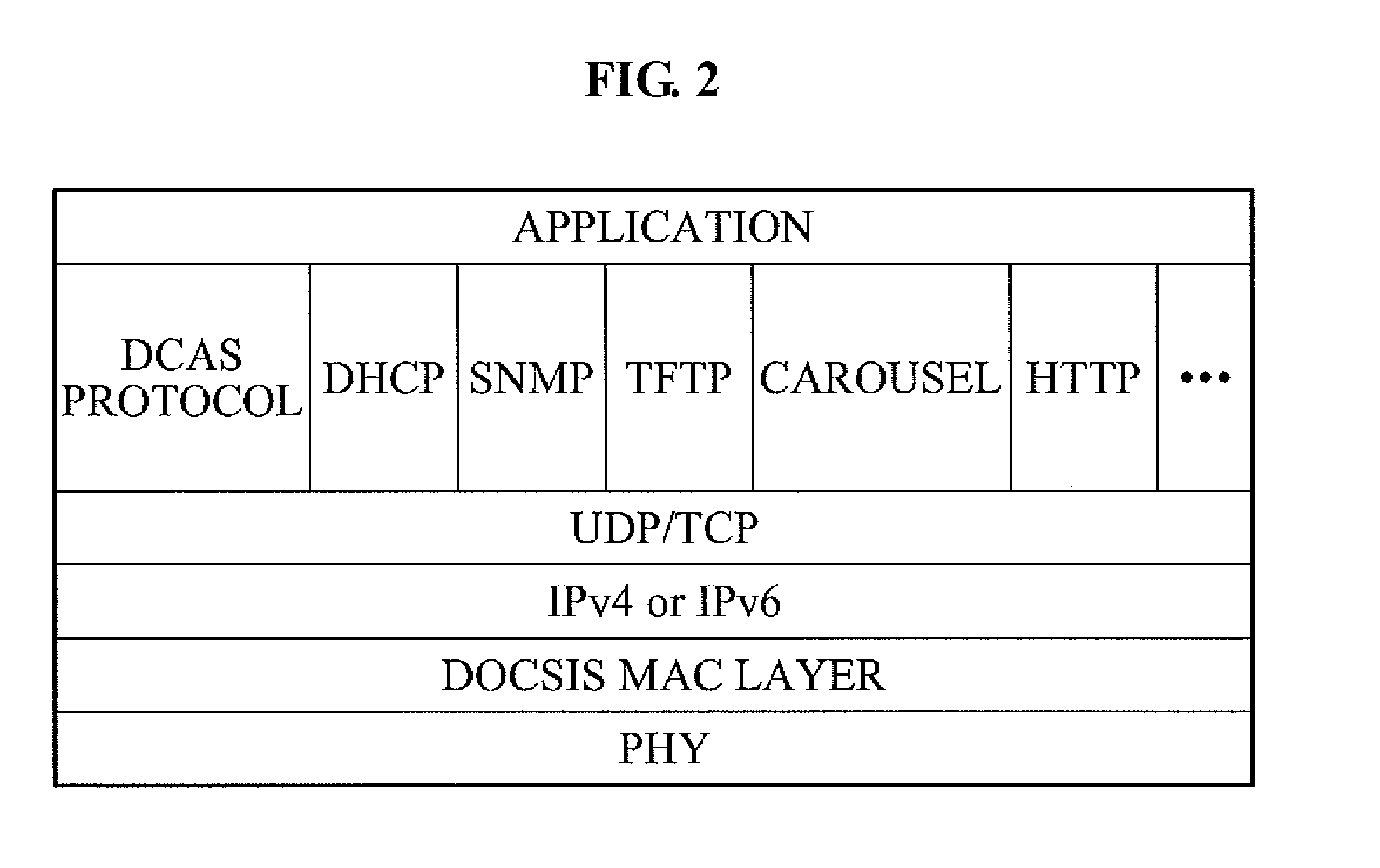
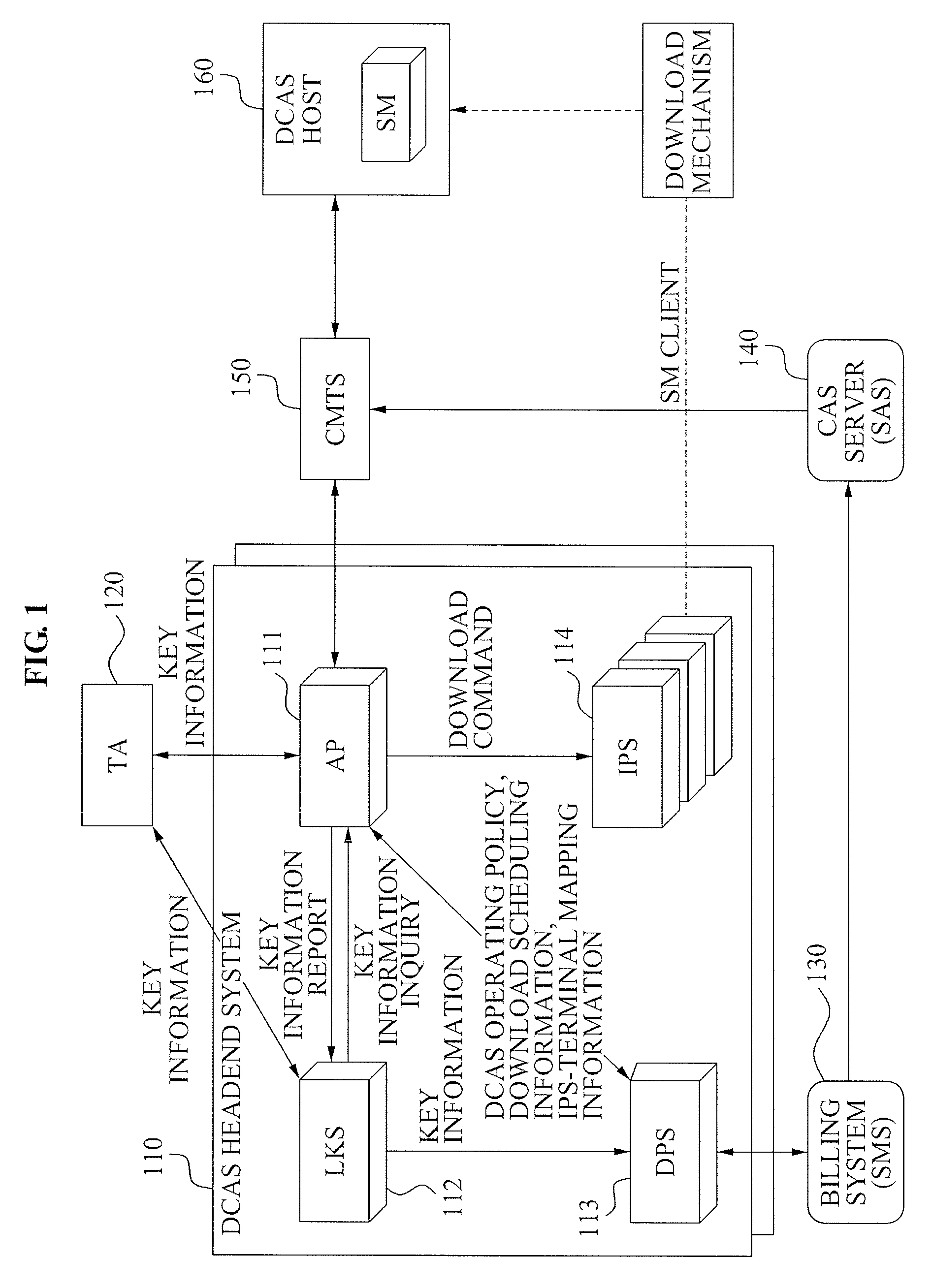
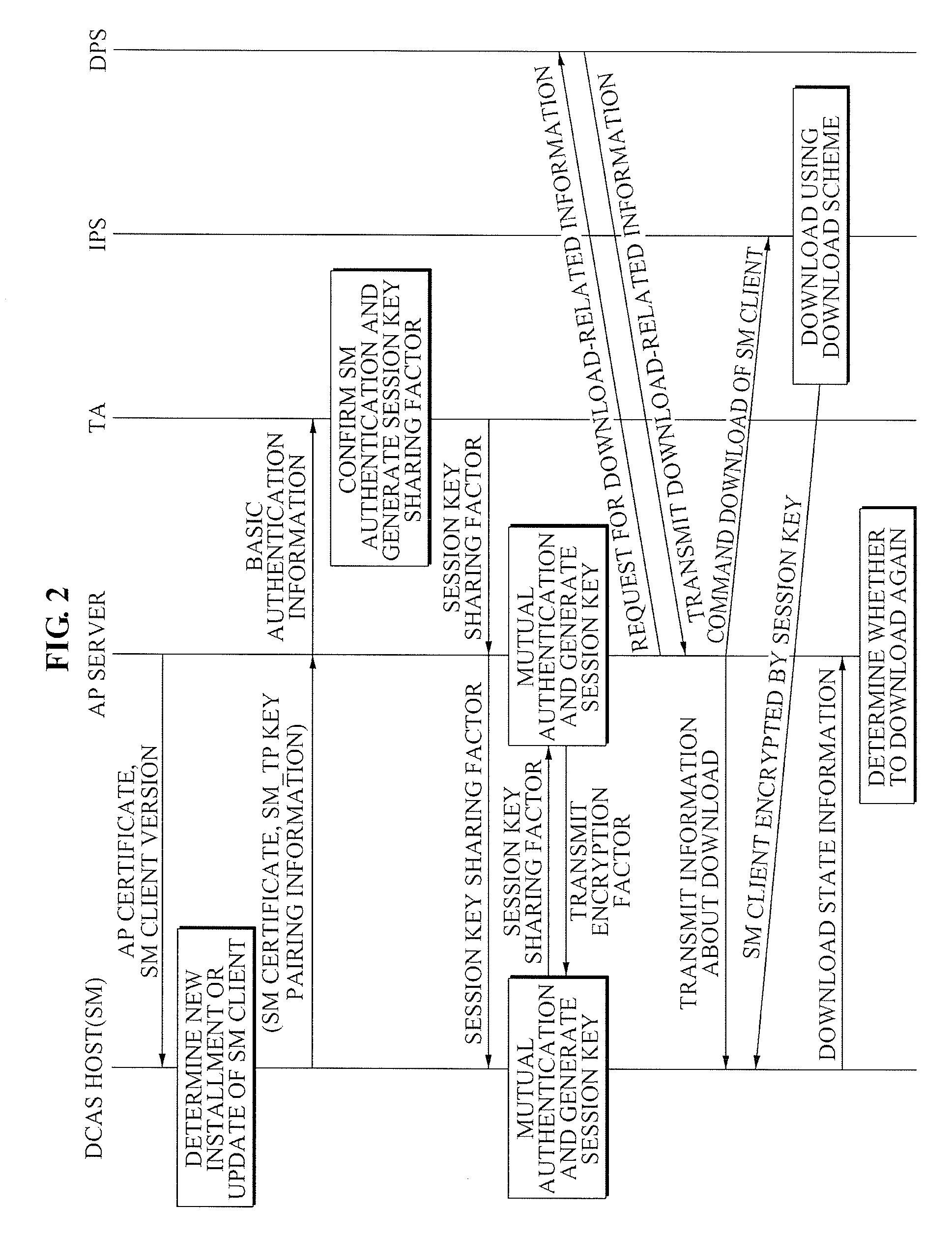
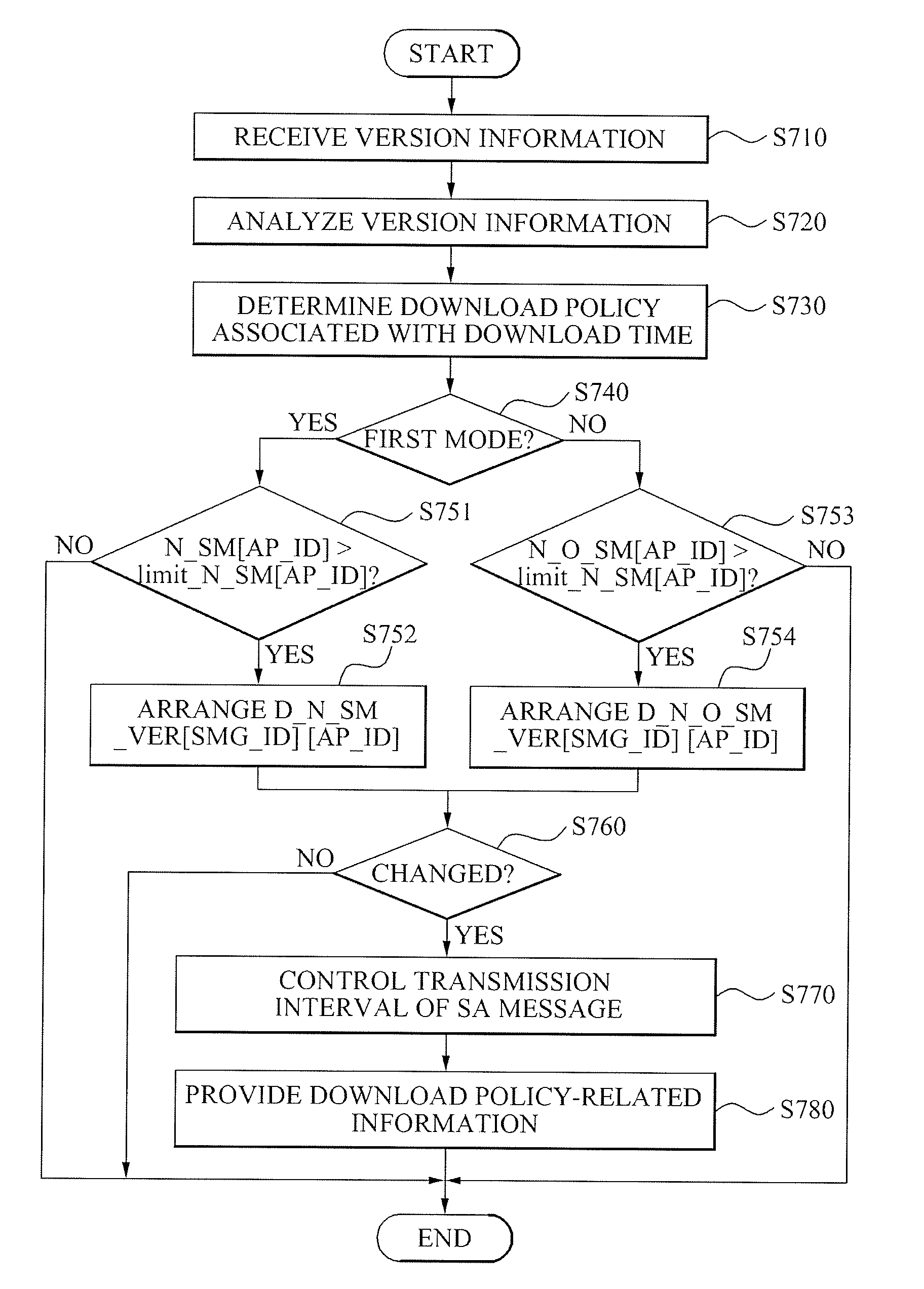
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46 results about "Downloadable Conditional Access System" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
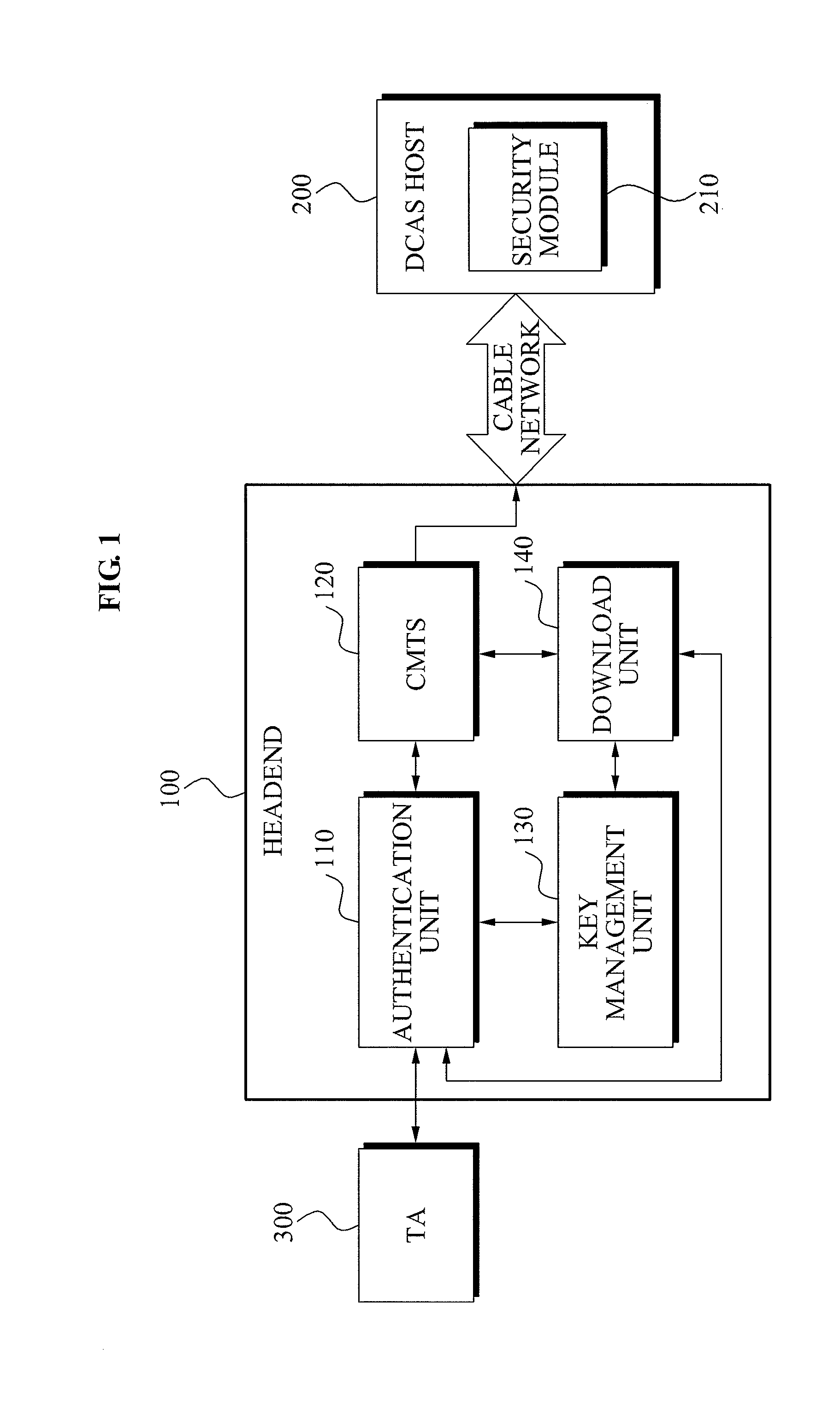
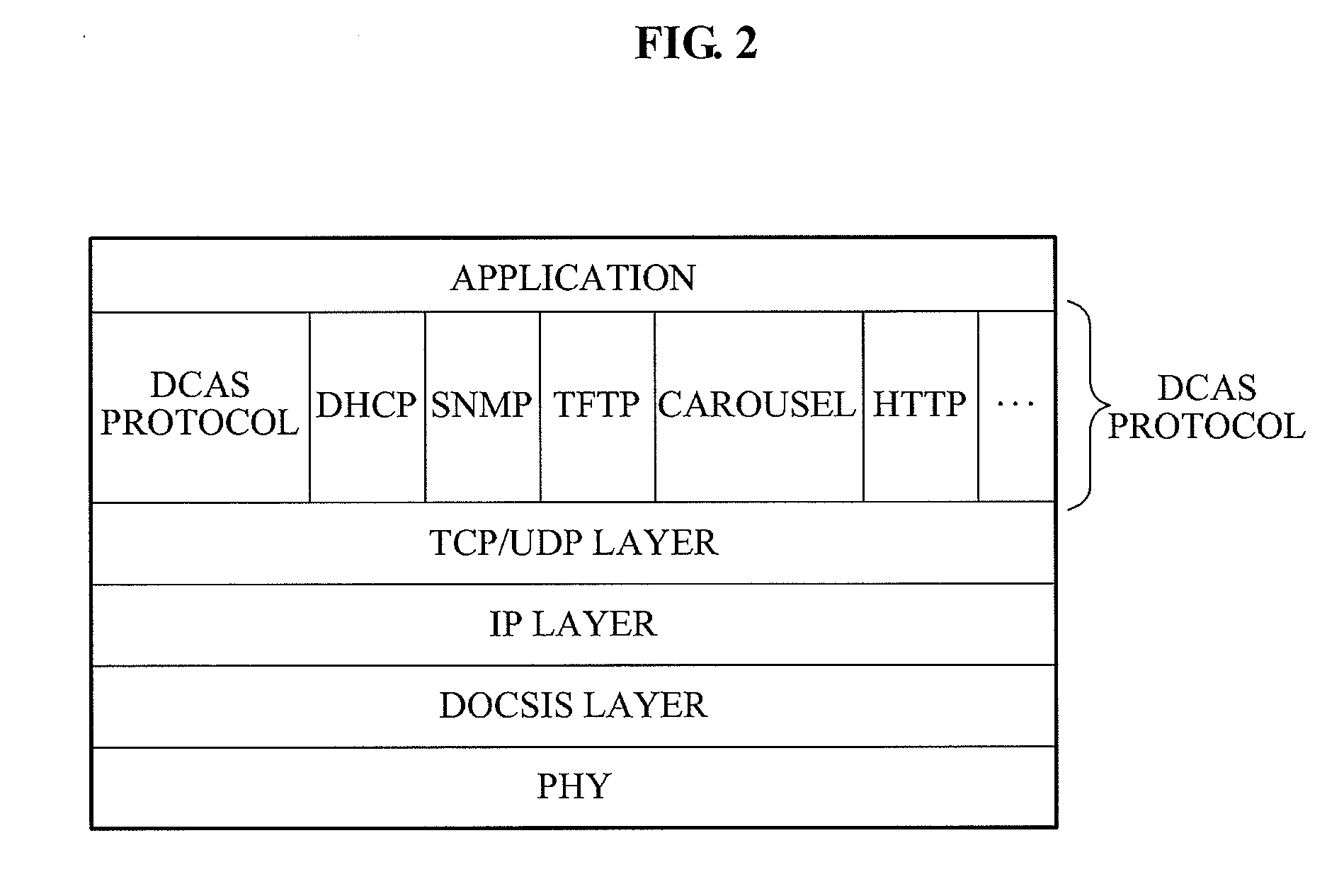
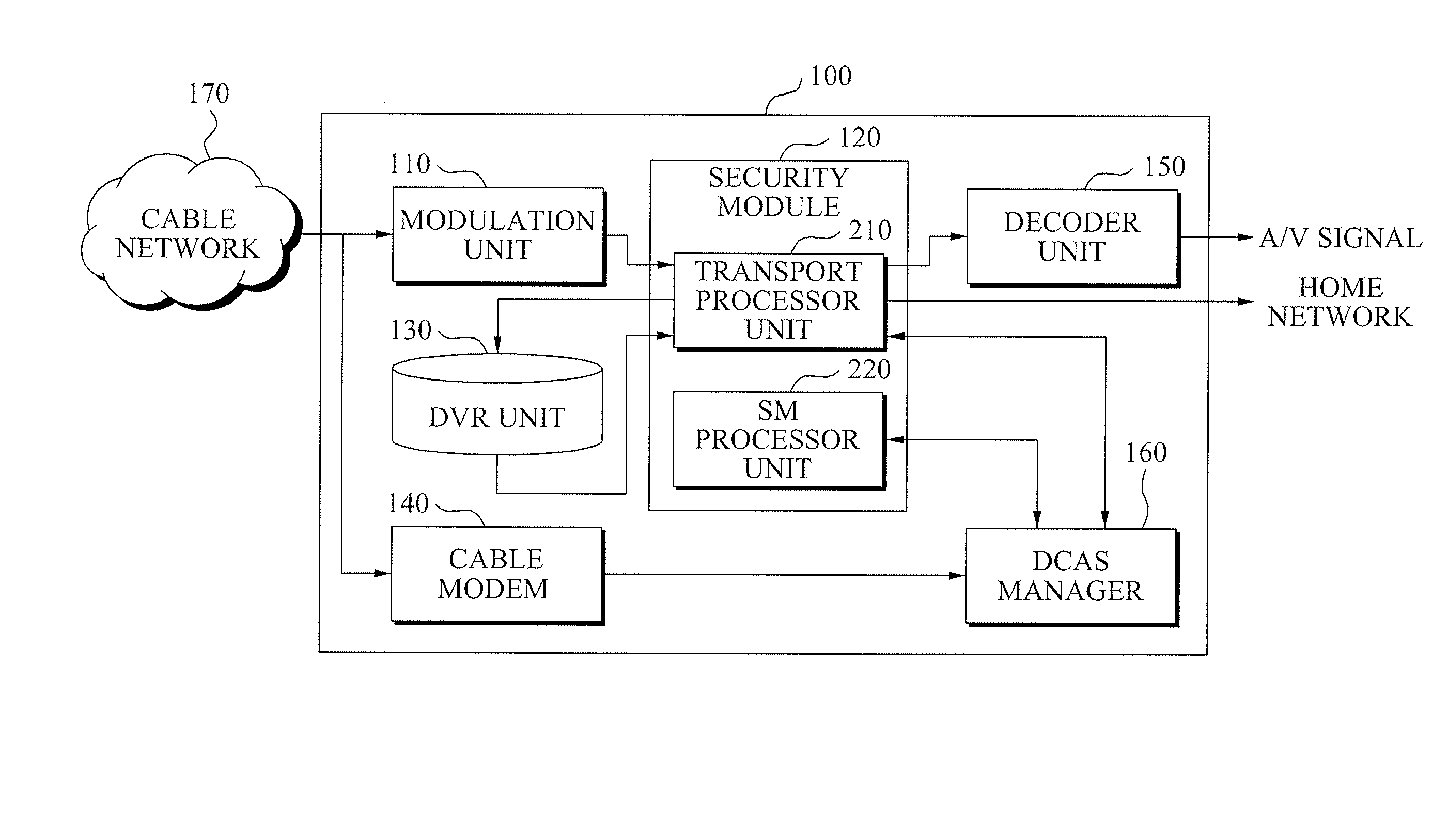
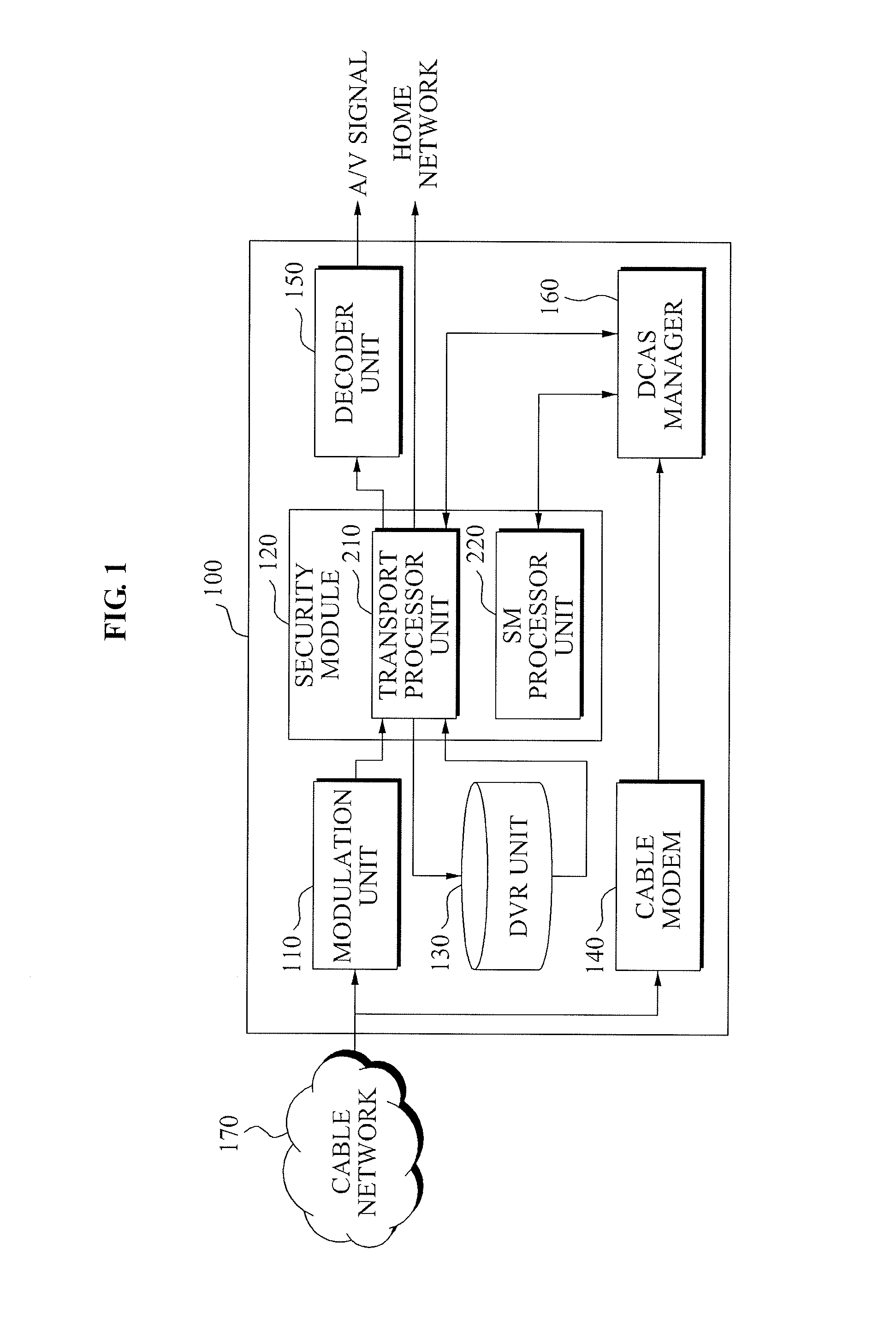
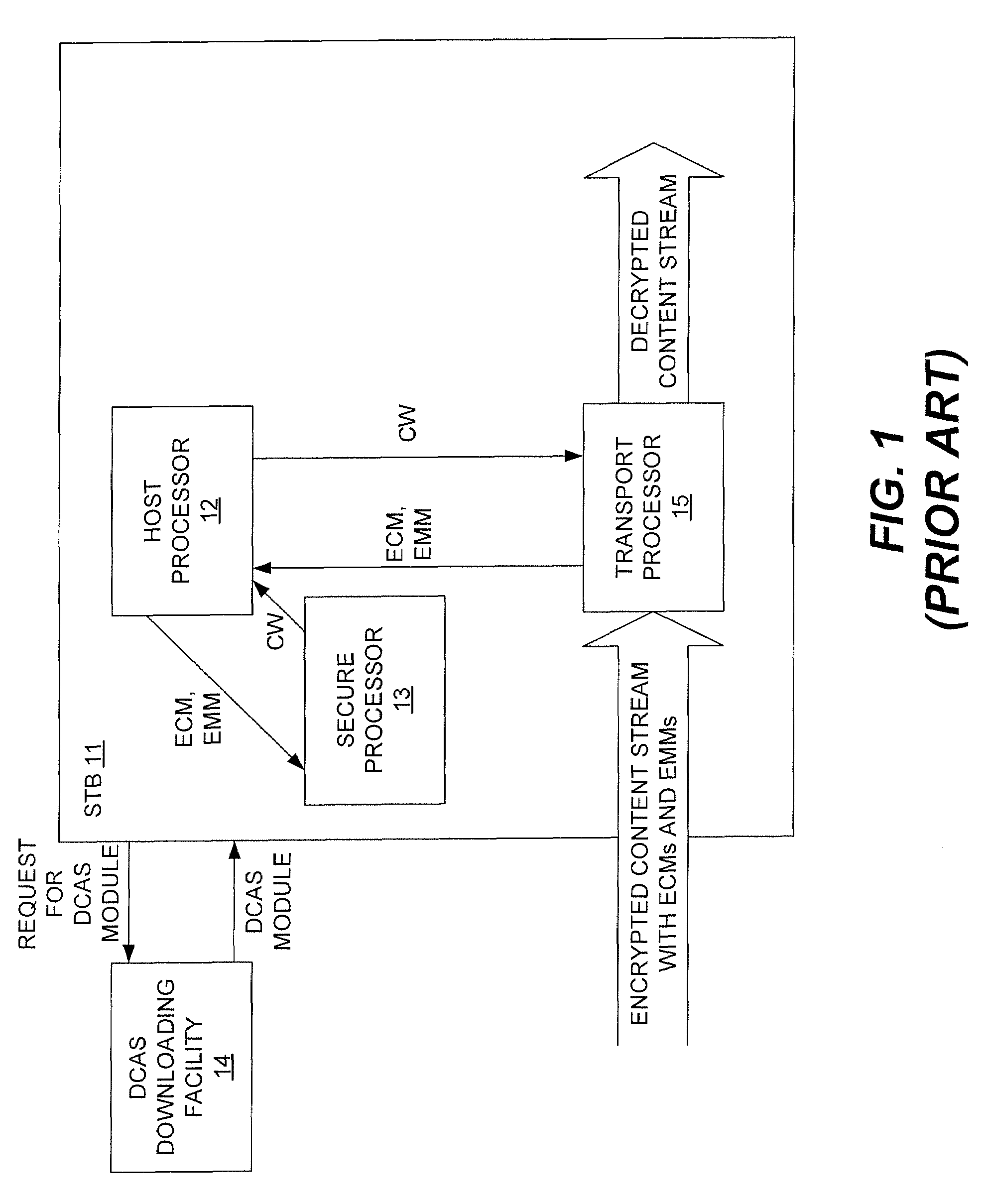
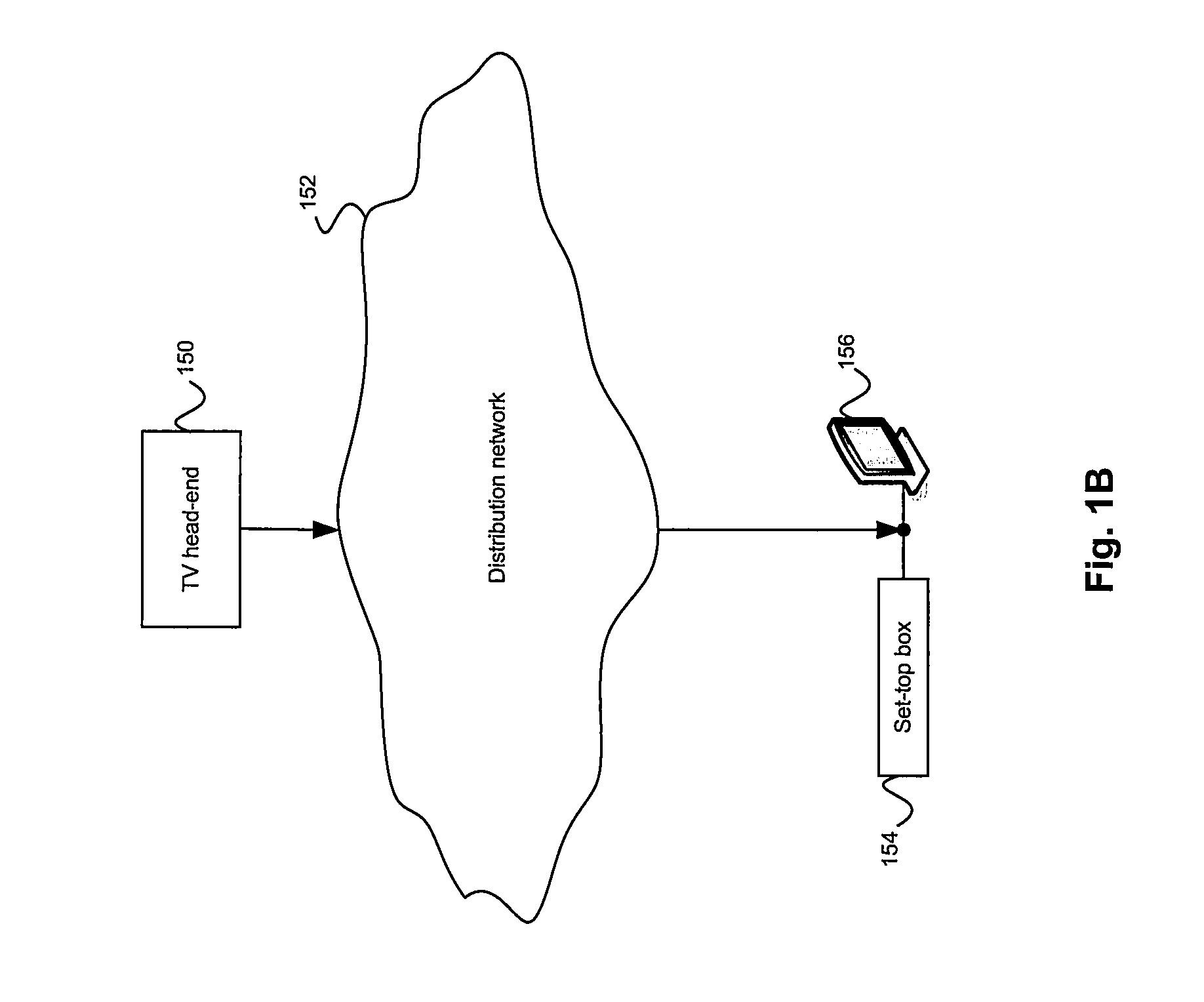
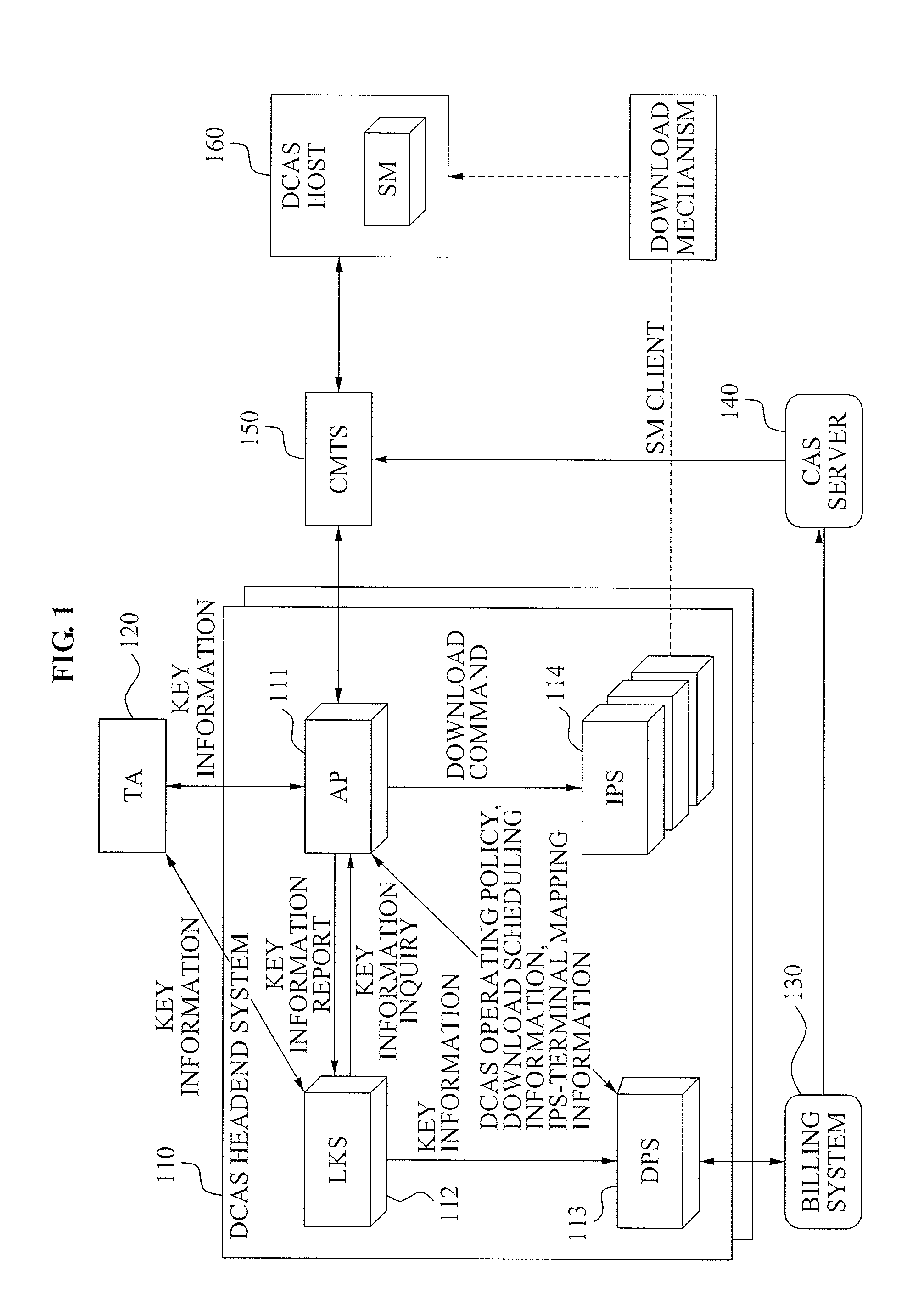
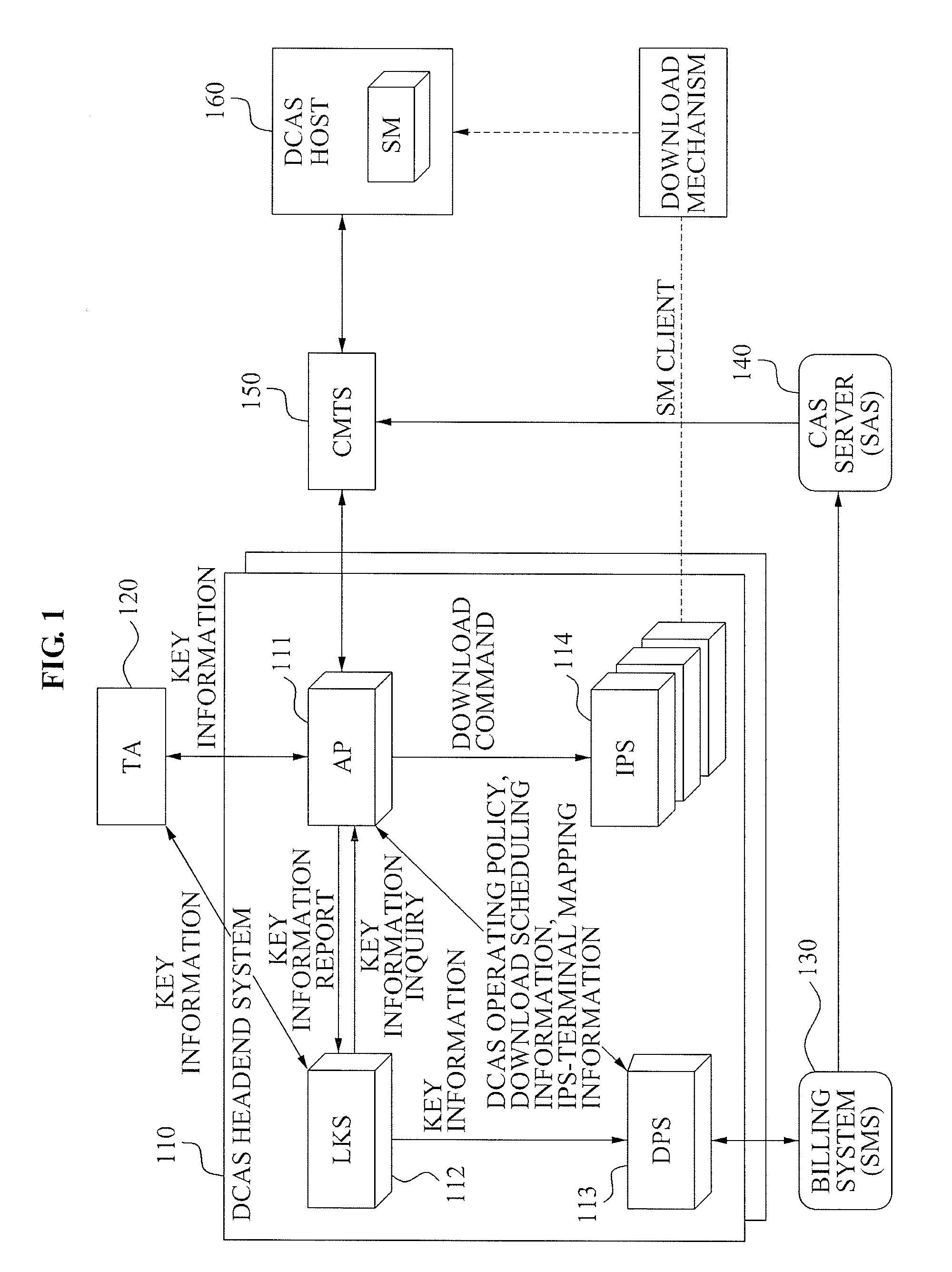
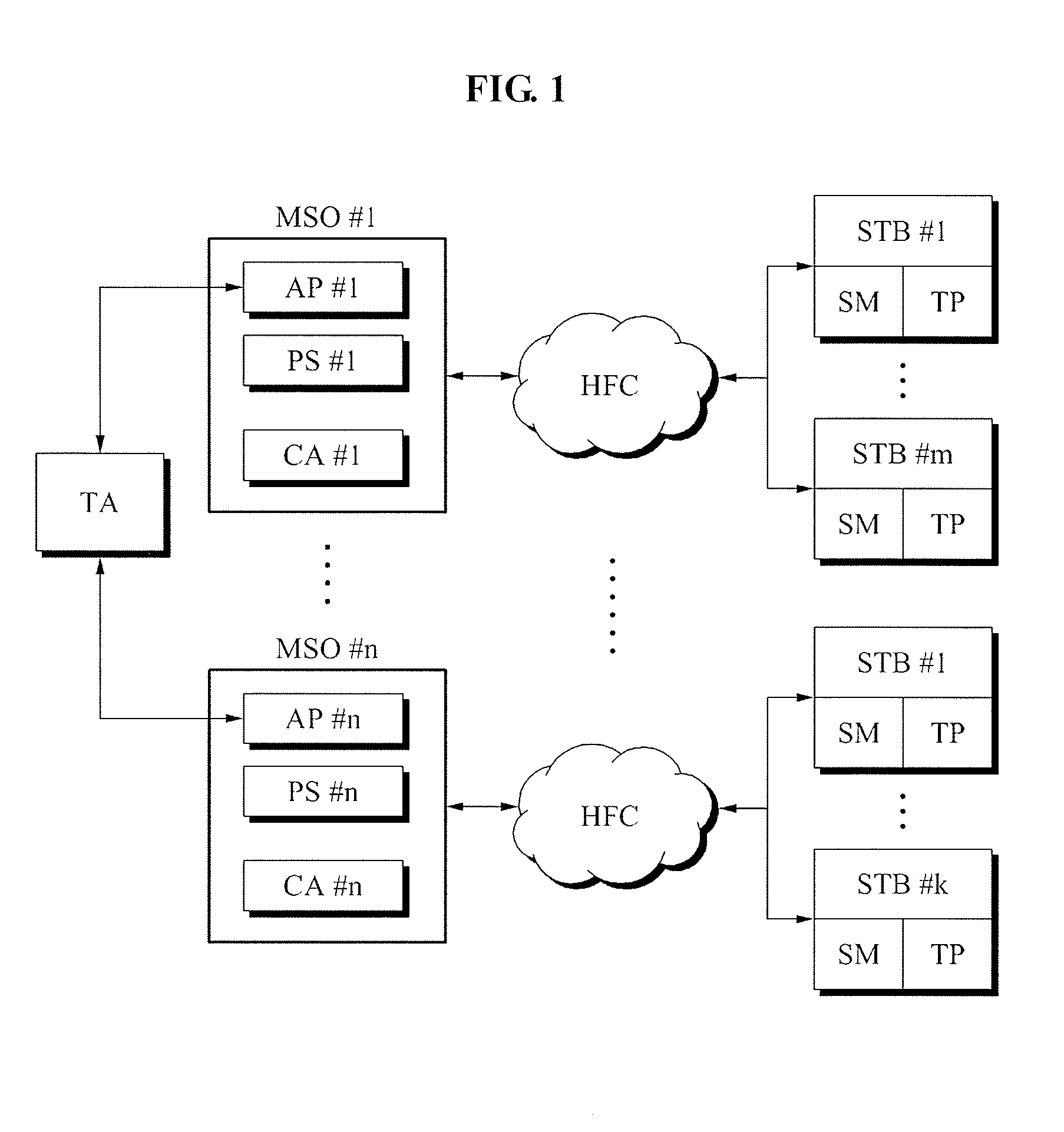
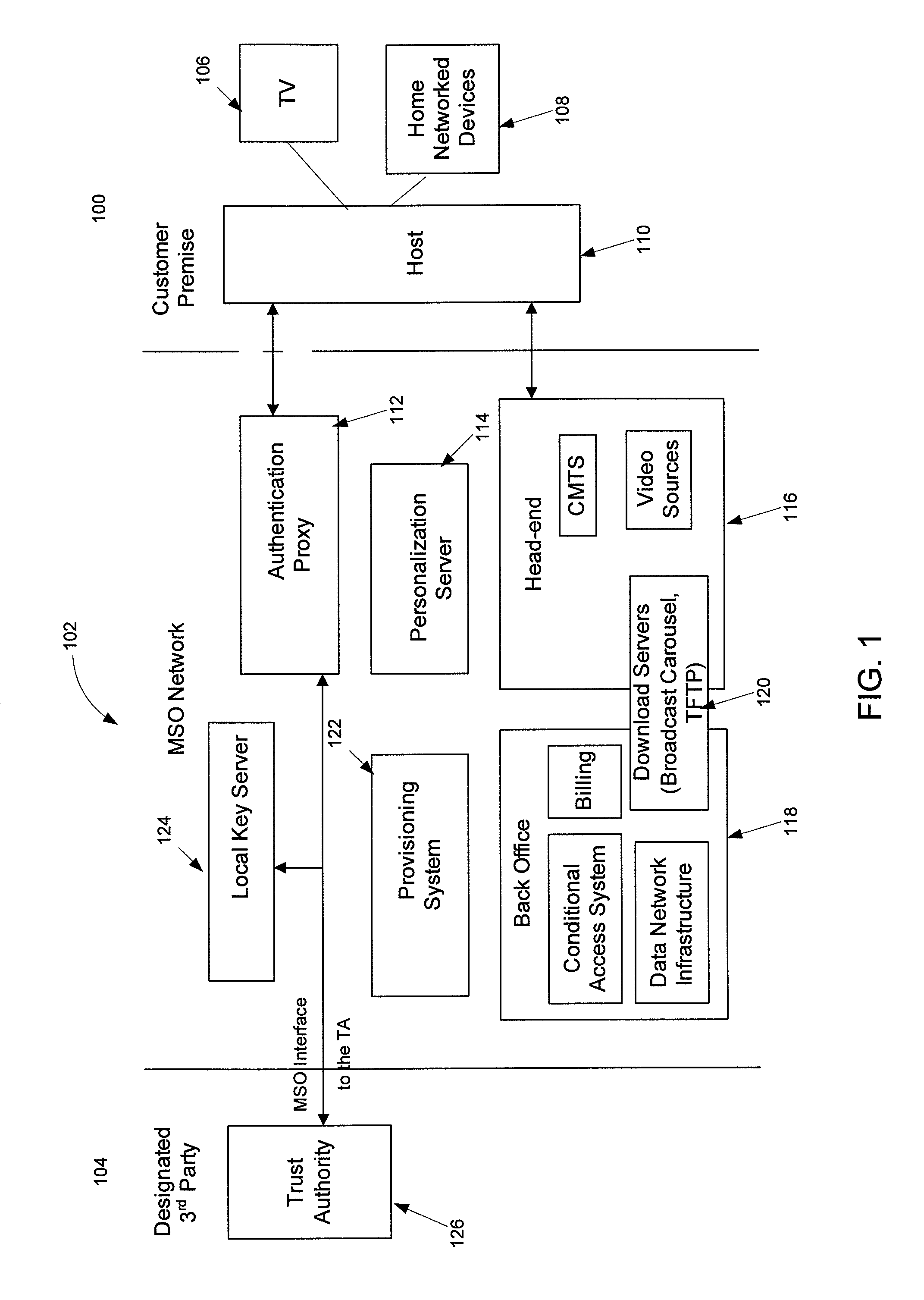
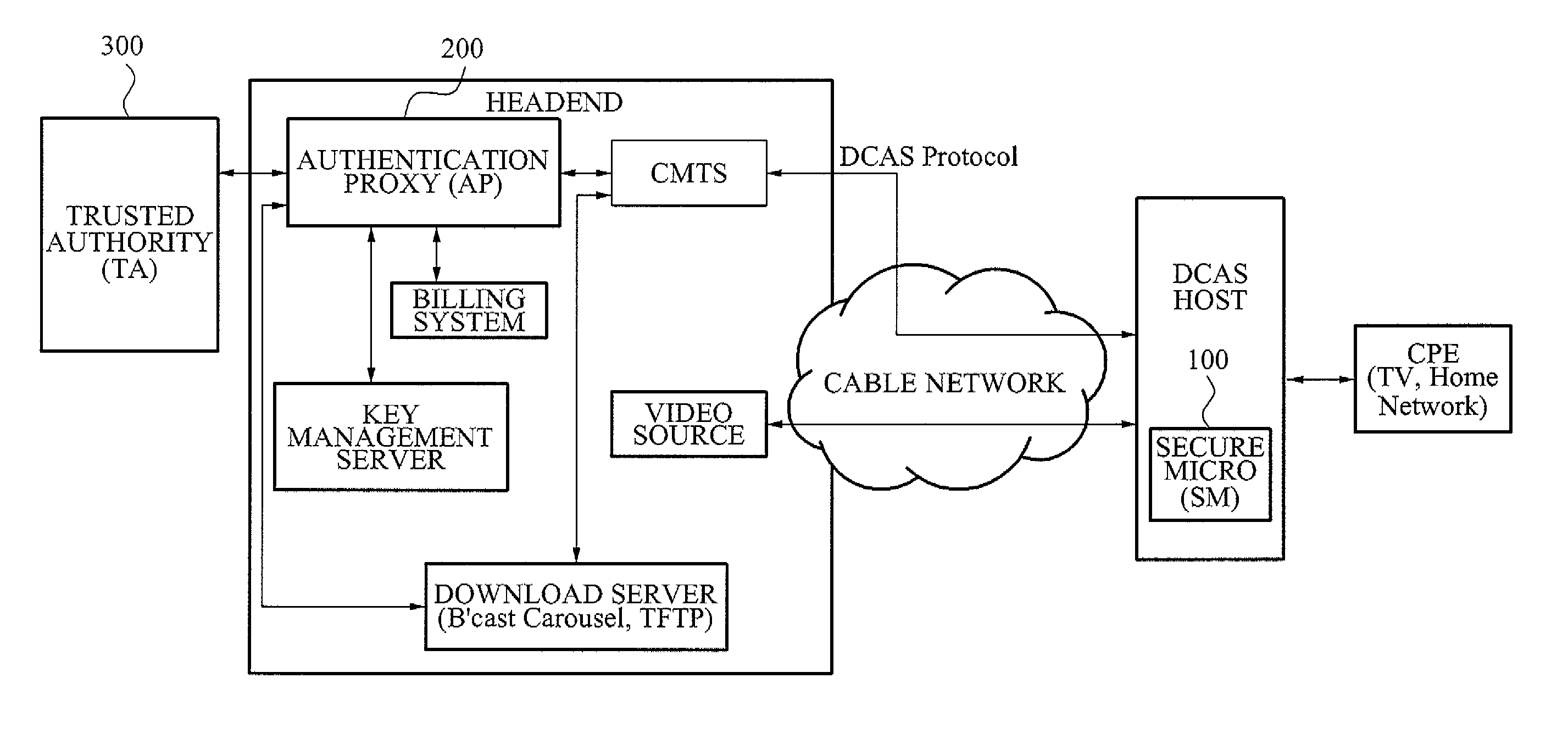
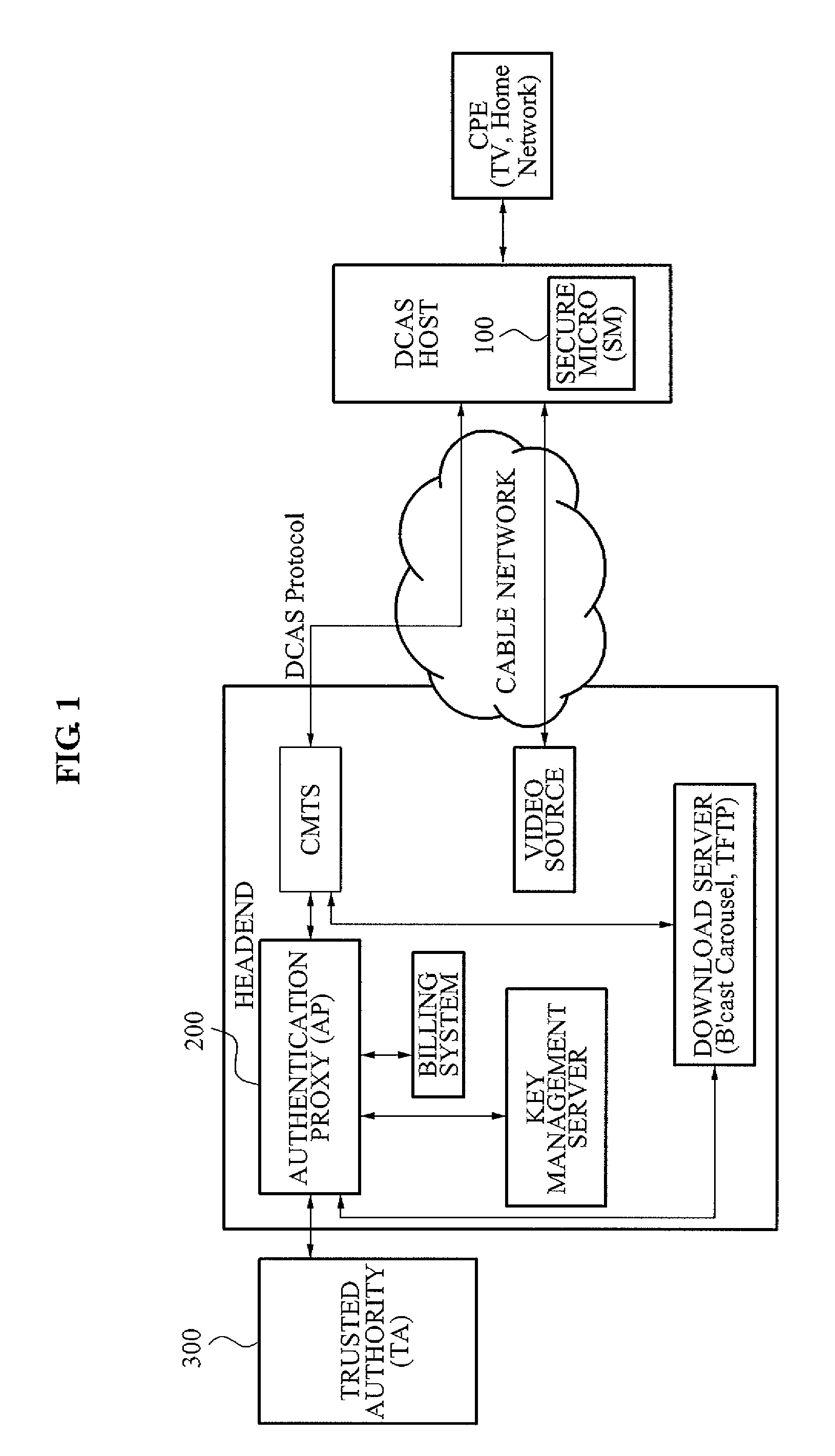
Downloadable Conditional Access System or DCAS was a proposal advanced by CableLabs for secure software download of a specific Conditional Access client (computer program) which controls digital rights management (DRM) into an OCAP-compliant host consumer media device. The National Cable & Telecommunications Association (NCTA) proposed that DCAS be used as a substitute for physical CableCARDs, a standard also created by CableLabs for which products began appearing in August 2004 as part of industry compliance to the FCC mandate, which in turn is pursuant to the Telecommunications Act of 1996. DCAS is growing in popularity as a less expensive alternative for CableCARD, with major North American operator deployments from Cablevision and Charter. DCAS deployments can be expected to grow in the