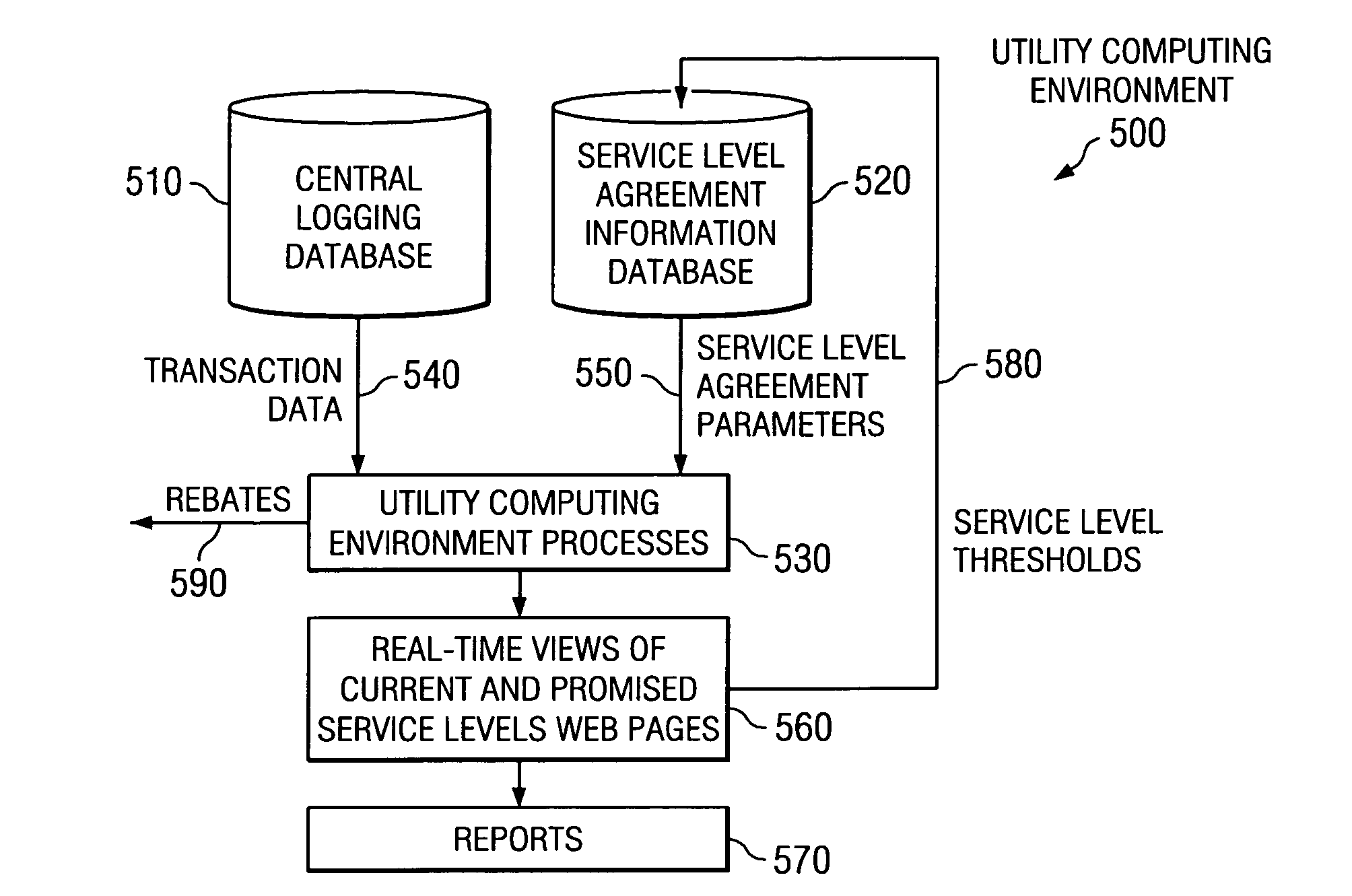
Method of displaying real-time service level performance, breach, and guaranteed uniformity with automatic alerts and proactive rebating for utility computing environment
InactiveUS20050066026A1Eliminate the potential discrepancyMetering/charging/biilling arrangementsMultiple digital computer combinationsUtility computingService-level agreement
The present invention provides a method, apparatus, and computer program product for displaying real-time service level performance, breach, and guaranteed uniformity with automatic alerts and proactive rebating for a utility computing environment. Service level agreement parameters, based on a service level agreement between a customer and a service provider, are used to identify discrepancies in a promised service level for the utility computing environment. A real-time view of a current service level and the promised service level for the customer are displayed. When a discrepancy between the promised service level and the current service level occurs, a rebate is generated for the customer. Alerts identifying the discrepancy and its root cause are provided to the customer and the service provider for the discrepancy. Alerts may also be provided prior to the occurrence of the discrepancy so that an action may be performed to eliminate the potential discrepancy.
Owner:IBM CORP
Virtual machine utility computing method and system
ActiveUS8336049B2Realize automatic adjustmentComplete banking machinesDigital computer detailsUtility computingResource utilization
An analytics engine receives real-time statistics from a set of virtual machines supporting a line of business (LOB) application. The statistics relate to computing resource utilization and are used by the analytics engine to generate a prediction of demand for the LOB application in order to dynamically control the provisioning of virtual machines to support the LOB application.
Owner:VMWARE INC
Customer supported automatic meter reading method
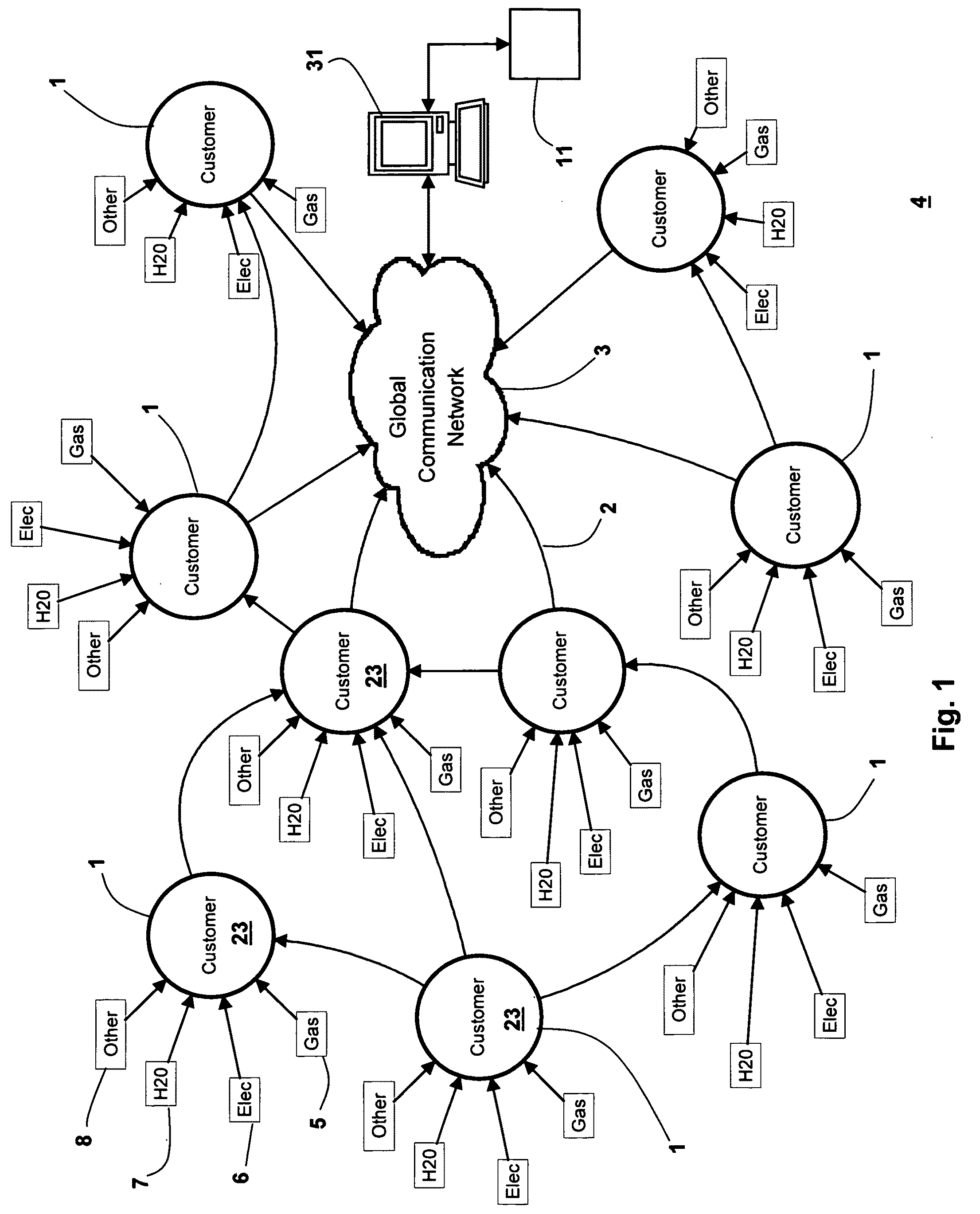
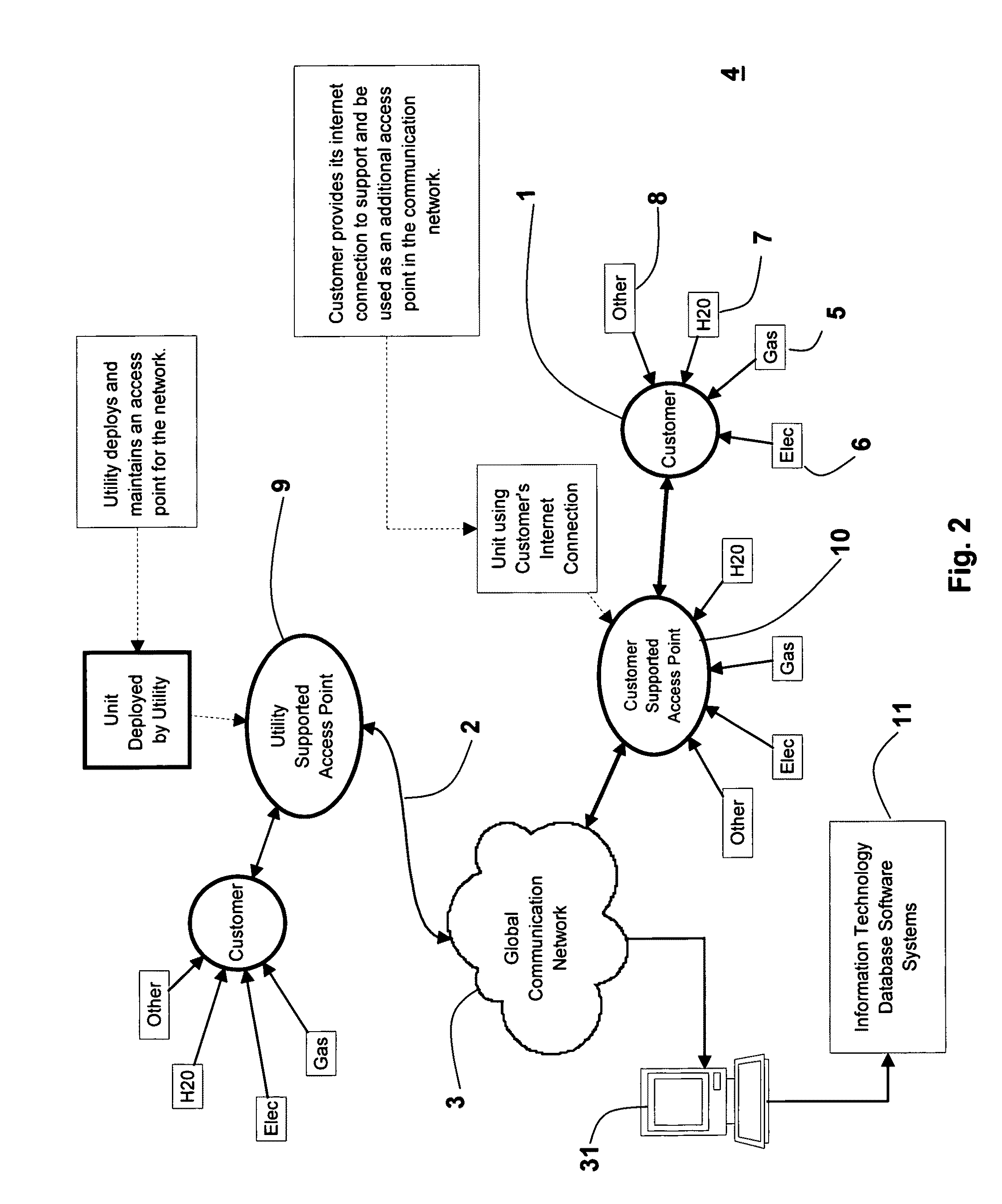
InactiveUS20090267792A1Reduce operating costsMuch-reduced capital costElectric signal transmission systemsTariff metering apparatusUtility computingDistribution system
A method is described in which an automatic metering reading (AMR) method is implemented in the utility distribution system. The AMR method comprises a mesh network in which selected customers of the utility company support the network by providing collocated internet access points via the customer's existing internet connections; thus providing AMR data “backhaul”, thereby minimizing the need for the utility to build and deploy all the access points needed to populate the mesh infrastructure network. This customer access point for which the customer is remunerated, in whole or in part by the utility, allows the utility to develop and implement all the network elements to meet the utility AMR needs at a much lower cost. The customer-supported method can allow the utility to efficiently and effectively service its metering needs via the global communications network without a major investment in hardware, software and personnel.
