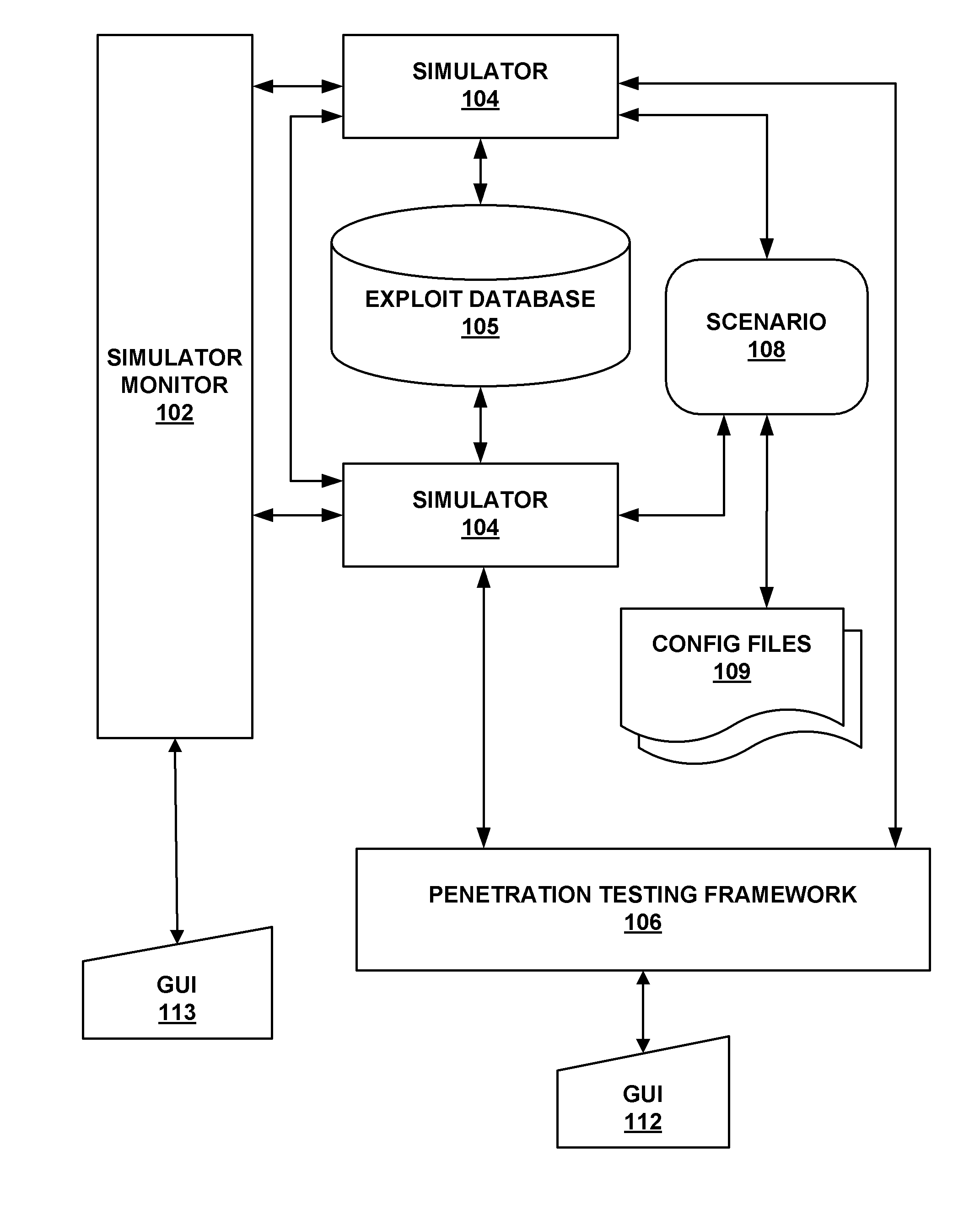
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
250 results about "Network agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
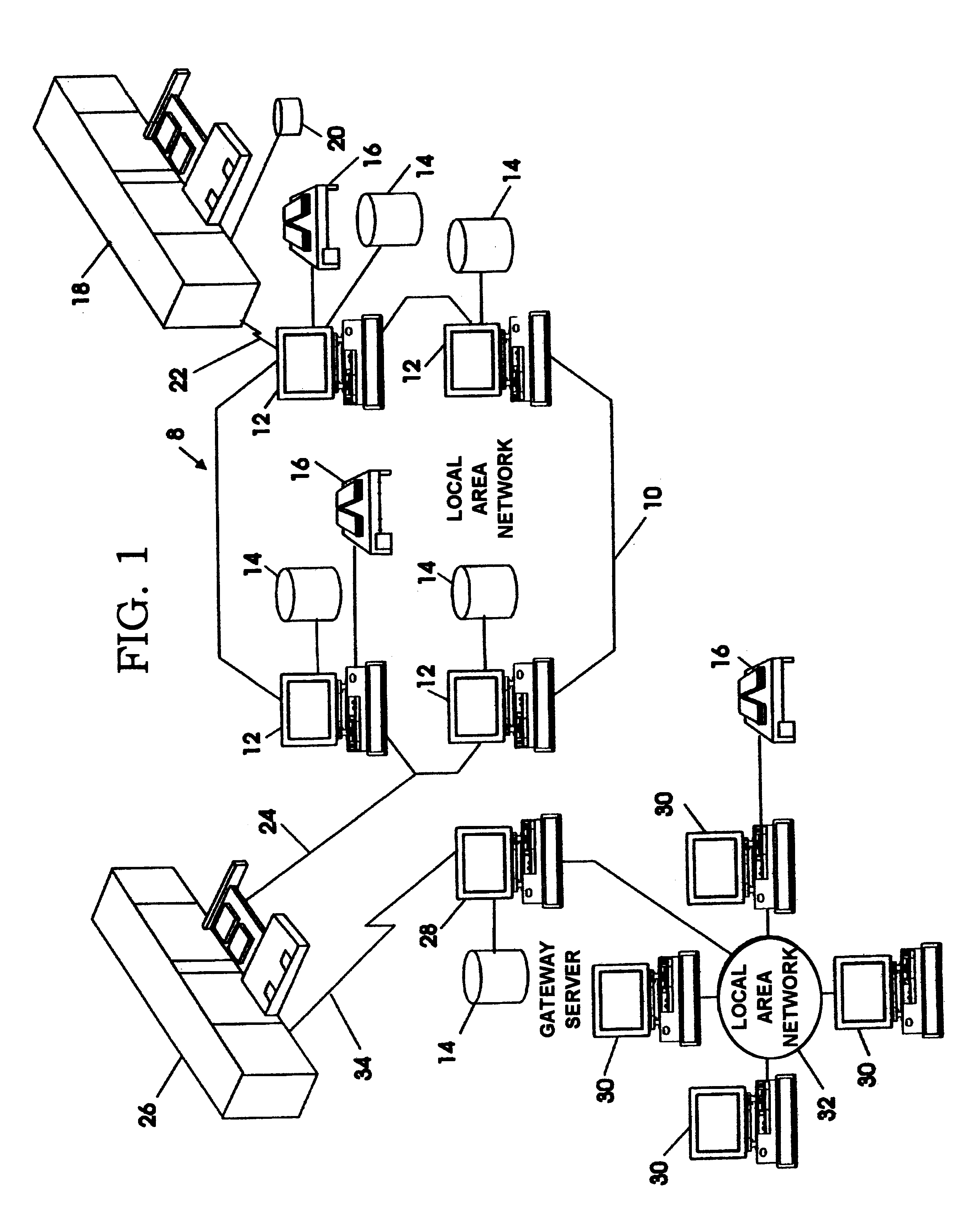
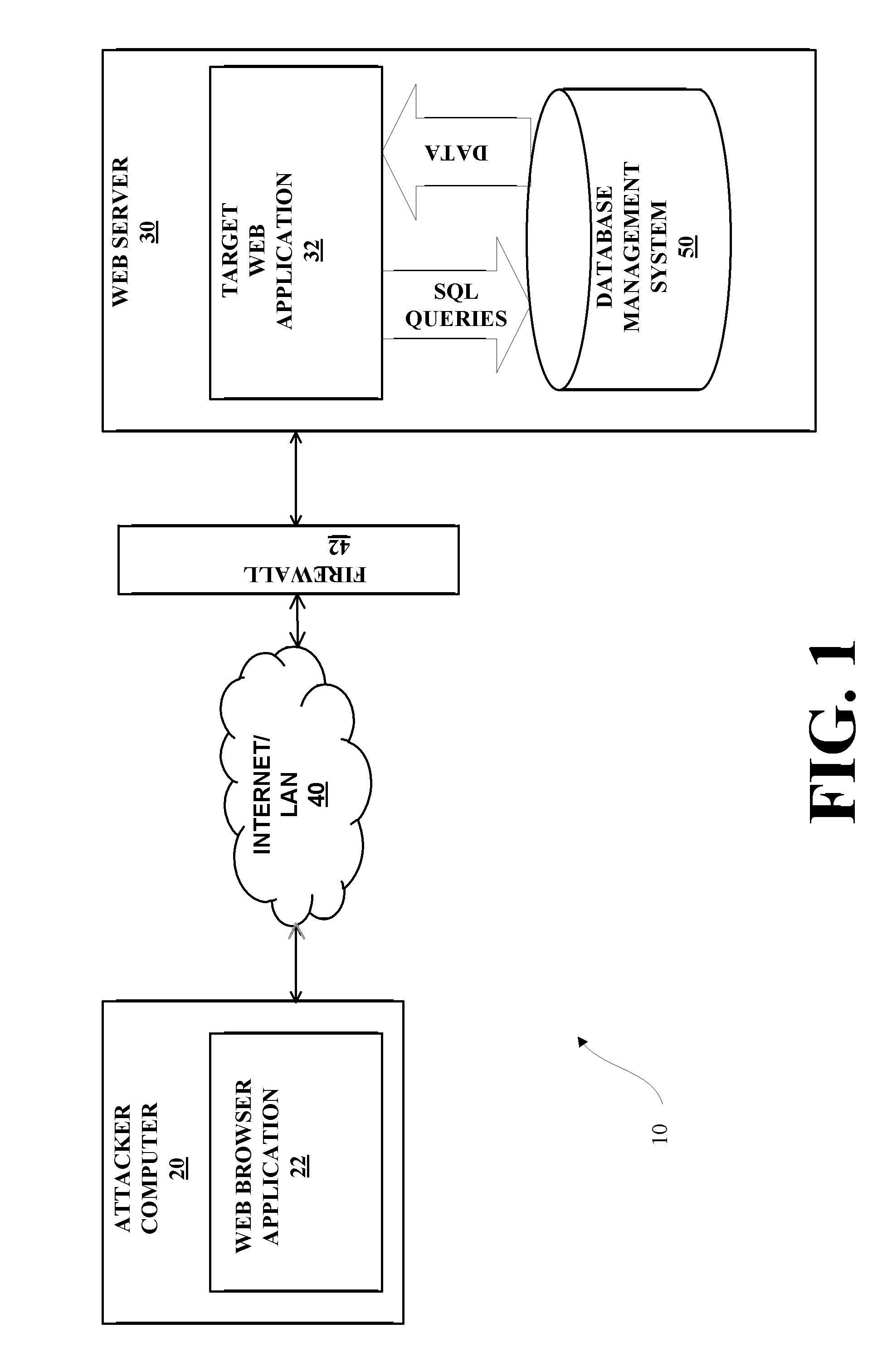
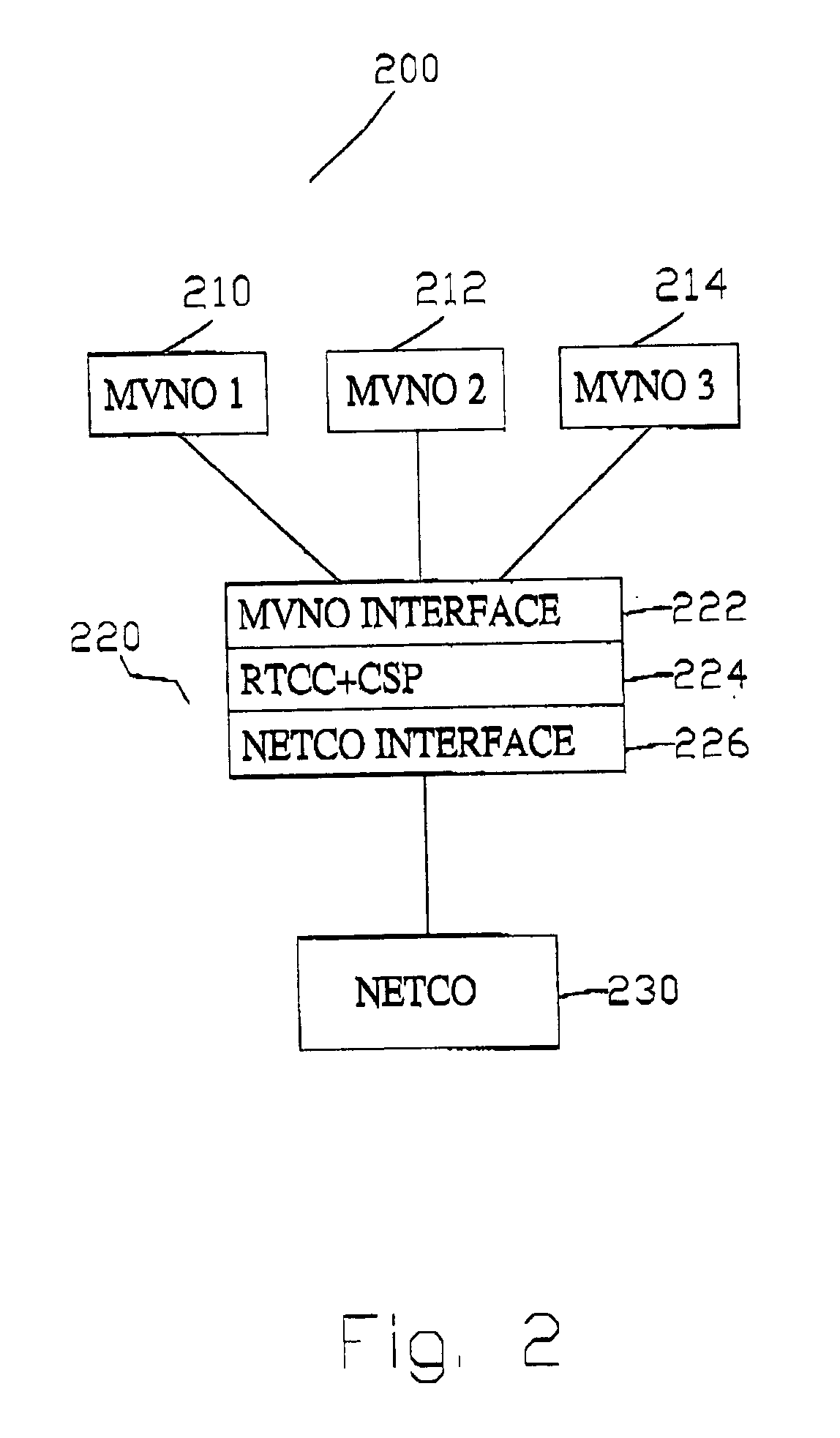
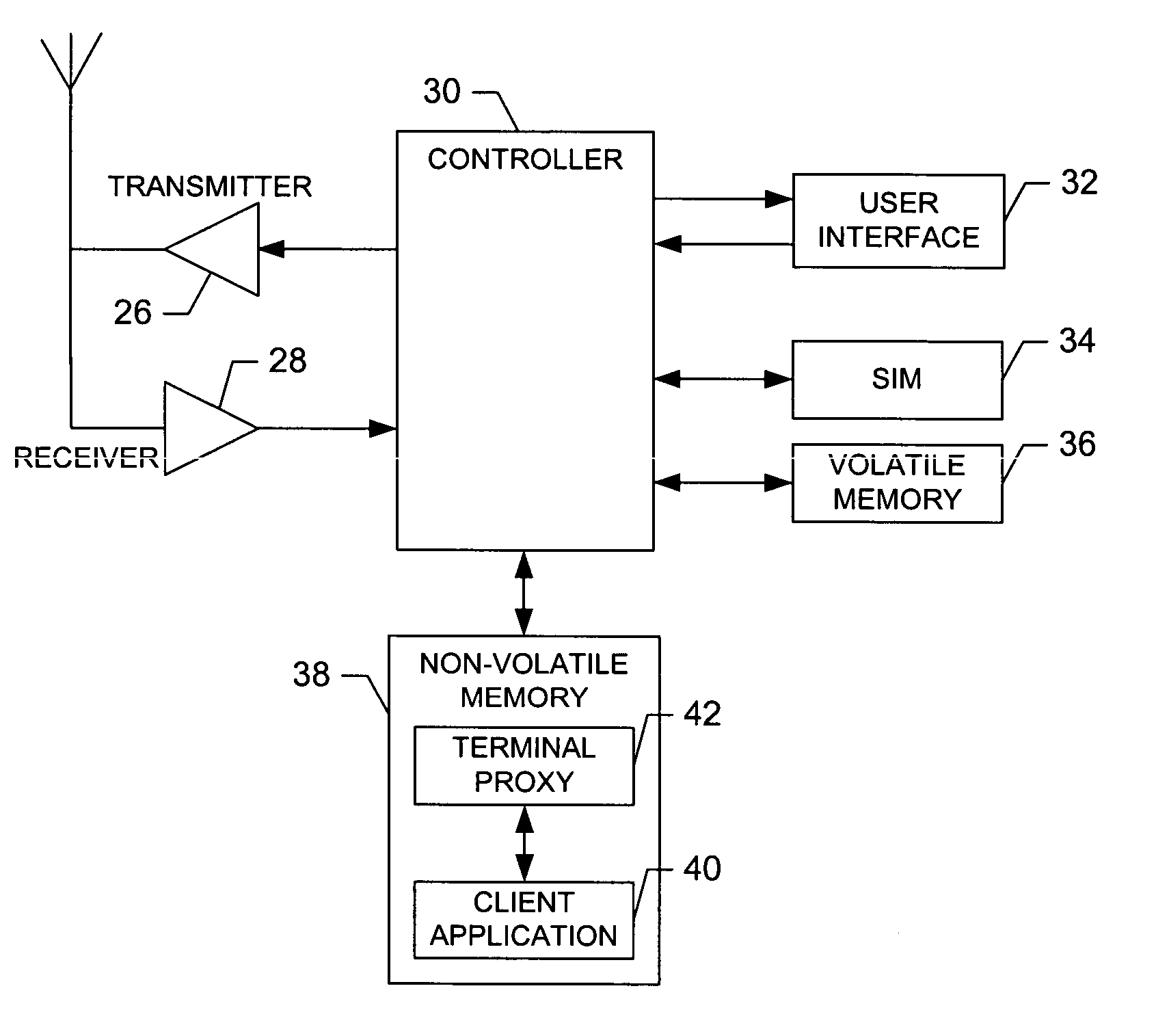
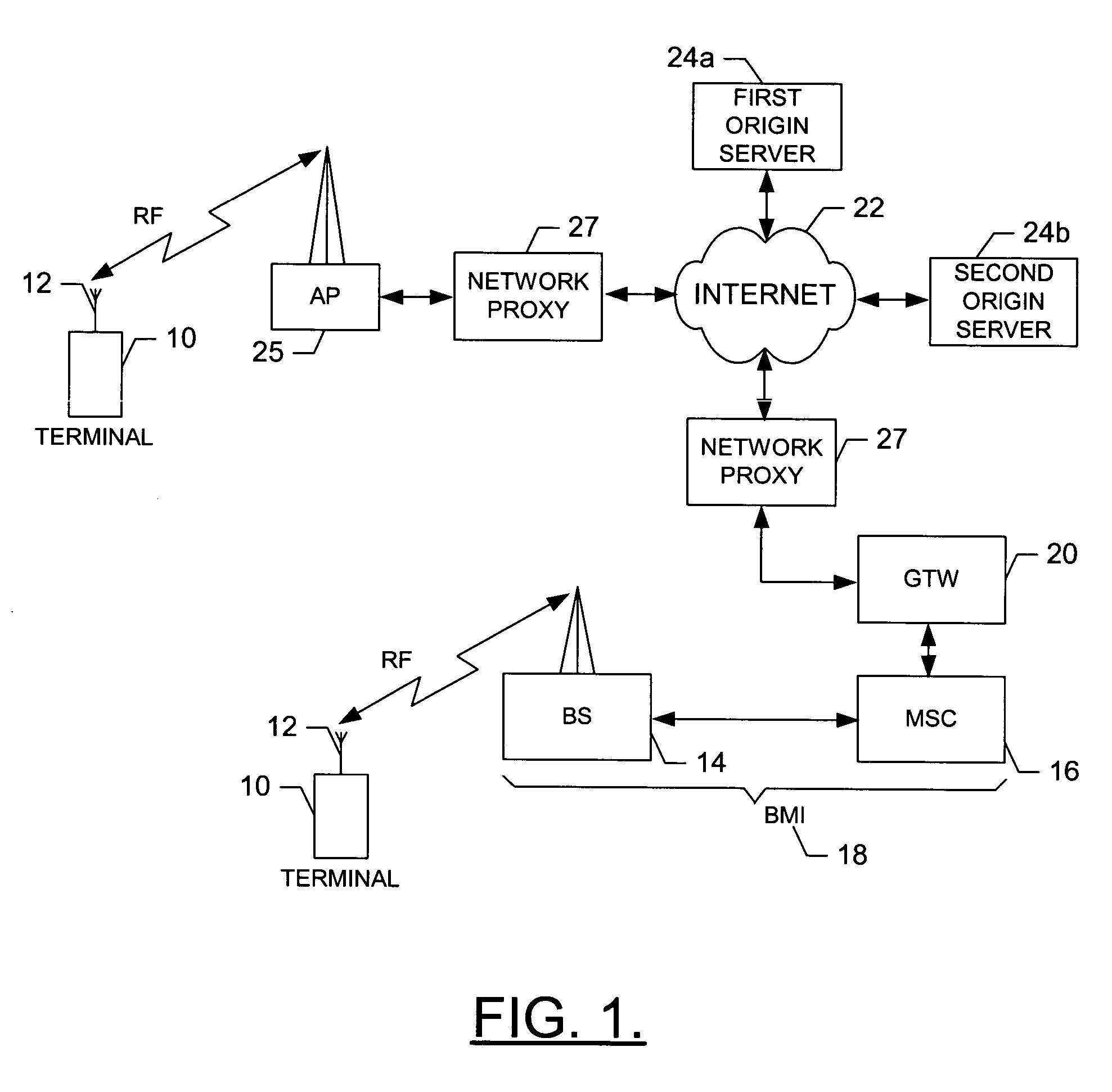
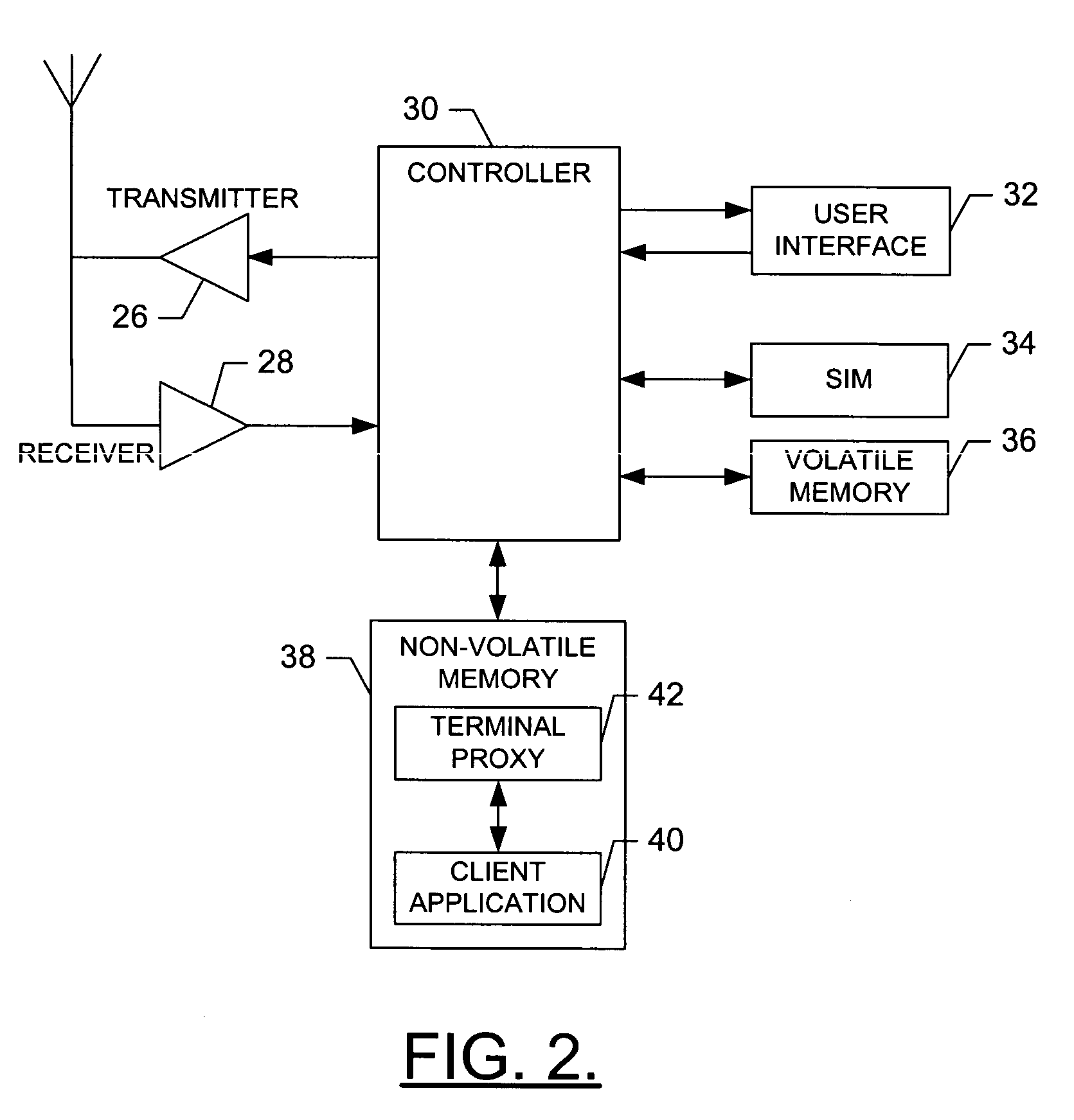
Network proxy apparatus and methods
ActiveUS7565407B1Digital data information retrievalMultiple digital computer combinationsNetwork agentThe Internet
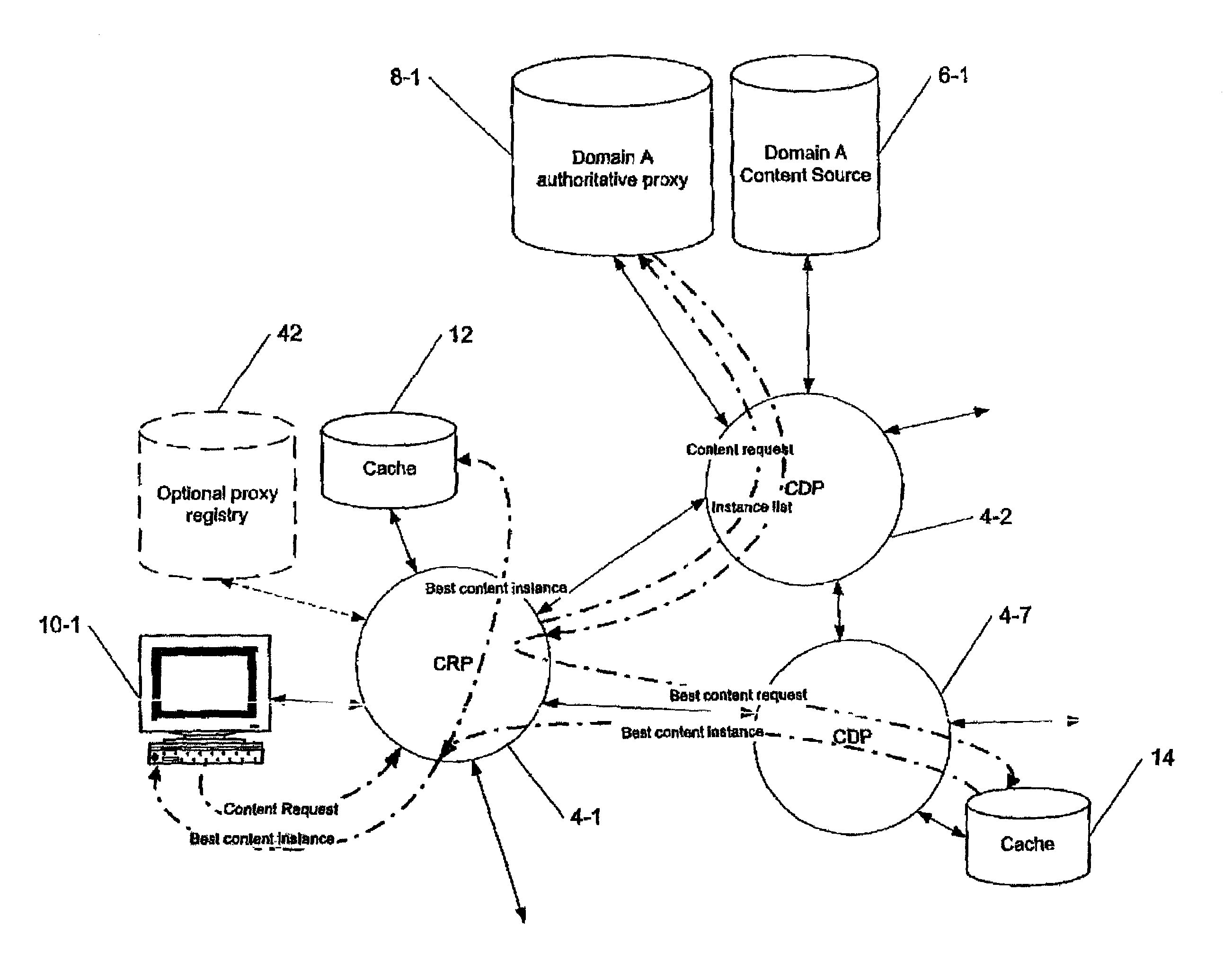
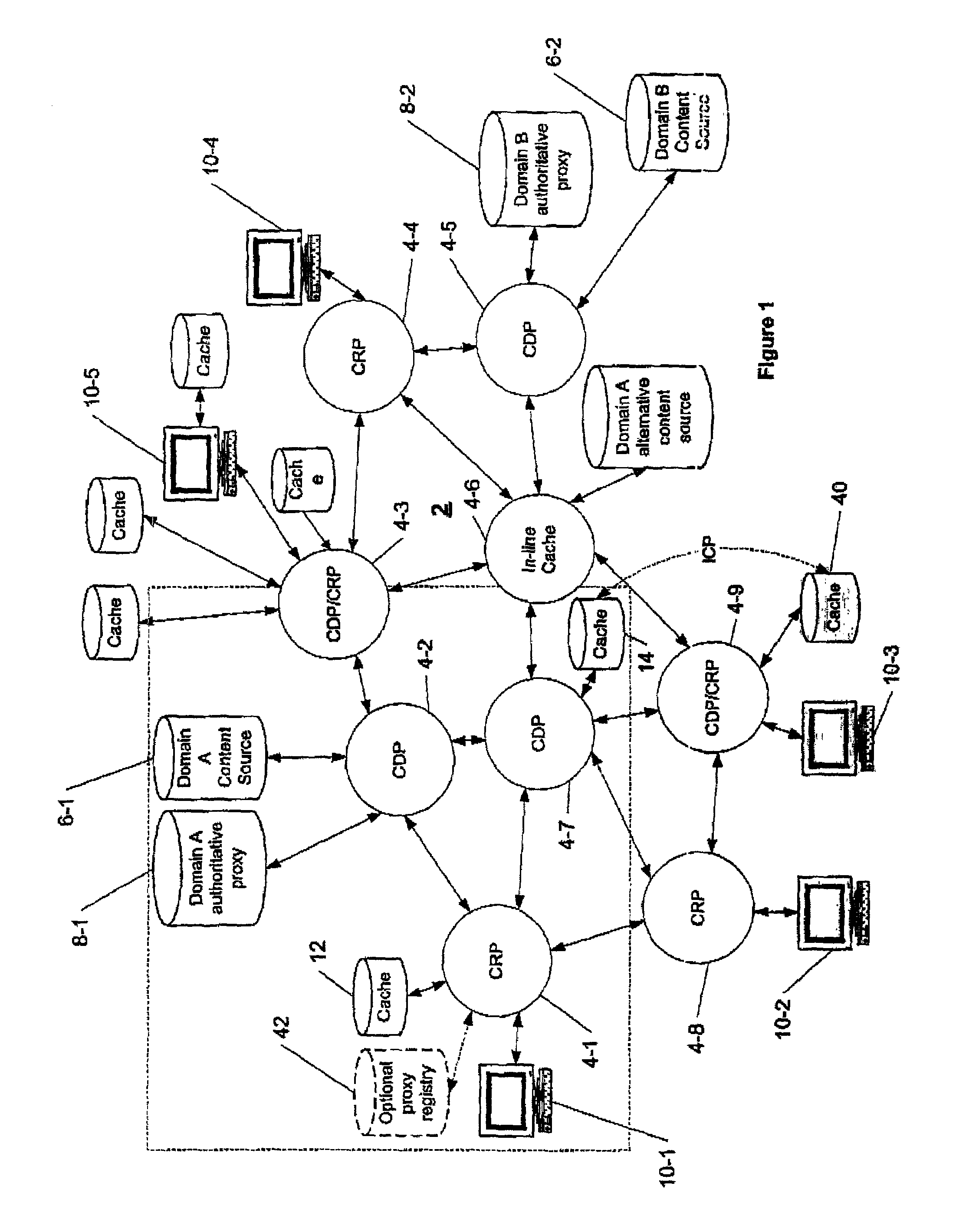
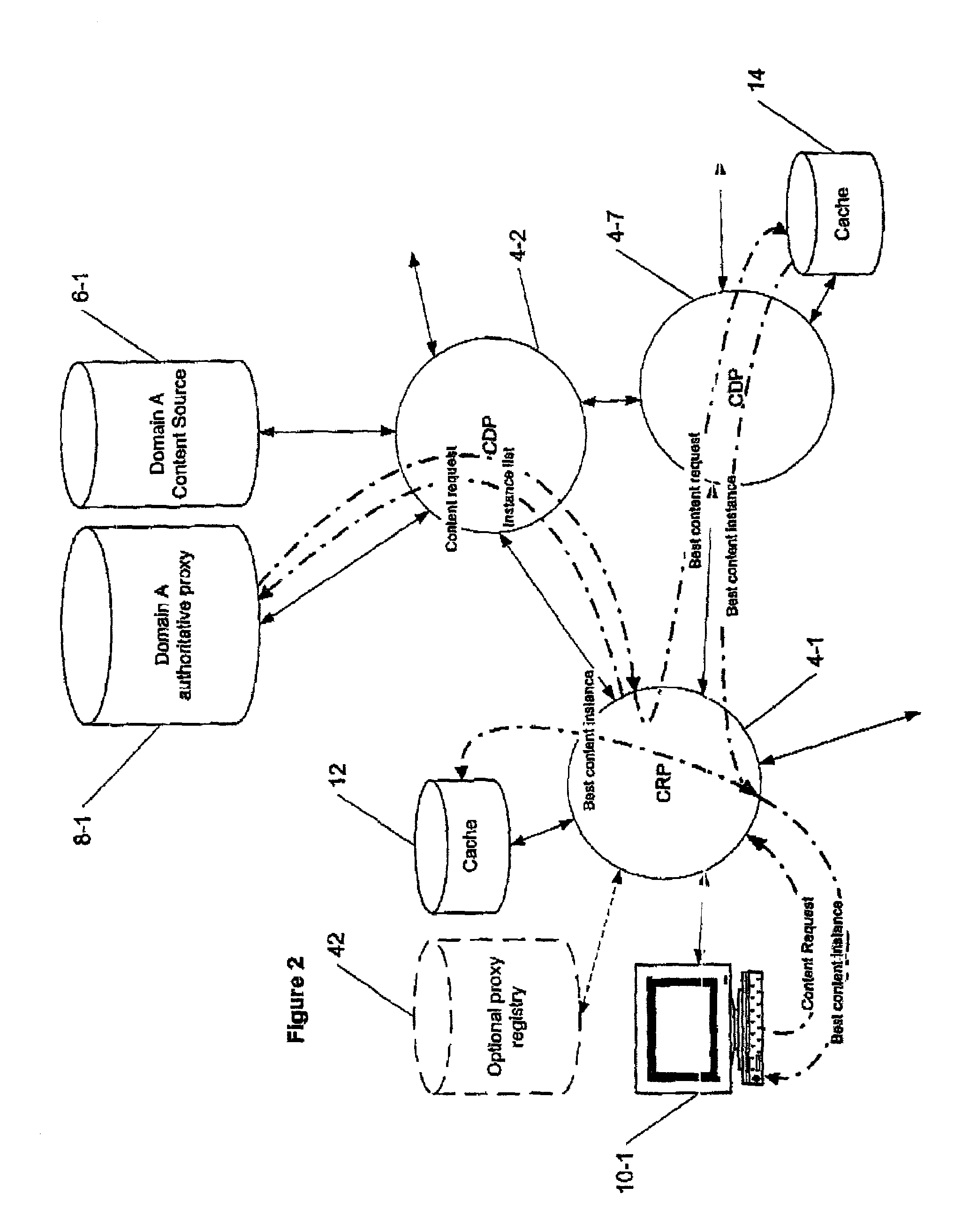
Content is frequently replicated across IP-based networks such as the Internet. Replicas are stored in caches throughout the network. However, to date there has been no mechanism to allow users not directly associated with the replicas to access replicas. Therefore although a copy of a content item may be stored geographically nearby, it may still be necessary to obtain the original content item from a server many thousands of miles away.By recording the location of content items and producing a mapping of a content item to all known replicas, it is possible to produce an authoritative proxy associated with a particular domain which is able to provide a list of URLs of alternative replica copies of a requested content item. In this way, a content request proxy associated with a requester of a content item may choose the best location for retrieving the content item from a list which may include local caches not directly associated with the requester.
