Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Incident analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An incident analysis involves gathering facts by inspecting the incident scene, interviewing witnesses, reviewing documentation, and analyzing those facts to determine the causal factors. The causal analysis is easier and more effective when it is done in two phases, a primary event analysis and a causal factor analysis.
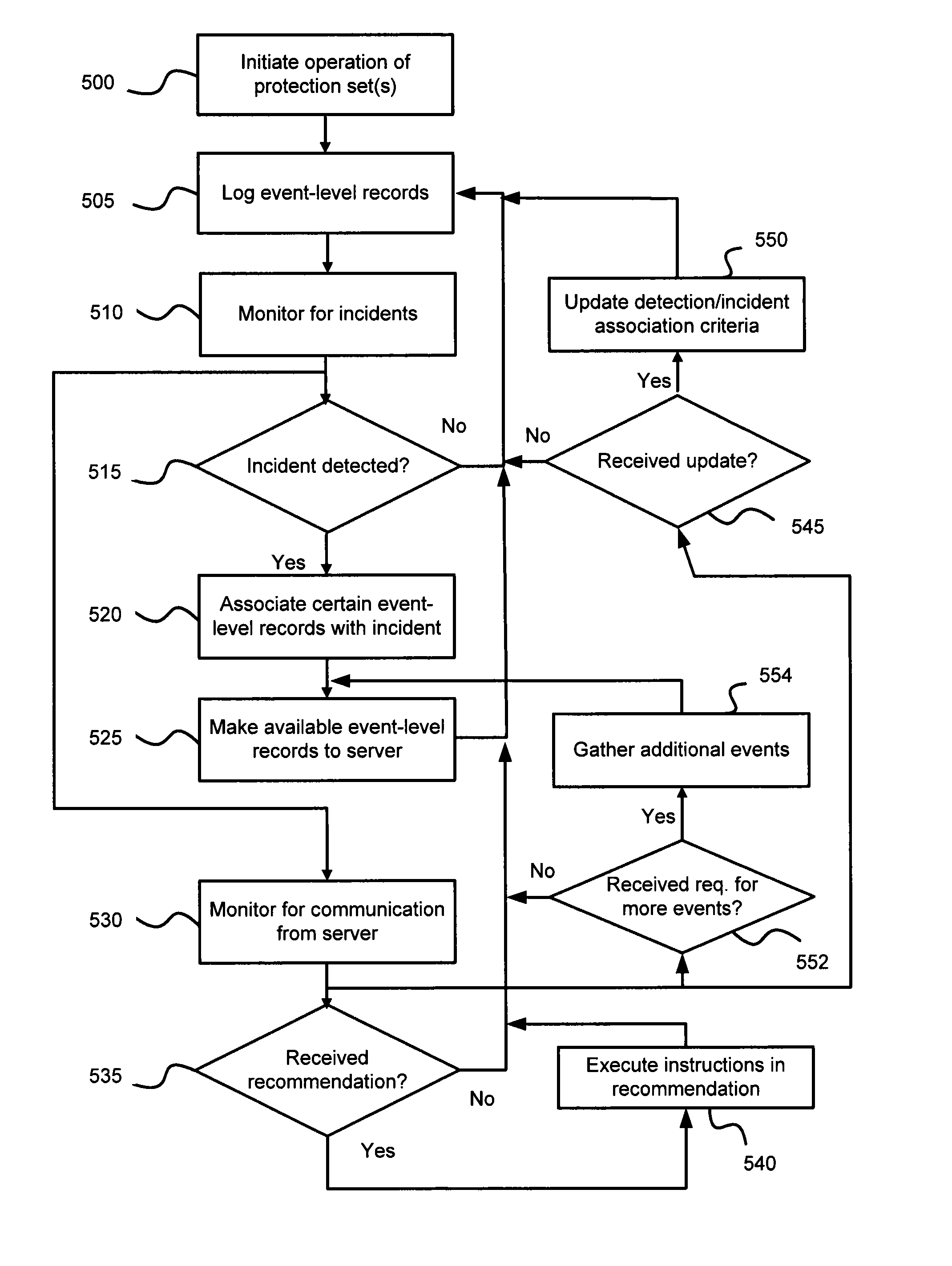
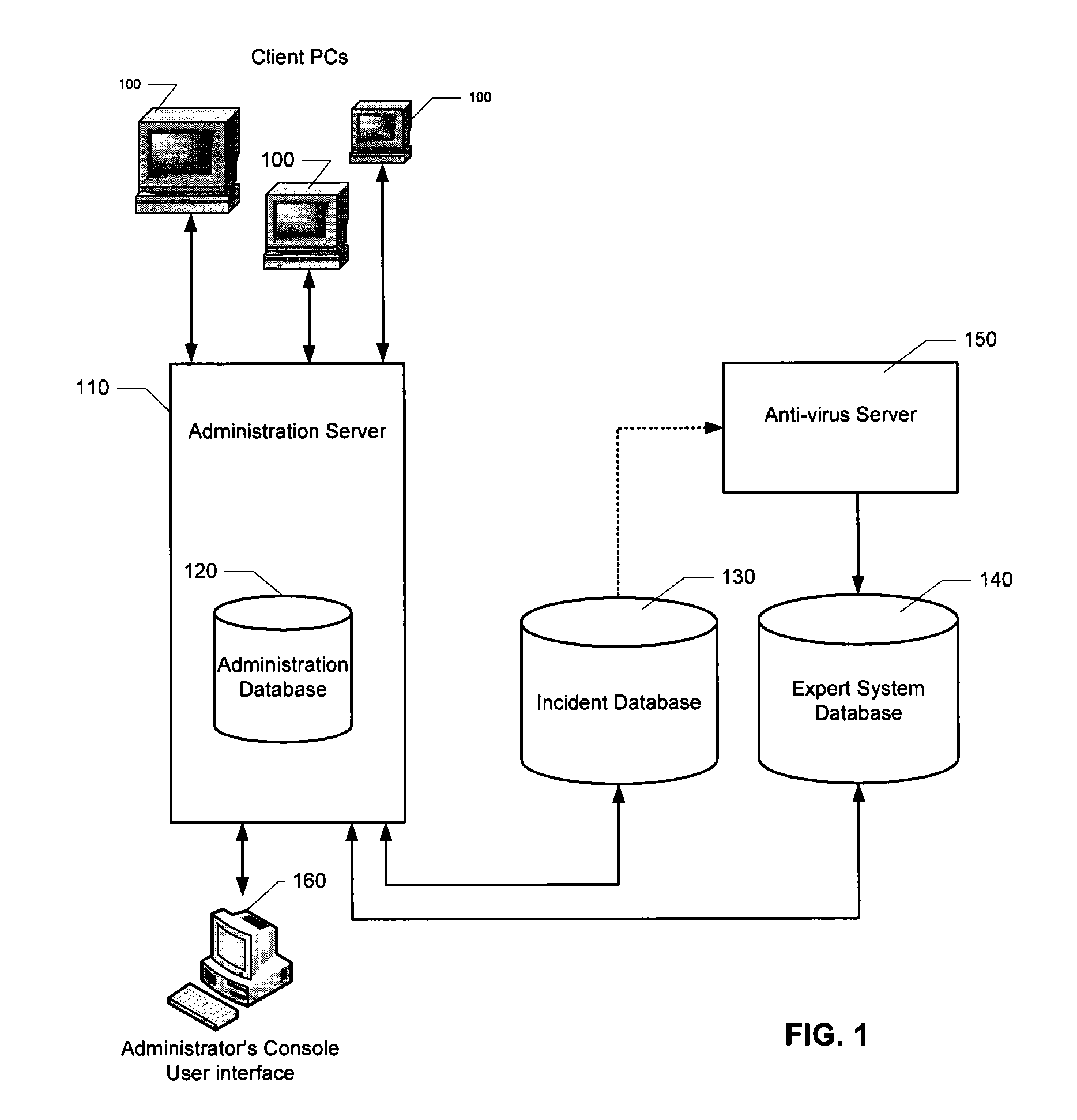
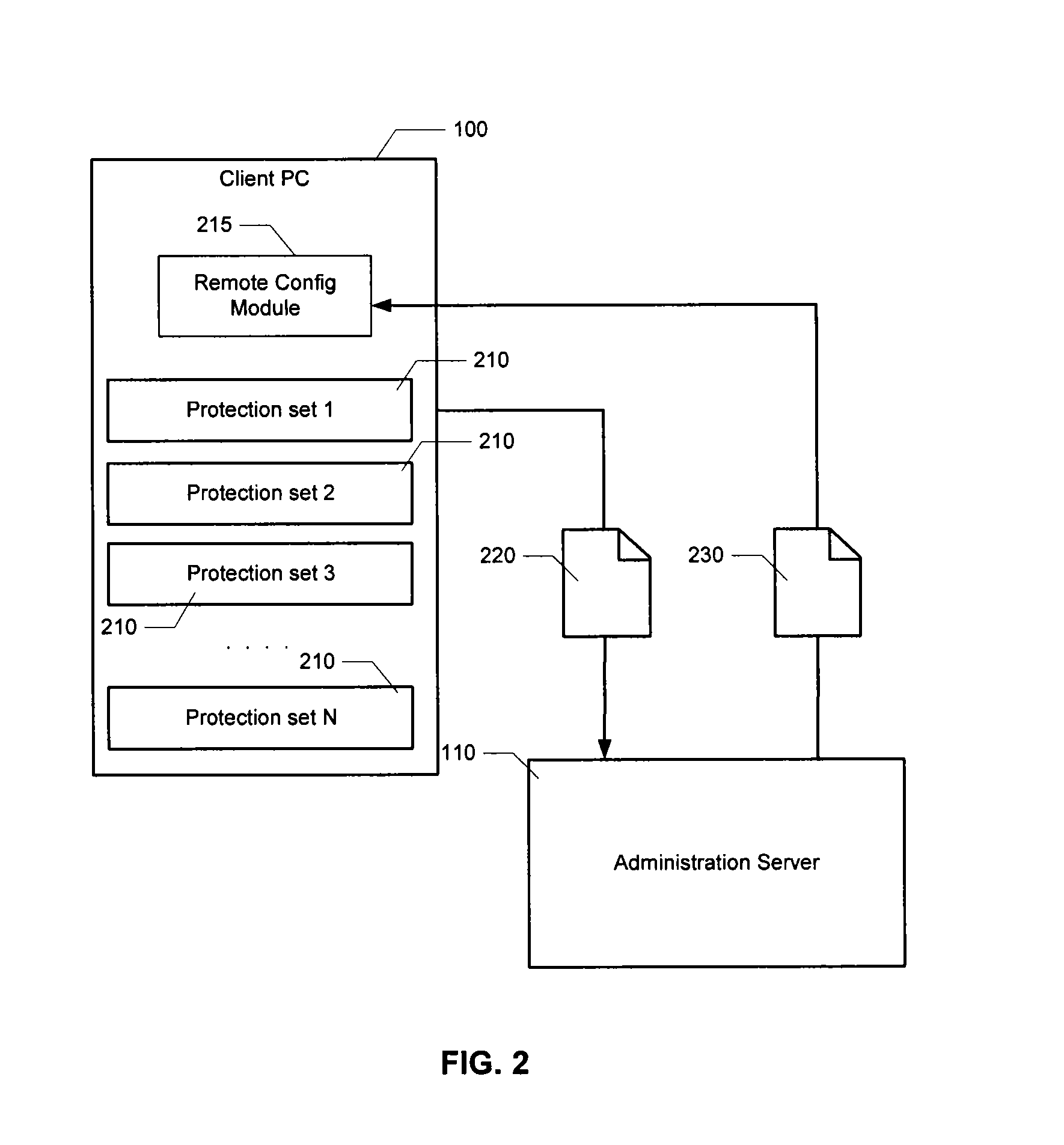
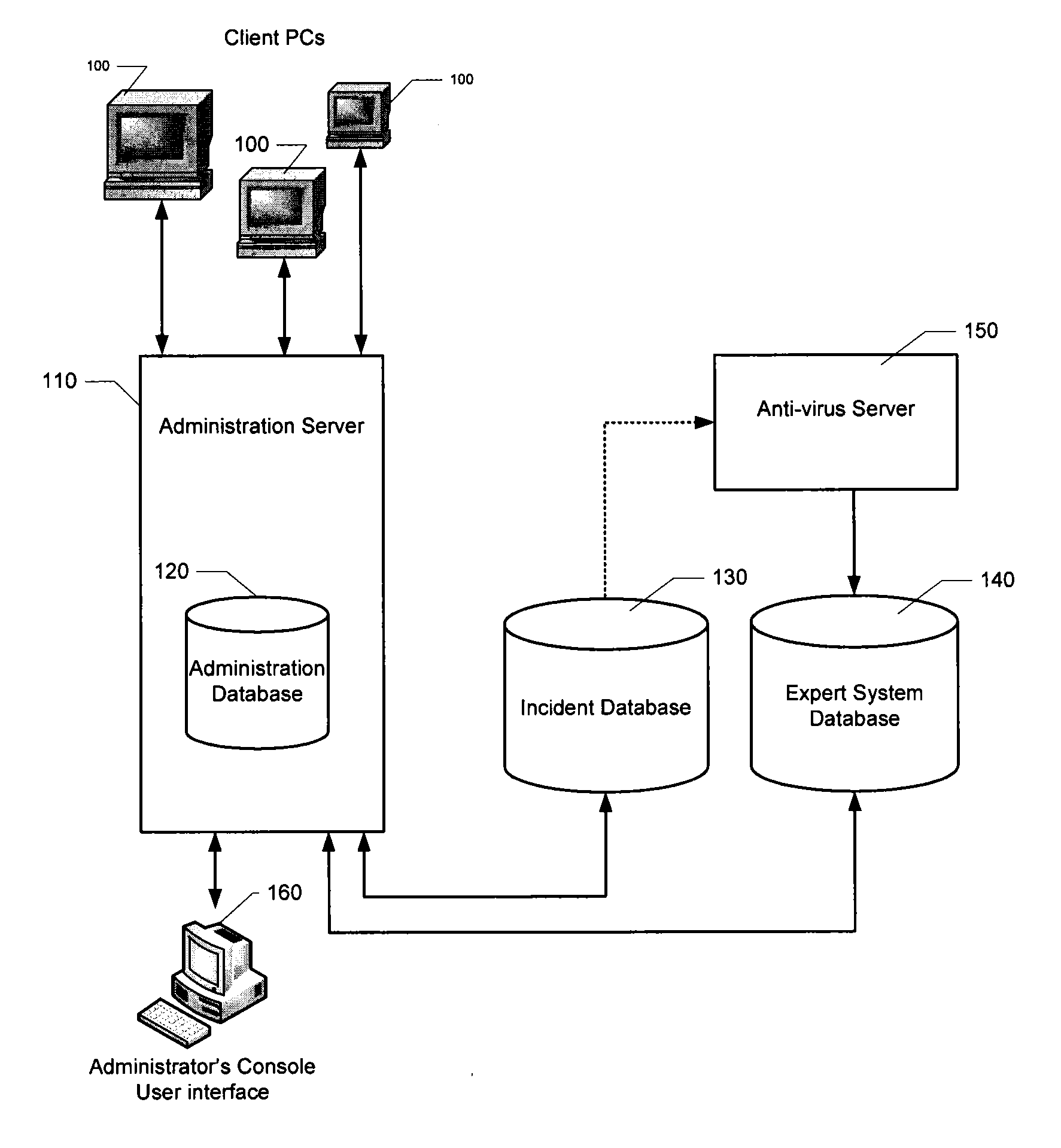
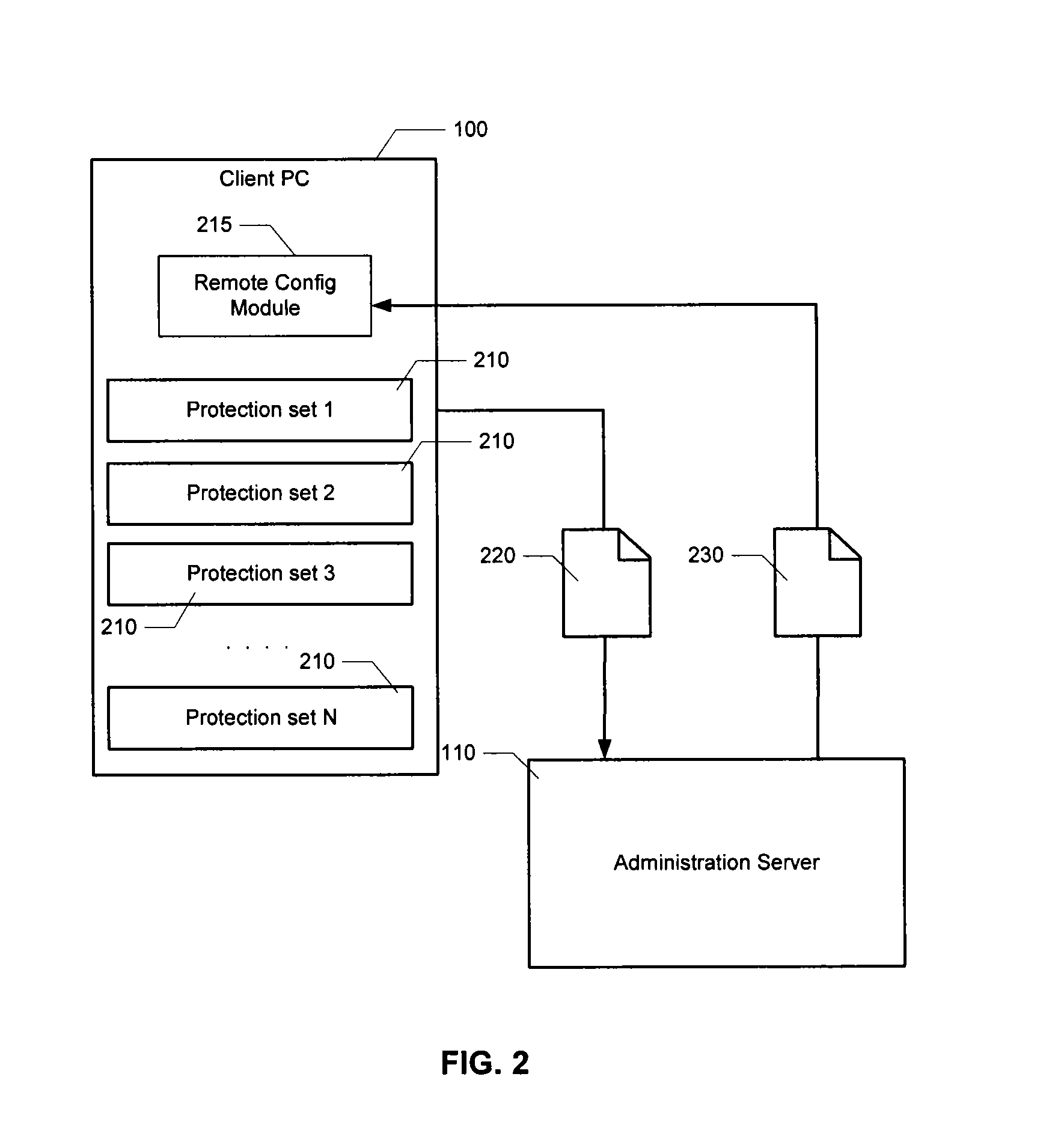
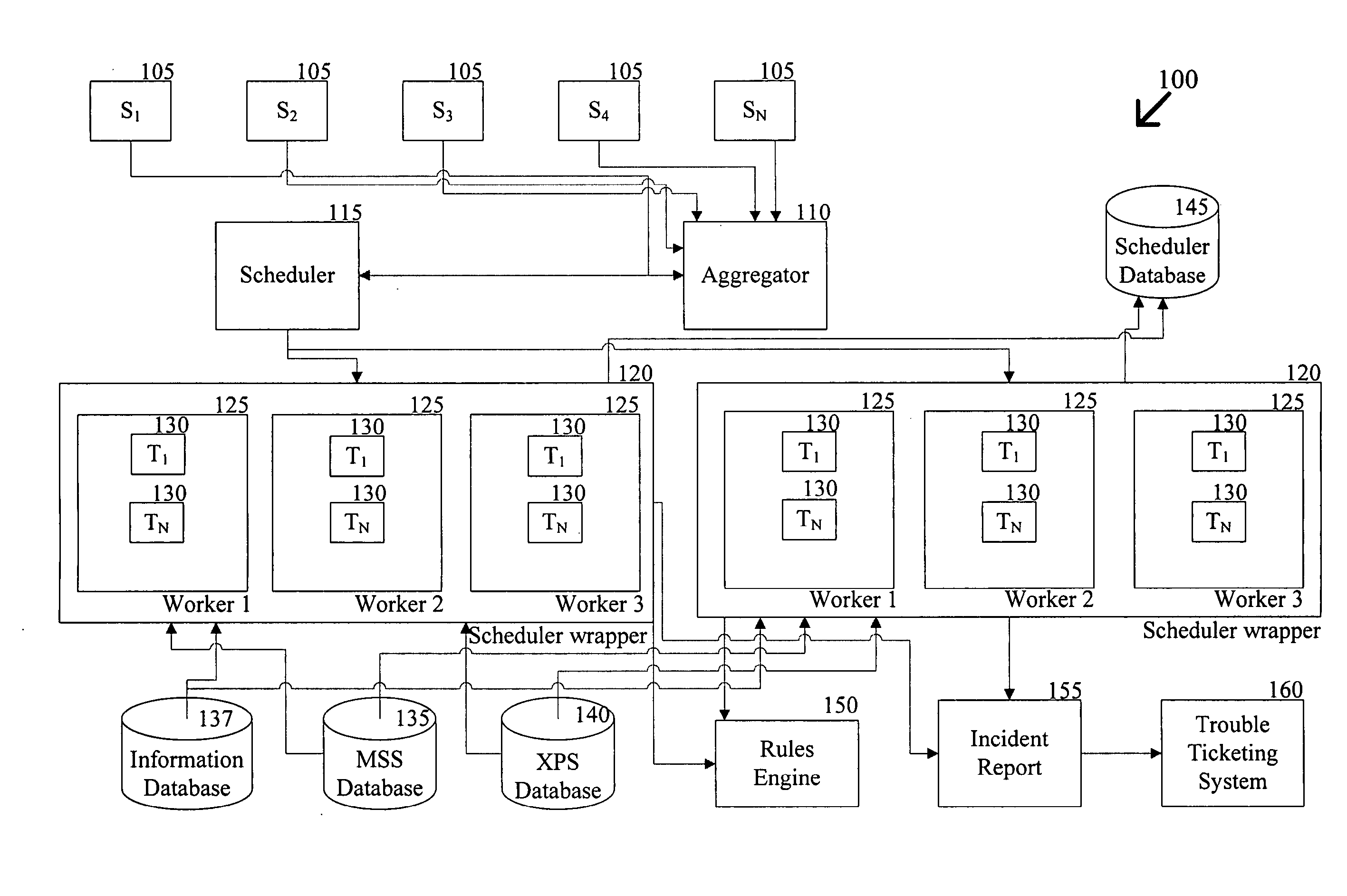
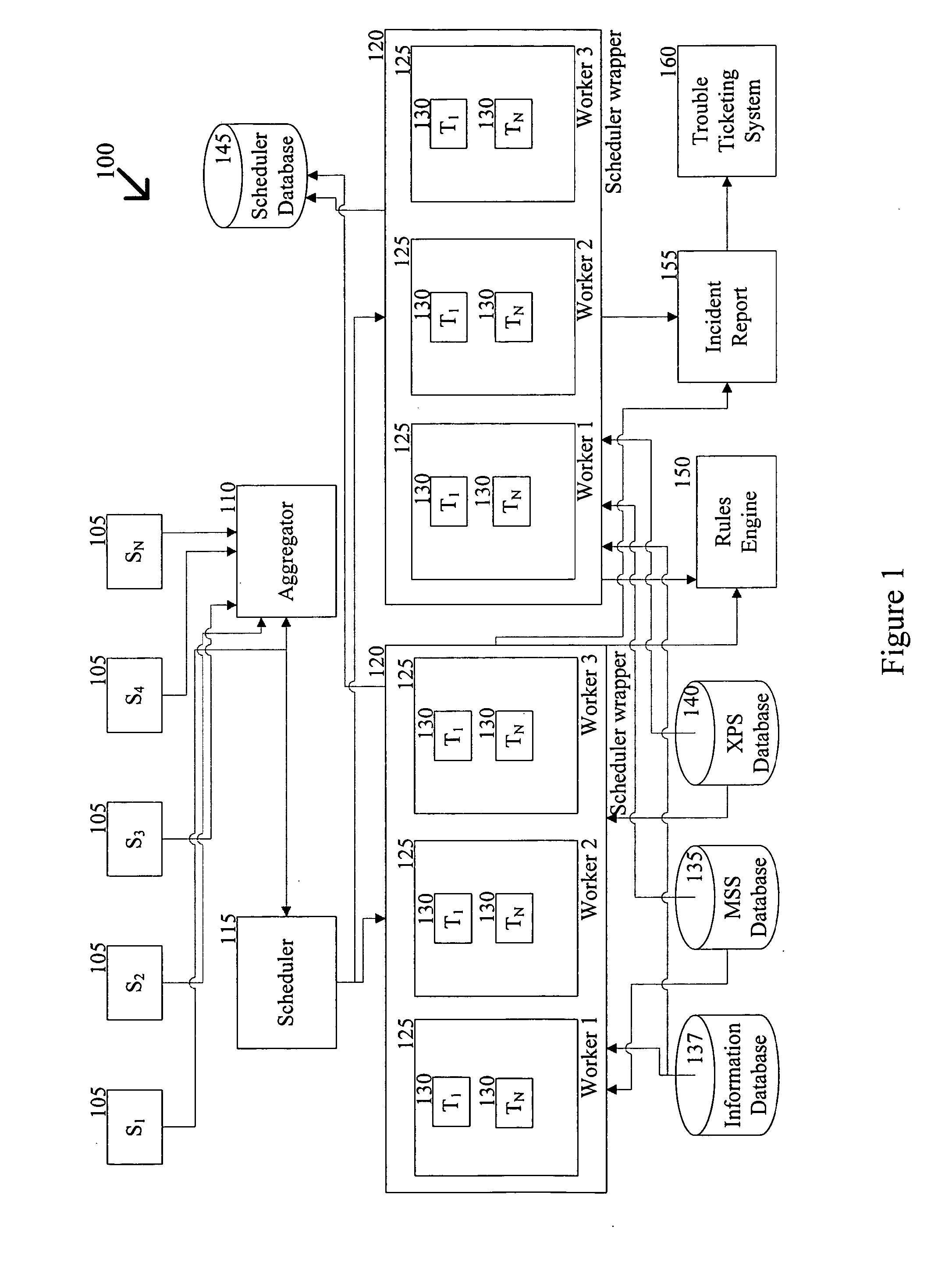
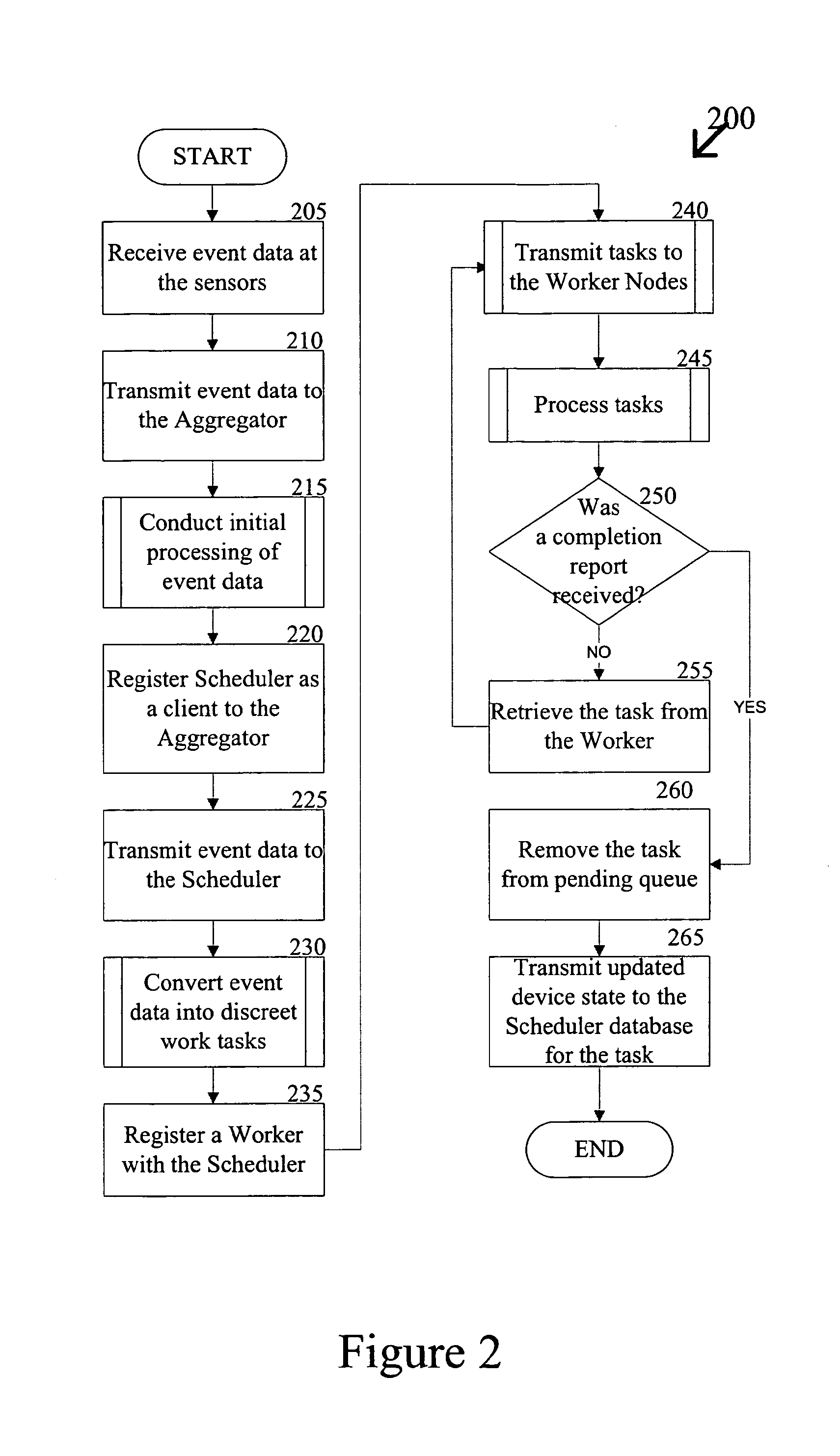
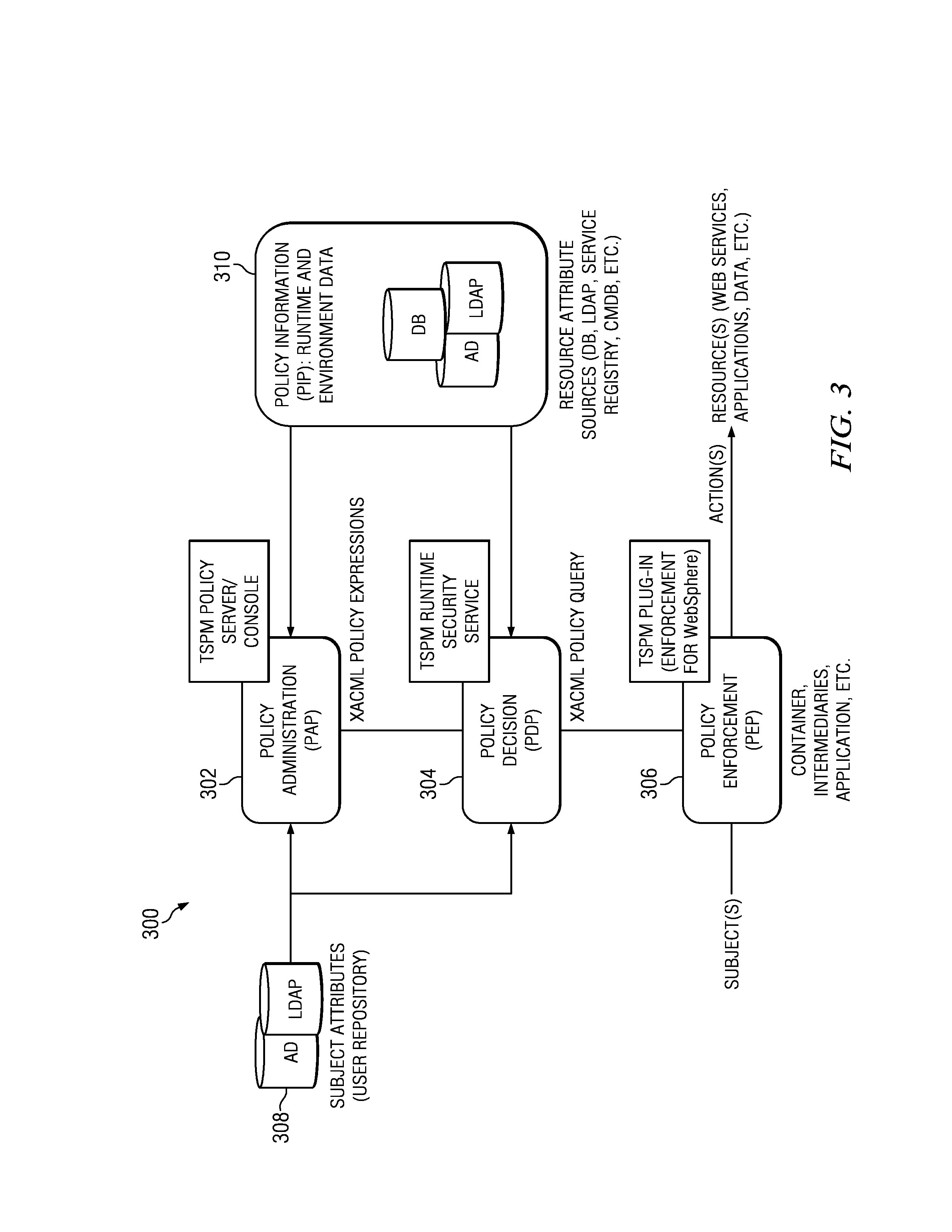
Automatic analysis of security related incidents in computer networks
ActiveUS8776241B2Shorten the timePrevent relapseMemory loss protectionError detection/correctionEvent levelRelevant information
Owner:AO KASPERSKY LAB
Automatic analysis of security related incidents in computer networks
ActiveUS20130055399A1Reduce time spent on investigatingEasy to detectMemory loss protectionError detection/correctionEvent levelChain of events
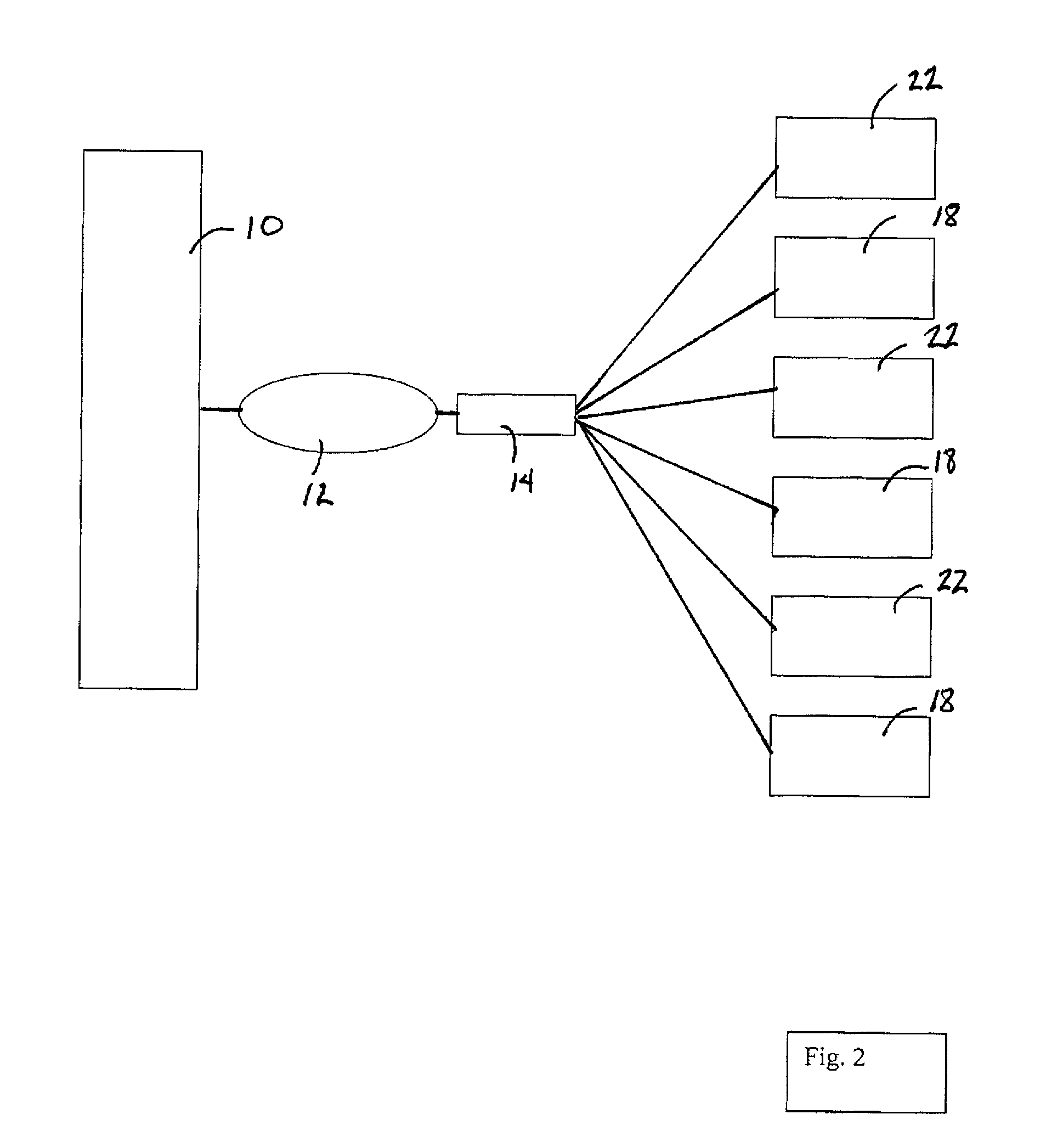
Solutions for responding to security-related incidents in a computer network, including a security server, and a client-side arrangement. The security server includes an event collection module communicatively coupled to the computer network, an event analysis module operatively coupled to the event collection module, and a solution module operatively coupled to the event analysis module. The event collection module is configured to obtain incident-related information that includes event-level information from at least one client computer of the plurality of client computers, the incident-related information being associated