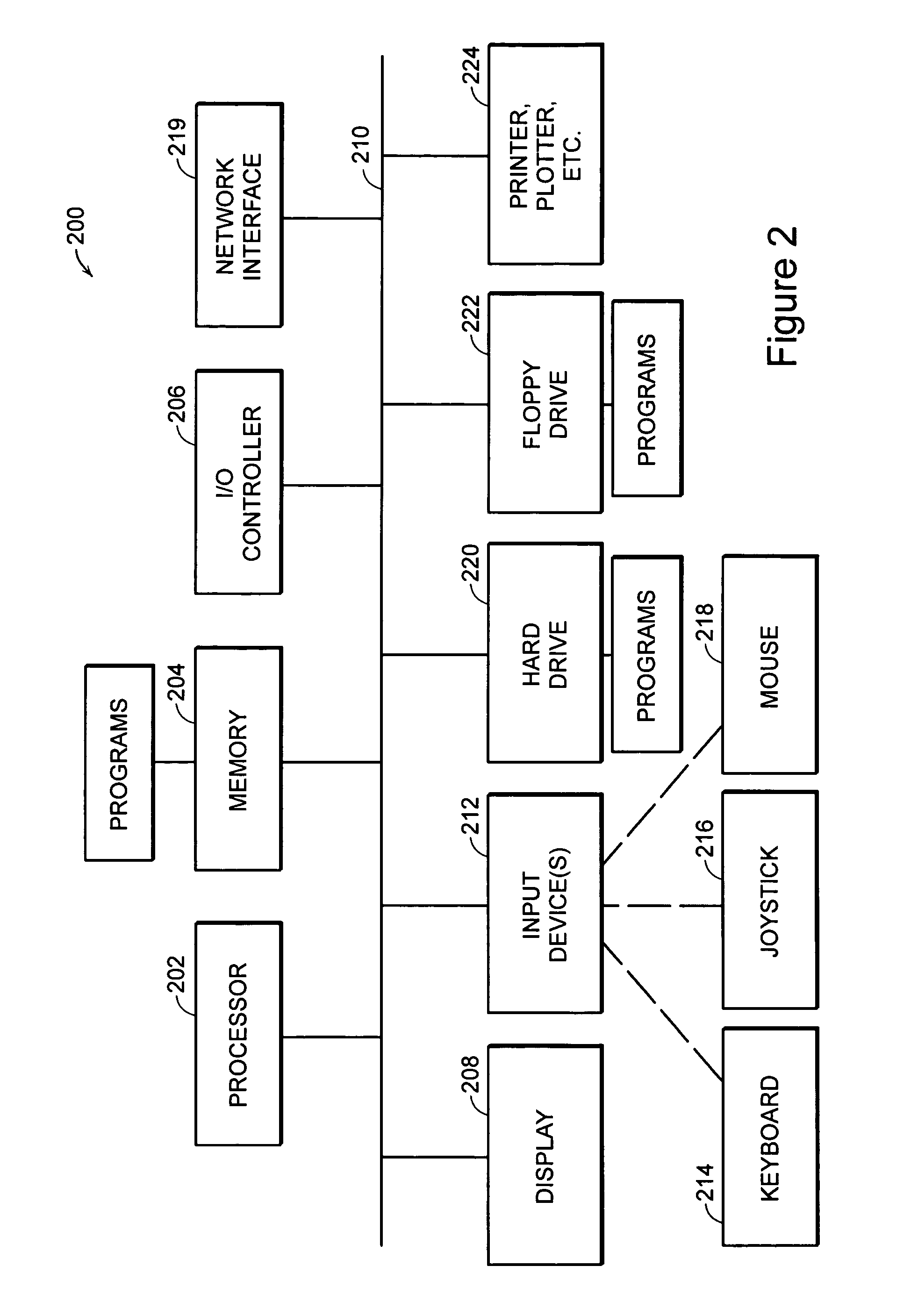
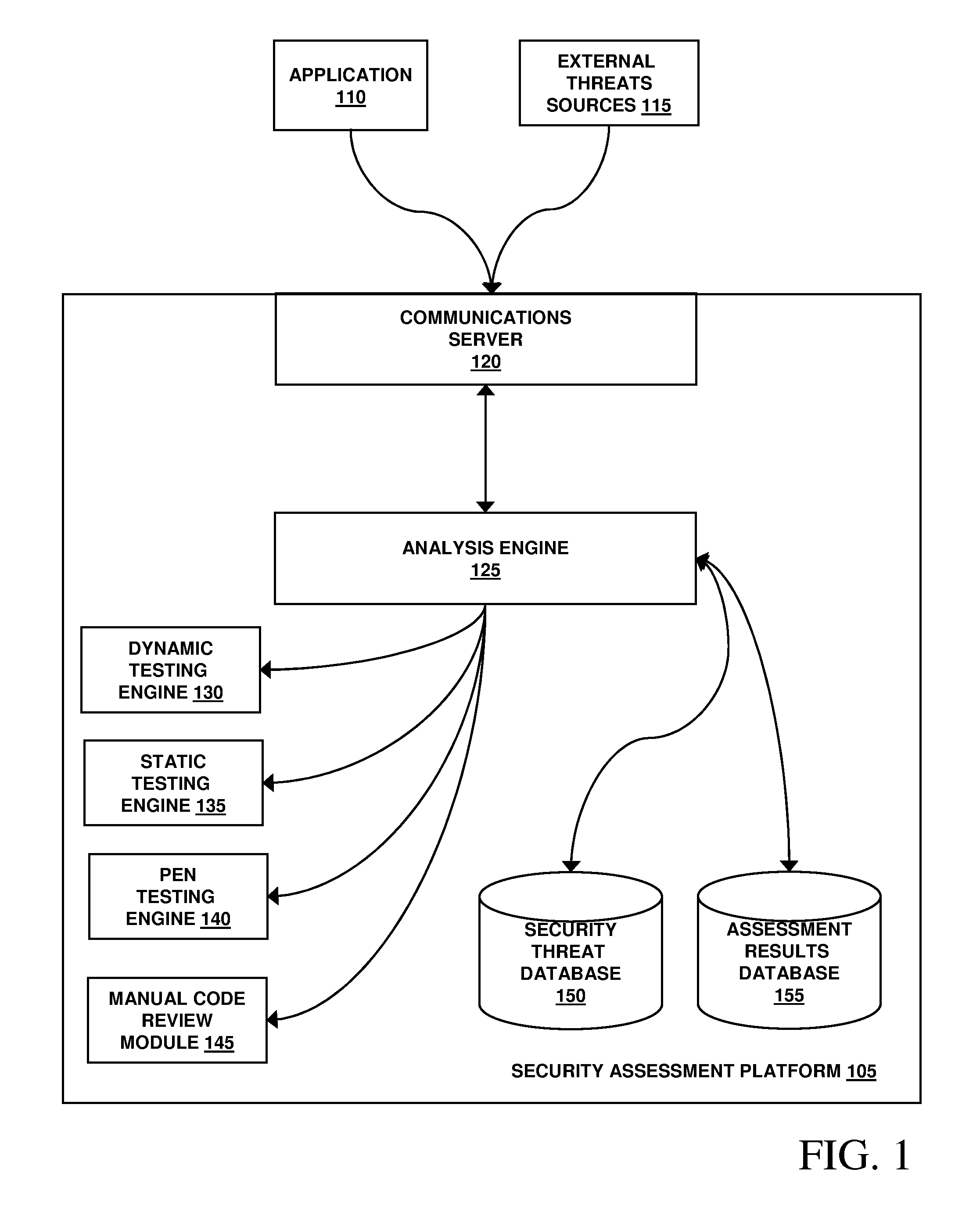
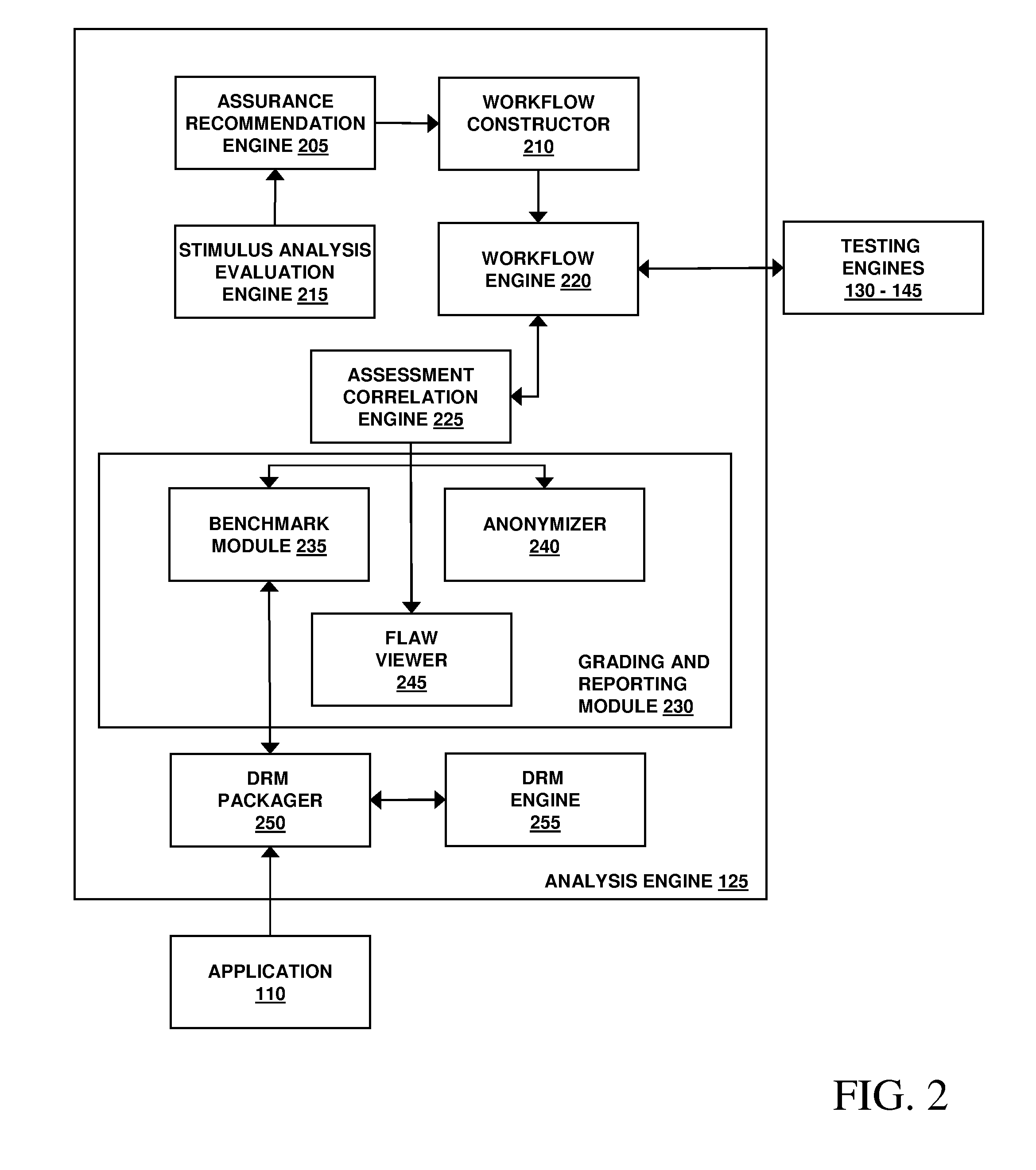
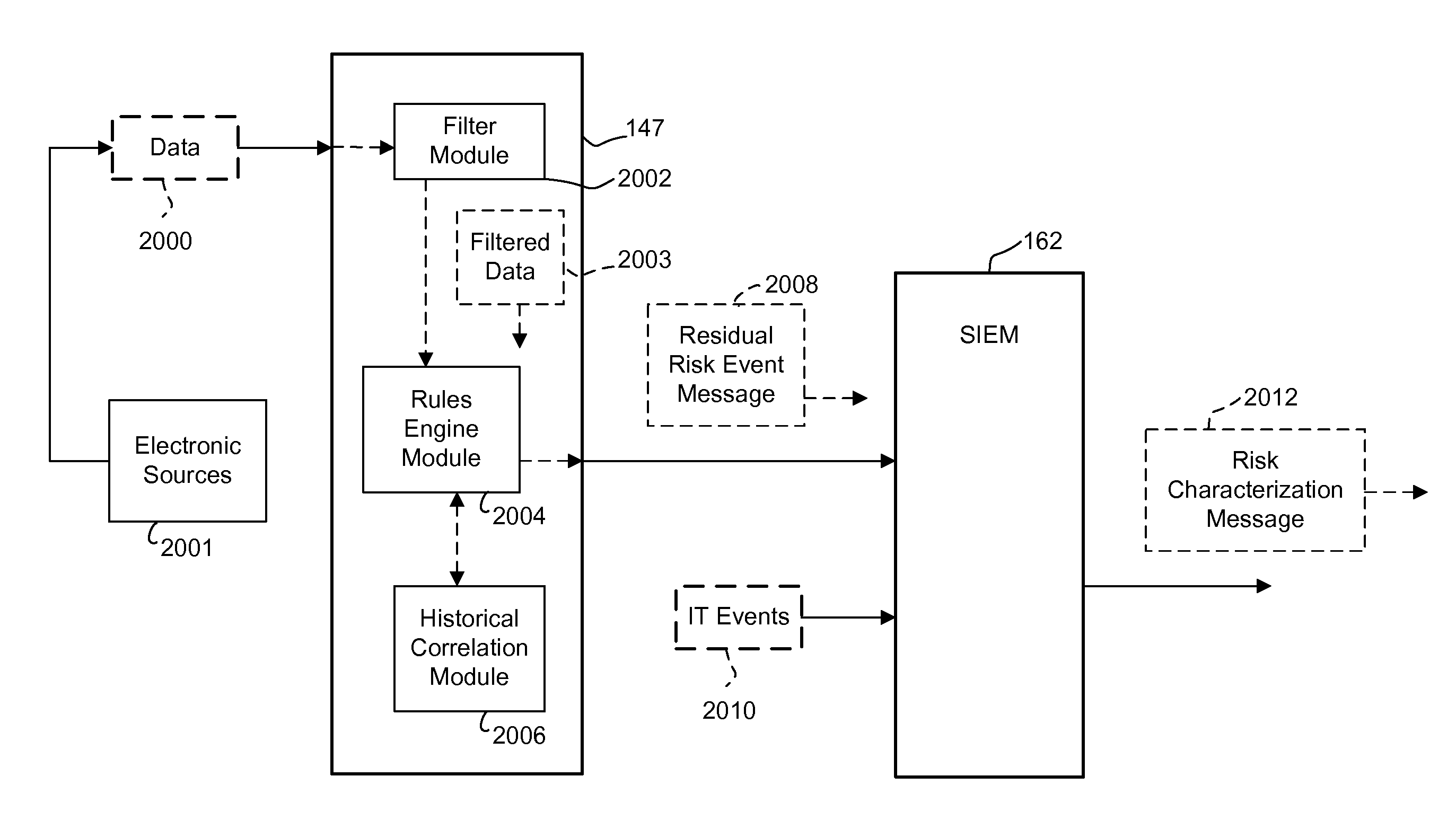
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6412 results about "Risk IT" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Risk IT provides an end-to-end, comprehensive view of all risks related to the use of information technology (IT) and a similarly thorough treatment of risk management, from the tone and culture at the top, to operational issues.
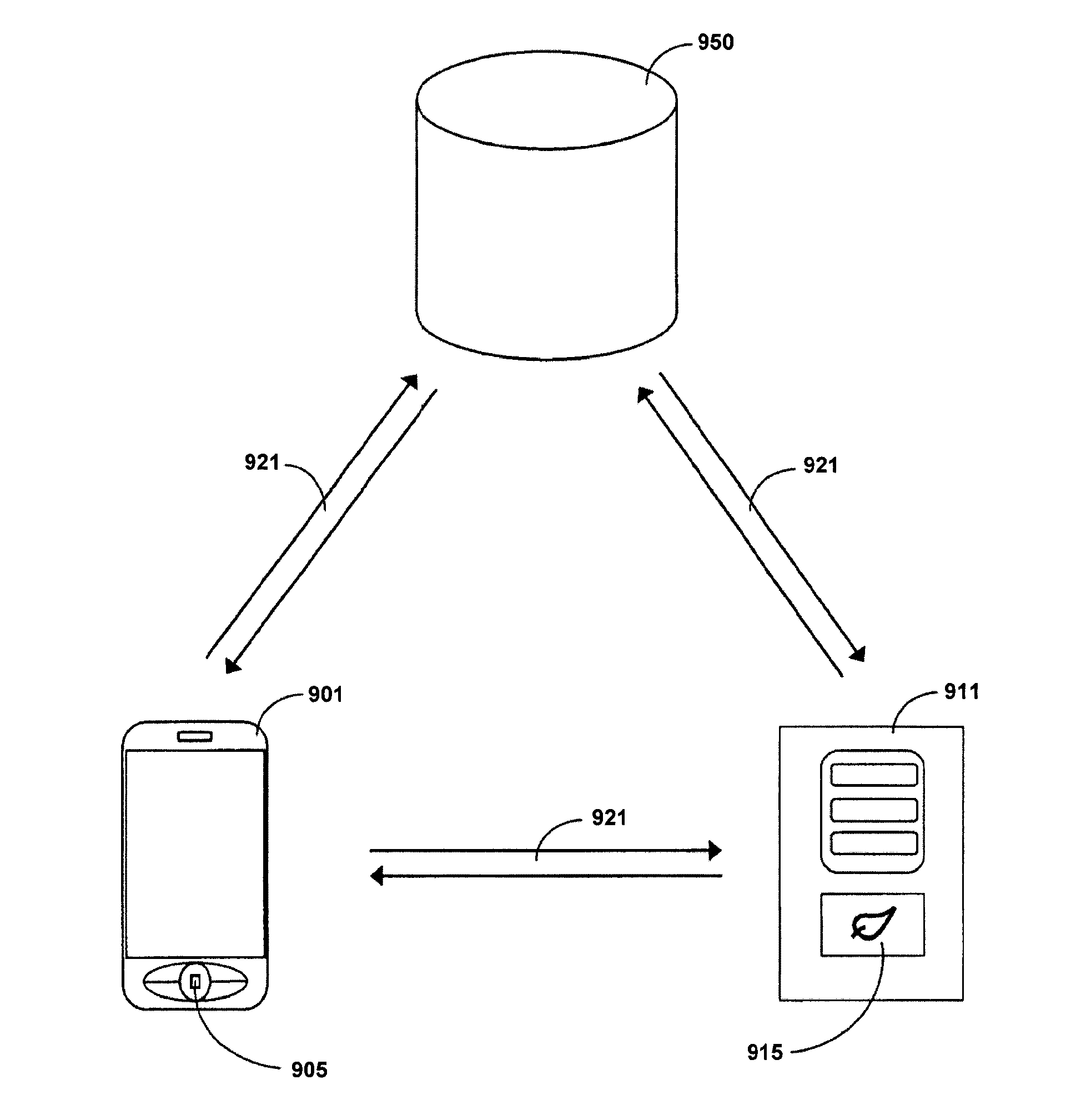
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
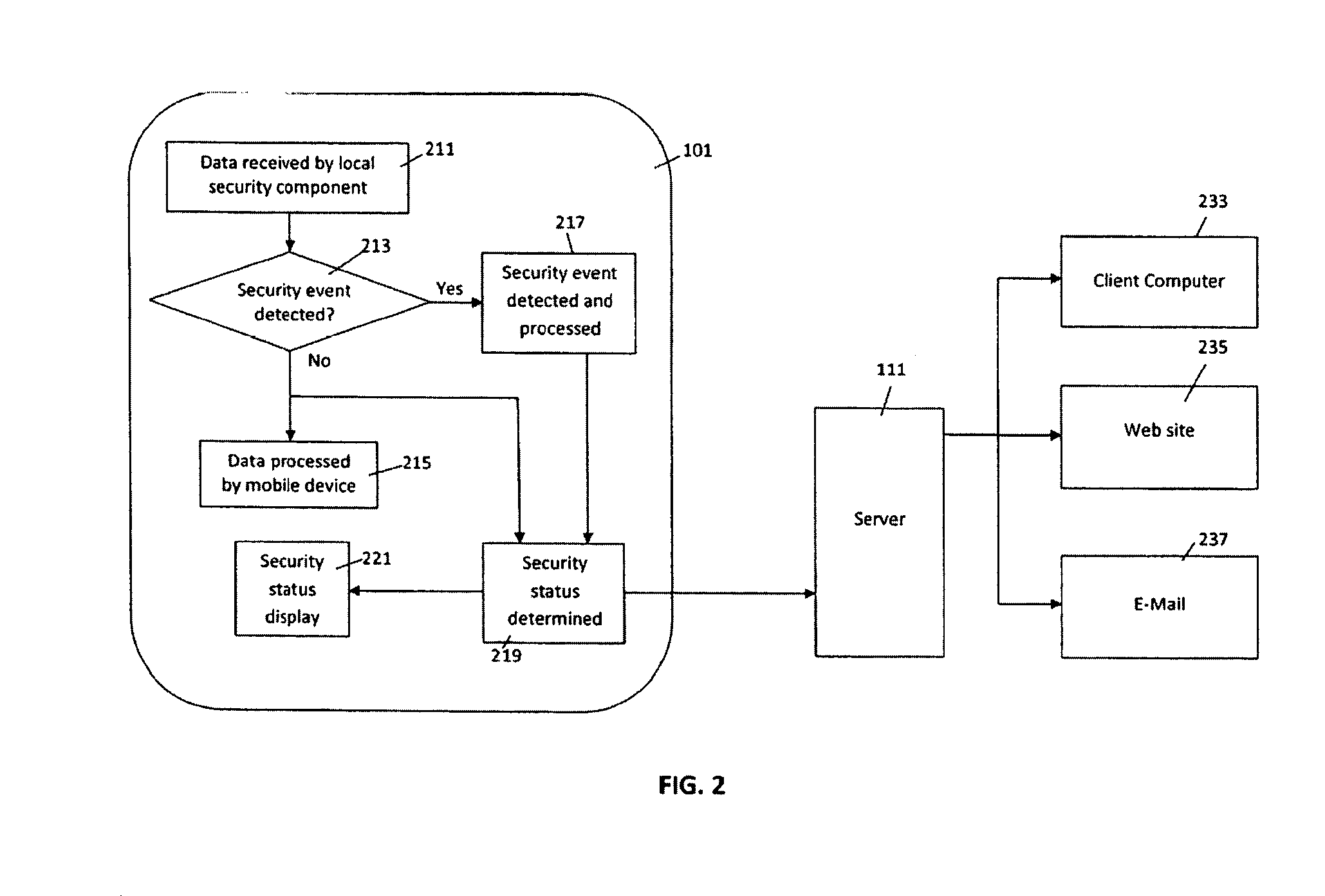
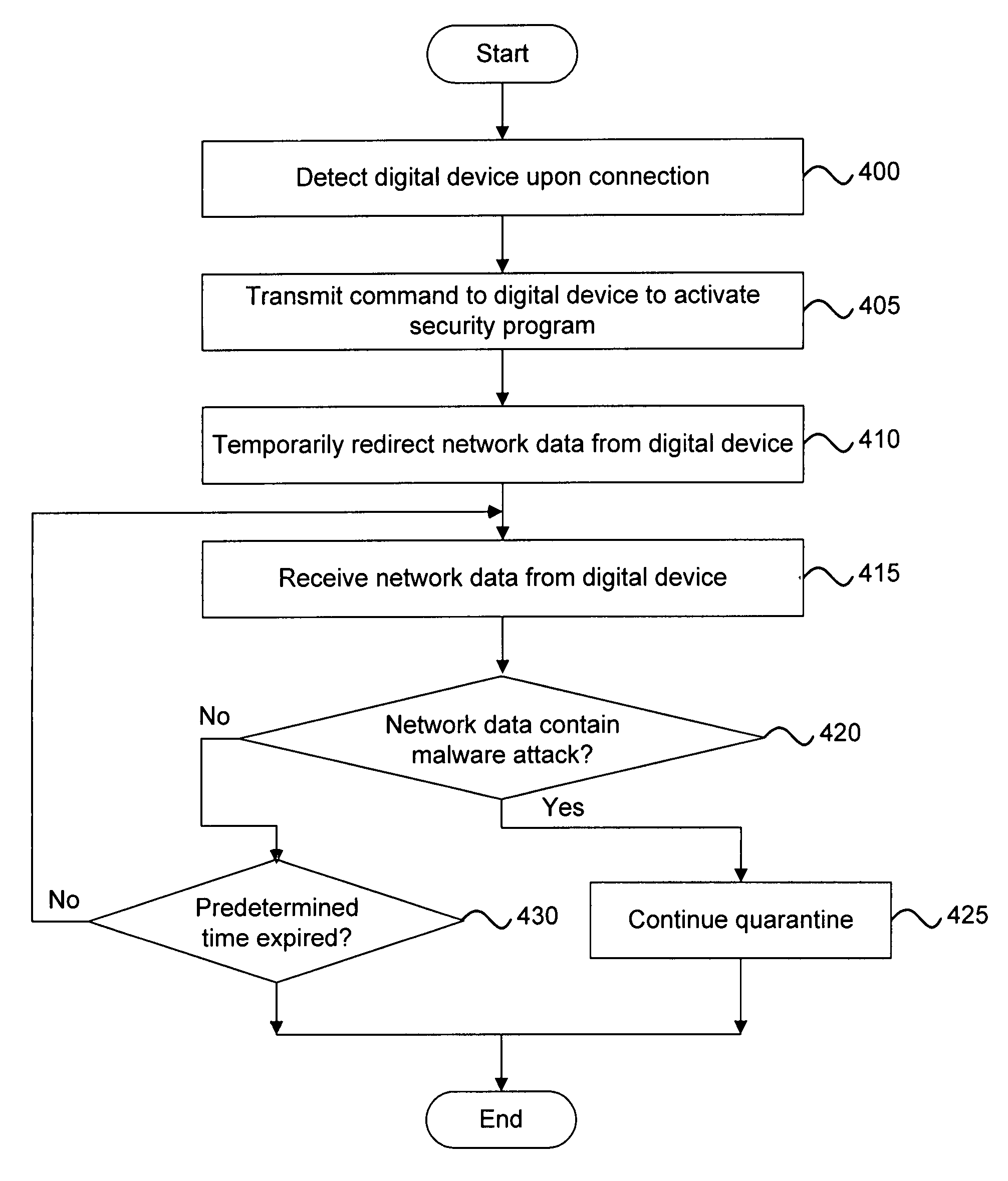
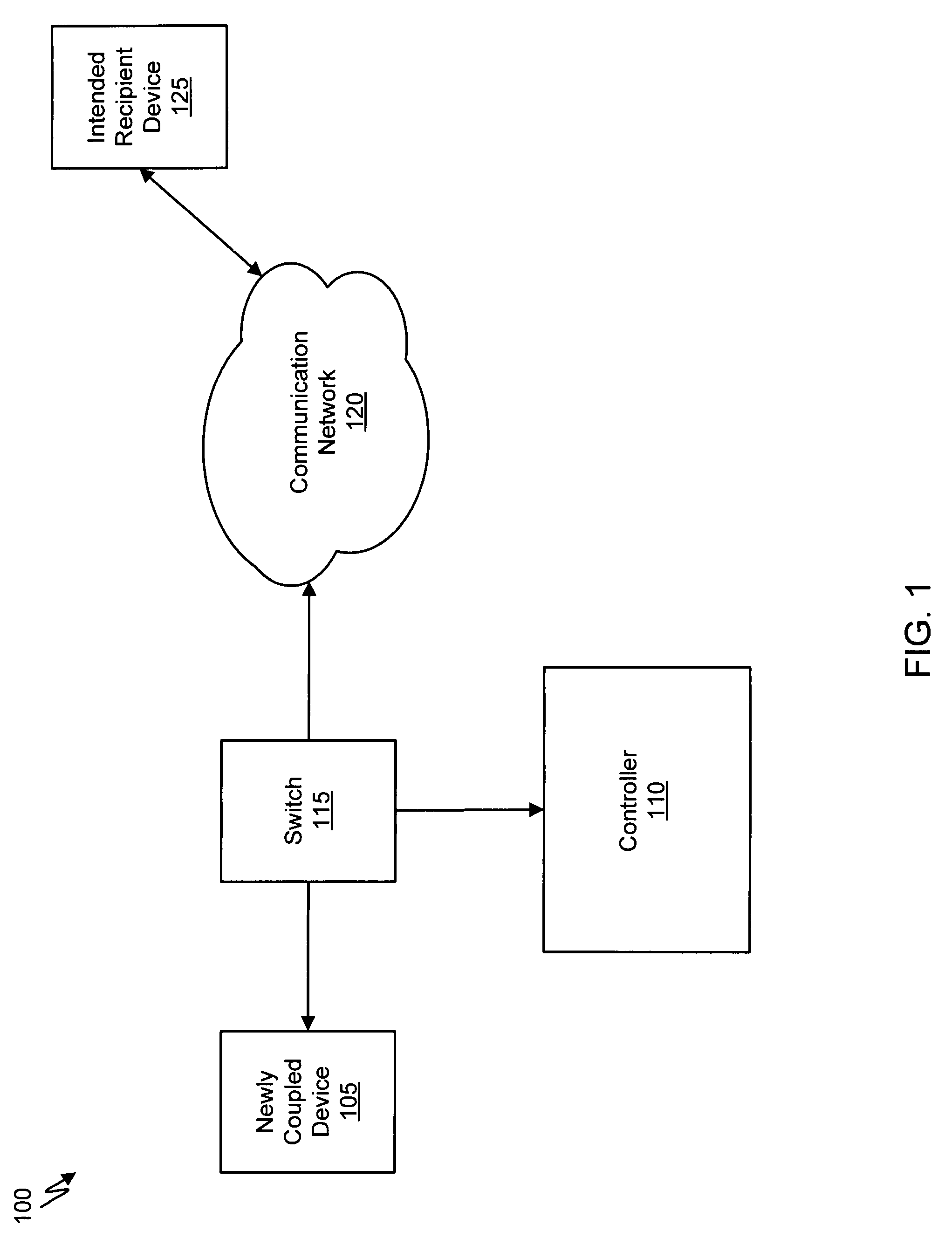
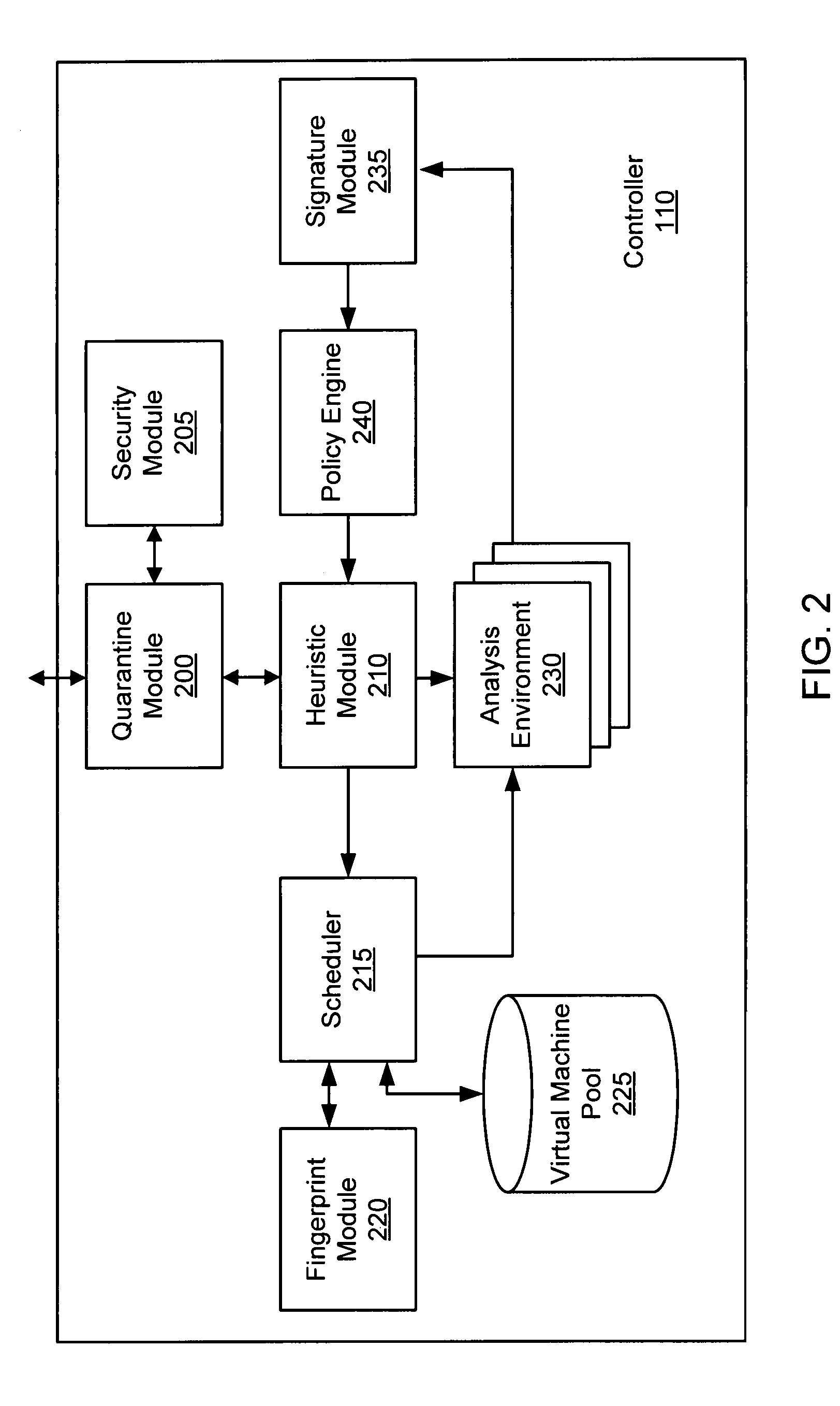
Malware containment and security analysis on connection
Systems and methods for malware containment and security analysis on connection are provided. Digital devices are quarantined for a predetermined period of time upon connection to the communication network. When a digital device is quarantined, all network data transmitted by the digital device is directed to a controller which then analyzes the network data to identify unauthorized activity and / or malware within the newly connected digital device. An exemplary method to contain malware includes detecting a digital device upon connection with a communication network, quarantining network data from the digital device for a predetermined period of time, transmitting a command to the digital device to activate a security program to identify security risks, and analyzing the network data to identify malware within the digital device.