coming years, thanks to favorable regulatory view from the STELA Reauthorization Act of 2014 and FCC appointing a Downloadable Security Technical Advisory Committee, and wider support for key ladder (K-LAD) functionality from system-on-chip (SoC) vendors and set-top box manufacturers.
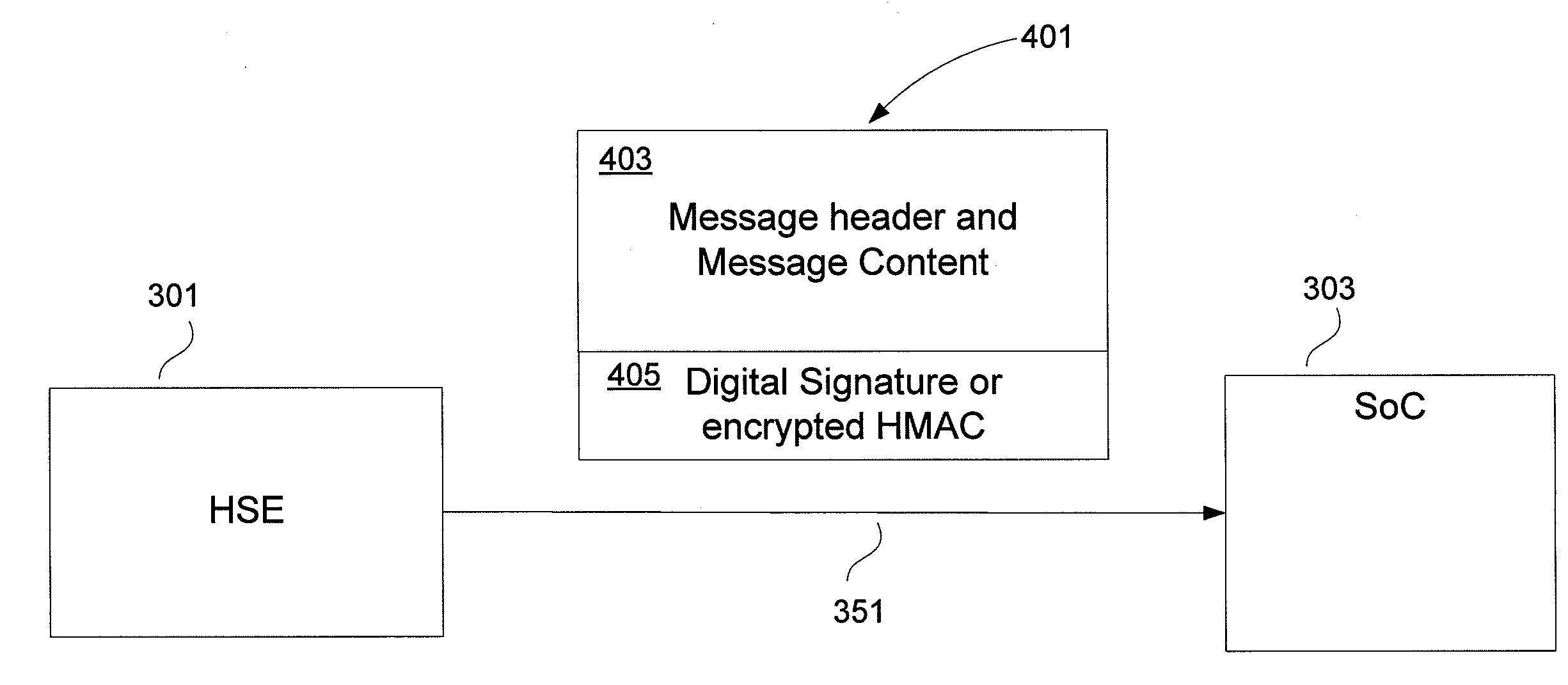
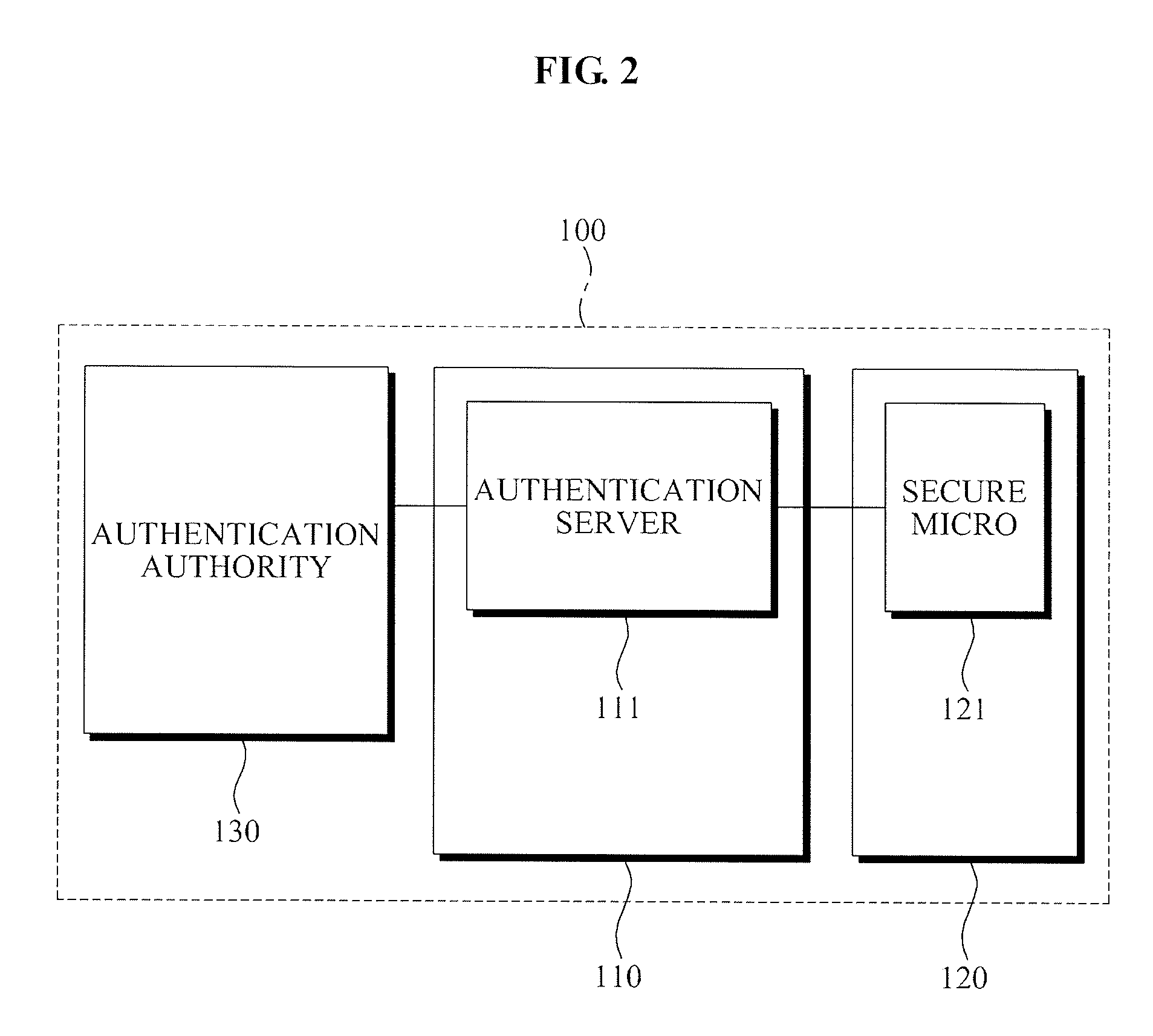
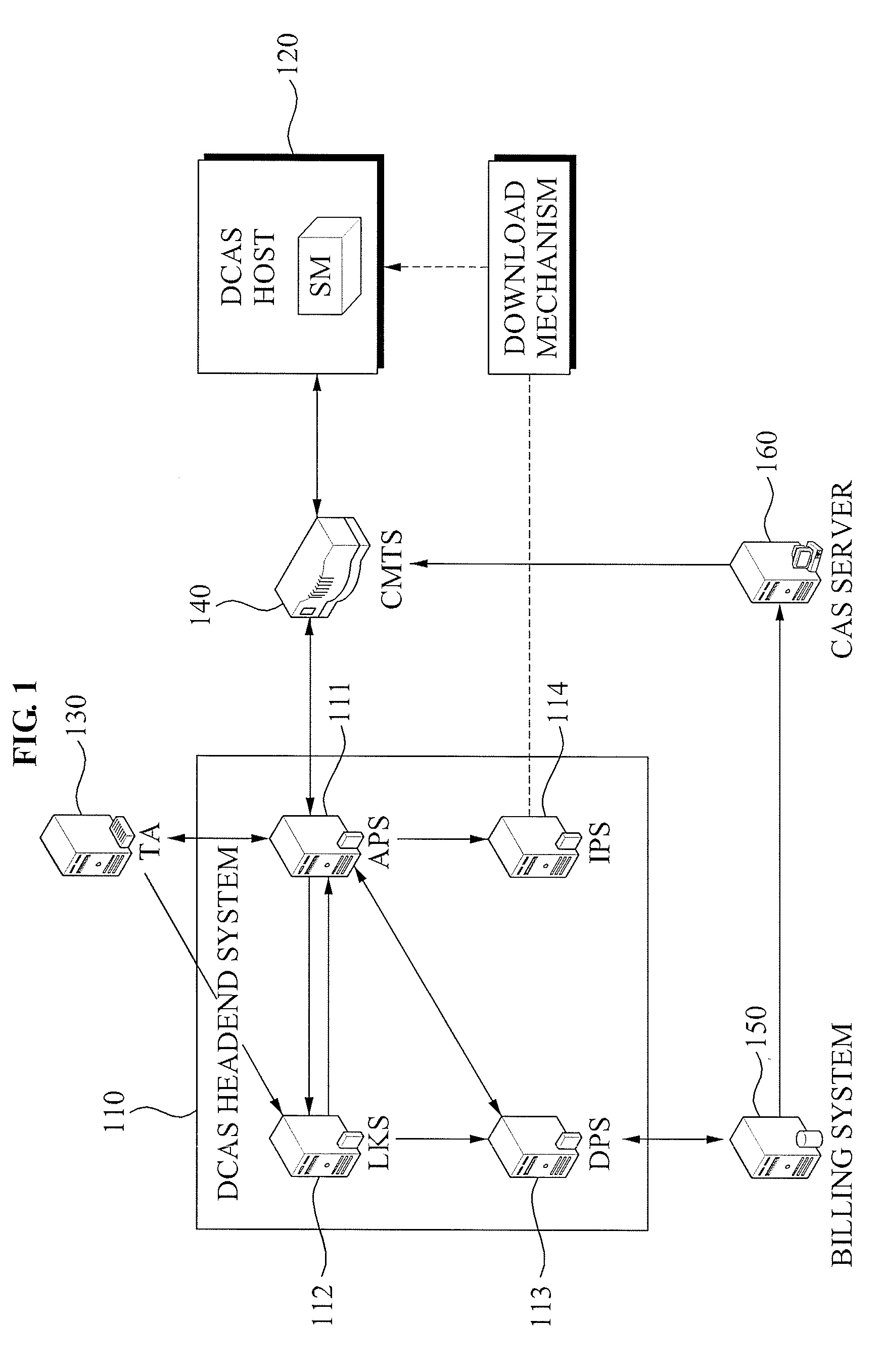
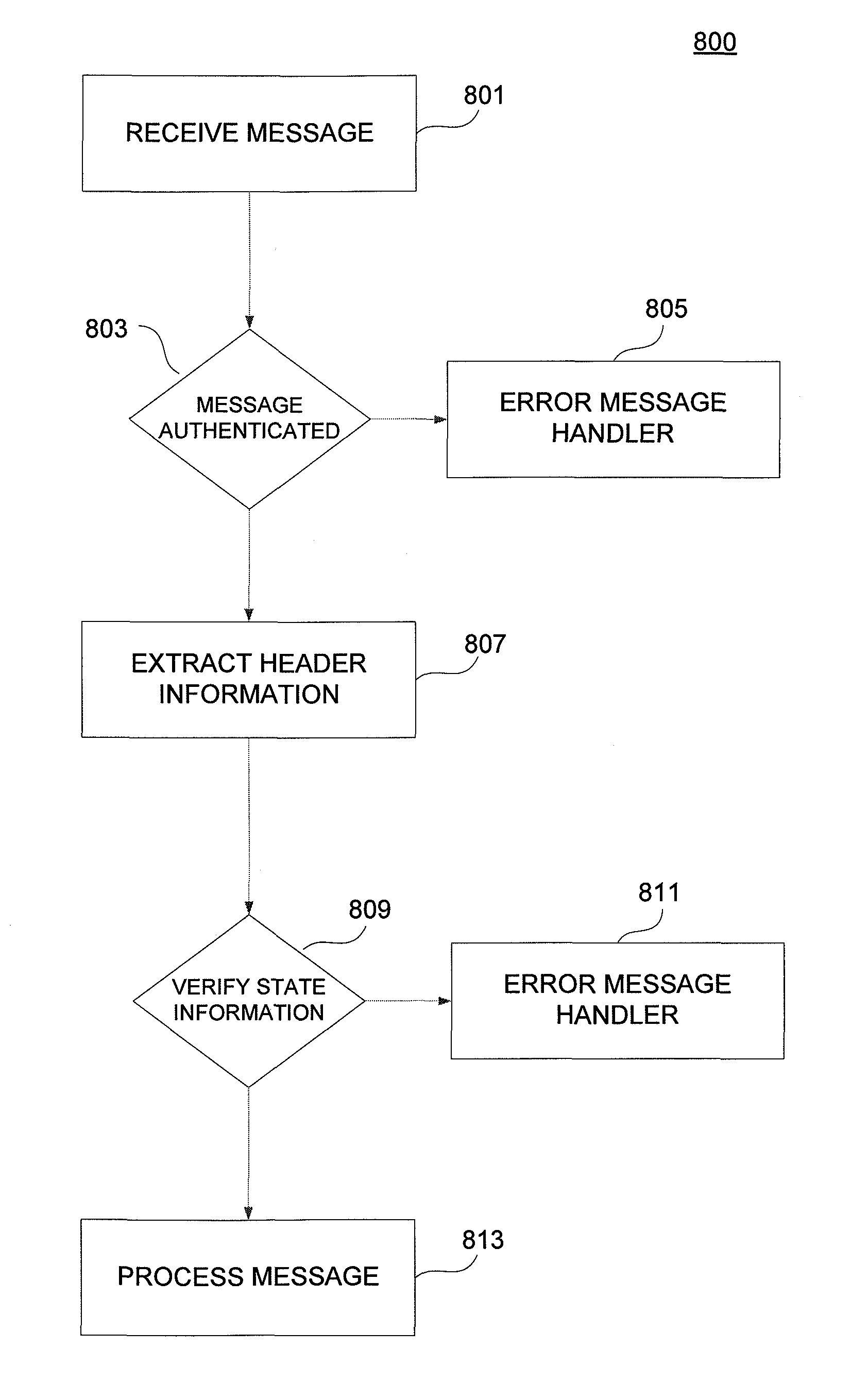
Authenticated Communication Between Security Devices
ActiveUS20100217985A1User identity/authority verificationTelevision systemsConditional access systemsDigital signature
Apparatuses, computer readable media, and methods establishing and maintaining trust between security devices for distributing media content are provided. Two security devices bind to establish an initial trust so that security information can be exchanged. Subsequently, trust is refreshed to verify the source of a message is valid. In an embodiment, the security devices may comprise a security processor and a system on a chip (SoC) in a downloadable conditional access system. Trust may be refreshed by a security device inserting authentication information in a message to another security device, where authentication information may assume different forms, including a digital signature (asymmetric key) or a hash message authentication code (HMAC). Trust may also be refreshed by extracting header information from the message, determining state information from at least one parameter contained in the header information, and acting on message content only when the state information is valid.
