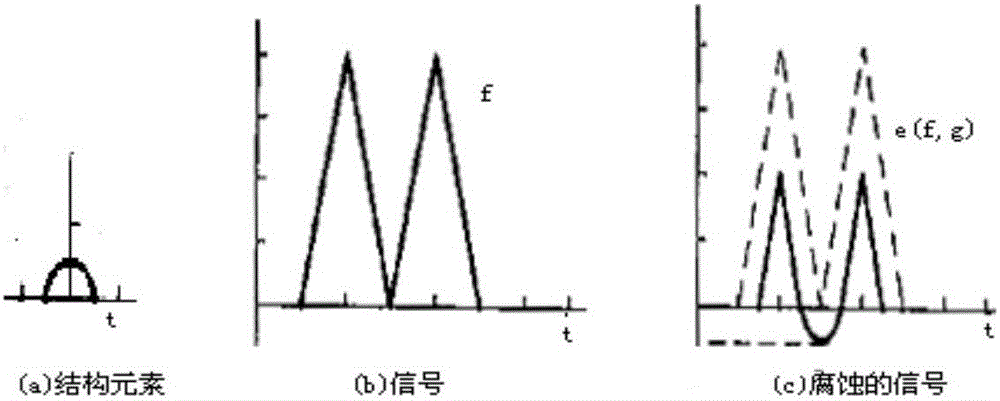
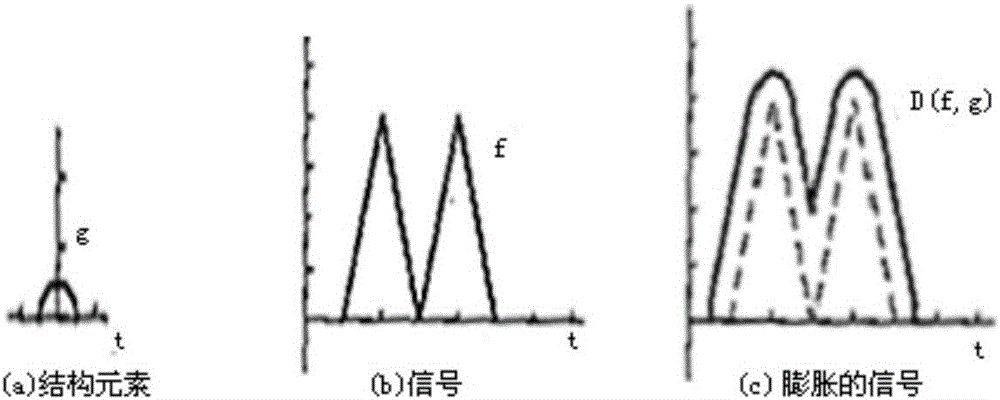
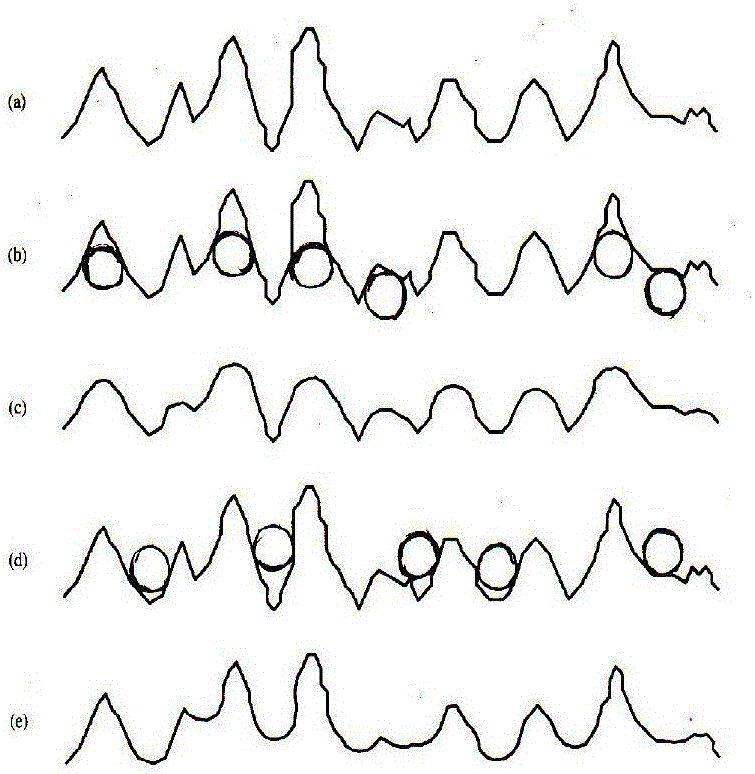
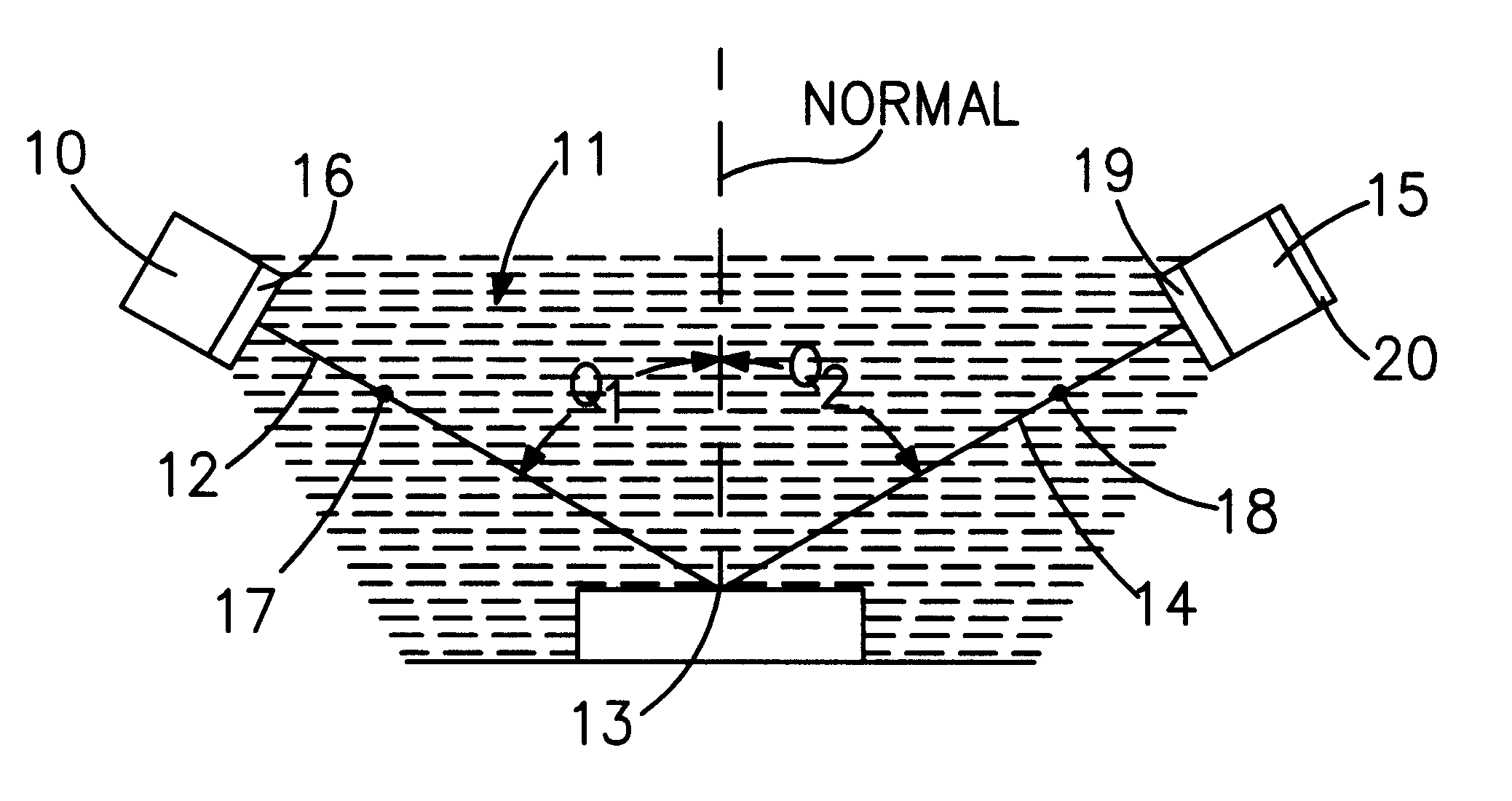
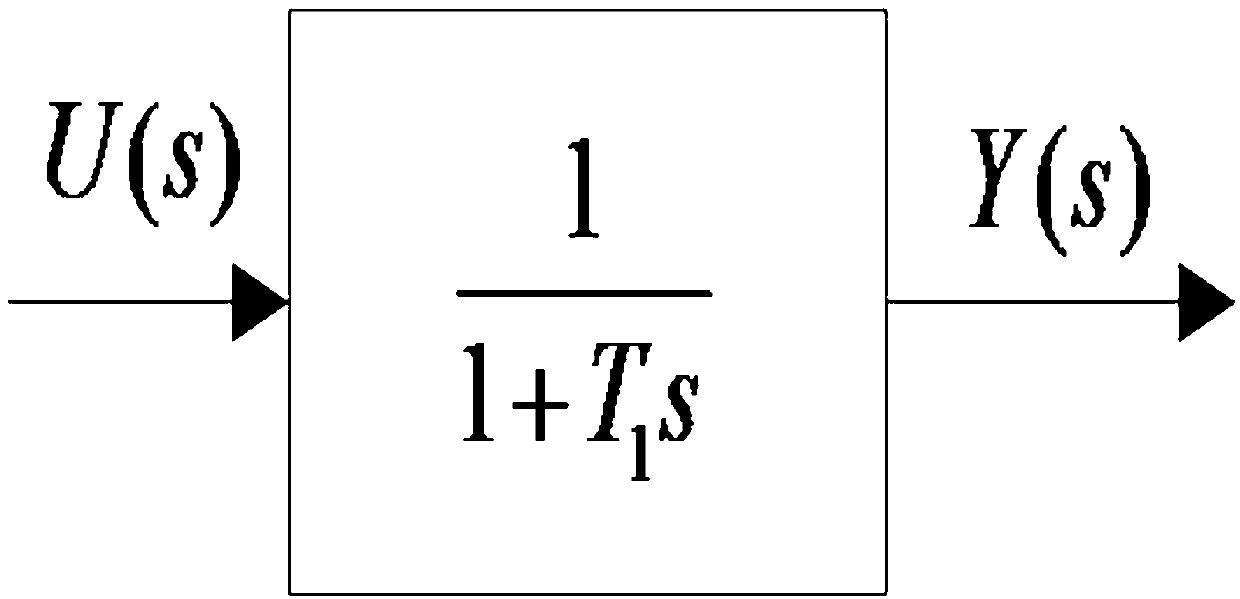Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
260 results about "Identifiability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In statistics, identifiability is a property which a model must satisfy in order for precise inference to be possible. A model is identifiable if it is theoretically possible to learn the true values of this model's underlying parameters after obtaining an infinite number of observations from it. Mathematically, this is equivalent to saying that different values of the parameters must generate different probability distributions of the observable variables. Usually the model is identifiable only under certain technical restrictions, in which case the set of these requirements is called the identification conditions.
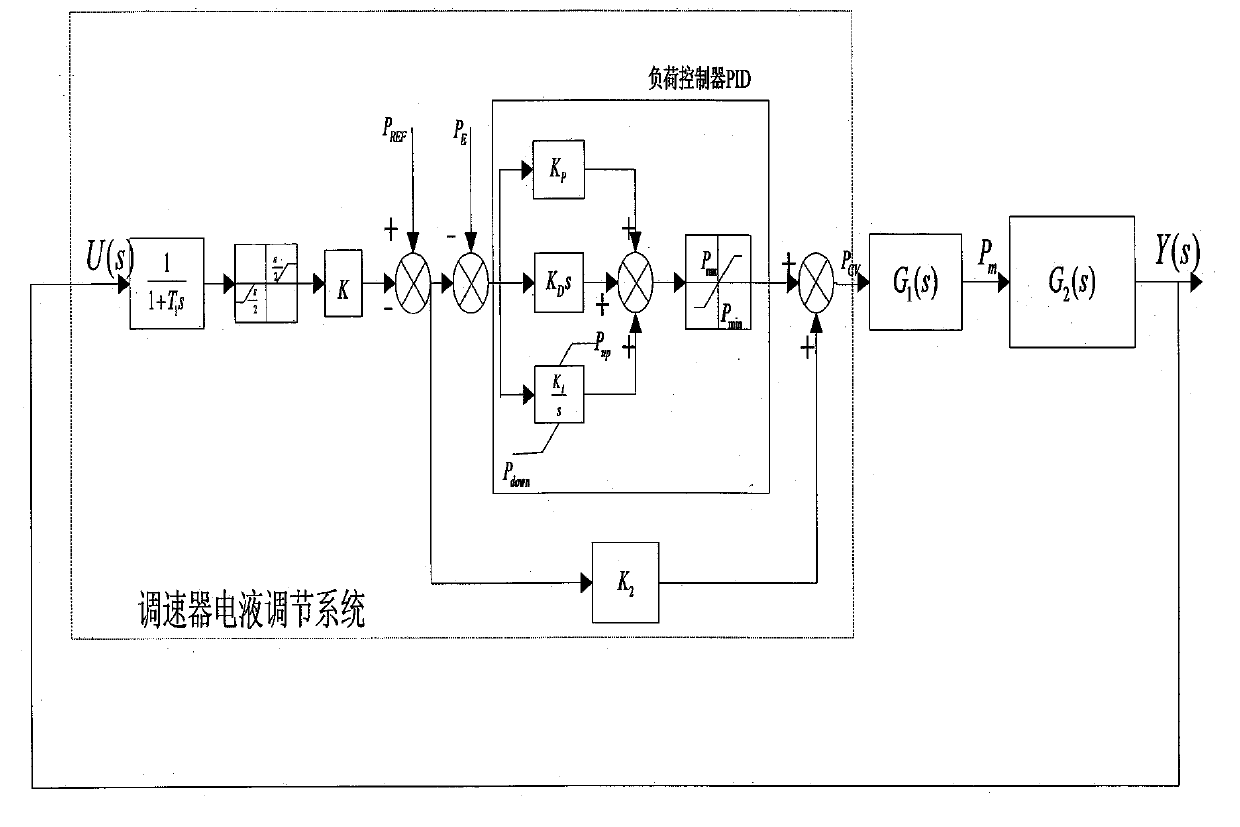
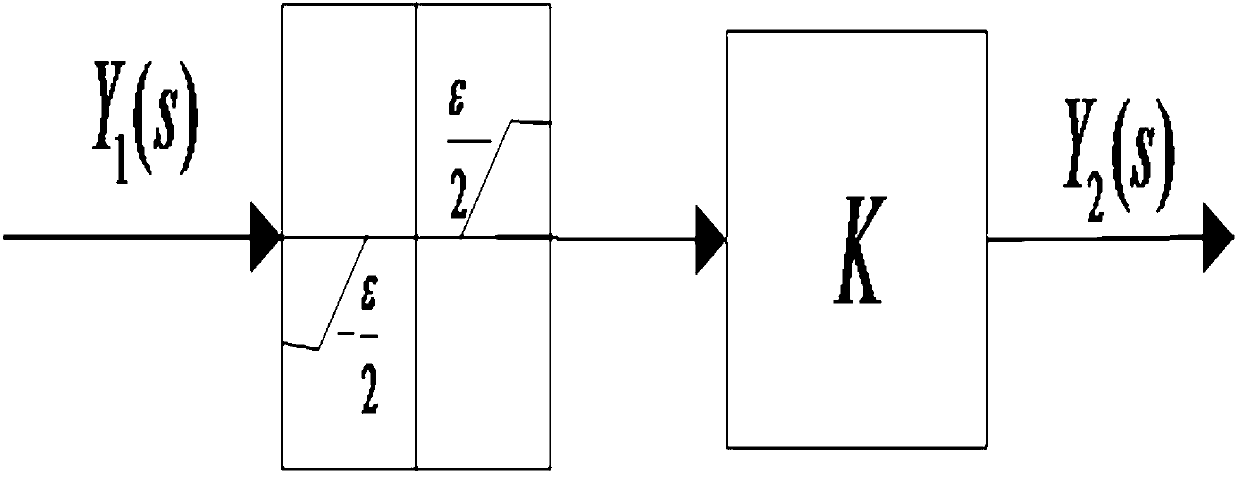
Power system load modelling method
ActiveCN101789598ASingle network parallel feeding arrangementsSpecial data processing applicationsSynthesis methodsLoad model
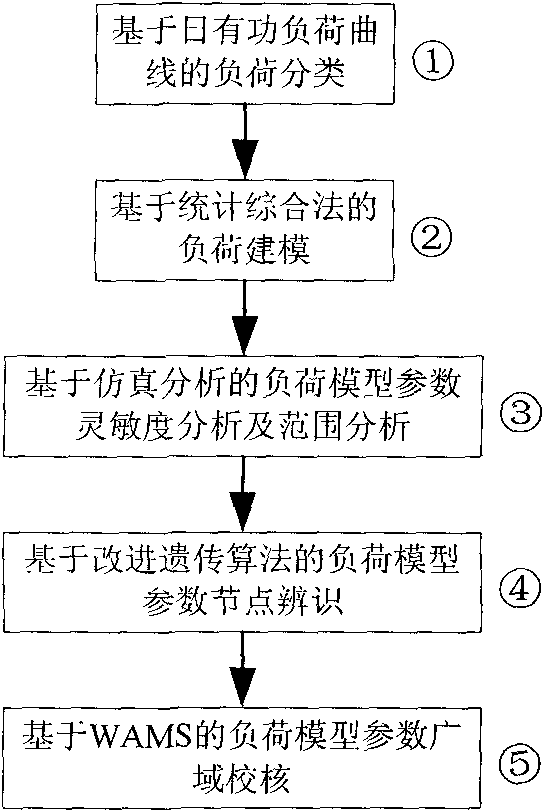
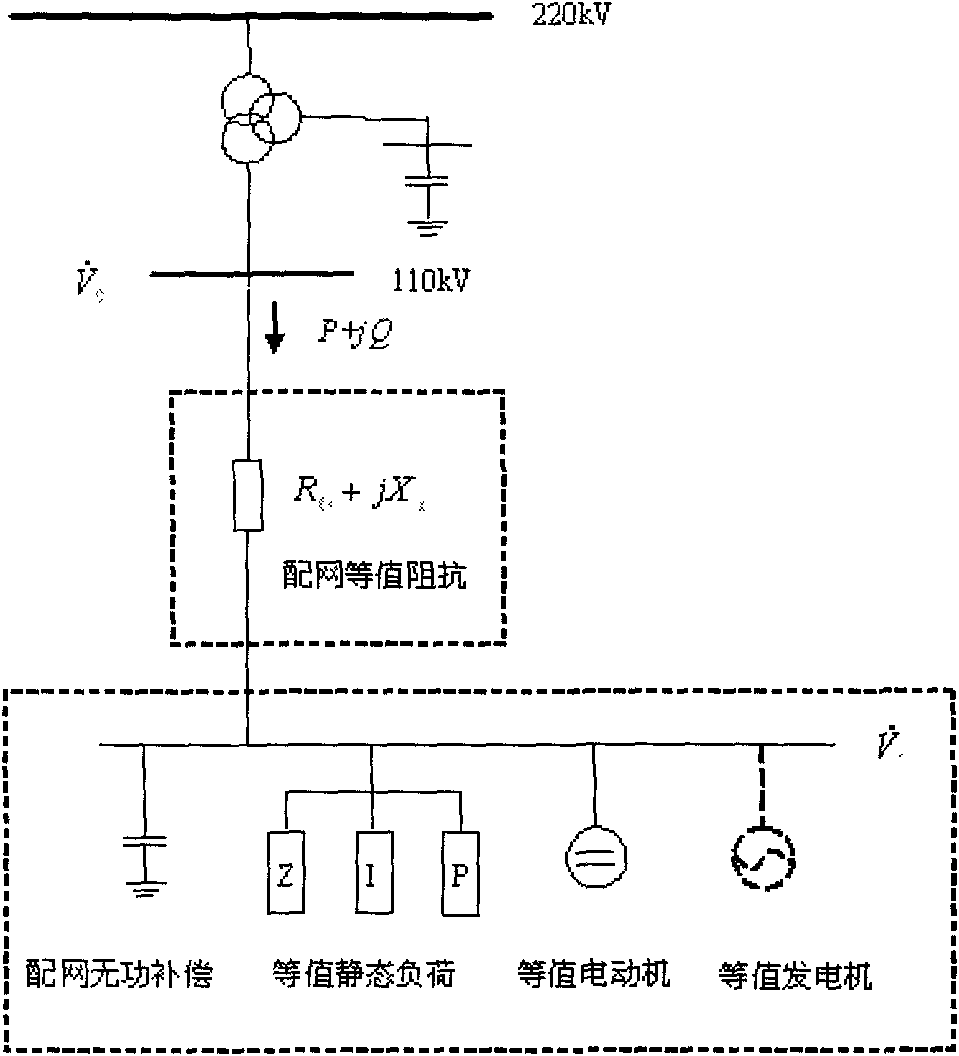
The invention discloses a power system load modelling method, including the steps that: A, load classification based on daily active load curve; B, load modelling based on statistic synthesis method; C, load model parameter sensitivity analysis and range analysis based on simulation analysis; D, load model parameter node identification based on genetic algorithm, namely node identification is carried out by taking fitted local disturbance data as target, setting low sensitivity parameter value