Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
138 results about "Operating system level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An operating system is the lowest-level program running on a computer. The operating system provides software interfaces for the computer hardware, basic input and output functions, file and network management, and memory allocation. On top of these functions the user may run a command line, web,...
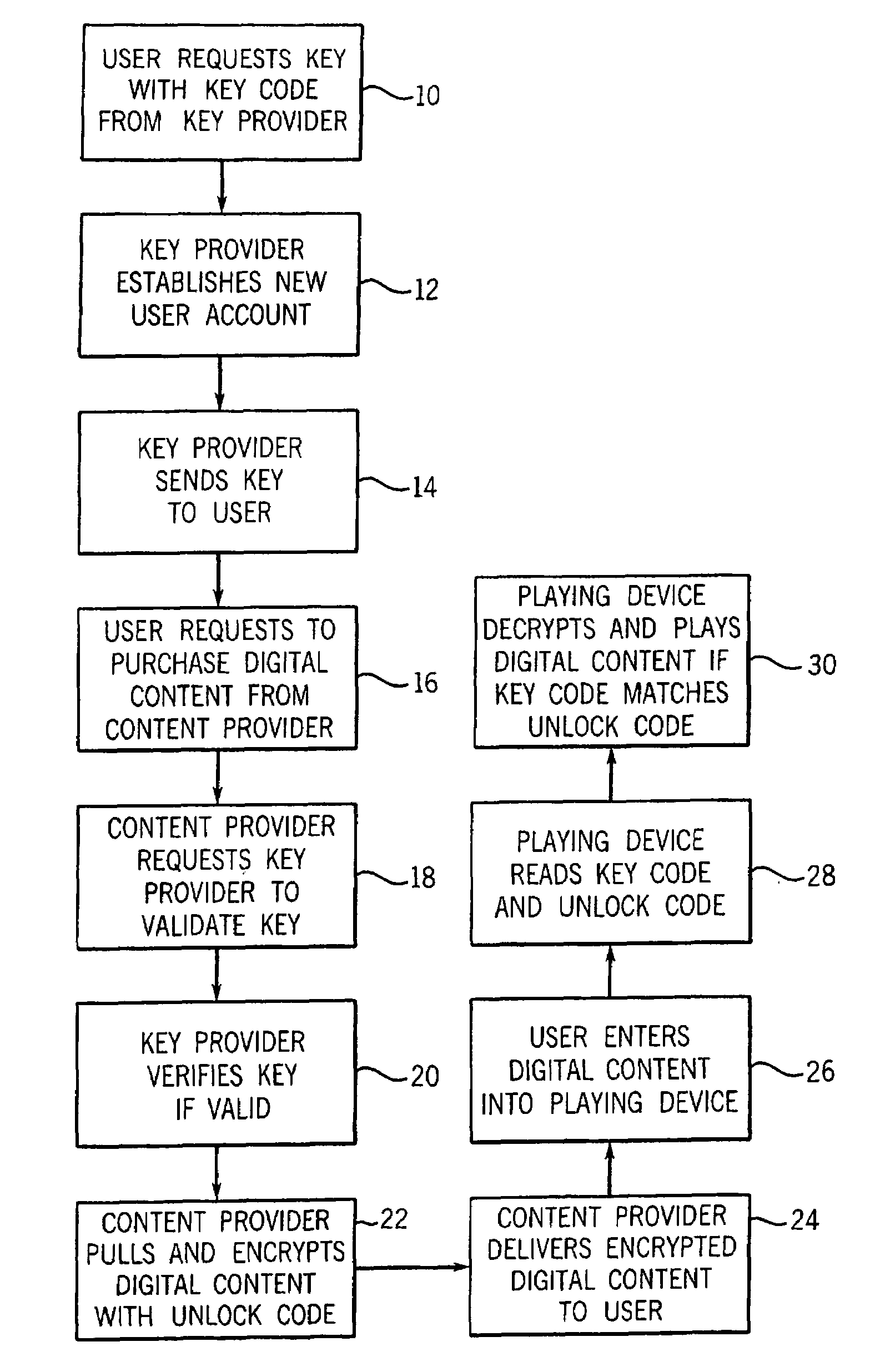
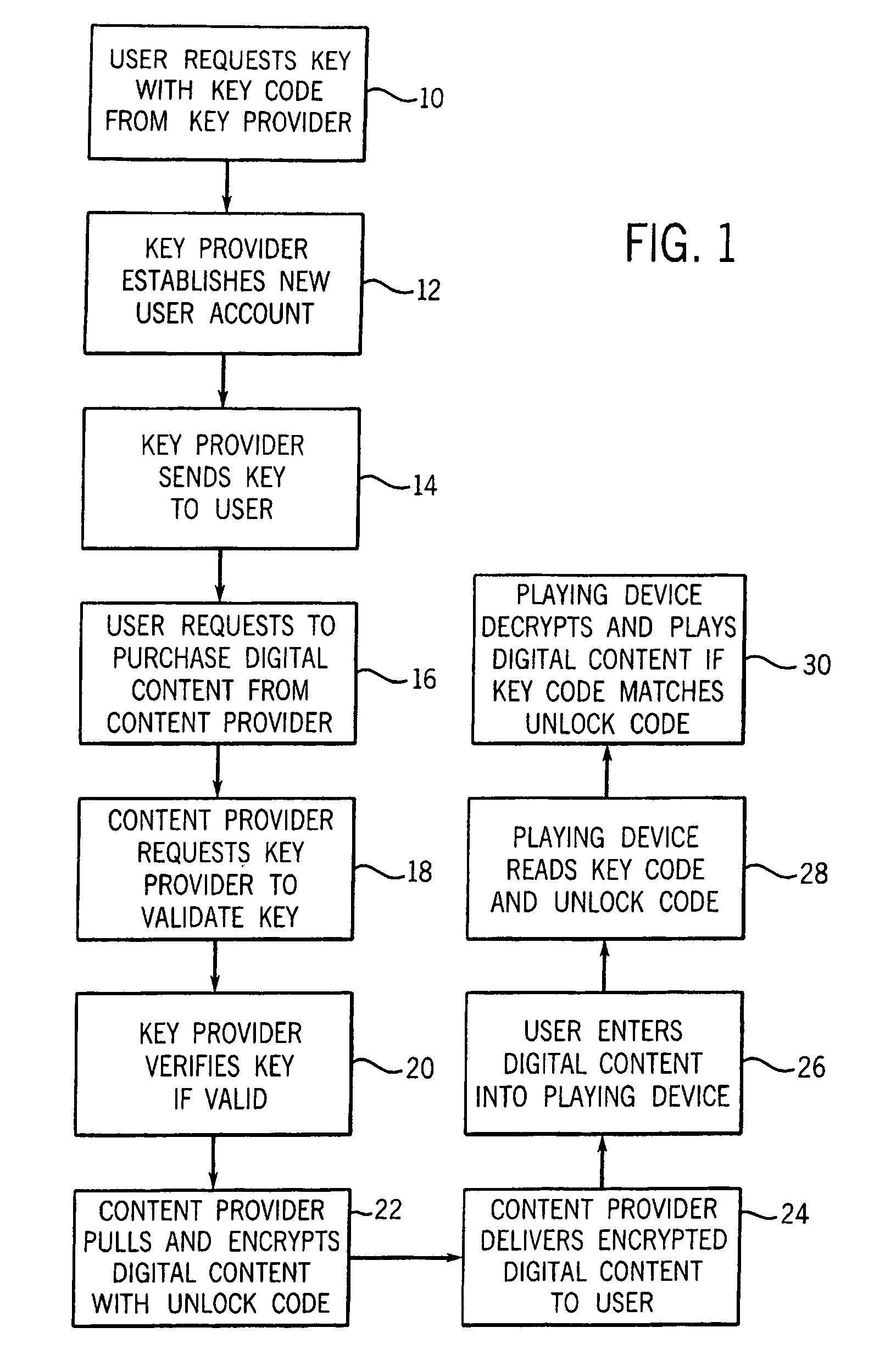
Usage pattern based user authenticator
InactiveUS6334121B1Control damagePreventing executionDigital computer detailsComputer security arrangementsOperational systemOperating system level
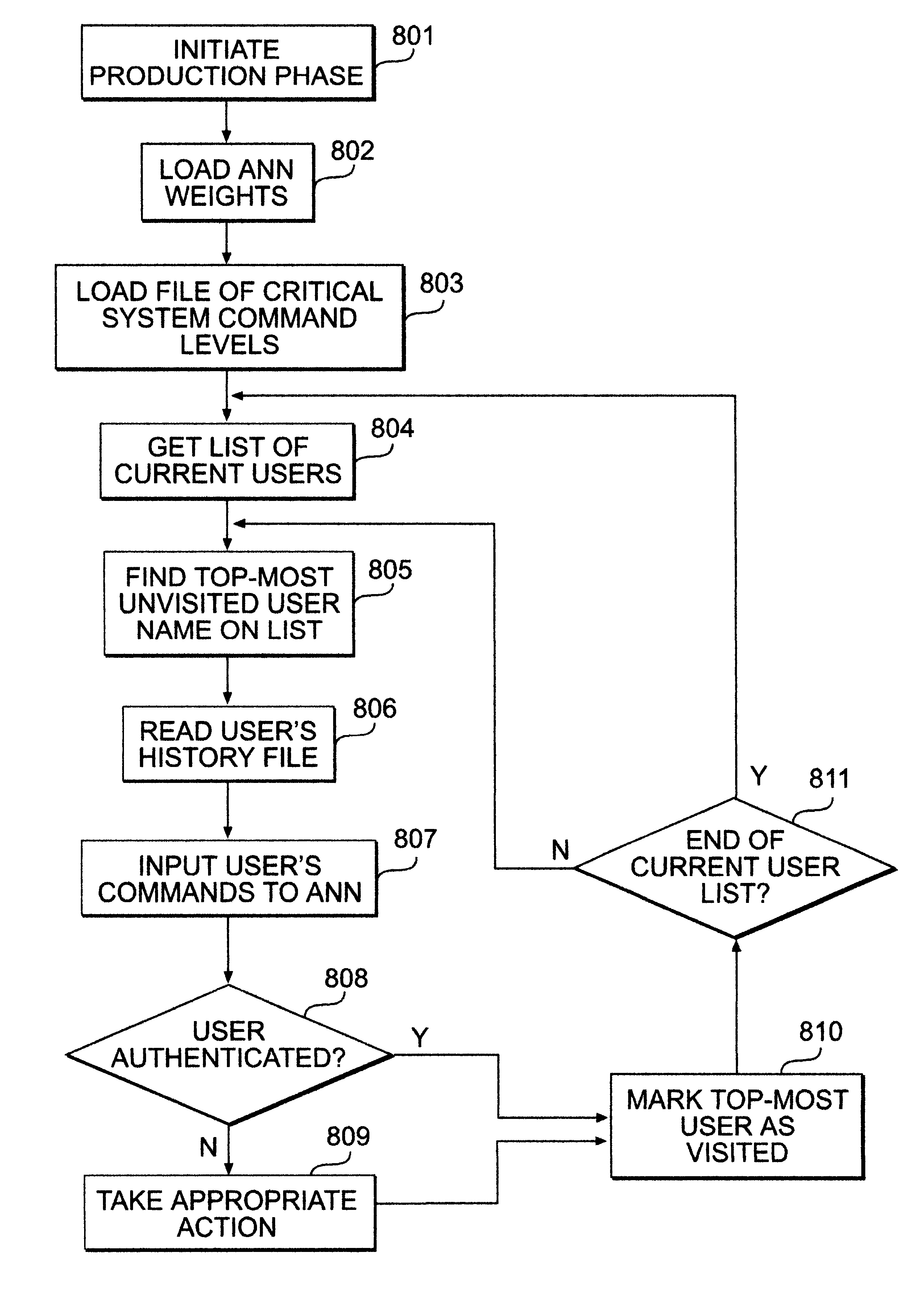
A usage based pattern authenticator for monitoring and reporting on user usage patterns in an operating system using a set of security rules and user usage patterns. This computer system security tool authenticates users at the operating system level in multi-user operating systems. It supports system administrators in limiting the ability of unauthorized users to disrupt system operations using a neural network and set of rules to track usage patterns and flag suspicious activity on the system. The data collection mode collects and stores usage patterns of authenticated users. The training mode trains an artificial neural network and sets the interconnection weights of the network. The production mode monitors and reports on usage patterns, and optionally performs automatic responses when confronted with non-authenticated users.
Owner:VIRGINIA COMMONWEALTH UNIV
System for managing radio modems
ActiveUS7949364B2Avoid collisionImprove efficiencySubstation equipmentRadio transmissionOperational systemModem device
Owner:NOKIA TECH OY
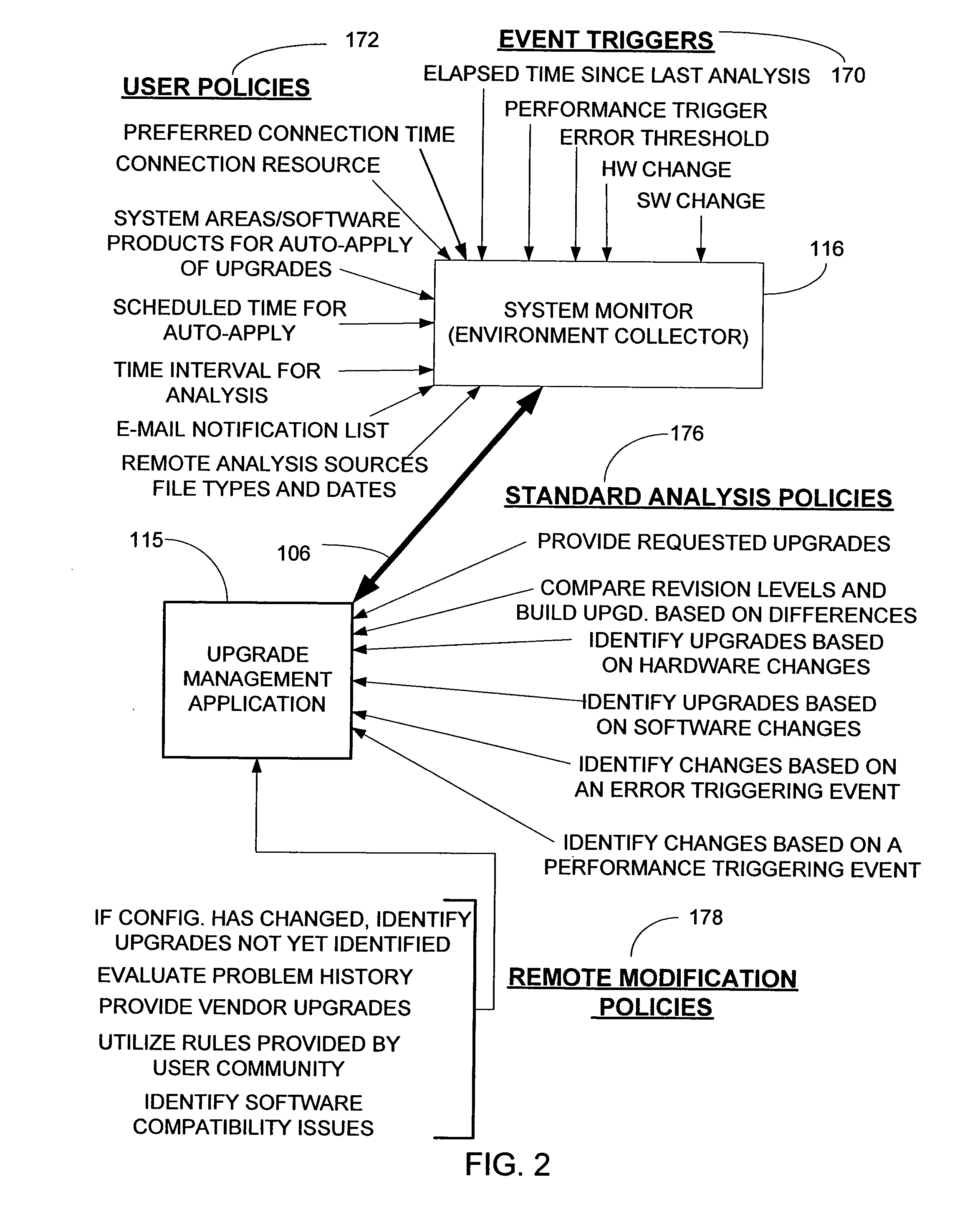
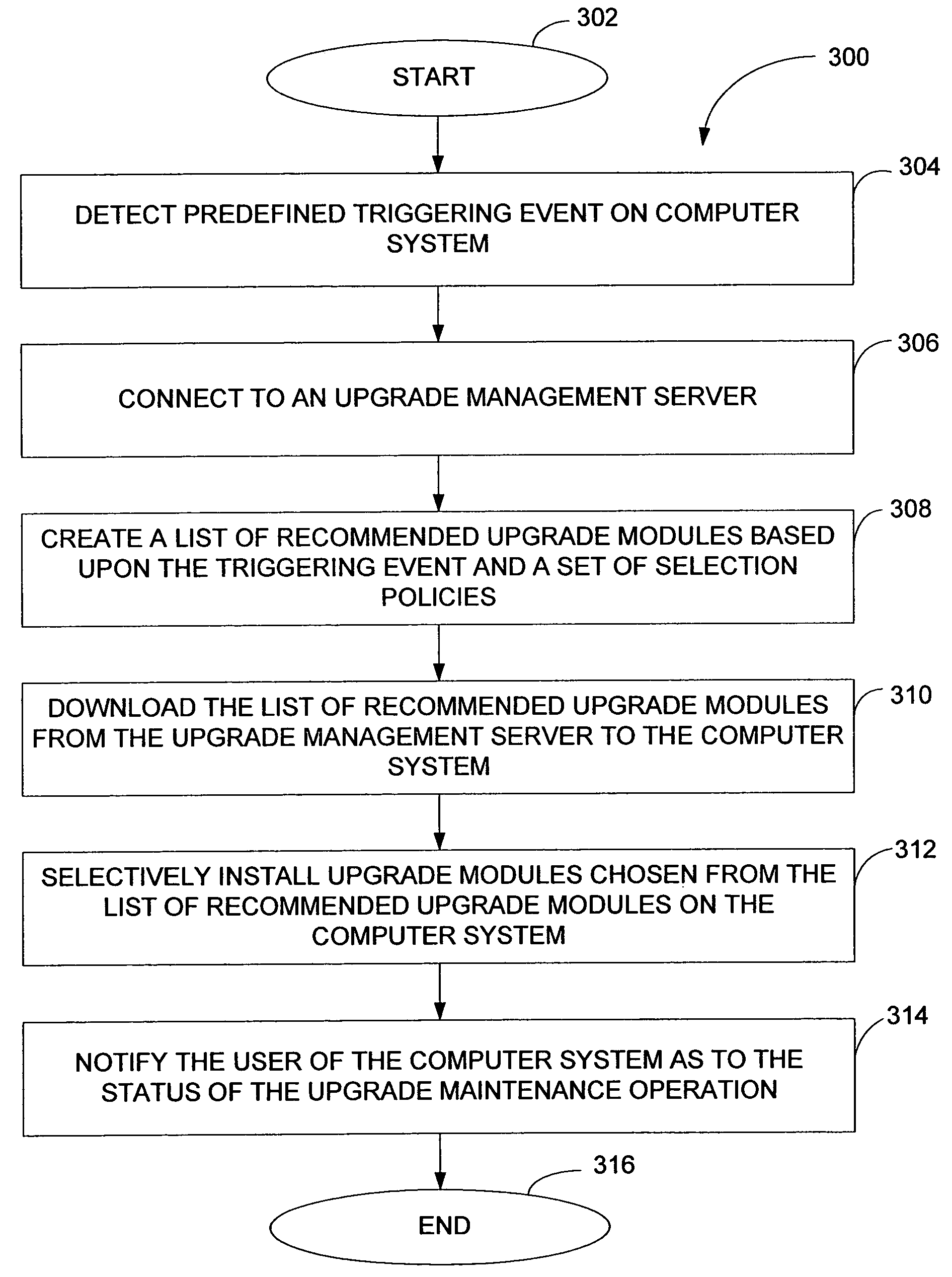
Computer application and methods for autonomic upgrade maintenance of computer hardware, operating systems and application software
ActiveUS20050066019A1Providing such maintenanceDigital computer detailsMultiprogramming arrangementsOperational systemComputer module
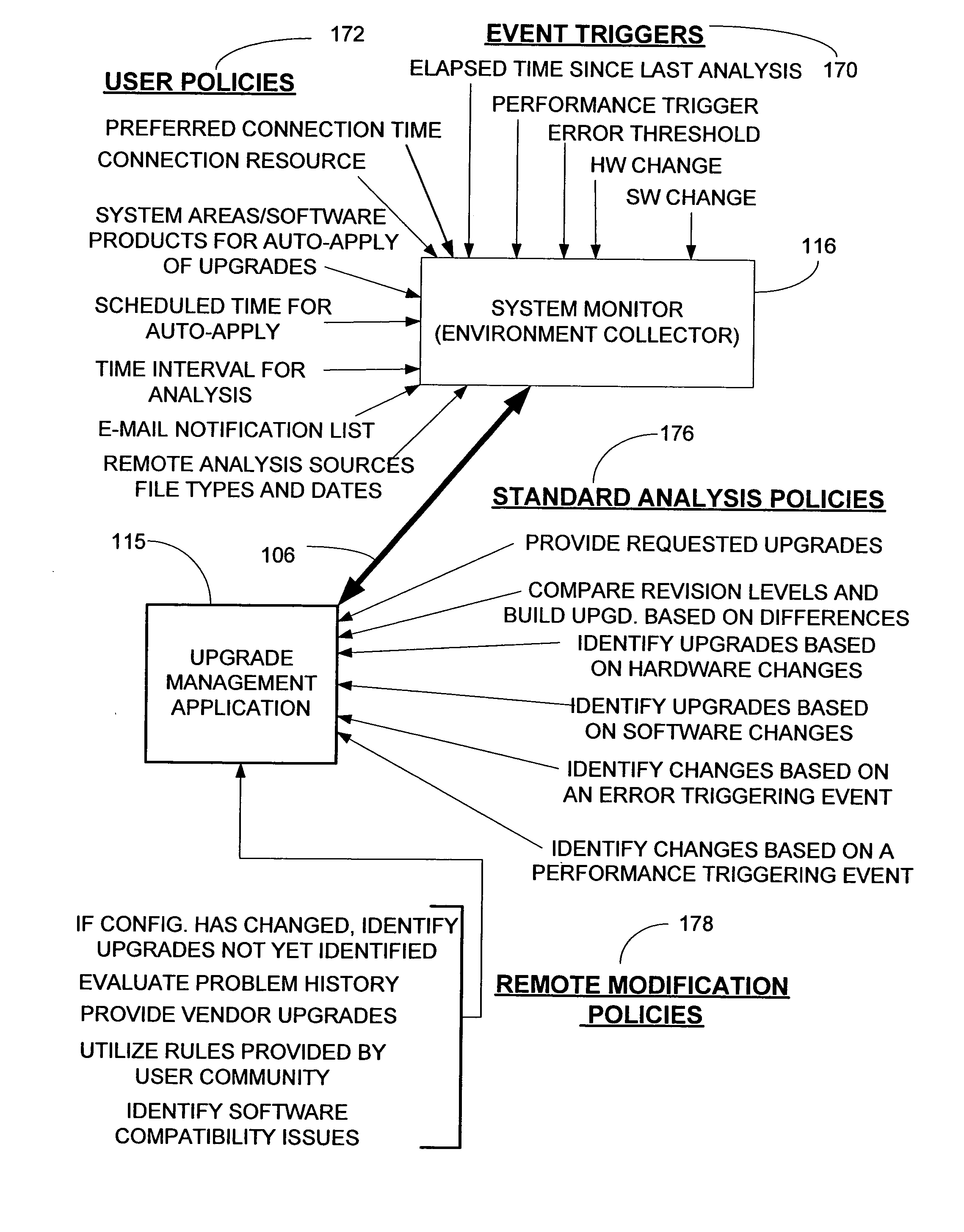
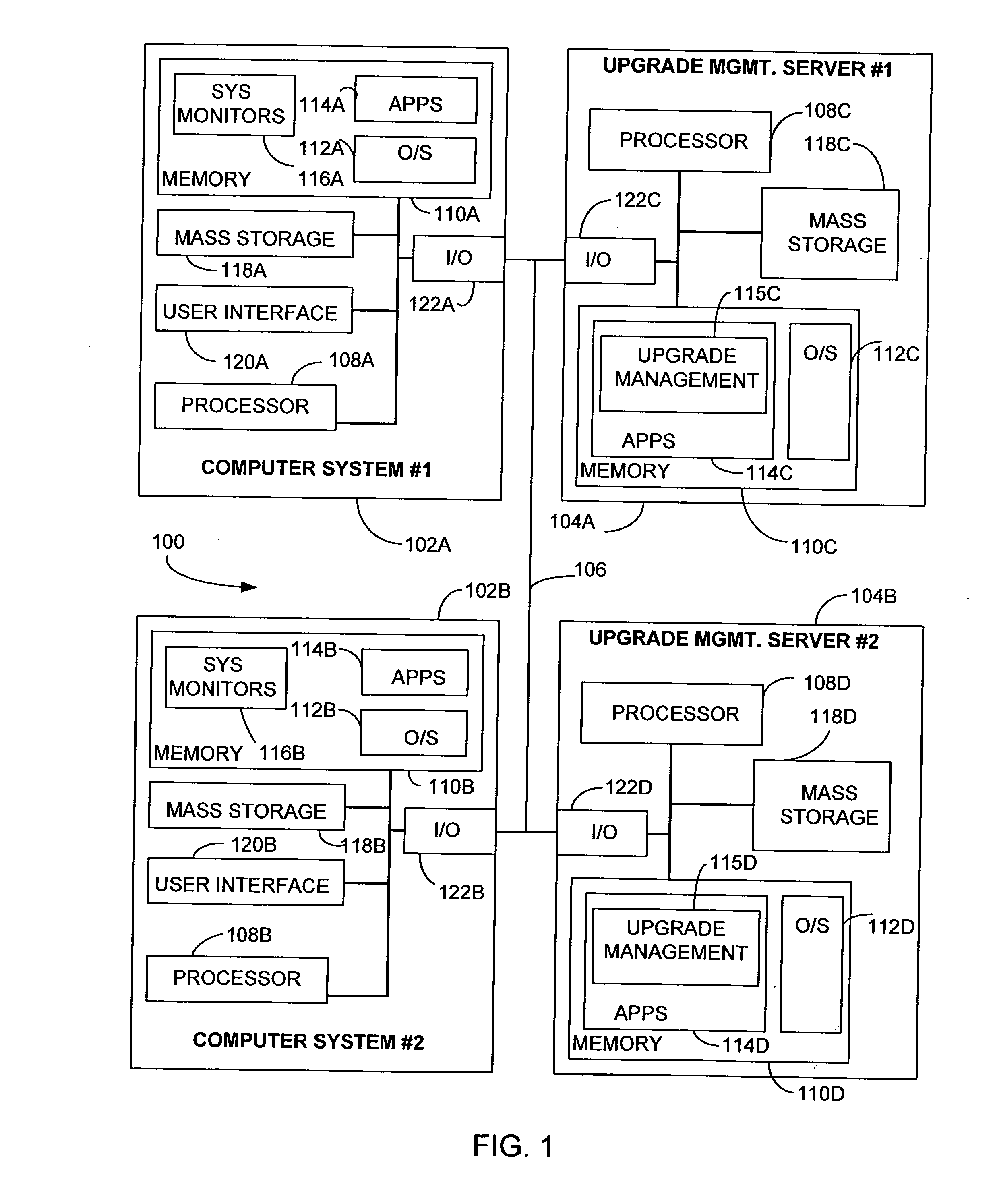
The present invention provides methods and a computer-readable program for providing autonomic, event driven upgrade maintenance of one or more software modules residing on a computer system. In a preferred embodiment, a method begins by detecting a predefined triggering event on the computer system indicative of a potential maintenance issue. Next the computer system connects to an upgrade management server, where the upgrade maintenance server creates a list of recommended upgrade modules to download to the computer system, the list based upon the triggering event and a set of selection policies. The method then downloads the list of recommended upgrade modules from the upgrade management server to the computer system, and selectively installs upgrade modules chosen from the list of recommended upgrade modules on the computer system. The user is then notified of the status of the upgrade maintenance operation.