Owner:COMCAST CABLE COMM LLC
Mutual authentication apparatus and method in downloadable conditional access system
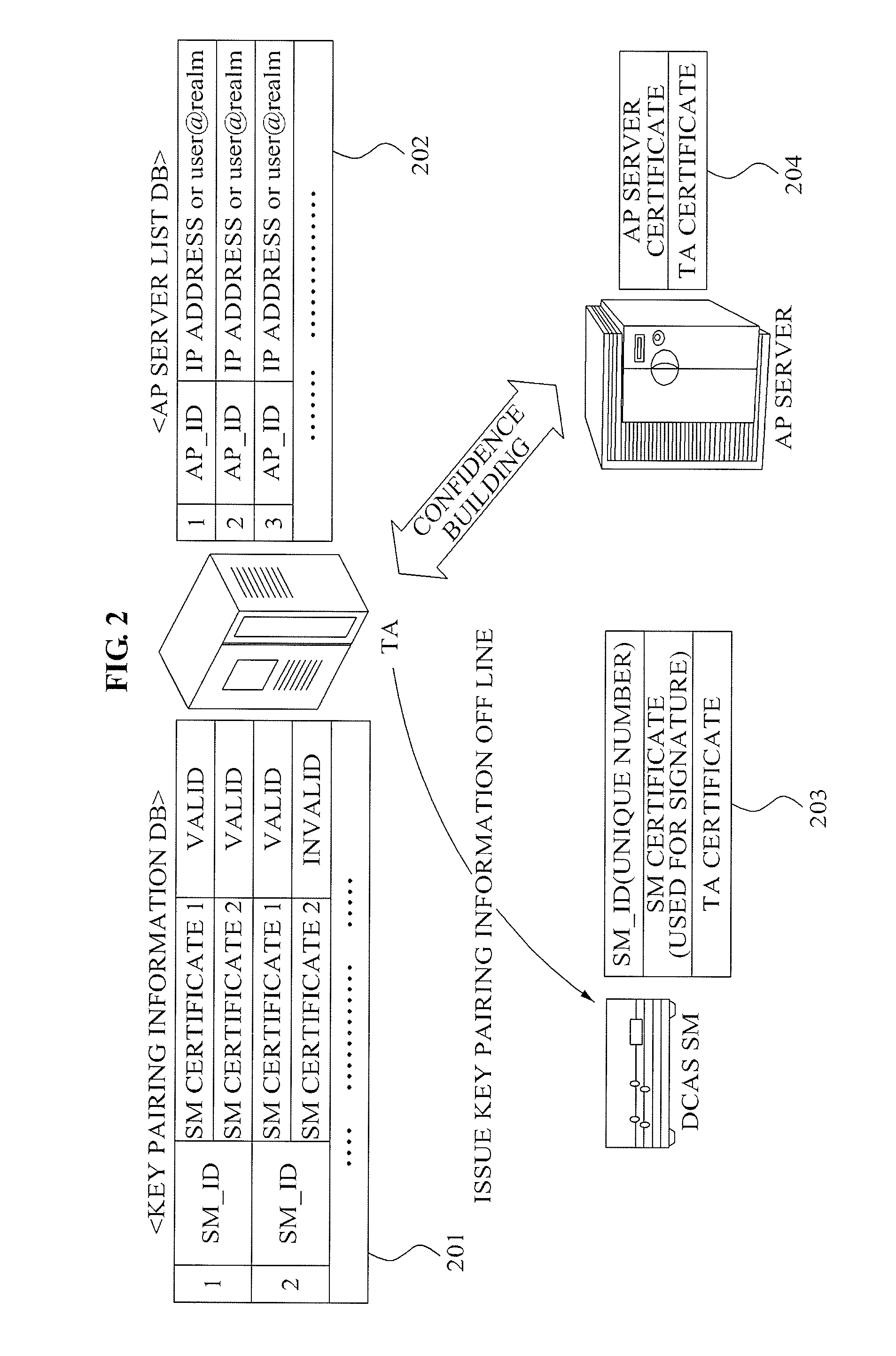
InactiveUS20100161966A1Key distribution for secure communicationUser identity/authority verificationTrusted authorityDownloadable Conditional Access System
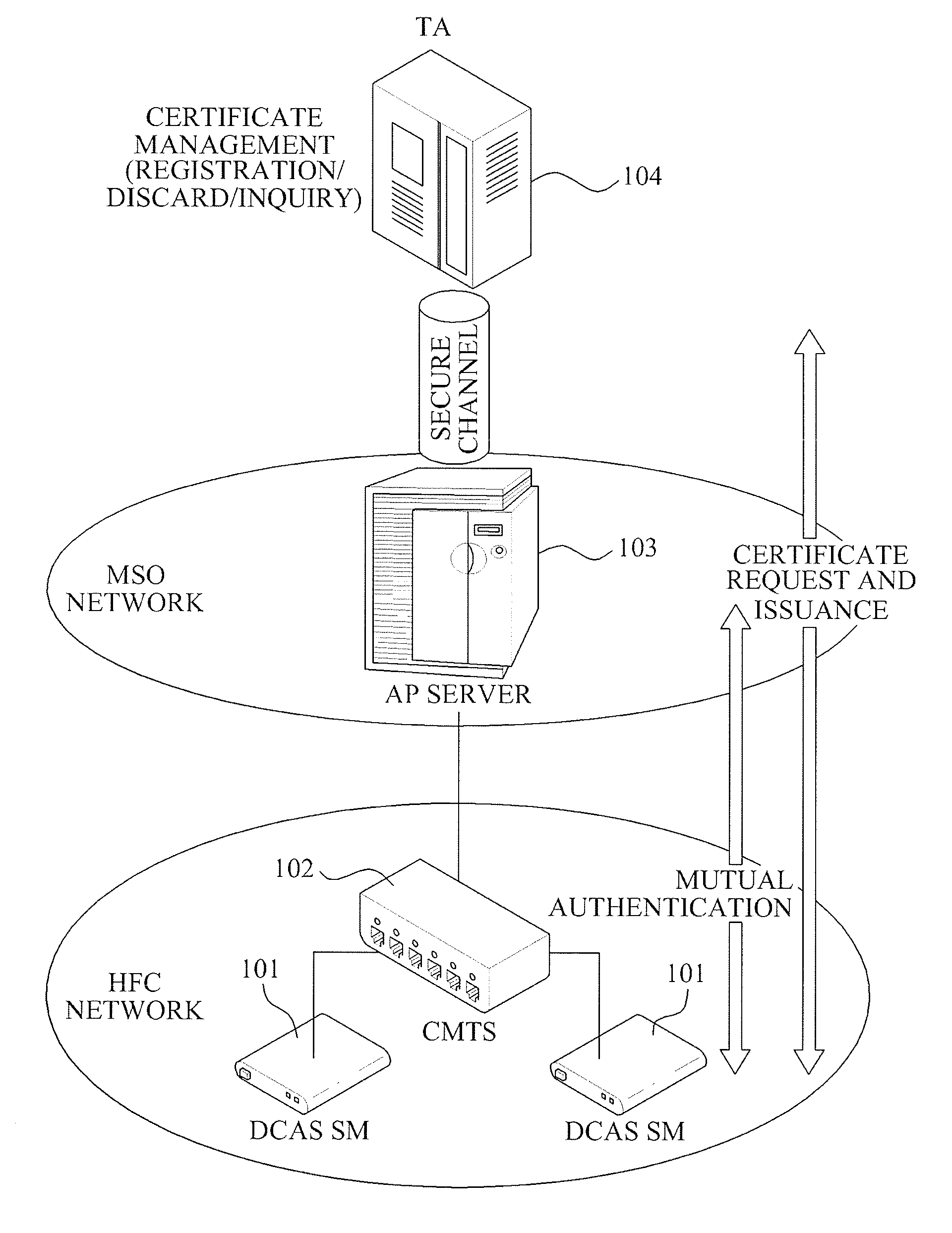
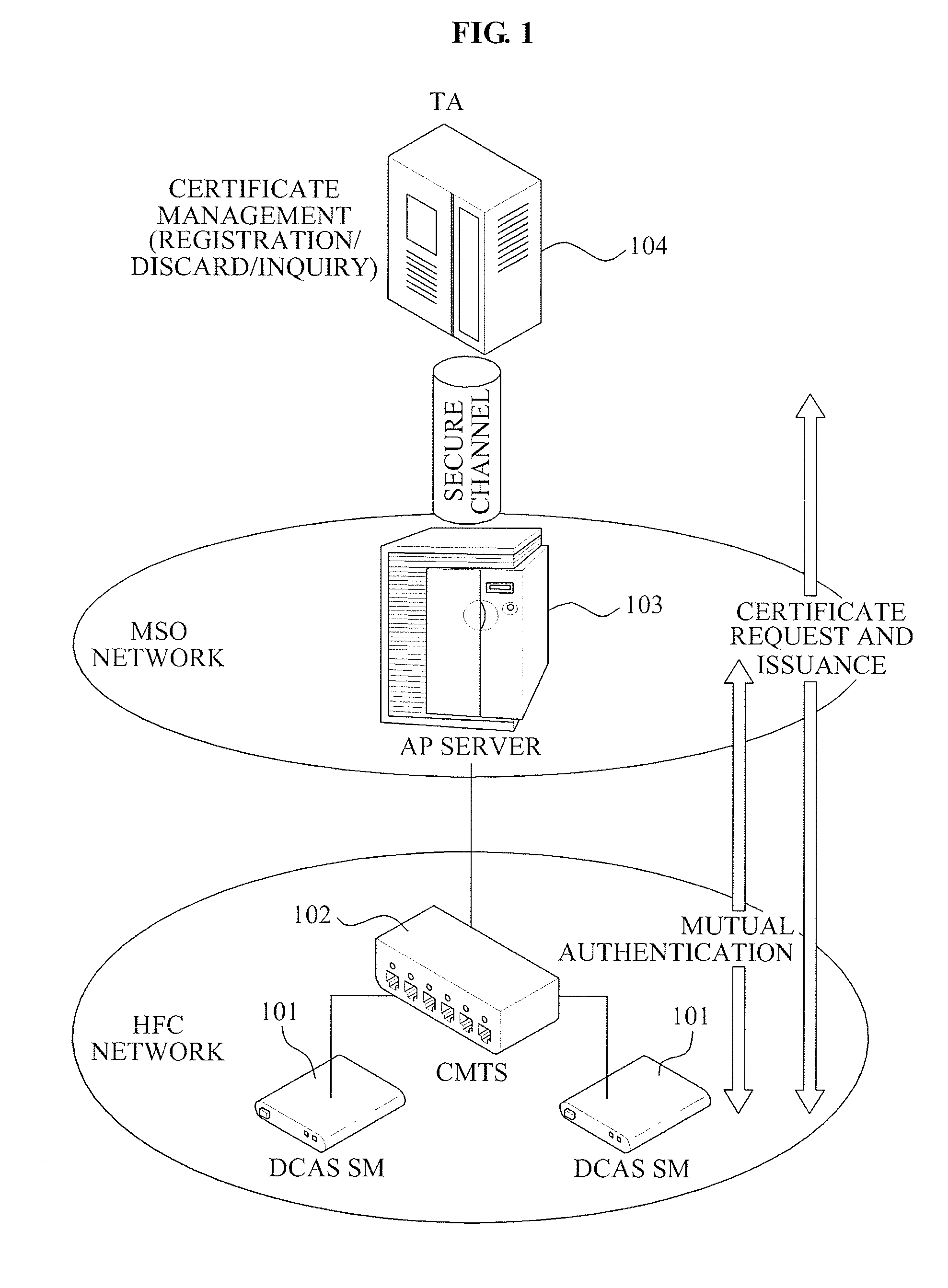
A mutual authentication method in a Downloadable Conditional Access System (DCAS) is provided. The mutual authentication method may receive authentication-related information about authentication between an authentication unit and a security module (SM) from a Trusted Authority (TA), generate an authentication session key using the authentication-related information, transmit the authentication session key by the authentication unit to the SM through a Cable Modem Termination System (CMTS), and control a Conditional Access System (CAS) software to be downloaded to the SM from the authentication unit, when the authentication is completed by the authentication session key.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus of mutual authentication and key distribution for downloadable conditional access system in digital cable broadcasting network
InactiveUS20090144541A1Increase costIncrease in costUser identity/authority verificationProgram loading/initiatingDownloadable Conditional Access SystemConditional access systems
A method and apparatus of X.509 certificate-based mutual authentication and key distribution for a Downloadable Conditional Access System (DCAS) in a digital cable broadcasting network is provided for composing a software-based secure DCAS in various Conditional Access Systems (CASs) based on an embodiment form of Conditional Access (CA) application for CA of digital cable broadcasting.
Owner:ELECTRONICS & TELECOMM RES INST
Multi-stream encryption method and apparatus, and host device for multi-channel recording
InactiveUS20100158480A1Television system detailsColor television signals processingComputer hardwareDownloadable Conditional Access System
A multi-stream encryption apparatus and method, and a host device for multi-channel recording of a plurality of fee-based broadcasting services in a Downloadable Conditional Access System (DCAS) are provided.
Owner:ELECTRONICS & TELECOMM RES INST
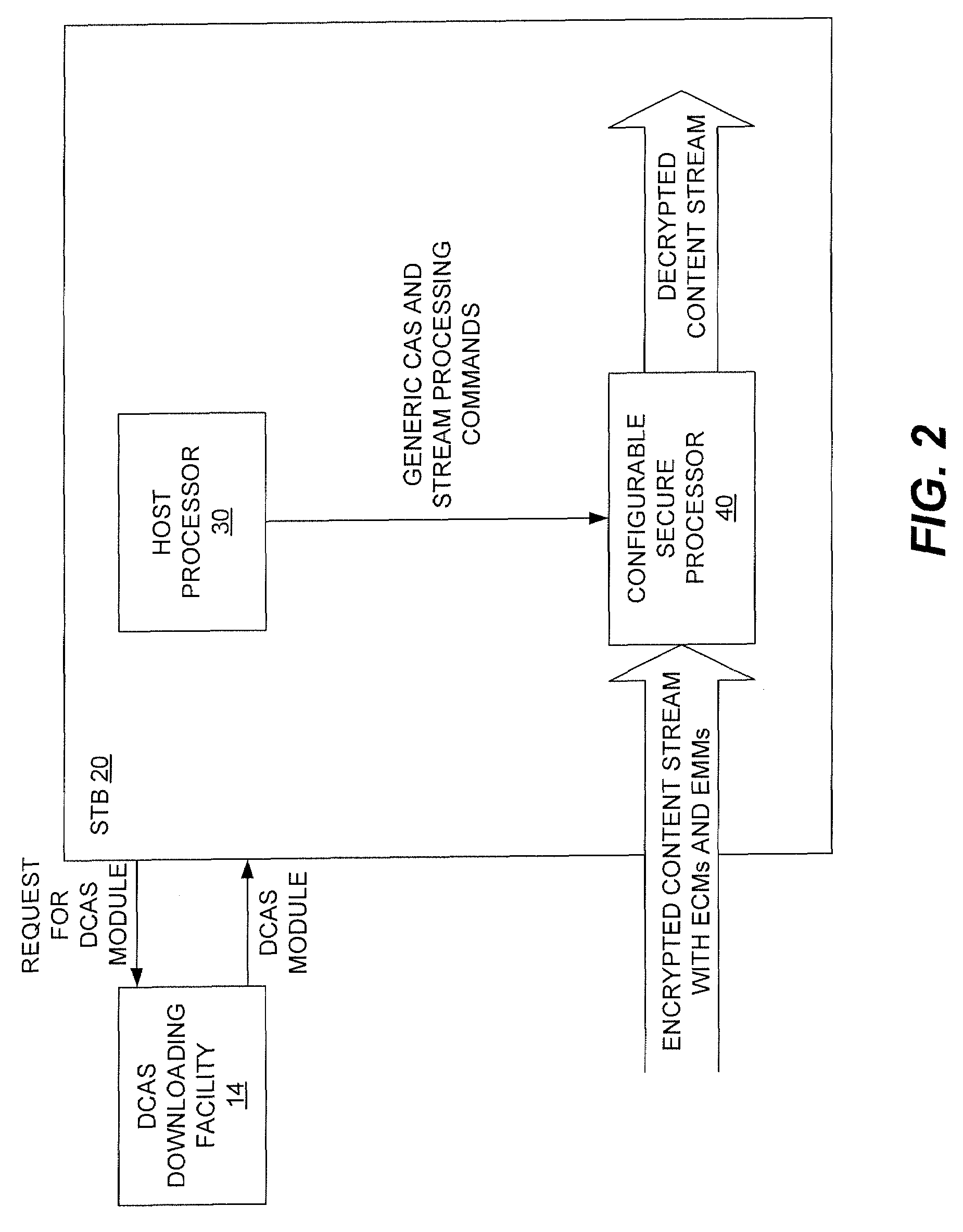
Method and Apparatus For Use in a Downloadable Conditional Access System
ActiveUS20080313463A1Key distribution for secure communicationUser identity/authority verificationDownloadable Conditional Access SystemSoftware modules
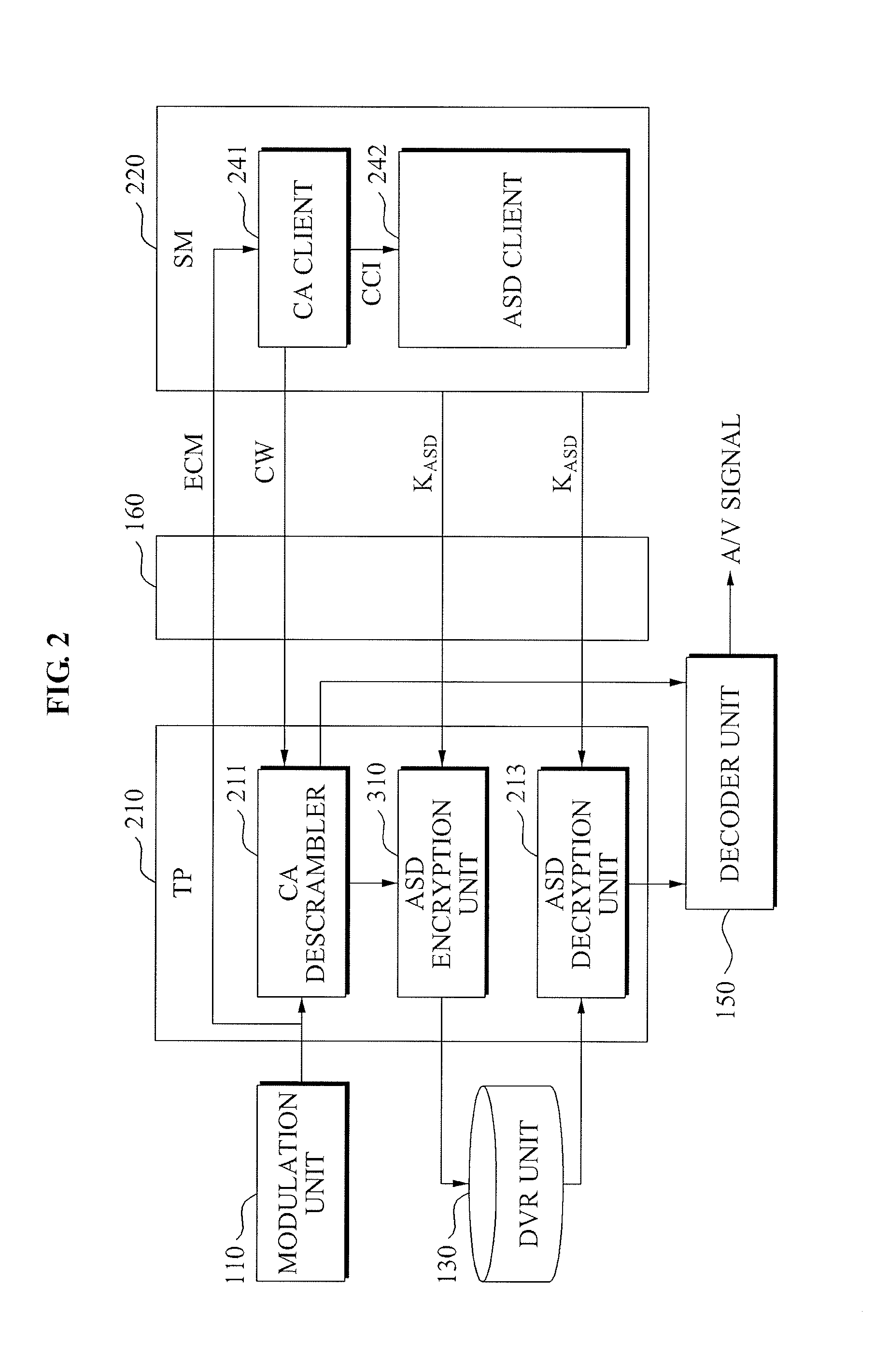
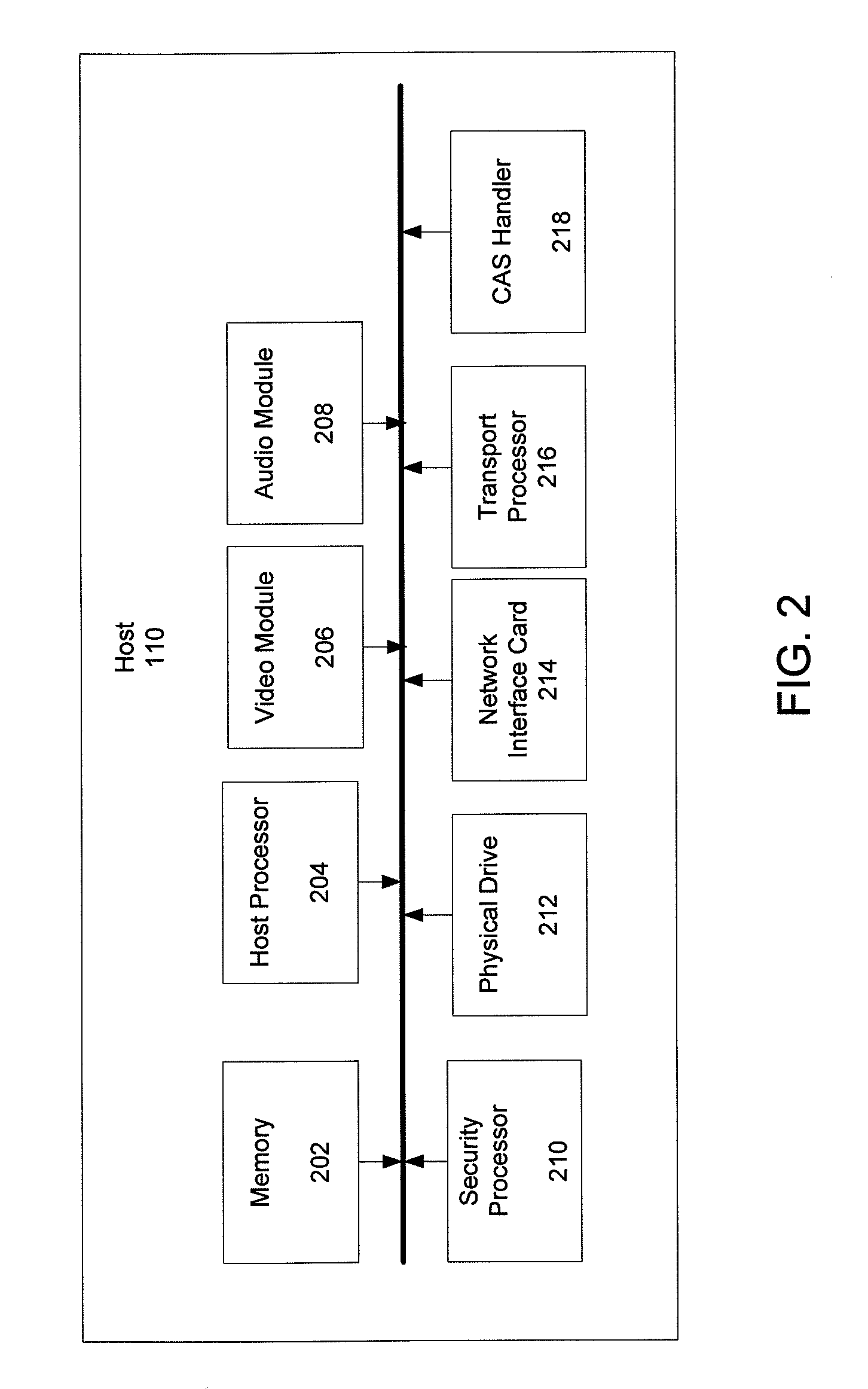
In a downloadable conditional access system (DCAS), preferably all DCAS-specific code is implemented in a configurable secure (CS) processor that is in communication with the host processor. Preferably, no DCAS-specific code is executed in the host processor. The host processor delivers commands to the CS processor, which the CS processor performs to configure itself in accordance with the particular DCAS encryption scheme used by the DCAS. Once configured, the CS processor executes a DCAS software module that has been downloaded to the CS processor, which looks for the corresponding EMMs and ECMs, processes them to obtain the CW, and then uses the CW to decrypt the content stream.
Owner:GENERAL INSTR CORP
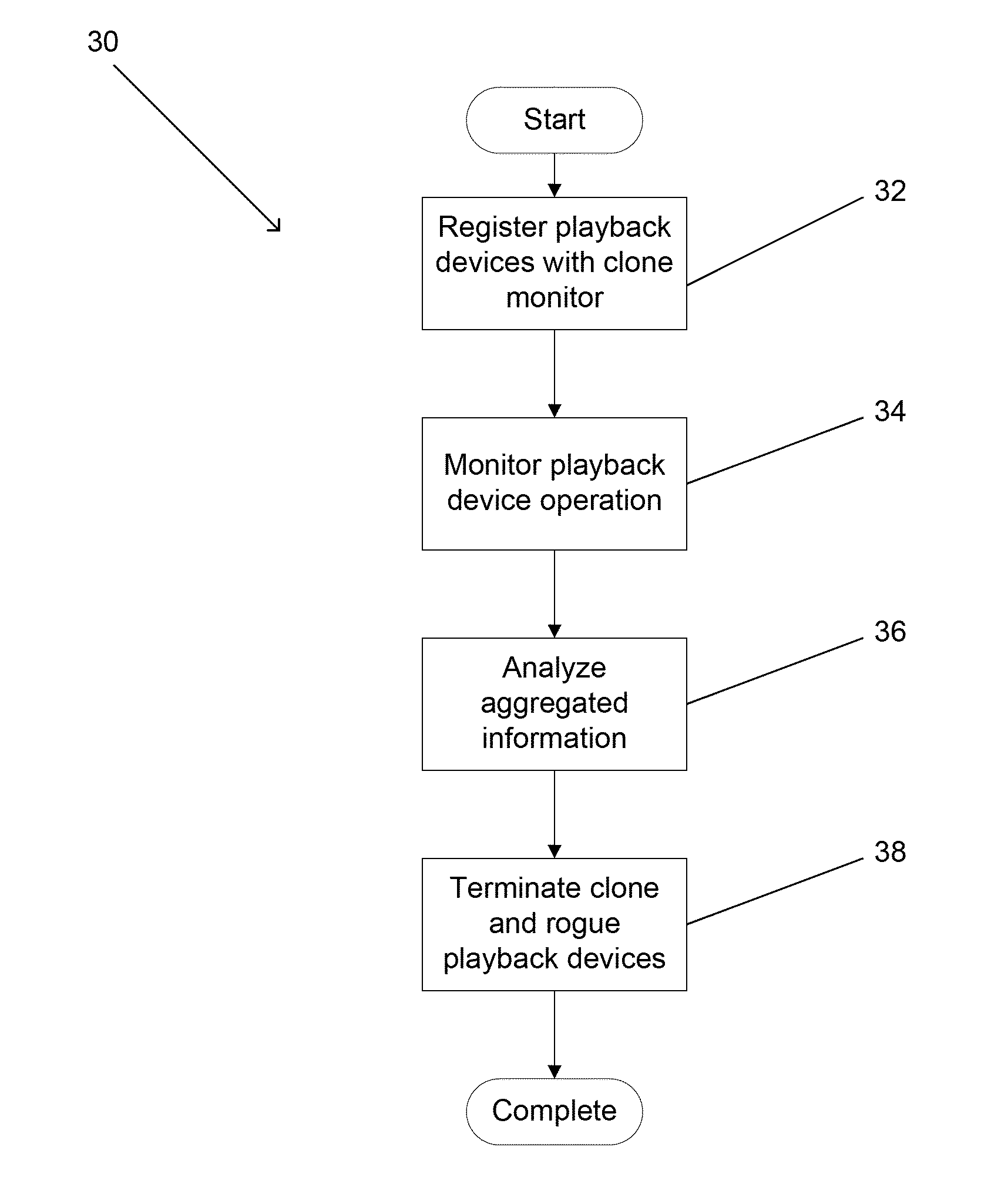
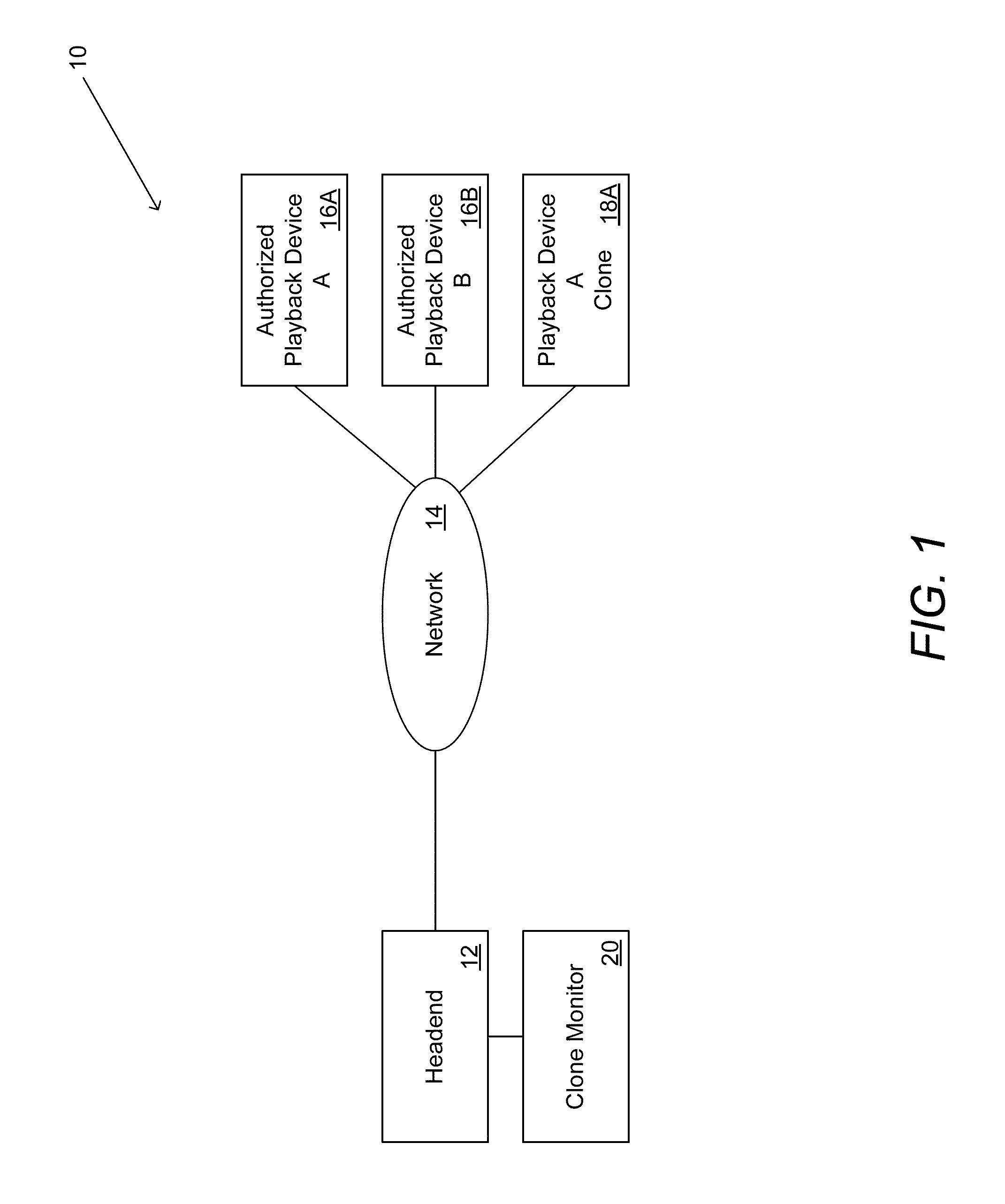
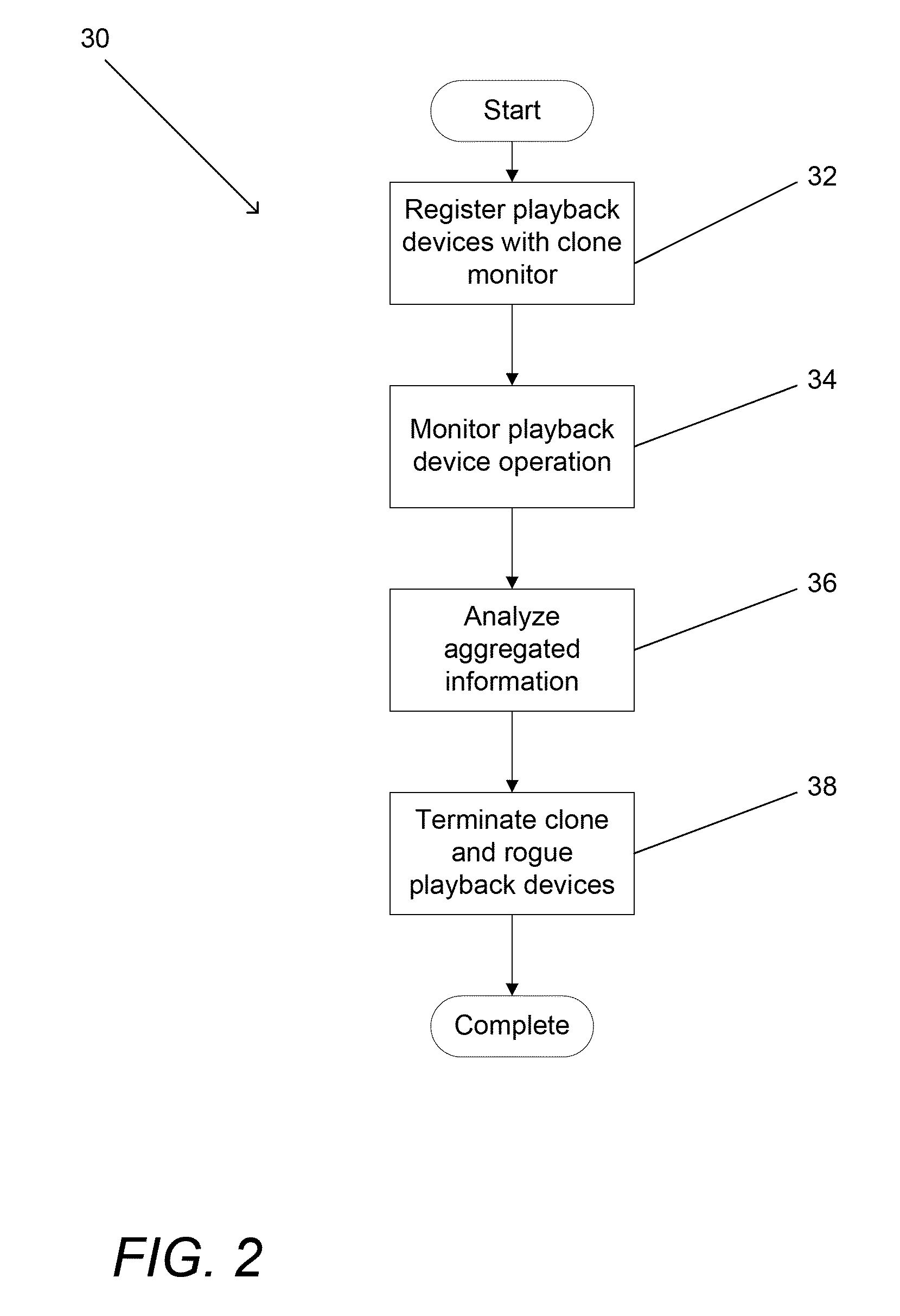
Systems and methods for detecting clone playback devices
ActiveUS20110030065A1Digital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemDownloadable Conditional Access System
Systems and methods are described for aggregating information obtained from messages between playback devices and content protection systems, including but not limited to conditional access systems, downloadable conditional access systems, and digital rights management systems, that include a unique identifier and applying user modifiable rules to the aggregated information to identify abnormal behavior associated with the unique identifier including but not limited to one or more clone playback devices utilizing the unique identifier or a rogue playback device utilizing a unique identifier. One embodiment includes a plurality of playback devices connected to a headend via a network, where the headend includes at least one content protection system, and a clone monitor configured to register playback devices based upon a unique identification supplied by each playback device, when communicating with the at least one content protection system. In addition, the clone monitor is configured to aggregate information associated with each playback device over time, where the information is obtained from messages that are transmitted between the playback device and the headend and that include a unique identifier, and the clone monitor is configured to apply rules to the aggregated information to identify at least one pattern of abnormal behavior in the aggregated information associated with a specific unique identifier.