Owner:CRICHLOW HENRY
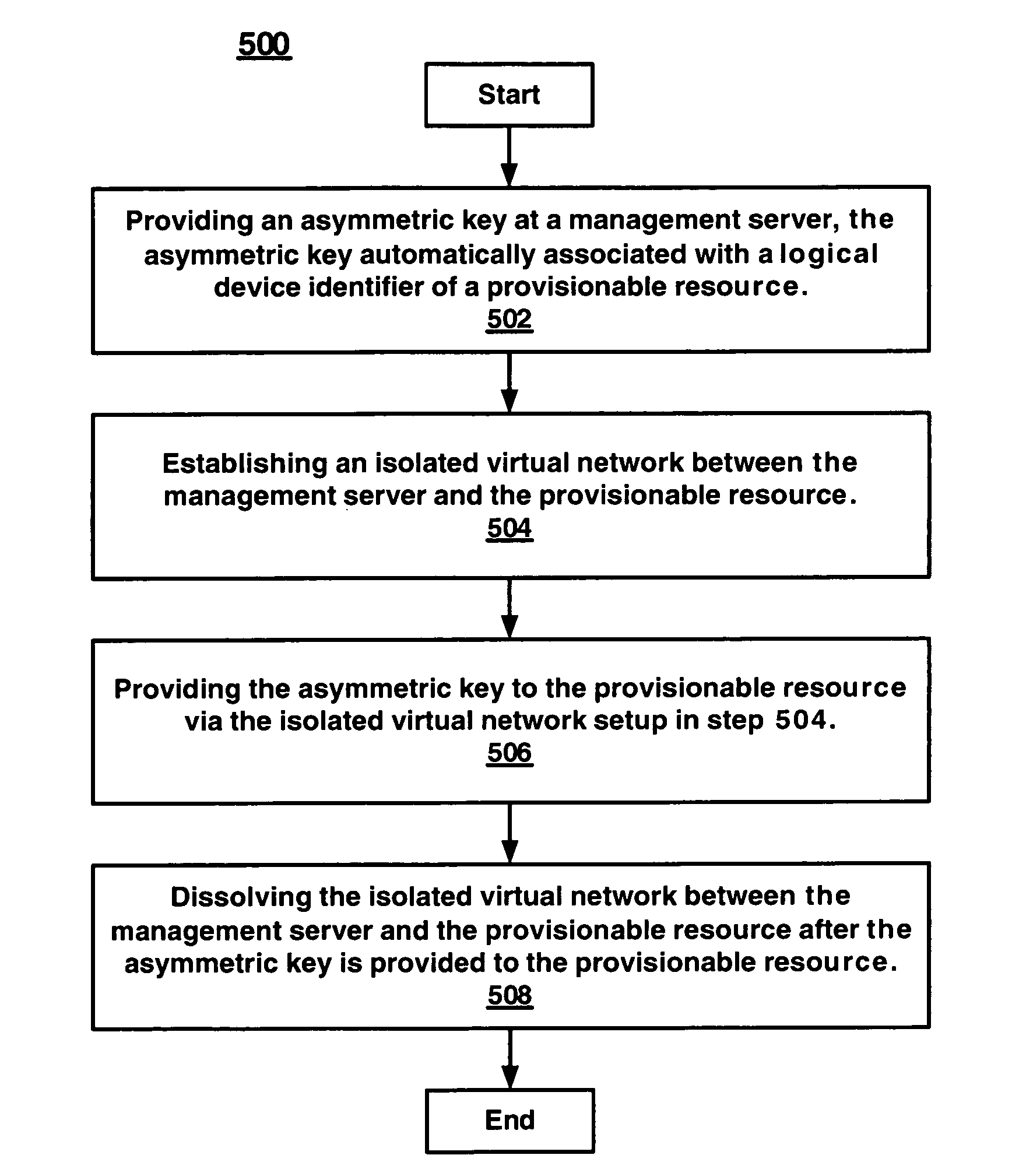
Method and apparatus for automatic and secure distribution of an asymmetric key security credential in a utility computing environment
ActiveUS20070098178A1Key distribution for secure communicationDigital data processing detailsUtility computingDevice Identifiers
Embodiments of the invention provide a method and an apparatus for automatic, secure, and confidential distribution of an asymmetric key security credential in a utility computing environment. In one method embodiment, the present invention provides an asymmetric key at a management server, the asymmetric key automatically associated with a logical device identifier of a provisionable resource. Additionally, an isolated virtual network is established between the management server and the provisionable resource for providing the asymmetric key to the provisionable resource. Then, after the asymmetric key is provided to the provisionable resource the isolated virtual network between the management server and the provisionable resource is dissolved.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
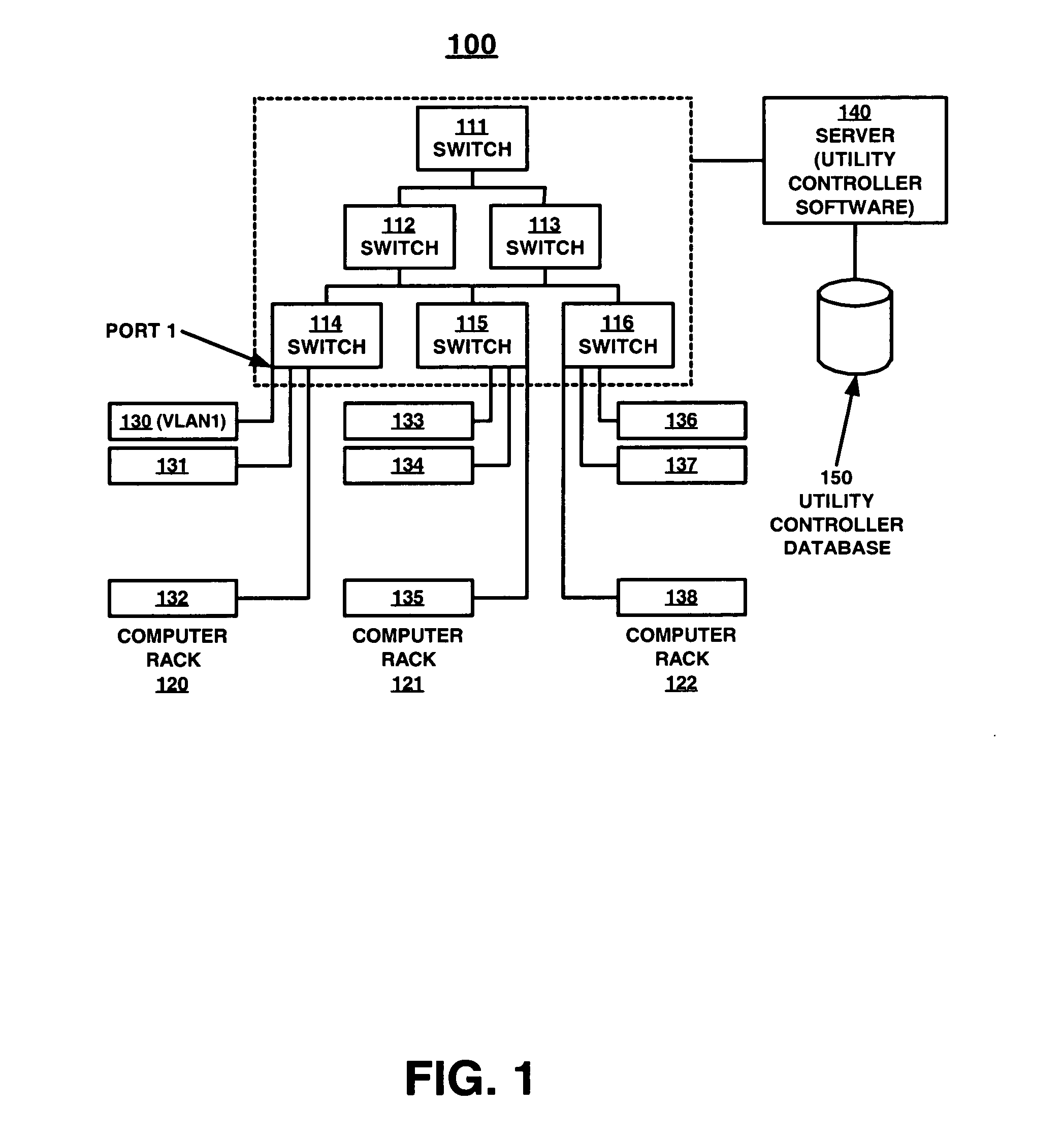
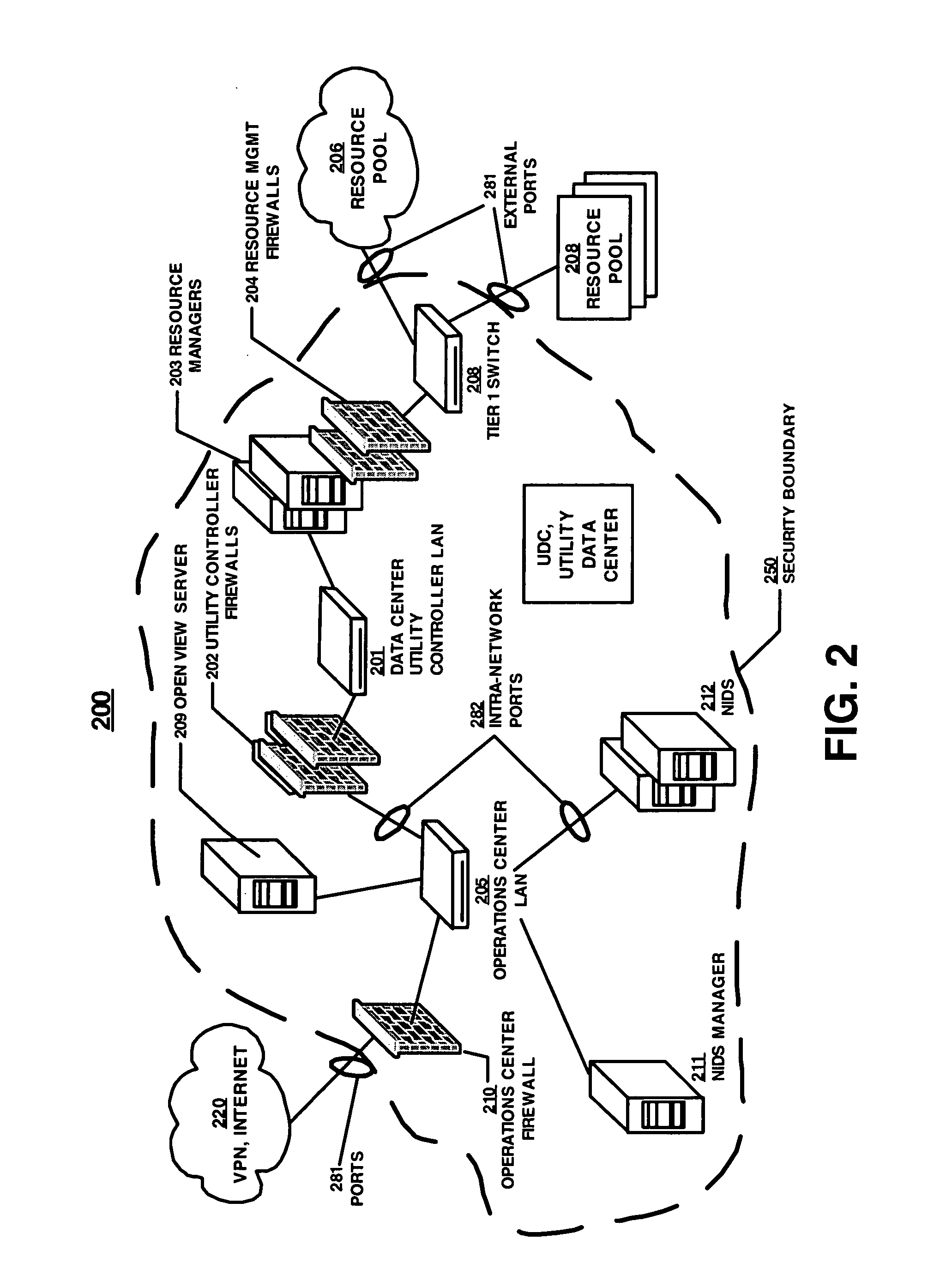
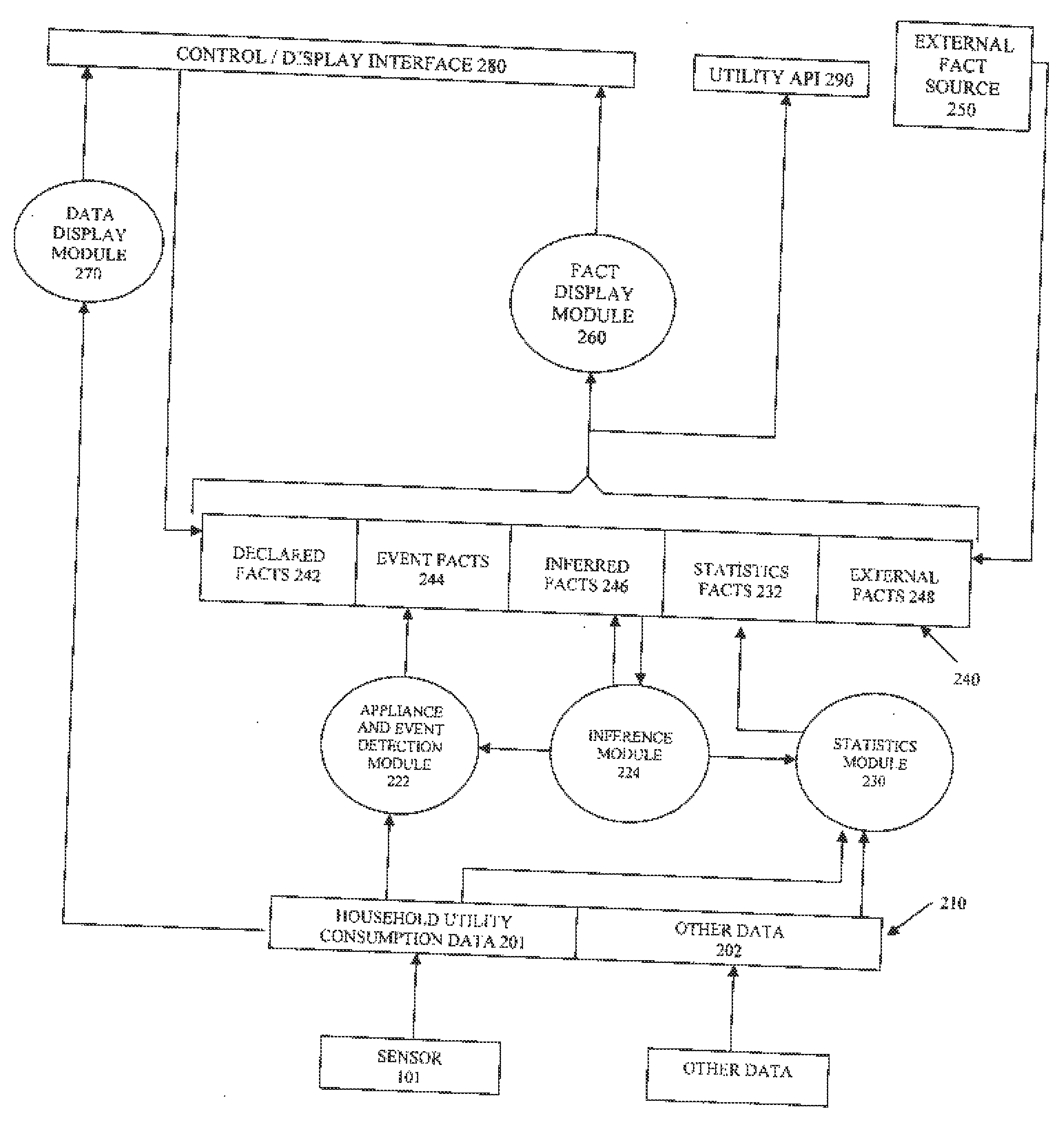
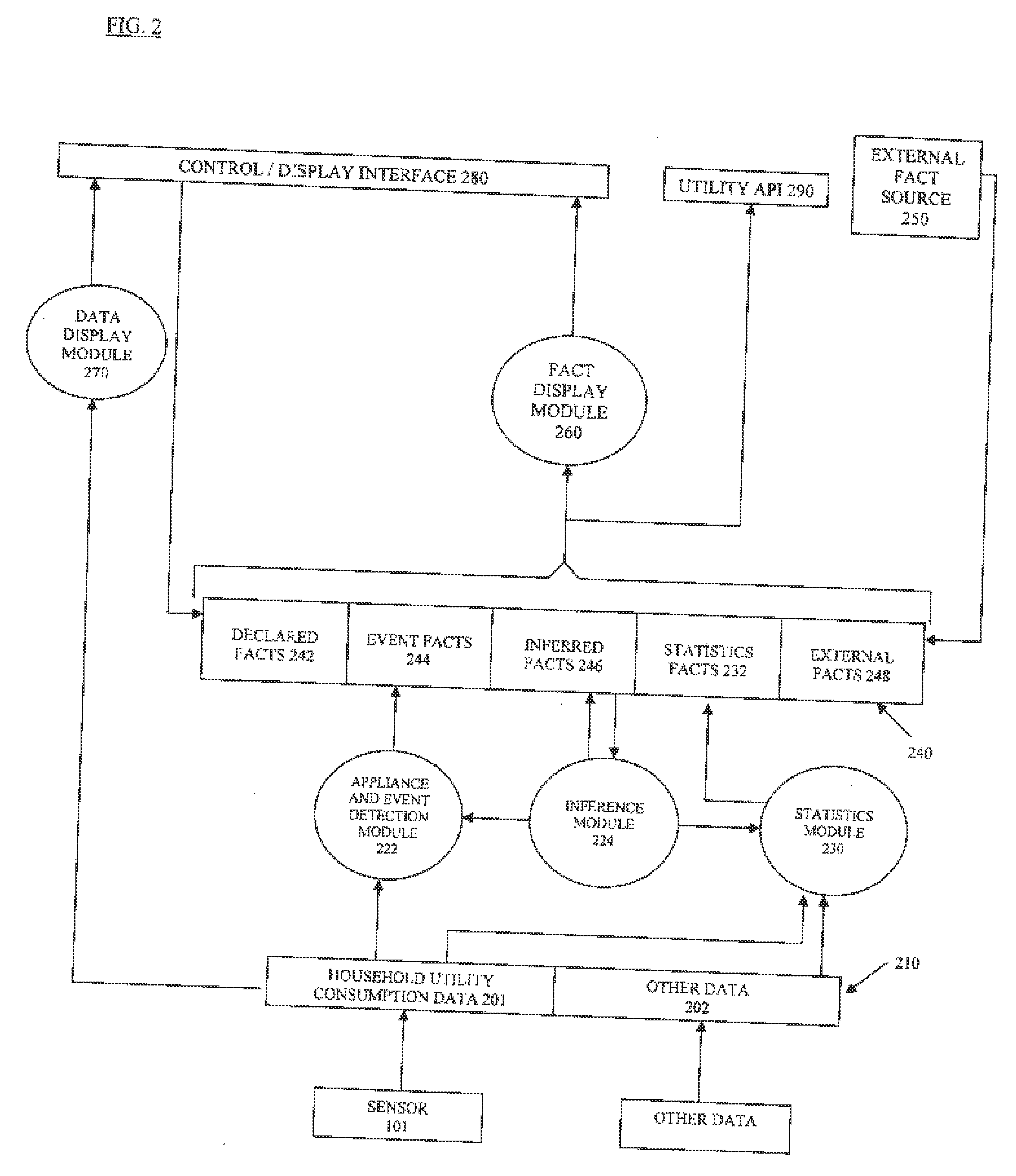
Utility data processing system
ActiveUS20110313964A1Tariff metering apparatusPower network operation systems integrationData processing systemUtility computing
A utility data processing system for processing data relating to consumption of a utility comprises: a fact memory for storage of facts relating to utility consumption received from fact sources, at least one fact source module for deriving facts from utility consumption data and adding the derived facts to the tact memory, an inference module for inferring new facts relating to utility consumption from one or more facts stored in the fact memory, and an interlace module.
Owner:ONZO
System and method for managing utility consumption
ActiveUS7349765B2Reducing peak demandMechanical power/torque controlLevel controlUtility computingUtility industry
A system, method, and apparatus are disclosed for managing utility consumption. An embodiment is disclosed for reducing peak demand for a utility by staggering requests for that utility. Another embodiment is disclosed in which sensors monitor utility consumption throughout a facility. Those items of equipment not in active use, but still drawing utility resources, are shut down after a predetermined interval. Another embodiment is disclosed in which storage and conversion technologies are used to offset peak demand and the associated peak demand costs.
