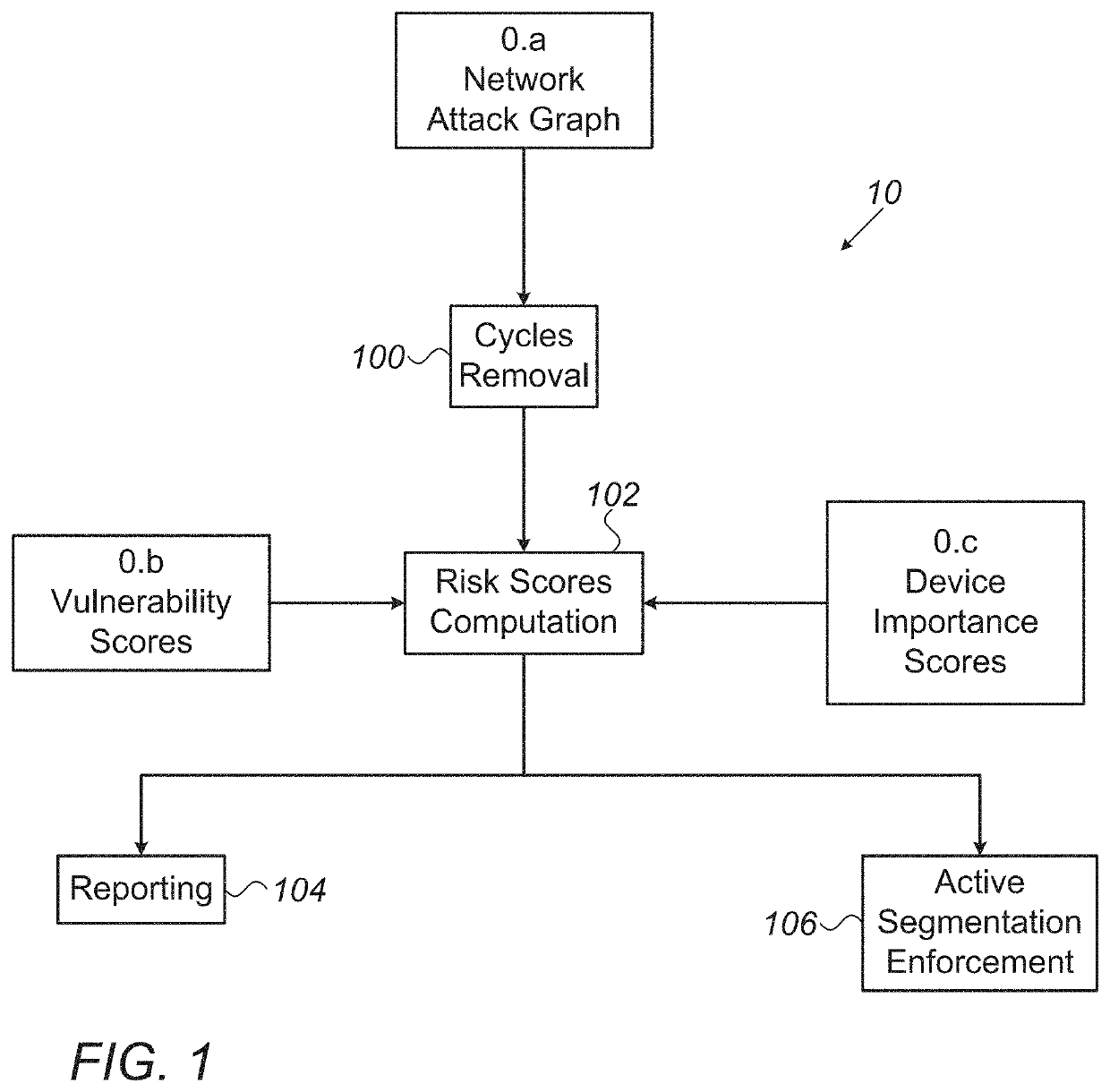
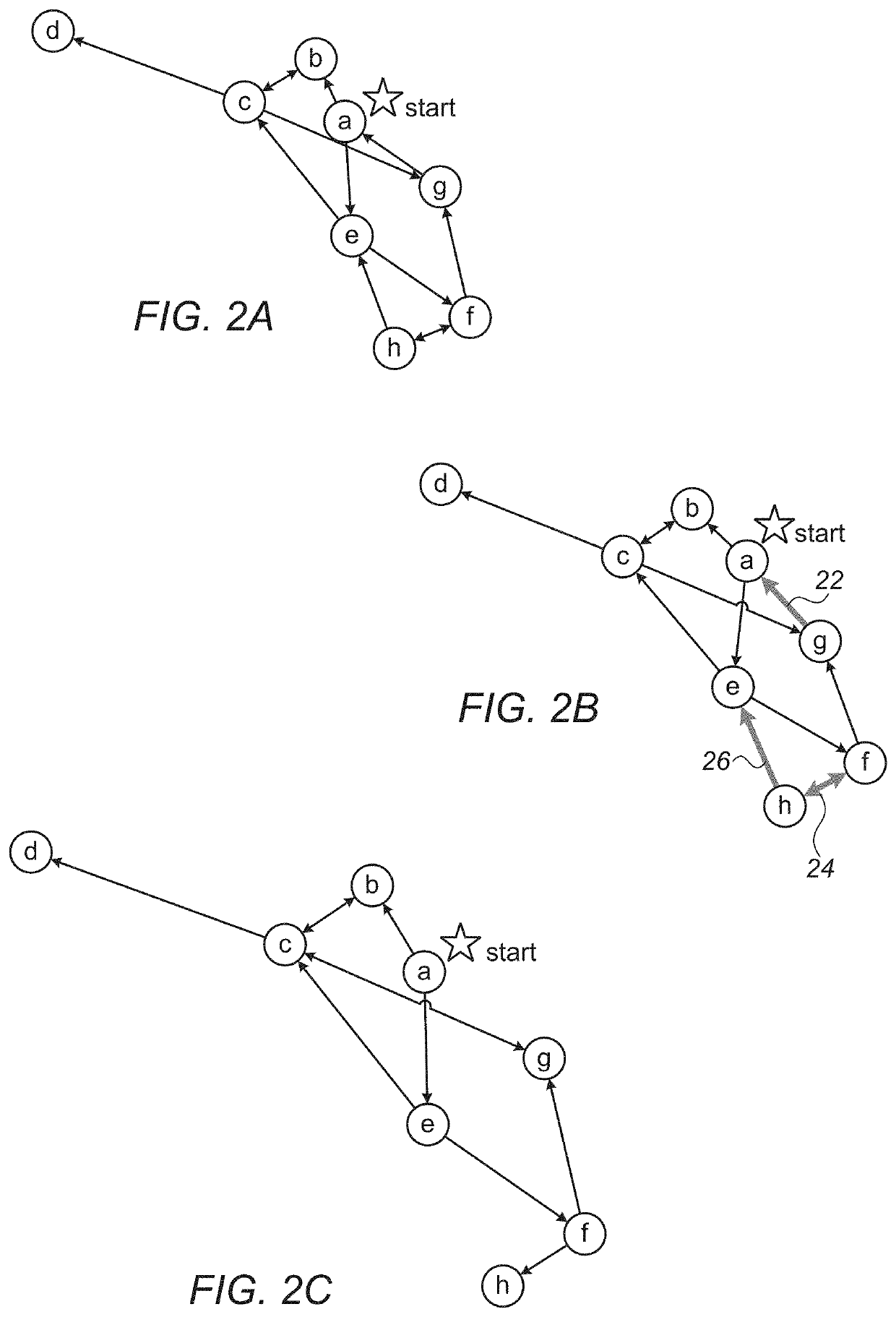
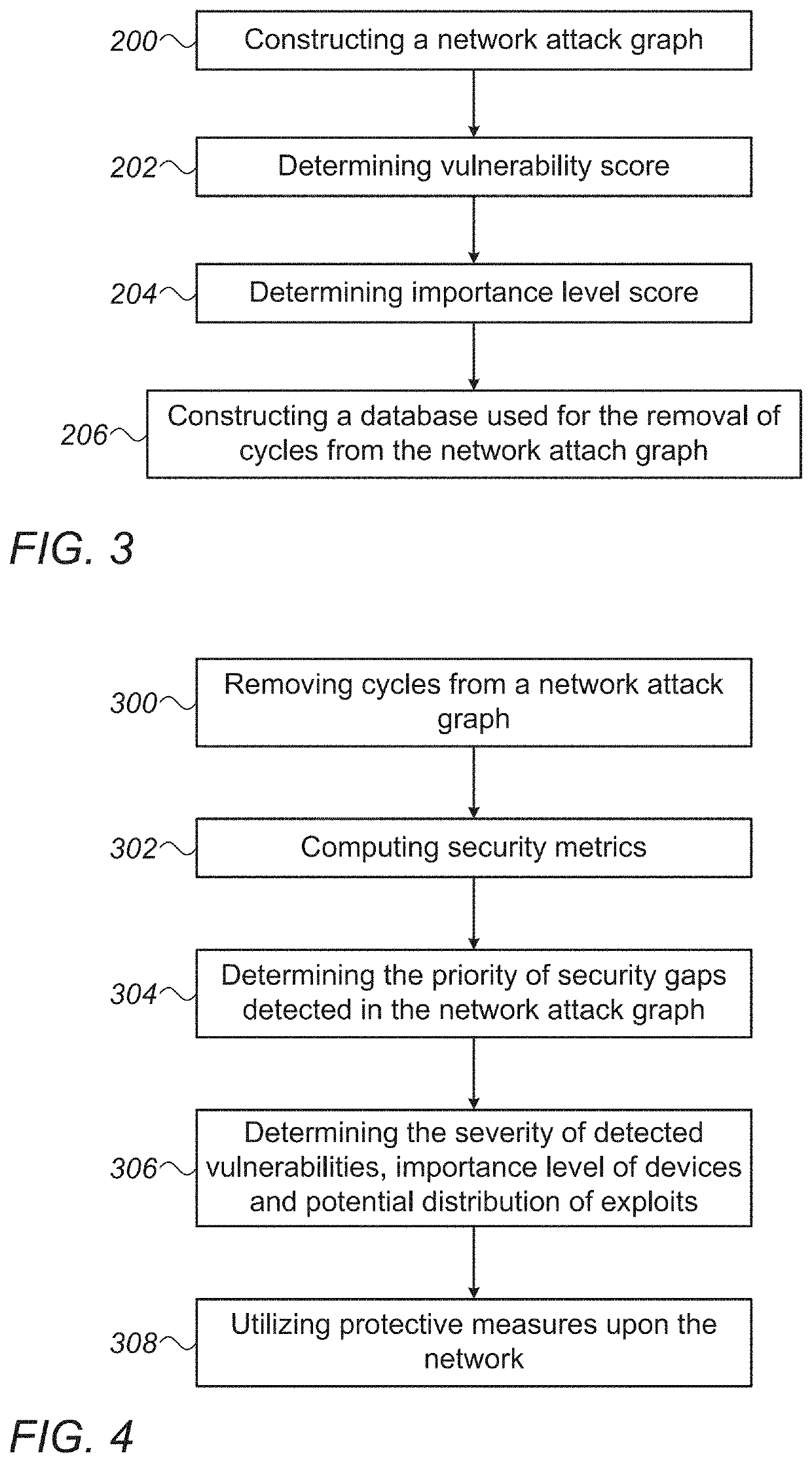
Operational Network Risk Mitigation System And Method
a technology of risk mitigation and network operation, applied in the field of cybersecurity systems and methods, can solve problems such as requiring relatively low computational resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
[0149]Given that V is the set of nodes in the attack graph and N represents the number of nodes in the attack graph, according to some embodiments equation N=IVI represents the number of network segments in an attack graph. Given that E is the set of edges in the attack graph and M represents the number of edges in the attack graph, according to some embodiments equation M=|E| represents the number of edges in an attack graph. The “FindCyclicEdges” method is executed in accordance with previously disclosed steps, where the depth-first search (DFS) traversal (previously disclosed in step 3.2.1), is performed at most M times for every edge in the attack graph, therefore, the upper bound on the complexity is O(M2+M*N) (given that O represents the limiting behavior of a function by describing the computation complexity of the aforementioned method). According to some embodiments, the actual complexity will be much lower, since the worst-case complexity of O(M+N) (wherein O(M+N) means th...
example 2
[0150]Further to using Example 1 above, and given that D is the maximal number of devices in a single network segment and K is the maximal number of vulnerabilities which can be possibly detected on a single device, the maximal number of exploits on each edge is D2*K. The upper bound on the computational complexity of the “ComputeRiskScores” method is O(M*D2*K+N2+N*D3*K) and it is dominated by the complexity O(M*D2*K) (as in operation 402 previously disclosed), O(N2) (as in operation 408 previously disclosed), or O(N*D3*K) (as in operation 410 previously disclosed). According to some embodiments, such polynomial complexity is fairly reasonable and should enable short execution times on modern machines, even for large networks with tens of thousands of devices, as long as proper segmentation is applied to keep D at a moderate range.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com