Application software calling method for intelligent terminal
A technology of application software and intelligent terminal, applied in program control design, instrument, electrical digital data processing, etc., can solve the possibility of being easily attacked by hackers, the security of sensitive data cannot be guaranteed, and the possibility of stealing private data and important information Large and other problems, to achieve the effect that is not easy to attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
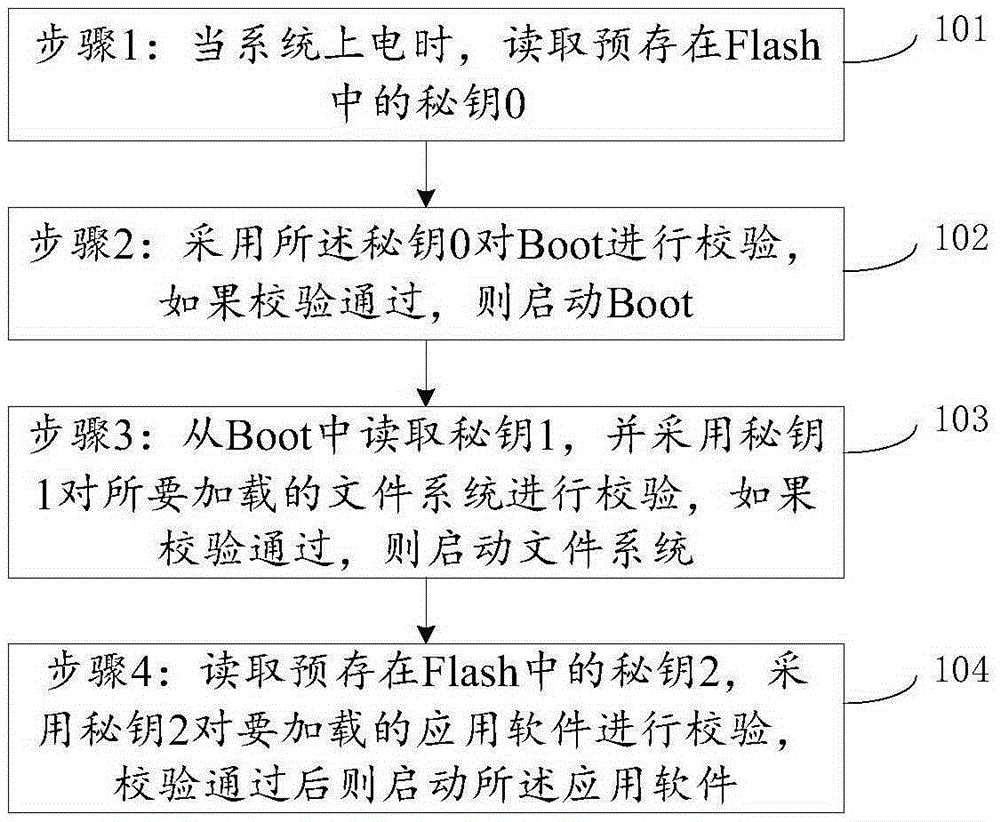
[0029] see figure 1 , is a schematic diagram of an application software calling method of a smart terminal provided in Embodiment 1 of the present invention.
[0030] Such as figure 1 As shown, an application software calling method includes:
[0031] 101 Step 1: When the system is powered on, read the secret key 0 pre-stored in the Flash;
[0032] 102 Step 2: Use the secret key 0 to verify the Boot, if the verification is passed, start the Boot, and go to step 3;
[0033] 103 Step 3: Read secret key 1 from Boot, and use secret key 1 to verify the file system to be loaded, if the verification is passed, start the file system, and go to step 4;
[0034] 104 Step 4: Read the secret key 2 pre-stored in the Flash, use the secret key 2 to verify the application software to be loaded, and start the application software after the verification is passed.
[0035] The secret key 0 and the secret key 2 are decryption keys and are pre-stored in Flash, and the secret key 1 is a signat...
Embodiment 2
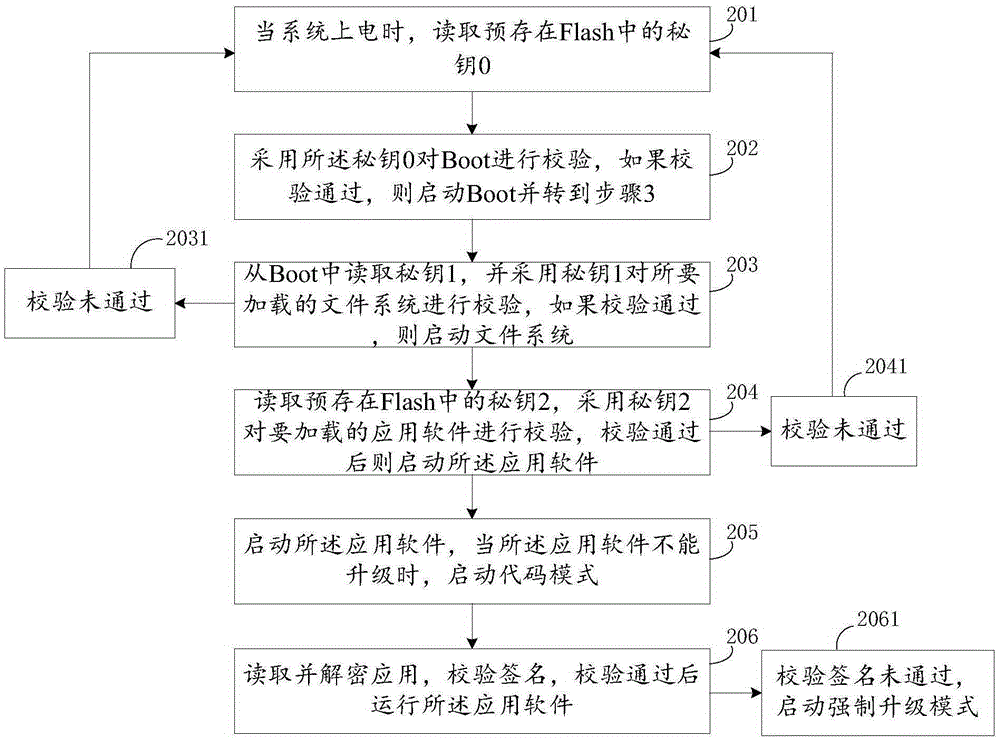
[0038] see figure 2 , is a schematic diagram of a method for starting an application software of a smart terminal according to Embodiment 2 of the present invention.