as statistic synthesis method surveying parameter value and adopting the genetic algorithm, so as to obtain multiple groups of load model parameters; E, load model parameter wide area check based on WAMS, namely load model parameter check is carried out by taking the multiple groups of solutions identified by node as initial value and taking accurate fitting on system wide area dynamic characteristic as target, so as to obtain unique solution capable of reflecting wide area dynamic characteristic when system is subject to disturbance. The invention solves the problems of multiple solutions and identifiability of overall measuring identifying method by load point classification and load model parameter aggregation and has popularization and application values.
Owner:STATE GRID HUBEI ELECTRIC POWER RES INST +1
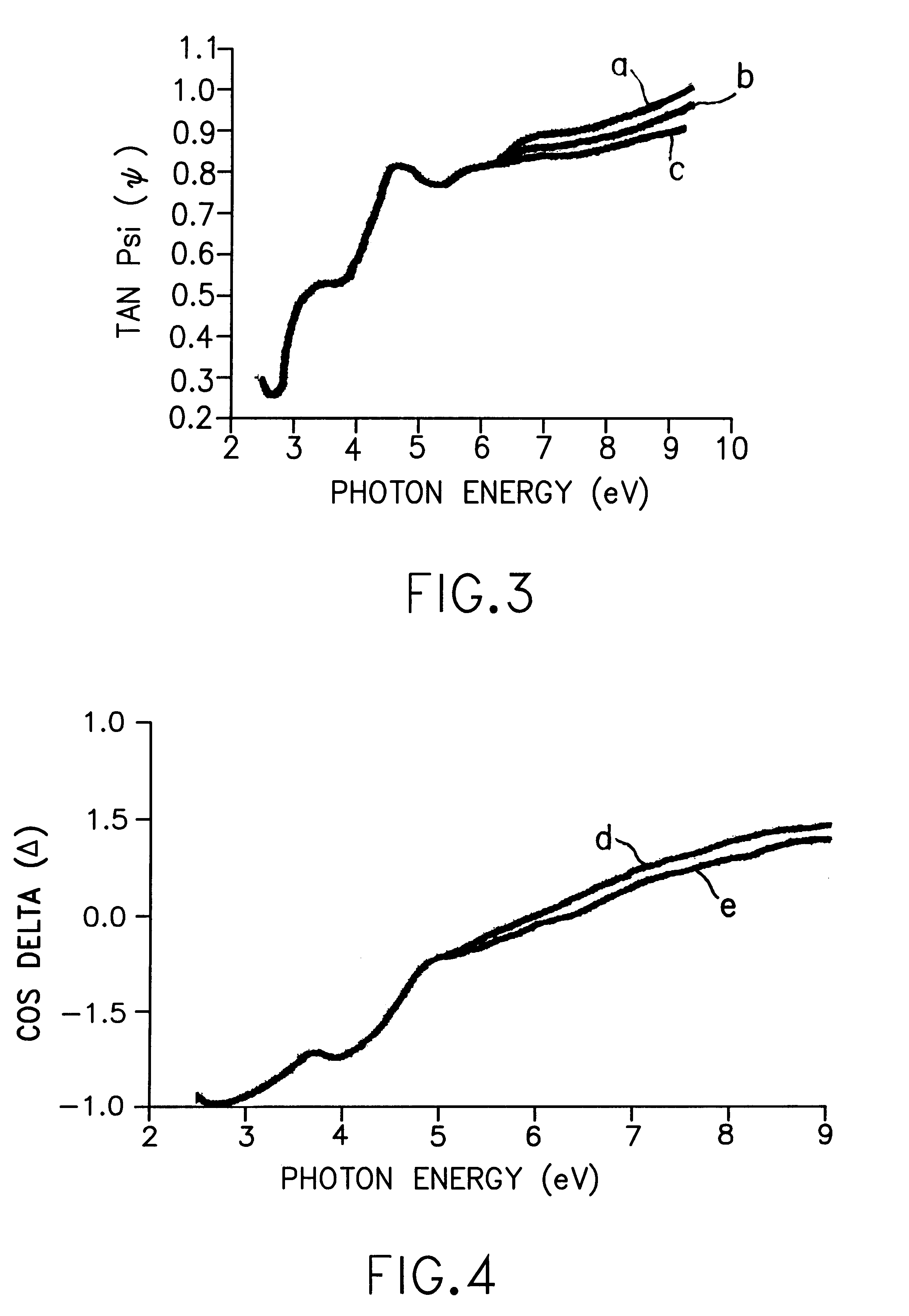
High photon energy range reflected light characterization of solids
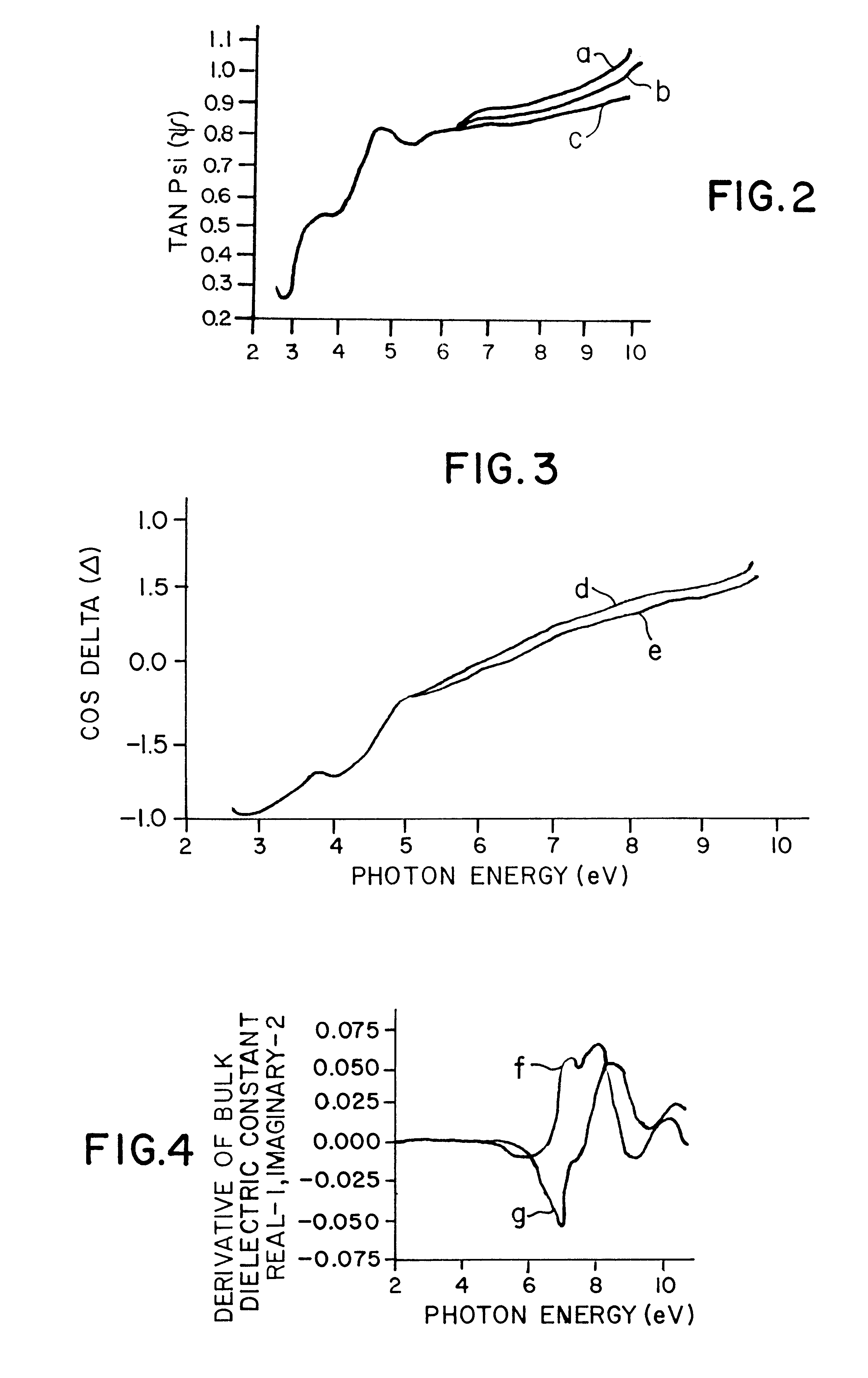
InactiveUS6414302B1Polarisation-affecting propertiesPhotoelectric discharge tubesMetrologyIdentifiability
Accuracy and sensitivity in the optical characterization of solids and solid materials are improved through the use of the interdependent features of: extending the photon energy range over which the metrology is performed to include a portion of the range up through 10 eV, in which, the higher photon energy of the light improves signal distinguishing ability; and providing a controlled ambient in the entire light path between the light source and a detector that prevents absorption and signal definiteness masking so as to sharpen the identifiability of the change parameters imparted into the reflected light. Combinations of specific devices and materials that for different types of ellipsometry are provided.