Owner:GOOGLE LLC
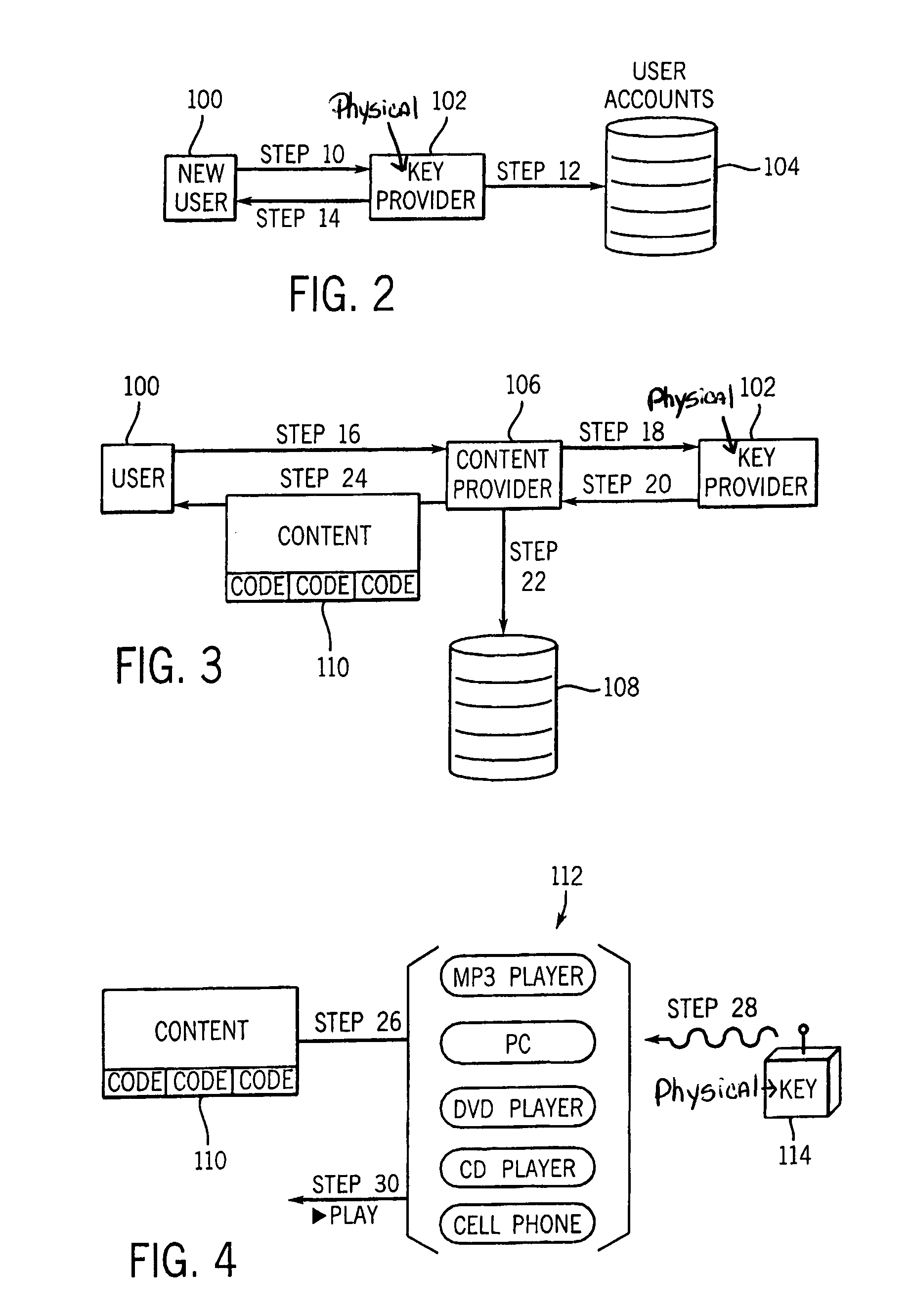
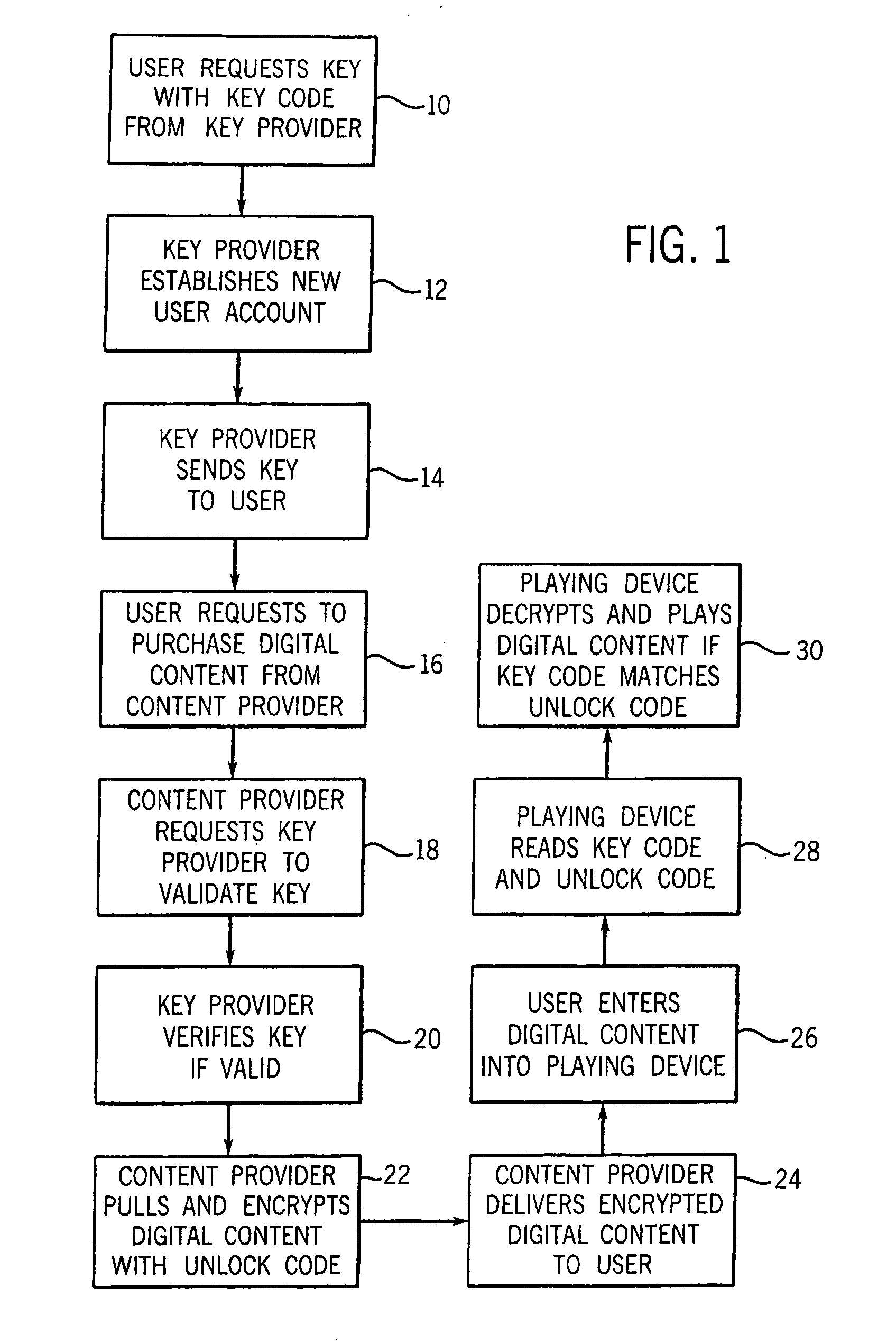
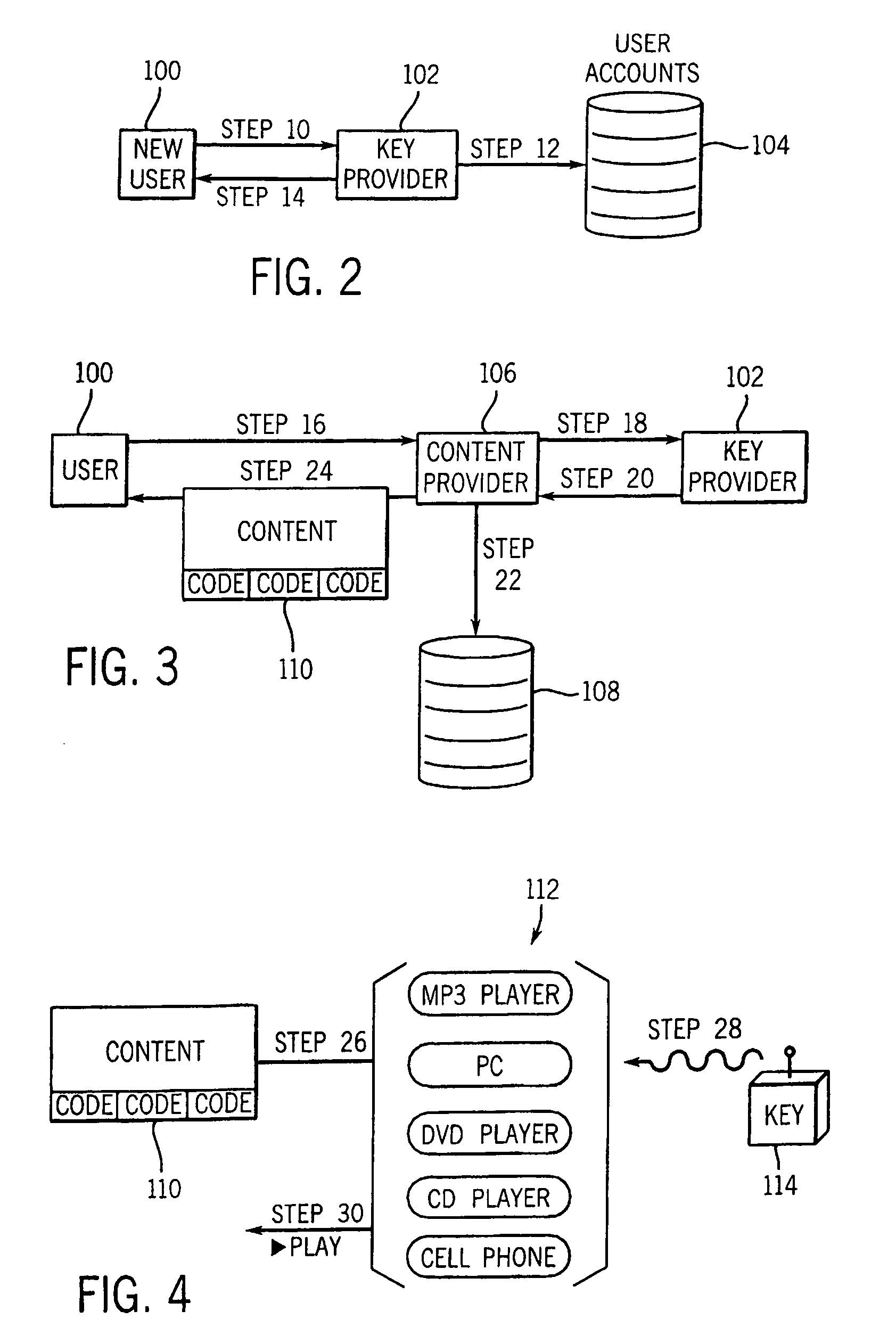
Digital content security system
InactiveUS6973576B2Provide protectionDigital data processing detailsUser identity/authority verificationHard disc driveOperational system
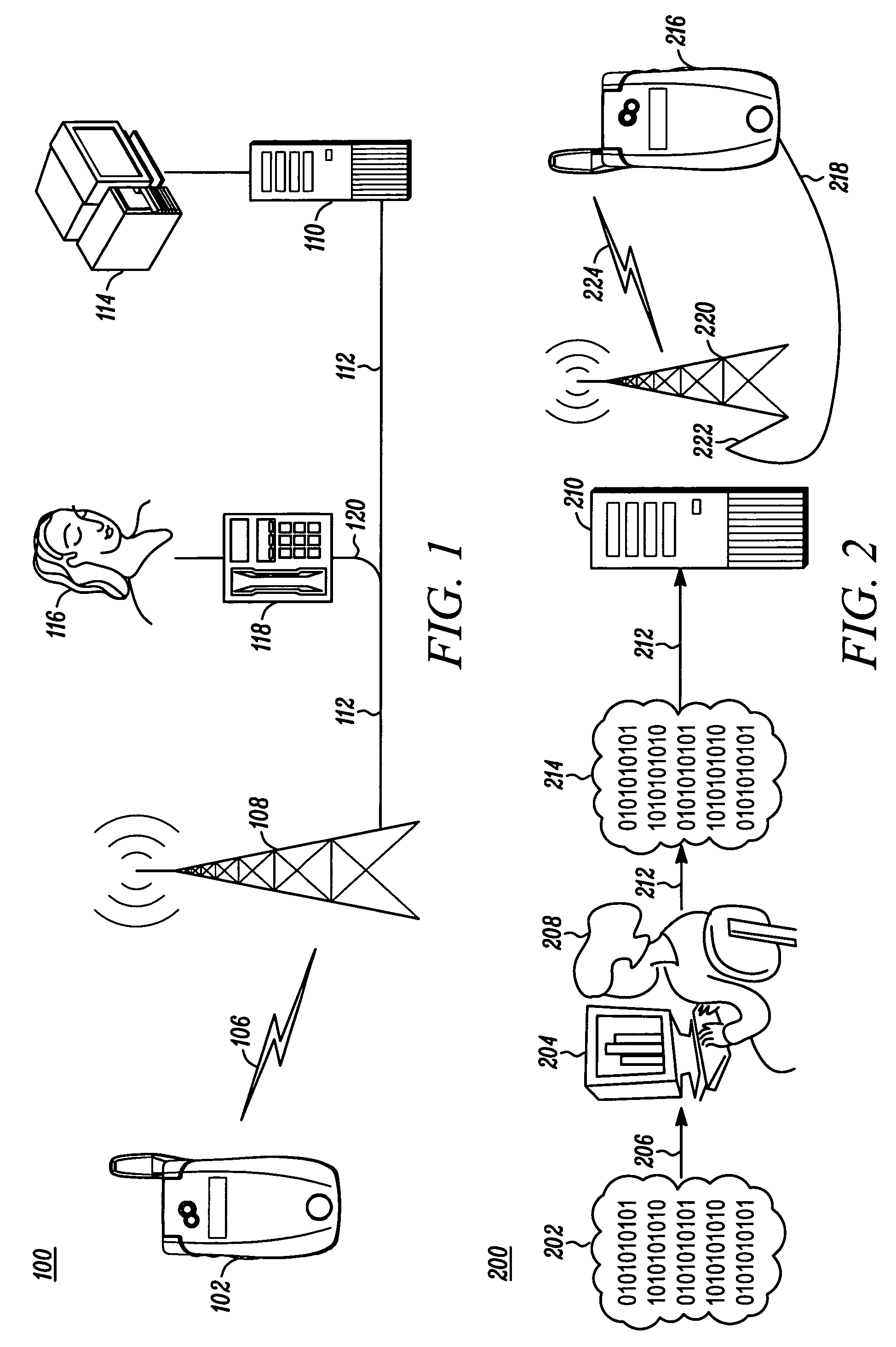
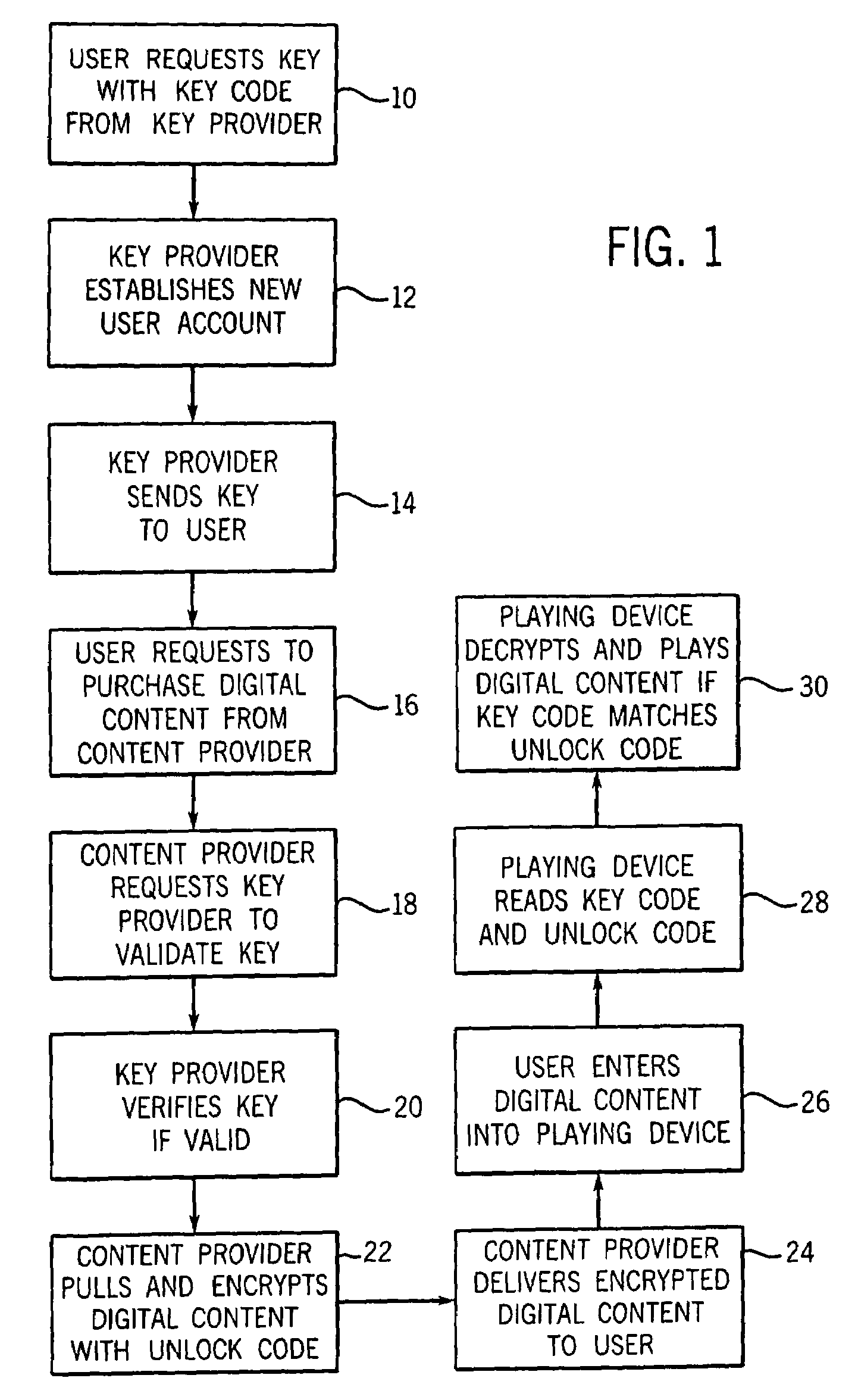
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
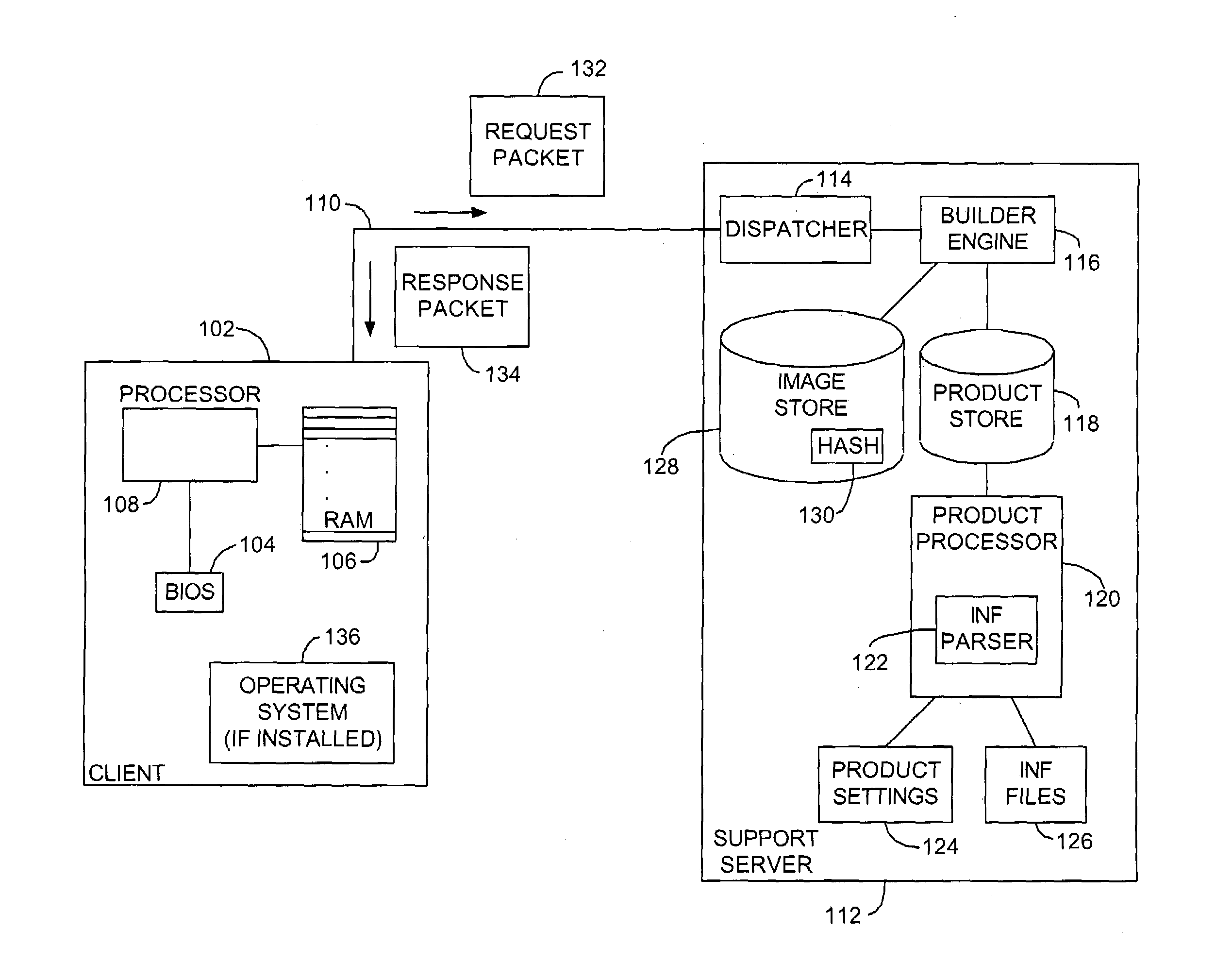
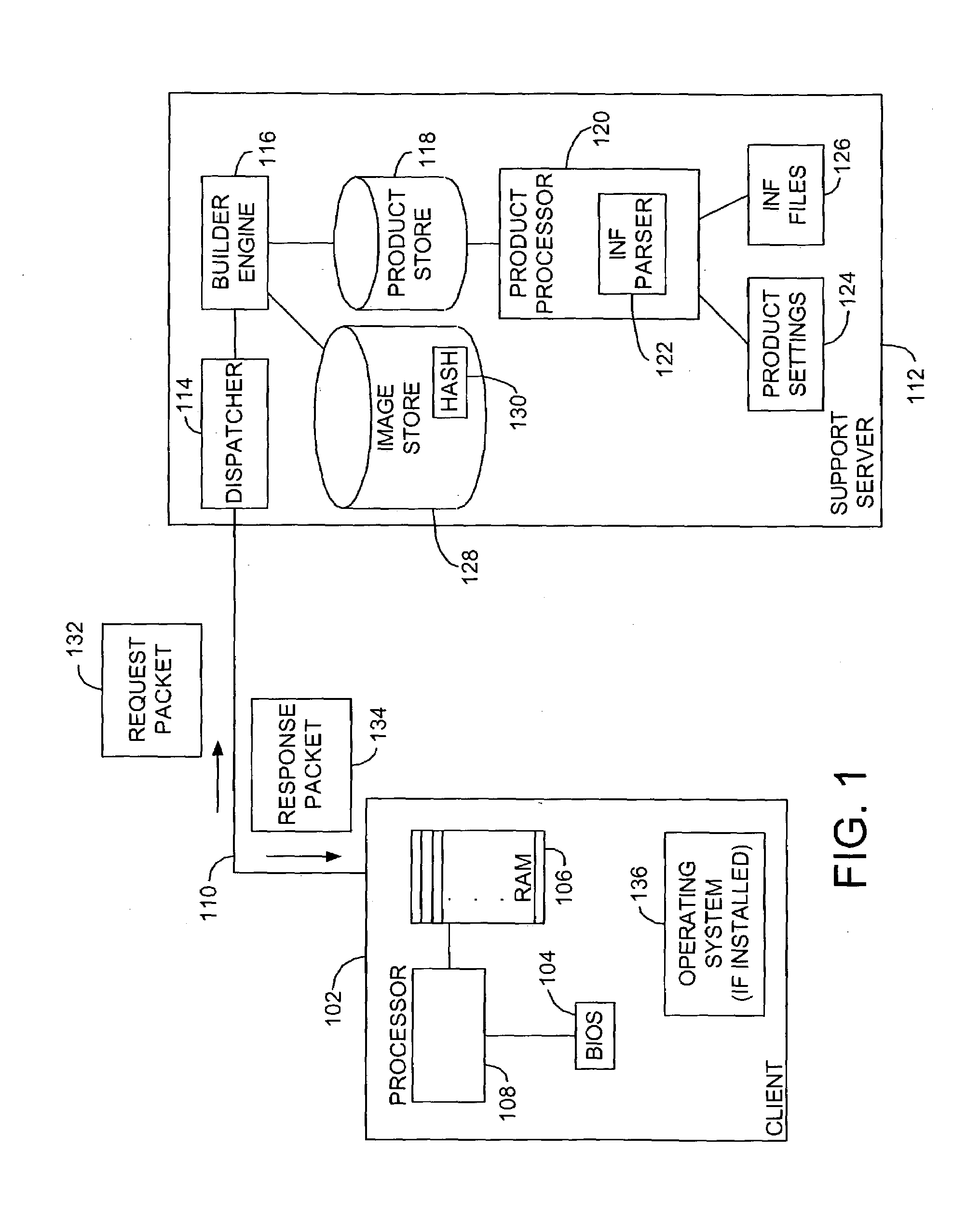
System and method for custom installation of an operating system on a remote client
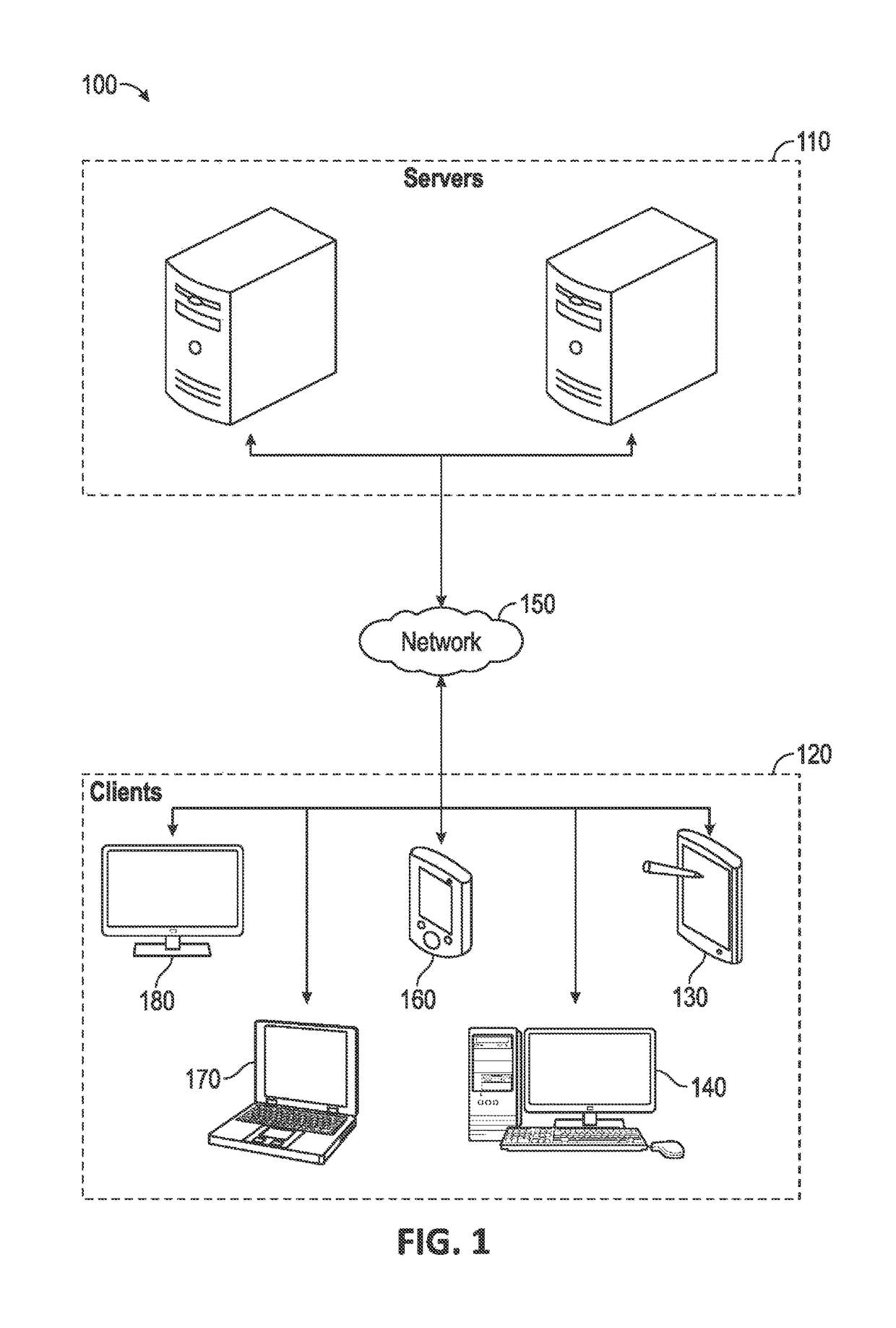
A platform for remotely installing an operating system on a client machine includes a builder engine, for instance running on a support server. The builder engine may interrogate a remote client, for instance a diskless thin client or a machine having a disk but malfunctioning, and receive a machine state image from that machine. The builder engine may then assemble a customized image or kernel of an operating system such as Microsoft Windows™ for transmission to the client. A file system may be initialized in electronic memory, or otherwise and the machine may commence operation, without having executed an operating system setup process. In embodiments, the client machine may then link to a complete image of an operating system to reinstall a comprehensive version of that system, or perform other tasks.
Owner:MICROSOFT TECH LICENSING LLC
Computer application and methods for autonomic upgrade maintenance of computer hardware, operating systems and application software
ActiveUS7624393B2Digital computer detailsProgram loading/initiatingOperational systemComputer module
The present invention provides methods and a computer-readable program for providing autonomic, event driven upgrade maintenance of one or more software modules residing on a computer system. In a preferred embodiment, a method begins by detecting a predefined triggering event on the computer system indicative of a potential maintenance issue. Next the computer system connects to an upgrade management server, where the upgrade maintenance server creates a list of recommended upgrade modules to download to the computer system, the list based upon the triggering event and a set of selection policies. The method then downloads the list of recommended upgrade modules from the upgrade management server to the computer system, and selectively installs upgrade modules chosen from the list of recommended upgrade modules on the computer system. The user is then notified of the status of the upgrade maintenance operation.
Owner:GOOGLE LLC
Digital content security system
InactiveUS20060064605A1Digital data processing detailsUser identity/authority verificationHard disc driveOperational system
Owner:PROXENSE
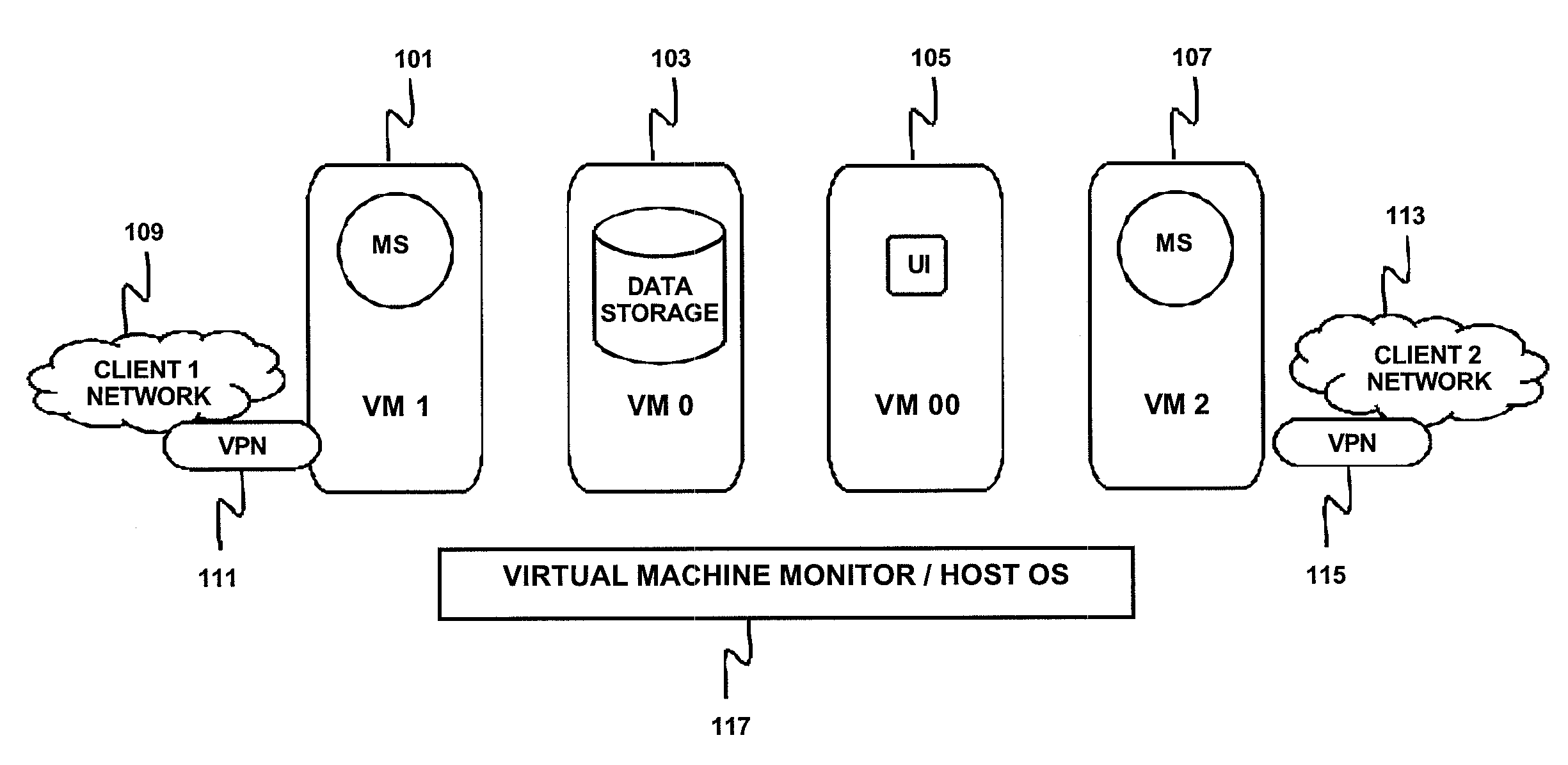
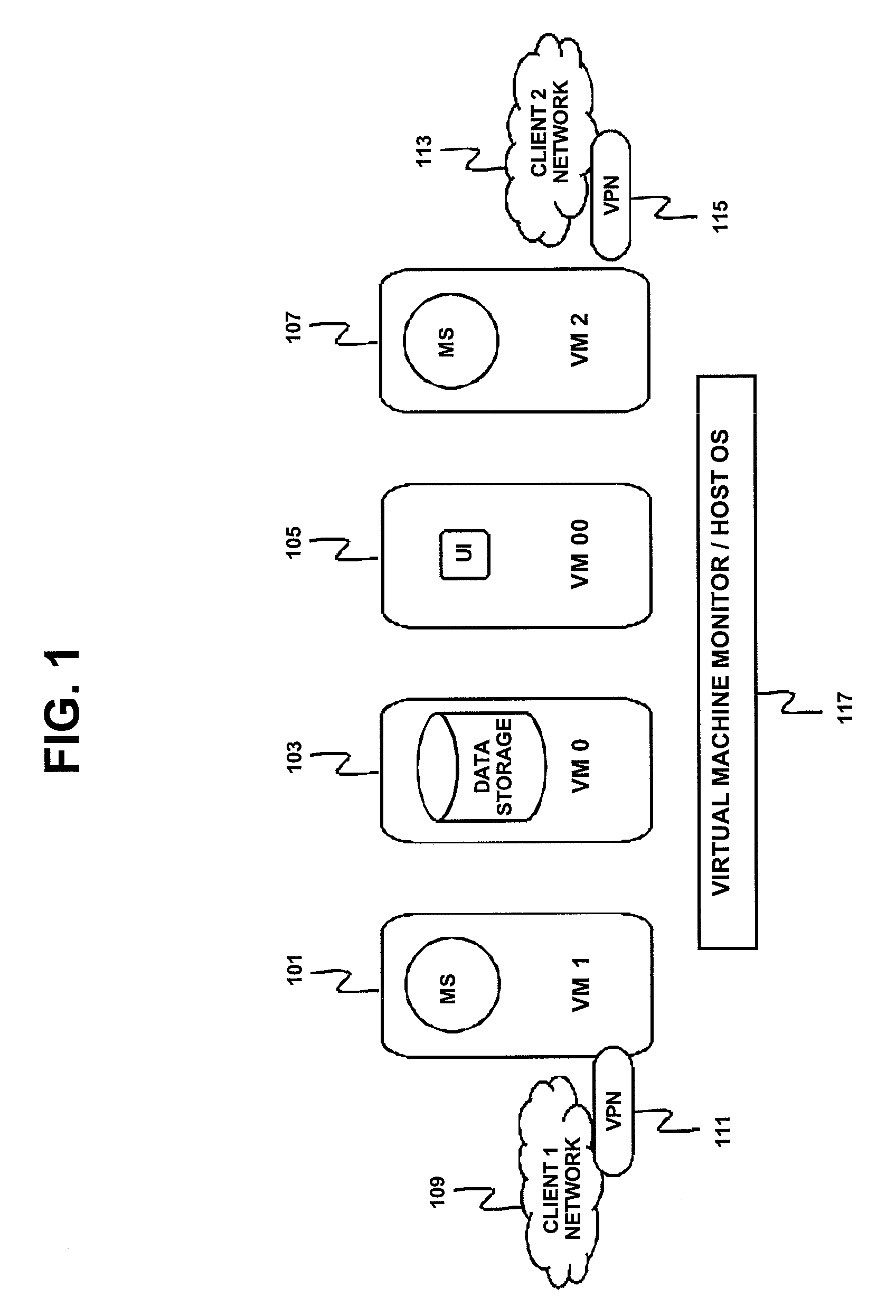
Method, Apparatus And Computer Program Product Implementing Multi-Tenancy For Network Monitoring Tools Using Virtualization Technology
InactiveUS20090113031A1Digital data processing detailsDigital computer detailsOperational systemManagement tool