Owner:CIENA
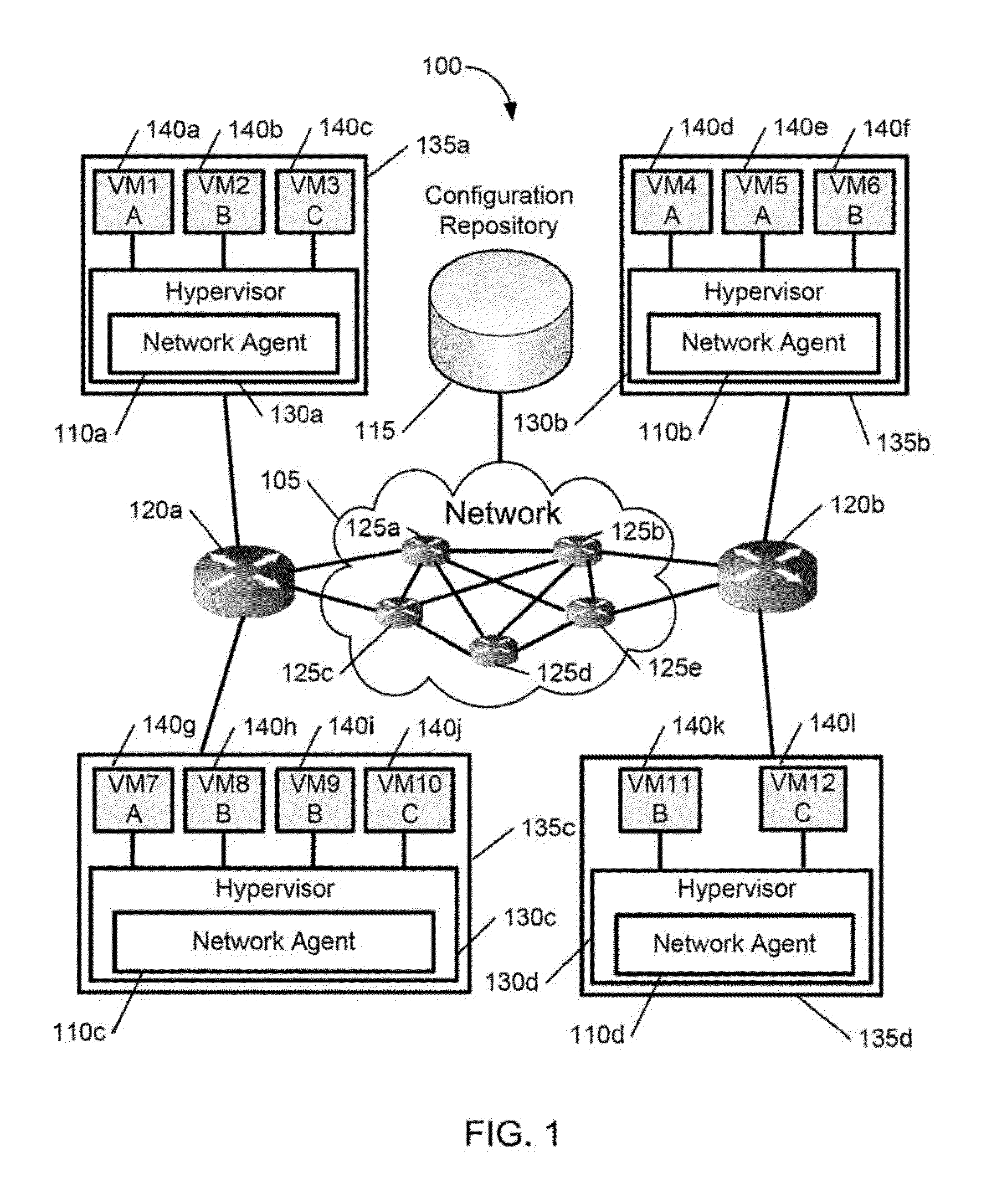
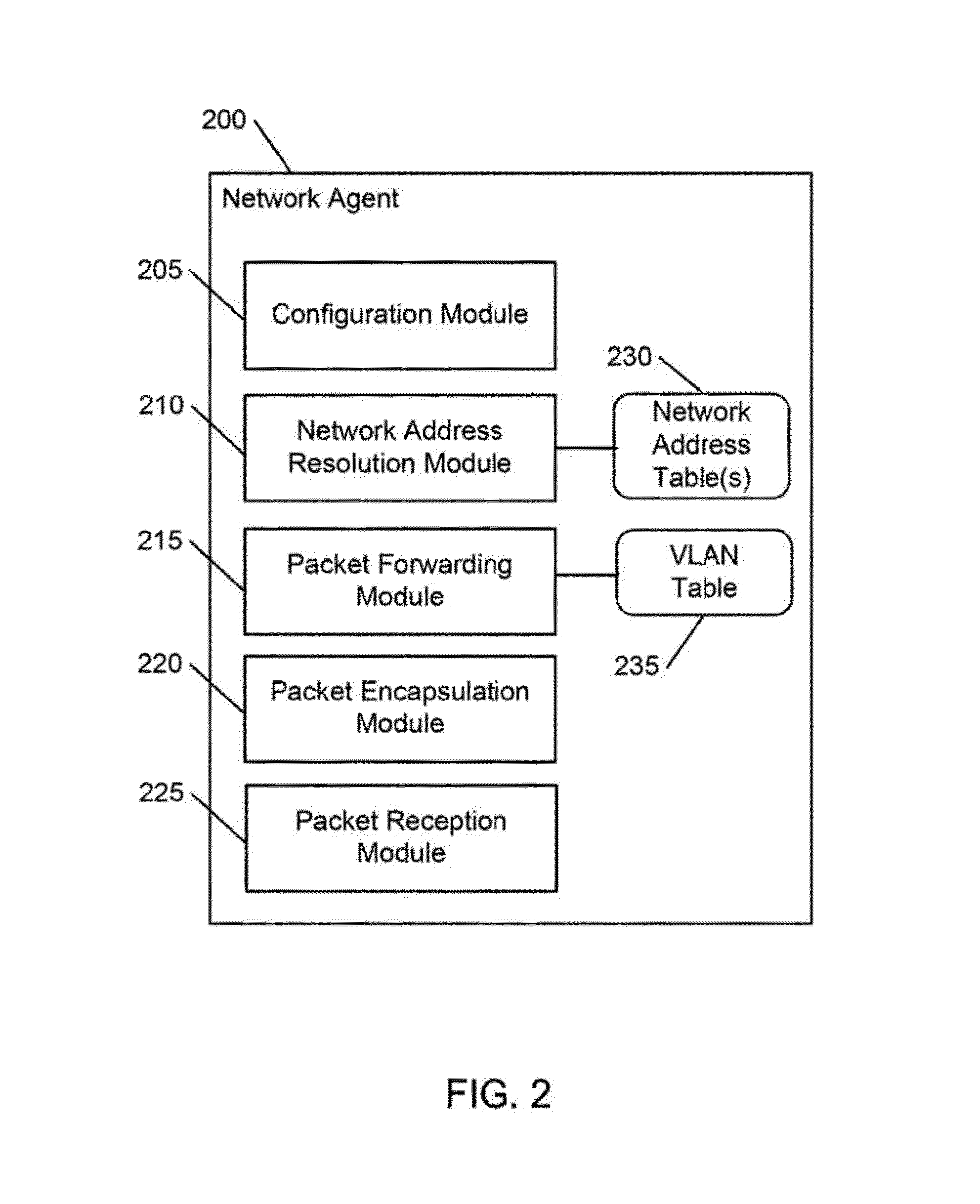
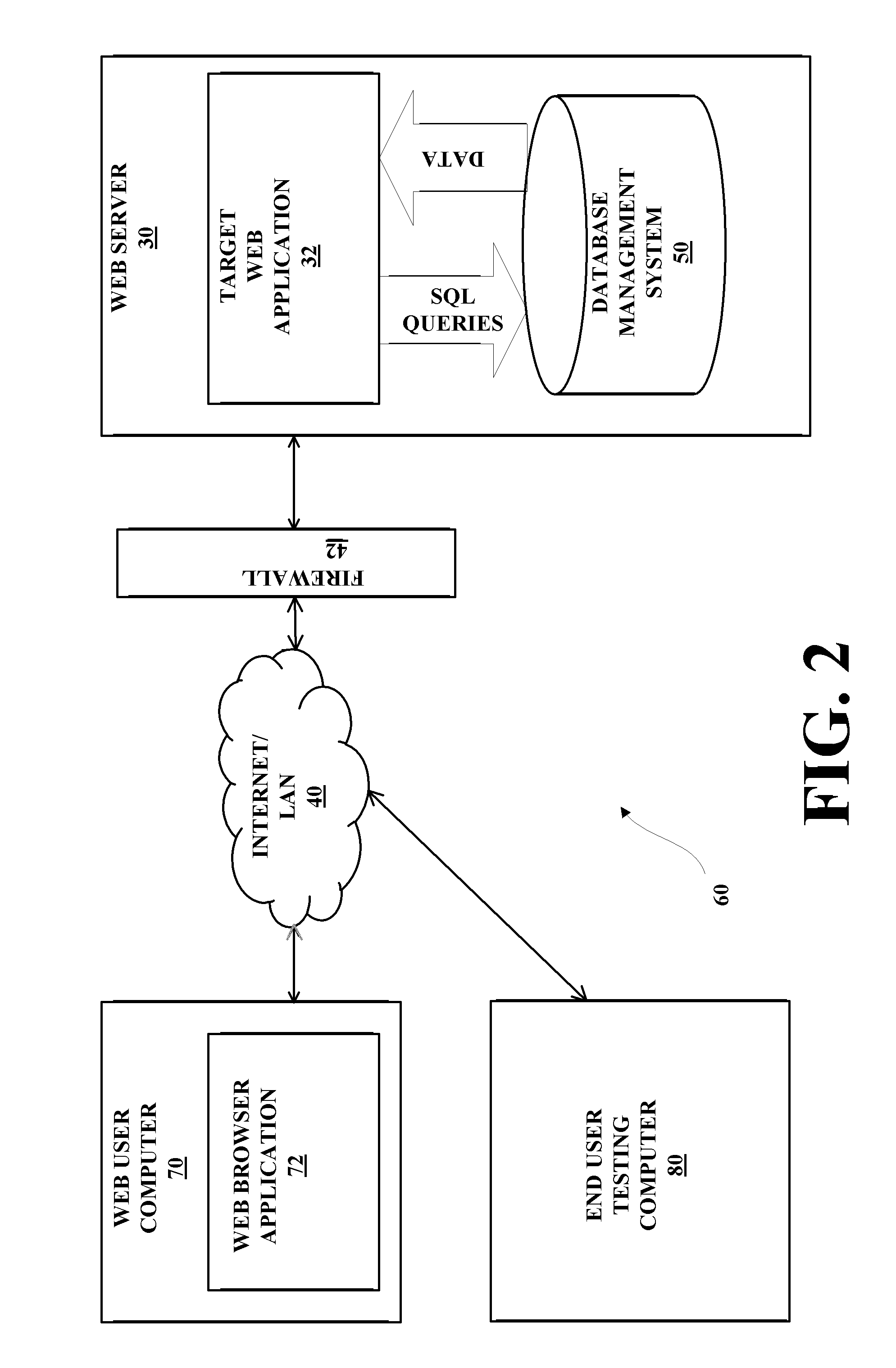
Scalable multi-tenant network architecture for virtualized datacenters
ActiveUS20140115584A1Data switching networksSoftware simulation/interpretation/emulationData packVirtualization
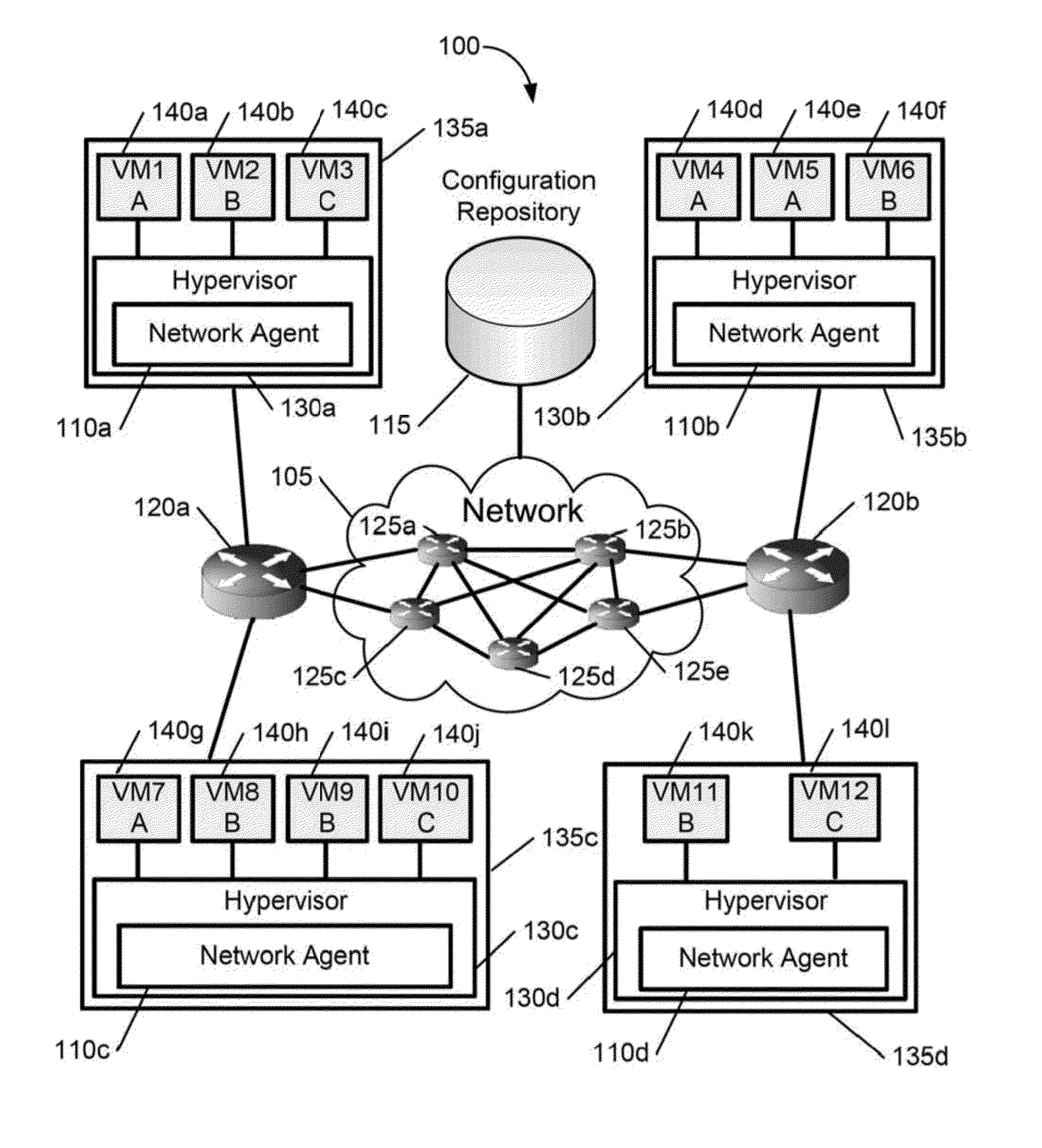
A scalable, multi-tenant network architecture for a virtualized datacenter is provided. The network architecture includes a network having a plurality of servers connected to a plurality of switches. The plurality of servers hosts a plurality of virtual interfaces for a plurality of tenants. A configuration repository is connected to the network and each server in the plurality of servers has a network agent hosted therein. The network agent encapsulates packets for transmission across the network from a source virtual interface to a destination virtual interface in the plurality of virtual interfaces for a tenant in the plurality of tenants. The packets are encapsulated with information identifying and locating the destination virtual interface, and the information is interpreted by switches connected to the source virtual interface and the destination virtual interface.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
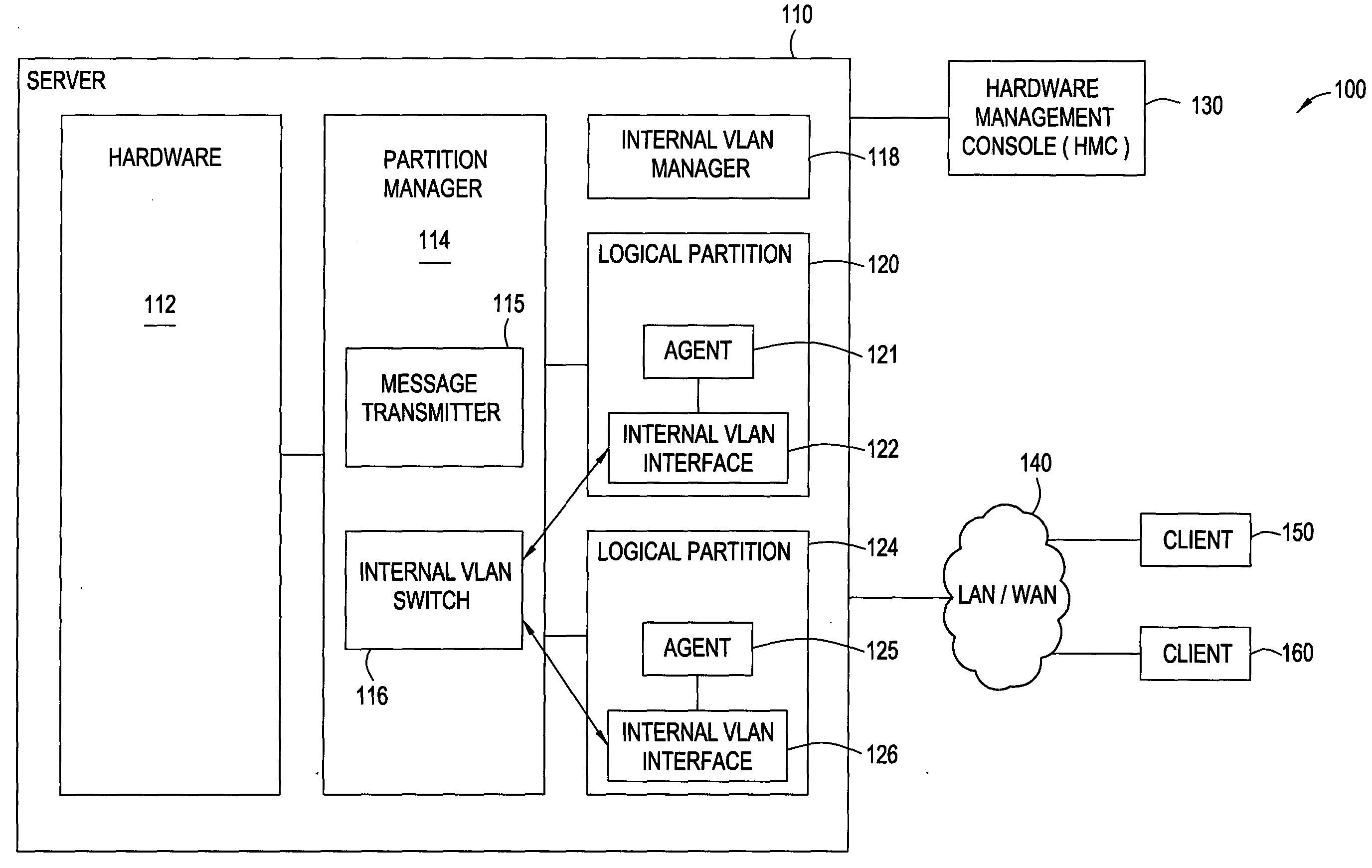
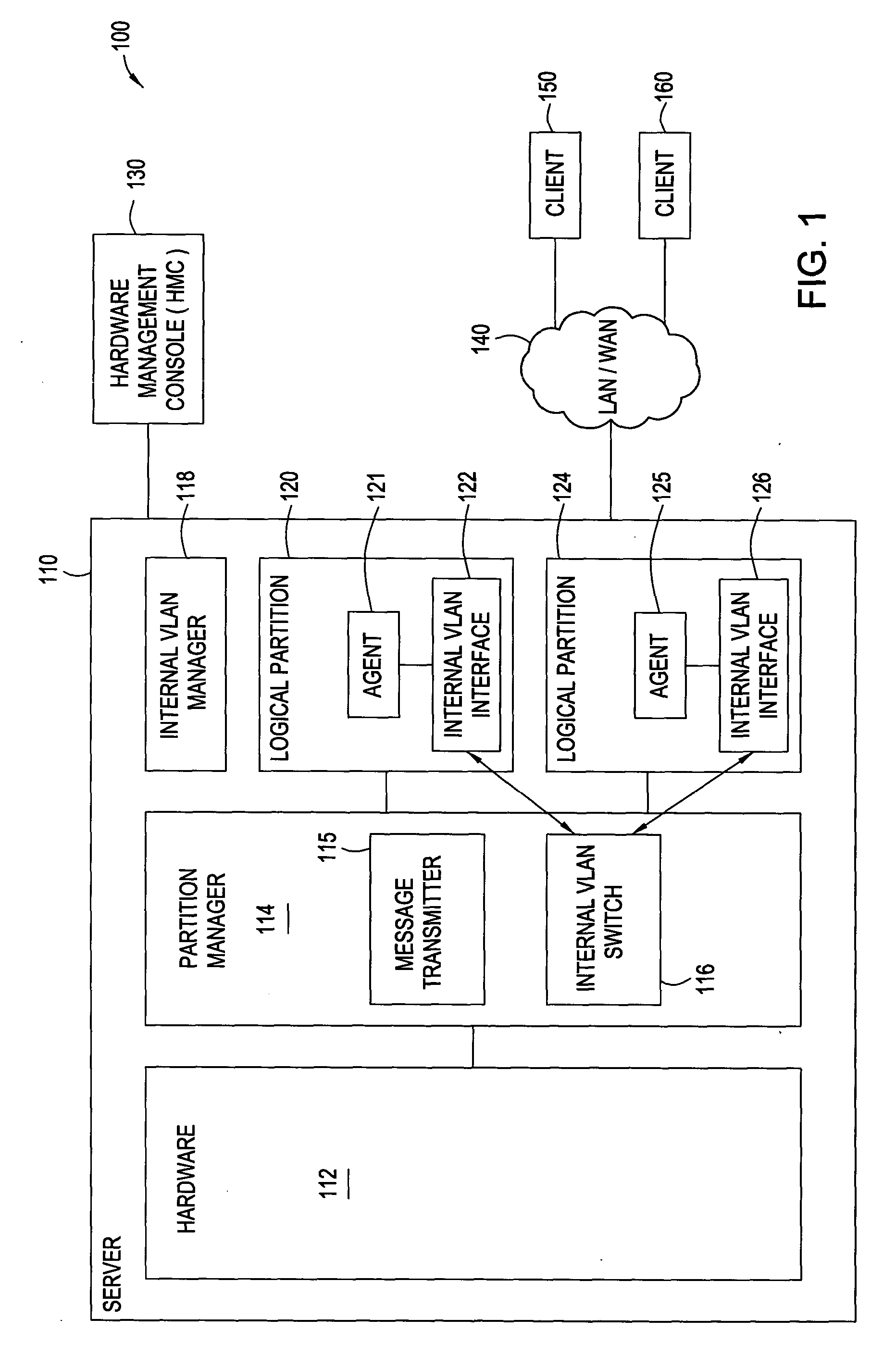
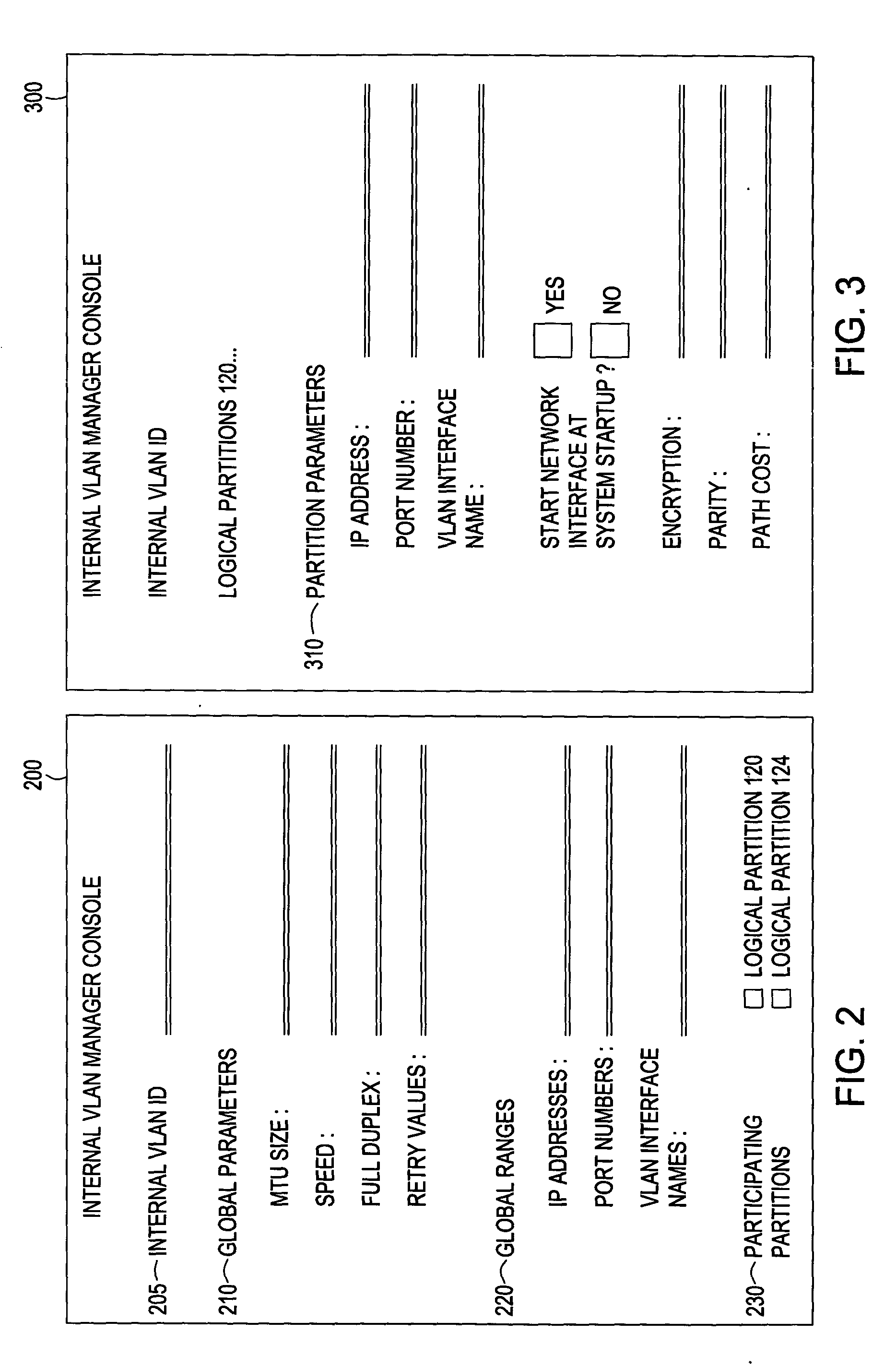
Auto-configuration of an internal vlan network interface
InactiveUS20050071446A1Facilitate communicationUser identity/authority verificationMultiple digital computer combinationsAuto-configurationNetwork agent
Methods and systems for auto-configuration of an internal network interface are disclosed. Embodiments may install an internal VLAN manager in a logically partitioned computer system along with network agents in each of the partitions in the logically partitioned system to facilitate configuring an internal communications network and the corresponding internal network interfaces in each participating partition. In particular, an administrator accesses internal VLAN manager, selects an internal VLAN ID, selects each of the participating partitions, and configures the communications network with global parameters and ranges. The internal VLAN manager then generates partition parameters and incorporates them into messages for each of the partitions selected to participate in the internal network. Each of the participating partitions receives one of the messages and, in response, invokes the corresponding network agent that extracts partition parameters from the message and creates or re-configures an internal network interface based upon the parameters.