Owner:JORDAN VALLEY SEMICON
Authentication system
InactiveUS20060158820A1Increase freedomUser identity/authority verificationPerson identificationBiological bodyEngineering
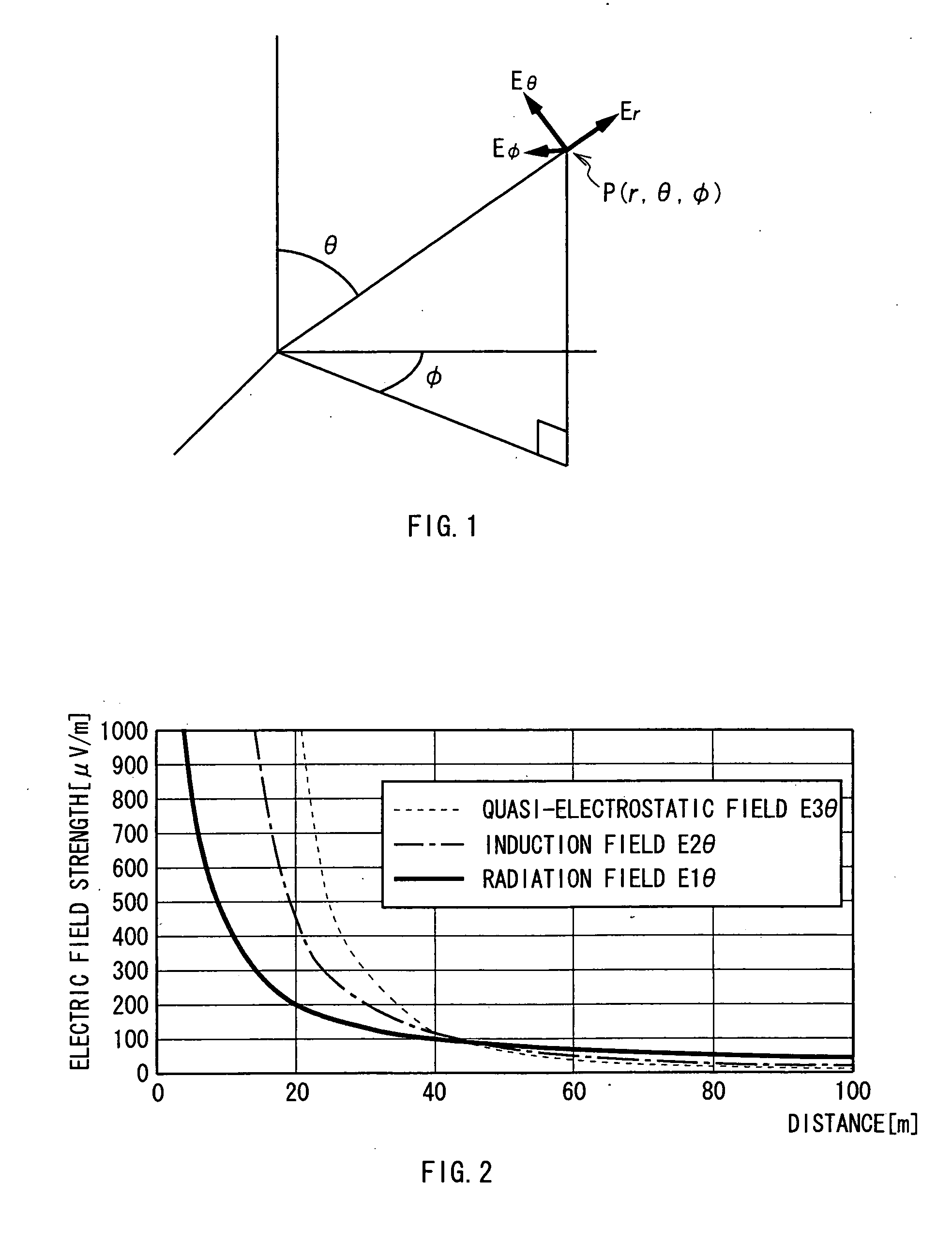
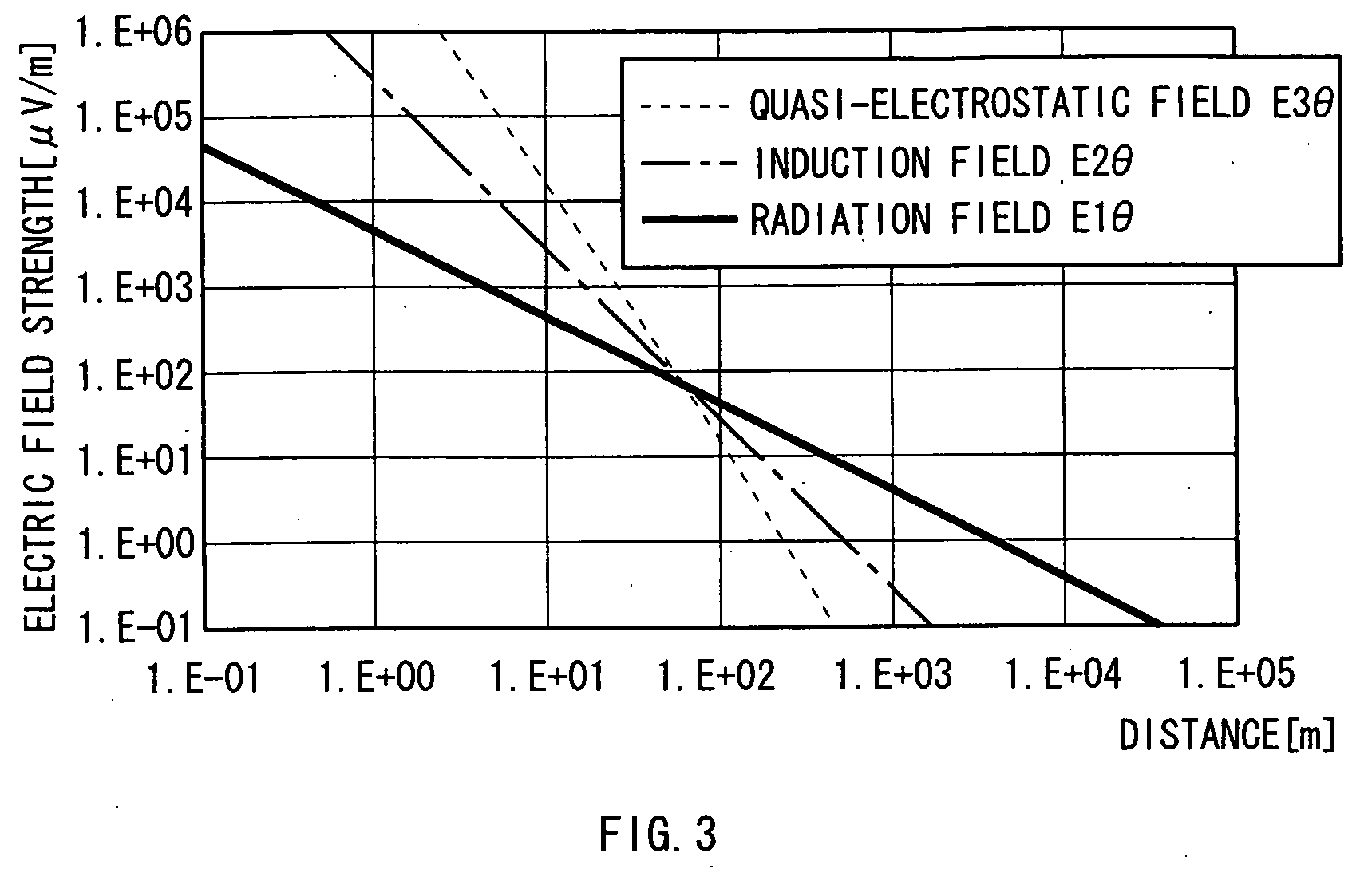
The present invention enables the degree of freedom in communication to be enhanced. According to the present invention, in an authentication system 1, during a walking motion of a user which is essentially required for the user to pass through an entrance / exit passage portion 4 (FIG. 6), tissue information D5 and walking information D7 as living organism identification information, a pattern specific to a user, is detected from an detection electrode 52 via an FET 11, based on a walking quasi-electrostatic field HSE formed in the neighborhood of the user. Thereby, information with high identifiability specific to the user can be obtained without controlling movements of the user and without performing special processing such as encryption. Thus, the degree of freedom in communication can be enhanced.
Owner:SONY CORP
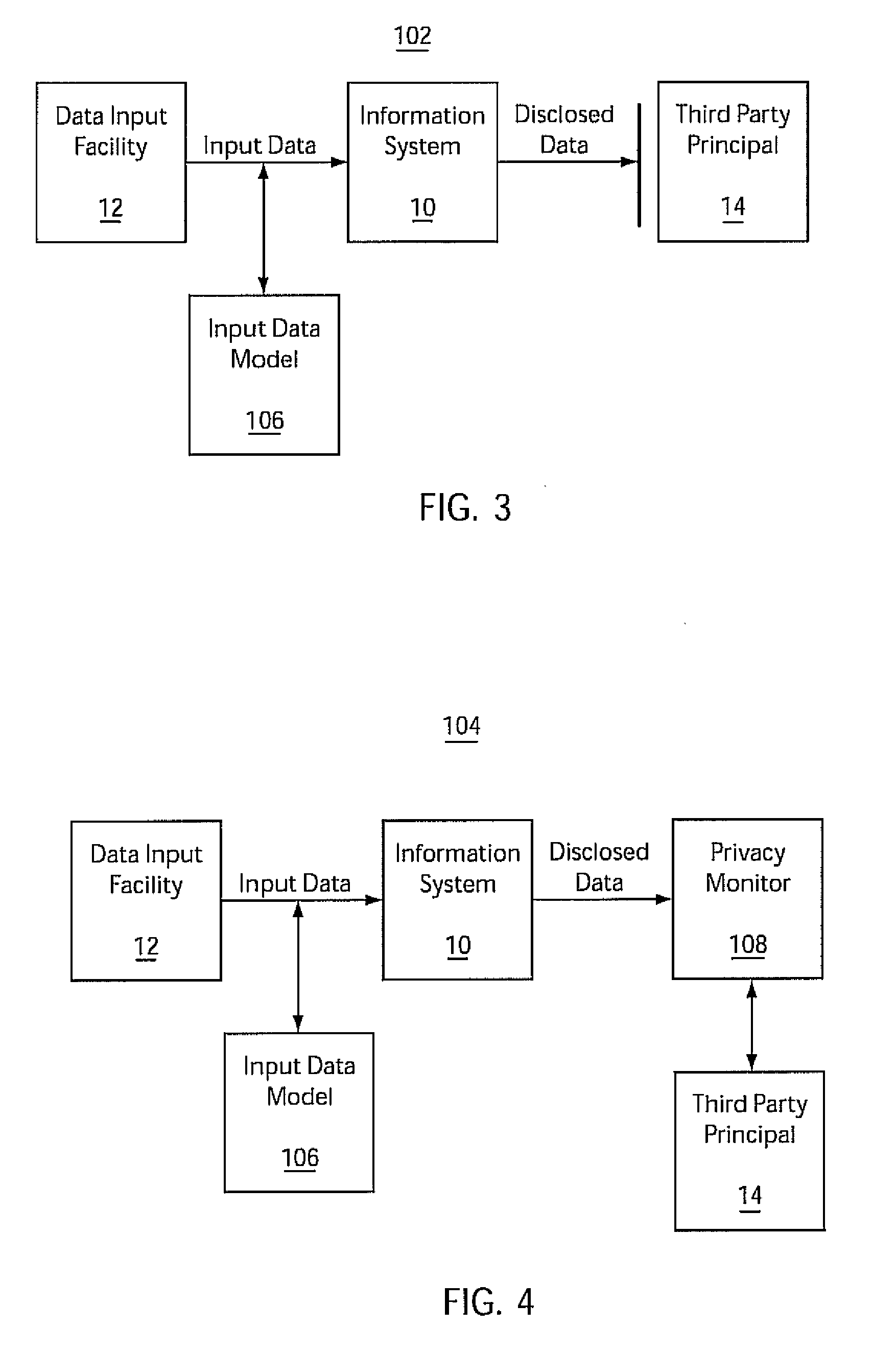
System and method for privacy protection using identifiability risk assessment
InactiveUS20090228990A1Mitigate unauthorized disclosure of the recordsDigital data processing detailsAnalogue secracy/subscription systemsThird partyPrivacy protection
Owner:INT BUSINESS MASCH CORP
Unmanned helicopter flight control system with fault diagnosis ability
PendingCN106406353AIncrease hardware redundancyImprove reliabilityElectric testing/monitoringPosition/course control in three dimensionsOperational systemSystems management
The invention discloses an unmanned helicopter flight control system with a fault diagnosis ability. The hardware device is composed of a navigation / flight control computer system, a sensor system, an execution mechanism system, a remote control and remote measurement system and a power supply system, wherein the navigation / flight control computer system is an active / standby dual-redundancy system; the sensor system provides sensor information for the navigation / flight control computer system; the remote control and remote measurement system is directly connected with an actuator system through remote control autonomous conversion; and the power supply system provides power for the sensor system, the navigation / flight control computer system and the remote control and remote measurement system. The software structure comprises a bottom operation system, a data I / O module, system management software, redundancy management software, flight control software, navigation control software and task execution software. Through adding the hardware redundancy to the flight control system of the invention, thereby enhancing the reliability; the retention of the remote control system can handle emergency states and non routine tasks; and due to the adding of the fault diagnosis method, the fault identifiability is enhanced.
Owner:BEIHANG UNIV
Morphological filtering-based electrical imaging reservoir fracture and cave body quantitative characterization method and system
ActiveCN106443802AImprove signal-to-noise ratioEasy to identifyElectric/magnetic detection for well-loggingAcoustic wave reradiationPore distributionMorphological filter
The present invention discloses a morphological filtering-based electrical imaging reservoir fracture and cave body quantitative characterization method and system. The method includes the following steps that: 1) noise suppression and blank band encryption interpolation are performed on original electric imaging logging data to obtain full-coverage rate electrical imaging logging data; 2) structural elements of appropriate shapes and scales are selected, and morphological filtering is performed on the obtained electrical imaging logging data in the step 1), so that fracture and cave pore distribution of different scales can be determined; and 3) the proportion of the porosity of fractures and the proportion of the porosity of corroded caves are calculated according to the fracture and cave pore distribution of different scales, so that a fracture and cave porosity spectrum which can indicate pore throat size and porosity distribution relationships can be obtained. According to the method of the invention, a mathematical morphological filtering method is introduced into imaging logging data processing; based on the filtering and anomaly recognition technologies of conductivity signals of different scales, the signal-to-noise ratio and identifiability of fracture and cave abnormal signals are improved; and exact information such as intuitive fracture and cave shapes and scale distribution can be provided for the processing and interpretation of electrical imaging logging data.
Owner:CHINA PETROLEUM & CHEM CORP +4
Ultrathin layer measurement having a controlled ambient of light path
InactiveUS6222199B1Polarisation-affecting propertiesInvestigating moving sheetsMetrologyFrequency spectrum
Metrology for ultrathin dielectric layers of the order of less than 10 nanometers in thickness is achieved by specular ellipsometry in a totally controlled ambient between the light source and the detector, in which, a precise 2.75 through 9.0 eV photon energy range continuum of light is employed. In the signal analysis there is the taking into consideration the effect of noise in the development of the ellipsometric parameter values and in the resulting data. In the invention the precise photon energy range operates to sharpen the identifiability of the change parameters imparted into the reflected light in the ellipsometry while minimizing absorption and signal definiteness masking; and the taking into consideration of noise in the signal analysis involves providing a simulated noise spectrum for comparison with the least squares fitting algorithm-derived parameters to determine the quality of the minimum and the reliability of the inferred parameters.
Owner:JORDAN VALLEY SEMICON
Realization method and device of fingerprint comparison in financial IC (integrated circuit) card
InactiveCN102222389AAchieve consistencyAchieve uniquenessCo-operative working arrangementsCoded identity card or credit card actuationIntegrated circuit layoutCard holder
The invention relates to a realization method and a device of fingerprint comparison in a financial IC (integrated circuit) card. The device for the fingerprint comparison in the financial IC card comprises a fingerprint and IC card reading and writing integration device (hereinafter referred to as integration device), a PC machine or terminal, and a bank background, wherein the integration device and the PC machine or the terminal are connected by a Rs232 or a USB interface of a switching board; the PC machine or the terminal communicates with the bank background by a TCP / IP (transmission control protocol / internet protocol) mode; and the realization process comprises three parts, such as fingerprint template registration, comparison in a fingerprint character IC card and secondary authentication of a background server. The invention has the beneficial effects that the problems that the data exchange is inconvenient and the data transmission can be not standardized in the existing bank fingerprint payment service are solved; fingerprint data extraction and the authenticity, the integration and the identifiability in the transformation process are guaranteed by the digital signing technology; dual-factor authentication based on the biological character recognition is formed by body authentication of an IC medium and the fingerprint comparison of a card holder; and the promotion and use difficulties of the fingerprint recognition technology in a bank service system is reduced, and the security is enhanced.
Owner:BEIJING TECHSHINO TECH
System and method for privacy protection using identifiability risk assessment
InactiveUS20080005778A1Mitigate unauthorized disclosure of the recordsOffice automationSpecial data processing applicationsThird partyPrivacy protection
A risk assessment system and method includes an information system configured to disclose information to a third party. A risk determination model is configured to compute identifiability risk for on one or more records in storage. The identifiability risk is compared to a threshold prior to being disclosed wherein the information system is informed of the identifiability risk exceeding the threshold prior to disclosure to the third party.