Owner:FIREEYE SECURITY HLDG US LLC
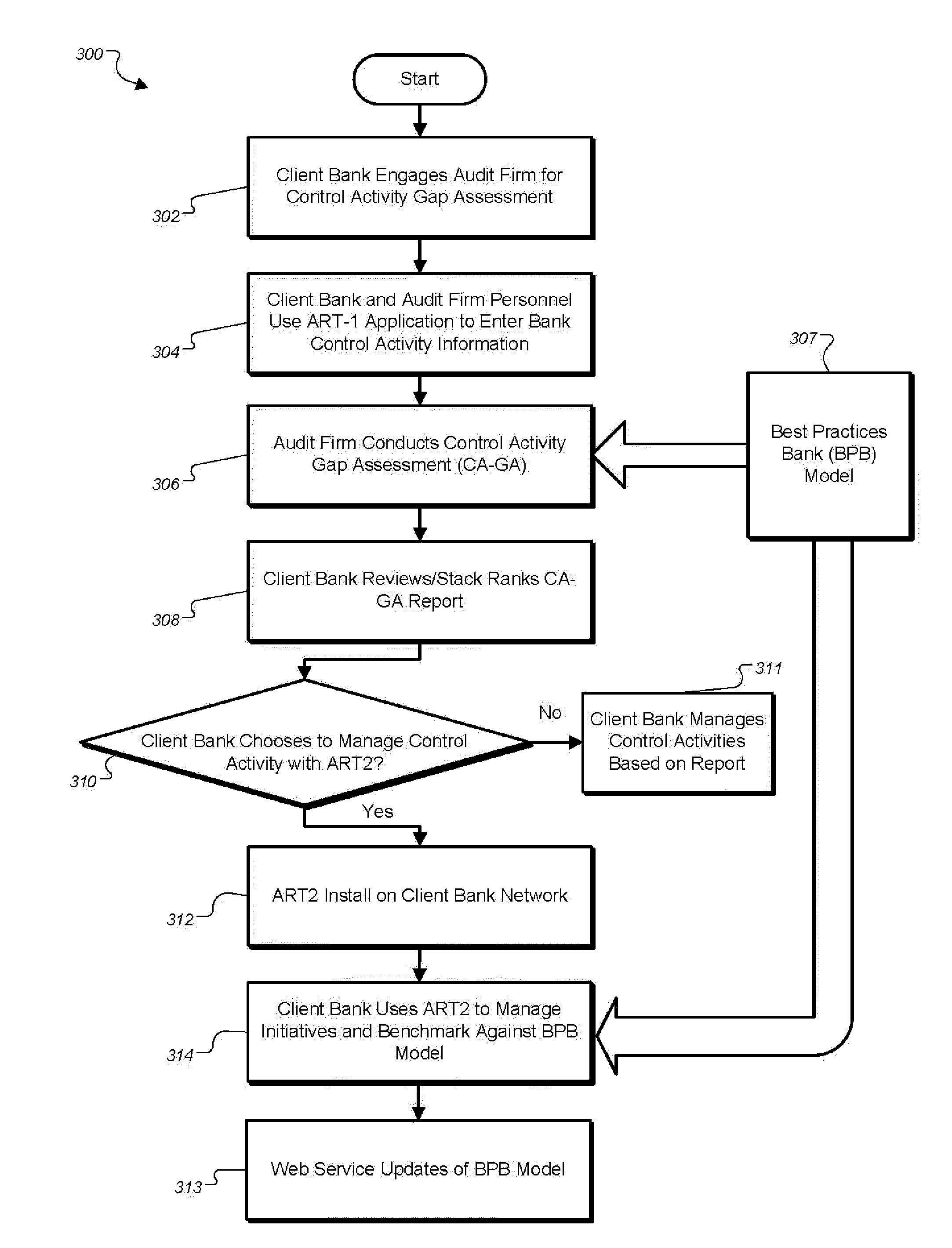
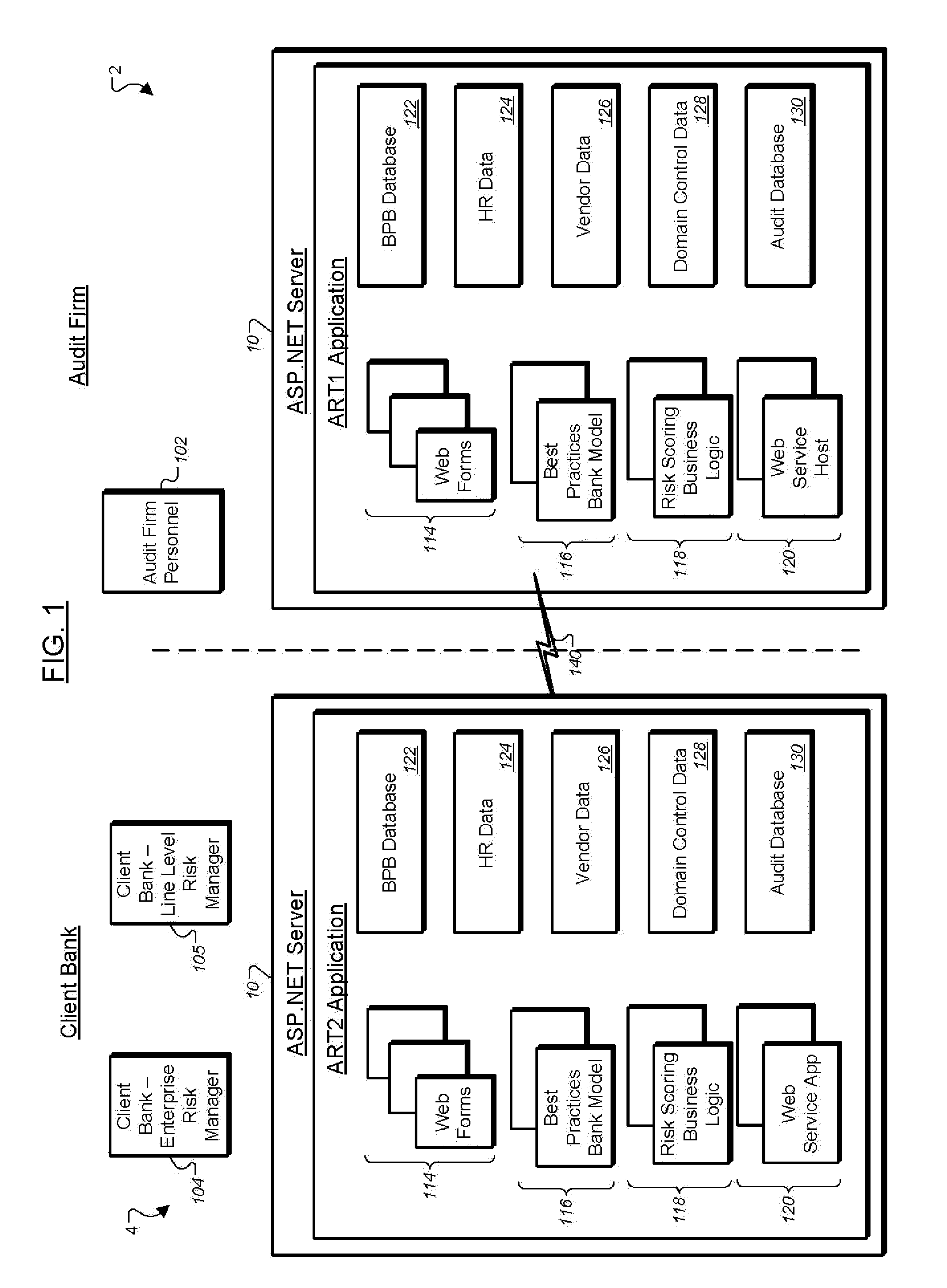
Financial audit risk tracking systems and methods
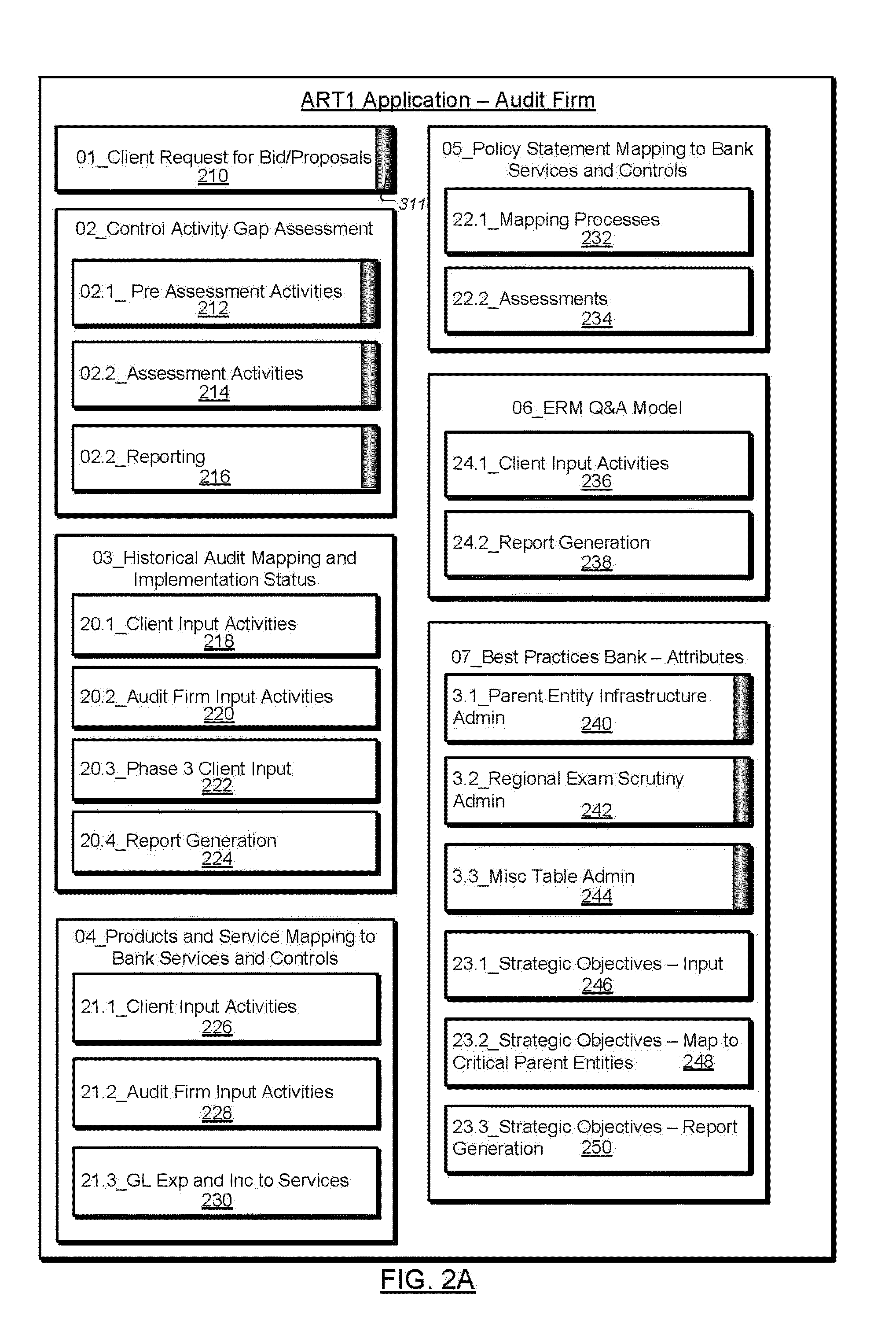
A system is provided for audit risk and tracking (ART) including an audit firm application (ART1) and a client bank application (ART2). The system maintains a data model of control activities for a best practices bank (BPB), against which control activity gap assessments are conducted for client banks. An interactive gap assessment report allows insight into controls that are lacking versus the BPB. The ART1 and ART2 systems interact to allow the client bank to interact with the audit firm to cooperate in assessing and managing business initiatives and other control, audit, and ERM activity. Novel risk scoring assessments are provided to help manage client bank controls in relation to the BPB model. A web service is provided that automatically updates the BPB model from ART1 to ART2.
Owner:BSA SERVICES L L C
Verification and authentication systems and methods
ActiveUS20080086759A1Improve securityMinimal amountDigital data processing detailsUser identity/authority verificationRisk levelExternal data
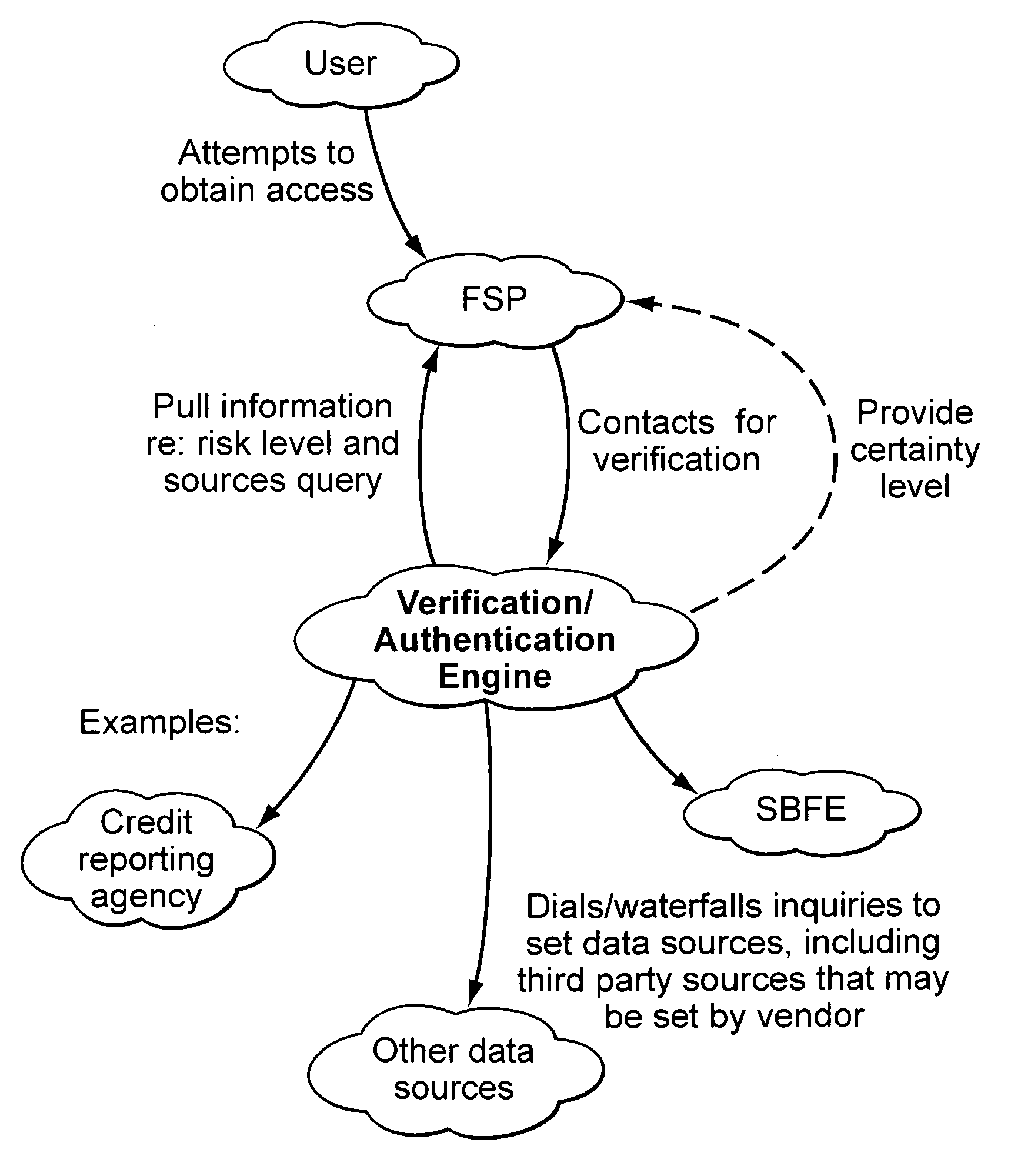
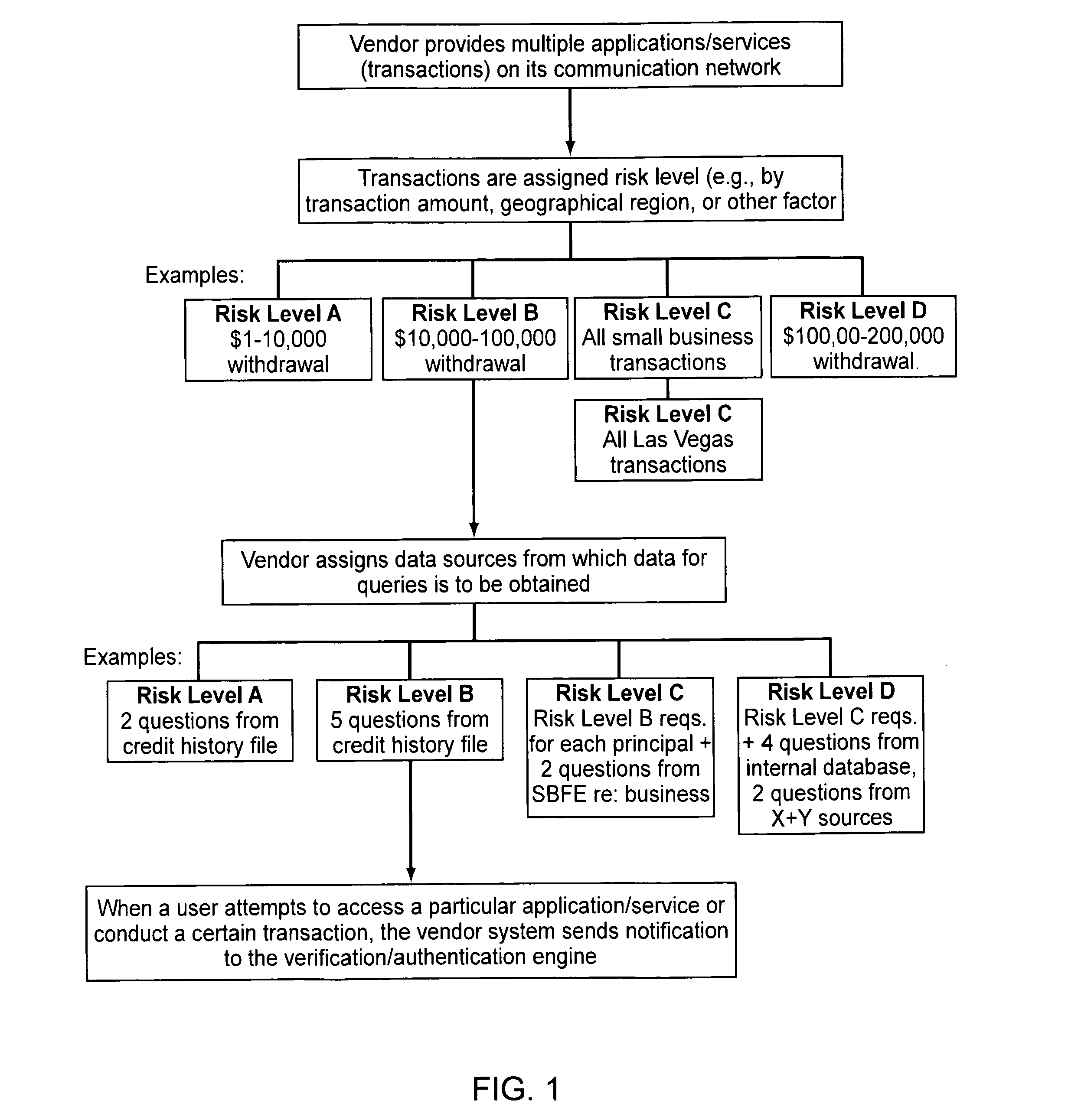
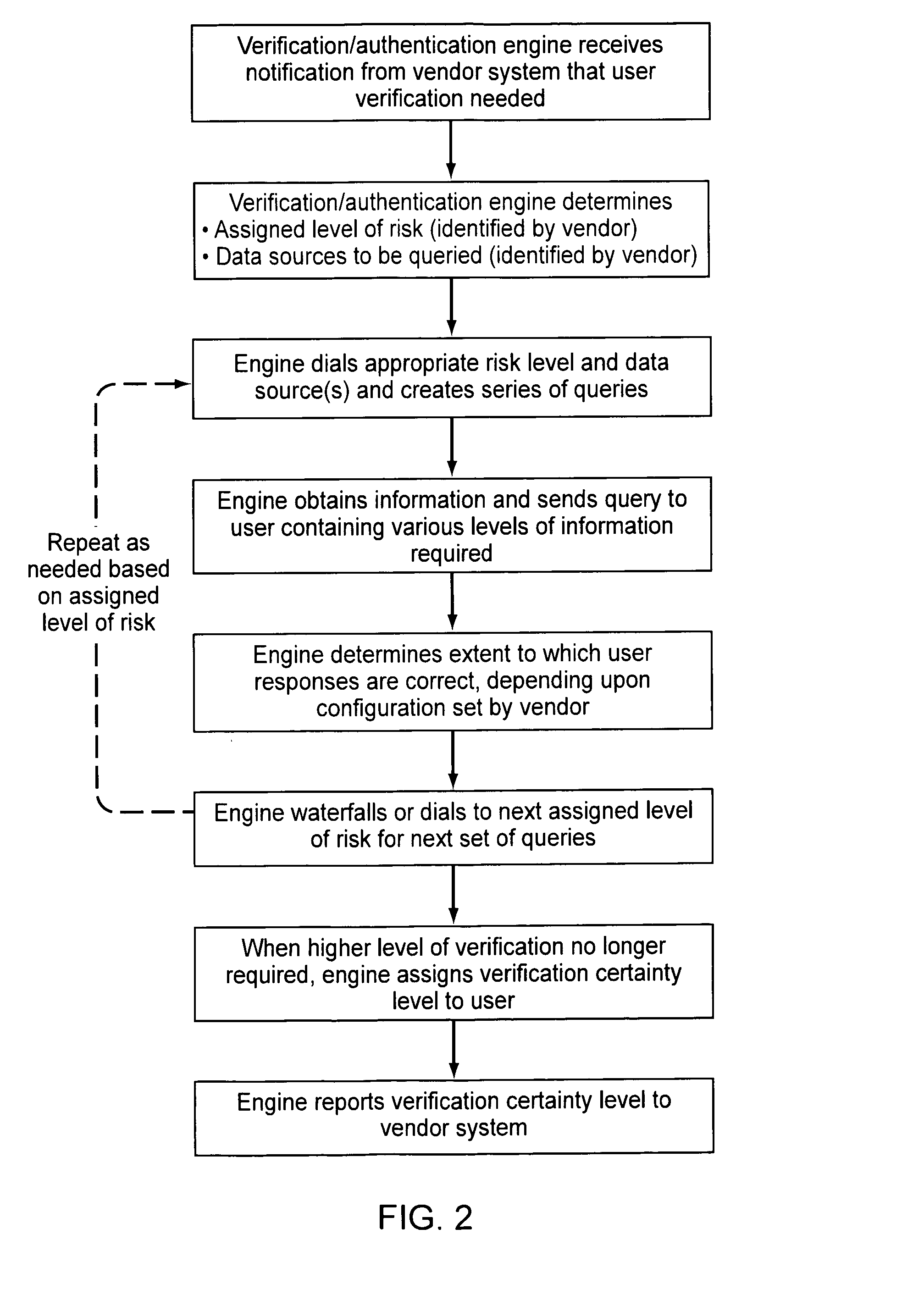
Embodiments of the present invention provide verification and / or authentication service engines that provide a customizable solution that can be “dialed” based on the risk level assigned to individual or grouped applications. The systems can also incorporate internal and external sources of data used to verify information provided by the user. It is dynamic and can pull information from a myriad of sources during the verification process, enabling credit reporting agencies (e.g., Equifax and others), FSPs, and other service providers to facilitate real-time approval and access to products and services.