Owner:GM GLOBAL TECH OPERATIONS LLC
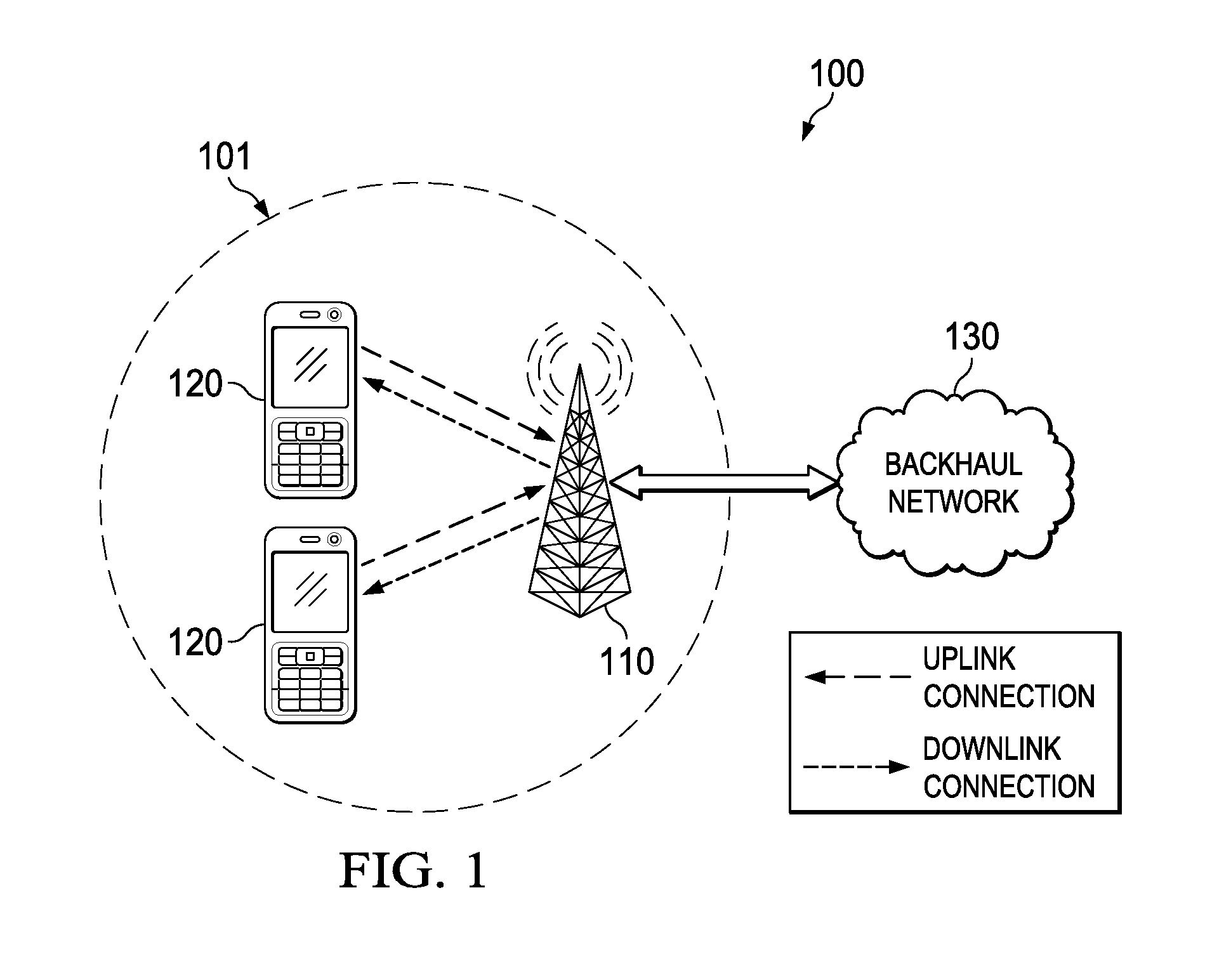
Method and apparatus for utility computing in ad-hoc and configured peer-to-peer networks
ActiveUS7716286B2Multiple digital computer combinationsOffice automationProgramming languageUtility computing
Owner:ZEROTOUCHDIGITAL
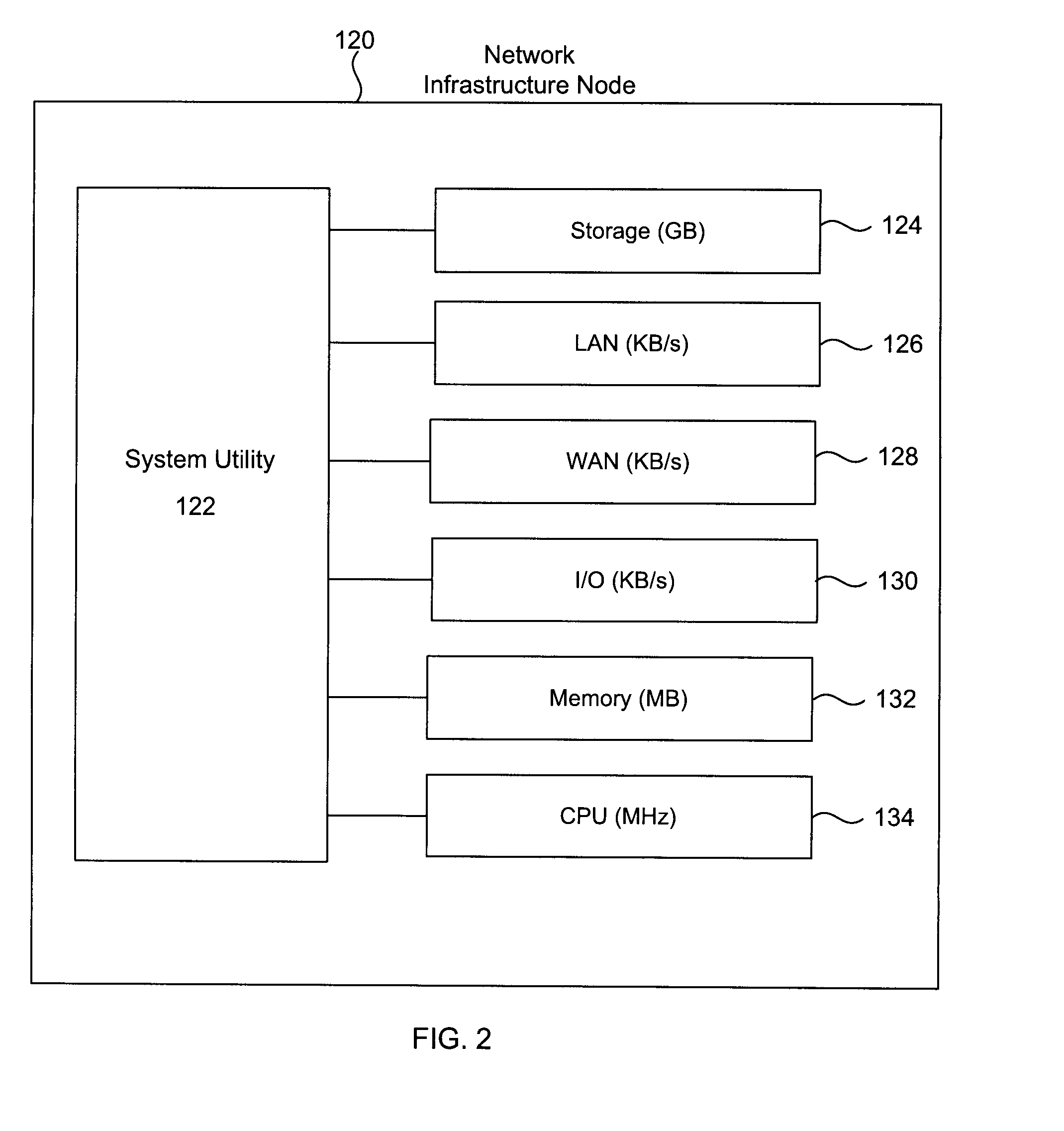
Method and System for Determining Computer Resource Usage in Utility Computing
ActiveUS20110219118A1Error detection/correctionMultiple digital computer combinationsComputer resourcesOccupancy rate
A universal platform for utility computing that allows service providers to charge clients for the services rendered according to a dimensionless cross-platform universal metric. The platform measures or monitors six metrics commonly used in software computing (MHz for CPU usage, Mbytes for memory usage, Kbytes / sec for I / O, Kbytes / sec for LAN, Kbits / sec for WAN and Gbytes for storage) and applies appropriate weighting and conversion factors to each consumption value to a value in the universal metric that can be applied agnostically to any system or application. The metric can also take other controllable variables into account, such as real estate cost, tax jurisdiction and electrical power. The metric effectively a metric makes diverse computing resources comparable. The total value of the resources consumed by a user determines the cost charged for the use of the computing services.
Owner:6FUSION USA INC
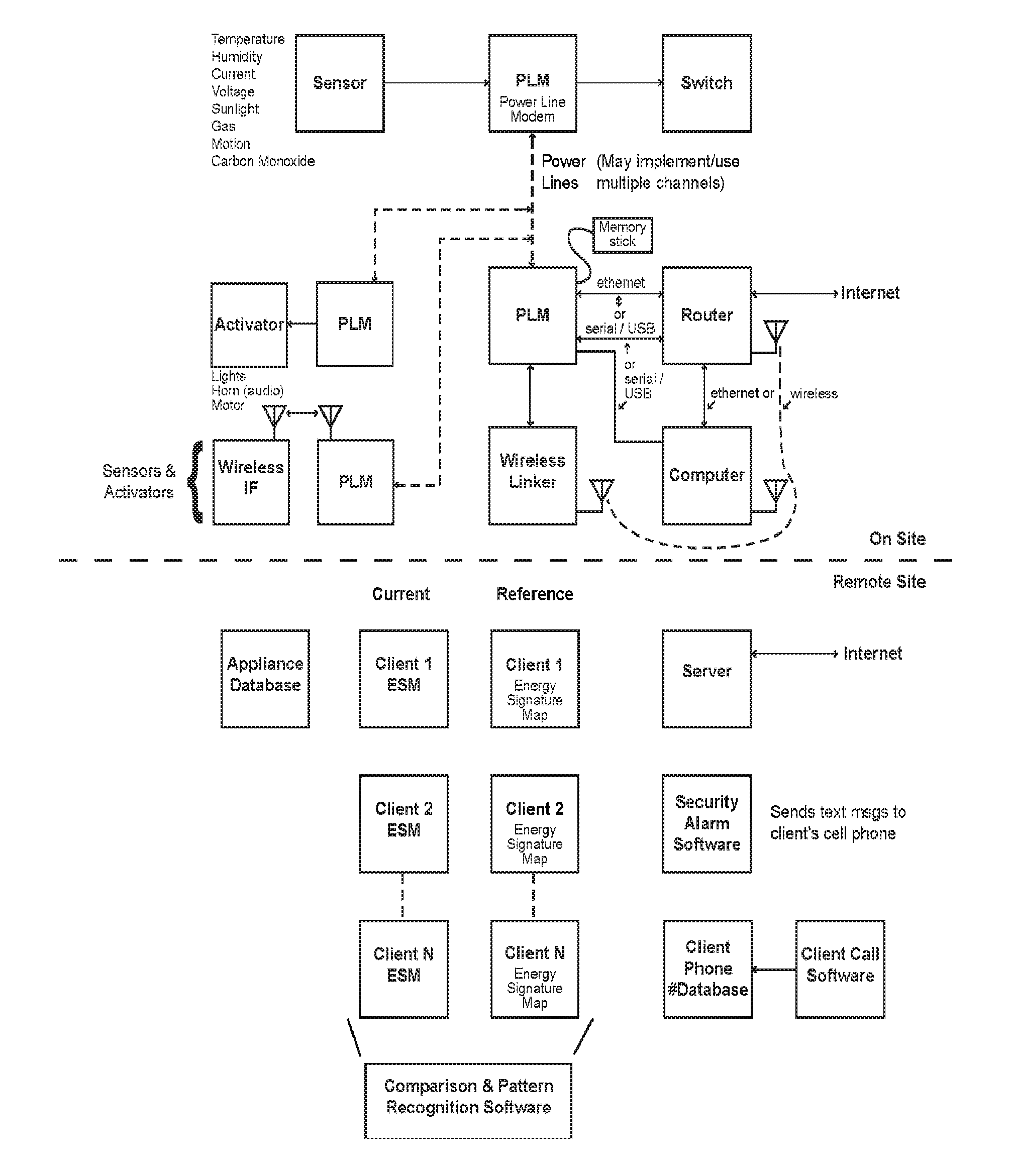
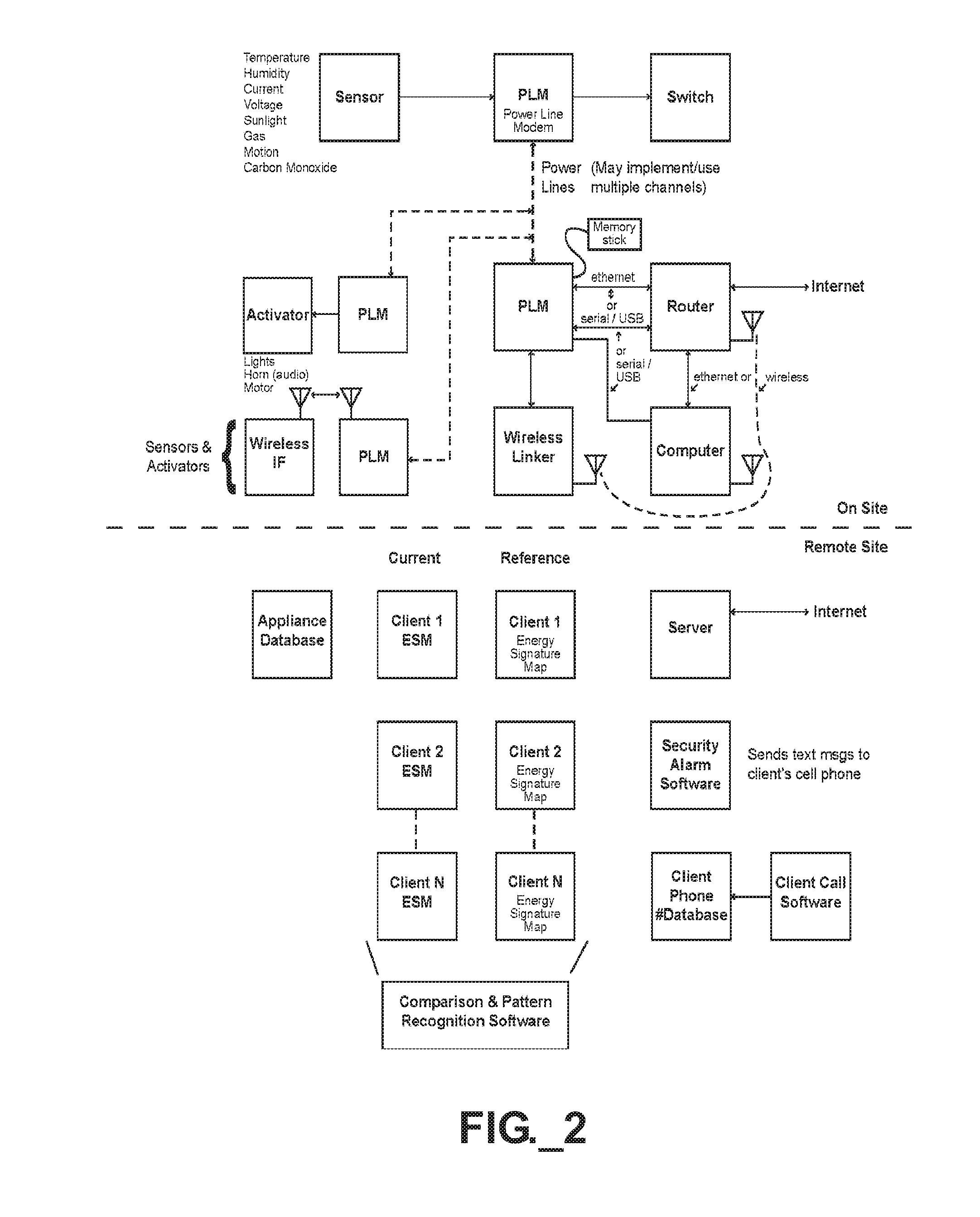
Systems and methods for managing utility consumption
A system and method for monitoring and managing utility consumption includes use of (A) one or more sensors arranged to monitor an operating condition and / or utility consumption of at least one segment or appliance of a first facility; (B) a memory including at least one of (i) stored utility consumption information correlated or normalized to at least one designated parameter affecting utility consumption or (ii) hypothetical utility consumption; (C) a processor to compare the monitored information with the stored information, and (D) an output medium to store and / or display the comparison information. Stored consumption information may relate to the first facility or a second facility. Hypothetical utility consumption information may relate to a segment or appliance of the first facility operated according to optimized conditions, or an upgraded segment or appliance.
Owner:TERRATRIM
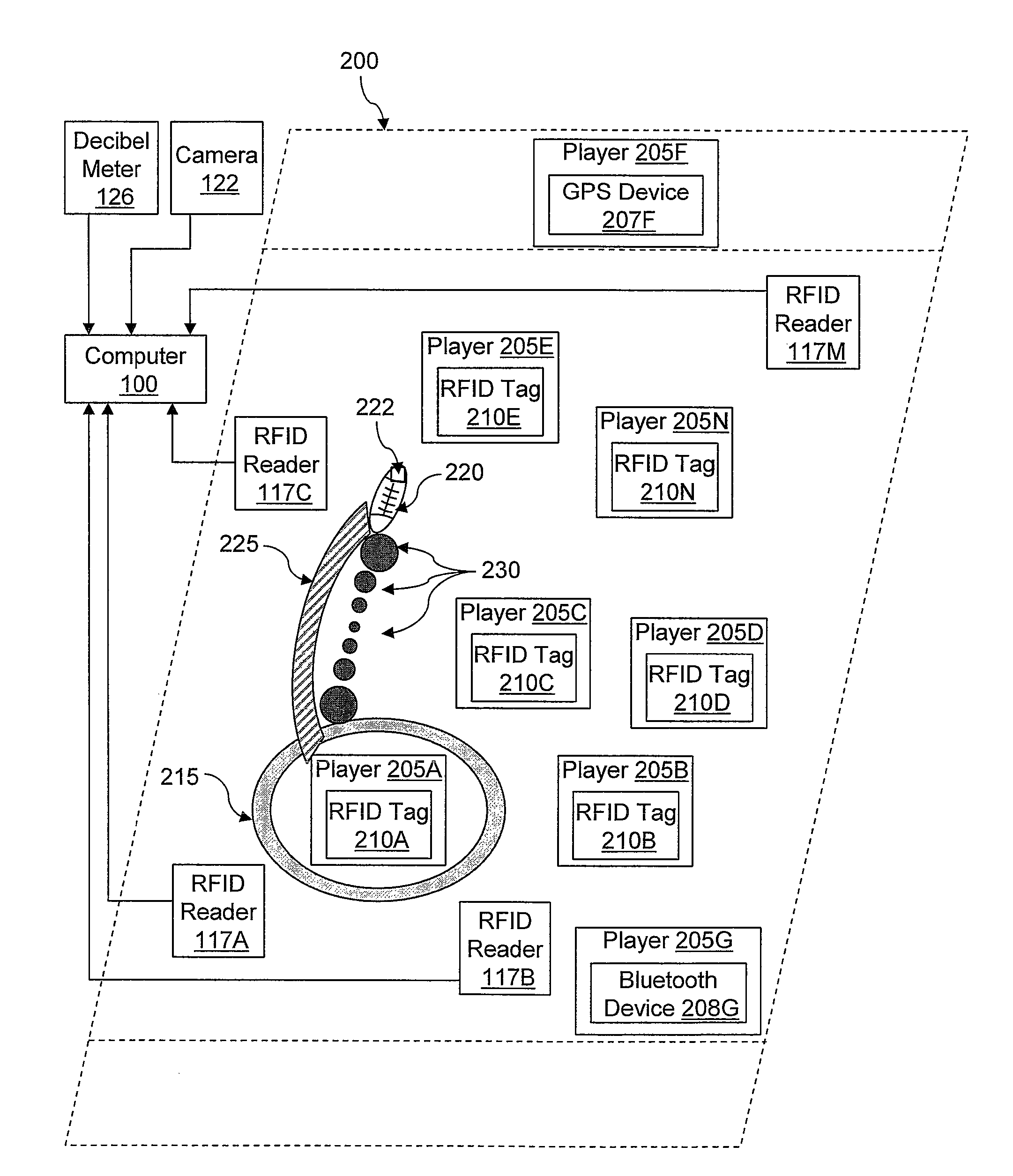
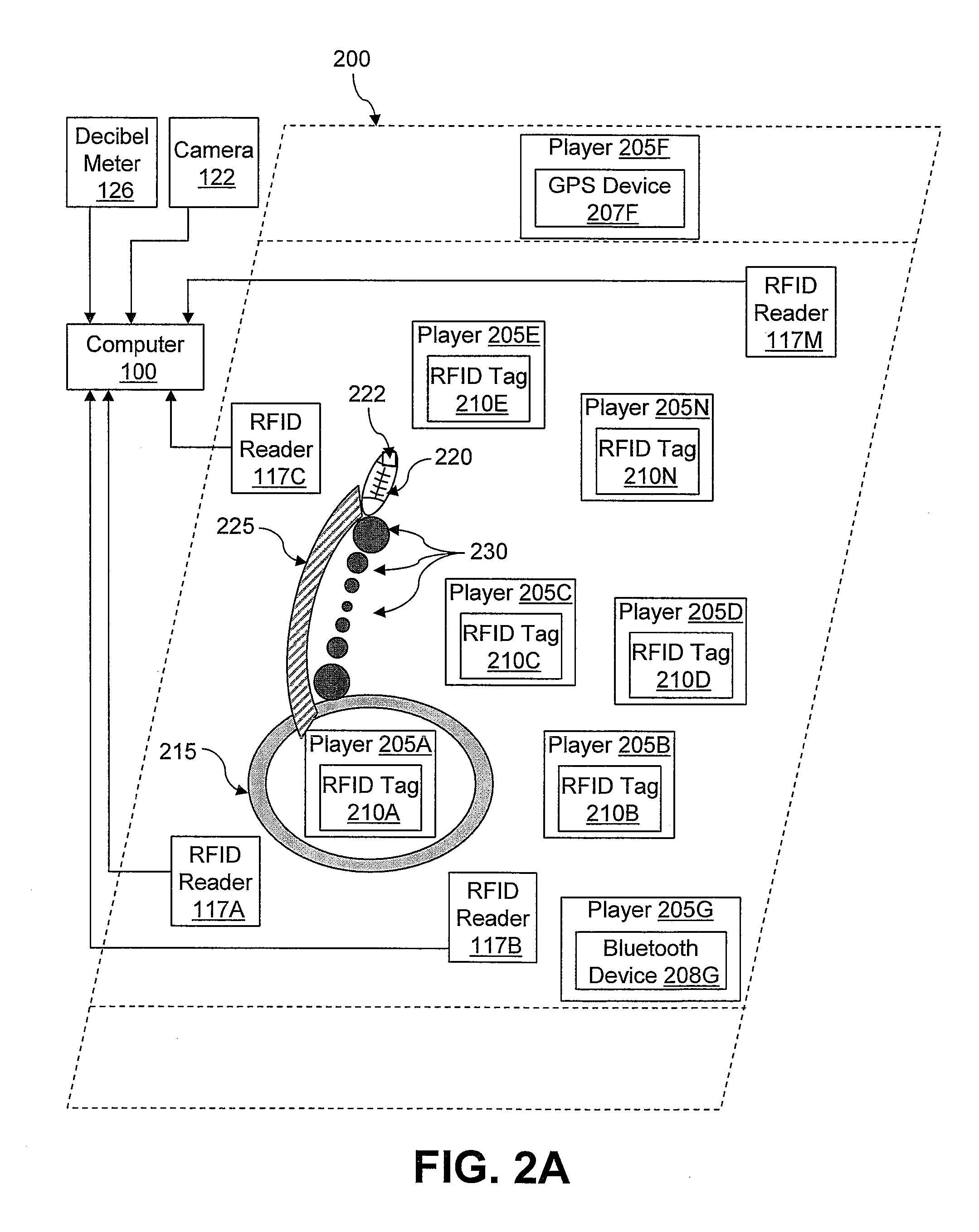
Modification of turf TV participant decorations based on multiple real-time factors
Owner:INT BUSINESS MASCH CORP
Method and apparatus for utility computing in ad-hoc and configured peer-to-peer networks
ActiveUS20090259720A1Multiple digital computer combinationsOffice automationProgramming languageUtility computing
Executing a program structure by leveraging a peer-to-peer network comprises generating a program structure comprising a plurality of program instructions. A first of a plurality of network peers then executes a portion of the program instructions which initiates the execution of code hosted by said first network peer, where said portion comprising fewer than all program instructions. The first network peer then migrates one or more of the program instructions, together with any requisite data, to at least one other of the plurality of network peer. The at least one other network peer then continues execution of the program structure until one or more of the objections of the program structure are achieved.