Owner:IBM CORP
Virtu identifying method based on texture analysis
InactiveCN101582162AWill not damage the structureRealize authenticity identification functionImage analysisFeature vectorIdentifiability
The invention discloses a virtu identifying method based on texture analysis, which comprises the following steps: selecting an acquiring point with identifiability on a genuine virtu, recording the position information of the acquiring point, obtaining a matching datum image of the acquiring point; obtaining a matching identification image of the corresponding acquiring point on an identified virtu according to the position information of the acquiring point of the genuine virtu; obtaining texture characteristic points of the matching datum image and the matching identification image based on a Gaussian kernel finite difference operator; appointing a plurality of directions of each texture characteristic point according to the gradient directions of adjacent points in a neighborhood; leading each texture characteristic point to obtain at least 32-dimension characteristic vectors based on the accumulated gradient directions of a plurality of adjacent points in the neighborhood; and using Euclidian distance of the characteristic vectors of the texture characteristic points as a similarity determination measurement of the image. The identifying method realizes the truth identification function through the uniqueness of the texture of the virtu without adding additional materials and damaging the structure of the virtu, and is easy to popularize and apply.
Owner:上海锦渡信息科技有限公司
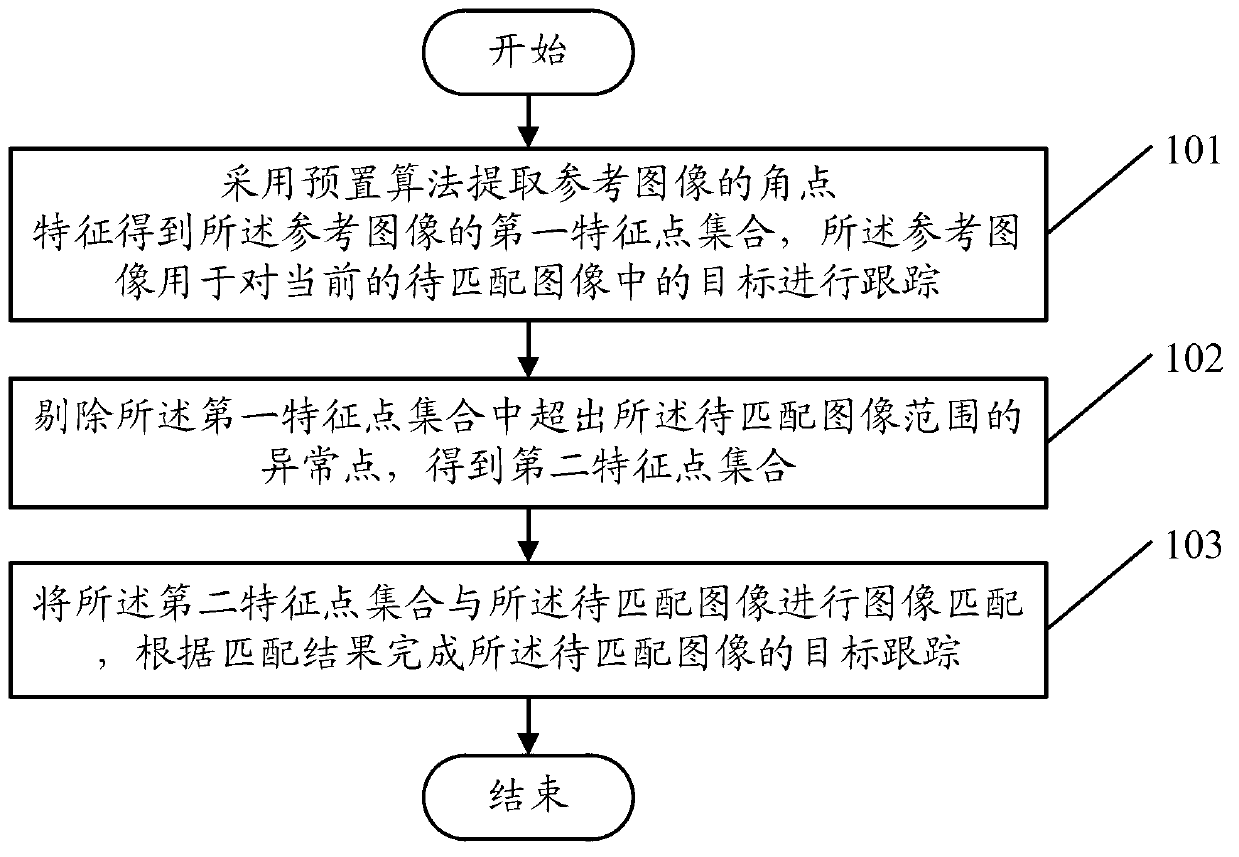
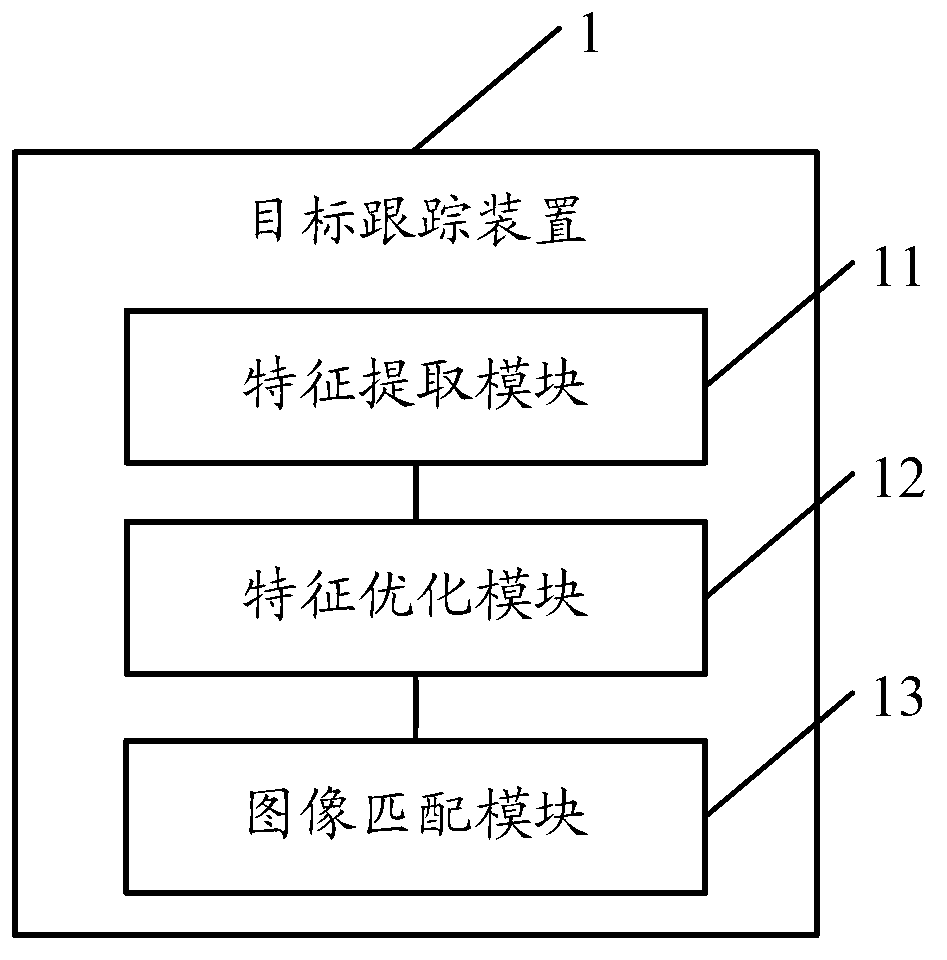
Target tracking method and device
ActiveCN103279952AGood recognition effectImprove stabilityImage analysisReference imageImage matching
The embodiment of the invention discloses a target tracking method, which comprises the steps of using a presetting algorithm to extract the corner feature of a reference image to obtain the first feature point set of the reference image, removing abnormal points which exceed the range of images to be matched from the first feature point set to obtain a second feature point set, matching the second feature point set with the images to be matched and finishing the target tracking of the images to be matched according to matching results. The embodiment of the invention additionally discloses a target tracking device. By using the target tracking method and the target tracking device, the extracted corner feature has good identifiability and stability, the matching speed is greatly improved, the feature point set of the reference image is optimized, the corners which exceed the range are removed, the problem that the matching cannot be realized due to a reason that the feature points exceed the range in the prior art is solved and the matching reliability is improved.
Owner:瑞得银纺(南通)信息技术有限公司
Tripolycyanamide molecular imprinting electrochemical sensor and preparation method thereof
InactiveCN102901756AReduce electrochemical activityImprove electrochemical activityMaterial electrochemical variablesCross-linkFunctional monomer
The invention discloses a tripolycyanamide molecular imprinting electrochemical sensor and a preparation method thereof. A molecular imprinting technology and an electro-analysis chemical detection technology are combined, the tripolycyanamide serves as template molecules, methacrylic acid serves as functional monomer, rosin which is the featured resource of Guangxi is used, and maleated rosin ethylene glycol diacrylate synthesized by using the rosin as the raw material serves as a cross-linking agent. The tripolycyanamide molecular imprinting electrochemical sensor can be used for measuring the content of the tripolycyanamide, and has high selection identifiability; and on the basis of the sensor, an electrochemical analyzing method for measuring the tripolycyanamide is simple and practical, and the shortcoming of complexity of the conventional method is overcome.
Owner:GUANGXI UNIV FOR NATITIES
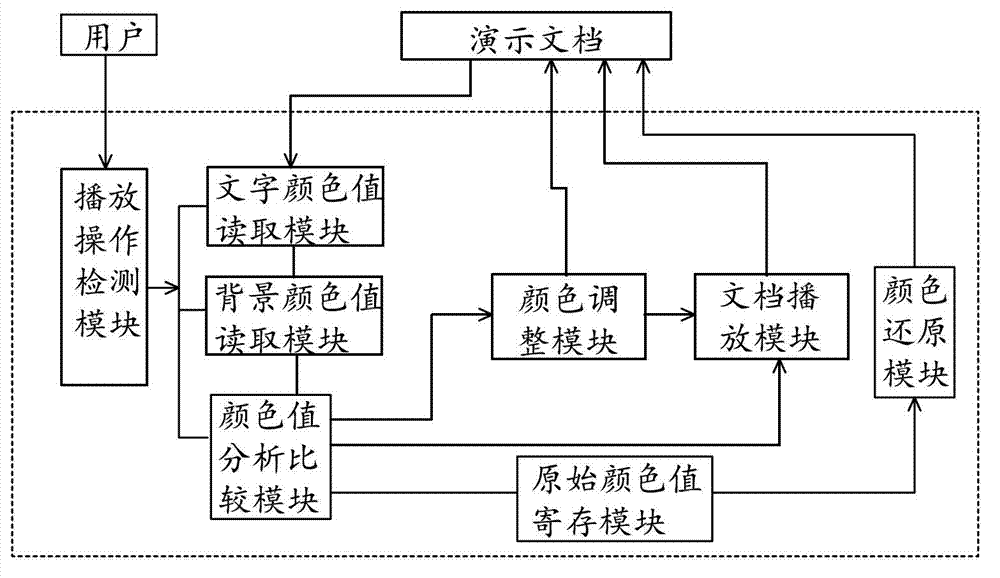
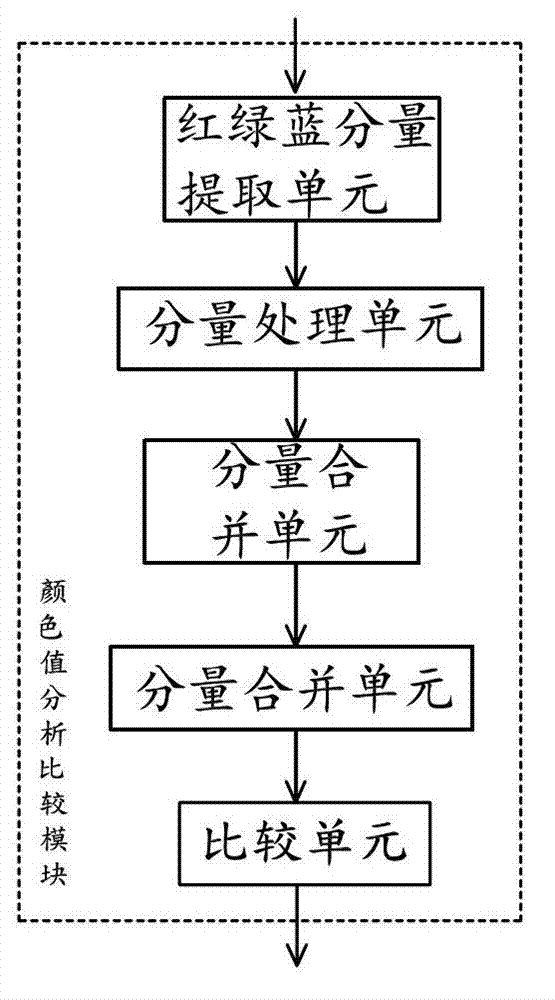
Method and system for adjusting colors of characters or backgrounds in presentation documents automatically
InactiveCN103049471ARecognizableSpecial data processing applicationsPattern recognitionDocumentation
The invention provides a method and system for adjusting colors of characters or backgrounds in presentation documents automatically. The method includes: detecting whether the presentation documents are played; reading color values of the characters and the backgrounds from codes of the presentation documents; analyzing approximation degree of the color values of the characters and the color values of the backgrounds, setting a temporary color value for the characters or the backgrounds in the presentation documents if the approximation degree is up to the standard required to adjust the colors, enabling color application chromatic aberration of the characters and the backgrounds to be large, and simultaneously depositing original color values of the characters and the backgrounds; playing the presentation documents according to current color values of the characters and the backgrounds; and detecting whether playing of the presentation documents is finished, and restoring colors of the characters or the backgrounds in the presentation documents into the original color values if on yes judgment. The method and system for adjusting the colors of the characters or the backgrounds in the presentation documents automatically can detect distinction degree of the character colors and the background colors automatically when the presentation documents are played. If the distinction degree is small, the character colors are adjusted automatically, the distinction degree of the character colors and the background colors is guaranteed, and identifiability is good.
Owner:ZHUHAI KINGSOFT OFFICE SOFTWARE +1
Solid oxide fuel cell stack fault diagnosis method and system
ActiveCN107180983AImprove accuracyEasy to identifySolid electrolyte fuel cellsFuel cellsStacking fault
The invention discloses a solid oxide fuel cell stack fault diagnosis method and system, wherein the method comprises: using an SOFC (solid oxide fuel cell) system model to simulate fault state and normal running state of a stack so as to obtain sample stack parameters under the fault state and normal running state of the stack; using the sample stack parameters to train a diagnosis model to obtain the strained diagnosis model; collecting real-time stack parameters, and entering in the trained diagnosis model to obtain a stack fault type. The SOFC system model is used herein to simulate the fault state and normal running state of the stack so as to obtain the stack parameters under the fault state and normal running state of the stack, and the collected stack parameters are entered in the trained diagnosis model to obtain one stack fault type. The diagnosis model herein is effective in diagnosing the normal running and fault type of the stack, the diagnostic results are highly accurate, and the method is high in practicality, identifiability and accuracy.