Owner:EQUIFAX INC
Artificial intelligence early warning system
ActiveCN109447048APrevent overpassSemantic analysisOther databases indexingThree levelInformation resource
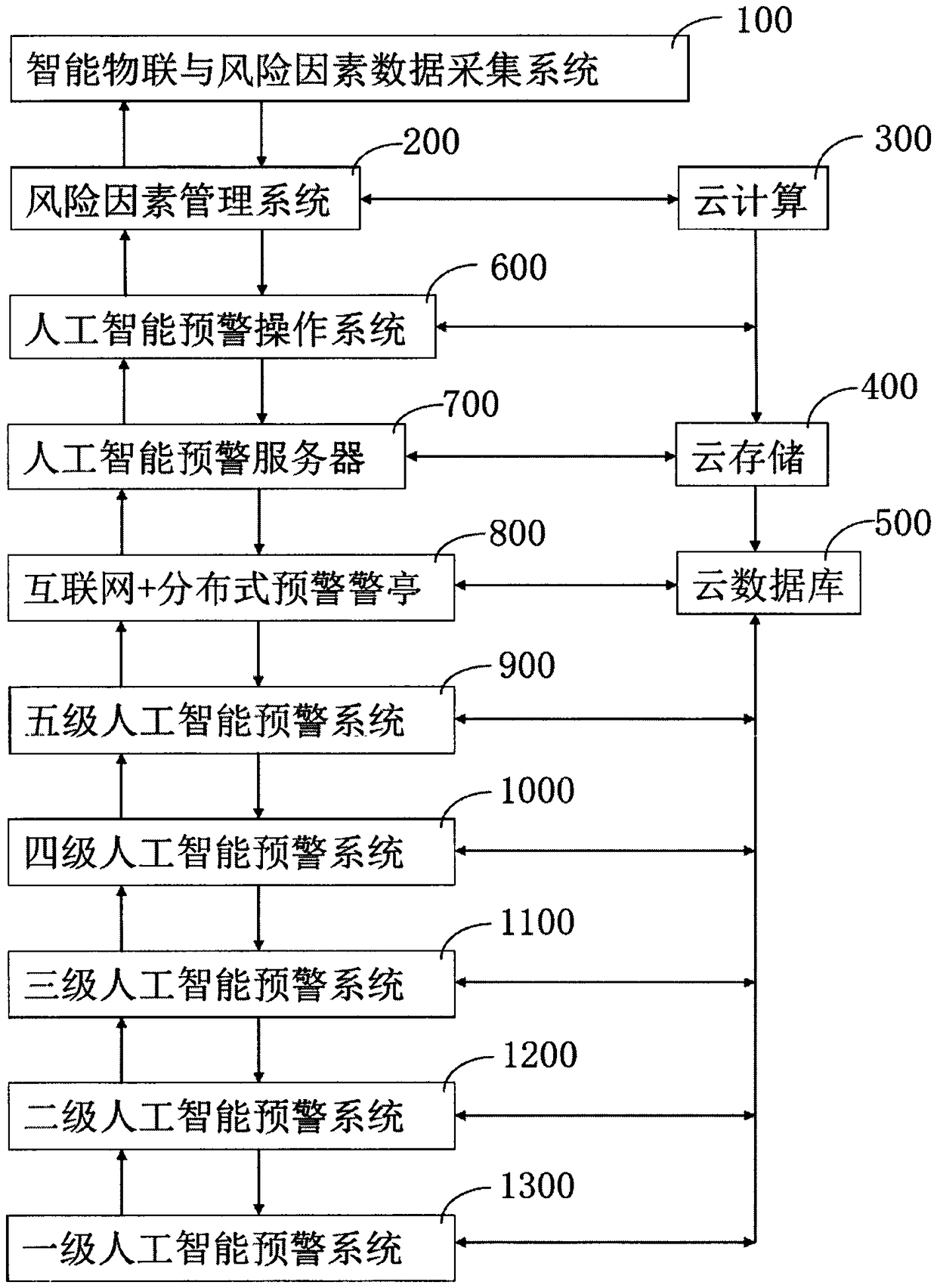
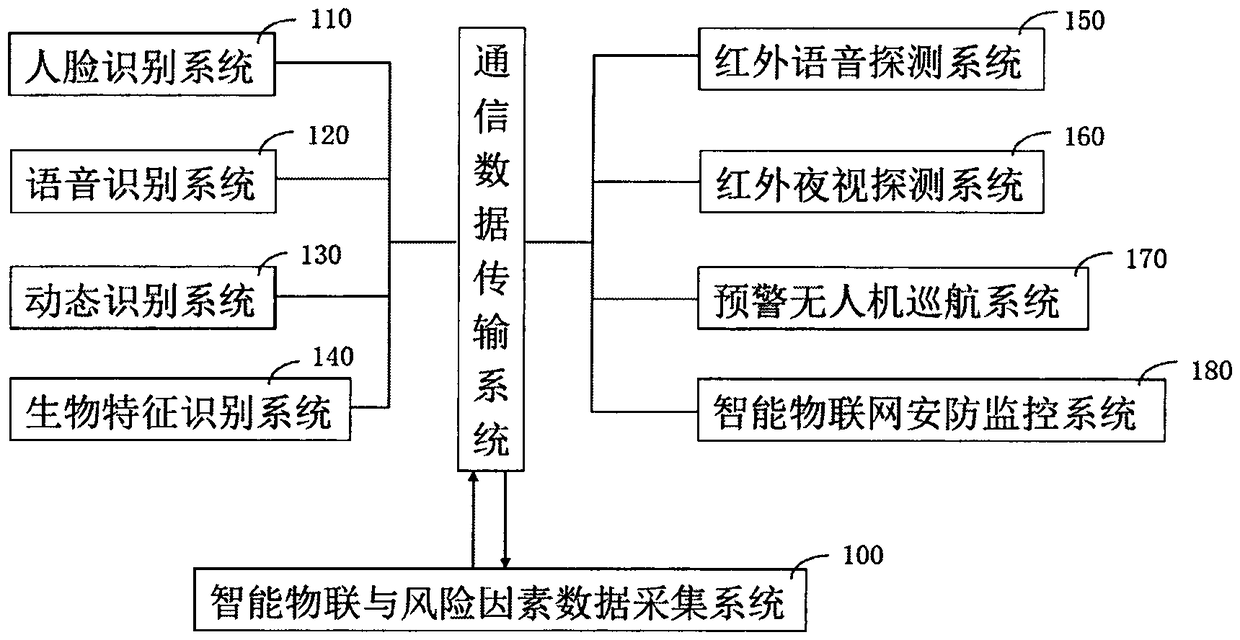
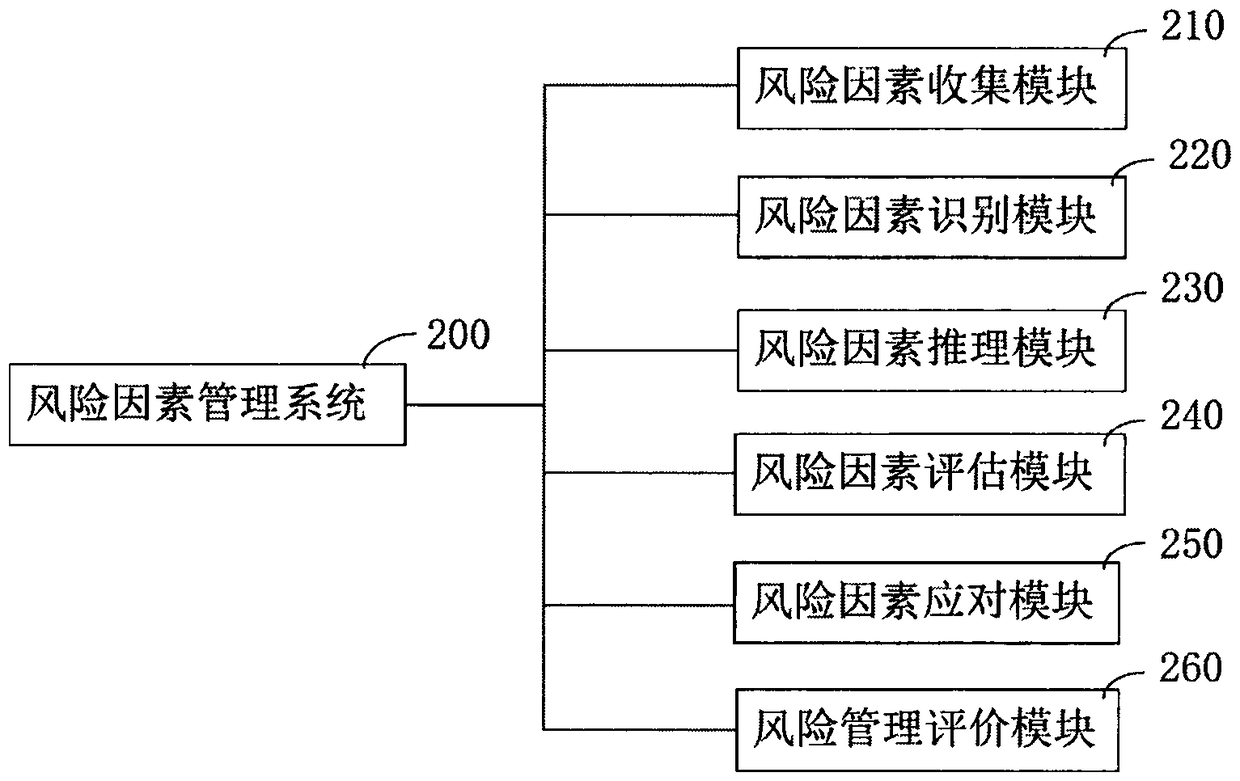
The invention relates to an artificial intelligence early warning system. The system comprises an intelligent Internet of Things and risk factor data acquisition system (100), and a risk factor management system (200), a cloud computing device (300), a cloud storage device (400), a cloud database (500), and an artificial intelligence early warning operation system (600), an artificial intelligenceearly warning server (700), an internet + distributed early warning police booth (800), a five-level artificial intelligence early warning system (900), a four-level artificial intelligence early warning system (1000), a three-level artificial intelligence early warning system (1100), a two-level artificial intelligence early warning system (1200) and a one-level artificial intelligence early warning system (1300). The artificial intelligence early warning system of the present invention collects, compares, analyzes, deduces, evaluates the risk factors, and carries out the cloud computing, cloud storage, graded alarming and prevention and control, so that all-weather 24-hour monitoring on monitoring points around the police box is achieved, a user can share information, the utilization rate of information resources is increased, and the safety guarantee is increased for maintaining the stability of the borderlands.
Owner:苏州闪驰数控系统集成有限公司
Design of computer based risk and safety management system of complex production and multifunctional process facilities-application to fpso's
InactiveUS20120317058A1Strong robust attributeStrong robust attributesDigital computer detailsFuzzy logic based systemsProcess systemsNerve network
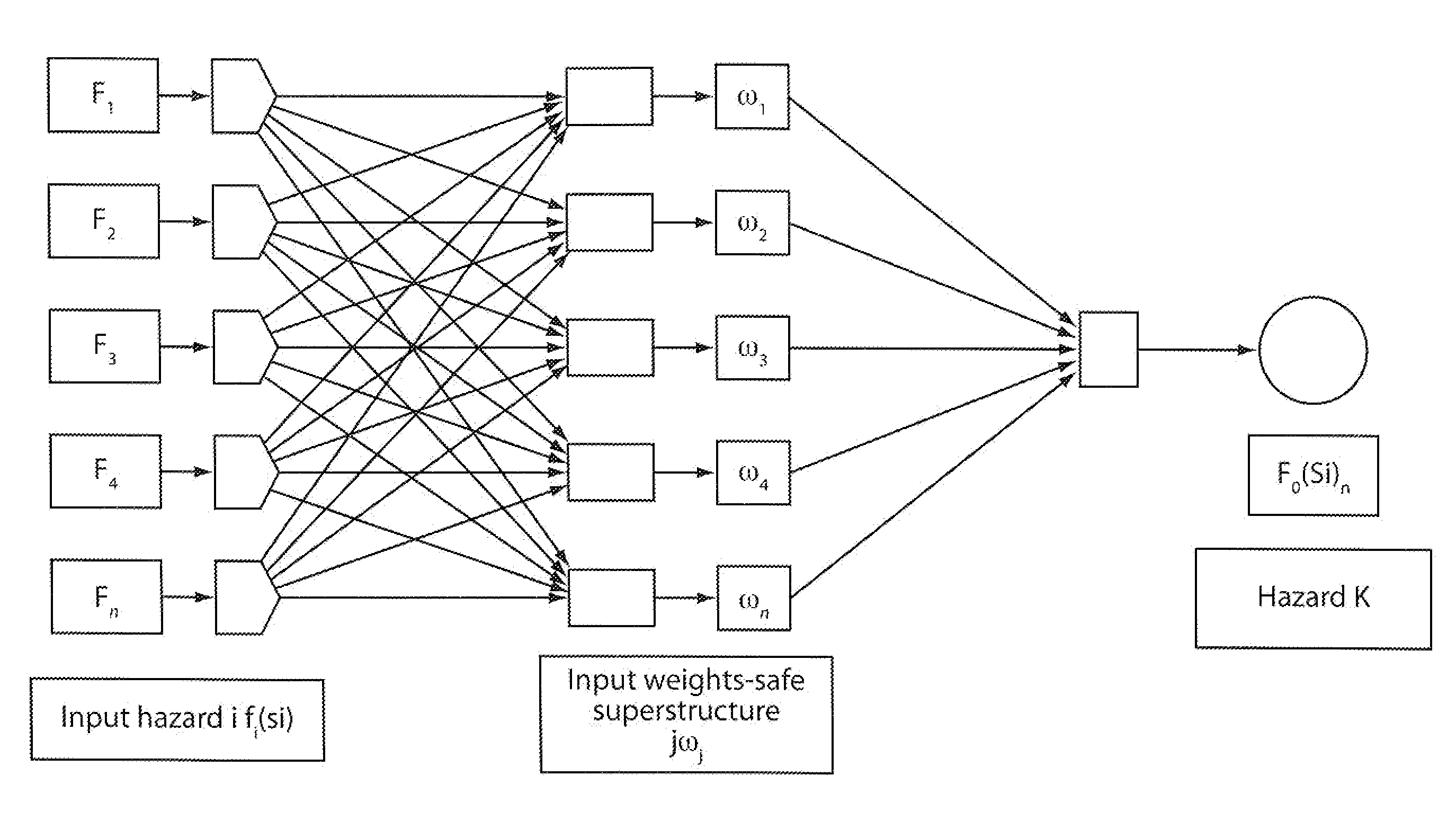
A method for predicting risk and designing safety management systems of complex production and process systems which has been applied to an FPSO System operating in deep waters. The methods for the design were derived from the inclusion of a weight index in a fuzzy class belief variable in the risk model to assign the relative numerical value or importance a safety device or system has contain a risk hazards within the barrier. The weights index distributes the relative importance of risk events in series or parallel in several interactive risk and safety device systems. The fault tree, the FMECA and the Bow Tie now contains weights in fizzy belief class for implementing safety management programs critical to the process systems. The techniques uses the results of neural networks derived from fuzzy belief systems of weight index to implement the safety design systems thereby limiting use of experienced procedures and benchmarks. The weight index incorporate Safety Factors sets SFri {0, 0.1, 0.2 . . . 1}, and Markov Chain Network to allow the possibility of evaluating the impact of different risks or reliability of multifunctional systems in transient state process. The application of this technique and results of simulation to typical FPSO / Riser systems has been discussed in this invention.
Owner:ABHULIMEN KINGSLEY E
End user risk management
ActiveUS20060020814A1Respond effectivelyMemory loss protectionDigital data processing detailsReal time analysisComputer science
A flexible, efficient and easy-to-use computer security management system effectively evaluates and responds to informational risks on a wide variety of computing platforms and in a rapidly changing network environment. An individual computer system dynamically monitors its end user, without regard to network connectivity, in order to calculate a risk score and to ensure that the end user's behavior does not put corporate information or other assets at risk. Data regarding such risks and responses are analyzed and stored in real-time.
Owner:CITRIX SYST INC
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
Malicious attack detection and analysis
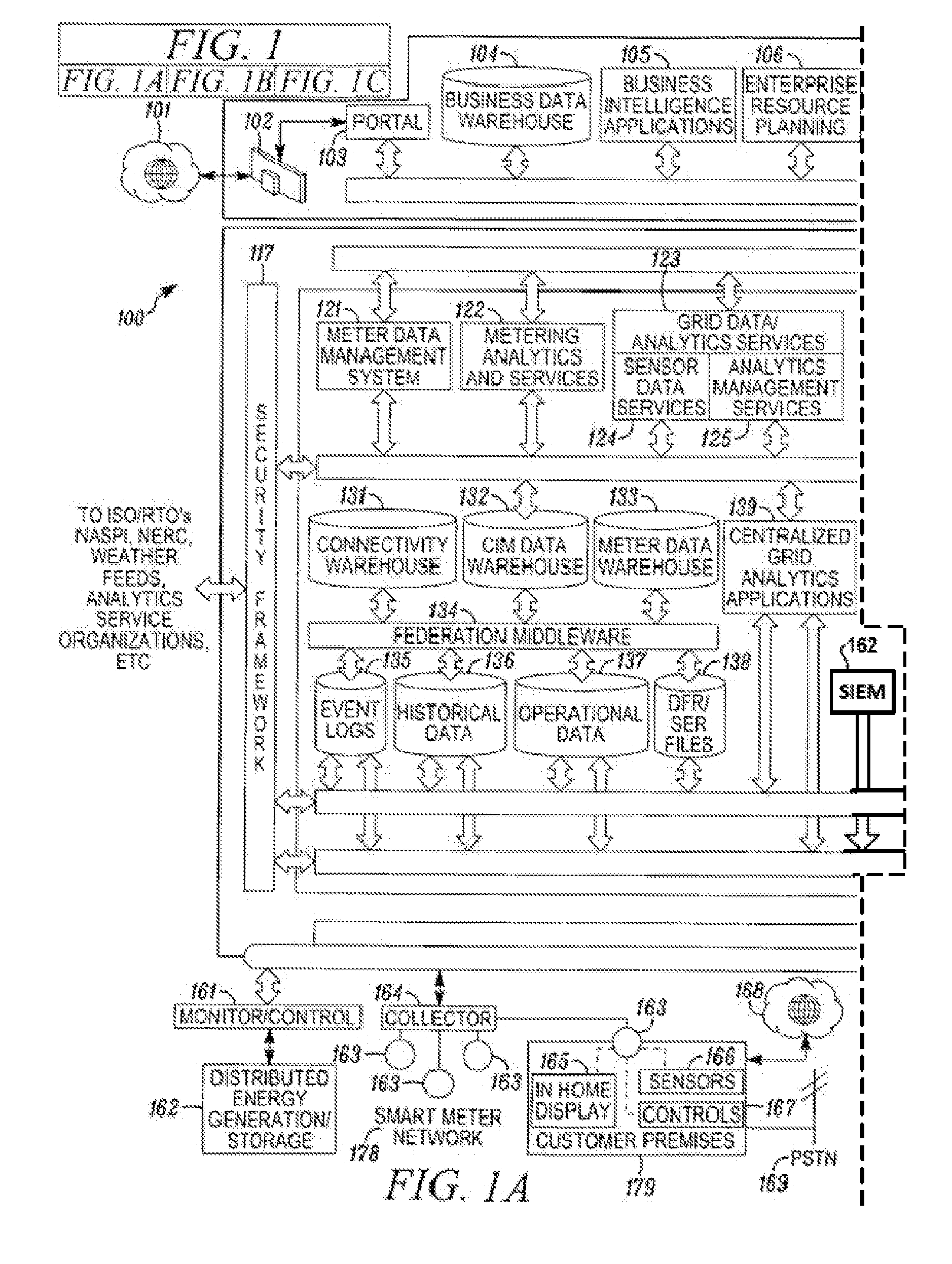
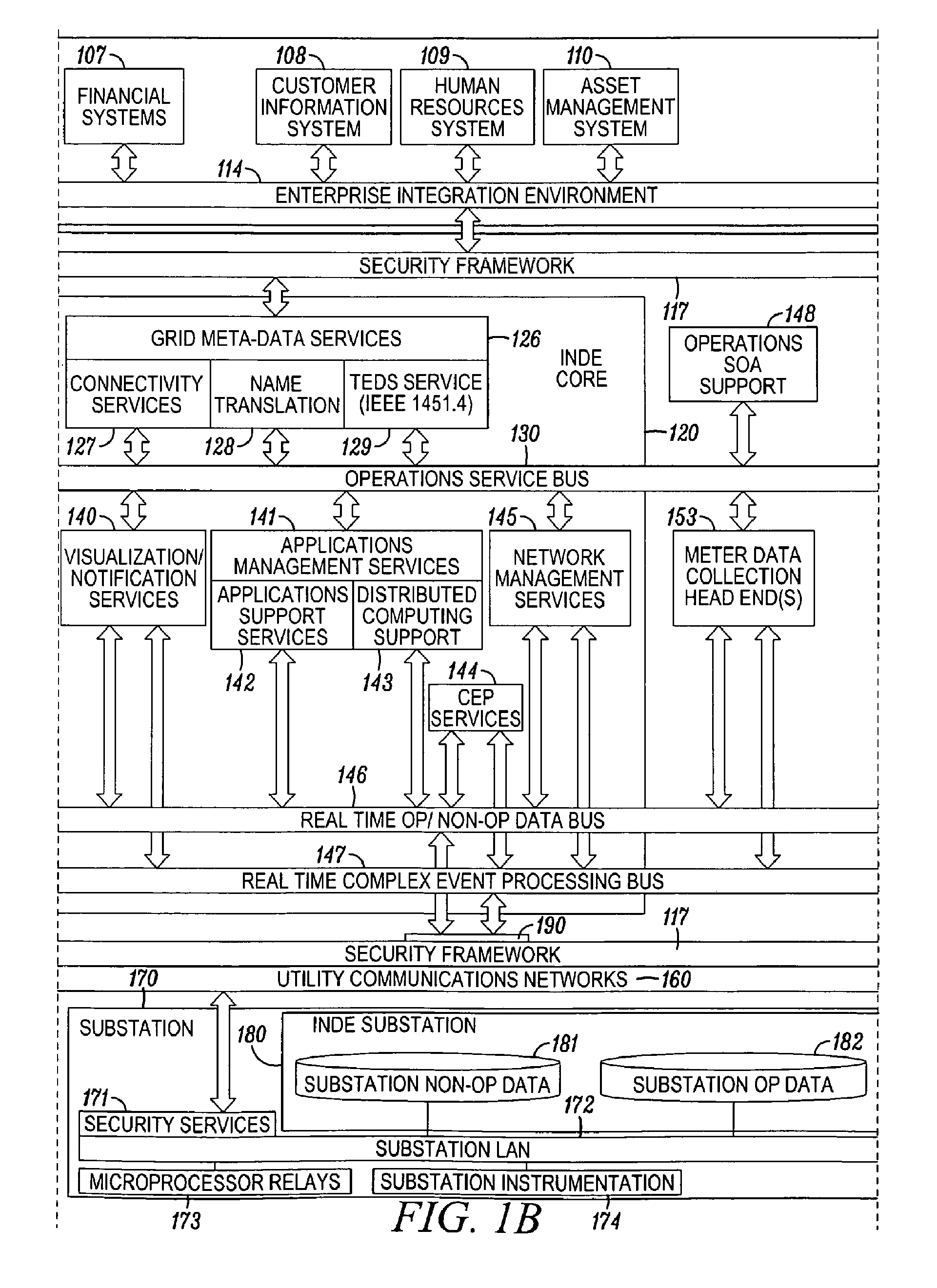