with at least a first incident which was detected by that at least one client computer and provided to the event collection module in response to that detection. The event analysis module is configured to reconstruct at least one chain of events causally related to the first incident and indicative of a root cause of the first incident based on the incident-related information. The solution module is configured to formulate at least one recommendation for use by the at least one client computer, the at least one recommendation being based on the at least one chain of events, and including corrective / preventive action particularized for responding to the first incident.
Owner:AO KASPERSKY LAB
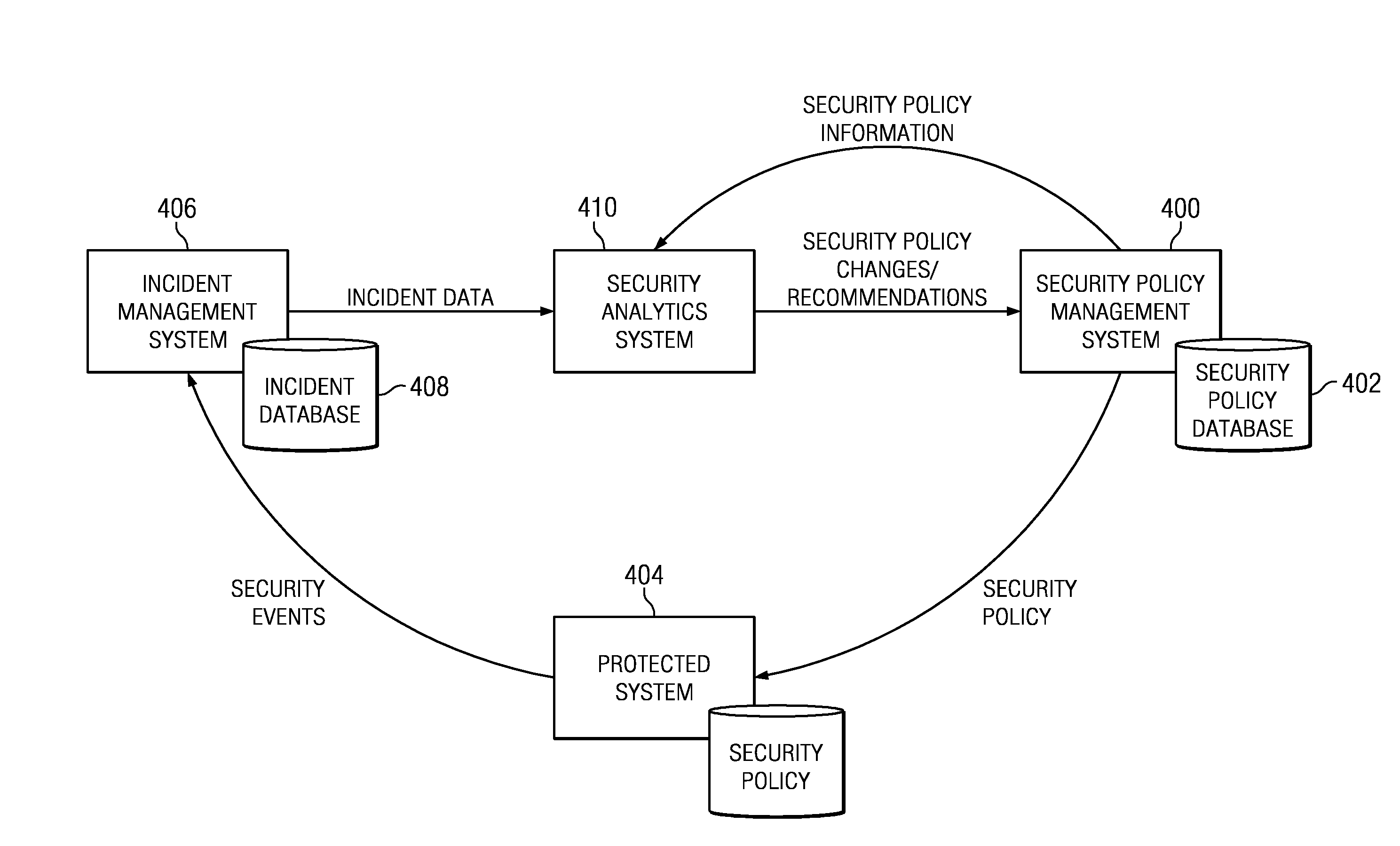
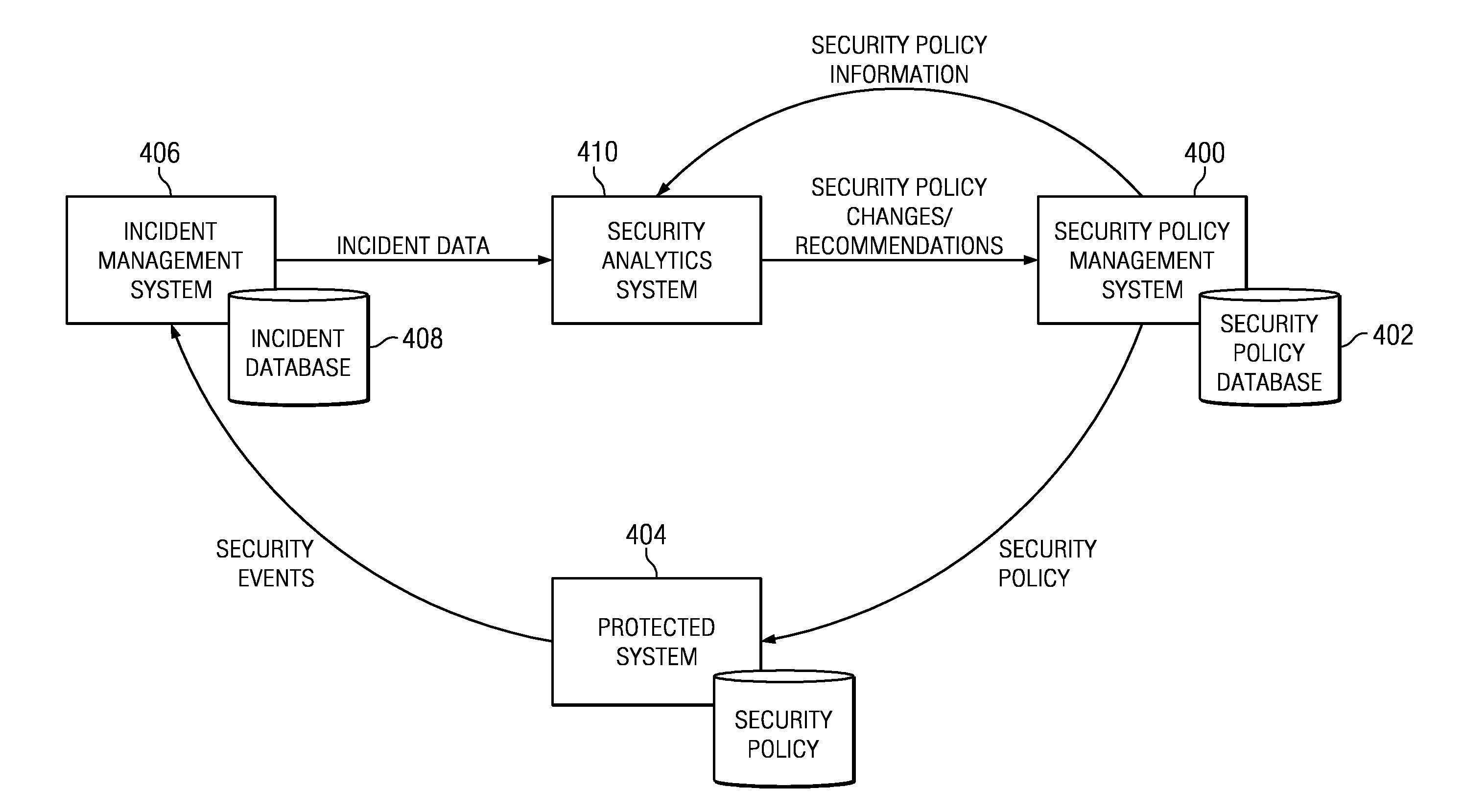
Security policy management using incident analysis
InactiveUS20130179938A1Understand perceived and measured effectiveness and costReduce in quantityError detection/correctionForecastingData setIncident analysis
A security analytics system receives incident data (from an incident management system) and security policy information (from a security policy management system). The security analytics system evaluates these data sets against one another, preferably using a rules-based analysis engine. As a result, the security analytics system determines whether a particular security policy configuration (as established by the security policy management system) needs to be (or should be) changed, e.g., to reduce the number of incidents caused by a misconfiguration, to increase its effectiveness in some manner, or the like. As a result of the evaluation, the security analytics system may cause a policy to be updated automatically, notify an administrator of the need for the change (and the recommendation), or take some other action to evolve one or more security policies being enforced by the security policy management system.