Owner:ZEROTOUCHDIGITAL
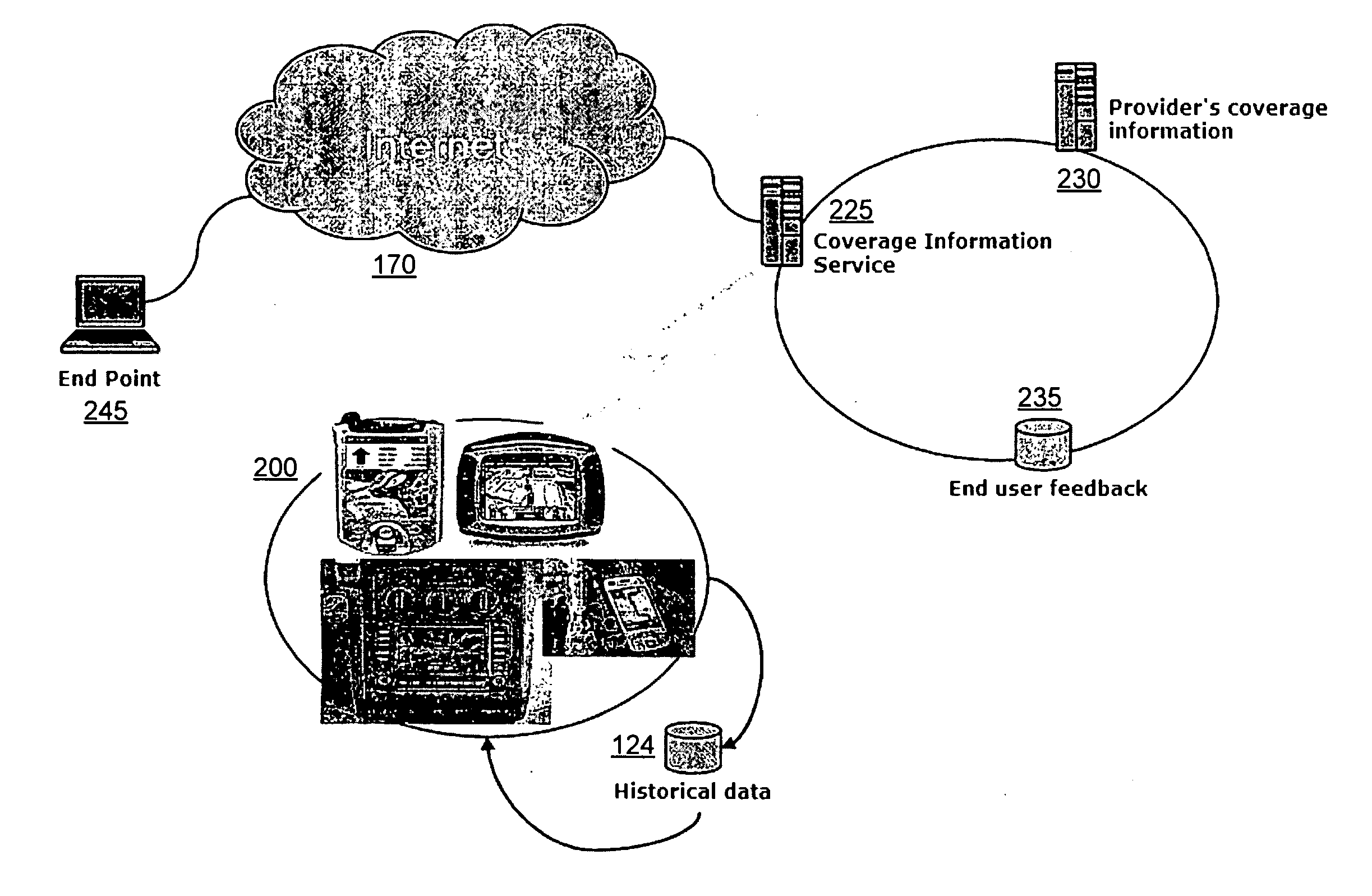
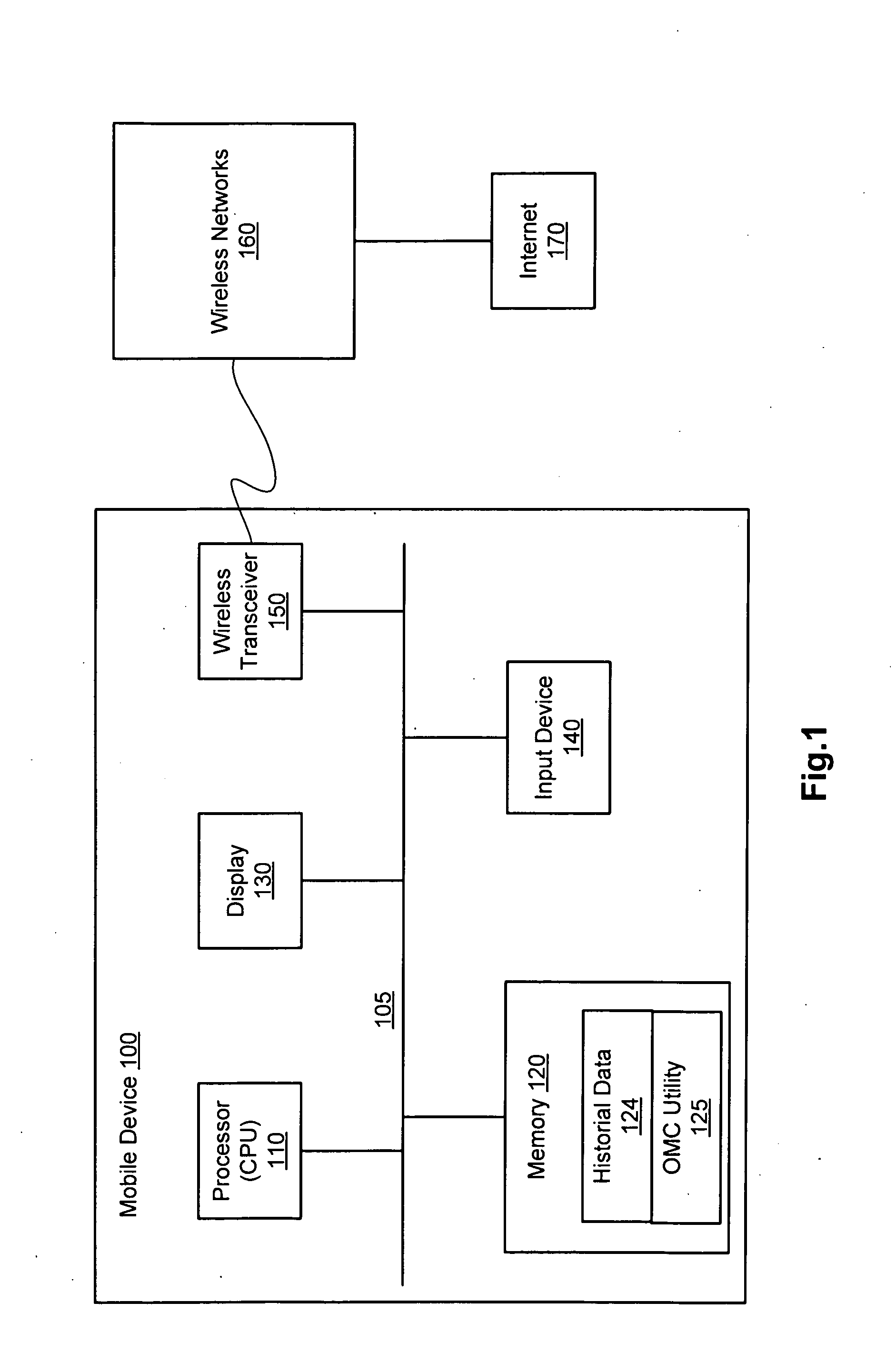
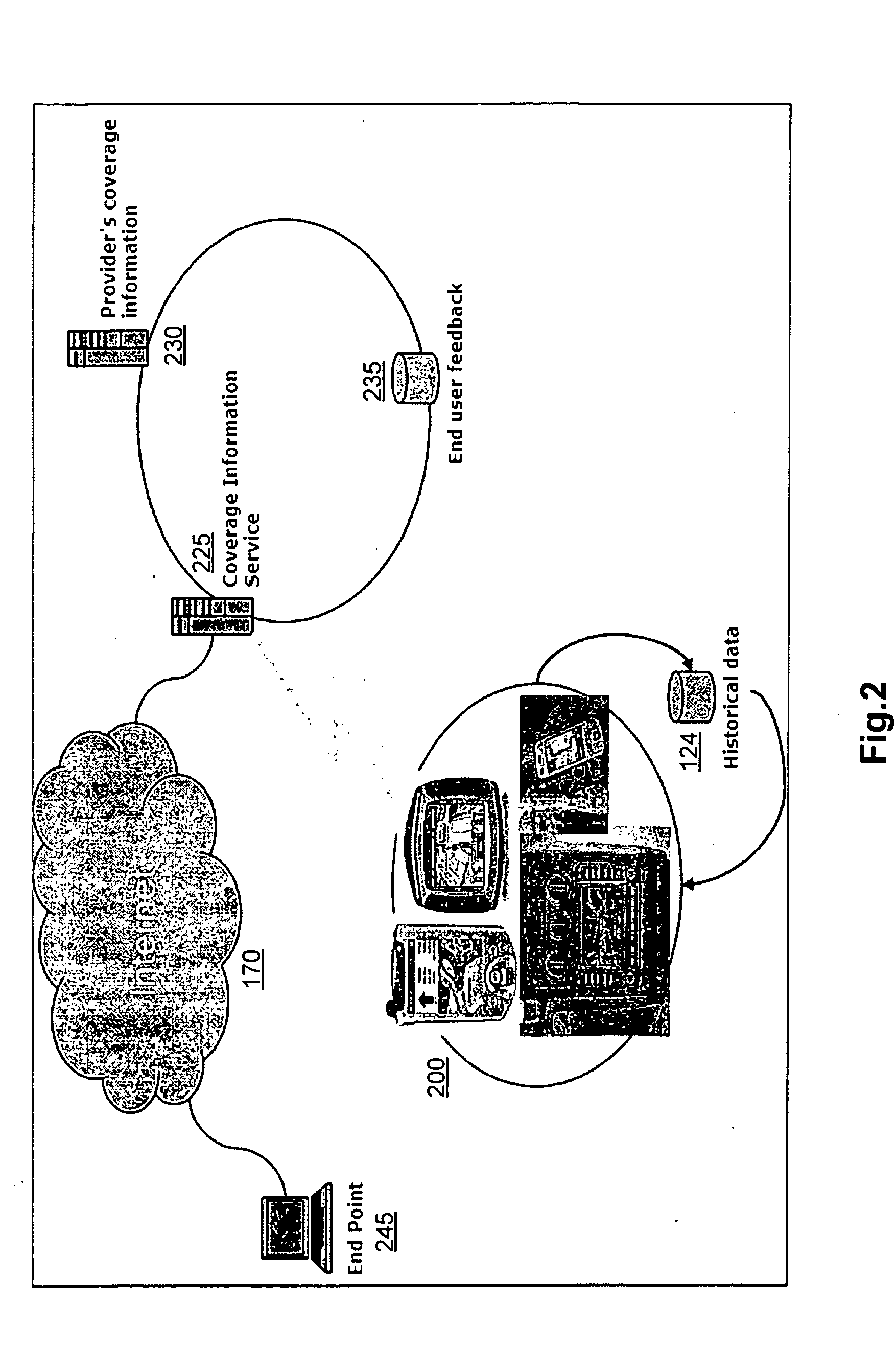
Route navigation for optimal mobile coverage
InactiveUS20100036604A1Increase coverageInstruments for road network navigationRoad vehicles traffic controlUtility computingWeb site
A utility within a mobile device or other device computes and provides an optimal mobile coverage route. The device receives a stating point / location and a destination point / location. The mobile device downloads a provider's mobile coverage information, accesses historical data stored by the mobile device, and obtains user feedback from the provider. The optimal mobile coverage route is then computed at the device, and the optimal mobile coverage route is provided via one of the following: a web site, or a text message (SMS) to, a voice operated feed, or any direct feed to the user of the mobile device. The computed optimal mobile coverage route is then used by the user of the mobile device when communicating with another mobile device while travelling from the starting point to the end point.
