Context-aware-based security access control method for RFID system
A security access control and context technology, applied in the field of context-related security access control, can solve the problems of difficult to meet the flexible and high security requirements of the Internet of Things RFID system, achieve simple methods, prevent users from abusing permissions, and solve security problems. Effects of privacy concerns
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
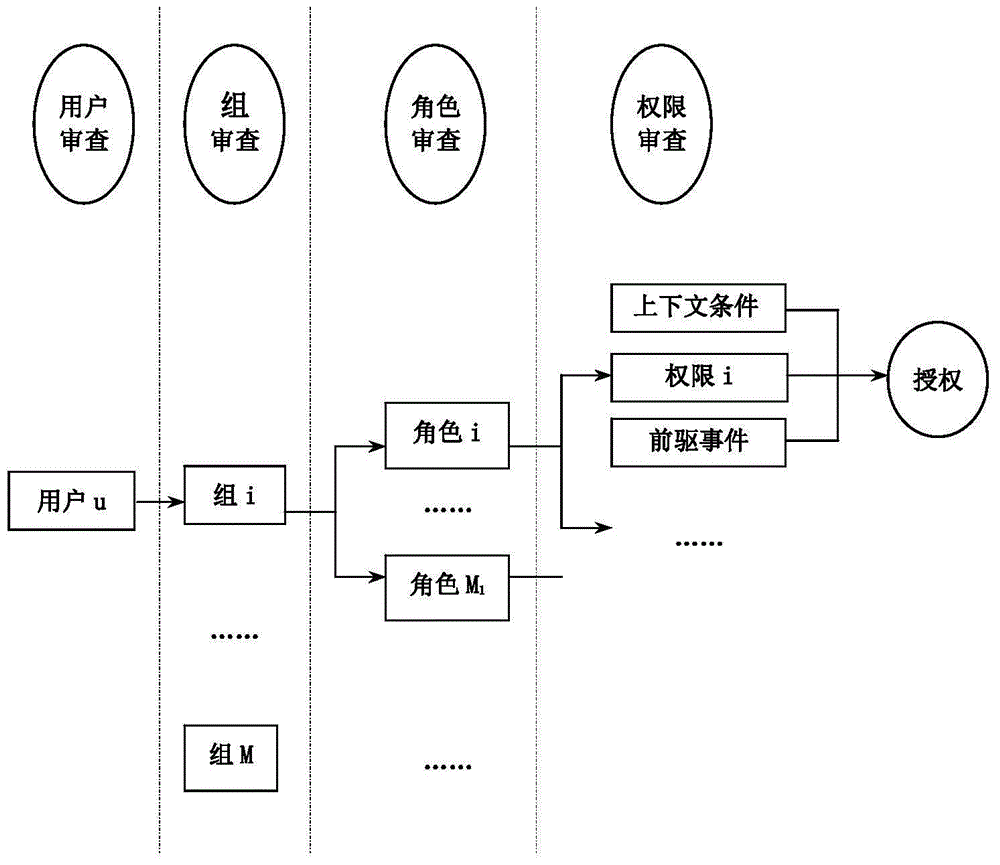
[0031] Such as figure 1 and figure 2 As shown, the context-based security access control method for RFID systems in the present invention is implemented based on a database, which includes a user set U, a user group set G, a role set R, a permission set P, an operation set OP and a context condition set Σ , wherein, the user set U, user group set G, role set R, authority set P, operation set OP and context condition set Σ are respectively composed of all users u, all user groups g, all roles r, all authority p, all operations op and all context conditions ∑ e In addition, each authority p is assigned one or more operations op, each role r is assigned one or more corresponding authority p according to the task of the role, and each user group g is assigned one or more ops according to the task of the user group For multiple corresponding roles r, the execution of each permission p is determined by the subset of contextual conditions ∑ e Defined, and the context condition su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com