Owner:IBM CORP
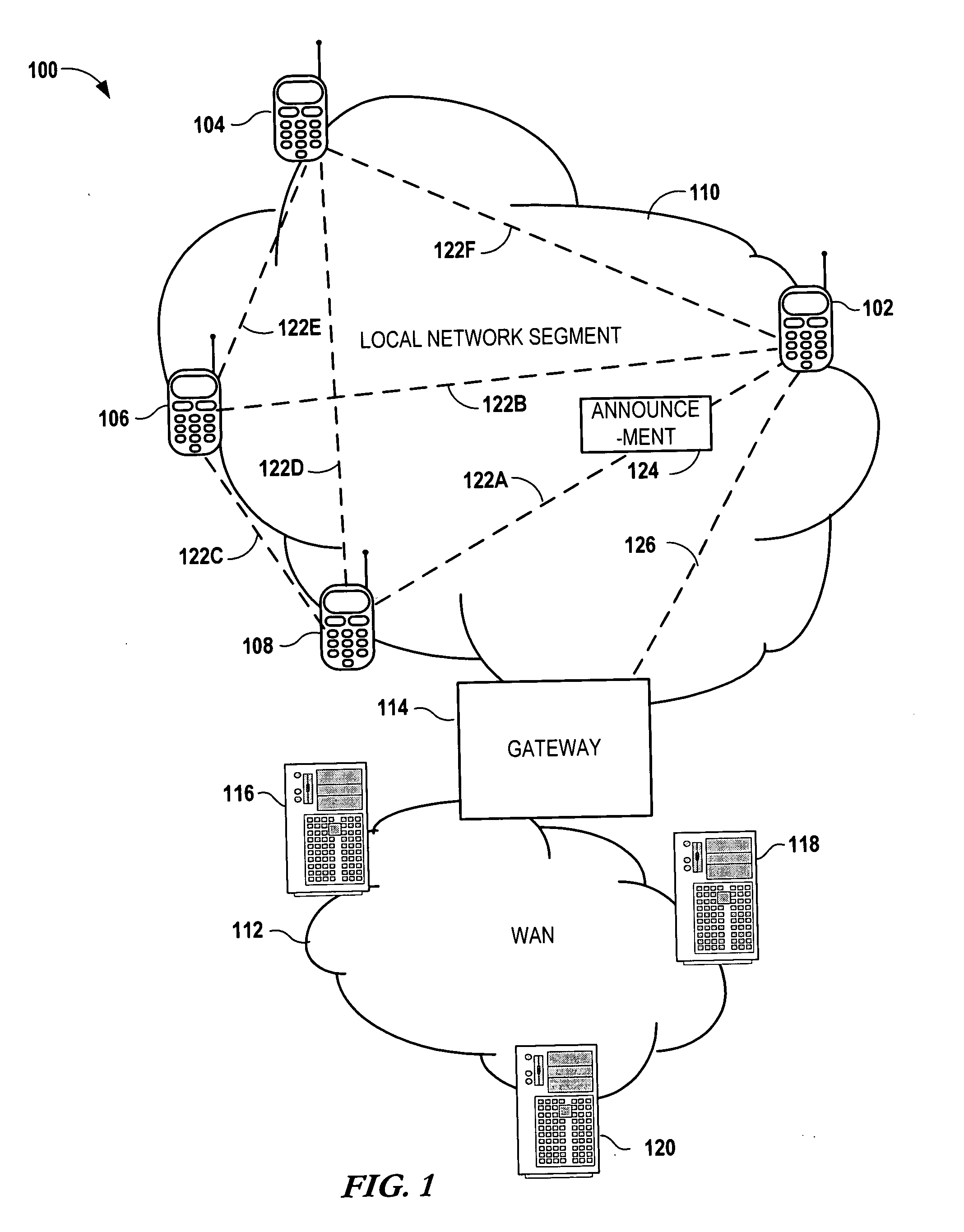
Local discovery of mobile network services
InactiveUS20070286100A1Special service provision for substationMultiplex system selection arrangementsNetwork agentService information
Local discovery of mobile network services involves coupling a communications device to a local network segment of a mobile data network. An announcement is sent from the communication device and / or a network entity (such as a network proxy) describing a service available via the respective devices. The announcement is receivable by any device on the local network segment. A request is received at the device for a detailed description of the service information in response to the announcement. A description of the service is sent from the communications device to the originator of the request in response to the request, and the service is established between the originator and the communication device and / or network entity in response to the sending of the description of the service
Owner:NOKIA CORP
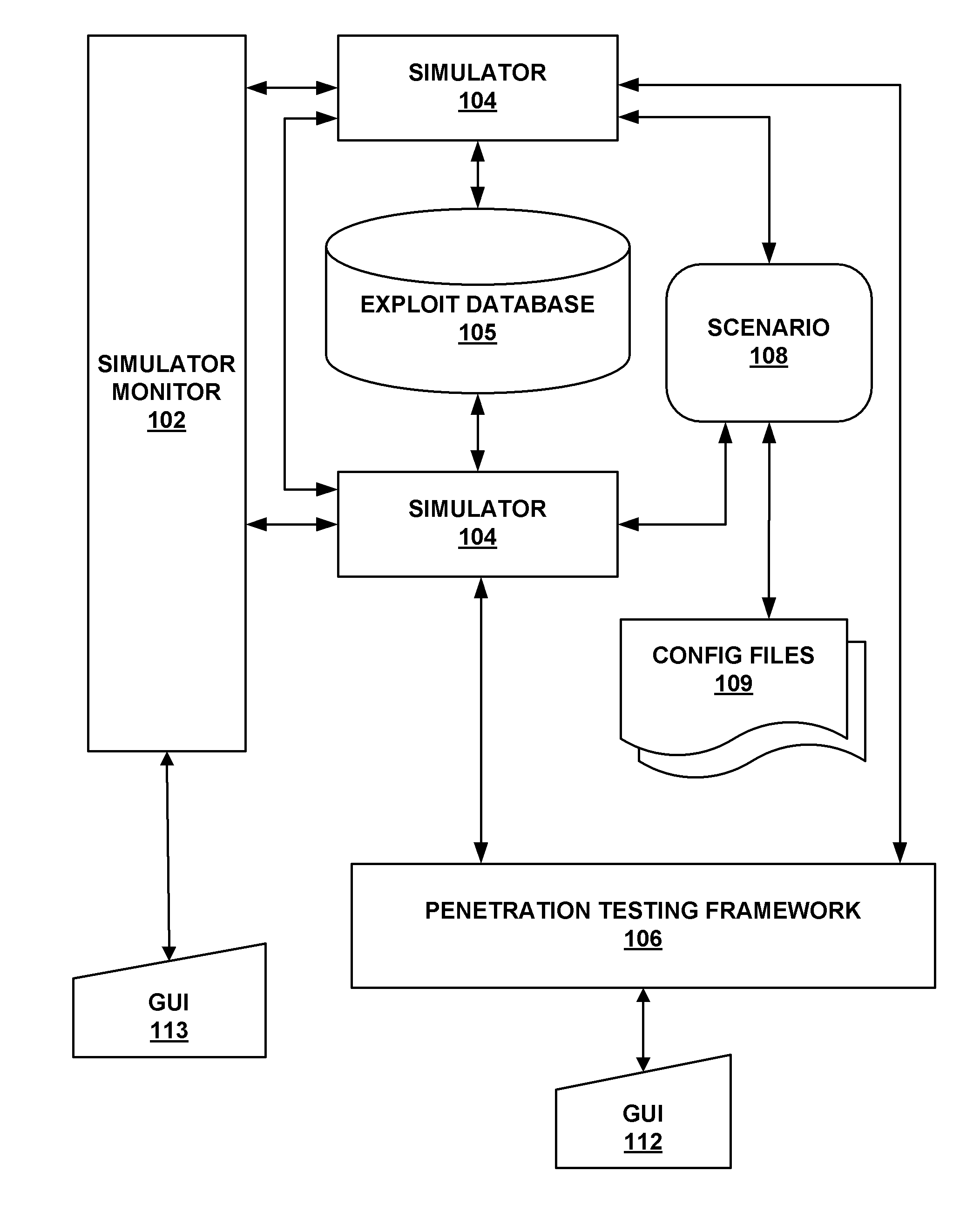
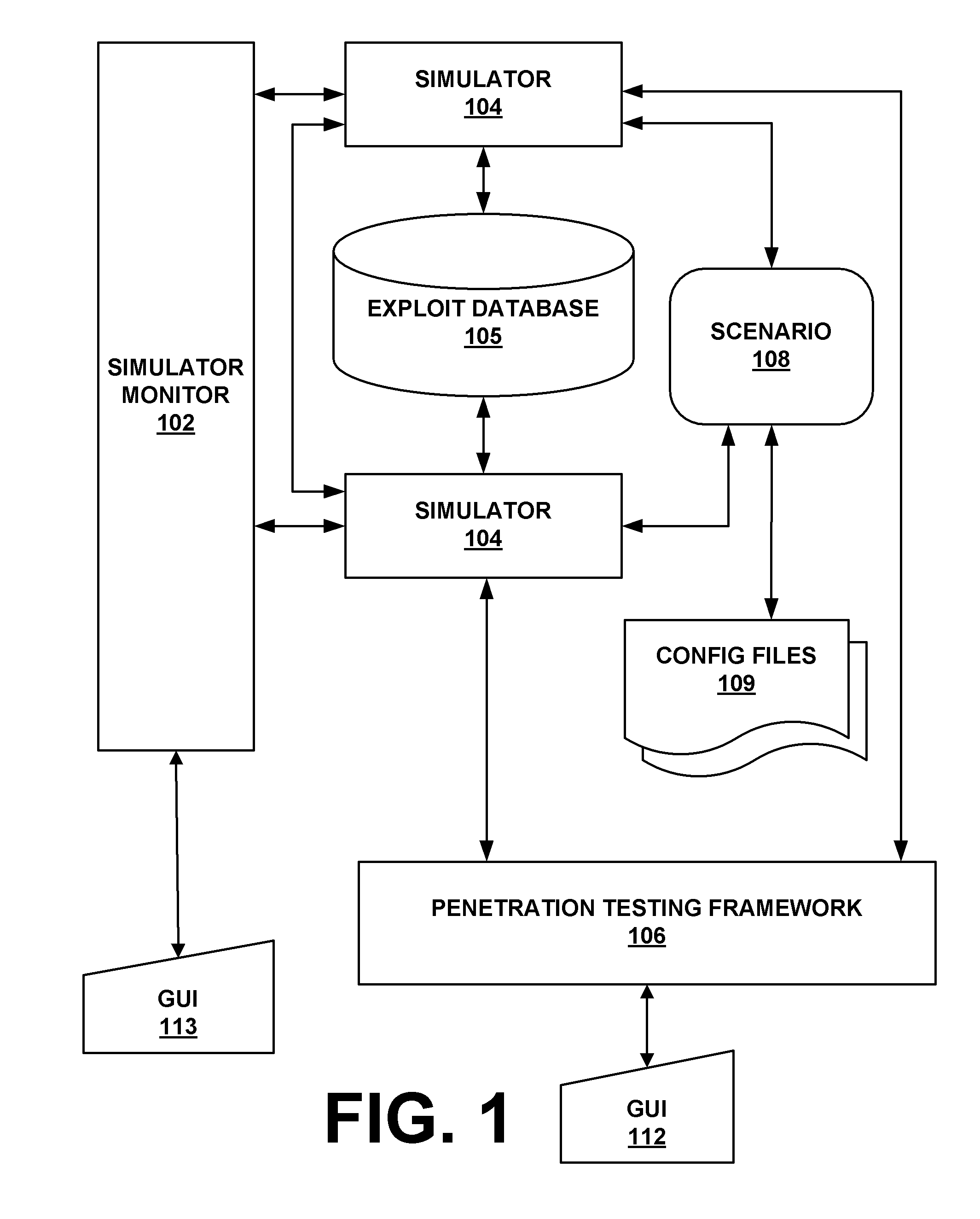
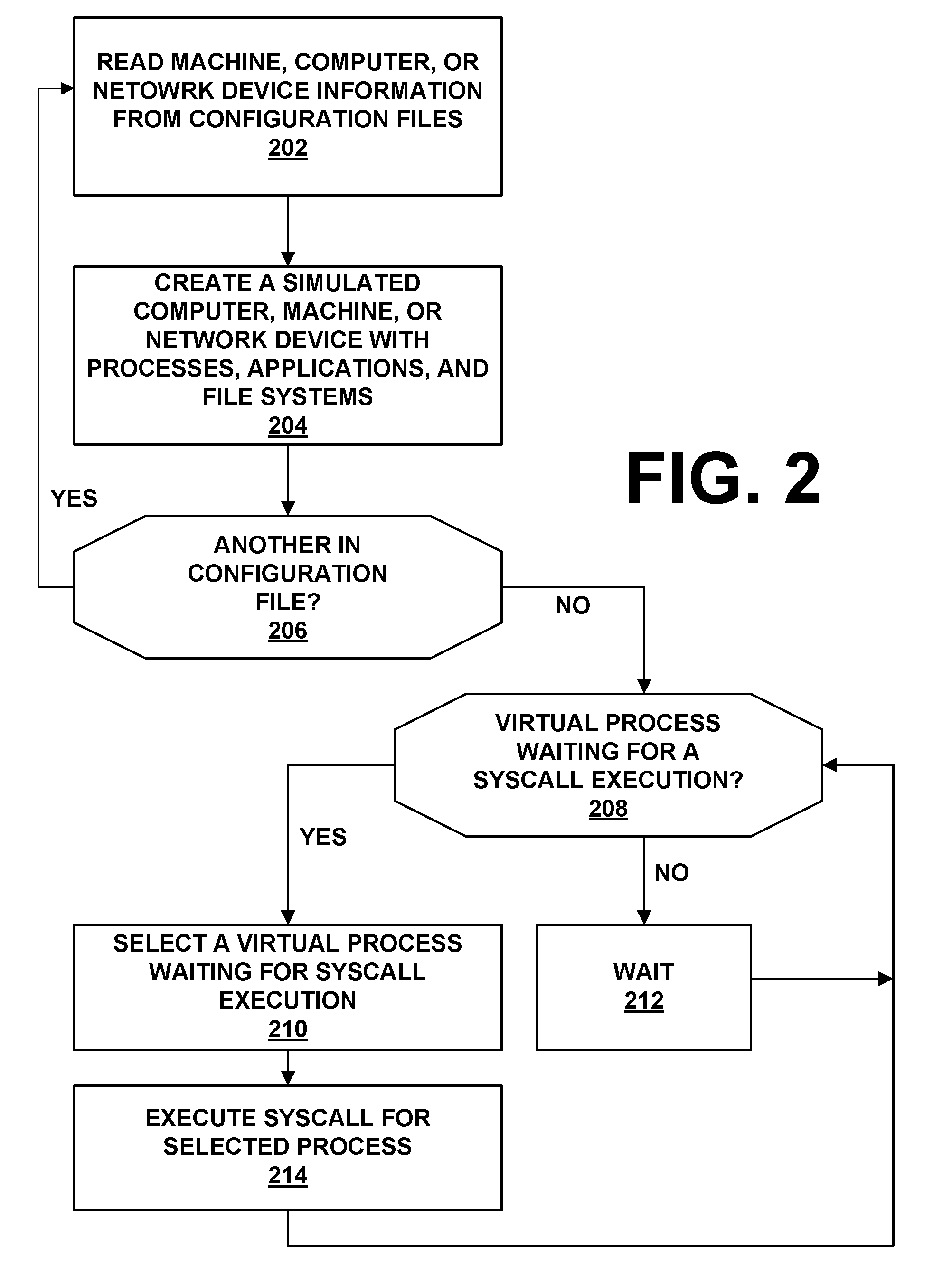
System and method for simulating computer network attacks
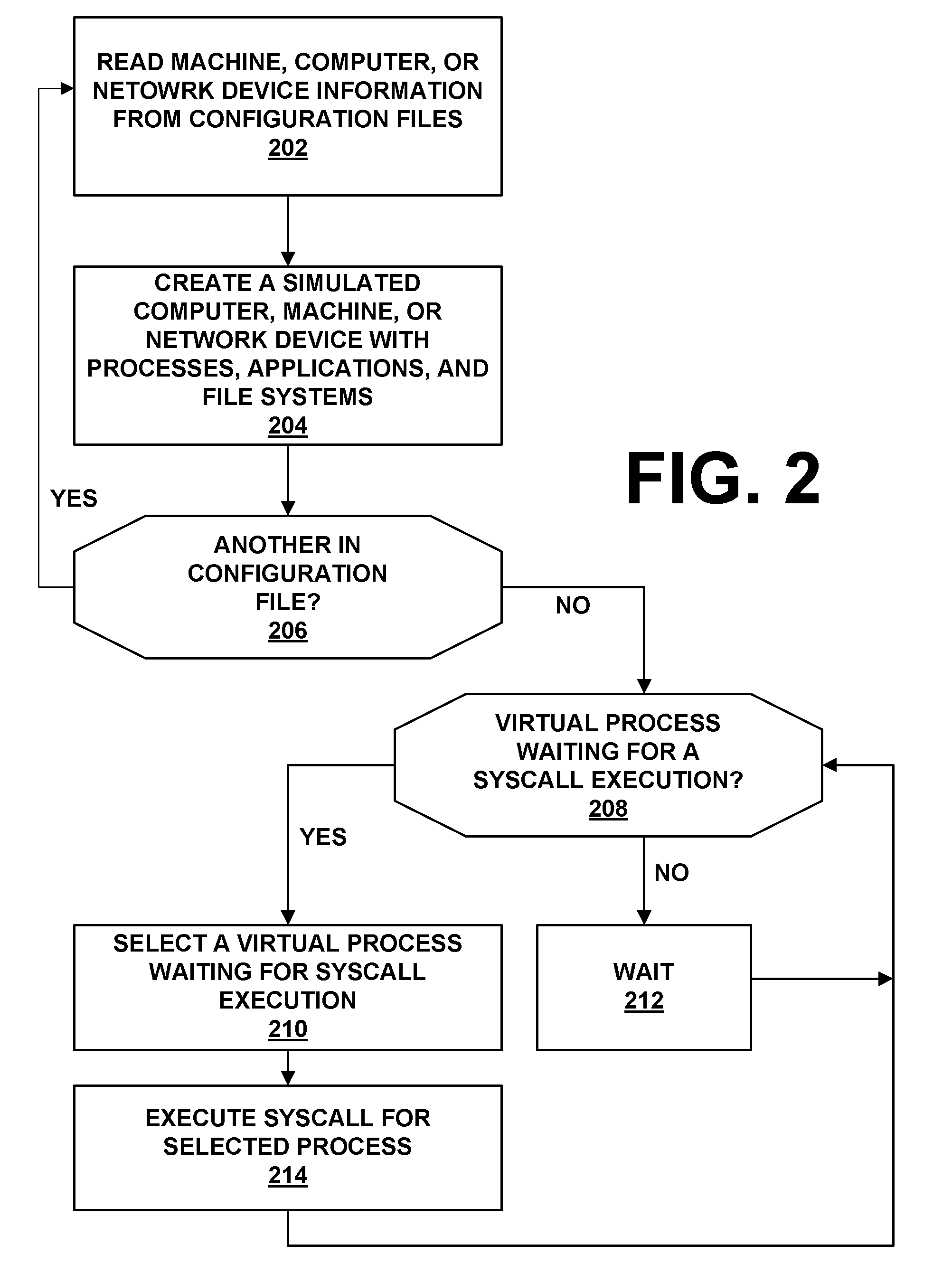
ActiveUS20090007270A1Memory loss protectionError detection/correctionOperational systemNetwork agent
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
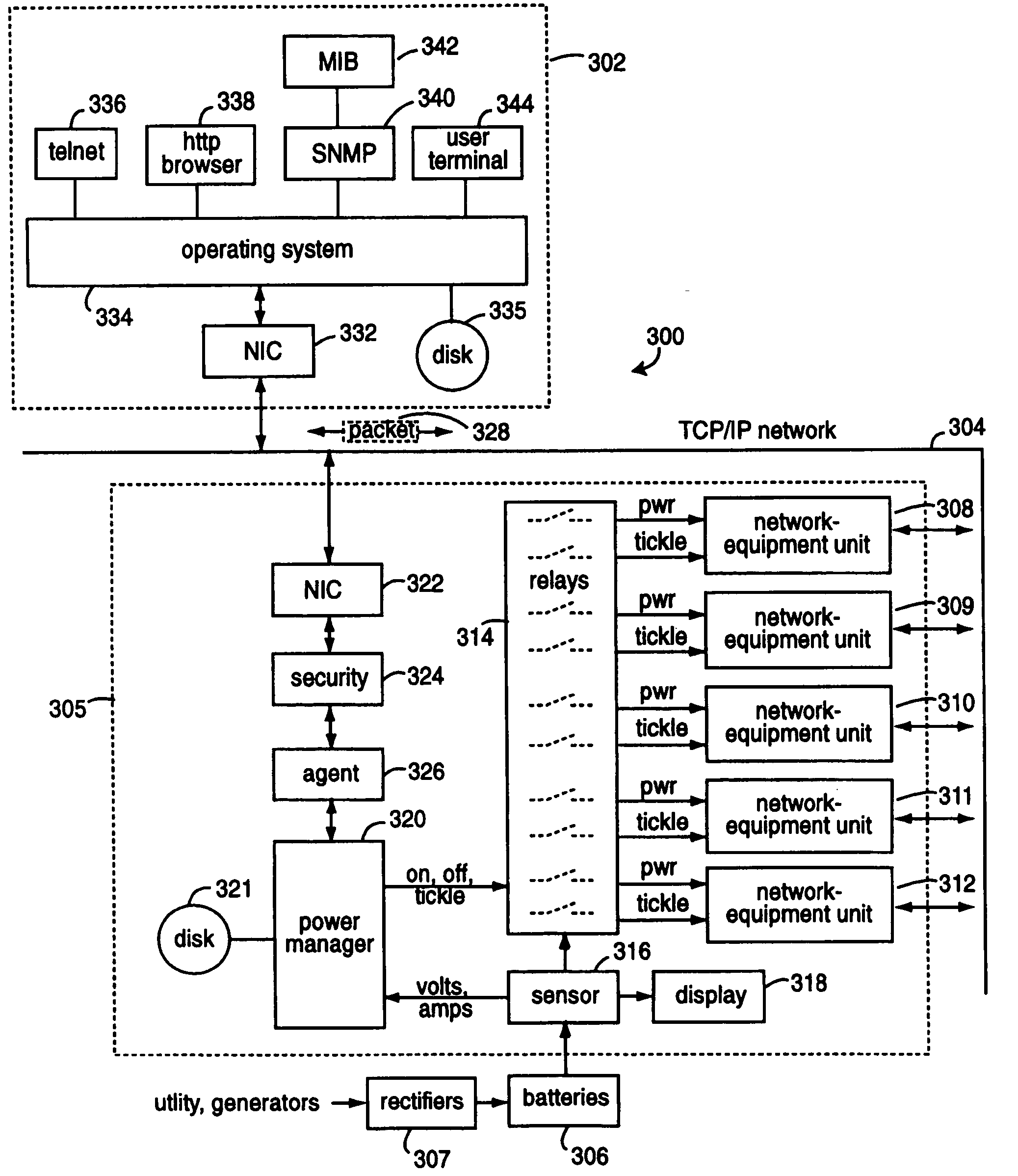
Network-connected power manager for rebooting remote computer-based appliances
InactiveUS20060031454A1Network errorReduce needCoupling device connectionsBatteries circuit arrangementsNetwork agentNetwork connection
A network comprises a power manager with a network agent in communication over a network with an network manager. The power manager is connected to control several intelligent power modules each able to independently control the power on / off status of several network appliances. Power-on and load sensors within each intelligent power module are able to report the power status of each network appliance to the network manager with variables in response to commands. Each intelligent power module is equipped with an output that is connected to cause an interrupt signal to the network appliance being controlled. The network manager is able to test which network appliance is actually responding before any cycling of the power to the corresponding appliance is tried.
Owner:SERVER TECHNOLOGY
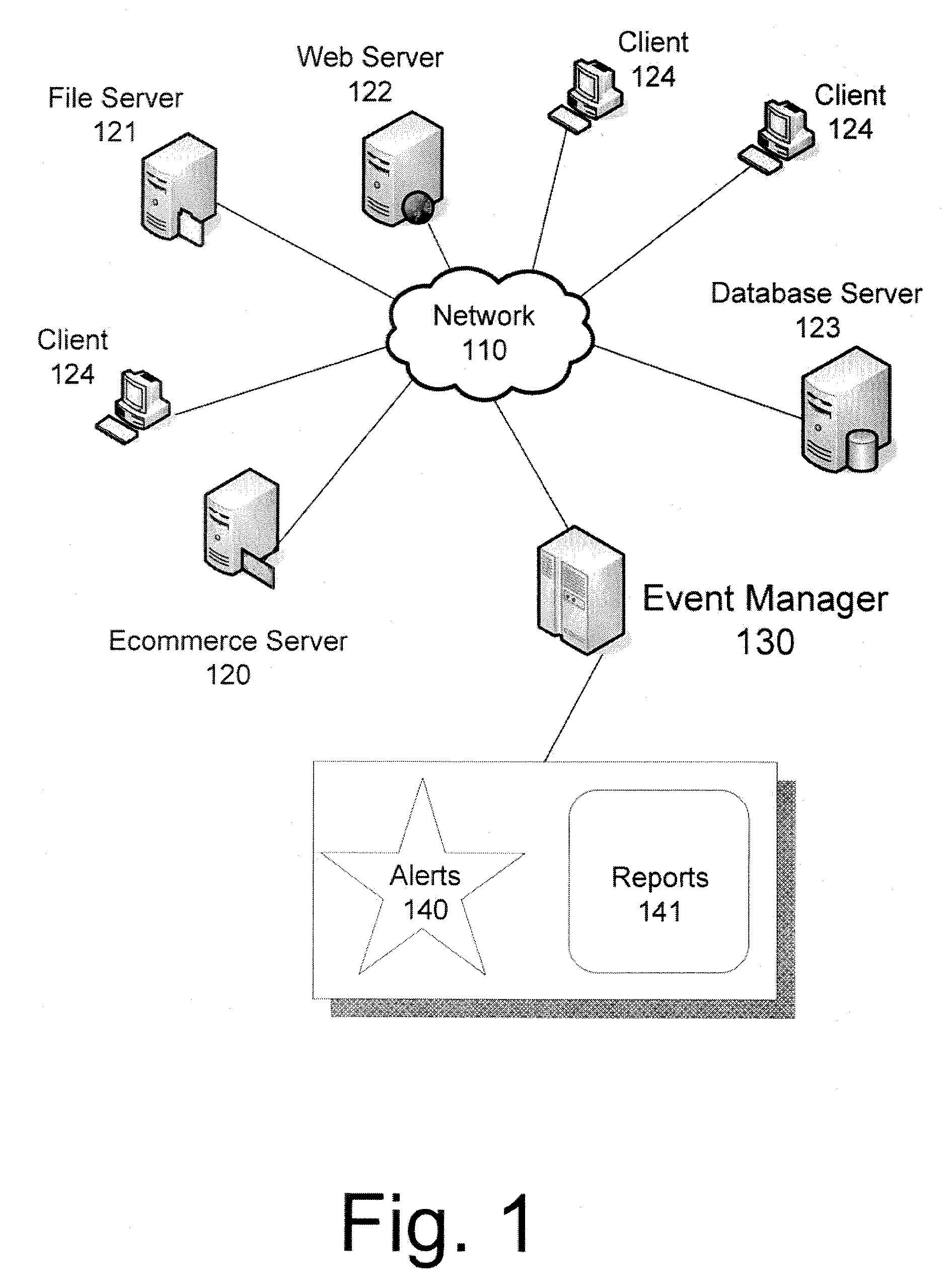
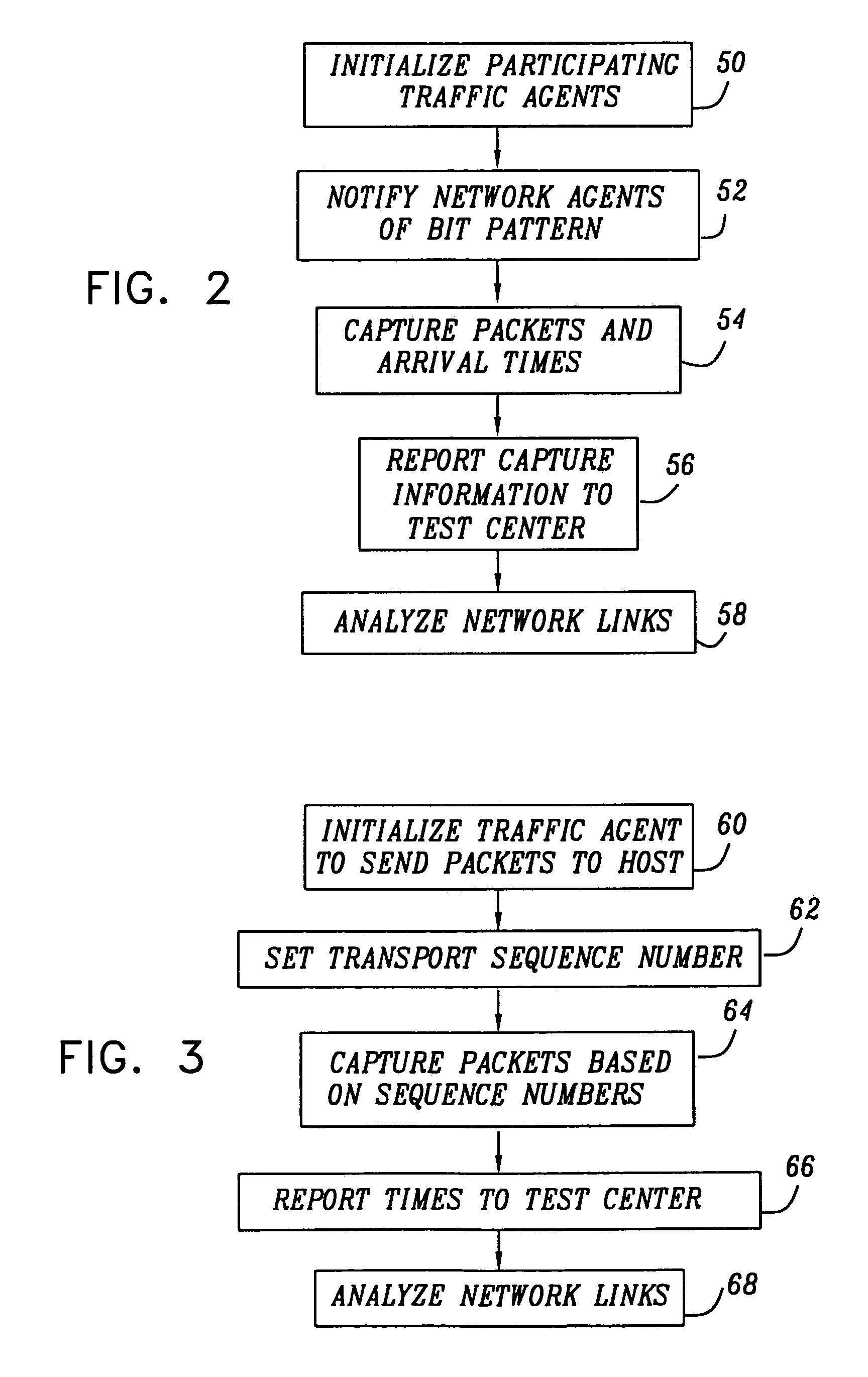
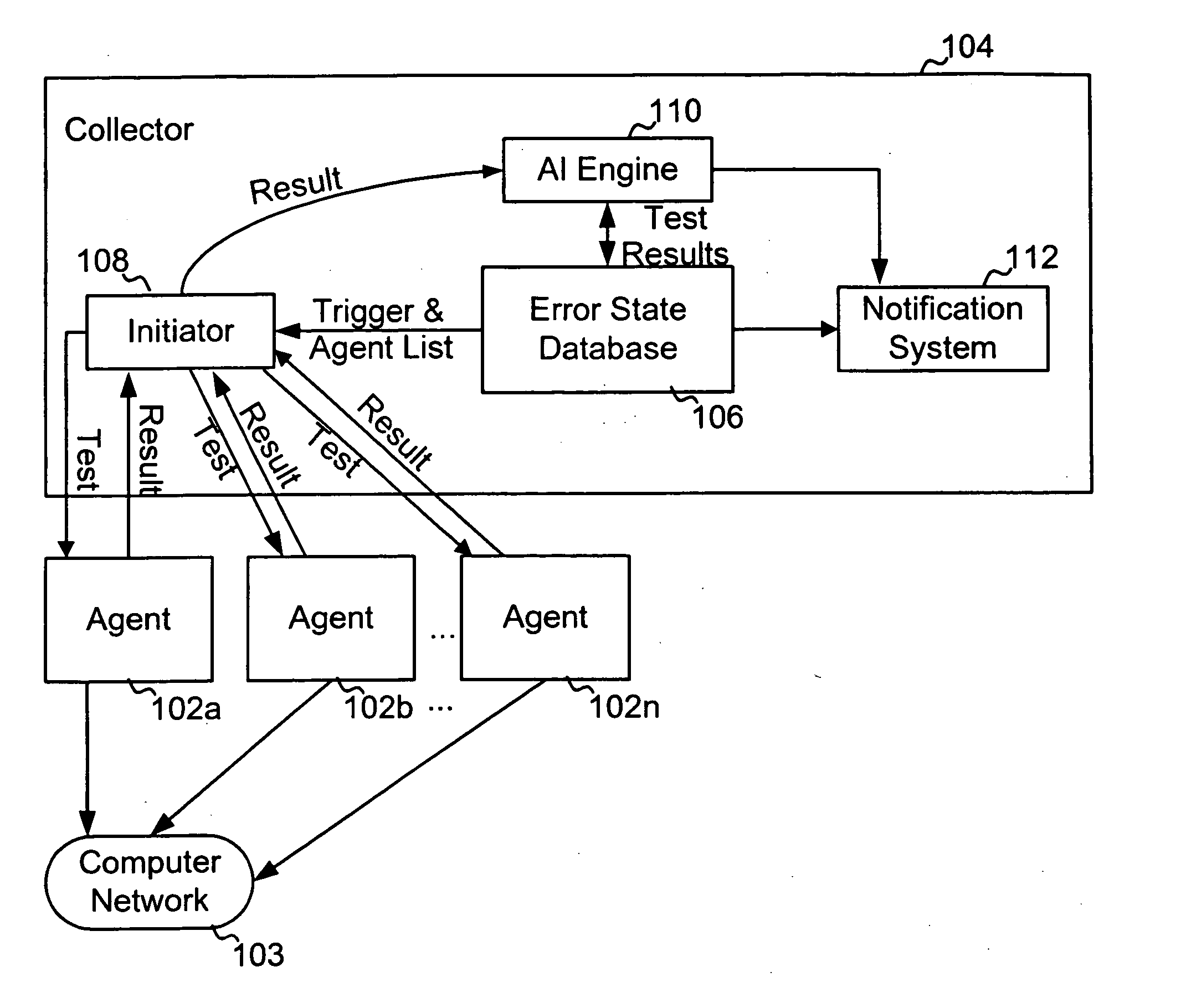
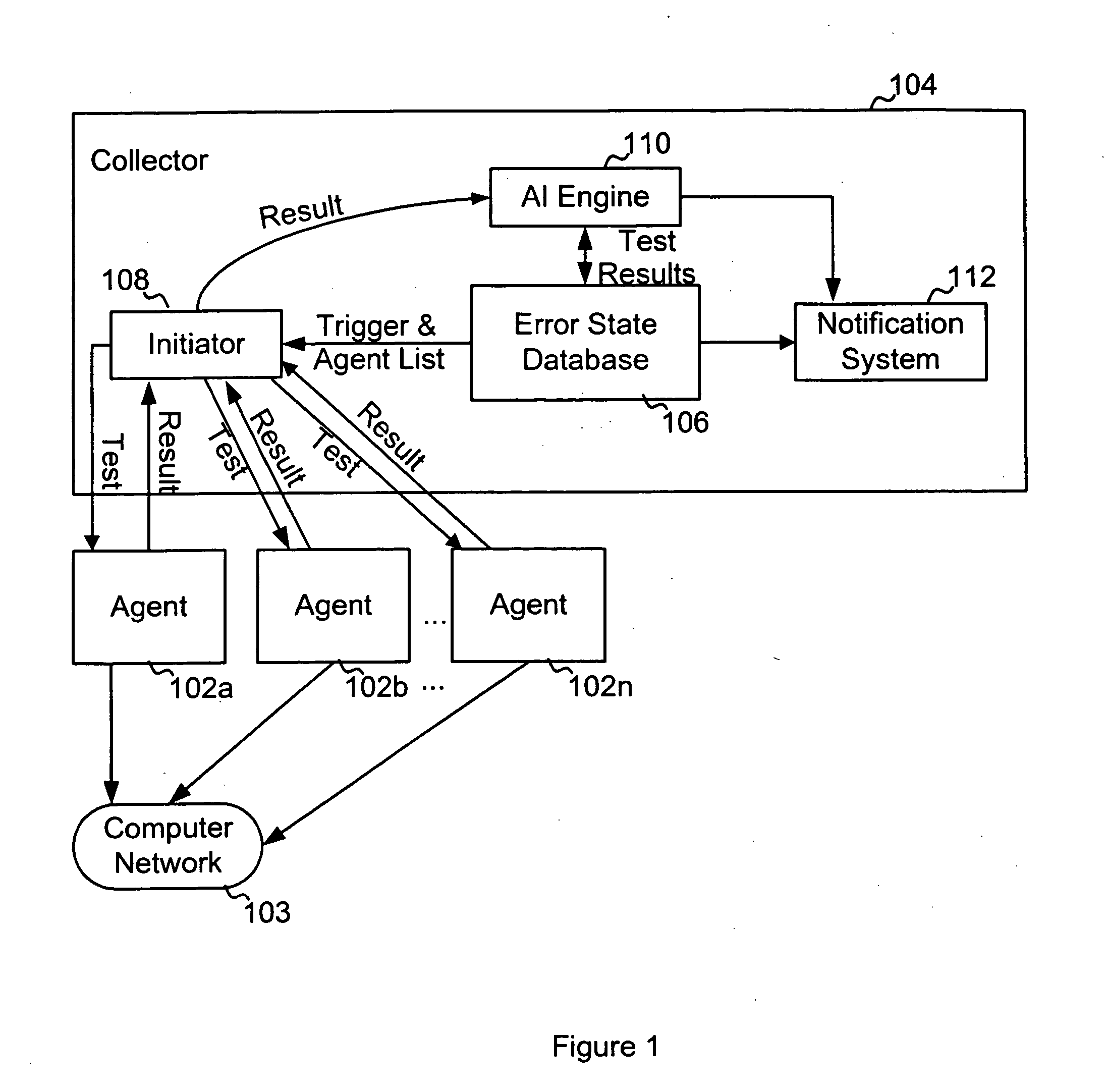
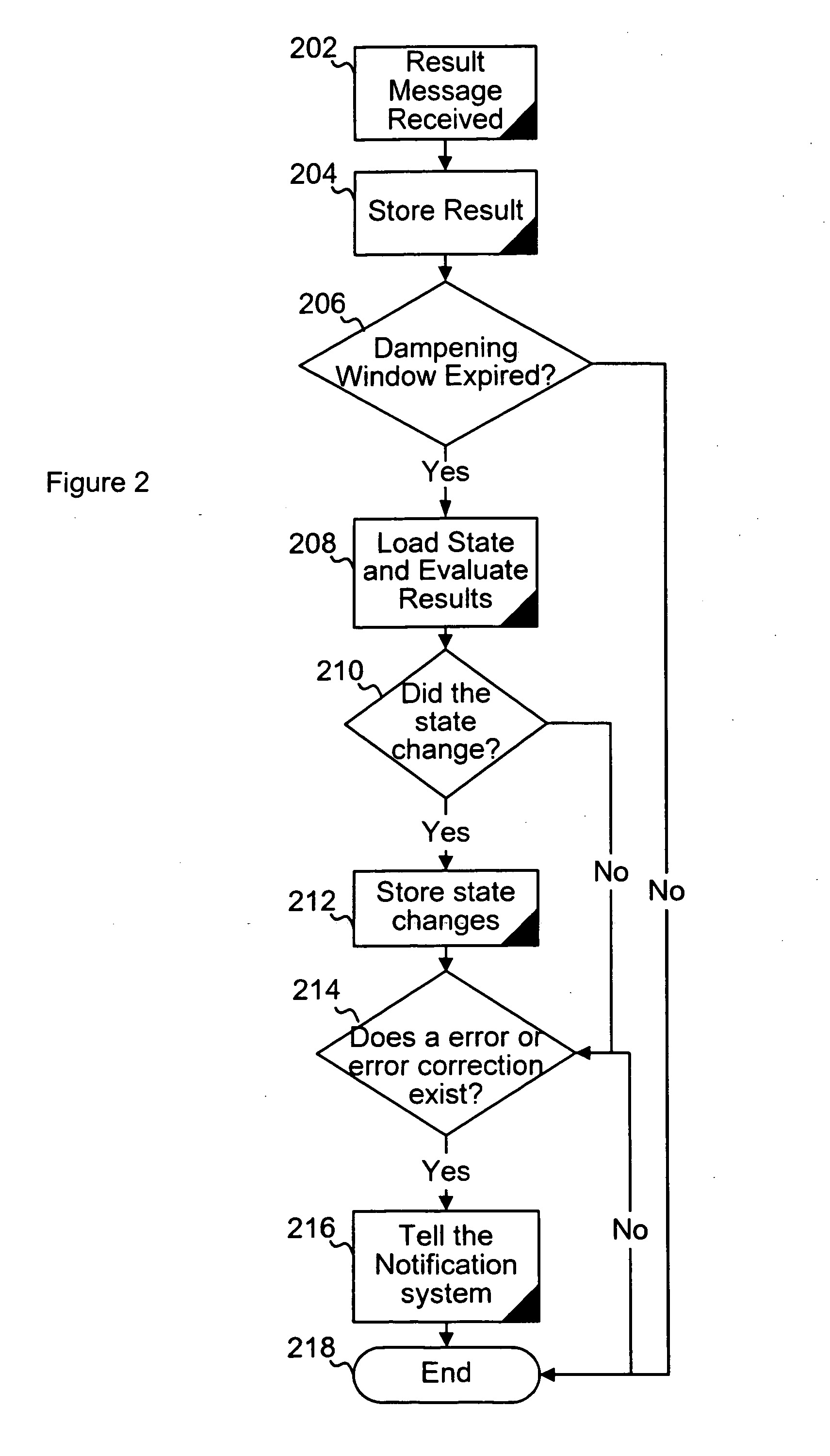
System and method for monitoring state information in a network
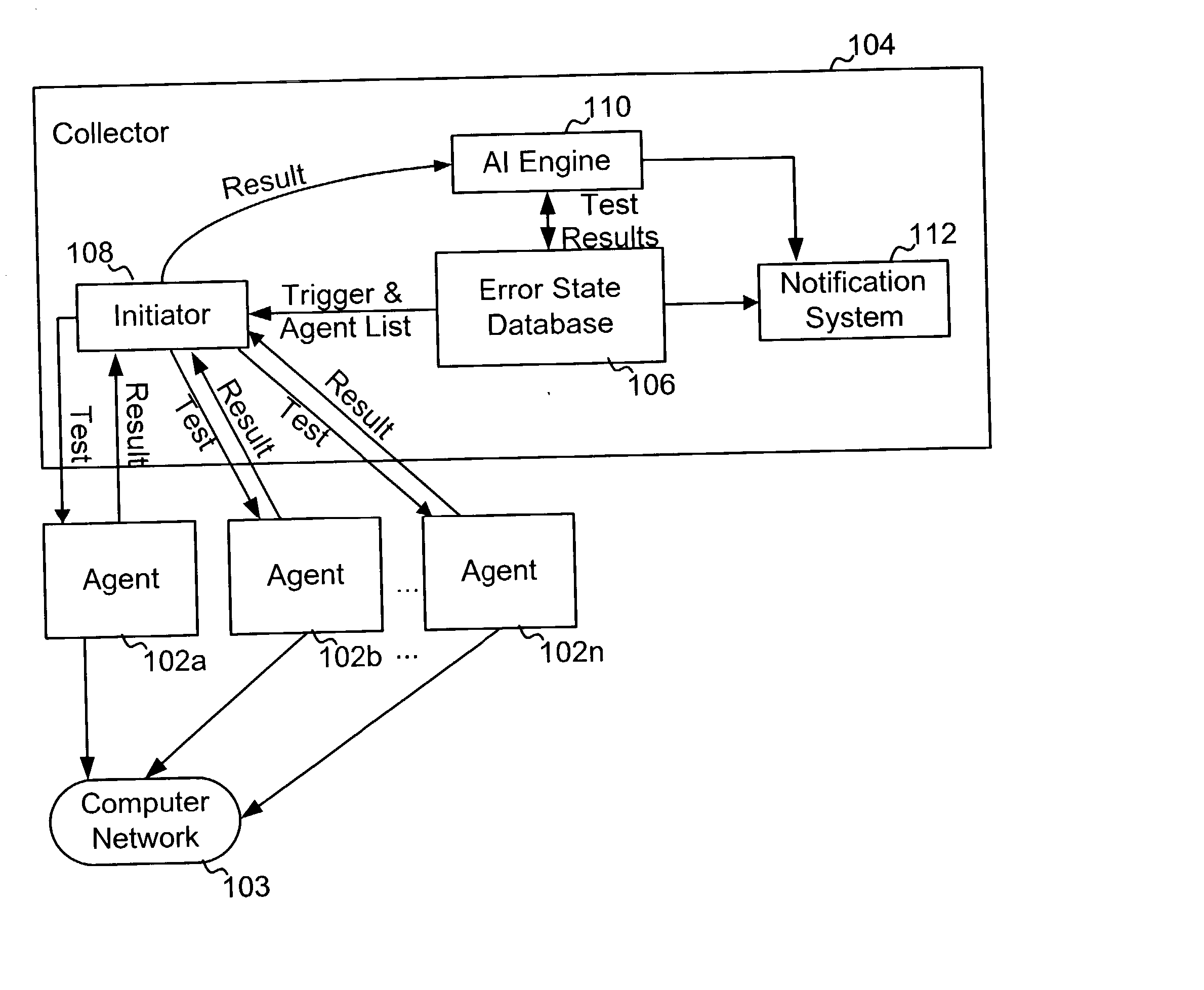