Owner:KYNDRYL INC
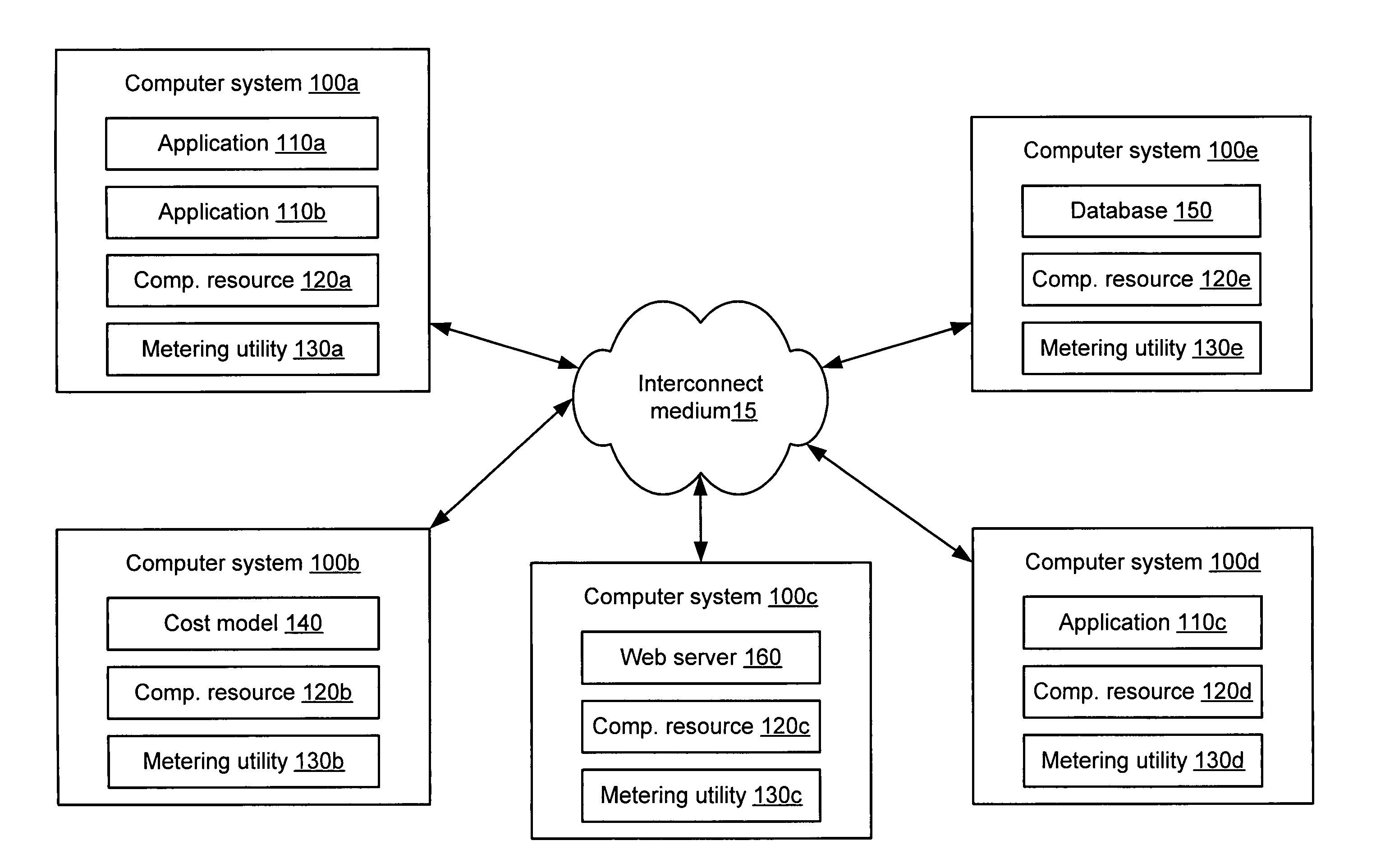
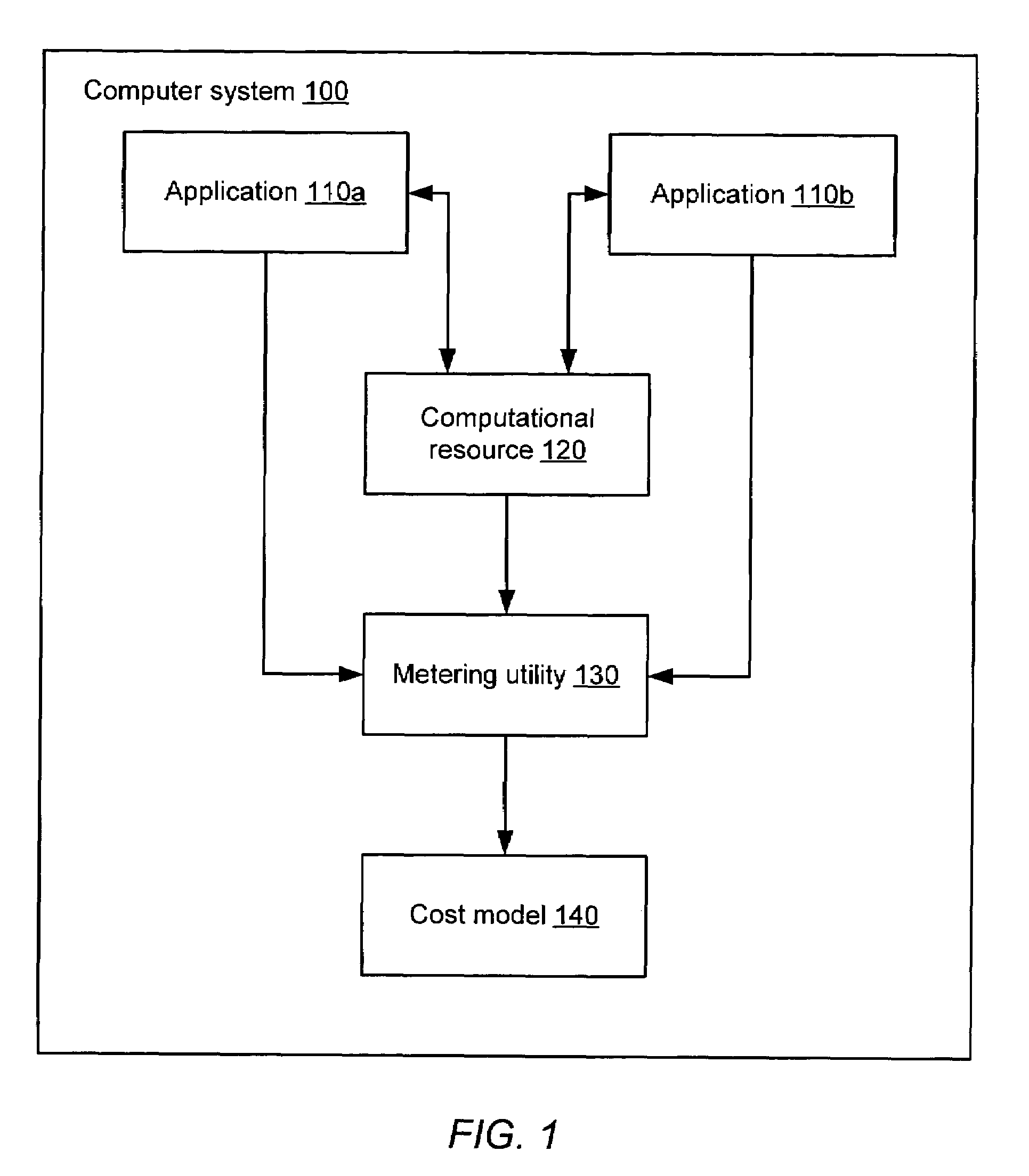
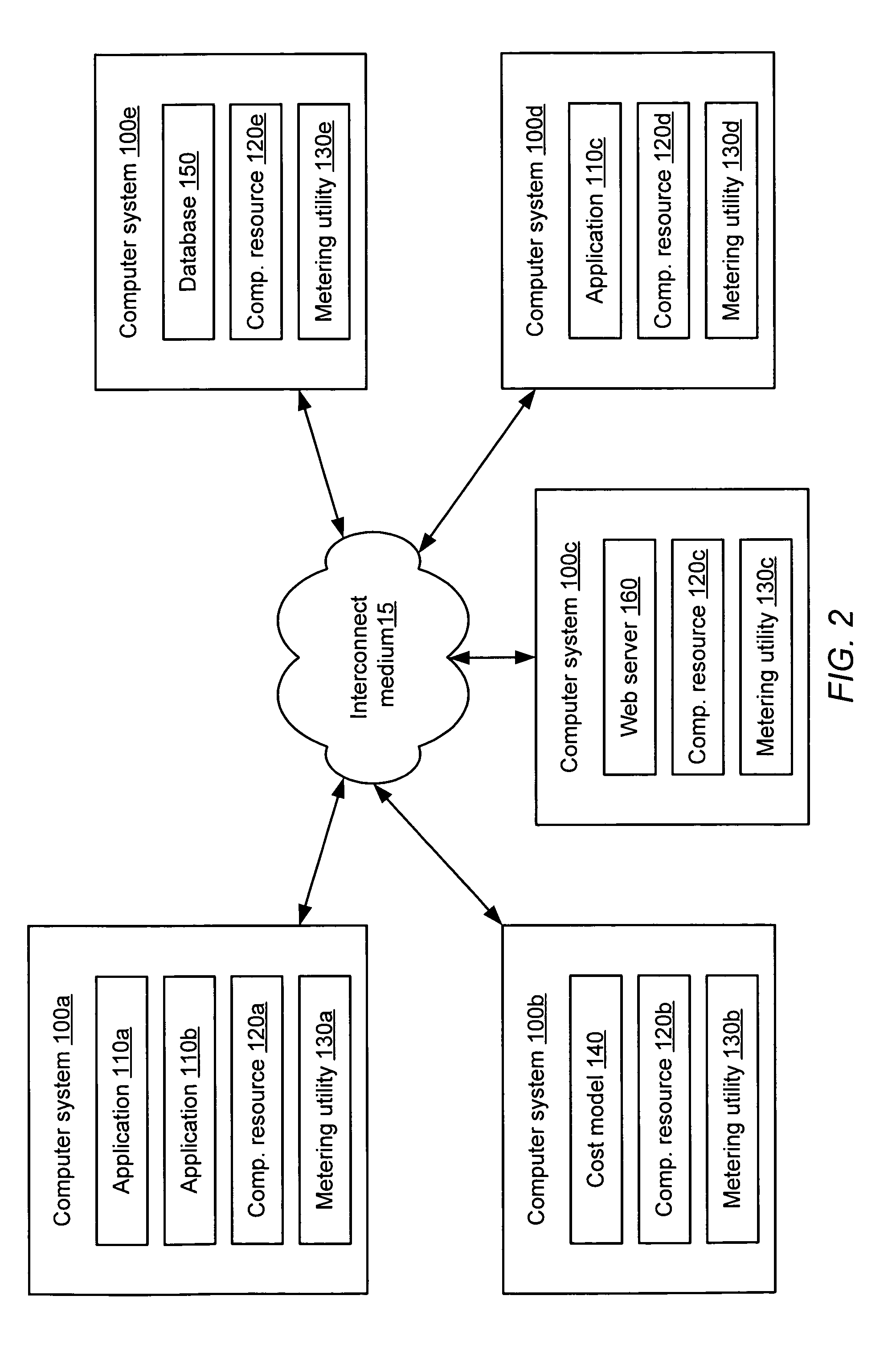
System and method for application resource utilization metering and cost allocation in a utility computing environment
A system and method for application resource utilization metering and cost allocation in a utility computing environment. In one embodiment, the system may include a computational resource, a plurality of applications configured to utilize the computational resource, a metering utility configured to measure utilization of the computational resource by a given one of the plurality of applications, and a cost model configured to allocate a first portion of a cost of the computational resource to the given application dependent upon the measured utilization of the computational resource by the given application.
Owner:ORACLE INT CORP
Method and apparatus for automatic and secure distribution of a symmetric key security credential in a utility computing environment
InactiveUS20060285693A1Key distribution for secure communicationDigital data processing detailsUtility computingDevice Identifiers
Embodiments of the invention provide a method and an apparatus for automatic, secure, and confidential distribution of a symmetric key security credential in a utility computing environment. In one method embodiment, the present invention establishes a symmetric key at a management server, the symmetric key automatically associated with a logical device identifier of a provisionable resource. Additionally, an isolated virtual network is established between the management server and the provisionable resource for providing the symmetric key to the provisionable resource. Then, after the symmetric key is provided to the provisionable resource the isolated virtual network between the management server and the provisionable resource is dissolved.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
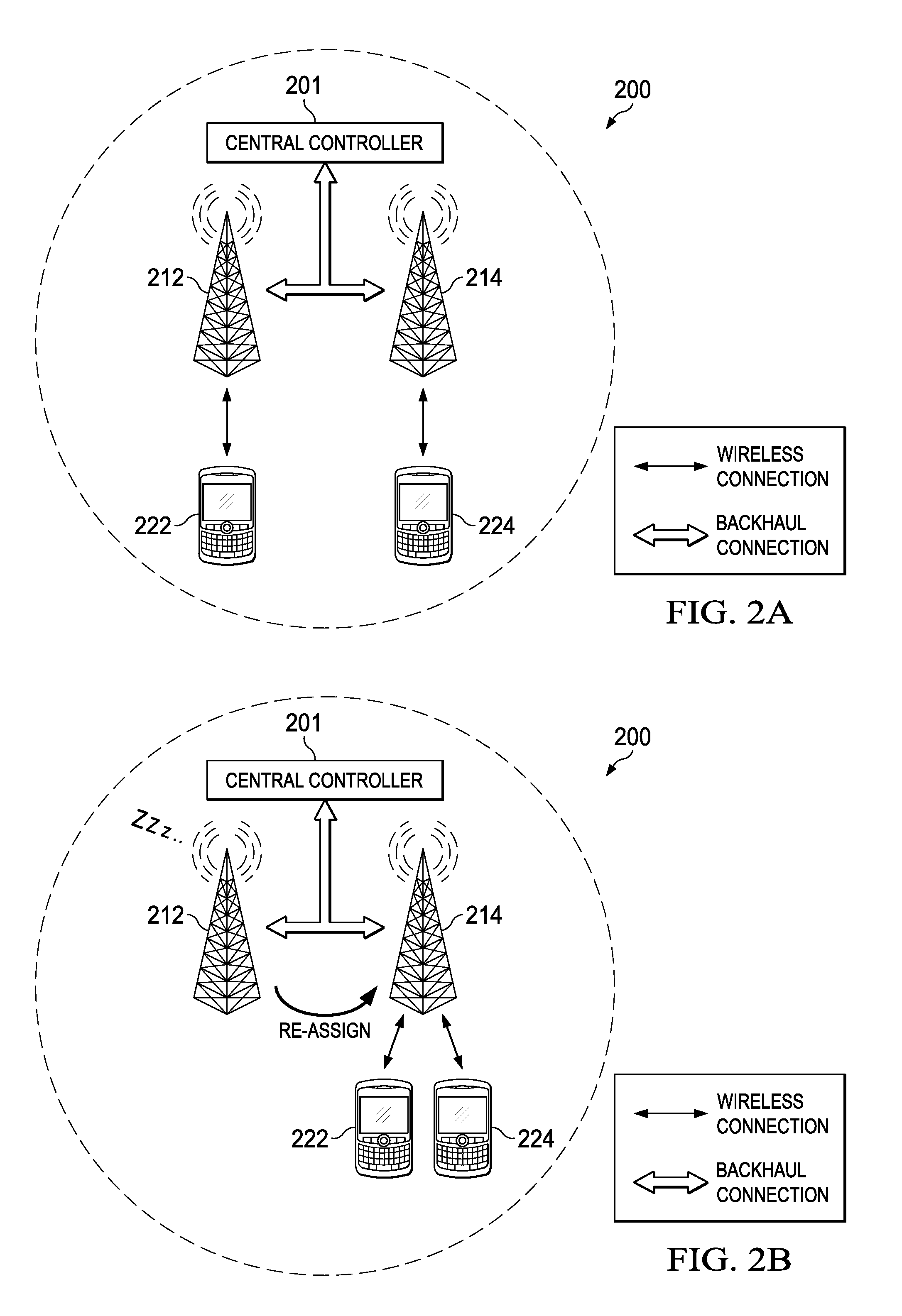
Methods for Dynamic Traffic Offloading and Transmit Point (TP) Muting for Energy Efficiency in Virtual Radio Access Network (V-RAN)
Energy efficient scheduling can be achieved by computing scheduling assignments in accordance with a transmit point (TP) muting utility. More specifically, candidate scheduling assignments that mute different combinations of transmit points are evaluated to determine which offers the highest utility. A greedy approach can be used to evaluate the candidate scheduling assignments in order to reduce the computational complexity of the scheduler. For example, a set of scheduling assignments may be evaluated during each iteration in a sequence of iterations, with each scheduling assignment muting a different one of the remaining TPs. At the end of each iteration, the scheduling assignment providing the highest utility is selected, and the TP muted by that scheduling assignment is muted during all succeeding iterations.