Method, apparatus and computer program product manage a plurality of networks with a single tenant network management tool using virtualization and implement control plane virtualization of the single tenant management tool; data storage virtualization of a data storage apparatus and network address virtualization of an available address range. A virtual machine may be implemented for each network of the plurality of networks to contain an instance of the single tenant management tool. In one implementation, a proxy is used to implement data storage virtualization. In another implementation, separate data storage is maintained for each network and data storage virtualization is achieved by managing the network protocol stack virtualization. The network address virtualization may be implemented using machine-level virtualization or operating-system-level virtualization.
Owner:IBM CORP
Method and apparatus for providing digital rights management
InactiveUS20060129496A1Data processing applicationsProgram/content distribution protectionVirtual file systemOperational system
A method and wireless mobile device employs a virtual file system (706) and a digital rights management file system (708), at an operating system level, and a user space digital rights manager (712), at an application or user space level. The user space digital rights manager (712) is operative to manage digital rights associated with content that is stored in the digital rights management file system (708). For example, although an application may request content that has digital rights associated with it from the virtual file system (706), and the virtual file system (706) communicates with the digital rights management file system (708) at the operating system level, the DRM file system (708) redirects the calls to the user space digital rights manager (712) at the user space level which performs the digital rights operations.
Owner:MOTOROLA INC
Digital content security system
InactiveUS7305560B2Digital data processing detailsUnauthorized memory use protectionHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
System and method for remote direct memory access without page locking by the operating system
InactiveUS7533197B2Digital computer detailsElectric digital data processingDirect memory accessOperational system
A multi-node computer system with a plurality of interconnected processing nodes, including a method of using DMA engines without page locking by the operating system. The method includes a sending node with a first virtual address space and a receiving node with a second virtual address space. Performing a DMA data transfer operation between the first virtual address space on the sending node and the second virtual address space on the receiving node via a DMA engine, and if the DMA operation refers to a virtual address within the second virtual address space that is not in physical memory, causing the DMA operation to fail. The method includes causing the receiving node to map the referenced virtual address within the second virtual address space to a physical address, and causing the sending node to retry the DMA operation, wherein the retried DMA operation is performed without page locking.