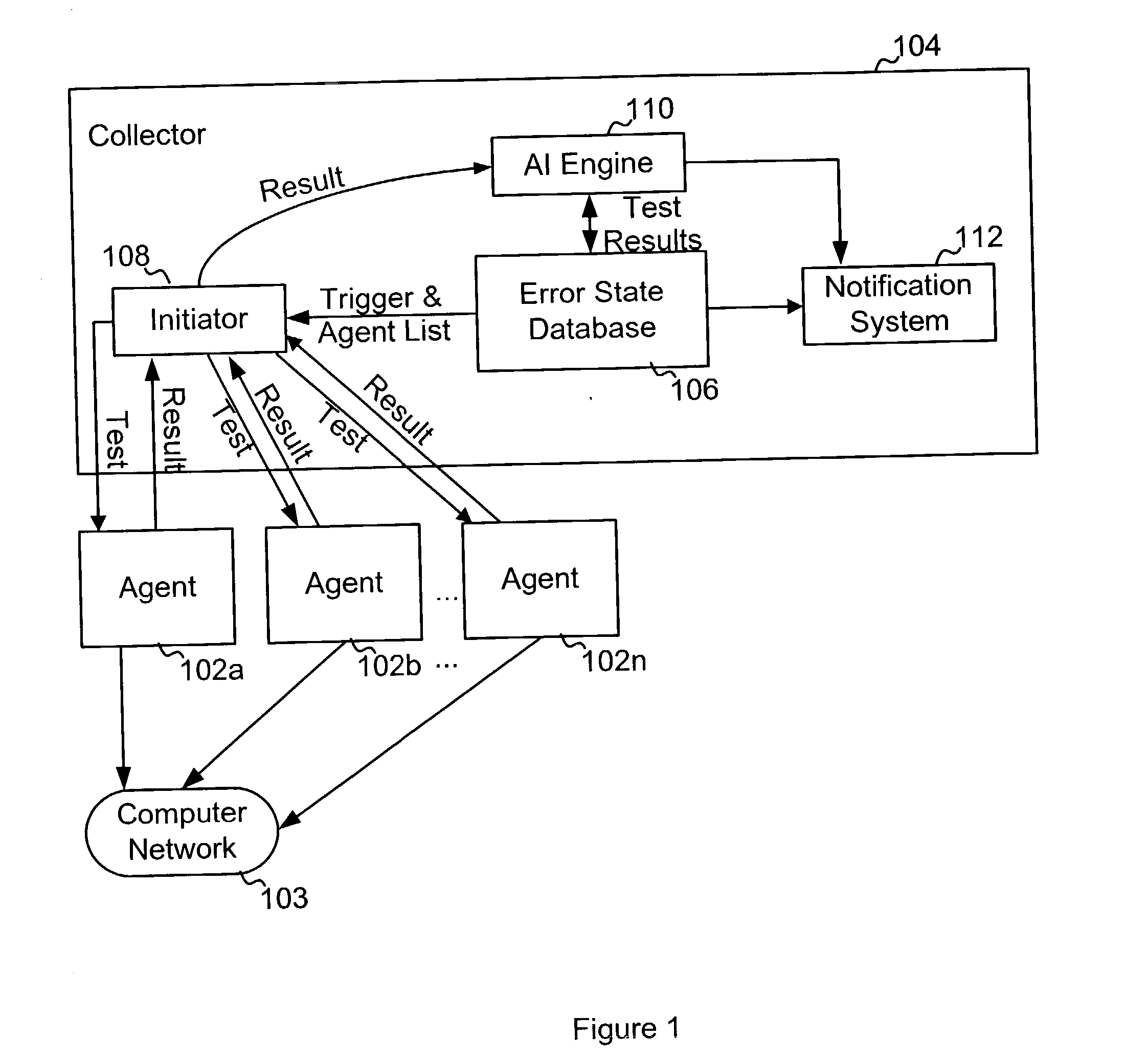
Agents are instructed execute network tests during monitoring intervals. Results of the tests are stored. After expiration of a dampening window period the results are retrieved and evaluated. The evaluation is used to update an error state stored in a data structure in a database as required. Notification of detected errors is provided if certain notification dampening criteria are satisfied.
Owner:CATBIRD NETWORKS
System and method for generating unsupported network information indicators
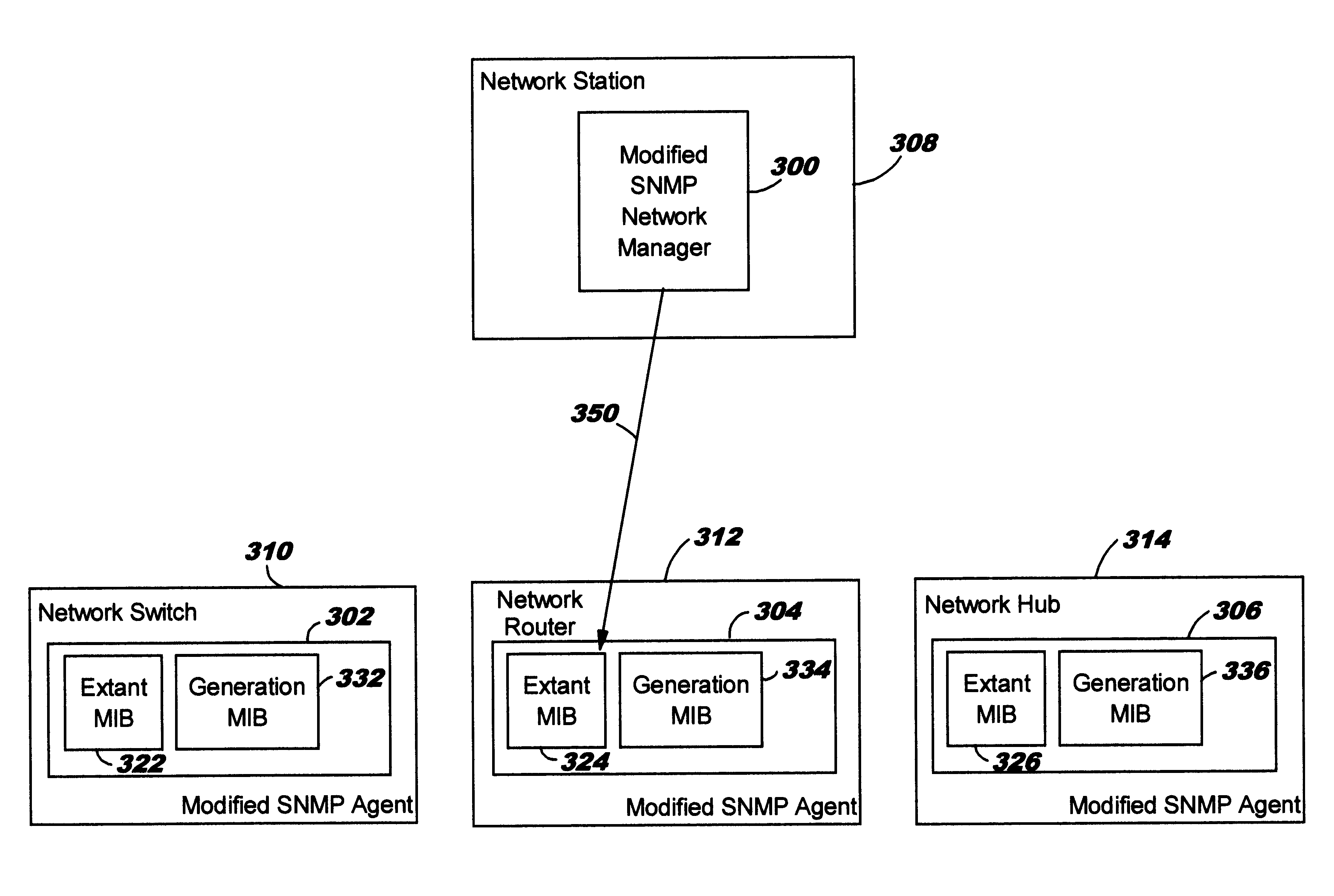
InactiveUS6176883B1Multiple digital computer combinationsData switching networksNetwork agentNetwork management
A system and method for generating unsupported network information indicators for monitoring and managing a network having at least one network manager resident within a network station and at least one network agent resident within a network device. The method and system accomplish their objects as follows. Network parameters of interest are selected. Network parameters accessible by the at least one network agent are determined. And, in response to the determining, the selected network parameters of interest are construed by utilizing the determined network parameters accessible to the at least one network agent.
Owner:IBM CORP
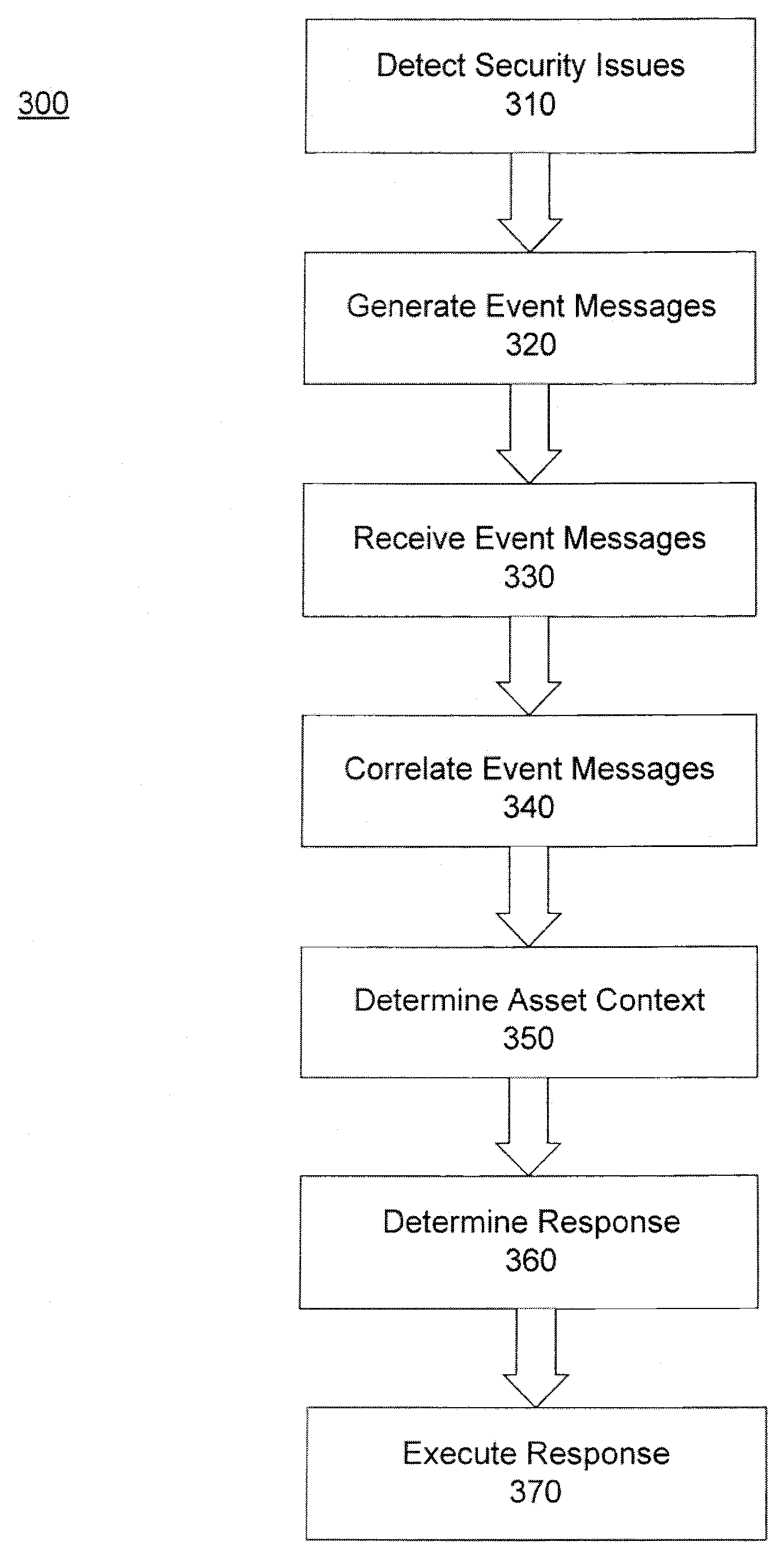
System and method for evaluating security events in the context of an organizational structure
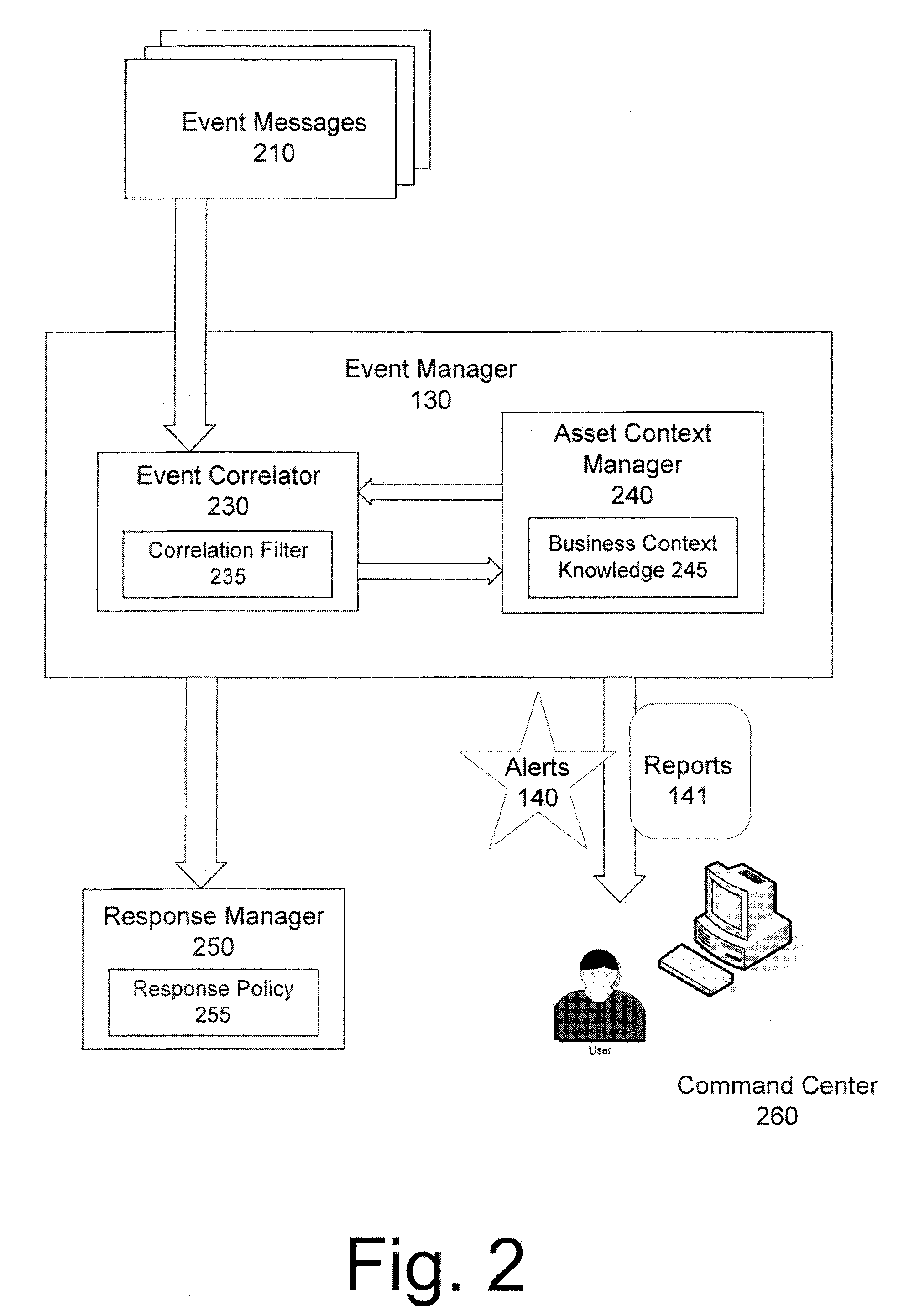
InactiveUS20080307525A1High response rateMemory loss protectionError detection/correctionNetwork agentContext manager
A system and method is provided for evaluating security threats to an enterprise network. The relative severities of security threats are determined, based in part, on the context of each threat within the enterprise network and in relation to the operation of a business. As a result, it is possible to prioritize security threats having the greatest magnitude and also threats that are directed against the most valuable business network devices. The invention comprises a plurality of network agents operating on a plurality of network devices for generating event messages. The event messages contain security data and are forwarded to an event manager for analysis. The event manager comprises an event correlator and an asset context manager. The event correlator detects security threats from the interrelationships between the security data contained in the event messages. In addition, the asset context manager utilizes business context knowledge specific to a particular business or business unit to determine a threat priority based on the importance of the threatened network device to the operation of the business.
