Data encryption method, device, data decryption method and device
A data encryption and data decryption technology, applied in the direction of user identity/authority verification, etc., can solve the problems of reducing data security, increasing the cost of data encryption processing, increasing the risk of key decryption, etc., to achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] This embodiment provides a data encryption method, such as figure 1 The method shown includes:
[0032] S11. Obtain a random number. The random number is used as an identification to distinguish different encrypted data. The random number may be pre-assigned, for example, it may be calculated based on hardware ID, network IP, encryption operation time and other data. In an actual application environment, the random numbers obtained by multiple encryptors are different, and the random numbers obtained by the same encryptor in different time periods may also be different. For example, in Internet applications, the server in the network can be used as a decryptor, and the user terminal can be used as an encryptor. The random number can be generated by the server and then distributed to the corresponding user terminal. Preferably, the random number can be a universally unique identifier (UniversallyUniqueIdentifier, UUID), and the UUID is a combination of the following pa...
Embodiment 2
[0051] This embodiment provides another data encryption method, such as image 3 As shown, the method includes:
[0052] S31. Obtain a random number, a token corresponding to the random number, and a time stamp. A token is a sign of information (a code composed of one or more binary digits). In Internet applications, only the node that obtains the token has the right to send information packets. The token can be generated by the decryption party and sent to the corresponding Encryptor, which enables the encryptor to have the authority to send encrypted data.
[0053] A timestamp (timestamp) is usually a sequence of characters used to uniquely identify a certain moment, for example, it may be the time when encrypted data is generated or the time when data is sent.
[0054] S32. Obtain a key required for encryption according to the random number.
[0055] S33. Use the key to encrypt the content to be encrypted.
[0056] S34. Generate a first abstract using the encrypted cont...
Embodiment 3
[0070] This embodiment provides a data encryption device, such as Figure 5 The unit shown consists of:
[0071] An acquisition unit 51, configured to acquire a random number;
[0072] An encryption key generating unit 52, configured to obtain a key required for encryption according to the random number;
[0073] An encryption unit 53, configured to use the key to encrypt the content to be encrypted;
[0074] The first summary generating unit 54 is configured to generate a first summary using the encrypted content.
[0075] This embodiment also provides a data decryption device corresponding to the above device, such as Figure 6 The unit shown consists of:
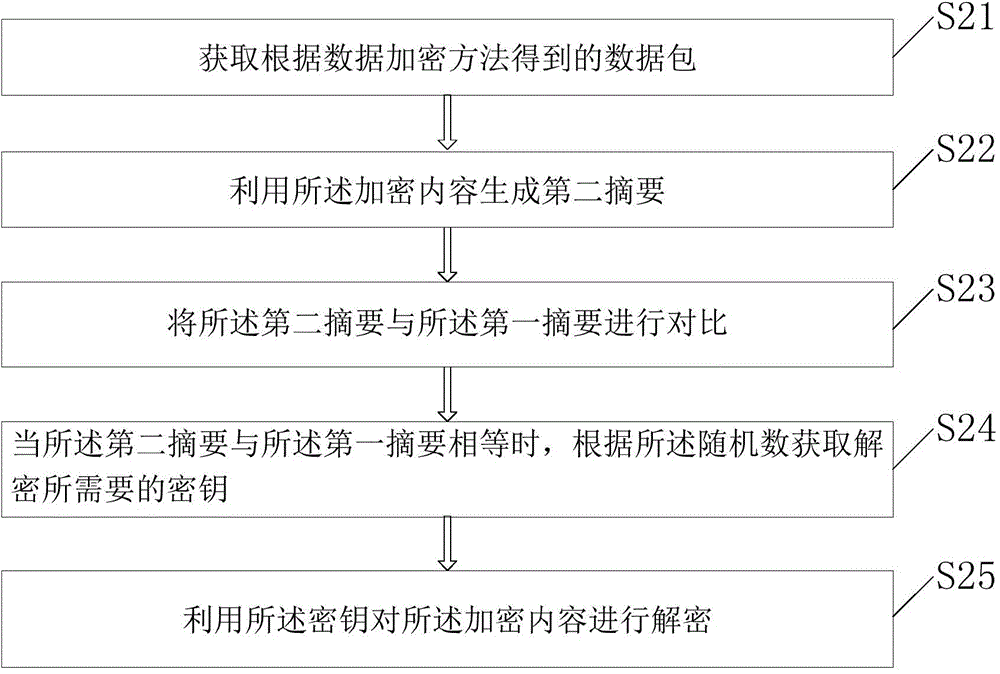
[0076] A data packet obtaining unit 61, configured to obtain the data packet obtained according to the above-mentioned data encryption device;
[0077] A second abstract generating unit 62, configured to generate a second abstract using the encrypted content;
[0078] Abstract comparison unit 63, configured to compa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com