Owner:SICORTEX
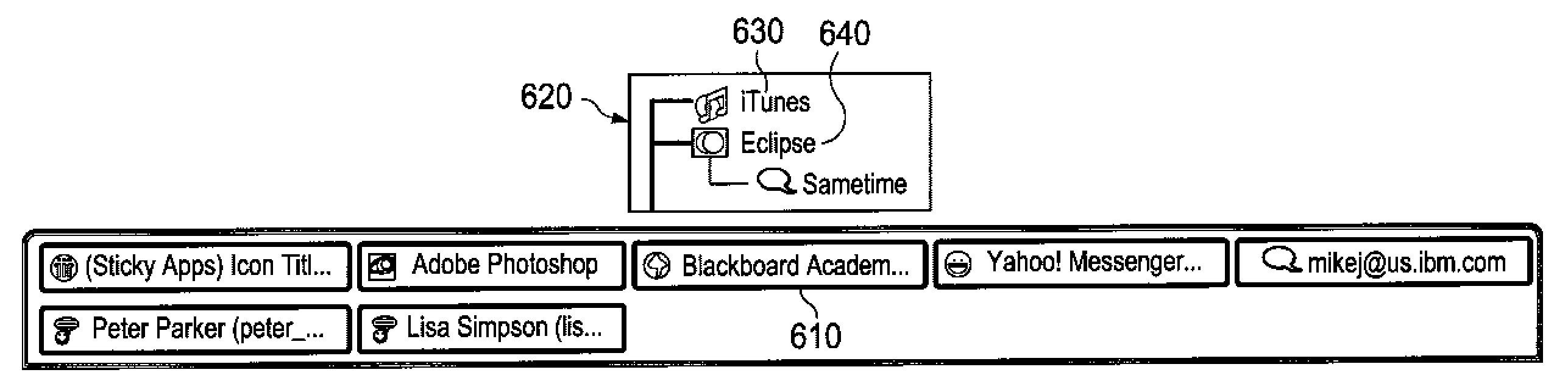
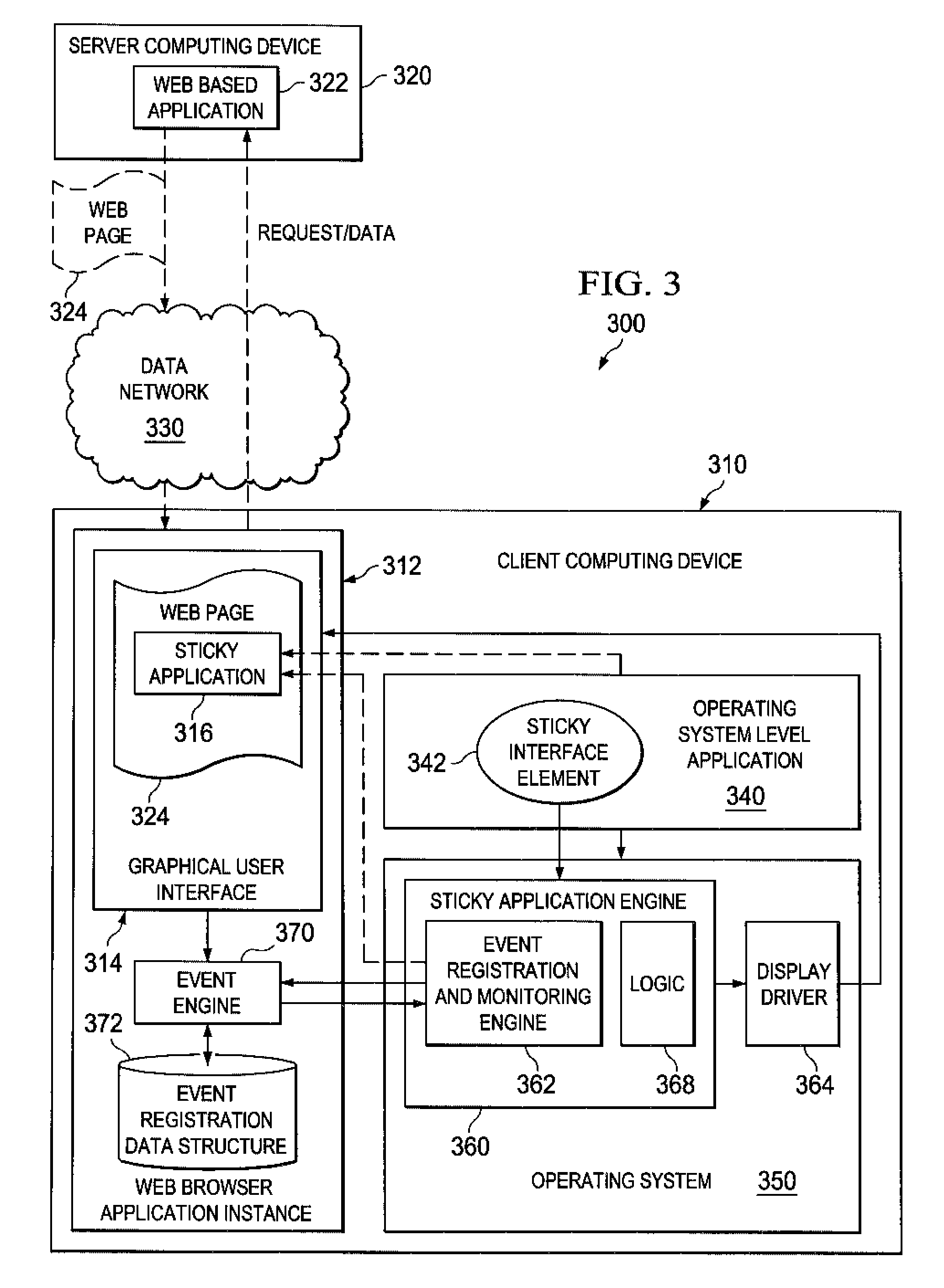
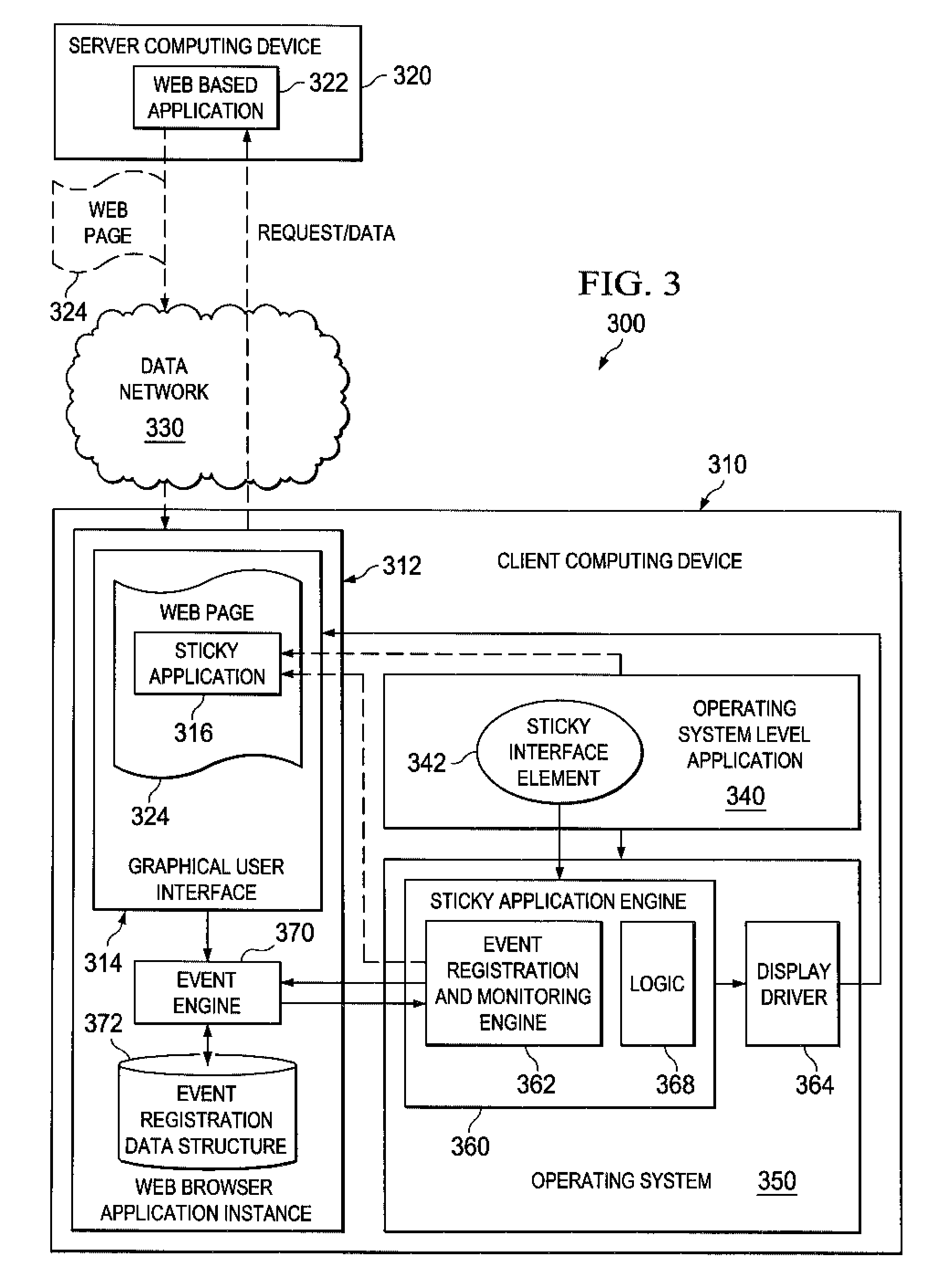
System and method for providing sticky applications
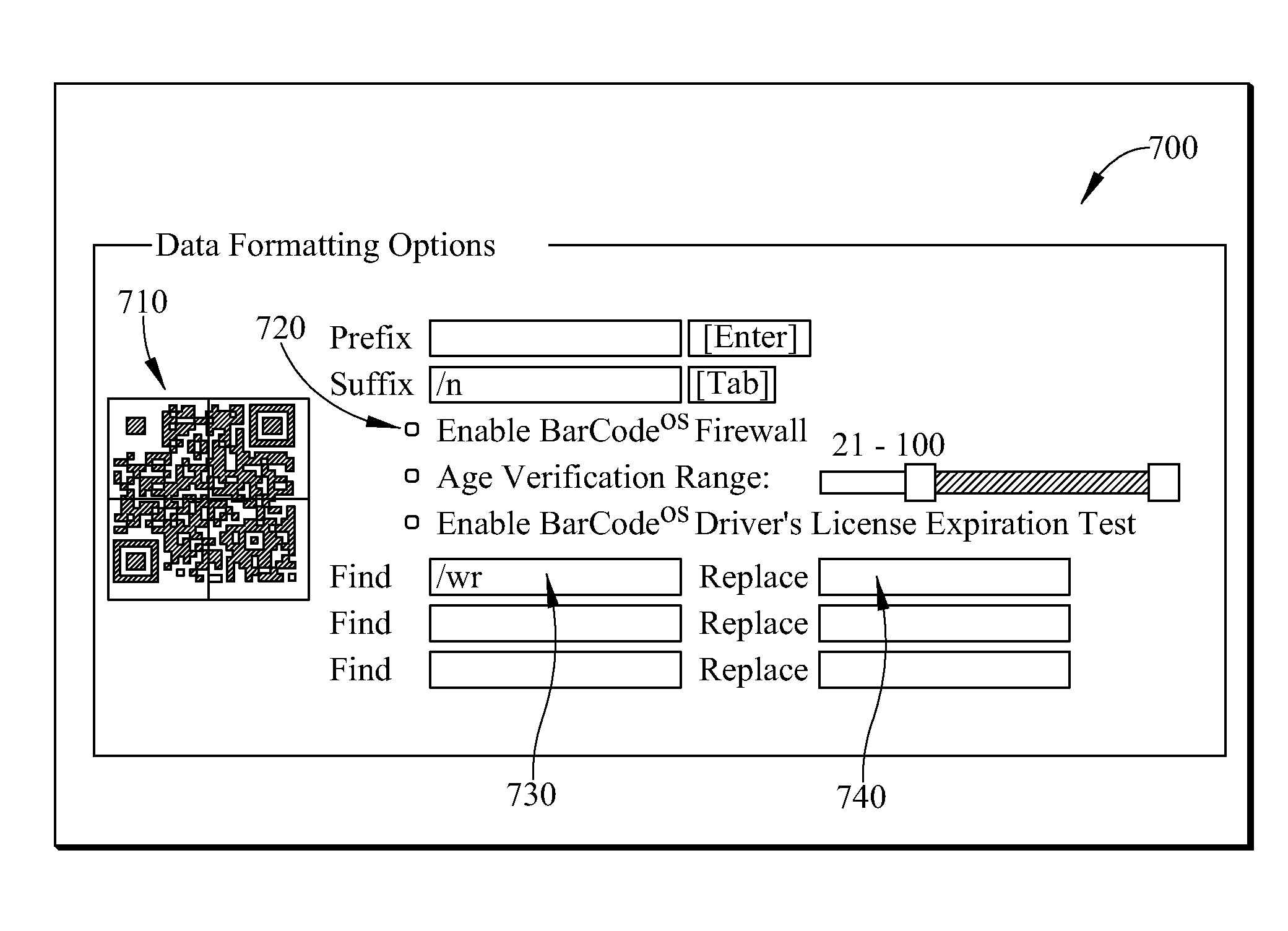
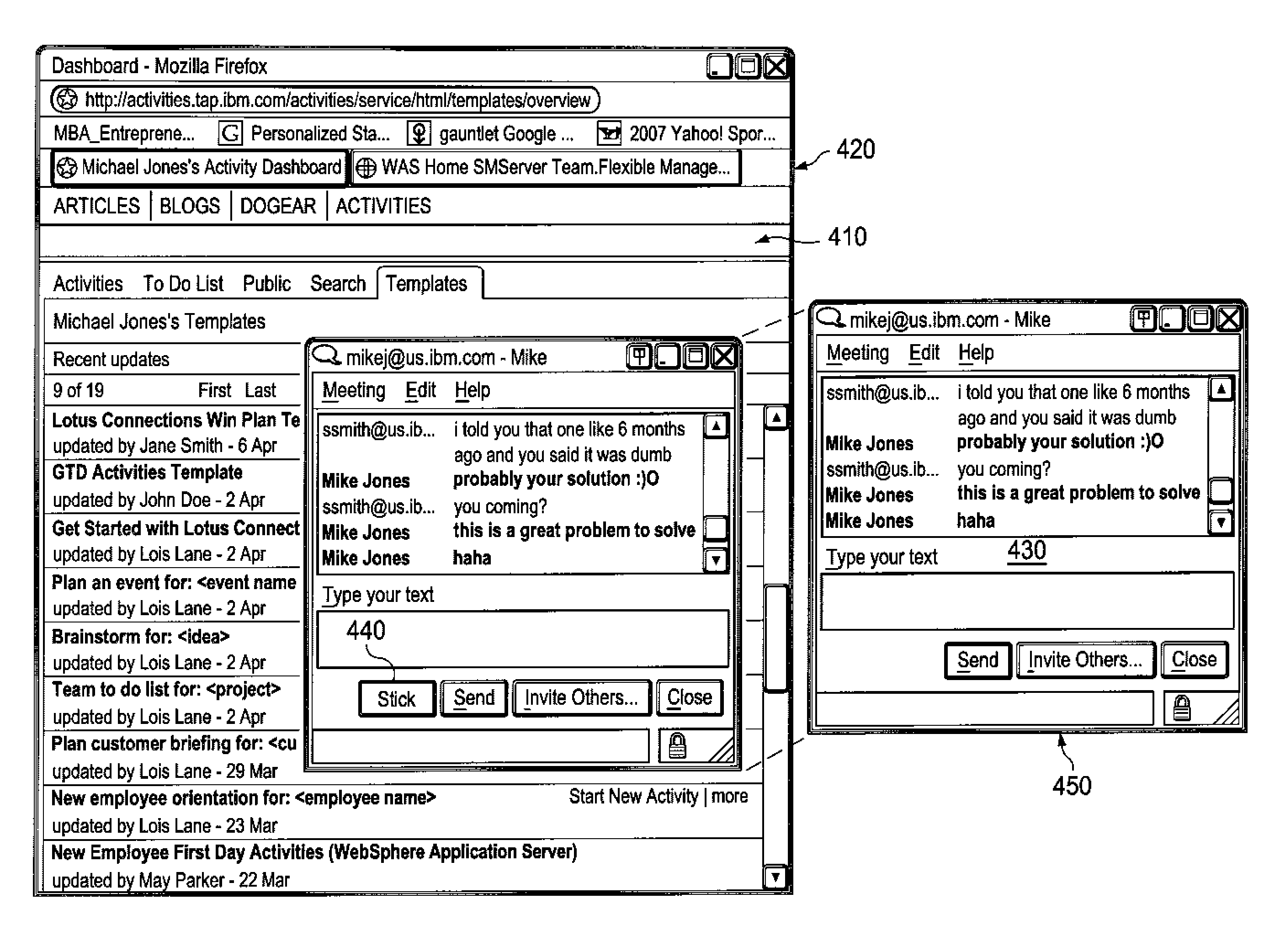
InactiveUS20090125833A1Execution for user interfacesInput/output processes for data processingWeb applicationOperational system
A system and method for providing sticky applications are provided. A “sticky application” is an operating system (OS) level application that has the ability to “stick” to web applications and become a part of the web page on which the web application is running. While the sticky application is stuck to the web application, it behaves as if it were a web application with respect to the user. When the user chooses to “unstick” the application, it will return to behaving as an OS level application. The sticky application imitates being a web-based application instead of an operating system level application while stuck. This imitation involves the sticky application being placed on pixel coordinates within a web page of the web application and the sticky application remaining in the pixel coordinates within the web page where it is placed even when a user modifies the representation of the web page.
Owner:IBM CORP
Digital content security system
InactiveUS7404088B2Digital data processing detailsUser identity/authority verificationHard disc driveOperational system
A Personal Digital Key Digital Content Security System (PDK-DCSS) is used to protect computers from unauthorized use and protect the digital content stored on computers from being wrongfully accessed, copied, and / or distributed. The basic components of the PDK-DCSS are (1) a standard hard drive device, with the addition of a PDK Receiver / Decoder Circuit (PDK-RDC) optionally integrated into the hard drive's controller, and (2) a PDK-Key associated with the PDK-RDC. The PDK-Key and RDC technology is utilized to provide two categories of protection: (1) hard drive access control for providing Drive-Level and Sector-Level protection and (2) operating system-level independent file protection for providing File-Level and Network-Level protection.
Owner:PROXENSE
System for managing radio modems
ActiveUS20080081663A1Avoid collisionImprove efficiencySubstation equipmentRadio transmissionModem deviceDual mode
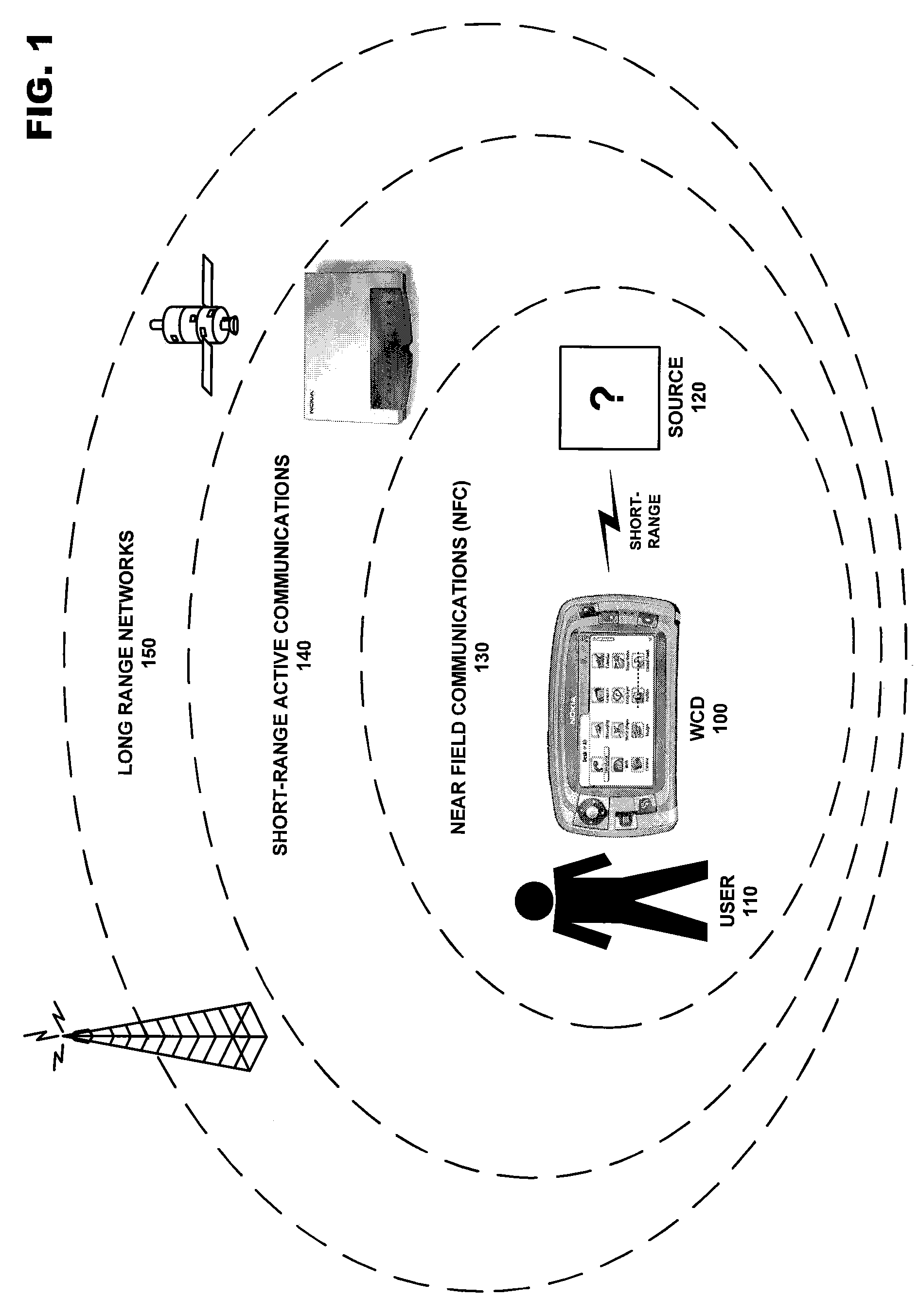
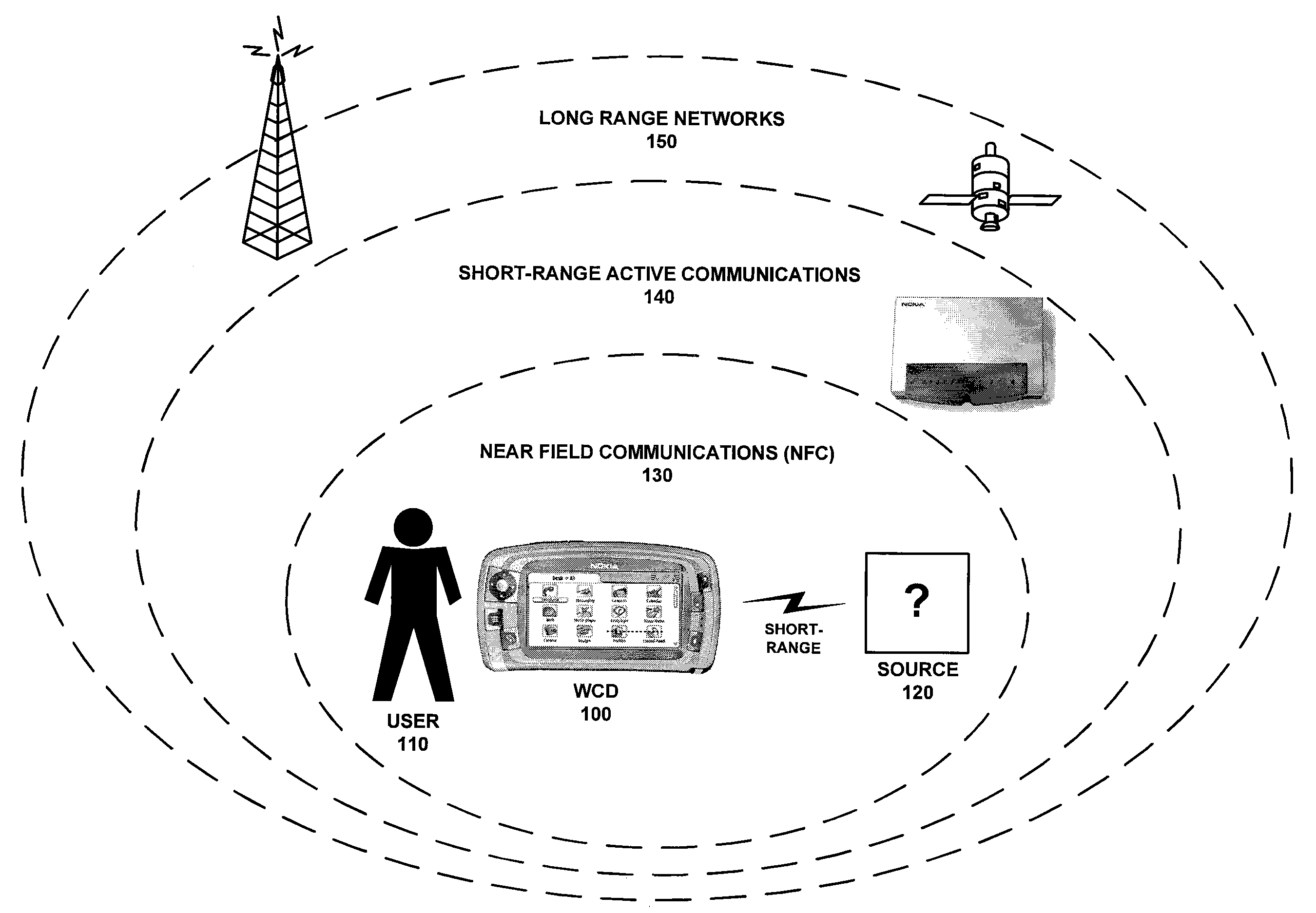
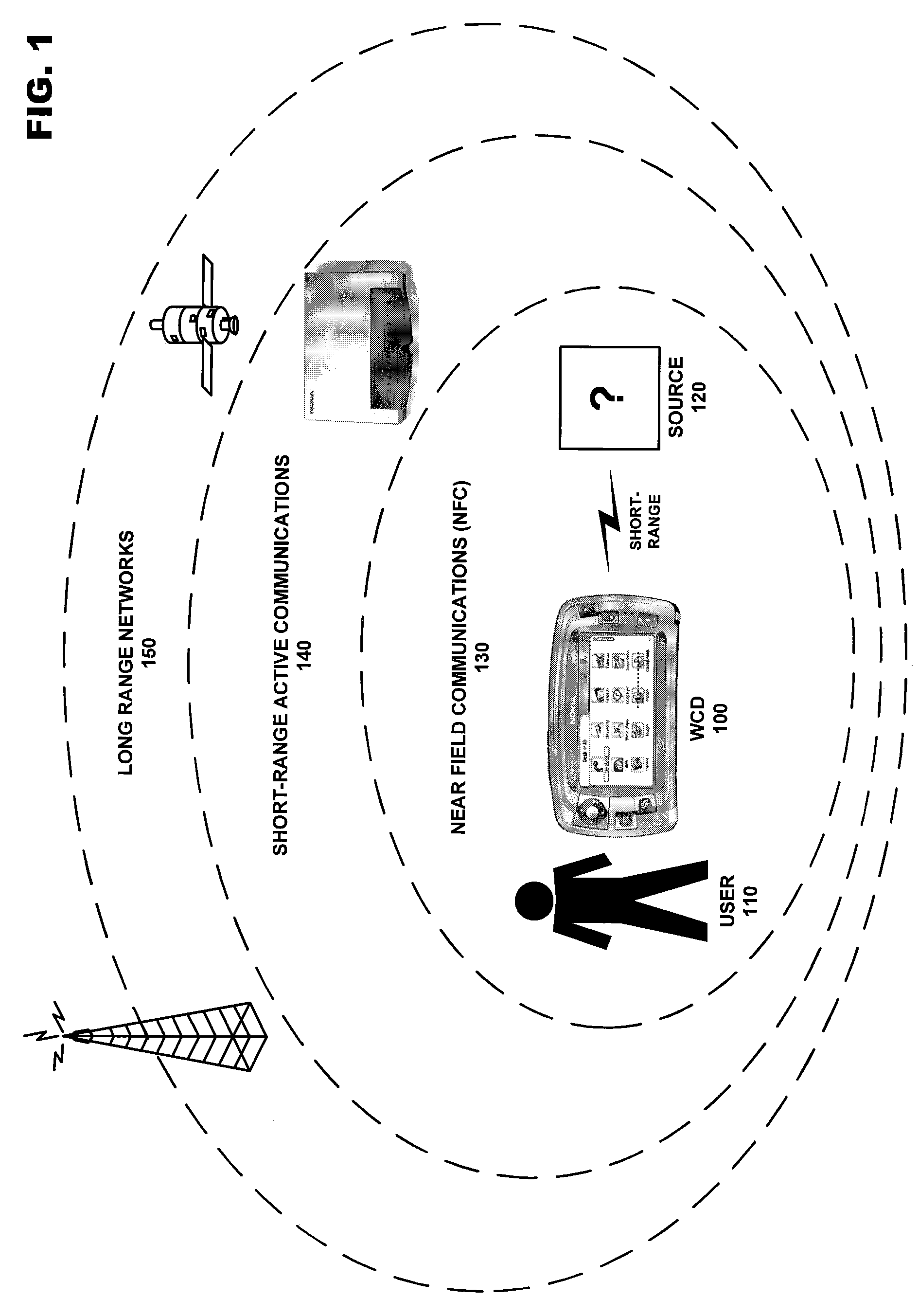
A system for managing the operation of a plurality of radio modems contained within the same WCD. One or more of the plurality of radio modems may be a dual-mode radio modem enabled to communicate using at least two separate radio protocols concurrently. The operation of the one or more dual-mode modems may be managed by resources encompassed in a radio modem interface coupled to, or integrated within, the dual-mode radio modem. These management resources may receive information from the operating system level of the WCD and from the at least two radio modem stacks utilizing the resources of the dual mode radio modem in order to coordinate the operation of the at least two radio protocols concurrently active in the modem.