Owner:VERIMATRIX INC
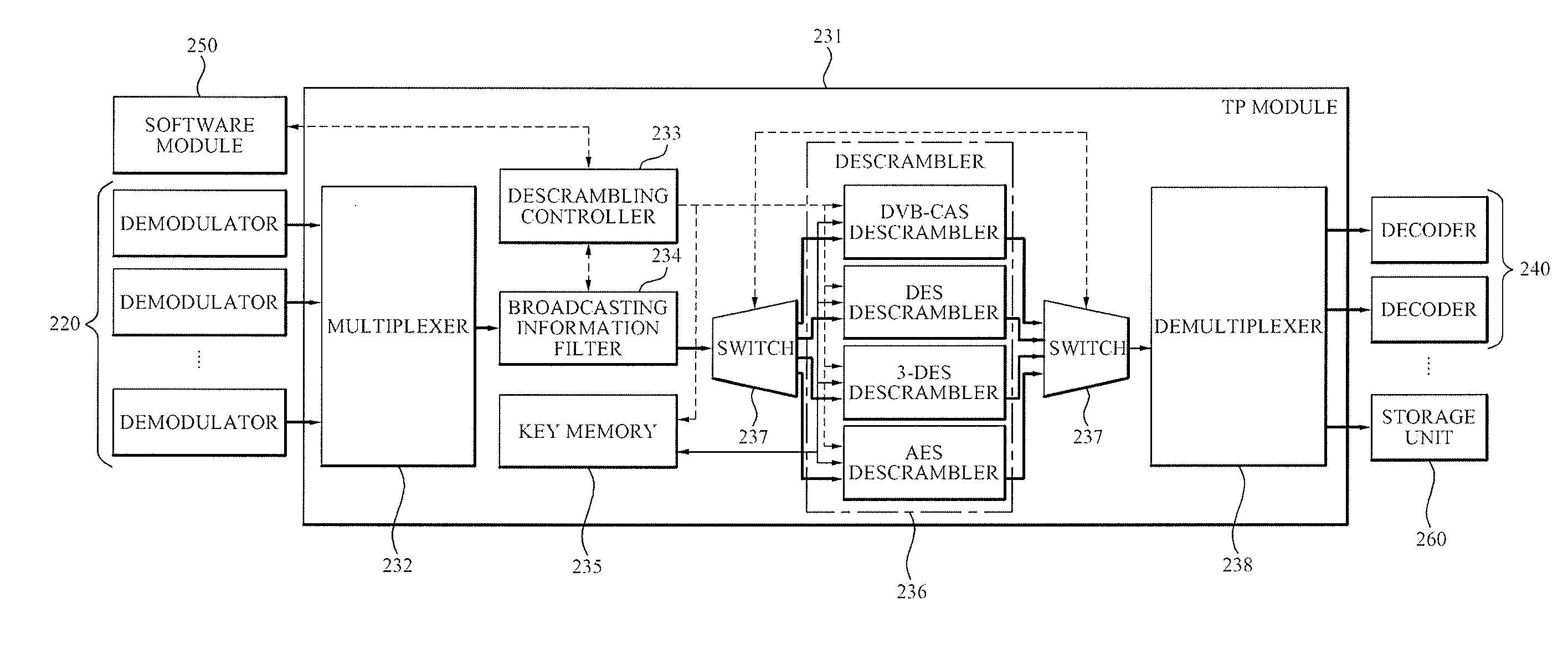
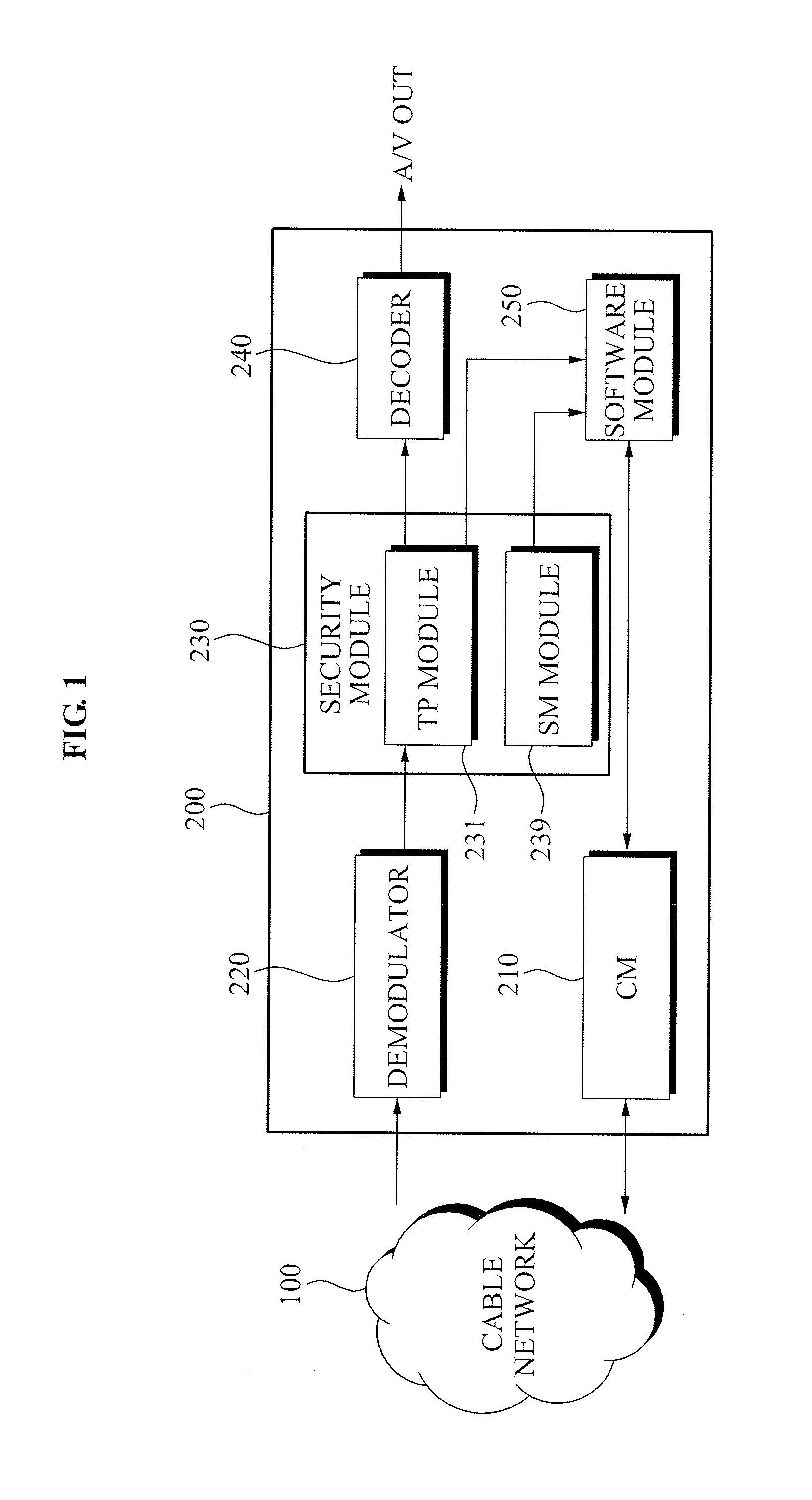
Method and apparatus for multi-stream processing of set top box in downloadable conditional access system
InactiveUS20090144766A1Two-way working systemsSelective content distributionConditional access systemsDownloadable Conditional Access System
A multi-stream processing apparatus of a set top box in a Downloadable Conditional Access System (DCAS), the apparatus including: a cable modem (CM) to allocate at least one communication channel with respect to a headend of a broadcasting company connected with a cable network; a demodulator to receive broadcasting information from the cable network using the at least one allocated communication channel and to demodulate the received broadcasting information; a security module to descramble the demodulated broadcasting information using an application downloaded from the headend of the broadcasting company; a decoder to restore the descrambled broadcasting information into an Audio / Video (A / V) signal and to transmit the A / V signal to a connected apparatus; and a software module to control the CM, the security module, the demodulator, and the decoder, and to perform routing of information.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for mutual authentication in downloadable conditional access system
ActiveUS20090150672A1Cost of operationFast system renewalDigital data processing detailsUser identity/authority verificationDownloadable Conditional Access SystemConditional access systems
Disclosed is a mutual authentication method and apparatus in a CAS including a headend system and DCAS host. In particular, example embodiments relate to a mutual authentication method and apparatus in DCAS, wherein the mutual authentication is performed between an authentication server of the headend system and an SM of a DCAS host, and then CAS software is downloaded to the SM. According to the example embodiments, there is provided a mutual authentication protocol between the authentication server of the headend and the SM of the DCAS host in a cable network, and also provided a mutual authentication method and apparatus in the DCAS where a substantial authentication based on a hardware, such as a smart card or a cable card, is not needed.
Owner:ELECTRONICS & TELECOMM RES INST
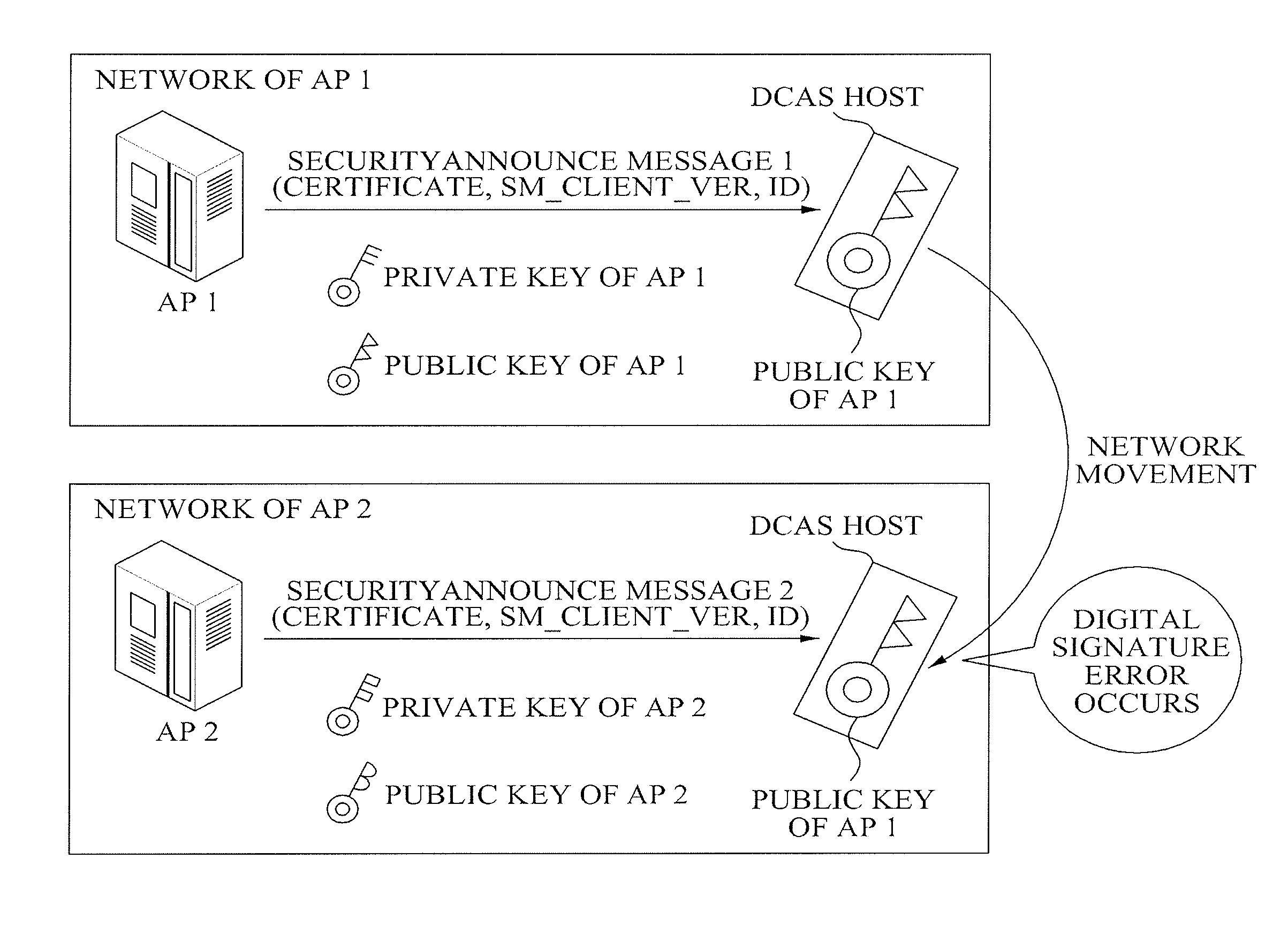
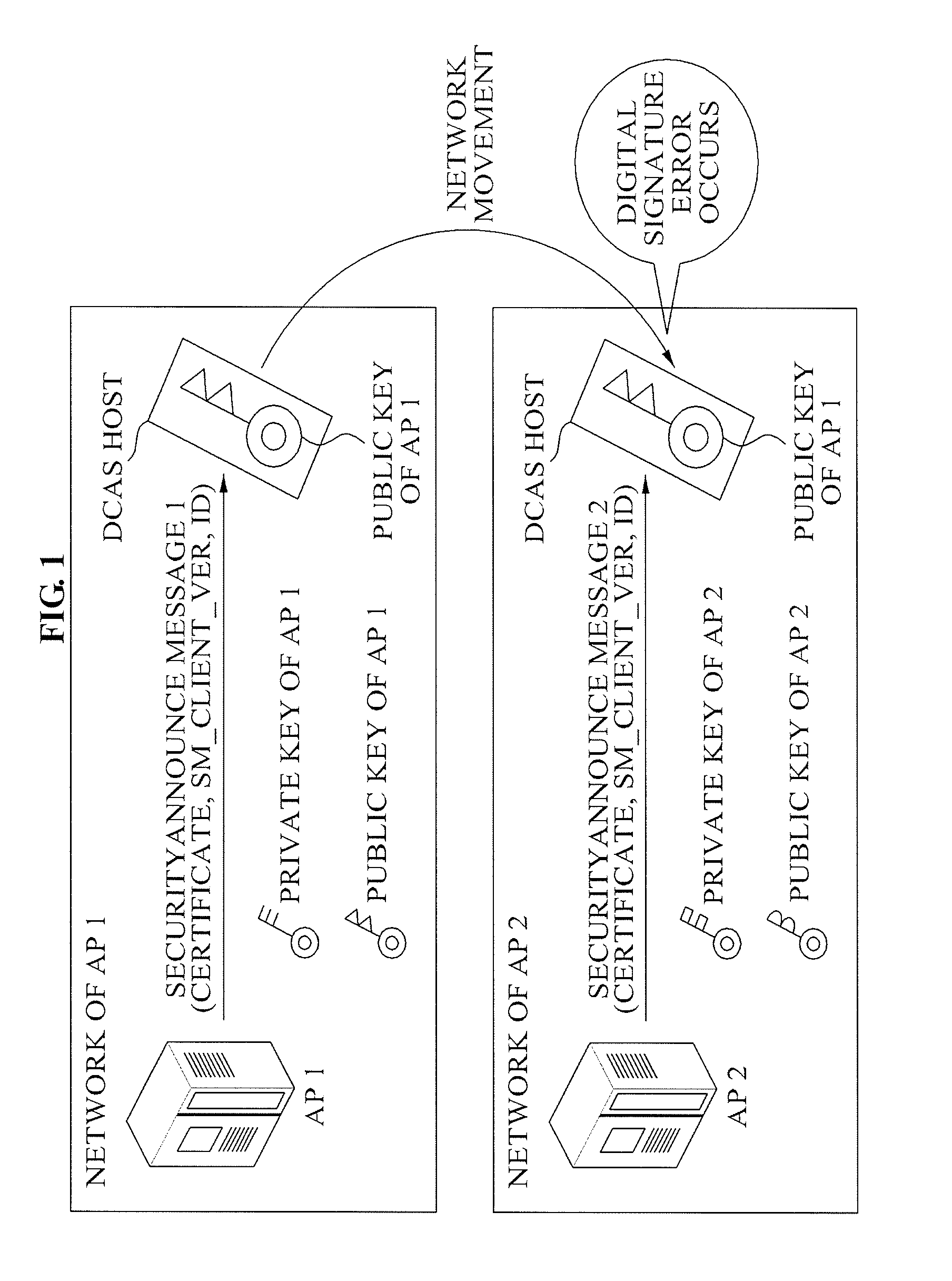
Method and apparatus for detecting movement of downloadable conditional access system host in dcas network
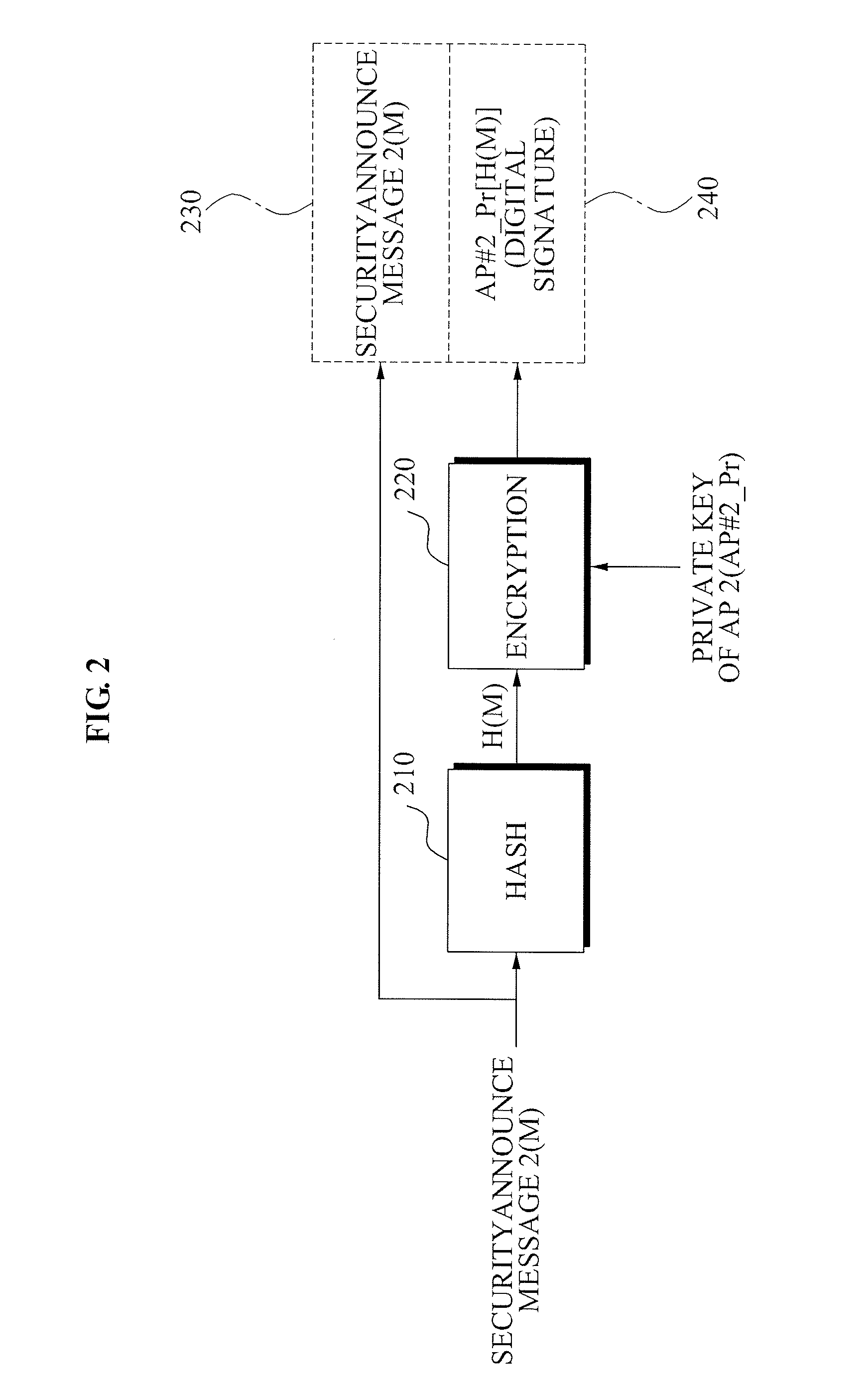
InactiveUS20090138720A1Efficient updateEncryption apparatus with shift registers/memoriesPublic key for secure communicationDigital signatureDownloadable Conditional Access System
A method of operating a Secure Micro (SM) of a host in a Conditional Access (CA) system is provided. The method includes: receiving, by the SM, a SecurityAnnounce message including a certificate of an AP server connected with a host; determining, by the SM, whether a public key stored in a memory in advance exists, and setting a flag as a first state when the public key stored in advance exists; verifying, by the SM, a digital signature with respect to the SecurityAnnounce message using the public key stored in advance; and acquiring, by the SM, another public key of the AP server by parsing the certificate and setting the flag as a second state based on whether the flag corresponds to the first state when the SM is unable to verify the digital signature.
Owner:ELECTRONICS & TELECOMM RES INST
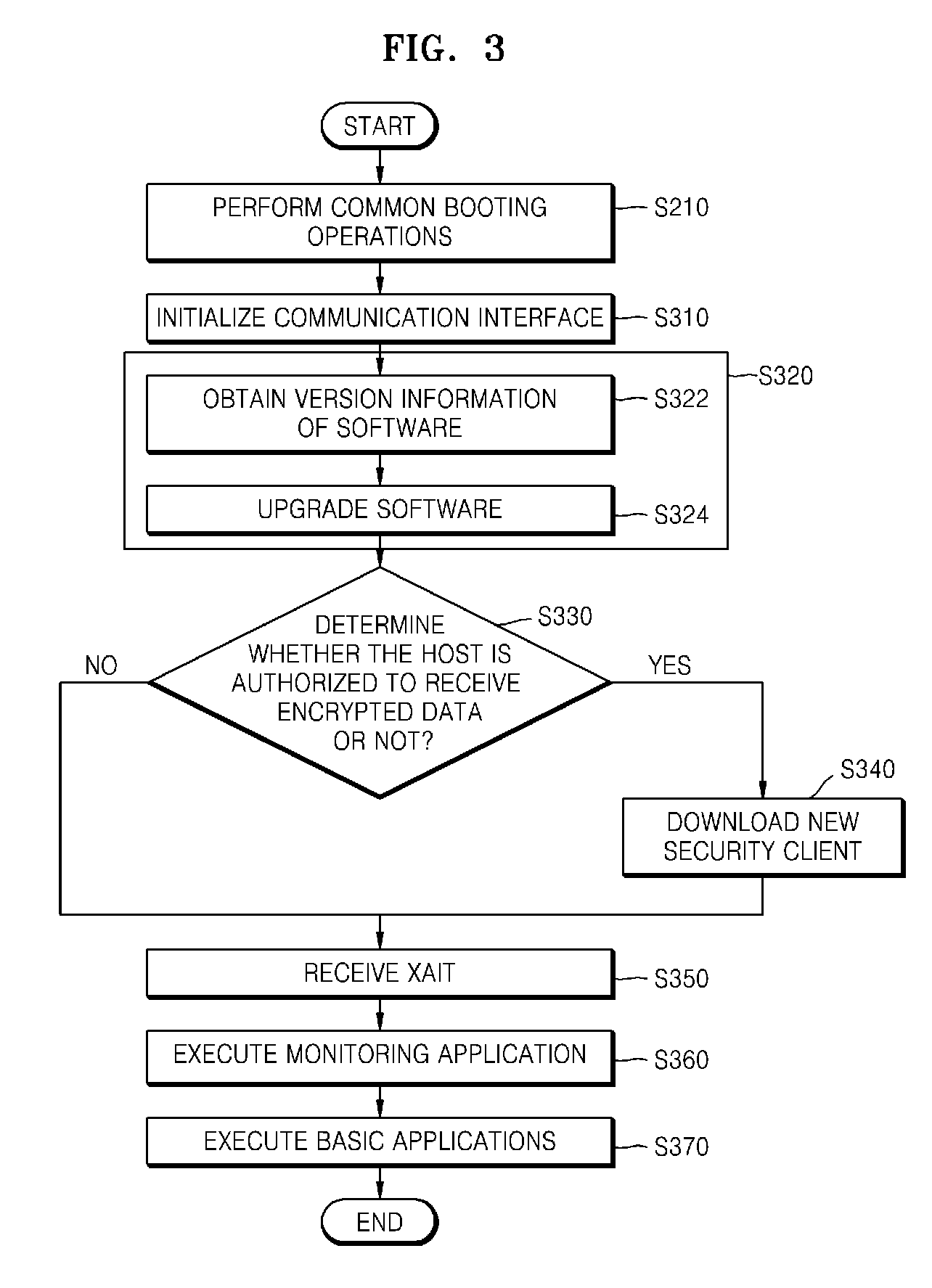
Method and apparatus for booting host
ActiveUS20090125710A1Efficient startDigital data processing detailsMultiple digital computer combinationsConditional access systemsDownloadable Conditional Access System
Provided are a method and a device for booting a host embodying a downloadable conditional access system (DCAS), wherein one of a plurality of pre-determined booting modes is decided as a booting mode of the host based on first information indicating whether a host can communicate with a broadcasting service provider and second information indicating whether a software-based security client providing information required for decrypting broadcasting data is installed to a hardware-based security module connected to the host, and the host is booted in the decided booting mode.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for mutual authentication in downloadable conditional access system
ActiveUS8621218B2Cost of operationFast system renewalDigital data processing detailsUser identity/authority verificationDownloadable Conditional Access SystemAuthentication server
Disclosed is a mutual authentication method and apparatus in a CAS including a headend system and DCAS host. In particular, example embodiments relate to a mutual authentication method and apparatus in DCAS, wherein the mutual authentication is performed between an authentication server of the headend system and an SM of a DCAS host, and then CAS software is downloaded to the SM. According to the example embodiments, there is provided a mutual authentication protocol between the authentication server of the headend and the SM of the DCAS host in a cable network, and also provided a mutual authentication method and apparatus in the DCAS where a substantial authentication based on a hardware, such as a smart card or a cable card, is not needed.
Owner:ELECTRONICS & TELECOMM RES INST
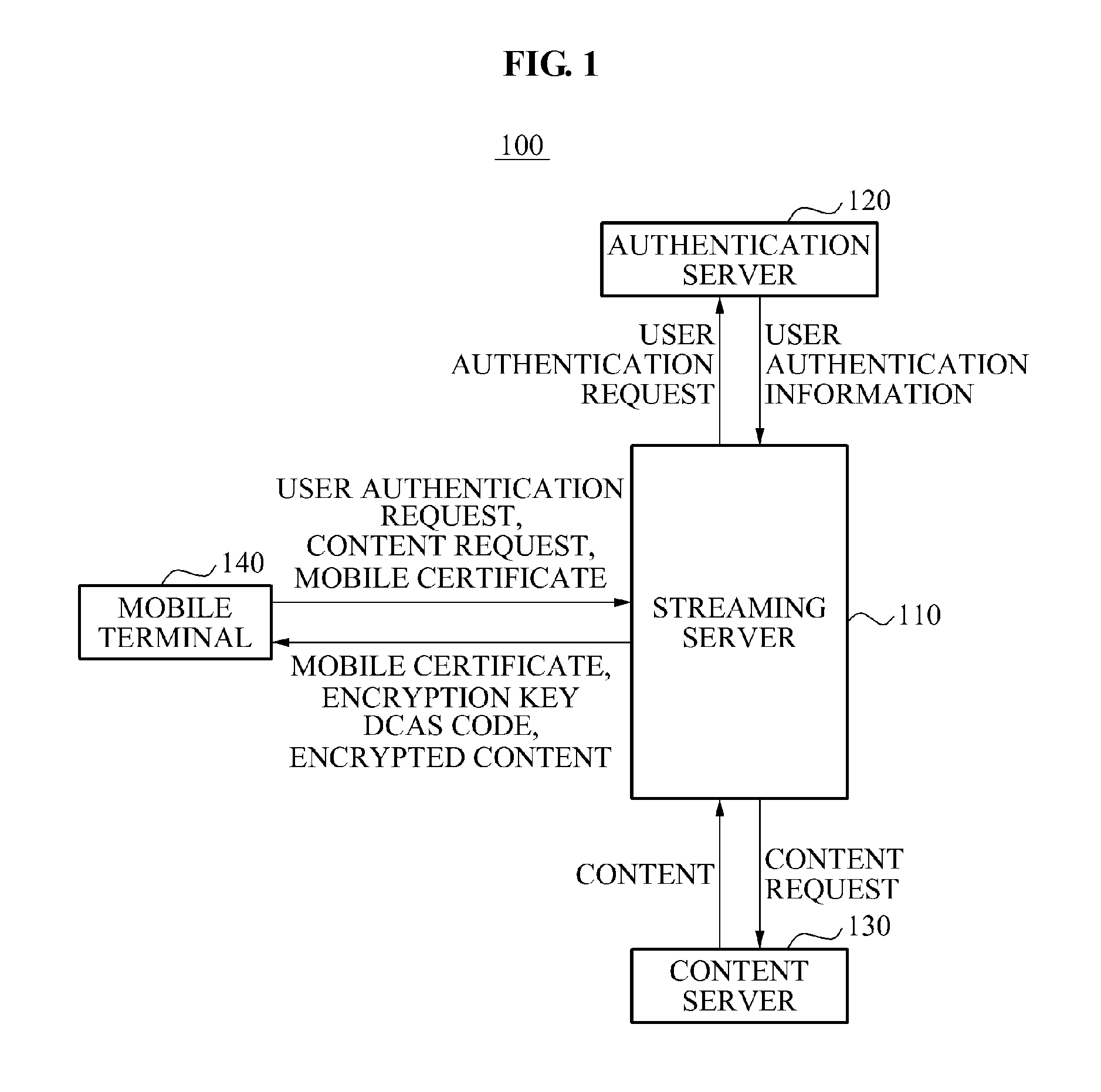
Mobile IPTV service system using downloadable conditional access system and method thereof
InactiveUS20130156187A1Key distribution for secure communicationTelevision systemsDownloadable Conditional Access SystemConditional access systems
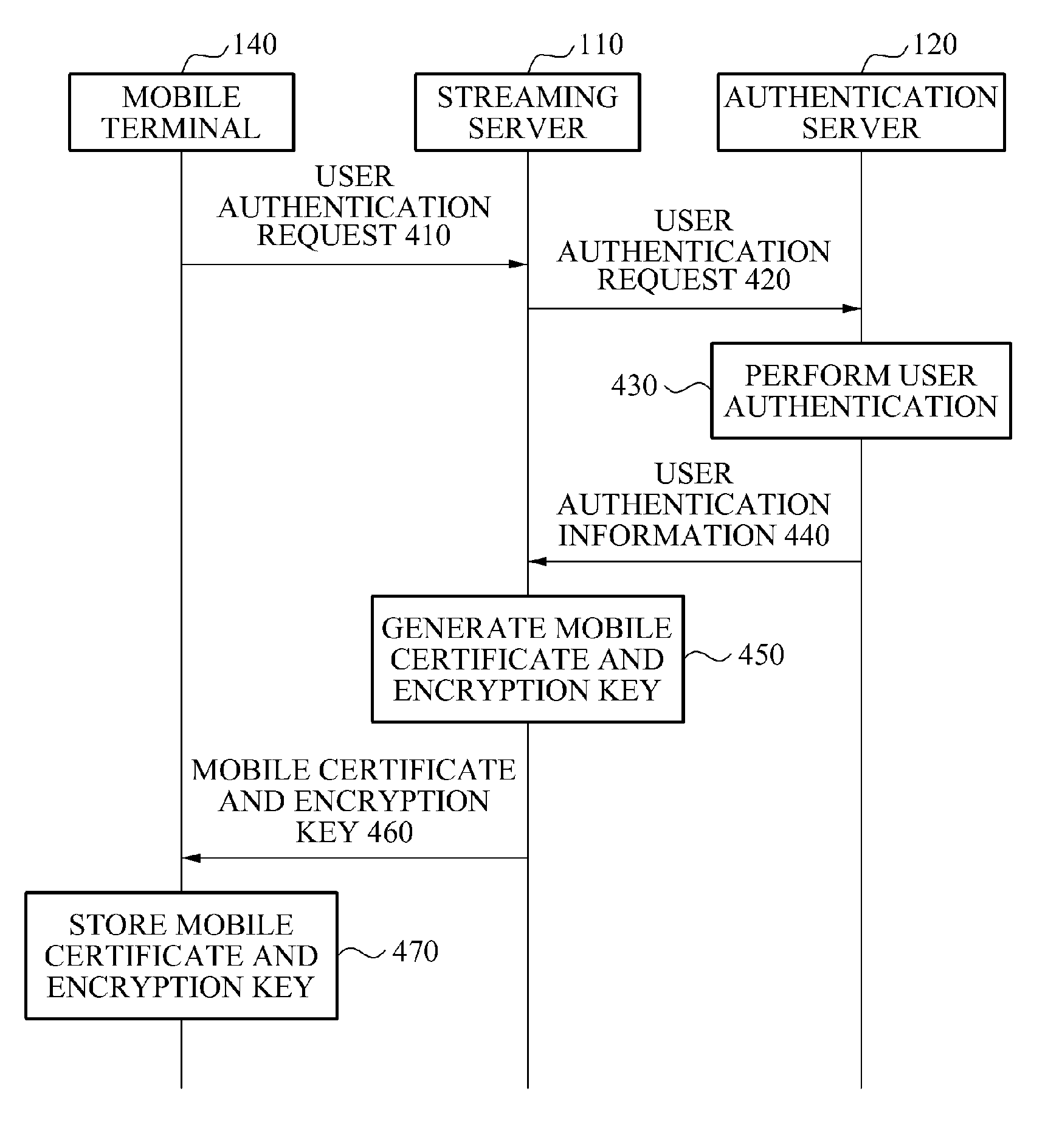
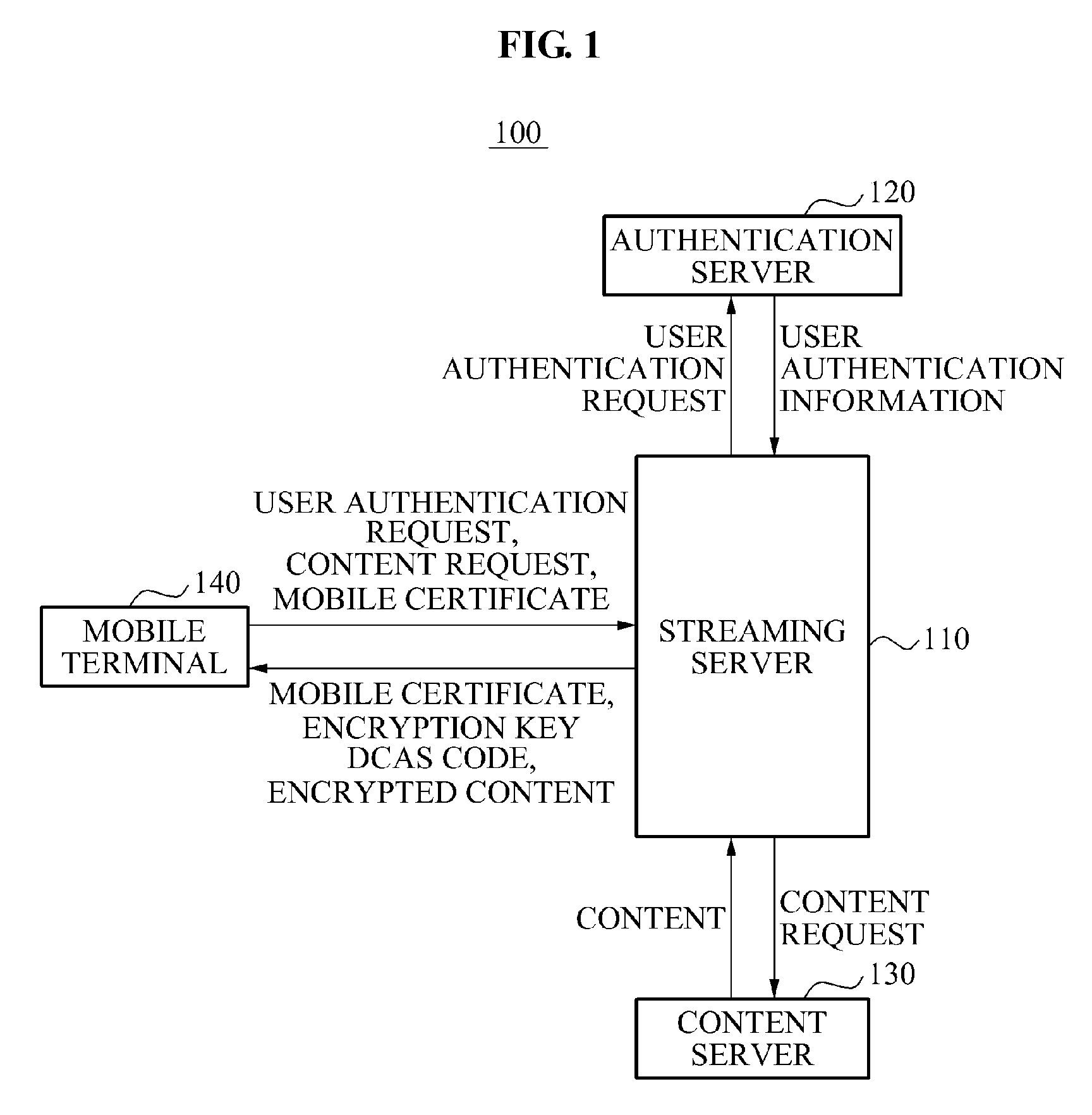
An apparatus and method associated with an Internet Protocol Television (IPTV) service in a mobile environment are provided. A streaming server may provide a mobile terminal with a mobile certificate and an encryption key. In response to a content request received from the mobile terminal, the streaming server may provide the mobile terminal with encrypted content and a Downloadable Conditional Access System (DCAS) code. The mobile terminal may decrypt the encrypted content using the encryption key and the DCAS code, and may play back the decrypted content.
