Electric power secondary system safety incident analysis method for non-conformity strategy access
A technology for power secondary systems and security incidents, applied to electrical components, transmission systems, digital transmission systems, etc., can solve problems such as weak information correlation, high database pressure, and on-site users struggling to solve various alarms, etc., to achieve Reduce time complexity, achieve precise positioning, and achieve intelligent effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The technical content of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
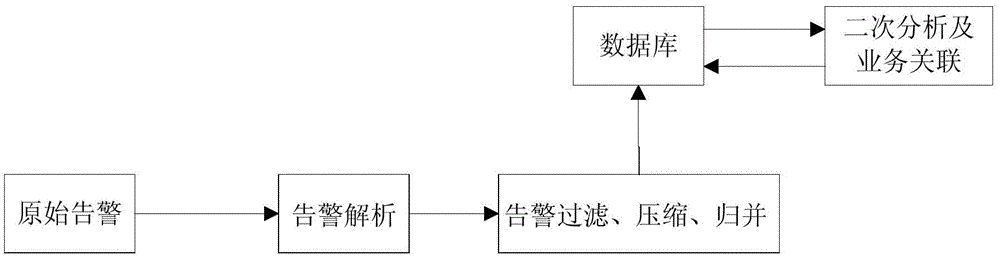
[0029] figure 1 It is an overall flow chart of the analysis method for the safety event of the power secondary system provided by the present invention. Among them, the original alarm data is processed by the agent module, and then processed by the alarm parsing and merging module (Logagent), and then placed in the database. The alarm secondary analysis module (loganlyse) reads the data from the database for secondary analysis and business association, and processes The results are put back into the database.
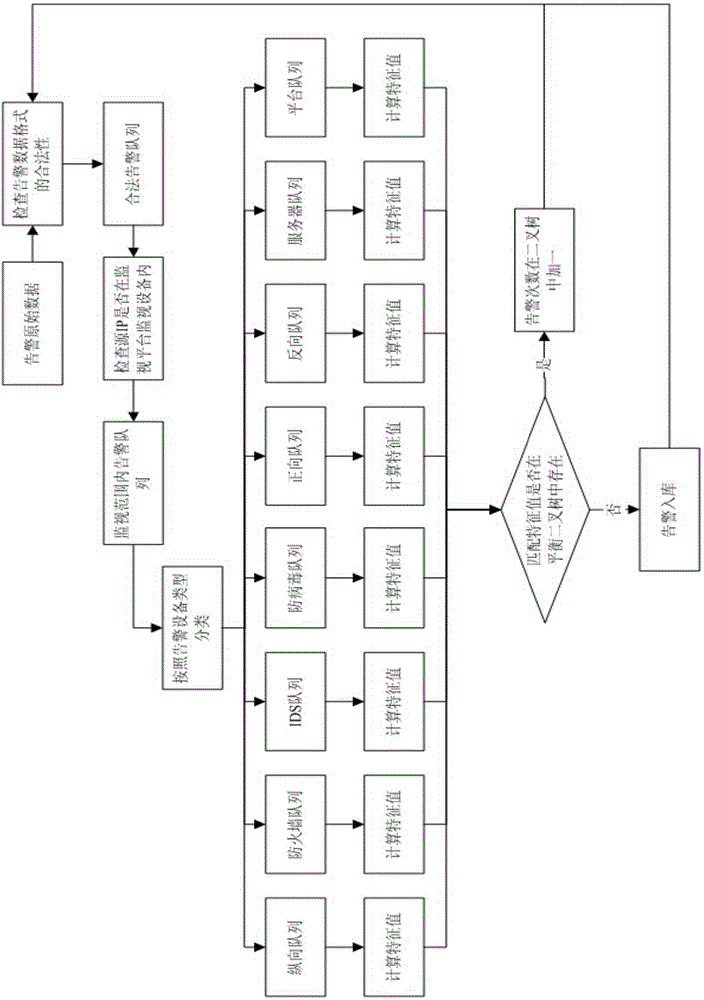
[0030] (1) Alarm parsing and merging.
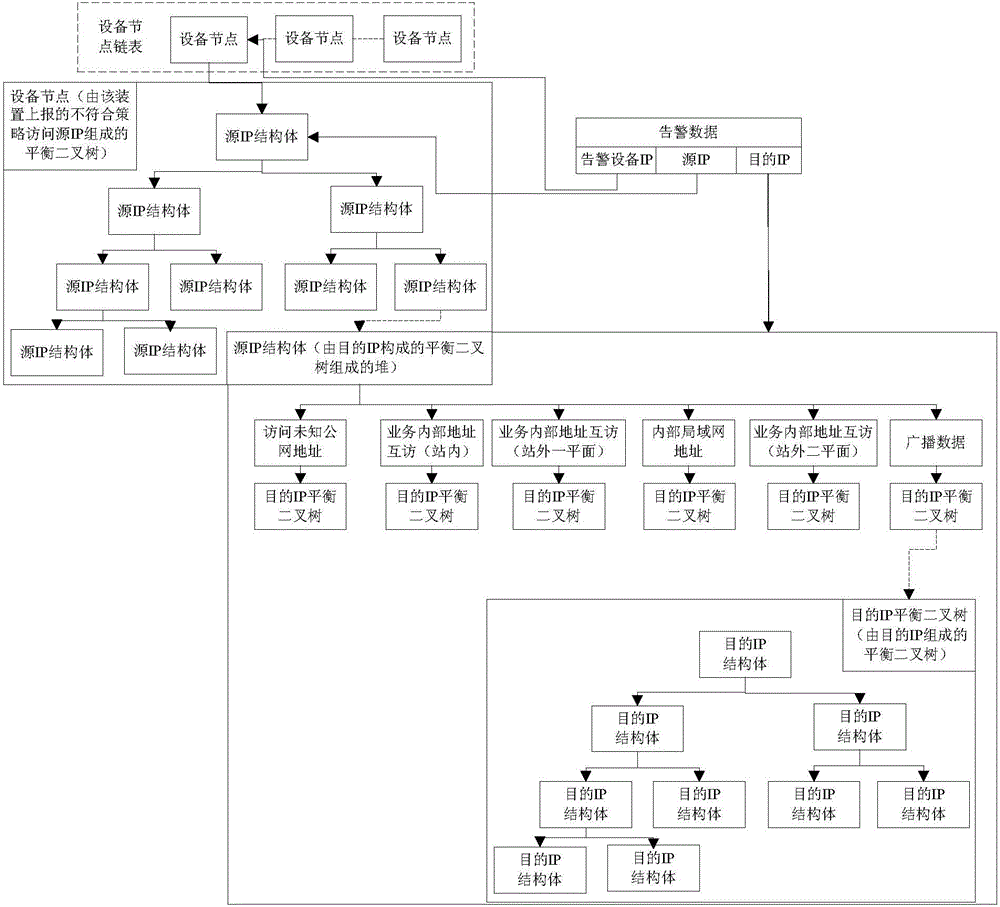
[0031] Such as figure 2 As shown, in the Chinese patent application with the application publication number CN103607291A, a method for analyzing and merging alarms for the intranet security monitoring platform of the power secondary system is disclosed, which includes t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com