Owner:IBM CORP
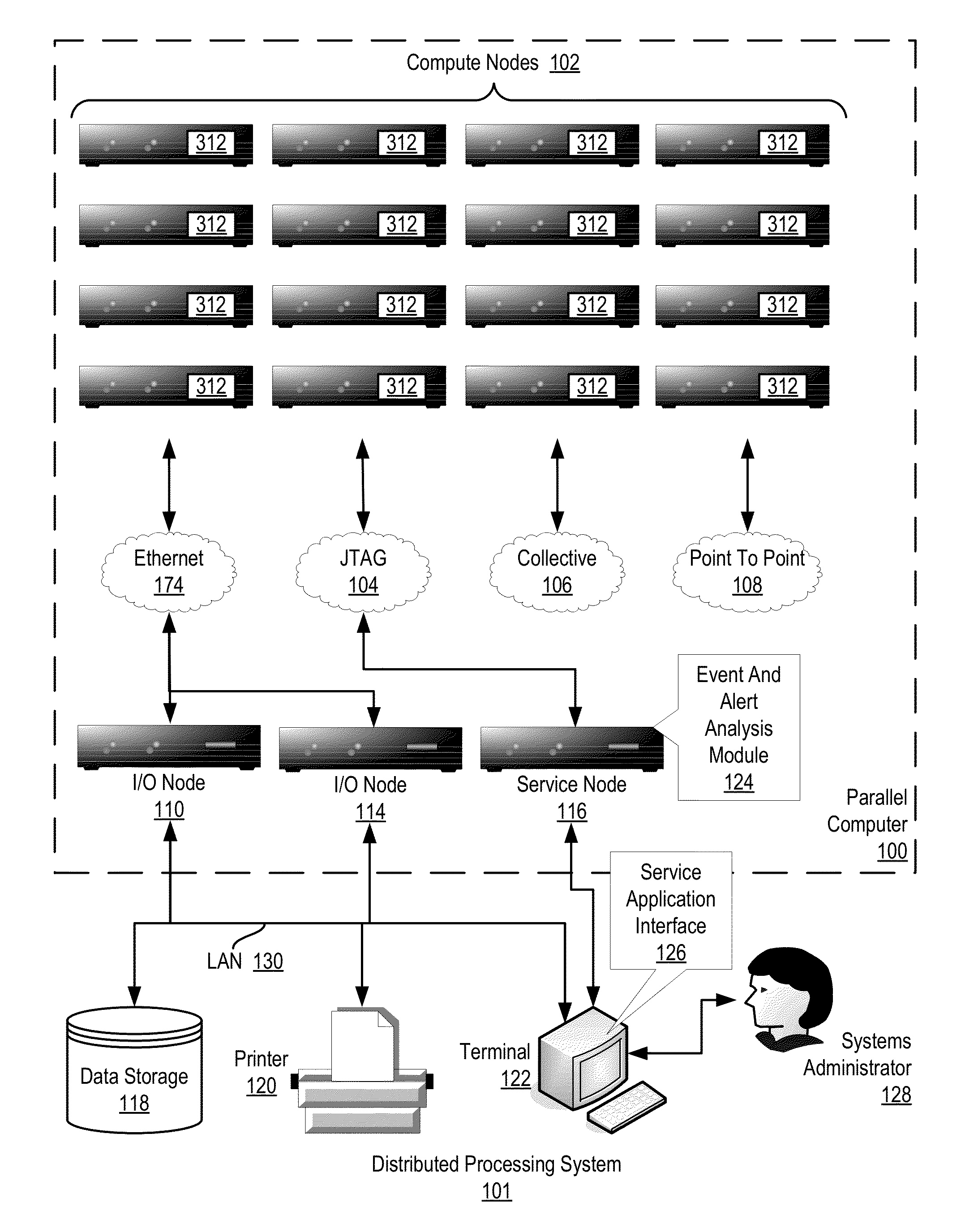
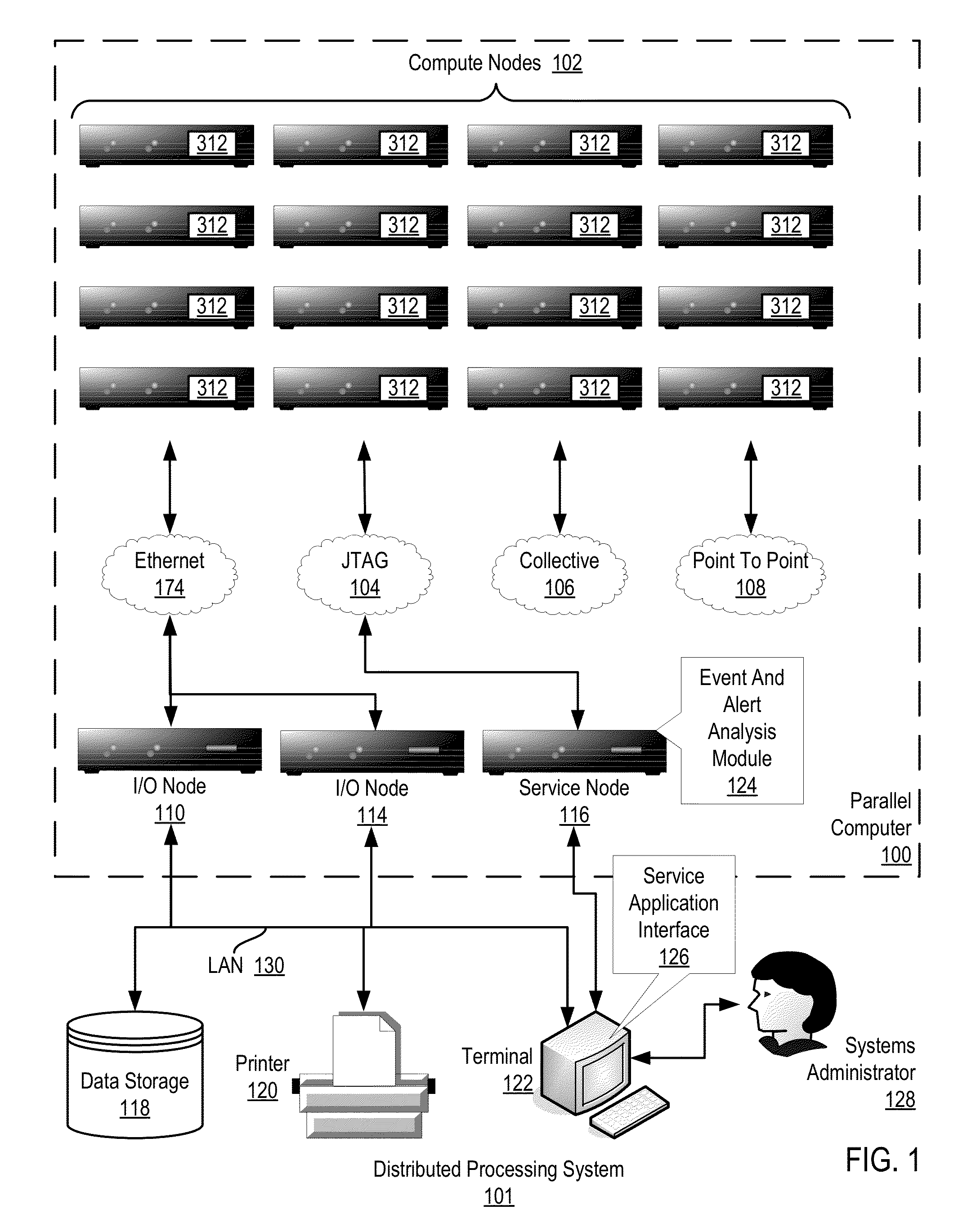
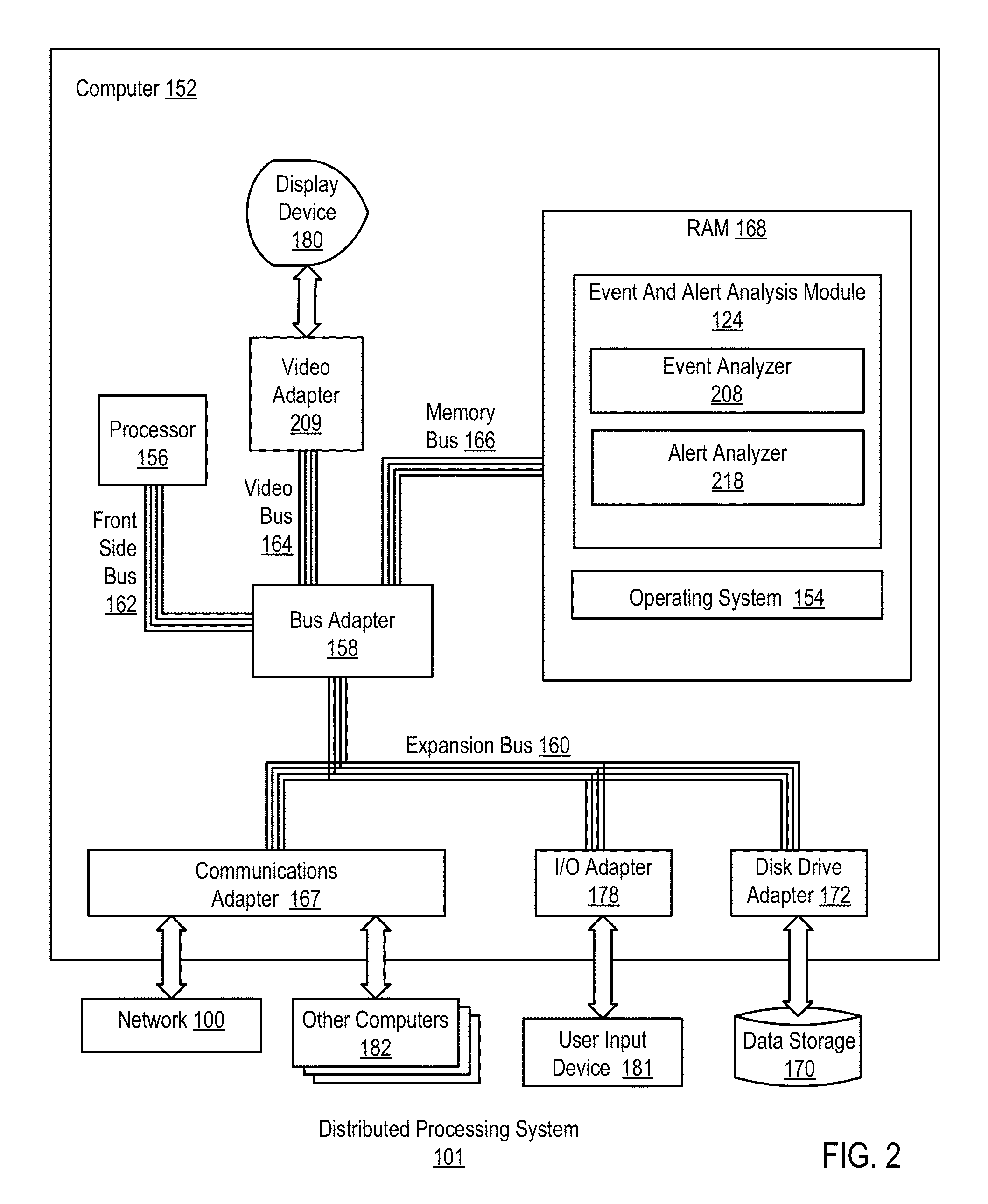
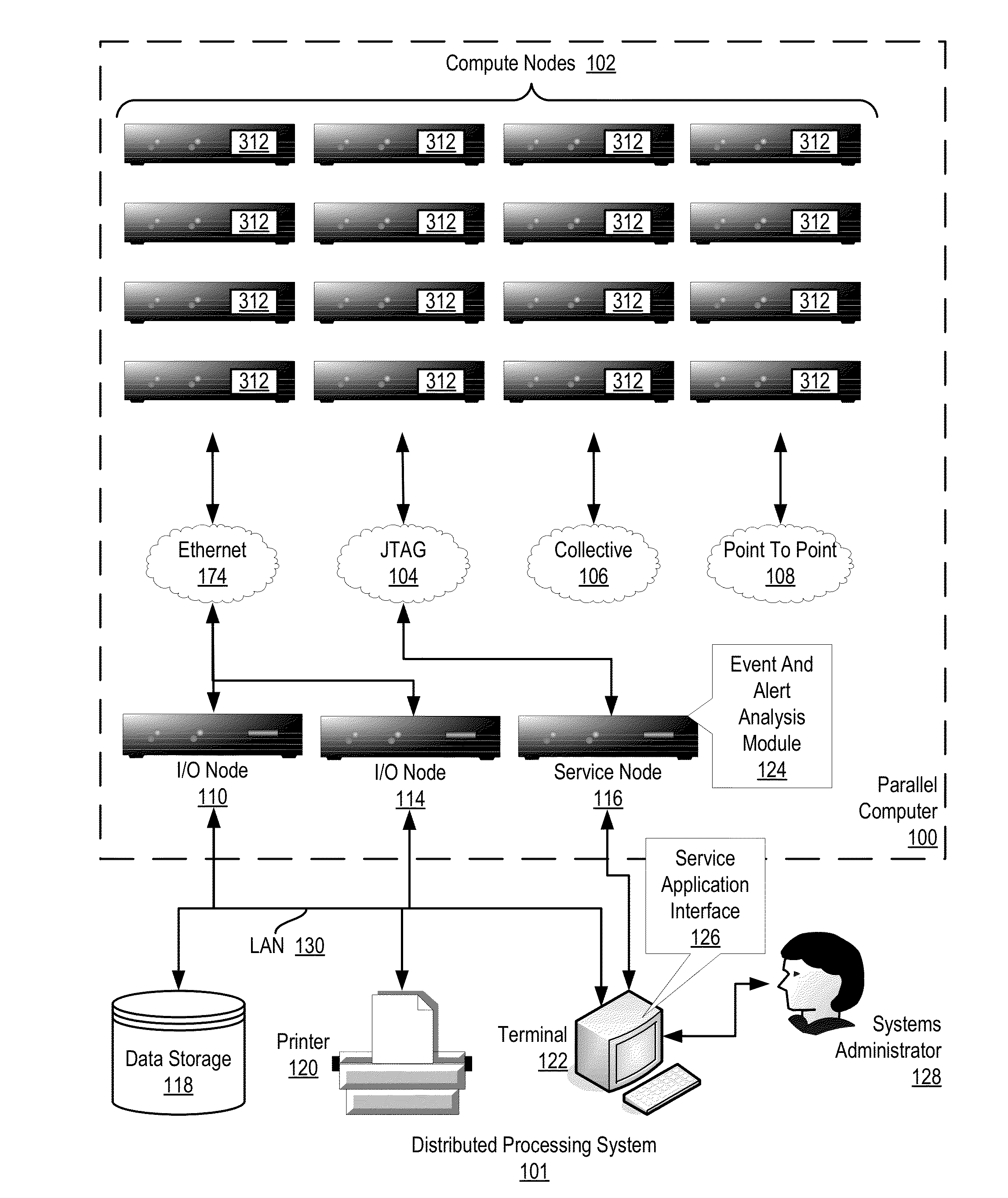
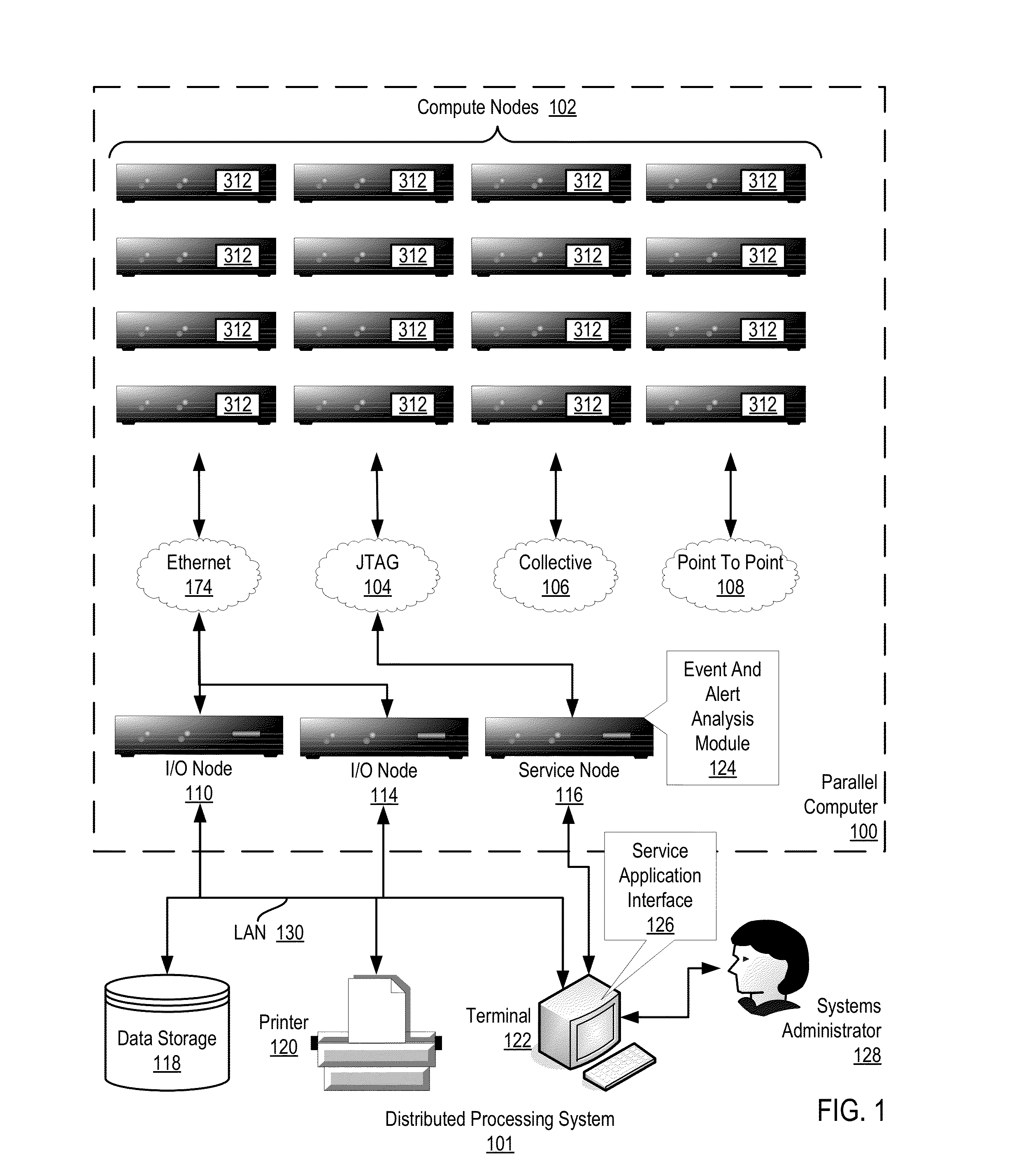
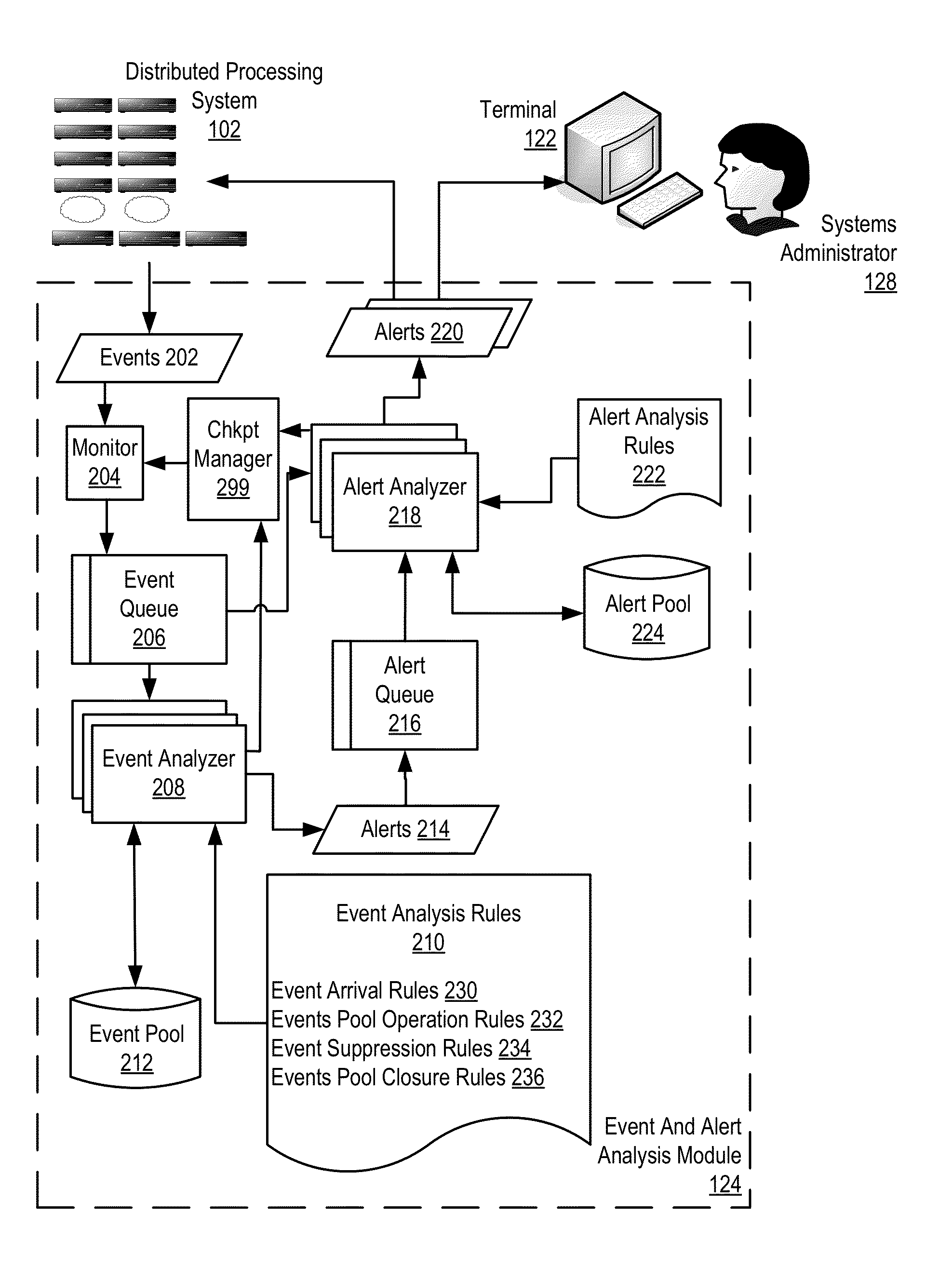
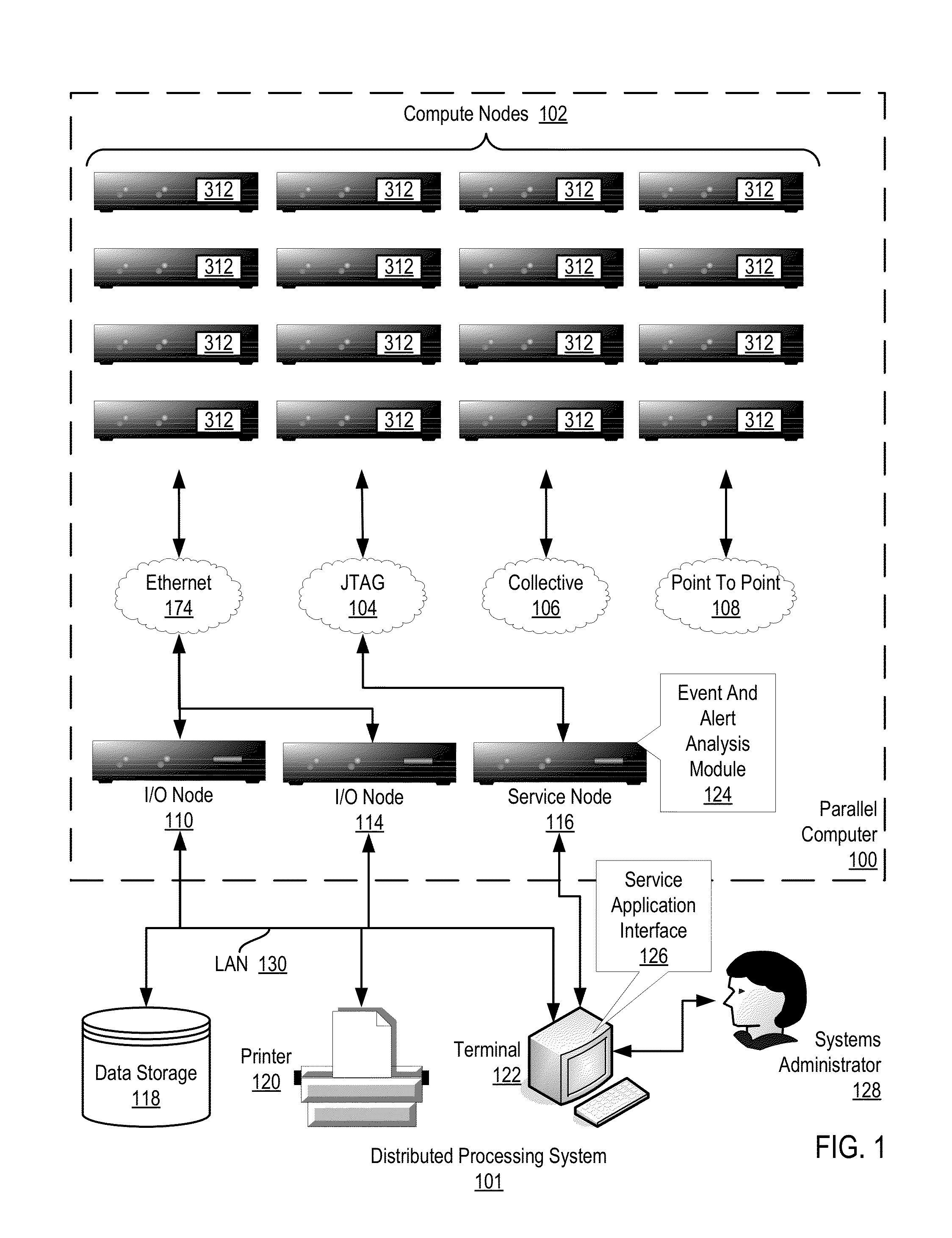
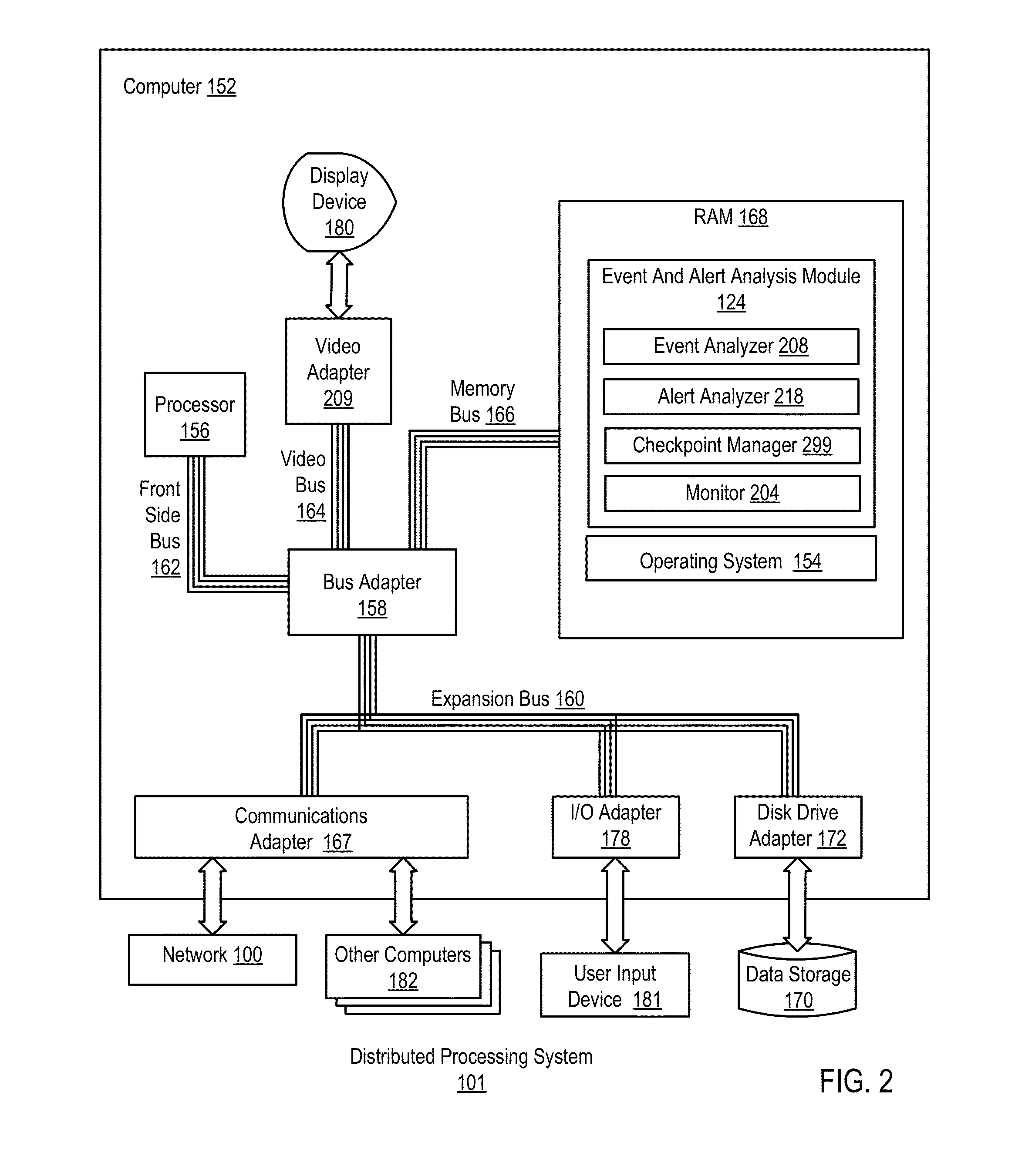
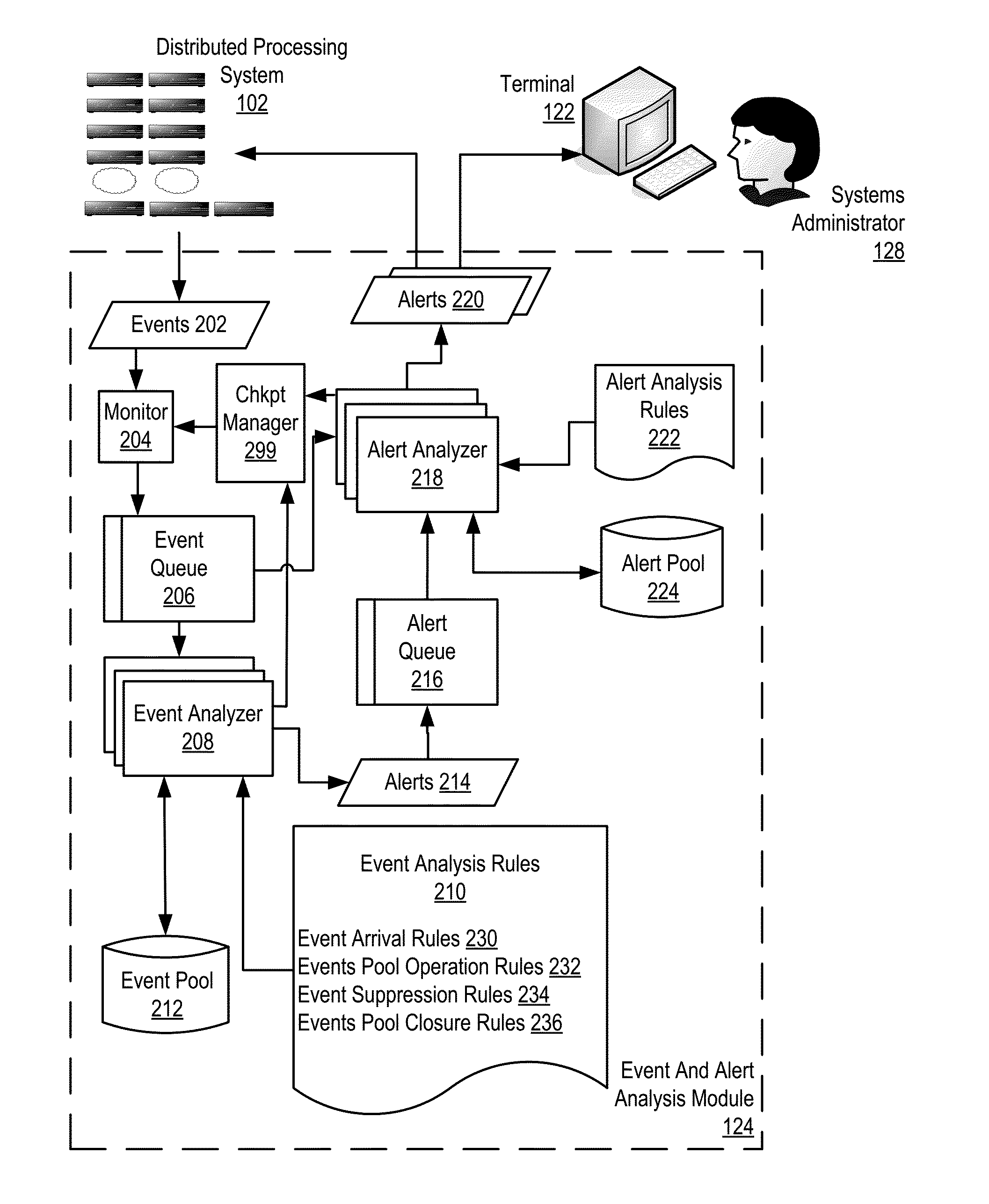
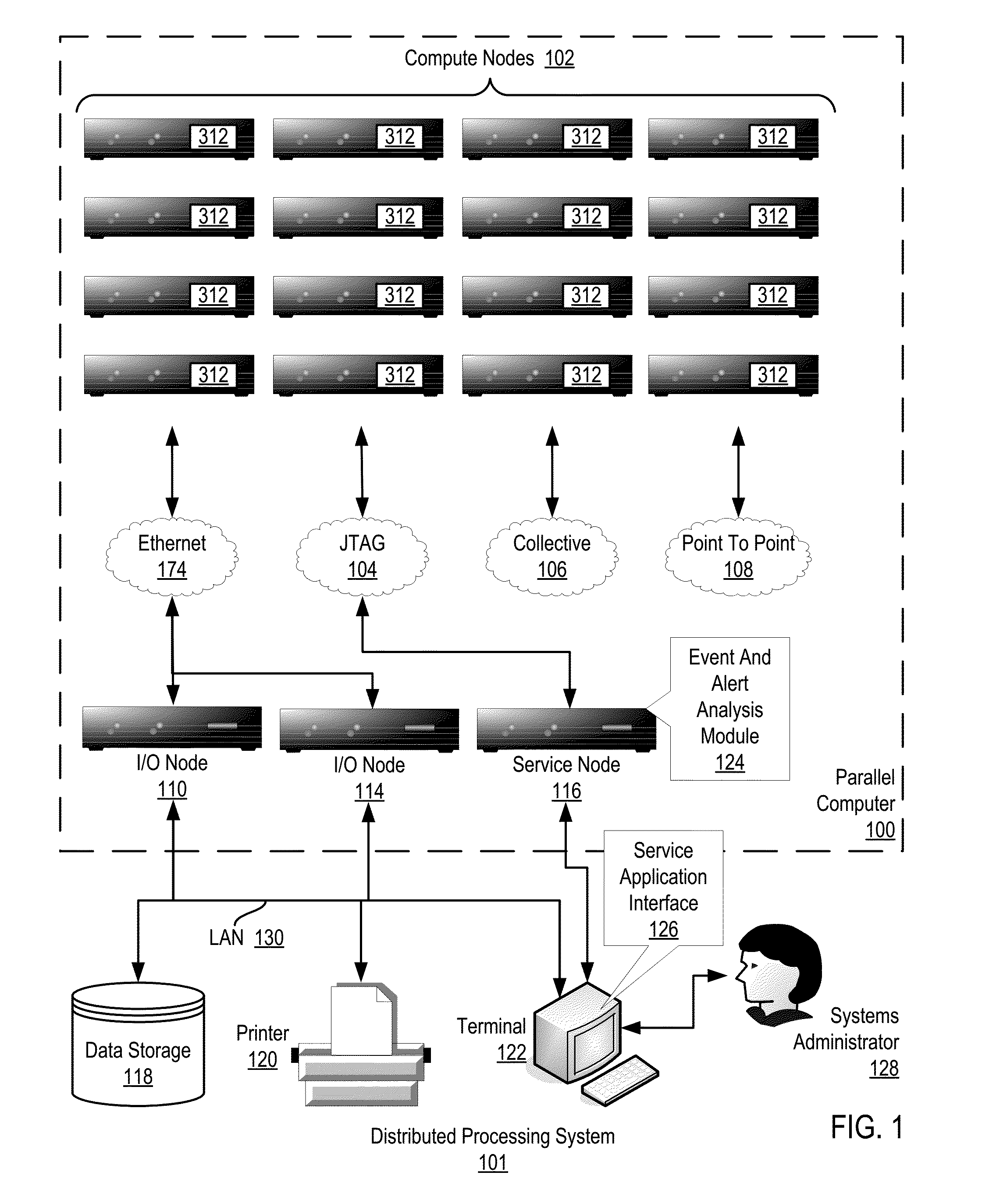
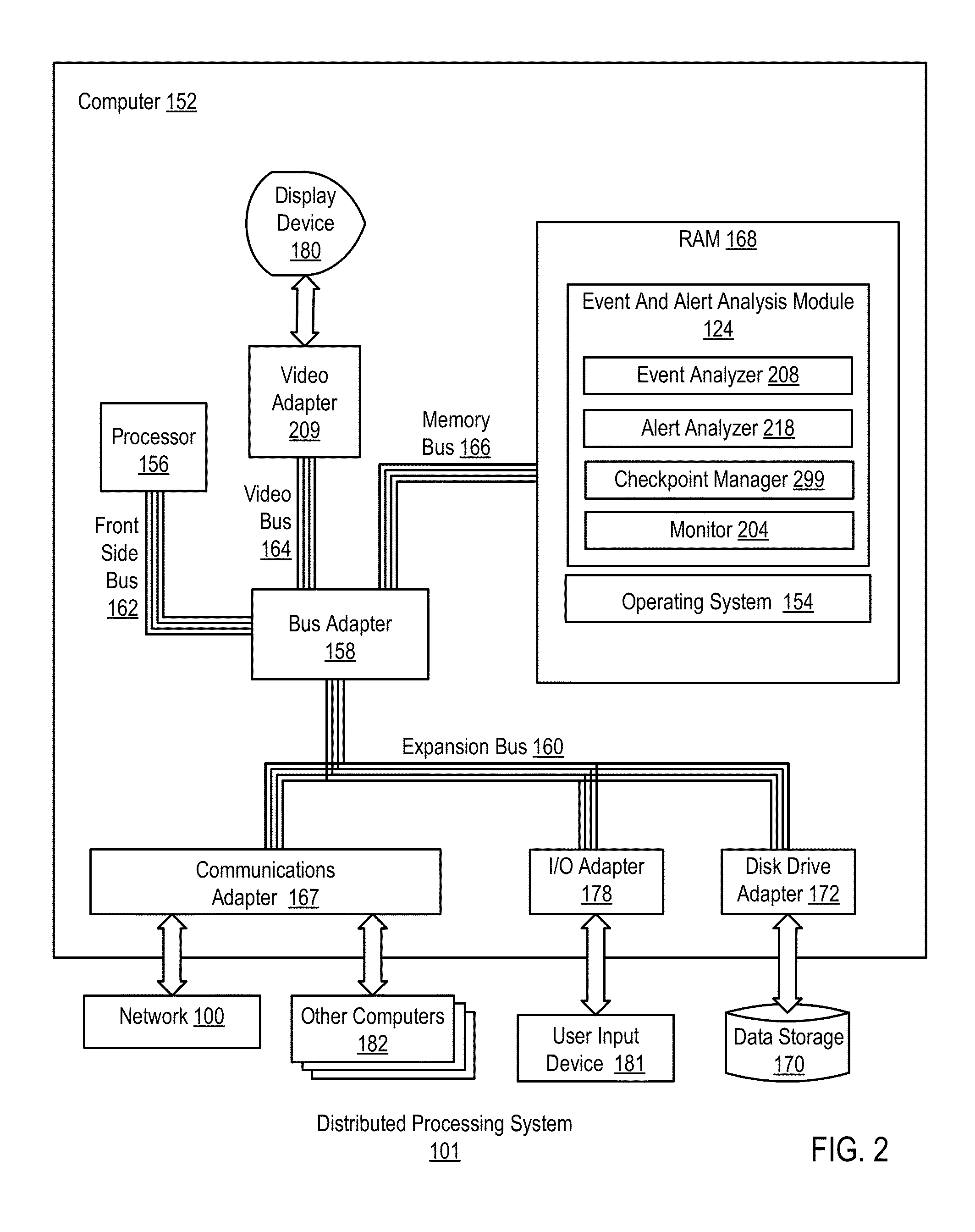
Administering event pools for relevant event analysis in a distributed processing system
Methods, systems, and computer program products for administering event pools for relevant event analysis are provided. Embodiments include assigning, by an incident analyzer, a plurality of events to an events pool; determining, by the incident analyzer, an event suppression duration; determining, by the incident analyzer in dependence upon event analysis rules, to suppress events having particular attributes indicating the events occurred during the event suppression duration; and suppressing, by the incident analyzer, each event assigned to the events pool having the particular attributes indicating the events occurred during the event suppression duration.
Owner:IBM CORP
Administering Incident Pools For Incident Analysis
InactiveUS20140040673A1Non-redundant fault processingRedundant operation error correctionIncident analysisData mining
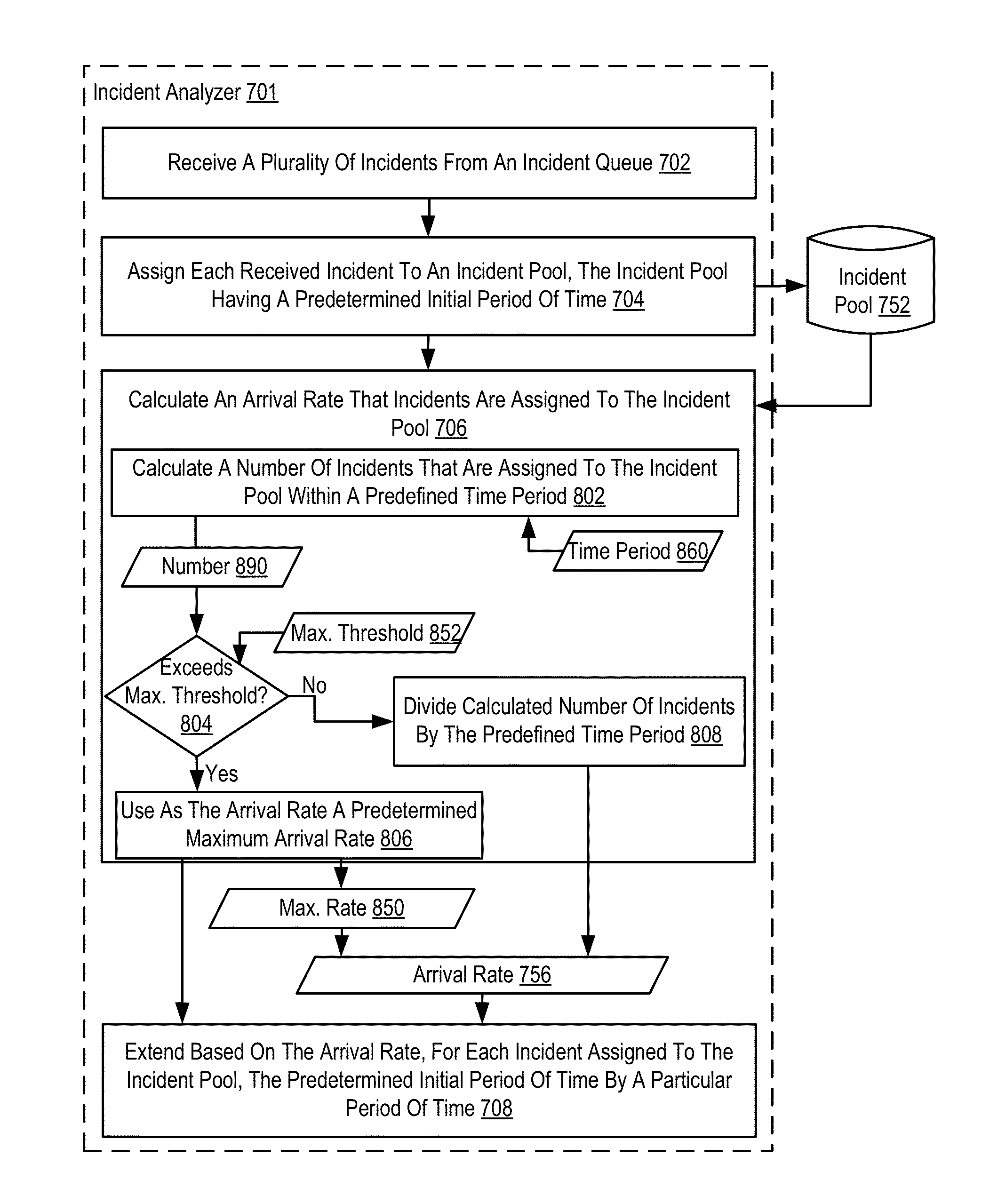
Methods, apparatuses, and computer program products for administering incident pools for incident analysis in a distributed processing system are provided. Embodiments include an incident analyzer receiving a plurality of incidents from an incident queue. The incident analyzer also assigns each received incident to an incident pool having a predetermined initial period of time. The predetermined initial period of time is the time within which the incident pool is open to the assignment of incidents. The incident analyzer calculates an arrival rate that incidents are assigned to the incident pool. The incident analyzer also extends based on the arrival rate, for each incident assigned to the incident pool, the predetermined initial period of time by a particular period of time.
Owner:IBM CORP
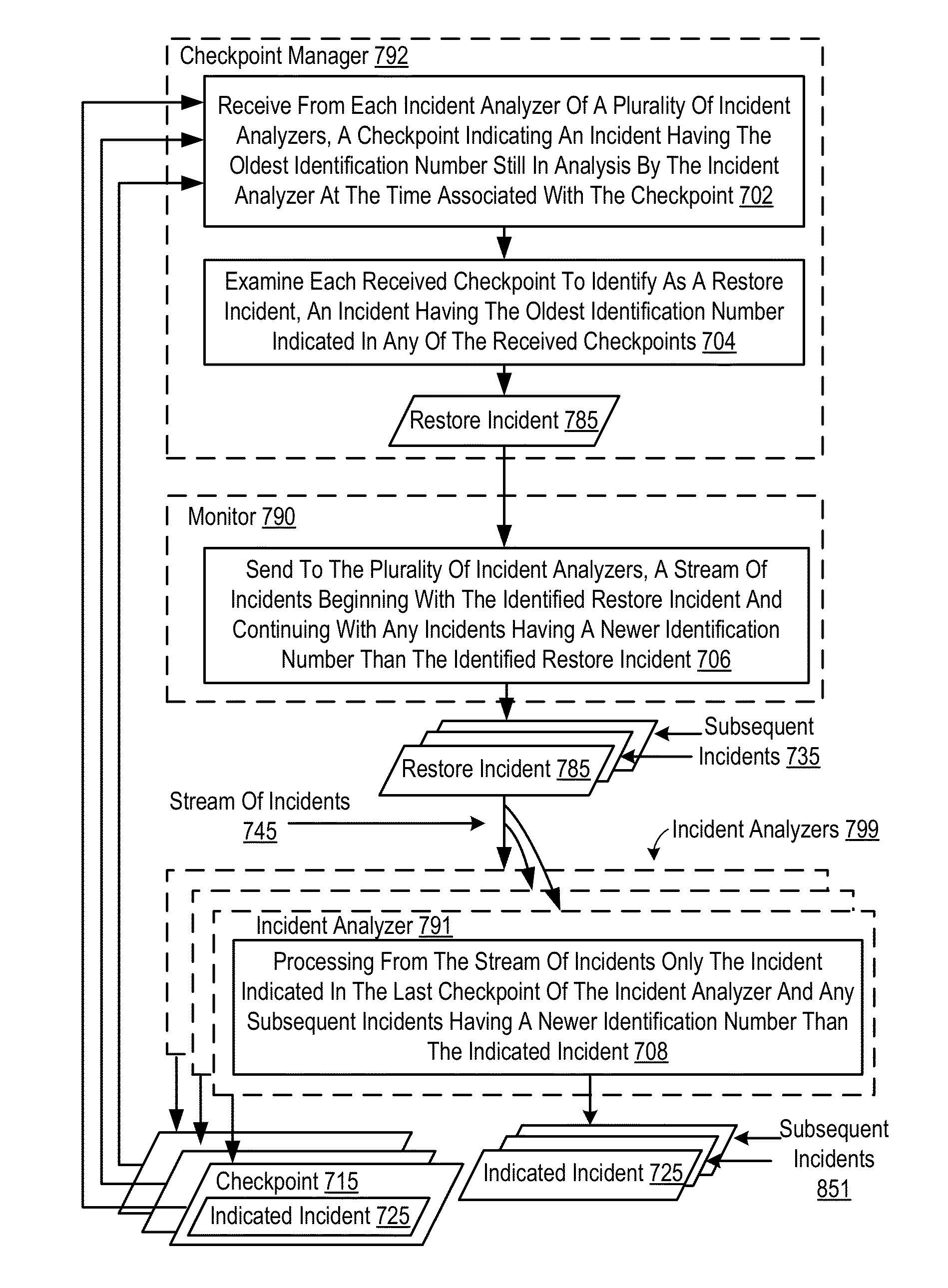
Administering Checkpoints For Incident Analysis