Owner:INTELLECTUAL DISCOVERY CO LTD
Method and system for an architecture of dcr DTV receiver soc with embedded reprogrammable security
ActiveUS20080266464A1Television system detailsColor television detailsEmbedded securityConditional access systems
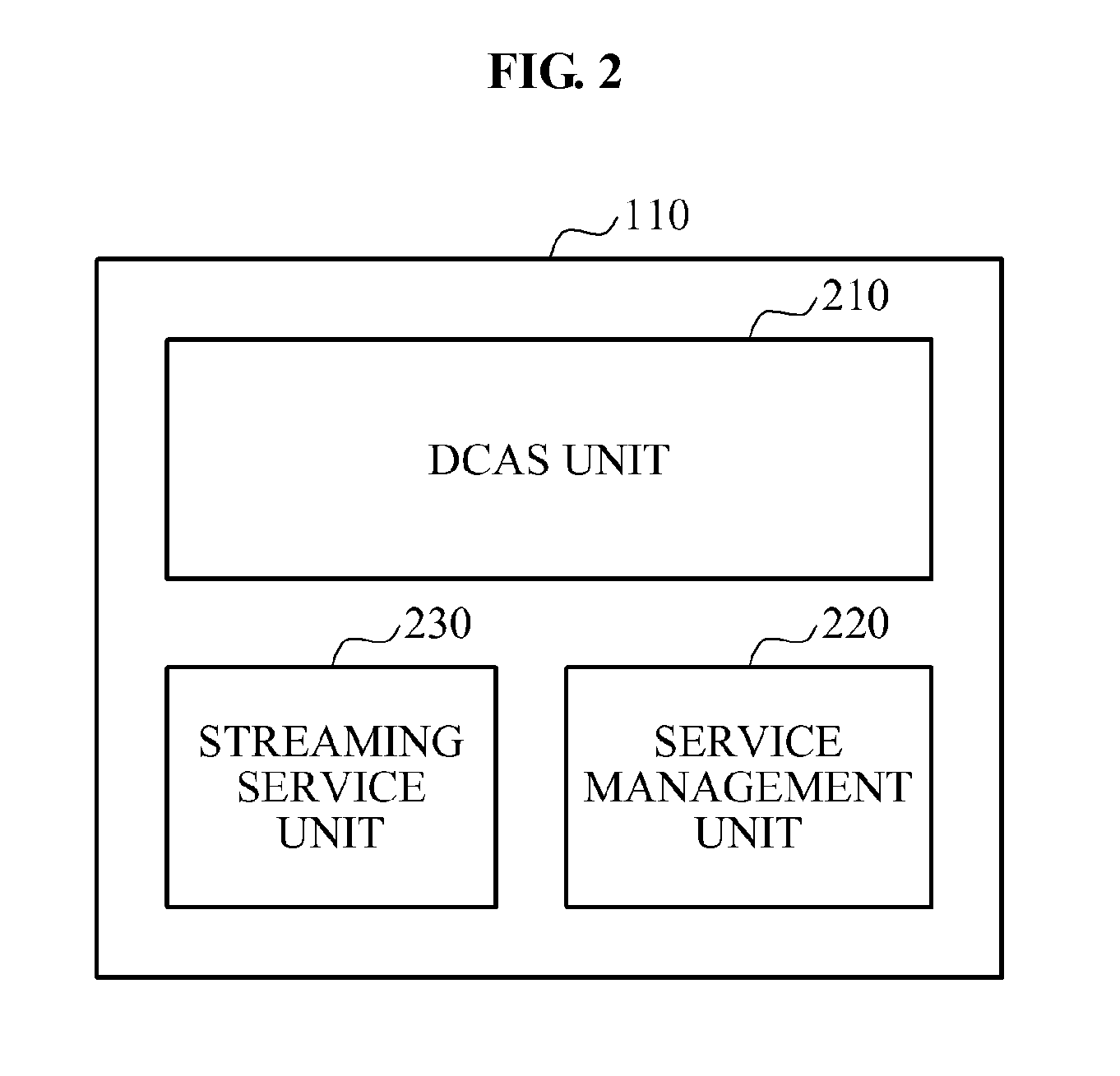
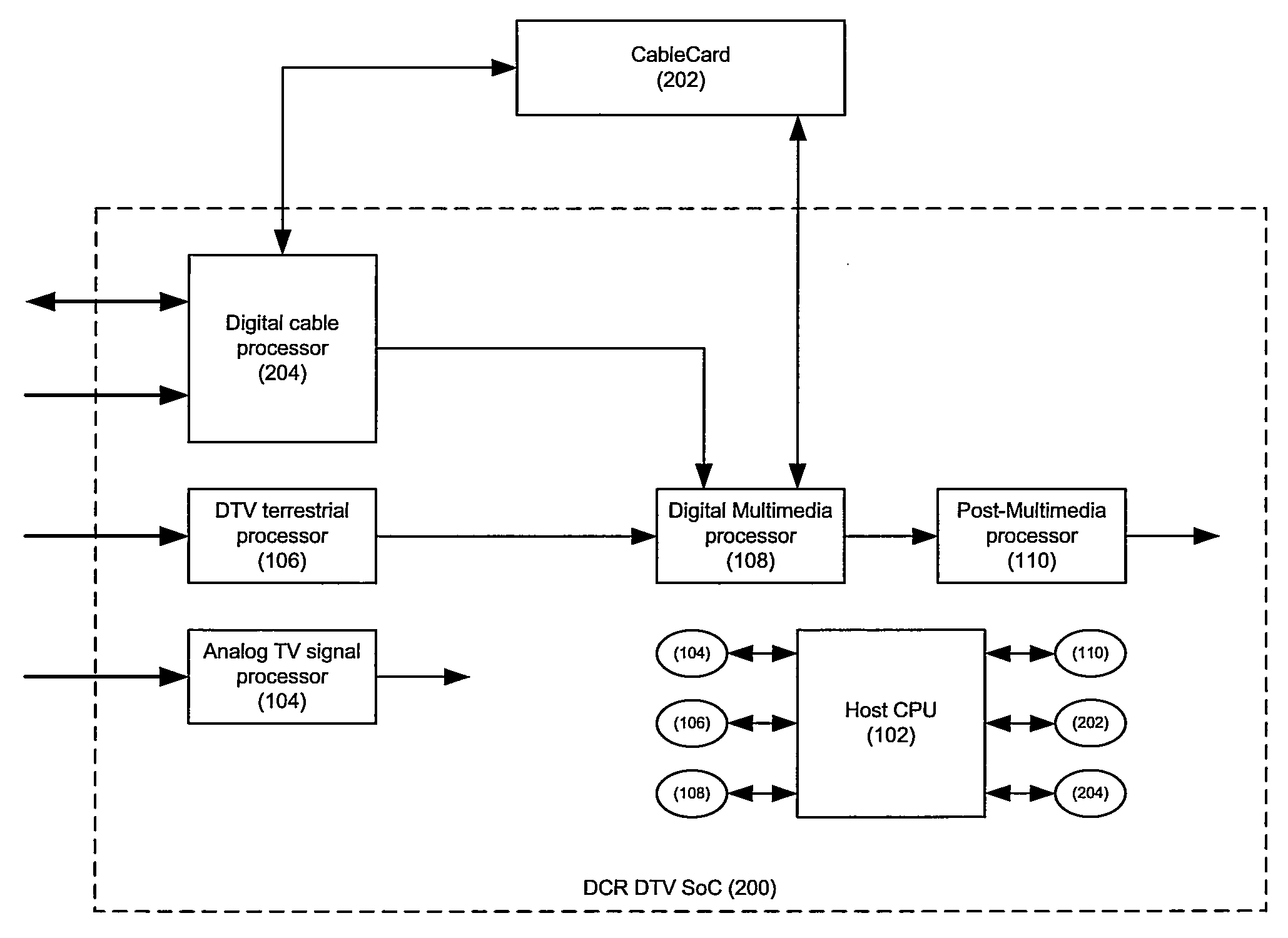
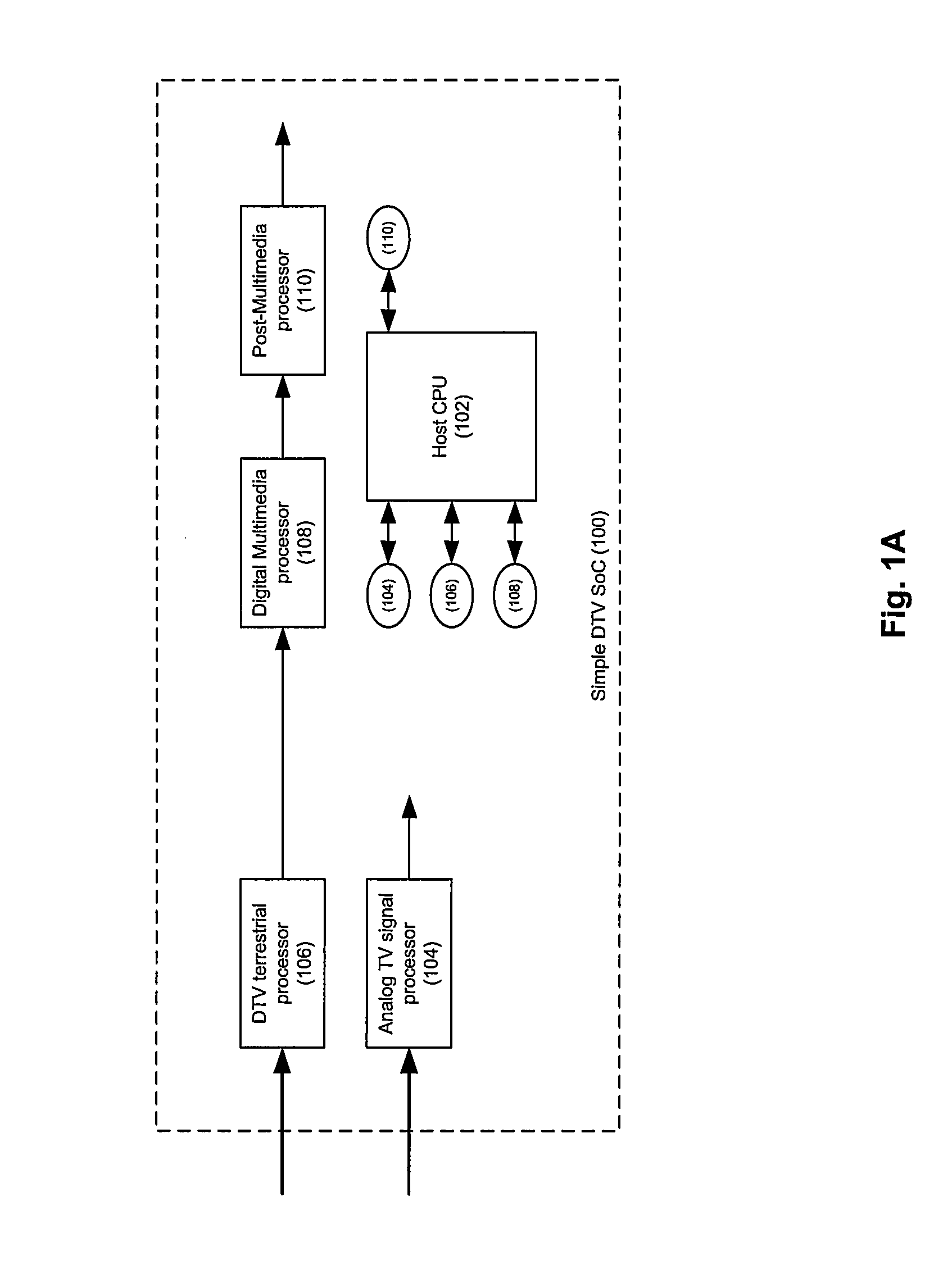
A security processor may be embedded within a digital cable ready (DCR) digital TV (DTV) system-on-chip to performing content protection operations during digital TV signal processing. The embedded security processor may be used to perform operations that are currently performed by an external entity, such as, for an example, a CableCard. The embedded security processor maybe configured to use a conditional access function including, but not limited to, CableLabs® Downloadable Conditional Access System (DCAS) based function. The security processor may be reprogrammable to enable the system-on-chip to be reconfigured with a different function and / or to allow operation with a new cable service provider. The security processor may enable secure reprogrammability of the system-on-chip utilizing security algorithms and / or other mechanisms including use of chip-specific identification information. The SoC may be enabled to operate with a CableCard whenever the security processor may be disabled.
Owner:AVAGO TECH INT SALES PTE LTD
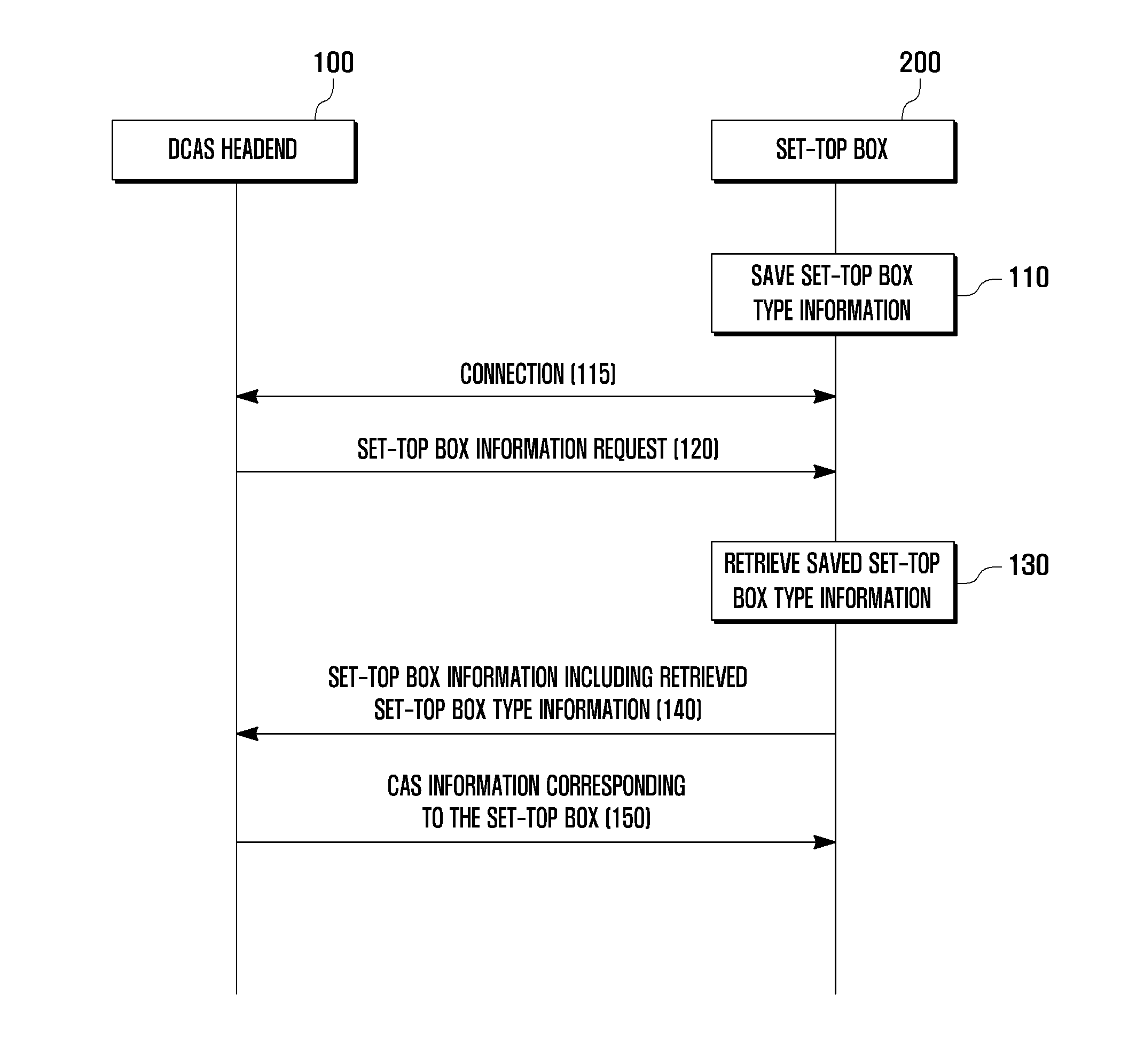
Method and system for identifying set-top box in download conditional access system
InactiveUS20110113465A1Analogue secracy/subscription systemsTwo-way working systemsDownloadable Conditional Access SystemConditional access systems
A set-top box identification method and system for identifying the set-top box which is currently connected to a Downloadable Conditional Access System (DCAS) based on set-top box manufacturer and / or set-top box model are provided. The set-top box identification method for the DCAS includes retrieving set-top box type information upon receipt of a set-top box information request transmitted by a DCAS headend, transmitting the set-top box information including the set-top box type information to the DCAS headend, and identifying, at the DCAS headend, the set-top box based on the set-top box information. The DCAS headend can acquire the information on the connected set-top box at any time and determine the manufacturer and model of the set-top box from the set-top box information.
Owner:SAMSUNG ELECTRONICS CO LTD
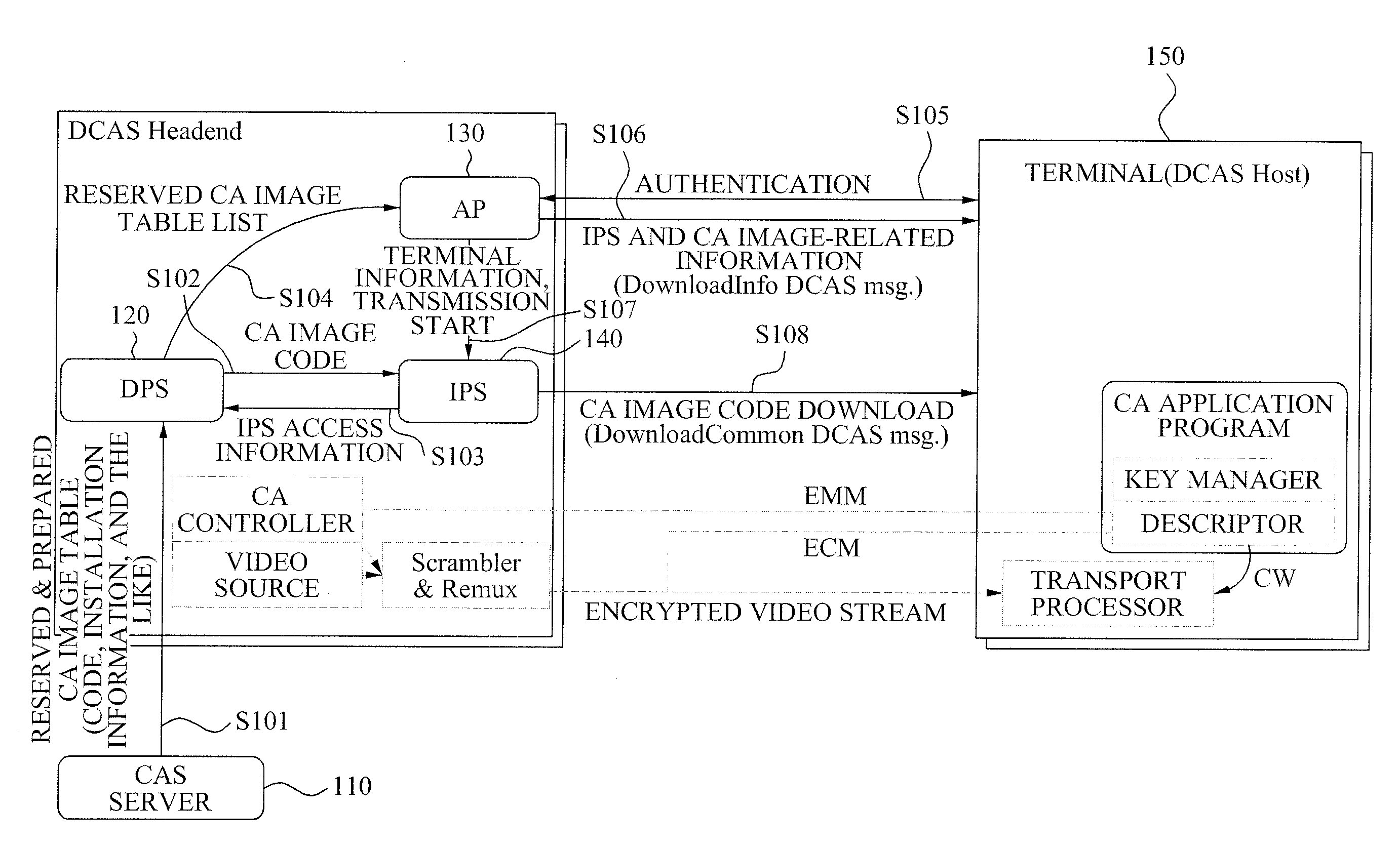
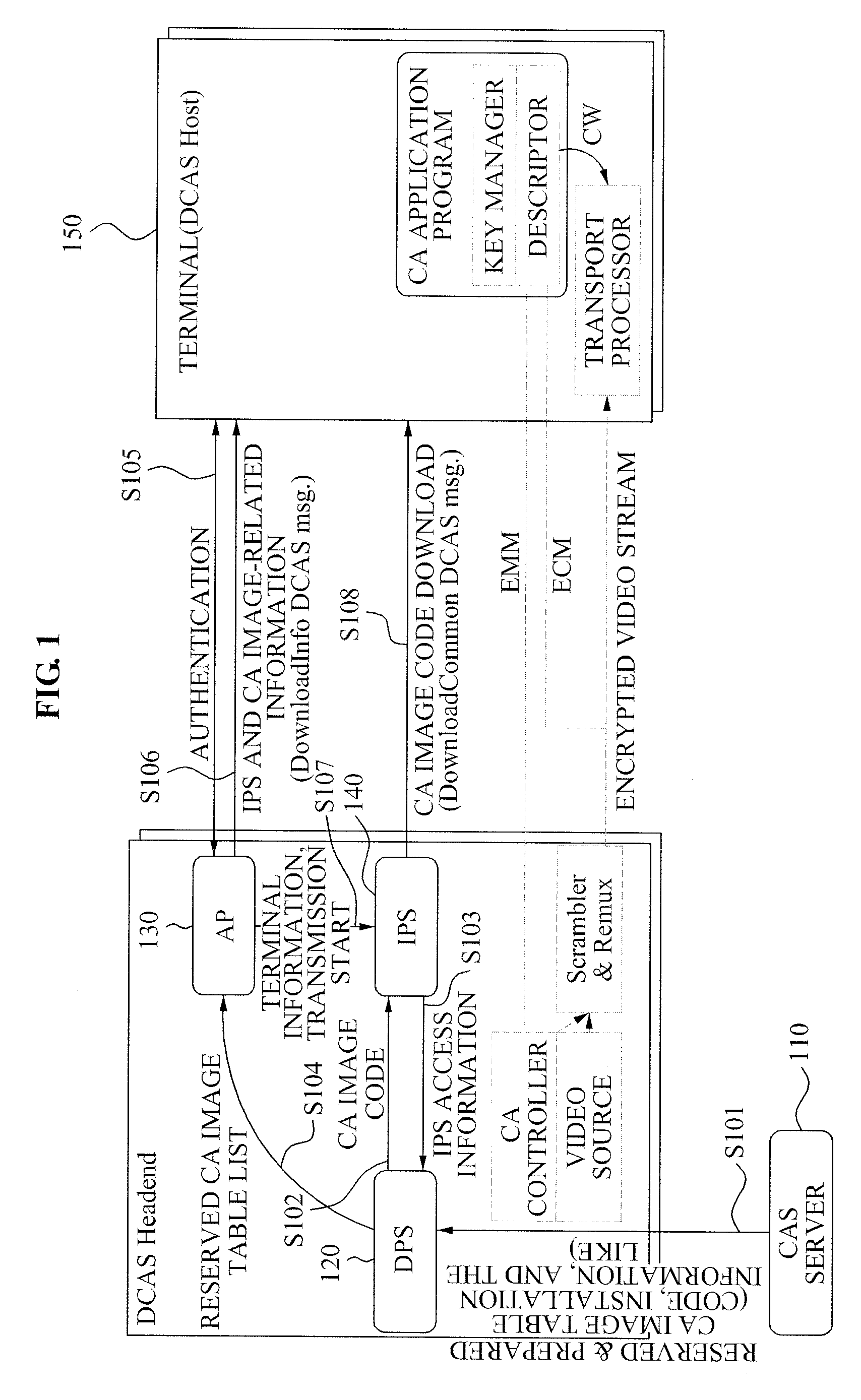
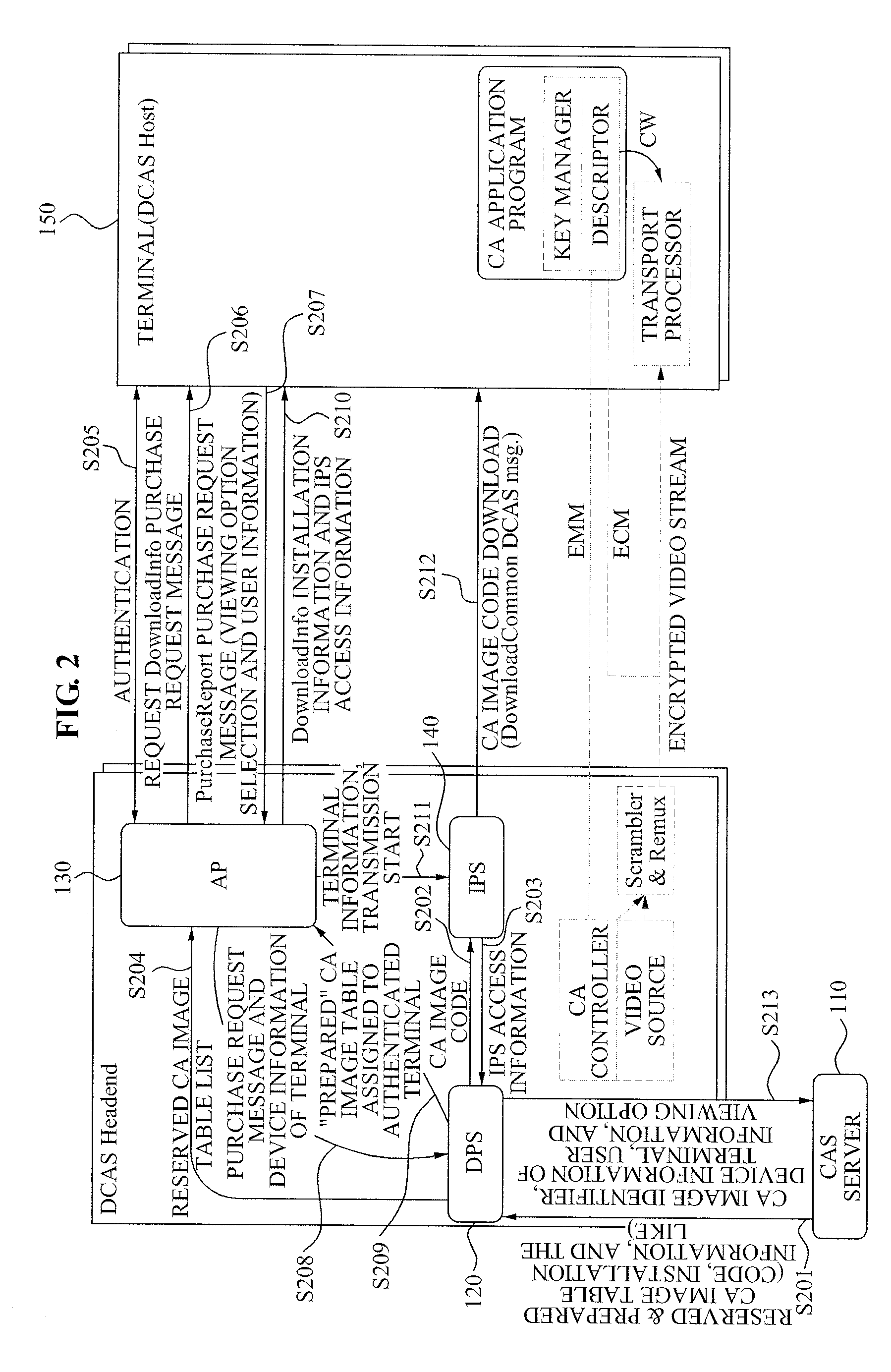
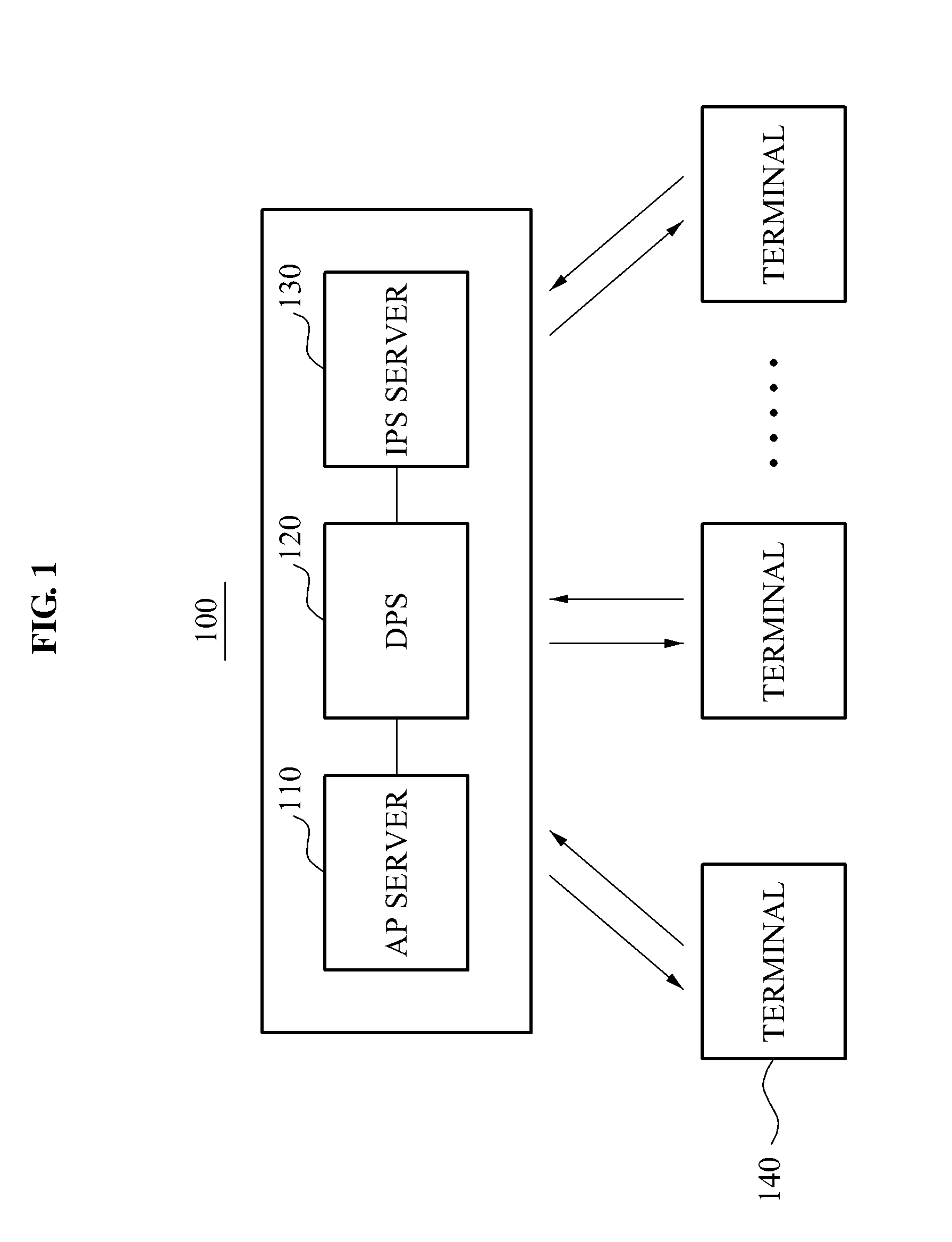
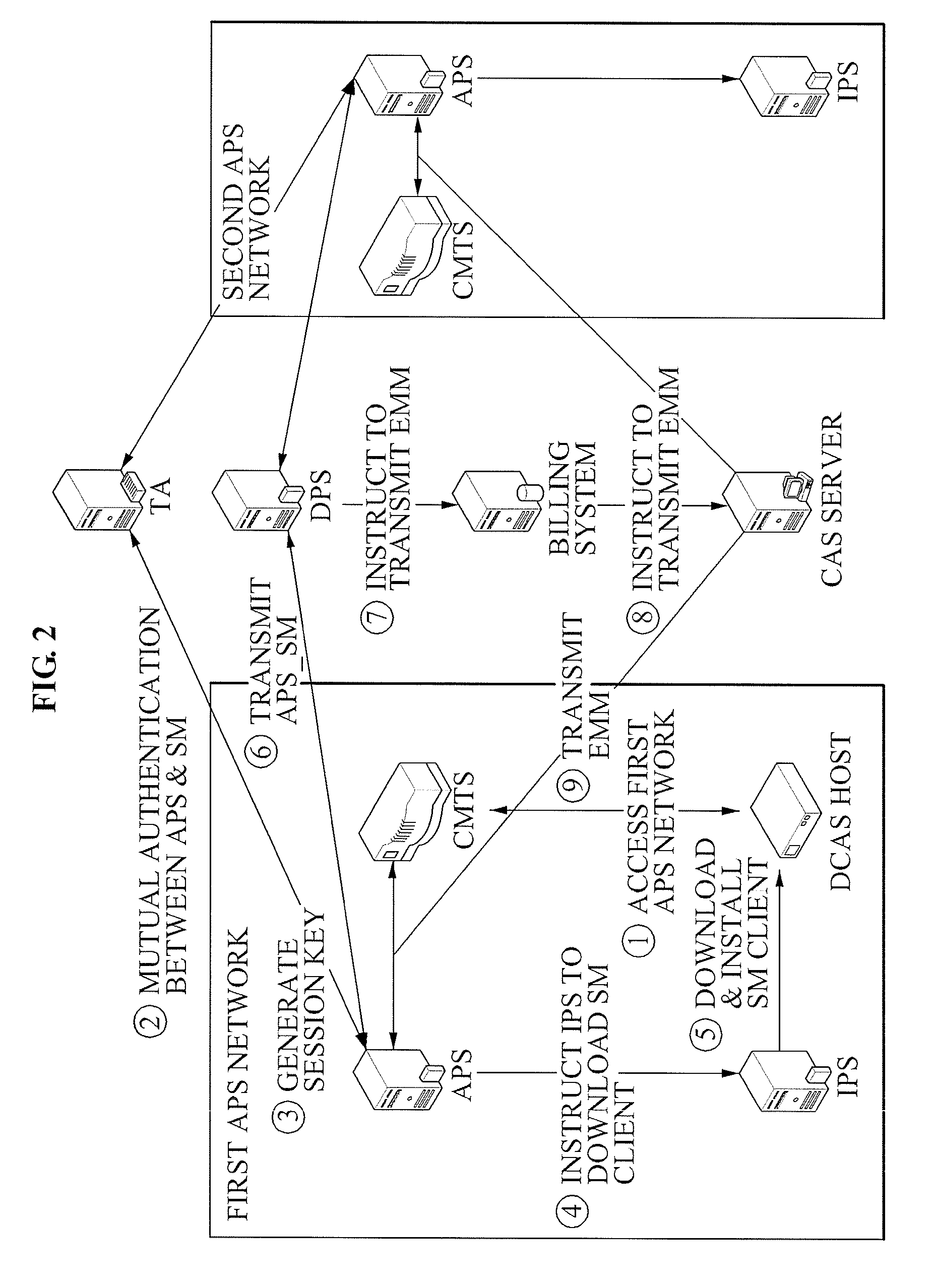
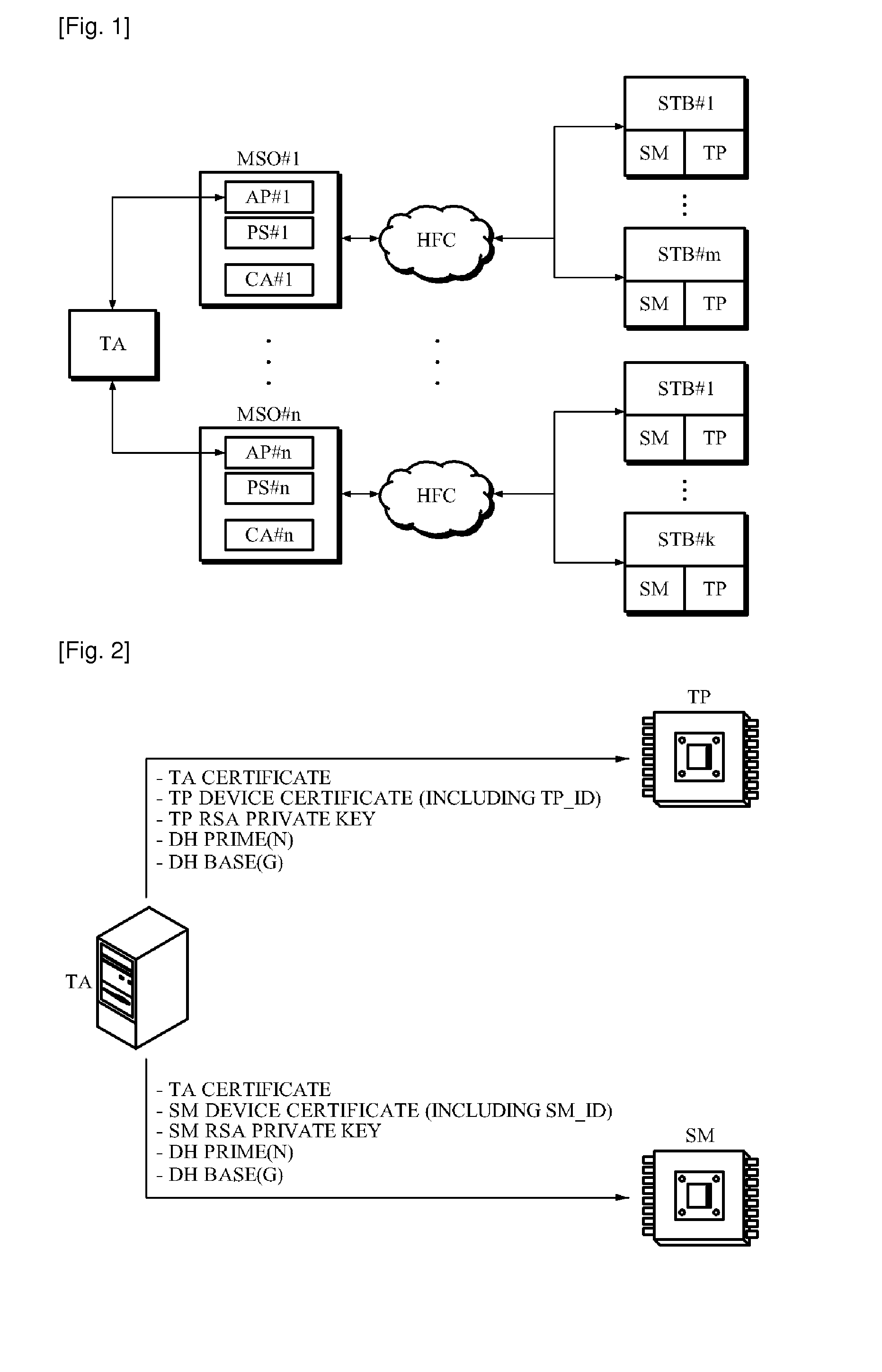
Downloadable conditional access system and controlling method for the same
InactiveUS20090158401A1Digital data processing detailsMultiple digital computer combinationsDownloadable Conditional Access SystemConditional access systems
A method and apparatus of supporting a fee-based broadcasting service in a Downloadable Conditional Access System (DCAS) is provided. A control method of a DCAS, the method including: receiving a Conditional Access (CA) image file from a Conditional Access System (CAS) server and receiving Integrated Personalization Server (IPS) access information from an IPS; providing an Authentication Proxy (AP) with information about the received CA image file; controlling the AP to provide a terminal with access information to the IPS and image installation information when the terminal joins a fee-based service based on verifying device information of the terminal; and controlling the IPS to enable the terminal to receive a CA image code of the terminal based on the access information and the image installation information.
