Real-time speech secret communication system based on information hiding
A technology of information hiding and secure communication, which is applied in the field of real-time voice secure communication system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
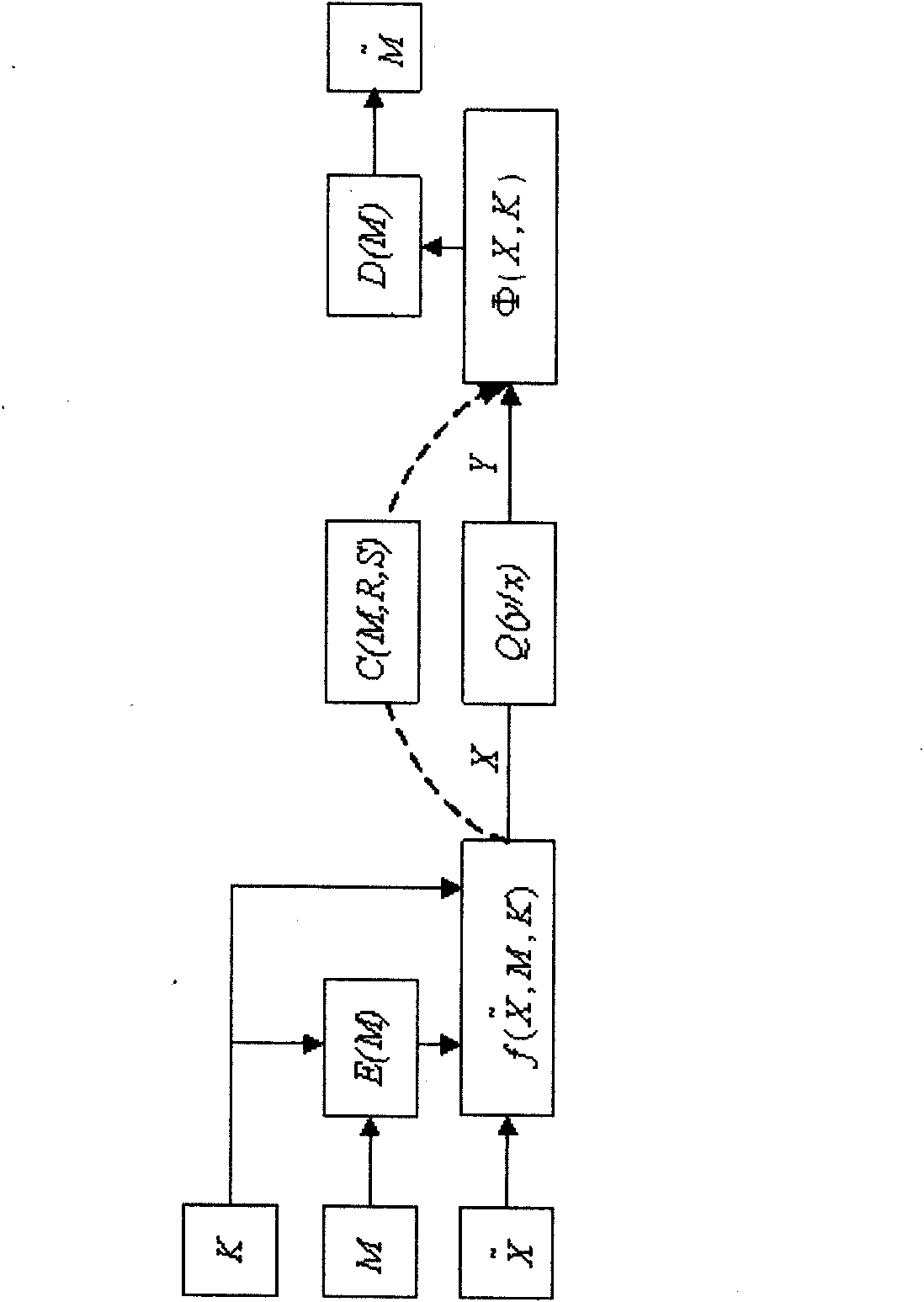
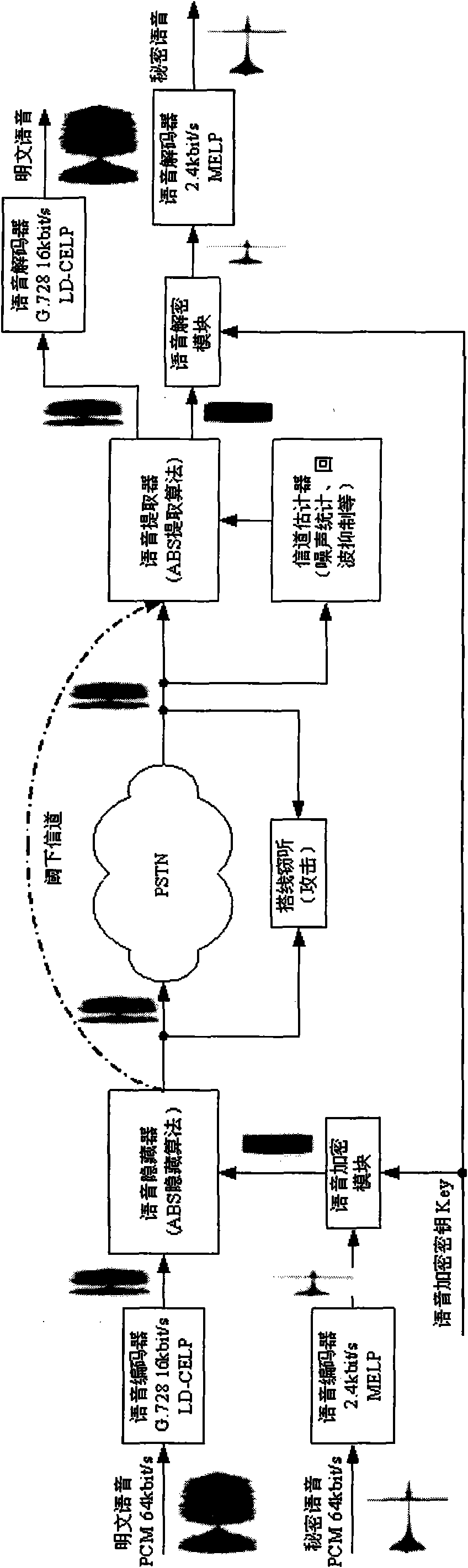
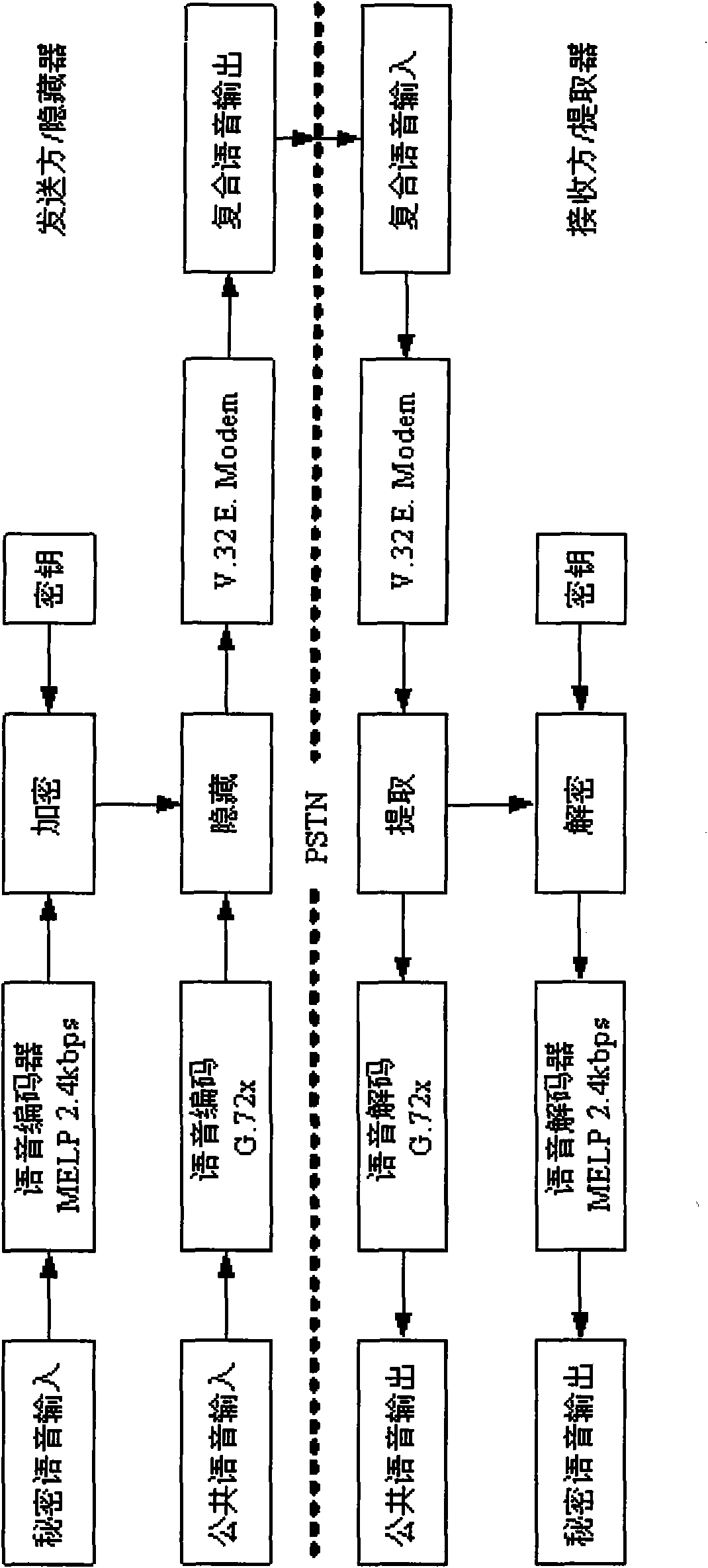
[0079] The development of secure communication system based on information hiding technology is a two-way full-duplex communication mode realized in the VC++ environment. The application platform is WindowsXP, and the code of the key algorithm is implemented by standard C, which is easy to be transplanted to the DSP hardware platform.
[0080] 1) Technical indicators
[0081] Technical indicators mainly include: communication rate, delay and bit error rate, etc.
[0082] (1) Communication rate
[0083] In the voice information hiding and confidential communication system, the voice signal sampling rate is 8kbps, and each frame of the transmitted voice signal is 20ms (160 points), which is divided into 4 subframes (each subframe is 5ms). In order to ensure the real-time performance of voice communication, The data communication rate is required to be greater than 12.8kbps.
[0084] (2) Delay
[0085] The requirement for delay can only be a theoretical estimate, and the calc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com