Methods, apparatuses, and computer program products for administering checkpoints for incident analysis are provided. Embodiments include a checkpoint manager receiving from each incident analyzer of a plurality of incident analyzers, a checkpoint indicating an incident having the oldest identification number still in analysis by the incident analyzer at the time associated with the checkpoint. The checkpoint manager examines each received checkpoint to identify, as a restore incident, an incident having the oldest identification number indicated in any of the received checkpoints. A monitor sends to the incident analyzers, a stream of incidents beginning with the identified restore incident and continuing with any incidents having a newer identification number than the identified restore incident. Each incident analyzer processes from the stream of incidents only the incident indicated in the last checkpoint of the incident analyzer and any subsequent incidents having a newer identification number than the indicated incident.
Owner:IBM CORP
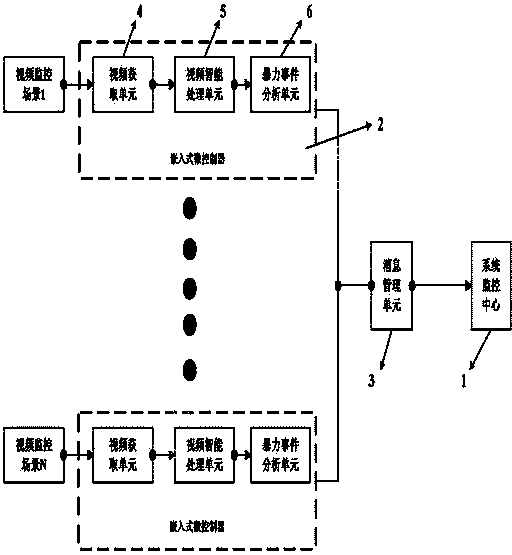
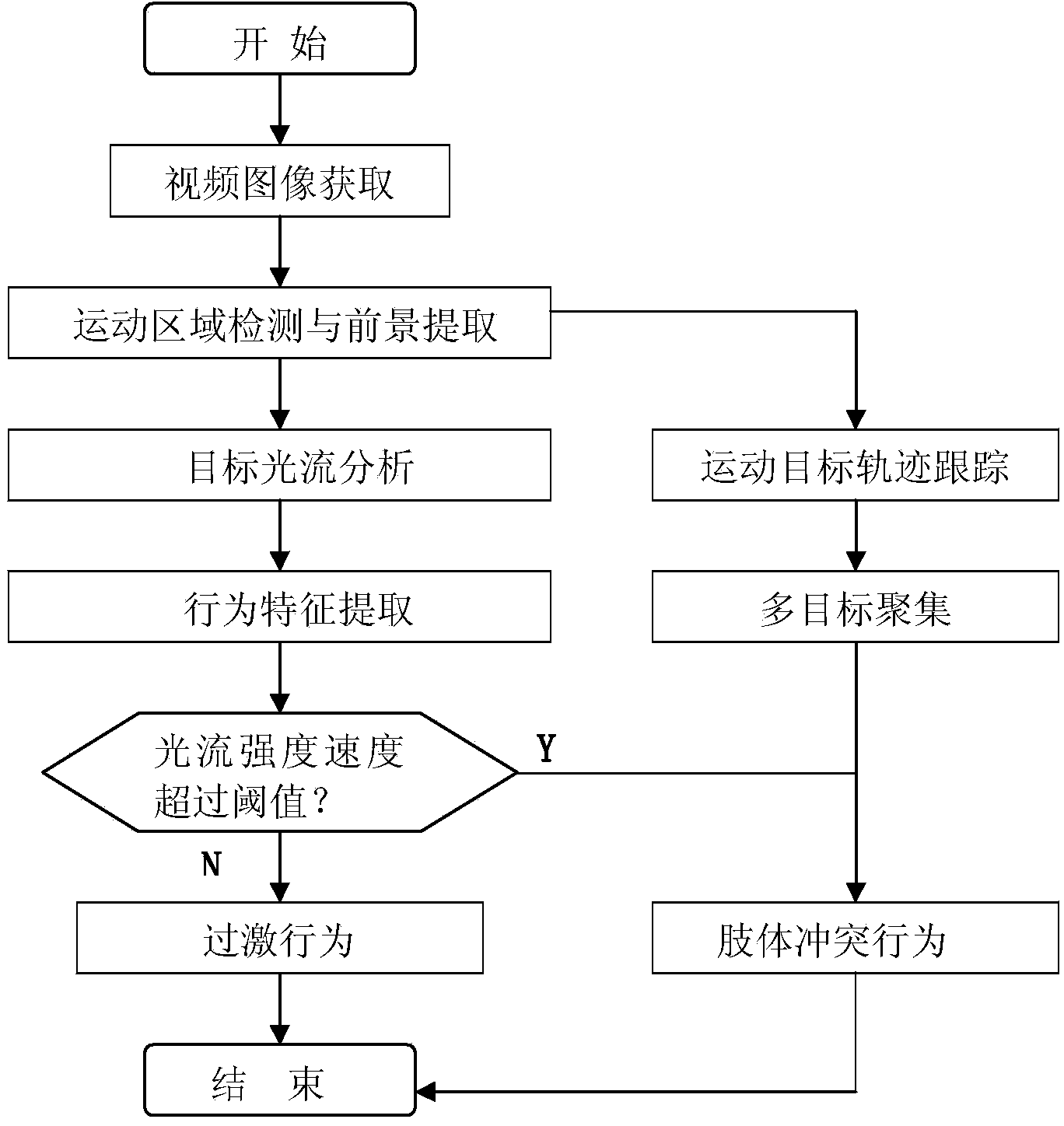
Automatic public place violence incident detection system and method thereof
InactiveCN104301697ATo evacuate the crowdIncreased violenceImage analysisClosed circuit television systemsMicrocontrollerPublic place
The invention relates to the field of public security, and in particular relates to an automatic public place violence incident detection system and a method thereof. The automatic public place violence incident detection system comprises an embedded microcontroller and a system monitoring center, wherein the embedded microcontroller comprises a video acquiring unit, an intelligent video processing unit and a violence incident analysis unit; the video acquiring unit is used for acquiring monitoring information; the intelligent video processing unit is used for analyzing and processing the monitoring information; the violence incident analysis unit is used for judging whether the monitoring information is violence action or not, if the monitoring information is violence action, an alarm can be made to remind citizens, a function of evacuating the crowd is achieved, and information can be also transmitted to the system monitoring center; the system monitoring center is used for monitoring and storing the violence monitoring information in real time, and an alarm can be given in the system monitoring center, so that the monitoring efficiency is improved, and the emergency speed is increased.