Owner:HUAWEI TECH CO LTD
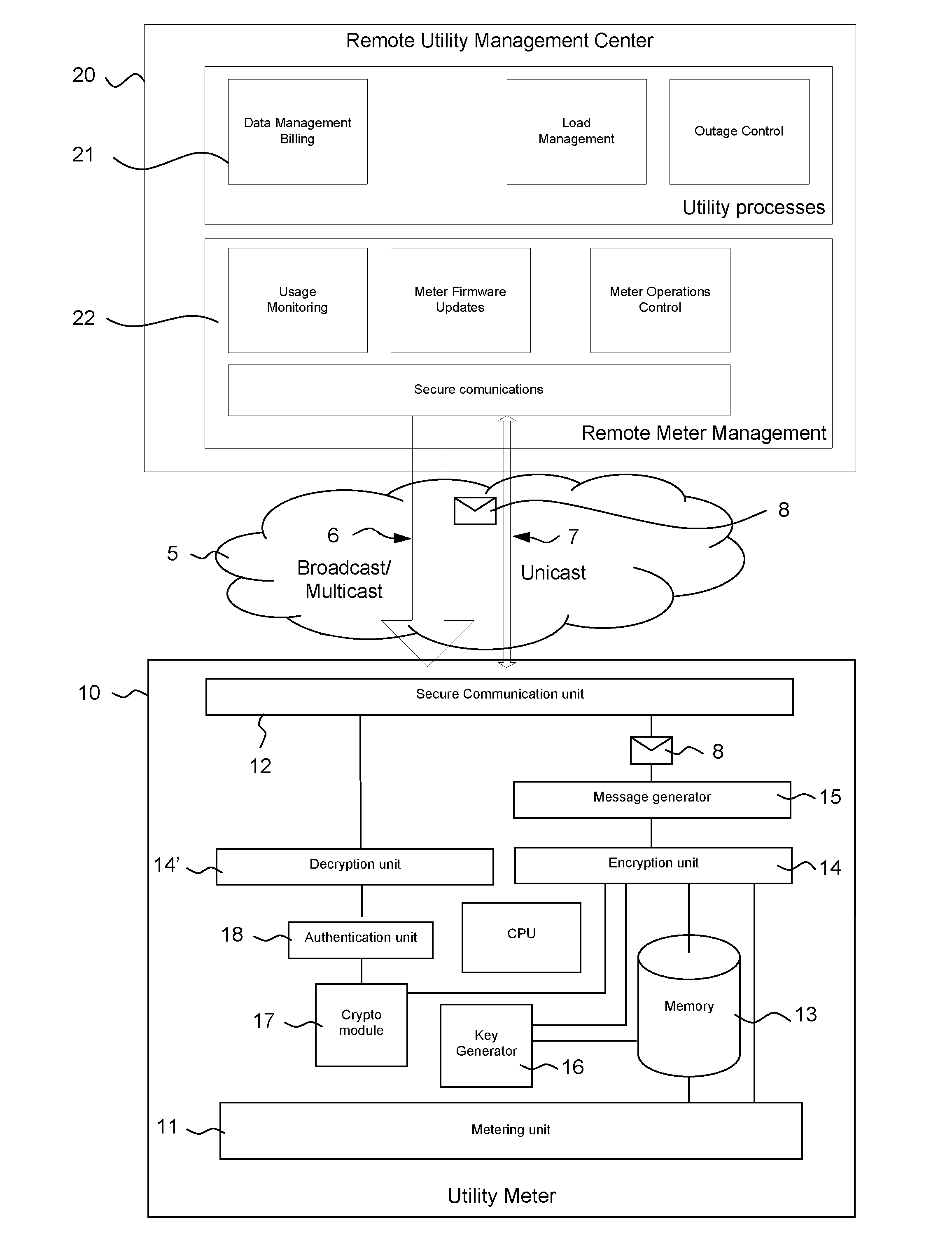
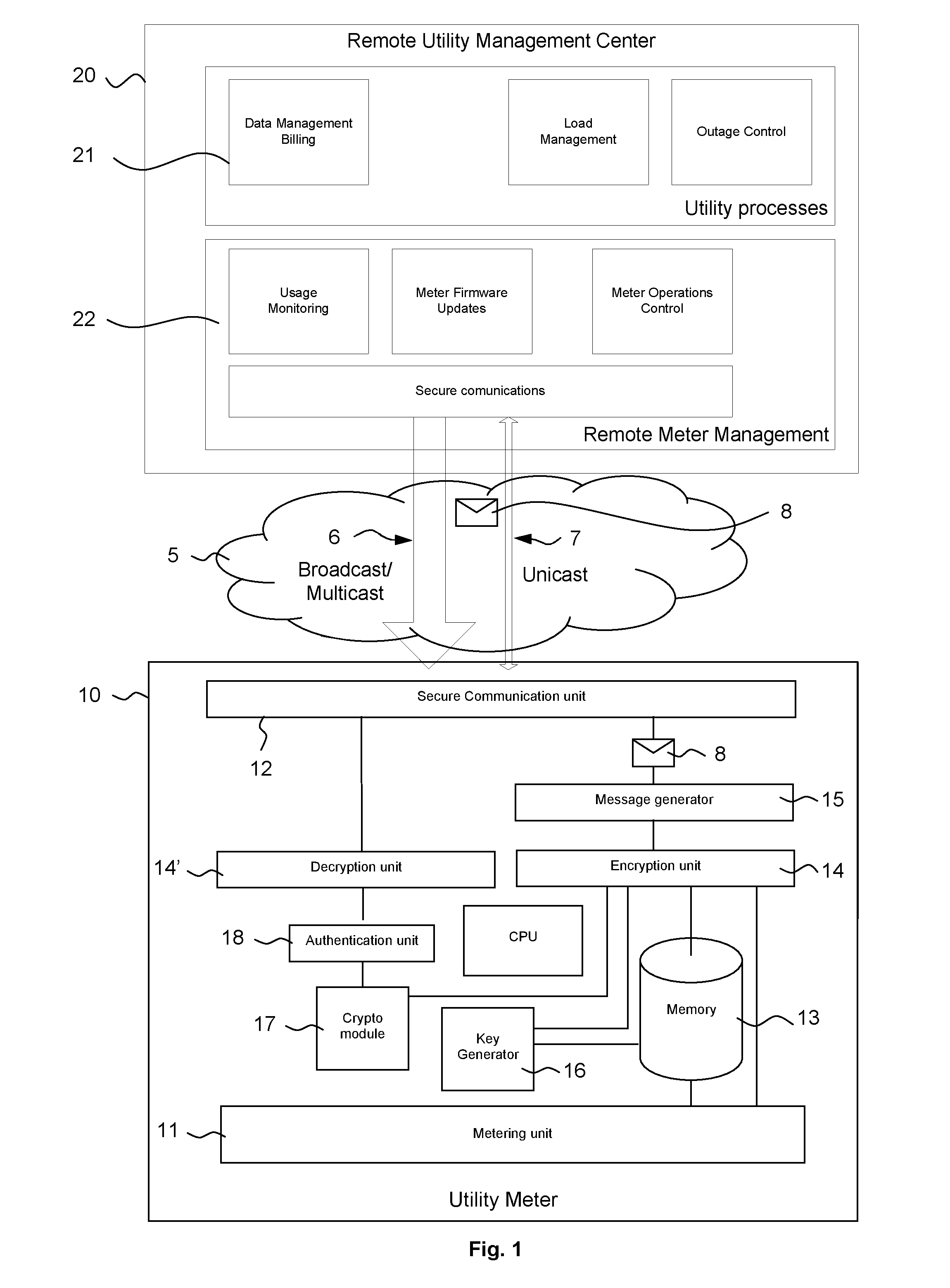
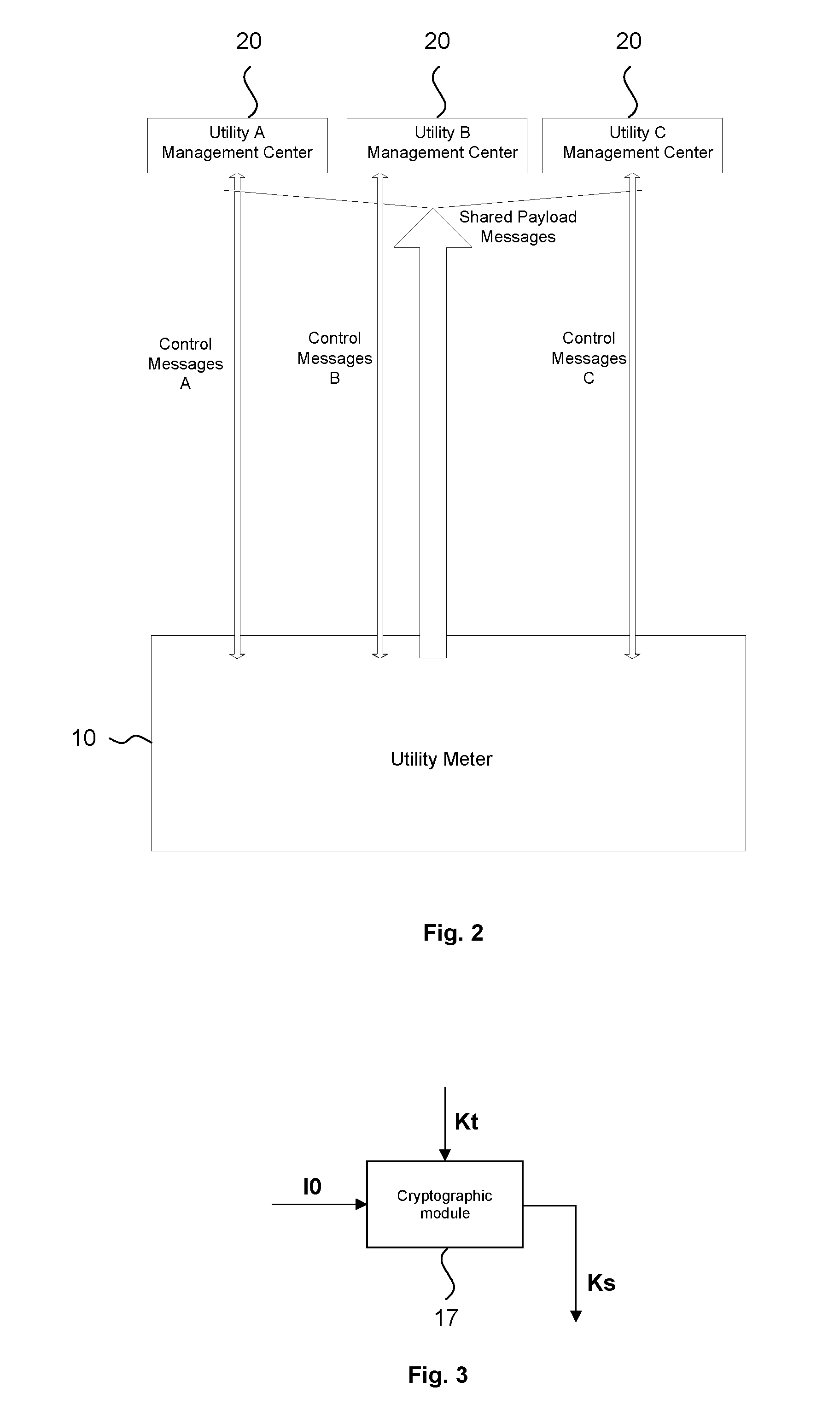
Utility meter for metering a utility consumption and optimizing upstream communications and method for managing these communications
ActiveUS20130314249A1Easy to transportEasy to splitElectric signal transmission systemsTariff metering apparatusUtility computingComputer hardware
A utility meter and method for metering consumption of at least one utility including: a metering unit, a communication unit for sending / receiving messages to / from a management center, a memory to store a unique identifier pertaining to the utility meter and a first key, an encryption unit for encrypting the utility consumption as a first cryptogram, a message generator for generating a utility message containing the first cryptogram, a key generator for generating a payload key to be used by the encryption unit for encrypting the utility consumption, a second cryptogram generated by the encryption unit by encrypting the payload key with the first key, the second cryptogram being intended to be included, by the message generator, at least once into the utility message to be sent to the remote management center.
Owner:NAGRAVISION SA
Market allocation design methods and systems
Owner:THE BOEING CO
Method for monitoring and displaying of utility consumption
ActiveUS8396740B1Data processing applicationsElectric devicesUtility computingUltimate tensile strength
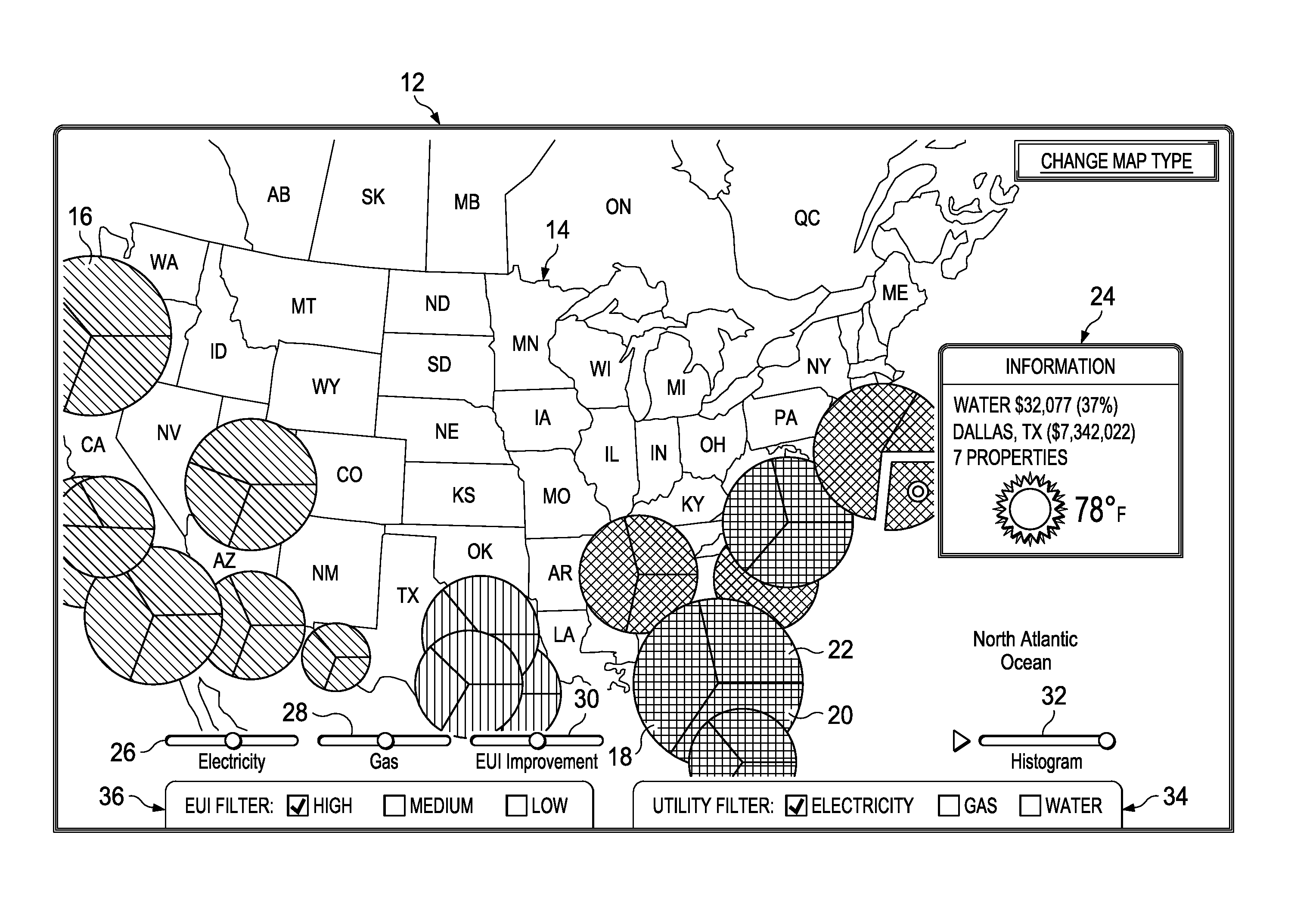
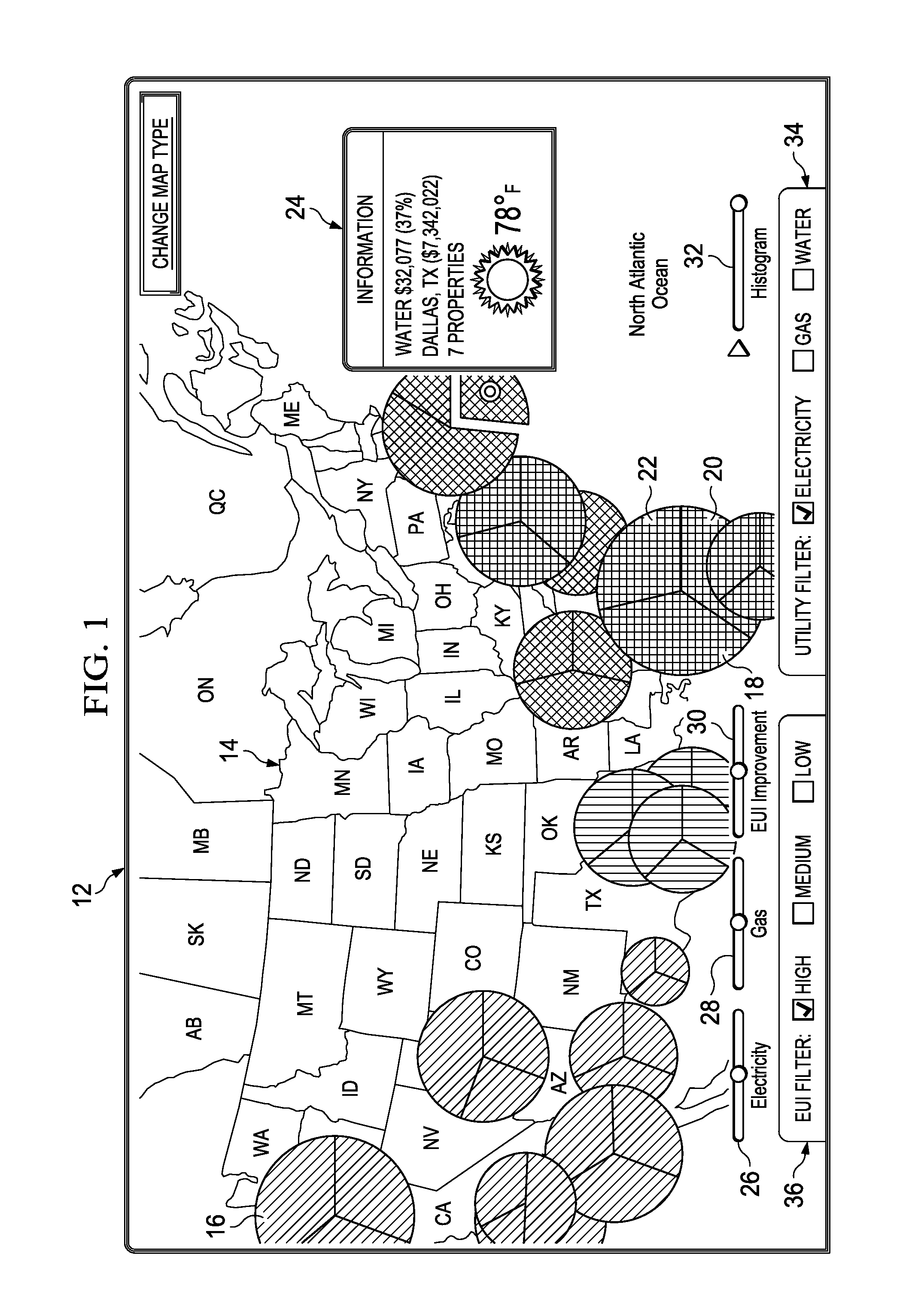
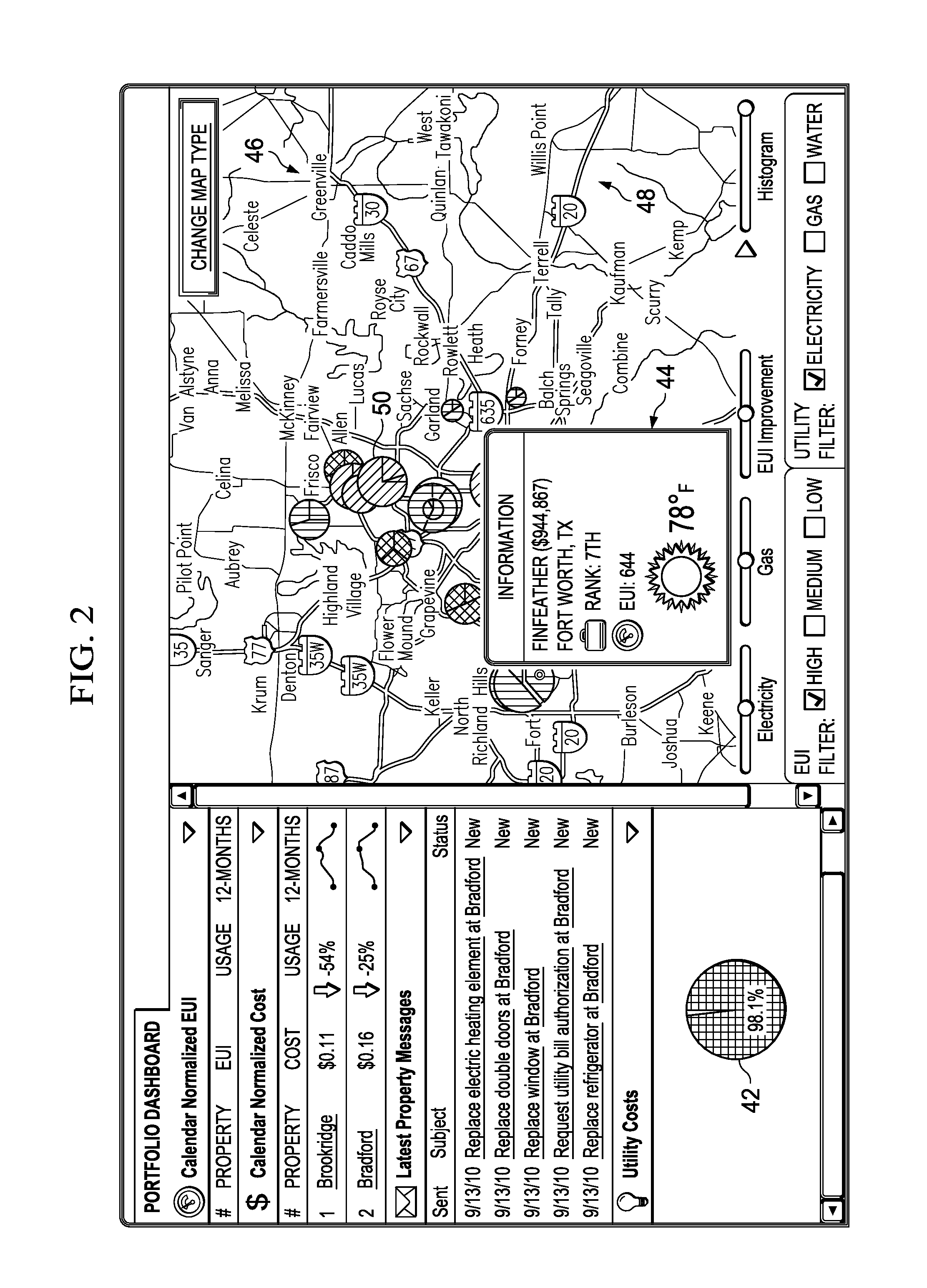
A method is disclosed for displaying utility consumption of a property portfolio for zones of a display area. First values correspond to utility consumption and second values corresponding to consumption intensity are first determined. The first values for each zone are ranked from high to low values and associated with a size of a geometric form corresponding to each of the zones. Similarly, the second values for each zone are ranked from high to low values and associated with a corresponding color, with a highest of the second values having a first color representing a highest consumption intensity, the smallest of the second values having a second color representing the lowest consumption intensity, and the remaining of the second values are associated with mixtures of the first color and second color. The respective geometric forms for each of the zones are displayed on the map at respective spatial locations.