Owner:ELECTRONICS & TELECOMM RES INST
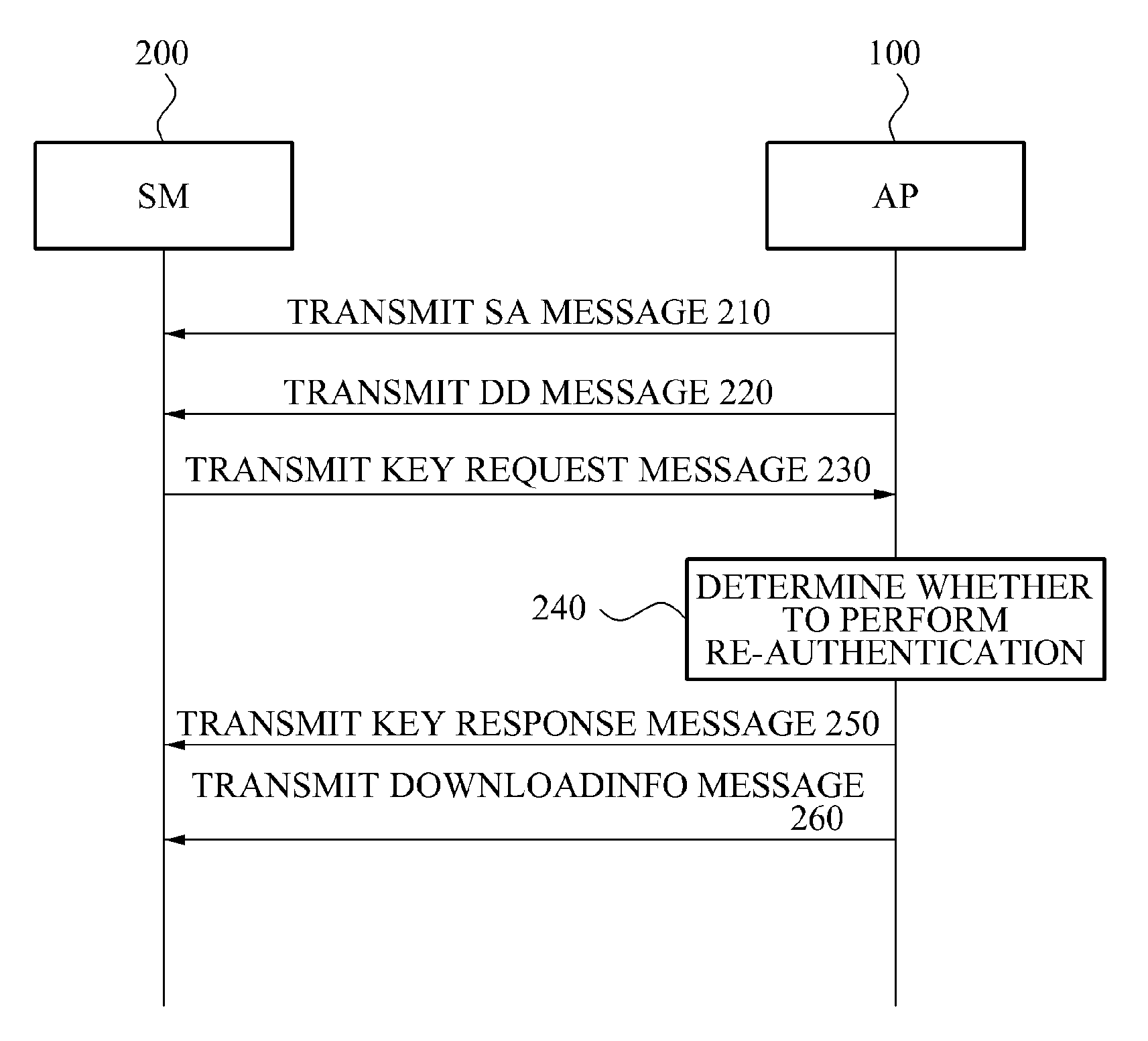
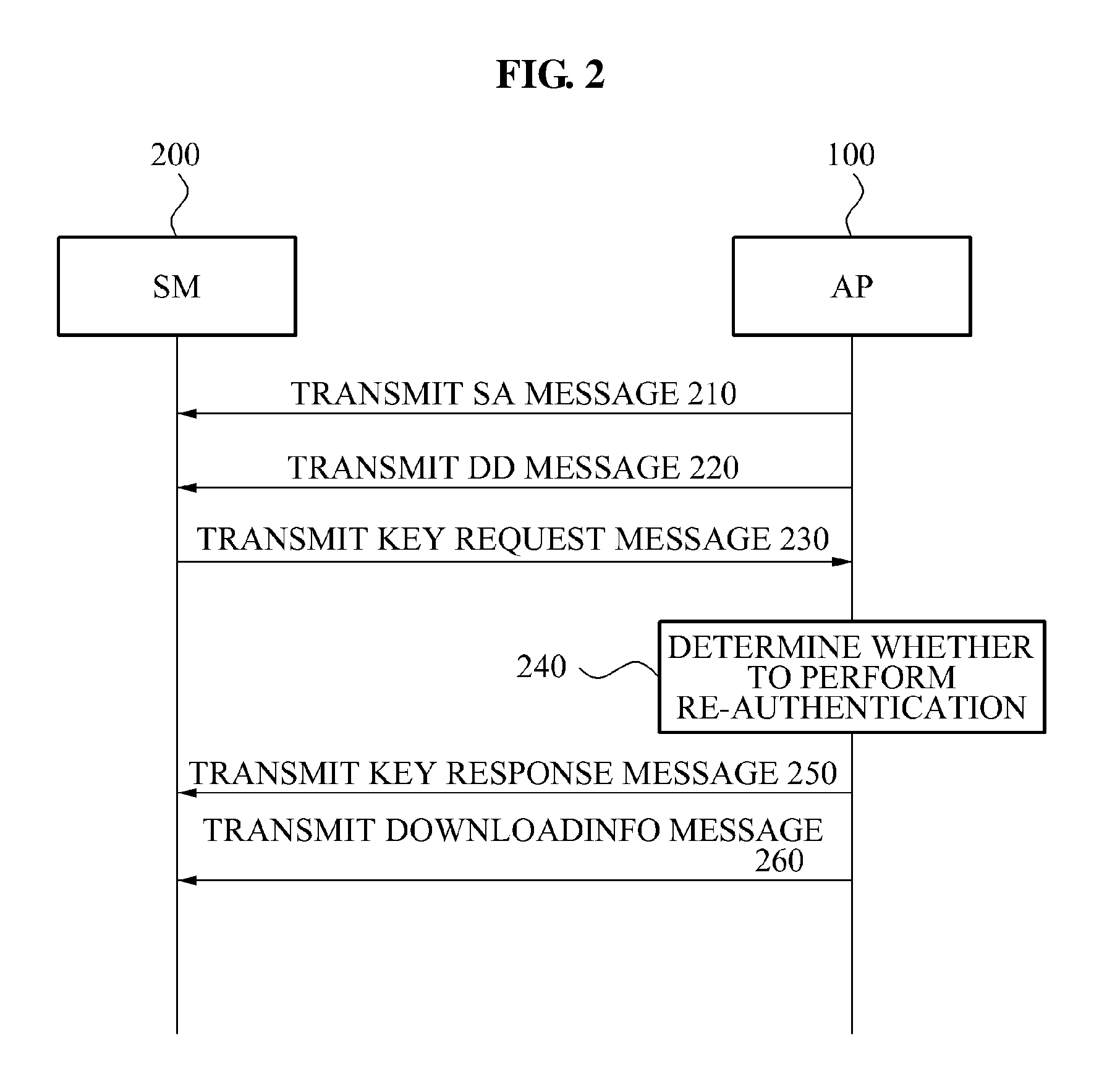
Re-authentication apparatus and method in downloadable conditional access system
ActiveUS20110078444A1Key distribution for secure communicationUser identity/authority verificationDownloadable Conditional Access SystemConditional access systems
Provided is a re-authentication apparatus in a Downloadable Conditional Access System (DCAS), the re-authentication apparatus includes: a receiving unit to receive a key request message from a Secure Micro (SM); a determination unit to determine whether to perform re-authentication depending on downloading of SM client image; an identification unit to identify an SM identifier using the key request message, when the re-authentication is performed as a result of the determination; an extraction unit to retrieve previous session information corresponding to the SM identifier and to extract keying information about the previous session information; and an encryption unit to control an encryption key about the SM client image to be reused, the SM client image being encrypted in a previous session based on the previous session information using the keying information.
Owner:ELECTRONICS & TELECOMM RES INST
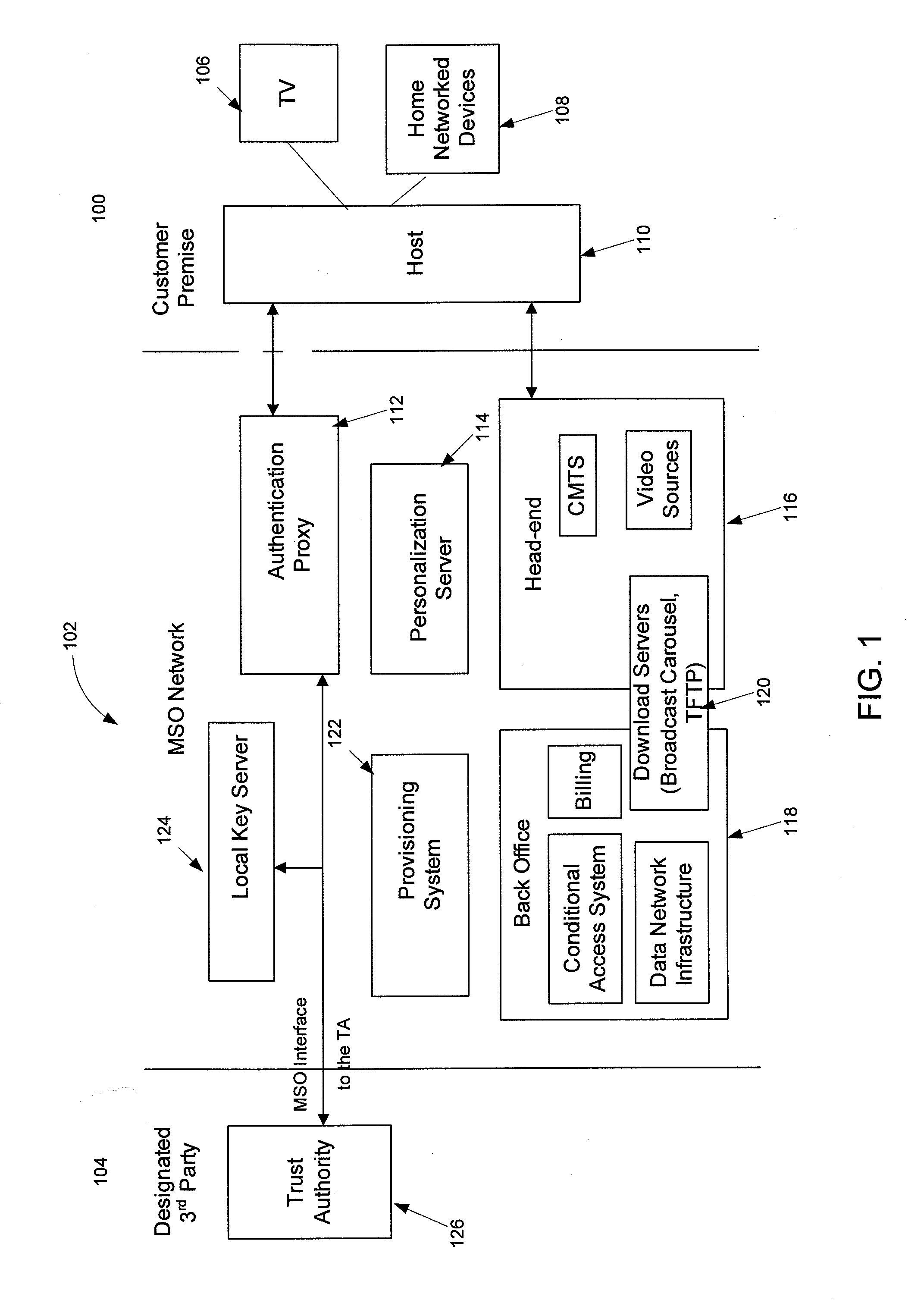
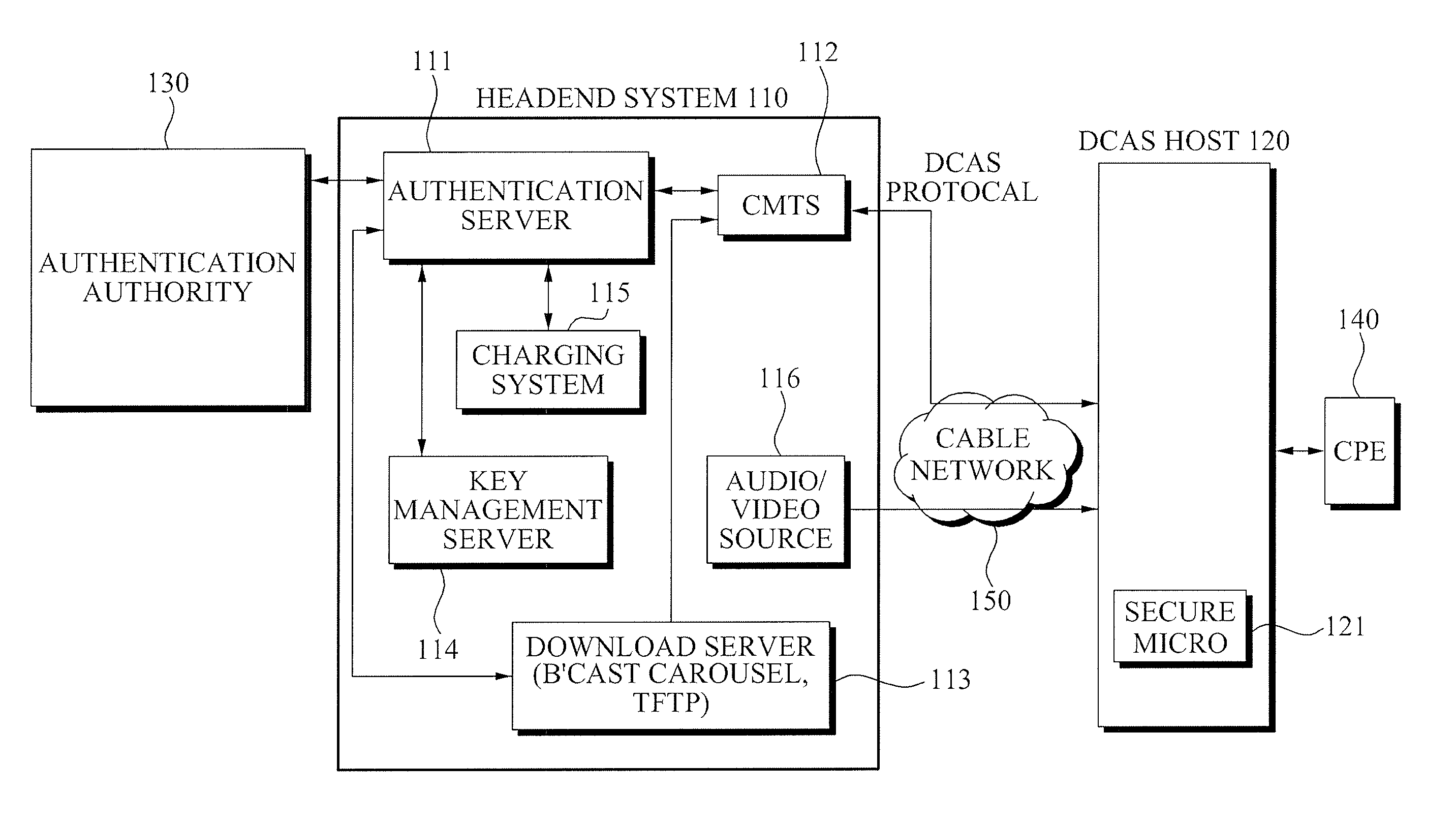
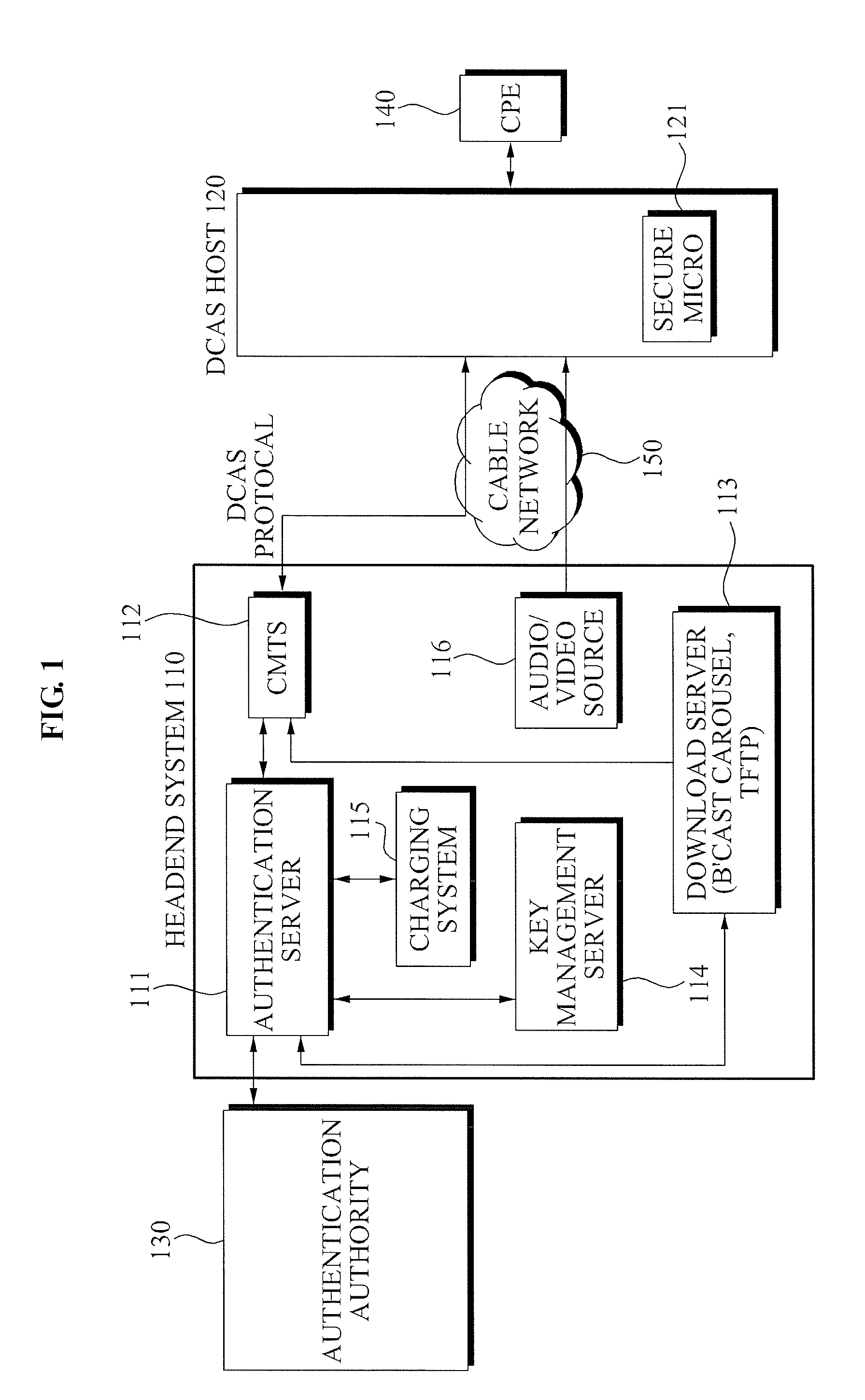
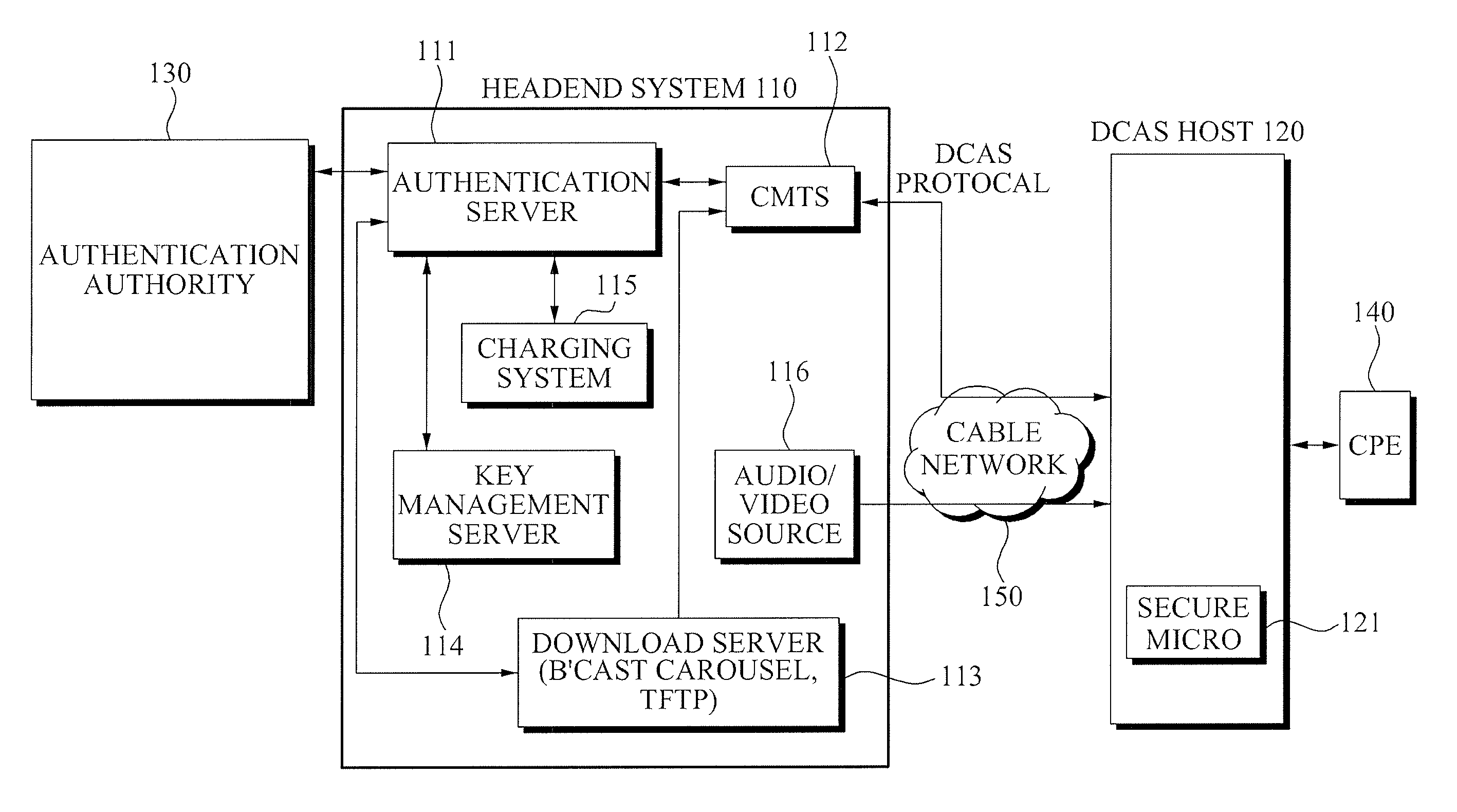
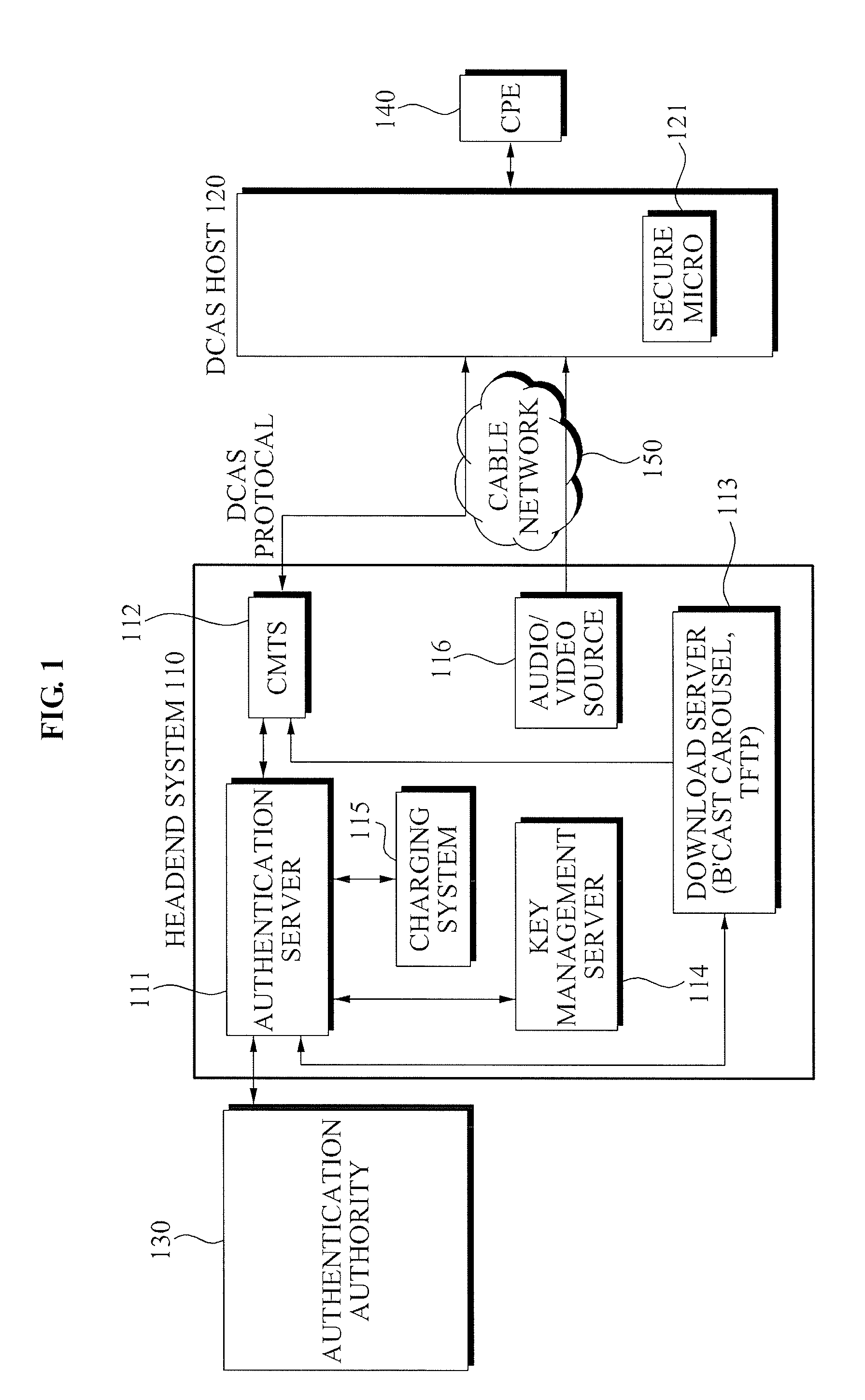
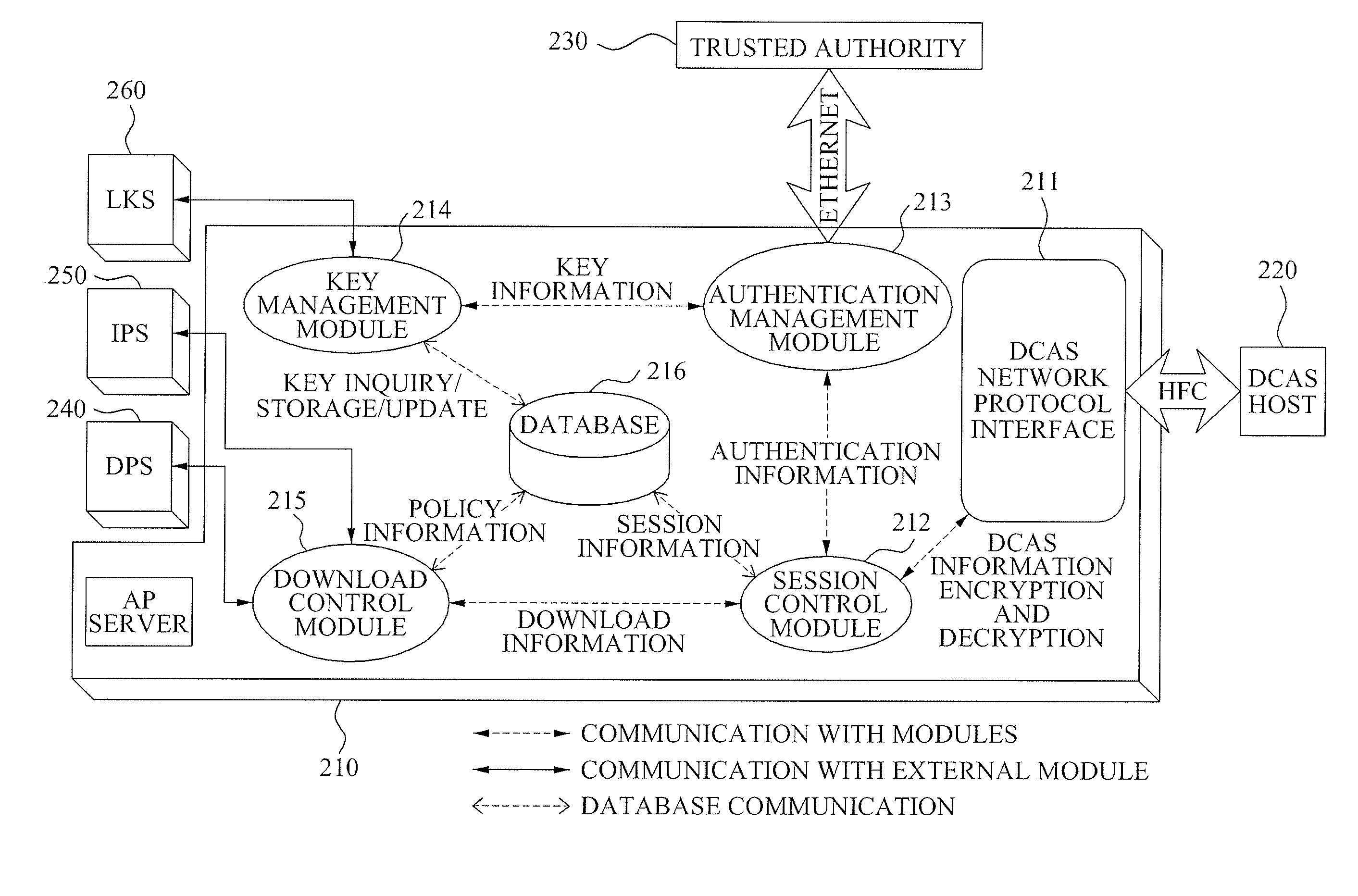
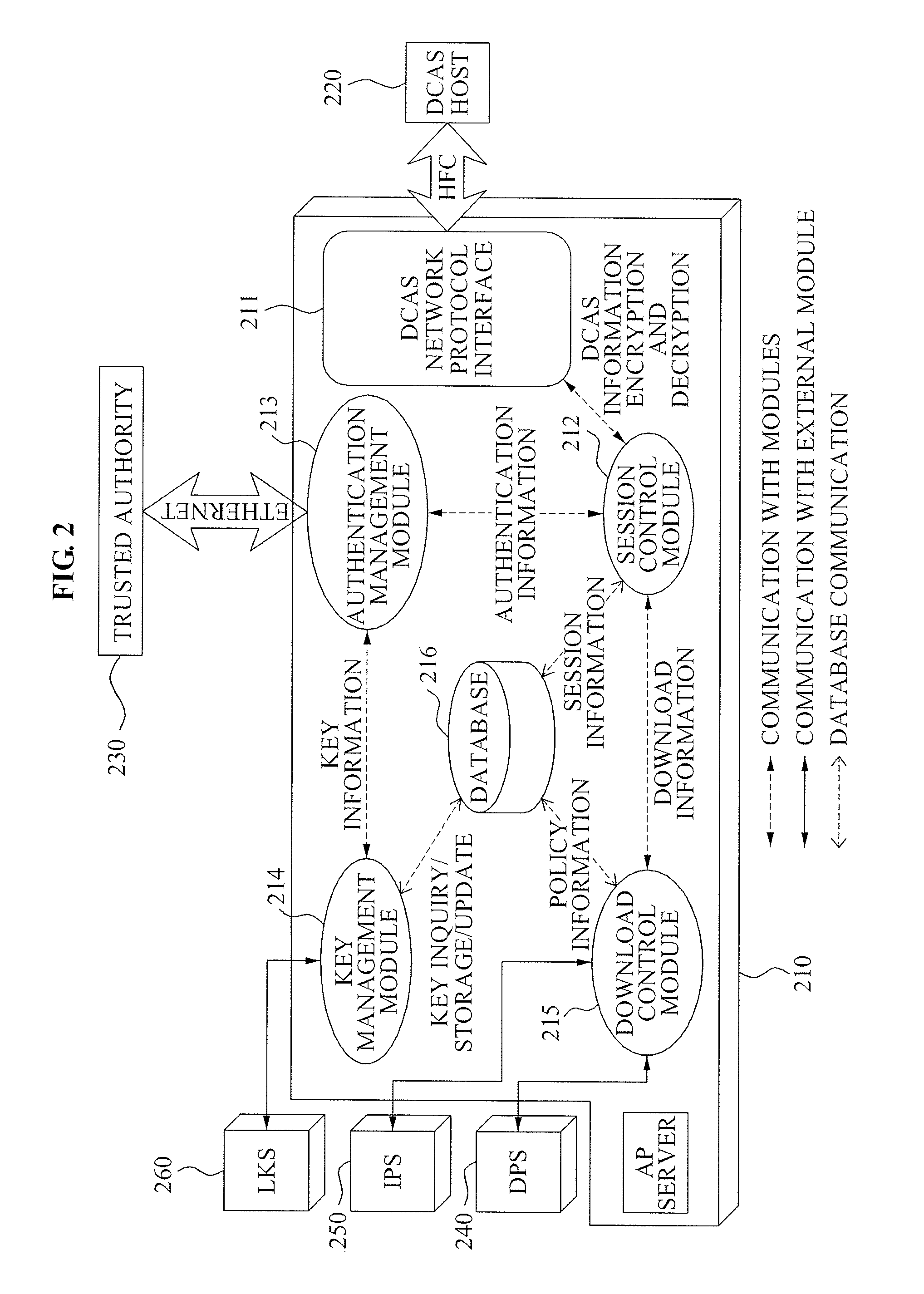
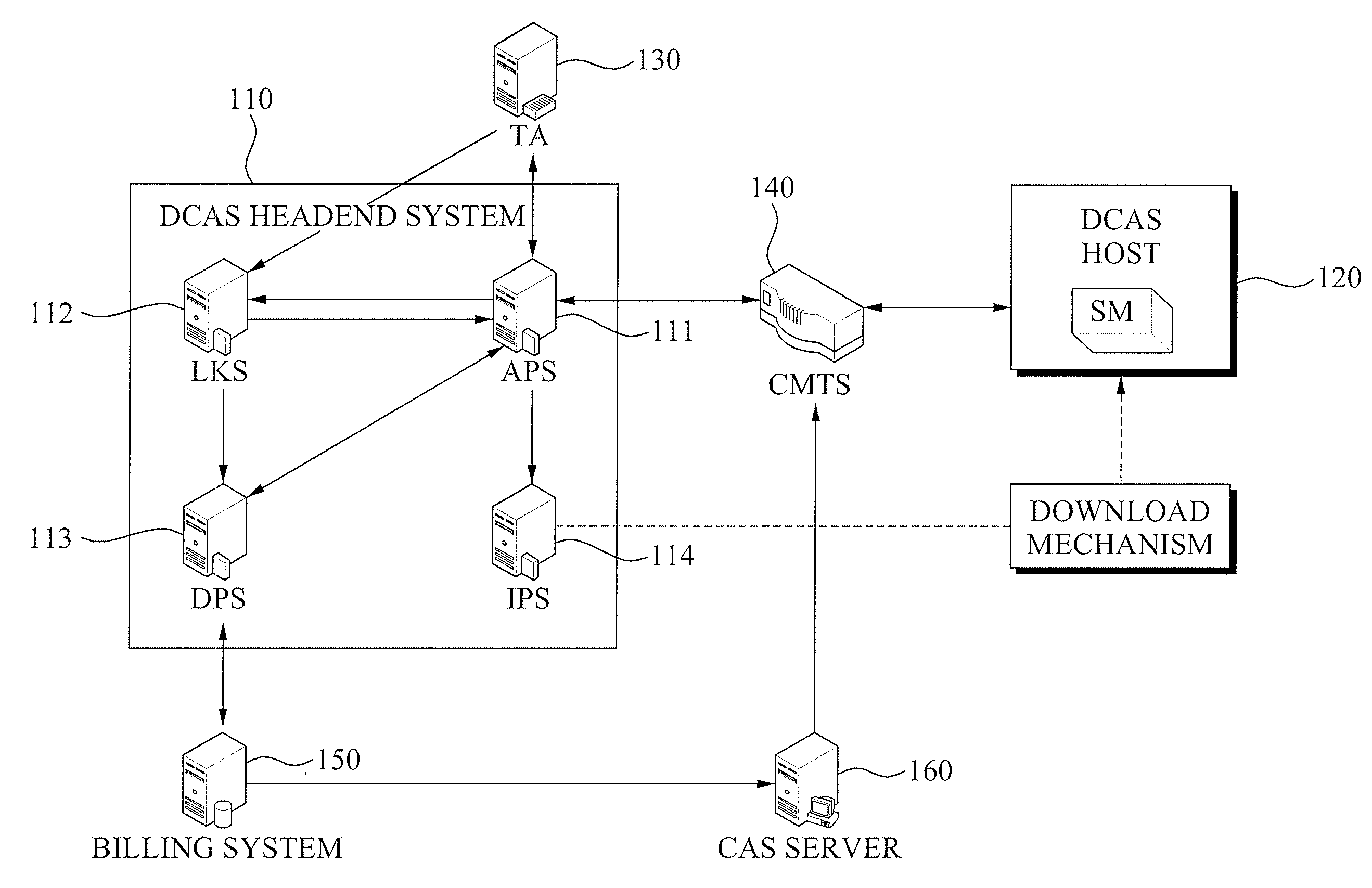
Headend system for downloadable conditional access service and method of operating the same
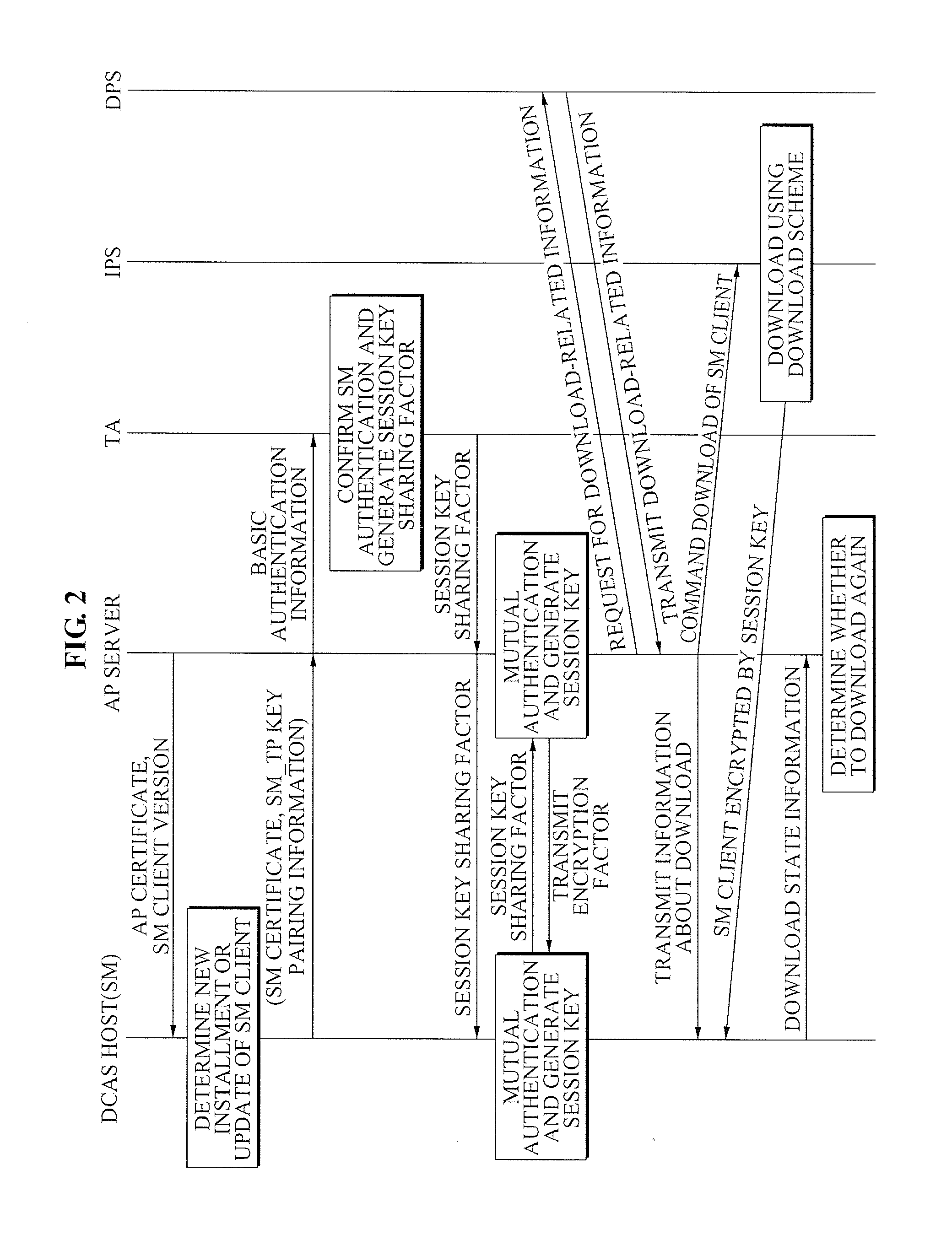
ActiveUS20090144539A1Efficient accessSafely downloadUser identity/authority verificationUnauthorized memory use protectionTrusted authorityPersonalization
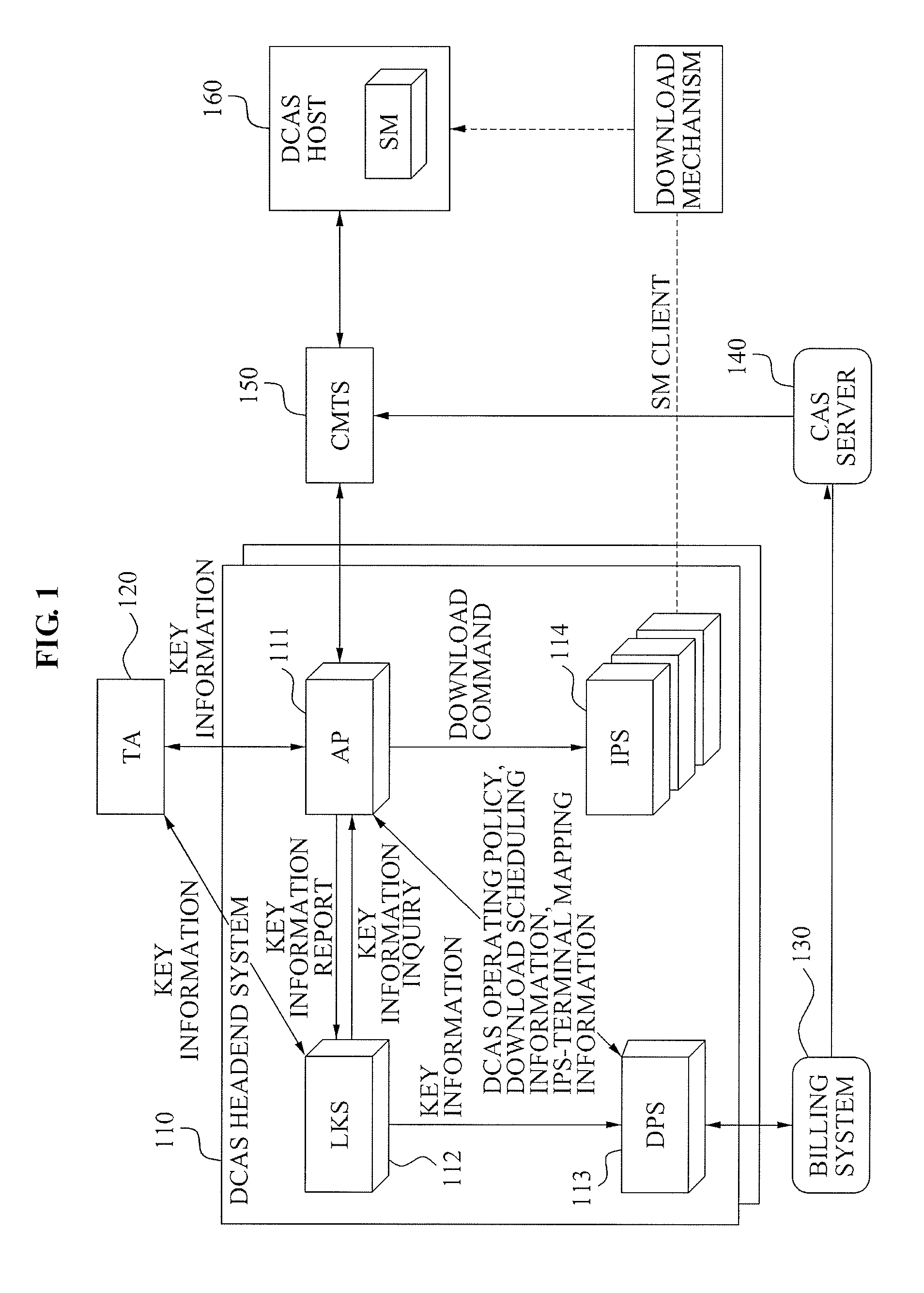
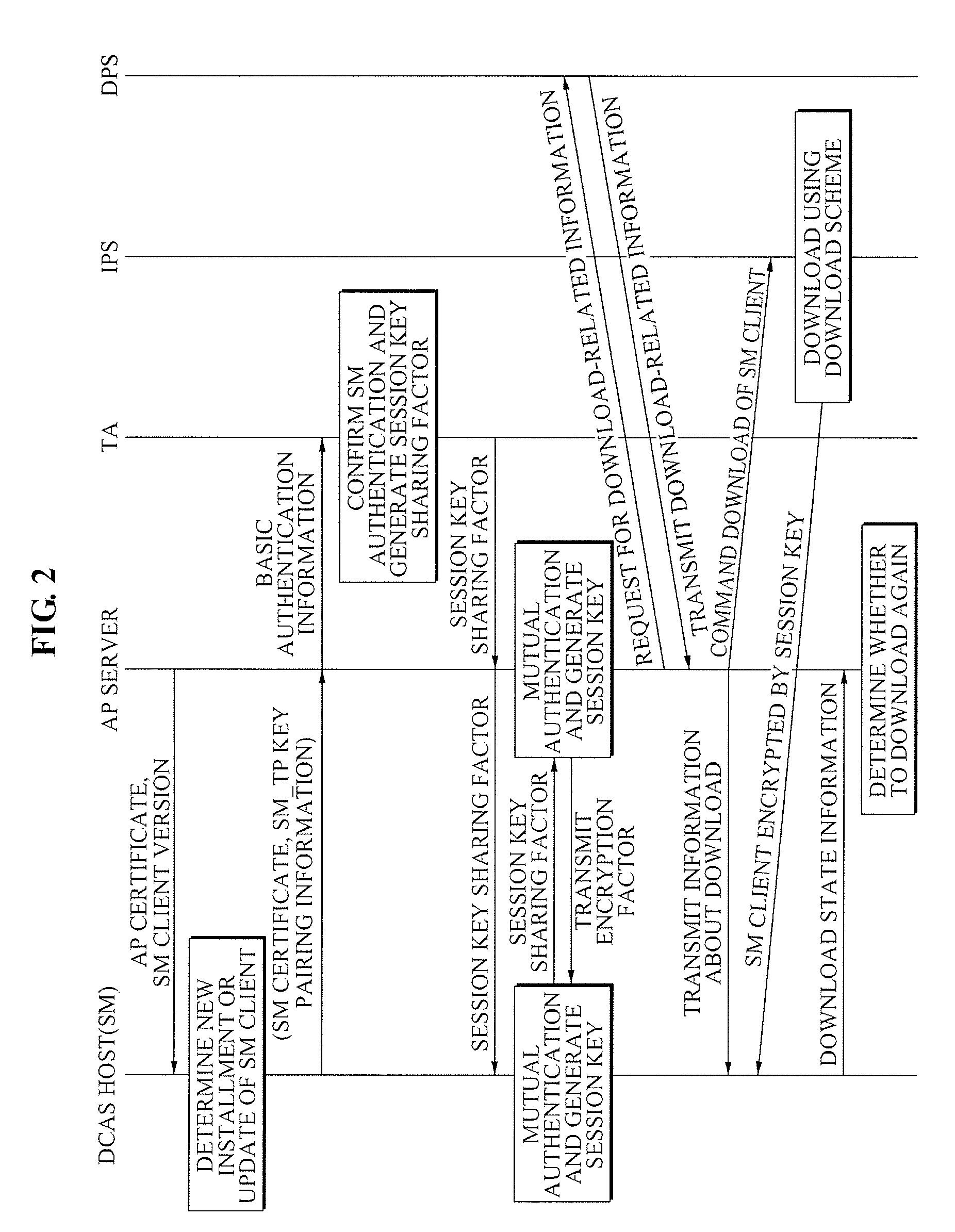
A method of operating a headend system for a downloadable conditional access service, the method including: receiving, by an Authentication Proxy (AP) server, basic authentication information from a Downloadable Conditional Access System (DCAS) host, the basic authentication information being required to authenticate the DCAS host; transmitting, by the AP server, the basic authentication information to an external trusted authority device which authenticates the DCAS host; generating, by the AP server, a session key for encrypting / decrypting a secure micro client using a session key sharing factor; obtaining, by the AP server, download-related information of the secure micro client from a DCAS Provisioning Server (DPS); and commanding, by the AP server, an Integrated Personalization System (IPS) server to download the secure micro client to the DCAS host based on the download-related information, the secure micro client being encrypted by the session key.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for detecting downloadable conditional access system host with duplicated secure micro
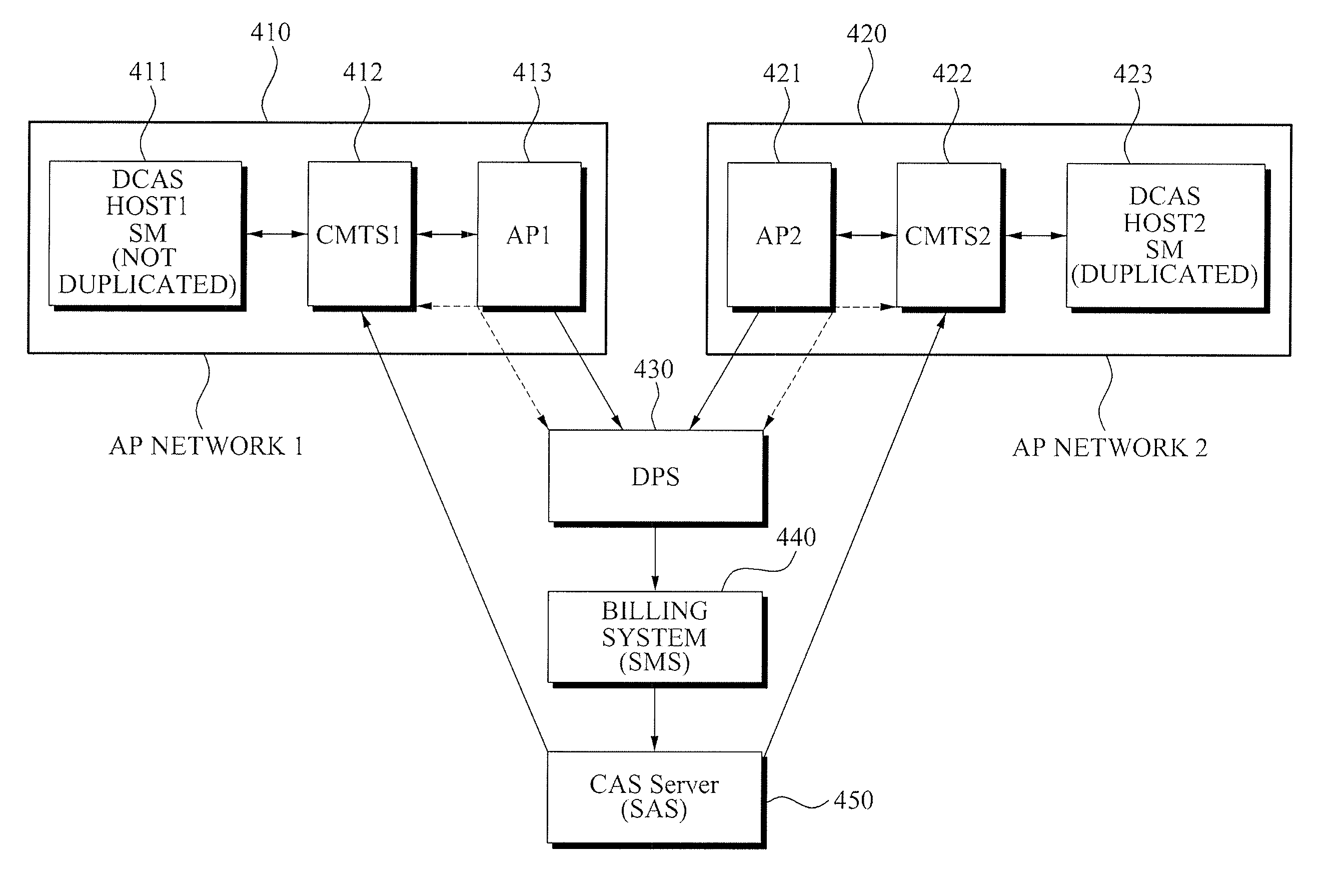
ActiveUS20090158395A1Efficiently determinedDigital data processing detailsAnalogue secracy/subscription systemsTime differenceDownloadable Conditional Access System
A method where a Downloadable Conditional Access System Provisioning Server (DPS) detects a duplicated secure micro is provided. A method of detecting a duplicated secure micro, the method including: generating authentication time difference information associated with a value of a difference between a time when a host is finally authenticated in a first address and a time when the host is authenticated in a second address; comparing the authentication time difference information with a first reference value and a second reference value, the second reference value being less than the first reference value; and determining whether the secure micro is duplicated based on a result of the comparing.