Owner:GUANGZHOU UNIVERSITY
Method and System for Analysis of Security Events in a Managed Computer Network
An event retrieval and analysis system compares counts of event data for a device to stored profile counts to determine if alerts should be triggered. Event data can be retrieved by a sensor. Rules for analyzing the event data can be retrieved based on the device. The event data is analyzed based on the rules to determine recordable events. Recordable events are organized into categories representing a type or severity of attack. Current event counts are calculated by summing the recordable events for each category. A normal profile is retrieved for the device and compared to the current event count. A percentage change trigger can be retrieved from a threshold matrix based on the current event count. The percentage increase of the current event count over the normal profile is calculated and compared to the percentage change trigger to determine if an alert is triggered by the analysis system.
Owner:KYNDRYL INC
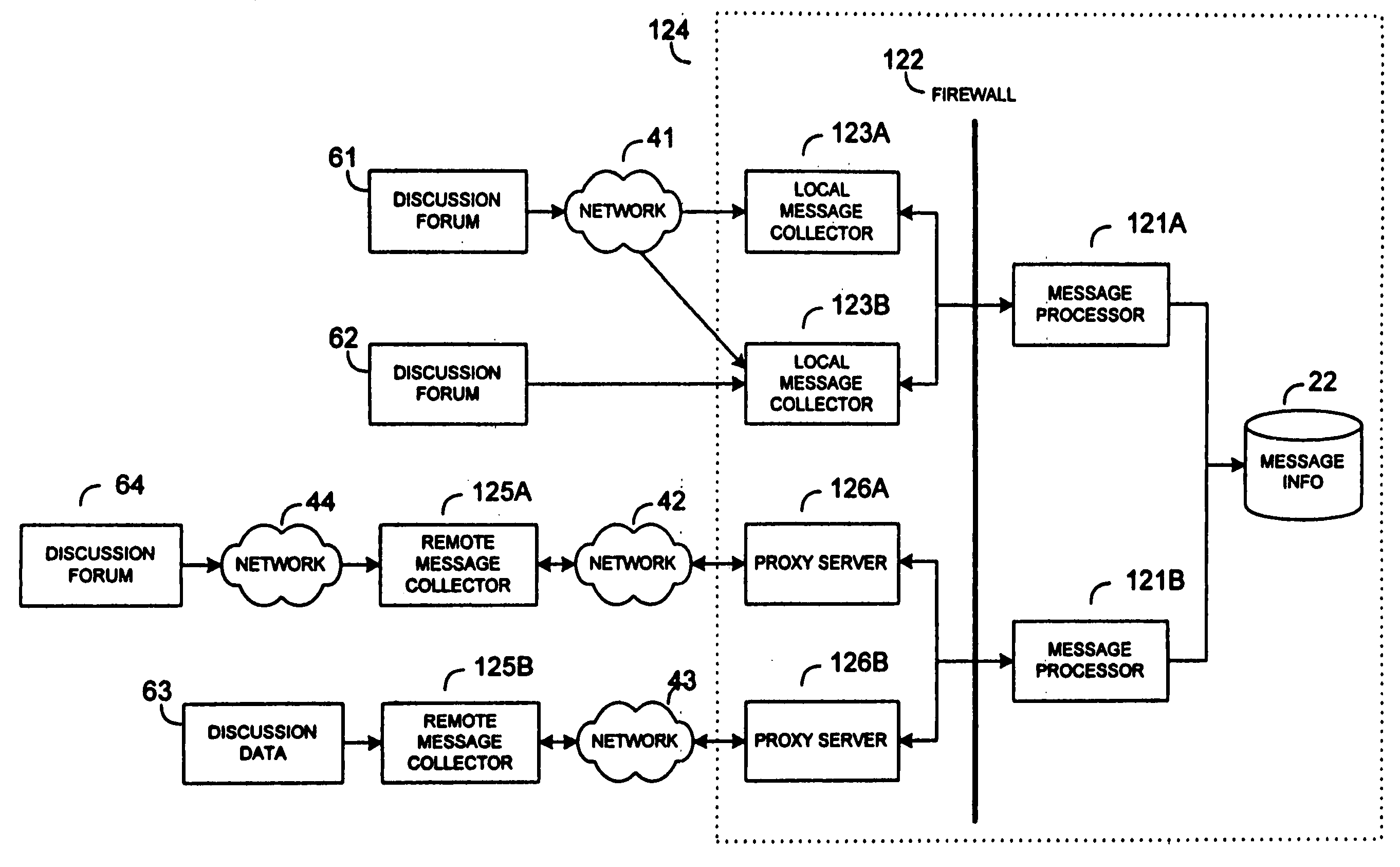
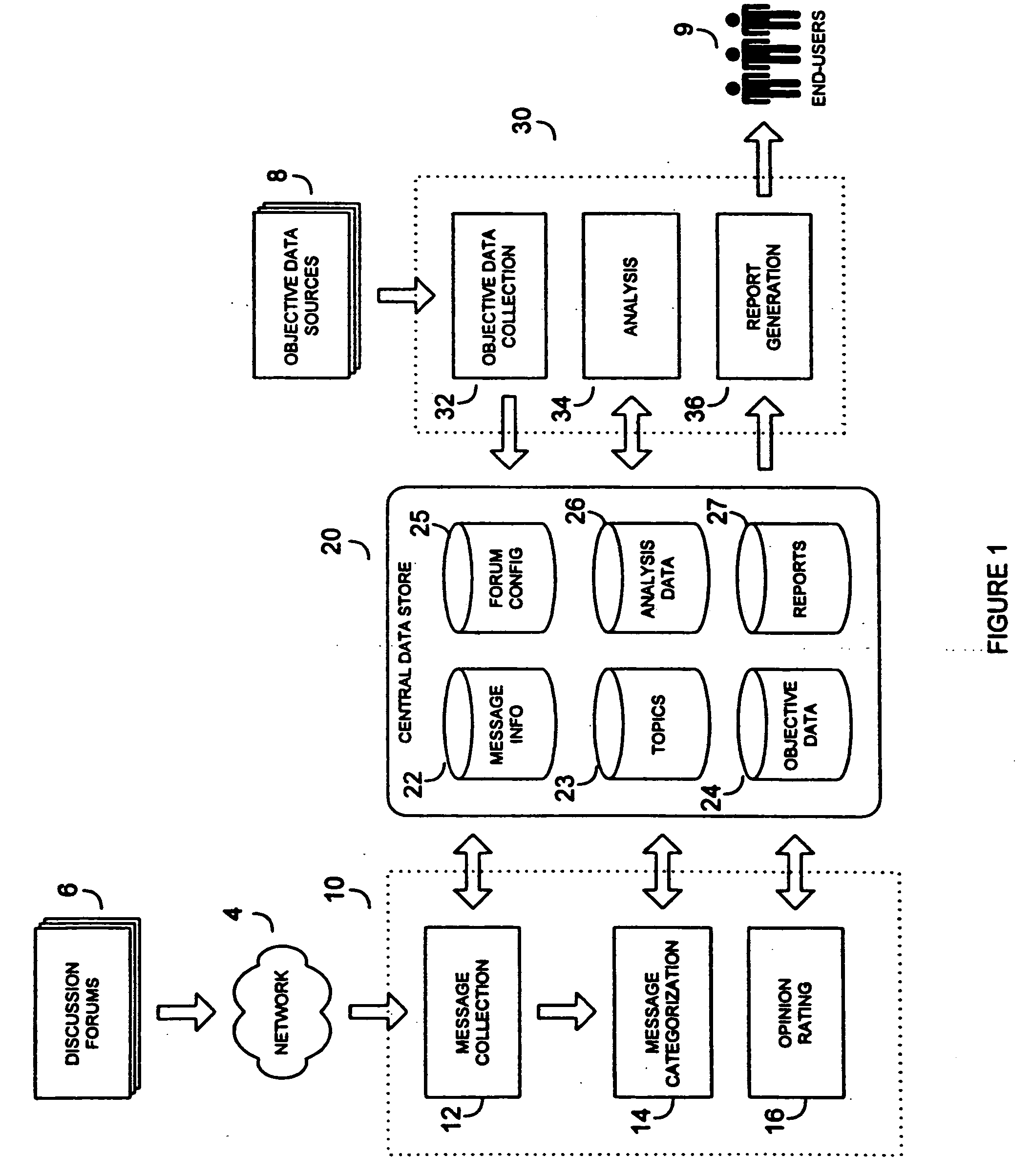
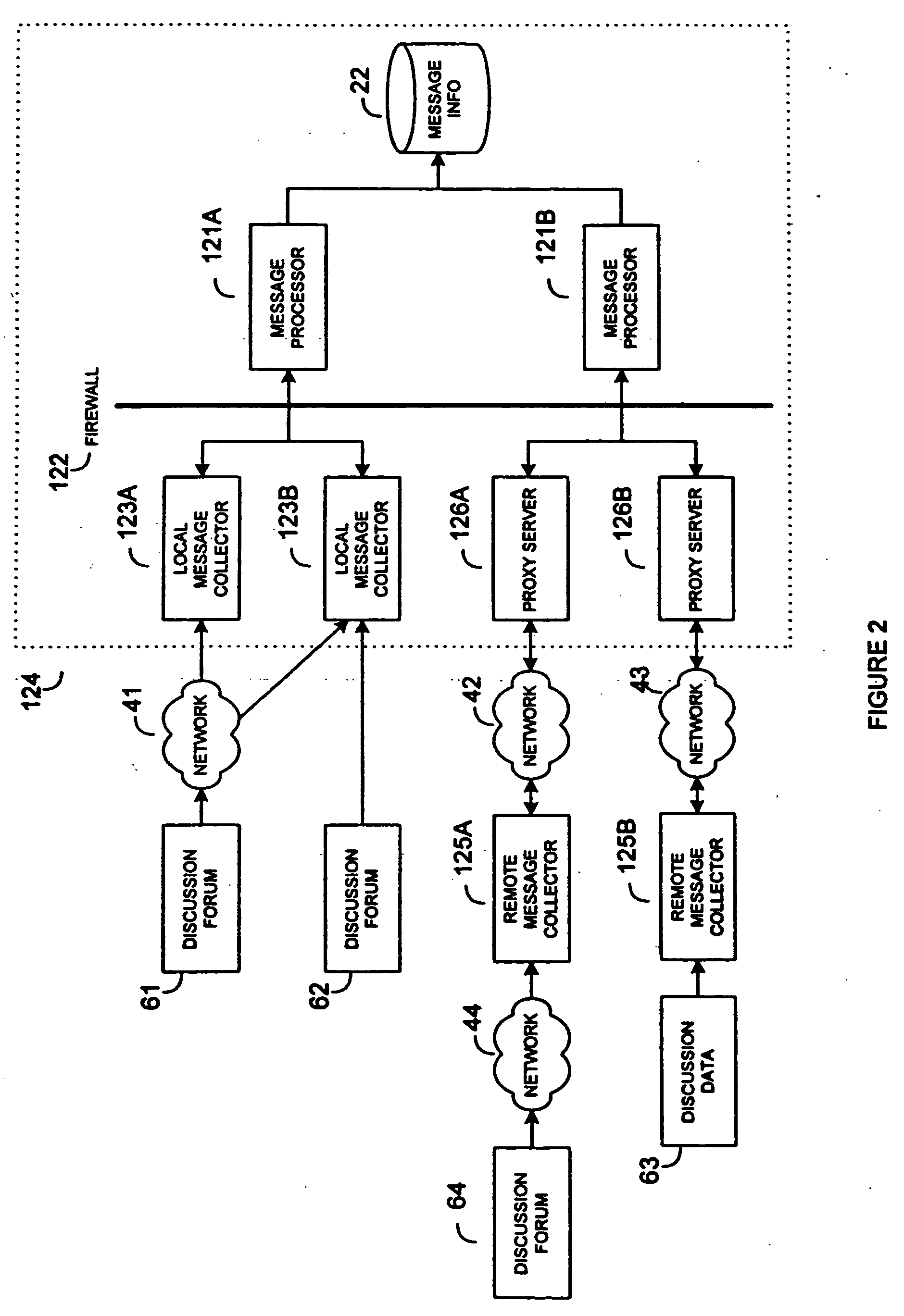
System and method for collection and analysis of electronic discussion messages
InactiveUS20060080162A1Market predictionsDigital data authenticationIncident analysisComputer science
A system and method for collecting and analyzing electronic discussion messages to categorize the message communications and the identify trends and patterns in pre-determined markets. The system comprises an electronic data discussion system wherein electronic messages are collected and analyzed according to characteristics and data inherent in the messages. Objective data is collected by the system for use in analyzing the electronic discussion data against real-world events to facilitate trend analysis and event forecasting based on the volume, nature and content of messages posted to electronic discussion forums. The message posting activity of a plurality of posters can be tracked to determine the tendency of individual posters to initiate or moderate discussions, accurately predict events external to the discussion forums, accelerate or decelerate a buzz level in a forum, or precede a rising market or a falling market.
Owner:BUZZMETRICS
Selecting During A System Shutdown Procedure, A Restart Incident Checkpoint Of An Incident Analyzer In A Distributed Processing System
InactiveUS20150355976A1Interprogram communicationRedundant operation error correctionIncident analysisComputer program
Methods, apparatuses, and computer program products for selecting during a system shutdown procedure, a restart incident checkpoint of an incident analyzer in a distributed processing system. Embodiments include the incident analyzer determining whether at least one incident is in a queue. If at least one incident is in the queue, the incident analyzer selects as the restart incident checkpoint, a last incident completed checkpoint. If at least one incident is not in the queue, the incident analyzer determines whether the last incident completed checkpoint matches a last incident analysis pool selection checkpoint. If the last incident completed checkpoint matches a last incident analysis pool selection checkpoint, the incident analyzer selects as the restart incident checkpoint, a monitor checkpoint. If the last incident completed checkpoint does not match the last incident analysis pool selection checkpoint, the incident analyzer selects as the restart incident checkpoint, the last incident completed checkpoint.
Owner:IBM CORP
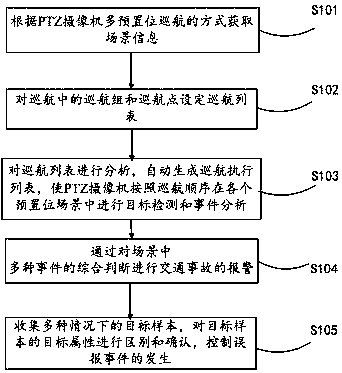
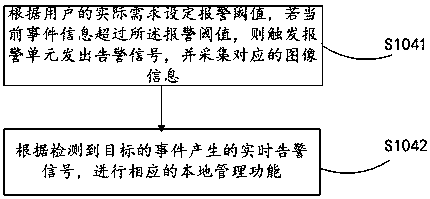
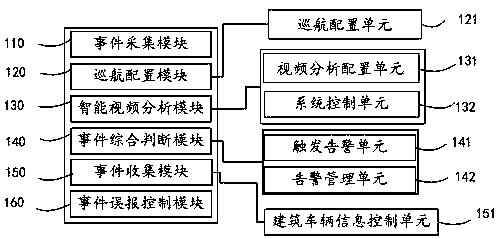
Video detection method and system of road traffic incident
InactiveCN107590834AAvoid secondary accidentsEnsure driving safetyImage analysisClosed circuit television systemsIncident analysisRoad traffic
The invention discloses a video detection method and system of a road traffic incident. The method comprises: scene information is obtained according to a multi-preset-position cruising mode of a PTZcamera; a cruise list is set for cruise groups and cruise points in cruising; the cruise list is analyzed and a cruise execution list is generated automatically, so that the PTZ camera carries out target detection and incident analyses in all preset position scenes according to a cruising sequence; and then various incidents in the scenes are determined comprehensively to carry out traffic incident alarming. Therefore, various traffic incidents can be discovered in real time and thus alarming signal can be triggered timely; and the field photos are captured and real-time picture recording is carried out. With the system disclosed by the invention, occurrence of secondary accidents is avoided and incident information is obtained immediately, so that the traffic incidents are processed timely and thus traffic safety and smooth traffic are guaranteed to the greatest extent.
Owner:BEIJING BOOSTIV TECH
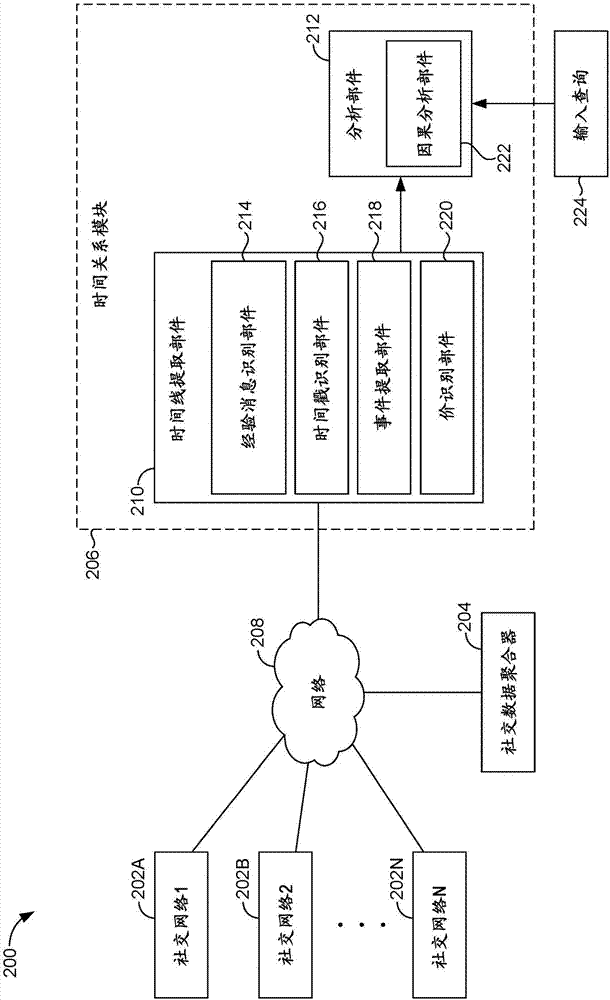
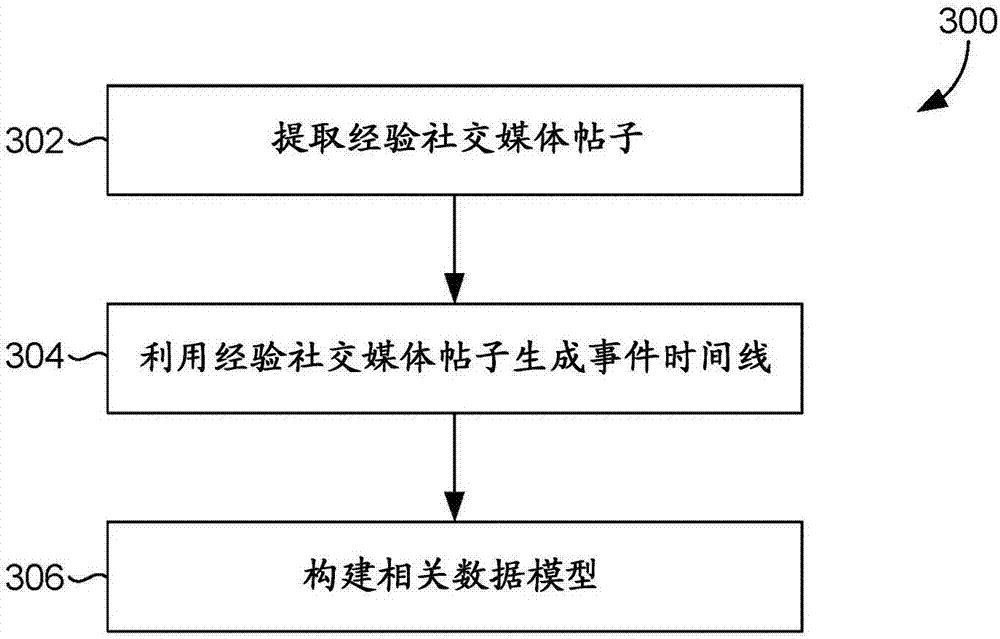
Modeling actions, consequences and goal achievement from social media and other digital traces
ActiveUS20160171063A1Digital data information retrievalDigital data processing detailsSocial mediaIncident analysis
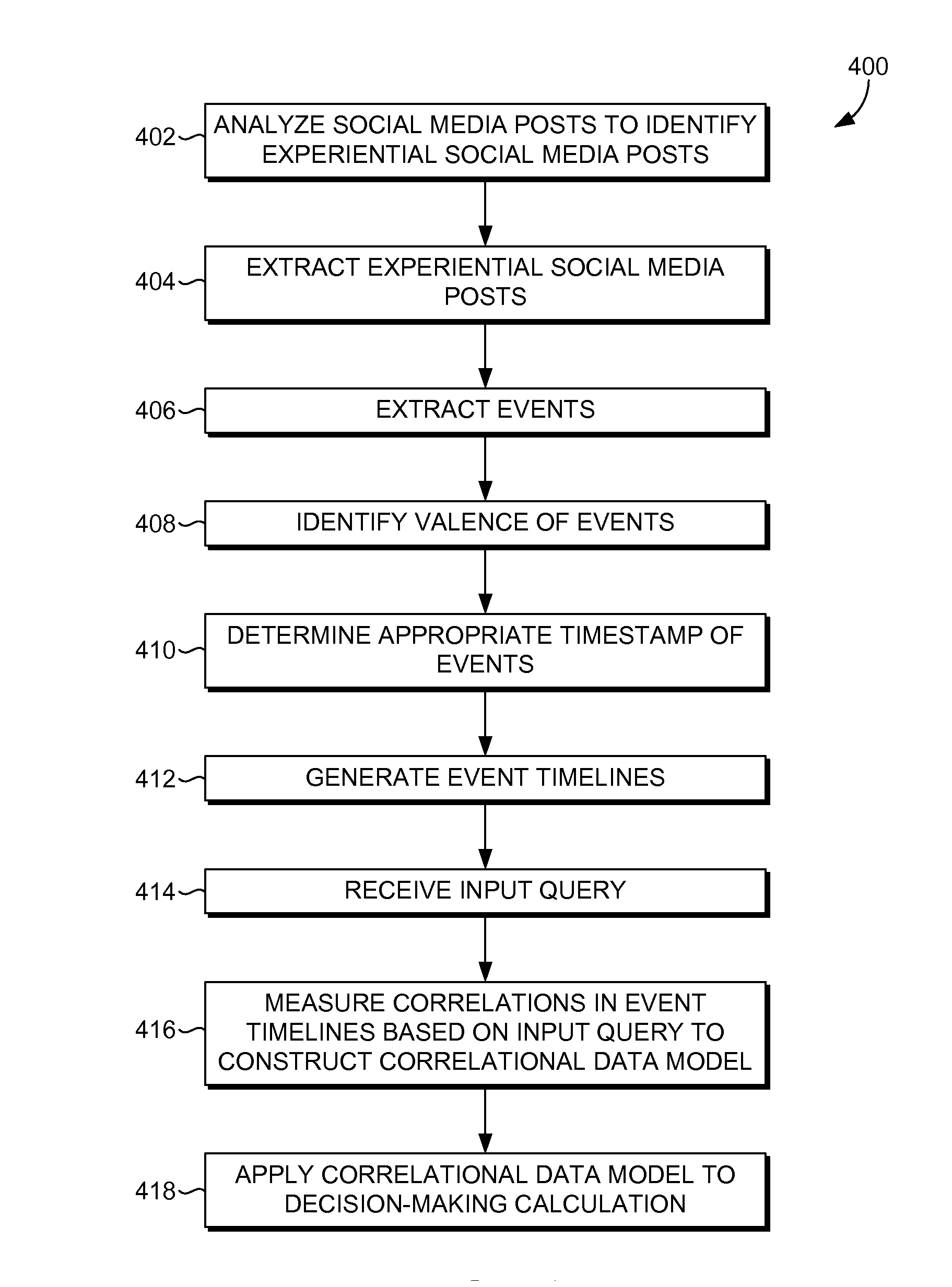
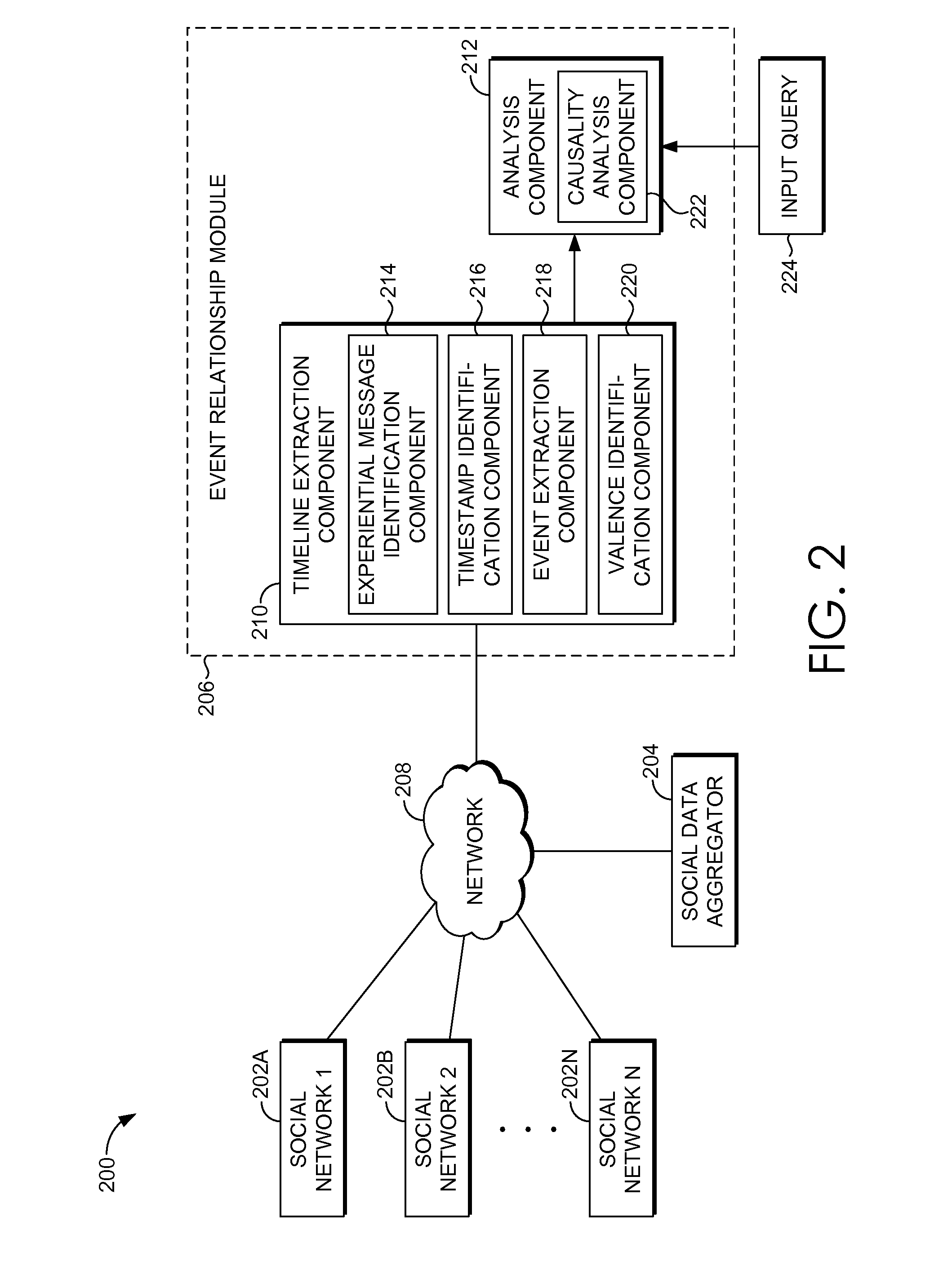
Systems, methods, and computer storage media are provided for analyzing a large amount of social media data from a large population of social media users and constructing correlational data models between one or more events that occur within each user's timeline. Social media posts directed to personal experiences of a large number of social media users are extracted. Event timelines are generated for each of the social media users, based on their personal experiences. The event timelines are analyzed with a particular event of interest to measure correlations between events occurring within the timelines and the particular event of interest. Using the measured correlations, a correlational data model is thereby constructed. The correlational data model may be used for application to decision-making calculations by one or more systems in an active or passive manner.