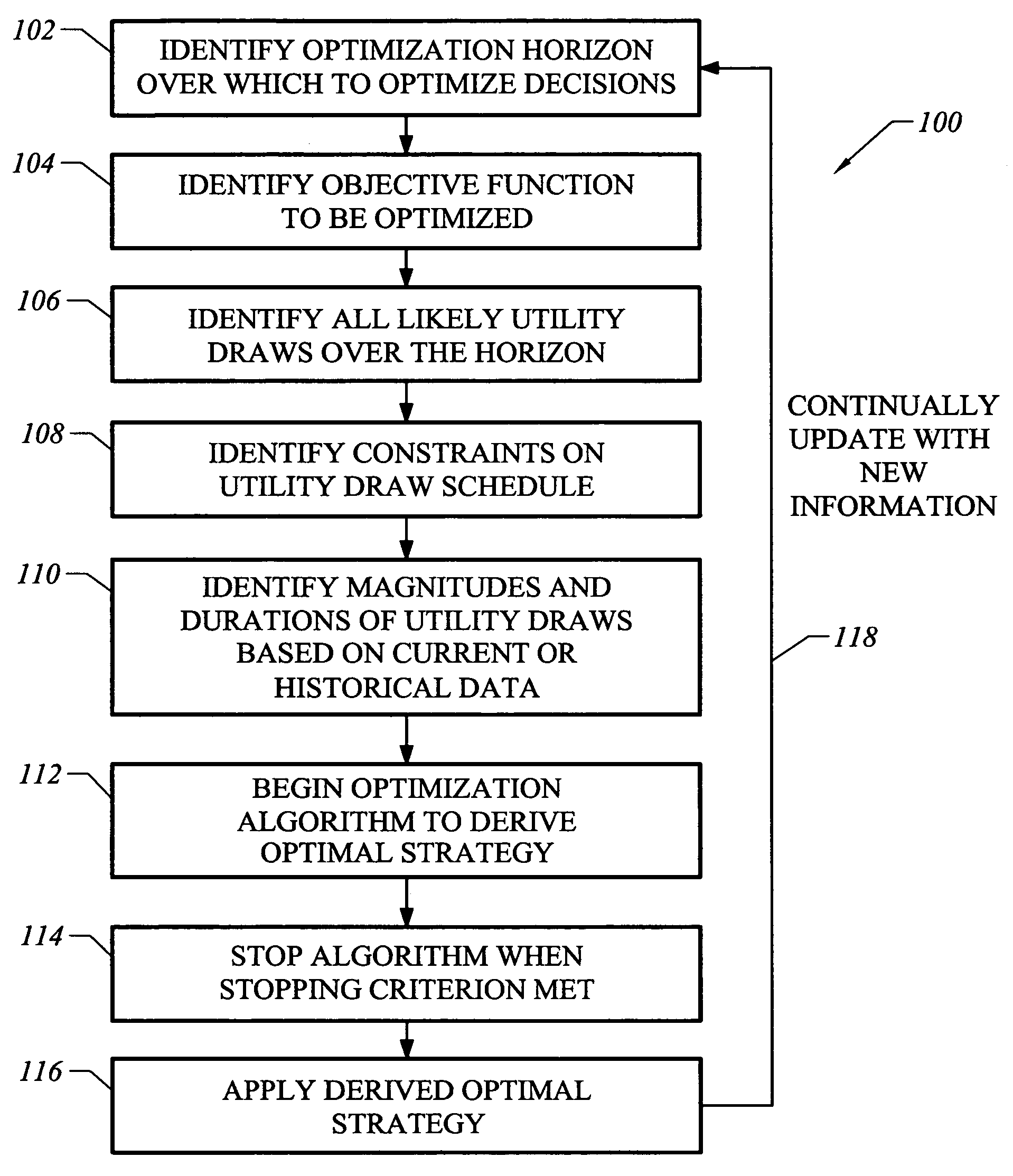
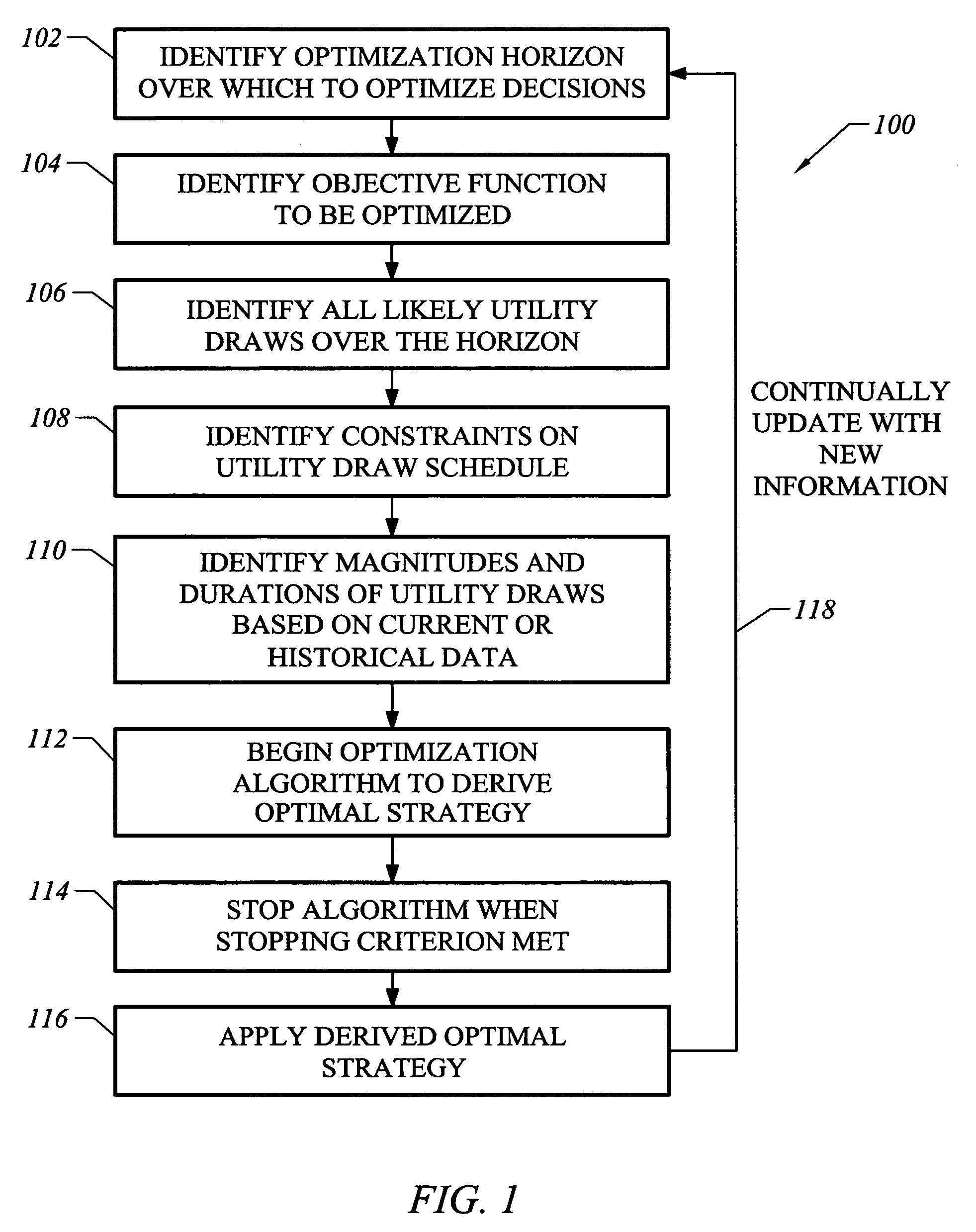
Owner:BYRAM LAB INC
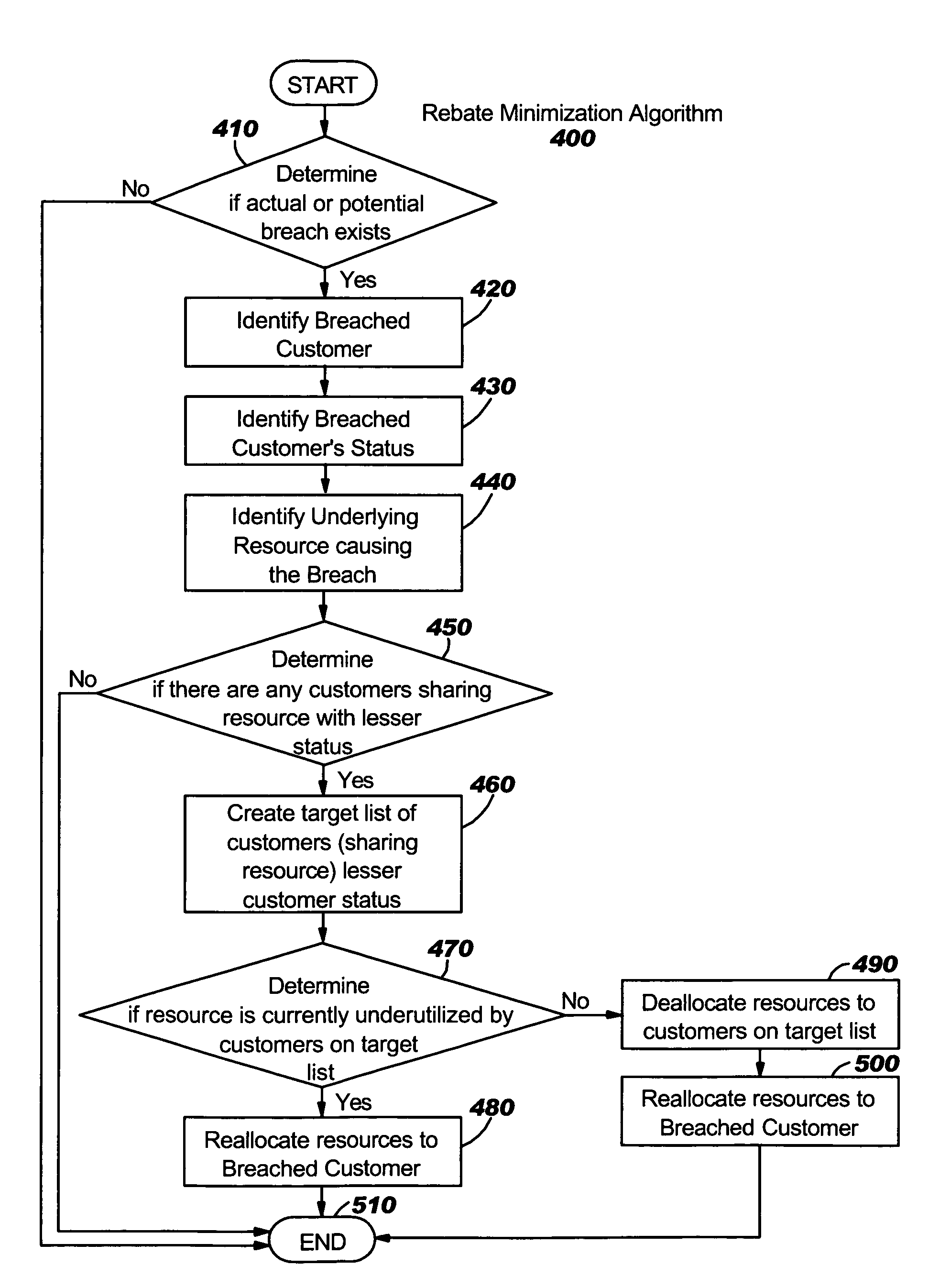
Algorithm for minimizing rebate value due to SLA breach in a utility computing environment
InactiveUS7269652B2Minimizing overall rebateMinimizing the total rebate dueMultiprogramming arrangementsMultiple digital computer combinationsUtility computingService-level agreement
The invention described is a new and useful process for minimizing the overall rebate a provider disburses to customers when a service level agreement (SLA) breach occurs in a utility computing environment. Specifically, the process compares performance data and resource usage with the SLAs of the customers, and reallocates shared resources to those customers who represent a lesser penalty to the provider in the event of an SLA breach. The process determines which resources, used by customers representing the lesser penalty, are operating below peak capacity. The process then reallocates these under-utilized resources to those customers requiring additional resources to meet SLA thresholds. If all resources are operating at peak capacity, the process reallocates the resources to those customers whose SLAs represent a greater penalty in the event of an SLA breach as compared to those customers whose SLAs provide for a lesser penalty, thereby minimizing the total rebate due upon an SLA breach.