Owner:浙江国氢能源科技发展有限公司
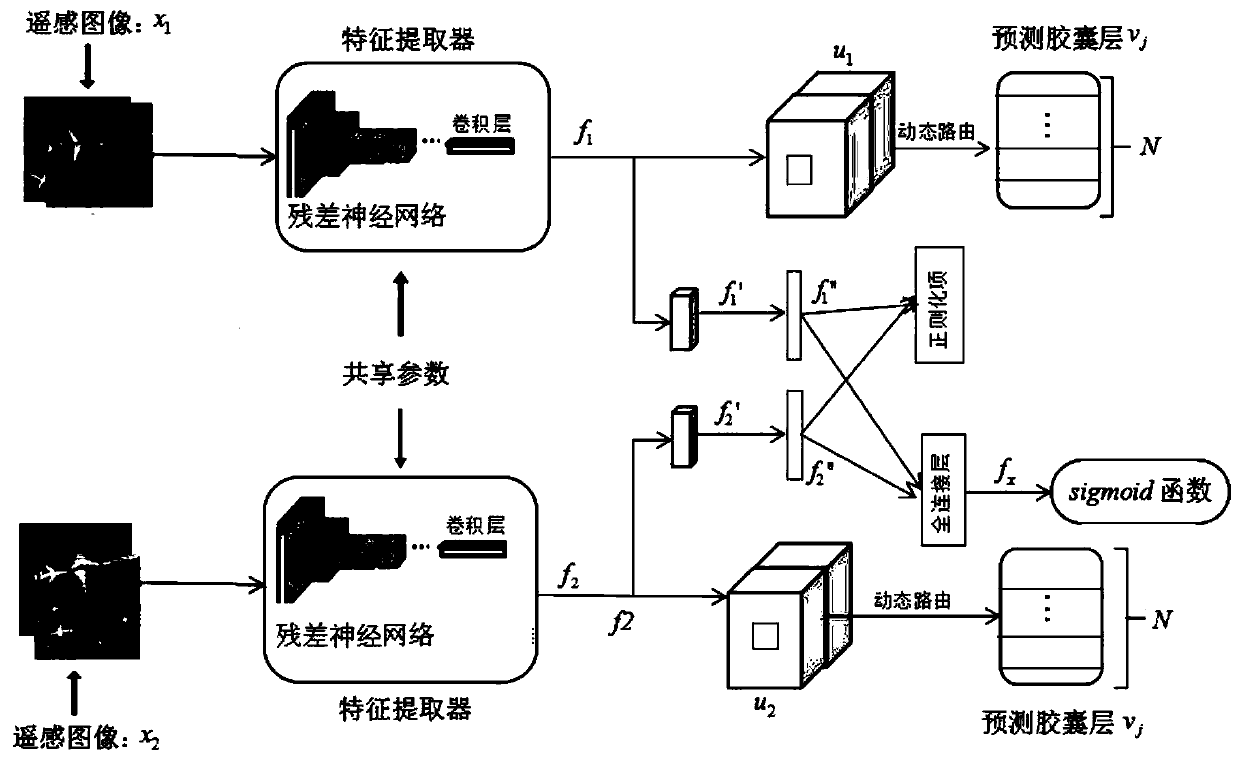
Convolutional neural network-based remote sensing image target detection method
ActiveCN110084195AEnhance expressive abilityEasy to identifyImage enhancementImage analysisData setAmbiguity
The invention discloses a convolutional neural network-based remote sensing image target detection method, and mainly solves the problems that a remote sensing target with an ambiguous appearance cannot be well identified and enough target semantic information cannot be obtained in the prior art. The method comprises the following implementation steps: 1, collecting remote sensing images to construct a data set, and dividing the data set into a training set and a test set; 2, constructing a network model, wherein the model comprises a feature extraction sub-network, an RPN candidate box generation network, a context information fusion sub-network and a multi-region feature fusion sub-network; 3, training the model by using the training set until the number of iterations of training is equal to a preset number of terminations; and 4, inputting the test image into the trained model to obtain a target detection result. The method can strengthen the expression capability of the characteristics, enriches the semantic information of the target, enables the target to have more identifiability, improves the detection precision, and can be used for resource exploration, disaster monitoringand remote sensing image target detection of urban planning.
Owner:XIDIAN UNIV
Doubly-fed induction generator parameter identification method
InactiveCN106169747AReduce the impactImprove recognition accuracySpecial data processing applicationsRenewable energy source integrationSystem of imprimitivityMATLAB
The invention discloses a Doubly-Fed Induction Generator (DFIG) parameter identification method, and belongs to the field of power system modeling. The DFIG parameter identification method comprises the following steps: firstly, determining an analytical expression of stator dq axis short circuit current under a condition of three-phase metal short circuit of a port of a doubly-fed induction generator, and determining parameters to be identified according to the analytical expression; building a single-machine infinite bus system of a doubly-fed wind turbine generator set based on a Matlab / Simulink platform, setting the three-phase metal short circuit at the port of the doubly-fed induction generator, and simulating to obtain a disturbed trajectory of the stator dq axis short circuit current; analyzing the identifiability of each parameter to be identified and the complexity for parameter identification by adopting a trace sensitivity method; and finally, identifying all the parameters to be identified by adopting a particle swarm optimization algorithm, and determining parameter identification values according to multiple identification results. Compared with a method based on active power and reactive power, the doubly-fed induction generator parameter identification method for DFIG parameter identification based on the stator dq axis short circuit current has the advantage that the influence caused by the current transformer control procedure is low; and the parameter identification values are determined according to the multiple parameter identification results, so that the problem of large errors possibly caused by single identification is avoided.
Owner:HOHAI UNIV
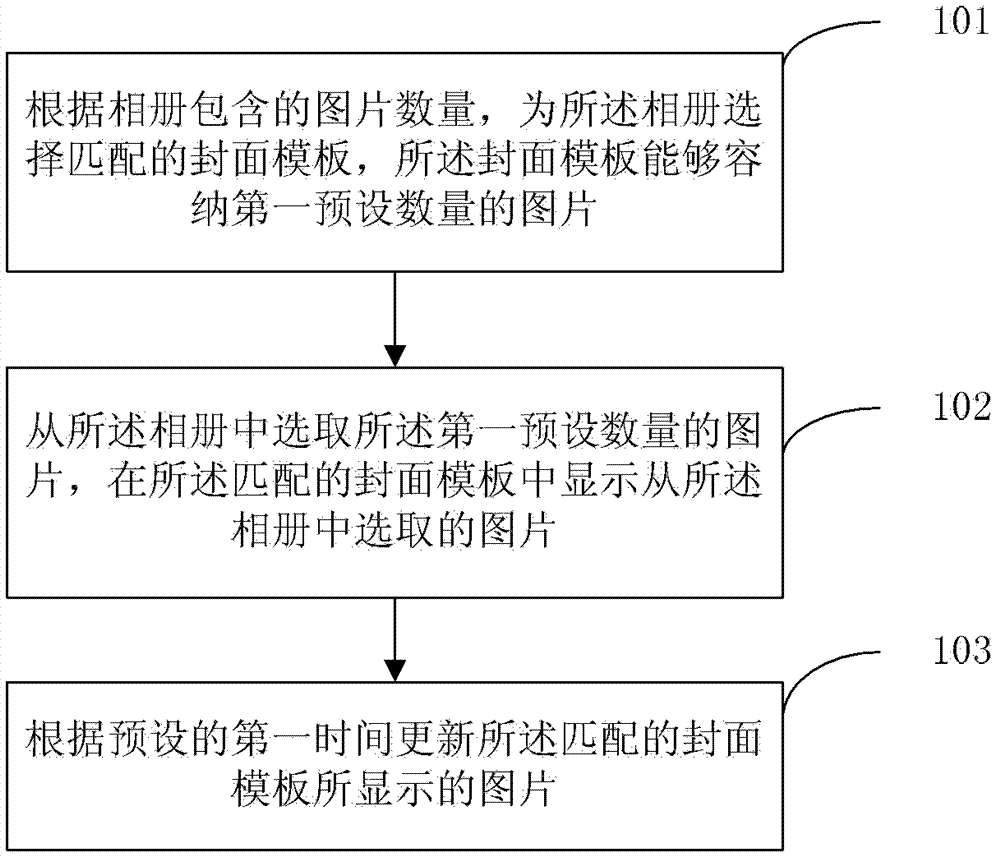
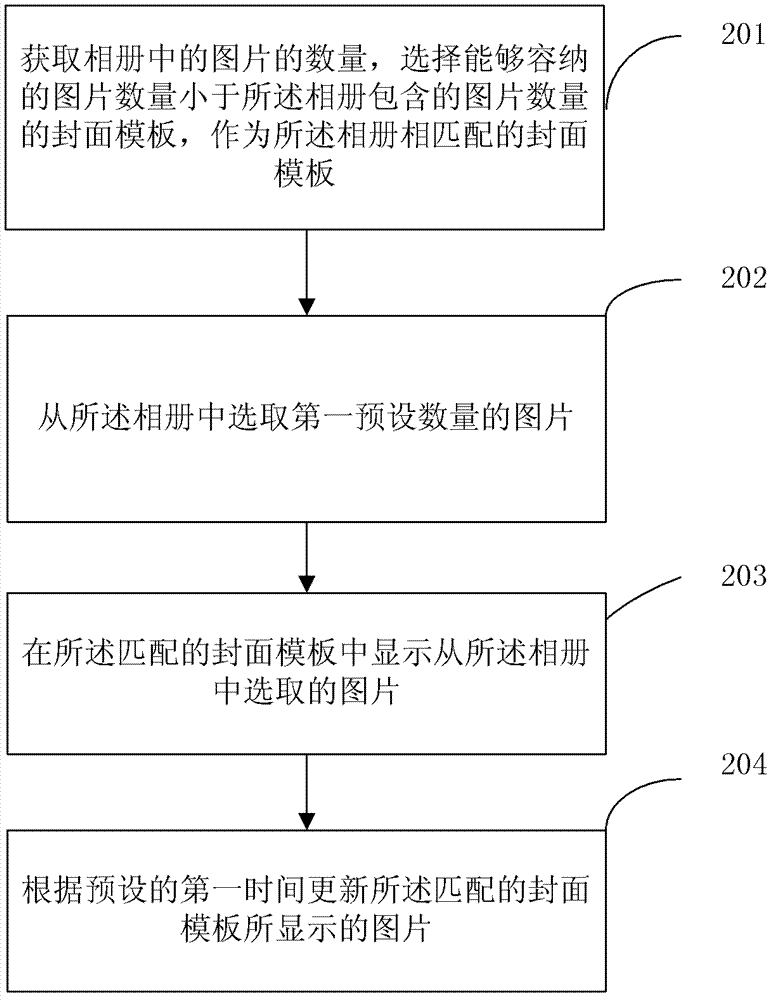
Photo album cover forming method and device
The invention discloses a photo album cover forming method and device and belongs to the technical field of communication. The photo album cover forming method comprises selecting a matched cover template for an album according to the number of images included in the album to enable the cover template to hold images of a first preset number; selecting the images of the first preset number from the album and displaying the images selected from the album on a matched cover template; updating images displayed through the matched cover template according to the preset first time. According to the photo album cover forming method and device, images on the album cover is dynamically updated, so that a user can obtain more information about the album according to the album cover and user identifiability of the album is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
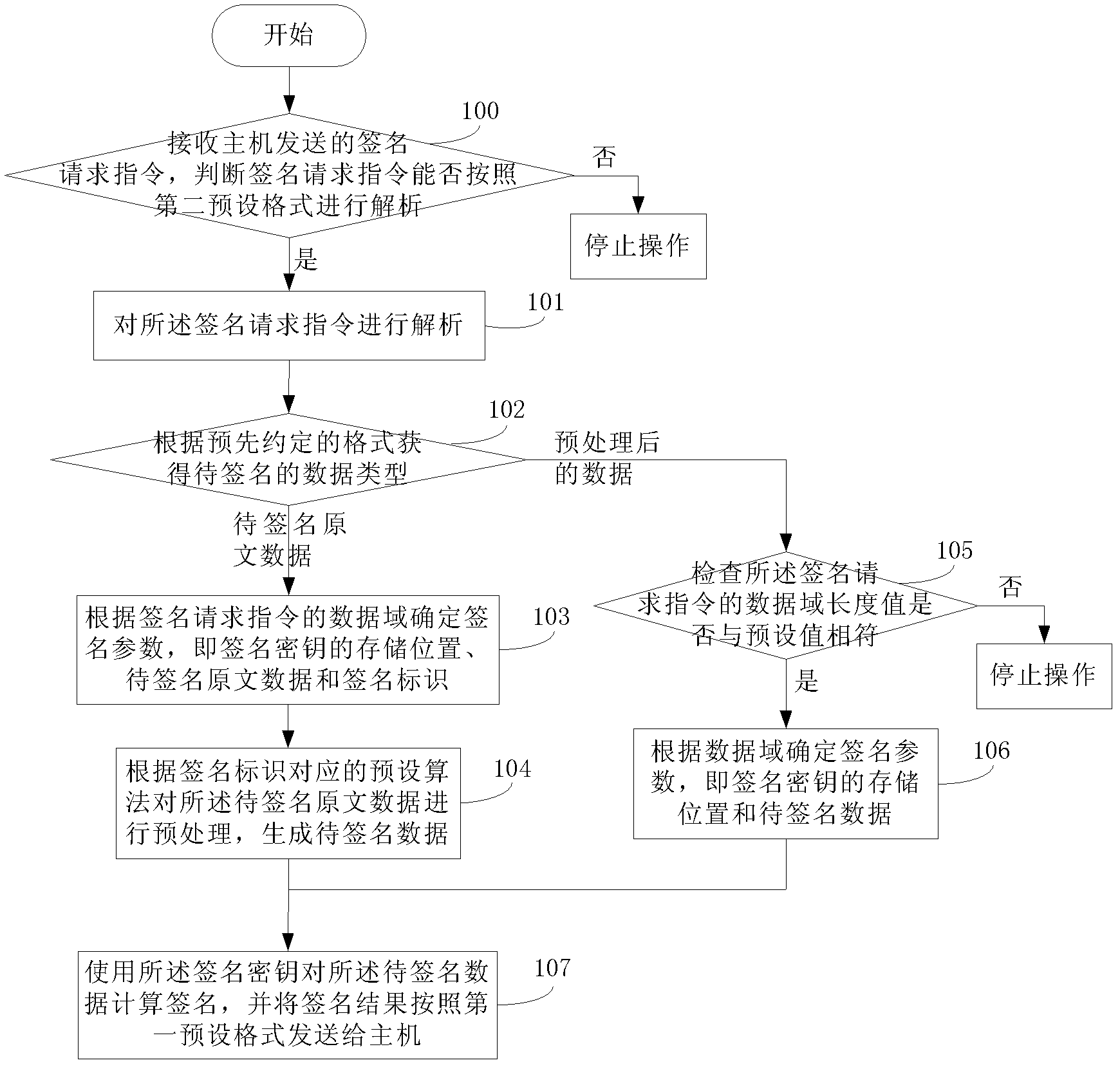
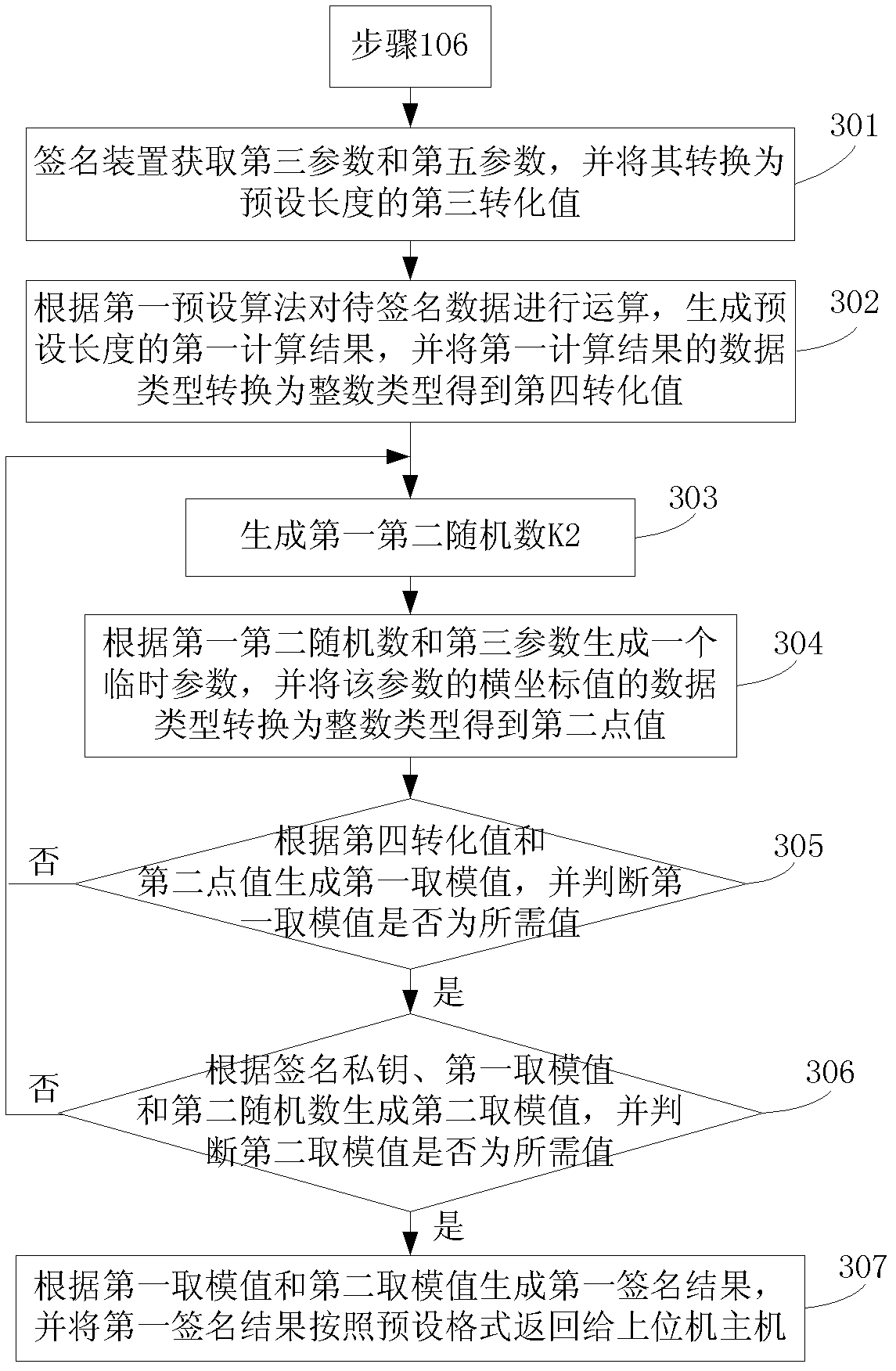
Signature realization method and signature realization device
ActiveCN102571357AHigh speedImprove securityUser identity/authority verificationData domainComputer science
The invention discloses a signature realization method and a signature realization device. The method comprises the following steps that: a receiving host machine sends signature request instructions, and in addition, the analysis is carried out according to preset rules; the type of data to be signed is detected according to the first part preset length, if the data to be signed is original text data to be signed, the storage position of a signature key, a signature mark and the original text data to be signed are determined according to data obtained through the analysis, the preprocessing is carried out on the user mark value and the user mark length in a data domain and the original text data to be signed according to the algorithm corresponding to the signature mark, and data to be signed is generated; if the data to be signed is pretreated data, when the data domain length value of the signature request instruction conforms to the preset vale, the storage position of the signature key and the data to be signed are determined according to the data domain; and the data to be signed is signed to generate signature results, and the signature results are sent to the host machine according to a first preset format. In the realization scheme of the method and the device provided by the invention, the safety and the identifiability of the signature are improved because of the participation of a signature public key and a user mark.