Owner:COMP ASSOC THINK INC
Network adapted for mobile devices
ActiveUS7779069B2Ticket-issuing apparatusHand manipulated computer devicesNetwork mobilityData acquisition module
Owner:WELLS FARGO BANK NAT ASSOC
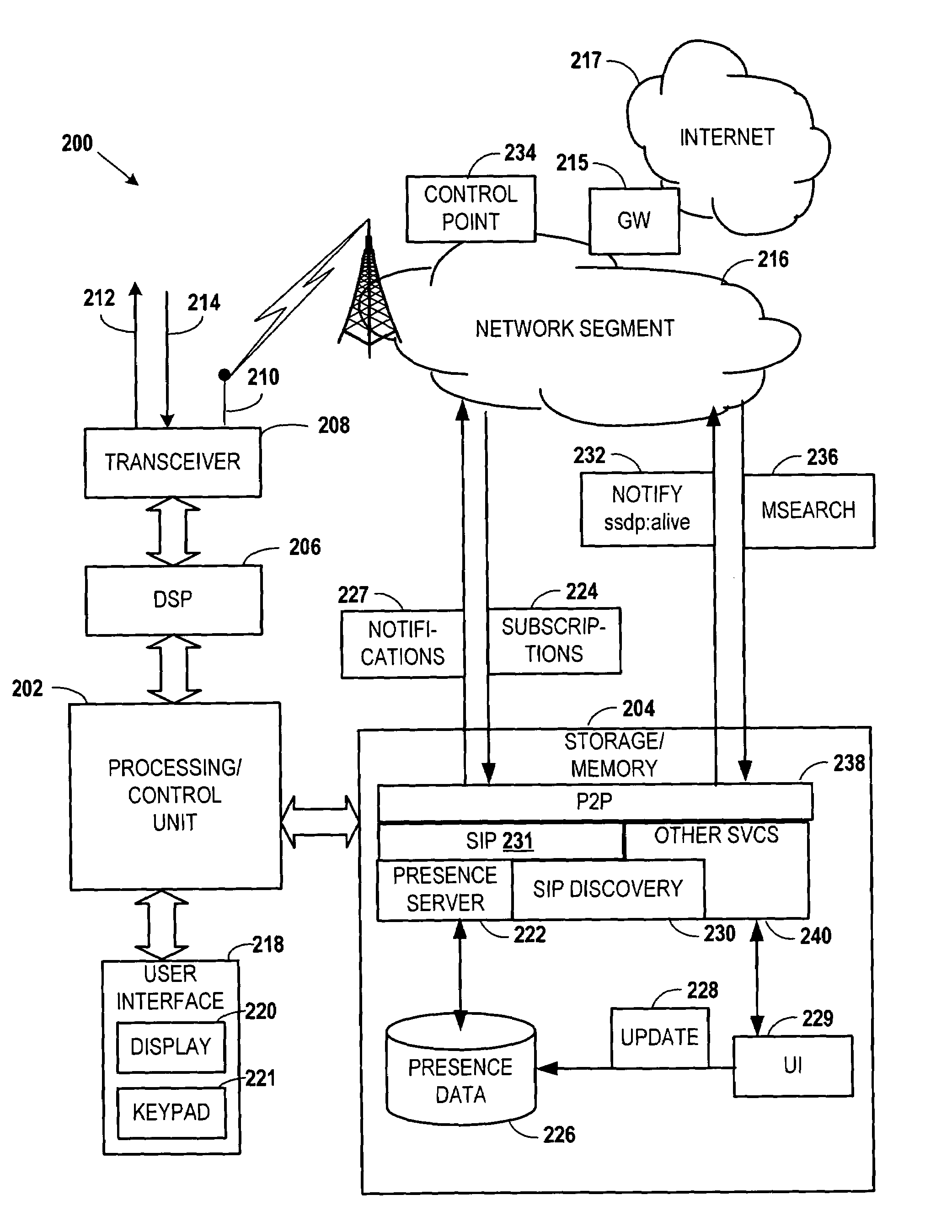
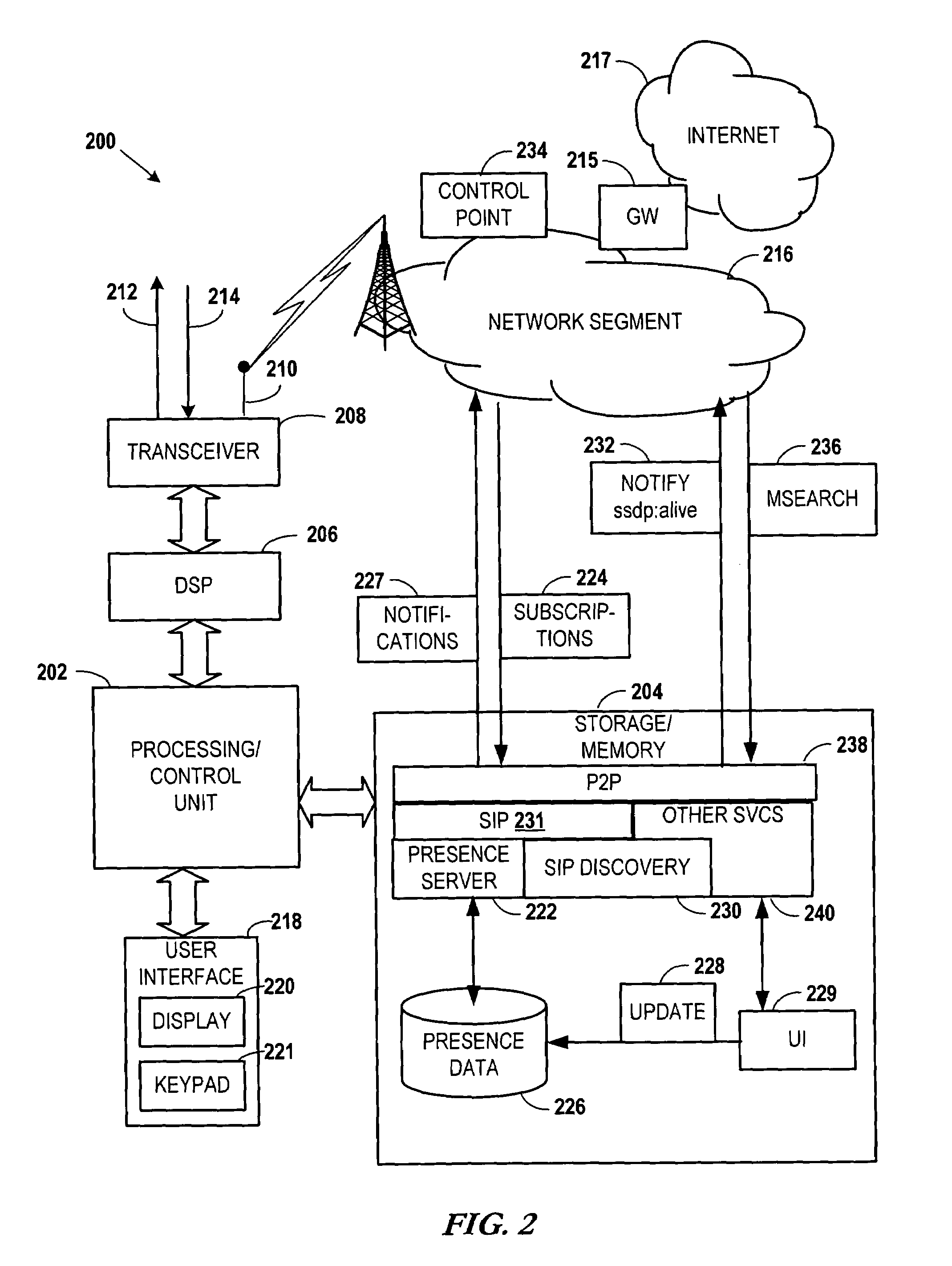
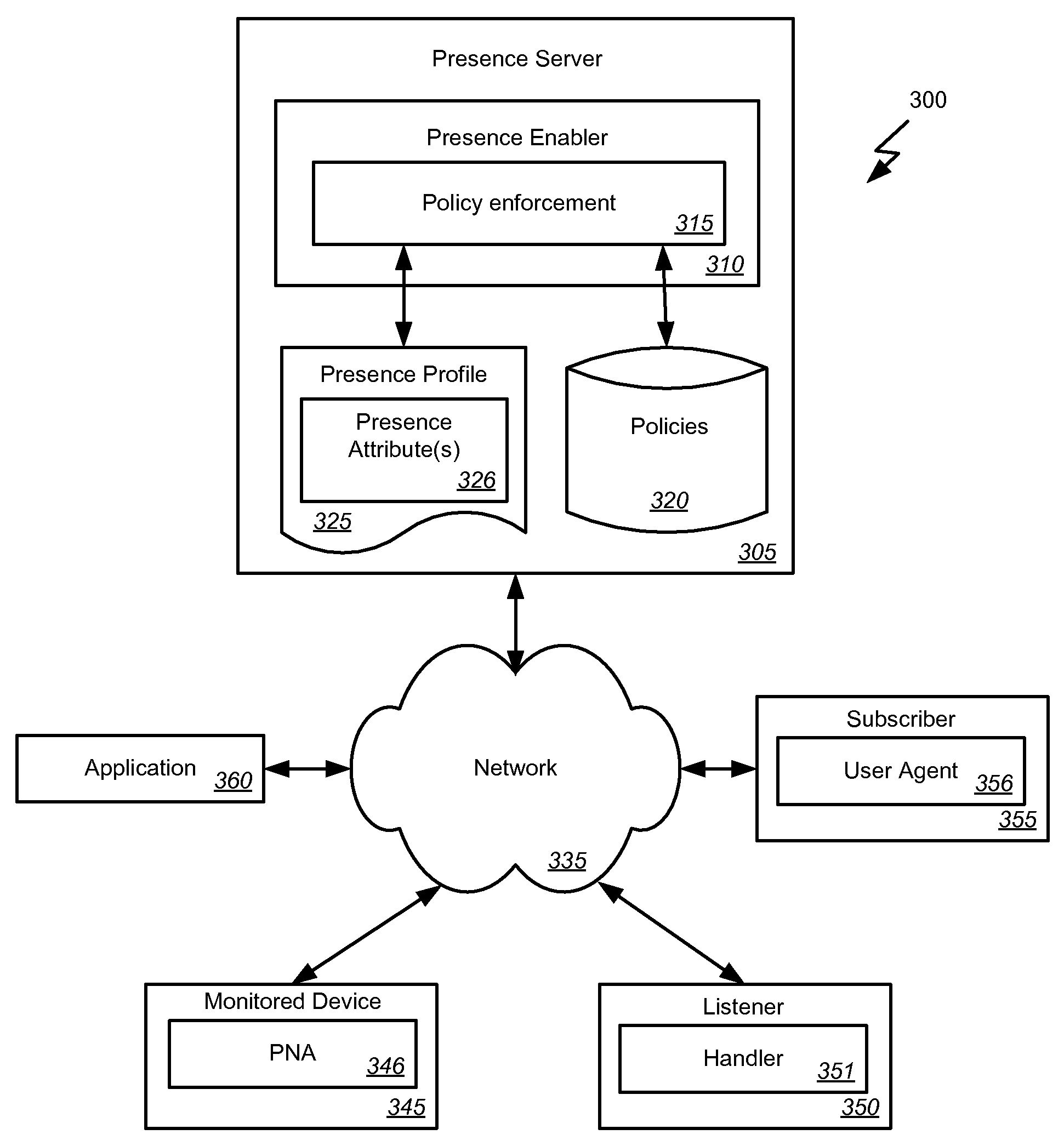
Presence-based event driven architecture
Embodiments of the invention provide systems and methods for using a presence-based network to monitor systems, devices, or agents. According to one embodiment, monitoring a system can comprise receiving a publication of one or more presence attributes from a presence network agent. The presence attributes can comprise at least one attribute indicating information other than presence information. A presence profile associated with the presence network agent can be updated based on the received presence attributes. One or more of the presence attributes of the presence profile associated with the presence network agent can be provided to a listener. For example, providing presence attributes to the listener can comprise providing a notification of a change in the at least one presence attribute. Additionally or alternatively, a request can be received from the listener for one or more presence attributes and the presence attribute can be provided in response to the request.
Owner:ORACLE INT CORP
System and Method for Providing Application Penetration Testing
InactiveUS20080263671A1Memory loss protectionError detection/correctionOperational systemNetwork agent
A system and method provide application penetration testing. The system contains logic configured to find at least one vulnerability in the application so as to gain access to data associated with the application, logic configured to confirm the vulnerability and determine if the application can be compromised, and logic configured to compromise and analyze the application by extracting or manipulating data from a database associated with the application. In addition, the method provides for penetration testing of a target by: receiving at least one confirmed vulnerability of the target; receiving a method for compromising the confirmed vulnerability of the target; installing a network agent on the target in accordance with the method, wherein the network agent allows a penetration tester to execute arbitrary operating system commands on the target; and executing the arbitrary operating system commands on the target to analyze risk to which the target may be exposed.
Owner:HELP SYST LLC
Network packet tracking
InactiveUS6958977B1Overcomes shortcomingError preventionTransmission systemsNetwork agentNetwork data
A method for testing of a communication network having a plurality of end-points, using one or more network agents coupled to the network at respective locations. The method includes specifying at least one packet filtering criterion, and transmitting one or more data packets meeting the at least one criterion through the network from one of the end-point to another. At least one of the data packets meeting the criterion is intercepted using the network agents at one or more of the respective locations in the network traversed by the at least one of the data packets. Information regarding the at least one intercepted packet at the one or more respective locations is recorded and processed to analyze a route of the at least one intercepted packet through the network.
Owner:CISCO TECH INC
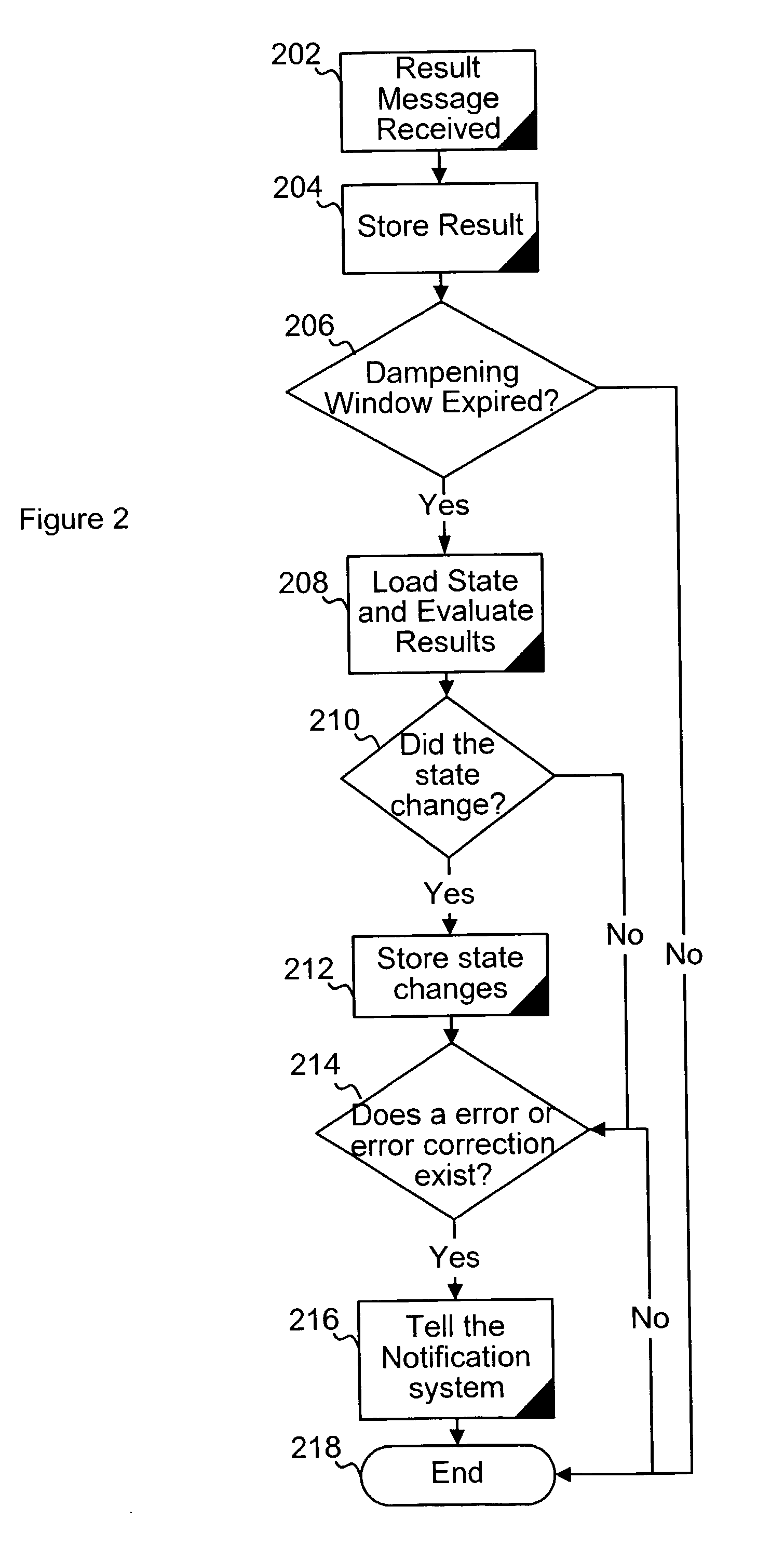
System and method for monitoring state information in a network
InactiveUS20050160335A1Error preventionFrequency-division multiplex detailsNetwork agentNetwork testing
Agents are instructed execute network tests during monitoring intervals. Results of the tests are stored. After expiration of a dampening window period the results are retrieved and evaluated. The evaluation is used to update an error state stored in a data structure in a database as required. Notification of detected errors is provided if certain notification dampening criteria are satisfied.
Owner:CATBIRD NETWORKS
Microcontroller controlled or direct mode controlled network-fabric on a structured ASIC
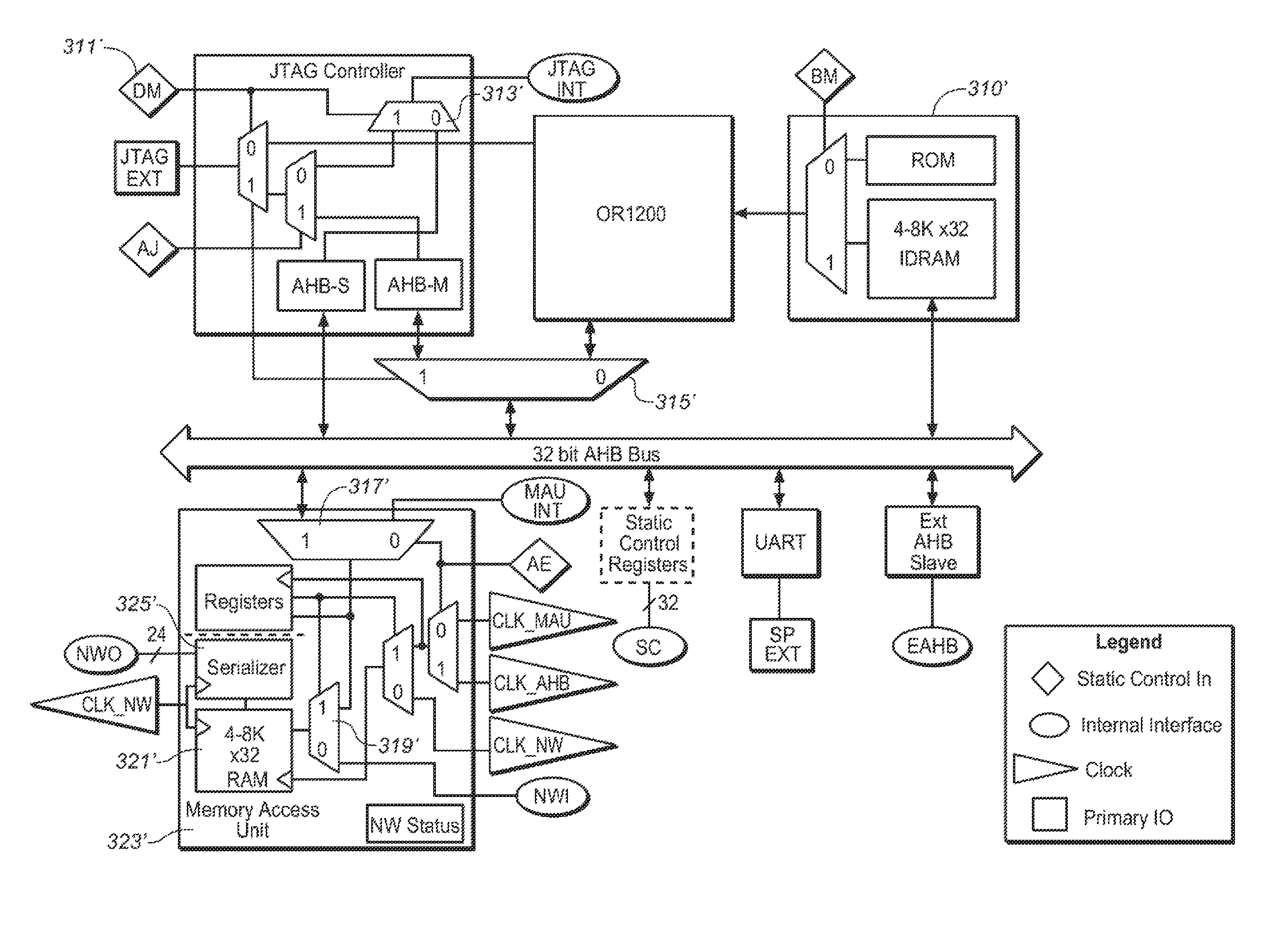
ActiveUS8677306B1Easy to switchElectronic circuit testingDetecting faulty computer hardwareMicrocontrollerIntelligent Network
A network-fabric used for testing with an external or internal tester is shown for a Structured ASIC. In one embodiment, the Structured ASIC uses a microprocessor, network-aware IO routing fabric comprising network agents in a scalable novel configuration, with the network-aware IO having a plurality of blocks connected in series in a plurality of paths in the fabric leading to and from the microprocessor and memory and / or logic, the blocks acting as intelligent network agents under processor control to determine what state they can assume, whether to pass a data signal or not along these paths, comprising open loops and closed loops running to and from the microprocessor and memory and / or logic, primarily for testing and determining the state of the memory and logic. In another embodiment a JTAG controller may receive JTAG test commands from an external testing apparatus and set up to communicate along the fabric.
Owner:INTEL CORP
System and method for simulating computer network attacks
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
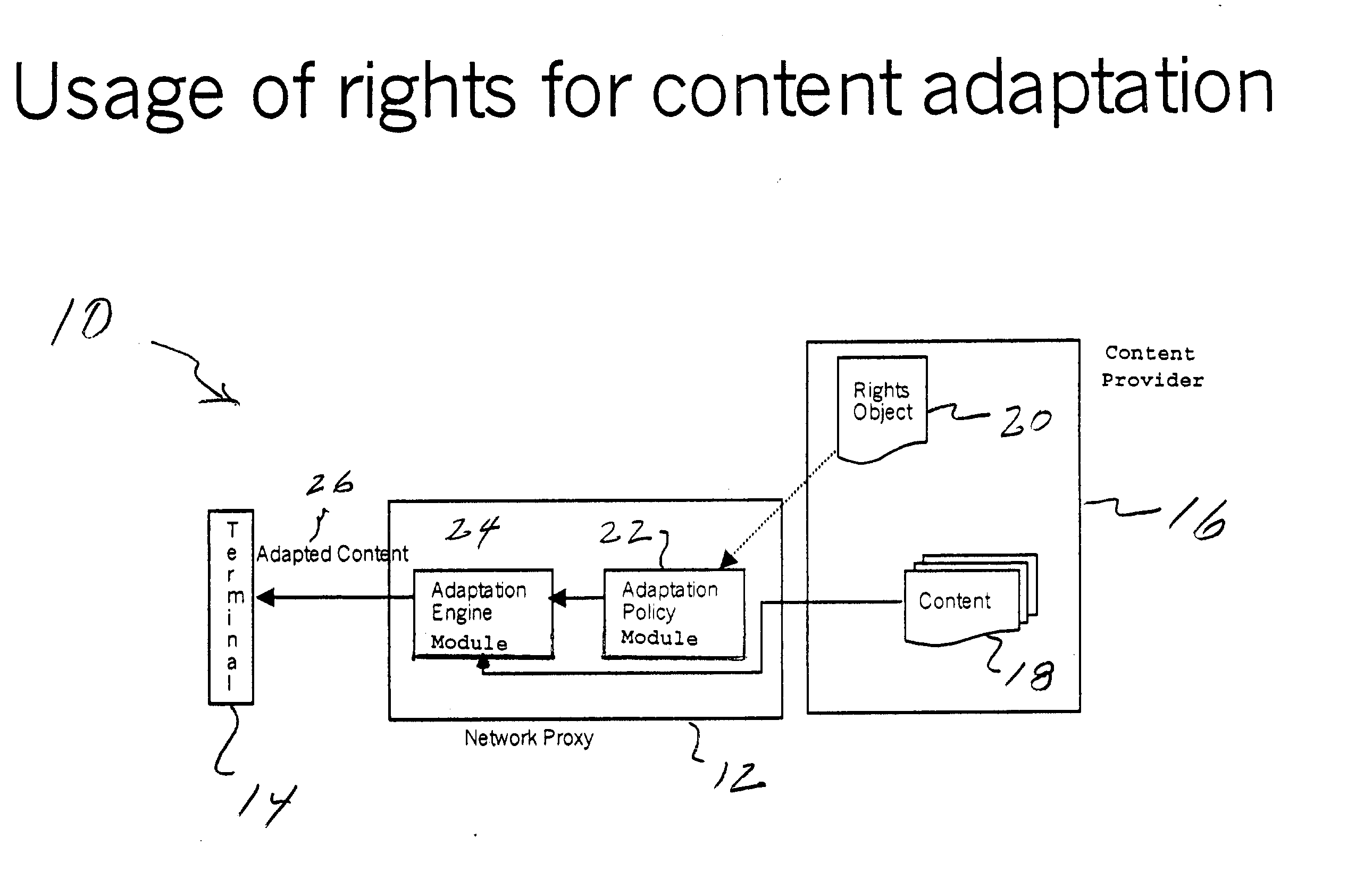
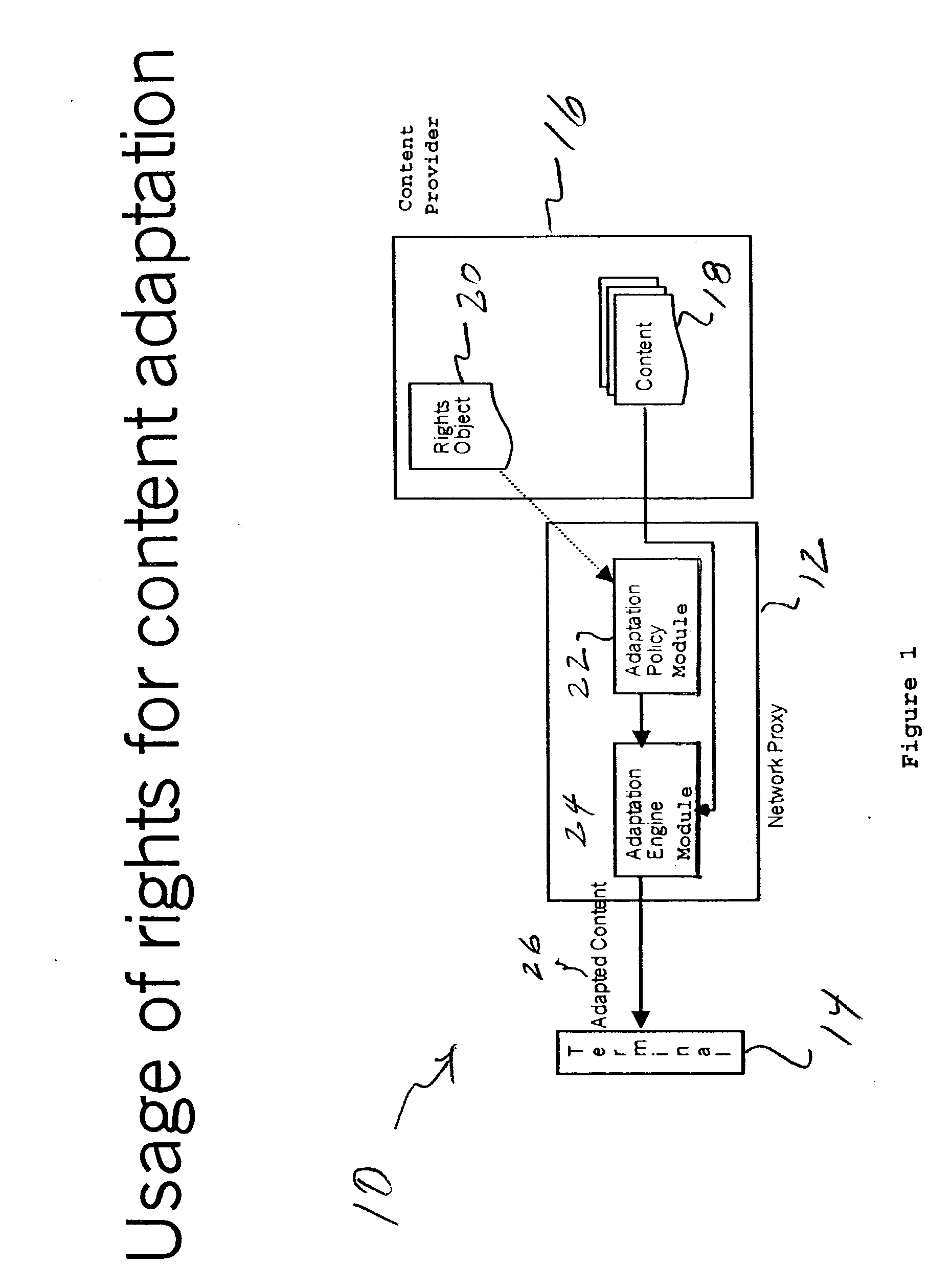
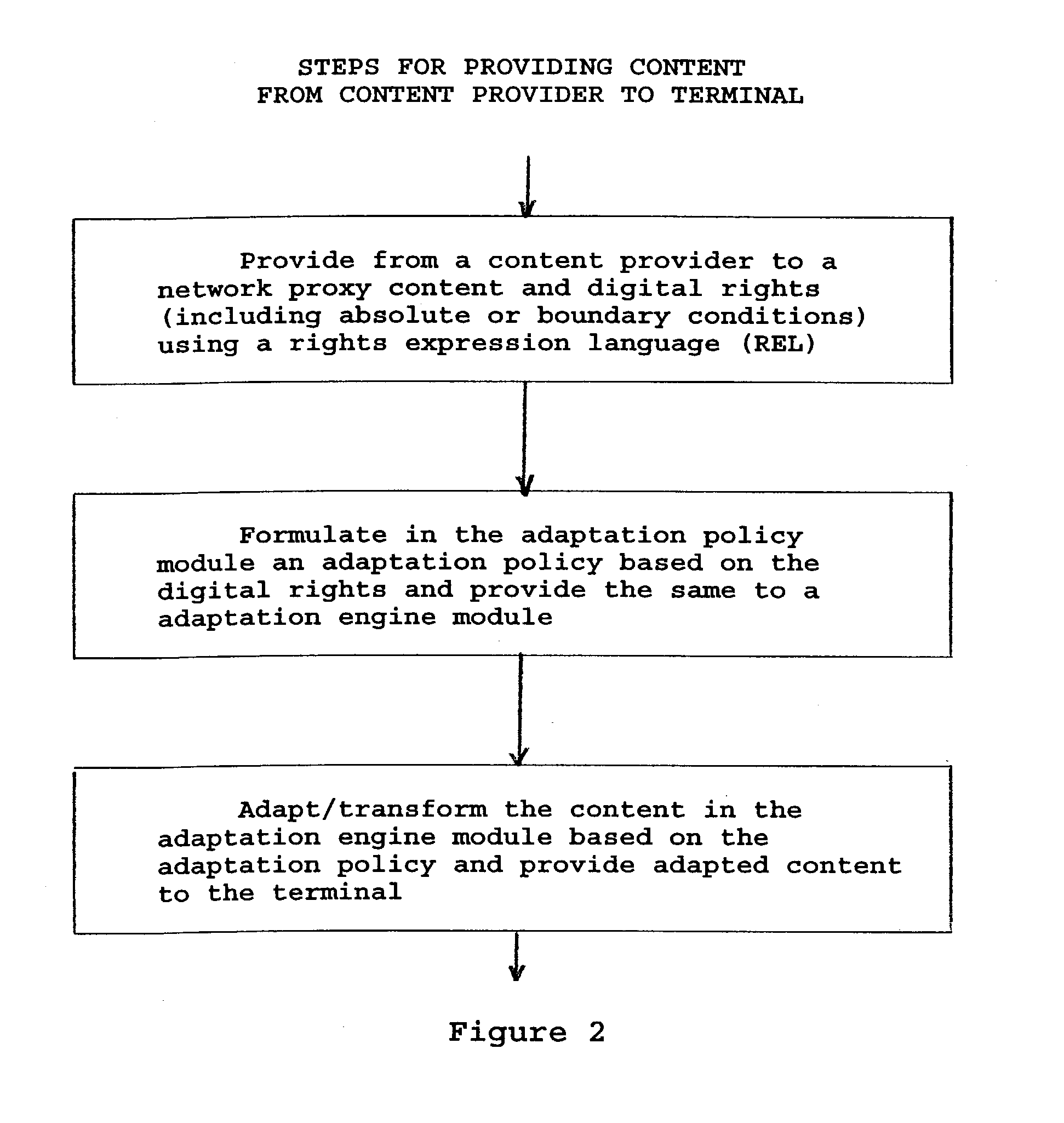
Method and apparatus to represent and use rights for content/media adaptation/transformation
The invention provides a method and apparatus for providing content in a network having a network proxy arranged between a mobile terminal and a content provider. The method features a step of adapting or transforming the content in the network proxy based on one or more digital rights issued by the owner of the content. The network proxy includes an adaption policy module that receives the digital rights and provides an adaption policy; and an adaption engine module that receives the adaption policy and the content from the content provider, and provides adapted content to the terminal. In operation, the network proxy uses the digital rights to determine an optimal adaptation policy and then uses that to transform the content.
Owner:CONVERSANT WIRELESS LICENSING LTD
Radio Network Controller With IP Mapping Table
InactiveUS20120014316A1Power distribution line transmissionNetwork topologiesHandoverWireless network
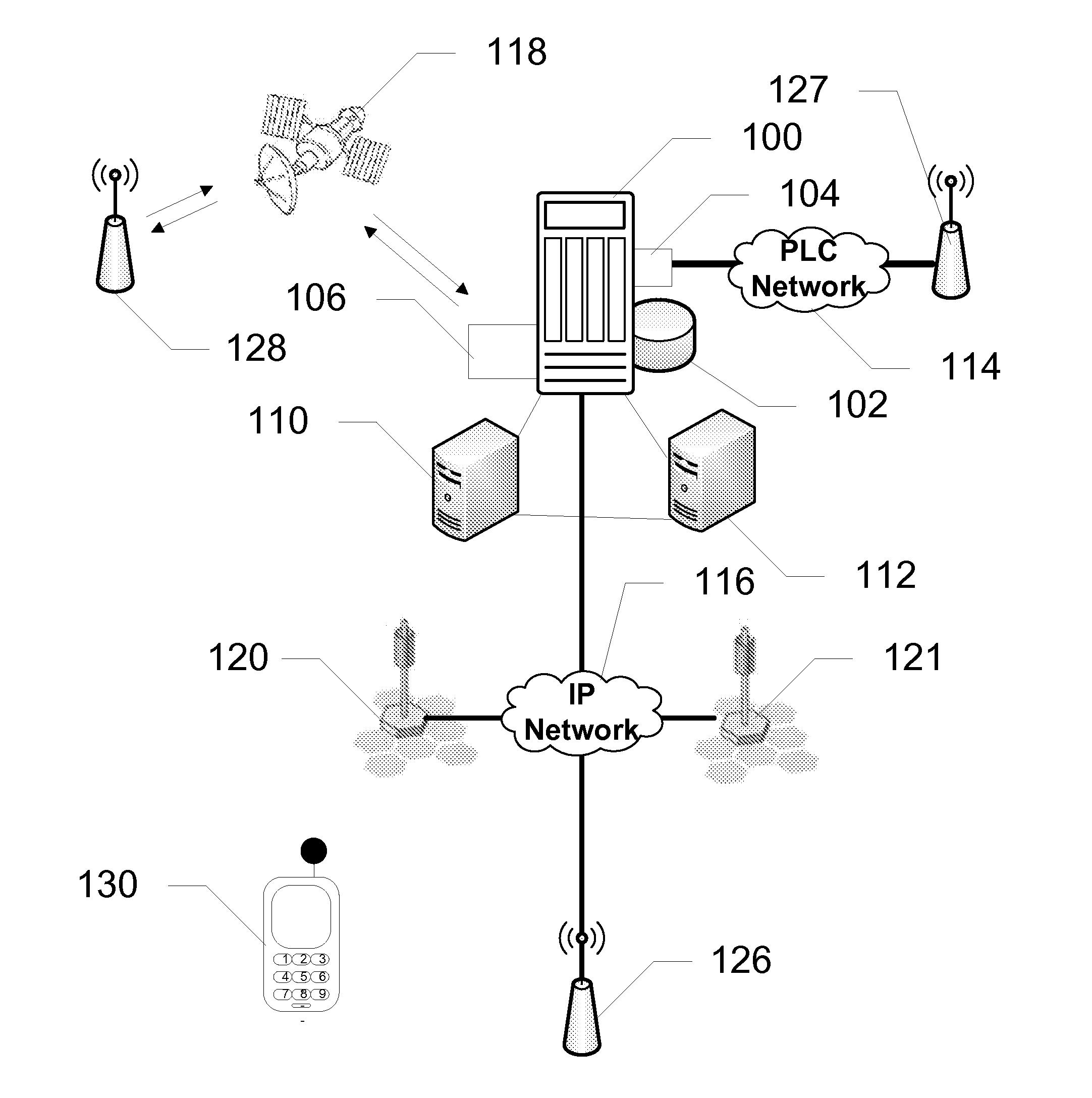
Devices, systems, and methods are disclosed for seamlessly routing data to mobile devices that undergo handovers from one access point to another. A controller, such as a RNC or BSC, includes logic to map the locations of mobile devices that are connected to various access points on one or more networks. The access points include base stations, Node Bs, wireless LAN, etc., and incorporate or are coupled to network agents. The network agent reports the location of the mobile device to the controller via a plurality of means such as over an IP network, a powerline network, or a satellite network. Using the database, or IP mapping table, having the most current locations of all the mobile devices under its domain or area, the controller can route data packets to the mobile devices using the most effective routing paths.
