Multi-key searchable encryption method and system based on attribute access control structure
A technology of access control and encryption method, which is applied in the field of cryptography and secure data sharing, and can solve problems such as data owner attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
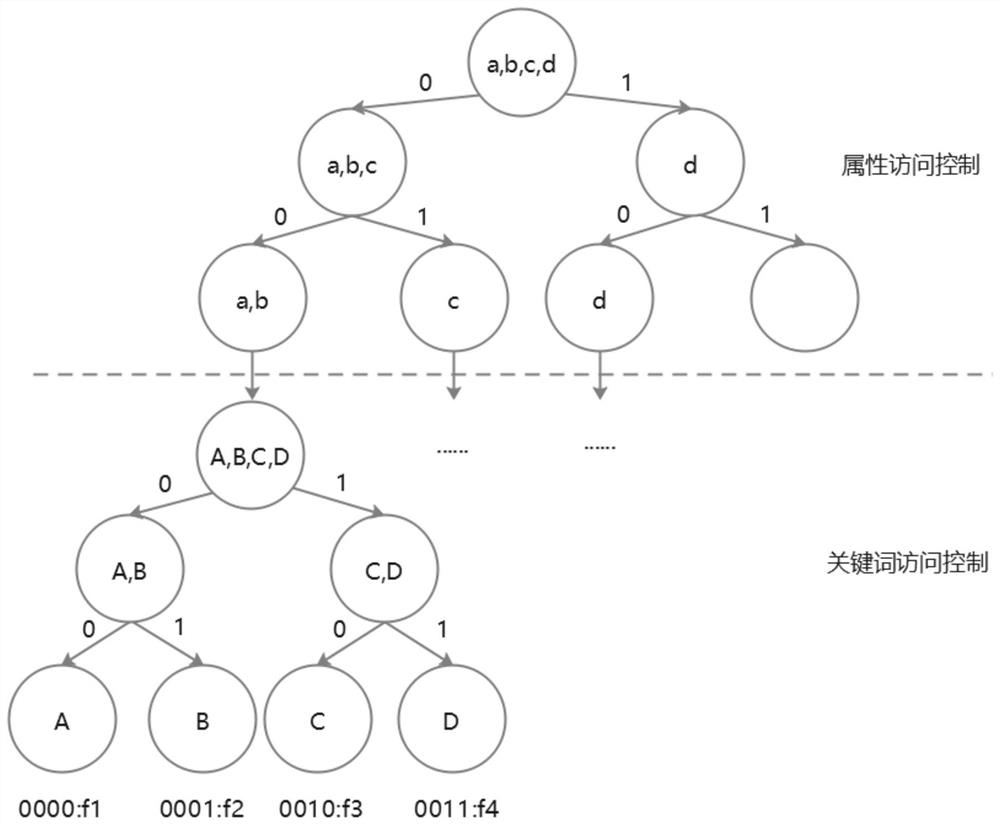
Image
Examples
Embodiment
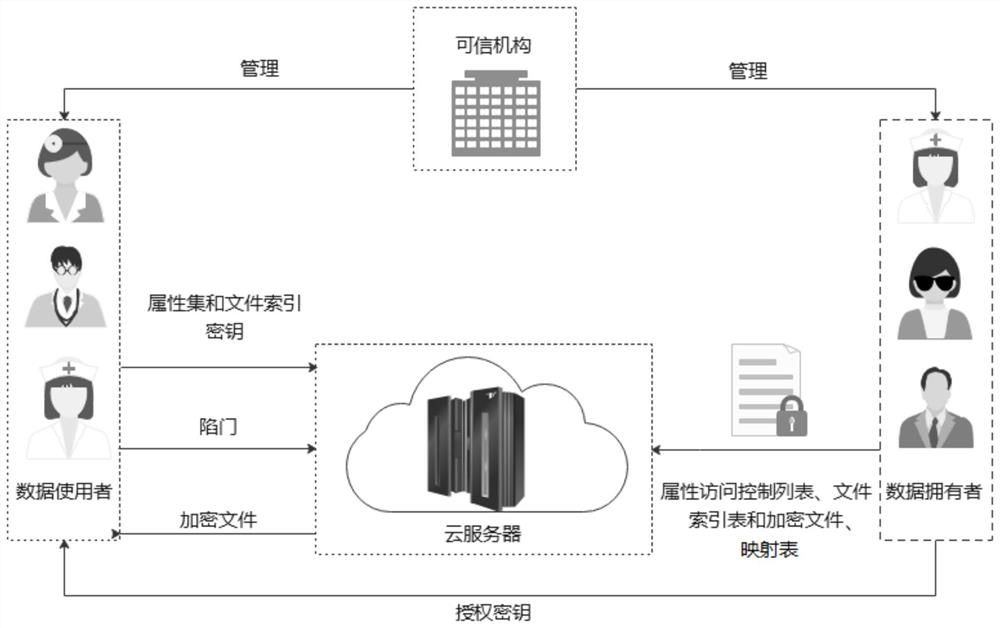
[0077] This embodiment discloses a multi-key searchable encryption method based on an attribute access control structure. The method is applied in a multi-key searchable encryption system based on an attribute access control structure. The system model is as follows figure 1 As shown, there are mainly four types of participants: an authority (Trusted Authority, TA), a cloud server (Cloud Server, CS), multiple data owners (Data Owner, DO) and multiple data users (Data User ,DU).
[0078] Among them, the authoritative organization (TA) is a third-party trusted organization, which is responsible for the generation of system public parameters and user attributes.
[0079] The cloud server (CS) is a designated server, which is honest and curious, that is, it can honestly execute instructions and return correct results, but it may actively collect and analyze user data, such as data owner's files, file indexes, data The attribute set of the user, the keyword of the query, etc.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com