Owner:FEITIAN TECHNOLOGIES
Method for implementing computer terminal safety admittance based on credible authentication gateway
InactiveCN101330494AAchieve uniquenessAchieving identifiabilityUser identity/authority verificationIdentifiabilityAuthentication
The invention discloses a method for realizing the safety admittance of a computer terminal based on a trusted authentication gateway, and belongs to the security technology field of the computer. The method comprises the following procedures: (1) the computer terminal initiates an access request to the gateway; (2) the basic identity information of the computer terminal is registered to the gateway; (3) an active label of the computer terminal is formed by the gateway; (4) the identity and the authority of the active label are verified through the trusted authentication gateway; (5) the trusted authentication gateway judges whether the identity and the authority of the active label are legal or not; (5.1), when the identity and the authority of the active label are illegal, the access of the computer terminal is barred; (5.2), when the identity and the authority of the active label are legal, the access of the computer terminal is permitted. The method has the advantages: firstly, the uniqueness and the identifiability of the identity of the computer terminal to the network are realized; secondly, the possibility that the terminal identification is falsified illegally can be avoided, and the terminal identification can not be forged.
Owner:瑞达信息安全产业股份有限公司
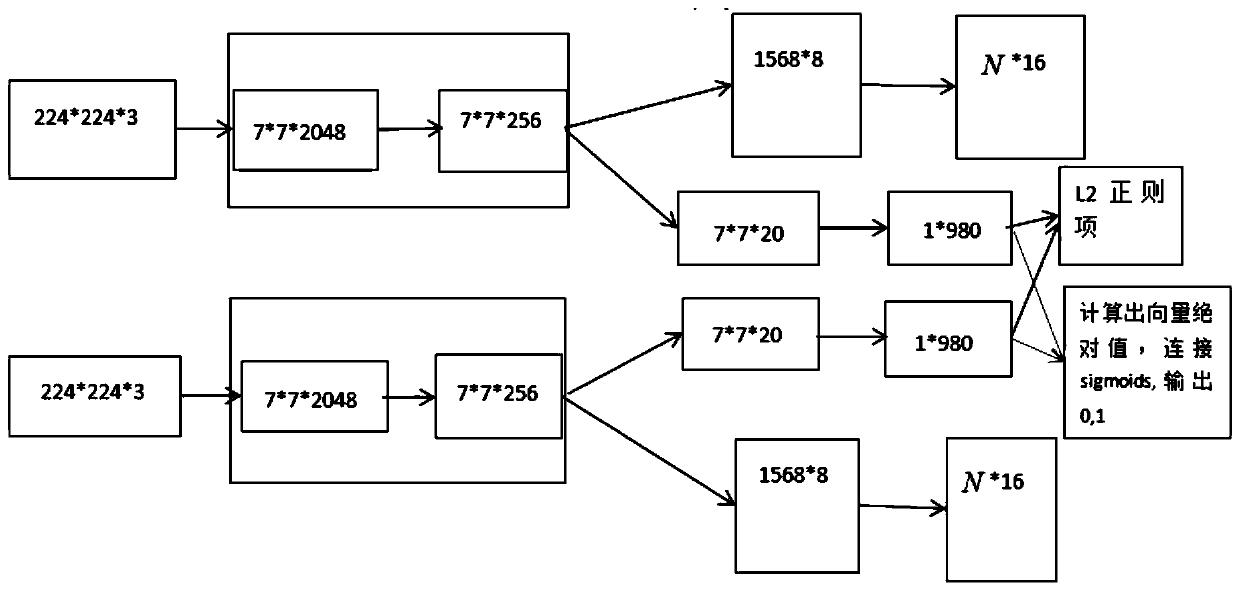
Optical remote sensing scene classification method based on deep twin capsule network
InactiveCN110321859AImprove performanceEliminate the vanishing gradient problemScene recognitionSensing dataData set
The invention discloses an optical remote sensing image scene classification method based on a deep twin capsule network. The method comprises the following steps of 1, deleting an average pooling layer of a deep residual network deep layer and a layer behind the average pooling layer; 2, taking the fine-tuned deep residual network as a feature extractor; 3, features of the input images are extracted respectively, and the obtained features are converted into capsule features; 4, introducing the thought of a twin network, and copying a single deep capsule network into a double deep capsule network to form two identical networks with shared feature extractor parameters; 5, calculating the distance between the two features to represent the similarity degree of the image pairs; and 6, carryingout capsule propagation by using a dynamic routing algorithm to finish image classification. Characteristic space information is stored by utilizing capsules, and a twinning network structure is combined, so that the characteristics have higher identifiability on a remote sensing data set. In addition, a regularization term is added to enhance the robustness of the model.
Owner:CHINA UNIV OF MINING & TECH
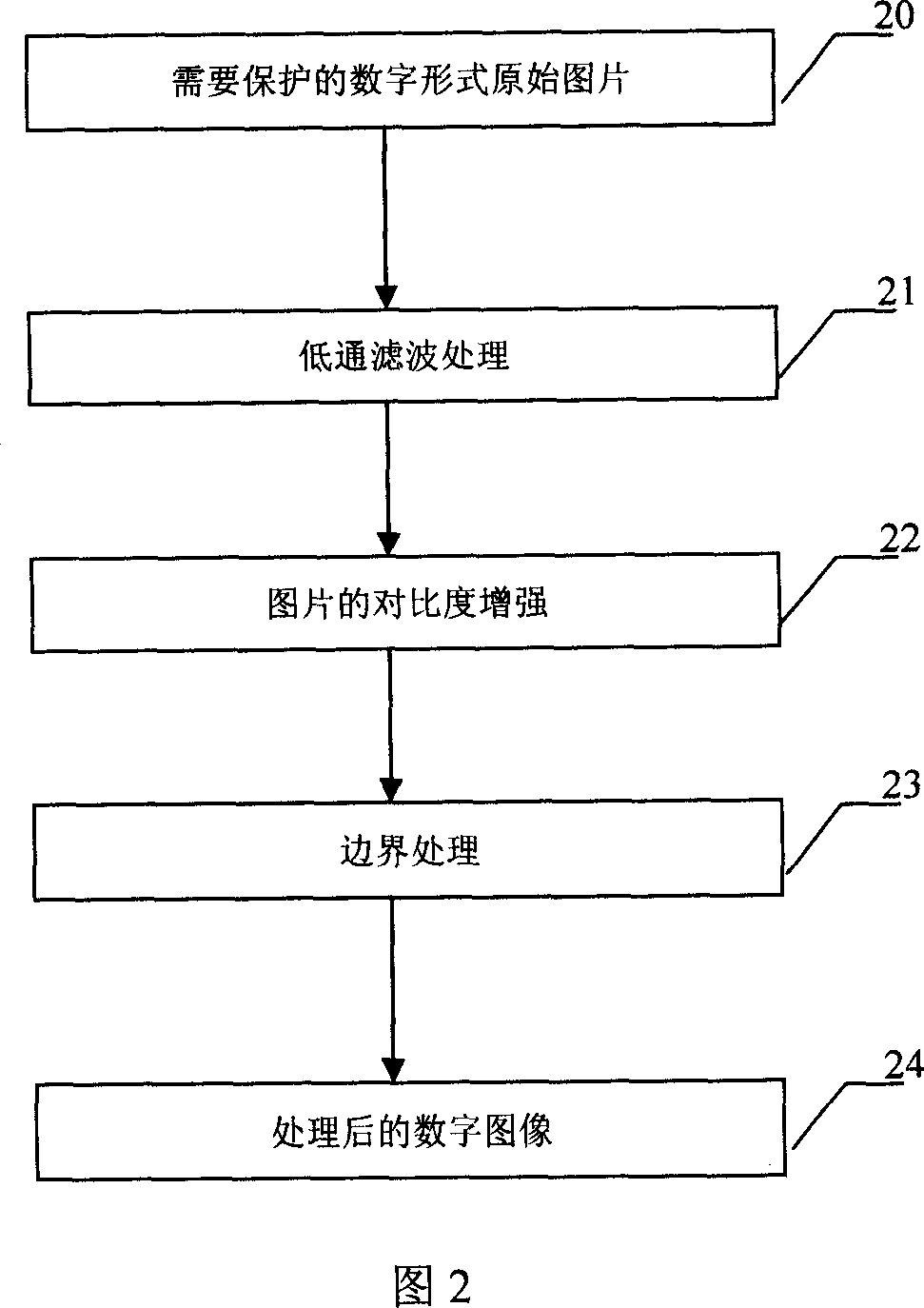
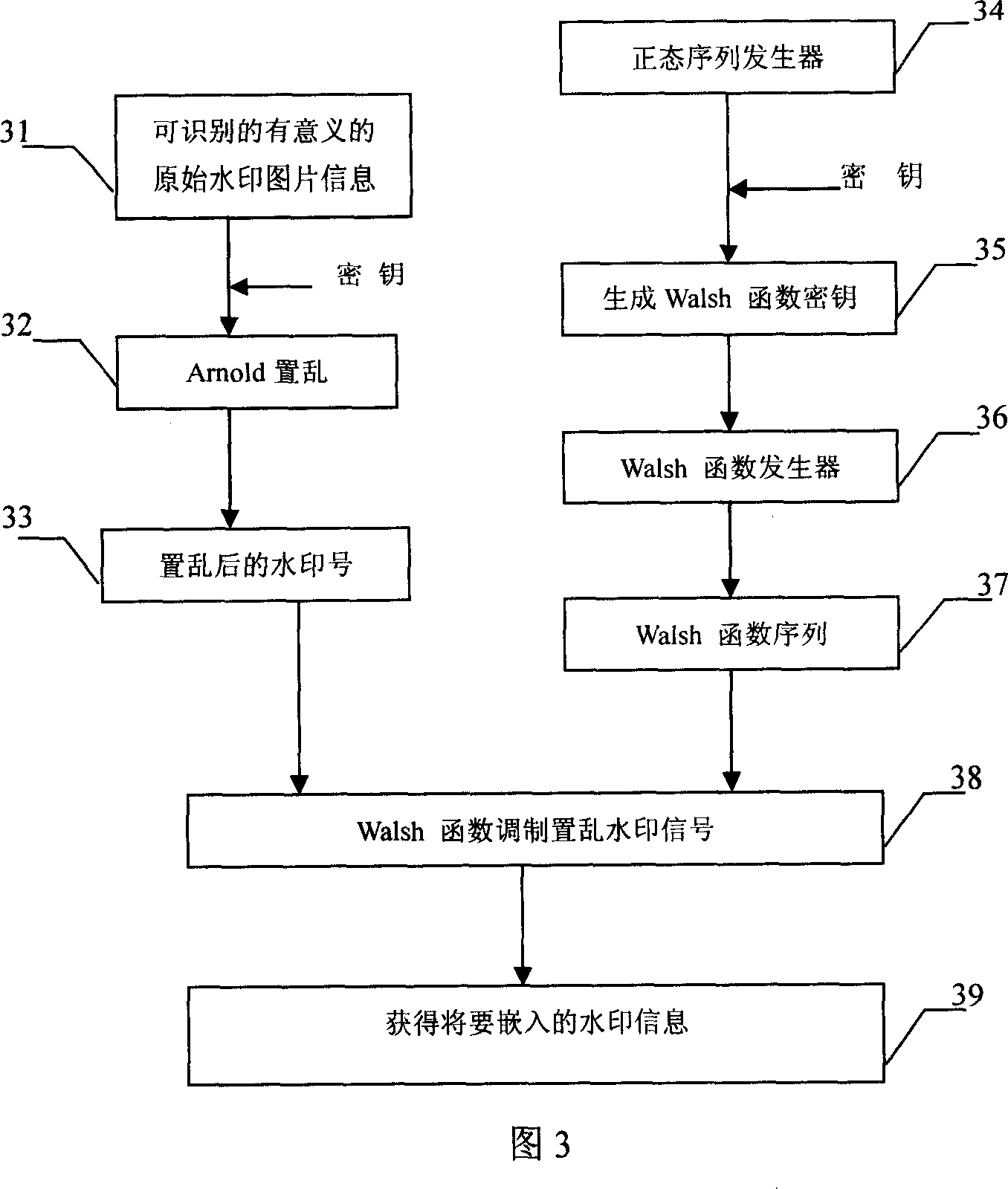
Implementation method of anti printing and scanning meaningful digital watermark with large capacity
InactiveCN1960428AImprove robustnessSuitable for a wide range of peopleImage data processing detailsPictoral communicationInformation securityIdentifiability
The method comprises: 1) generating high capacity of digital watermarking signals 2) pre-processing the original image to be embedded with the watermark; 3) embedding watermark information; 4) processing the watermark image before extracting the watermark; 5) extracting the watermark; 6) enhancing the image watermark information. The invention features the following: 1) embedding binary image high capacity information that enhances the identifiability of watermark information; 2) having strong robustness of anti-print and anti-scanning that can be used in anti-fake of all certificates and prints; using Hausdorff-based distance geometric correction process, which can effectively correct all geometric attack to watermark signal in the print and scanning process such as rotation, scaling and translation.