Owner:AT&T INTPROP I L P
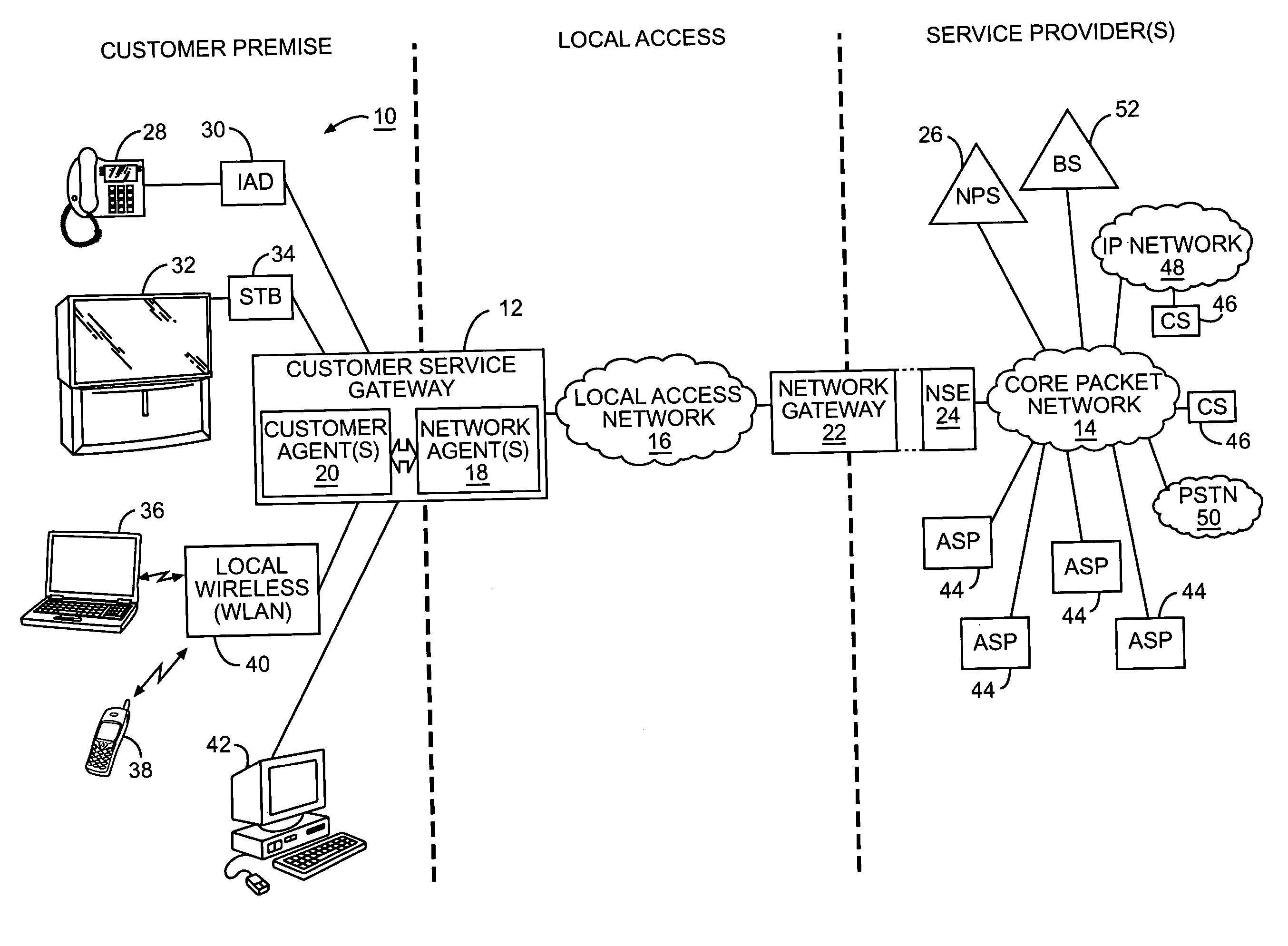
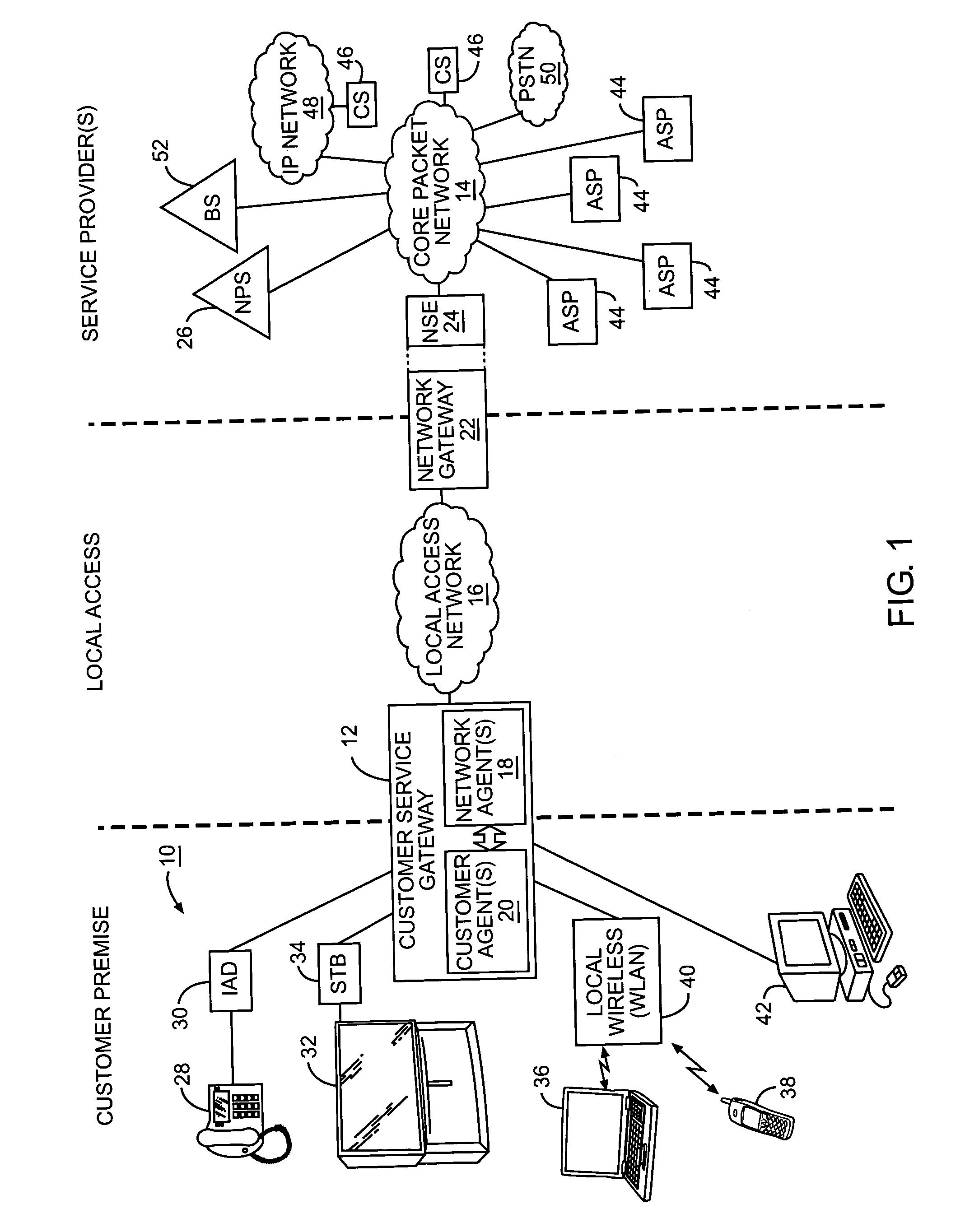
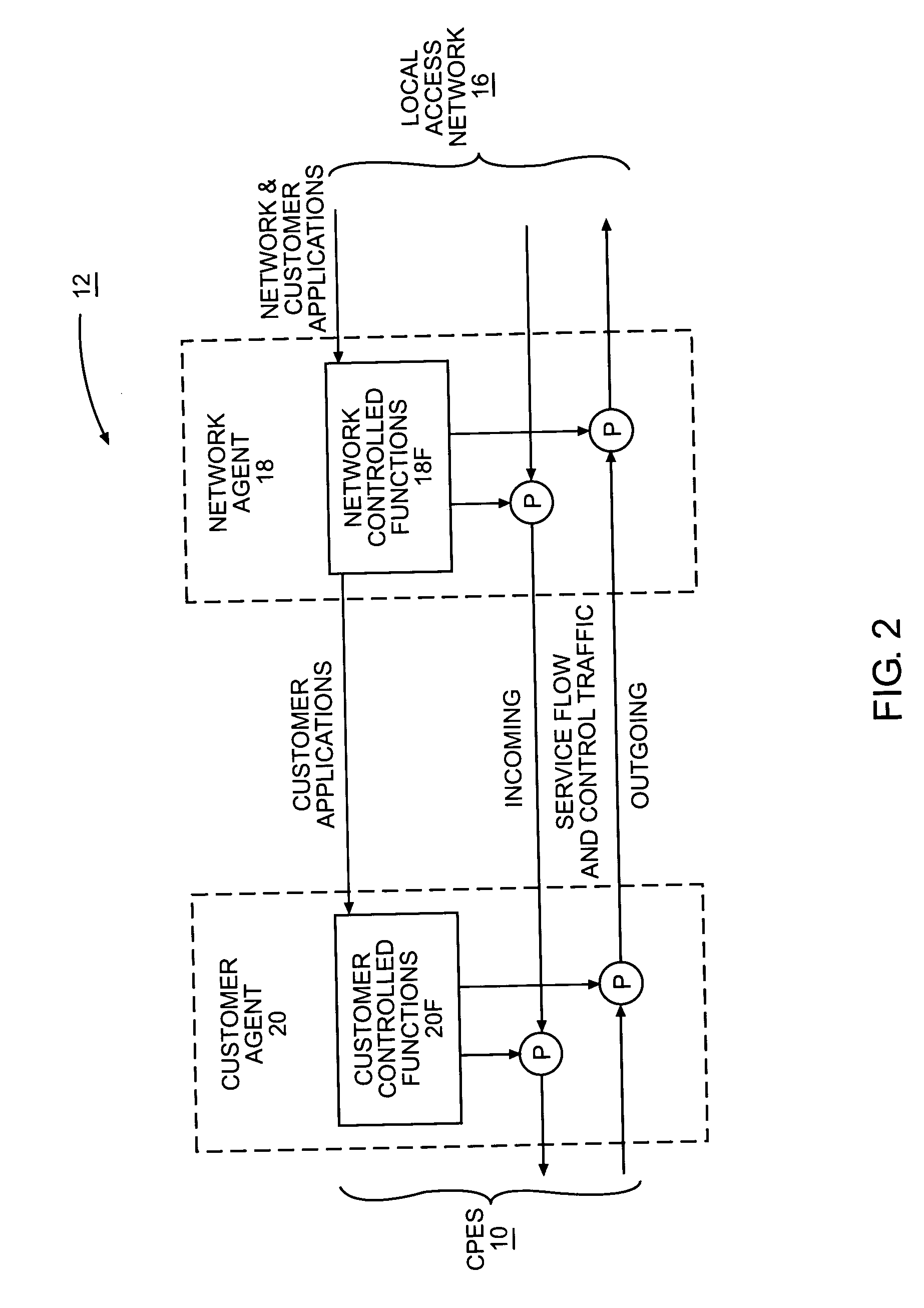
Network controlled customer service gateway for facilitating multimedia services over a common network
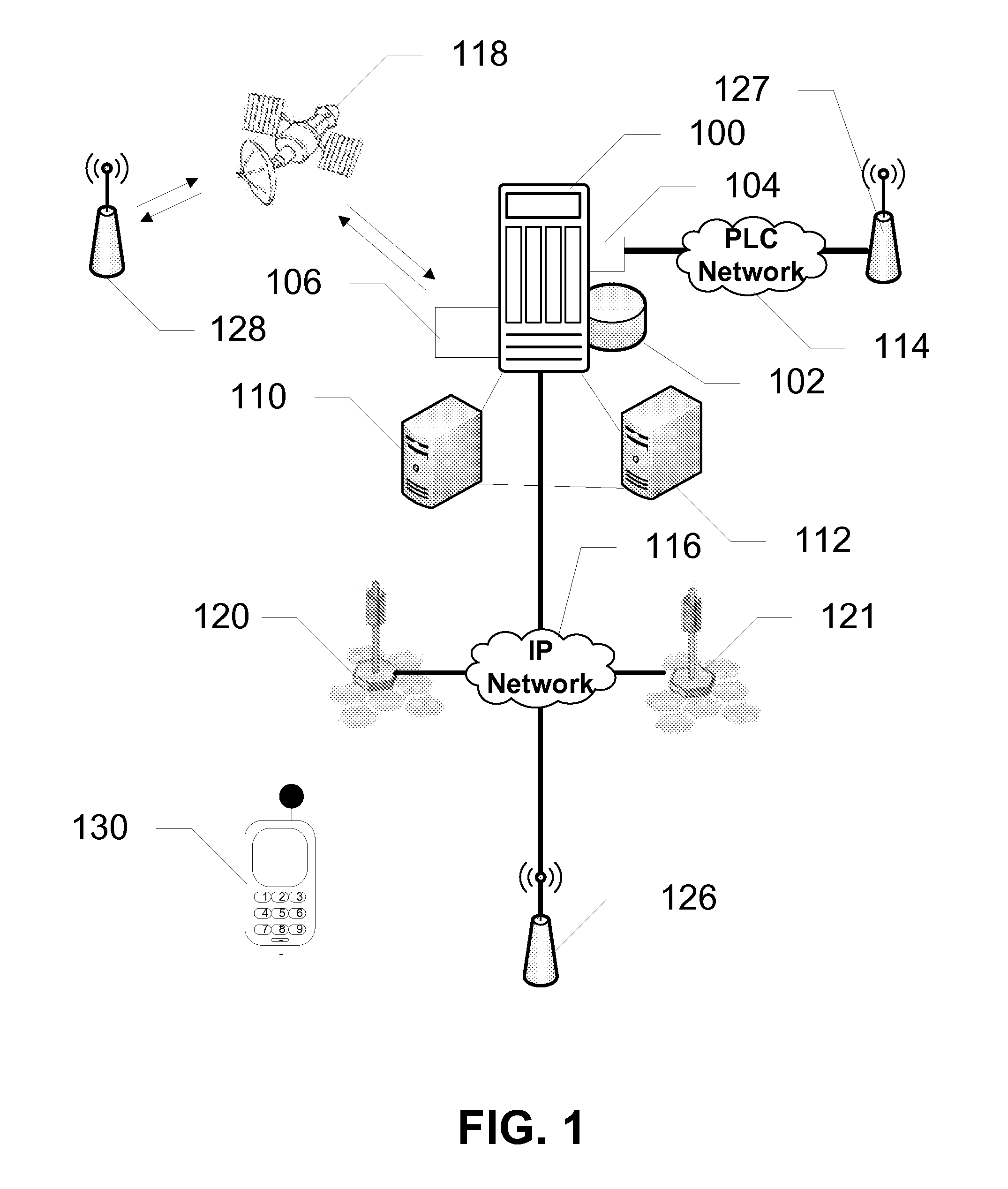
The present invention provides a customer service gateway acting as an interface between various customer premise equipment for a customer and a local access network. The customer service gateway has one or more customer agents and network agents. A network agent is a secure and trusted agent of the service providers, and is not accessible by the customer or the customer premise equipment for manipulation. The customer service gateway may support different types of services using different types of media from the different service providers. In operation, the service providers may sent applications to a network agent, which will run the applications to implement functions to monitor or control services or service flows for the services. The monitoring and control functions may be used to implement various types of service or service flow analysis, as well as any type of tagging, characterization, or processing of the service flows.
Owner:NORTEL NETWORKS LTD
Network brokering system
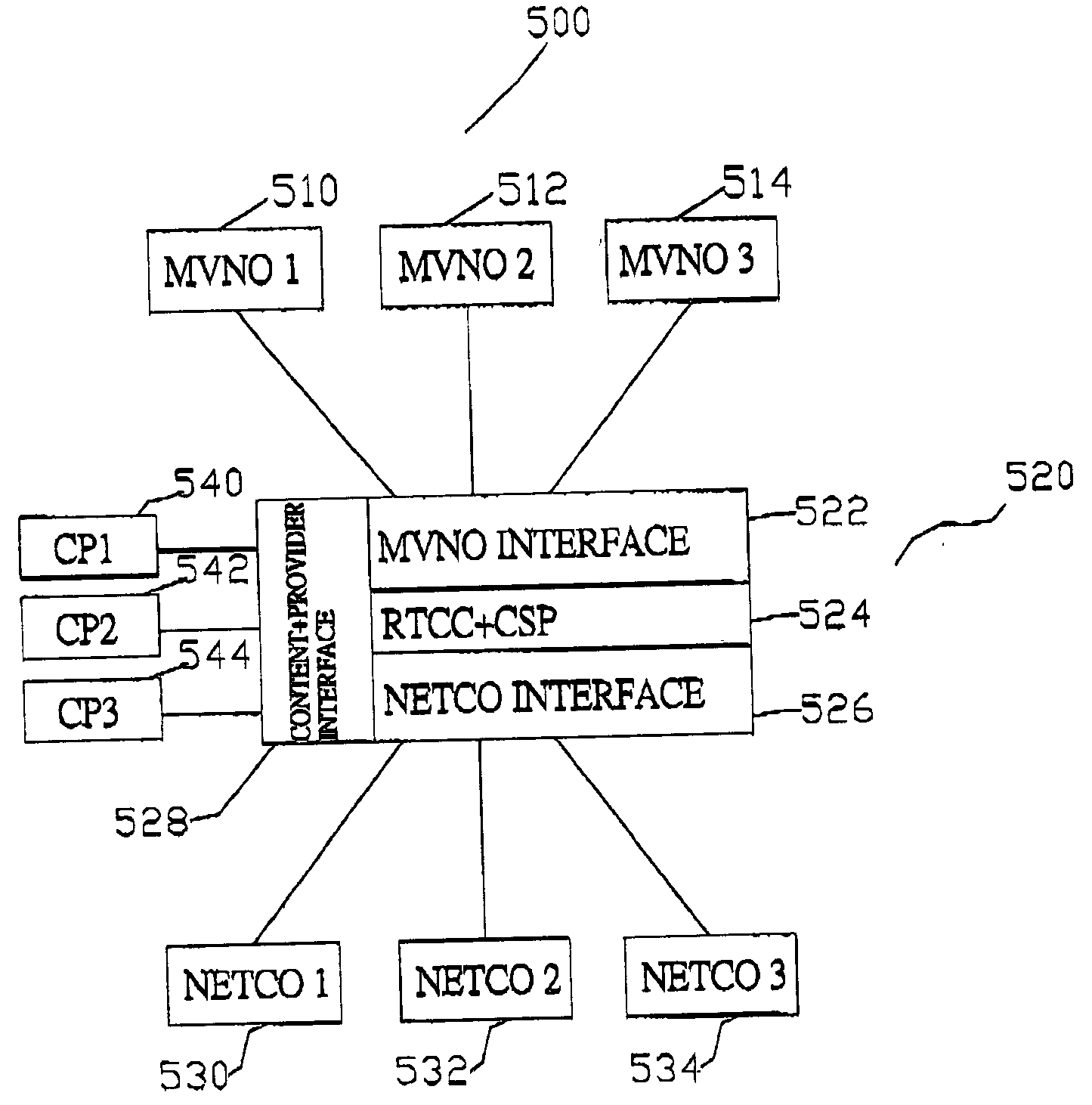
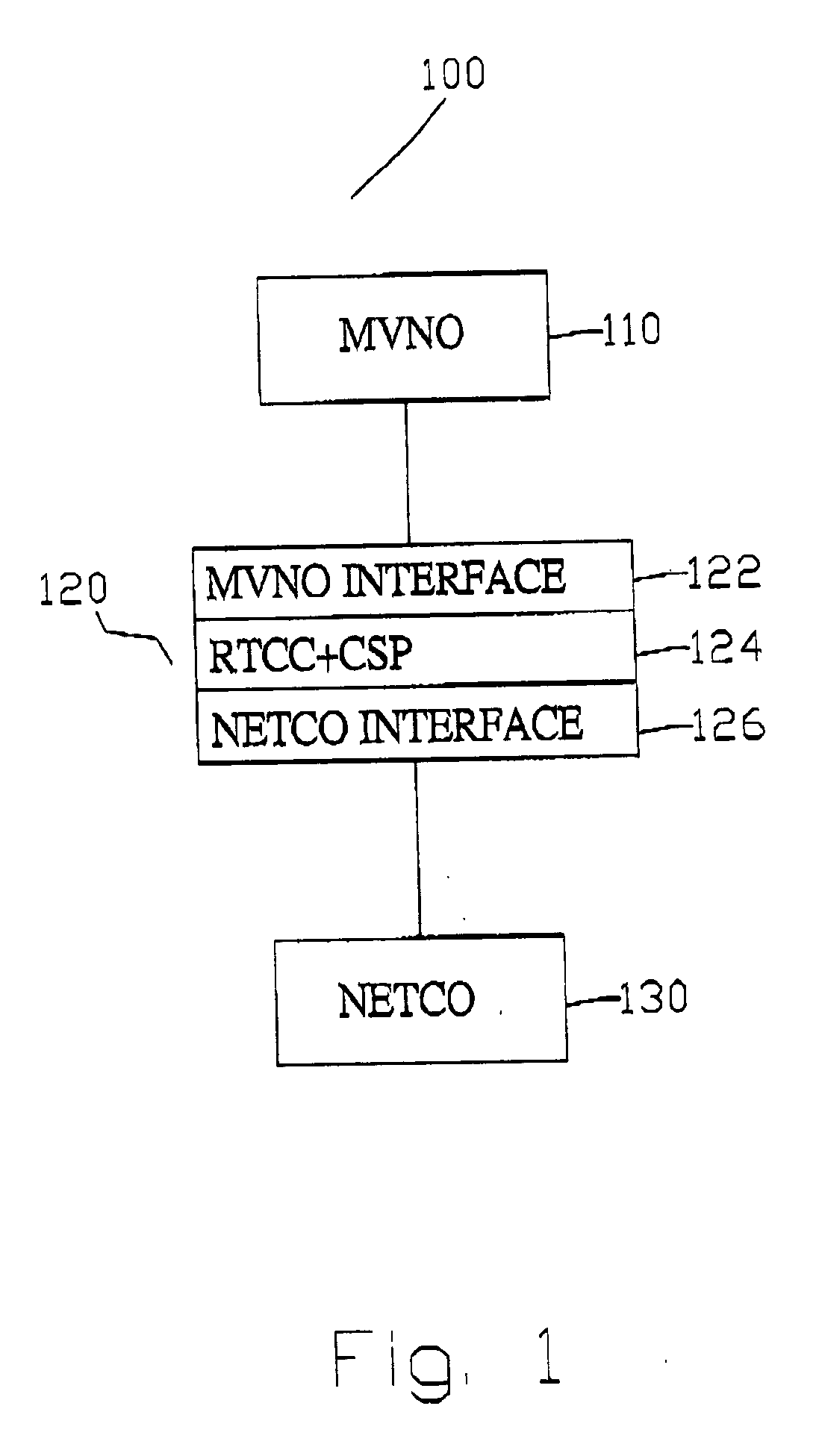
InactiveUS20050074014A1Increase valueMetering/charging/biilling arrangementsData switching by path configurationPaymentCyber operations
A network and network services brokering system between network companies and mobile virtual network operators which provides efficient billing systems in order to provide improved network services to subscribers. The network brokering system comprises a virtual network operator who provides network services to subscribers, a network company who provides usage of their physical networks to the virtual network operator, and a network broker who interfaces between the network company and virtual network operator. Additionally, the network broker provides interfacing between virtual network operators and independent content providers. The network broker further comprises a real-time call control and common service platform for real-time controlling of call, billing, and payment information. Using the real-time call control and common service platform allows complex billing such as partial pre-paid and partial post-paid payment schemes. Through the services of the network broker, the virtual network operator has usage of the network company's networks.
Owner:FAR EASTONE TELECOMM
System and method for proxy-based redirection of resource requests
InactiveUS20050060410A1Lower latencyIncrease delayMultiple digital computer combinationsSecuring communicationNetwork agentComputer science
A system and method are provided for requesting a resource over at least one network. The system includes a terminal, a host and a network proxy. The terminal can send a first request for the resource over a first network and a second network. In turn, the host can receive the first request and send a first response, where the first request identifies the resource at a first location on the host. The network proxy, which can communicate with the host over the second network independent of the first network, can receive the first response from the host, and reformulate the first request into a second request that identifies the resource at a second location. The network proxy can send the second request to a host of the resource at the second location such that the host of the resource at the second location can respond to the second request.
Owner:NOKIA CORP
A robust point to point based stream scheduling method
InactiveCN1604569ASave bandwidthReduce correlationData switching networksMulticast networkMedia server
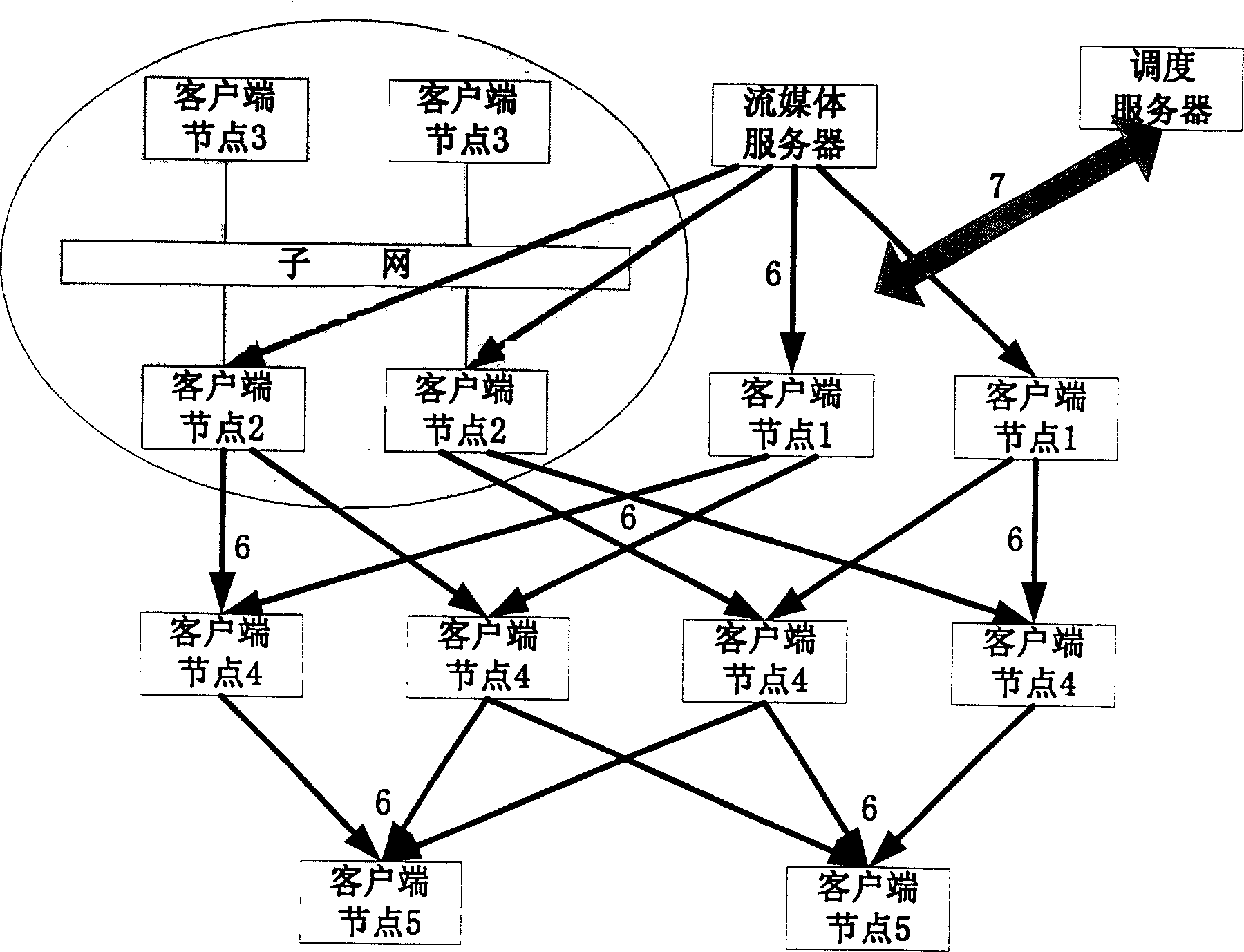
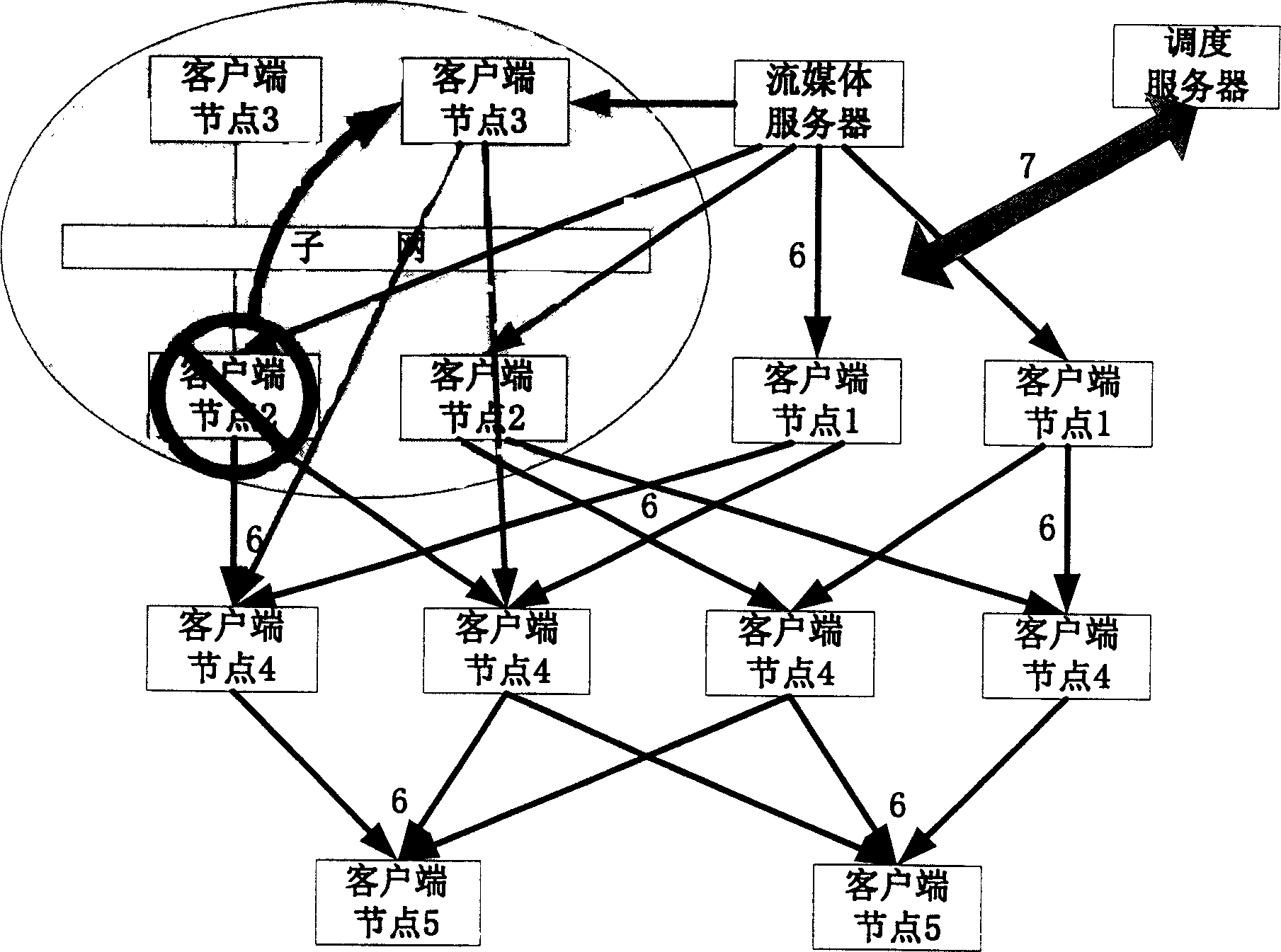
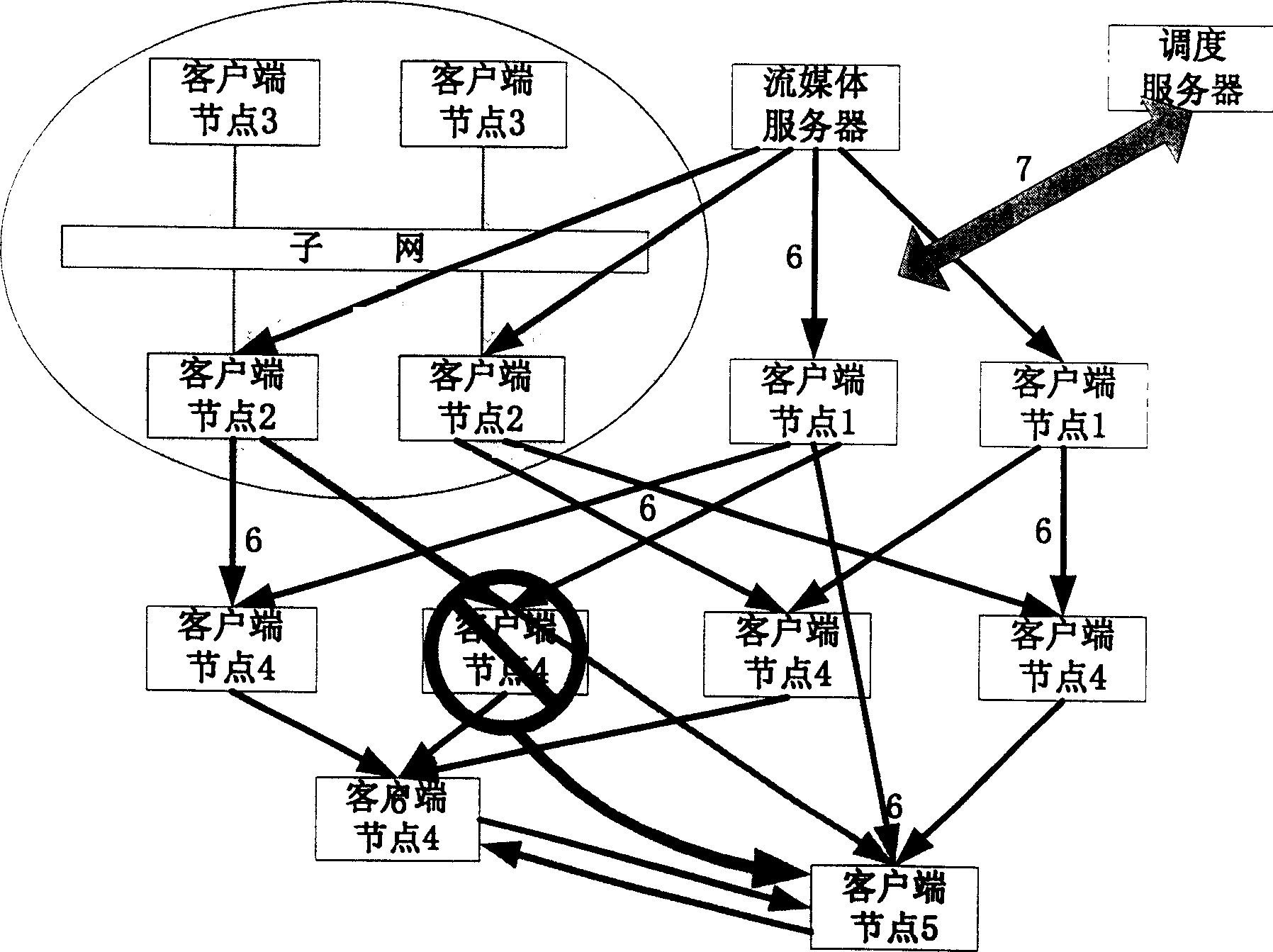
This invention belongs to information transmission technique field and relates to a robust flow dispatching method based on point to point. The method is to integrate dispatching server, flow media server and customer terminal points into one living broadcast network gives different definitions to functions in network of each customer points and gives different functions to each customer points in the network. The entrance and exit of the new customer point make changes of the network topological structure and realizes the flow dispatching through network topological form dynamic update and monitoring and part of changing customer point.