A system for characterizing malicious activity in an intelligent utility grid system includes a system storage in which to store a database including a plurality of rules. A collector is operable to collect and store in the system storage information-technology (IT) data including IT-related activity from the intelligent grid system. A complex event processing (CEP) bus is operable to receive non-IT data including location-specific event data from a plurality of electronic sources, the CEP bus further operable to disregard the non-IT data failing to meet a predetermined level of relevance to one of a plurality of risk-related events. A processor is operable to apply the plurality of rules to the relevant non-IT data to: associate an undesired event with reference to the IT-related activity; and determine a probability that the undesired event is indicative of malicious activity. The processor further applies a risk characterization to the undesired event based on the probability and the IT-related activity.
Owner:ACCENTURE GLOBAL SERVICES LTD
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
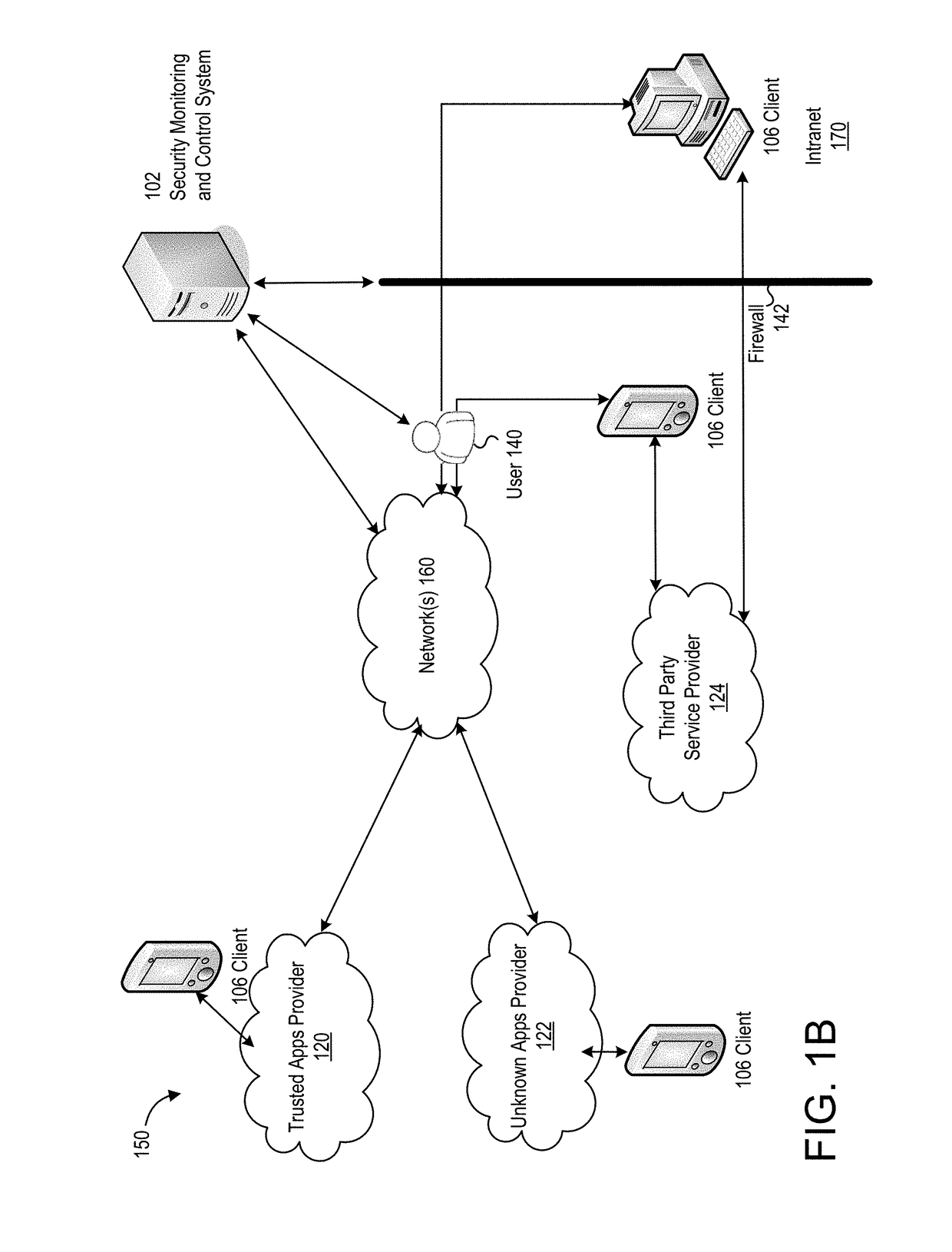
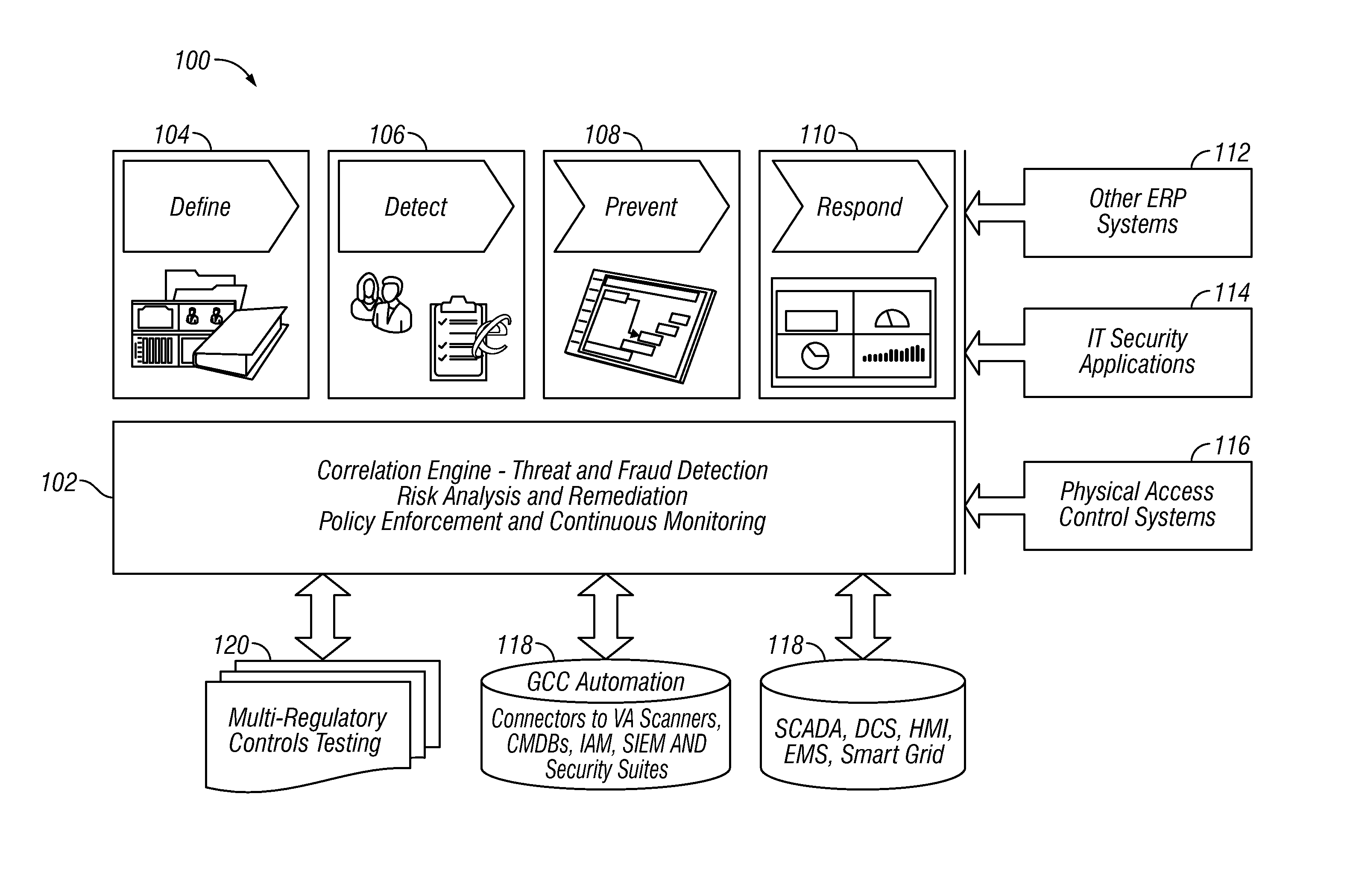
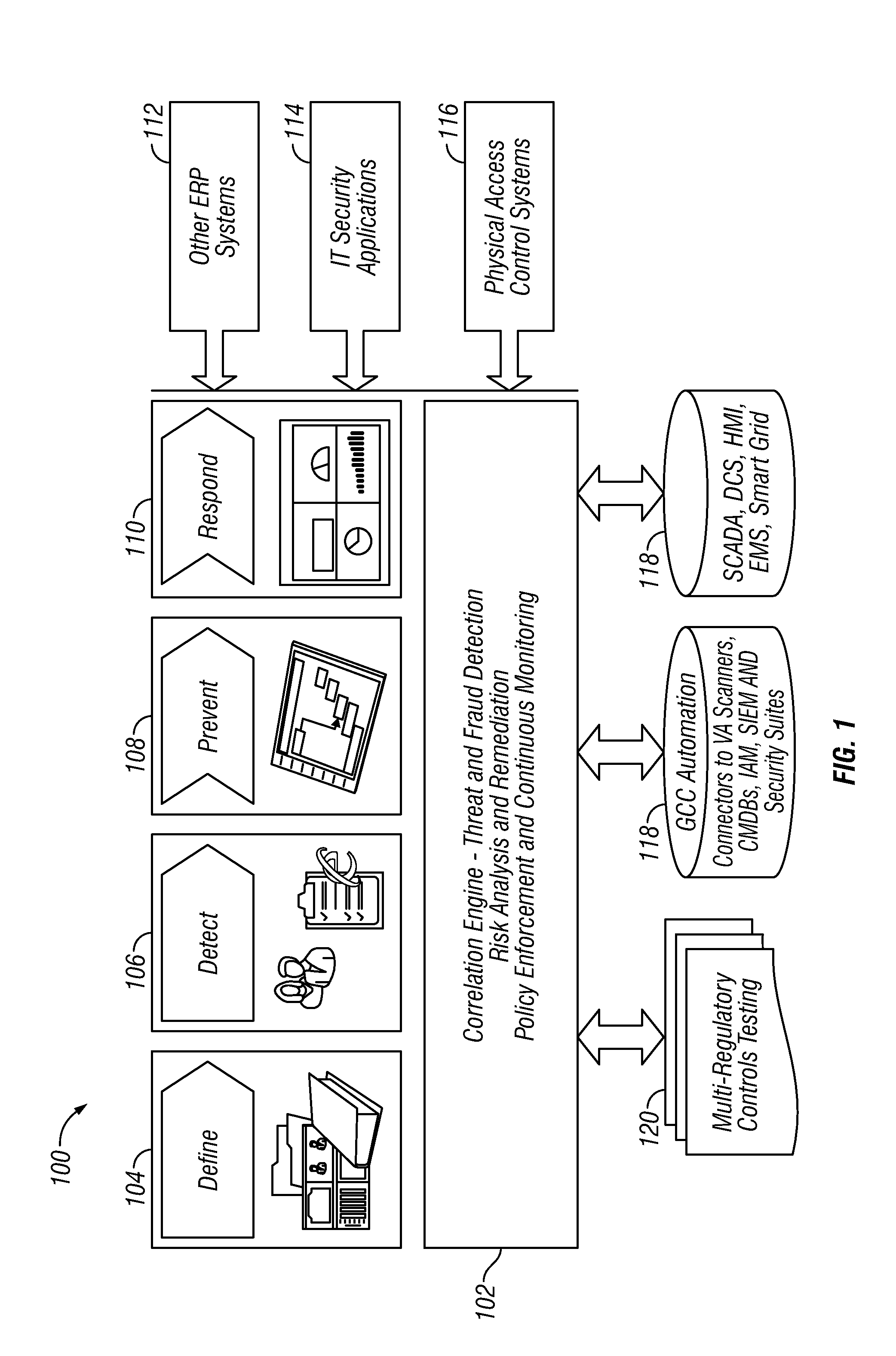
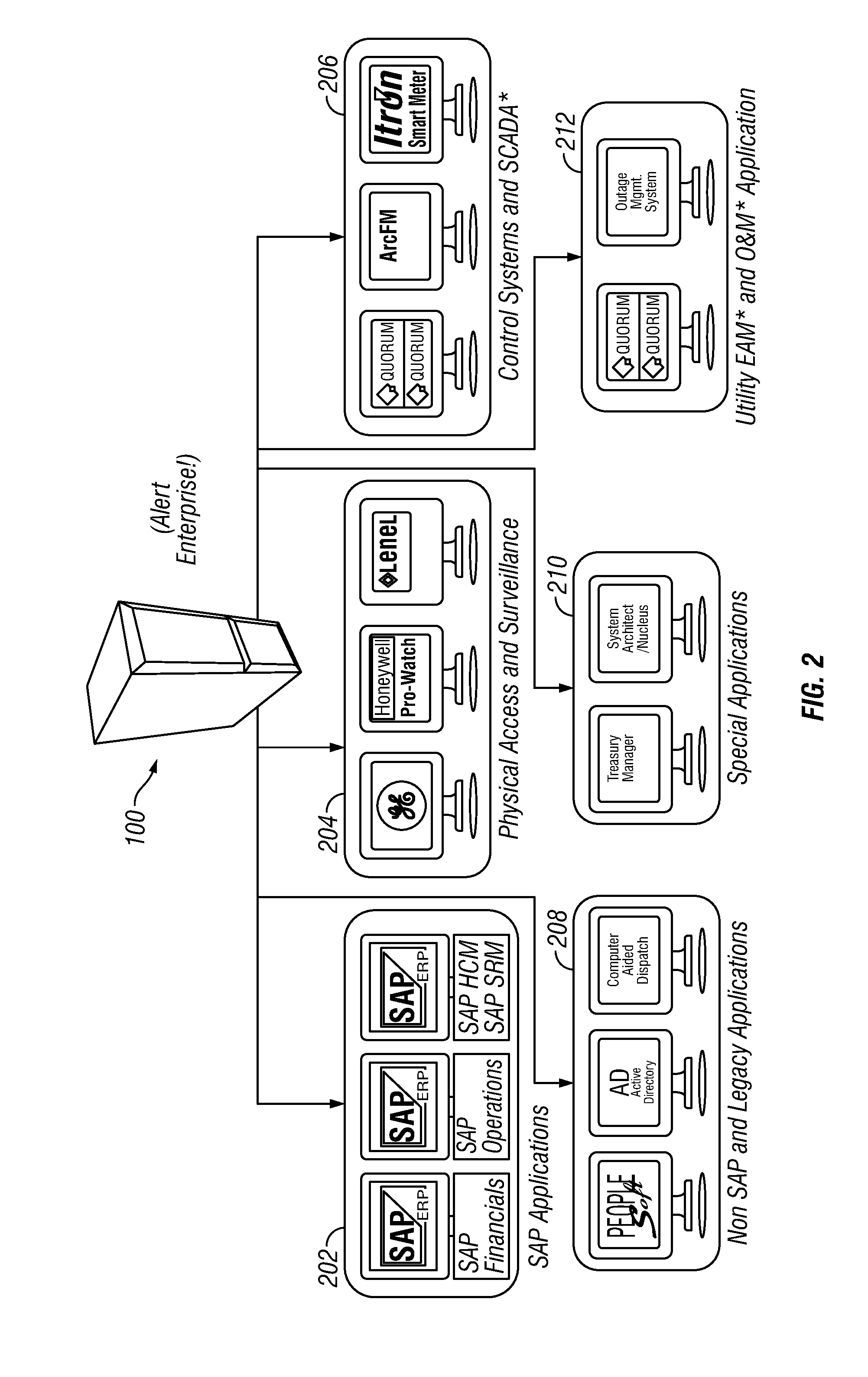
Situational intelligence
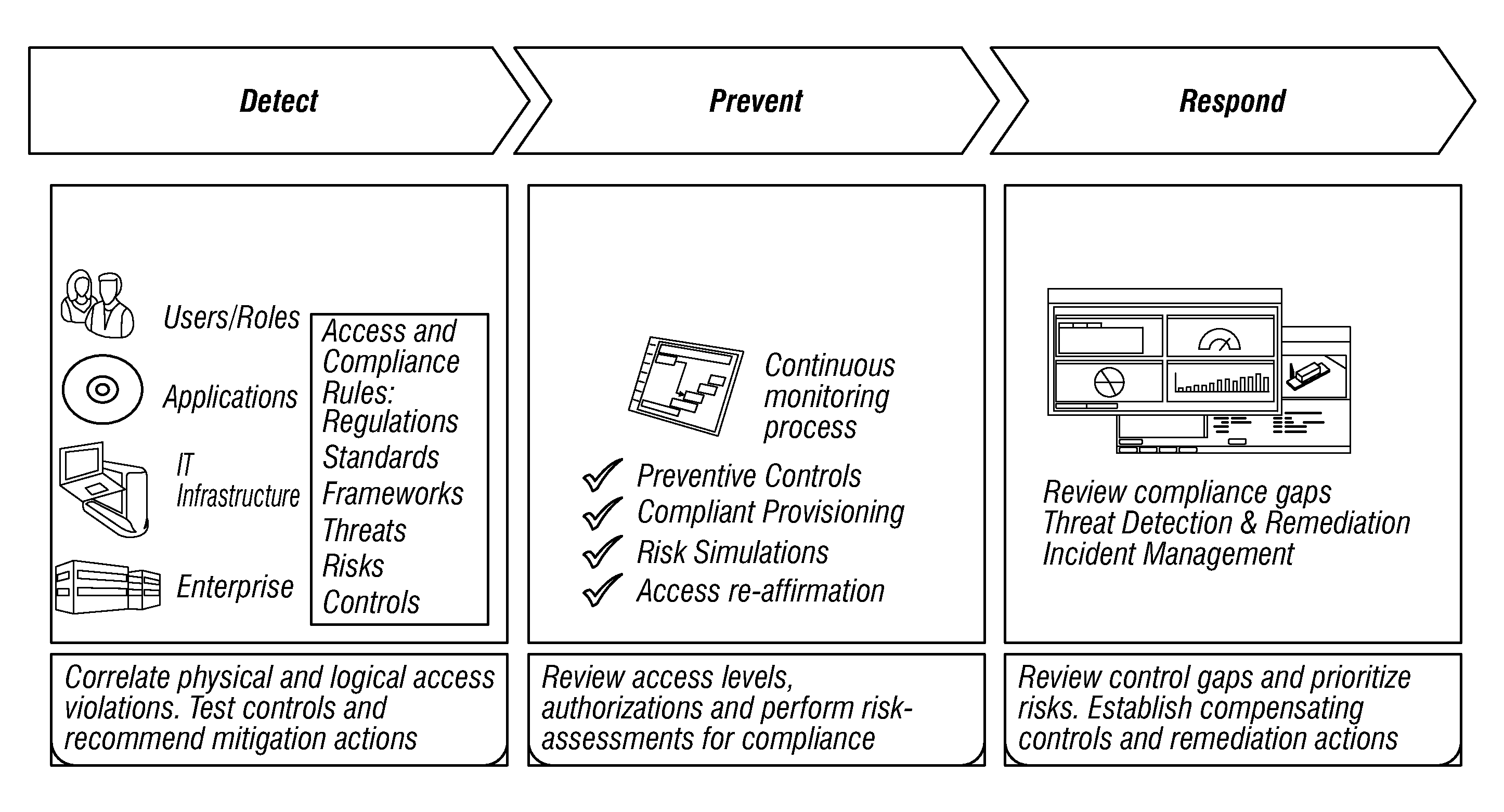
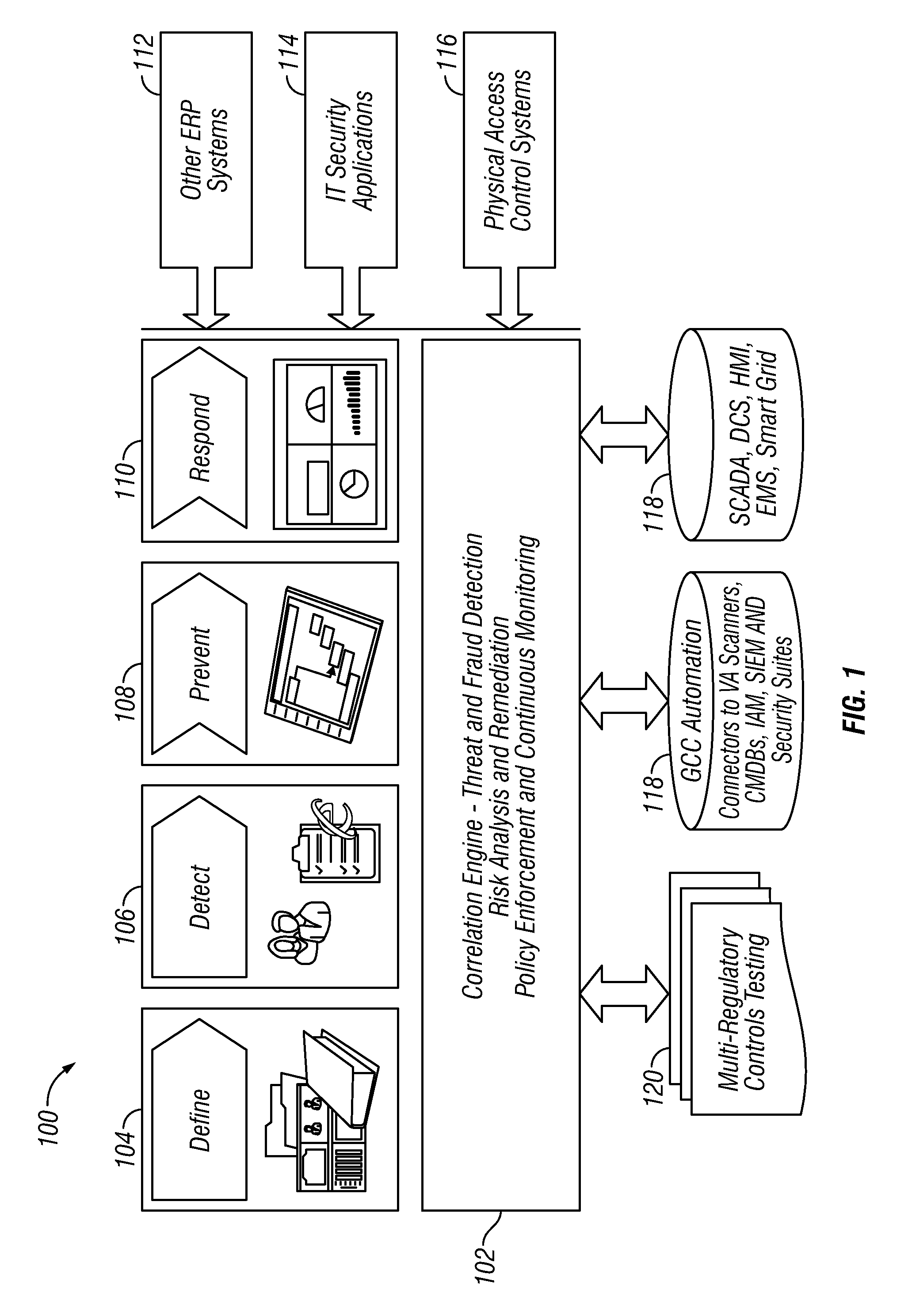
ActiveUS20120224057A1Color television detailsClosed circuit television systemsDashboardRemedial action
A method and apparatus is provided that includes techniques for providing complete solutions for role-based, rules-driven access enforcement, the techniques including situational awareness and video surveillance. An embodiment addresses blended risk assessment and security across logical systems, IT applications, databases, and physical systems from a single analytic dashboard, with auto-remediation capabilities. Further, an embodiment provides capability and functionality for co-relating seemingly innocent events and activities to detect real threats and risks, while providing powerful alerting and automated remedial action strategies for decisive action.
Owner:ALERT ENTERPRISE
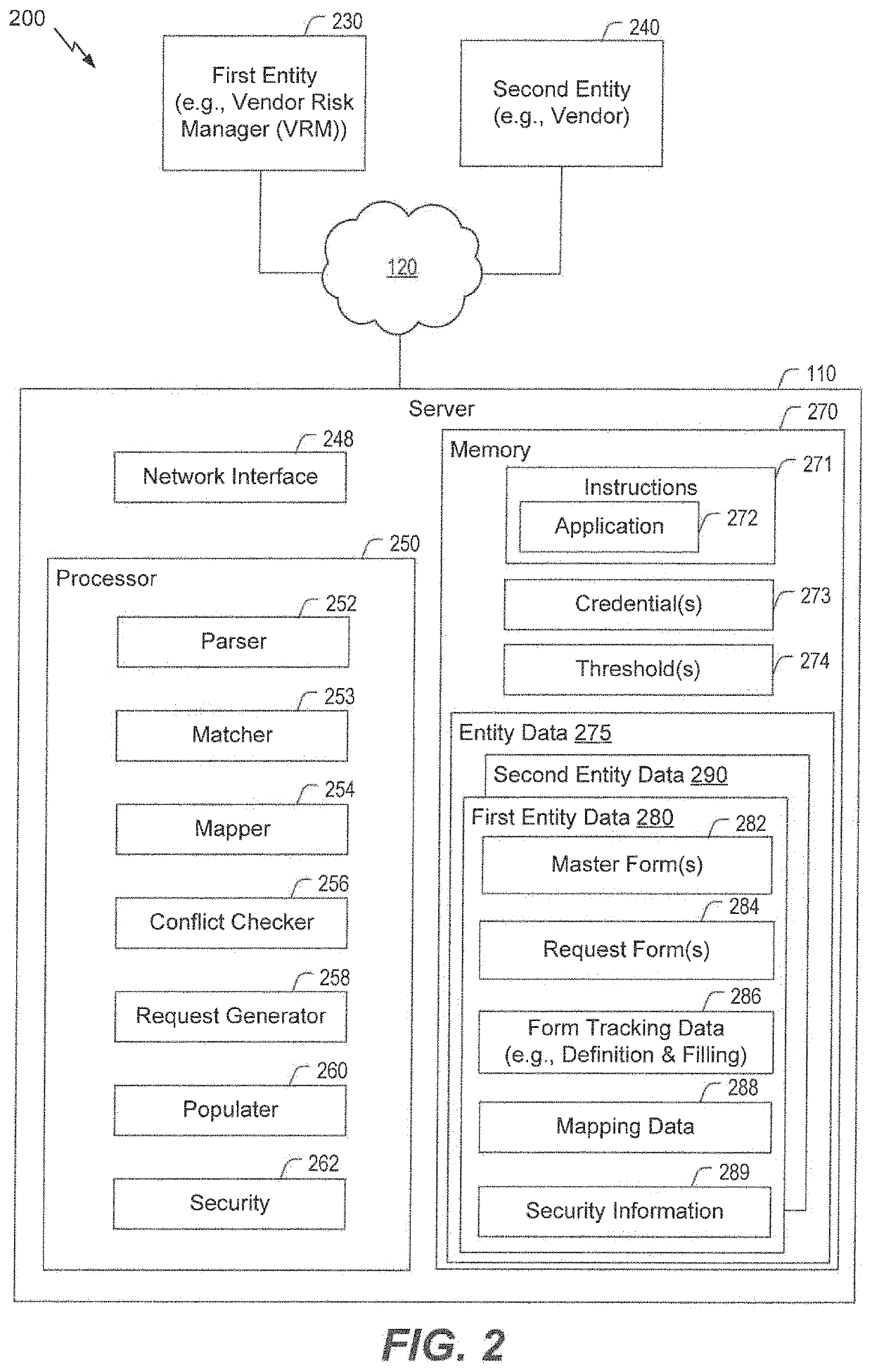
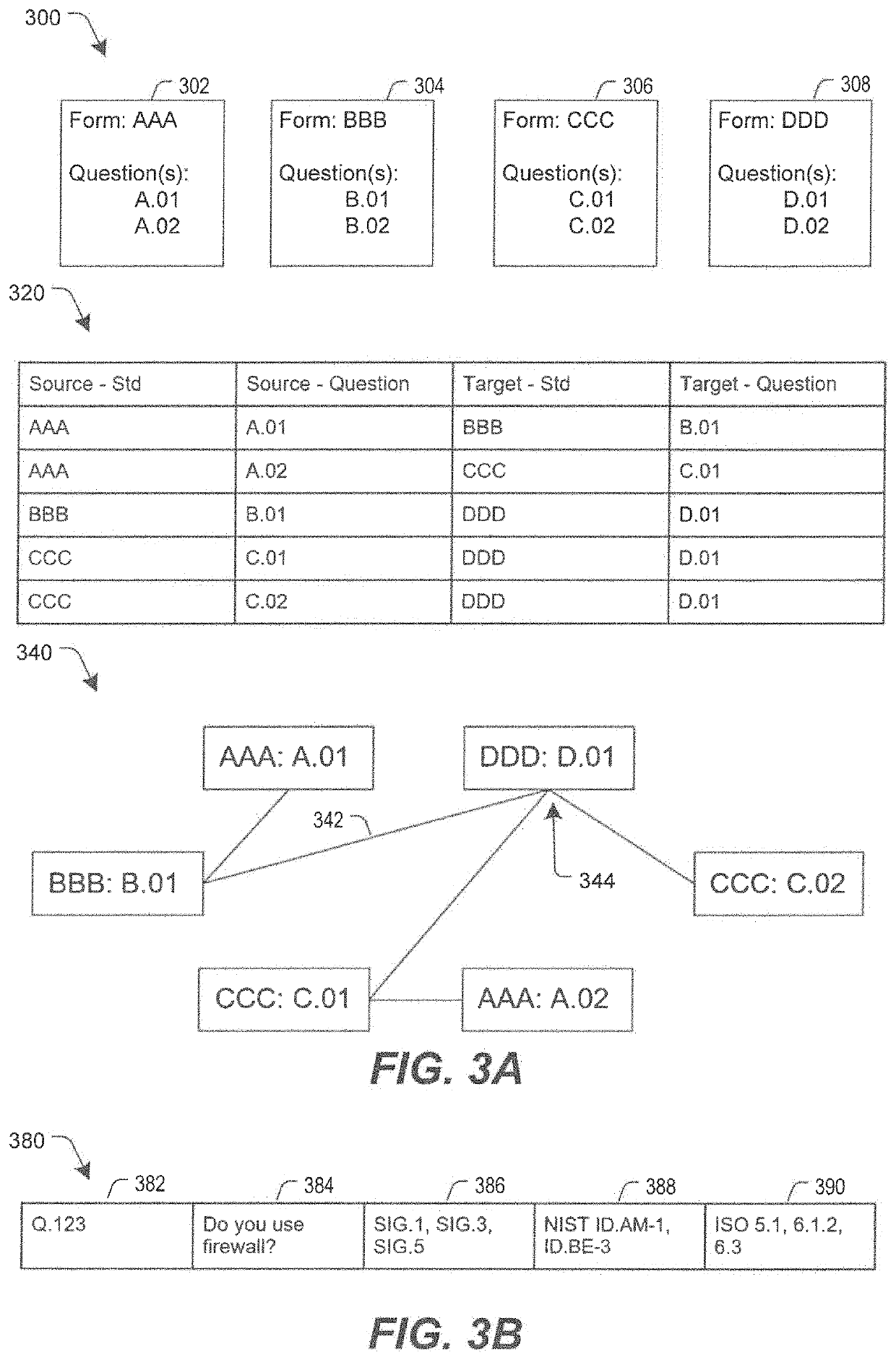
Inquiry response mapping for determining a cybersecurity risk level of an entity
ActiveUS10546135B1Reduce future data conflictImprove response mappingPlatform integrity maintainanceMachine learningRisk levelData set
The present disclosure provides a method, system, and device for inquiry response mapping for determining a cybersecurity risk level of an entity. To manage and / or evaluate a cybersecurity risk level based on a relationship between a first entity and a second entity, questionnaires (e.g., requests or inquires) are often exchanged between two entities. One or more aspects of the present disclosure provide populating data sets (e.g., questionnaires) indicative of risk level for the first entity or the second entity. One or more other aspects of the present disclosure further provide determining a cybersecurity risk level of an entity by mapping responses to a plurality of inquiry sets directed to the first entity or the second entity.
Owner:SECURITYSCORECARD
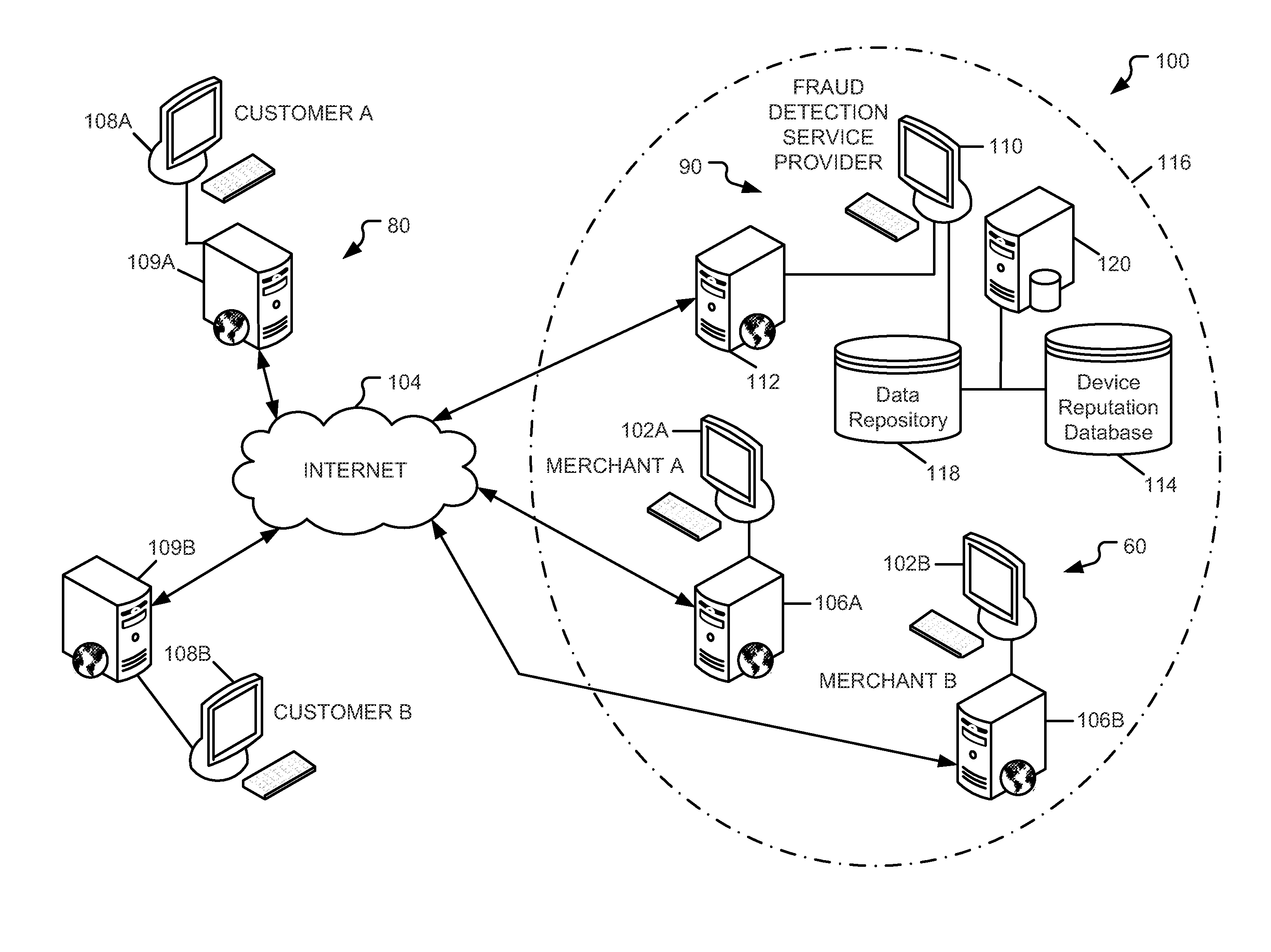
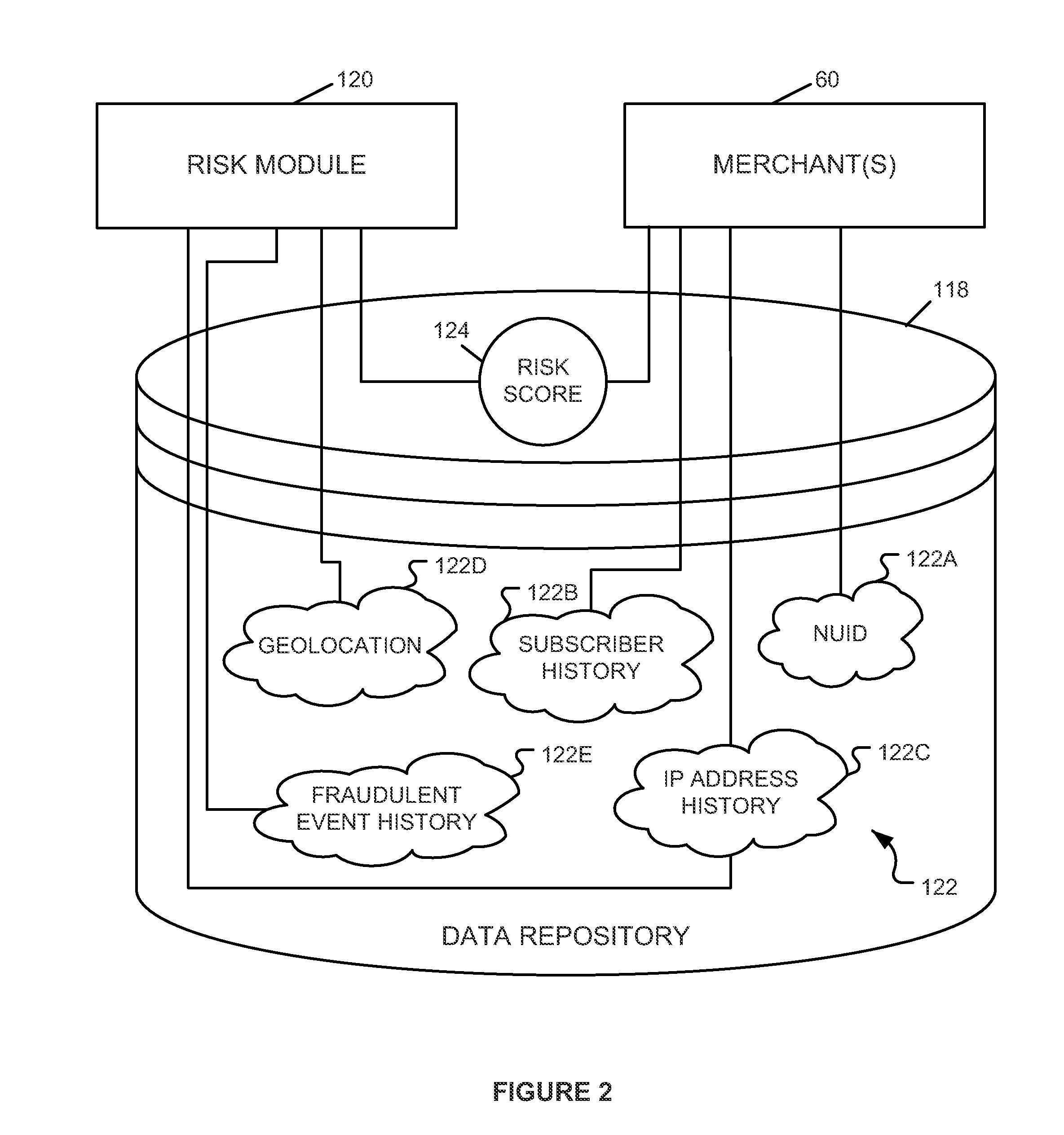
System and method for evaluating risk in fraud prevention
A method of determining a risk score indicating a risk that an electronic transaction will involve fraud and / or abuse. The method includes receiving transaction data associated with a not yet completed transaction from a merchant. The transaction data includes one or more characteristics related to the transaction. A profile is selected that identifies network devices each associated with the characteristics and having a device reputation. Next, a profile-based risk factor is determined as a function of a percentage of the network devices having a negative reputation. The risk score is determined as a function of the profile-based risk factor. In some embodiments, a transaction-based risk factor may also be determined. In such embodiments, the risk score is determined as a function of the profile-based and transaction-based risk factors. The risk score is provided to the merchant to be used thereby to determine whether to proceed with the transaction.