Owner:JILIN UNIV
Speed regulator parameter identification method combined with frequency locus and particle swarm optimization
ActiveCN103345546AConvenient and timely accessAvoid field testingSpecial data processing applicationsElectric power systemUnit speed
The invention relates to a speed regulator parameter identification method combined with a frequency locus and the particle swarm optimization. The speed regulator parameter identification method can be used for identifying parameters of a unit speed regulator. According to the speed regulator parameter identification method, an input and output model of a speed regulator system is set up, and identifiability of corresponding parameters is proved; an electromechanical transient simulating calculation module of the PSASP software is directly called through an interface, the speed regulator parameters are obtained, a simulation frequency curve after a power system is interfered is obtained, the speed regulator parameters are regulated based on the particle swarm optimization, and therefore the simulation frequency curve is close to an actual measurement frequency curve as much as possible; the optimized speed regulator parameters are obtained through repeated parameter optimization. According to the speed regulator parameter identification method, parameter identification of a speed regulating system can be finished only by utilizing a fault recording curve of a frequency and parameters of other components of the system, much troublesome on-spot tests can be avoided, and the relevant parameters of the speed regulator can be conveniently obtained by dispatch personnel in time.
Owner:STATE GRID CORP OF CHINA +1
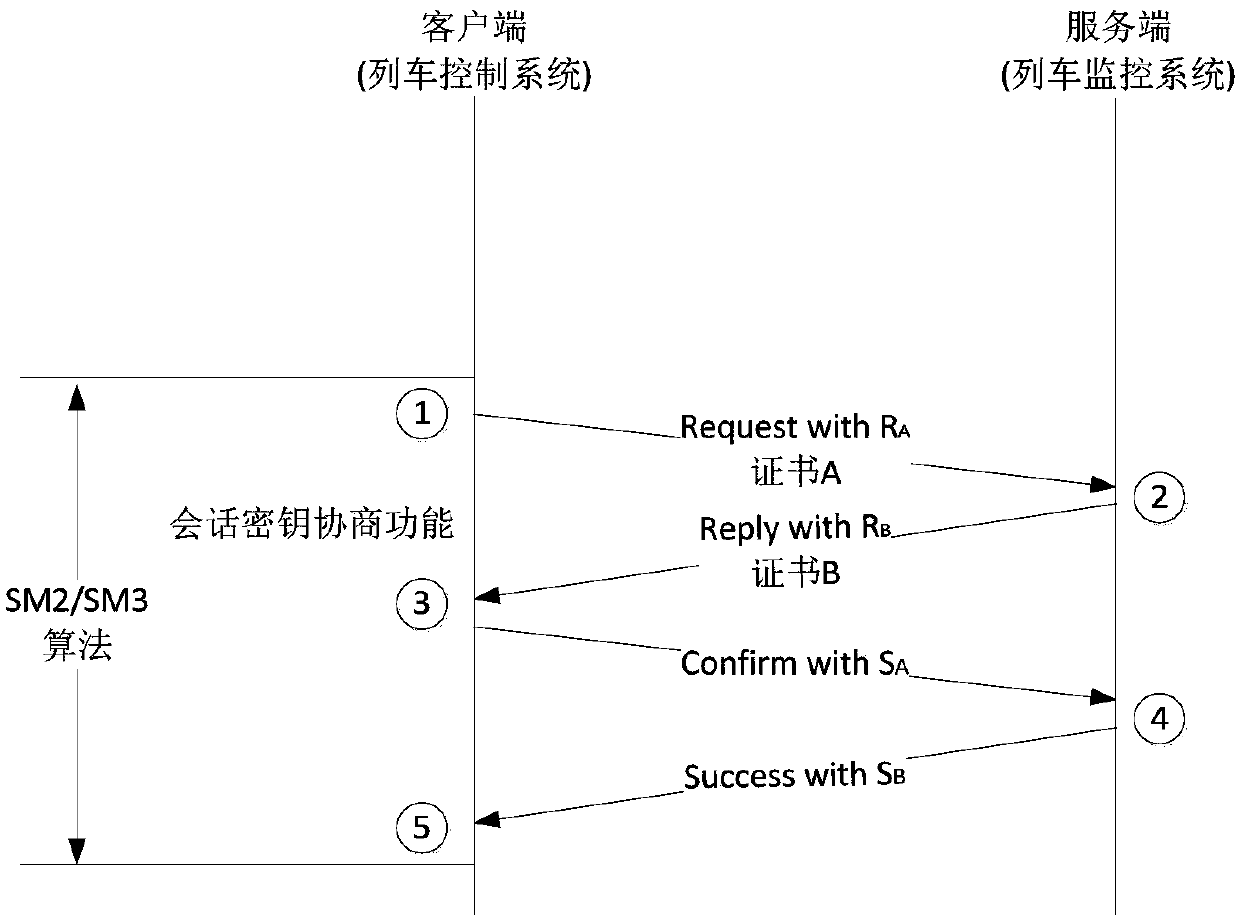
Vehicle-ground wireless communication encryption method and device applied to train monitoring system
PendingCN109688585AImprove information security protection capabilitiesSelf-controllableKey distribution for secure communicationUser identity/authority verificationConfidentiality protectionMonitoring system
The invention relates to a vehicle-ground wireless communication encryption method and device applied to a train monitoring system. The method comprises the following steps: establishing a communication association relationship and communication authentication by using a SM2 algorithm, and implementing management by adopting a dynamic key; encrypting and decrypting vehicle-ground wireless communication data by using a SM1 algorithm; and implementing integrity verification on the vehicle-ground wireless communication data by using a SM3 algorithm in order that the vehicle-ground wireless communication data are under identifiability protection, non-repudiation protection, confidentiality protection and integrity protection. Compared with the prior art, the vehicle-ground wireless communication encryption method has the advantages that a data encryption technology is applied to application layer equipment of the train monitoring system, so that the information safety protection performance of the vehicle-ground wireless communication is improved greatly.
Owner:CASCO SIGNAL
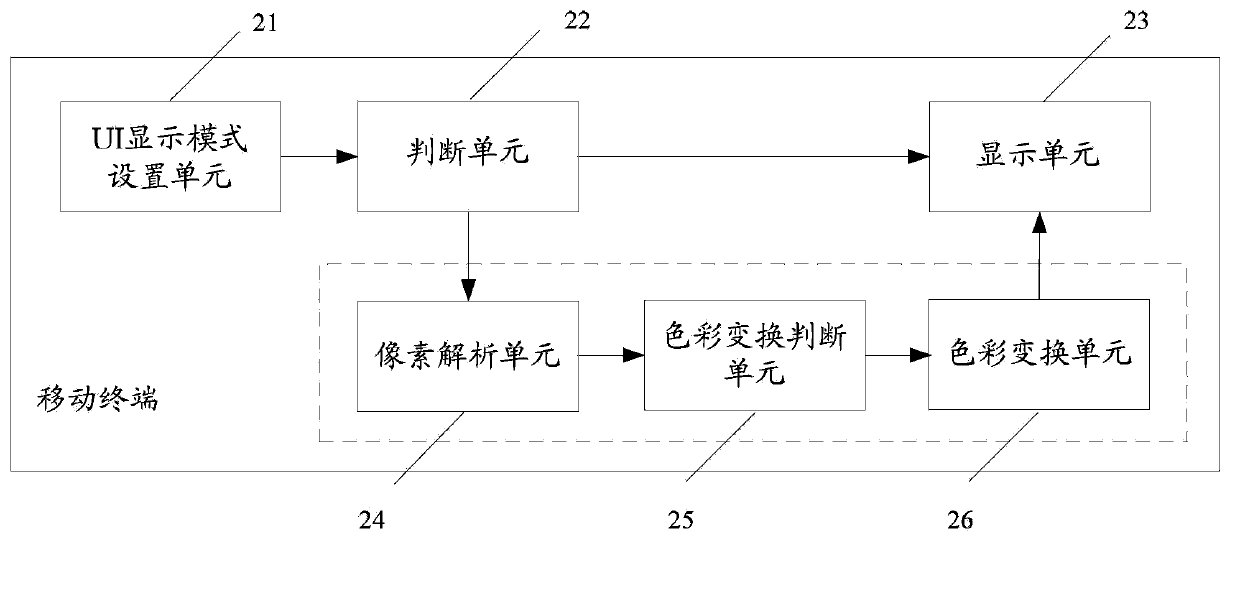
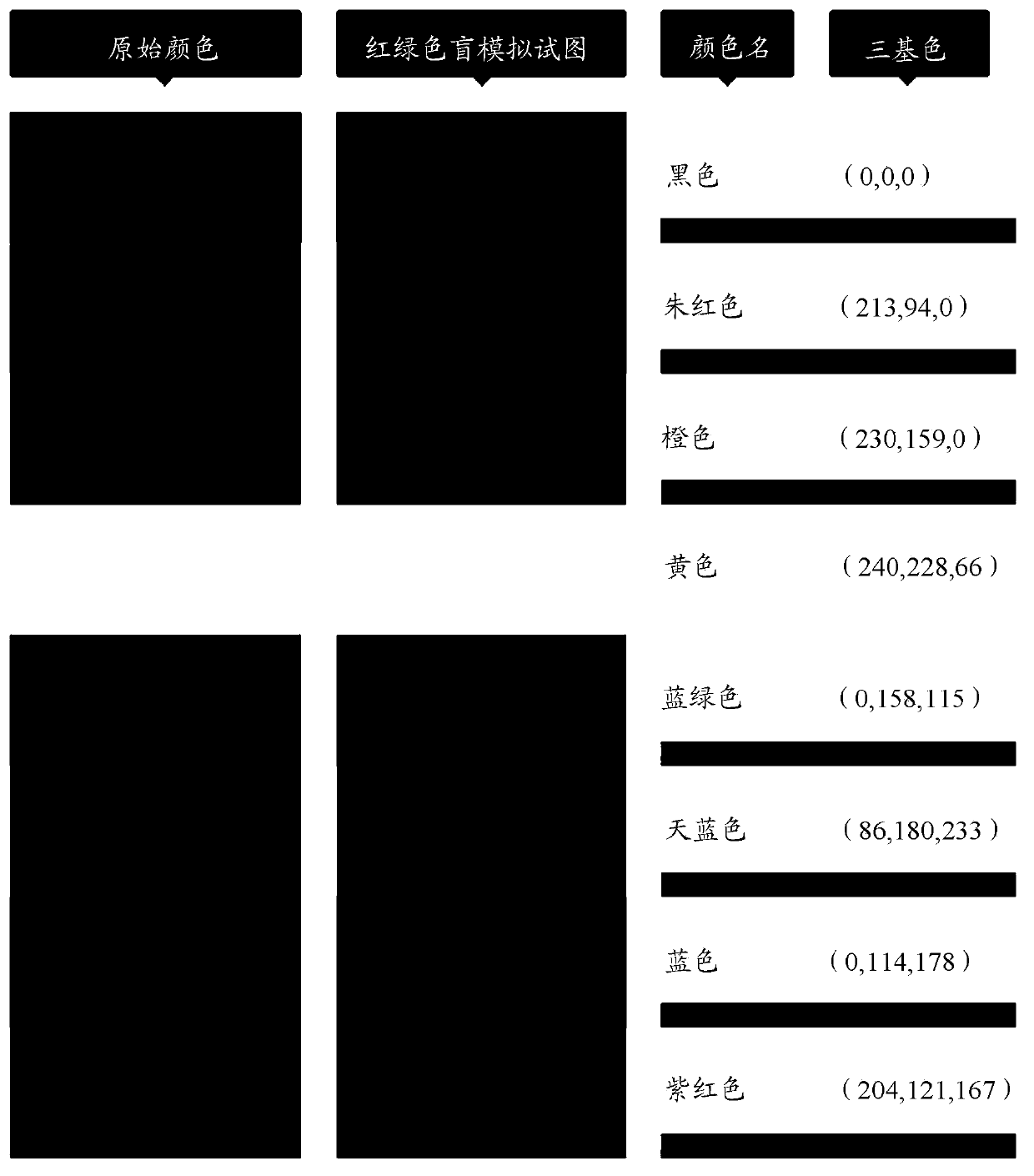
Mobile terminal and method for displaying interface thereof
ActiveCN103870148AImprove experienceSolving recognition difficultiesDigital output to display deviceIdentifiabilityComputer science
The invention discloses a method for displaying a UI (User Interface), which is characterized in that a mobile terminal sets a UI display mode as a normal display mode or a friendly color display mode according to setting operation by a user; according to the UI display mode set by the user, UI information is displayed in the normal display mode or the friendly color display mode. The invention also discloses the mobile terminal for realizing the method for displaying the UI. By the adoption of the method and the mobile terminal provided by the invention, the problem that people with red-green color blindness have a difficulty in identifying the UI information of various mobile terminals with changeful colors; the identifiability and the readability of the UI information of the mobile terminal are effectively improved; due to the free setting of the UI display mode of the mobile terminal, the compatibility with the habits of existing users is realized.
Owner:ZTE CORP
Touch screen position detection method
ActiveCN102033637AImprove legibilityIncrease mutual capacitanceInput/output processes for data processingImage resolutionTouchscreen
The invention discloses a touch screen position detection method. The method comprises the following steps of: applying a plurality of first driving signals to a first detection end of a touch screen detection region, detecting signals at a second detection end of the touch screen detection region and acquiring a first coordinate value according to a detection result of the second detection end; applying a plurality of second driving signals to the second detection end, detecting the signals of the first detection end and determining a second coordinate value according to a detection result of the first detection end; and determining a touch position by using the first coordinate value and the second coordinate value. In the method, a driving end and an inducing end are used as the driving ends respectively, and a plurality of detection lines are simultaneously used for driving each time, so the identifiability of a detection signal is improved, the step effect is avoided and the detection time is saved on the premise of not affecting resolution.
Owner:SHANGHAI TIANMA MICRO ELECTRONICS CO LTD
Method and device for self-adapting of Baud rate in field of power monitoring
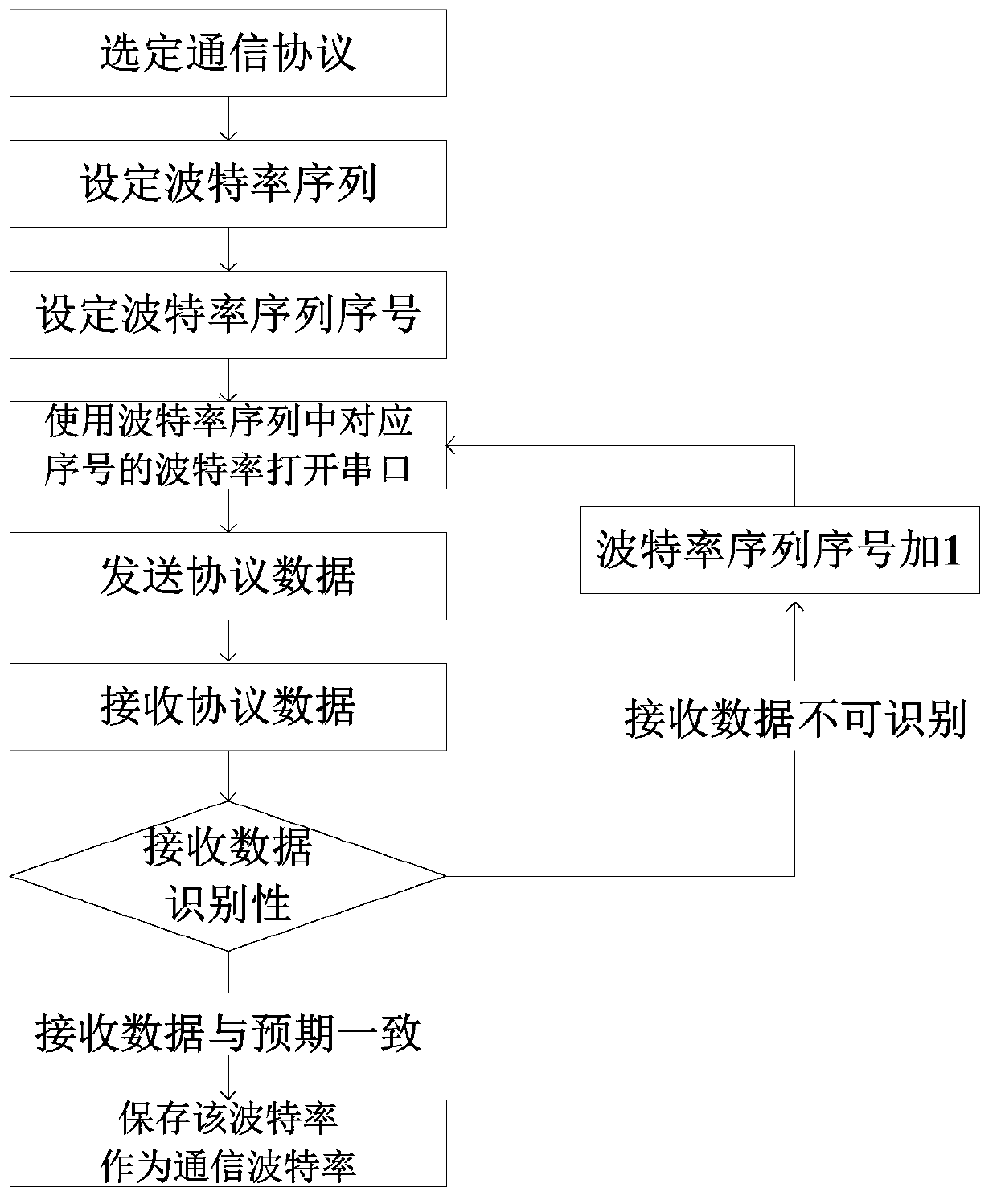
ActiveCN103389960AIncrease flexibilityImprove experience comfortElectric digital data processingMonitor equipmentSelf adaptive
The invention discloses a method and a device for self-adapting of Baud rate in the field of power monitoring. The method comprises the following steps of selecting a communication protocol; setting a Baud rate sequence; setting numbers of the Baud rate sequence; using the Baud rate with corresponding number in the Baud rate sequence to open a serial port; sending the protocol data to monitoring equipment; receiving the protocol data which is returned from the monitoring equipment; analyzing and judging the identifiability of the data; if the received data cannot be identified, closing the serial port, and adding the number of the Baud rate sequence with 1; and if the received data are uniform with the expected data, maintaining the Baud rate as the communication Baud rate. The method has the beneficial effect that the self-adapting of the Baud rate between control equipment and the monitoring equipment in the monitoring field can be realized. The device for realizing the self-adapting of the Baud rate in the field of power monitoring has the advantages that the structure is simple, and the comfortability of user experience is improved.
