Identity authentication method with privacy protection and password retrieval function
An identity authentication and password technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve problems such as unwillingness to provide mobile phone numbers to websites, not using emails, and infrequently using emails.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0083] 1. Dynamic link library method (general method)
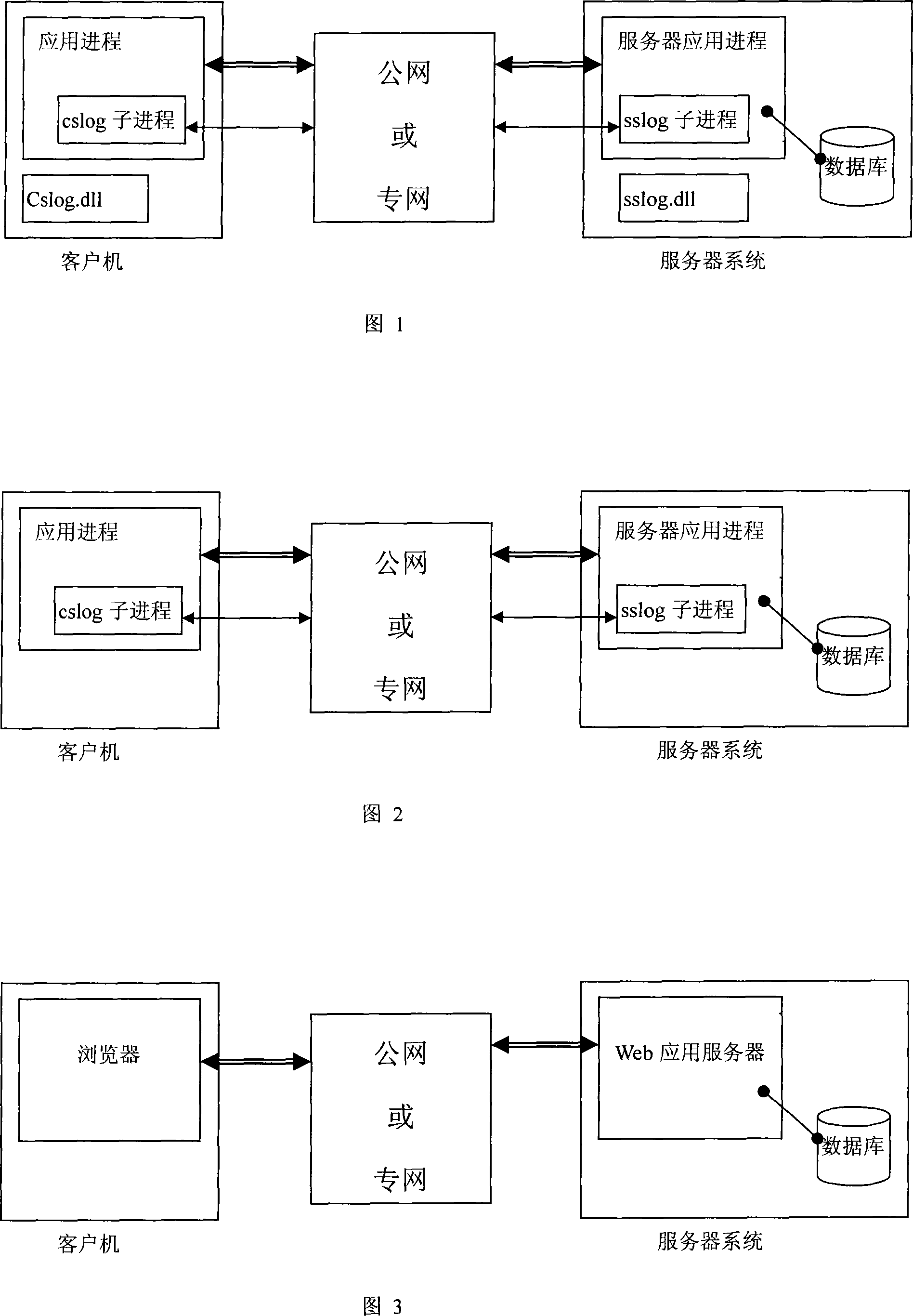
[0084] As shown in Figure 1, the cslog sub-process of the client application process and a sslog sub-process of the server cooperate to complete the processes of registration, login and password retrieval described in the present invention. The server can have multiple sslog sub-processes at the same time. The cslog subprocess is generated by calling the cslog.dll library function; the sslog subprocess is generated by calling the sslog.dll library function.