Owner:IOVATION
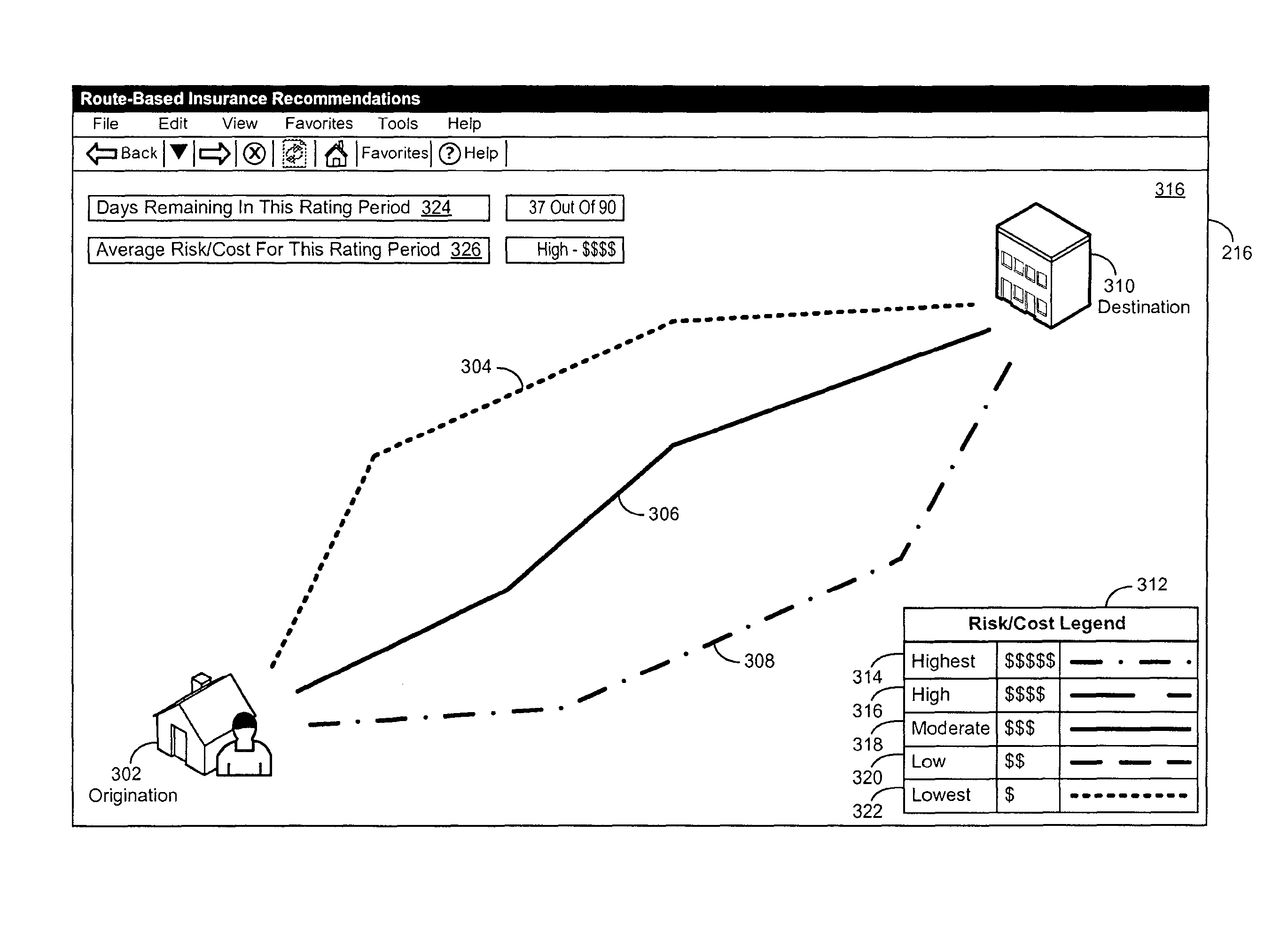
Systems and methods for real-time driving risk prediction and route recommendation
A system, method, and computer-usable medium are disclosed for providing routing-based insurance. A telematics device exchanges information related to a user's traversal of a route with a routing-based insurance system. The telematics device determines the current location and destination of the user, which it provides to the routing-based insurance system, for processing to determine available route segments between the two locations. A set of risk score data is generated for each of the available route segments, which in turn is used to generate a set of risk score differential data. Route advisement data, comprising routing instructions and the set of risk score differential data for the route segment, is generated and provided to the telematics device. A route segment is selected by the user and then traversed. The set of risk score differential data associated with the traversed route segment is determined and associated with the user's insurance policy. Insurance policy price data, corresponding to the traversed route segment, is generated and in turn is processed to generate insurance policy adjustment data. The insurance policy price adjustment data is then processed to modify pricing data associated with the user's insurance policy.
Owner:USAA
Risk management in a vehicle Anti-collision system
ActiveUS20130278442A1More dataInstruments for road network navigationArrangements for variable traffic instructionsCommunications systemIT risk management
Device, system and method, in a vehicle communication system, of transmitting a risk value in a message, wherein the risk value identifies quantitatively a risk of vehicle collision. Embodiments determine risk value by combining sub-risk values wherein sub-risks comprise: (i) vehicle behavior; (ii) weather and road conditions; (iii) current traffic; and (iv) location history. Embodiments include driver warnings responsive to the risk value in a received message. Embodiments include a collision type in a message. Embodiments include unique features of: risk is applicable to receiving vehicles; risk is applicable to a geographical region; computation and storage of location histories; messages free of IP and MAC addresses; haptic devices used for driver warning.
Owner:ZETTA RES & DEV - FORC SERIES
Method and system for evaluating network safety situation
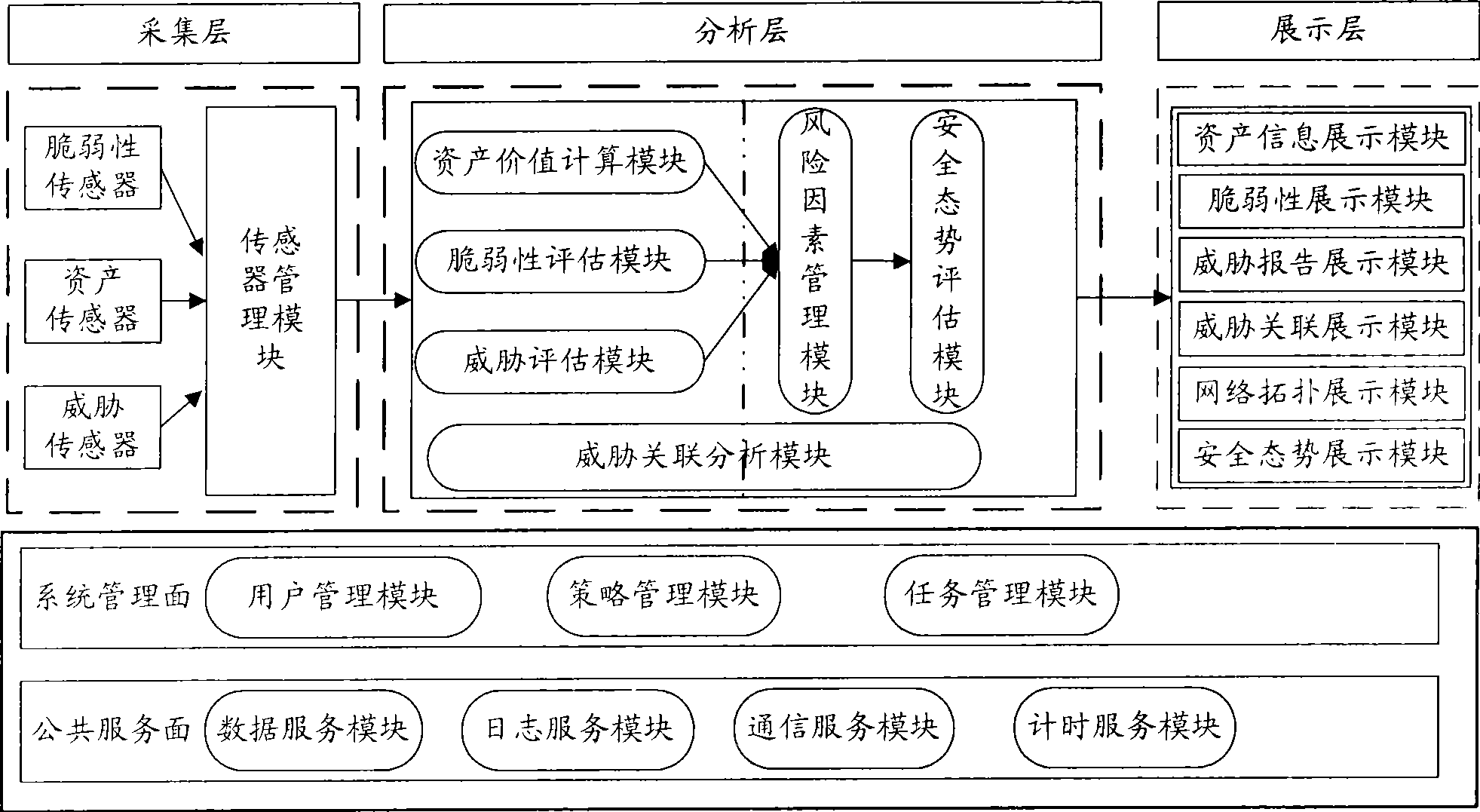
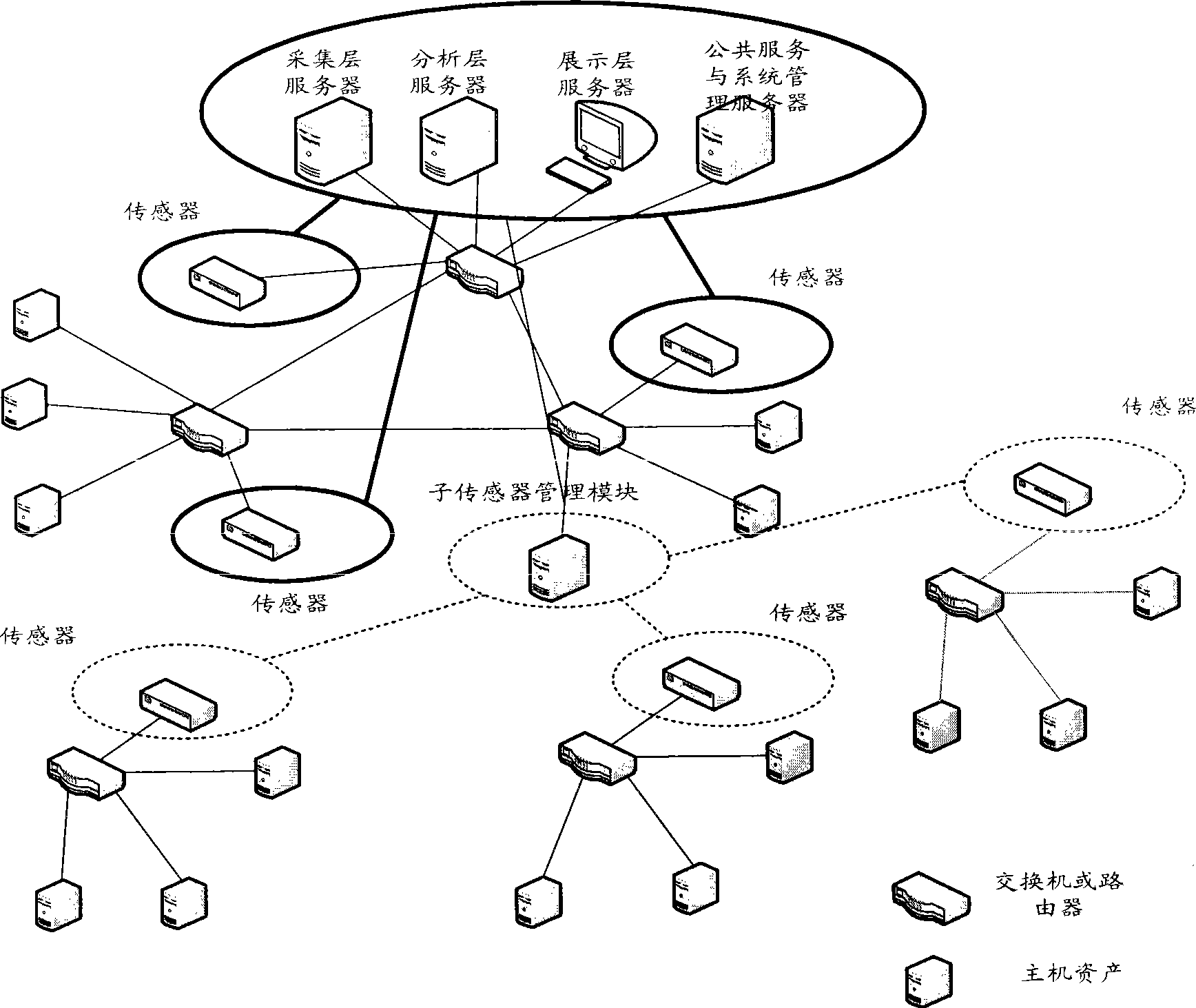
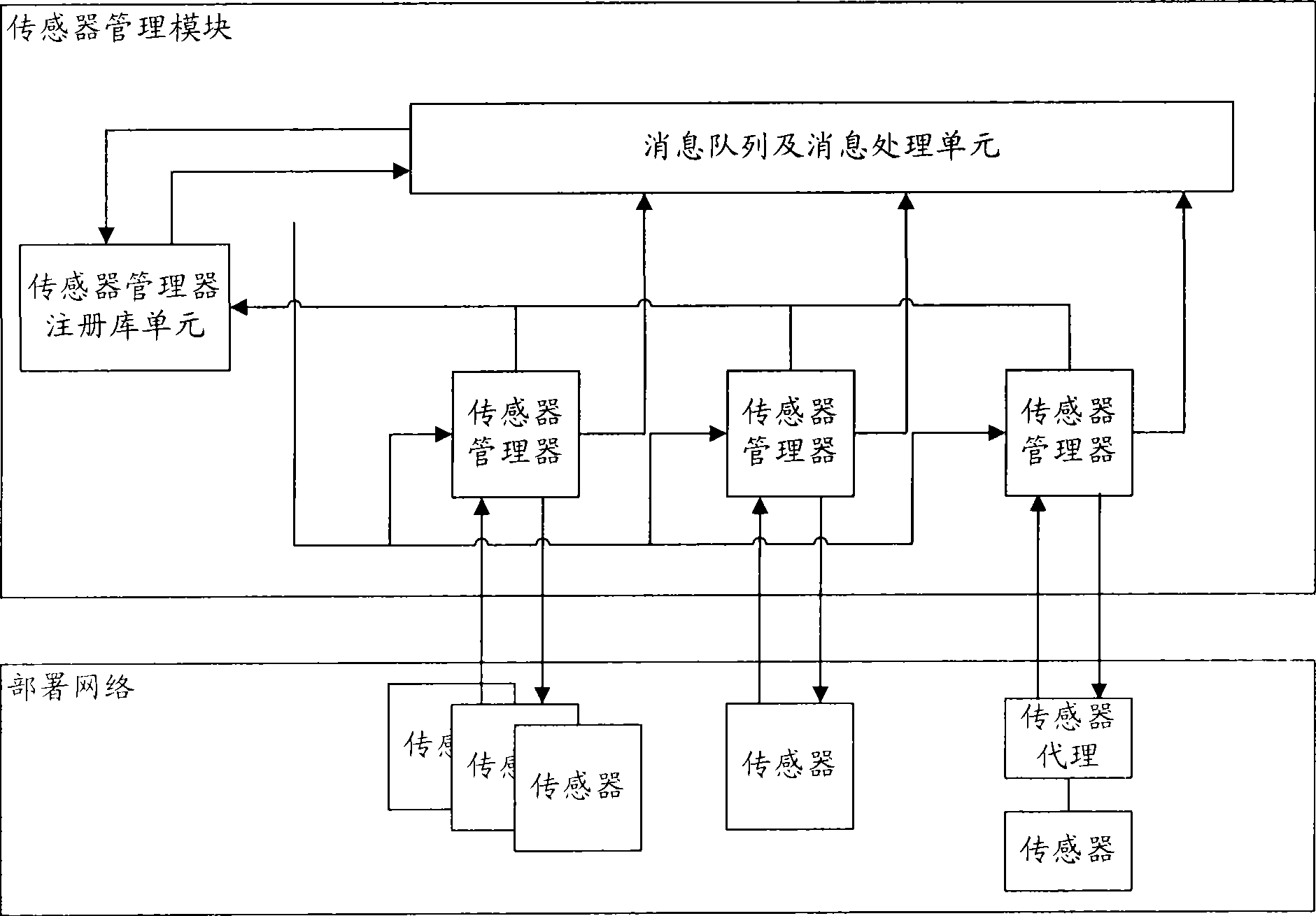
InactiveCN101436967AEasy to operateImprove securityData switching networksThree levelSecurity solution
The invention relates to a method for evaluating the security situation of a network and a system thereof. The system has a two-surface three-level framework and is provided with a public service surface and a service management surface for executing uniform coordinated management on each functional module of the system; according to a service logic processing flow, the system is divided into three levels: an acquisition level, an analysis level and an exhibition level for completing four evaluating operations of assets, frangibility, threat and security situation; the invention is based on the characteristic of service operation in the network, combines the prior risk evaluation method, the prior flow and the prior security detection tool and provides a set of a novel dynamic real-time evaluation method. The system can analyze the assets and service of the network and the risk of the whole network and carries out the evaluation of the security situation. The system can provide the security state of the whole network in macroscopy, can deepen to specific service and assets and know the specific security problem, thereby effectively helping network security personnel to analyze the root of the security problem and assisting to provide a security solution proposal and implement a defense measure.
Owner:BEIJING UNIV OF POSTS & TELECOMM
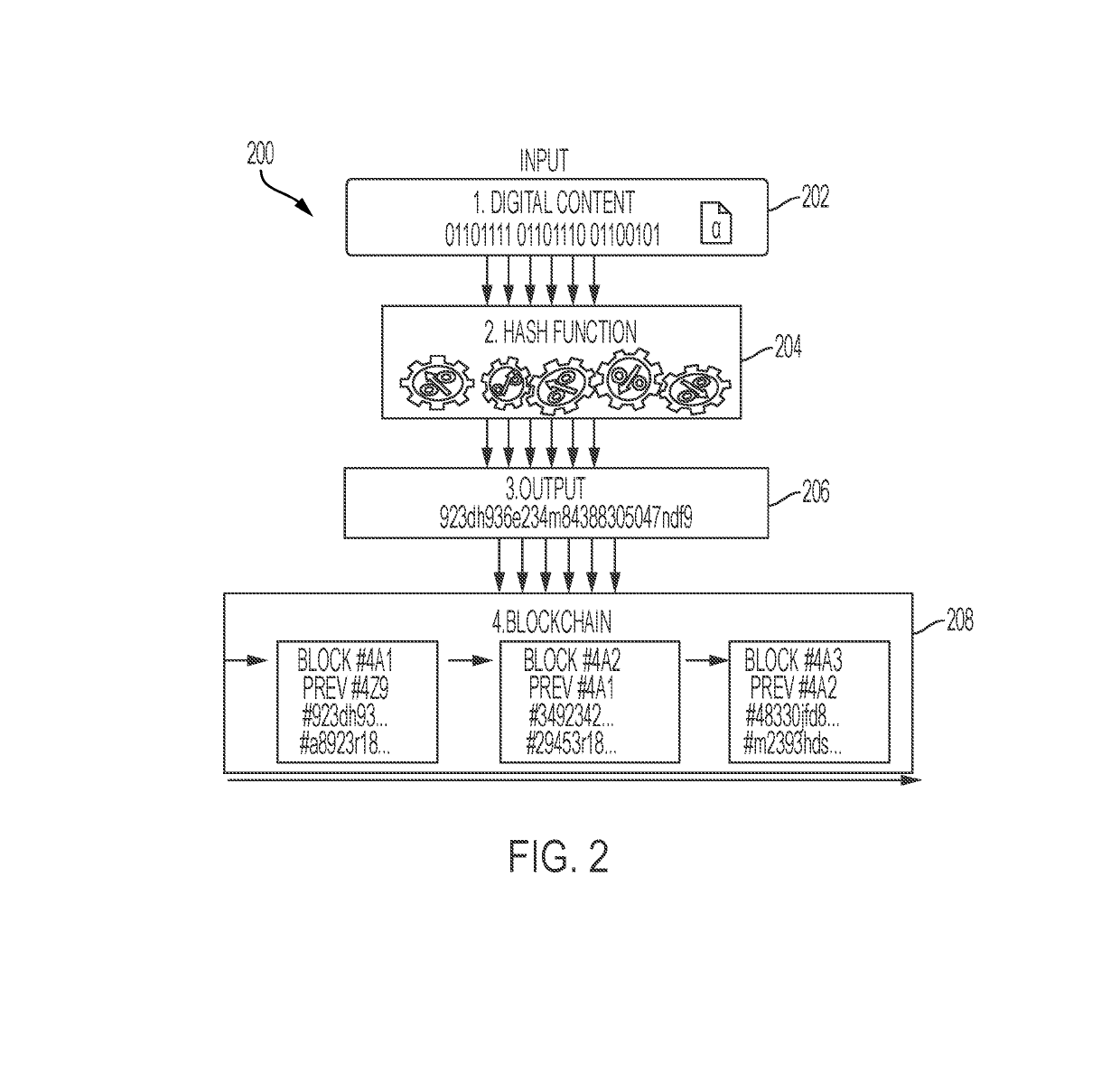
System and method for validation of distributed data storage systems
InactiveUS20190132350A1Eliminate needConveniently determinedEncryption apparatus with shift registers/memoriesCryptography processingGraphicsReal time validation
Provided herein is a risk framework tool for a distributed ledger-based computing system (i.e., blockchain) that can present a common risk framework to a user that can then allow for the user to determine what risks are important for it to manage. The risk framework can then take those specified risks and convert them in to a plurality of tests that can be used to validate the organization's blockchain system. In one or more examples, the risk framework can provide a graphical user interface to user that allows them specify the risks they wish to manage within the blockchain computing system, and based on the user's inputs, can determine one or more continuous real-time validation tests to be performed on the blockchain computing system so as to characterize the risk specified by user using the risk framework.
Owner:PRICEWATERHOUSECOOPERS LLP
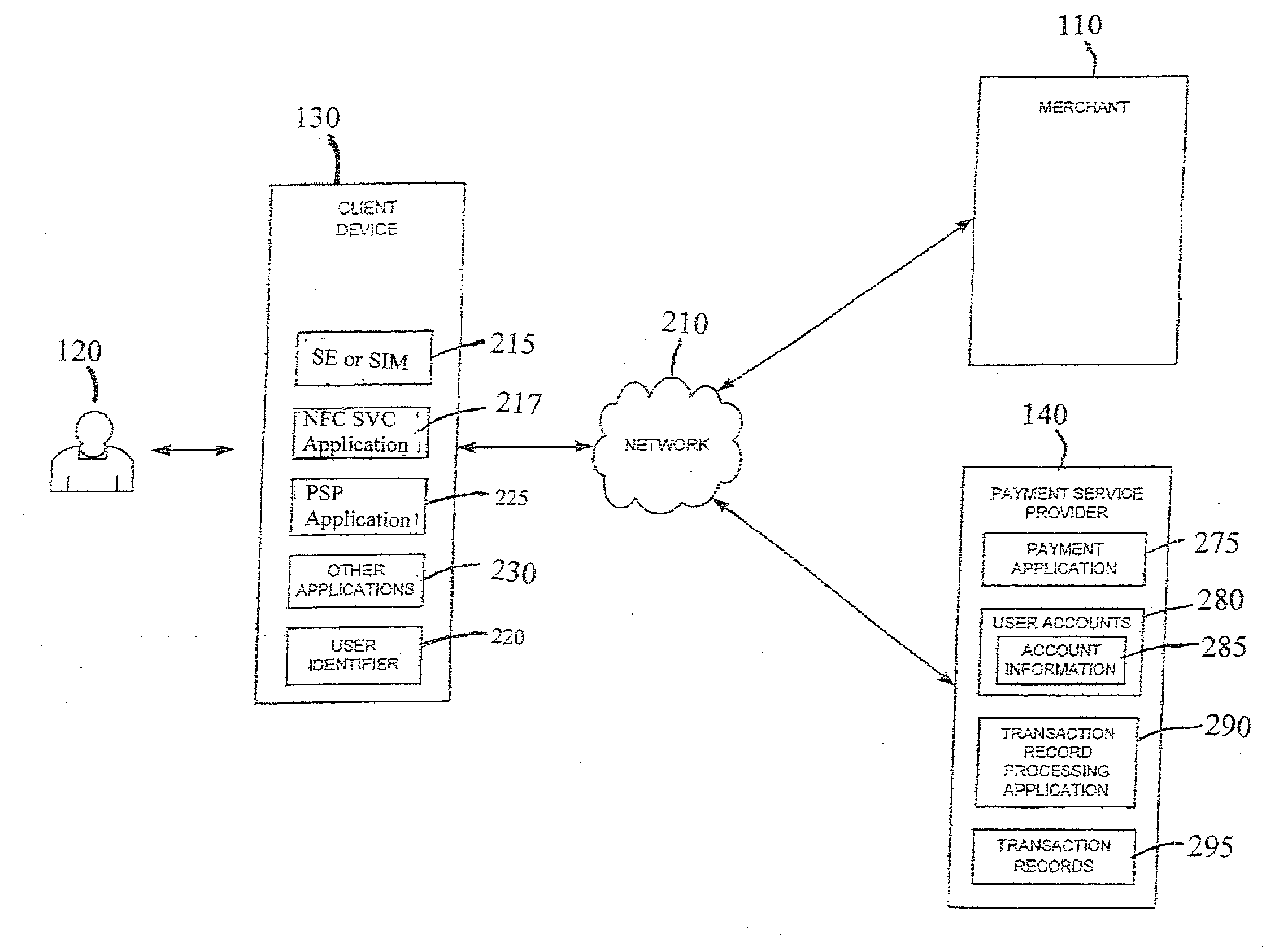
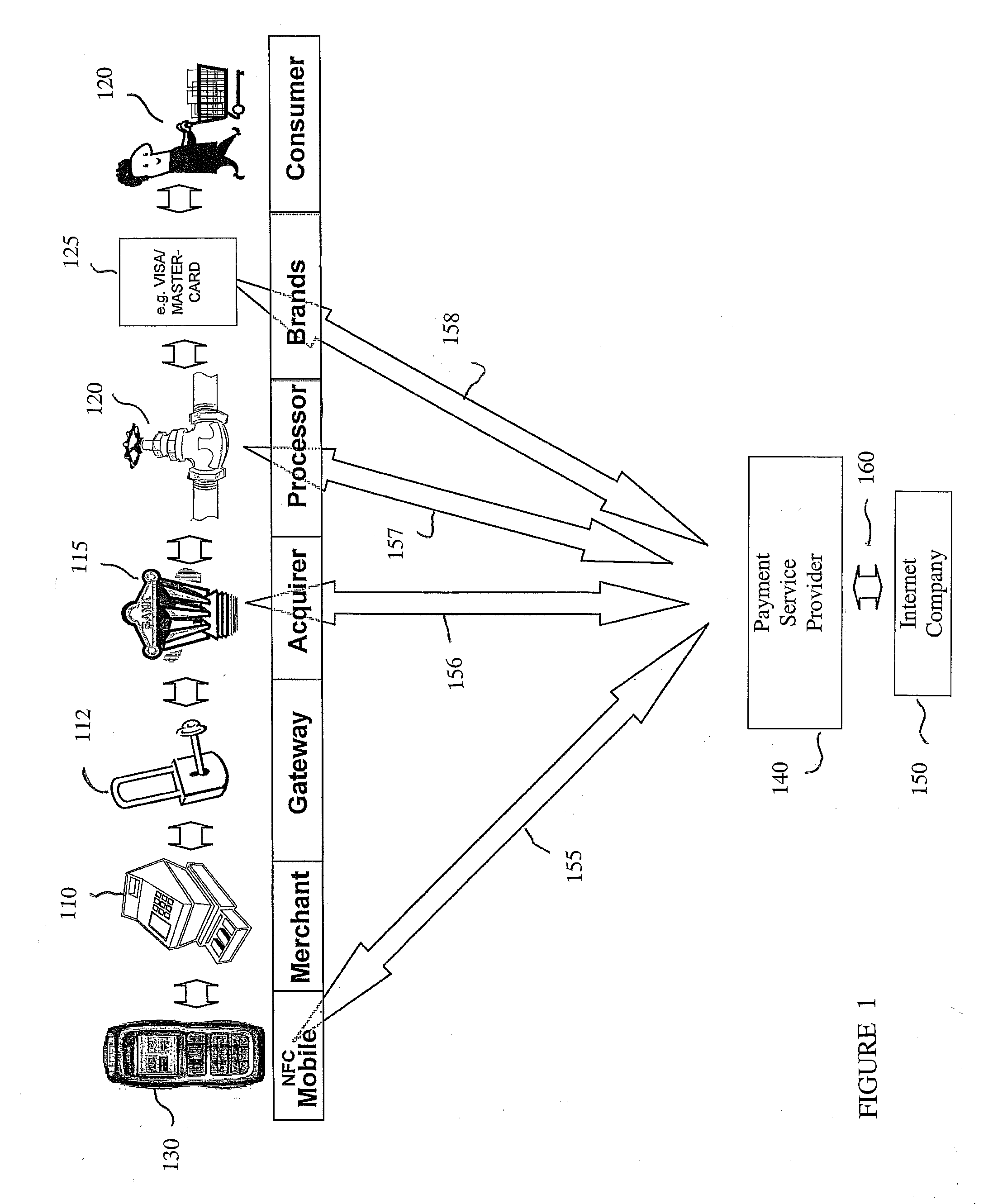
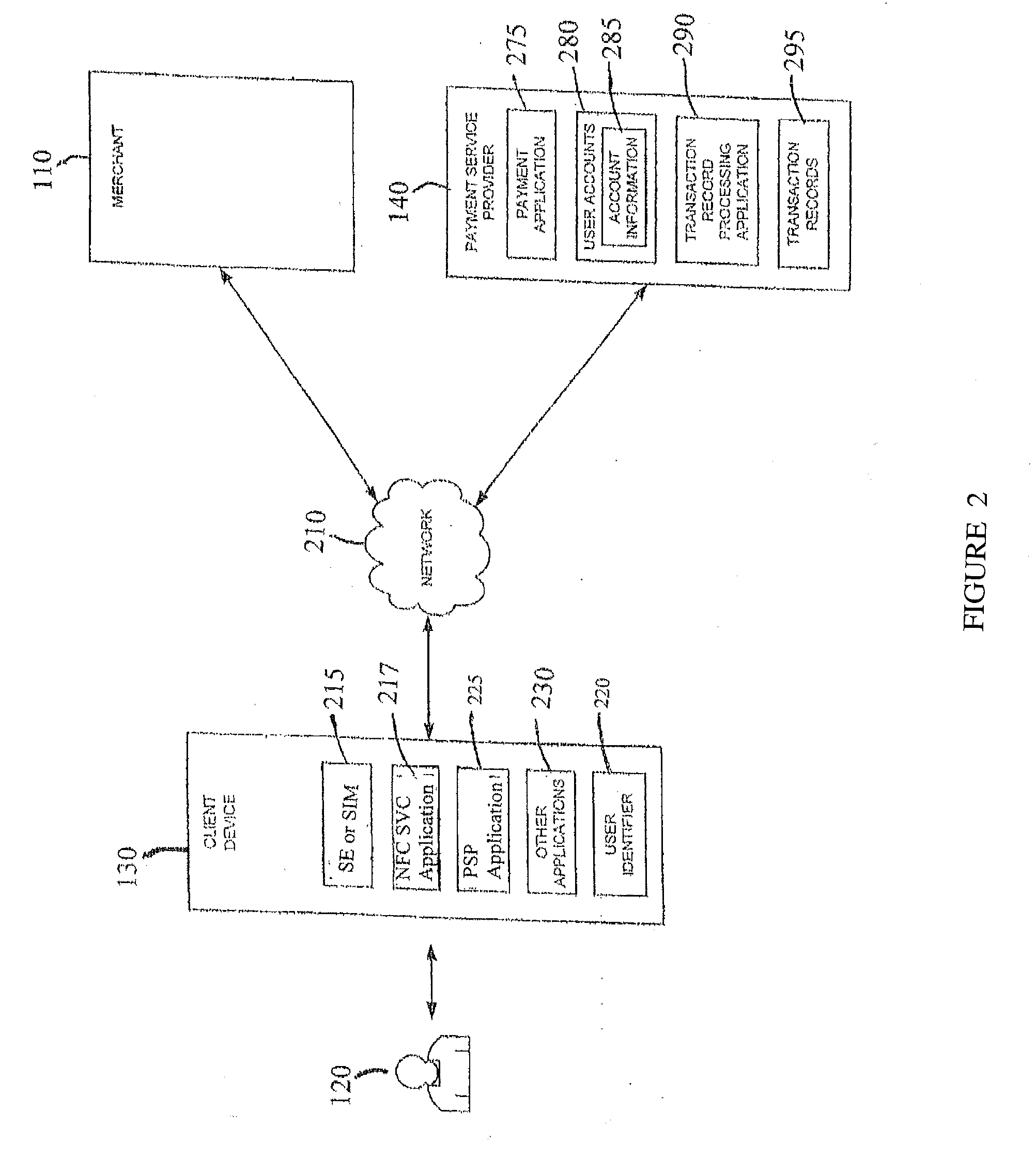
Mobile User Identify And Risk/Fraud Model Service
InactiveUS20090307778A1Risk dataGeneration of riskDigital data processing detailsAnalogue secracy/subscription systemsIdentity theftBluetooth
Transactions using, for example, Near Field Communication (NFC), Bluetooth, online, or other applications, may pose a risk of fraud or identity theft. According to an embodiment, a method of evaluating transaction information in view of potential fraud and / or risk includes receiving transaction information at a remote location. The method also includes correlating the received transaction information with user data maintained at the remote location. The method further includes generating a score and / or risk or fraud data based on the correlating. Such transactions may be facilitated by a payment service provider. Related methods, devices, and systems are also disclosed.