Owner:MICROSOFT TECH LICENSING LLC
Traffic accident handling method, system and server
PendingCN109242739AProcessing speedReduce labor costsData processing applicationsMachine learningIncident analysisTraffic accident
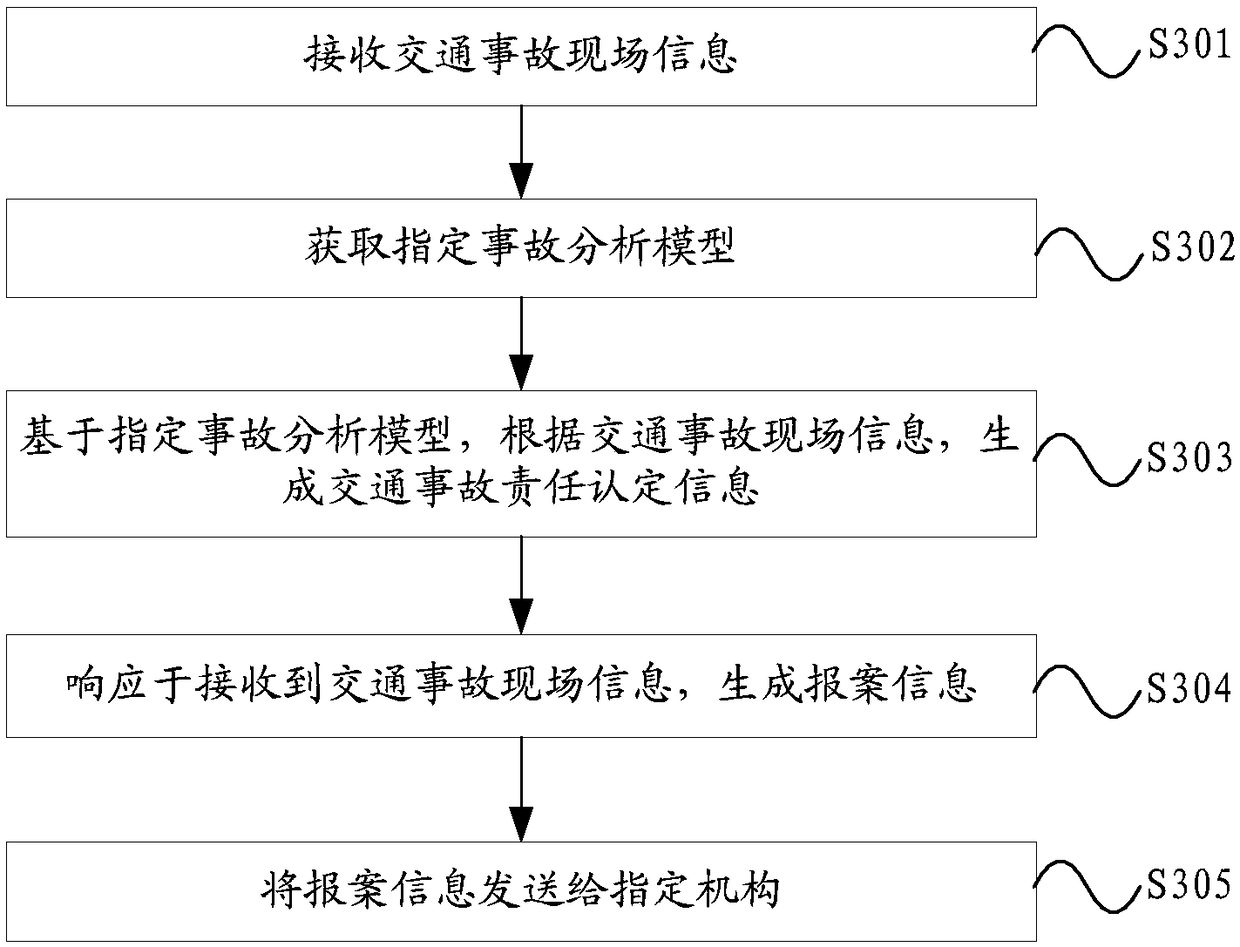
The embodiment of the invention provides a traffic accident processing method, a system and a server. As the embodiment of the invention receives the traffic accident scene information, obtaining thespecified incident analysis model, accident analysis model based on assignment, according to the traffic accident scene information, generating traffic accident liability identification information, Ability to use a specified incident analysis model, there is no need for traffic policemen and insurance personnel to go to the scene to investigate, no traffic accident personnel are required to waitat the scene, on the one hand, it saves manpower cost, so that the accident processing time is reduced, so that the accident processing speed is improved, on the other hand, the waiting time of the traffic accident personnel is greatly reduced, so that the traffic accident personnel without serious hindrance can leave the accident scene quickly, traffic congestion is avoided or the congestion timeis shortened, and the problem of high human cost and more time-consuming of the traffic accident processing flow in the prior art is solved to a certain extent.
Owner:PING AN TECH (SHENZHEN) CO LTD
Administering checkpoints for incident analysis
Methods, apparatuses, and computer program products for administering checkpoints for incident analysis are provided. Embodiments include a checkpoint manager receiving from each incident analyzer of a plurality of incident analyzers, a checkpoint indicating an incident having the oldest identification number still in analysis by the incident analyzer at the time associated with the checkpoint. The checkpoint manager examines each received checkpoint to identify, as a restore incident, an incident having the oldest identification number indicated in any of the received checkpoints. A monitor sends to the incident analyzers, a stream of incidents beginning with the identified restore incident and continuing with any incidents having a newer identification number than the identified restore incident. Each incident analyzer processes from the stream of incidents only the incident indicated in the last checkpoint of the incident analyzer and any subsequent incidents having a newer identification number than the indicated incident.
Owner:INT BUSINESS MASCH CORP
Modeling actions, consequences and goal achievement from social media and other digital traces
Systems, methods, and computer storage media are provided for analyzing a large amount of social media data from a large population of social media users and constructing correlational data models between one or more events that occur within each user's timeline. Social media posts directed to personal experiences of a large number of social media users are extracted. Event timelines are generated for each of the social media users, based on their personal experiences. The event timelines are analyzed with a particular event of interest to measure correlations between events occurring within the timelines and the particular event of interest. Using the measured correlations, a correlational data model is thereby constructed. The correlational data model may be used for application to decision-making calculations by one or more systems in an active or passive manner.
Owner:MICROSOFT TECH LICENSING LLC
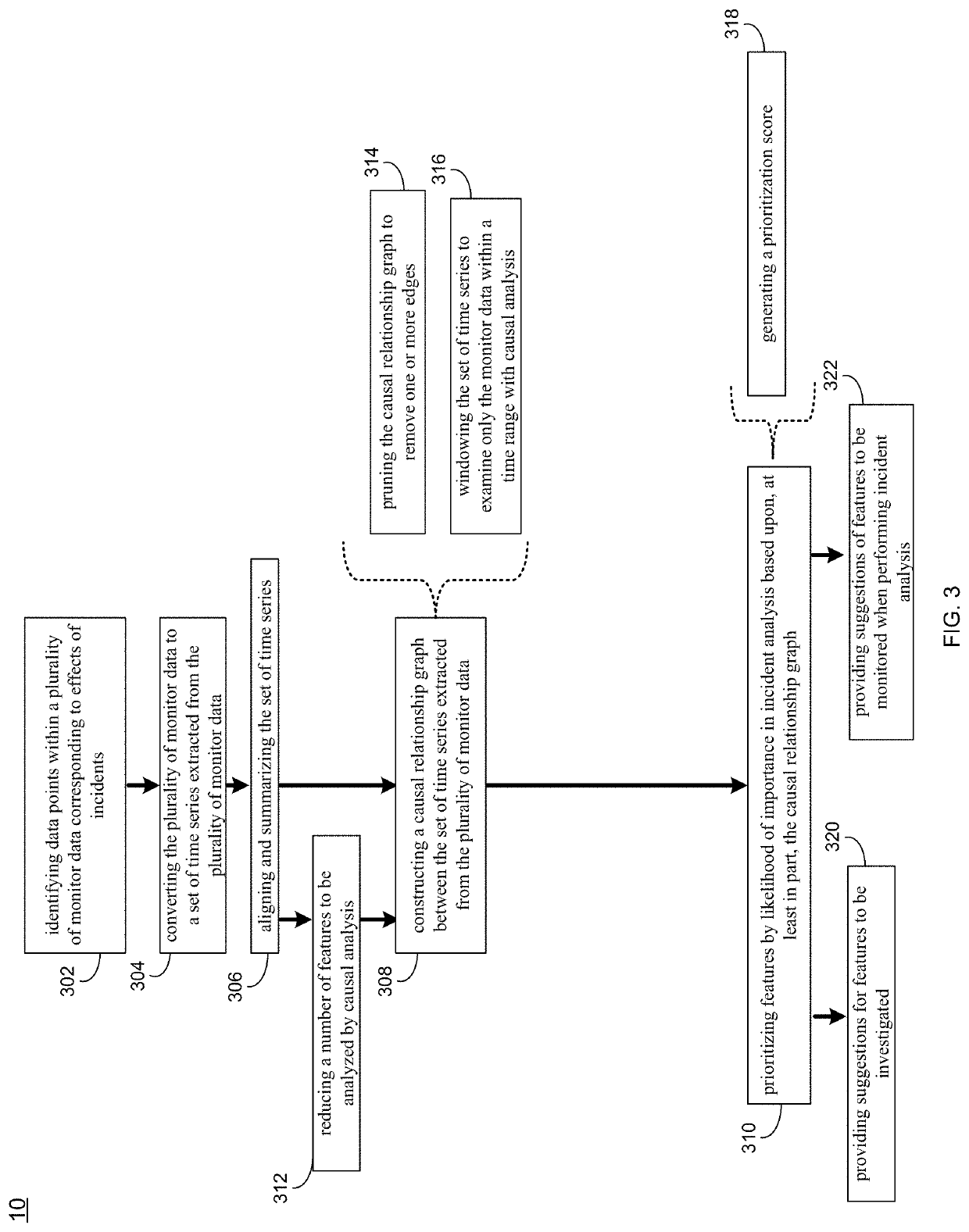
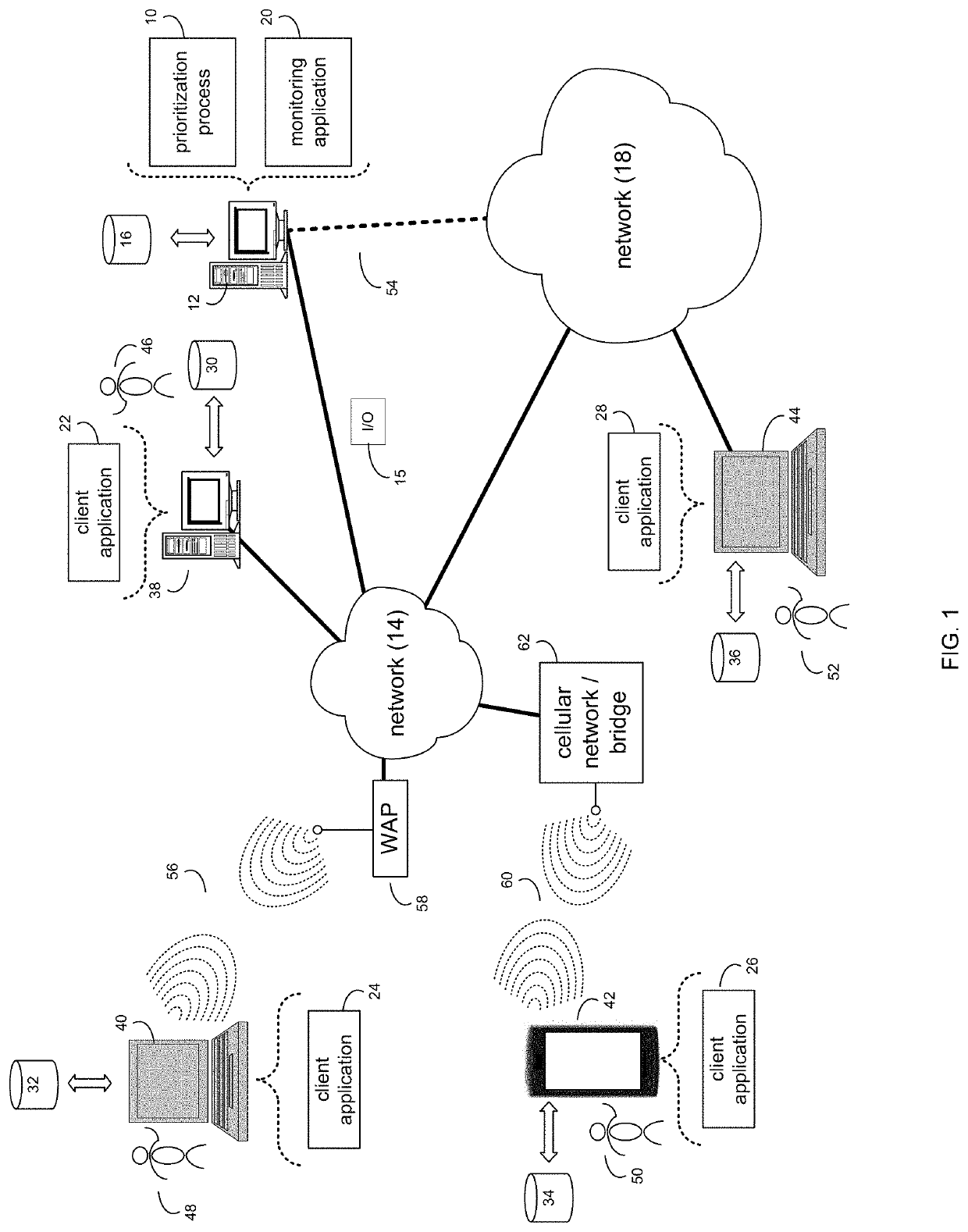
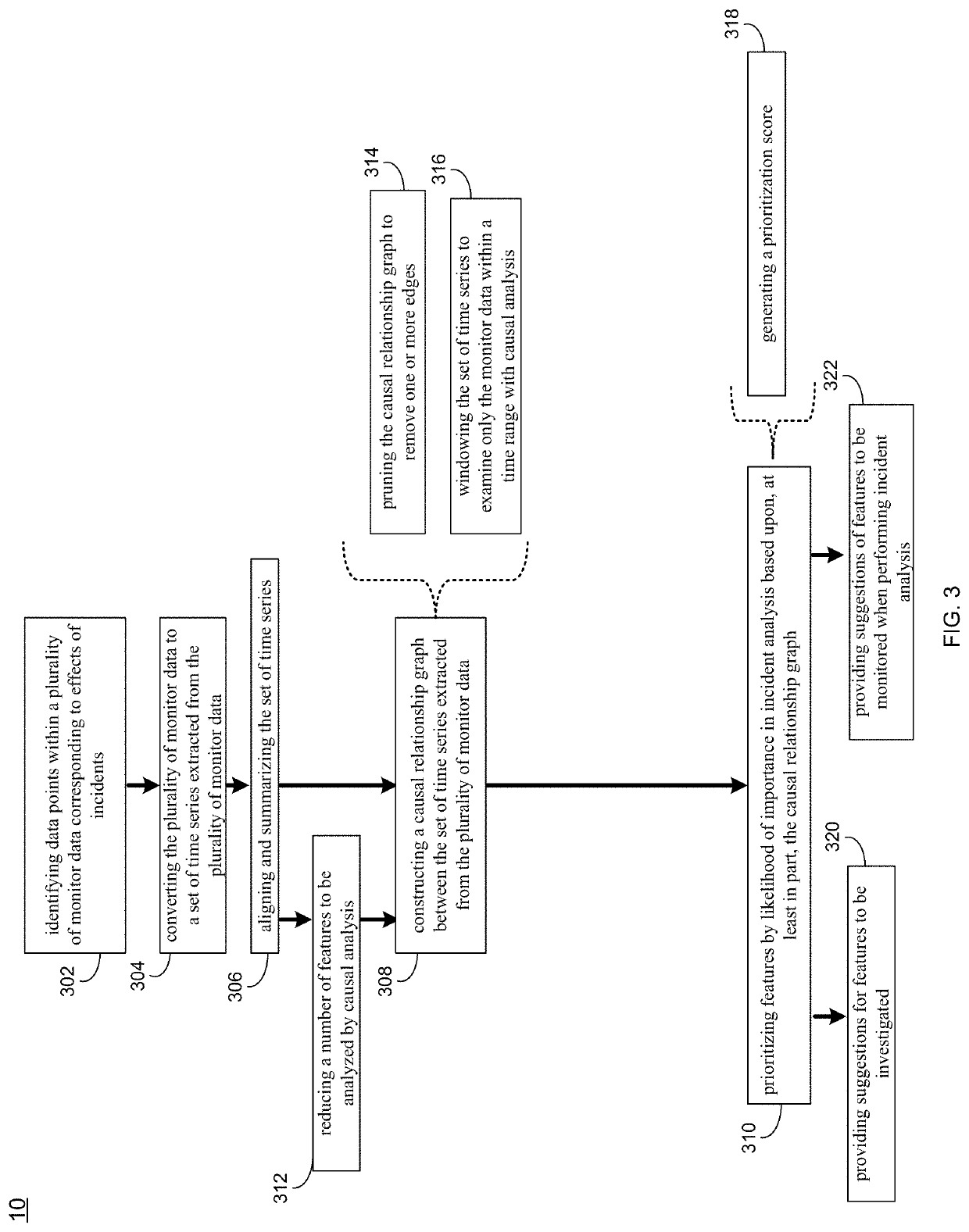
Prioritization of data collection and analysis for incident detection
A method, computer program product, and computer system for prioritization of data collection and analysis for incident detection. Data points within a plurality of monitor data corresponding to effects of incidents may be identified by a computing device. The plurality of monitor data may be converted to a set of time series extracted from the plurality of monitor data. The set of time series may be aligned and summarized. A causal relationship graph may be constructed between the set of time series extracted from the plurality of monitor data. Features may be prioritized by likelihood of importance in incident analysis based upon, at least in part, the causal relationship graph.
Owner:IBM CORP
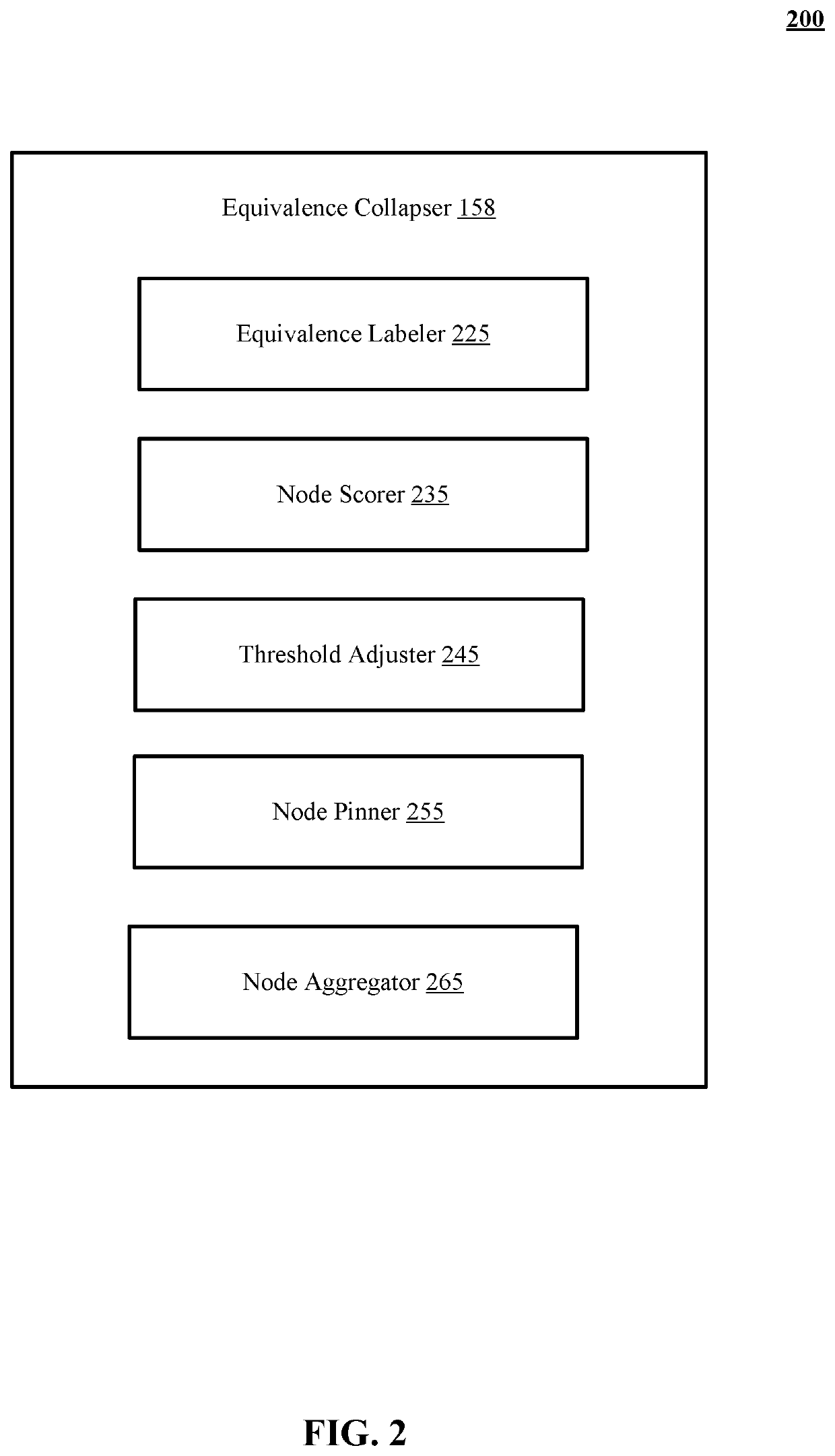
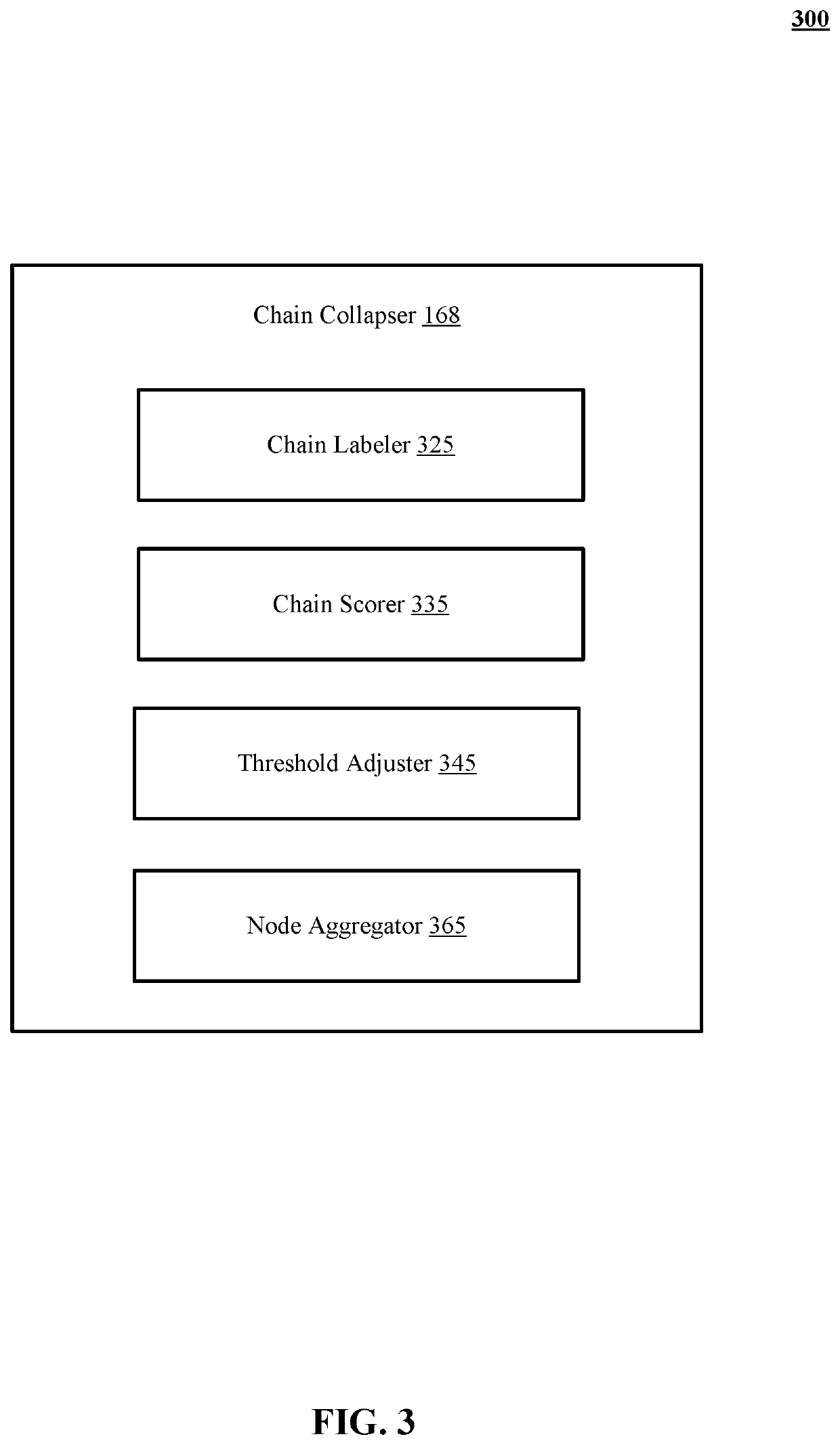
Systems and methods to show detailed structure in a security events graph
The technology disclosed includes a system to reduce clutter during graph presentation for security incident analysis. The system includes logic to score nodes potentially collapsed by equivalence, of indicated interest for security incident analysis, to prevent aggregation. The system includes logic to aggregate and hide equivalent nodes that have matching degrees, that are connected to matching nodes by matching edge types, and that have scores below a first selected threshold. The system does not collapse nodes that are interesting for security analysis and keeps them visible. The technology disclosed identifies chains of at least three nodes having degrees of 1 or 2, without branching from any node in the chain. The identified chains are collapsed into chain-collapsed single nodes. Two different cases of chains including whisker chains ending in a leaf node and chains connected at both ends to two other nodes are presented.