Owner:康威通信技术股份有限公司
Method, device and equipment for expanding short text to be processed
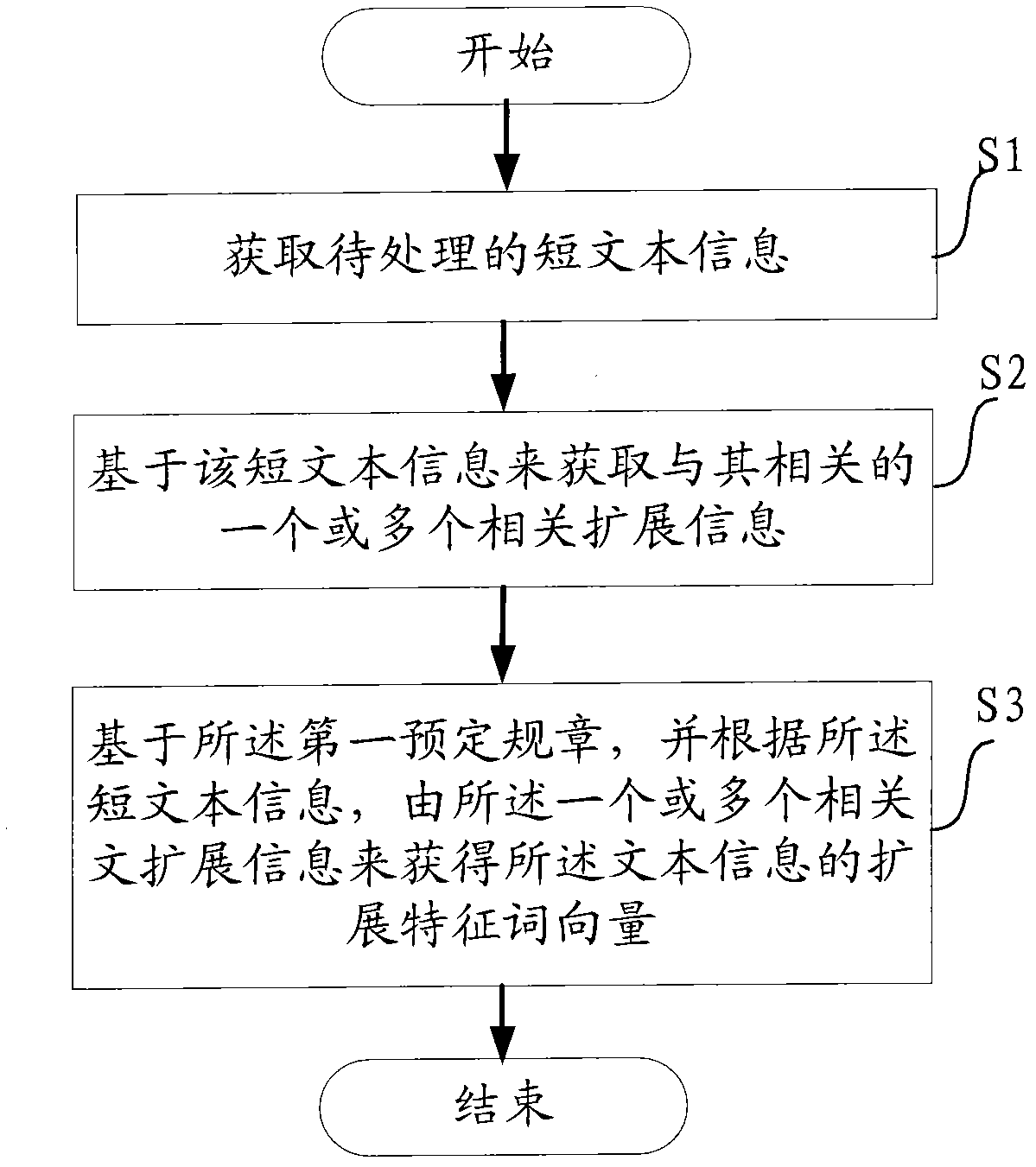
ActiveCN102567290AImprove scalabilityImprove targetingSpecial data processing applicationsSoftware engineeringData mining
The invention provides a method, device and computer equipment for expanding a short text to be processed. The method disclosed by the invention comprises the following steps of: obtaining short text information to be processed; obtaining one or more relevant expansion information which is relevant to the short text information through the short text information; and obtaining an expansion characteristic word vector of the short text information by using one or more relevant expansion information according to a first preset rule and the short text information. Compared with the prior art, the method, the device and the computer equipment, disclosed by the invention, have the following advantages: 1) the short text information can be better expanded, the commonality is strong, the maintenance is convenient, and expansion characteristic information with stronger pertinence and identifiability is obtained; and 2) the method, the device and the computer equipment are not limited to the short text form and a short text characteristic matching list does not need to be pre-stored, so that the application prospect is wider.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Object identification structure and object provided with the same
InactiveUS20060097514A1Improve heat resistanceOther printing matterPolarising elementsExtremely hardIdentifiability
An object identification structure for generally distributed products is provided which is extremely hard to forge, high in identifiability, and can be manufactured inexpensively. The object identification structure comprises a single layer cholesteric liquid crystal film which is substantially colorless and transparent when viewed from the front and appears colored when viewed from a predetermined oblique direction.
Owner:NIPPON OIL CORP
Method for supporting user to browse multiple format resources and equipment
ActiveCN102314437AImprove browsing efficiencyImprove user experienceSpecial data processing applicationsIdentifiabilityUser equipment
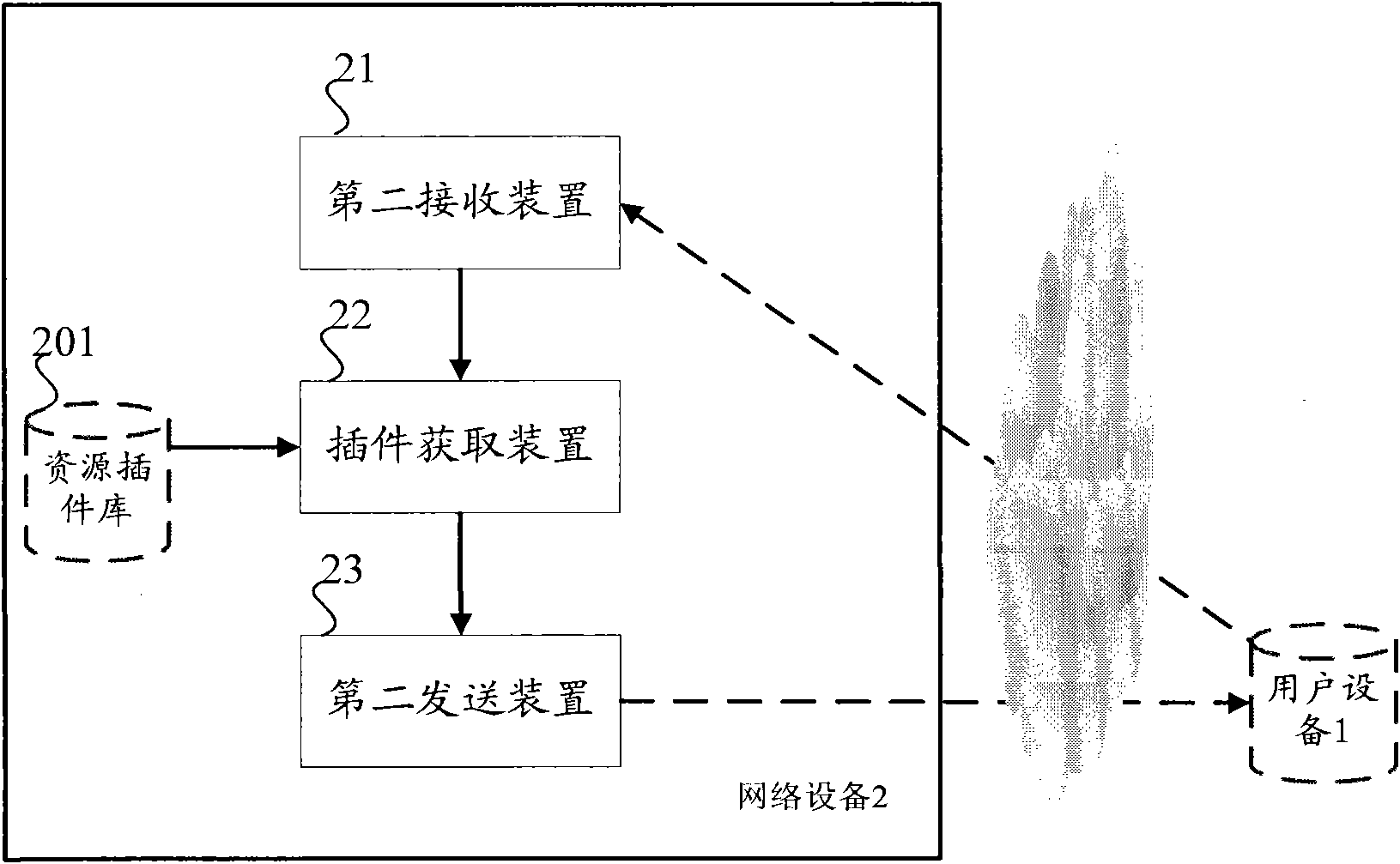
The invention aims to provide a method for supporting a user to browse multiple format resources and equipment. The method comprises the following steps of: detecting the identifiability of the resources by user equipment so as to acquire one or more unknown resources; sending resource analyzing requests about the unknown resources to a network server; receiving supporting plugins acquired on the basis of the resource analyzing requests and sent by the network server; and installing the supporting plugins. In the invention, by identifying the unknown resources and acquiring and installing the supporting plugins adapted to the unknown resources, a user is supported to browse the multiple format resources, so the user browsing efficiency and the user utilization experience are improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
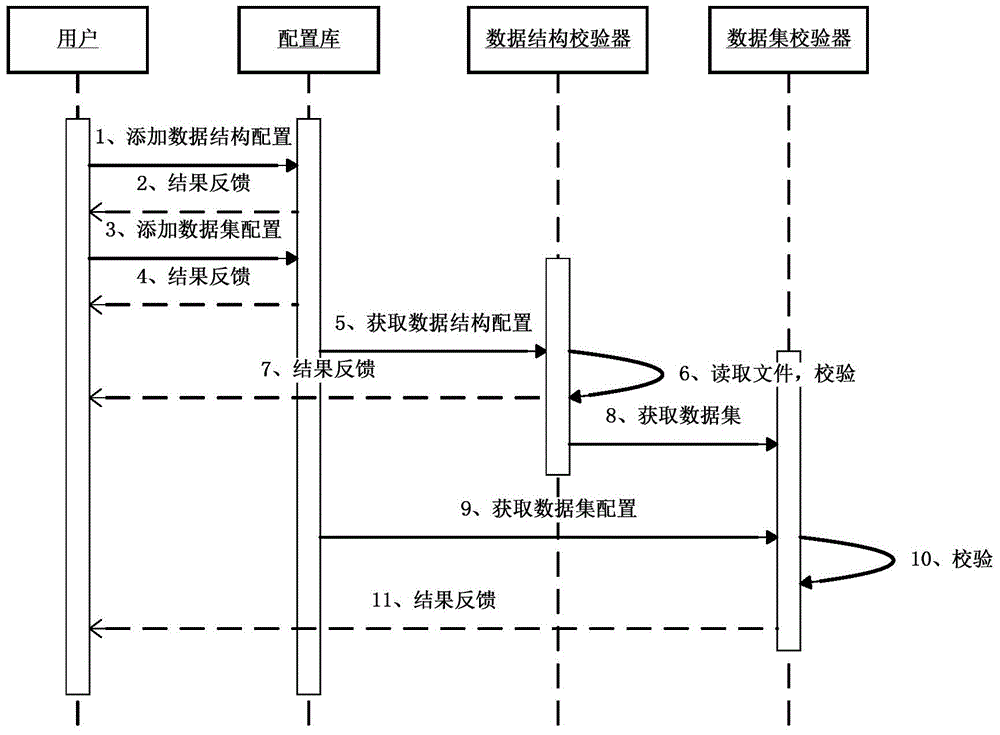
Calibration system and method based on EXCEL data structure
ActiveCN104915262AGuaranteed Diversity ChecksImprove acceleration performanceFault responseData setData mining
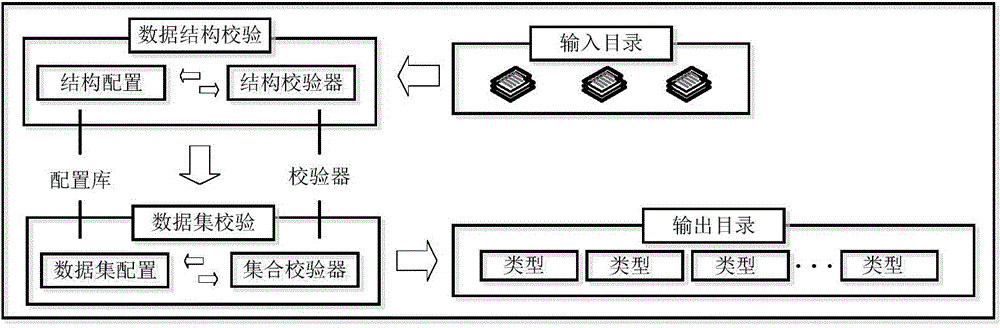
The invention relates to the technical field of computer application, in particular to a calibration system and method based on an EXCEL data structure. The system is composed of two parts, namely a configuration library and calibrators, and externally connected with standard input and output; the configuration library comprises associated configuration information of a data structure and a data set, and provides rule bases for the calibrators; the two calibrators refer in particular to the data structure and the data set. First analysis matching is conducted on an EXCEL file through a structural calibrator, and if the matching fails, a prompt is given; if no prompt is given, on the basis of the successful first analysis matching, second analysis matching is conducted on the file by using a data calibrator, a matching result is only needed to meet a subclass of the data set, the file is stored in a classified mode according to the result and rules, otherwise, illegality is affirmed. The EXCEL data structure and the data set are stored in a configuration-based mode, the system has the advantages that the expansibility is good, the application range is wide, and the identifiability is high, and the system can be applied to multiple service-type systems to conduct legal check on files.
Owner:G CLOUD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com