Owner:PAYPAL INC
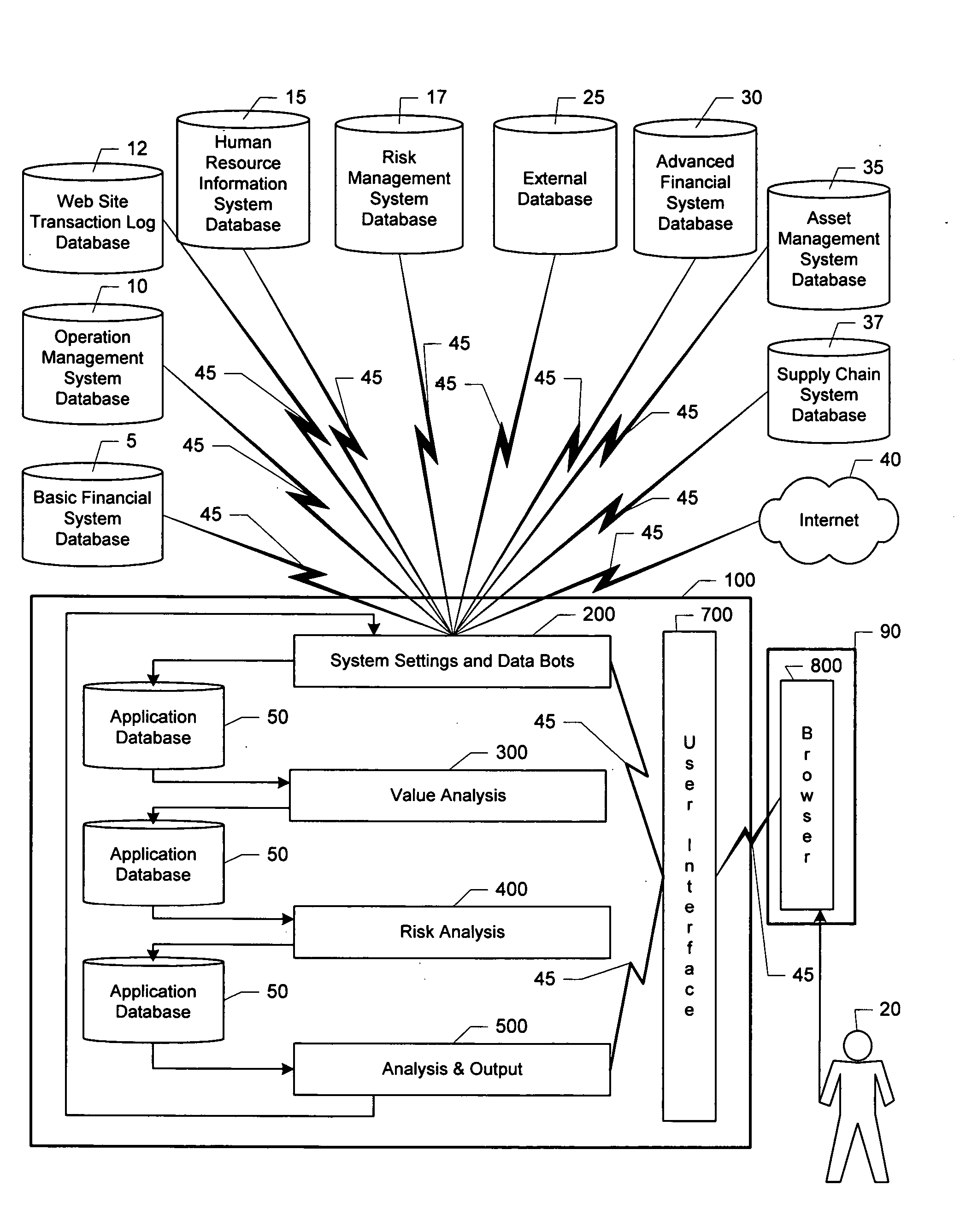
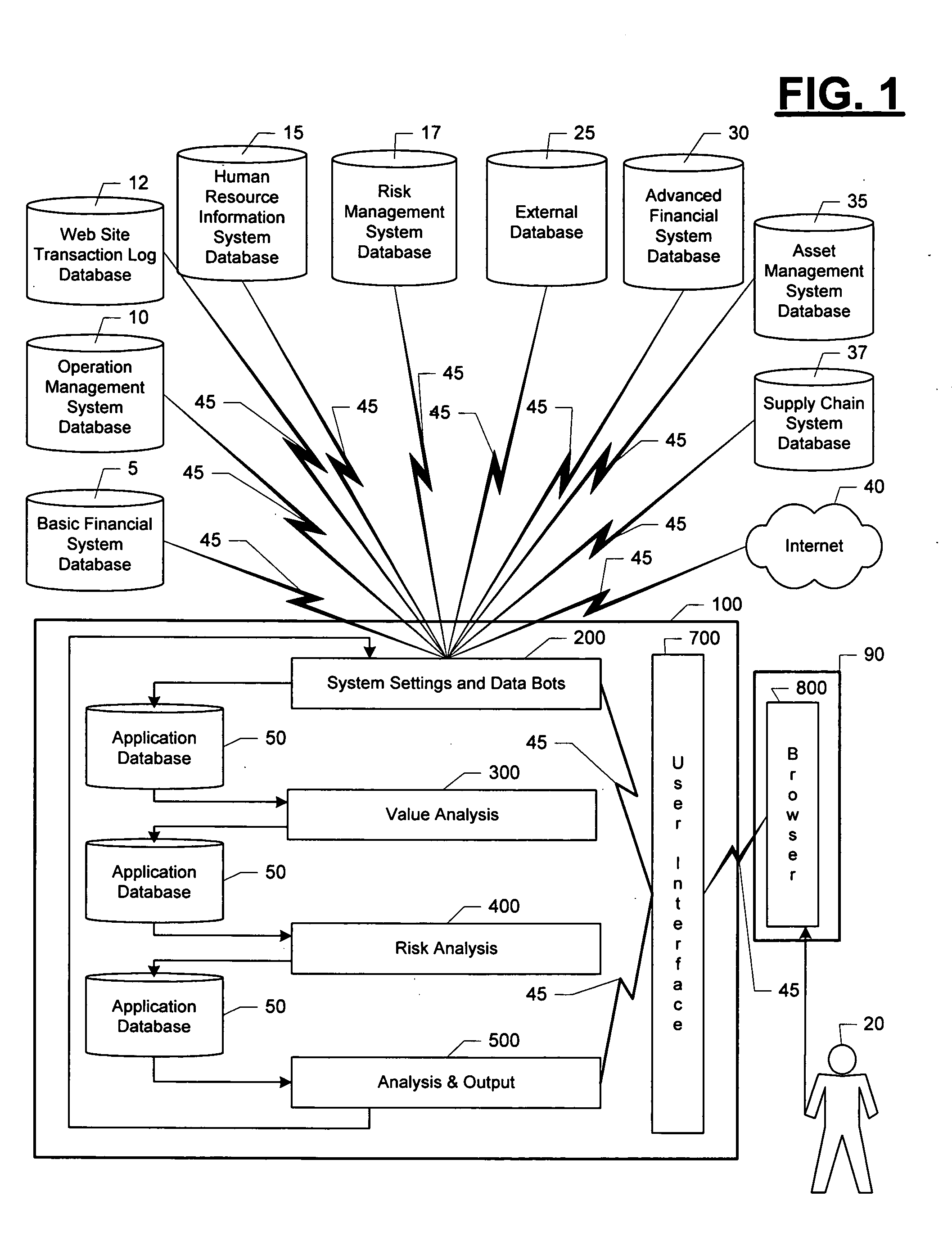
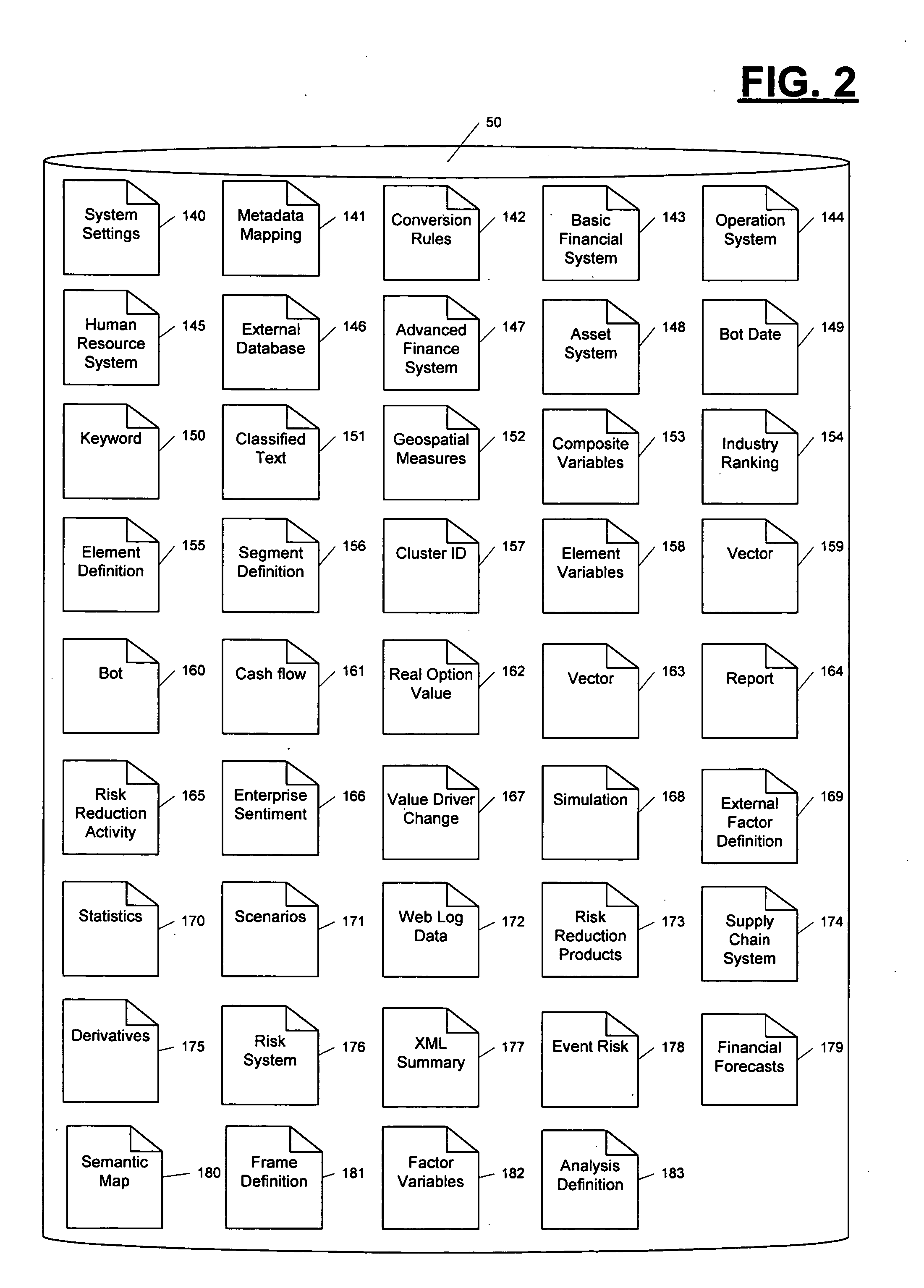
Value and risk management system
InactiveUS20050071266A1Increases scale and scopeEnhances efficiency and effectivenessFinanceSpecial data processing applicationsEngineeringManagement system
A method of and system for creating an organization risk matrix and an organization value matrix and using said matrices to support the optimization of one or more aspects of organization risk and value.
Owner:EDER JEFFREY
Systems and methods for investigation of financial reporting information
Owner:PRICEWATERHOUSECOOPERS
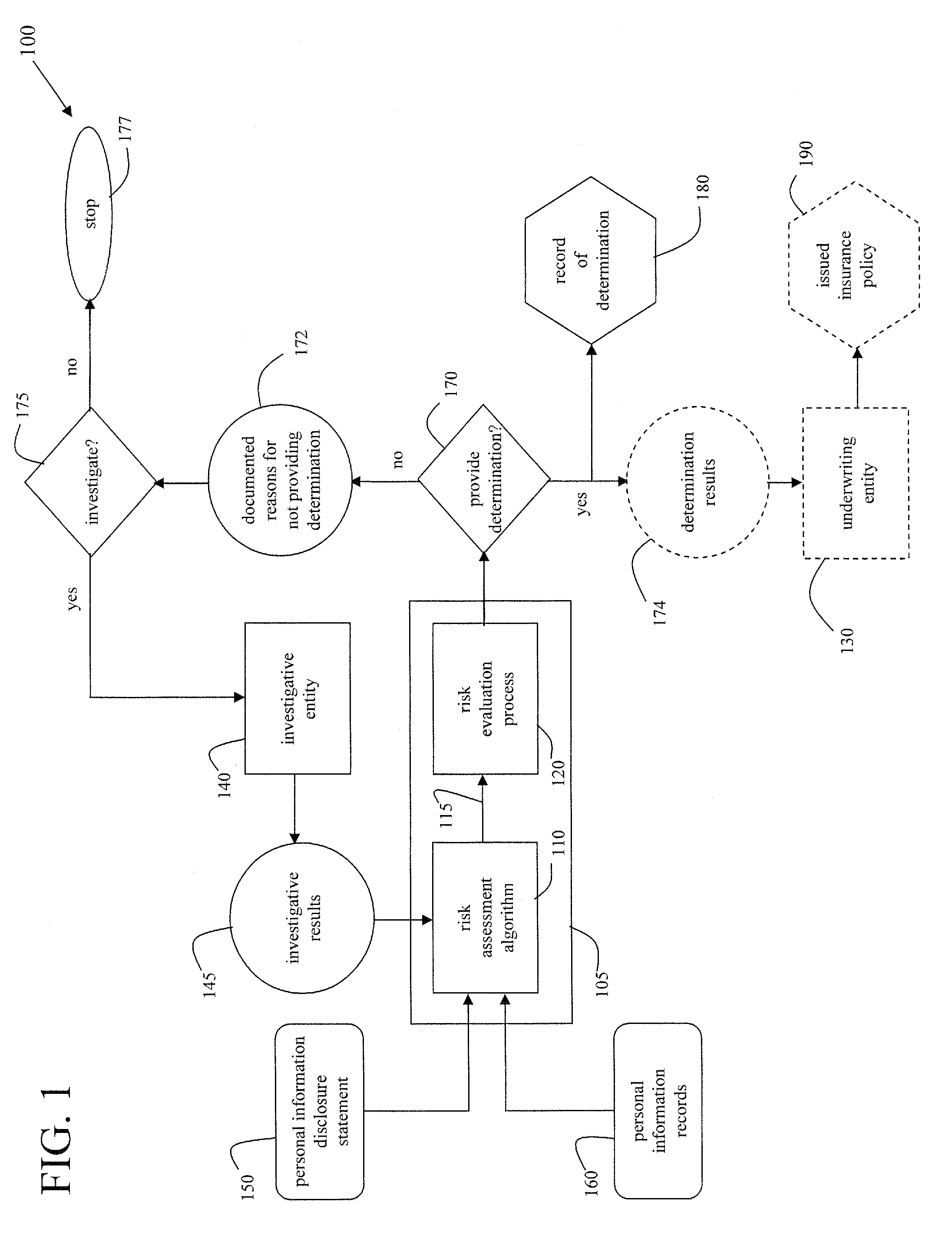
Methods of deterring, detecting, and mitigating fraud by monitoring behaviors and activities of an individual and/or individuals within an organization
InactiveUS20070294195A1Reduce fraudReduce detectionFinanceSpecial data processing applicationsRelevant informationKnowledge management
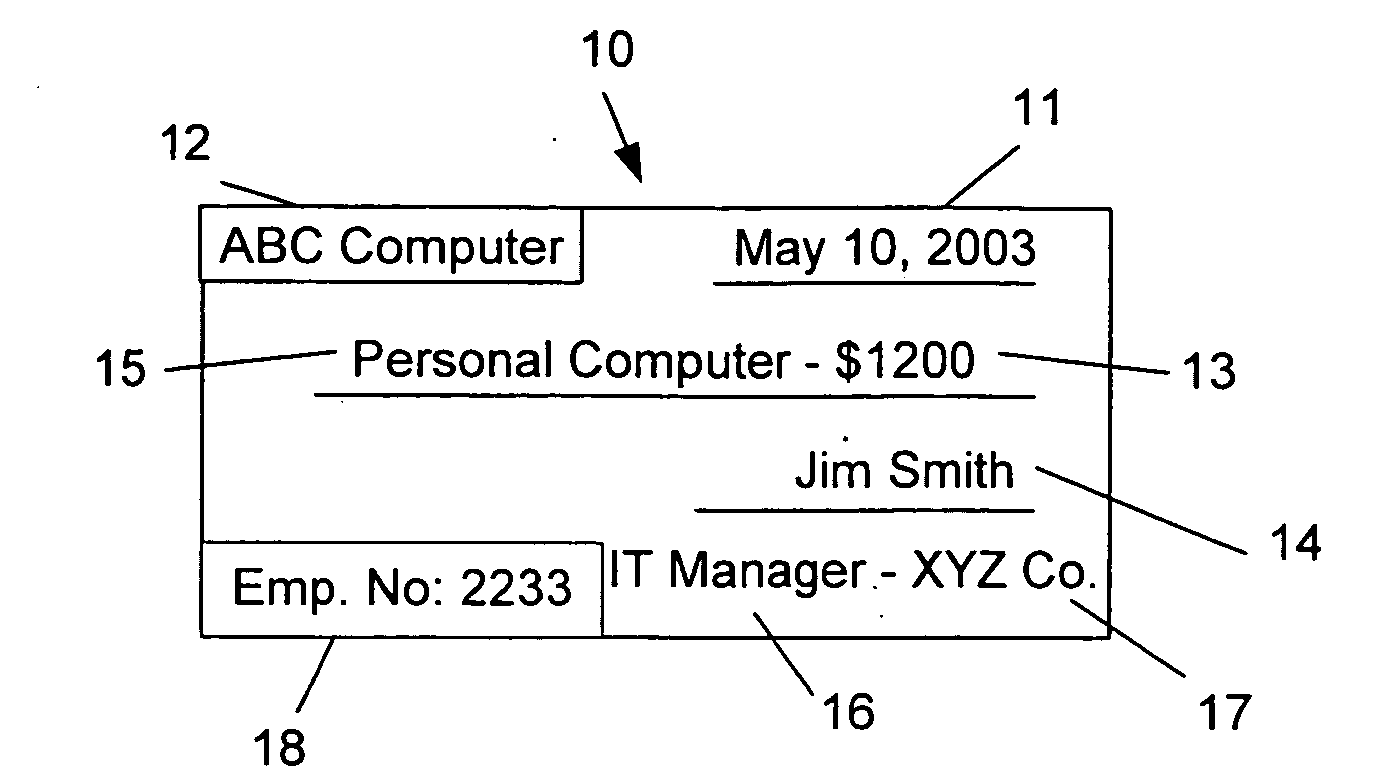
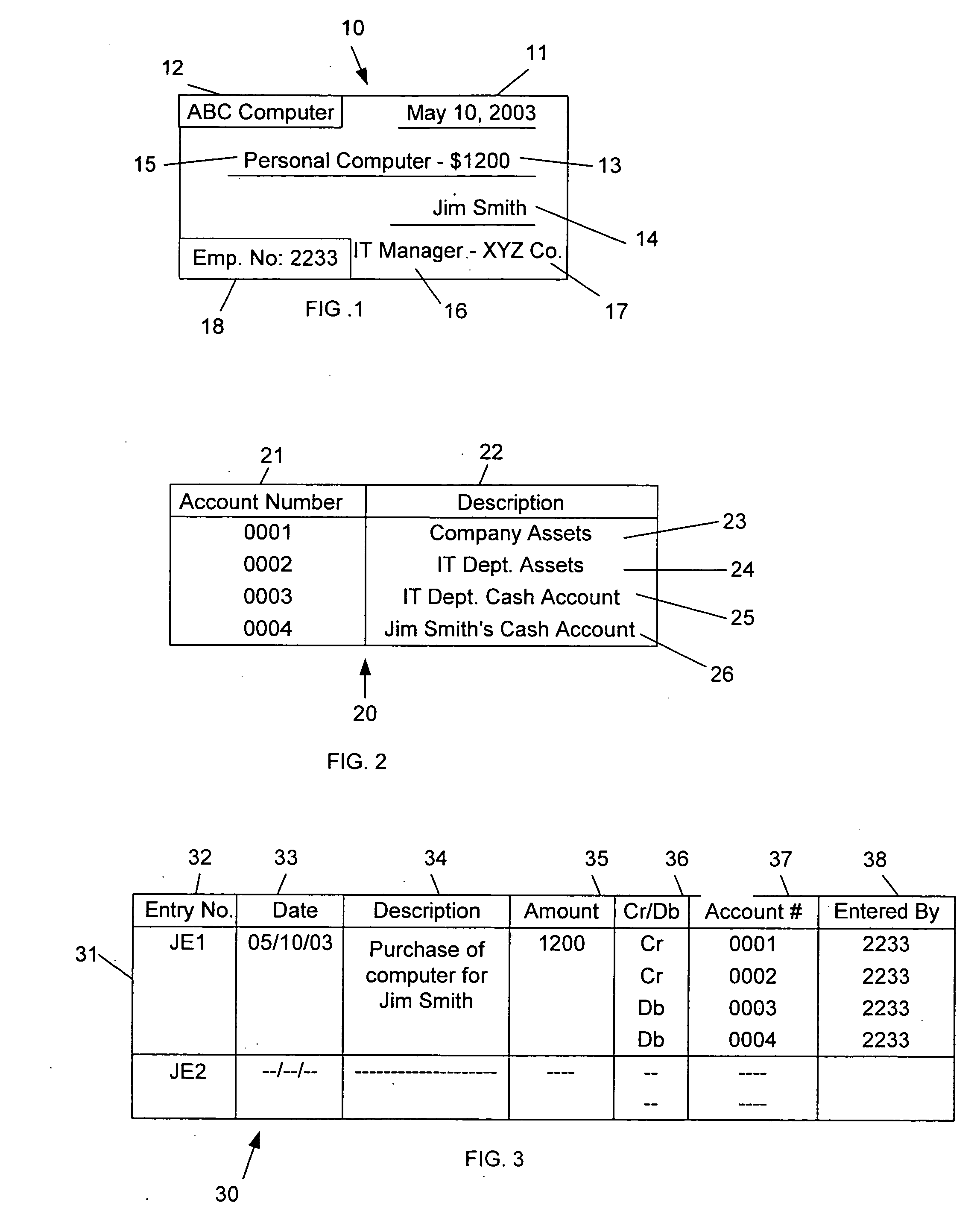
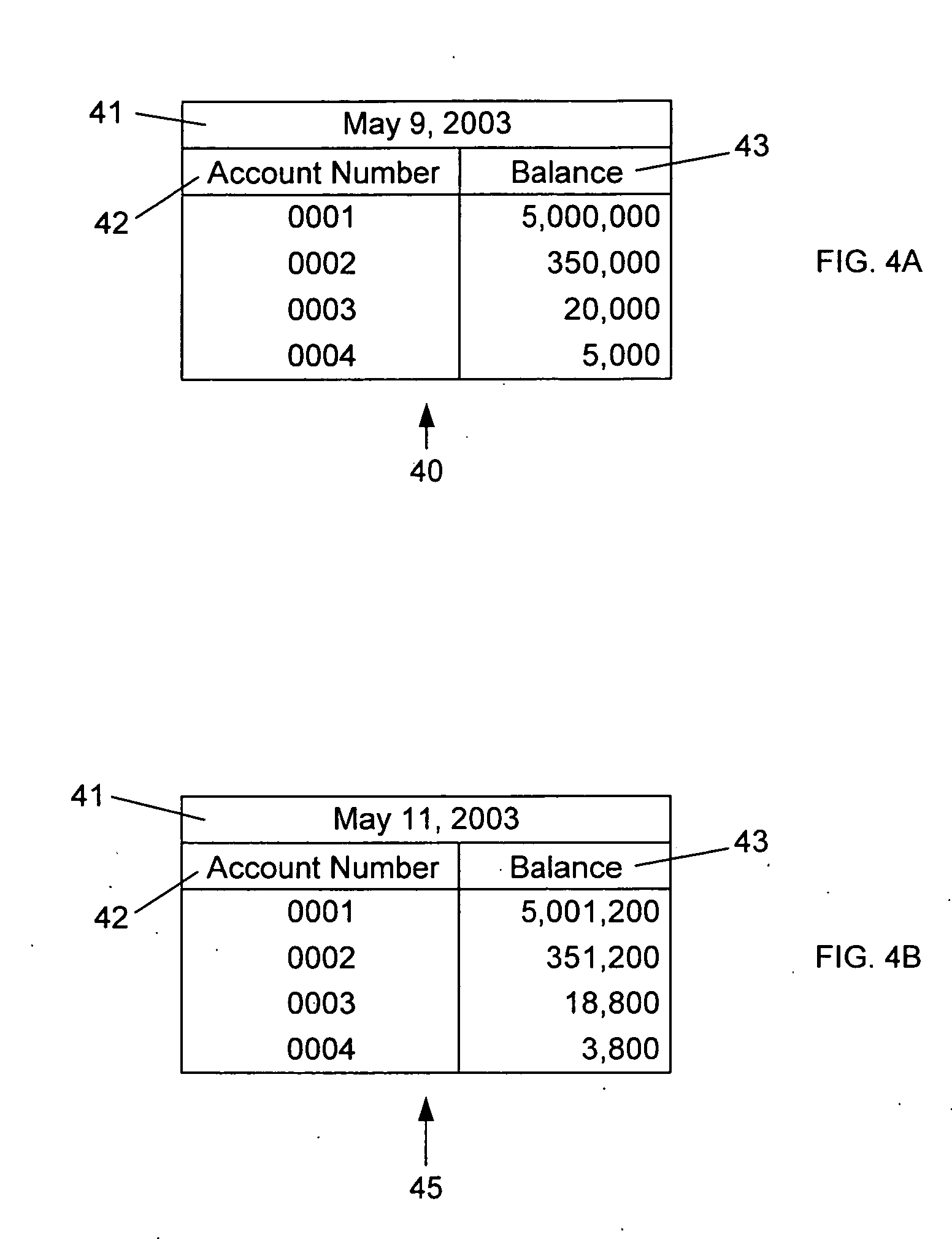
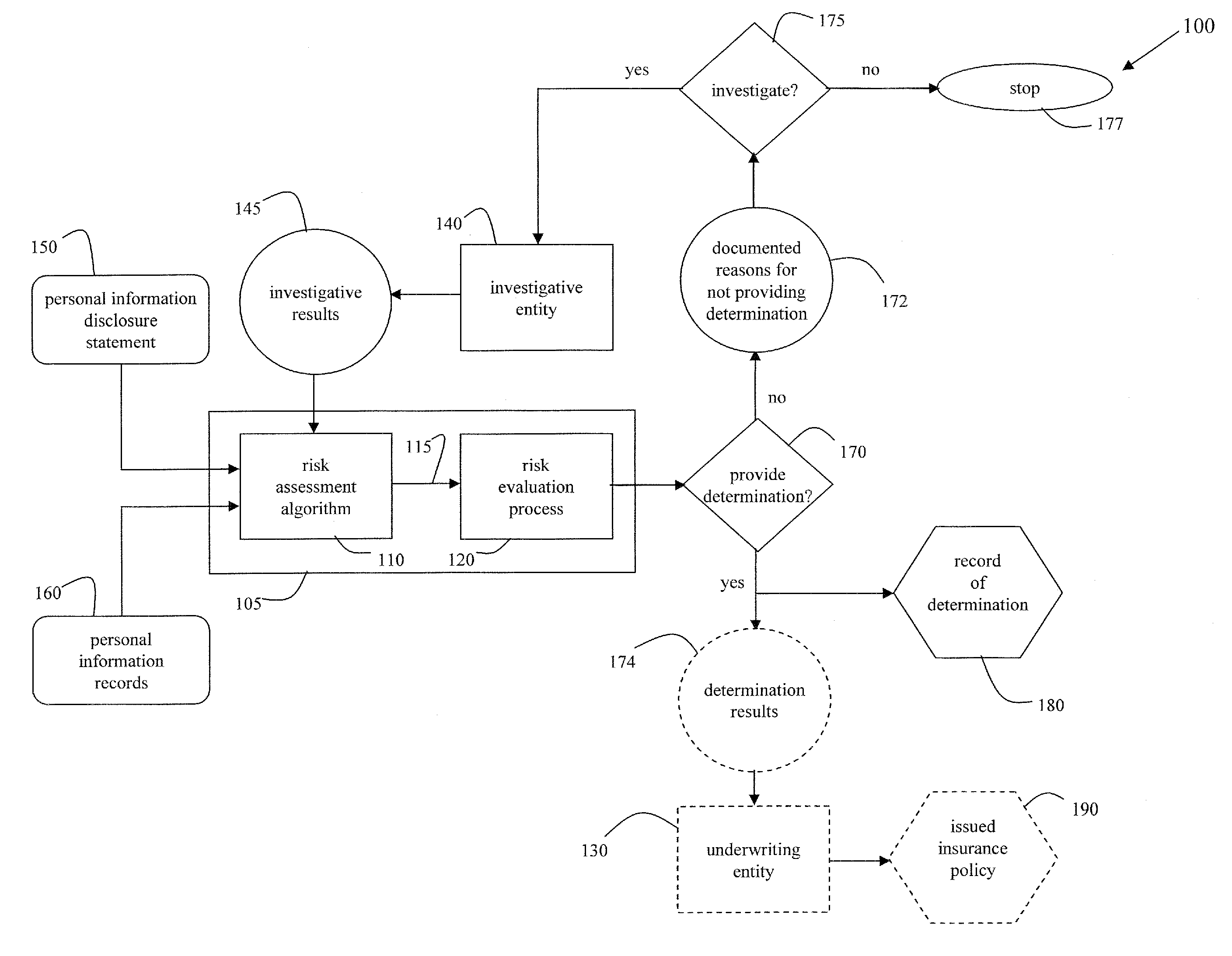
A cooperative arrangement and method to help deter and / or detect and / or mitigate fraud by evaluating and then monitoring the information of an individual or individuals for changes in fraud risk. A personal information disclosure statement, personal information records, and other relevant information associated with an individual, or a plurality of individuals, associated with an organization, an individual potentially to be associated with an organization, or an individual acting in his or her individual capacity are obtained. Information is extracted from the personal information disclosure statement, the personal information records, and the other relevant information and entered into a risk assessment algorithm. The risk assessment algorithm operates on the entered information and generates risk assessment data. The risk assessment data is evaluated to make a determination of fraud risk with respect to the individual(s). A decision to provide a fraud risk determination means that the risk associated with the individual, with respect to committing fraud, is acceptable. Risk assessment data on a plurality of key individuals within an organization may be generated and evaluated to make a determination of fraud risk with respect to the organization itself.