Owner:ELECTRONICS & TELECOMM RES INST
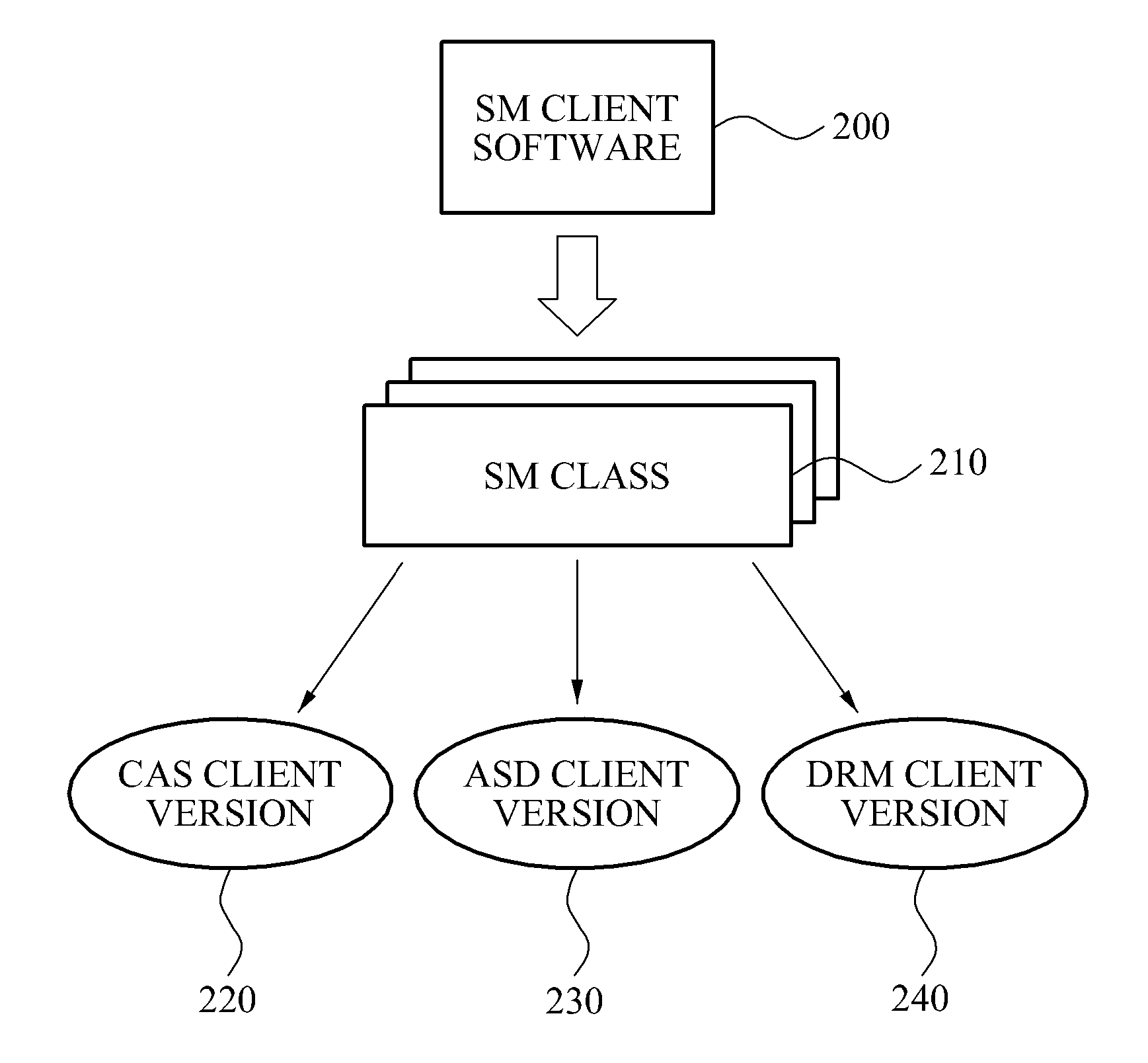
Dcas headend system and method for processing error of secure micro client software
InactiveUS20110154098A1Digital data processing detailsAnalogue secracy/subscription systemsDownloadable Conditional Access SystemComputer terminal
A Downloadable Conditional Access System (DCAS) headend system and method for processing an error of Secure Micro (SM) Client Software are provided to prevent further transmission of SM Client Software where an error occurred, and to prevent unnecessary traffic due to repeat reinstallation of SM Client Software between an Authentication Proxy (AP) server and a terminal, by changing policy information regarding a transmission of SM Client Software associated with error information, when a number of terminals that transmit the error information exceeds a reference value as a result of analyzing result information regarding a reception and an installation of the SM Client Software received from a terminal corresponding to a DCAS headend system.
Owner:ELECTRONICS & TELECOMM RES INST
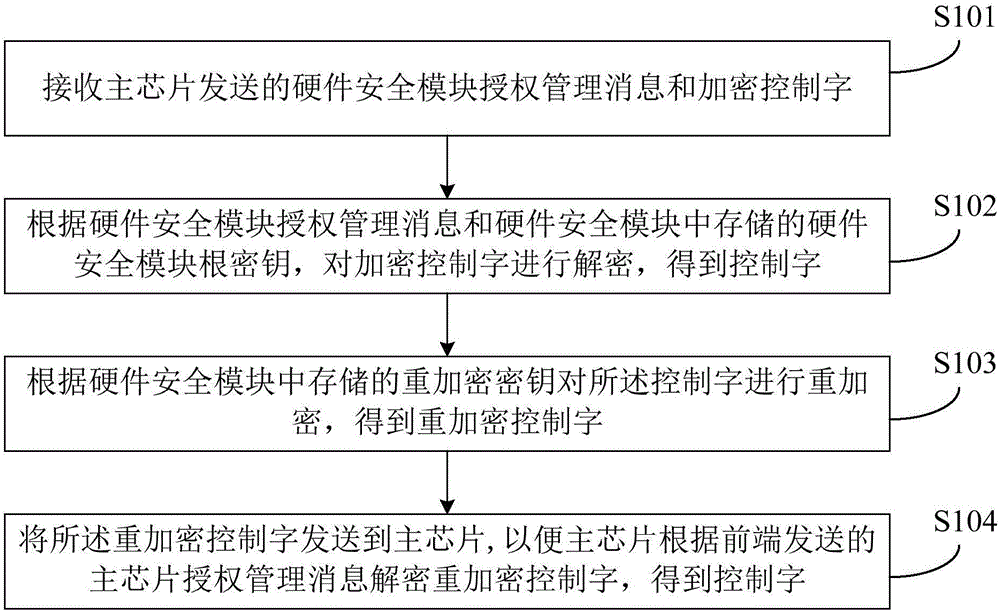
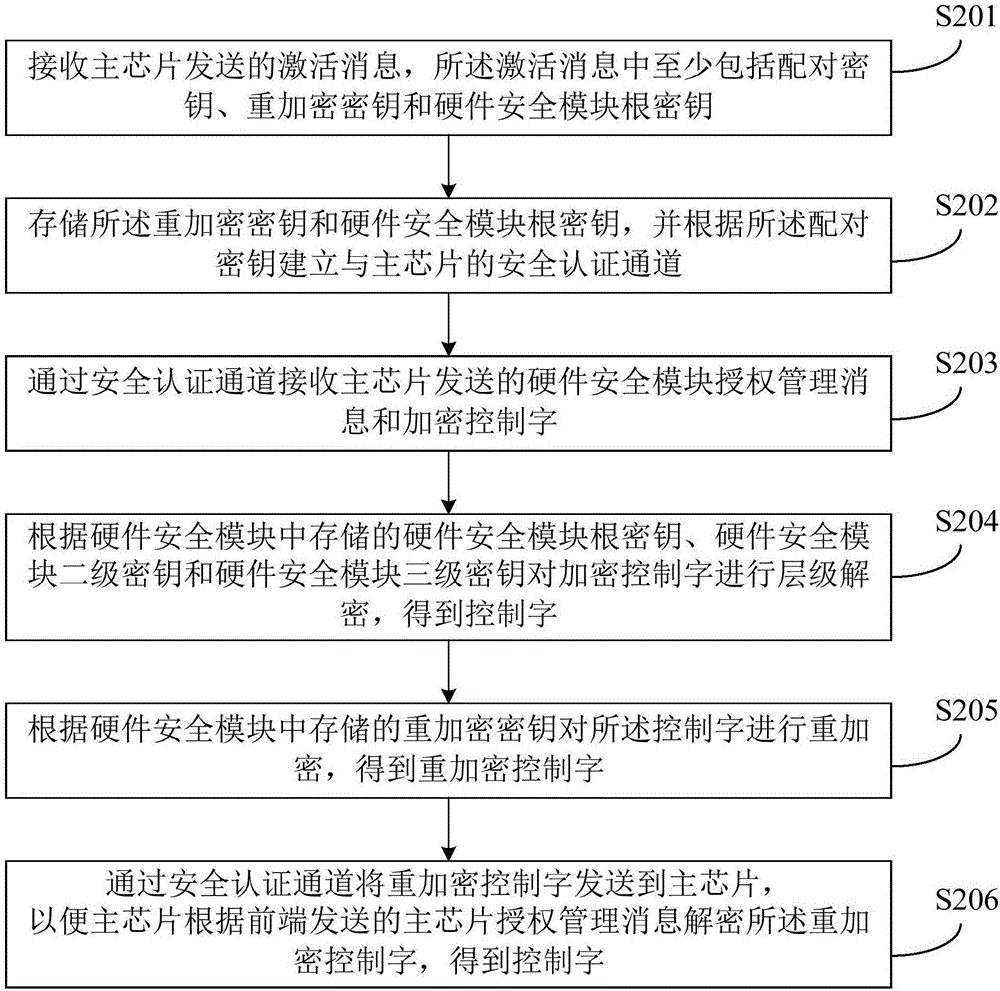
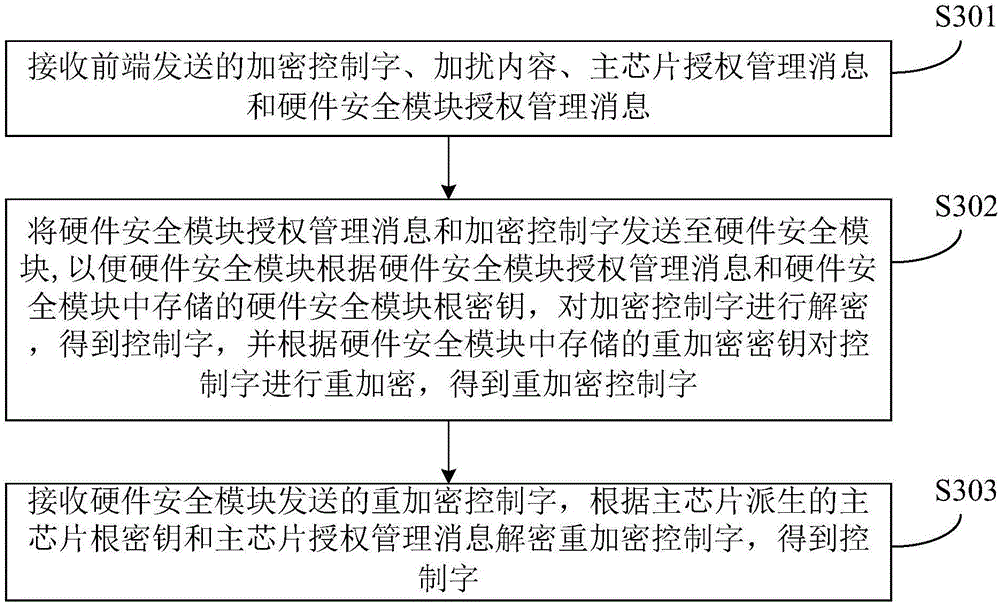
Method of protecting encrypted control word, hardware security module, main chip and terminal
ActiveCN106803980AImprove securityInternal/peripheral component protectionProgram/content distribution protectionHardware security moduleDownloadable Conditional Access System
The embodiment of the invention discloses a method of protecting encrypted control words, a hardware security module, a main chip and a terminal. The method is applied to a downloadable conditional access system including a front end and a terminal, and the terminal comprises the main chip and the hardware security module. The method includes the following steps: receiving a hardware security module authorization management message and an encrypted control word sent from the main chip, wherein the hardware security module authorization management message includes a secret key for decrypting encrypted the control word; decrypting the encrypted the control word and obtaining a control word on the basis of the hardware security module authorization management message and a hardware security module root key stored in the hardware security module; re-encrypting the control word on the basis of a re-encryption secret key stored in the hardware security module, and obtaining a re-encrypted control word; and sending the re-encrypted control word to the main chip so that the main chip decrypts the re-encrypted control word according to a main chip authorization management message sent from the front end, and obtaining a control word. According to the embodiment of the invention, the security of the DCAS is improved by means of the hardware security module.
Owner:ACADEMY OF BROADCASTING SCI STATE ADMINISTATION OF PRESS PUBLICATION RADIO FILM & TELEVISION +3
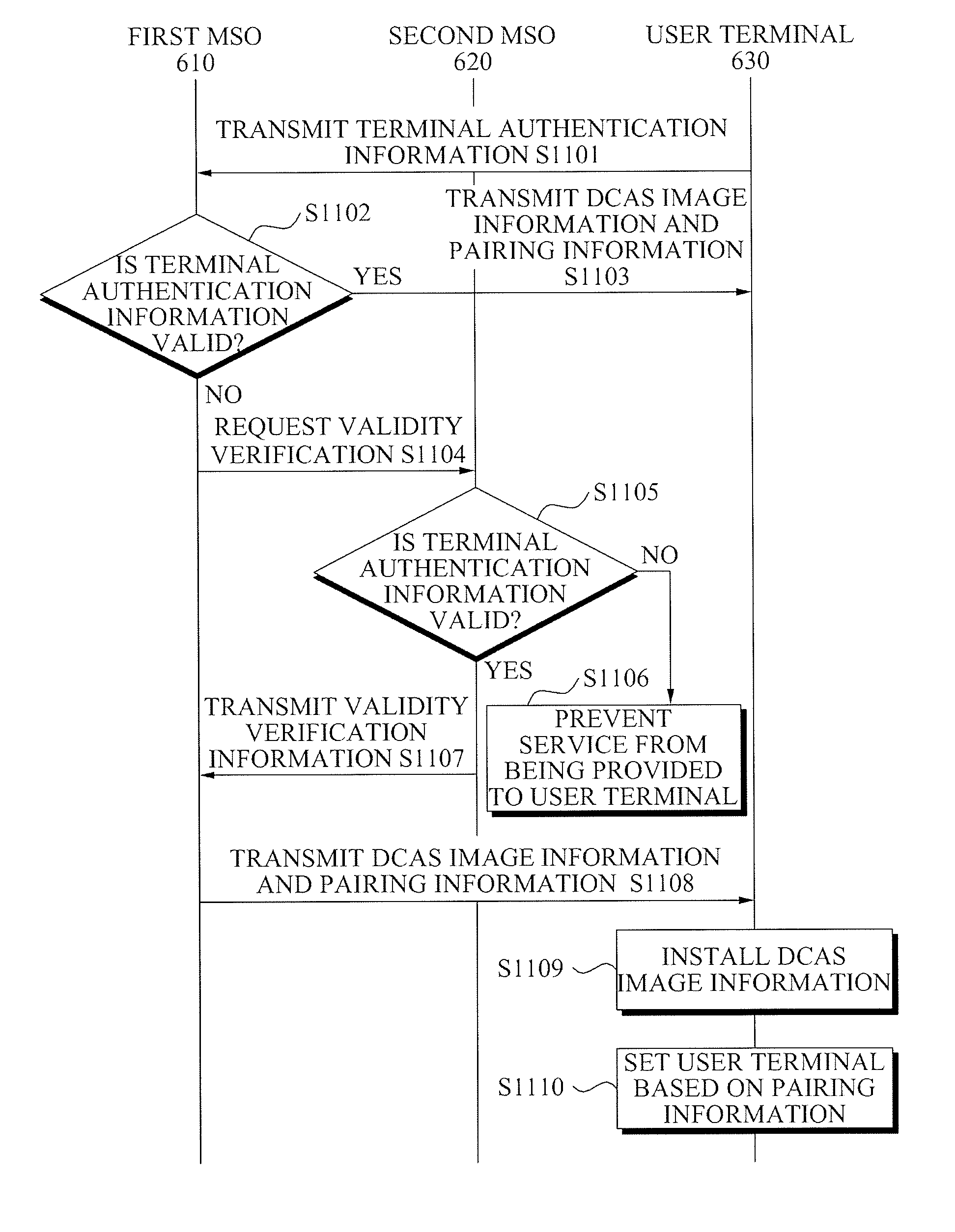
Terminal authentication apparatus and method in downloadable conditional access system
InactiveUS20100162353A1Digital data processing detailsUser identity/authority verificationReference databaseDownloadable Conditional Access System
A terminal authentication apparatus and method in a Downloadable Conditional Access System (DCAS) is provided. The terminal authentication method may determine whether terminal authentication information, received from a DCAS terminal, is valid by referring to a database, may transmit DCAS image information and pairing information about the terminal authentication information to a user terminal, when the terminal authentication information is valid, and thereby may enable the DCAS terminal to set the user terminal based on the pairing information.
