Method for realizing network and card locking function of terminal and terminal
A terminal and functional technology, which is applied in the field of realizing the function of terminal card lock and card lock, can solve the problems of algorithm loopholes, tampering programs, and low security of card lock card function, so as to achieve the effect of improving confidentiality and protecting interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
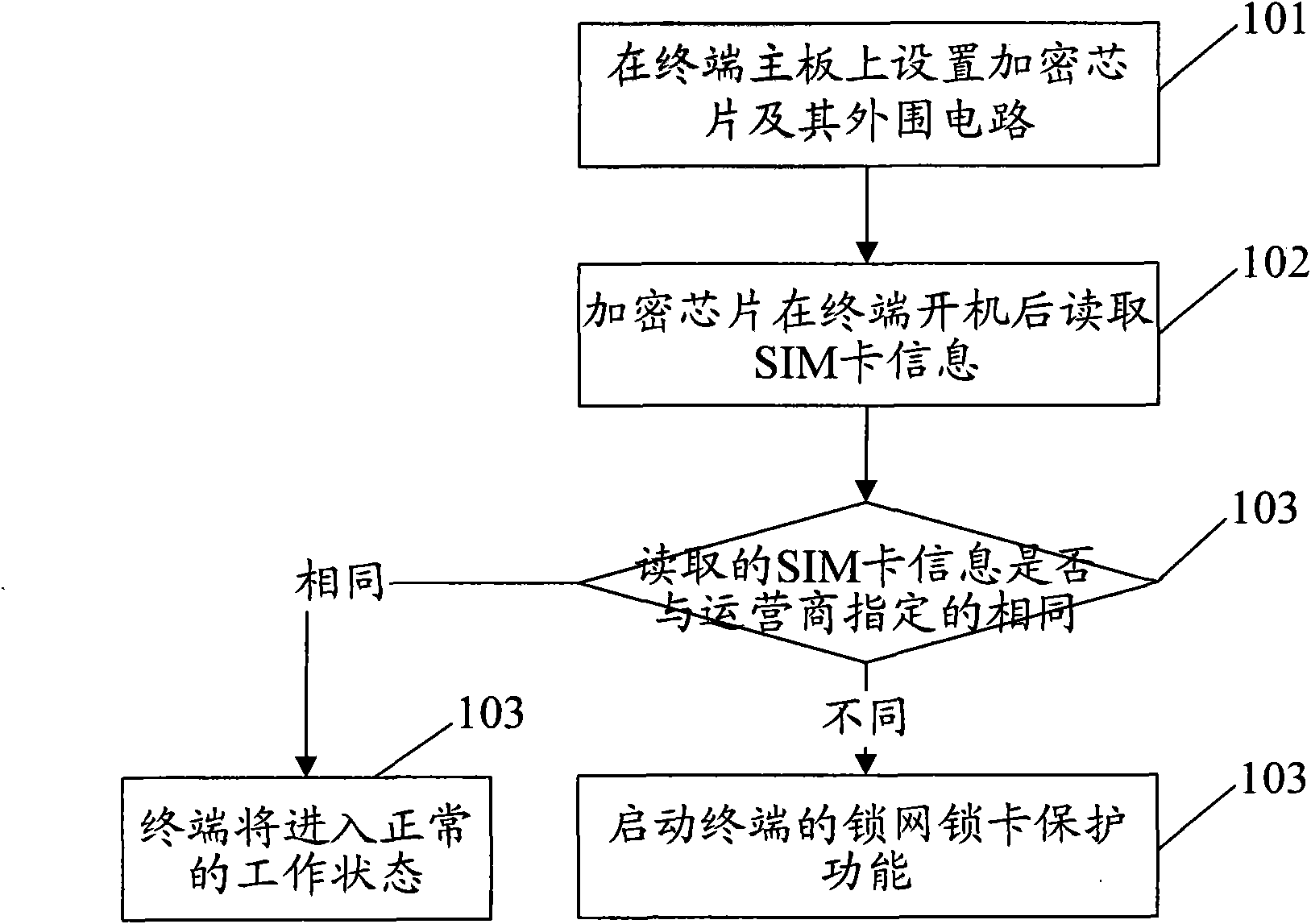
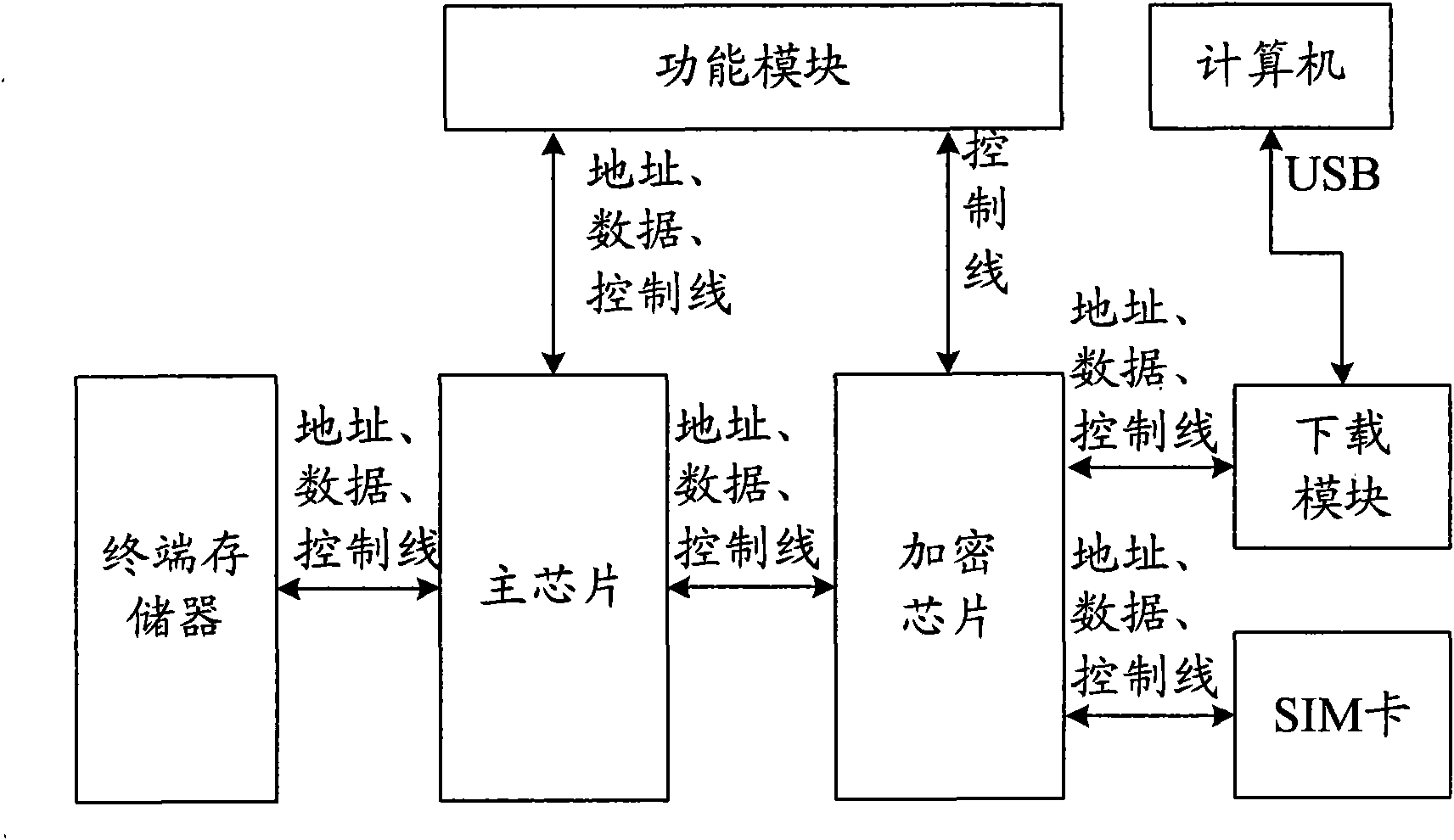
[0028] The basic idea of the present invention is: an encryption chip and its peripheral circuits are set on the main board of the terminal, and the encryption chip reads the SIM card information after the terminal is turned on, and judges whether the read SIM card information is consistent with the stored information of the operator. The SIM card information is the same, and when it is determined that the read SIM card information is different from the stored SIM card information, the network lock card lock protection function of the terminal is activated.
[0029] Wherein, in the process of judging whether the read SIM card information is the same as the stored SIM card information specified by the operator, when it is determined that the read SIM card information is the same as the stored SIM card information, the terminal will enter the normal state. working status.
[0030] In the present invention, the SIM card information includes: Mobile Country Code (MCC), Mobile Ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com