Owner:NOKIA TECHNOLOGLES OY
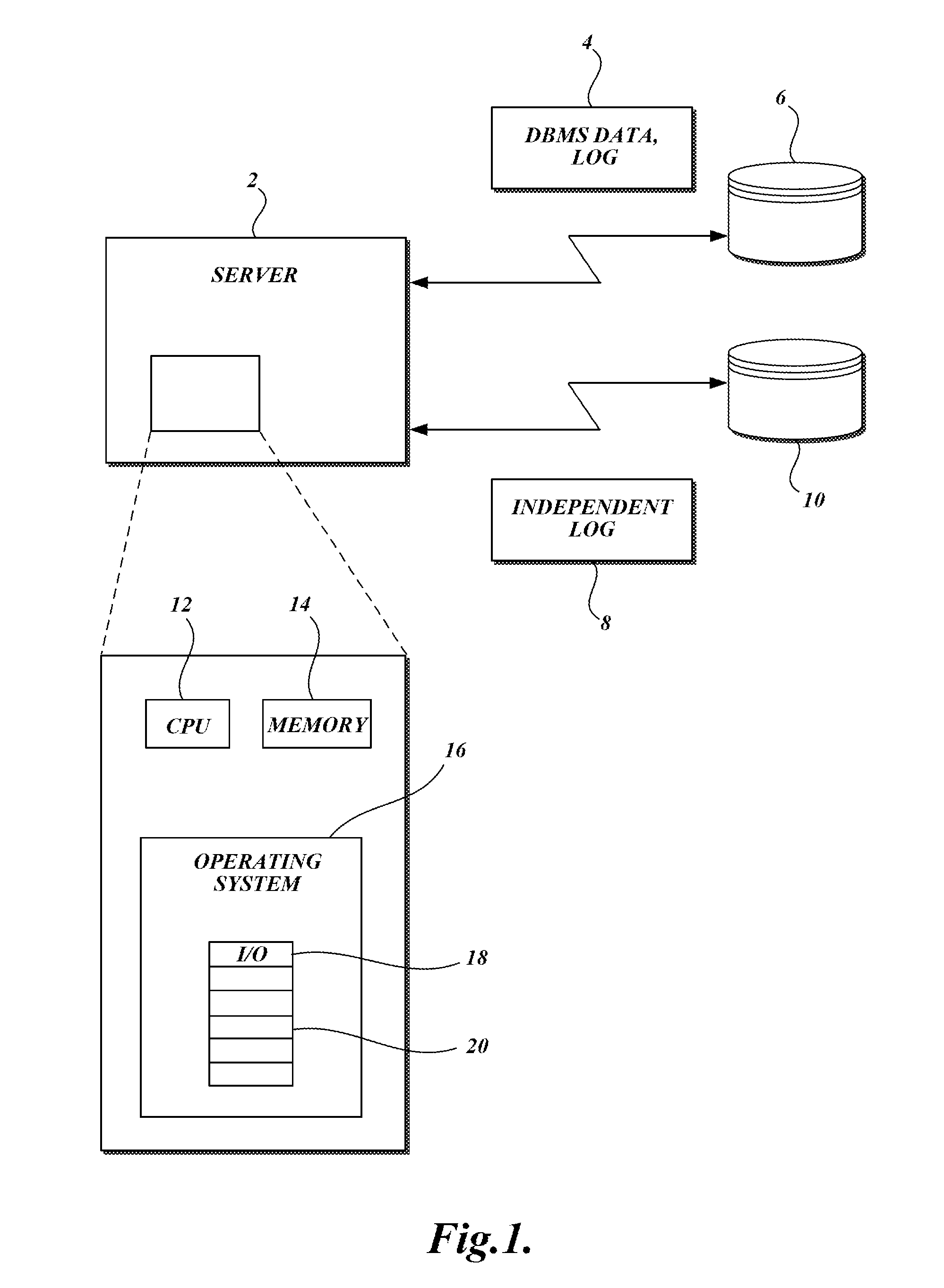
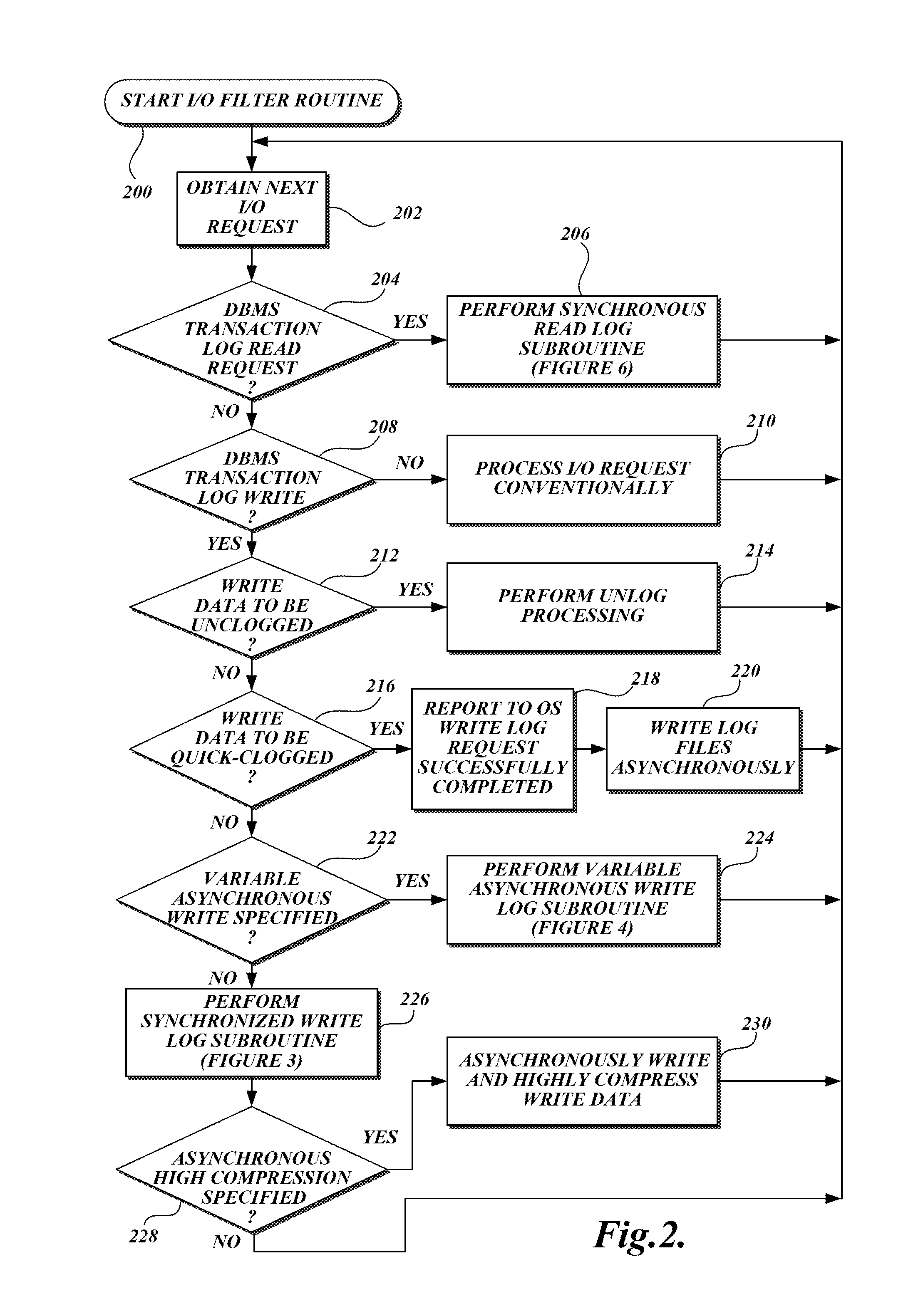
System and Method For Providing High-Availability and High-Performance Options For Transaction Log
InactiveUS20130325828A1Avoid lossPrevent corruptionDigital data information retrievalError detection/correctionOperational systemTransaction log
The present invention provides a method and system for using an operating system level I / O filter driver for providing transparent database transaction log file redundancy. In accordance with the method, the I / O filter driver intercepts a database management system request to write data to the database transaction log file. The I / O filter driver writes the data to at least two transaction log files.
Owner:CONFIO
System and method for synchronizing smart mobile terminal and cloud virtual mobile terminal
ActiveCN103442024AGood serviceSolve the problem of running very slowlyTransmissionComputer hardwareWeb service
The invention discloses a system for synchronizing a smart mobile terminal and a cloud virtual mobile terminal. The system comprises the smart mobile terminal and a cloud end, wherein the smart mobile terminal operates in an android operating system, the cloud end comprises the virtual mobile terminal and a Web server, and the Web server serves as an mediation for interaction between the smart mobile terminal and the virtual mobile terminal, is communicated with the smart mobile terminal through WiFi or a 3G wireless network and then is communicated with the virtual mobile terminal through a wired network. A virtual mobile phone having the same operating system with a physical mobile phone is established at the cloud end, the physical mobile phone can be timely recovered to be of the initial state when the system of the physical mobile phone goes wrong, and real-time backup at a level of the operating system can be carried out on the physical mobile phone.
Owner:HANGZHOU INST OF ADVANCED TECH CHINESE ACAD OF SCI
Extensible memory object storage system based on heterogeneous memory
ActiveCN110134514ARealize dynamic usageEliminate overheadMemory architecture accessing/allocationResource allocationMemory objectHeterogeneous network
The invention relates to an extensible memory object storage system based on a heterogeneous memory, which comprises a DRAM (Dynamic Random Access Memory) and an NVM (Non-Volatile Memory), and is configured to: execute a memory allocation operation through a Slab-based memory allocation mechanism and divide each Slab Class into a DRAM (Dynamic Random Access Memory) domain and an NVM domain; monitor access heat degree information of each memory object at an application layer level; and dynamically adjust a storage area of corresponding key value data in each Slab Class based on the access heatdegree information of each memory object, store the key value data of the memory object with relatively high access heat in each Slab Class in a DRAM domain, and store the key value data of the memoryobject with relatively low access heat in each Slab Class in an NVM domain; and monitor the access heat of the memory object at the application layer level. Dynamic use of the DRAM / NVM heterogeneousmemory is achieved, and compared with a traditional method of monitoring the access heat of the application at the hardware or operating system level, huge hardware and operating system expenditure iseliminated.
Owner:HUAZHONG UNIV OF SCI & TECH
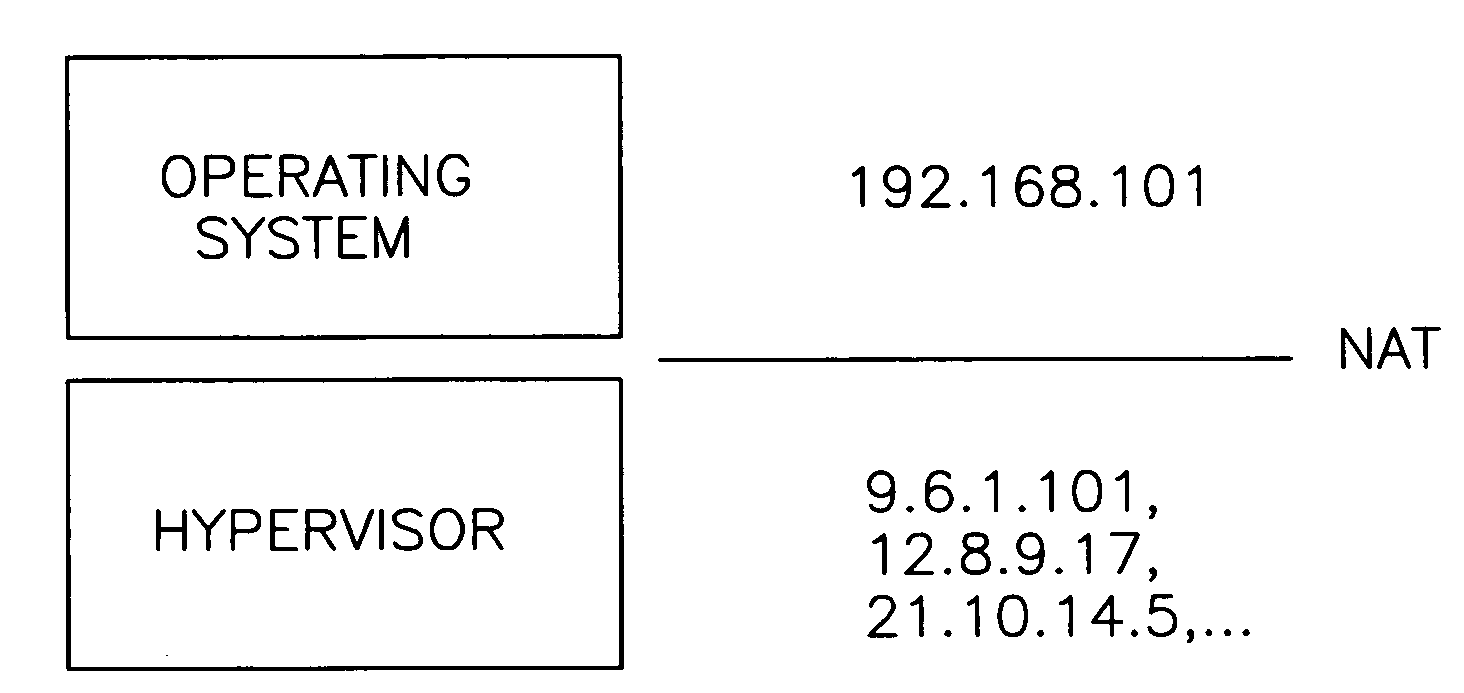
Methods and apparatus for maintaining network addresses
ActiveUS20070294421A1Network traffic/resource managementAssess restrictionPrivate IPOperational system
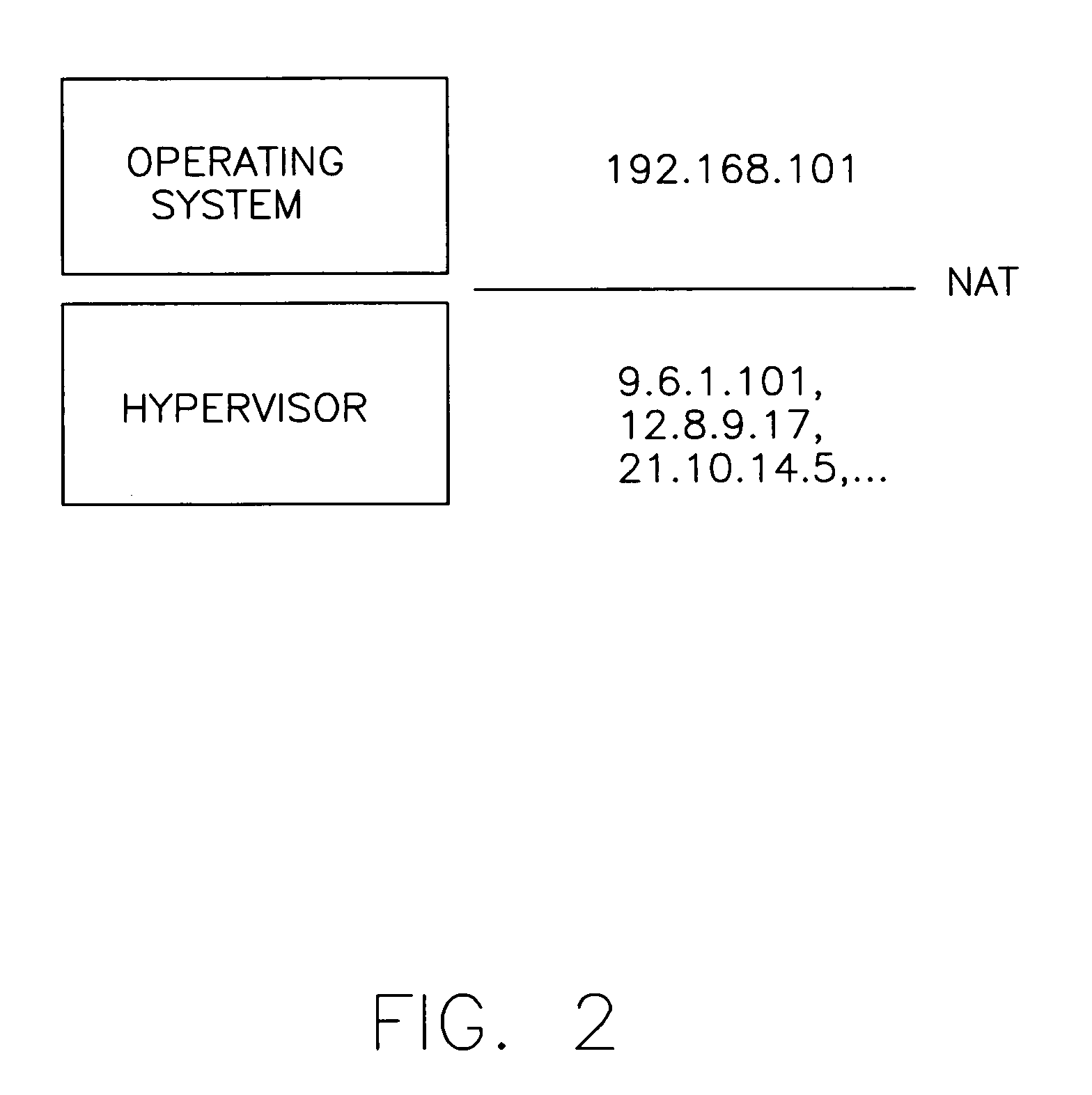
This present invention relates to a method for using hypervisors to enable stable wireless network connections. The crux of the invention involves pushing the control of the networking devices from the Operating System level down to a networking front end hypervisor level. The hypervisor will control all networking devices, the authentication for these devices, and the selection of which connection to use. The hypervisor will also perform Network Address Translation (NAT) to the Operating System. Thus, the Operating System will receive a single, private IP address for use with the Operating System's applications. The hypervisor will handle the change of the IP address when roaming between networks and hide it from the Operating System through the use of the NAT.
Owner:LENOVO PC INT
Virtualization method based on operating system layer
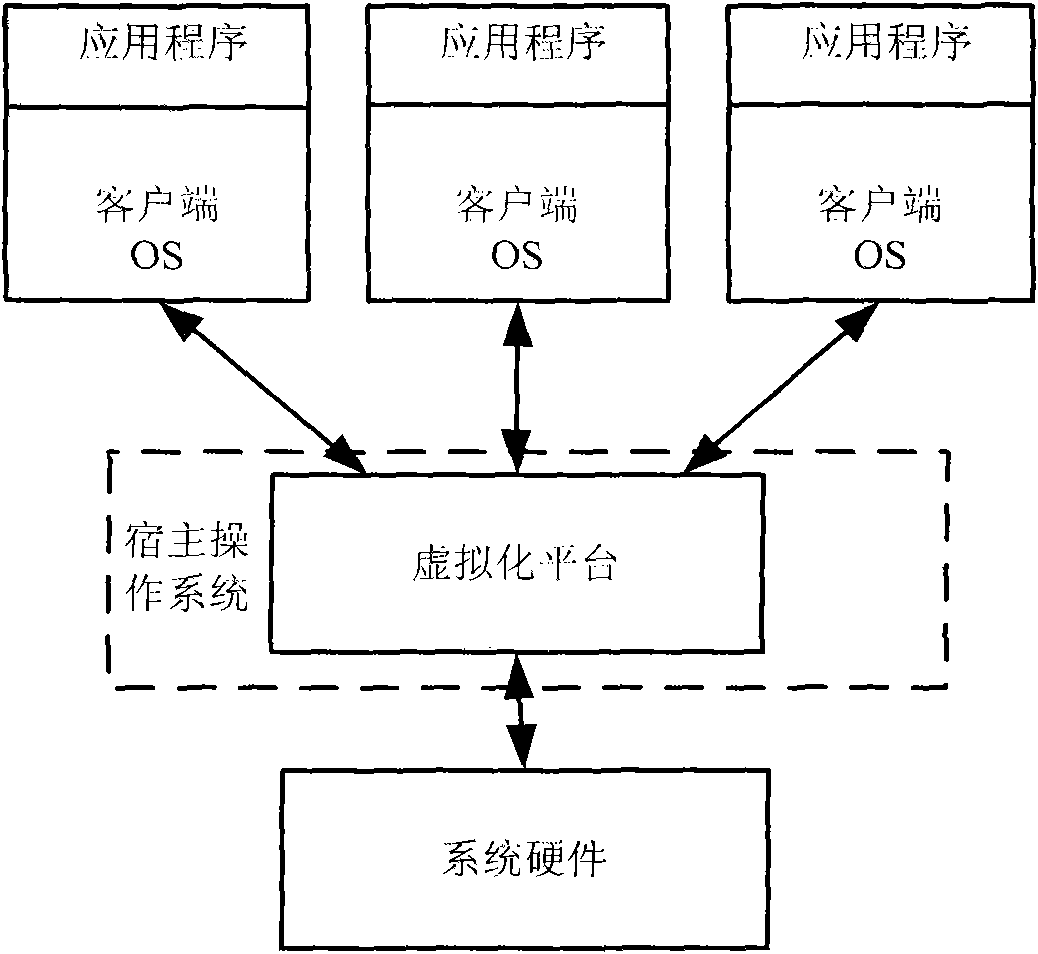
InactiveCN102339229AReduce overheadImprove performanceSoftware simulation/interpretation/emulationVirtualizationNetwork operating system
The invention provides a bottom virtualization process (namely, virtualization for an operating system layer). According to a method, virtualization is realized by adding a virtual server function in an operating system layer. The bottom virtualization process comprises the following steps of: forming a virtualized layer on a hardware layer, thereby finishing virtualized integration of physical equipment; installing a plurality of client operating systems on the virtualized layer; and running an application program in the client operating systems. The client operating systems are communicated with the hardware through a VMM (Virtual Machine Monitor) in the virtualized layer, wherein the VMM is used for determining the access of all virtual machines to physical resources. In a virtualization solution, the VMM plays a role of a traditional operating system in a software set and the traditional operating system as the client operating system runs on the virtualized layer at a position of the application program. Compared with other virtualization processes, the bottom virtualization process has the advantages that a manager need not install and maintain a single operating system embodiment for each application, thereby lowering the management cost.