Owner:ELECTRONICS & TELECOMM RES INST
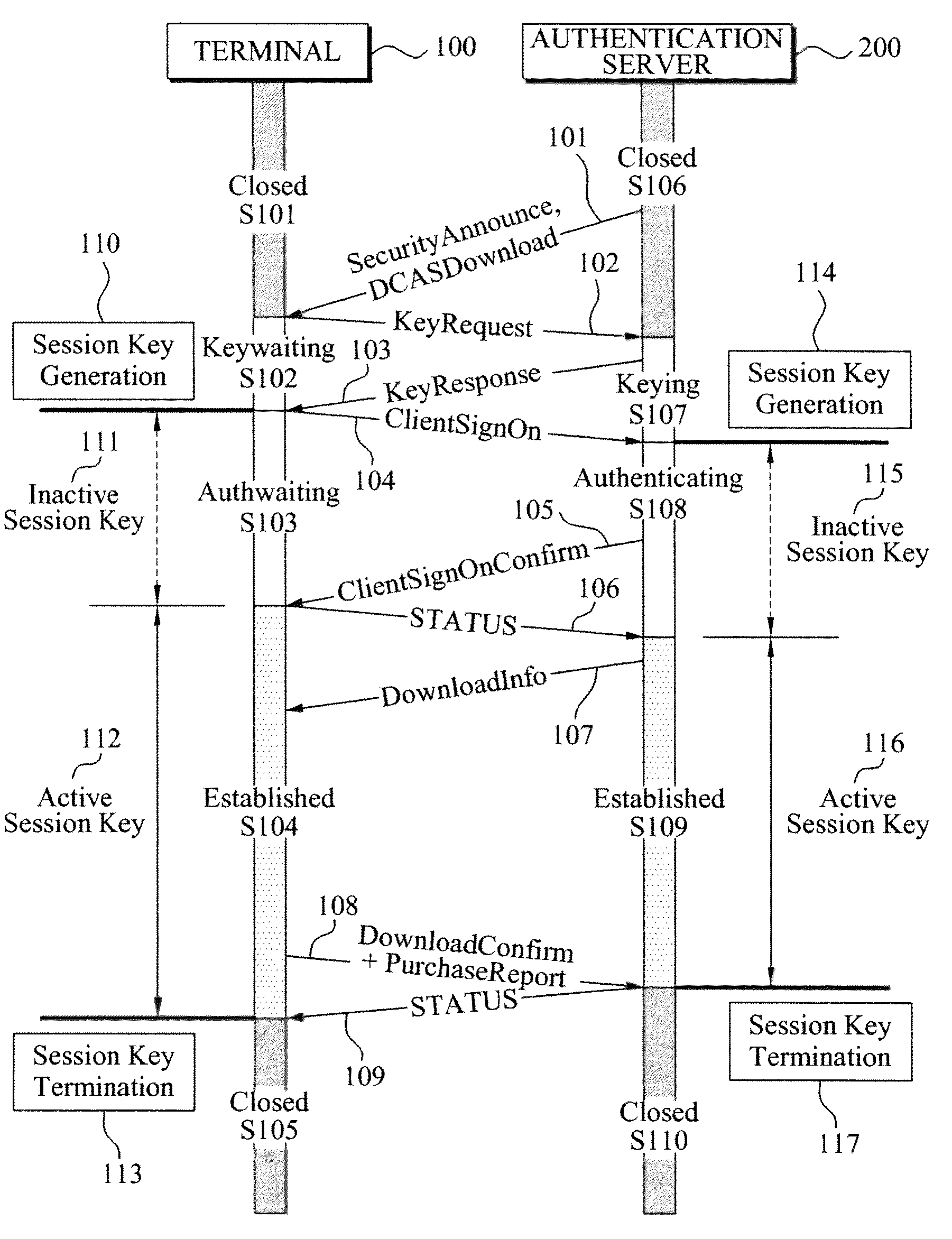
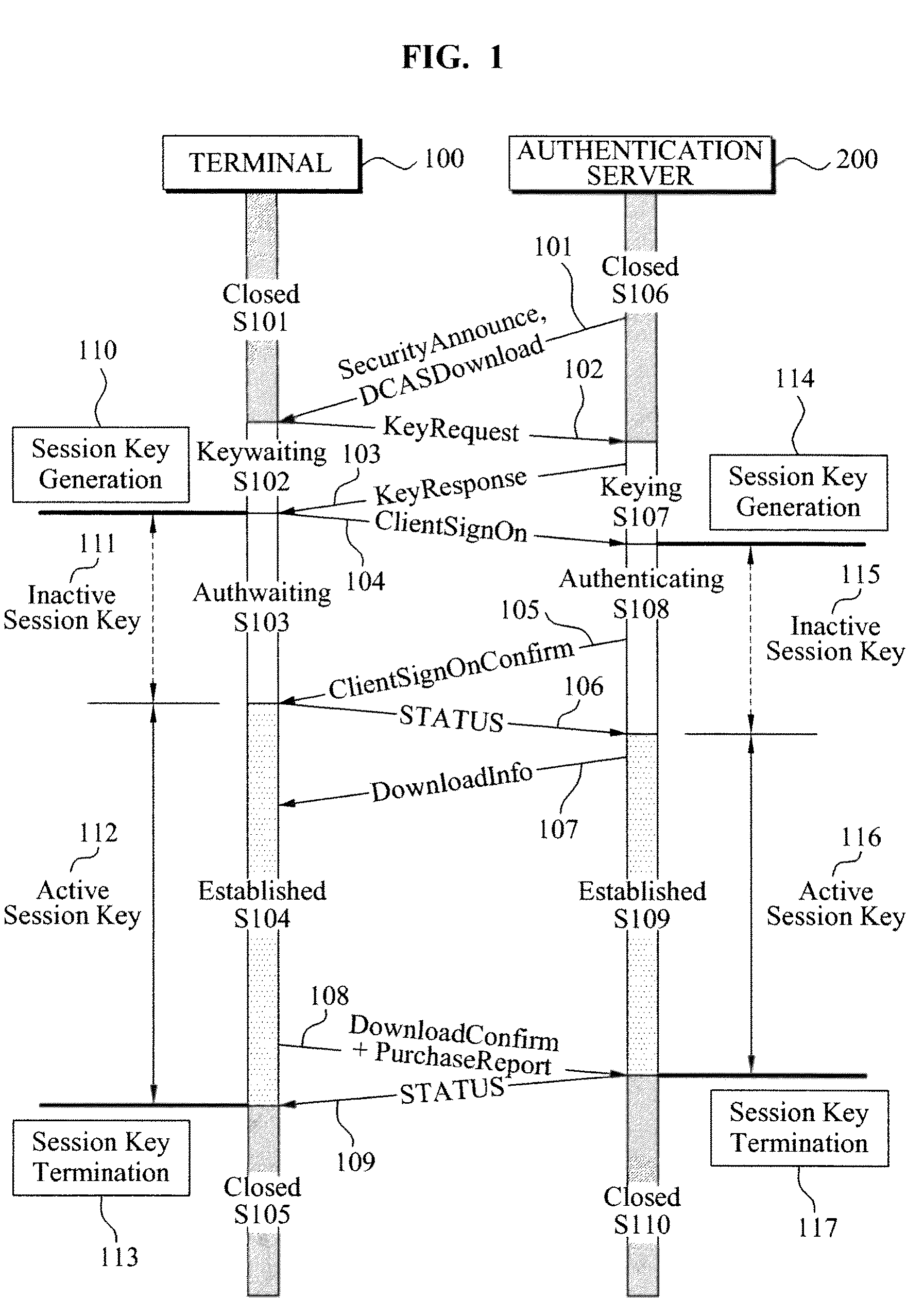
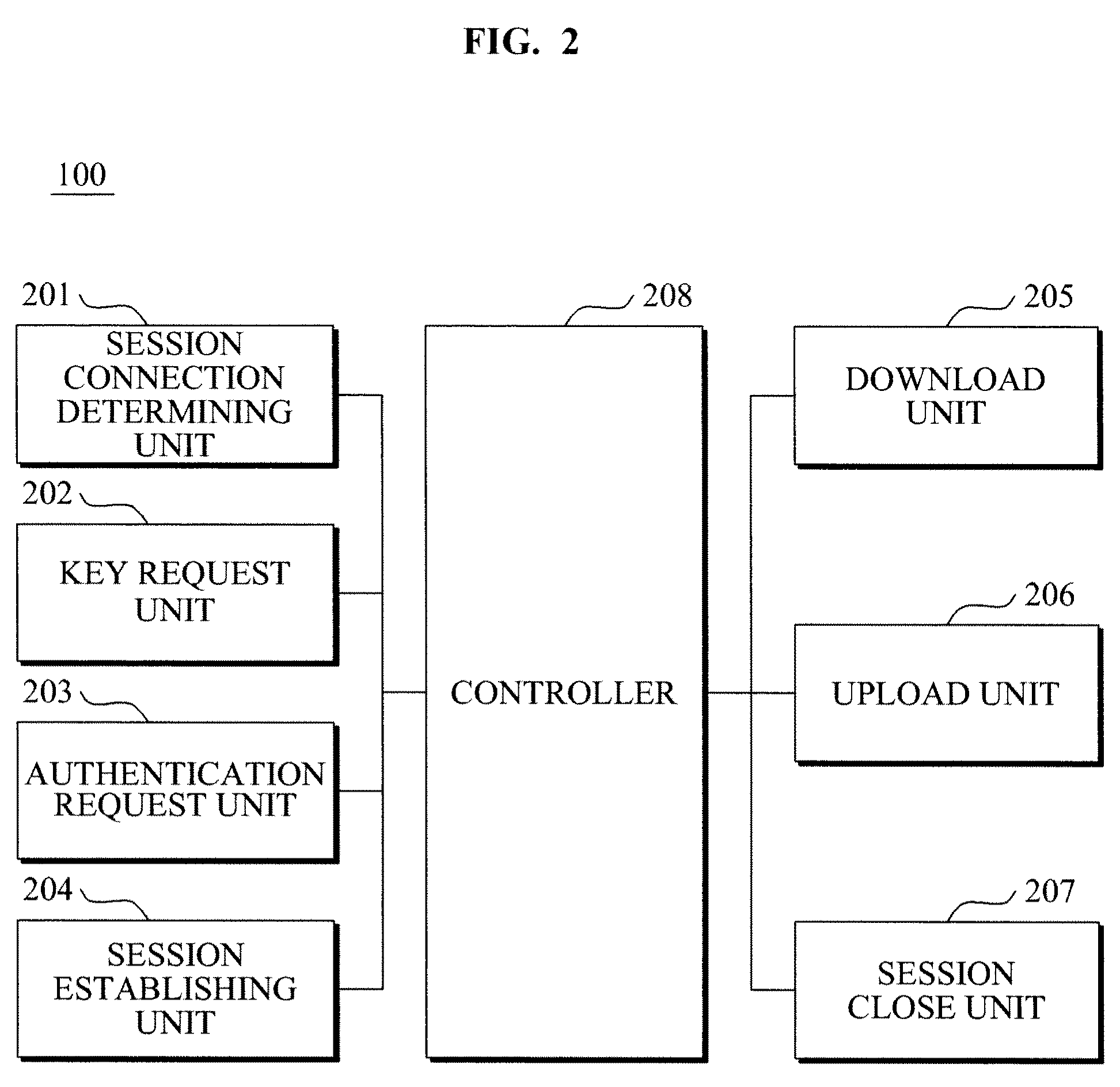
Downloadable conditional access system and method of session control for secured 2-way communication between authentication server and host device in downloadable conditional access system
InactiveUS8166298B2Generate efficientlyUser identity/authority verificationOperator-supported drilling machinesSession controlDownloadable Conditional Access System
Disclosed is a downloadable conditional access system (DCAS) including a key request unit to transmit a key request message to an authentication server, an authentication request unit to request authentication from the authentication server based on a key response message received from the authentication server in response to the key request message, and a session establishment unit to establish a session with the authentication server, based on an authentication response message received in response to the authentication request.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus of managing entitlement management message for supporting mobility of dcas host
InactiveUS20090138957A1Improve efficiencyReduce waste of resourcesUser identity/authority verificationData switching by path configurationPersonalizationDownloadable Conditional Access System
A method of supporting a mobility of a Downloadable Conditional Access System (DCAS) host is provided. The method includes: by the second authentication proxy server: performing mutual authentication with a secure micro of the host to generate a session key; requesting an integrated personalization system to download a secure micro client to the host, wherein the secure micro client is encoded using the session key; and transmitting, to a DPS, mapping information between the second authentication proxy server and the secure micro of the host, wherein, in response to receiving the mapping information, the DPS instructs a CAS server to transmit an entitlement management message to the network of the second authentication proxy server without transmitting the entitlement management message to the network of the first authentication proxy server.
Owner:ELECTRONICS & TELECOMM RES INST
Authenticated communication between security devices
ActiveUS9282106B2User identity/authority verificationTelevision systemsChannel state informationHash-based message authentication code
Apparatuses, computer readable media, and methods establishing and maintaining trust between security devices for distributing media content are provided. Two security devices bind to establish an initial trust so that security information can be exchanged. Subsequently, trust is refreshed to verify the source of a message is valid. In an embodiment, the security devices may comprise a security processor and a system on a chip (SoC) in a downloadable conditional access system. Trust may be refreshed by a security device inserting authentication information in a message to another security device, where authentication information may assume different forms, including a digital signature (asymmetric key) or a hash message authentication code (HMAC). Trust may also be refreshed by extracting header information from the message, determining state information from at least one parameter contained in the header information, and acting on message content only when the state information is valid.
Owner:COMCAST CABLE COMM LLC
Mobile IPTV service system using downloadable conditional access system and method thereof
InactiveUS9037848B2Key distribution for secure communicationDigital data processing detailsConditional access systemsDownloadable Conditional Access System
An apparatus and method associated with an Internet Protocol Television (IPTV) service in a mobile environment are provided. A streaming server may provide a mobile terminal with a mobile certificate and an encryption key. In response to a content request received from the mobile terminal, the streaming server may provide the mobile terminal with encrypted content and a Downloadable Conditional Access System (DCAS) code. The mobile terminal may decrypt the encrypted content using the encryption key and the DCAS code, and may play back the decrypted content.
Owner:INTELLECTUAL DISCOVERY CO LTD
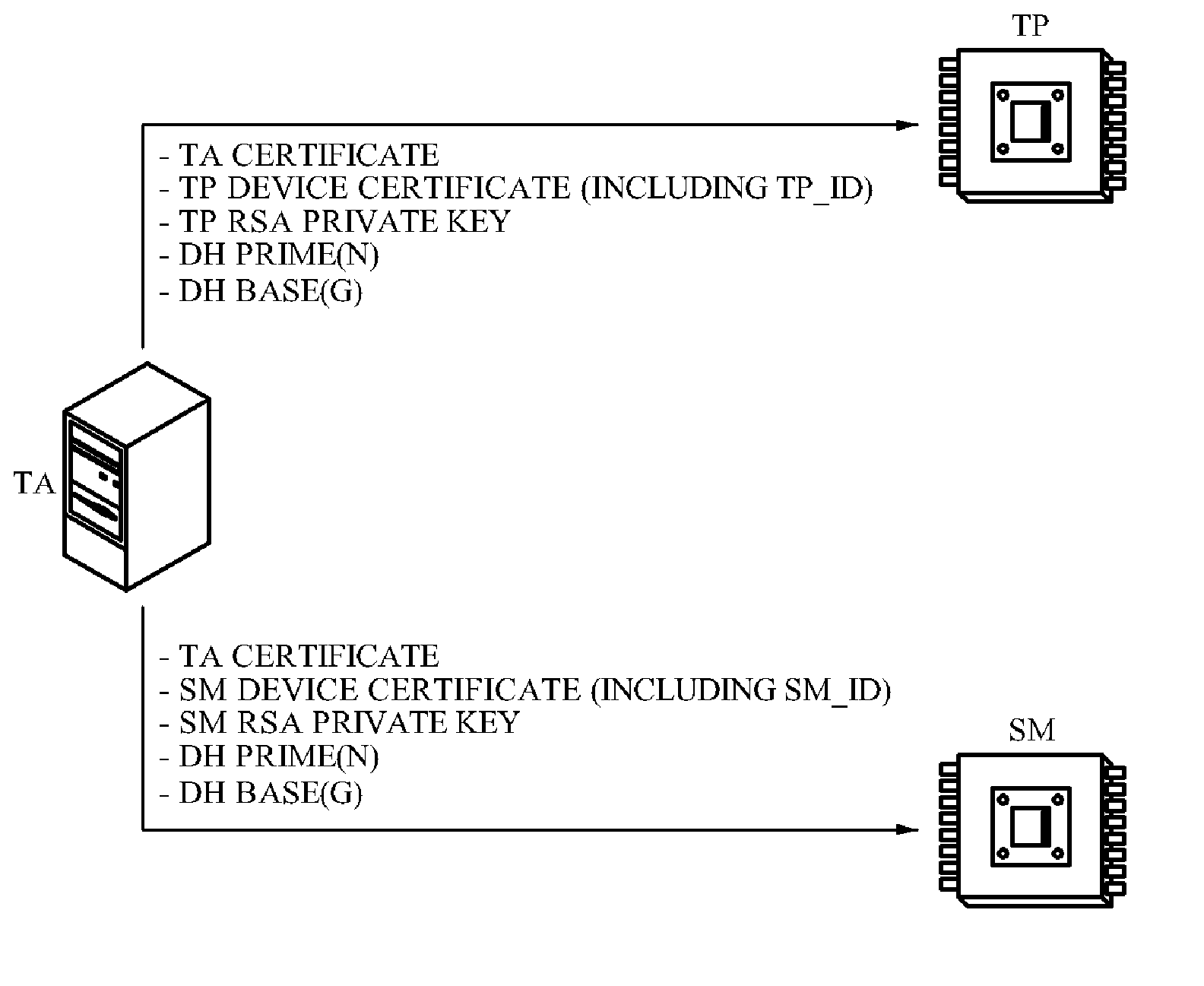
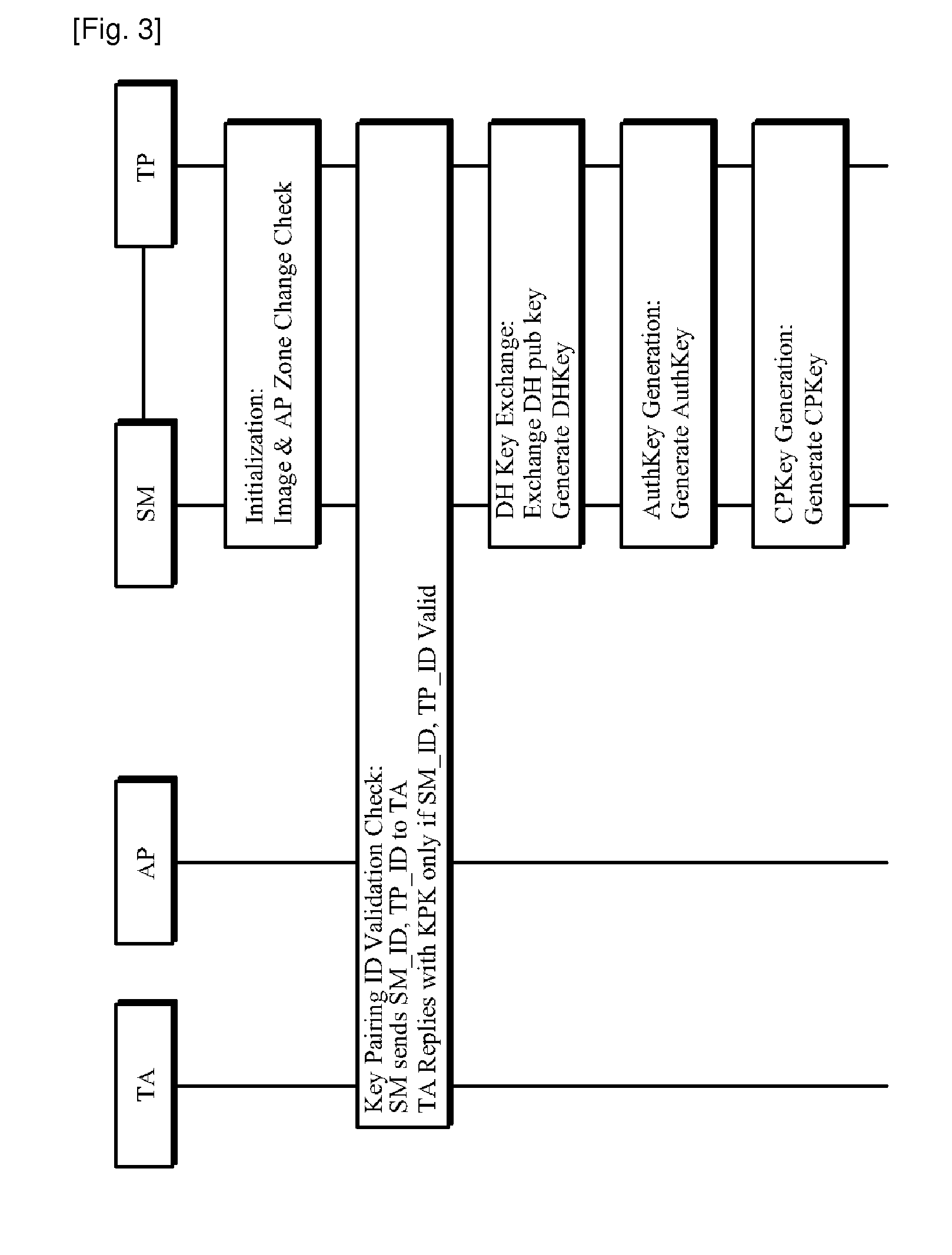
Paring method between sm and tp in downloadable conditional access system, set-top box and authentication device using this
InactiveUS20110051933A1Safer pairingAvoid connectionTelevision system detailsKey distribution for secure communicationTrusted authorityDownloadable Conditional Access System
The present invention relates to a technology of paring a secure micro (SM) and a transport processor (TP) in a downloadable conditional access system (DCAS). More specifically, predetermined security components generated by a trusted authority which is a certificate authority are previously embedded into the SM and the TP, and pairing between the SM and the TP is performed by association of the security components with the TA. Accordingly, safe pairing can be assured and the leakage of security information from the SM by malicious hacking can be prevented.
Owner:ELECTRONICS & TELECOMM RES INST
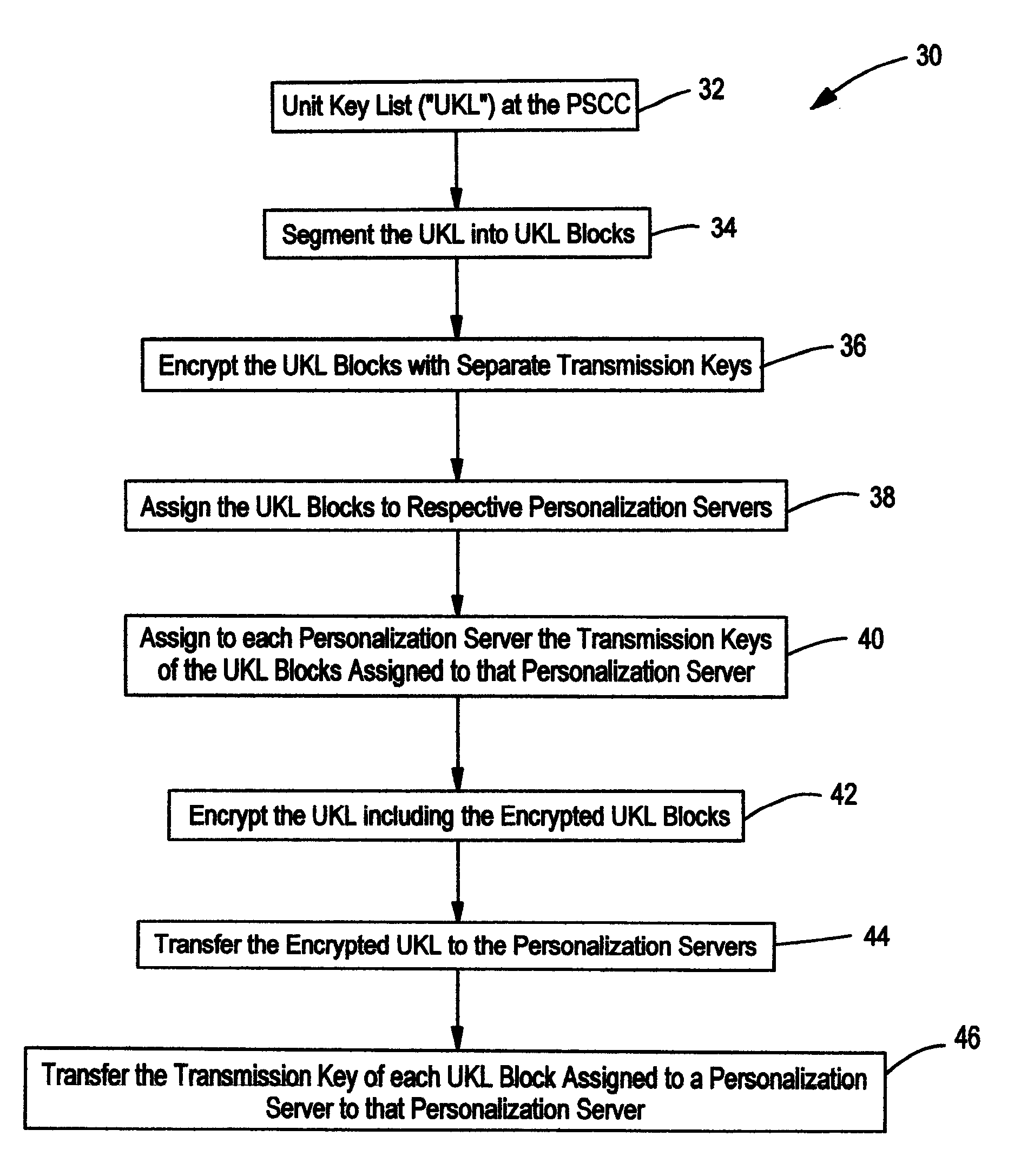
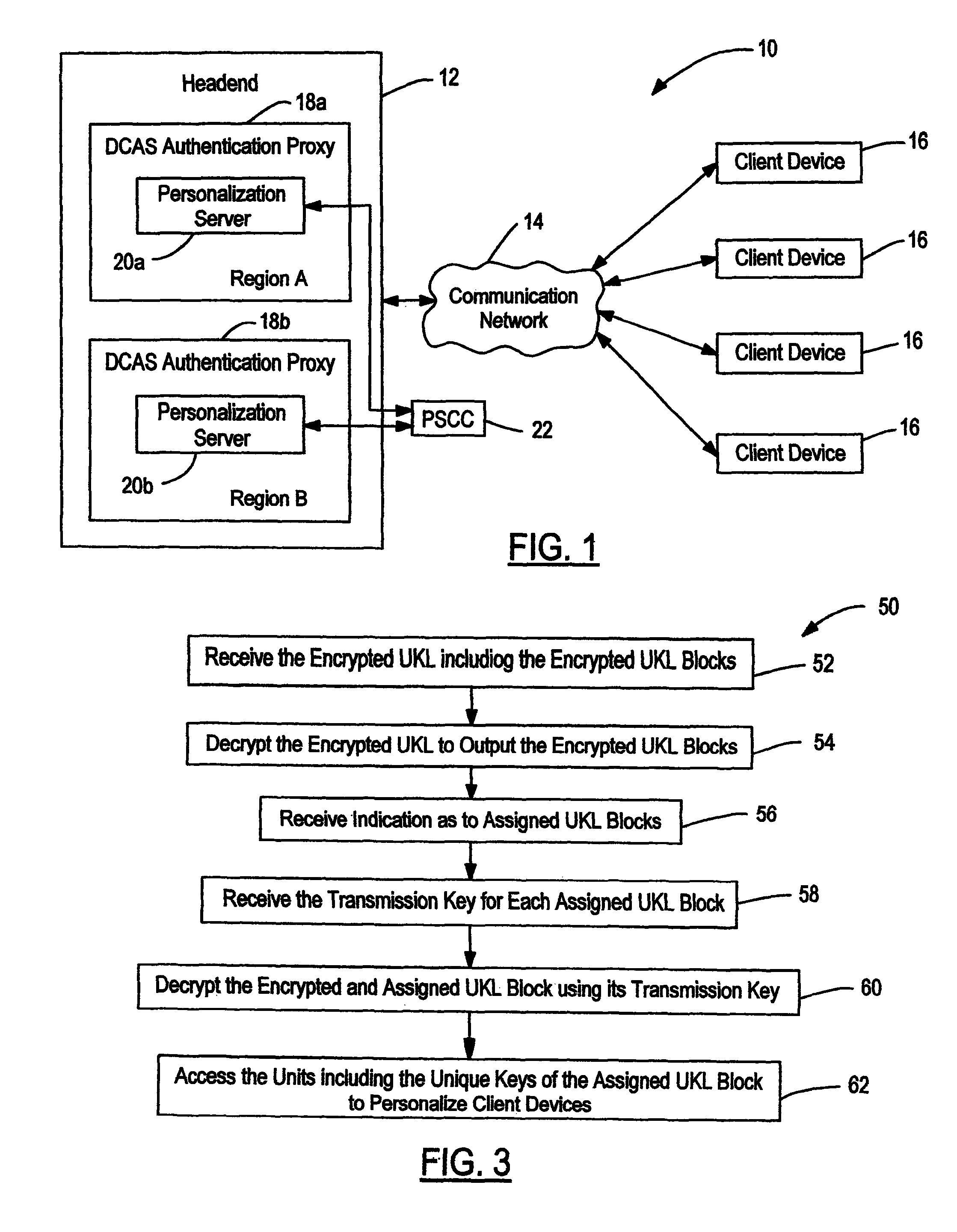
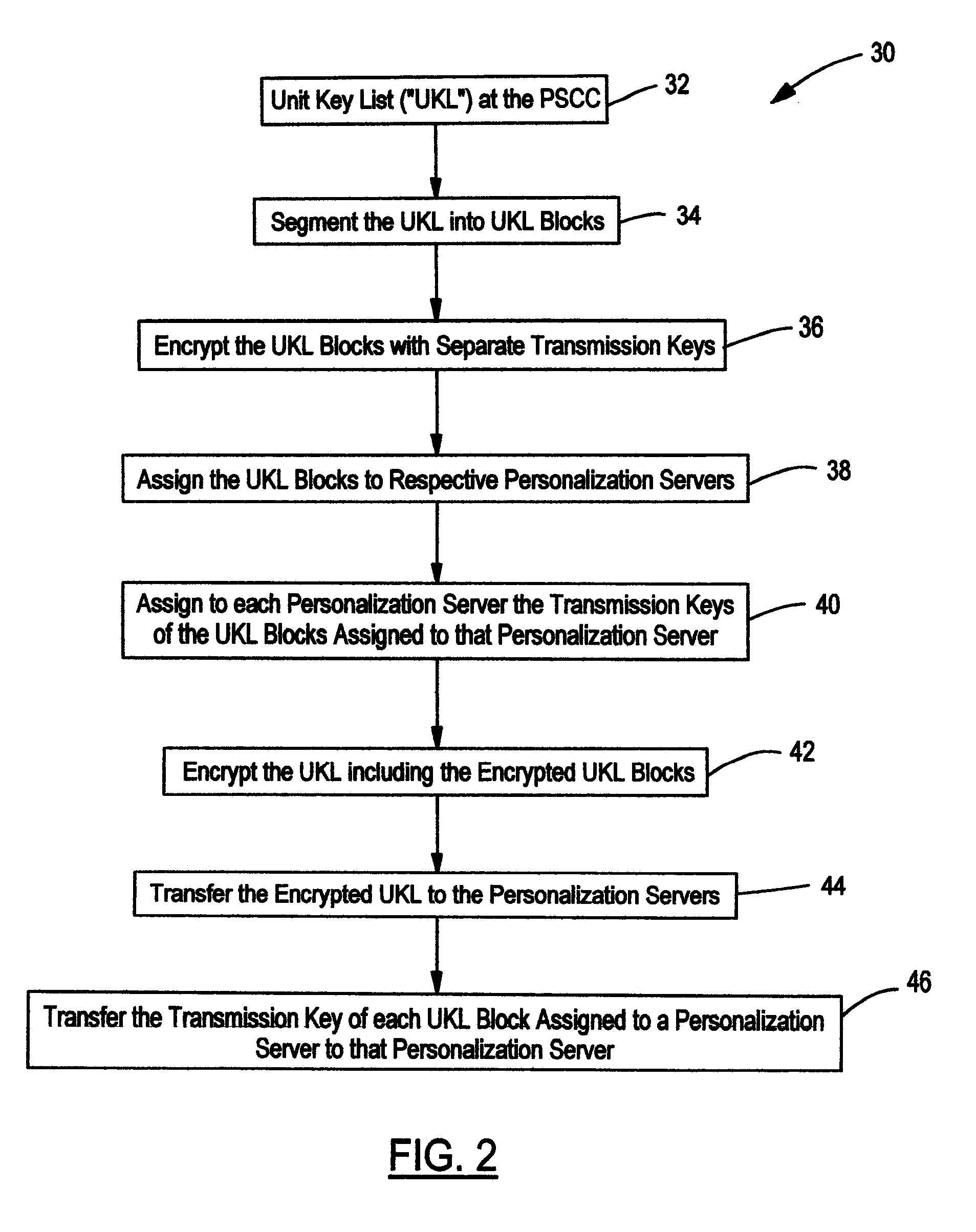
Content delivery with segmented key list
ActiveUS8385555B2Key distribution for secure communicationMultiple keys/algorithms usageDownloadable Conditional Access SystemConditional access systems
A content delivery network and method employing a Downloadable Conditional Access System (“DCAS”) includes first and second personalization servers. A unit key list having unique keys is segmented into different blocks. Each block is encrypted with a separate transmission key corresponding to that block such that first and second blocks are respectively encrypted with first and second transmission keys. The encrypted blocks are communicated to the personalization servers. The first transmission key is communicated to the first personalization server without being communicated to another personalization server such that the first server can decrypt the first block using the first transmission key to access the keys of the first block. The second transmission key is communicated to the second personalization server without being communicated to another personalization server such that the second server can decrypt the second block using the second transmission key to access the keys of the second block.
Owner:COMBINED CONDITIONAL ACCESS DEV & SUPPORT
Apparatus and method for mutual authentication in downloadable conditional access system
InactiveUS20100235626A1User identity/authority verificationTelevision systemsTrusted authorityProtocol processing
A mutual authentication apparatus in a Downloadable Conditional Access System (DCAS) includes an announce protocol processor to authenticate SecurityAnnounce information using an Authentication Proxy (AP) and to transmit the authenticated SecurityAnnounce information to a Secure Micro (SM), a keying protocol processor to relay KeyRequest information and KeyResponse information between a Trusted Authority (TA) and the SM in response to the SecurityAnnounce information, a decryption unit to decrypt the KeyResponse information using the SM, an authentication protocol processor to determine whether a first encryption key of the KeyResponse information is identical to a second encryption key generated by the AP, and a download protocol processor to control DownloadInfo to be transmitted from the AP to the SM, the DownloadInfo permitting the SM to download SM Client Image information.
Owner:ELECTRONICS & TELECOMM RES INST
Method and apparatus for detecting downloadable conditional access system host with duplicated secure micro
ActiveUS8490155B2Efficiently determinedDigital data processing detailsAnalogue secracy/subscription systemsDownloadable Conditional Access SystemConditional access systems
Owner:ELECTRONICS & TELECOMM RES INST
Method of controlling download load of secure micro client in downloadable conditional access system
ActiveUS8260919B2Improve securityEffective controlMultiple digital computer combinationsDigital data authenticationDownloadable Conditional Access SystemConditional access systems
A method of controlling a download load of a Secure Micro (SM) client in a Downloadable Conditional Access System (DCAS) is provided. The method of controlling a download load of an SM client including: analyzing version information of SMs and version information of SM clients to control the download load generated in the DCAS, the version information of the SMs and the version information of the SM clients being provided from an Authentication Proxy (AP) server, and the SM clients being installed in the SMs; determining a download policy associated with a download time of a target SM client for the SMs based on a result of the analysis; and providing the AP server with the determined download policy.
Owner:ELECTRONICS & TELECOMM RES INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com