Owner:CURRY EDITH L +3
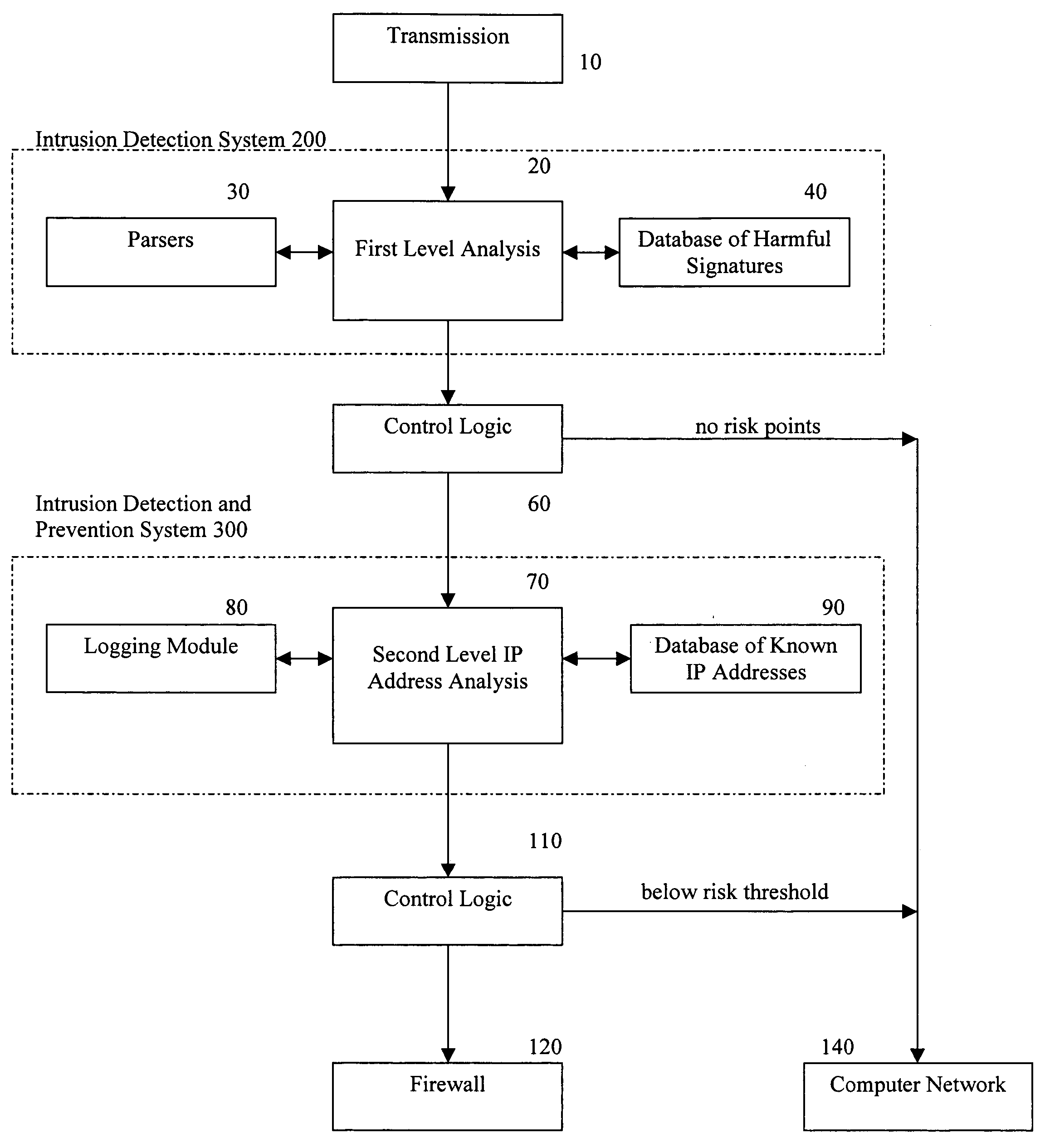
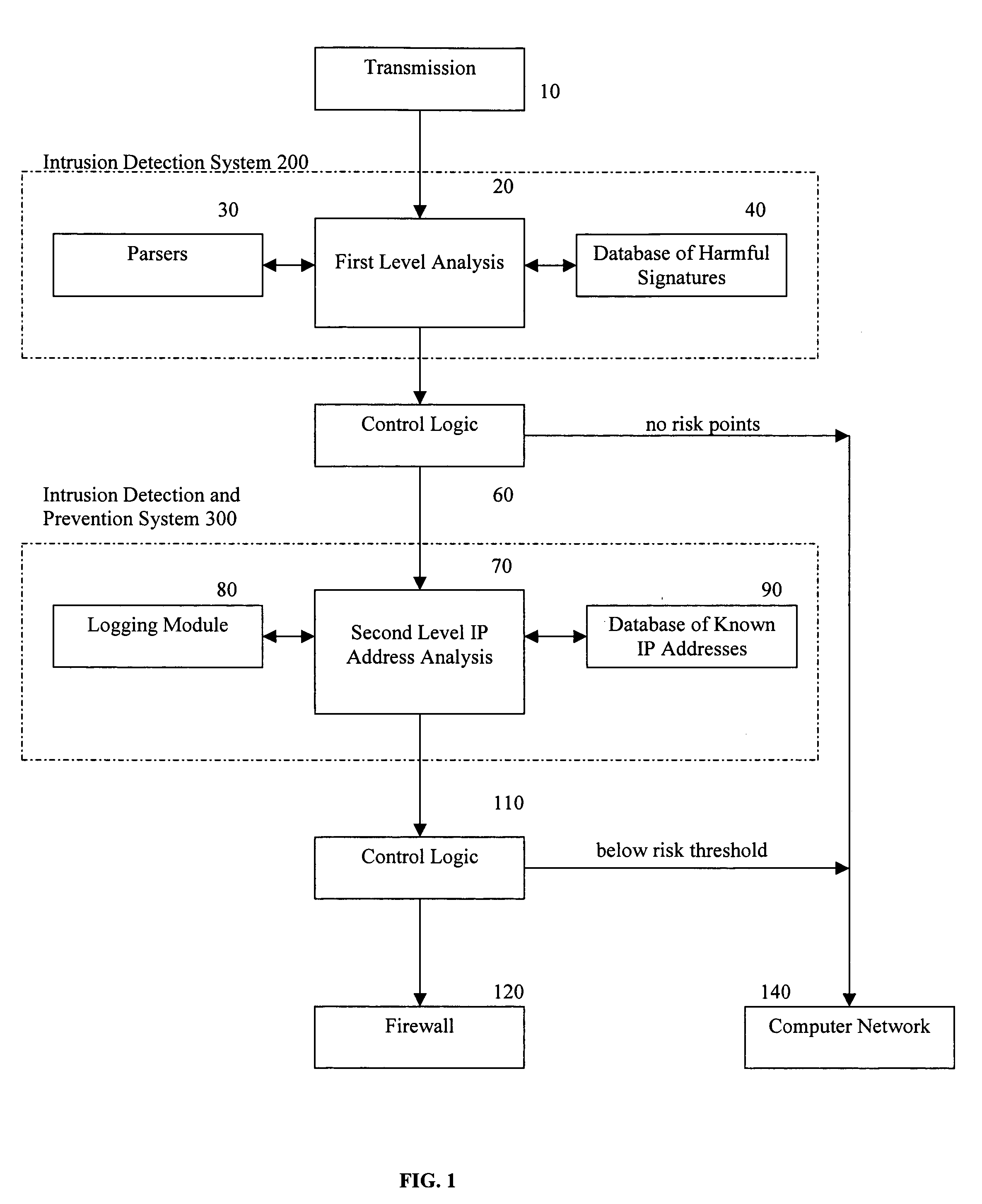
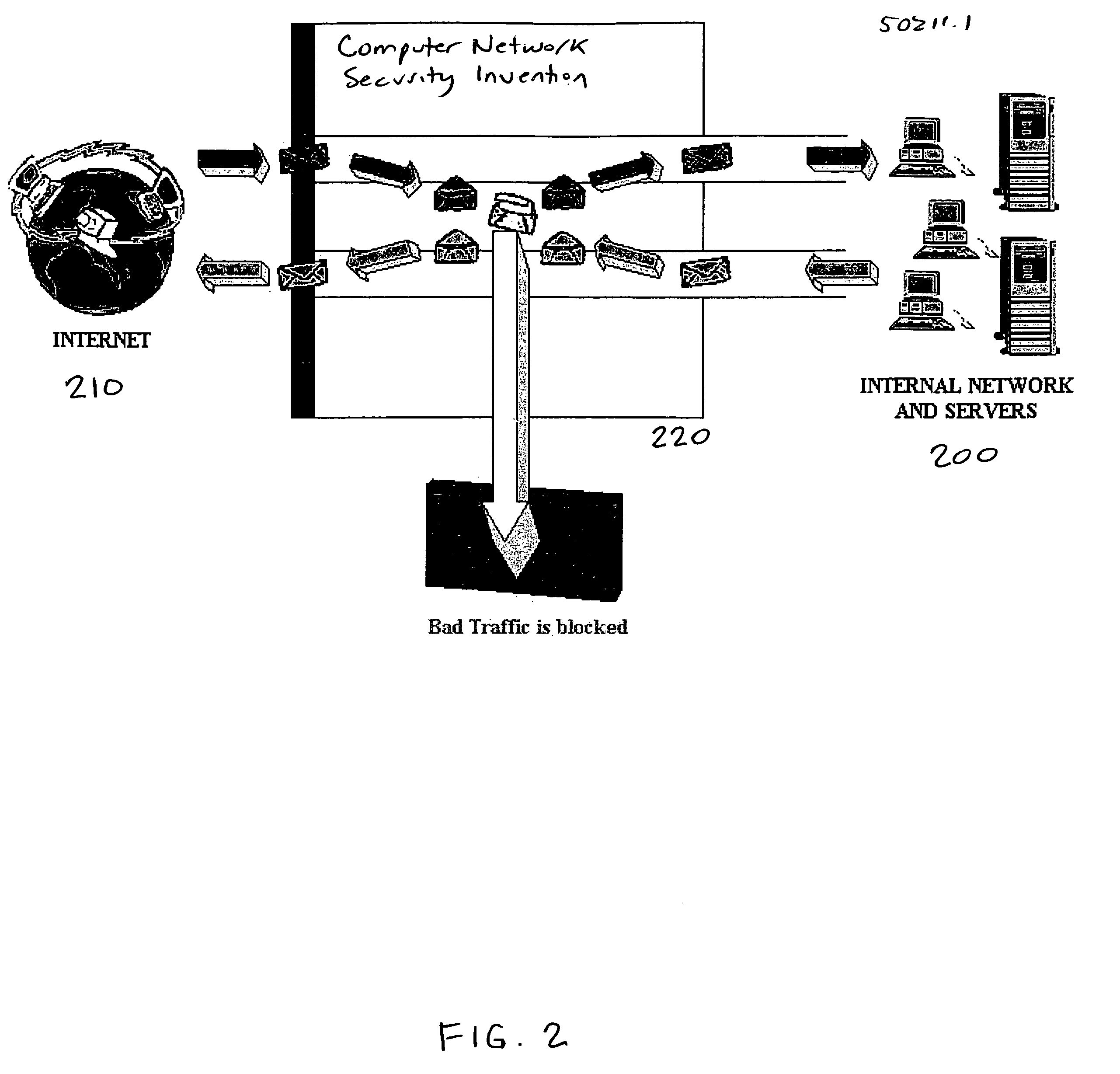
Methods and apparatus for computer network security using intrusion detection and prevention
InactiveUS7225468B2Memory loss protectionDigital data processing detailsIp addressIntrusion detection and prevention
A method provides security to a computer network by selectively blocking network transmissions from selected IP addresses. The method includes the steps of: establishing a risk threshold whereby transmissions from IP addresses exceeding said risk threshold are selectively blocked; receiving a network transmission having an originating IP address and payload; analyzing the payload of said transmission and assigning a current risk rating to said IP address on the basis of said analysis; comparing the originating IP address of said transmission to a database of known IP addresses, each of said known IP addresses having a previous cumulative assigned risk rating, said previous cumulative assigned risk rating being based on at least one previous transmission from a known IP address; assigning a new cumulative risk rating to said originating IP address; logging the new cumulative risk rating for said originating IP address in said database of known IP addresses. The new cumulative risk rating is compared to said risk threshold and the transmission is blocked if said new cumulative risk rating exceeds said risk threshold.
Owner:DIGITAL SECURITY NETWORK
Systems and methods for risk triggering values
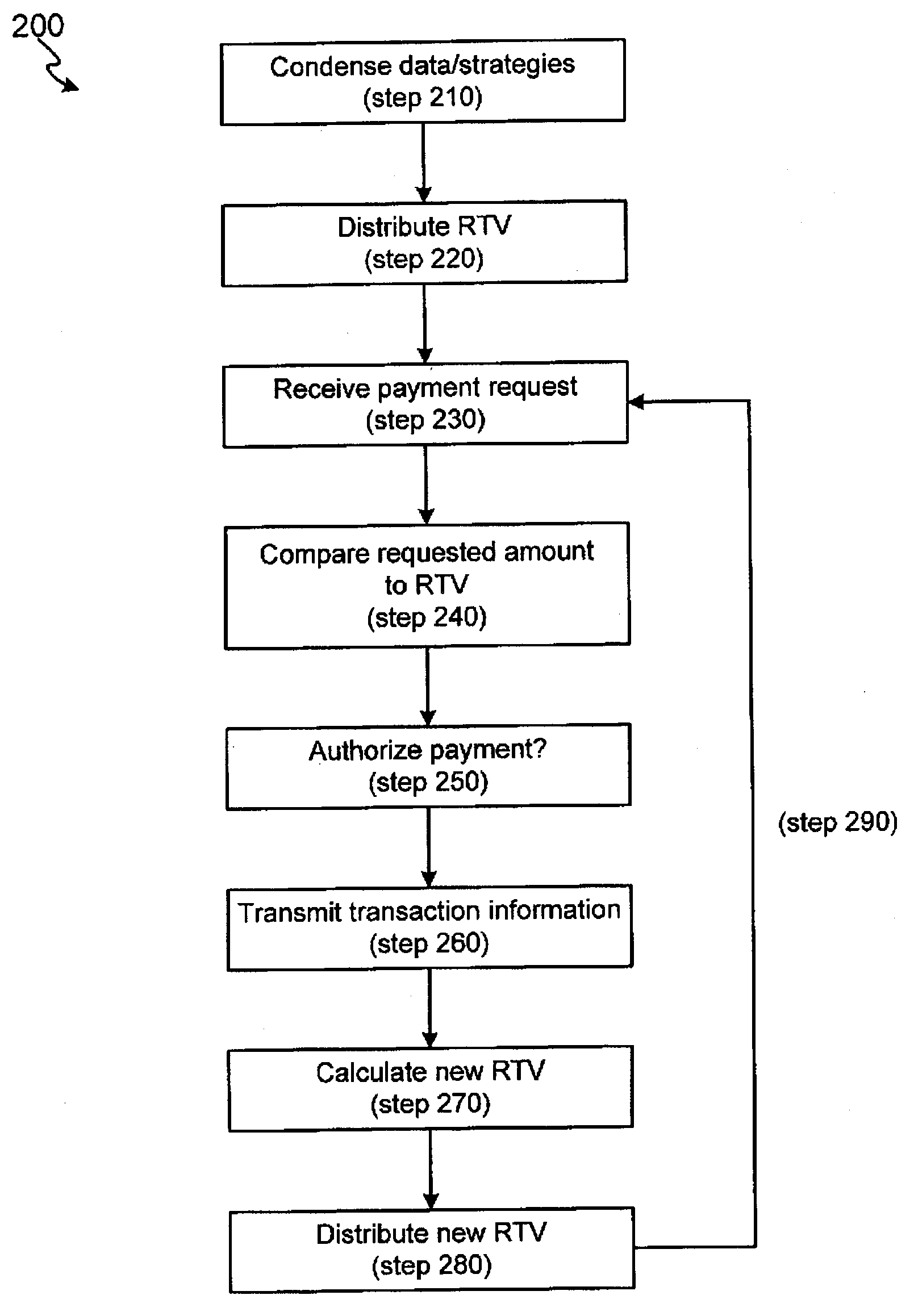
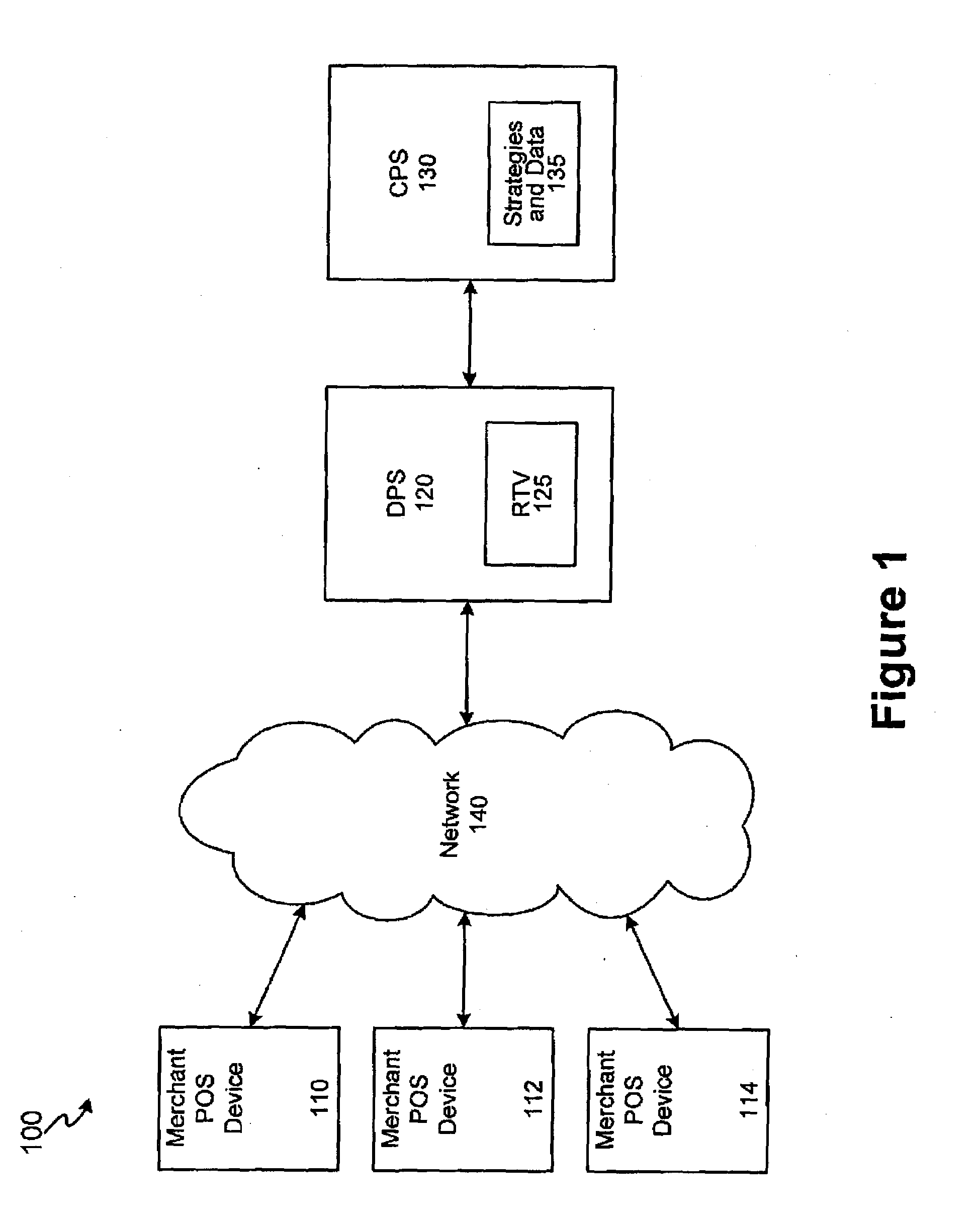
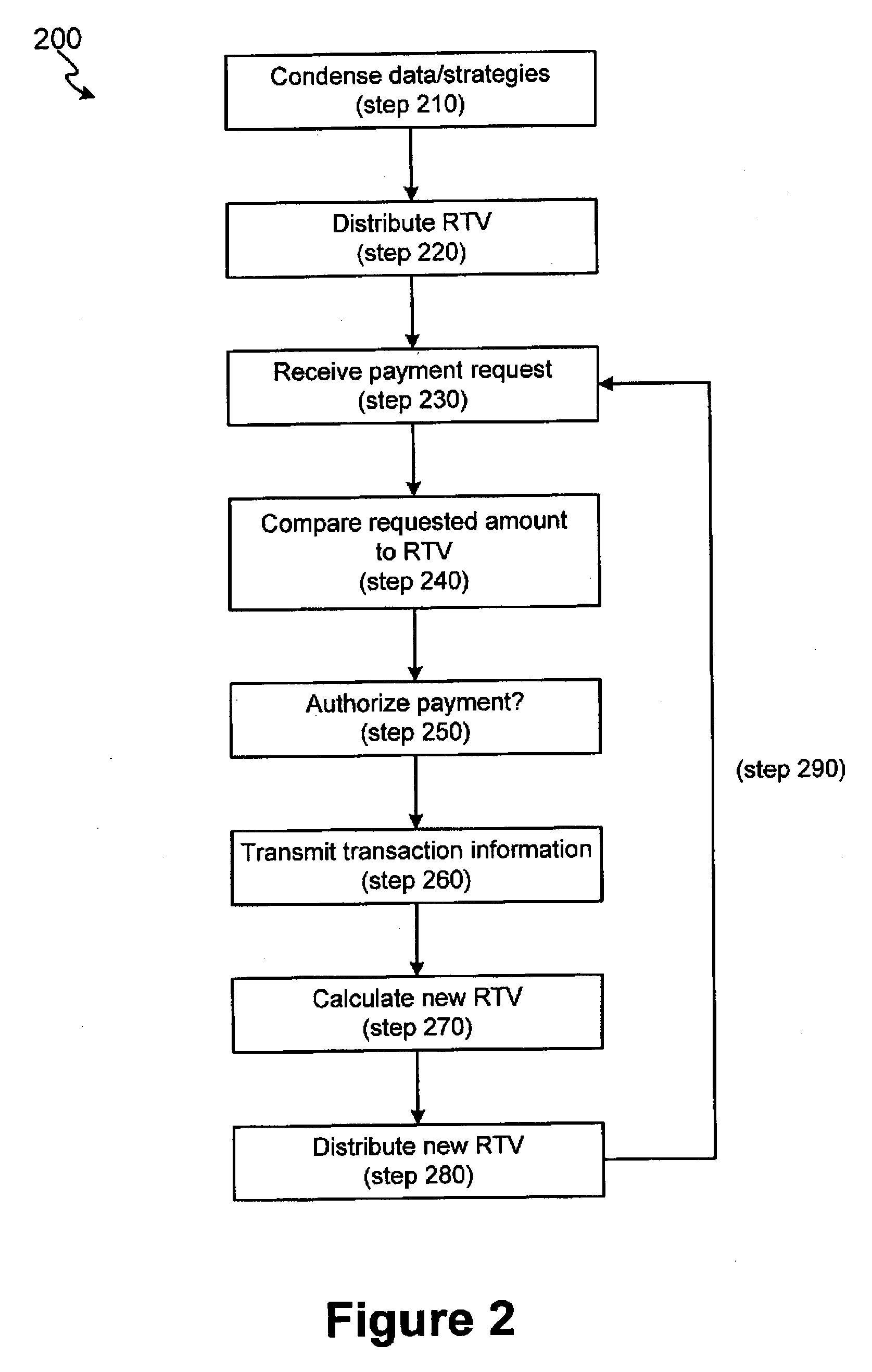
InactiveUS20080275821A1Facilitate authorizationComplete banking machinesFinancePaymentComputer science
The invention includes systems and methods for facilitating risk assessment for point of sale transactions utilizing at least one risk triggering value (RTV) stored within a distributed (e.g., local and / or regional) processing site. An RTV is a condensed version of a set of complex risk data and strategies usually found in central processing sites. The distributed site, after receiving a request for payment authorization, a risk value is calculated for the request. The distributed processing site compares the risk value to the RTV to determine whether to authorize payment. If the risk value is less than or equal to the RTV, the payment is authorized while a risk value greater than the RTV will not be authorized. After one or more authorizations, the distributed processing site forwards the information from the transaction(s) to the central site, wherein the central site calculates a new RTV for the account and distributes the new RTV to the distributed processing site.
Owner:LIBERTY PEAK VENTURES LLC
Network security testing
ActiveUS7325252B2Improve viewing effectShort working hoursMemory loss protectionError detection/correctionSecurity solutionWork period
To answer the security needs of the market, a preferred embodiment was developed. A preferred embodiment provides real-time network security vulnerability assessment tests, possibly complete with recommended security solutions. External vulnerability assessment tests can emulate hacker methodology in a safe way and enable study of a network for security openings, thereby gaining a true view of risk level without affecting customer operations. Because this assessment can be performed over the Internet, both domestic and worldwide corporations benefit. A preferred embodiment's physical subsystems combine to form a scalable holistic system that can be able to conduct tests for thousands of customers any place in the world. The security skills of experts can be embedded into a preferred embodiment systems and automated the test process to enable the security vulnerability test to be conducted on a continuous basis for multiple customers at the same time. A preferred embodiment can reduce the work time required for security practices of companies from three weeks to less than a day, as well as significantly increase their capacity. Component subsystems typically include a Database, Command Engine, Gateway, multiple Testers, Report Generator, and an RMCT.