Owner:戴元顺
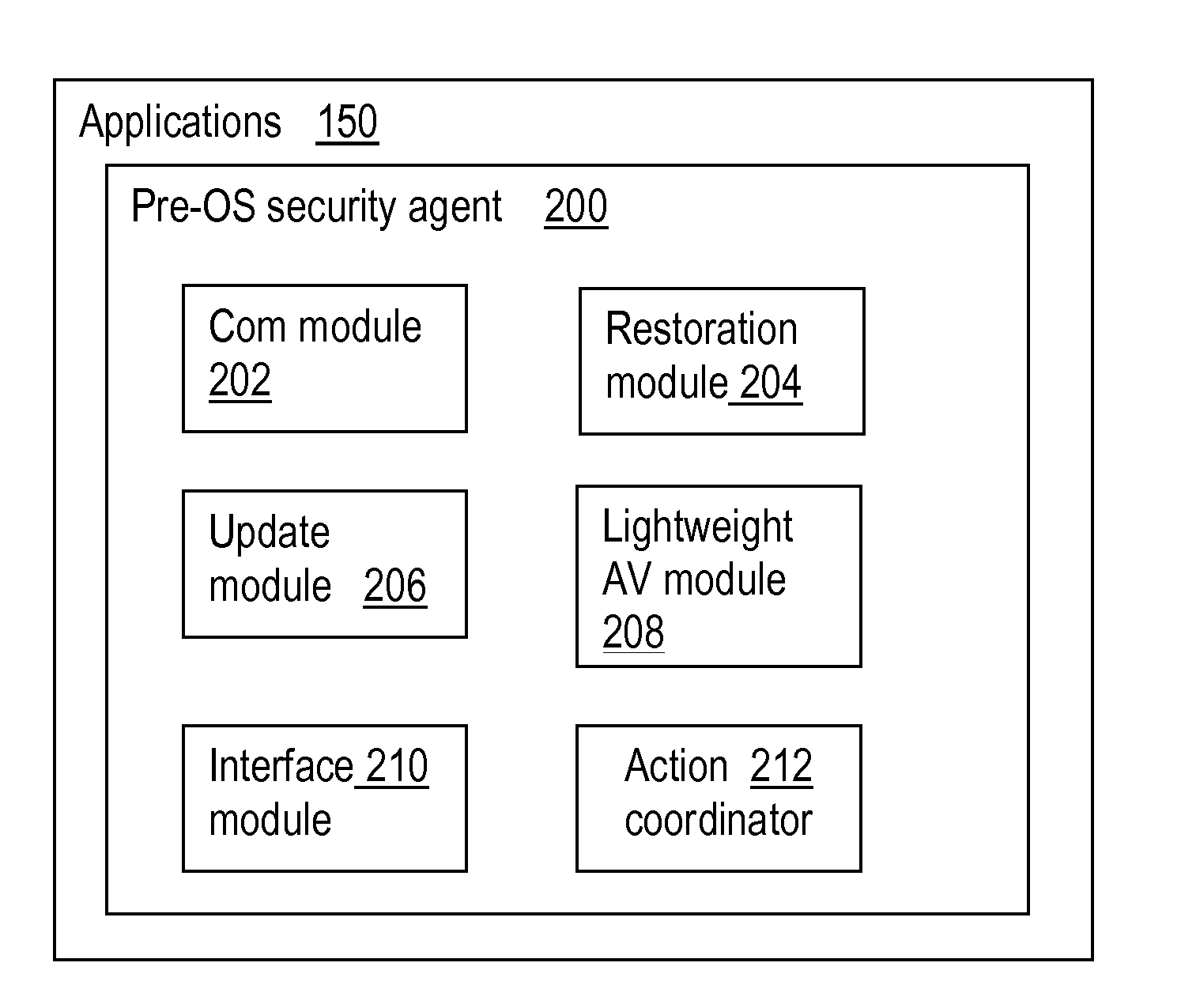
Firmware-level security agent supporting operating system-level security in computer system
ActiveUS8910283B1Facilitates system securityReduce startup timeMemory loss protectionError detection/correctionOperational systemFile system
A pre-OS security agent runs in an environment independent of the operating system (OS) but interfaced with the file system and able to exchange information with a security application running over the OS. Prior to the start-up of the OS, an indication of a state or condition is obtained relating to a risk of an inability of the security application to function normally, or to a change in the computer system affecting the start-up of the OS. Based on the indication, a set of one or more actions are determined for resolving the state or condition. The pre-OS security agent executes the set of one or more actions in response to the indication.
Owner:AO KASPERSKY LAB
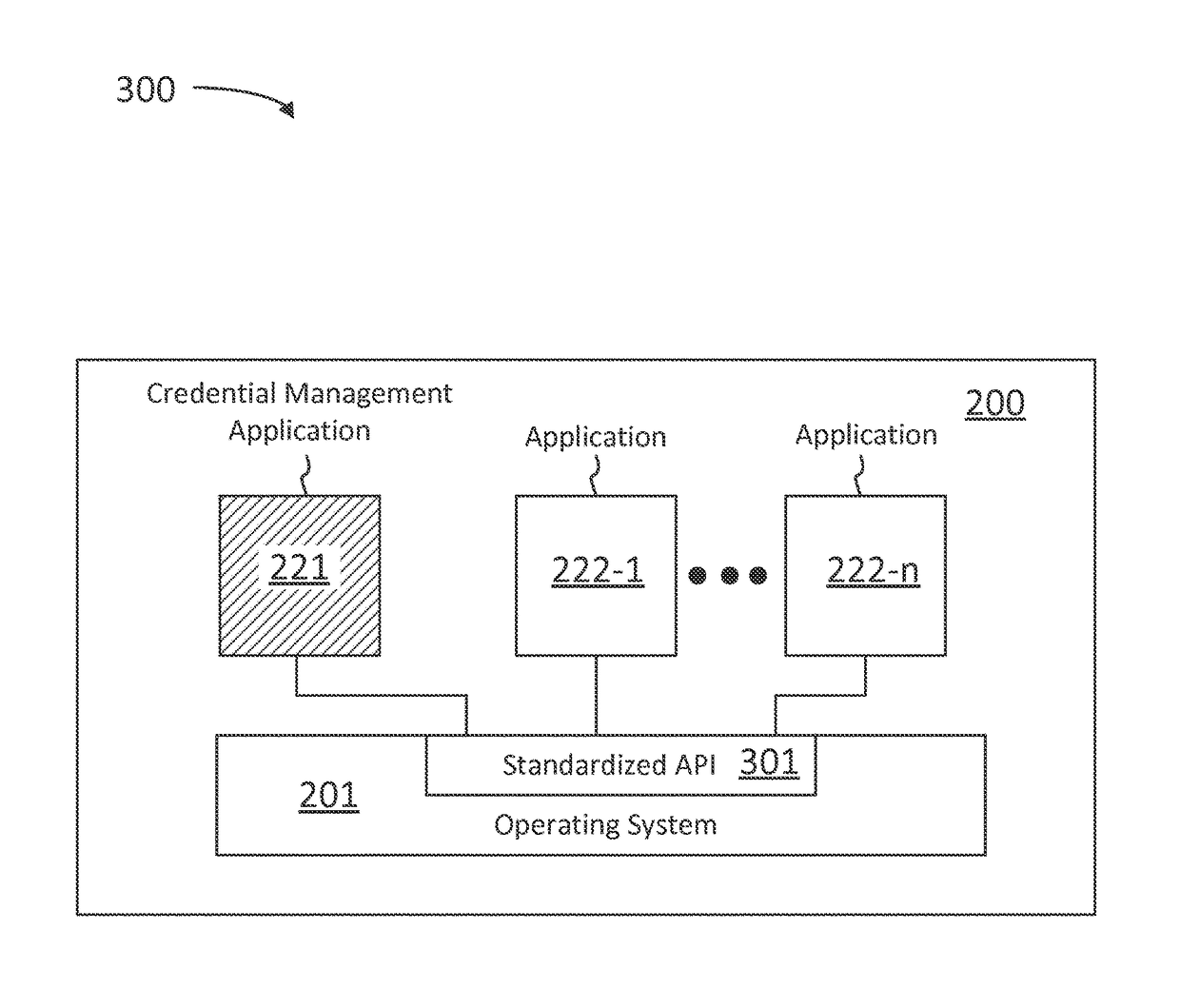
Operating system interface for credential management
ActiveUS9825934B1User identity/authority verificationNatural language data processingOperational systemCredential management
A computer-implemented method for providing an operating system level interface for communicating credential data between applications includes detecting, by an operating system, a field configured to receive an authentication credential and identifying a credential management application configured to provide authentication credentials. The method includes requesting, by the operating system and using an operating system interface configured to communicate authentication credentials, the authentication credential from the credential management application. And when the credential management application provides the authentication credential using the operating system interface configured to communicate authentication credentials, the method includes providing the authentication credential for entry into the field.
Owner:GOOGLE LLC
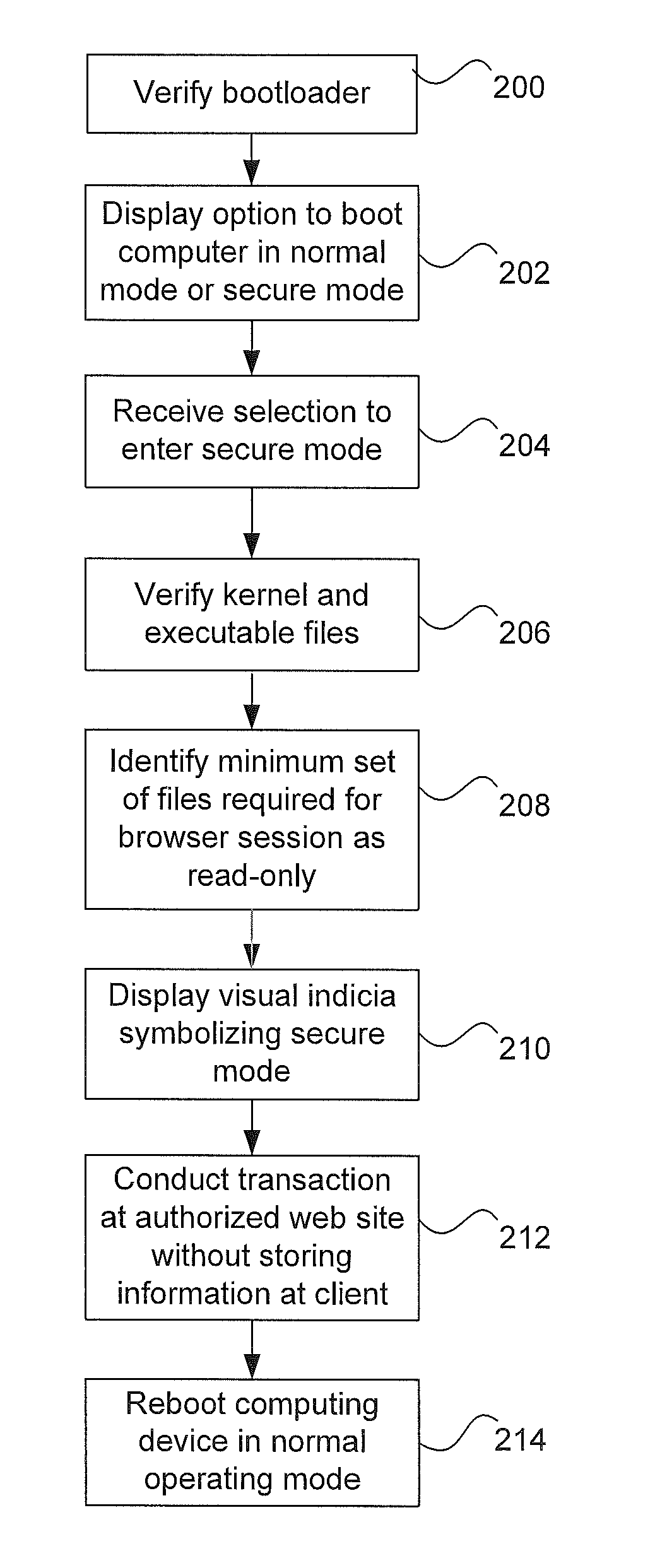
System and method for operating a computing device in a secure mode
ActiveUS8700895B1Memory loss protectionDigital data processing detailsOperational systemProgram validation
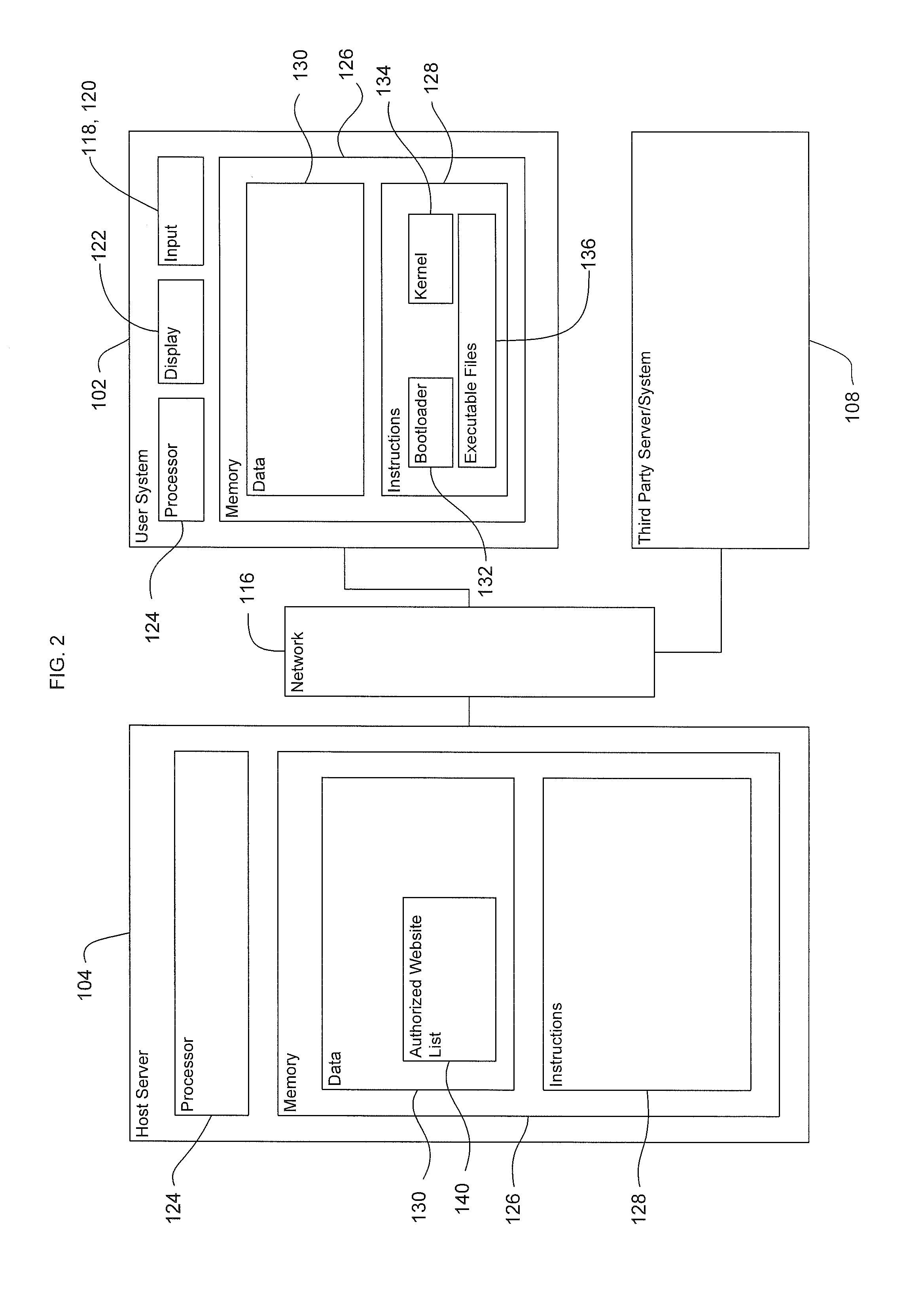
A computing device operates in a secure operating mode in response to user selection. Computer hardware is initialized to verify a bootloader of an operating system, and the bootloader verifies the operating system kernel. The kernel then verifies operating-system level executable files. After verification, a limited set of the verified files is loaded into a portion of the memory that is subsequently marked by the kernel as read-only. These files are executed to provide a basic Internet browser session; all other files are identified as non-executable. When the user accesses an authorized website and conducts a transaction that requires a user to provide information, the information is encrypted during transmission of the network. In addition, such information cannot be accessed by other parties since the information provided is not persisted at the computing device.
Owner:GOOGLE LLC
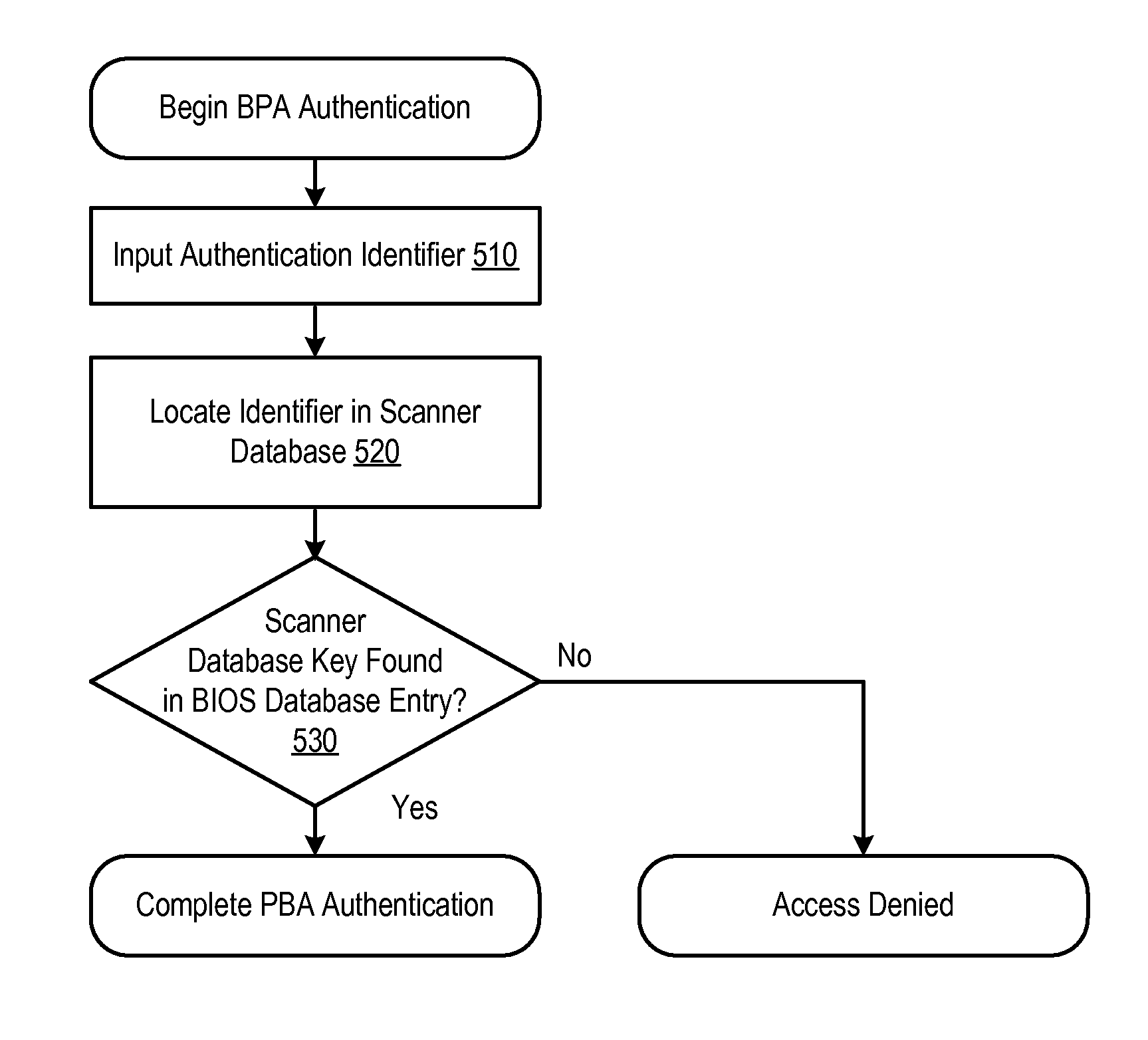
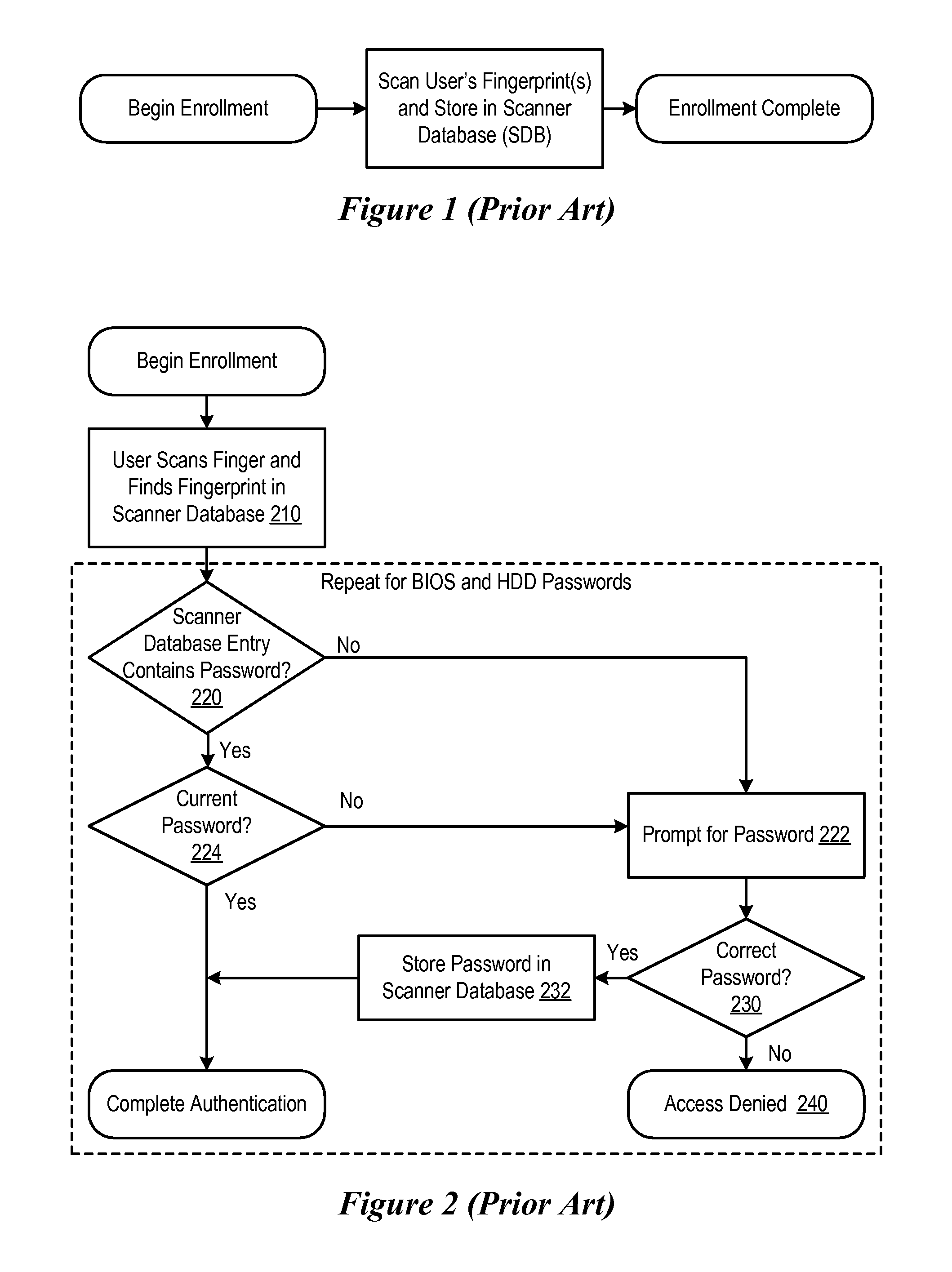
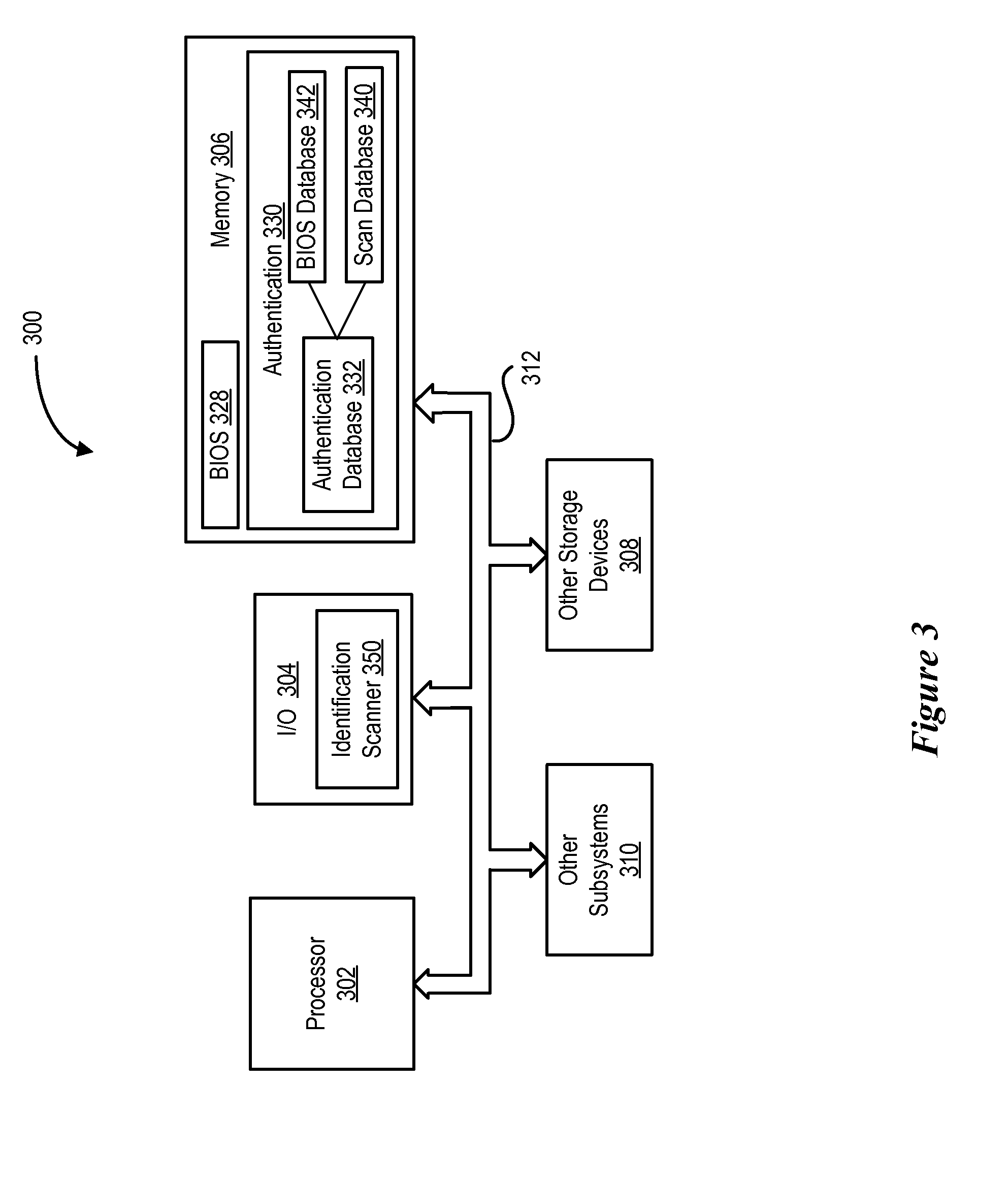
System and Method for Enrolling Users in a Pre-Boot Authentication Feature
InactiveUS20080052526A1Increase experienceSimple processDigital data authenticationSecret communicationPre-boot authenticationOperational system
An authentication method set forth which includes an interface that can be used by operating system level software to verify and set various hardware level passwords, like the BIOS boot password and hard disk password. The method further specifies an application behavior that allows an operating system level pre-boot authorization (PBA) enrollment application to set and verify and make use of any hardware level passwords that are needed for PBA enrollment.
