Trusted safety network system
A secure network and credible technology, applied in the field of information security, can solve problems such as software code loopholes and hidden safety hazards, and achieve the effects of avoiding security threats, improving security reliability, and ensuring credible integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
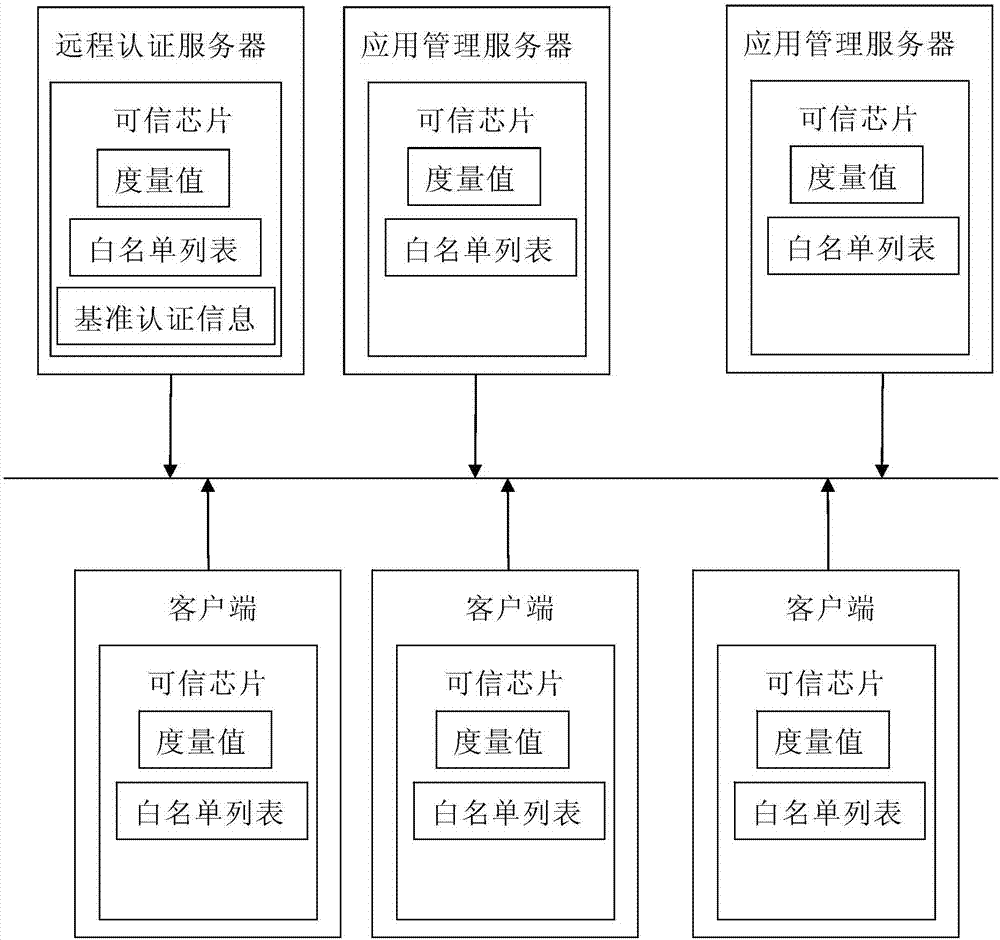
[0029] Such as figure 1 As shown, the present invention discloses a trusted and secure network system, which is implemented based on a client-server architecture, and each network node is a trusted host installed with a trusted chip, wherein at least one server is configured as a remote authentication server, and the configured At least one server serves as the application management server, and the remote authentication server and the application management server may also be the same server.
[0030] 1. Integrity of network nodes
[0031] Verify the integrity of the underlying structure of network nodes through trusted boot. During the startup process of the network node, the CPU, storage module, power supply module, disk and other hardware structures, BIOS (Basic Input Output System, Basic Input Output System), Bootloader (bootloader), sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com