Owner:NETSKOPE INC
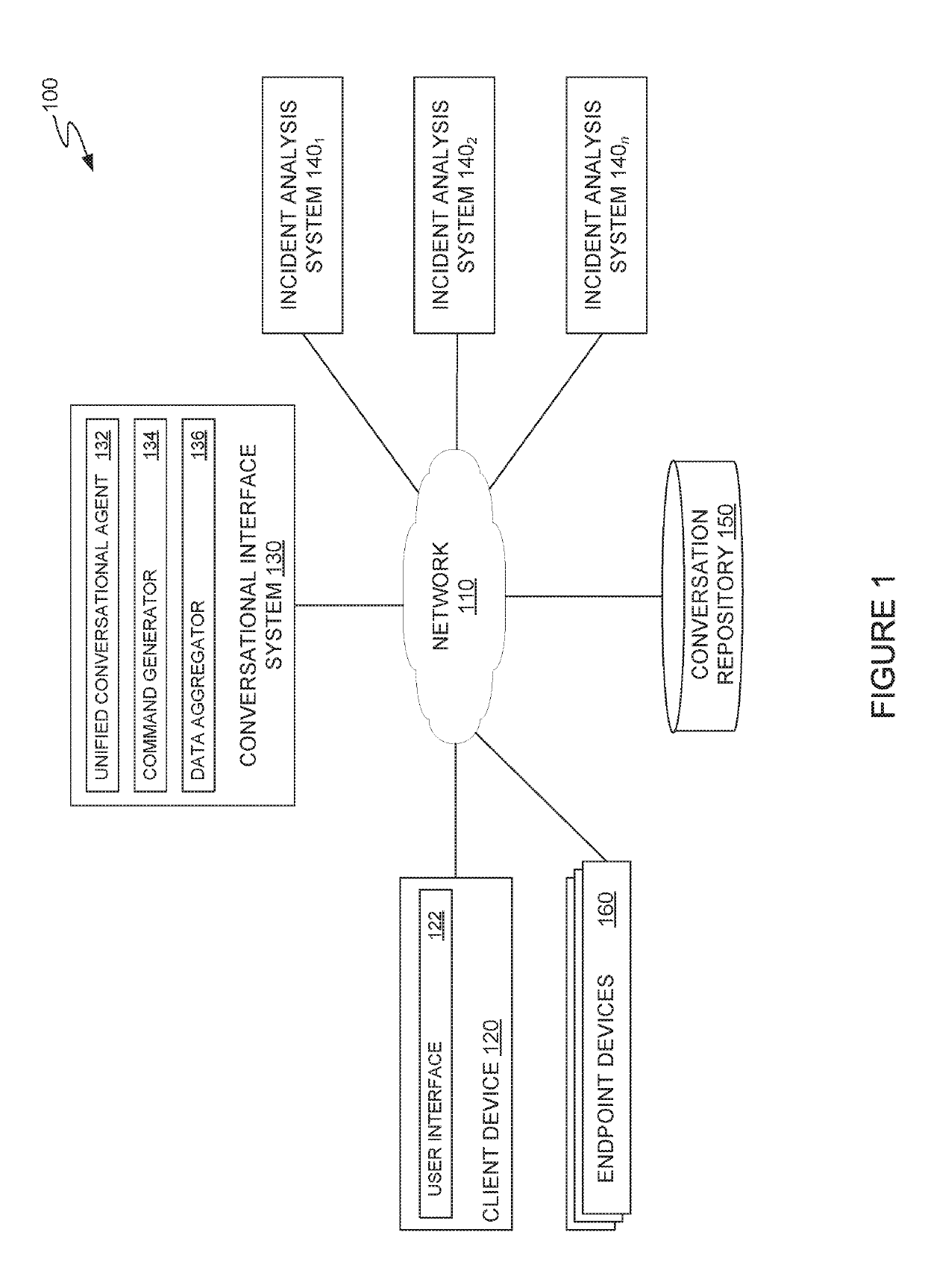
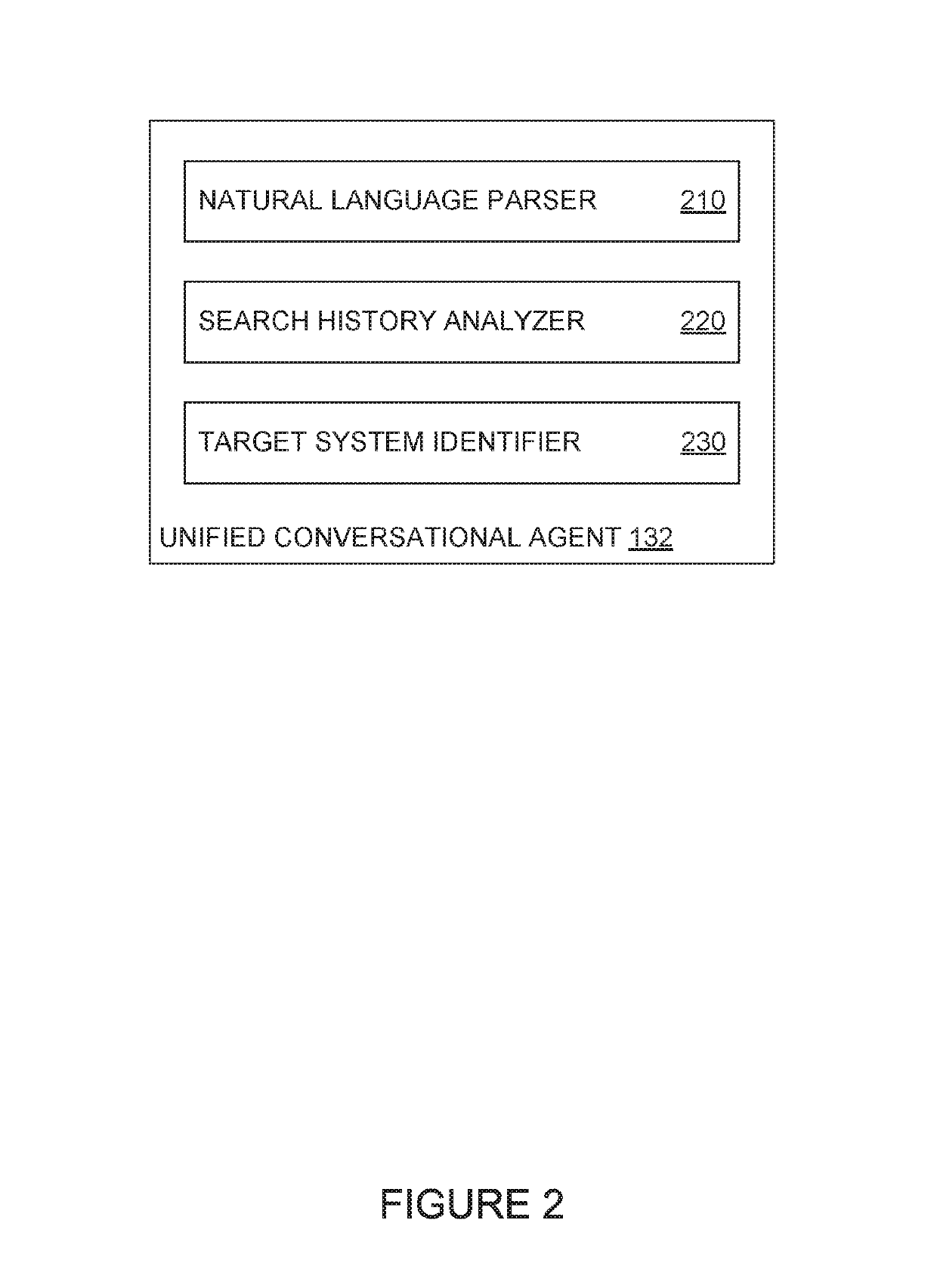
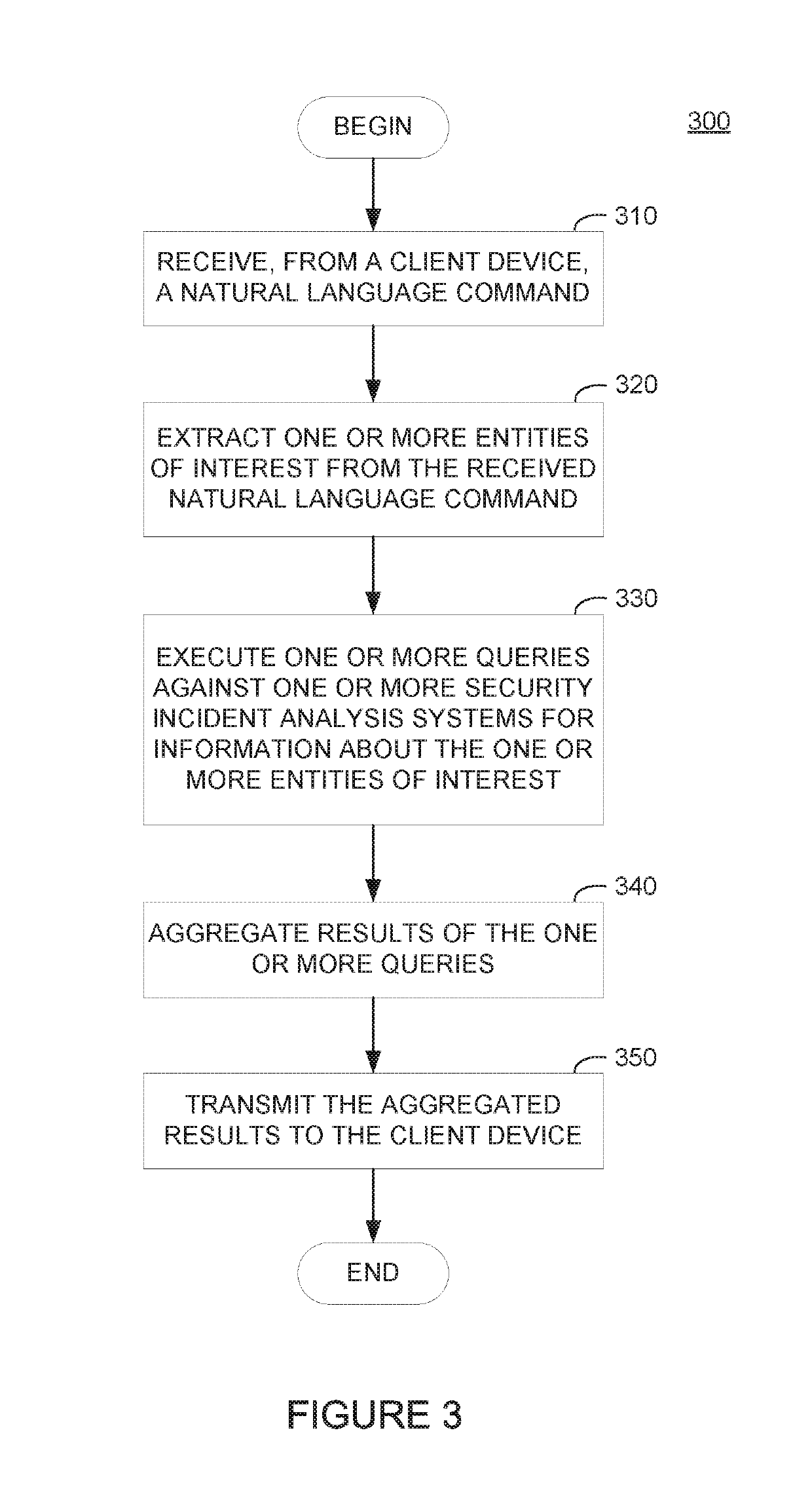
Handling computer security incidents through a unified conversational agent
ActiveUS10418036B1Avoid unsafe incidentsNatural language translationSemantic analysisIncident analysisData mining
The present disclosure relates to security incident analysis systems, and more specifically to searching across multiple security incident analysis systems through a unified conversational agent. One example method generally includes receiving, from a client device, a natural language command requesting information about a security incident from a first incident analysis system. One or more keywords related to the security incident are extracted from the natural language command. The unified conversational agent executes a search against the first incident analysis system and one or more second incident analysis systems for the information about the security incident based on the extracted one or more keywords and transmits, to the client device, an indication of the information about the security incident aggregated from the executed search against the first incident analysis system and the one or more second incident analysis systems.
Owner:CA TECH INC
Flow guide line law violation snapshot system
A diversion line illegal capture system, including a road section front-end system, a network transmission system and a monitoring center system, the road section front-end system is set at the entrance and exit of a highway ramp and has a microwave vehicle detector (radar), a capture camera and traffic event analysis instrument. The output end of the microwave vehicle detector is connected to the traffic event analyzer in one-way communication and the traffic event analyzer is connected to the capture camera in two-way communication. Send a trigger signal to the traffic event analyzer after the line, the traffic event analyzer controls the capture of the capture camera, the capture camera sends the captured vehicle photos back to the traffic event analyzer, and the output of the traffic event analyzer communicates with the monitoring system through the network transmission system Central system connection. The invention is convenient for the traffic law enforcement department to monitor whether the vehicle illegally rolls over the diversion line.
Owner:JIANGSU SANYI BUILDING TECH
Electric power secondary system safety incident analysis method for non-conformity strategy access
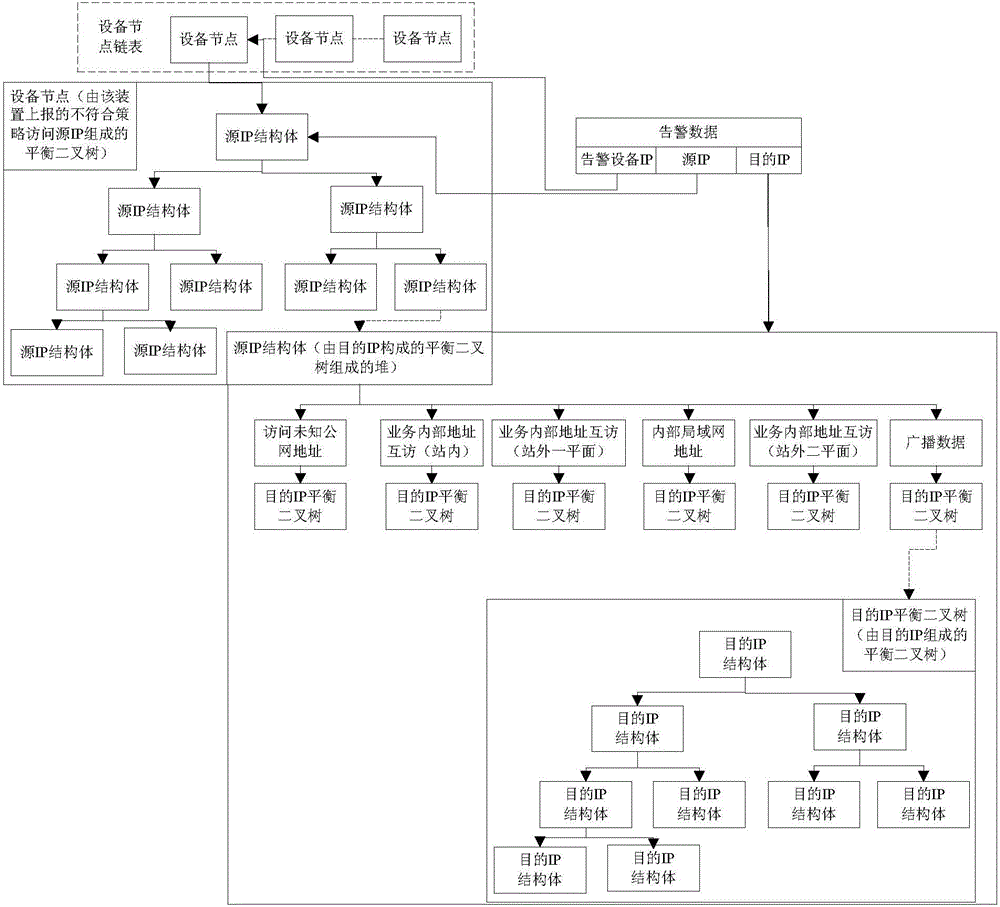
ActiveCN104601361ARealize intelligenceRealize practicalityData switching networksAlarm messageIncident analysis
The invention provides an electric power secondary system safety incident analysis method for non-conformity strategy access. The method includes the steps: (1) extracting a characteristic value of a new alarm when a new alarm is given; polling a device linked list in a real-time non-conformity strategy access alarm list, judging whether the new alarm is positioned in a node of the device linked list or not, and turning to the step (2) if the new alarm is positioned in the node of the device linked list; turning to the step (3) if not; (2) indicating the new alarm if the new alarm is positioned in the node of the device linked list, and associating the new alarm with an alarm maintained by the node; (3) finding a corresponding position in the device linked list and inserting the new alarm if not; (4) updating the real-time non-conformity strategy access alarm list. By the aid of association mining, numerous non-conformity strategy access alarm messages appearing on the site is analyzed twice to form a more significant alarm message, and function support is provided for rapid positioning and timely processing of the alarm.
Owner:BEIJING KEDONG ELECTRIC POWER CONTROL SYST +1
Method and system for analyzing and processing fault tripping event of high-voltage transmission long line
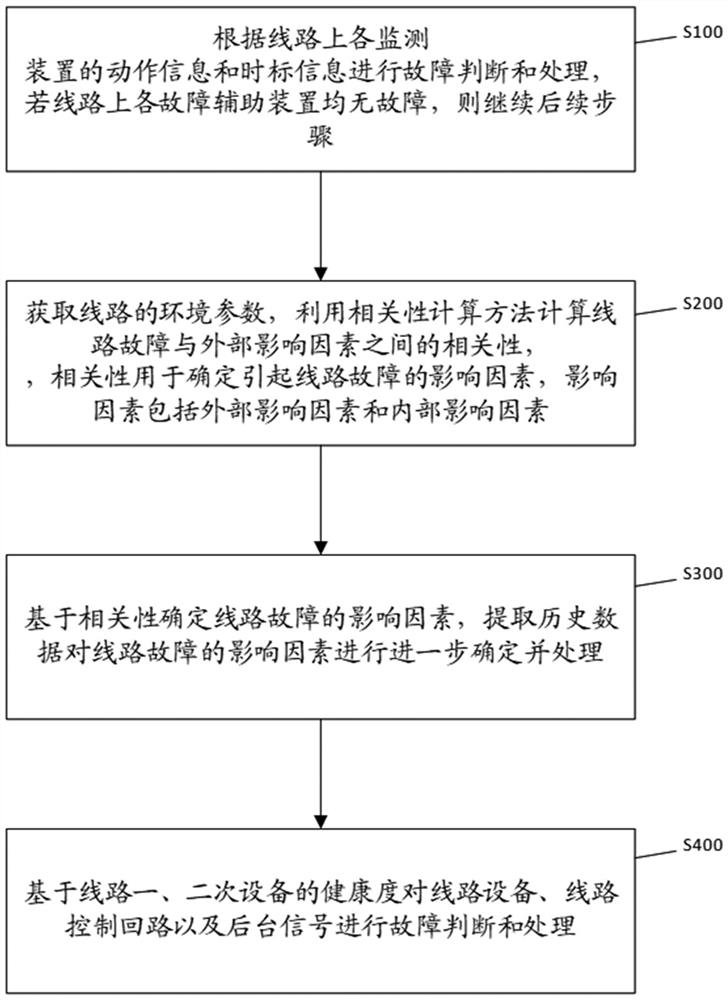
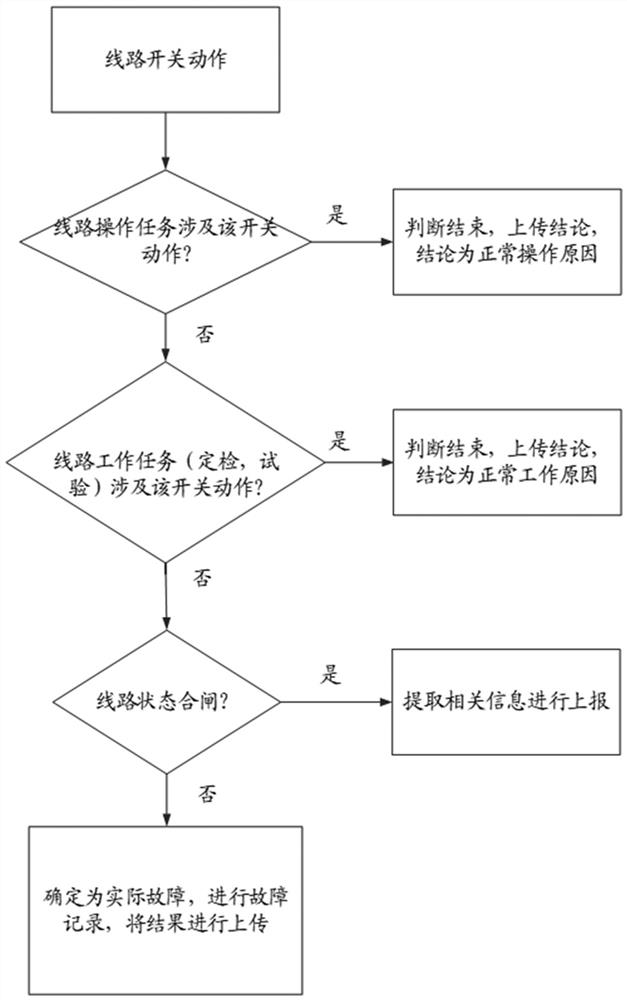
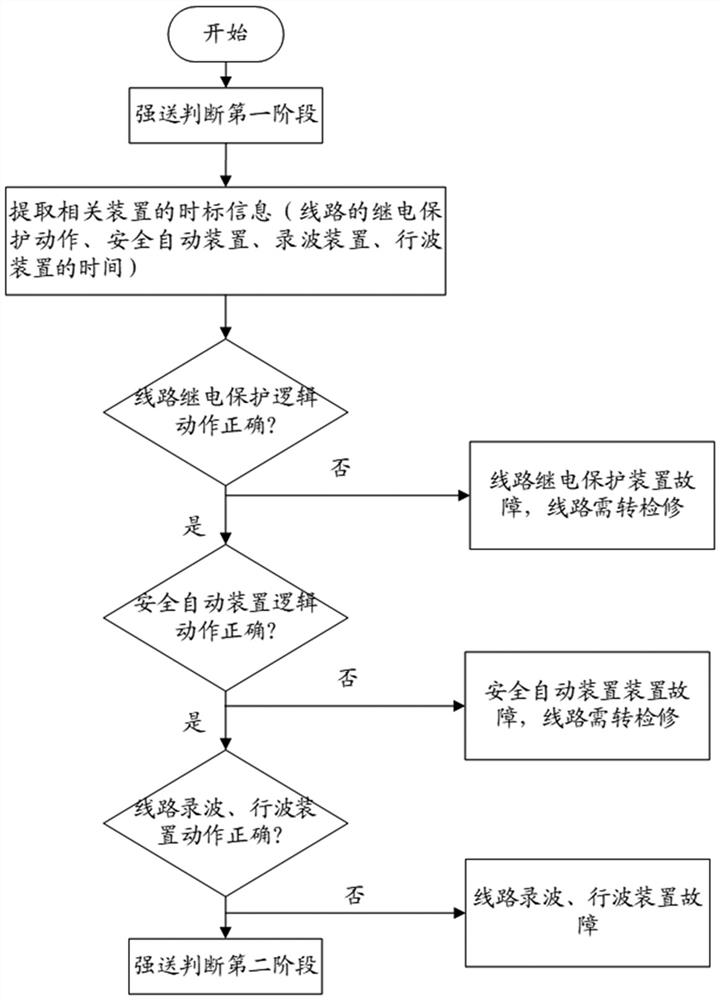
ActiveCN114696467AEasy to analyzeShort analysis timeEmergency protective circuit arrangementsCharacter and pattern recognitionIncident analysisCalculation methods
The invention provides a high-voltage transmission long line fault trip event analysis processing method and system, and the method comprises the steps: carrying out the fault judgment and processing according to the motion information and time mark information of each monitoring device on a line, and continuing the subsequent steps if each monitoring device on the line has no fault; acquiring environmental parameters of the line, and calculating the correlation between the line fault and the external influence factors by using a correlation calculation method; determining influence factors of the line fault based on correlation, and extracting historical data to further determine and process the influence factors of the line fault; and performing fault judgment and processing on the line equipment, the line control loop and background signals based on the health degrees of the line primary and secondary equipment. According to the invention, the fault conditions of the power transmission line and related devices are effectively analyzed and judged by integrating monitoring data in various aspects, help can be provided for workers to quickly and comprehensively analyze line problems, the analysis time is shortened, and the working efficiency is improved.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
Administering incident pools for incident analysis
Methods, apparatuses, and computer program products for administering incident pools for incident analysis in a distributed processing system are provided. Embodiments include an incident analyzer receiving a plurality of incidents from an incident queue. The incident analyzer also assigns each received incident to an incident pool having a predetermined initial period of time. The predetermined initial period of time is the time within which the incident pool is open to the assignment of incidents. The incident analyzer calculates an arrival rate that incidents are assigned to the incident pool. The incident analyzer also extends based on the arrival rate, for each incident assigned to the incident pool, the predetermined initial period of time by a particular period of time.