Owner:DELL PROD LP
OS Security Filter
ActiveUS20140283118A1Digital data processing detailsAnalogue secracy/subscription systemsOperational systemData operations
A system and method for protecting against the unauthorized use of operating system level commands is disclosed. The system includes a computer module including: a processor configured for performing data operations; a memory unit configured to store instructions executable by the processor; and an operating system module for supporting basic functions of the computer module, such as scheduling tasks, executing applications, and controlling peripherals. A virtual keyboard is connected to the computer module for creating one or more events or sequences of events recognizable by the operating system module. A system level command filter module is provided for filtering system level commands from the one or more recognizable events or sequences of events.
Owner:ID INTEGRATION
System and method for providing sticky applications
InactiveUS7925988B2Execution for user interfacesInput/output processes for data processingWeb applicationOperating system level
A system and method for providing sticky applications are provided. A “sticky application” is an operating system (OS) level application that has the ability to “stick” to web applications and become a part of the web page on which the web application is running. While the sticky application is stuck to the web application, it behaves as if it were a web application with respect to the user. When the user chooses to “unstick” the application, it will return to behaving as an OS level application. The sticky application imitates being a web-based application instead of an operating system level application while stuck. This imitation involves the sticky application being placed on pixel coordinates within a web page of the web application and the sticky application remaining in the pixel coordinates within the web page where it is placed even when a user modifies the representation of the web page.
Owner:INT BUSINESS MASCH CORP
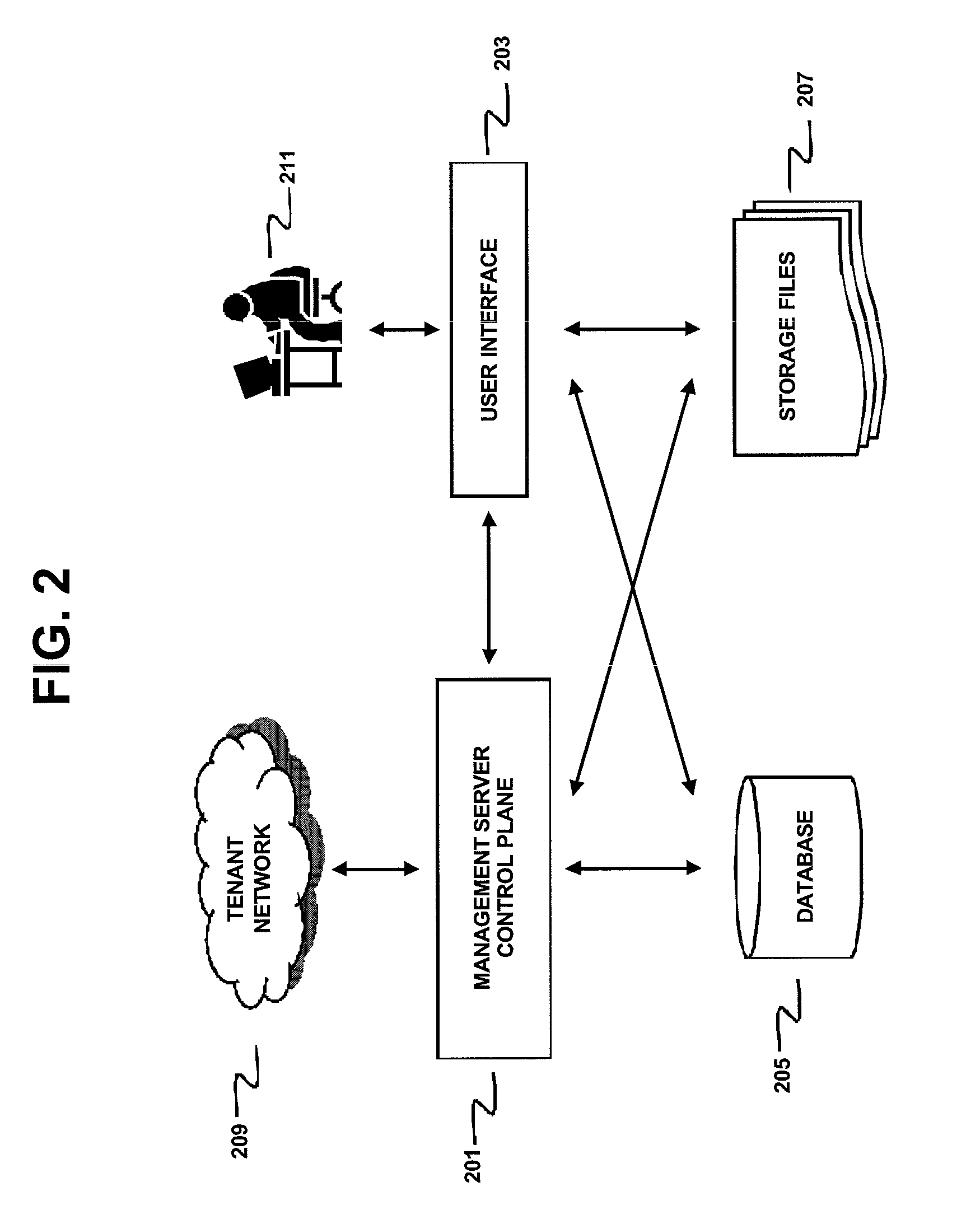
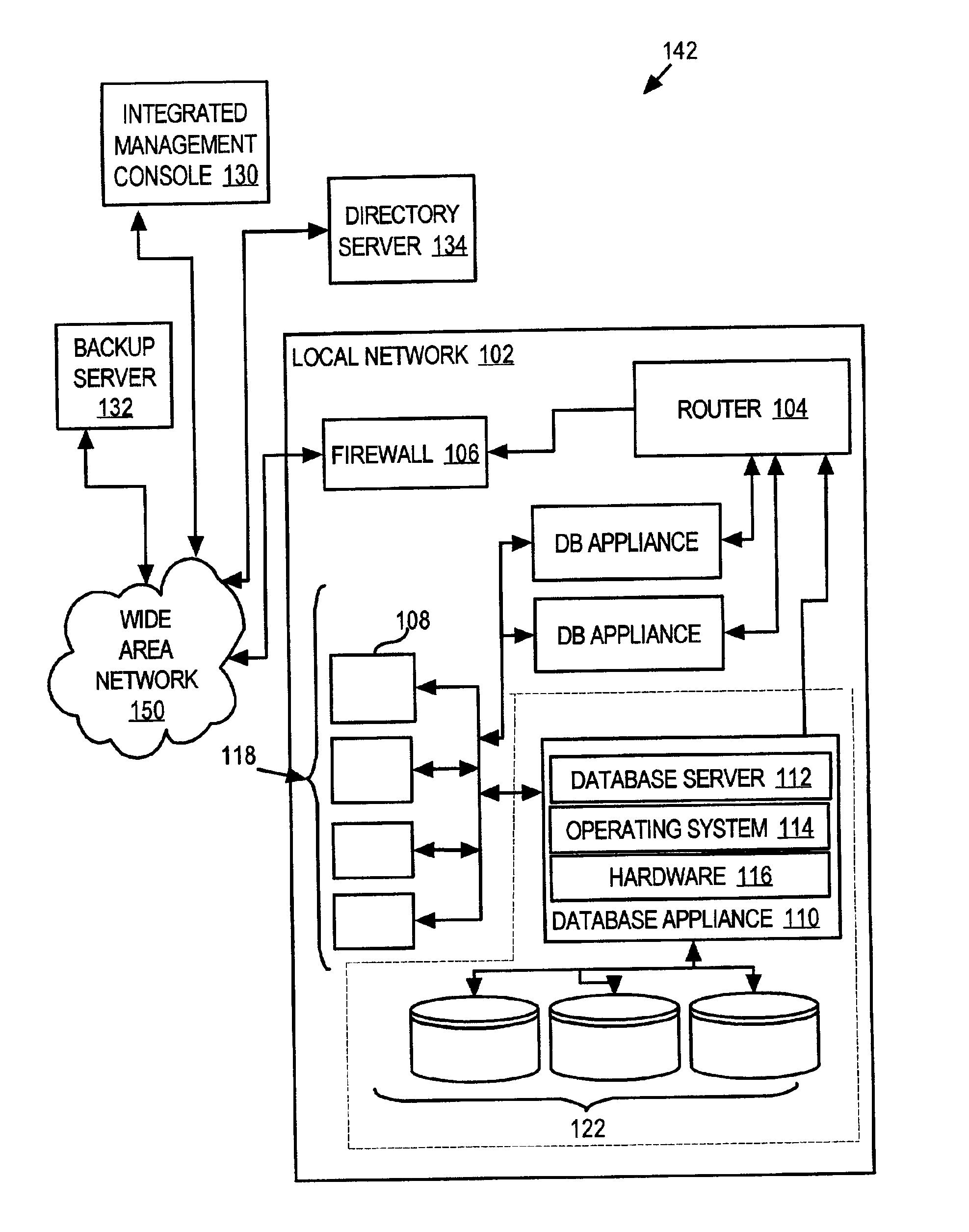
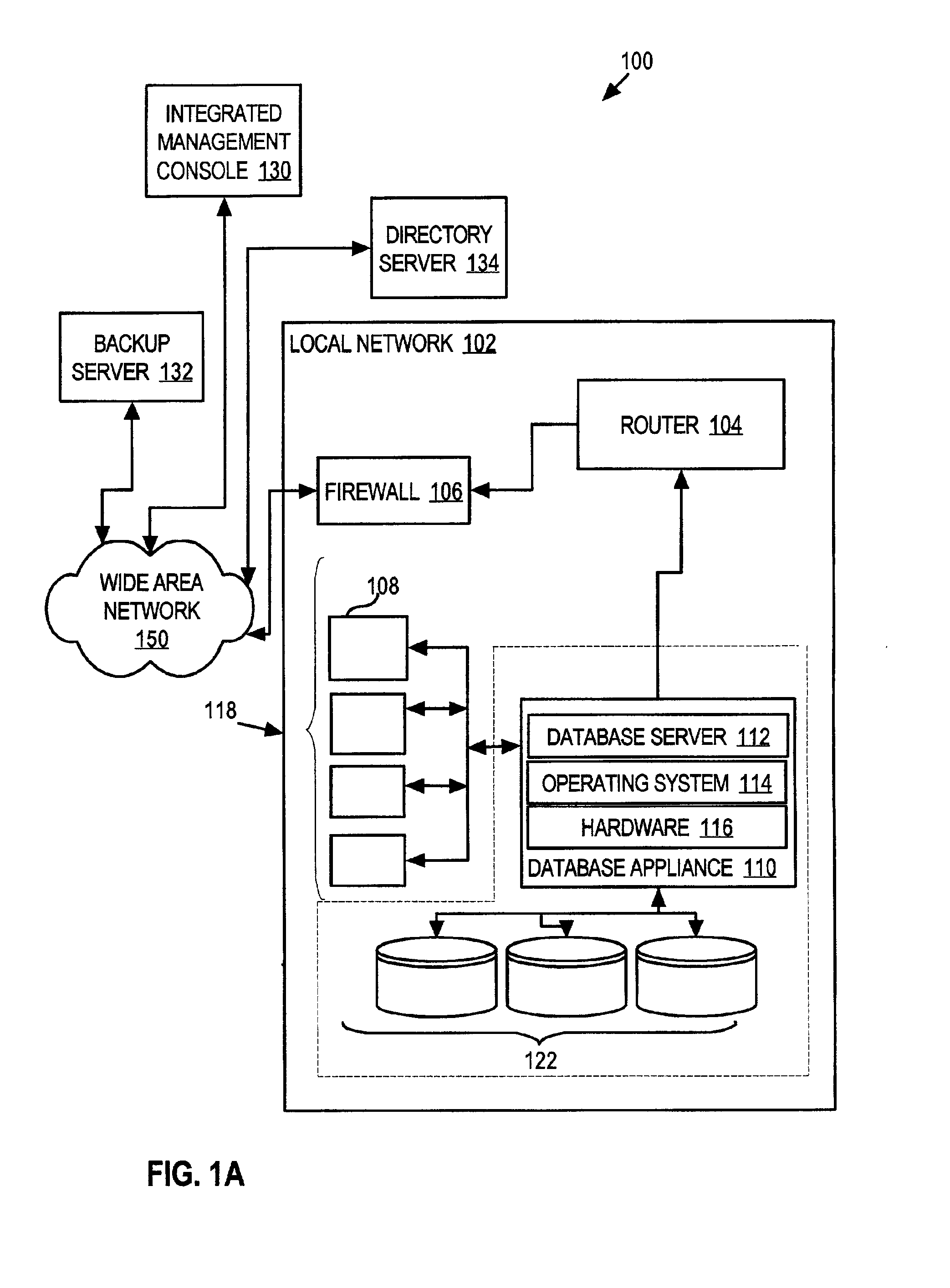
Techniques for managing configuration for a system of devices arranged in a network
InactiveUS6988102B2Low costImprove usabilityData processing applicationsMultiprogramming arrangementsOperational systemDatabase server
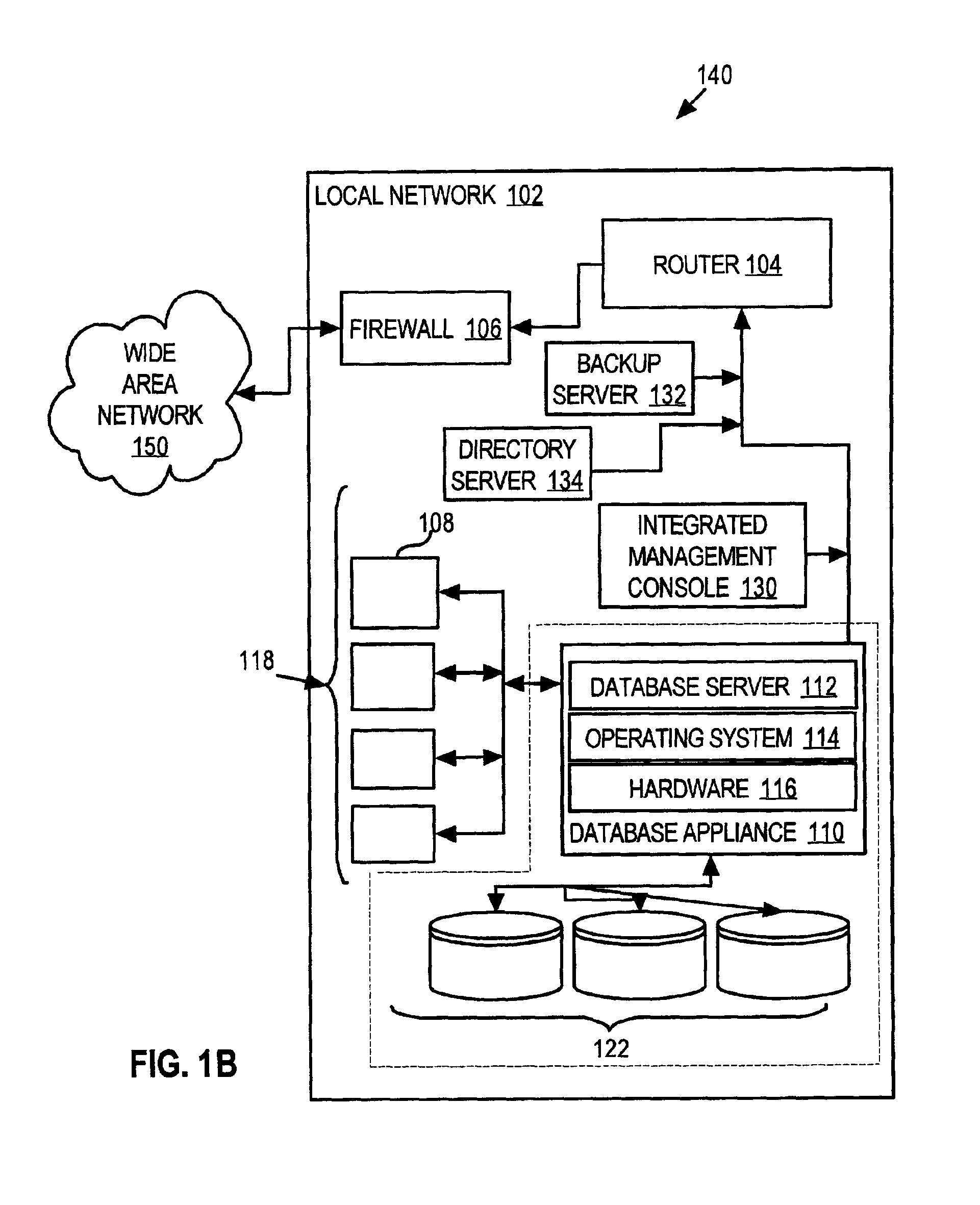
A database system that incorporates numerous features that reduce the total cost of maintaining the database system is provided. That database system includes a database appliance that executes a database server on a platform that includes a special purpose operating system specifically tailored to the services required by the database server. The database appliance configures itself by detecting the environment in which it resides and setting operational parameters based on the detected environment. The configuration metadata of all components of the system are stored in a centralized repository which itself may reside external to the system. Both the database server configuration and the operating system configuration are managed by a remotely located integrated management console, which interacts with and configures the system at the database system level, the operating system level and, optionally, at the hardware subsystem level. Backup management may also be performed remotely. The remote components, such as the integrated management console, the backup server, and the configuration repository, may communicate with the system through a wide area network, such as the Internet, or directly through a dial-up connection.