[0039] Such as figure 2 As shown, a smart terminal application software calling method includes:
[0040] 201 Step 1: When the system is powered on, read the secret key 0 pre-stored in the Flash;
[0041] 202 step 2: use the secret key 0 to verify the Boot, if the verification is passed, start the Boot, and go to step 3;
[0042] 203 Step 3: Read secret key 1 from Boot, and use secret key 1 to verify the file system to be loaded, if the verification passes, start the file system, and go to step 4;
[0043] 204 Step 4: Read the secret key 2 pre-stored in the Flash, use the secret key 2 to verify the application software to be loaded, and start the application software after the verification is passed.
[0044] Further, step 3 of 203: read the secret key 1 from the Boot, and use the secret key 1 to verify th...
Embodiment 3
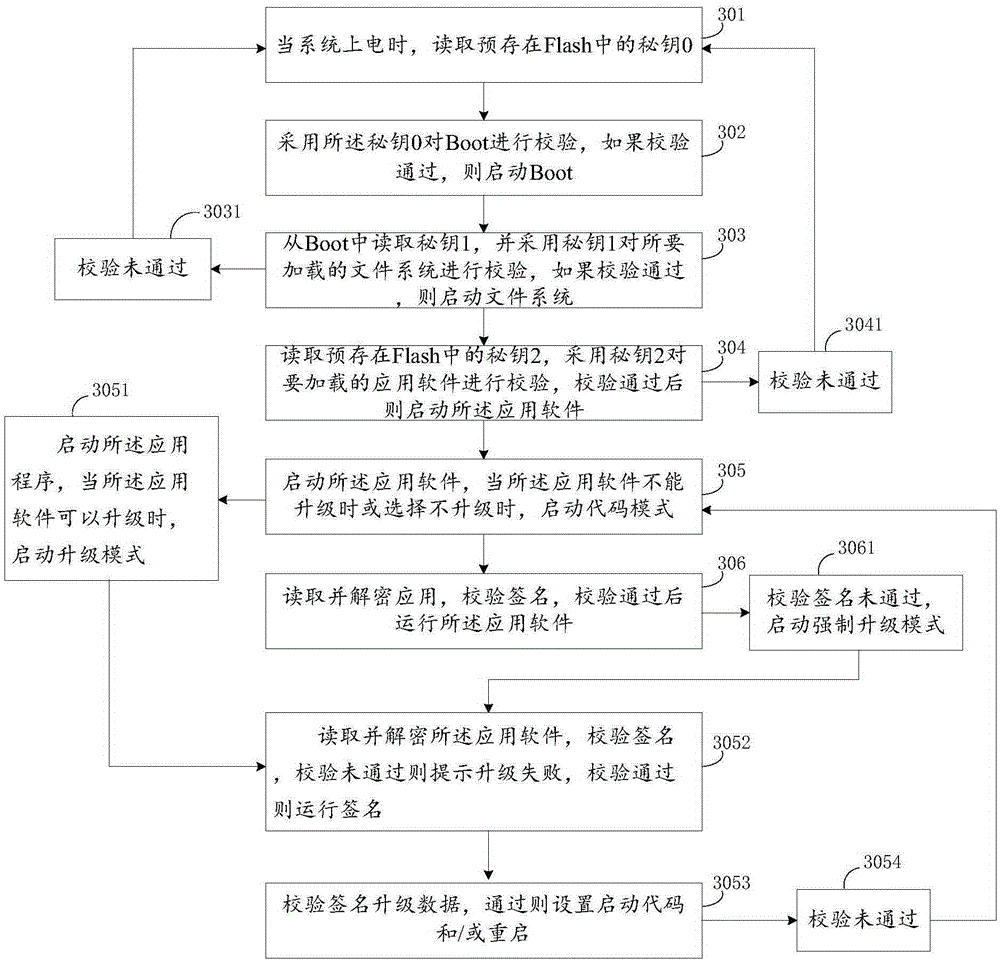
[0055] see image 3 , is a schematic diagram of a method for starting and / or upgrading application software of a smart terminal according to Embodiment 3 of the present invention.
[0056] Such as image 3 As shown, a smart terminal application software calling method includes the following steps:
[0057] 301 Step 1: When the system is powered on, read the secret key 0 pre-stored in the Flash;
[0058] 302 step 2: use the secret key 0 to verify the Boot, if the verification is passed, start the Boot, and go to step 3;
[0059] 303 Step 3: Read secret key 1 from Boot, and use secret key 1 to verify the file system to be loaded, if the verification passes, start the file system, and go to step 4;
[0060] 304 Step 4: Read the secret key 2 pre-stored in the Flash, use the secret key 2 to verify the application software to be loaded, and start the application software after the verification is passed.
[0061] Further, step 3 of 303: read the secret key 1 from the Boot, and u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com