Owner:ALERT LOGIC
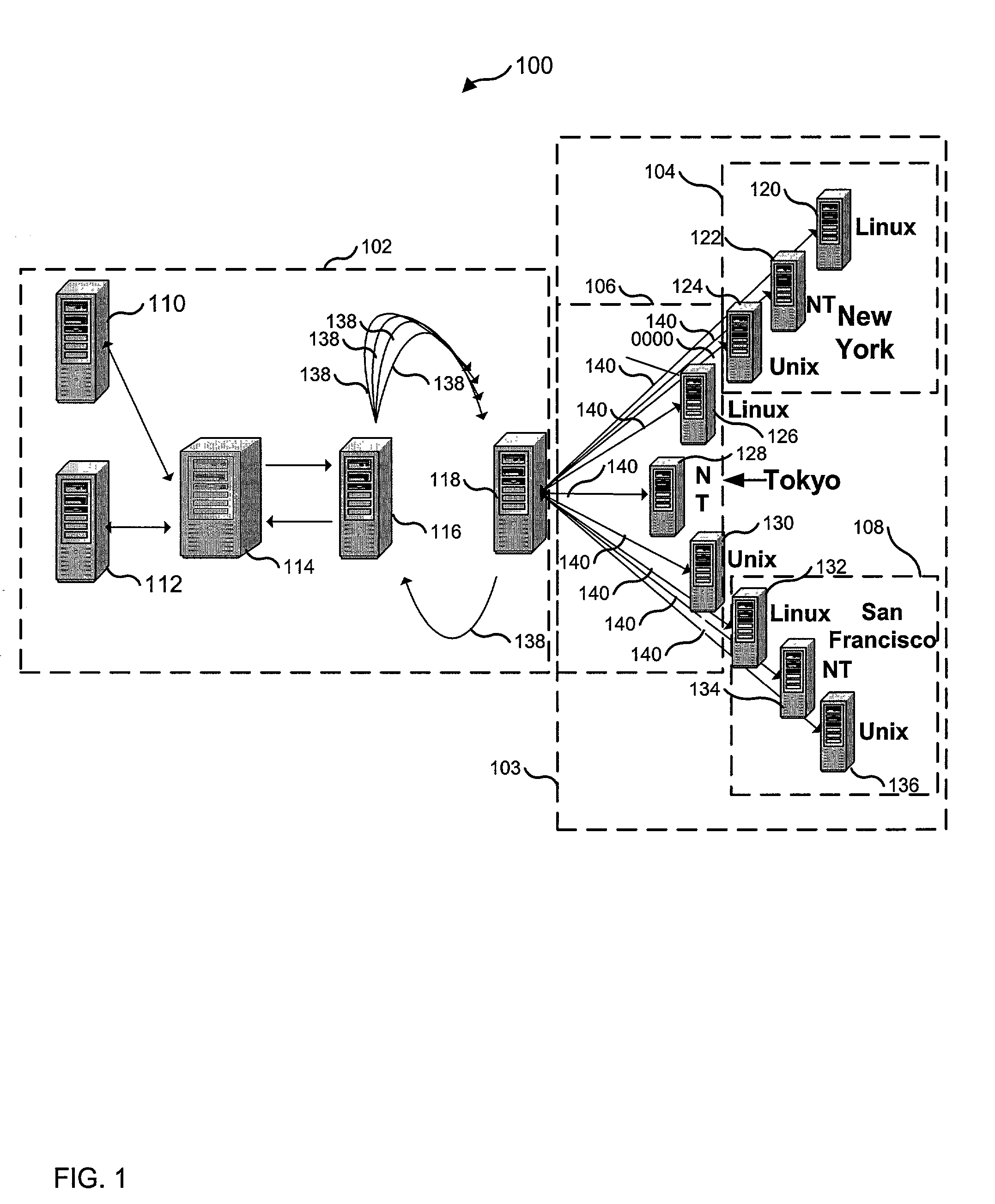
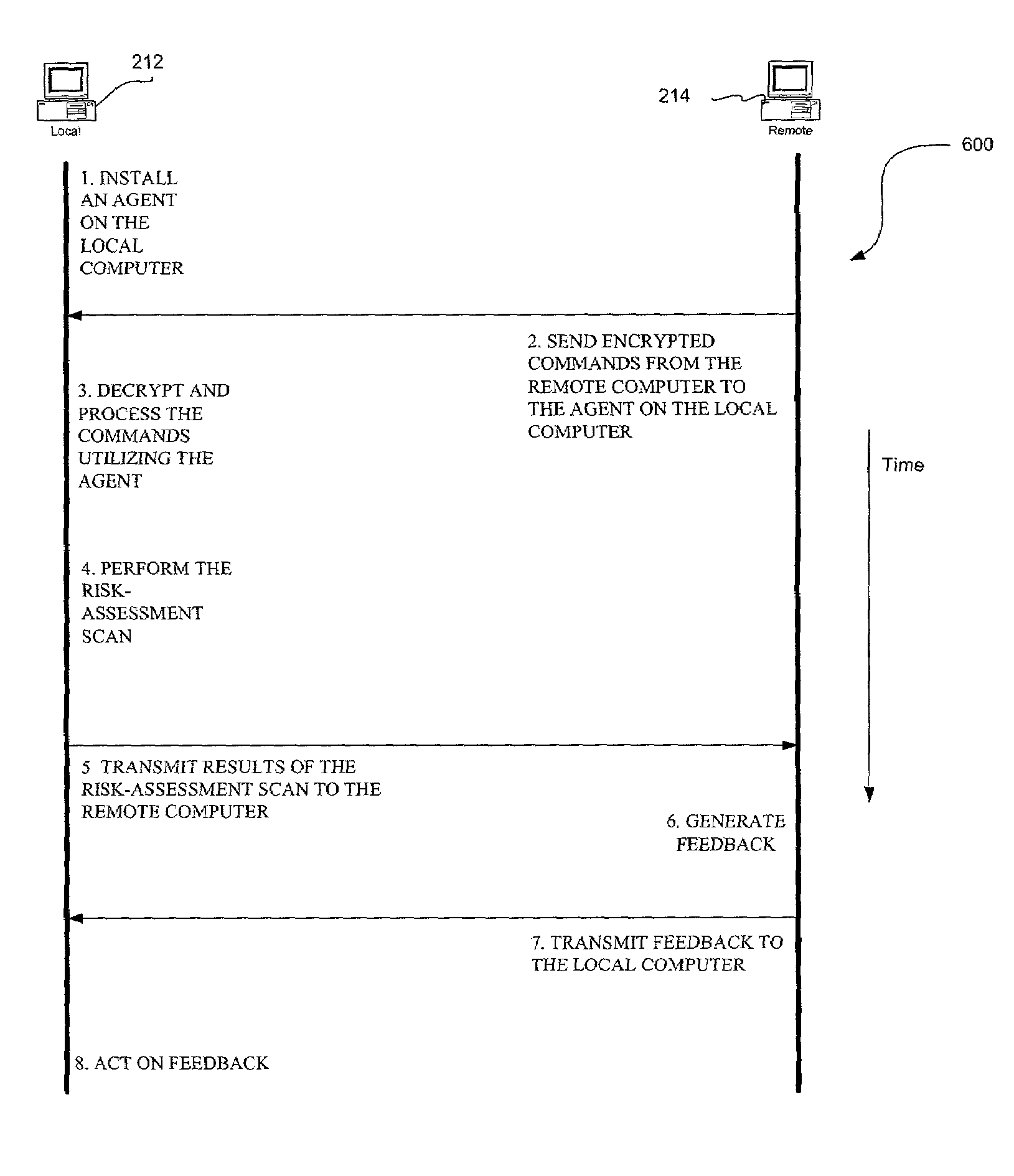
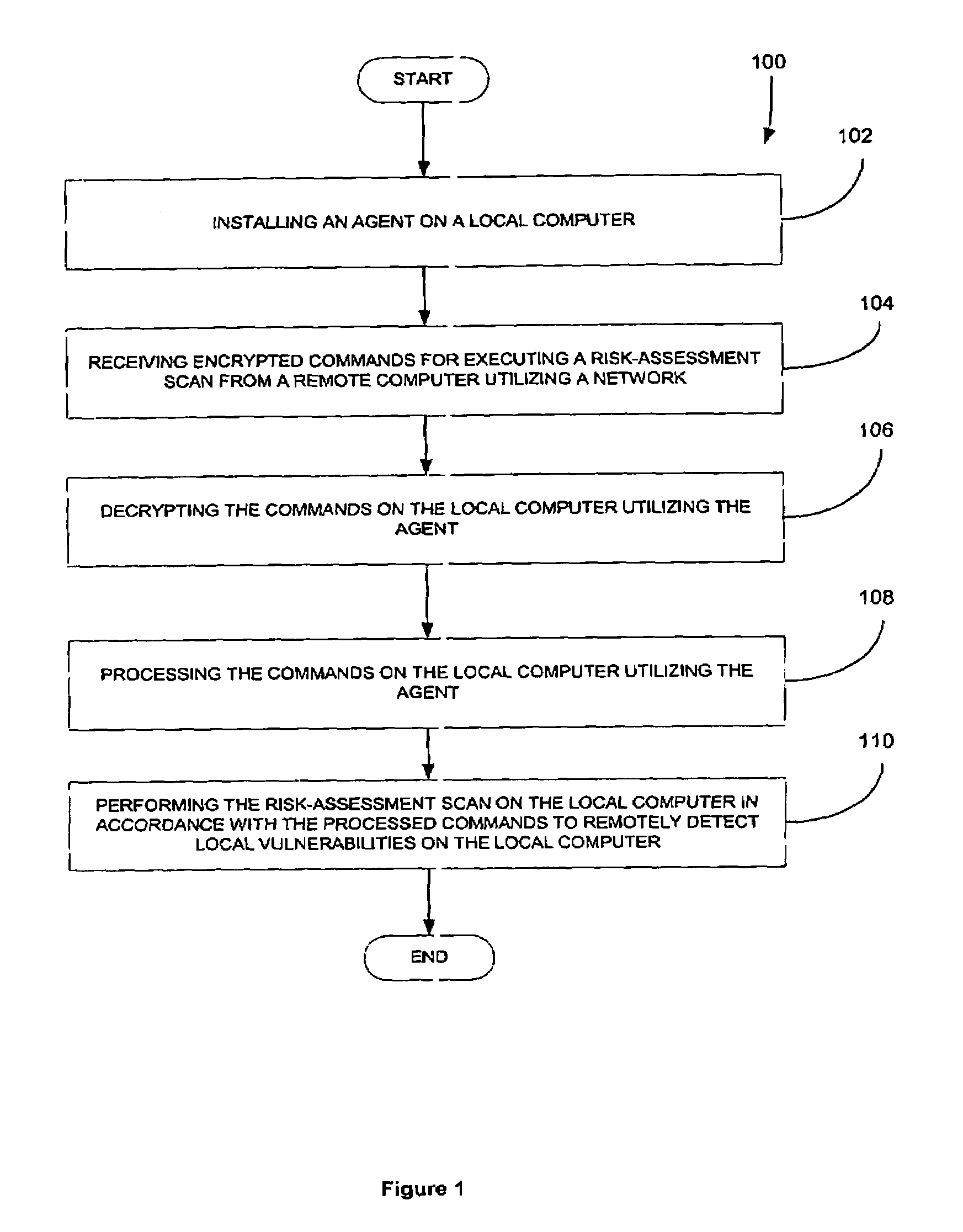
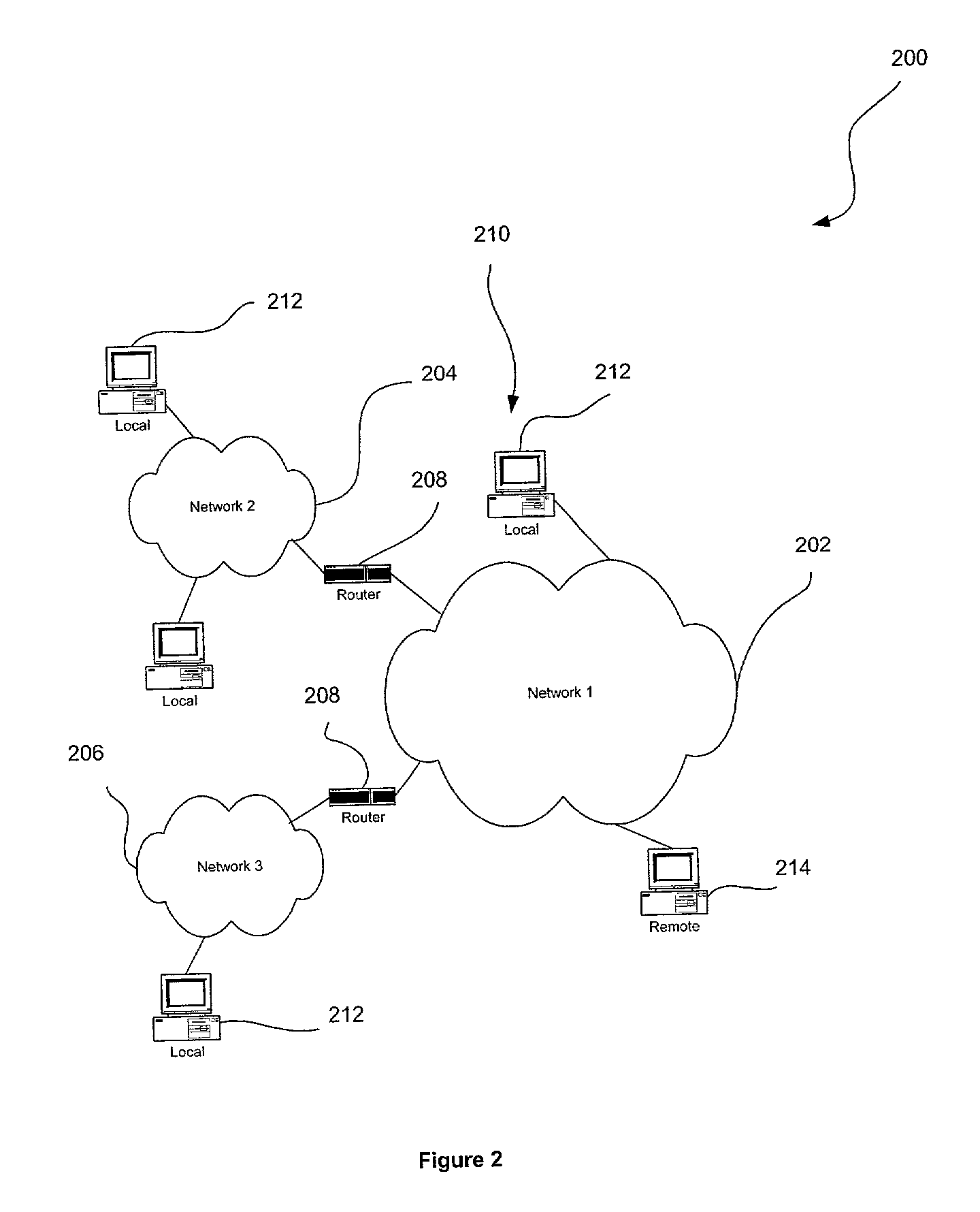
Network-based risk-assessment tool for remotely detecting local computer vulnerabilities
ActiveUS7096503B1Memory loss protectionUnauthorized memory use protectionRemote computerRisk evaluation
A system, method and computer program product are provided for remotely detecting vulnerabilities on a local computer. Initially, an agent is installed on a local computer for receiving encrypted commands from a remote computer utilizing a network. Next, the commands are decrypted and processed on the local computer utilizing the agent. A risk-assessment scan is then performed on the local computer utilizing the agent in accordance with the processed commands for the purpose of remotely detecting local vulnerabilities on the local computer.
Owner:MCAFEE LLC
Policy/rule engine, multi-compliance framework and risk remediation
Owner:ALERT ENTERPRISE
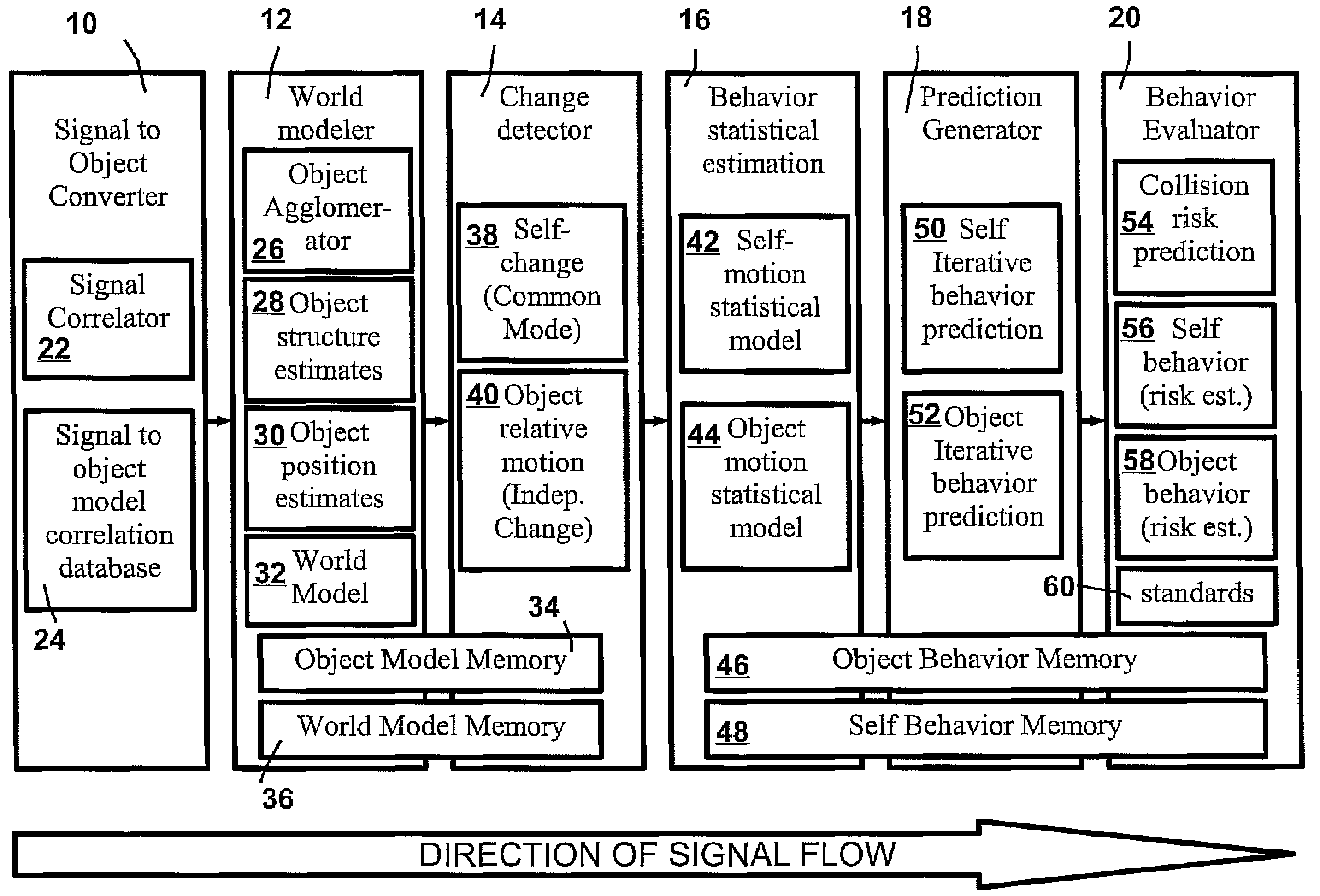
Extra-vehicular threat predictor
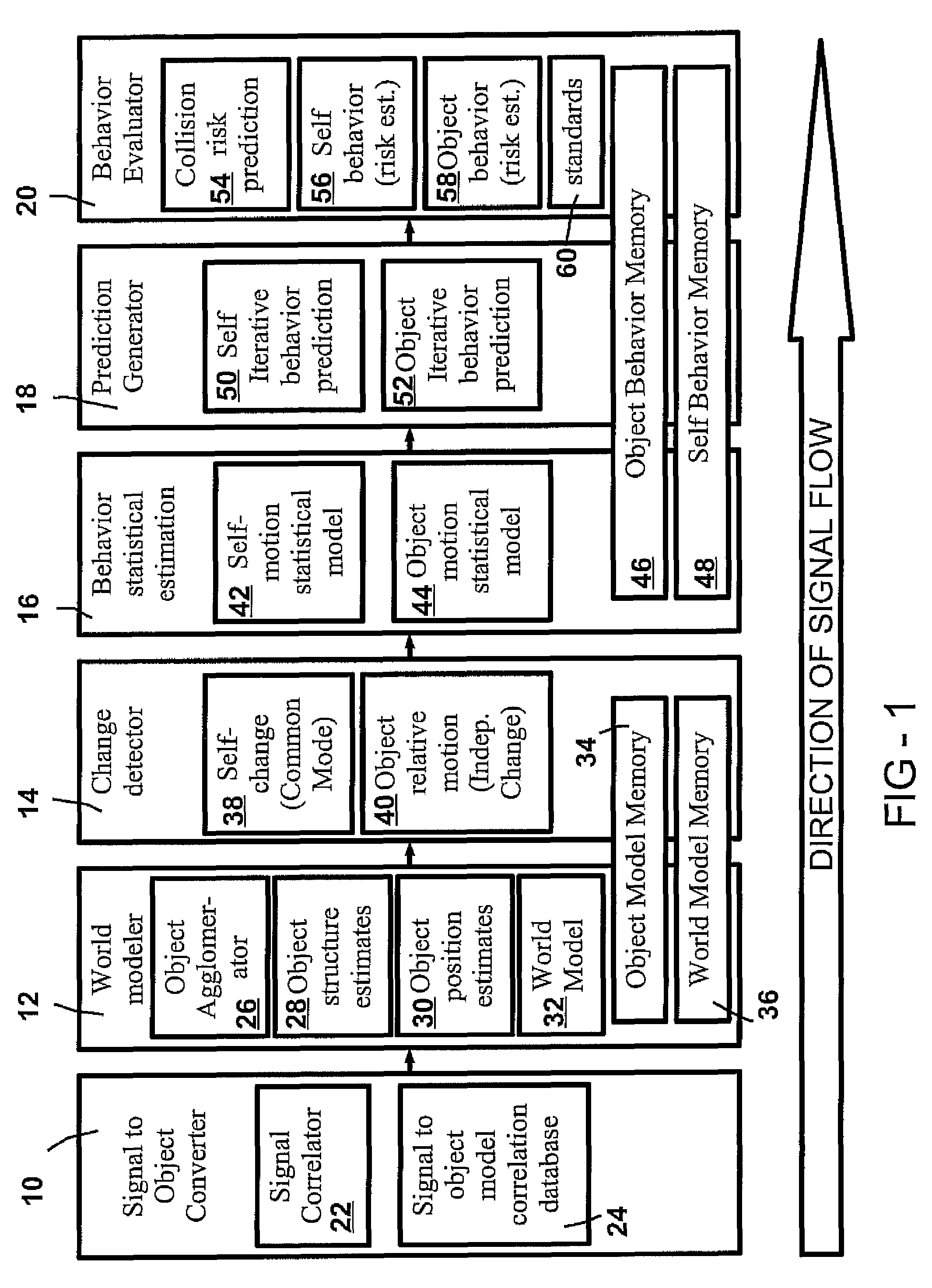
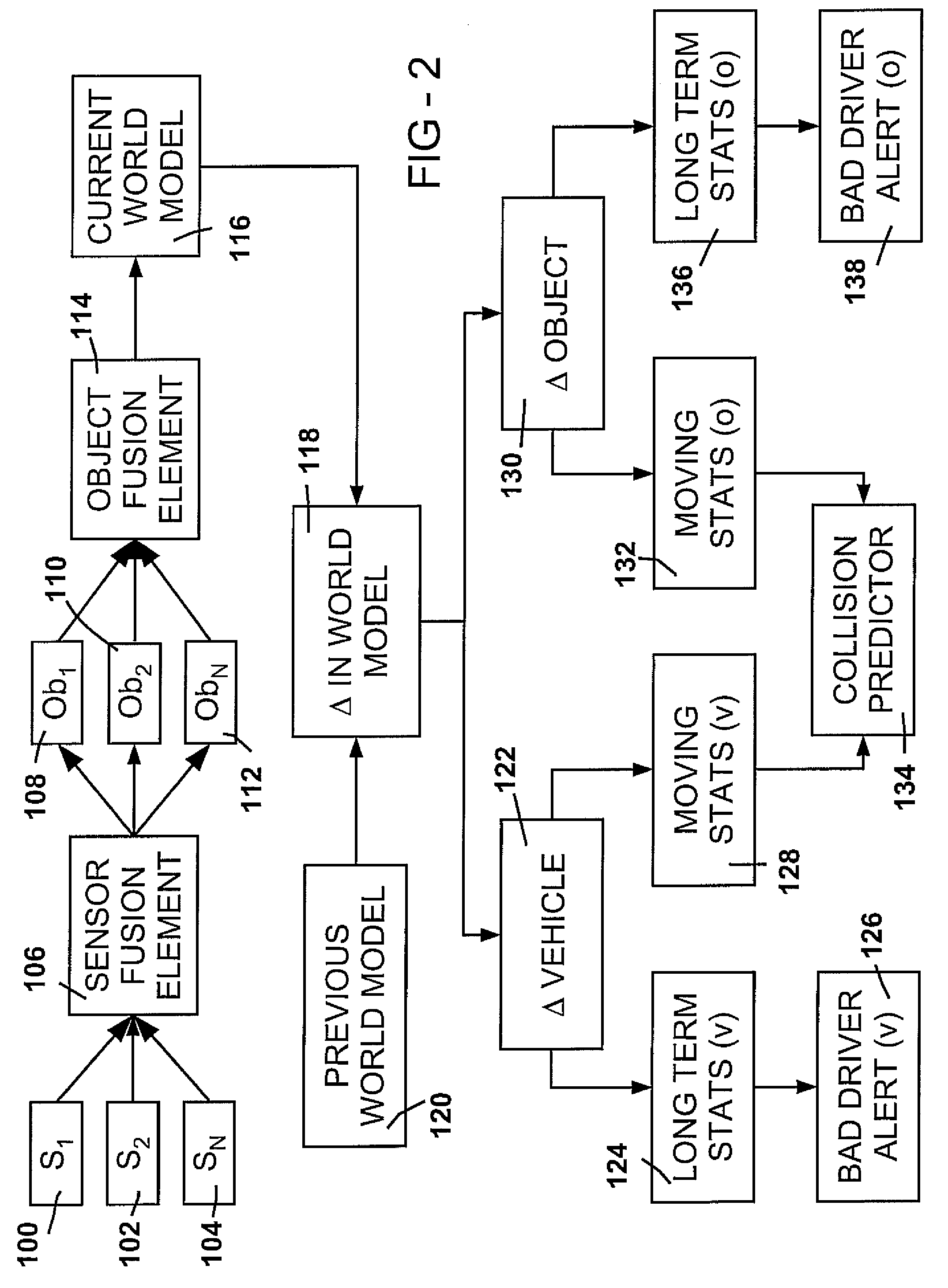
An apparatus for facilitating the safe operation of a vehicle comprises a sensor system, a sensor signal to object identifier, and a world model implemented using, for example, a multiple-input multiple-output (MIMO) algorithm such as a spiking neuron algorithm. Alerts may be provided to the vehicle operator under several conditions, such as the identification of a collision risk between the vehicle and an object, identification of a vehicle risk due to excessive uncertainty in the predicted vehicle path, or identification of an object risk due to excessive uncertainty in a predicted object path.
Owner:TOYOTA MOTOR CO LTD
Method, system, and computer program product for risk assessment and risk management
Owner:NAT BRITANNIA GROUP
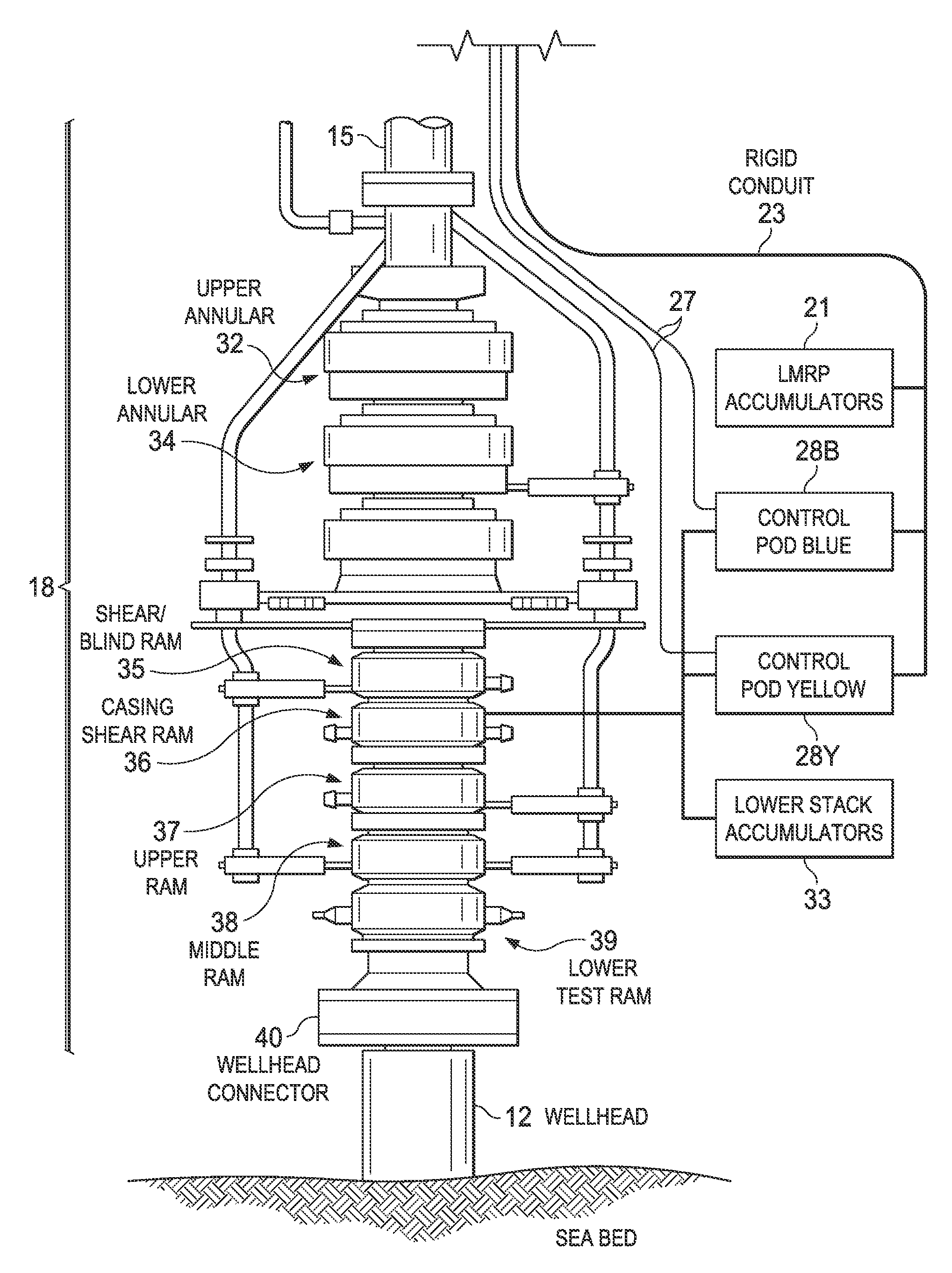
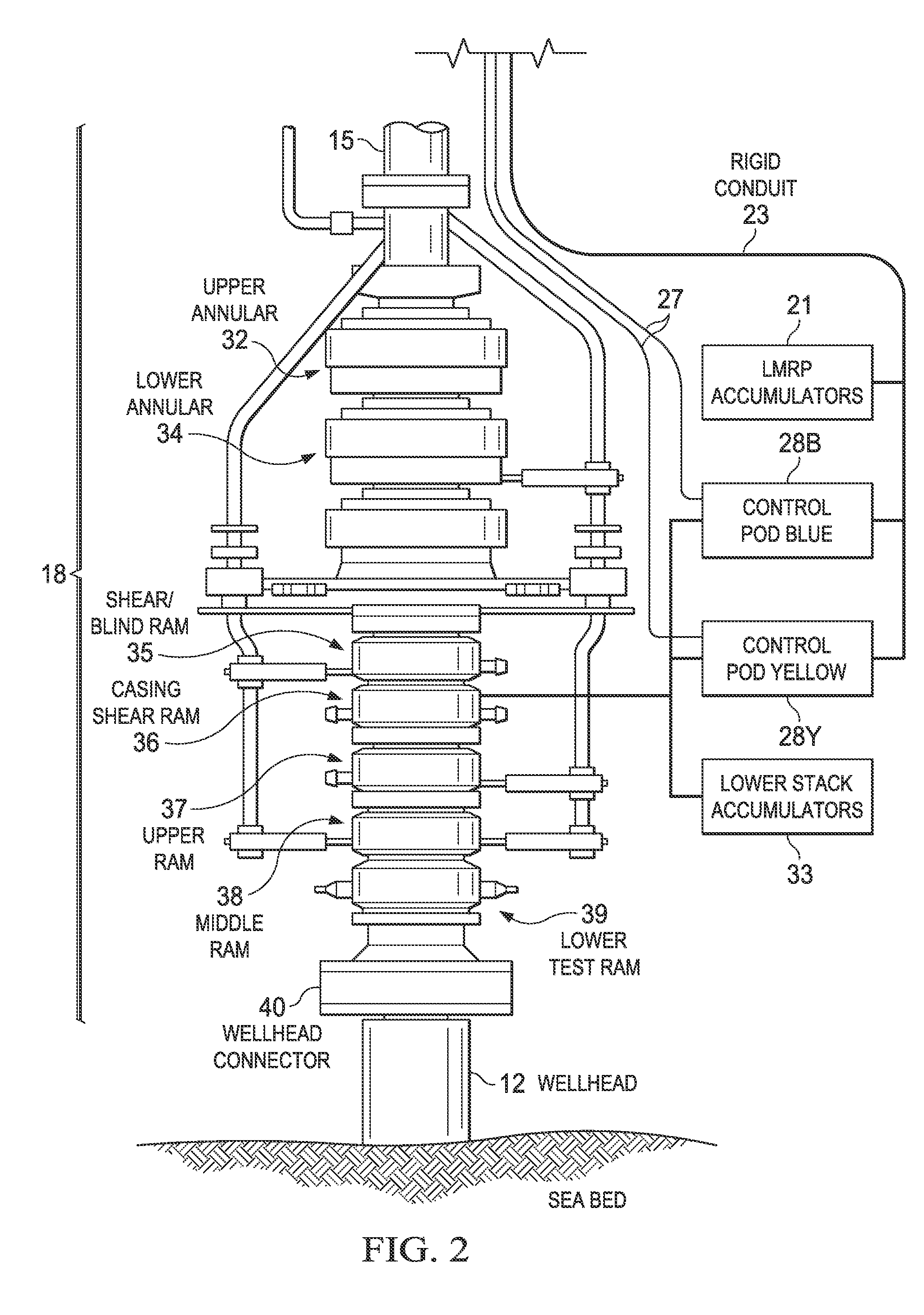
Monitoring the health of a blowout preventer
InactiveUS20120197527A1Electric/magnetic detection for well-loggingFluid removalTraffic signalDisplay device
A computerized monitoring system and corresponding method of monitoring the status and health of a blowout preventer. The system includes a graphics display at which a graphical user interface (GUI) displays the health of various sealing elements and control systems by way of “traffic light” indicators. The health indicators are evaluated, by the monitoring system, based on a risk profile for each of the indicated elements and control systems. The risk profiles are evaluated based on inputs such as measurement inputs, feedback signals, mechanical positions, diagnostic results, drilling conditions, and other status information of the blowout preventer at a given time and based on levels of redundancy and levels of deviation from normal conditions. The GUI includes recent history of changes in operating condition, and alarm indications such as poor health, along with the times of those events.
Owner:BP CORP NORTH AMERICA INC
Pervasive, domain and situational-aware, adaptive, automated, and coordinated analysis and control of enterprise-wide computers, networks, and applications for mitigation of business and operational risks and enhancement of cyber security
ActiveUS8856936B2Minimize false positivesTrue to riskMemory loss protectionError detection/correctionApplication softwareBusiness process
Owner:ALBEADO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com