Owner:ORACLE INT CORP
Method of fast switching control for different operation systems operated in computer
ActiveUS7549041B2Extended boot timeReduce boot timeDigital computer detailsData resettingOperational systemOperating system level
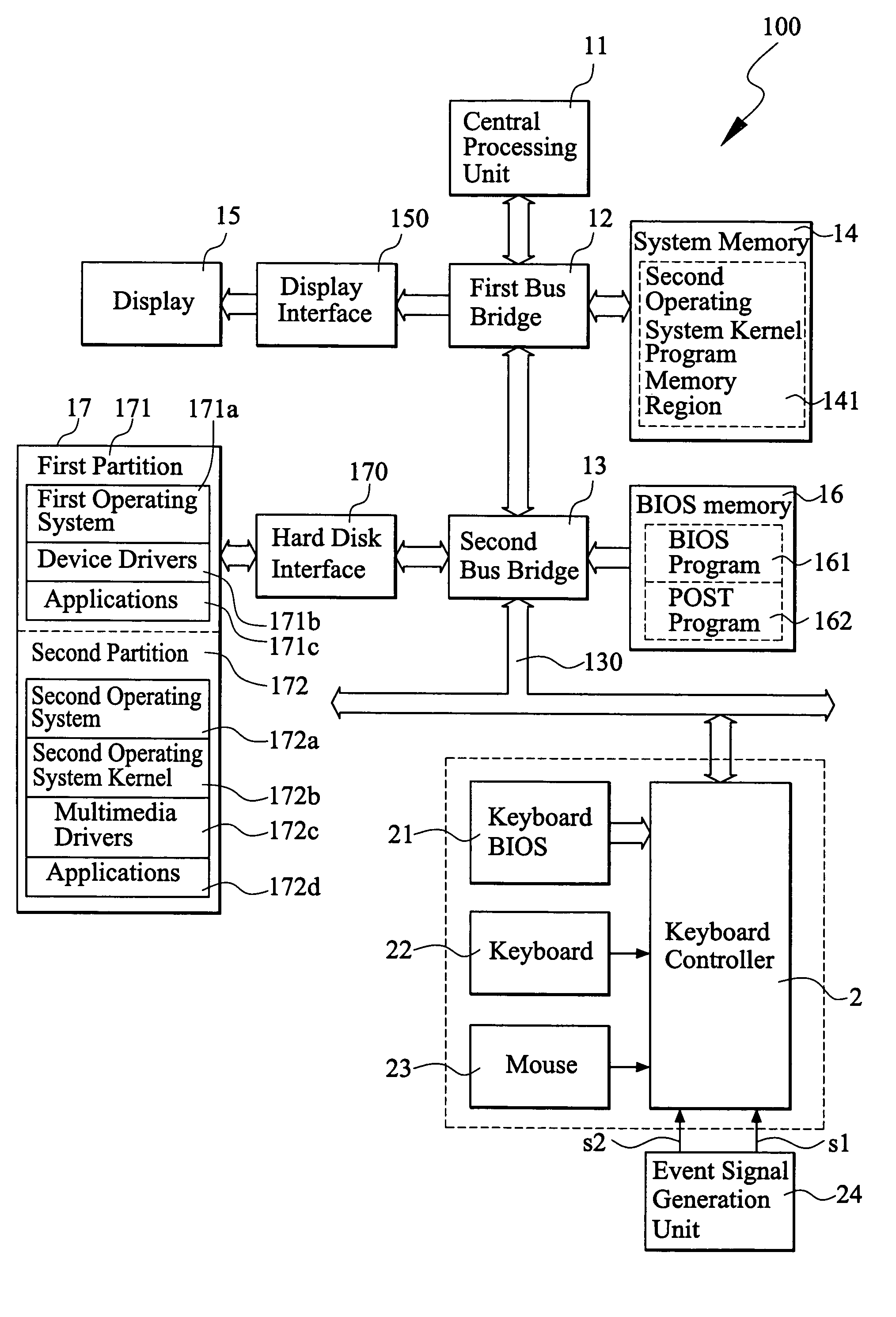
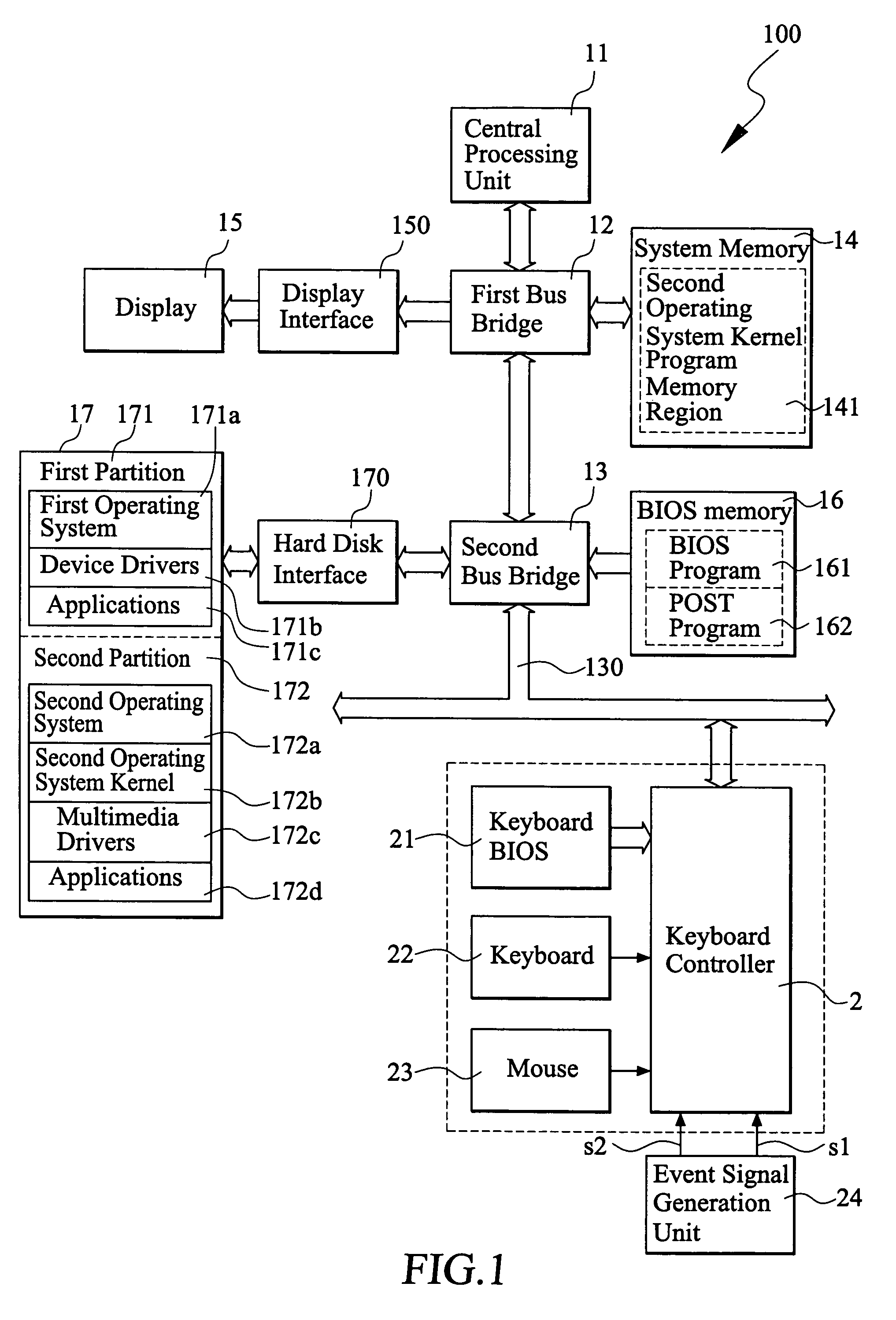
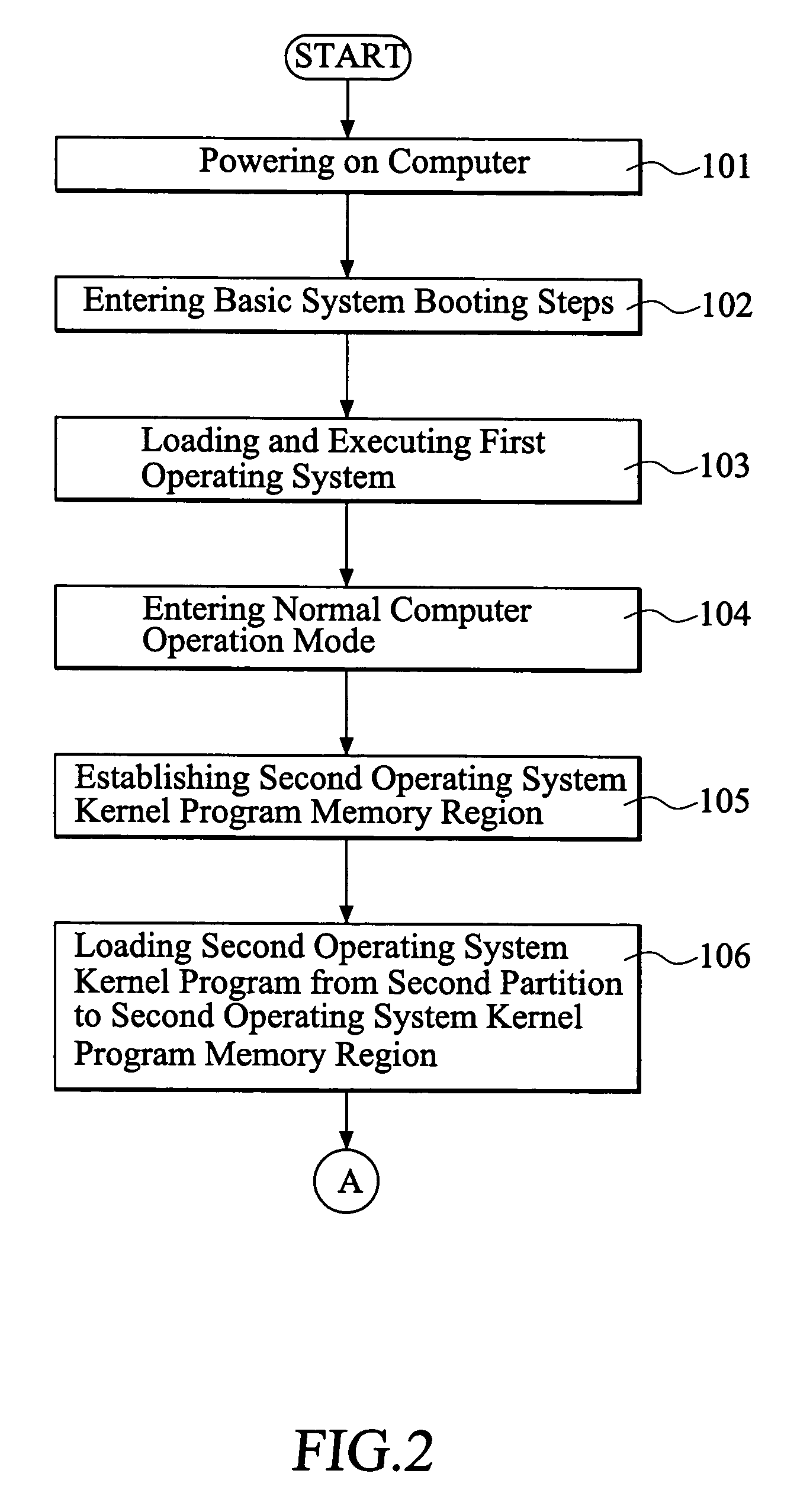
A method of fast switching control for different operation systems operated in computer is provided, including installing a first operating system, a second operating system and a second operating system kernel program in a hard disk of the computer. An event signal generation unit is connected to the computer. When the computer completes the booting process, the first operating system is loaded and executed, the second operating system kernel program memory region is established in a system memory, and the second operating system kernel program is loaded into the second operating system kernel program memory region. When the computer detects that a preset event signal is generated from the event signal generation unit, the second operation system kernel program preloaded in the second operating system kernel program memory region is executed, so that the computer is switched from executing the first operation system to executing the second operation system.
Owner:GETAC TECH CORP
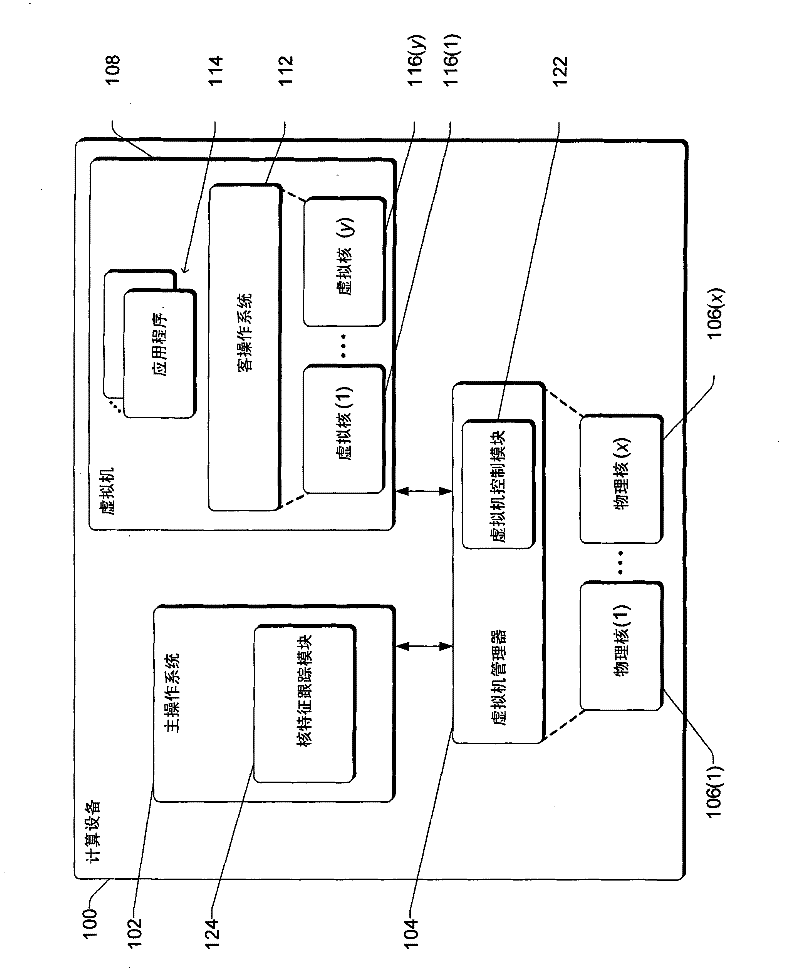
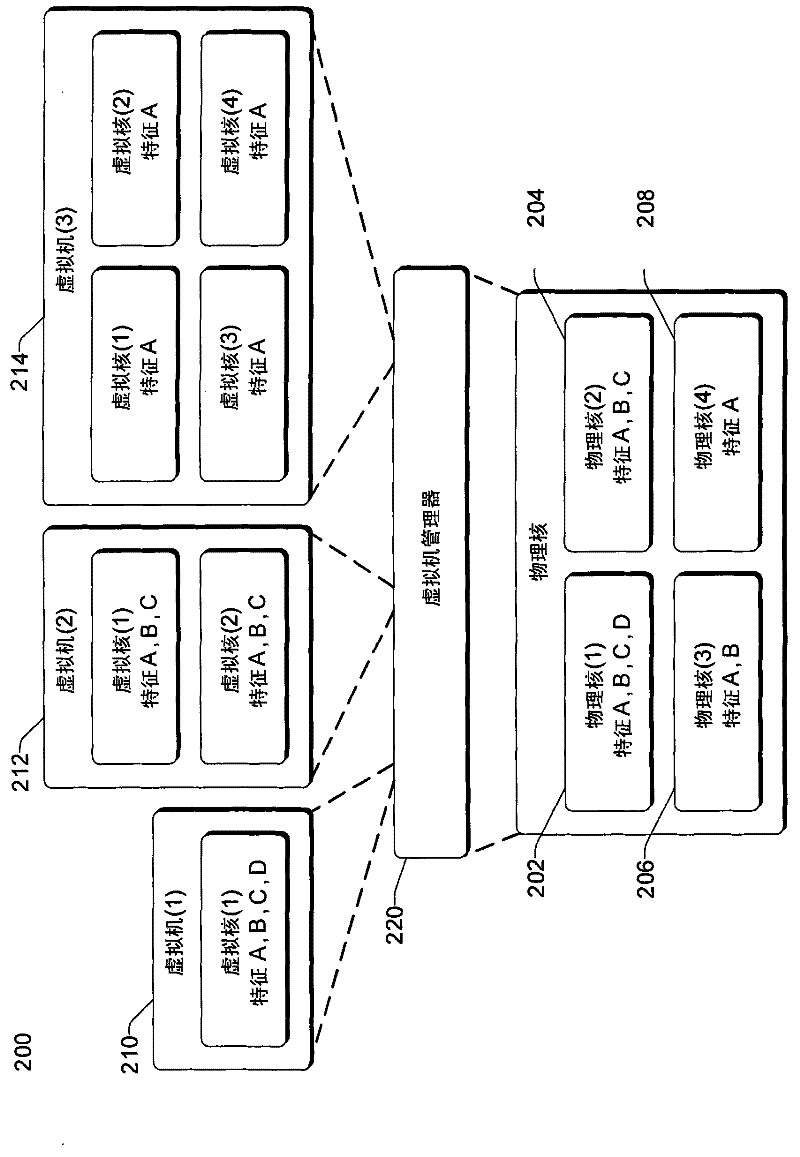
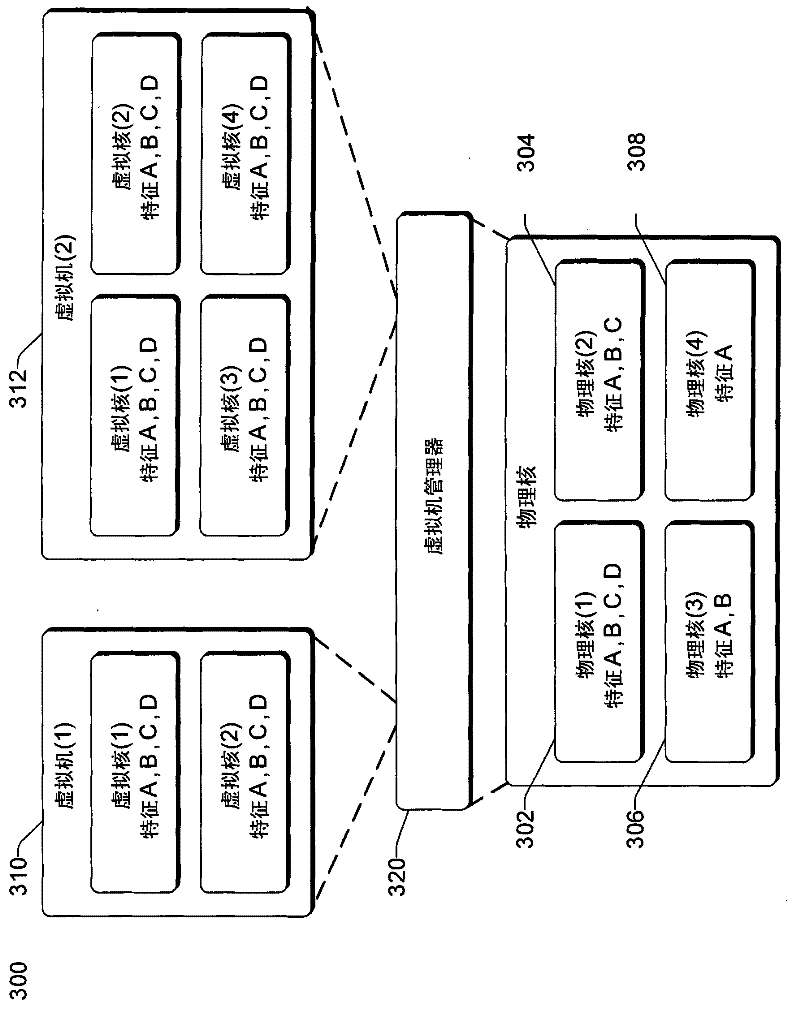
Virtual machine and/or multi-level scheduling support on systems with asymmetric processor cores
ActiveCN102402458AMultiprogramming arrangementsSoftware simulation/interpretation/emulationPhysics processing unitOperating system level
The present invention relates to a virtual machine and / or a multi-Level Scheduling Support on systems with asymmetric processor cores. Different processor cores in a computing device can support different features. In one or more embodiments, the features supported by each of multiple physical processor cores of a computing device are identified. A set of one or more features of the multiple physical processor cores to make available to virtual processor cores of the virtual machine are determined based at least in part on both the one or more features supported by each of the multiple physical processor cores and a number of virtual processor cores of the virtual machine. In additional embodiments, a multi-level scheduling model is used. An operating system level scheduler of an operating system schedules multiple applications for execution on multiple processor cores, and a user level scheduler of an application schedules application threads of that application for execution on one or more of the multiple processor cores.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for providing context sensing and fusion
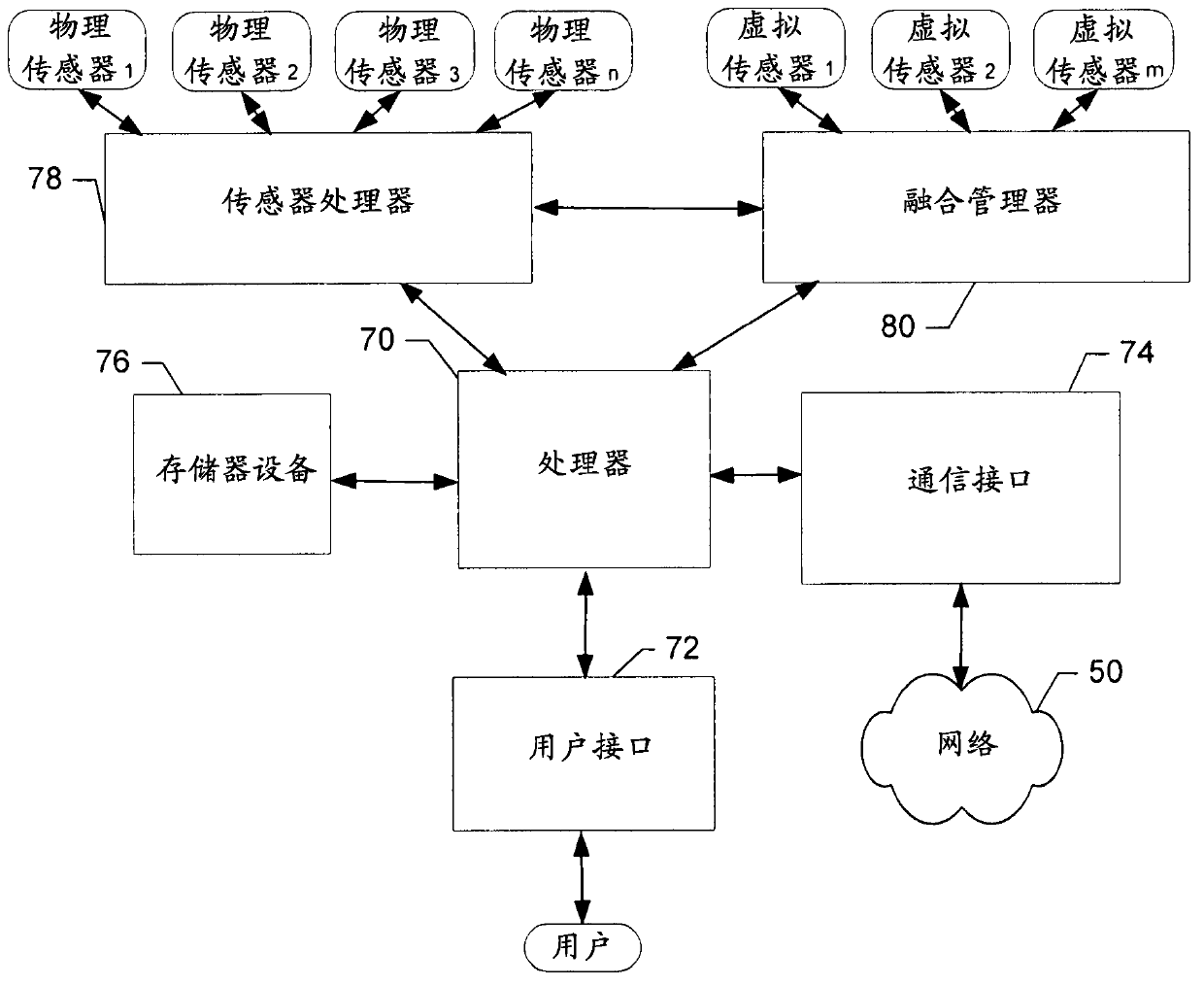
InactiveCN102893589AProgram control using stored programsDevices with GPS signal receiverContext sensingOperating system level
A method for providing context sensing and fusion may include receiving physical sensor data extracted from one or more physical sensors, receiving virtual sensor data extracted from one or more virtual sensors, and performing context fusion of the physical sensor data and the virtual sensor data at an operating system level. A corresponding computer program product and apparatus are also provided.
Owner:NOKIA TECHNOLOGLES OY
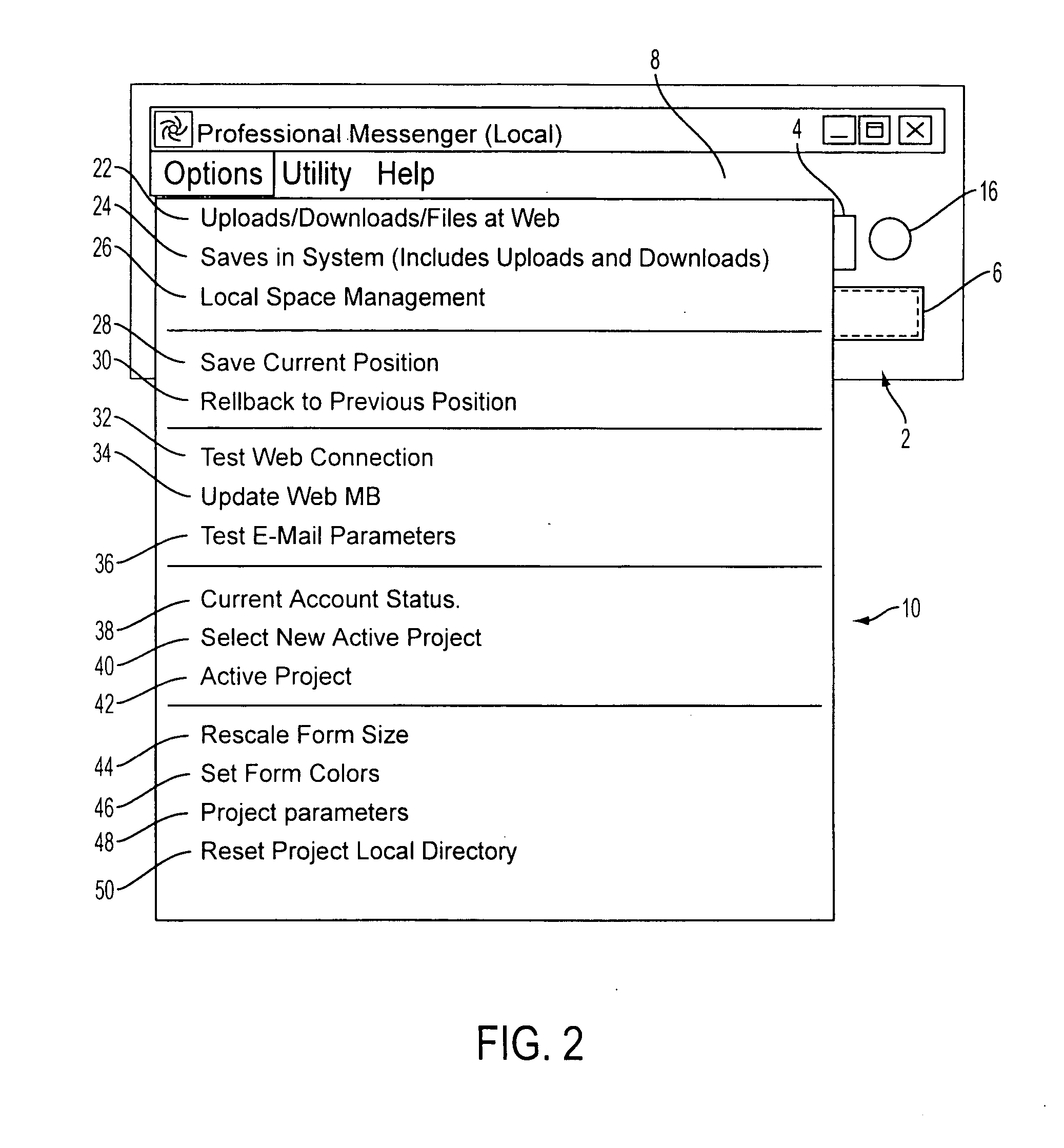
Simplified, secure electronic project data exchange
InactiveUS20050262148A1Simple rollback featureResolution problemSpecial data processing applicationsOperational systemInternet privacy
A system and method of exchanging project data between disparate levels of users, independent of whether the user is a client or professional, or which operating system level or software is employed.
Owner:DAVITT HAROLD HUGH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com