Owner:TSINGHUA UNIV
Dynamics performance parameter optimizing method of high-speed train
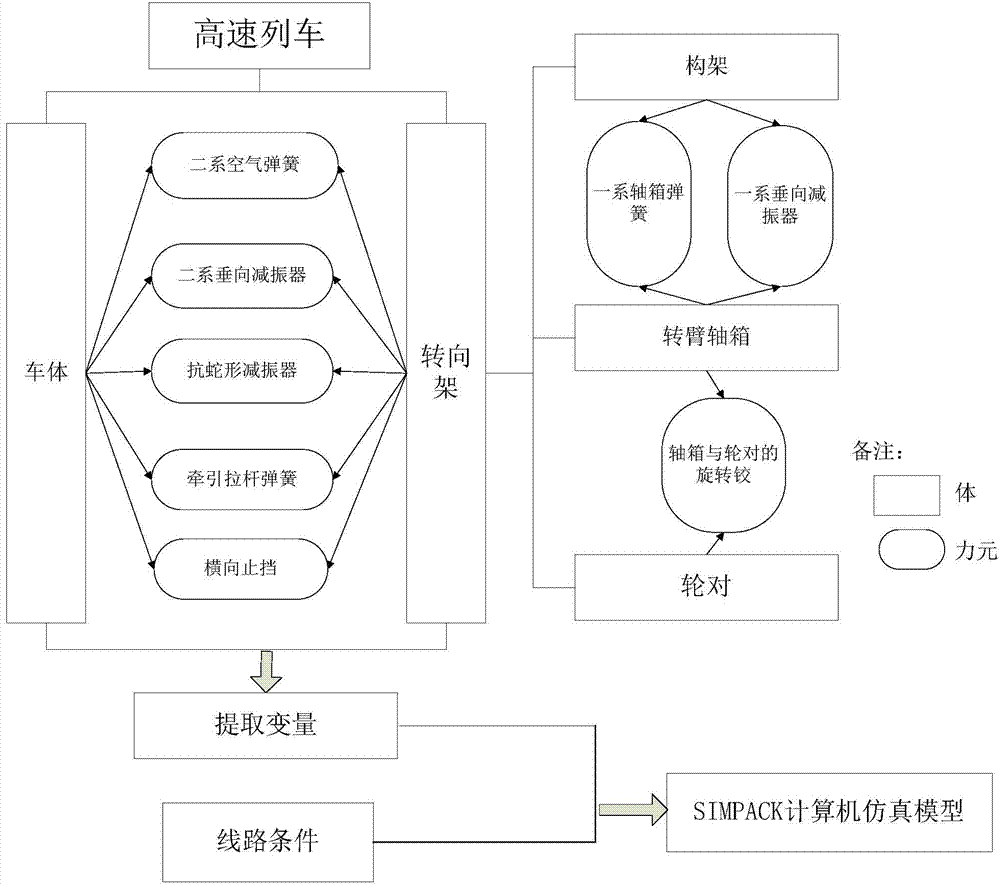
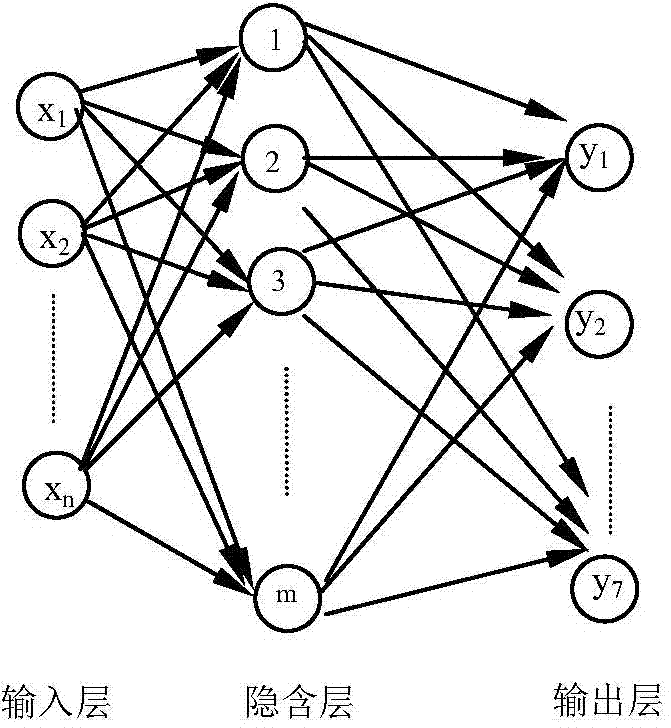
ActiveCN104765916AImprove operational safetyImproved smoothness and comfortSpecial data processing applicationsNetwork modelDesign space
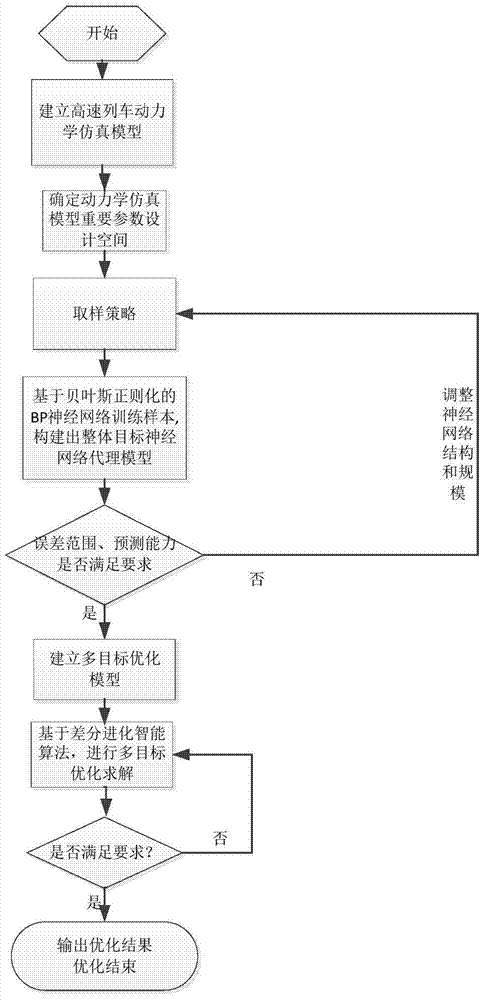
The invention provides a dynamics performance parameter optimizing method of a high-speed train, relates to the field of parameter design optimizing based on the dynamics simulation analysis of the high-speed train, and aims at effectively replacing a dynamics simulation model of the high-speed train by a comprehensive target neural network agent model and combining the design analysis and the multi-target optimization algorithm of the high-speed train in the multi-disciplinary field to analyze and optimize the dynamics simulation approximation model of the high-speed train. The method specifically comprises the steps of building a multi-rigidity dynamics simulation model for the high-speed train; determining related important input / output design spaces; selecting sampling strategy to obtain a design space sample set suitable for the dynamics performance analysis of the high-speed train; improving the generalization accuracy of the comprehensive target neural network by the bayesian regularization method; adjusting the number of nodes in a hidden layer to build the comprehensive target neural network agent network model of which the error is controlled to be within a certain of range; performing multi-target optimization through the intelligent differential evolution algorithm by using the improved comprehensive target neural network agent network model to obtain the optimized high-speed train design parameters. The method is mainly applied to the dynamics analysis and design optimization of the high-speed train.
Owner:成都天佑创软科技有限公司
System and method for implementing internet television medium interaction
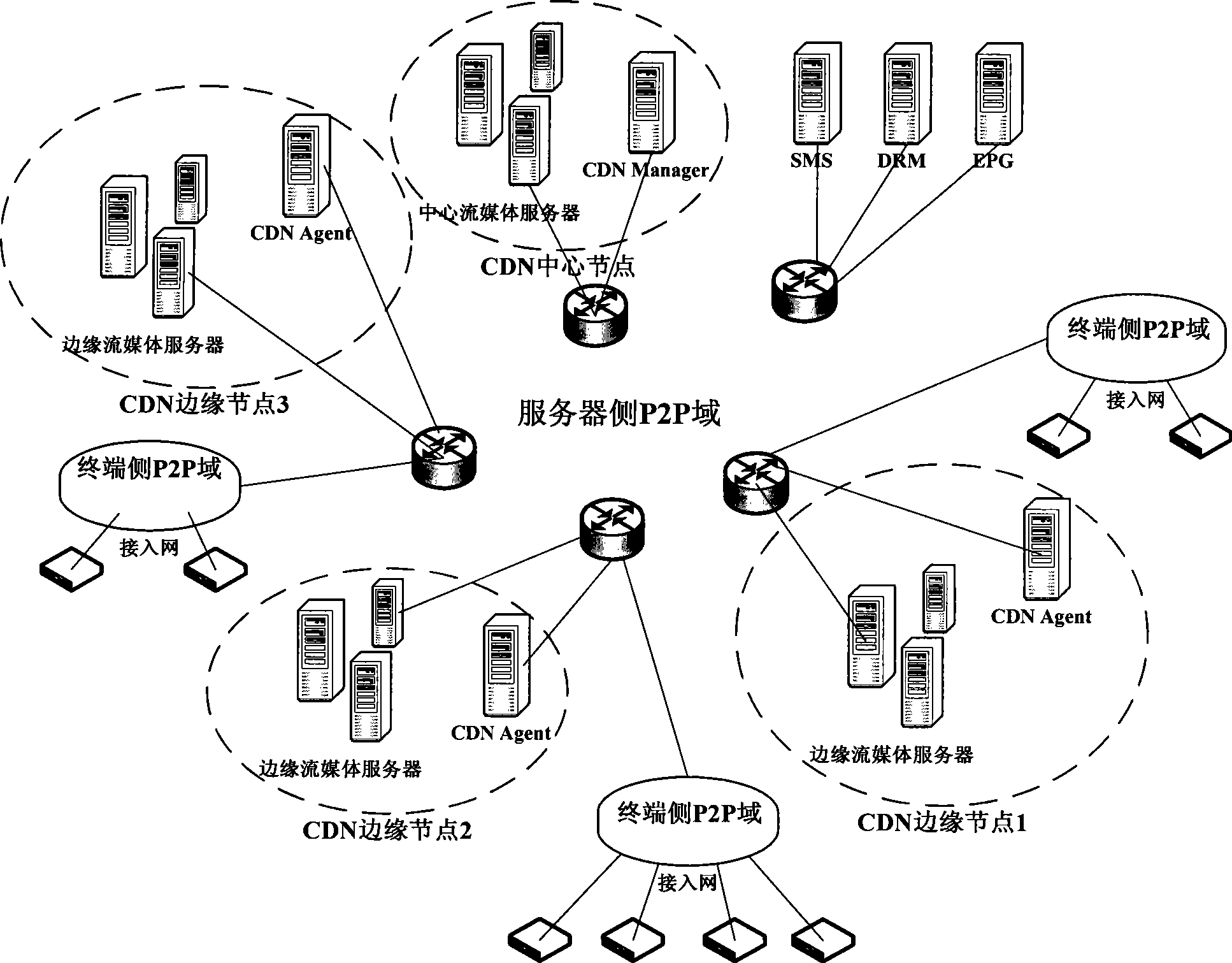
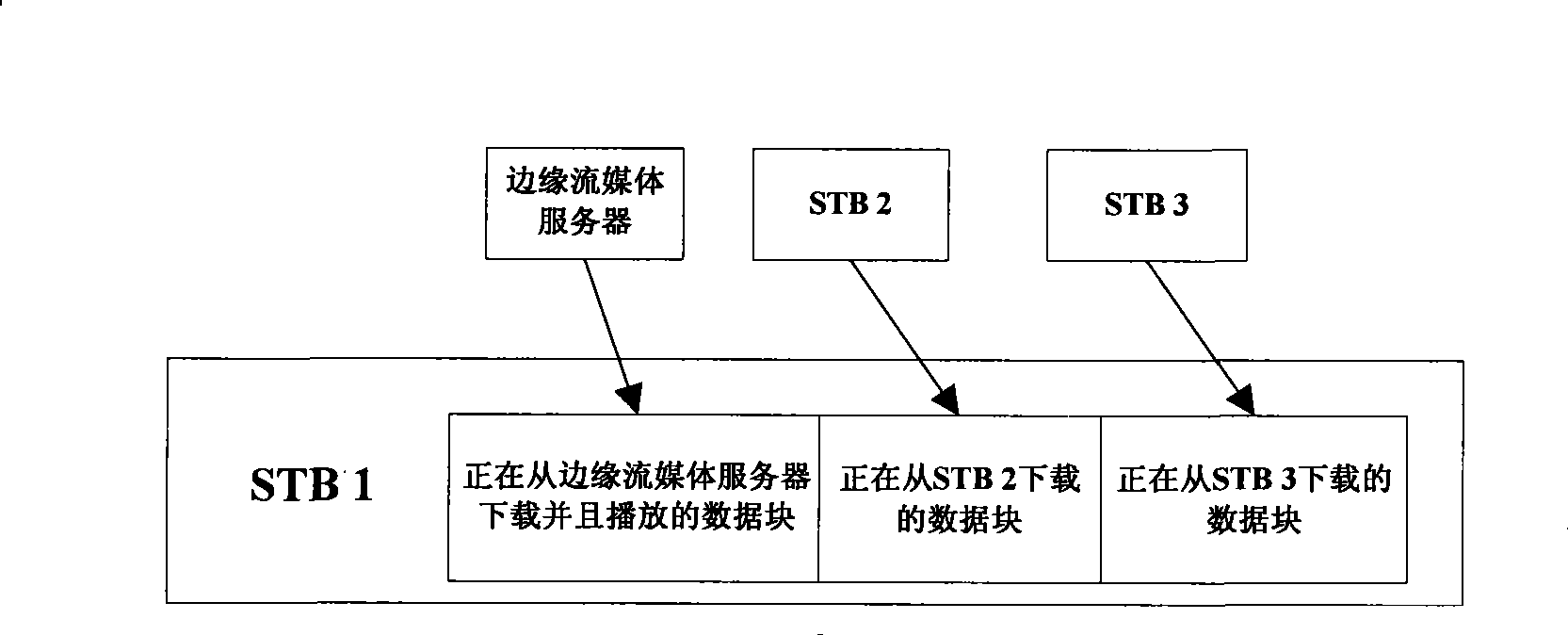
InactiveCN101378494ARelieve pressureImprove service qualityAnalogue secracy/subscription systemsTwo-way working systemsContent distributionQuality of service
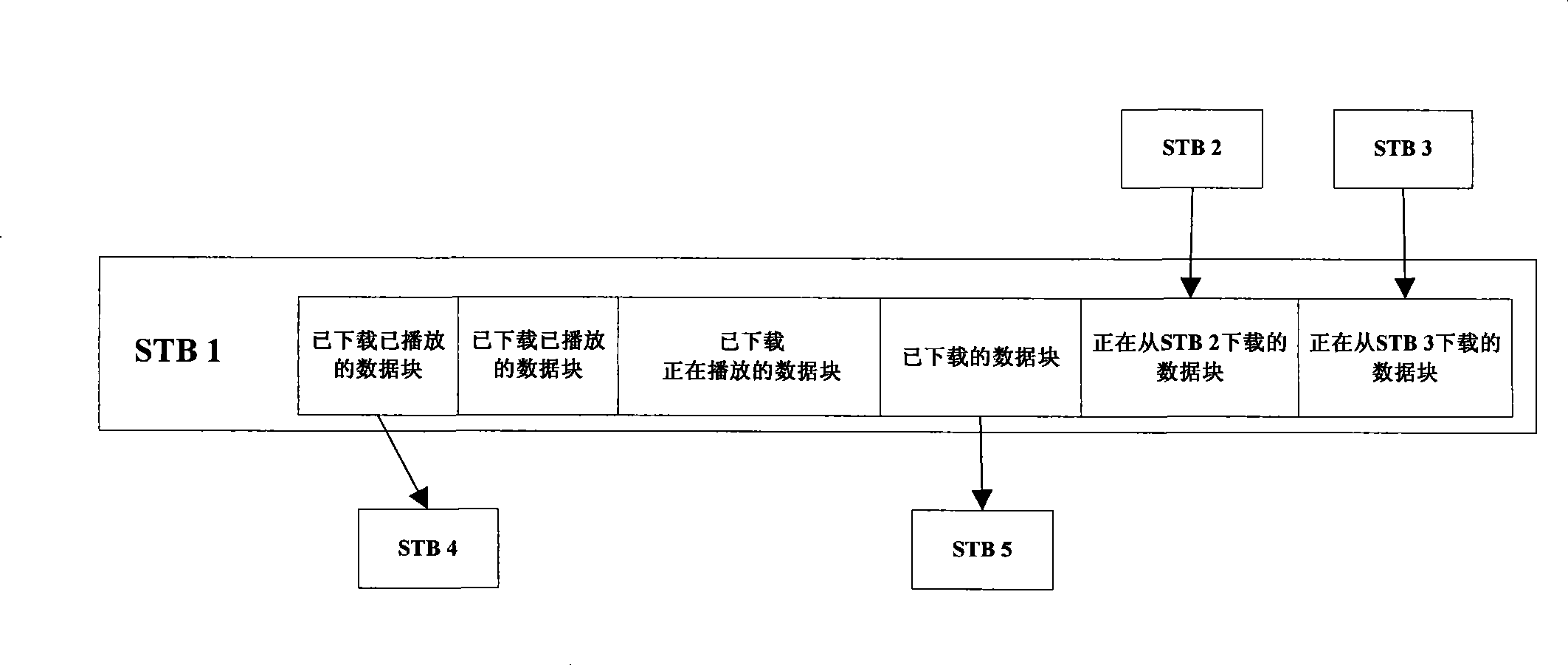
The invention discloses a method and a system to realize the interaction between the Internet and TV media, wherein, the method comprises that a user terminal sends a request of time-shift TV media files for videoing on demand, recorded broadcasting or live broadcasting to a marginal streaming media server of a point-to-point domain of the margin where the user terminal is located; the marginal streaming media to which the request is sent sends a first block of data of a target media file to the user terminal; after receiving the first block of data of the target media file, the user terminal starts immediately to play the first block of data of the media file and simultaneously requests the tables of node information which can provide the subsequent data blocks of the target media file from a content distribution network agent in the point-to-point domain of the terminal side where the user terminal is located; the content distribution network agent sends back the node information table which can provide the subsequent data blocks; and the user terminal requests to download and play the subsequent data blocks of the target storage file. The method and the system of the invention have the advantages of high service quality and being capable of reducing the load of a central streaming media server and the marginal streaming media server and reducing the construction cost.
Owner:ZTE CORP
Micro-service engine based on proxy mode
ActiveCN109981789AImprove development efficiencyReduce operation and maintenance costsData switching networksNetwork agentDistributed computing
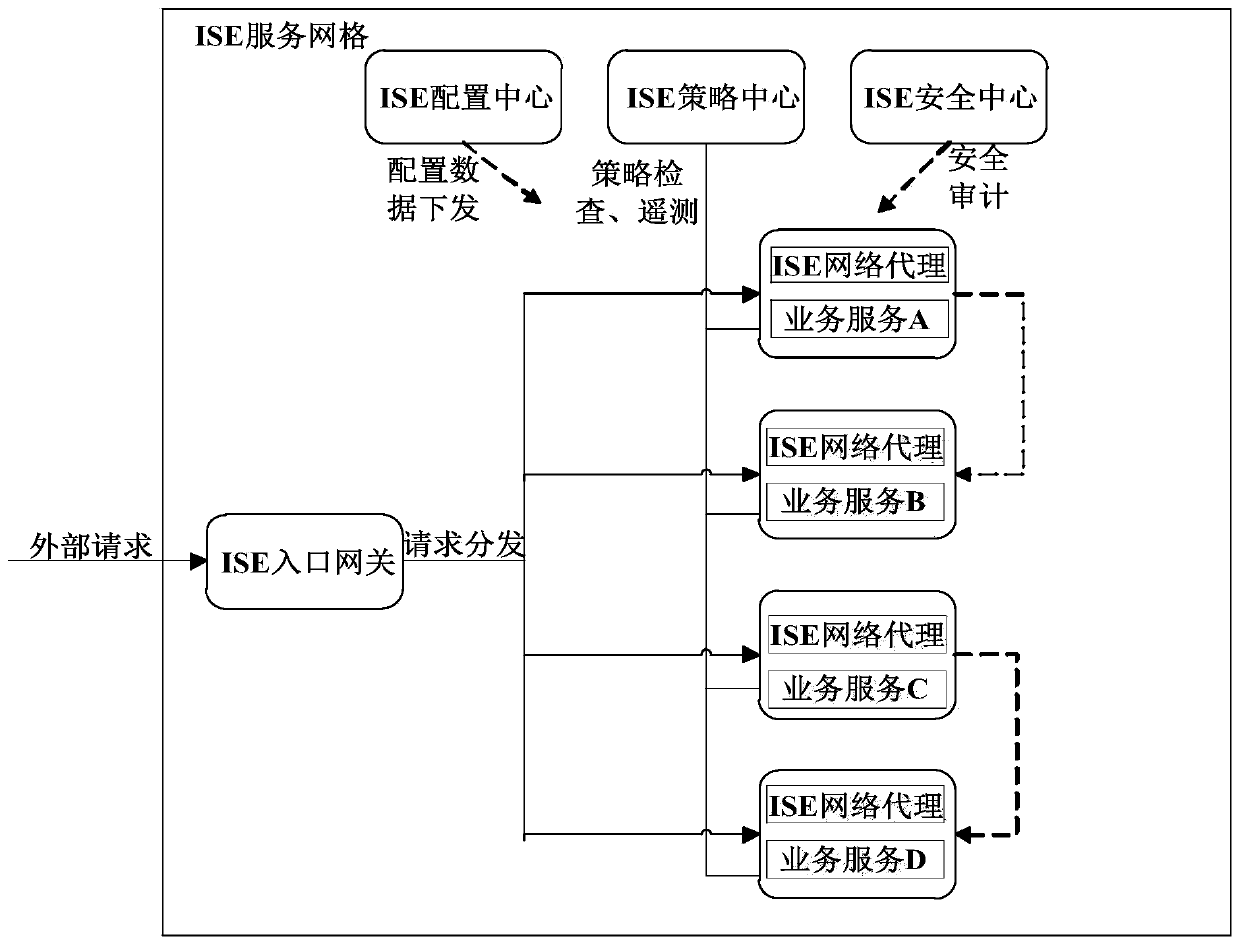
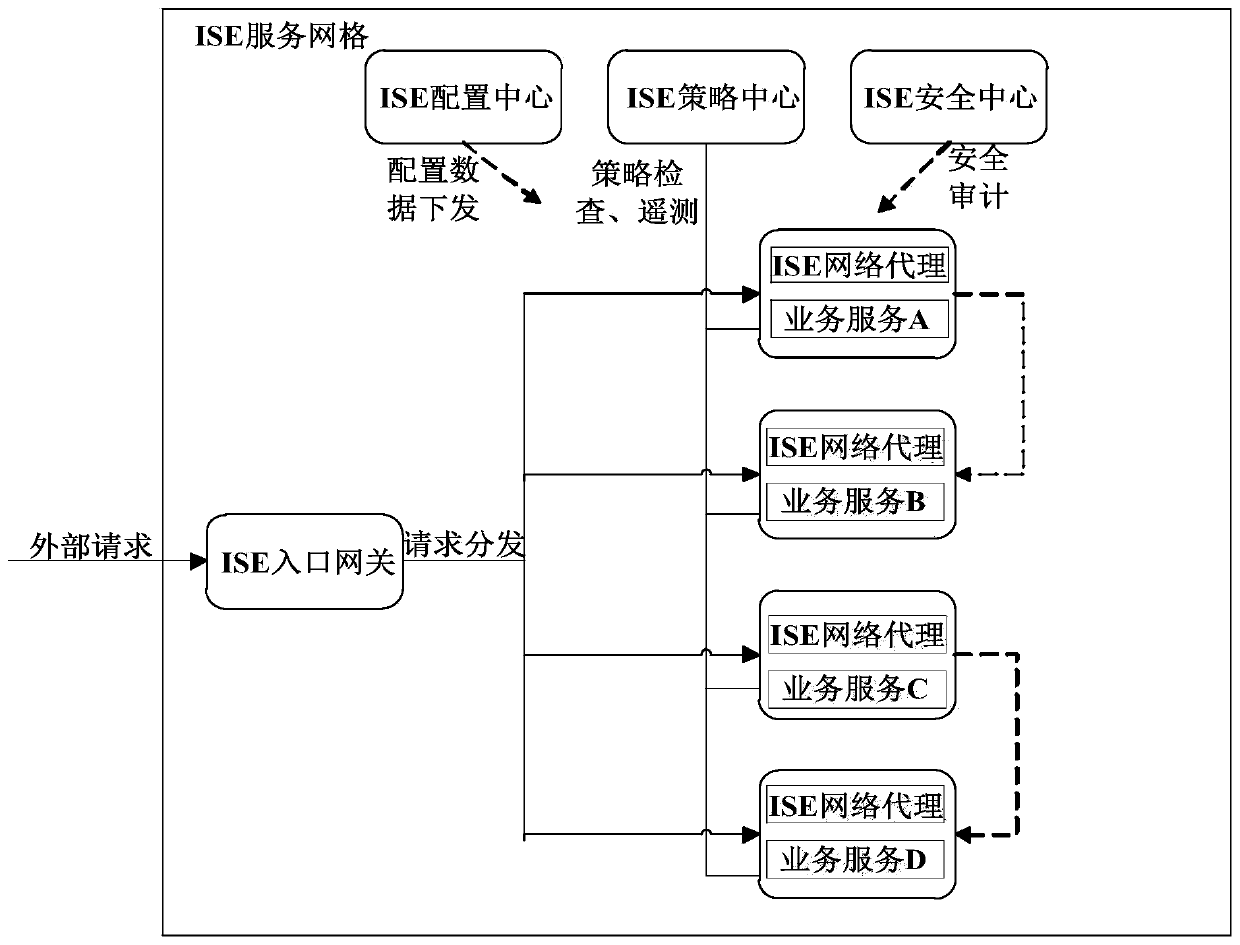
The invention particularly relates to a micro-service engine based on a proxy mode. The micro-service engine based on an proxy mode establishes an ISE service grid for deployed business services, andthe ISE service grid comprises an ISE entrance gateway, an ISE network agent, an ISE strategy center, an ISE configuration center and an ISE security center; and an external request is received through the ISE entrance gateway, and the external request is issued to the business service through the ISE network agent. According to the micro-service engine based on the proxy mode, the ISE network proxy is used for uniformly forwarding the communication flow of the micro-service application in a proxy manner, so that the problems of communication routing, flow control, fusing, safety, performancedata collection and the like among the micro-service applications are well solved, the development efficiency of the applications is improved, and the operation and maintenance cost is reduced.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Machine-to-machine gateway architecture and functionality