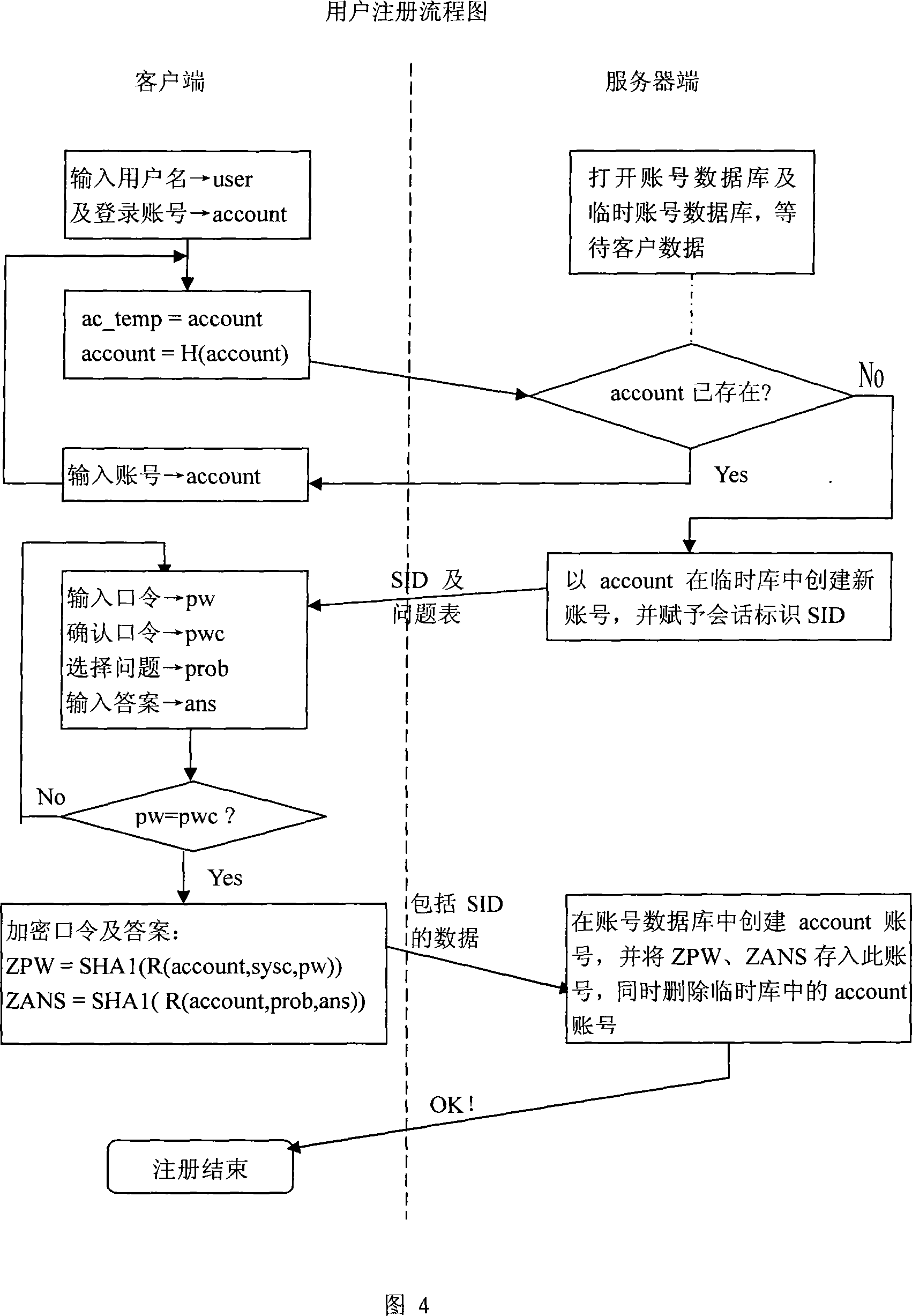
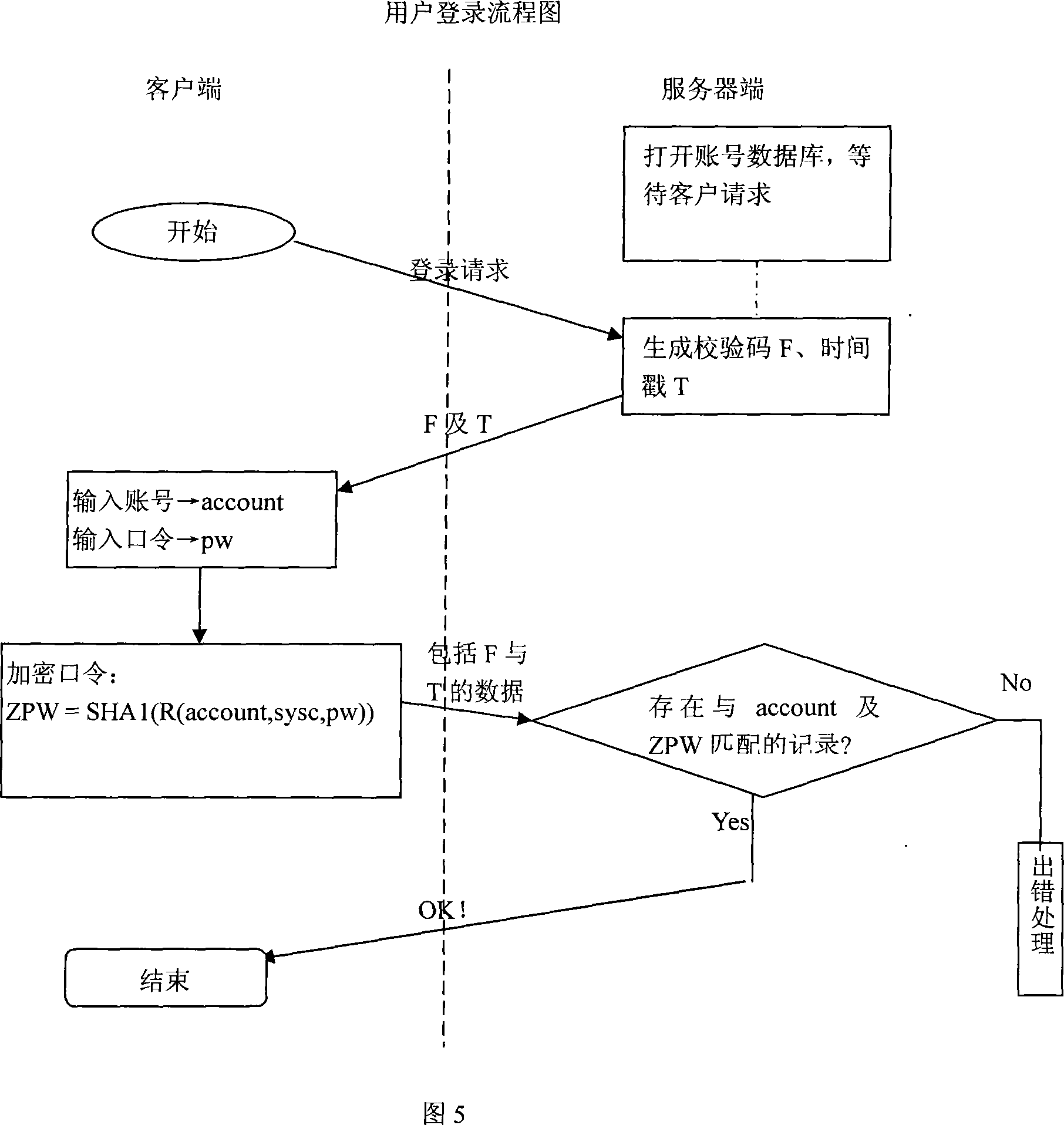
[0085] The dynamic link library is divided into two library files, which may be named cslog.dll and sslog.dll. Among them, cslog.dll includes three modules czhuce, cdenglu, and cklzh for client registration, login, and password retrieval; sslog.dll includes four modules for the server: szhuce, sdenglu, sklzh, and idatabase. Except idatabase, each module runs as a thread when called, and idatabase provides the interface with the user database and related settings, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com