Owner:GOOGLE LLC
Data processing method and system for utility computing environment
InactiveCN1598850AMetering/charging/biilling arrangementsMultiple digital computer combinationsUtility computingService-level agreement
Owner:INT BUSINESS MASCH CORP
System and method for providing utility consumption as shown on periodic utility bills and associated carbon emissions
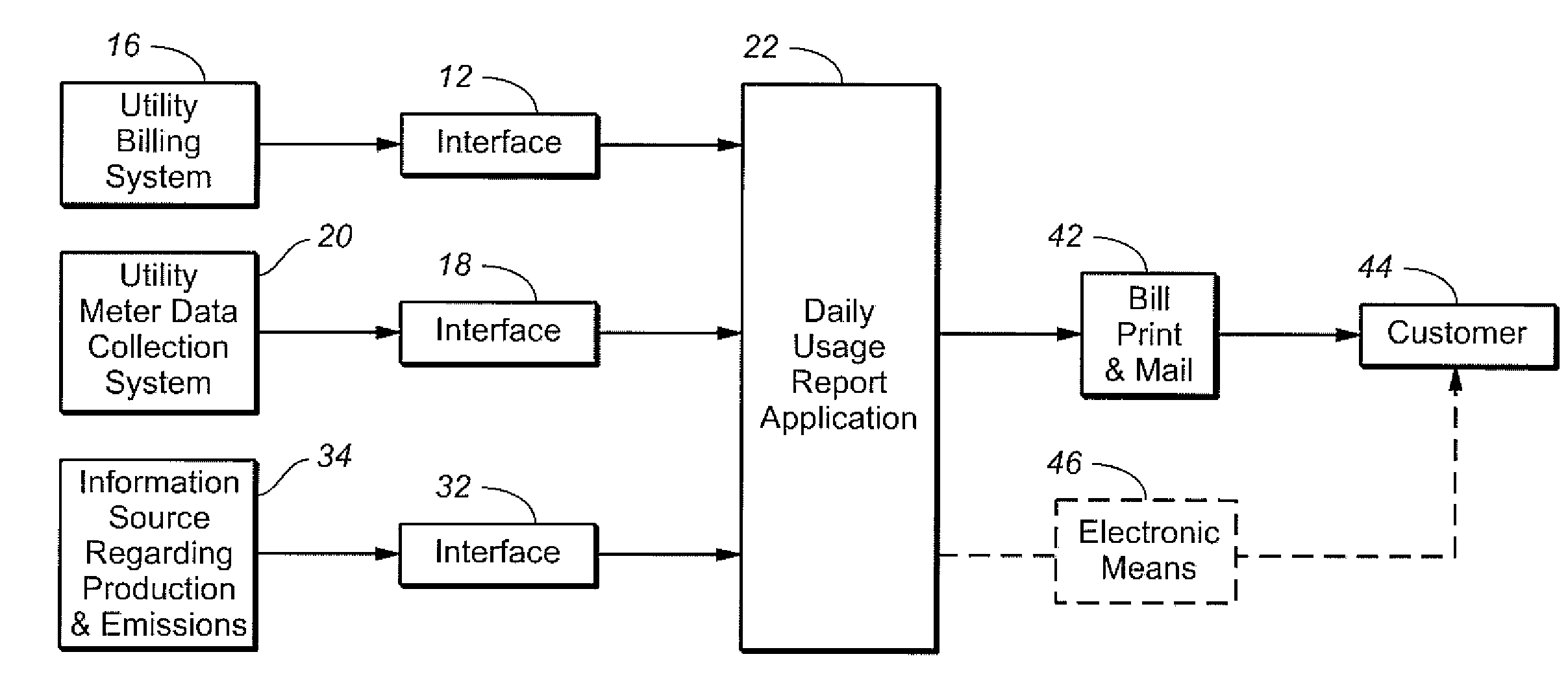
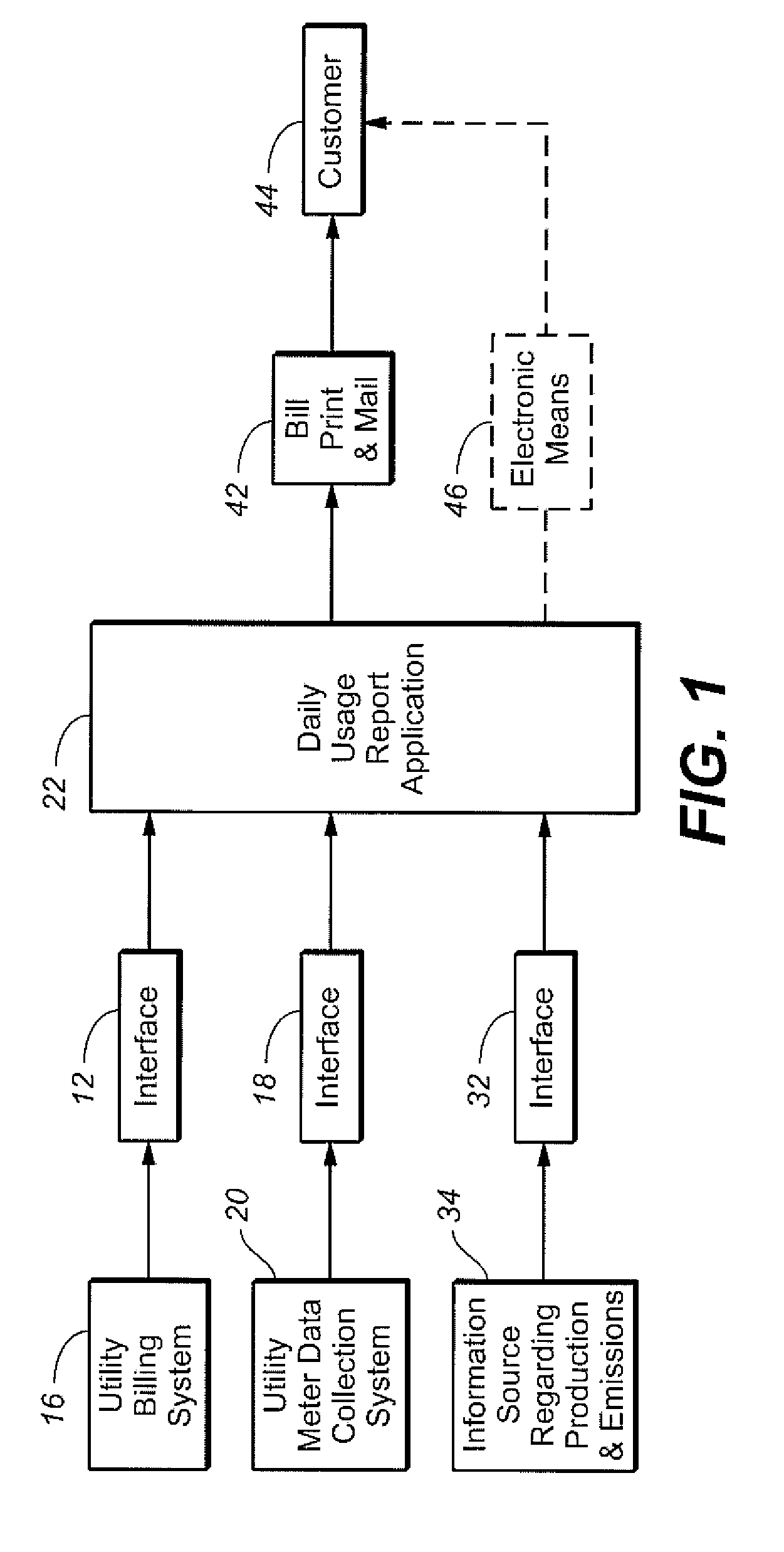
Utility usage data of a customer in numeric form provided by the utility meter data collection system in usage intervals of not less frequent than daily intervals is received, along with billing-related data of the customer. The received utility usage data of the customer is converted from numeric form to a graphical form that shows the total daily usage information for a calendar period that matches that for the printed utility bill of the customer. The graphical form is printed on the printed utility bill or on a paper suitable for use as an insert accompanying the printed utility bill to be mailed to the customer. In another embodiment, electricity usage data of the customer is received, along with electricity generation data regarding quantity and percentages of a utility's total electricity generation attributable to at least two the following electricity generation sources: Natural Gas-Baseload, Natural Gas-Peaking, Coal, Hydro, Nuclear, and Renewable. Information is derived regarding proportion of the customer's actual electricity usage attributable to the sources of electricity generation from the electricity generation data and the electricity usage data. Preferably, the carbon emissions attributable to the customer's actual electricity usage is calculated and presented to the customer.
Owner:EMETER CORP
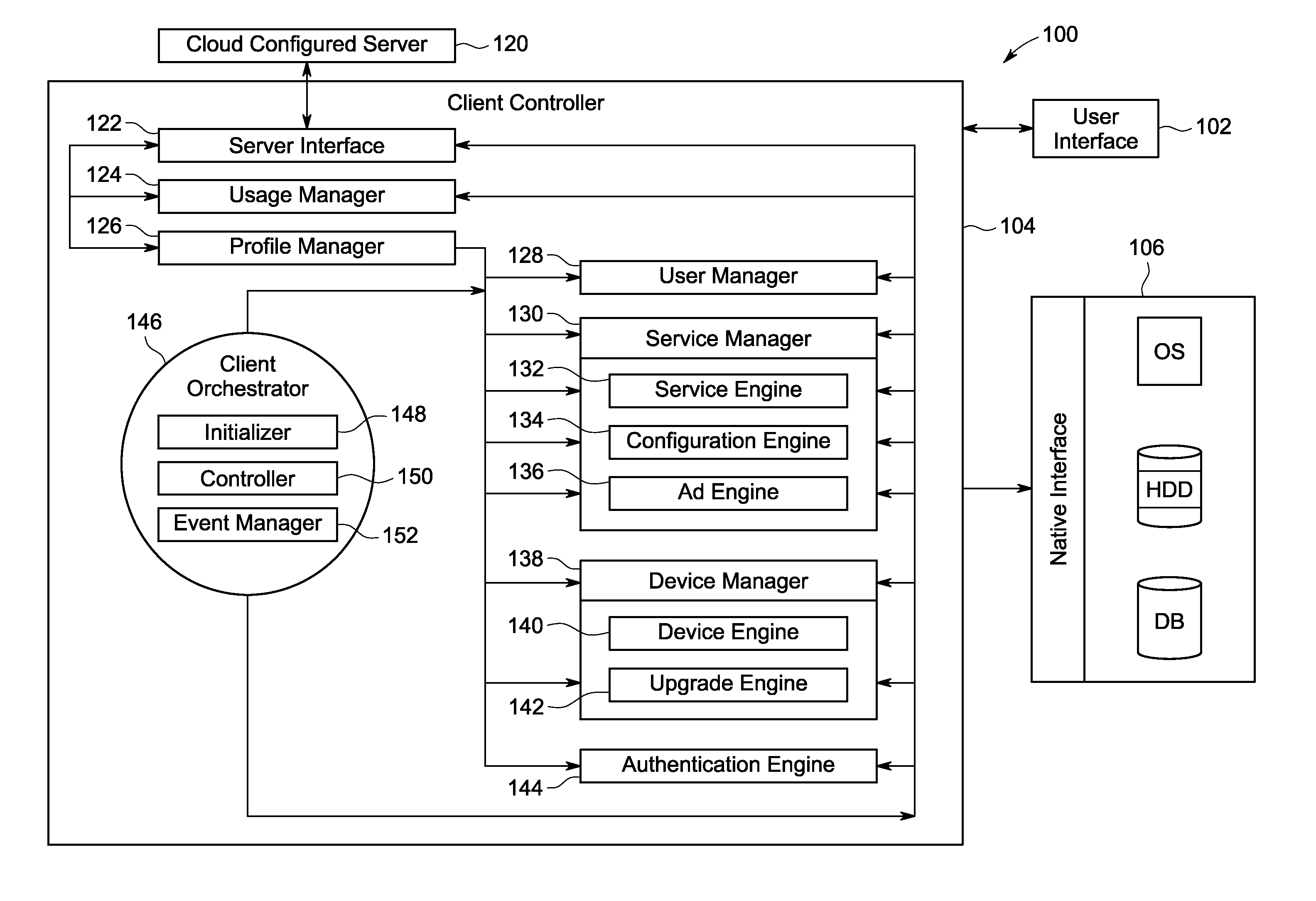
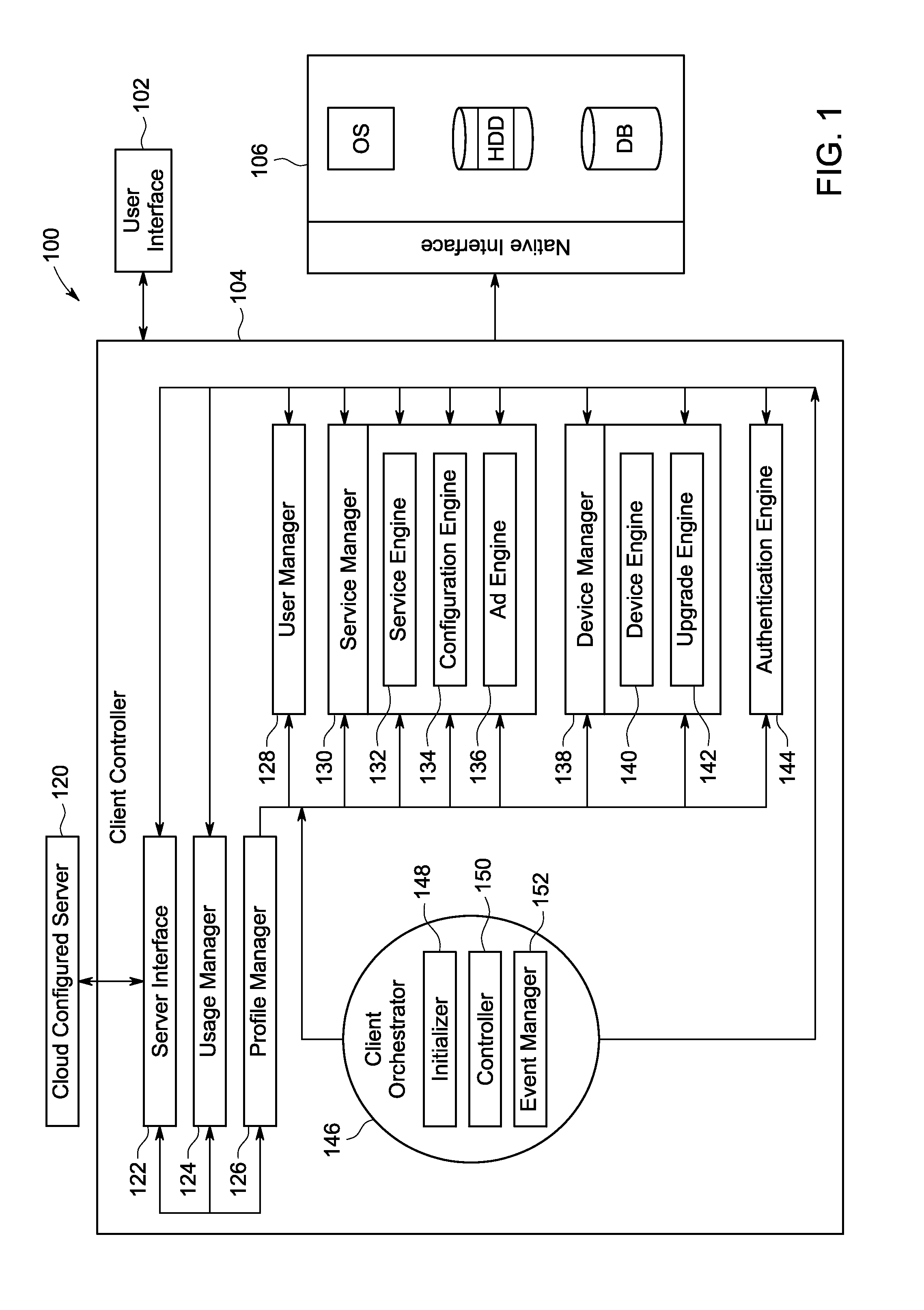
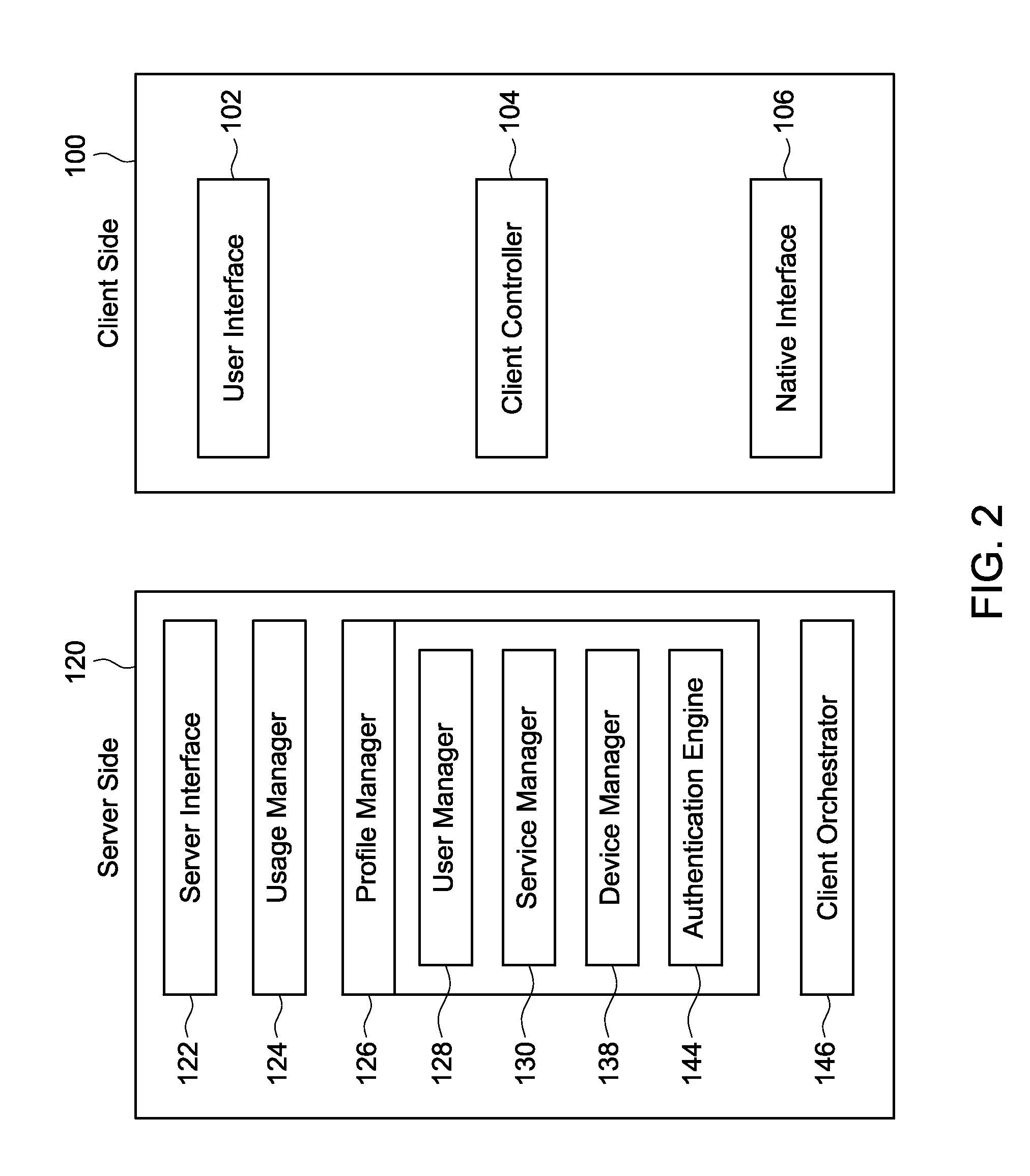
System and method for delivering cloud based utility services
System and method for delivering cloud based utility services to a plurality of user devices associated with a user in a cloud based managed utility computing environment are provided. The system comprises a client side component having a client controller configured for receiving user profile, applications, content and type and characteristics of each of the user devices, a user interface for accessing the user profile, applications, content and type and characteristics of each of the user devices and a native interface for interacting with at least one operating system of each of the user devices. The system further comprises a server side component configured for acquiring the user profile, applications, content and type and characteristics of each of the user devices. The server side component is configured for delivering the cloud based utility services based on the type and characteristics of each of the user devices associated with the user.
Owner:NOVATIUM SOLUTIONS PVT
Method and apparatus for utility computing in ad-hoc and configured peer-to-peer networks
InactiveUS20100199328A1Digital data processing detailsComputer security arrangementsProgramming languageUtility computing
Executing a program structure by leveraging a peer-to-peer network comprises generating a program structure comprising a plurality of program instructions. A first of a plurality of network peers then executes a portion of the program instructions which initiates the execution of code hosted by said first network peer, where said portion comprising fewer than all program instructions. The first network peer then migrates one or more of the program instructions, together with any requisite data, to at least one other of the plurality of network peer. The at least one other network peer then continues execution of the program structure until one or more of the objections of the program structure are achieved.
Owner:ZEROTOUCHDIGITAL
Method of displaying real-time service level performance, breach, and guaranteed uniformity with automatic alerts and proactive rebating for utility computing environment
InactiveUS7523041B2Eliminate the potential discrepancyMetering/charging/biilling arrangementsMultiple digital computer combinationsUtility computingService-level agreement
The present invention provides a method, apparatus, and computer program product for displaying real-time service level performance, breach, and guaranteed uniformity with automatic alerts and proactive rebating for a utility computing environment. Service level agreement parameters, based on a service level agreement between a customer and a service provider, are used to identify discrepancies in a promised service level for the utility computing environment. A real-time view of a current service level and the promised service level for the customer are displayed. When a discrepancy between the promised service level and the current service level occurs, a rebate is generated for the customer. Alerts identifying the discrepancy and its root cause are provided to the customer and the service provider for the discrepancy. Alerts may also be provided prior to the occurrence of the discrepancy so that an action may be performed to eliminate the potential discrepancy.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com