Owner:IBM CORP
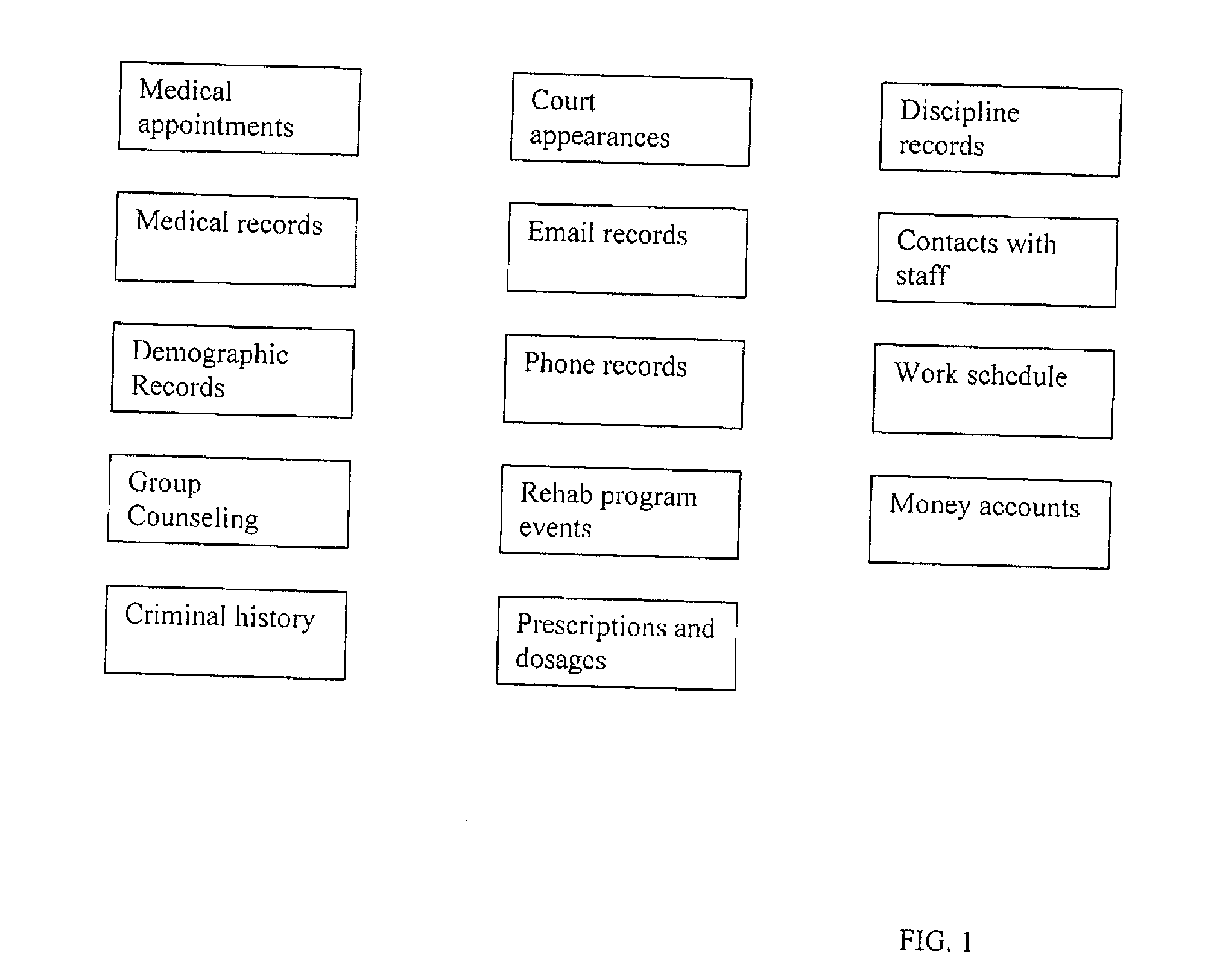
Mechanism for Multiple System Common Scheduling and Analysis of Unrelated Events in a Corrections Facility
ActiveUS20130262521A1Easy to useData processing applicationsDigital data processing detailsDirect entryIncident analysis
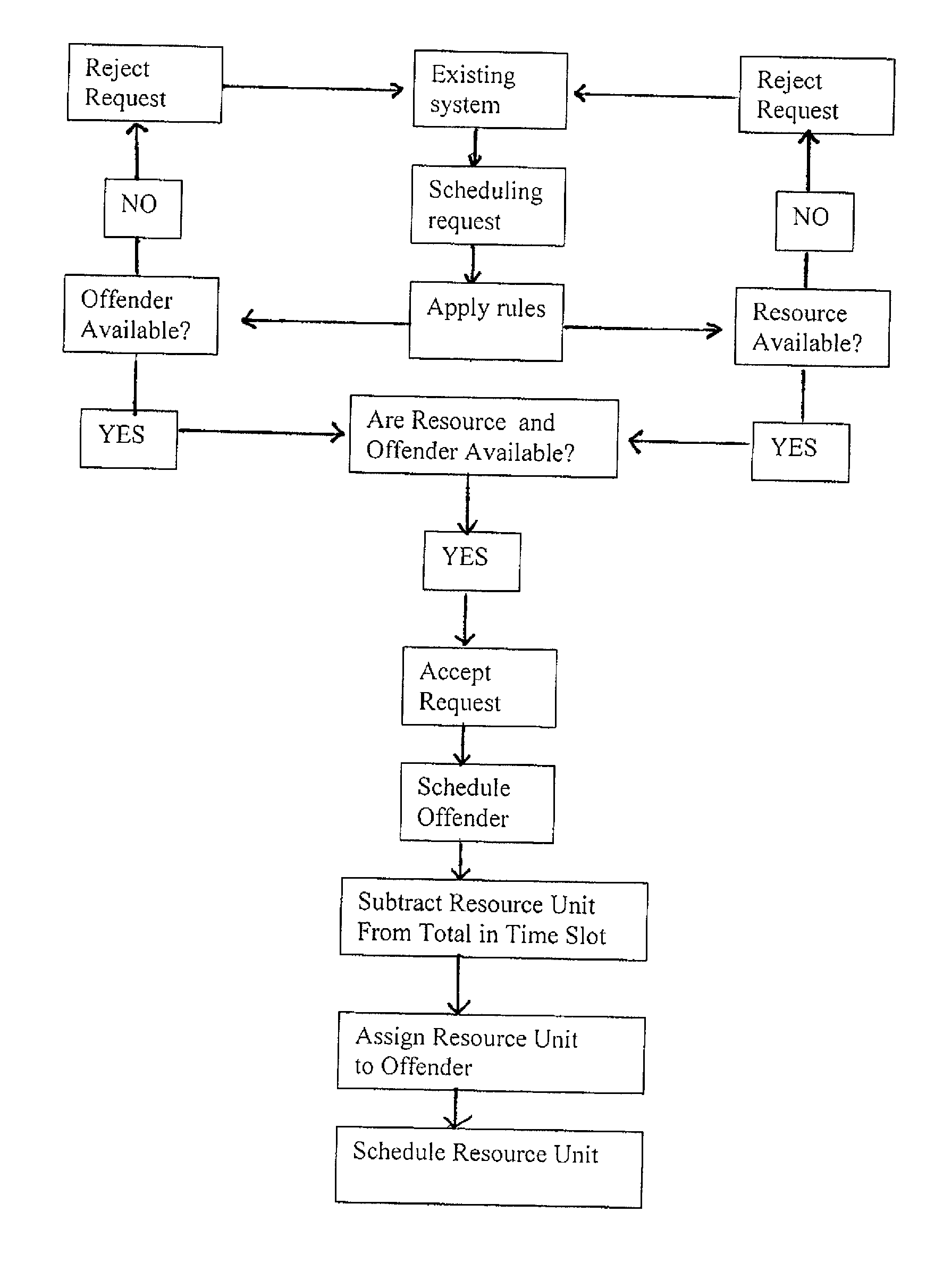
A method is presented for use in correctional facilities to manage resources. Particularly, the method includes using a scheduling engine capable of receiving scheduling requests from other systems or direct entry of scheduling data and which is equipped to provide reports that inform the facility of the schedules of all inmates, transportation requirements, and space accommodations. The method may be employed for evaluating the needs for transportation and space and may also be used to generate reports that show relationships between inmates based on activities, locations, and time.
Owner:ADVANCED TECH GRP
Security policy management using incident analysis
InactiveUS20130179936A1Understand perceived and measured effectiveness and costReduce in quantityError detection/correctionForecastingData setIncident analysis
A security analytics system receives incident data (from an incident management system) and security policy information (from a security policy management system). The security analytics system evaluates these data sets against one another, preferably using a rules-based analysis engine. As a result, the security analytics system determines whether a particular security policy configuration (as established by the security policy management system) needs to be (or should be) changed, e.g., to reduce the number of incidents caused by a misconfiguration, to increase its effectiveness in some manner, or the like. As a result of the evaluation, the security analytics system may cause a policy to be updated automatically, notify an administrator of the need for the change (and the recommendation), or take some other action to evolve one or more security policies being enforced by the security policy management system.
Owner:IBM CORP
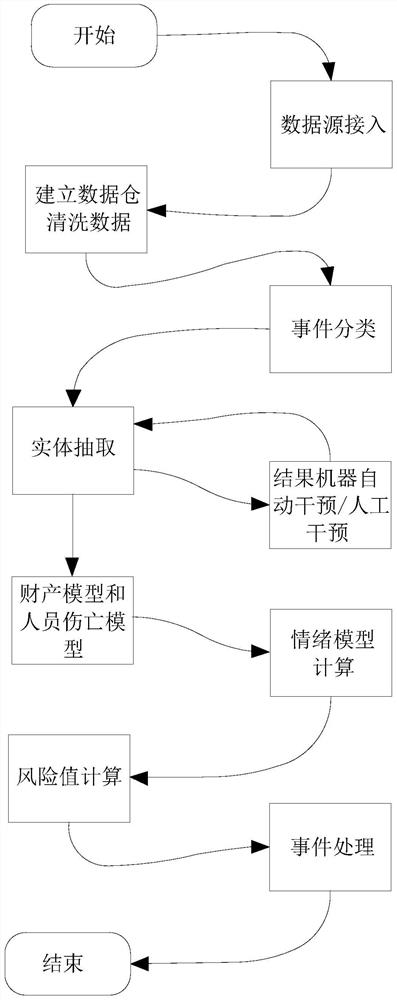
Natural language processing method for early warning risk upgrading event
PendingCN114328907AResolve conflicts and disputesData processing applicationsCharacter and pattern recognitionAnalytic modelIncident analysis
The invention provides a natural language processing method for early warning a risk upgrading event, which comprises the following steps of: S1, establishing a data warehouse, and accessing a data source into the data warehouse; s2, on the basis of natural language processing, event information in a data source is extracted and processed through an event analysis related model; and S3, inputting a result value of the event analysis correlation model into an early warning analysis model, and carrying out risk upgrading event upgrading risk value analysis and early warning. Various elements in the event are scientifically and efficiently analyzed through a natural language processing technology, the risk analysis model is obtained by combining massive event data training, the risk of converting a certain event into a high-risk case can be accurately obtained, related workers can intervene in the event in advance according to the risk, contradictory disputes are resolved, and the risk analysis efficiency is improved. And the occurrence of high-risk cases is prevented.
Owner:浙江嘉兴数字城市实验室有限公司
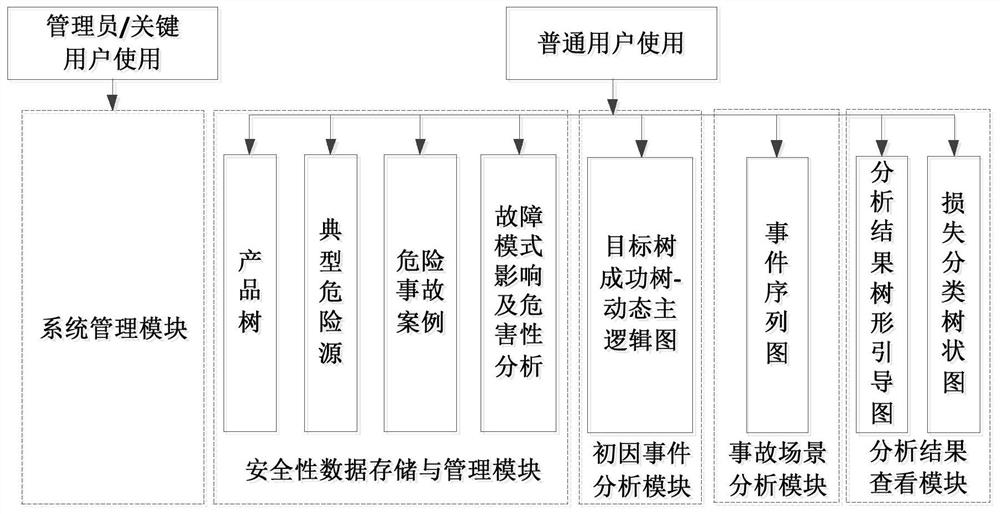
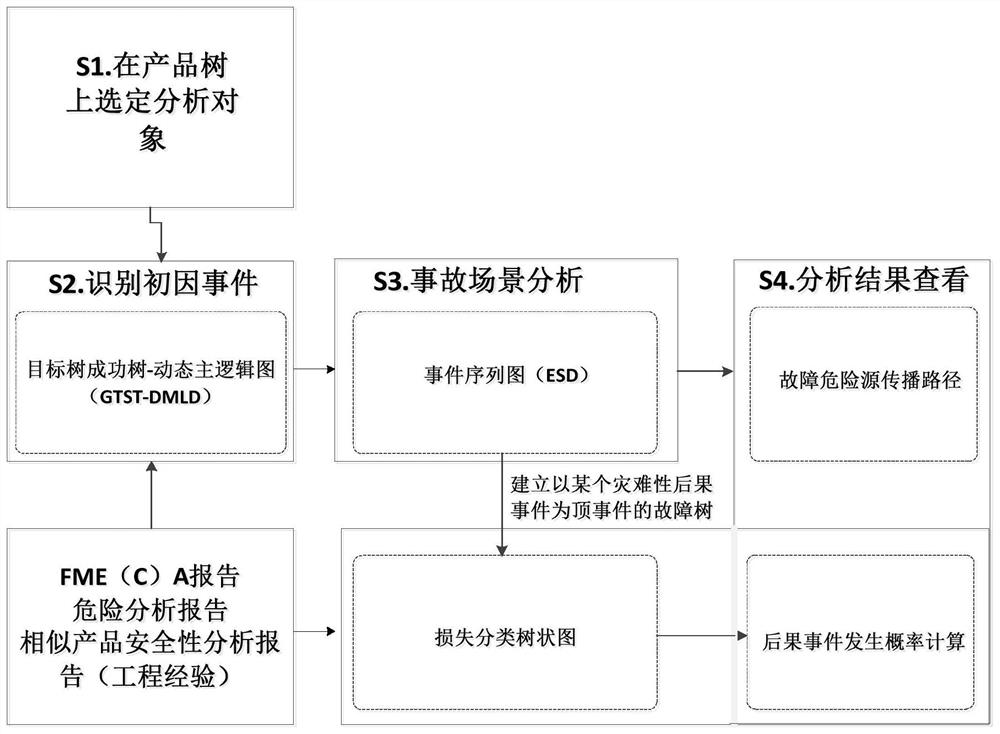
An Analysis System for Identifying Fault Hazard Sources of Air Defense Missile Weapon System
ActiveCN108197847BReduce the level of accident riskRealize analysisResourcesIncident analysisWeapon system
Owner:BEIJING INST OF ELECTRONICS SYST ENG
Prioritization of data collection and analysis for incident detection
A method, computer program product, and computer system for prioritization of data collection and analysis for incident detection. Data points within a plurality of monitor data corresponding to effects of incidents may be identified by a computing device. The plurality of monitor data may be converted to a set of time series extracted from the plurality of monitor data. The set of time series may be aligned and summarized. A causal relationship graph may be constructed between the set of time series extracted from the plurality of monitor data. Features may be prioritized by likelihood of importance in incident analysis based upon, at least in part, the causal relationship graph.
Owner:INT BUSINESS MASCH CORP
Selecting during a system shutdown procedure, a restart incident checkpoint of an incident analyzer in a distributed processing system
InactiveUS9361184B2Interprogram communicationRedundant operation error correctionIncident analysisComputer program
Owner:INT BUSINESS MASCH CORP
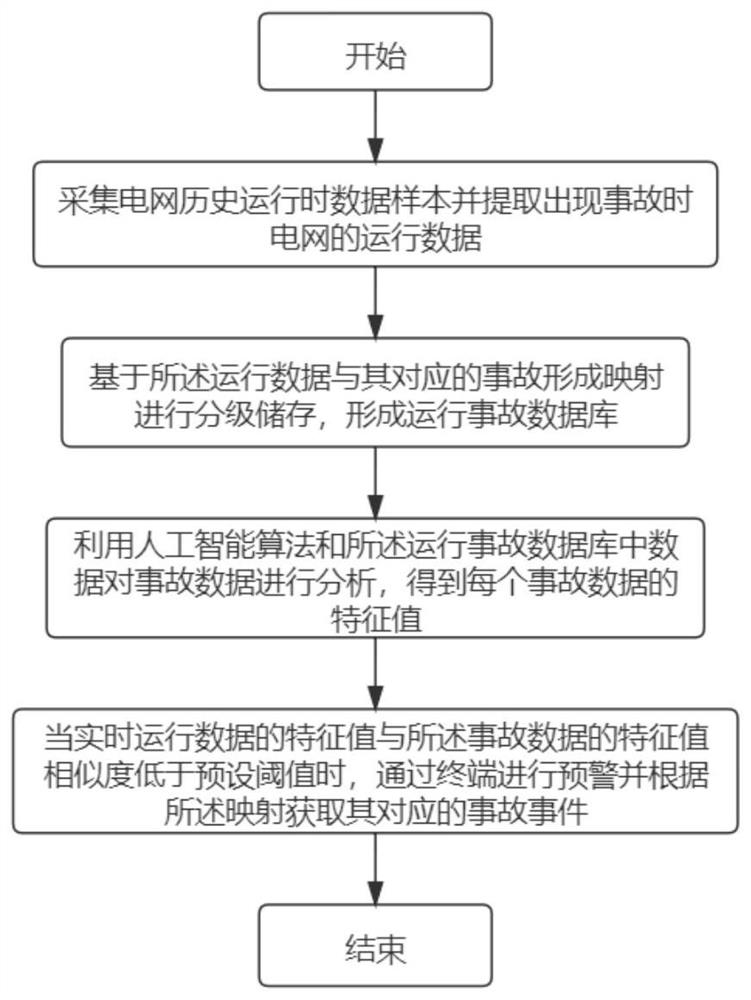
Power grid accident event analysis method based on artificial intelligence
PendingCN113902251AEasy to implementImprove efficiencyCharacter and pattern recognitionResourcesAlgorithmIncident analysis
The invention discloses a power grid accident event analysis method based on artificial intelligence. The method comprises the following steps: collecting a data sample during historical operation of a power grid and extracting operation data of the power grid when an accident occurs; forming mapping based on the operation data and corresponding accidents, performing hierarchical storage, and forming an operation accident database; analyzing the accident data by using an artificial intelligence algorithm and operating data in the accident database to obtain a characteristic value of each accident data; and when the similarity between the characteristic value of the real-time operation data and the characteristic value of the accident data is lower than a preset threshold value, performing early warning through the terminal and obtaining a corresponding accident event according to mapping. Through intelligent analysis of power grid accidents, the efficiency and coordination of power grid dispatching work are improved, and promotion of an intelligent power grid is facilitated.
Owner:GUANGDONG POWER GRID CO LTD +1
A method and device for analyzing nuclear power plant operating events
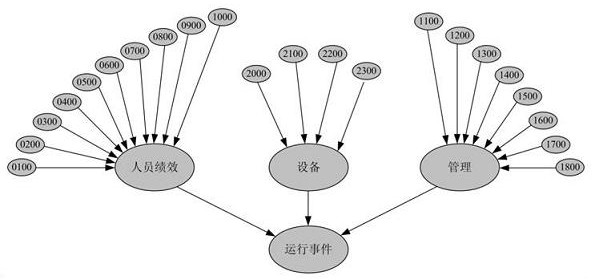
ActiveCN109345121BImprove analysis efficiencyImprove analysis accuracyMathematical modelsResourcesNuclear plantNuclear power
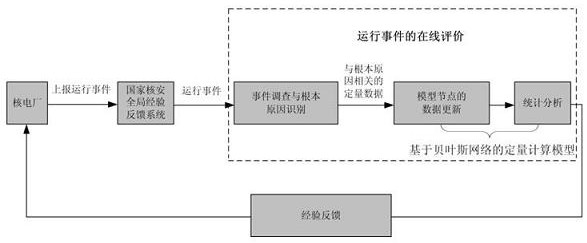
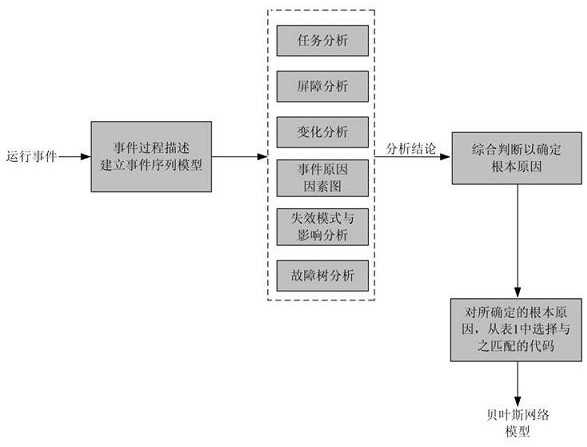
A method and device for analyzing nuclear power plant operating events, relating to the field of nuclear power plant safety technology, wherein the method includes step 1, investigating the operating event, forming an operating event report and uploading it to the experience feedback system of the National Nuclear Safety Administration; step 2 1. The analysis module conducts qualitative analysis on the operation event and identifies the root cause of the operation event; step three, imports the root cause quantitative data obtained in step two into the quantitative calculation module built based on the Bayesian network model, quantitative calculation and Update the occurrence frequency of such operational events in real time; step 4, determine the experience of preventing and reducing the occurrence of such operational events based on the calculation results obtained in step 3, and feed back the obtained experience to the operating organizations of nuclear power plants. The invention comprehensively uses a qualitative analysis program and a quantitative calculation tool to analyze the operation event of the nuclear power plant, improves the analysis efficiency and accuracy of the operation event of the nuclear power plant, and is beneficial to reduce the occurrence probability of the operation event.
Owner:HUNAN INST OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com