Owner:DRNC HLDG INC
Cloud computing system and control method thereof
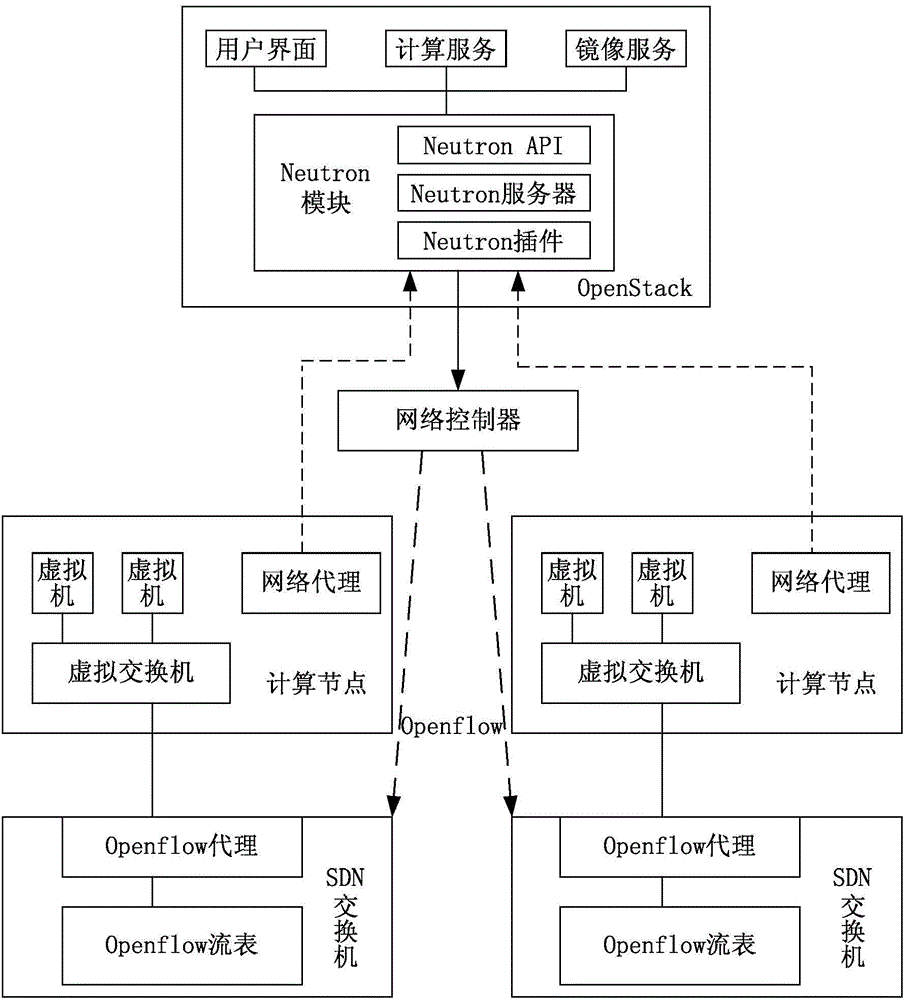
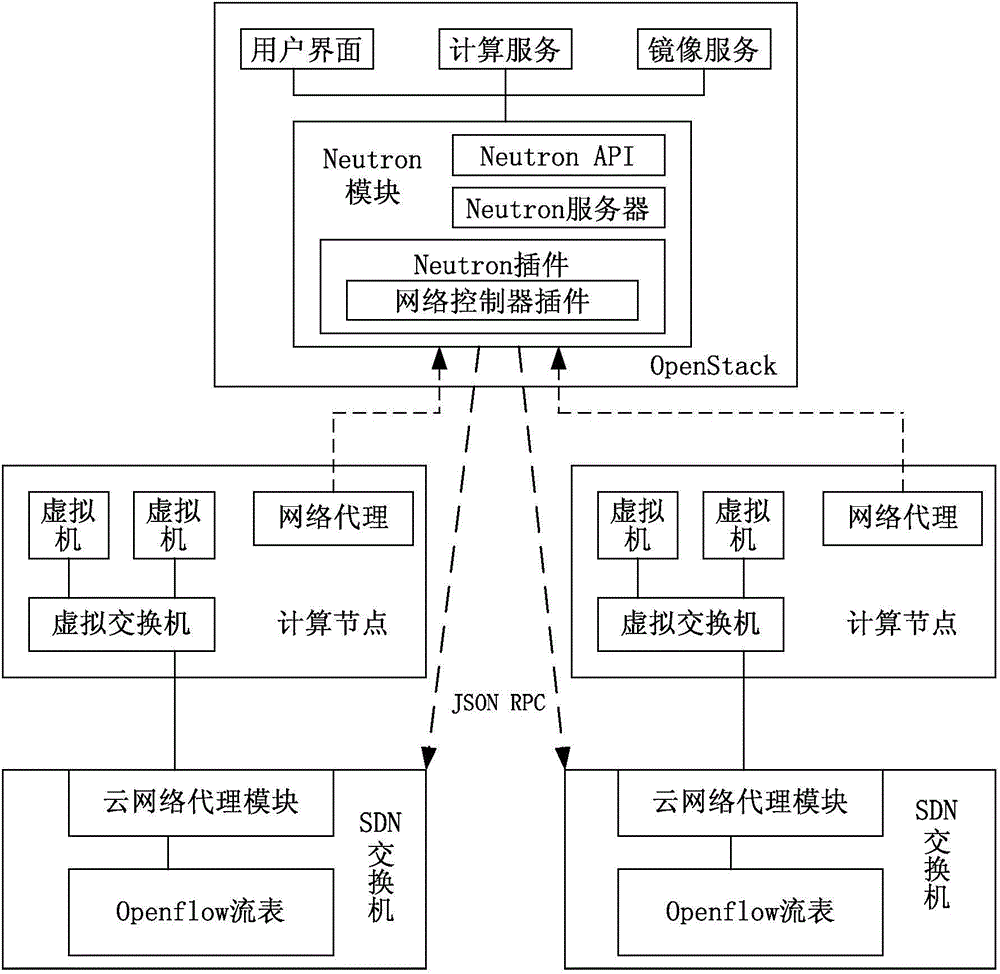
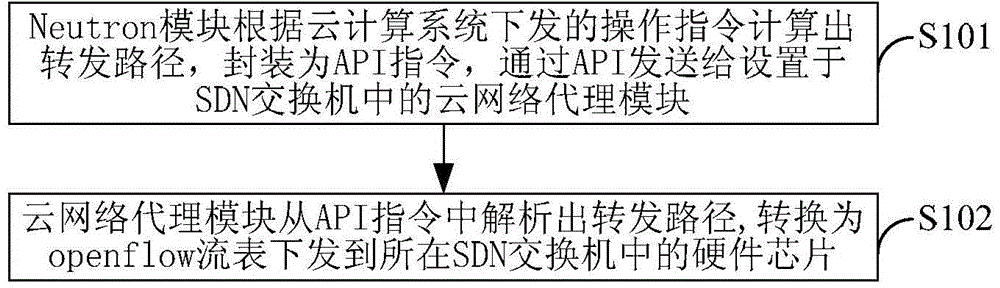
The invention discloses a cloud computing system and a control method thereof. The cloud computing system comprises a Neutron module arranged in an OpenStack management platform, a cloud network agent module arranged in a software-defined network (SDN) switch, and a hardware chip used for converting the forwarding path into an openflow table and issuing the openflow table into the SDN switch, wherein the Neutron module is used for computing a forwarding path according to an operation instruction issued by the cloud computing system and packaging the forwarding path into an application program interface (API) instruction, and sending the API instruction to the cloud network agent module by virtue of an API; the cloud network agent module is used for analyzing the forwarding path from the API instruction. According to the cloud computing system, the building cost of the OpenStack-based cloud computing system can be lowered, and the performance of the SDN switch is fully utilized.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Distributed networking agent and method of making and using the same
InactiveUS7742436B2Easy to useNetwork traffic/resource managementConnection managementCommunications systemNetwork agent
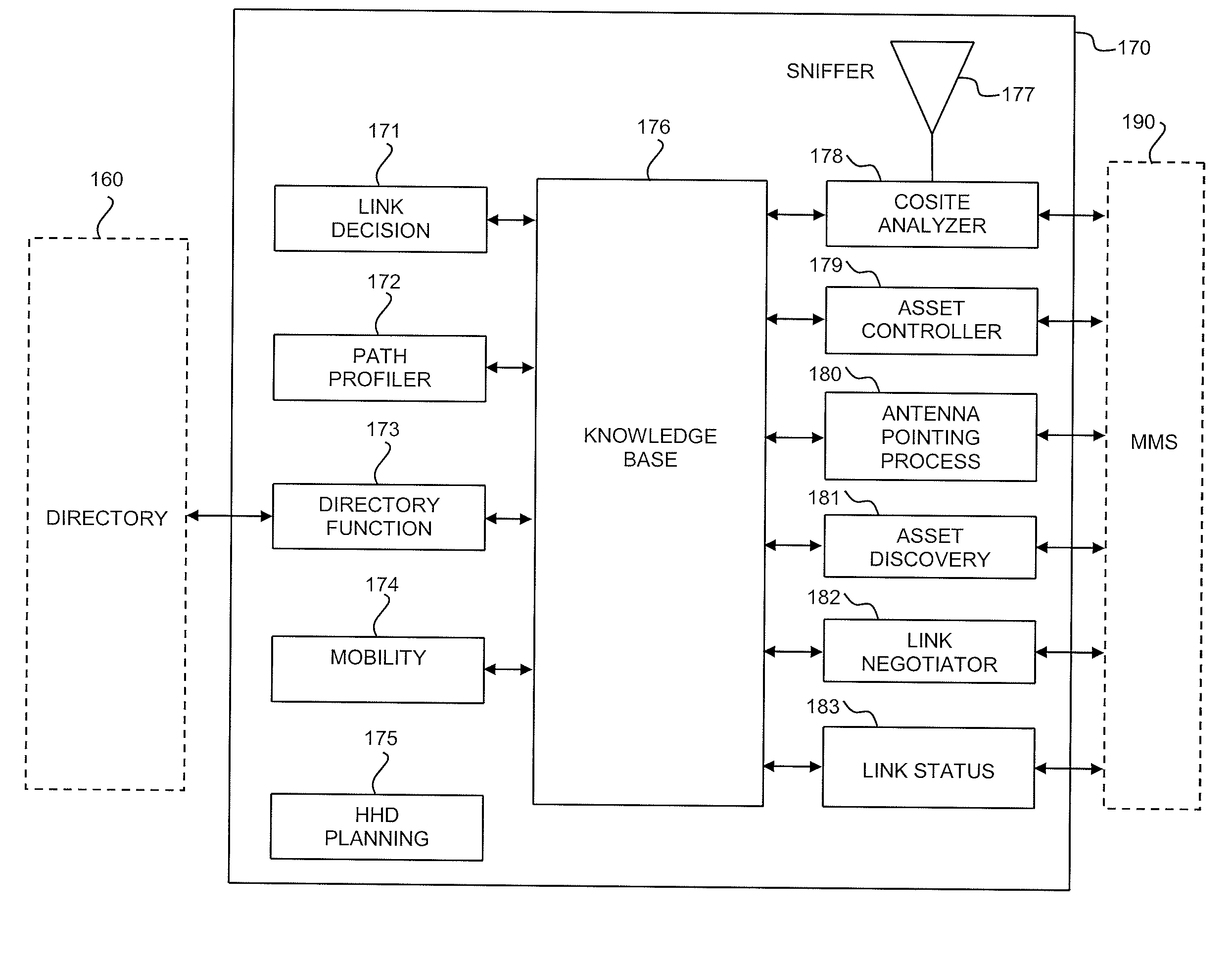
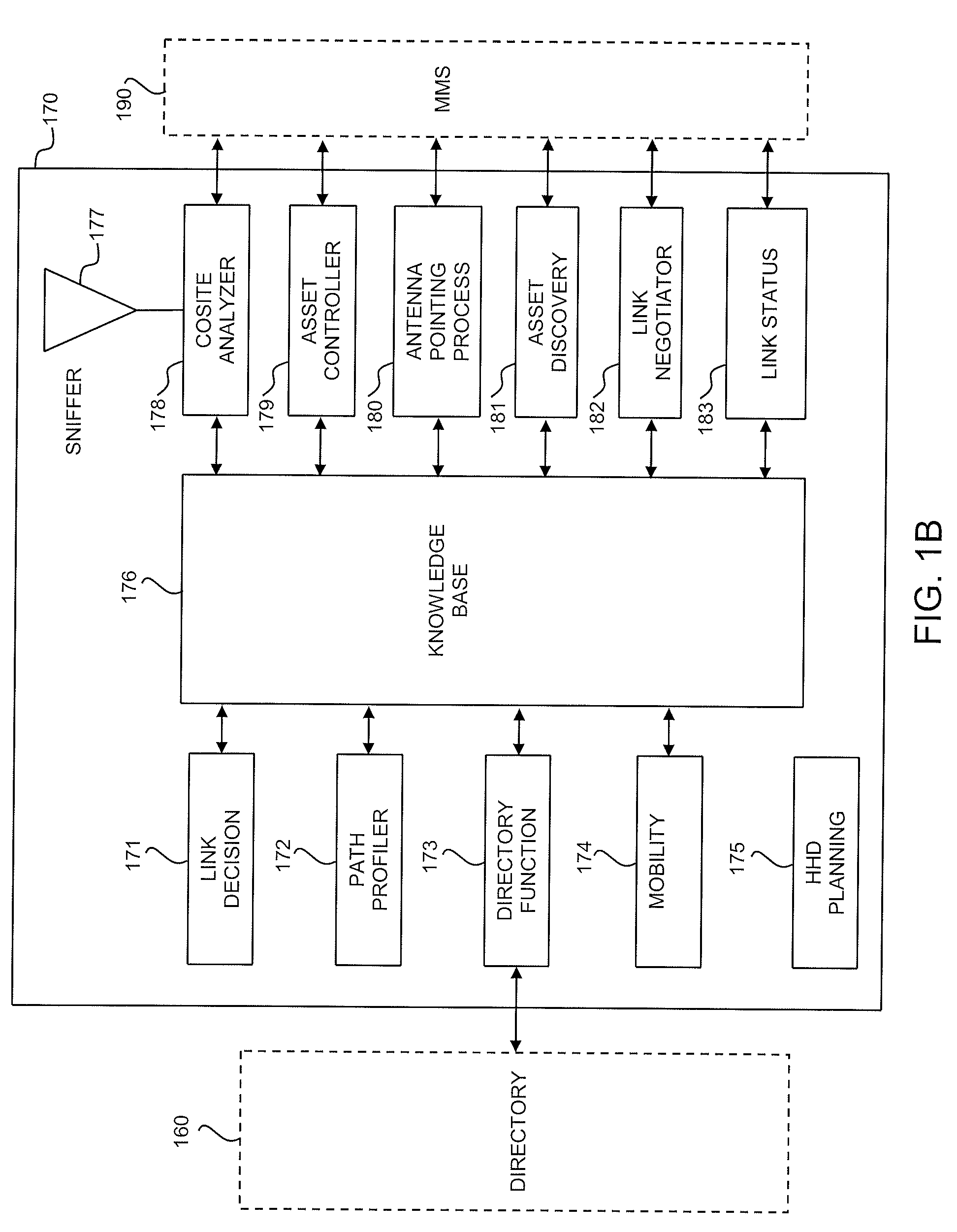
The present invention relates to an agent for distributed networking and a processor-readable software code. The agent may include, for example, a cosite analyzer, an EMI sniffer, an asset controller module, an asset discovery module, and a link negotiator. The agent may be configured to initiate and optimize network configurations for radio communications systems based on parameters. The software code may receive data associated with a network plan, may determine if any planned links are included in the network plan and may establish connectivity of a confirmed link between at least two nodes in the network. Additionally, the software code may determine if a non-planned link should be added to the network and may establish connectivity for the non-planned link based on a priority associated with the non-planned link.
Owner:GENERAL DYNAMICS MISSION SYST INC
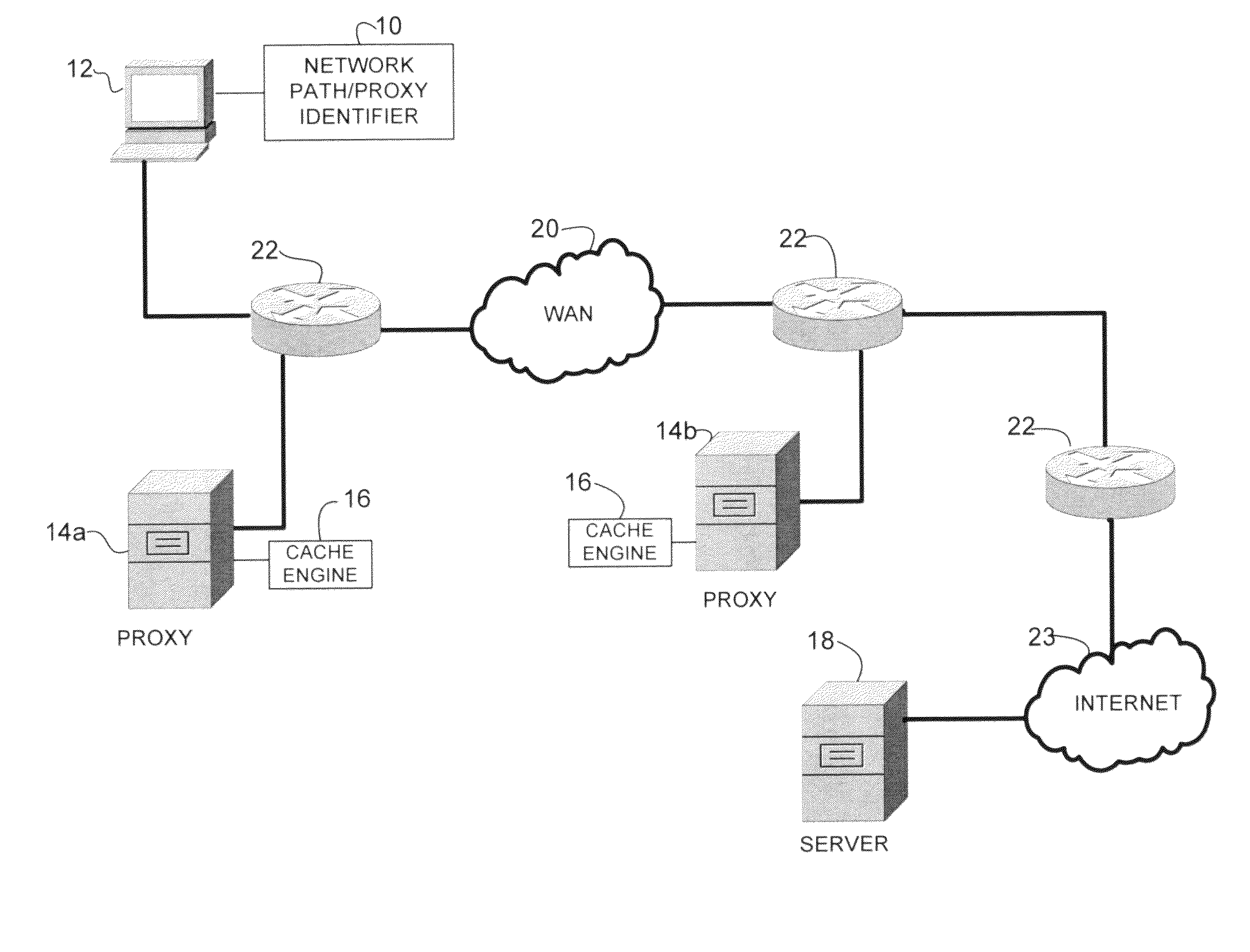
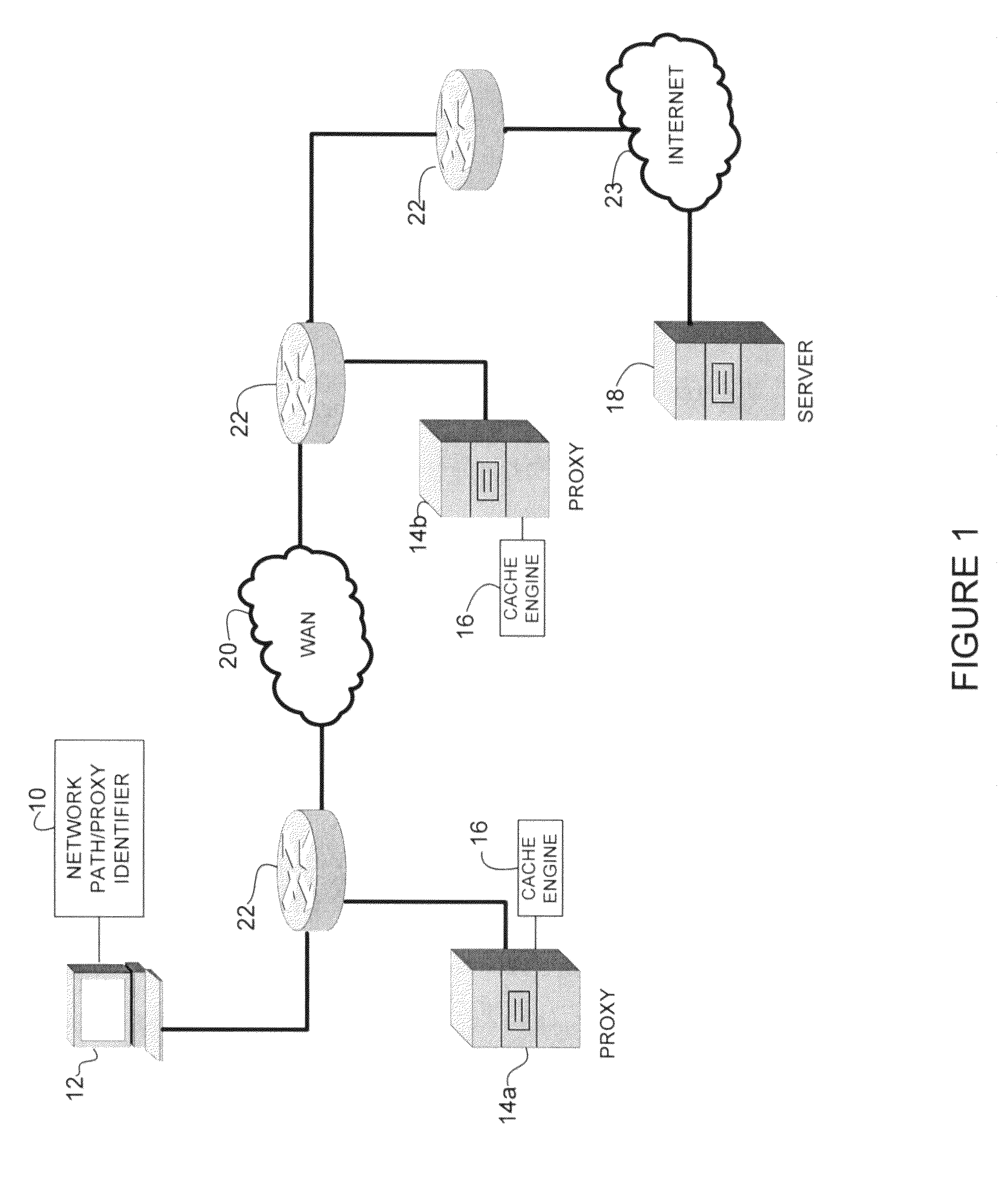
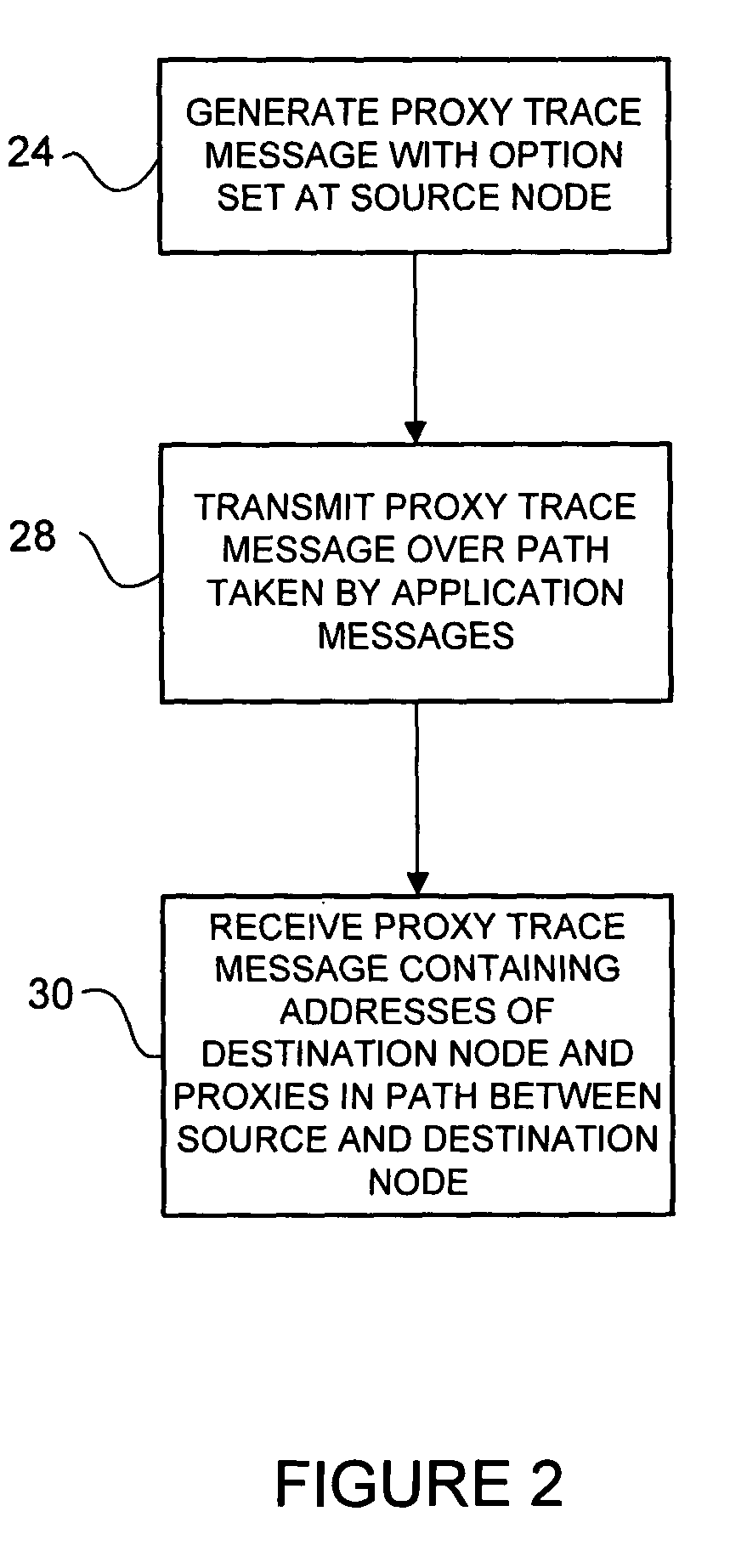
Identifying network path including network proxies
A method and system for identifying a network path between a source node and a destination node are disclosed. In one embodiment, the method includes generating a proxy trace message at the source node, transmitting the proxy trace message over the network path towards the destination node, and receiving the proxy trace message at the source node. The proxy trace message follows a path taken by application messages transmitted by the source node and the received proxy trace message includes addresses of the destination node and proxies in the network path.
Owner:CISCO TECH INC
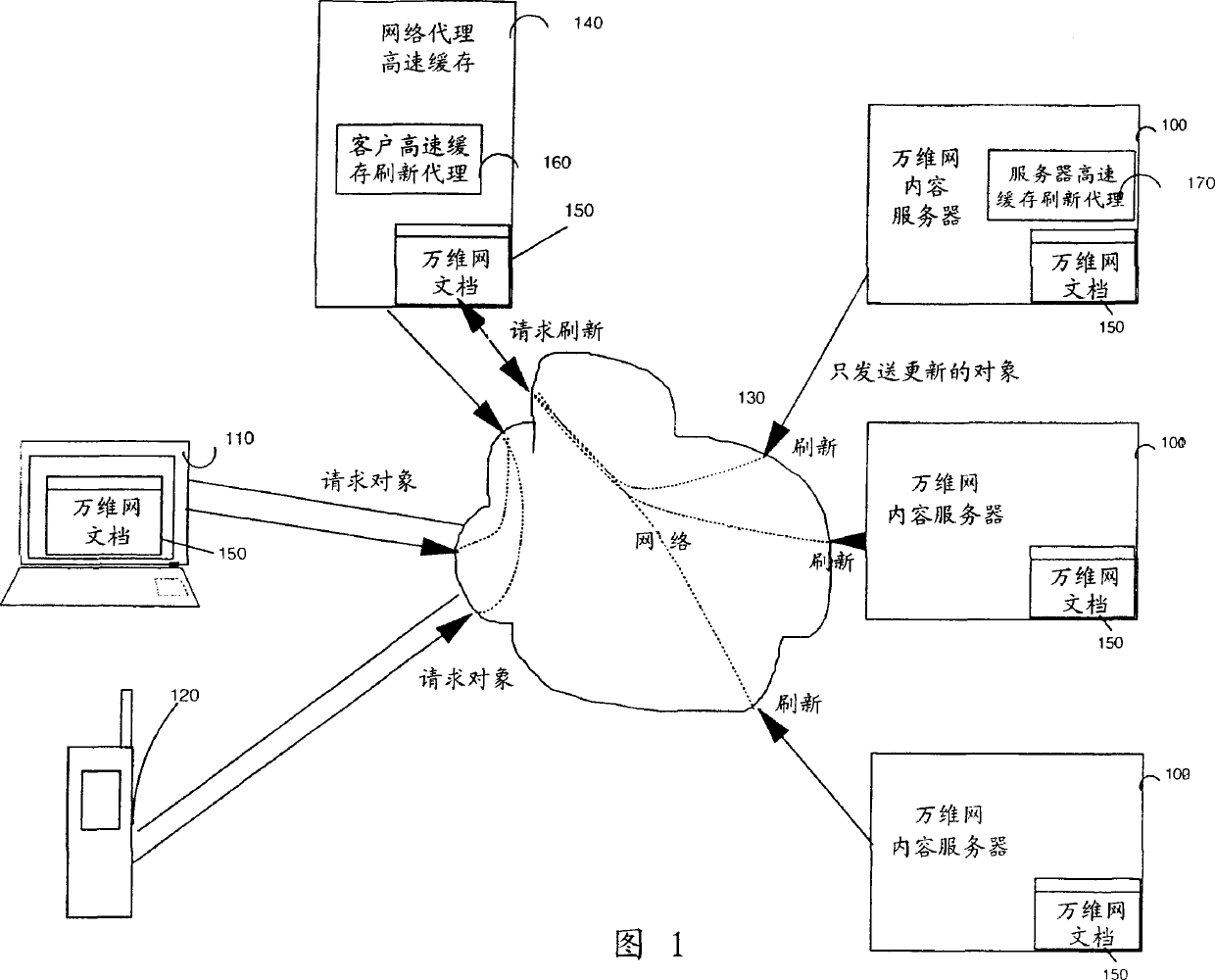
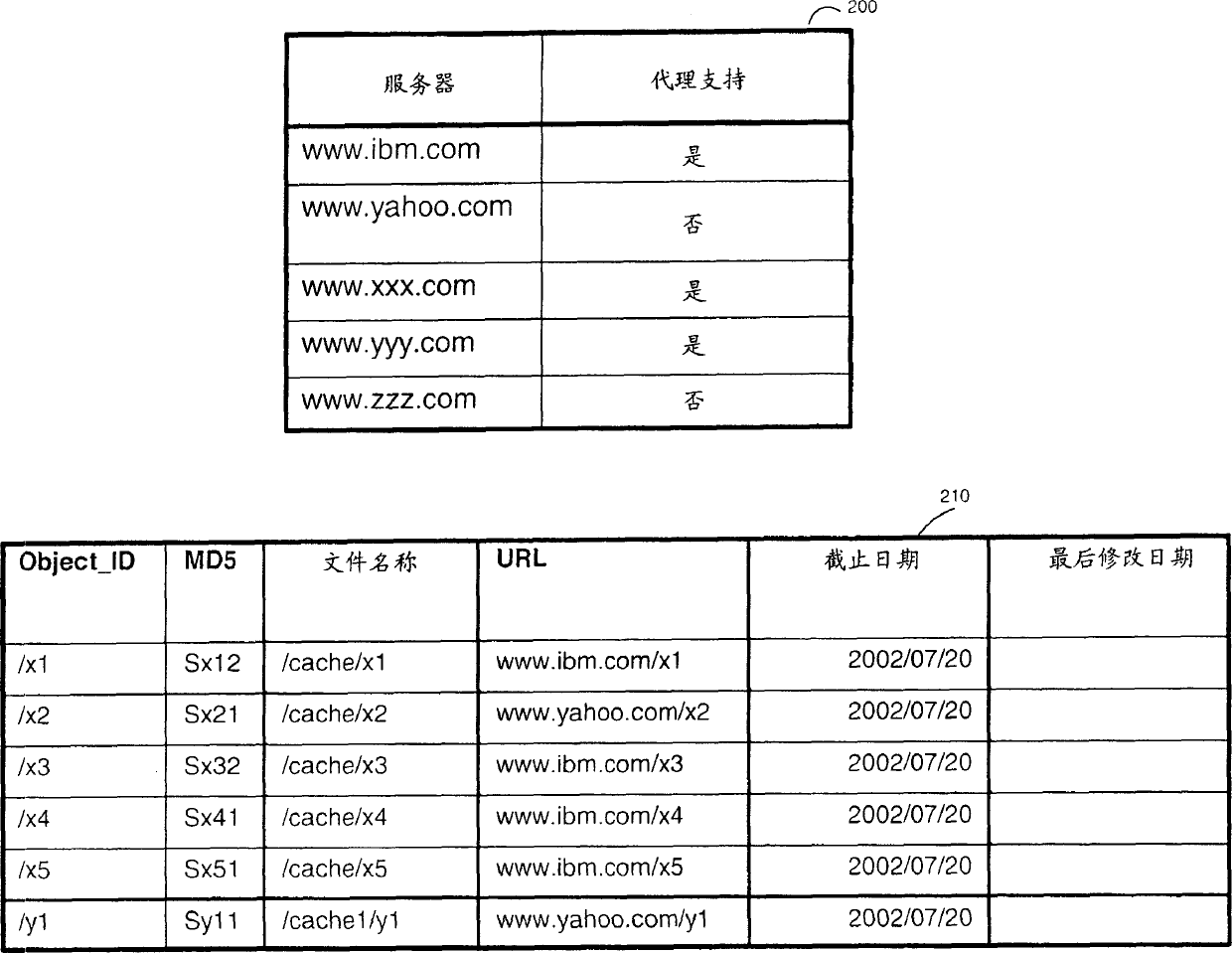
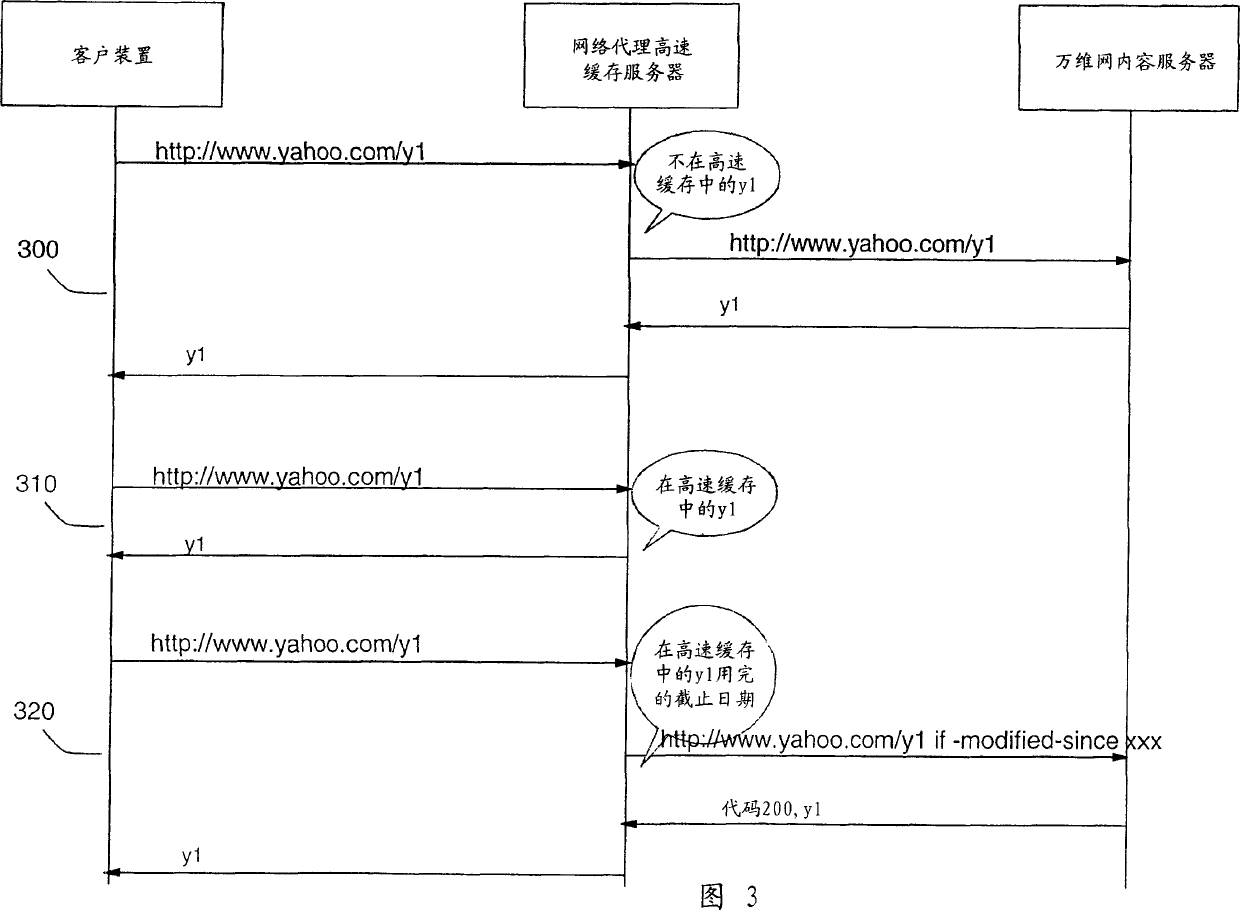
System and method for updating network proxy cache server object
InactiveCN1484155AReduce data volumeReduce businessSpecial data processing applicationsSecuring communicationNetwork agentCache server
A method and computing systems for refreshing objects stored by a Proxy cache server from Web content servers. The refresh is requested by the Proxy cache server only if the expiration date attached to a stored object has expired. The refresh of one object is requested by the Proxy cache server to the Web content server upon a request from the browser of a client device. Additionally, the Proxy cache server can send a Refresh_request command to the Web content servers applying to a list of objects for which the expiration date has expired. The refreshed objects are not sent by the Web content server if the last modified date has changed but rather if, and only if, the object content, identified by a signature, has been changed. This method and system have the advantage of offloading the computing resources involved for data transfer through the network connecting the servers.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com